Magic cube encryption and decryption method
An encryption method, Rubik's cube technology, applied in the direction of digital transmission system, electrical components, transmission system, etc., to achieve the effect of fast decryption speed, high dependence, and strong encryption strength
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
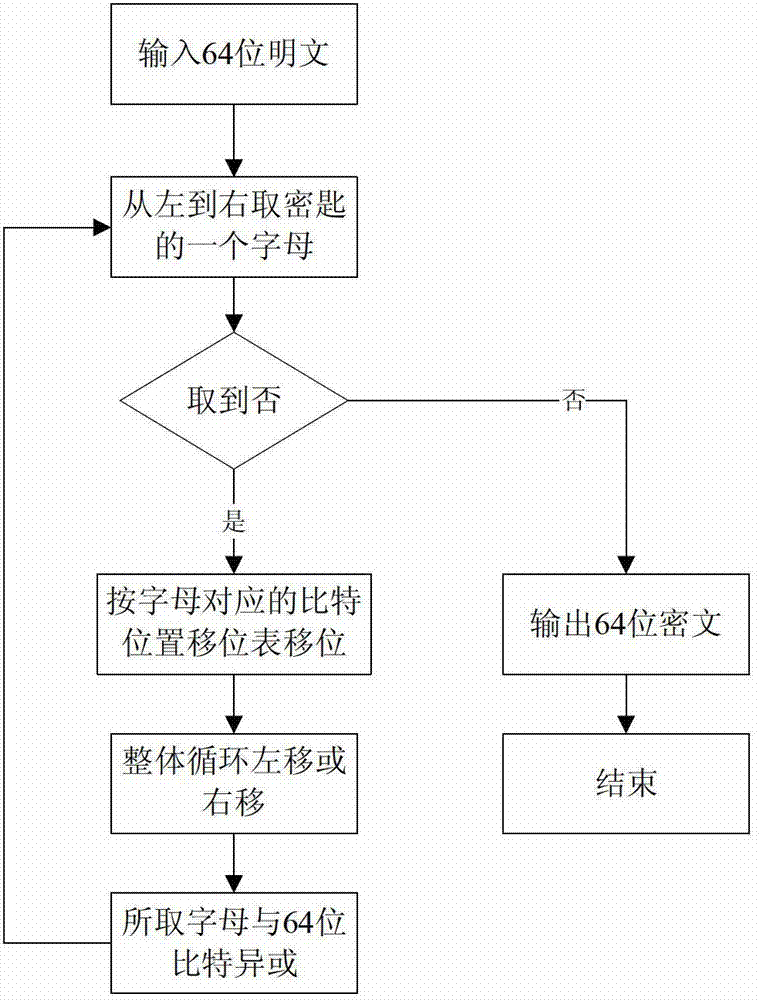
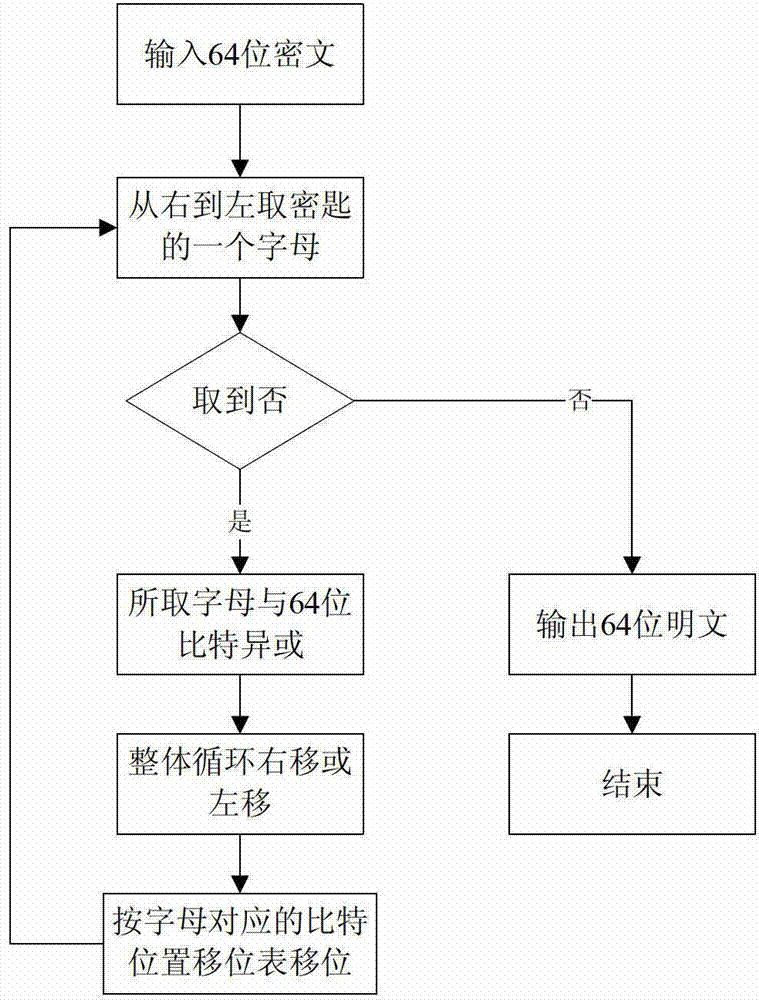
[0043] Plaintext: abcdefgh
[0044] Key: 12345
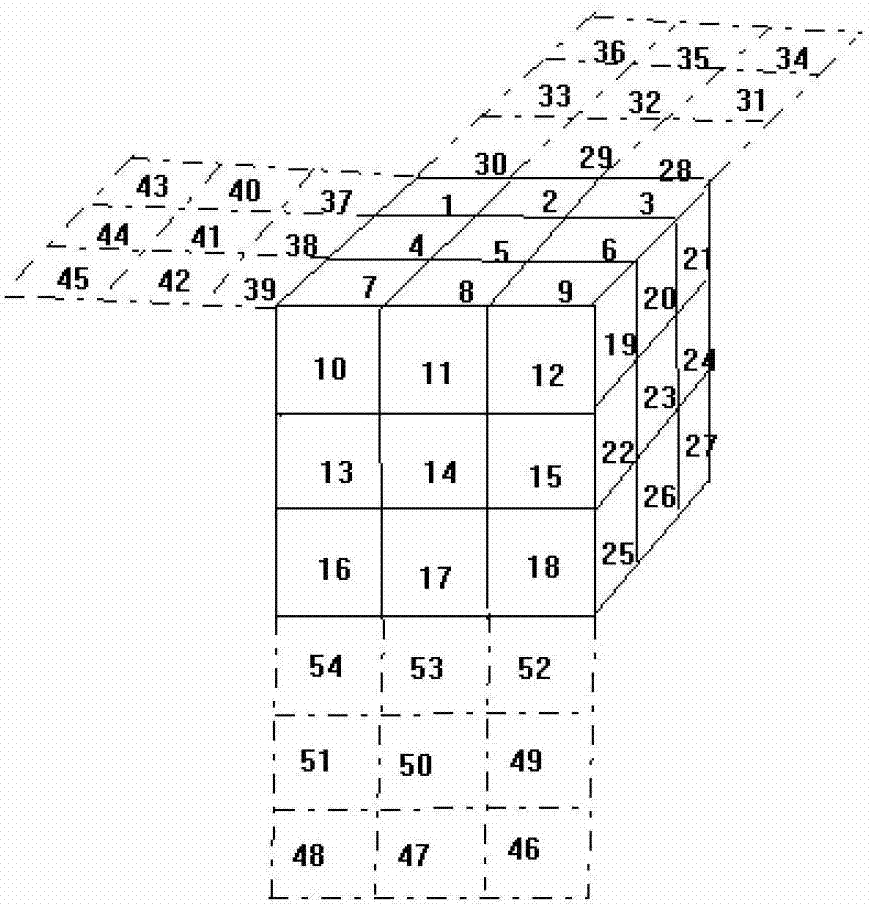
[0045] 1) In this example, the plaintext is 8 bytes (that is, 64 bits), and segmentation processing is not required. Plaintext binary such as Figure 4 a means:
[0046] 2) By querying Table 2 and Table 1, the Rubik's Cube transposition rules for the characters "1", "2", "3", "4" and "5" that make up the key are respectively obtained.
[0047] 3) Take the first character "1" of the key from left to right, and transpose the plaintext according to the Rubik's Cube transposition rule for the character "1".
[0048] Specifically, the transposition rules for the character "1" are:
[0049] Such as Figure 4 As shown in b, the first group transposes: the 3rd place is changed to the 34th place, the 34th place is changed to the 52nd place, the 52nd place is changed to the 12th place, and the 12th place is changed to the 3rd place.
[0050] The second set of transpositions: 6th to 31st, 31st to 49th, 49th to 15th, 15th to 6th.
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com