JPEG domain image steganography method and system based on generative adversarial network
A network and image technology, applied in the field of JPEG domain image steganography based on generative adversarial network, to achieve the effect of improving adaptability and security, high precision and simple design
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
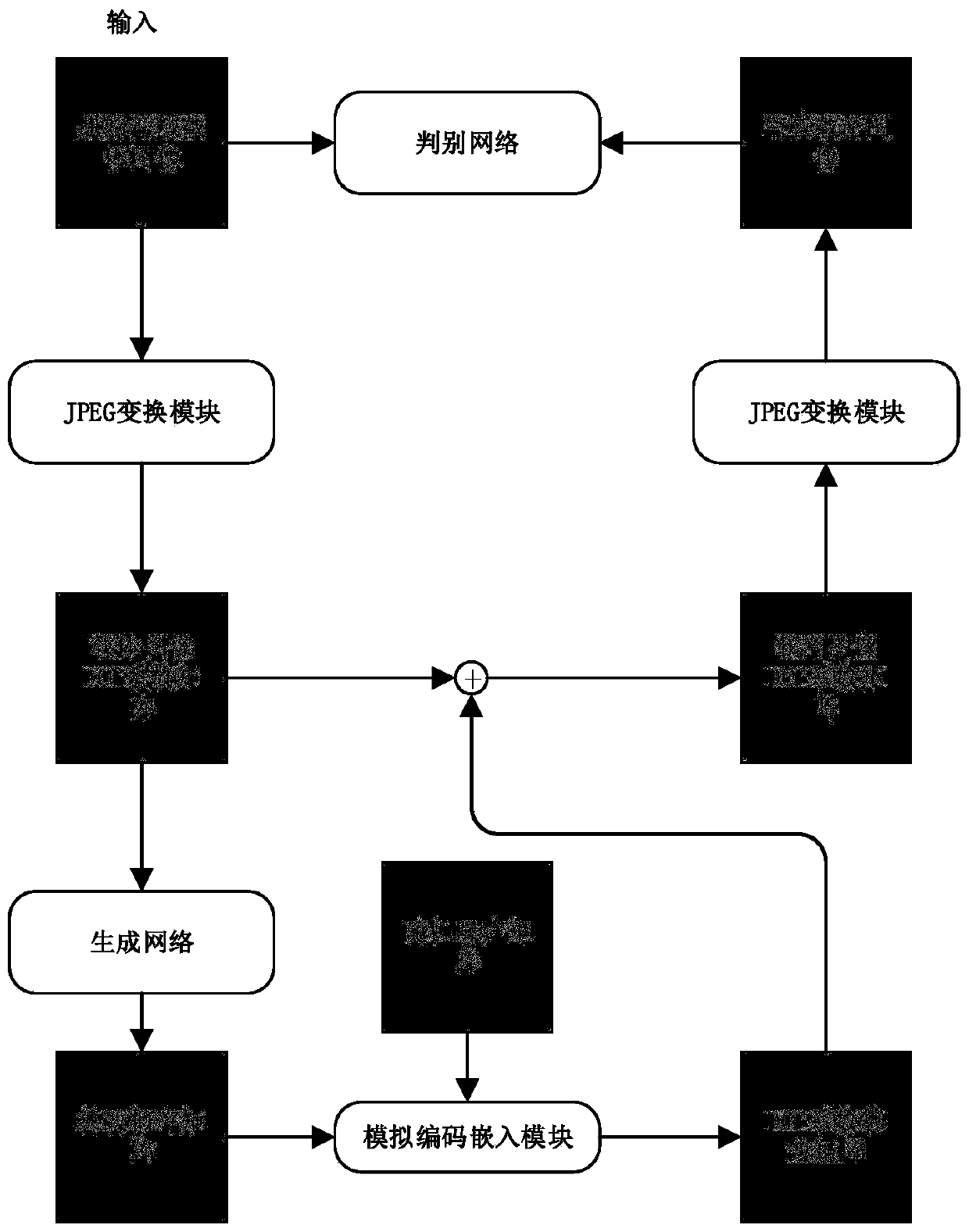
[0055] This embodiment provides a JPEG domain image steganography method based on generating an adversarial network, wherein the specific process of generating an adversarial network training is as follows: figure 2 shown, including the following steps:
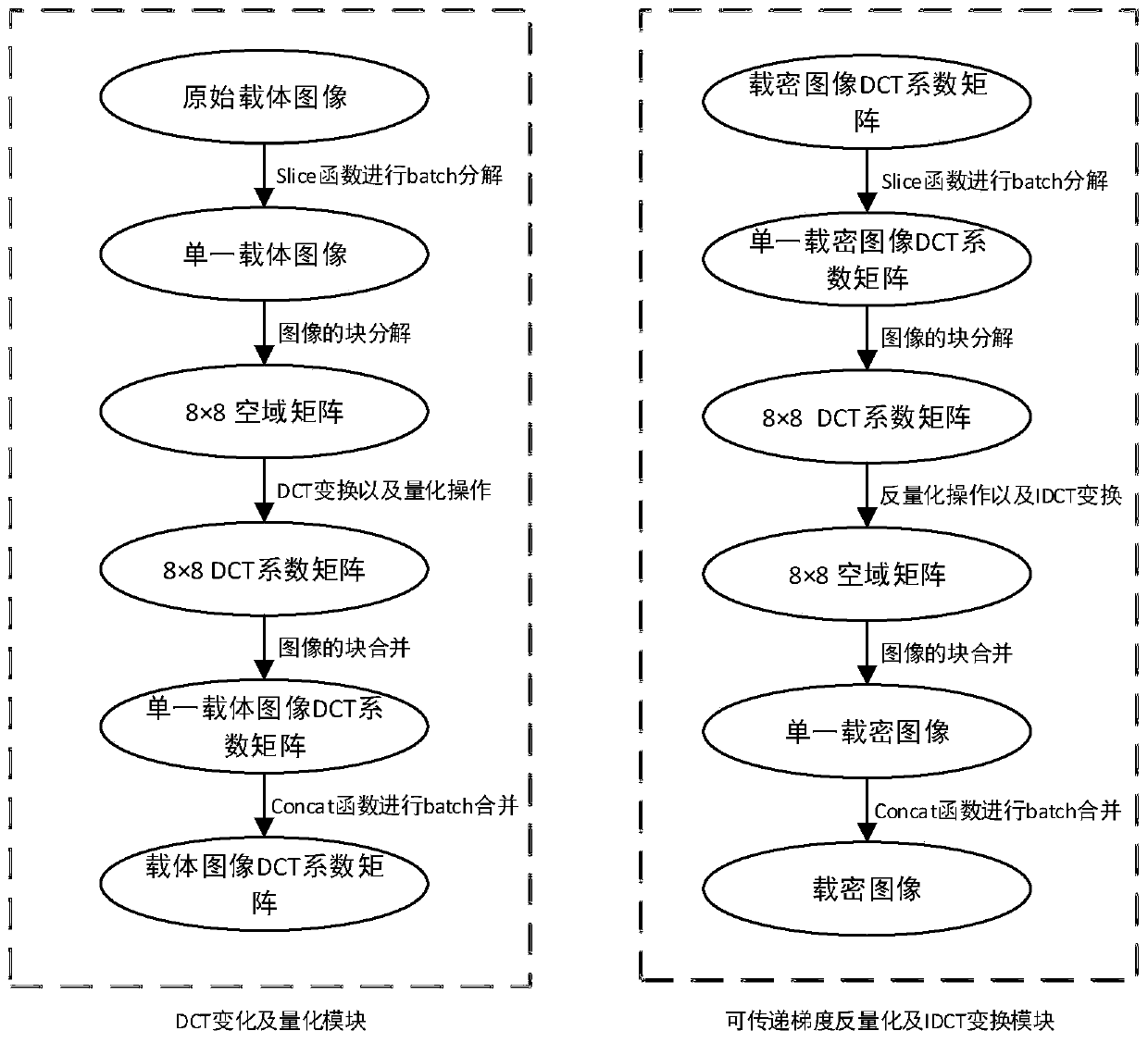
[0056] S1: Input the original carrier image to the transferable gradient JPEG transformation module, use the slice function to obtain a single carrier image, and perform 8*8 blocks for each carrier image, and perform a matrix on each block matrix and DCT transformation matrix Change operation to obtain the DCT matrix corresponding to the spatial domain image, and then divide the DCT coefficient matrix and the quantization matrix corresponding to the compression quality factor QF to obtain the quantized DCT coefficient matrix. DCT coefficient matrix. The specific realization of the transferable gradient JPEG transformation module proposed by the present invention is as attached image 3 shown.
[0057] S2: Input the DCT co...
Embodiment 2
[0075] This embodiment provides a JPEG domain image steganography method based on generating an adversarial network, wherein the specific process of generating an adversarial network training is as follows: figure 2 shown, including the following steps:
[0076] S1: Input the original carrier image to the transferable gradient JPEG transformation module, use the slice function to obtain a single carrier image, divide each carrier image into 8*8 blocks, and change the matrix of each block matrix and DCT transformation matrix operation to obtain the DCT coefficient matrix corresponding to the spatial domain image, and then divide the DCT coefficient matrix and the quantization matrix corresponding to the compression quality factor QF to obtain the quantized DCT coefficient matrix. A matrix of DCT coefficients with the same size as the vector. The specific realization of the transferable gradient JPEG transformation module proposed by the present invention is as attached imag...
Embodiment 3
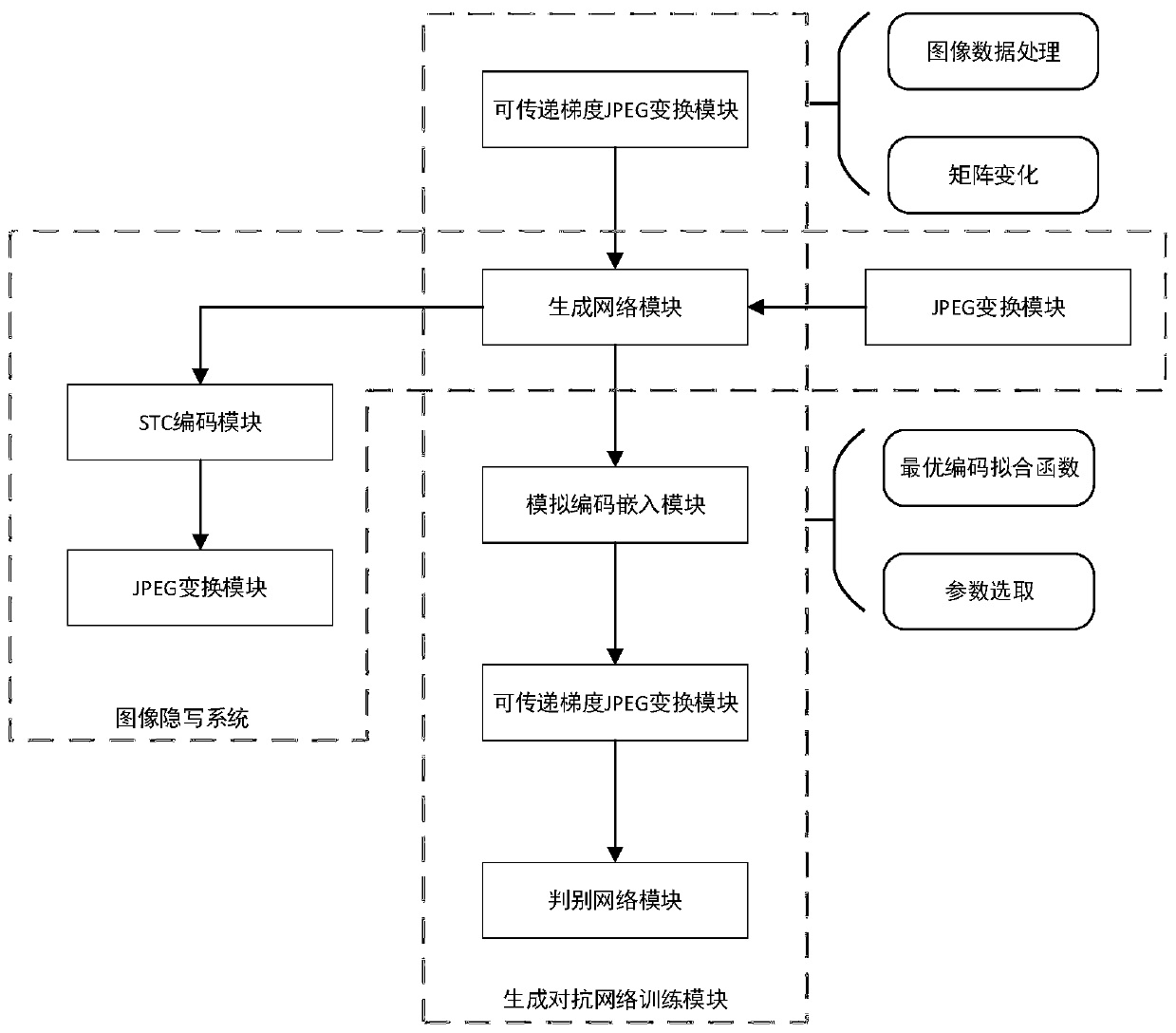
[0093] The present embodiment provides a JPEG image steganography system based on generating an adversarial network, including a generating network module obtained by a JPEG domain image steganography method based on generating an adversarial network, an information encoding module, and a JPEG transformation module, such as figure 1 As shown in the image steganography system, the steps are as follows:
[0094] S1: Convert the input carrier image into a DCT coefficient matrix through the JPEG transformation module.
[0095] S2: Input the DCT coefficient matrix of the carrier image to the generation network module to obtain a tamper probability matrix and convert it into a corresponding embedded cost value. The parameters of the generated network in the generated network module are parameters trained by the generated confrontation network training module.
[0096] S3: An information coding module using a Syndrometrellis code (STC) generates a tampering matrix with the same size...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com