High-capacity image steganography method and a secret information extraction method
A secret information and large-capacity technology, applied in the field of large-capacity image steganography and secret information extraction, can solve the problems of small embedded information, complex extraction, and easy detection of hidden algorithms
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
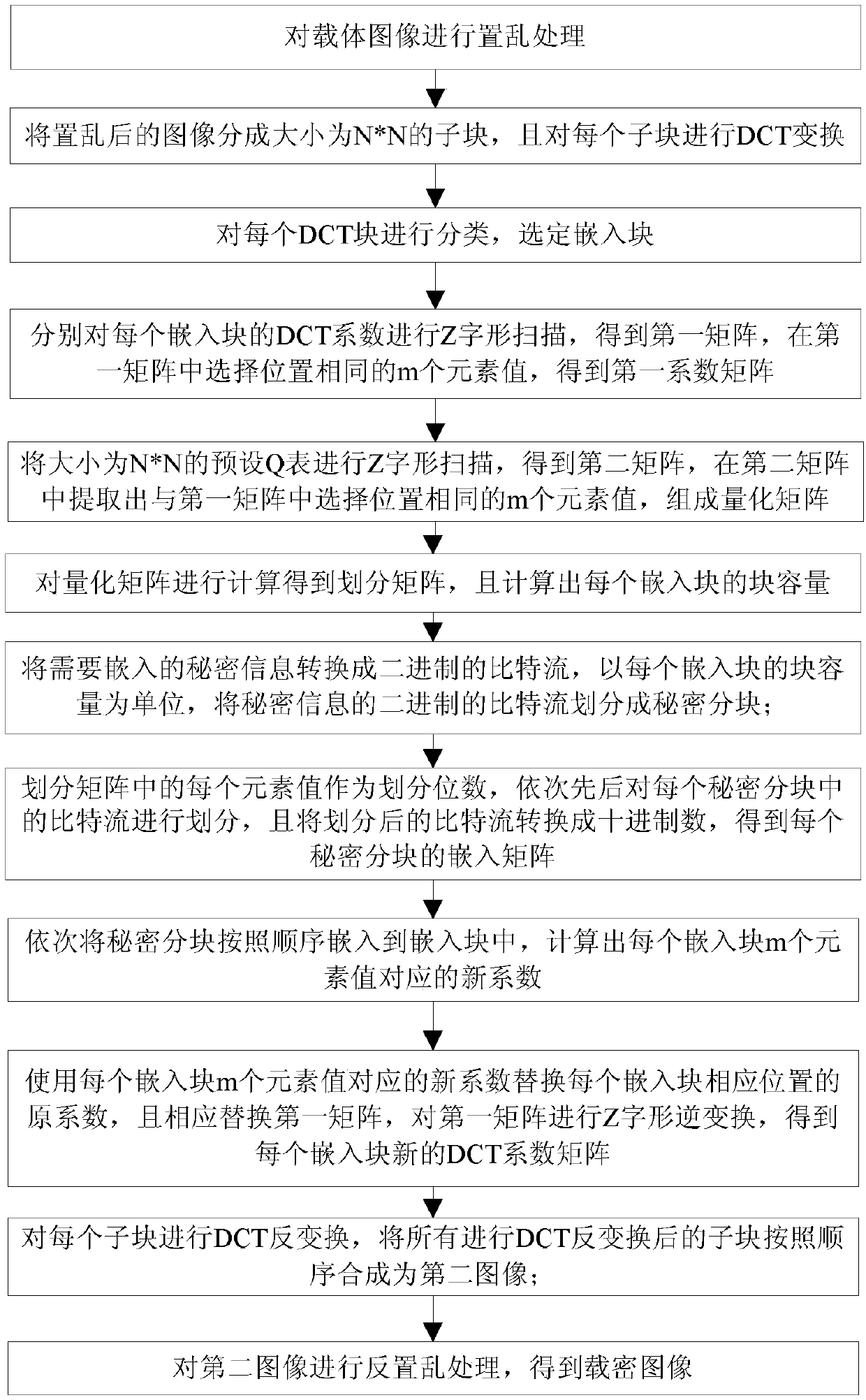
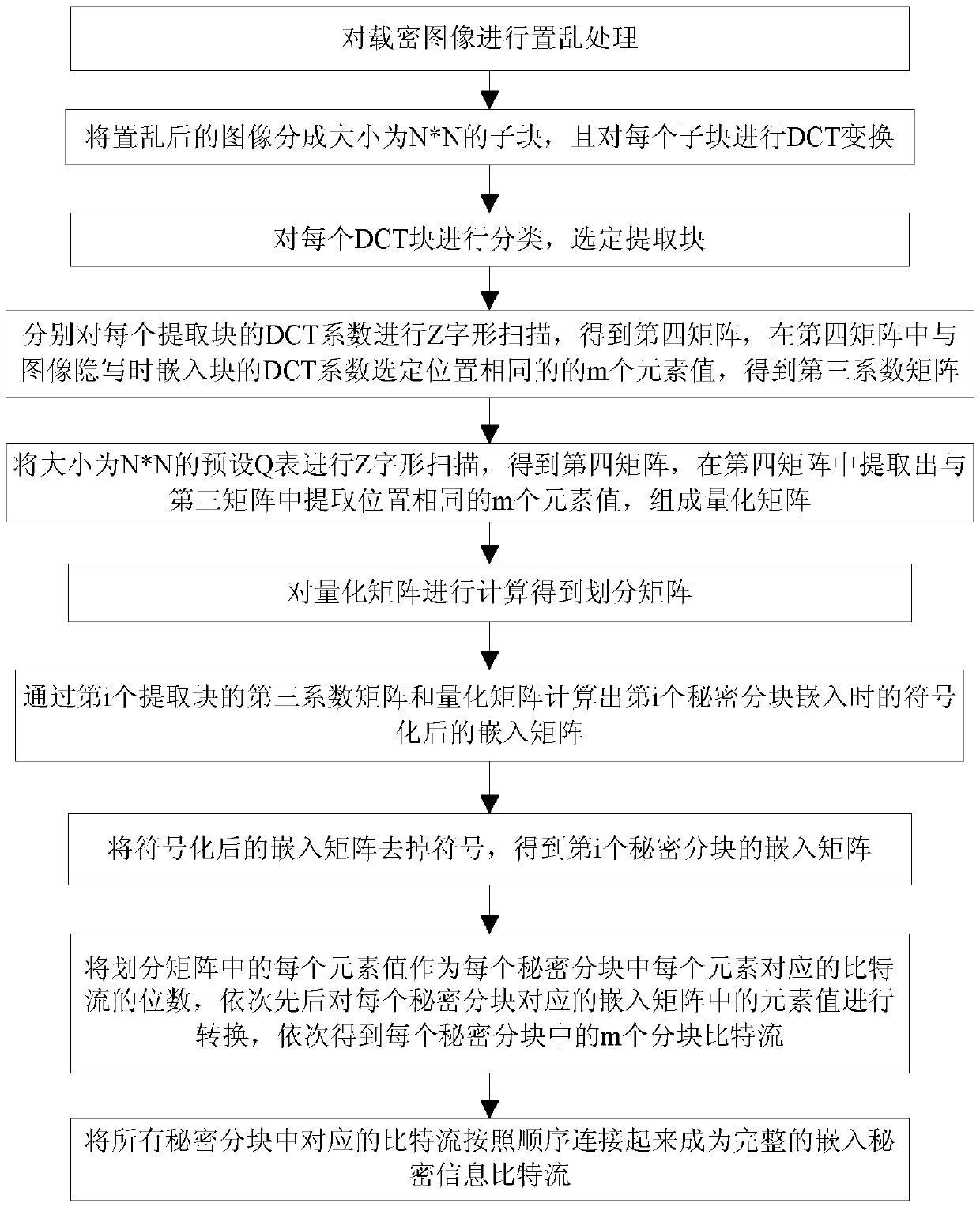
[0061] like figure 1 As shown, a large-capacity image steganography method is used to embed secret information into the carrier image, including the following steps:
[0062] Step 1. Perform scrambling processing on the carrier image to obtain a scrambled carrier image;
[0063] Among them, in this embodiment, one of the four scrambling algorithms is arbitrarily selected, and the pair size is N 1 *N 2 The carrier image is scrambled, and the specific steps of the first scrambling algorithm are as follows:
[0064] Step 1-1a, calculate the sum of the row number and column number of each pixel of the carrier image, wherein any pixel of the carrier image is represented by the i-th row and the j-th column, i=1, 2, 3... N 1 ,j=1, 2, 3..N 2 ;
[0065] Step 1-1b, judging whether the value of i+j can be divisible by 2, if yes, proceed to step 1-...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com