Quantum key classification providing method for improving electric power data transmission security
A technology of quantum key and power data, applied in the field of high-level provision, can solve the problem of mismatch between the speed of quantum key distribution and business demand, achieve fast encryption and decryption, improve practicability, and achieve simple effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
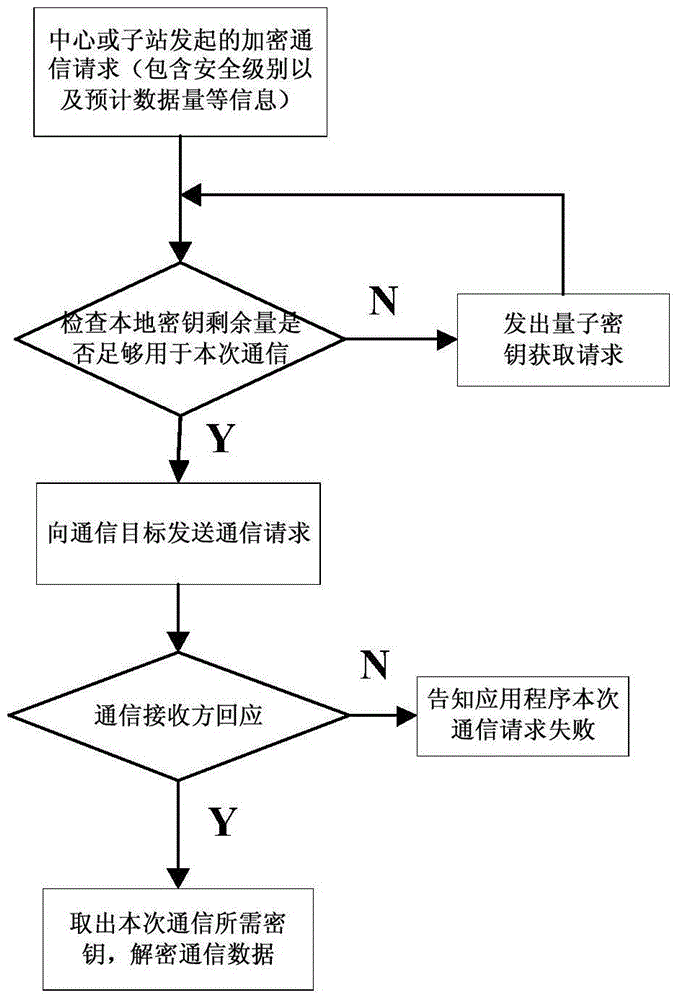
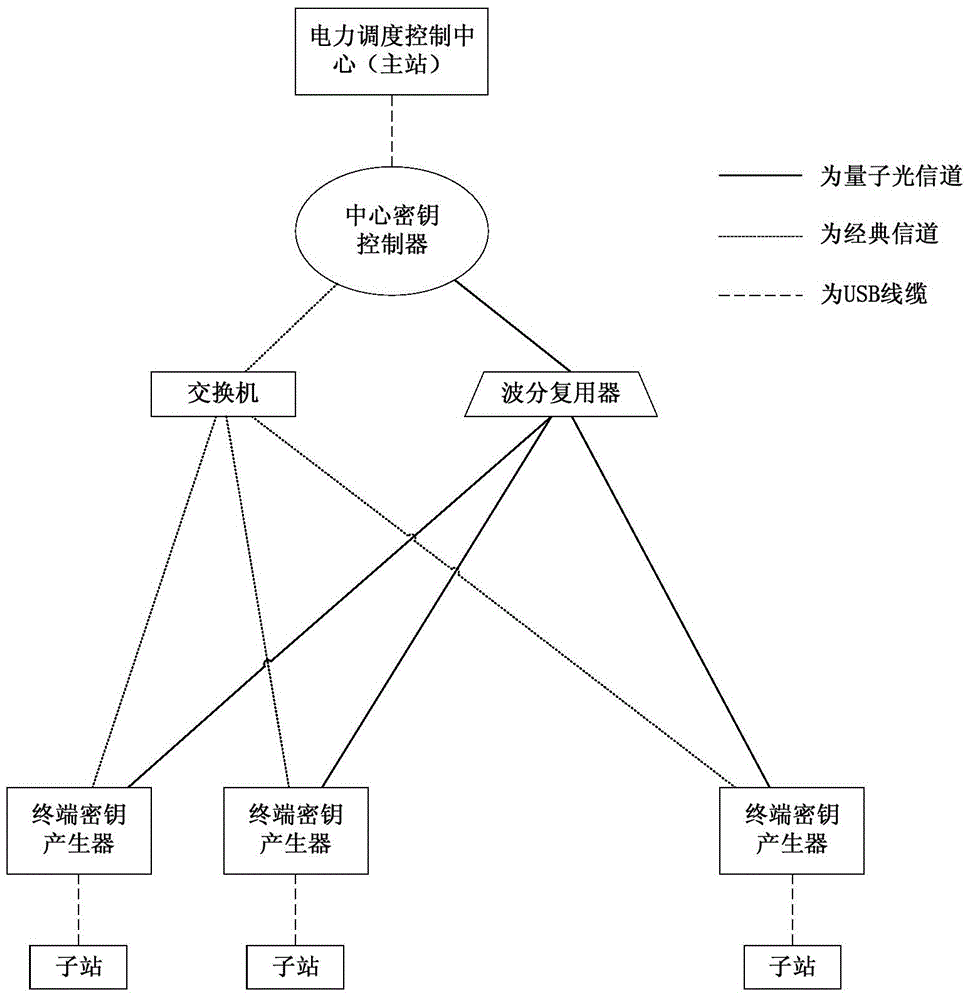
[0088] The power dispatching control center (master station) needs to remotely control the substations, and the storage capacity of the key in the key memory module is insufficient.
[0089] Step 1: The power dispatching control center (master station) sends the destination substation ID, security level requirements, and expected traffic of this encrypted communication to the central key controller through a USB cable. In this example, it is assumed that substation 1 is secure. The level is 0, and the expected traffic is 1500 bytes.
[0090] Step 2: After the central key controller receives the request information, it knows that this business is a remote communication, which requires the highest security and can accept a delay of less than 10 seconds, and then calculates the required traffic based on the expected traffic usage of this communication. A key of 3000 bytes (including additional overhead and key redundancy) is required to complete this communication, and the remain...
Embodiment 2
[0098] The power dispatching control center (master station) needs to remotely control the substations, and the storage capacity of the key in the key memory module is insufficient.
[0099] Step 1: The power dispatching control center (master station) sends the destination substation ID, security level requirements, and expected traffic of this encrypted communication to the central key controller through a USB cable. In this example, it is assumed that substation 1 is secure. The level is 5, and the expected traffic is 3000 bytes.
[0100] Step 2: After the central key controller receives the request information, it knows that this business is telemetry communication, which requires high security and can accept a delay of less than 4 seconds, and then calculates it based on the expected traffic usage of this communication To complete this communication, a key of 1000 bytes (including additional overhead and key redundancy) is required, and the remaining key of substation 1 i...
Embodiment 3
[0106] The sub-station responds to the telemetry instruction of the electric power dispatching control center (main station), and the storage capacity of the key in the key memory is sufficient.
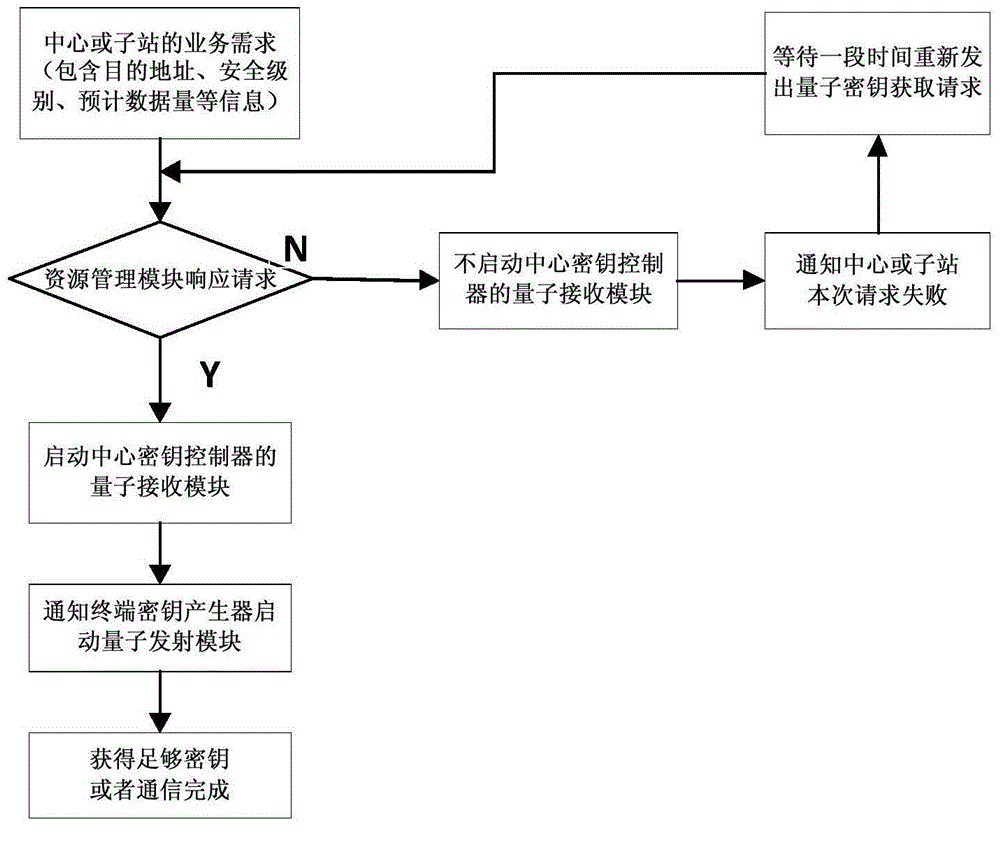
[0107] Step 1: Substation 1 responds to the instruction request of the power dispatching control center (master station) to send the current line parameter data. The security level of this communication is -1, and the expected traffic is 5000 bytes. The request is sent to the terminal key generator.
[0108] Step 2: The terminal key generator receives the request and checks that the current quantum key used for symmetric encryption has been used for 1 hour and the replacement time (2 hours) has not yet been reached.
[0109] Step 3: The terminal key generator sends an encrypted communication request to the central key controller.
[0110] Step 4: After receiving the information that the central key controller agrees to this encrypted communication, the terminal key generator returns...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com