Generative robust image steganography method
A generative, image-based technology, applied in image watermarking, image data processing, image data processing, etc., can solve the problems of not considering the consistency between generator and extractor, limited DCGAN network performance, and low accuracy of information extraction. Achieve the effect of strong statistical undetectability of secret-carrying images, overcome the poor quality and high concealment of secret-carrying images
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
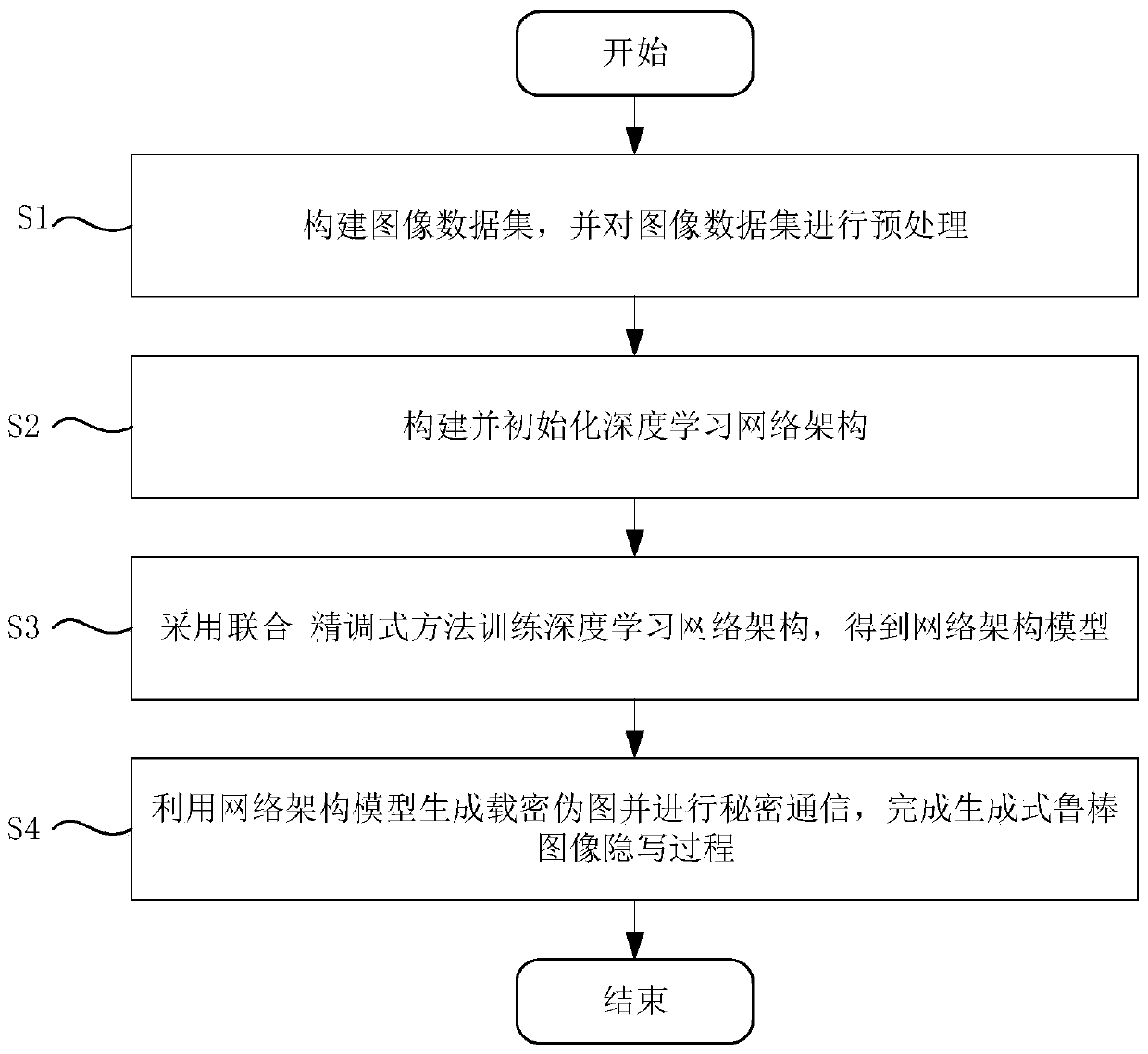
[0071] Such as figure 1 As shown, a generative robust image steganography method includes the following steps:
[0072] S1: Construct an image dataset and preprocess the image dataset;
[0073] S2: Build and initialize the deep learning network architecture;
[0074] S3: Use the combined-fine-tuning method to train the deep learning network architecture to obtain the network architecture model;
[0075] S4: Use the network architecture model to generate secret-carrying pseudo-images and perform secret communication to complete the process of generative robust image steganography.
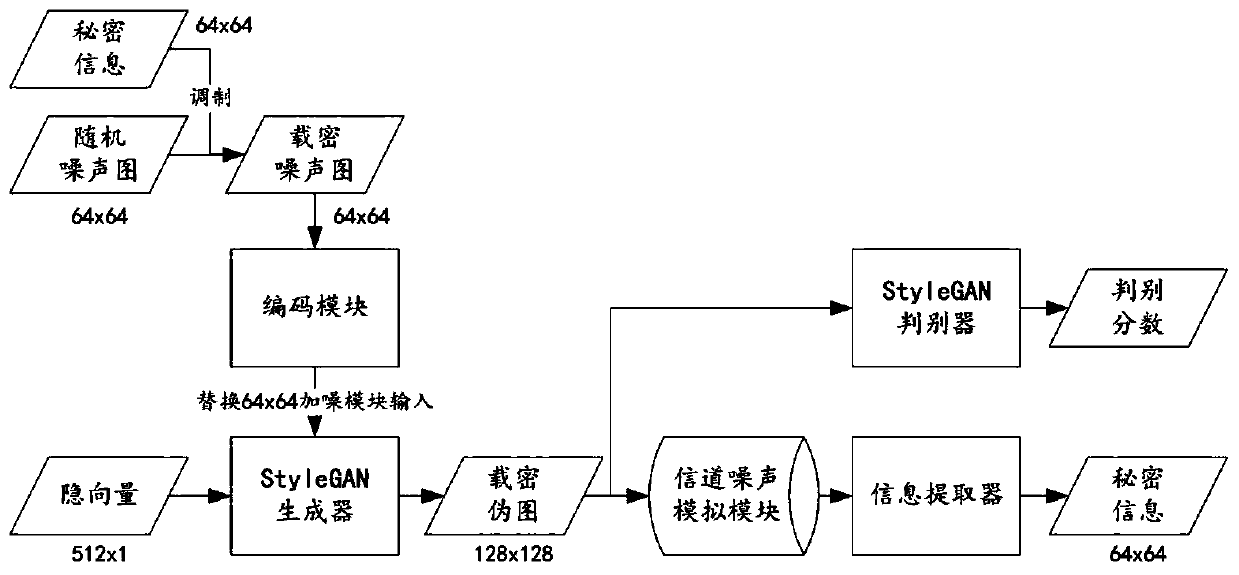
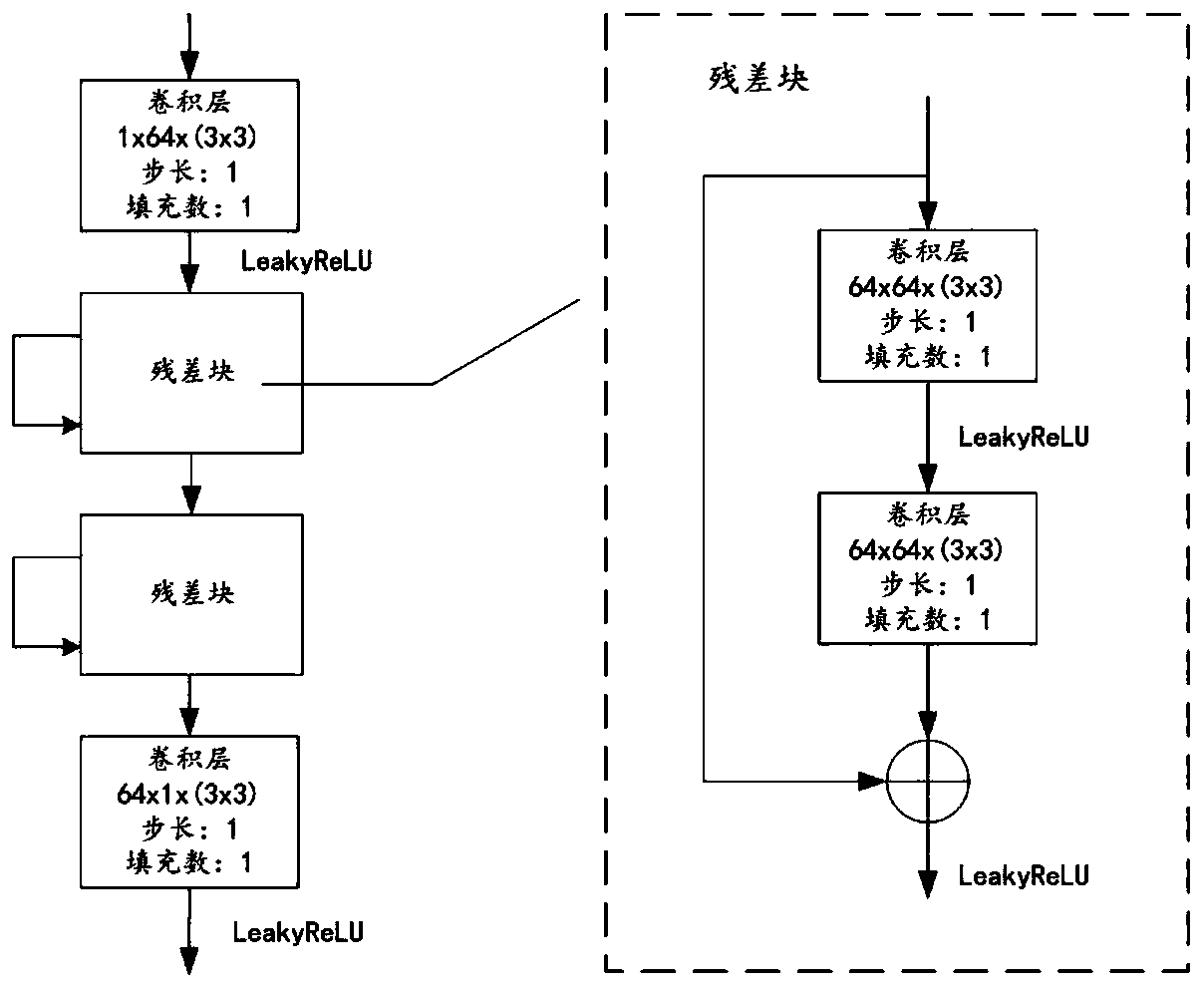
[0076]In the specific implementation process, by using the Generative Adversarial Network StyleGAN, the embedding process of secret information is integrated into the image generation process, and a generative image steganography architecture that can bear a large amount of secret information and has certain robustness is constructed. , the resulting generative image steganography method has the ...
Embodiment 2
[0105] More specifically, the existing technology has the following technical defects:
[0106] (1) Traditional carrier-modified image steganography algorithms, also known as content-adaptive image steganography algorithms, are greatly challenged in the face of advanced steganalyzers based on convolutional neural networks. This is because the method needs to heuristically design the distortion cost function. Due to a series of factors such as the designer's own limitations and the complexity of the algorithm, it is difficult to achieve accurate modeling comprehensively and effectively, which leads to content-based adaptive Image steganography algorithms are easily detected by steganalyzers based on convolutional neural networks.
[0107](2) The carrier-modified image steganography scheme based on generative adversarial networks is still in-depth research. At present, only UT-GAN is slightly more secure than traditional image steganography algorithms, but it is still easy to be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com