Ciphertext information generation method for image steganography
A technology of information generation and secret information, applied in the direction of image data processing, image data processing, instruments, etc., can solve the problem of not being a bit stream, reducing the anti-statistical detection of the steganography system, achieving good universality and improving steganography The effect of low performance and computational complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
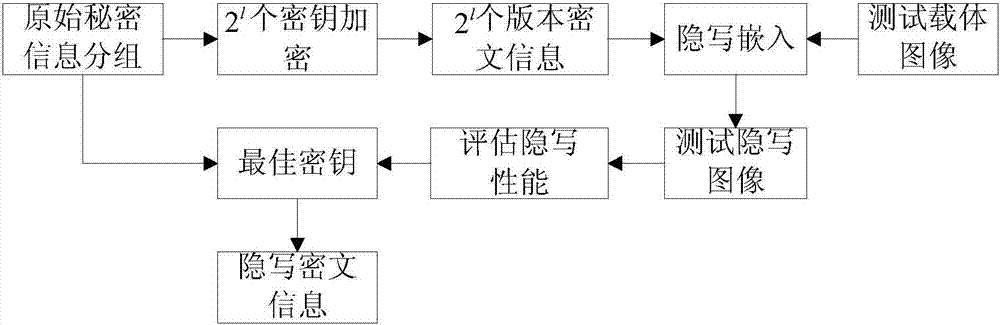
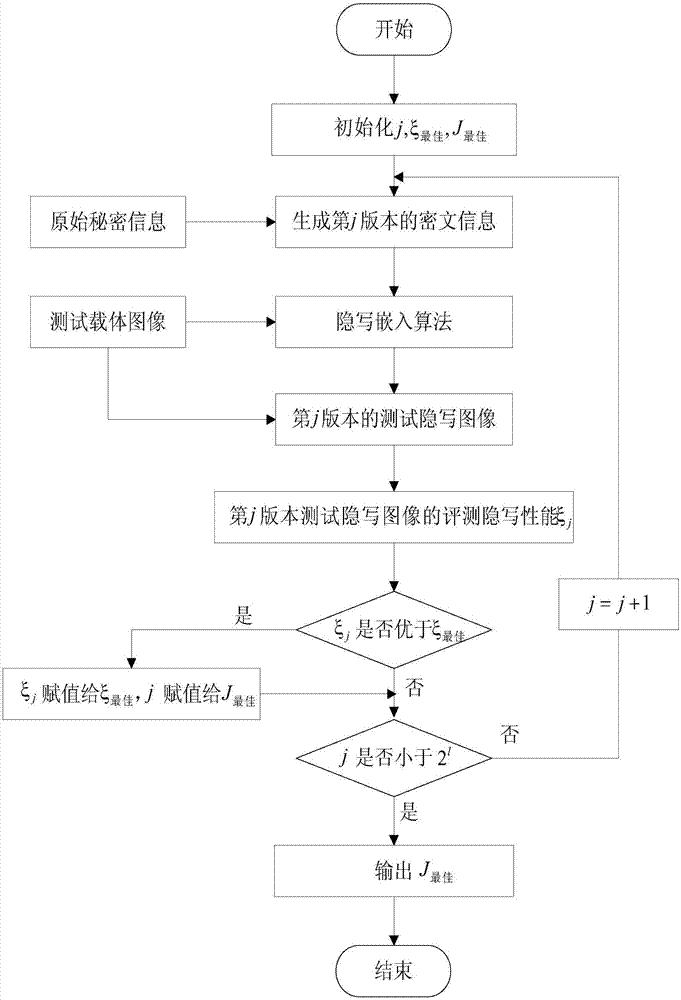
[0023] Such as figure 1 A method for generating ciphertext information for image steganography in the present invention is characterized in that: comprising the following steps:
[0024] Step (1), original secret information grouping: encode the original secret information into a bit stream with length n, use A=(e 1 ,e 2 ,...,e n ) means, where e i ∈{0,1}, i=1,2,...,n, then divide the bit stream with length n into k groups with length l, where k=n / l, the bit stream after grouping A=(A 1 ,A 2 ,...,A k ), where the mth group of secret information is A m =(e l(m-1)+1 ,e l(m-1)+2 ,...,e l(m-1)+l ), m=1,2,...,k;
[0025] Step (2), generate 2 l A key of length l: put 0, 1, ..., 2 l -1 out of 2 l The number is converted into a binary number of length l as 2 l keys, where the xth key uses key x =(e x1 ,e x2 ,...,e xl ) means, where ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com