Method and system for obtaining target password rule set in exhaustion-method decryption
An acquisition method and technology of exhaustive method, applied in the field of target password rule set acquisition in exhaustive method decryption, can solve problems such as low efficiency, achieve the effect of improving efficiency and reducing the number of attempted passwords
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
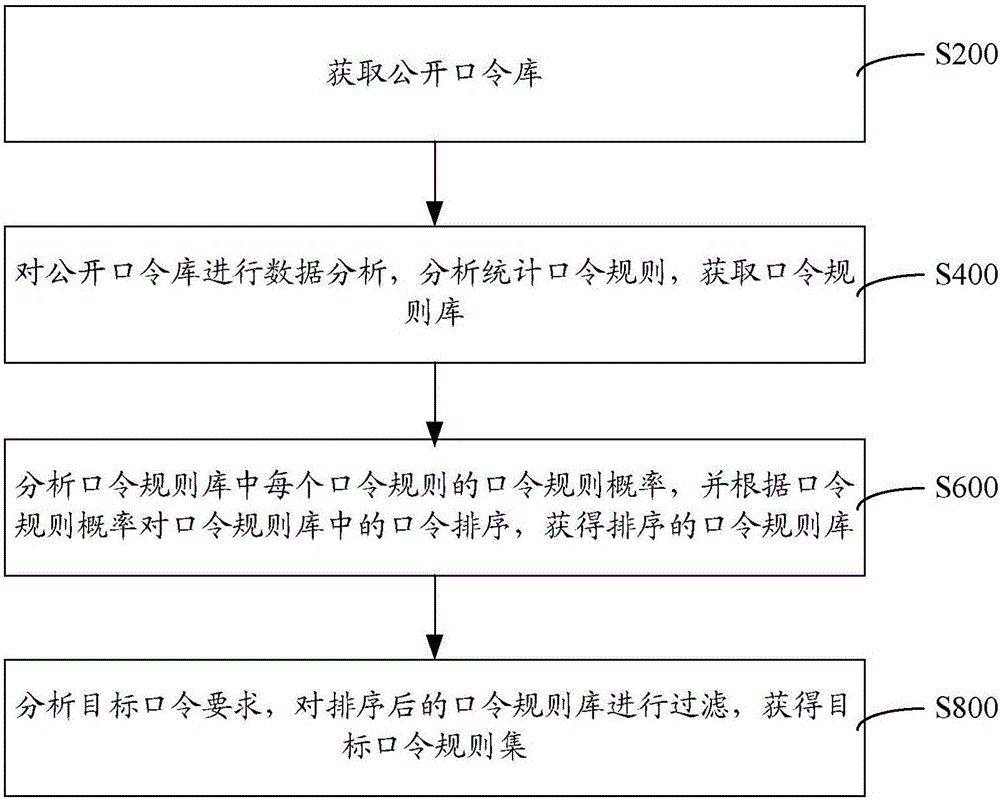
[0023] like figure 1 As shown, a method for obtaining the target password rule set in the exhaustive method decryption, including steps:
[0024] S200: Obtain a public password database.
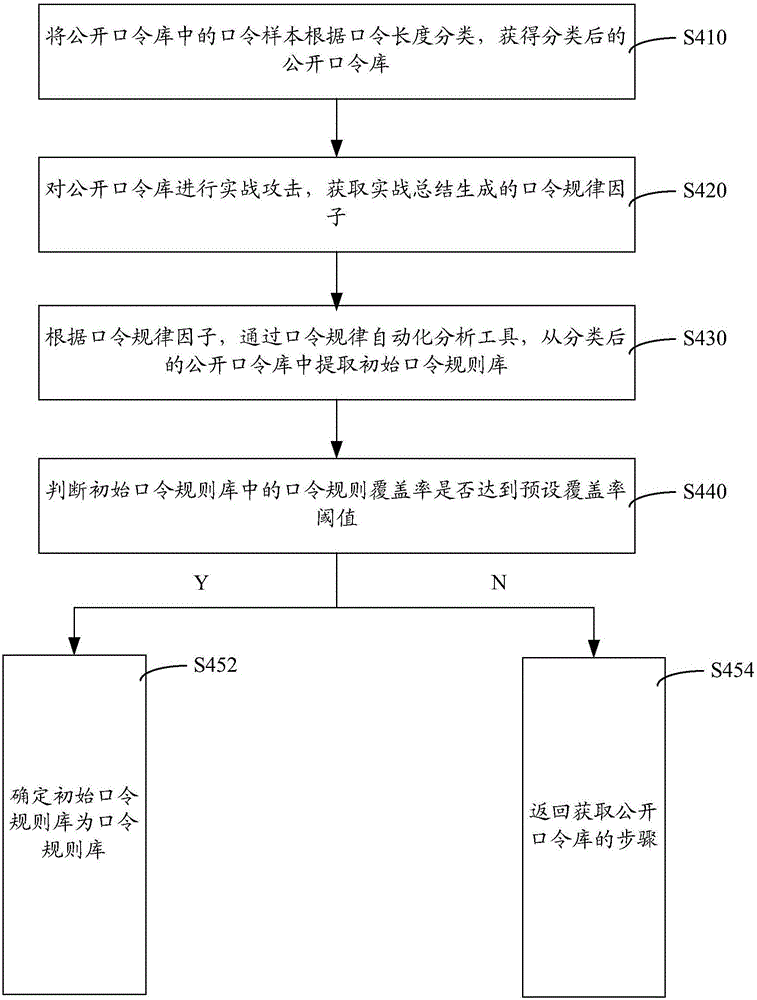
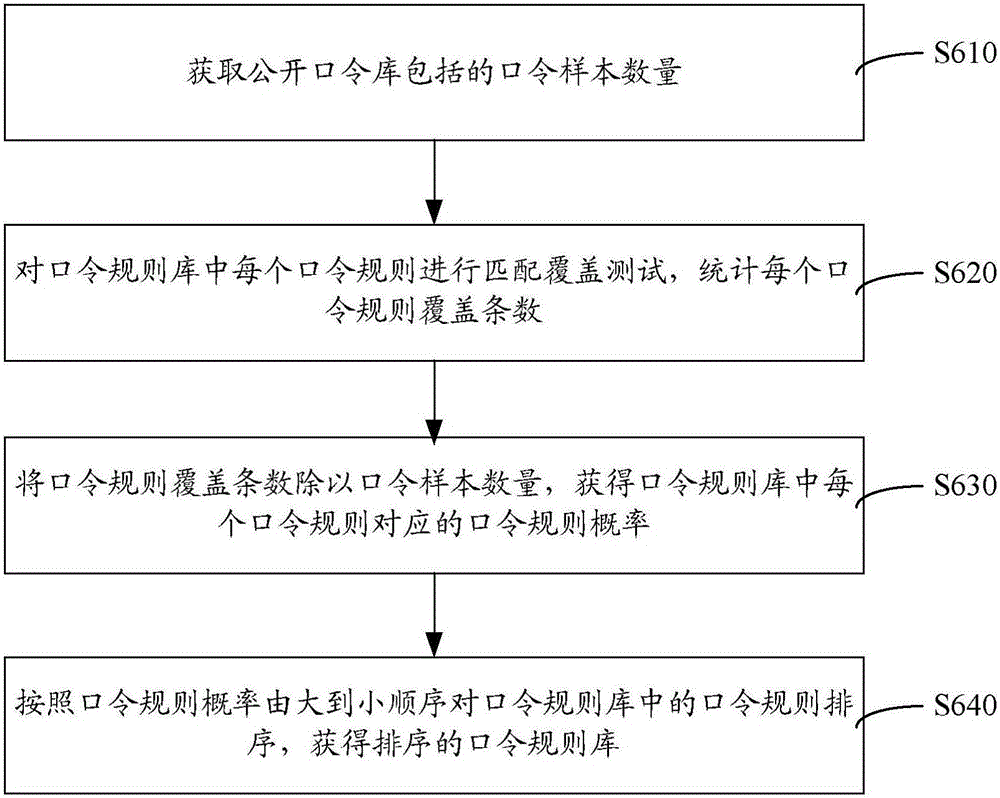
[0025] The public password database can be obtained based on historical experience data, for example, by making full use of big data, cloud data, and the Internet, passwords formed in different parts of the world, different regions, different countries, different nationalities, and different cultural backgrounds can be obtained. Specifically, a preliminary classification and analysis of the public password database can also be carried out here, specifically, the public passwords can be classified according to regions, and the public passwords can be classified according to languages. More specifically, the public password database can include the domestic 163 mailbox database, csdn forum database, Tianya forum database, qq account database, weibo account database, foreign yahoo mailbox data...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com