Improved EMD image steganography embedding and extraction methods based on weight vector prevention
A value vector, image technology, applied in the field of improved EMD image steganography embedding and extraction based on unweighted vector, image steganography embedding and extraction field, can solve the limitation of secret information expression range, EMD method image visual embedding quality and embedding Capacity compromise, limited embedded capacity, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
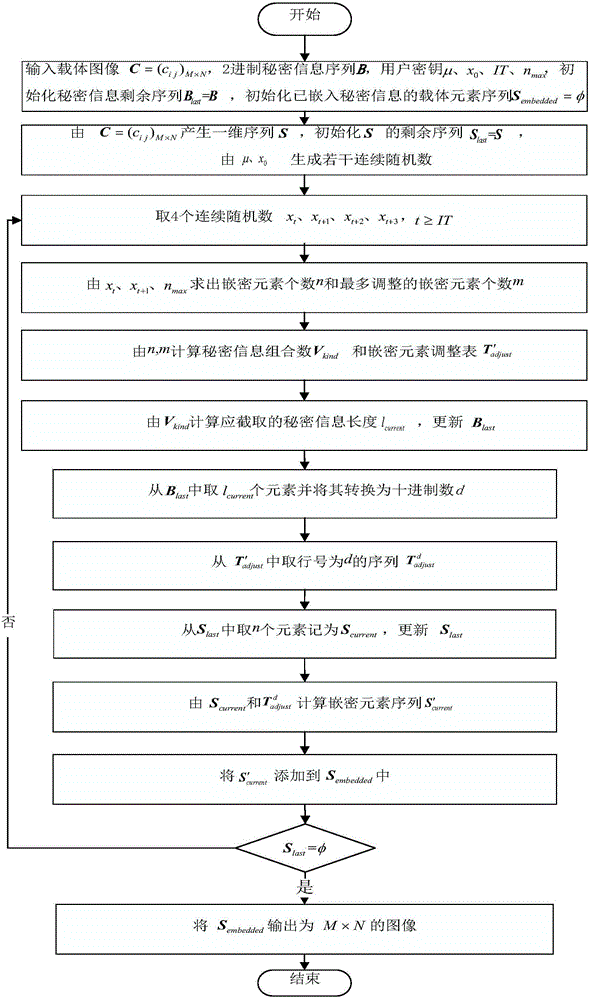
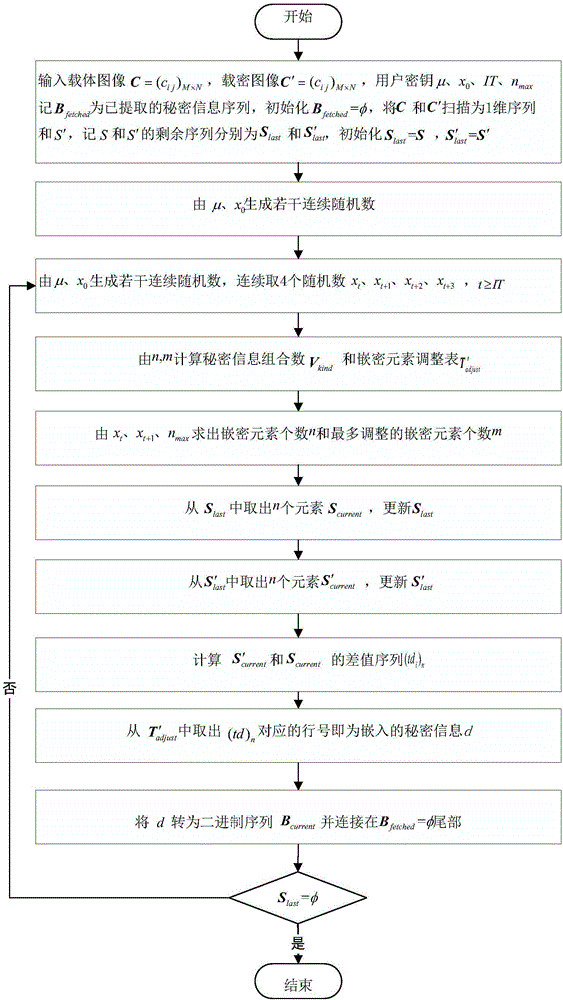
[0152] The following takes JAVA jdk1.8.0_65 as the case implementation environment, and describes the implementation of the present invention in detail in conjunction with the accompanying drawings, but is not limited to this implementation case, where figure 1 is the embedded flowchart, figure 2 is the extraction flow chart.
[0153] The specific implementation steps of the embedding method:
[0154] Step 1: Assume that the carrier image C is converted into a 1-dimensional sequence in row-first order as S={160,160,163,157,153}; initialize the remaining sequence S of S last =S, input the secret information bit string B={1,1,1,0,1,0}, initialize the remaining sequence B of B last =B, initialize the carrier element sequence S that has been embedded with secret information embedded = φ;
[0155] Step 2: Enter user key μ=4,x 0 = 0.3519407329674913, IT = 1059, n max =6: A number of random numbers can be continuously generated by the formula (2), and the first IT numbers are ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com