Revocable key external package decryption method based on content attributes
A content attribute and key technology, applied in the field of cryptography in information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
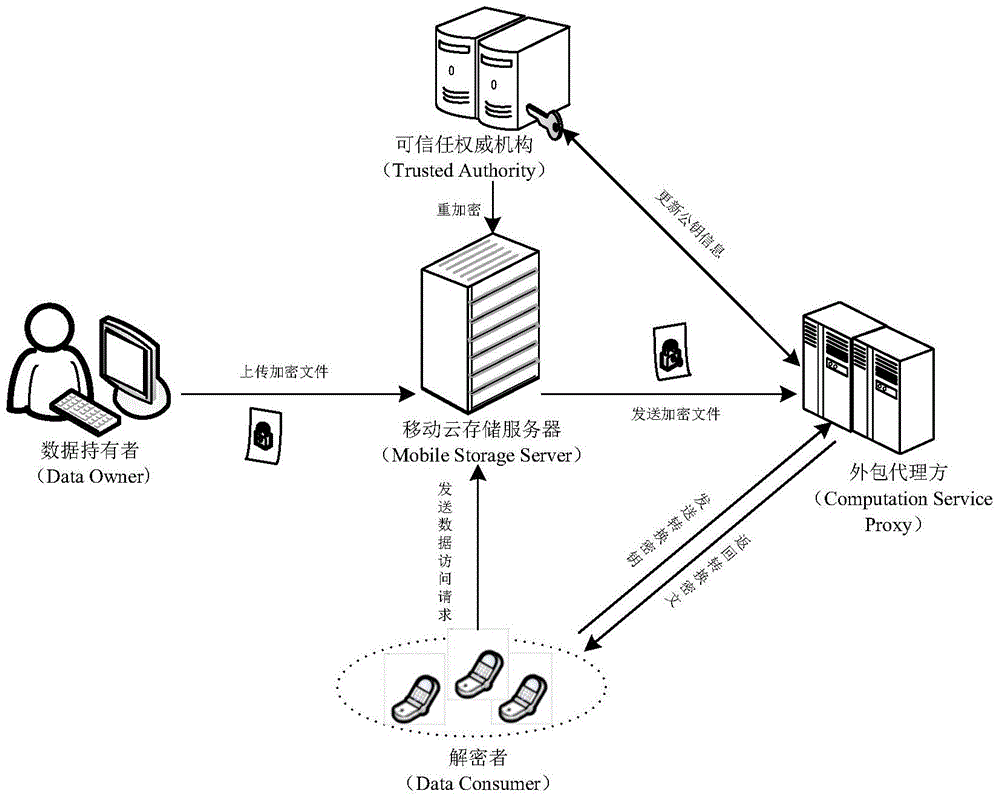
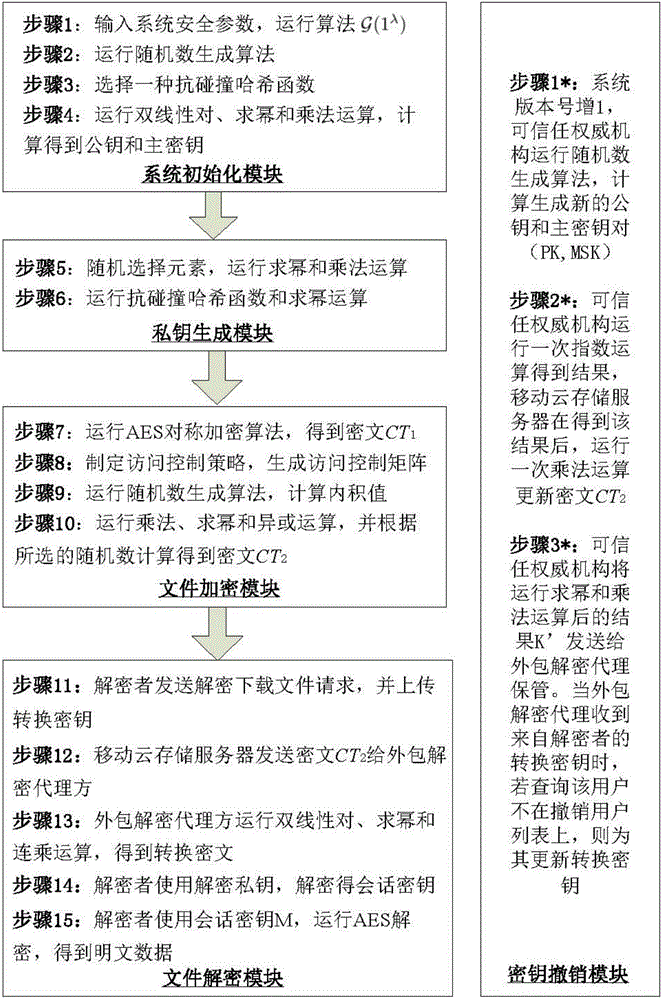
[0087] Such as Figure 1-2 , The present invention is a revocable key outsourcing decryption method based on content attributes, the method is realized by five modules: a system initialization module, a private key generation module, a file encryption module, a file decryption module and a key revocation module. See figure 2 ,, combined with the flow chart, the specific implementation steps of the method are introduced as follows:
[0088] Module 1: System initialization module:
[0089] Step 1: The trusted authority (TA, Trusted Authority) inputs the system security parameter λ, and runs the algorithm Output two groups G and G whose order is a prime number p T And a bilinear mapping operation e: G×G→G T ;
[0090] Step 2: Next, run the random number generation algorithm, randomly select a generator g in the G group, two random elements u, f, and Z in the G group p An element α in the domain.
[0091] Step 3: The trusted authority selects a collision-resistant hash fu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com