System and method for detecting real-time security threats in a network datacenter
a network datacenter and real-time security technology, applied in the direction of software maintenance/management, unauthorized memory use protection, instruments, etc., can solve the problems of consuming or needlessly risking the impact of operations, and listeners may be particularly configured to negate challenges
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
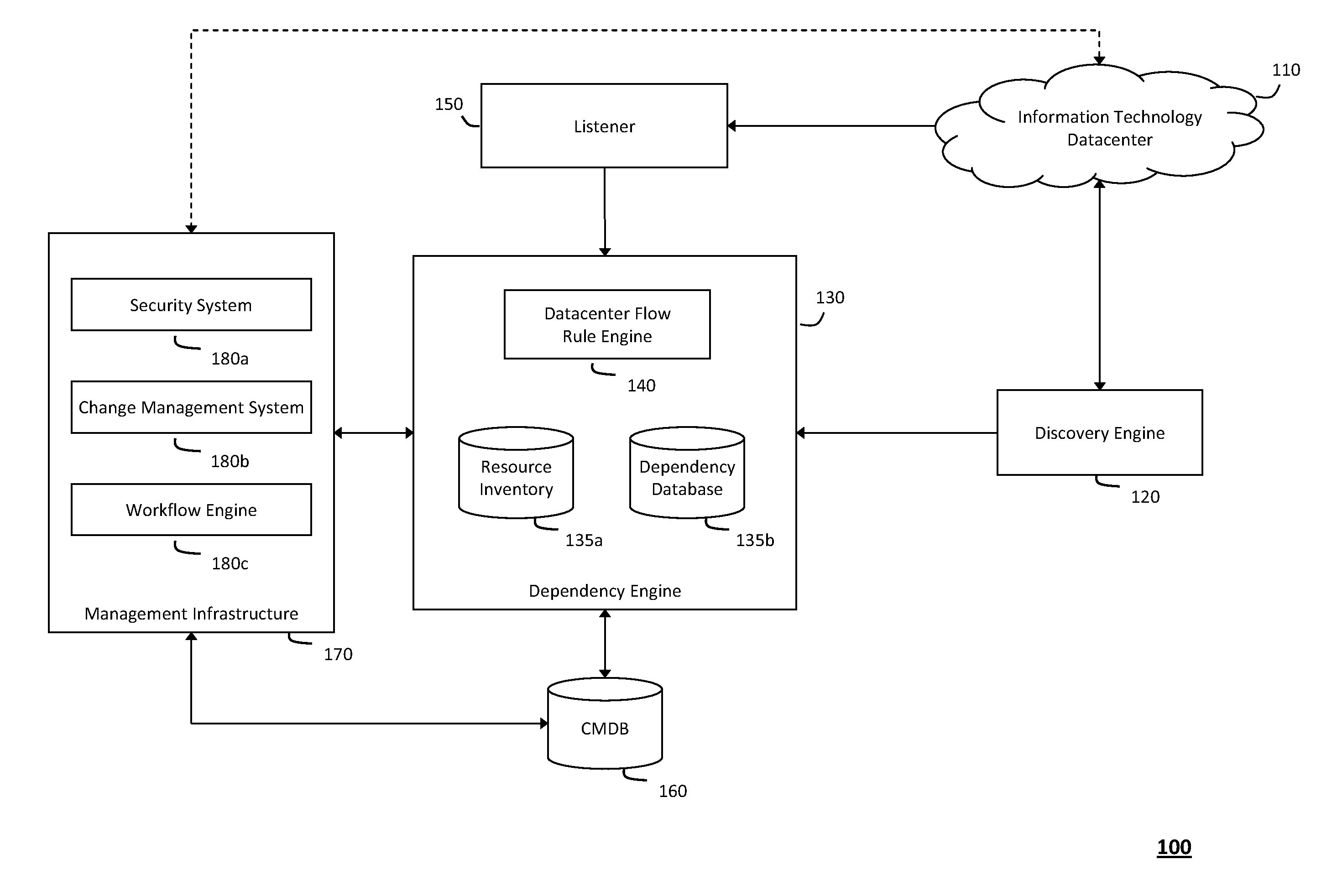
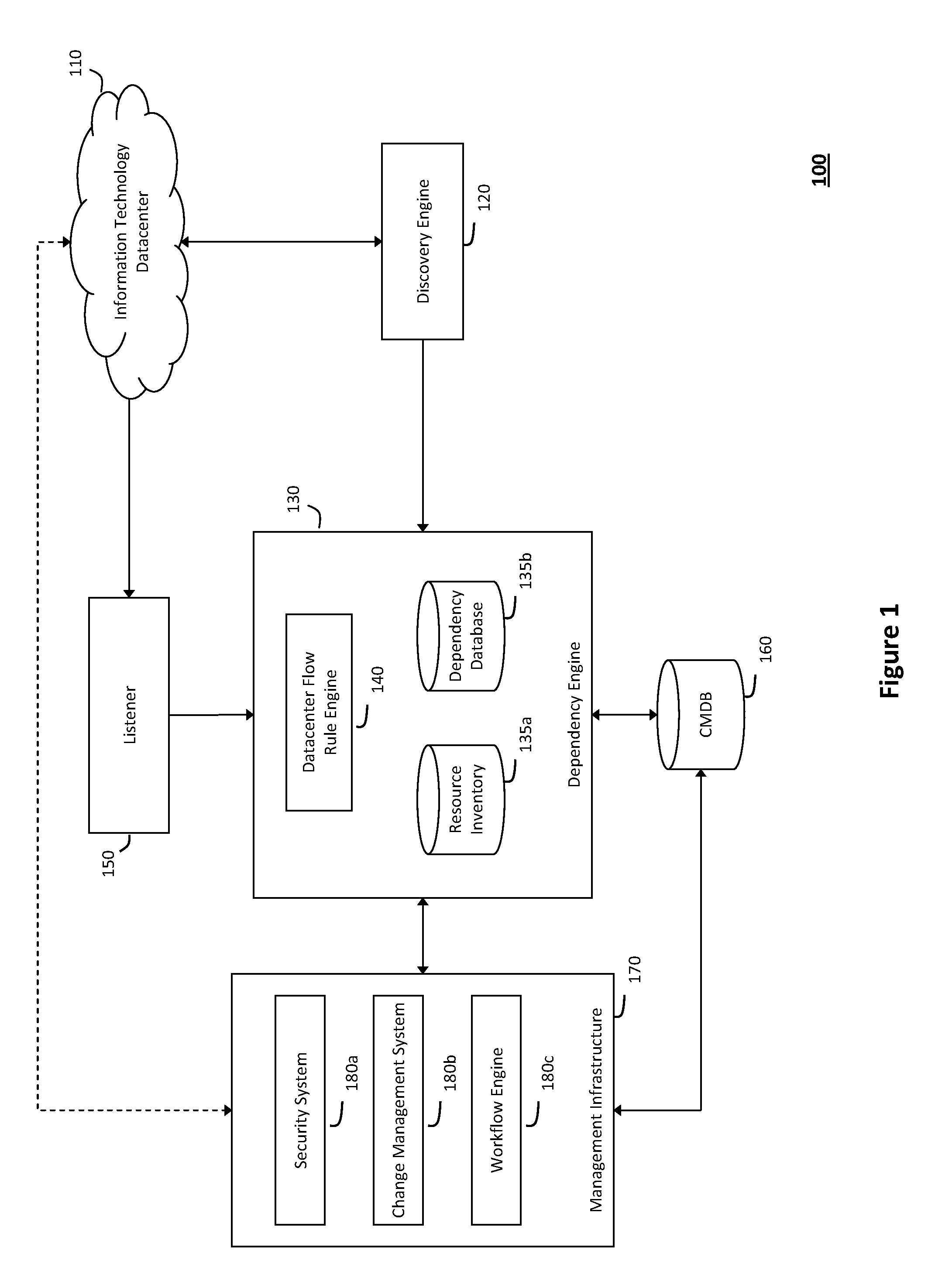
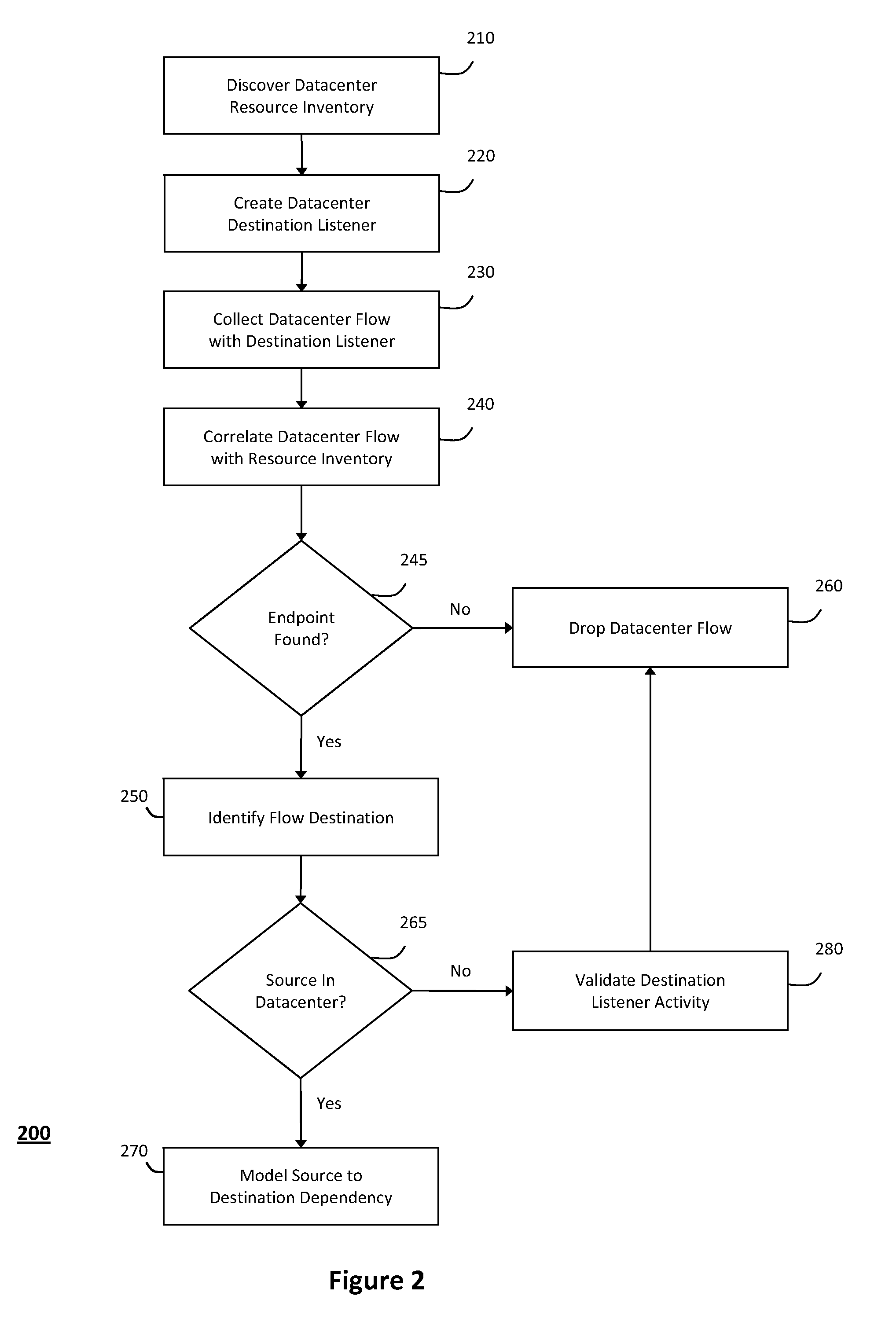
[0027]According to one aspect of the invention, FIG. 1 illustrates an exemplary system 100 for creating a configuration management database 160 in a network datacenter 110, wherein the configuration management database 160 created with the techniques described herein may be used to model interdependencies, detect real-time security threats, and manage proposed changes in the network datacenter 110. In particular, the system 100 shown in FIG. 1 and described herein may obtain accurate and timely information describing relationships and interdependencies in the datacenter 110, which may then be stored in a dependency database 135b containing information describing such relationships and interdependencies. As such, the information describing the relationships and interdependencies in the dependency database 135b may be used to seed the configuration management database 160. For example, in one implementation, the system 100 may employ Netflow or various other network protocols that can...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com