Method for scheduling decryption machines
A decryption machine and ciphertext technology, which is applied in the inspection of the authenticity of banknotes, processing coins or valuable banknotes, instruments, etc. The effect of utilization efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
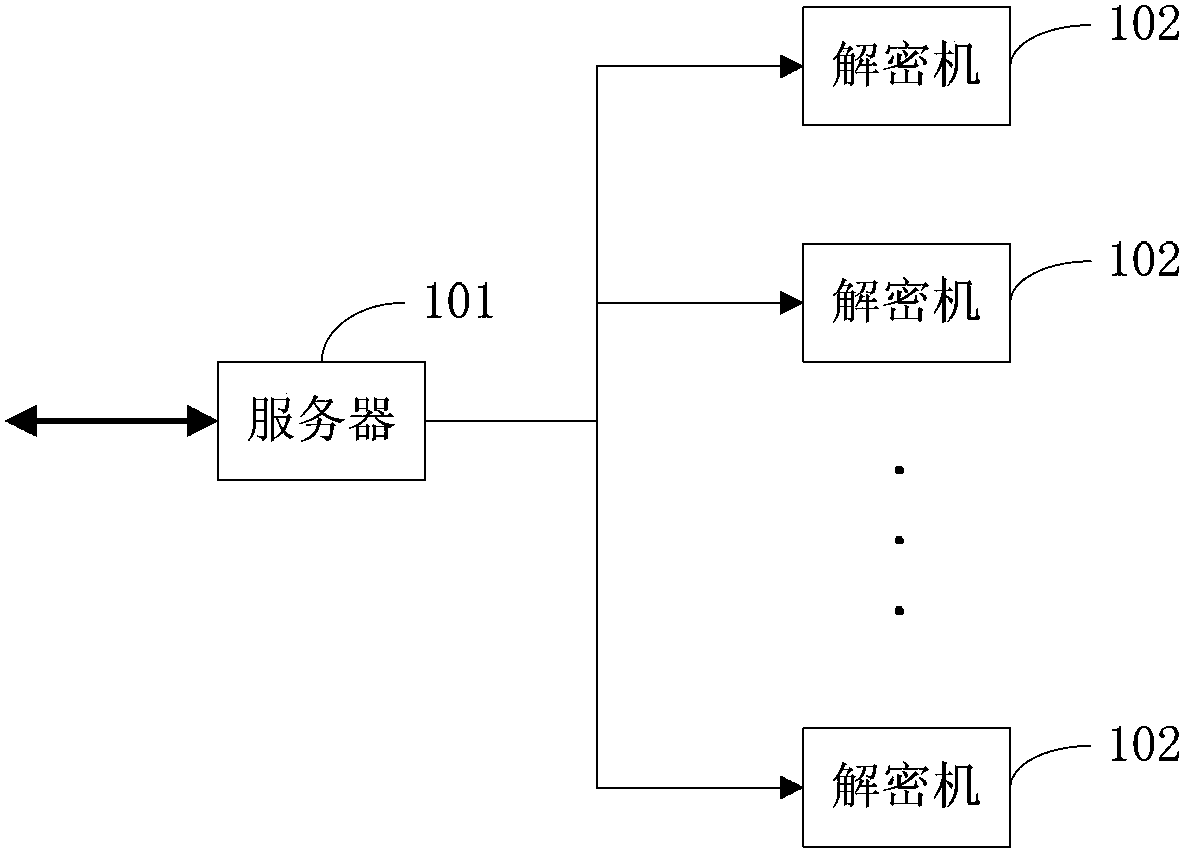
[0068] Set a digital code for each decryption machine, so that the decryption machine and the digital code have a one-to-one correspondence;
[0069] Then in step 2, the method for the server to select one decryption machine from all the decryption machines whose working status is idle as the specified decryption machine is: the server judges whether the number of decryption machines whose working status is idle is one, and if so, then the working status The decryption machine that is idle is the designated decryption machine, otherwise, the decryption machine corresponding to the smallest digital code among all the decryption machines whose working status is idle is the designated decryption machine.
[0070] It can be seen that this embodiment is relatively simple. When the number of decryption machines whose working status is idle exceeds one, the server only needs to compare the numbers of the decryption machines to quickly determine the designated decryption machine.
specific Embodiment 2
[0071] In addition to the working status of all decryption machines, the decryption machine working status table also includes the IP addresses of all decryption machines;
[0072] In this way, in step 2, the method for the server to select one of all decryption machines whose working status is idle as the specified decryption machine is: the server judges whether the number of decrypting machines whose working status is idle is one, and if so, then the working status Use an idle decryption machine as the designated decryption machine, otherwise, perform step 2-1, step 2-2 and step 2-3 in sequence;
[0073] Step 2-1: The server determines the IP addresses of all decryption machines whose working status is idle;
[0074] Step 2-2: The server queries the decryption machine load balancing table according to the IP addresses of all decrypting machines whose working status is idle, and determines the cumulative number of tasks of all decrypting machines whose working status is idle...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com