Image steganography method and system based on generative steganography confrontation
A generative and steganographic technology, applied in image data processing, image data processing, neural learning methods, etc., can solve the problems of low visual quality of generated images, small steganographic capacity, low security, etc., to improve anti-detection ability, the effect of reducing the disappearance of the gradient, and improving the ability of detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
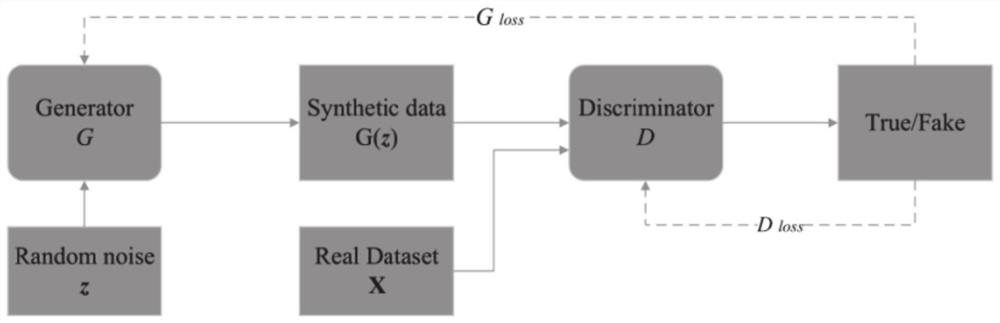
[0049] Such as figure 1 As shown, the existing generative confrontation network GAN is composed of a generator and a discriminator. The generator inputs noise to generate images, and the discriminator is used to distinguish real images from generated images; the discriminator and generator are trained at the same time, and the two are constantly The adversarial game is carried out in the ground, and finally the Nash equilibrium is reached, and the generator generates the result consistent with the real image. The training process of GAN is the optimization of the minimax problem; including:
[0050] (1) The discriminator D correctly judges whether the input data comes from the real data sample x or the fake data sample G(z) generated by the generator as much as possible;
[0051] (2) The generator G learns the data distribution of the real data set samples, and tries to make the performance of the fake data G(z) generated by the generator on D consistent with the performance ...
Embodiment 2
[0133] This embodiment provides an image steganography system based on generative steganographic confrontation, including:
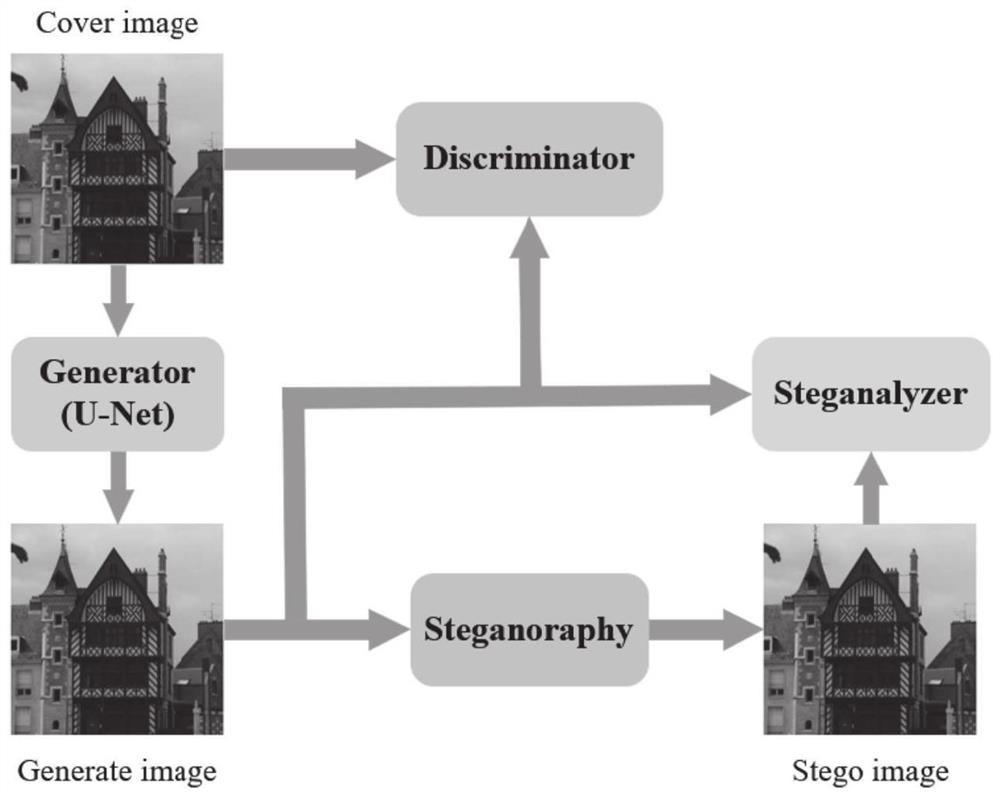
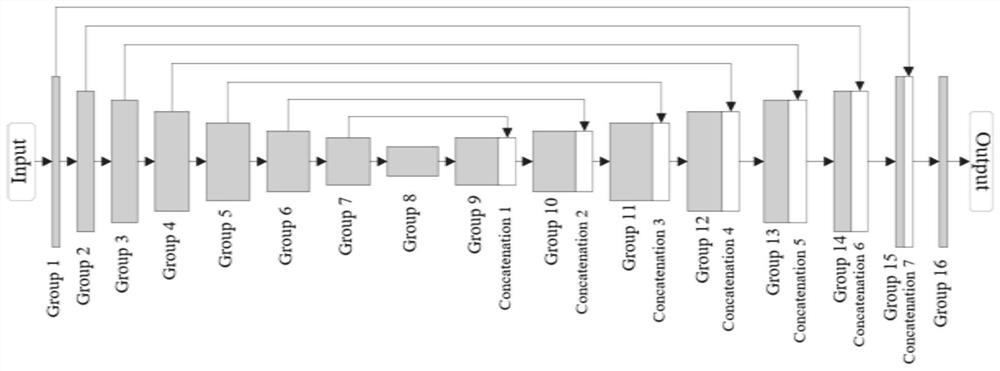
[0134] The model construction module is configured to construct a generative steganographic confrontation model comprising a generative network, a steganographic device, a discriminative network and a steganalytic network, wherein the generative network converts the original image into a carrier image by using the same layer jump method, so The steganography device embeds the secret image into the carrier image to obtain the secret image, the discrimination network judges the authenticity of the carrier image, and the steganalysis network judges whether the secret image contains secret image information;
[0135] The confrontation training module is configured to construct the loss functions of the generation network, the discrimination network, and the steganalysis network according to the judgment results of the discrimination network and the steganalys...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com