Method for efficiently, parallelly and safely encrypting and decrypting high-capacity data packets
A data packet, large-capacity technology, applied in electrical components, transmission systems, etc., can solve problems such as low security, server pressure, and poor computing efficiency, and achieve the effect of improving encryption speed.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
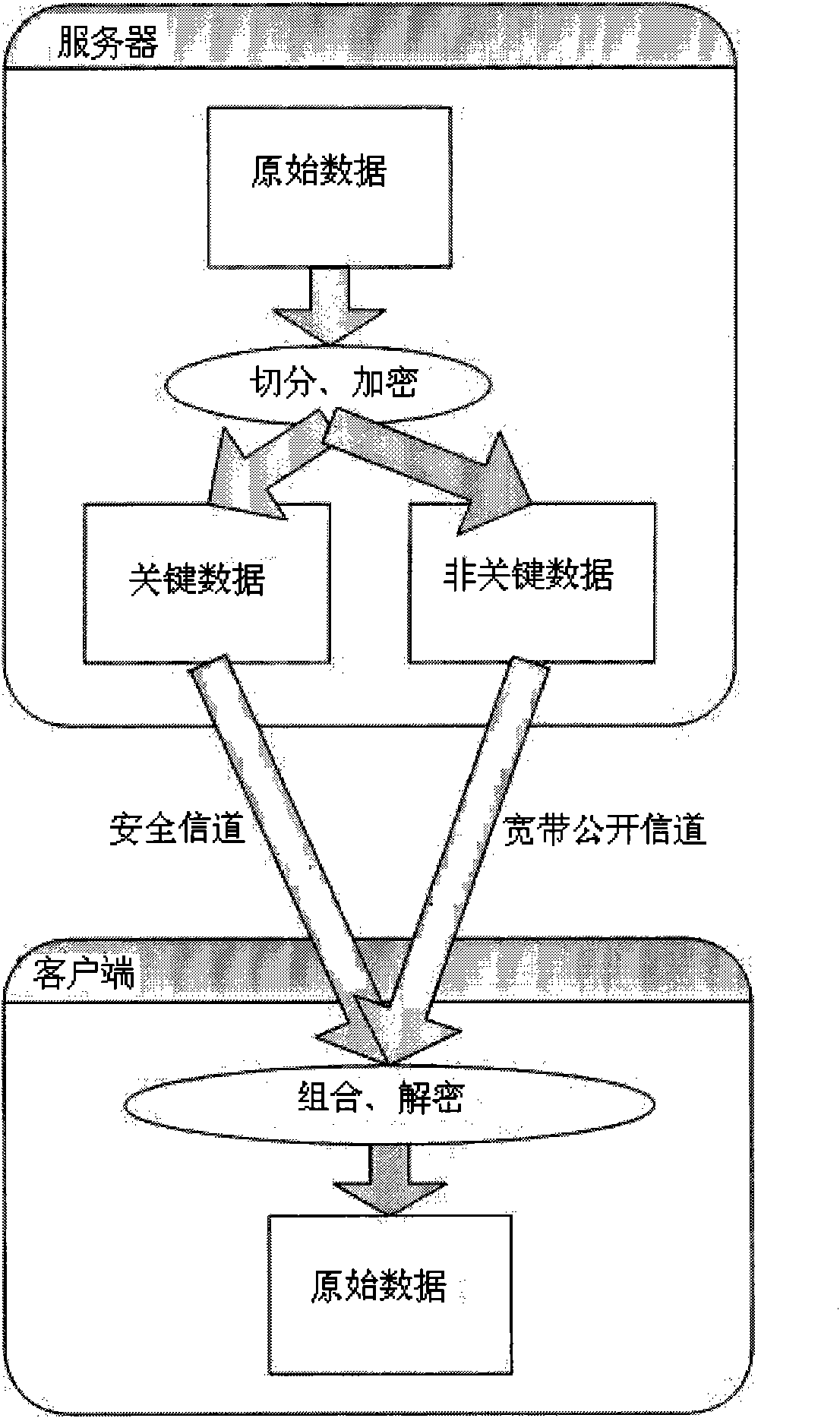
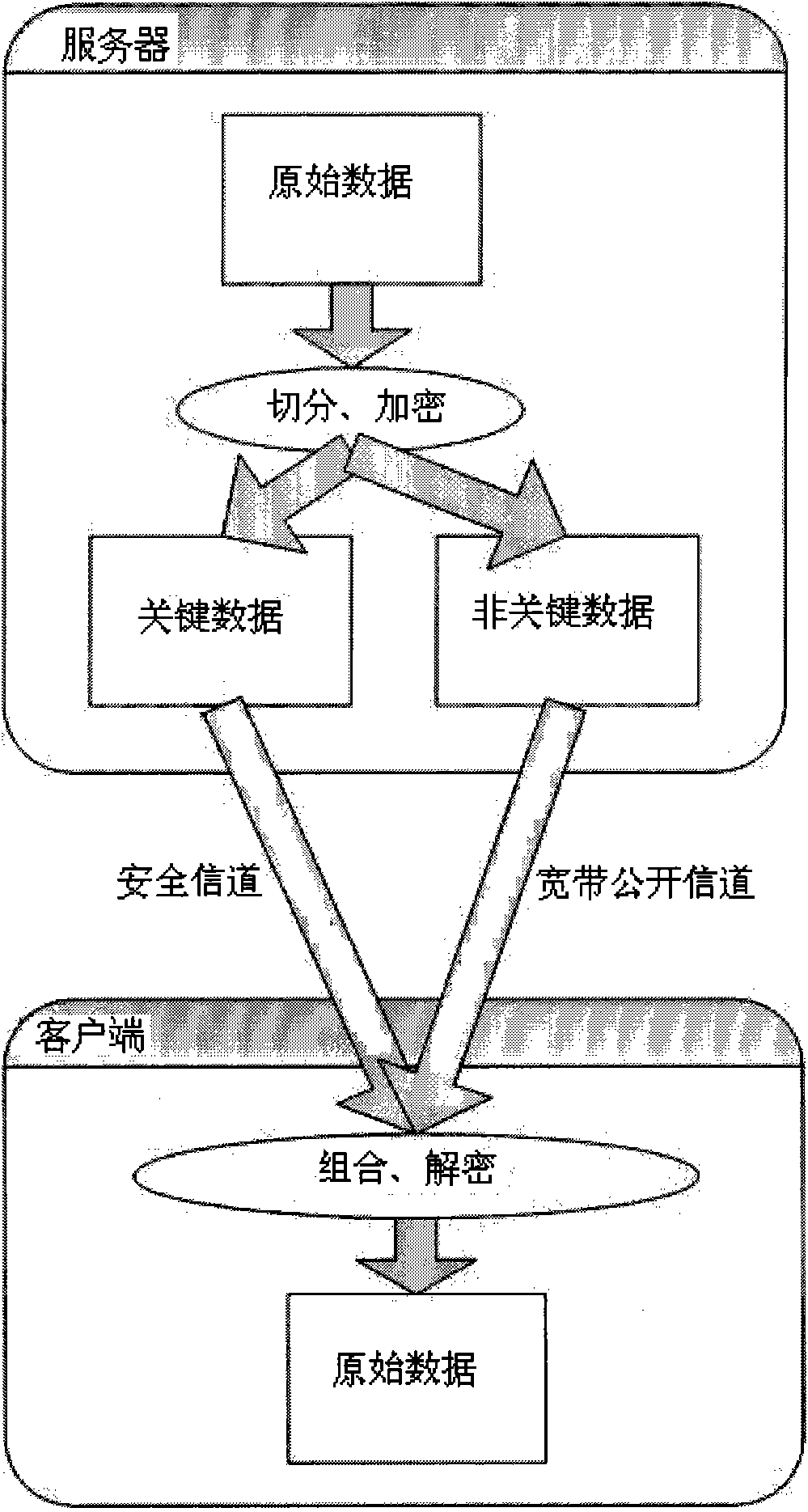
[0014] Such as figure 2 As shown, the efficient parallel safe encryption and decryption method of large-capacity data packets of the present invention specifically includes the following steps:
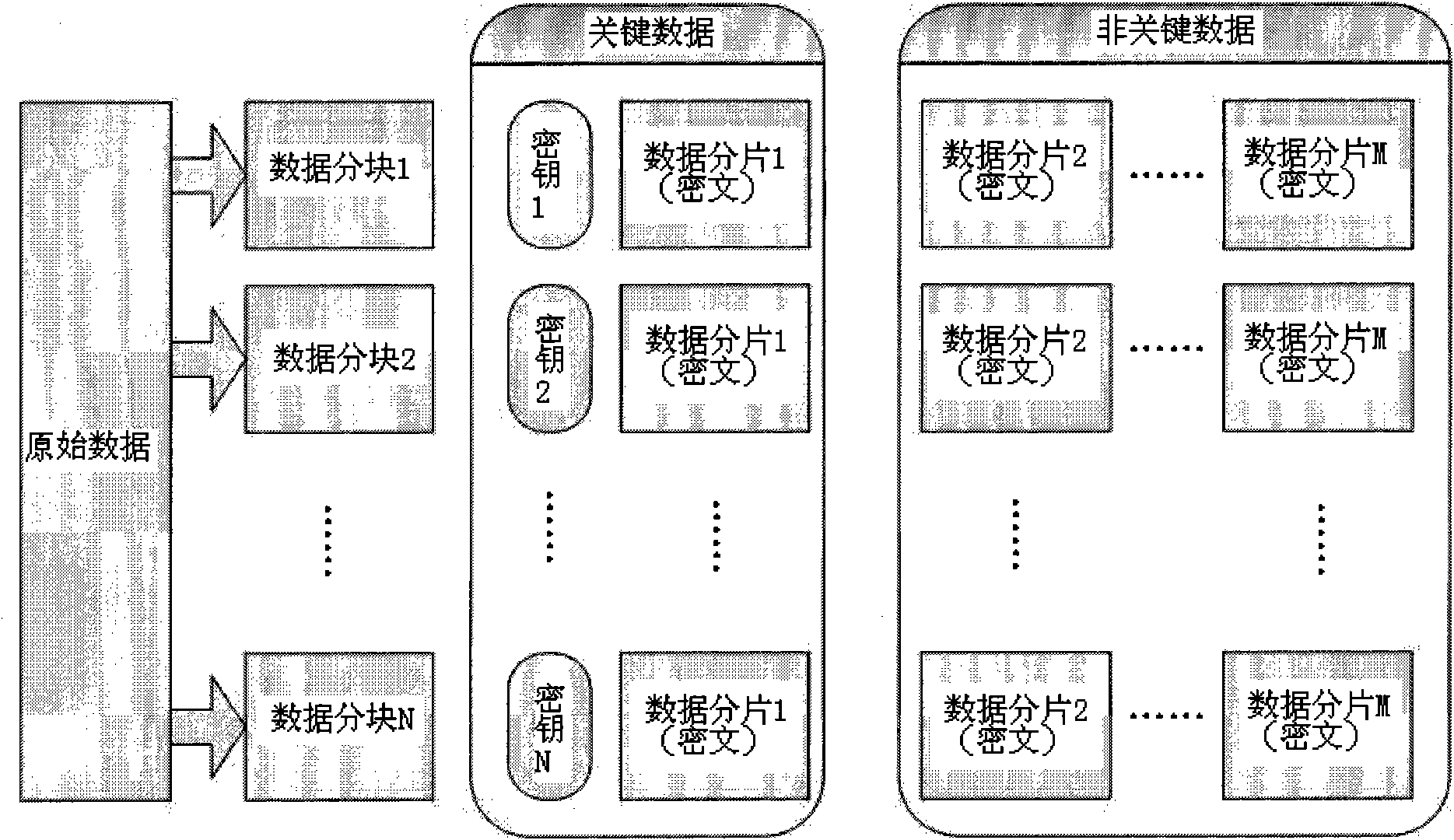
[0015] (1) After the server obtains a large-capacity data packet, it divides the data packet into a fixed number of blocks (see figure 1 , divided into N blocks of data blocks), except for the last block which is slightly smaller, the other blocks have the same size; then, all the data blocks are decomposed into fixed-volume data slices (see figure 1 , divided into M pieces of data slices), except for the last block, the volume of other blocks is an integer multiple of the data slice volume.
[0016] For the original data (large-capacity data packet), that is, the division of the plaintext is divided into two levels, the higher level is the data block, and the lower level is the data slice. The number of data blocks is fixed, and the volume is basically the same (except for the las...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com