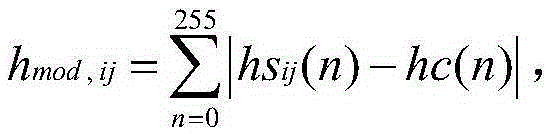Optimal coupling image steganography method based on packet replacement
An optimal matching and best matching technology, applied in image data processing, image data processing, instruments, etc., can solve problems such as inability to obtain secret information, and achieve the effect of improving concealment performance and security, and improving visual concealment.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
[0022] In this embodiment, it is assumed that the cover image is marked C, and the secret mark that needs to be embedded in the cover image C is S. The following combination figure 1 , to illustrate the optimal matching image steganography method based on packet permutation in this embodiment. The image steganography method includes the following steps in sequence:
[0023] (1) Convert the secret information S into a binary bit stream, and group the converted binary bit stream with 8 bits as a group to obtain N groups of binary bit streams, wherein each group of binary bit streams has 2 8 There are 256 combination schemes for each group of binary bit rates;
[0024] (2) According to each combination scheme in each group of binary bit streams, select the corresponding inversion bits of each combination scheme, and perform inversion processin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com