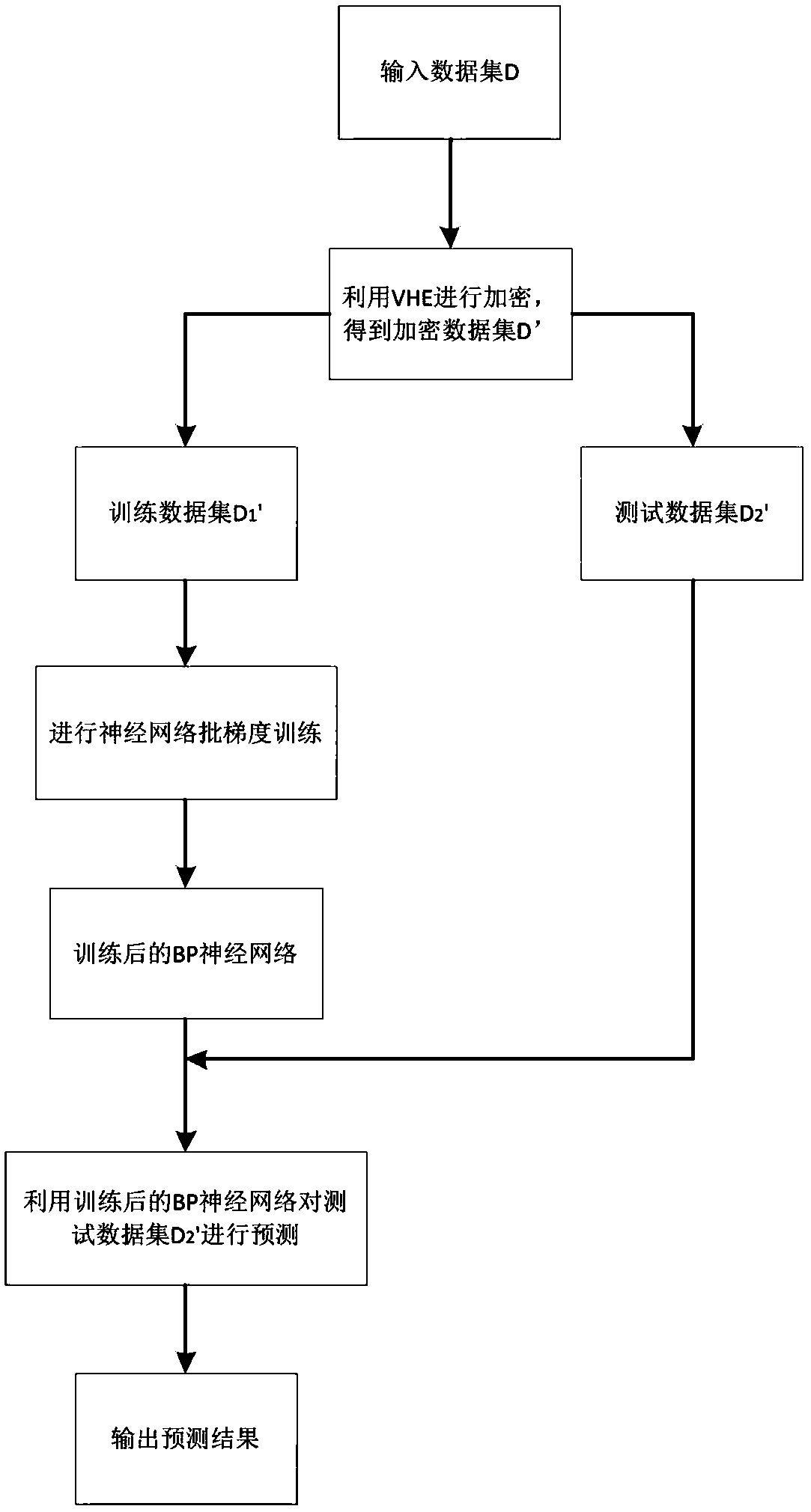
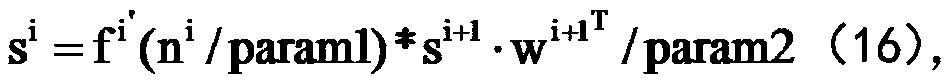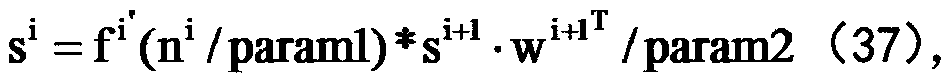VHE-based privacy protection neural network training and predicting method
A technology of neural network and prediction method, applied in the field of vector homomorphic computing, can solve problems such as data security cannot be guaranteed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
[0109] In this embodiment, the number of hidden layers in the BP neural network is 1, then the learning rate is set to α, and two weight matrices w are initialized 1 and w 2 ;
[0110] w 1 Represents the weight matrix between the input layer and the hidden layer, with a size of (the input vector dimension of the data set D plus 1, the number of neurons in the hidden layer);
[0111] w 2 Indicates the weight matrix between the hidden layer and the output layer, the size is (the number of neurons in the hidden layer, the number of neurons in the output layer)
[0112] Simultaneously initialize 2 threshold vectors b 1 and b 2 , b 1 Represents the threshold vector of the hidden layer, b 2 Represents the threshold vector of the output layer, all initialized to all zero vectors;
[0113] Define the activation function f of the hidden layer 1 and the activation function f of the output layer 2 ;
[0114] The input to the hidden layer is:
[0115] The output of the hidde...
specific Embodiment 2
[0141] Based on the specific embodiment 1, this embodiment uses data for further description.
[0142] The input of data set D =
[0143](8 307 130 3504 12 70 1; 8 350 165 3693 11.5 70 1; 8 318 150 3436 11 701; 8 304 150 3433 12 70 1; 8 302 140 3449 10.5 70 1; 829 198 4341 10 70 1; 8454 22020 4354 9 70 1; 8 440 215 4312 8.5 70 1; 8 455 225 4425 10 70 1; 8 390 1903850 8.5 70 1; 8 383 170 3563 10 70 1; 8 340 160 3609 80 1; ;8 455 225 3086 10 70 1; 4 113 95 2372 15 70 3; 6 198 95 2833 15.5 70 1; 6199 97 2774 15.5 70 1; 461835 20.5 70 2; 4 110 87 2672 17.5 70 2; 4 107 90 2430 14.5 70 2; 4 104 95 237517.5 70 2; 4 121 113 2234 12.5 70 2; 6 19990 2648 15 70 1; 8 360 215 4615 14 701 ;8 307 200 4376 15 70 1; 8 318 210 4382 13.5 70 1; 8 304 193 4732 18.5 70 1; 497 88 2130 14.5 71 3; 1002634 13 71 1; 6 225 105 3439 15.5 71 1; 6 250 100 3329 15.5 71 1; 6 250 88 330215.5 71 1; 6 232 100 3288 15.5 71 1; 8 350 165 4209 12 71 1 1; 8 400 175 4464 11.571 1 1 1 ;8 351 153 4154 13.5 71 1; 8 3...
specific Embodiment 3
[0155] Based on specific embodiment 1, this embodiment uses data for further description.
[0156] The input of data set D =
[0157] ([[-3, -2.7, -2.4, -2.1, -1.8, -1.5, -1.2, -0.9, -0.6, -0.3, 0, 0.3, 0.6, 0.9, 1.2, 1.5, 1.8], [- 2, -1.8, -1.6, -1.4, -1.2, -1, -0.8, -0.6, -0.4, -0.2, -2.2204, 0.2, 0.4, 0.6, 0.8, 1, 1.2])
[0158] The output of dataset D =
[0159] ([0.6589, 0.2206, -0.1635, -0.4712, -0.6858, -0.7975, -0.8040, -0.7113, -0.5326, -0.2875, 0, 0.3035, 0.5966, 0.8553, 1.0600, 1.1975, 1.2618])
[0160] Among them, the data is first uniformly enlarged by 10000 times and truncated to an integer, and then encrypted with VHE; there are 2 neurons in the input layer, 3 neurons in the hidden layer, and 1 neuron in the output layer; the activation function of the hidden layer is a nonlinear function y= tanh x, the data is reduced by 400 times before passing the tanhx function, and then enlarged by 400 times after passing the tanh x function; the output layer excitation ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com