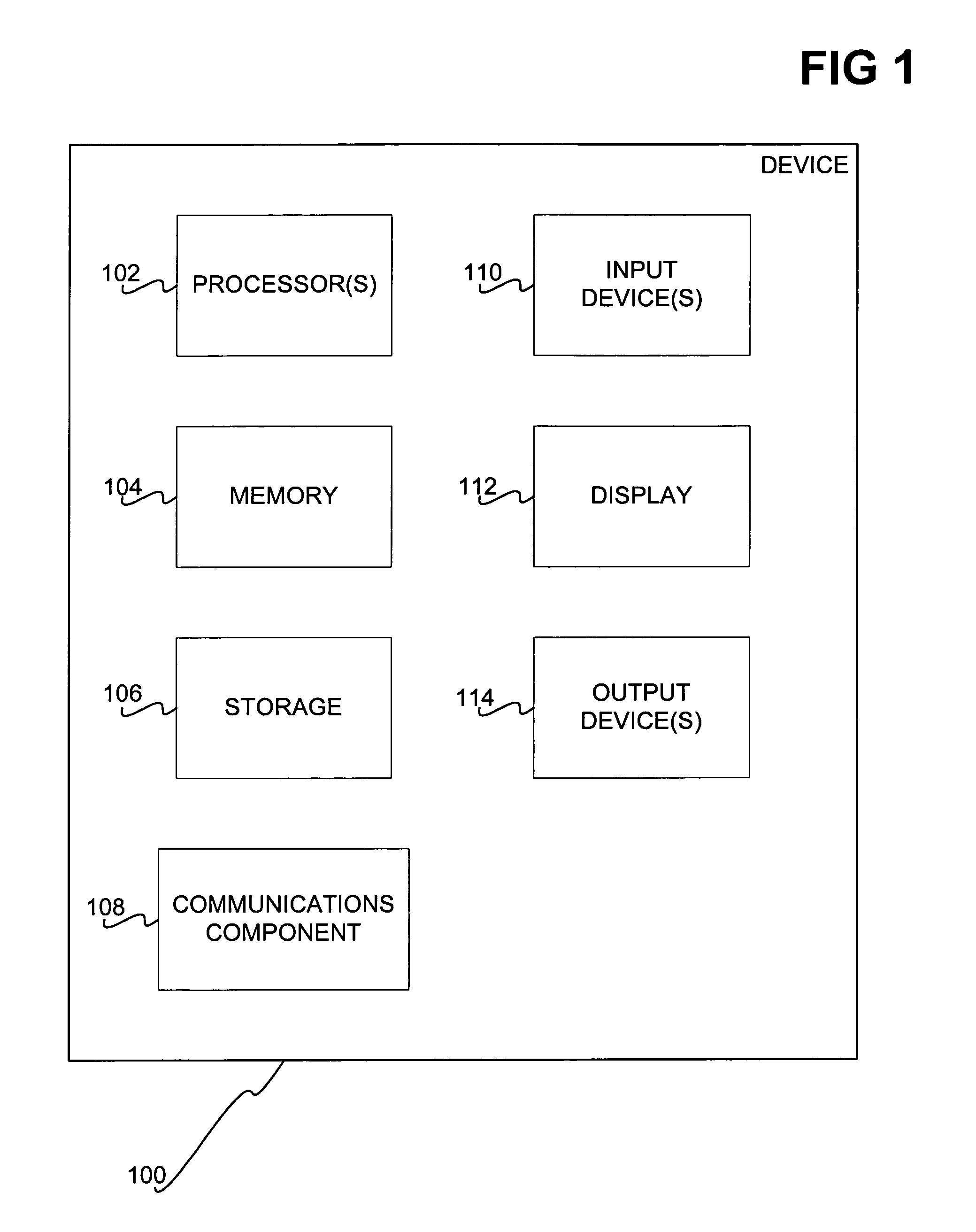
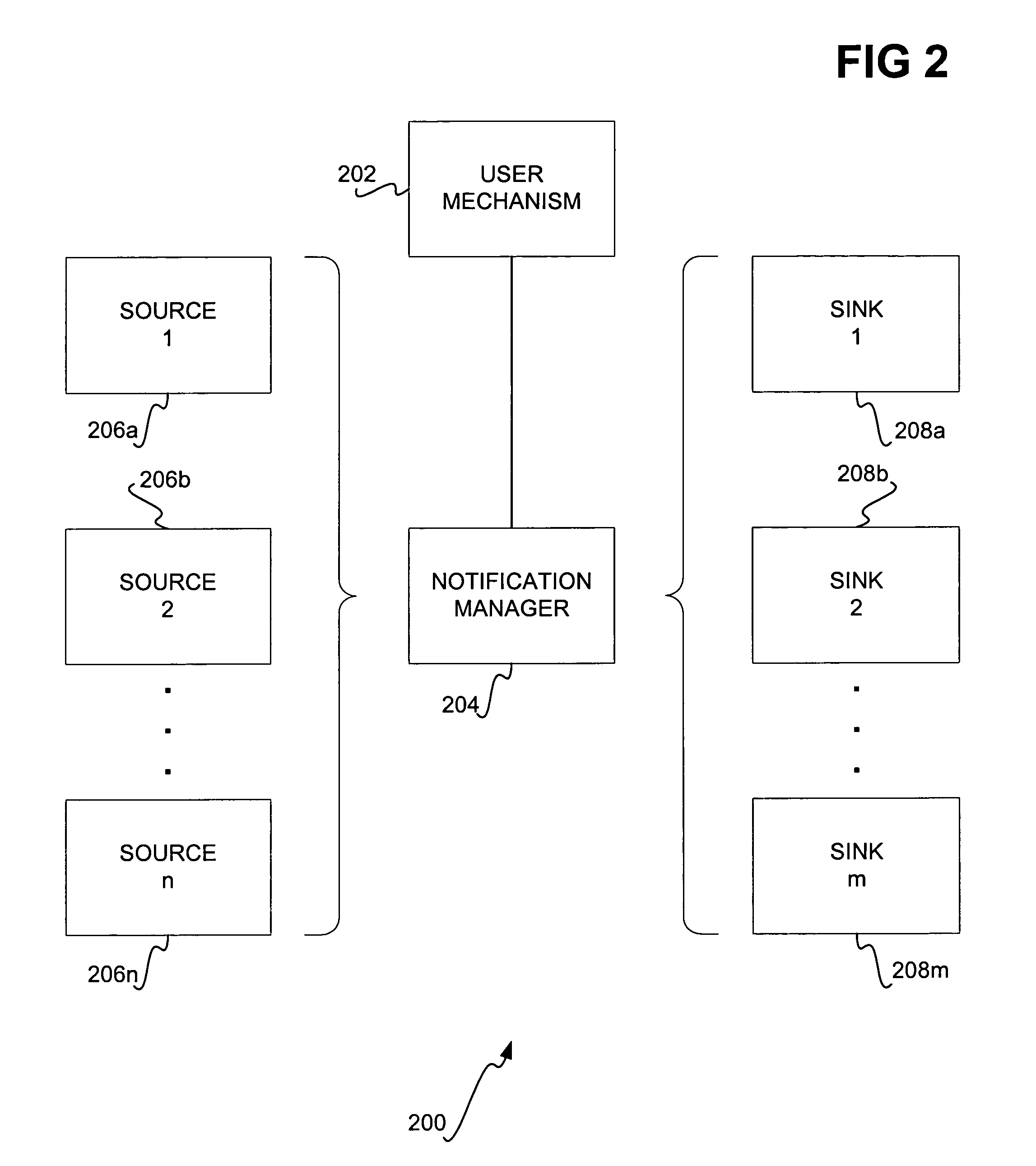
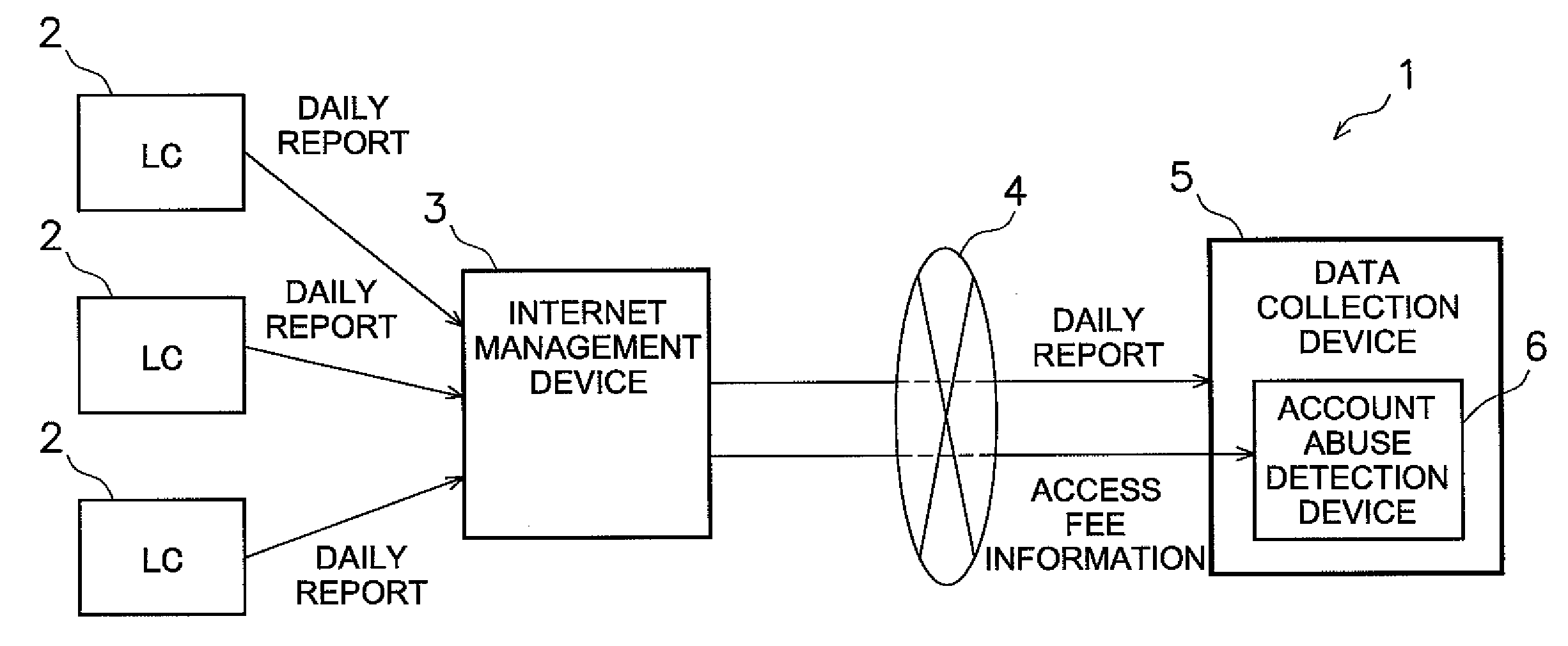
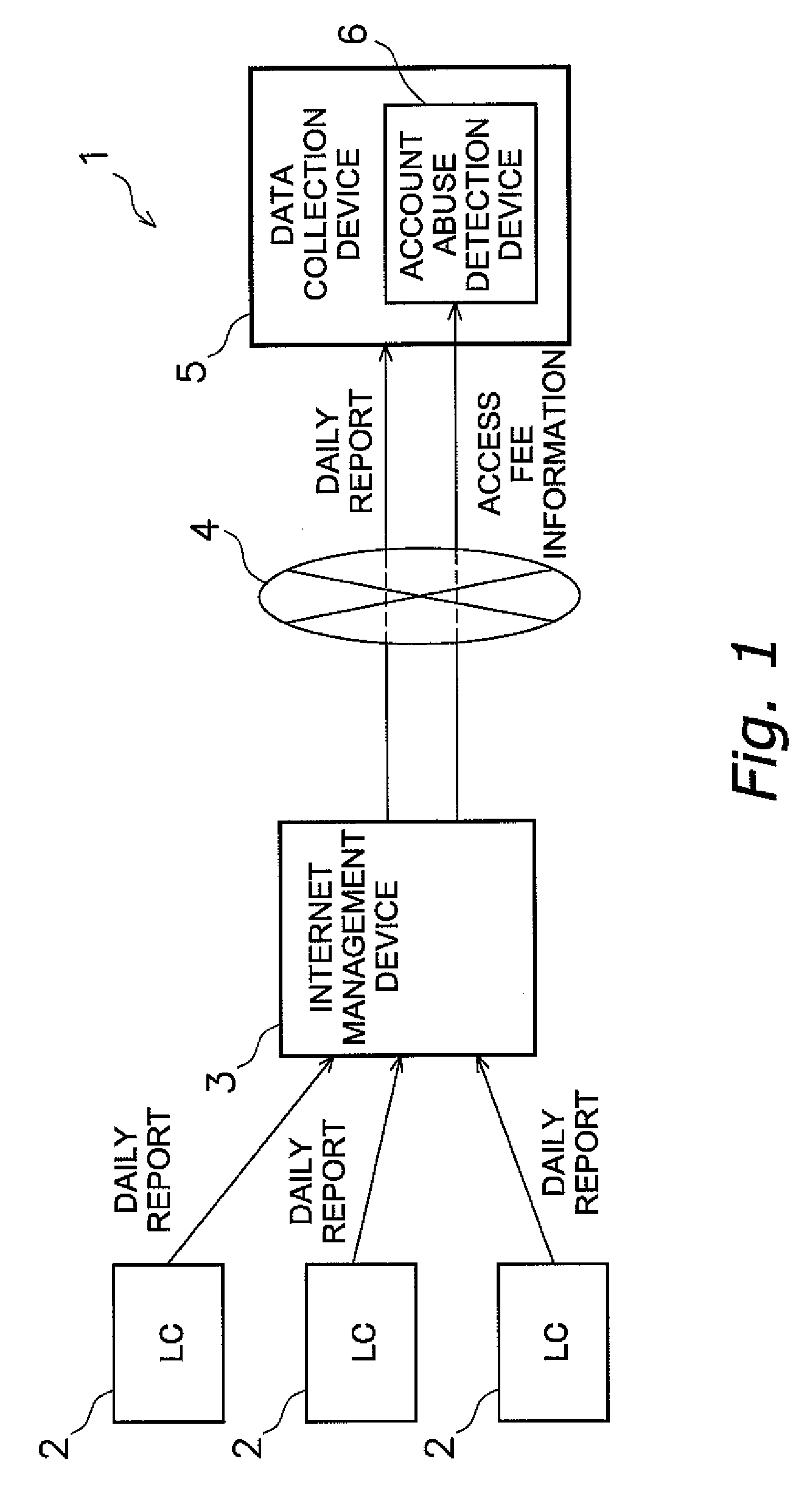
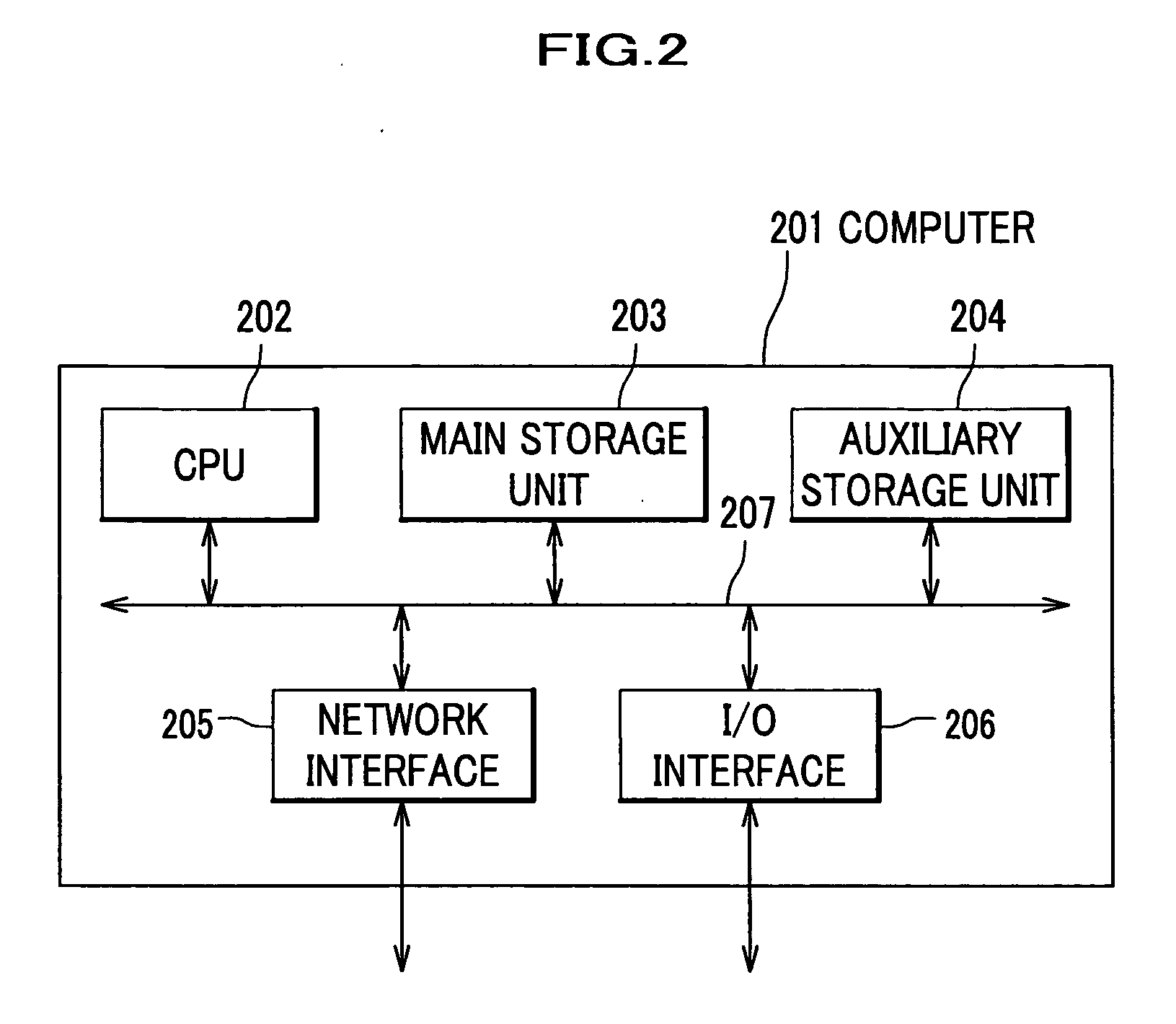
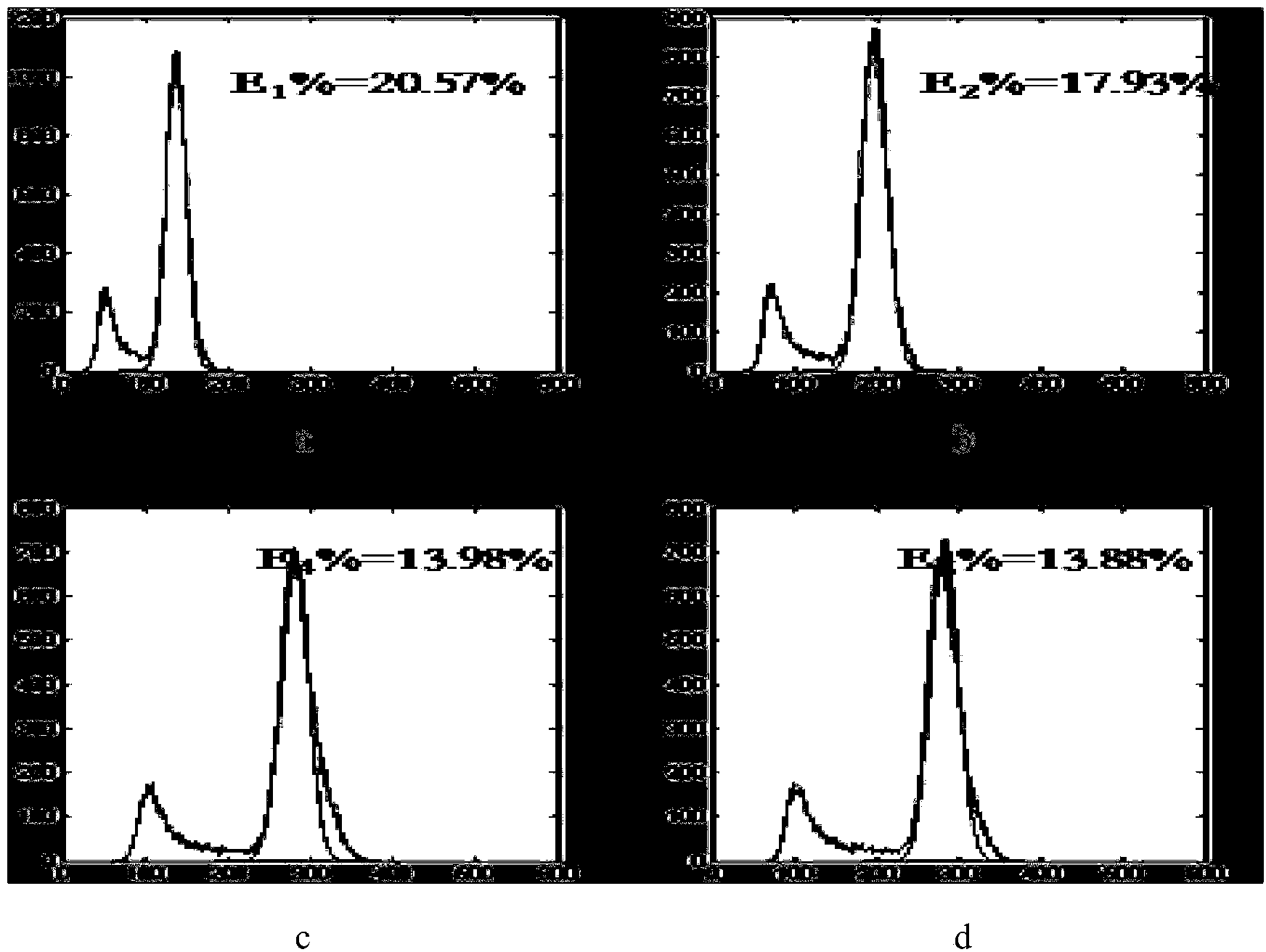
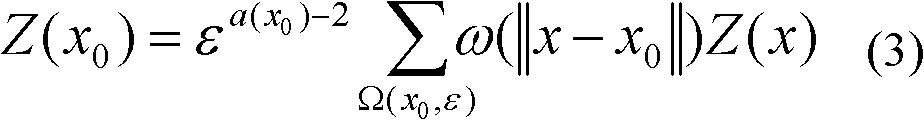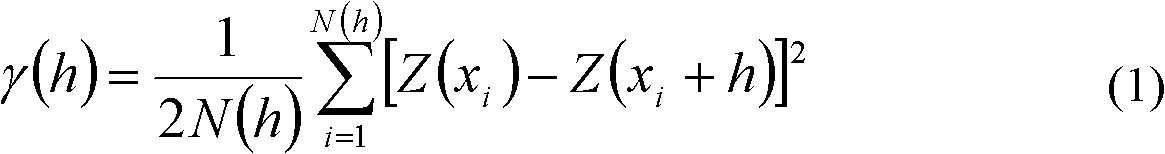Patents
Literature
204 results about "Value of information" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
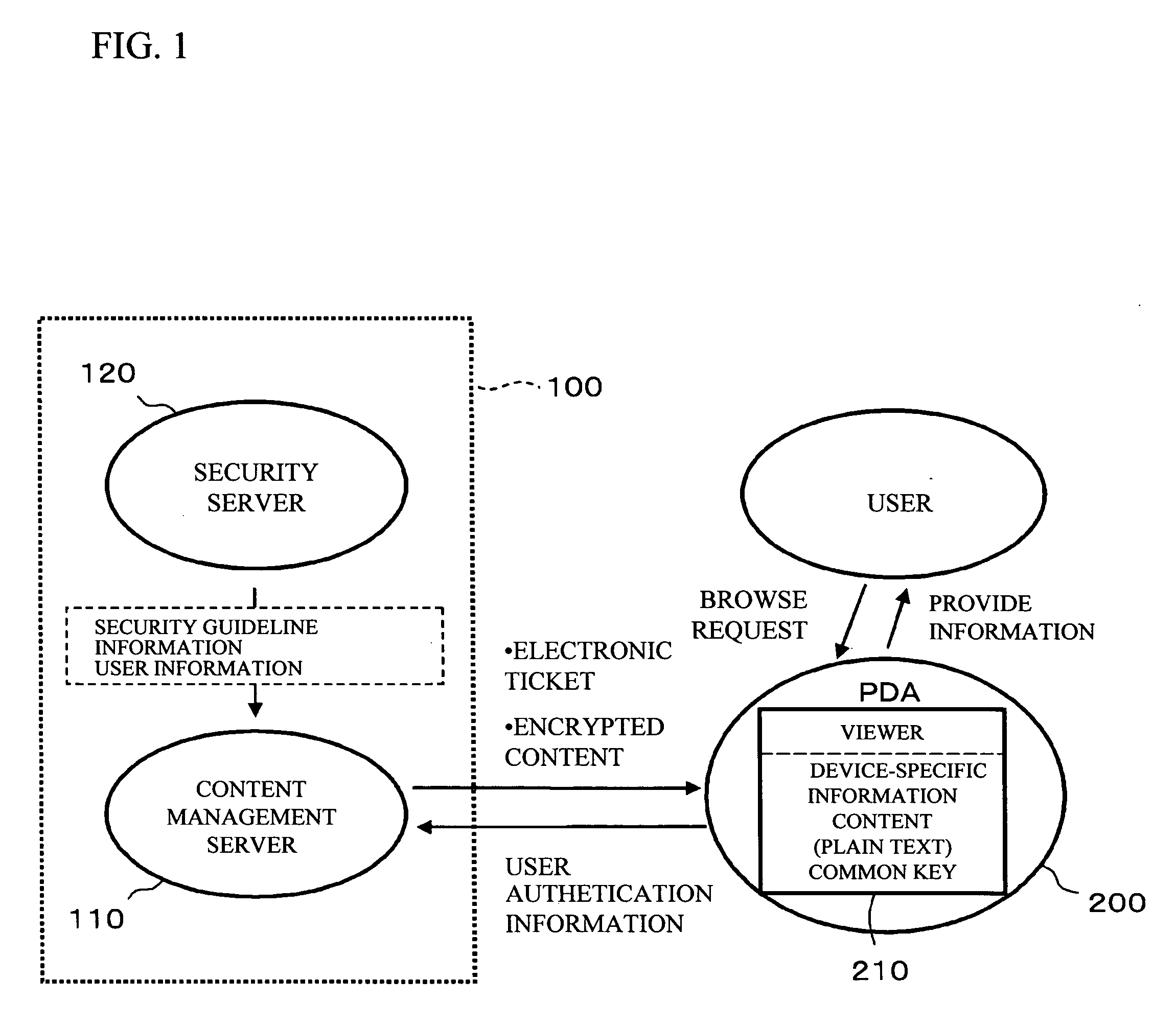
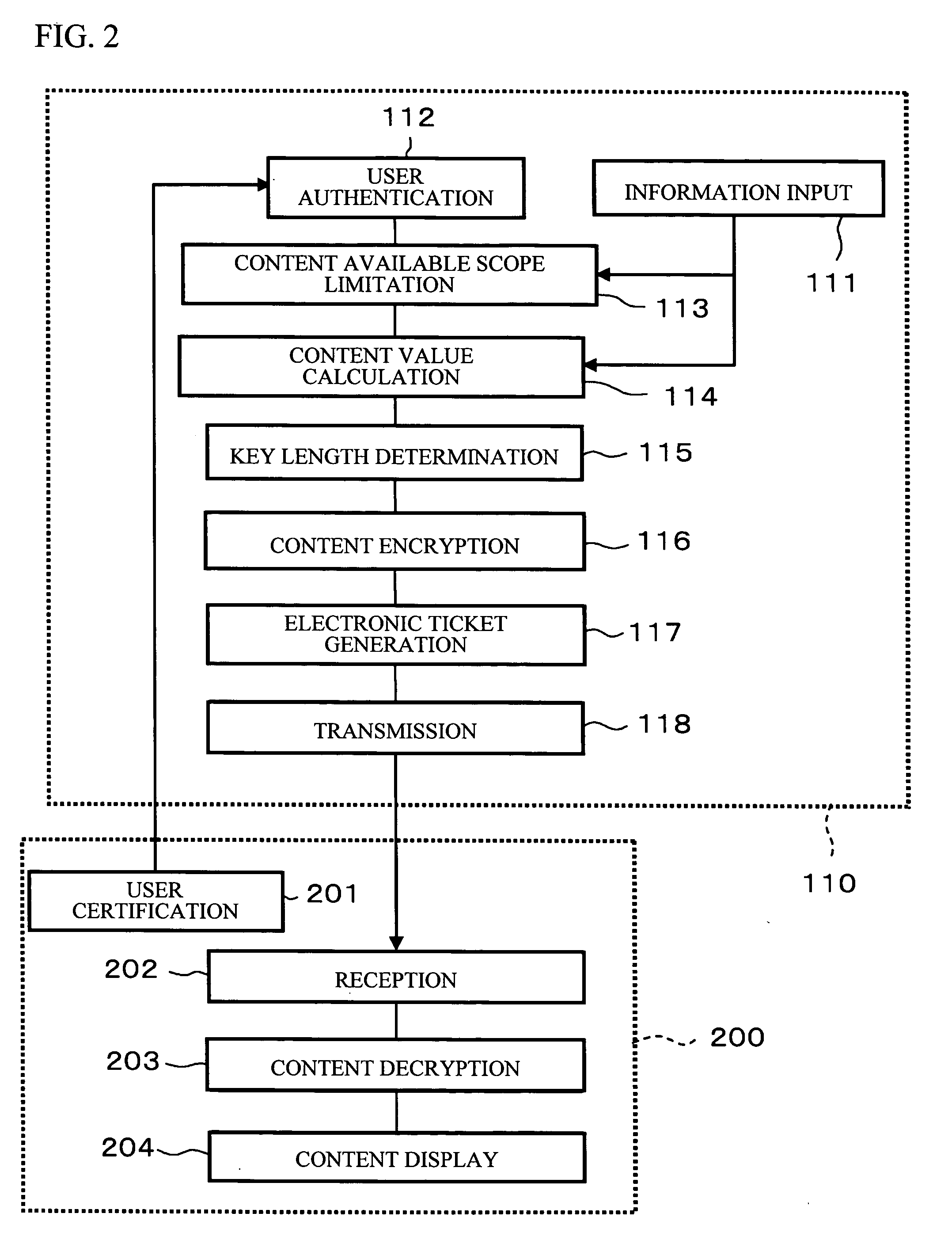
Value of information (VOI or VoI) is the amount a decision maker would be willing to pay for information prior to making a decision.
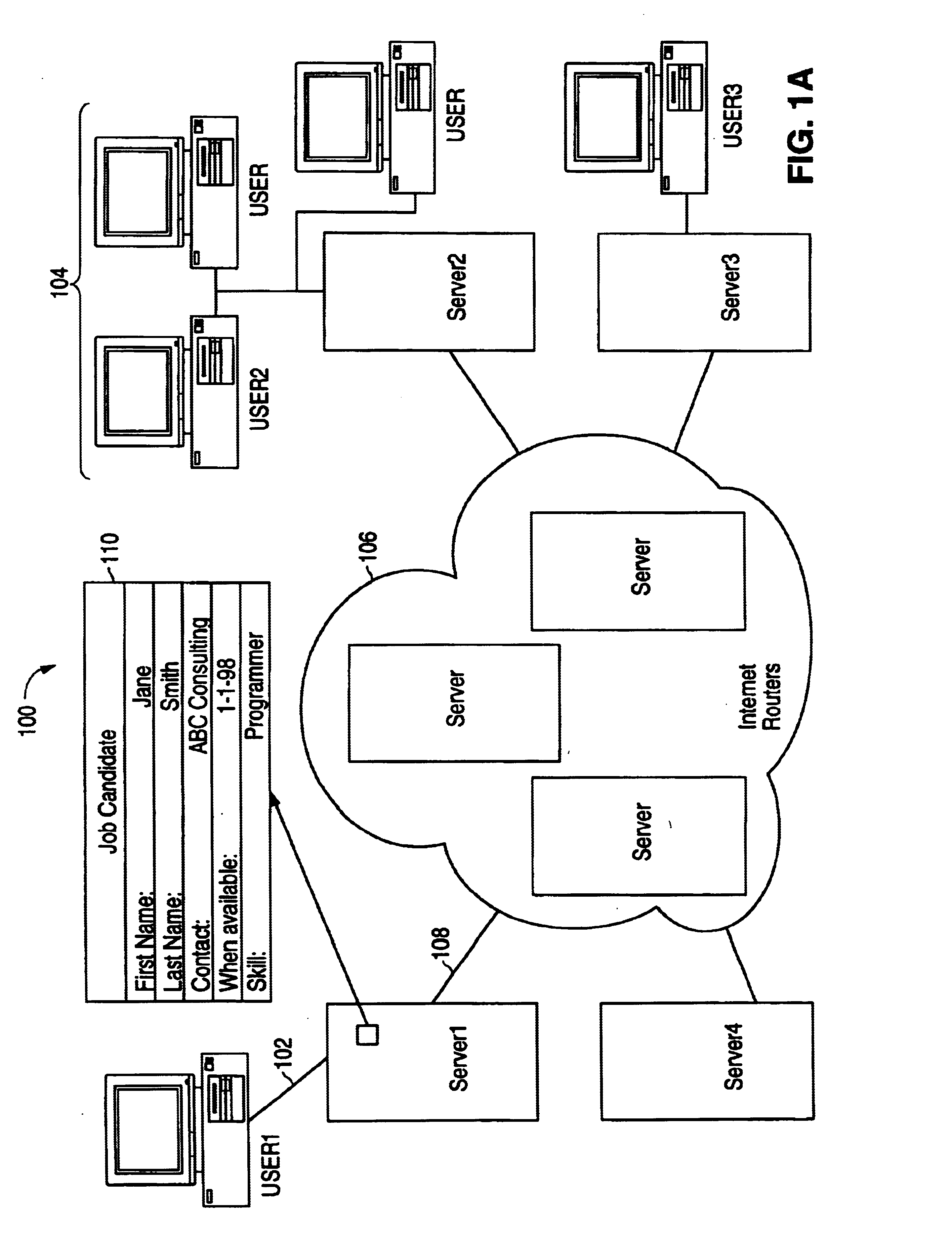
Product value information interchange server
InactiveUS7133834B1Improve recognitionImprove market shareMarket predictionsClient-sideService information
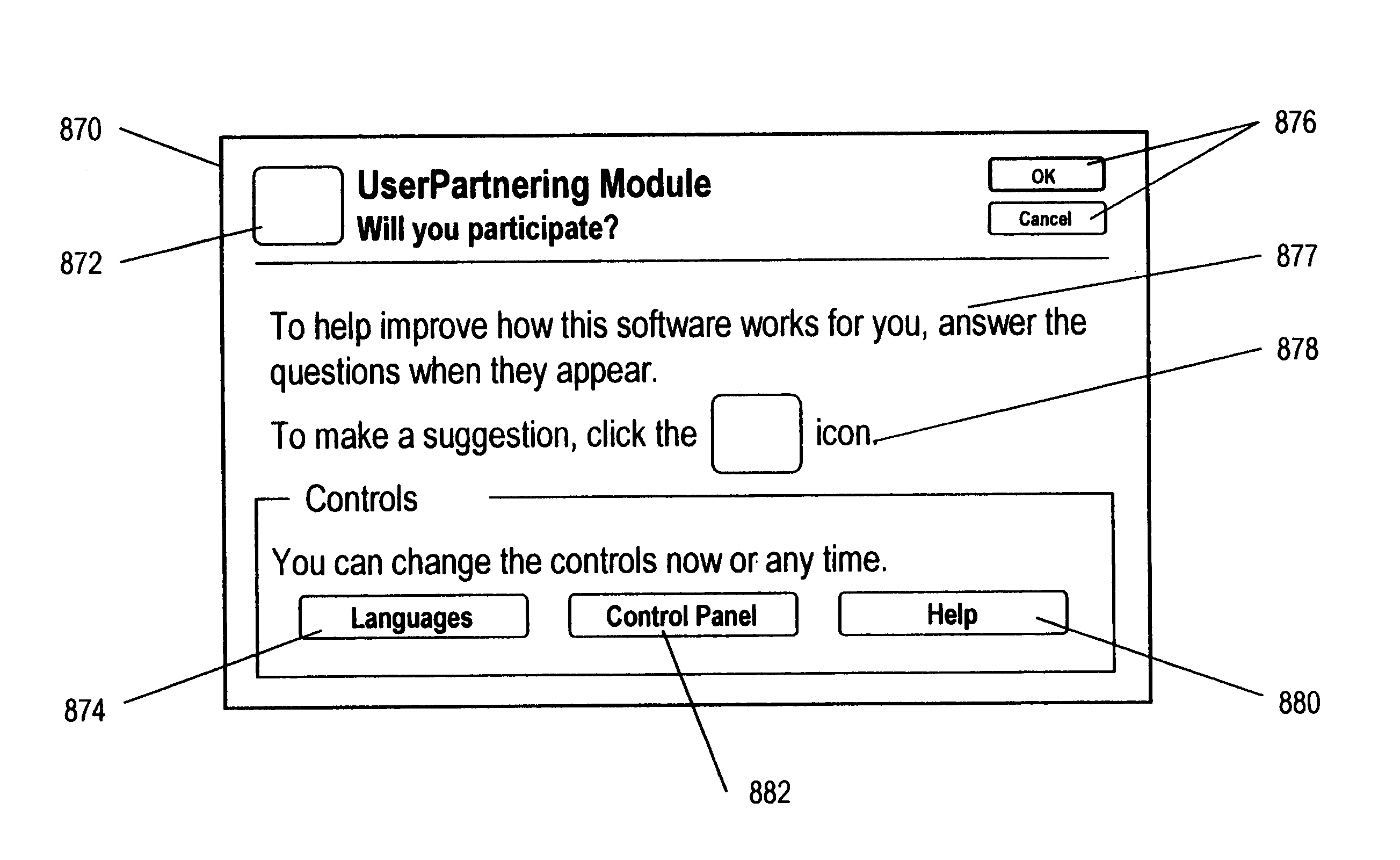
An electronically accessible server receives, stores, and sends value information from customers. The server or other digital medium stores the value information generated by independent users. Triggers or interactions can be used to determine when value information would be useful for a user of a client system. The value information can include customer assessments, usage frequency, navigational pointers, executable program code, instructions, product information, and service information. A digital medium is used to store value information generated by independent users. The medium can be coupled to an electronic communication network to allow for interchange of information.
Owner:LODSYS GRP
Methods and apparatus for predicting and selectively collecting preferences based on personality diagnosis
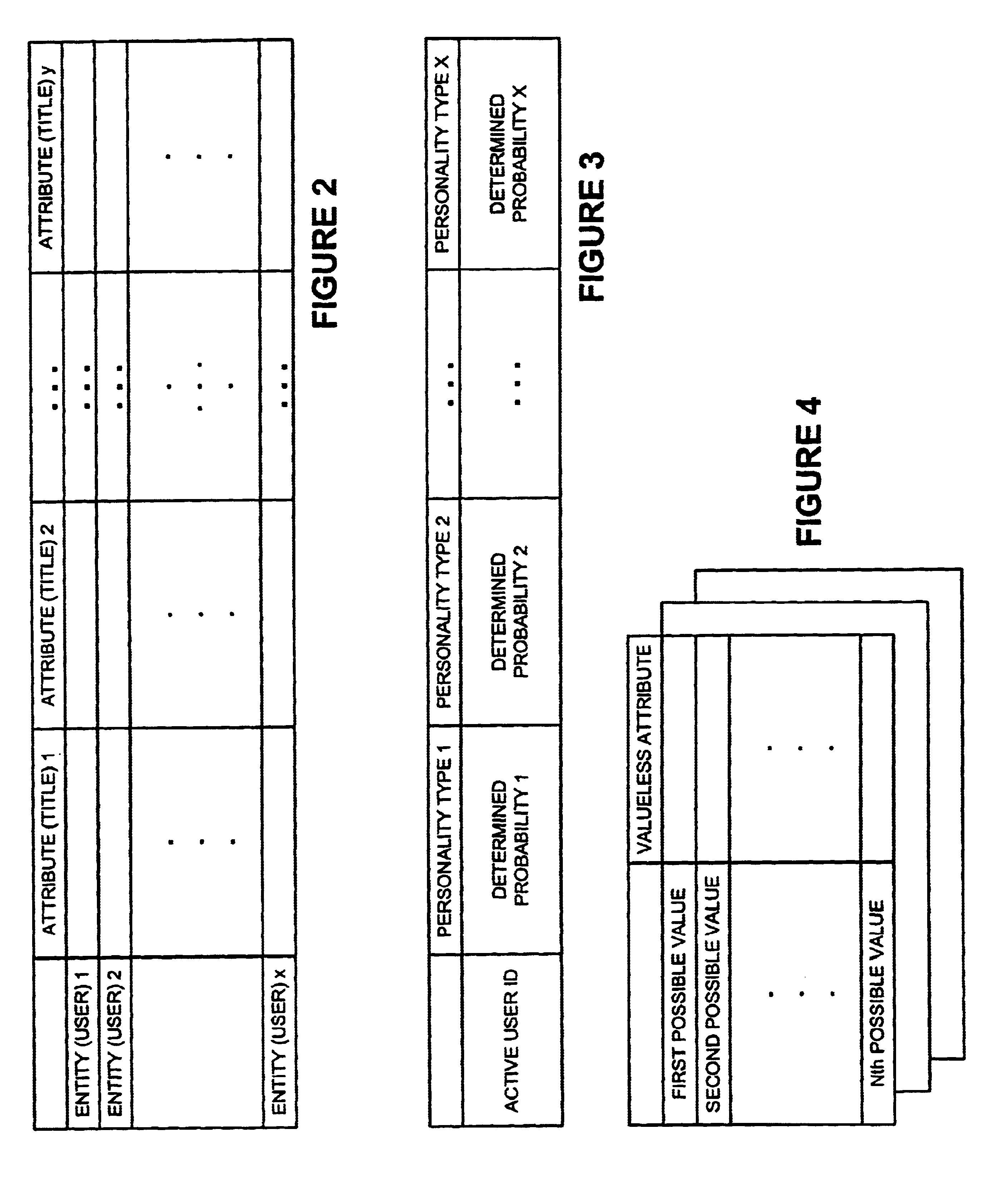
InactiveUS20040076936A1Minimal effectCumbersome processMarket predictionsBuying/selling/leasing transactionsProbabilistic semanticsValue of information
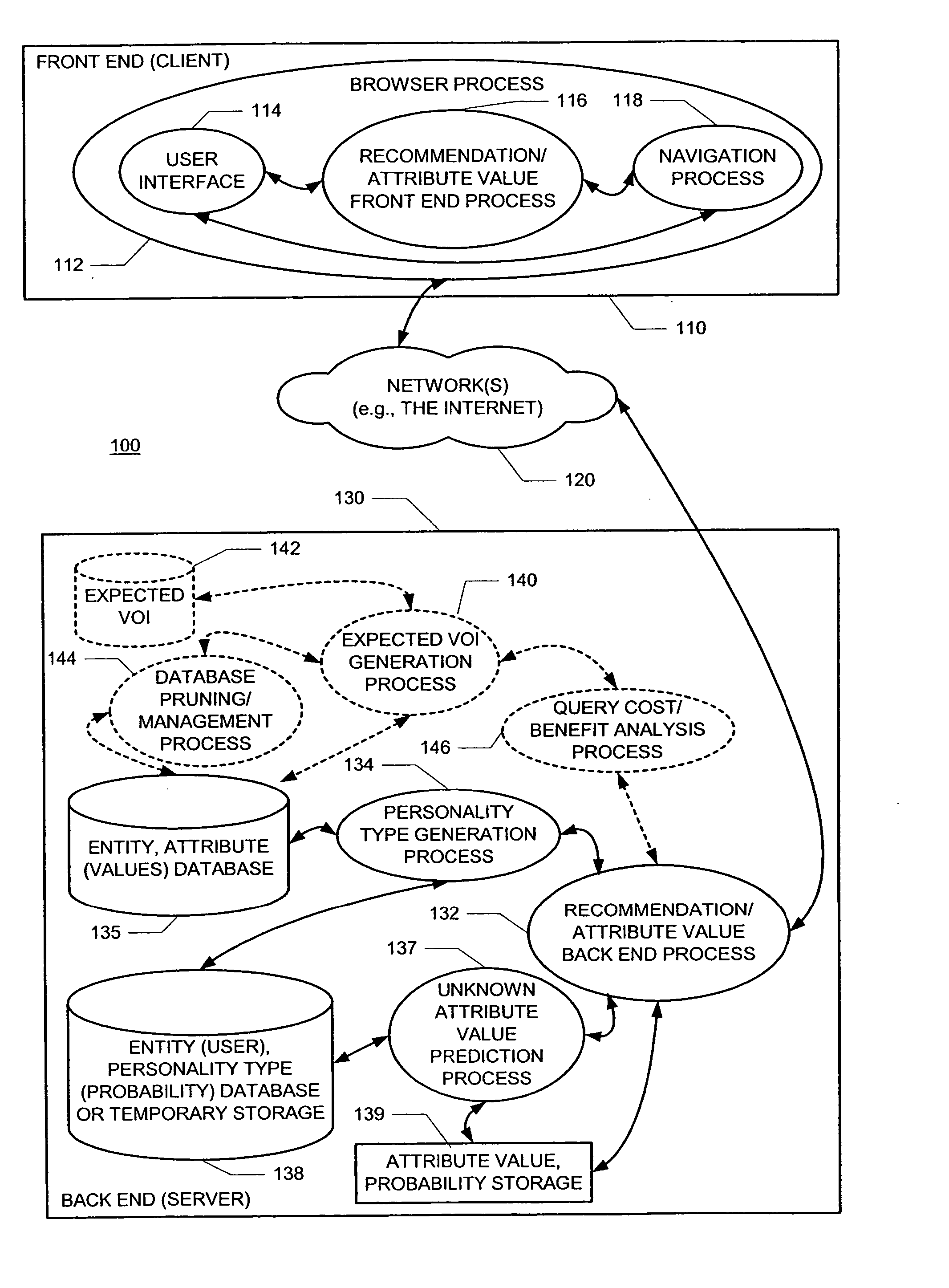
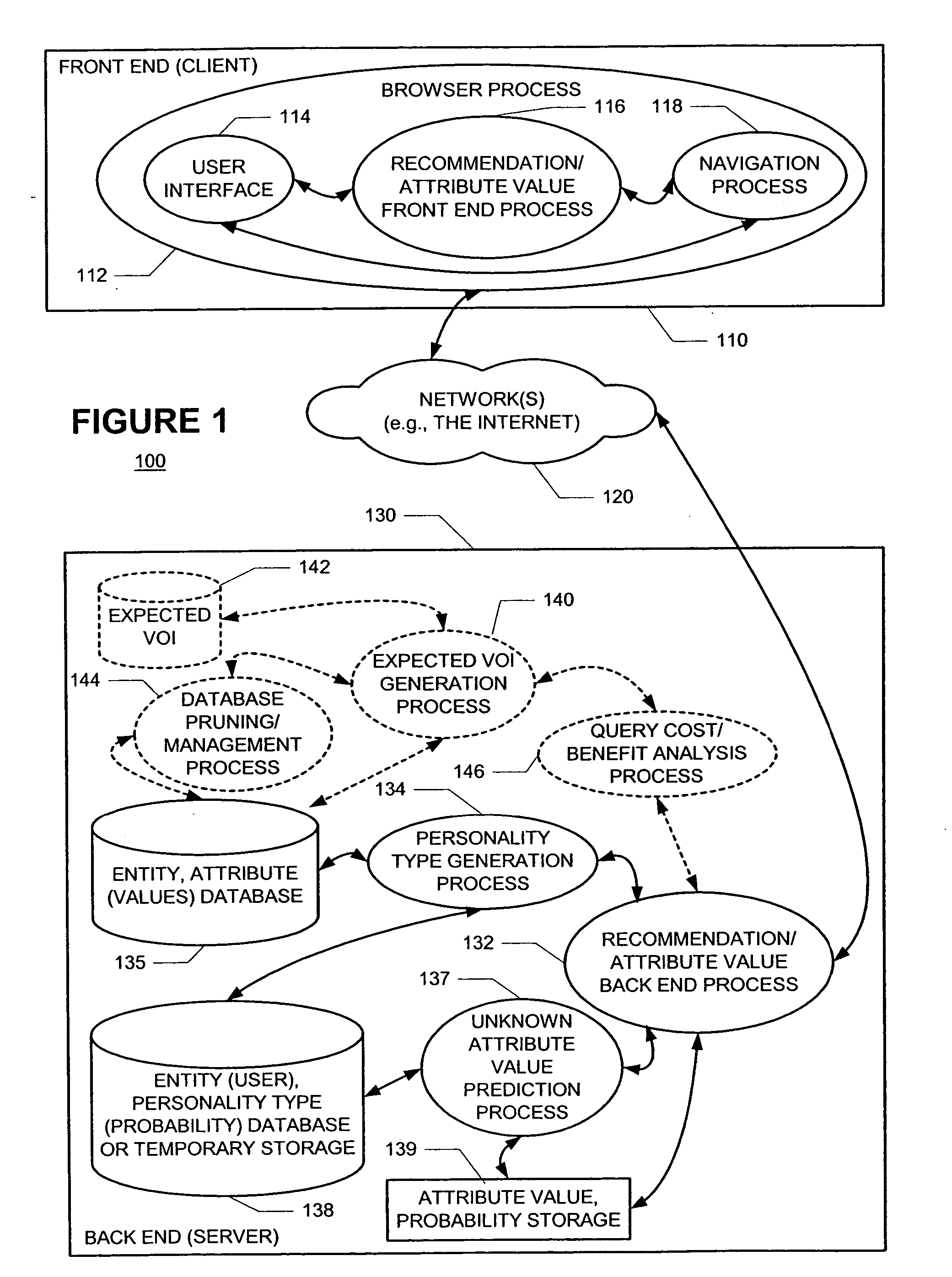
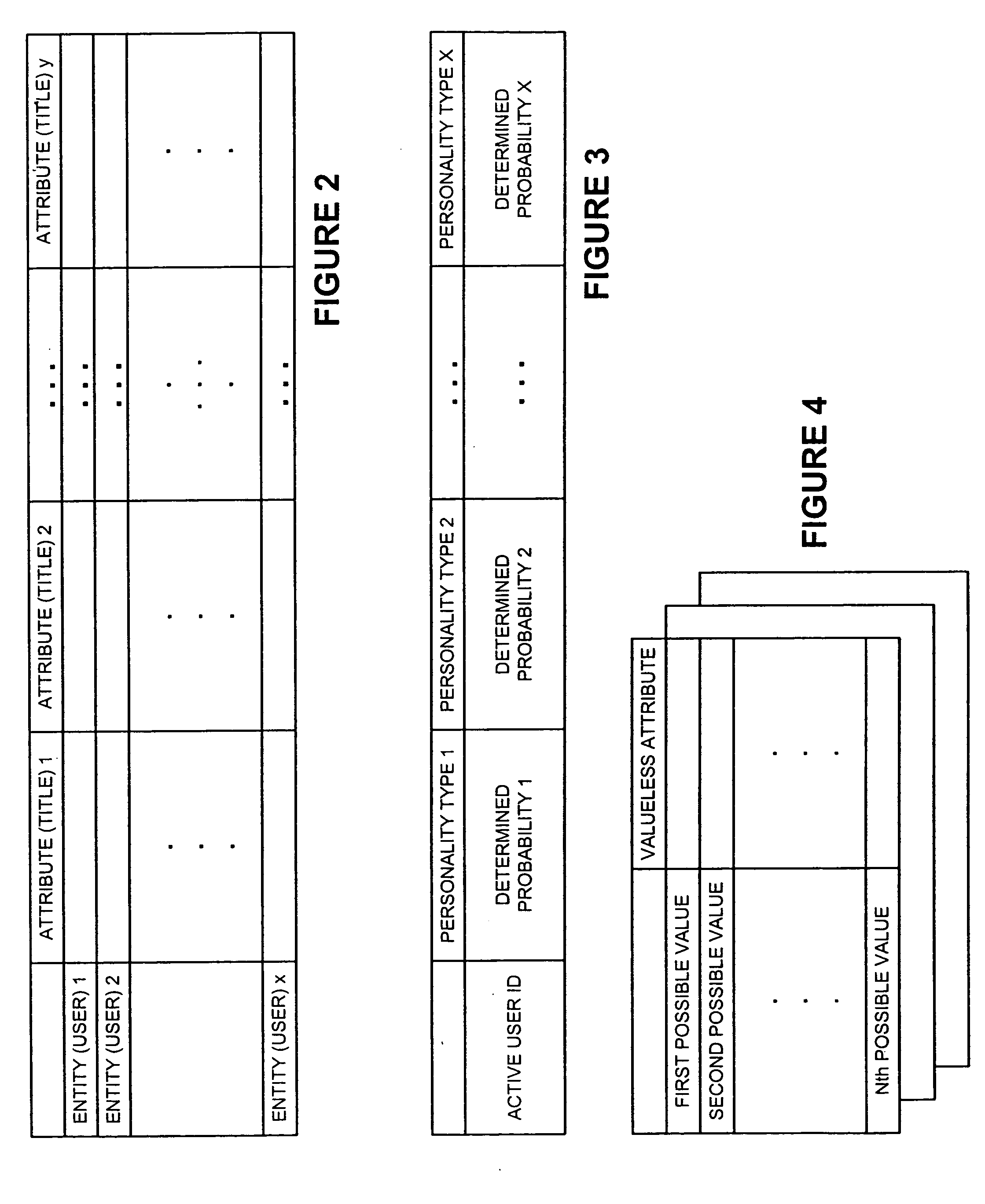
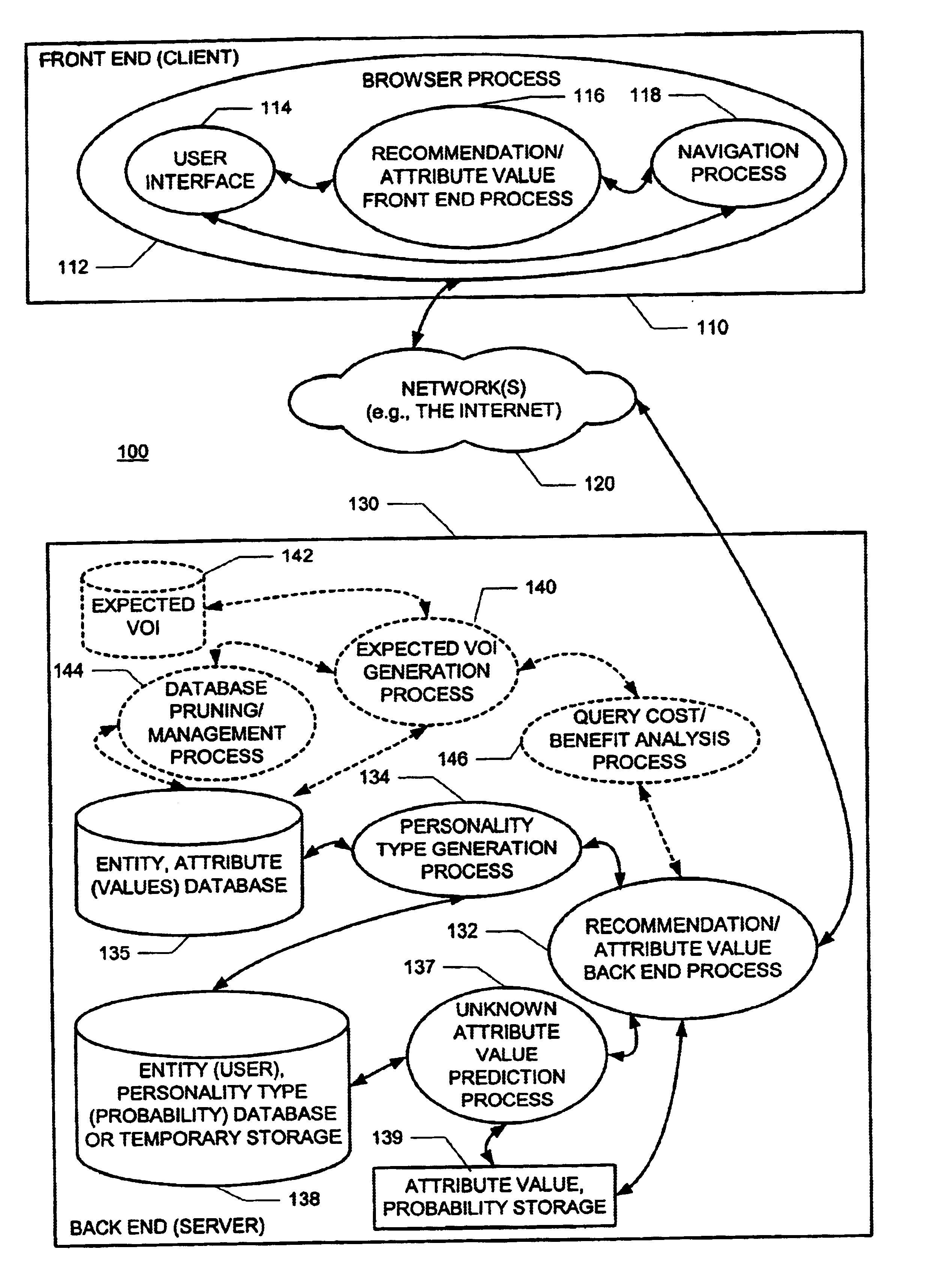
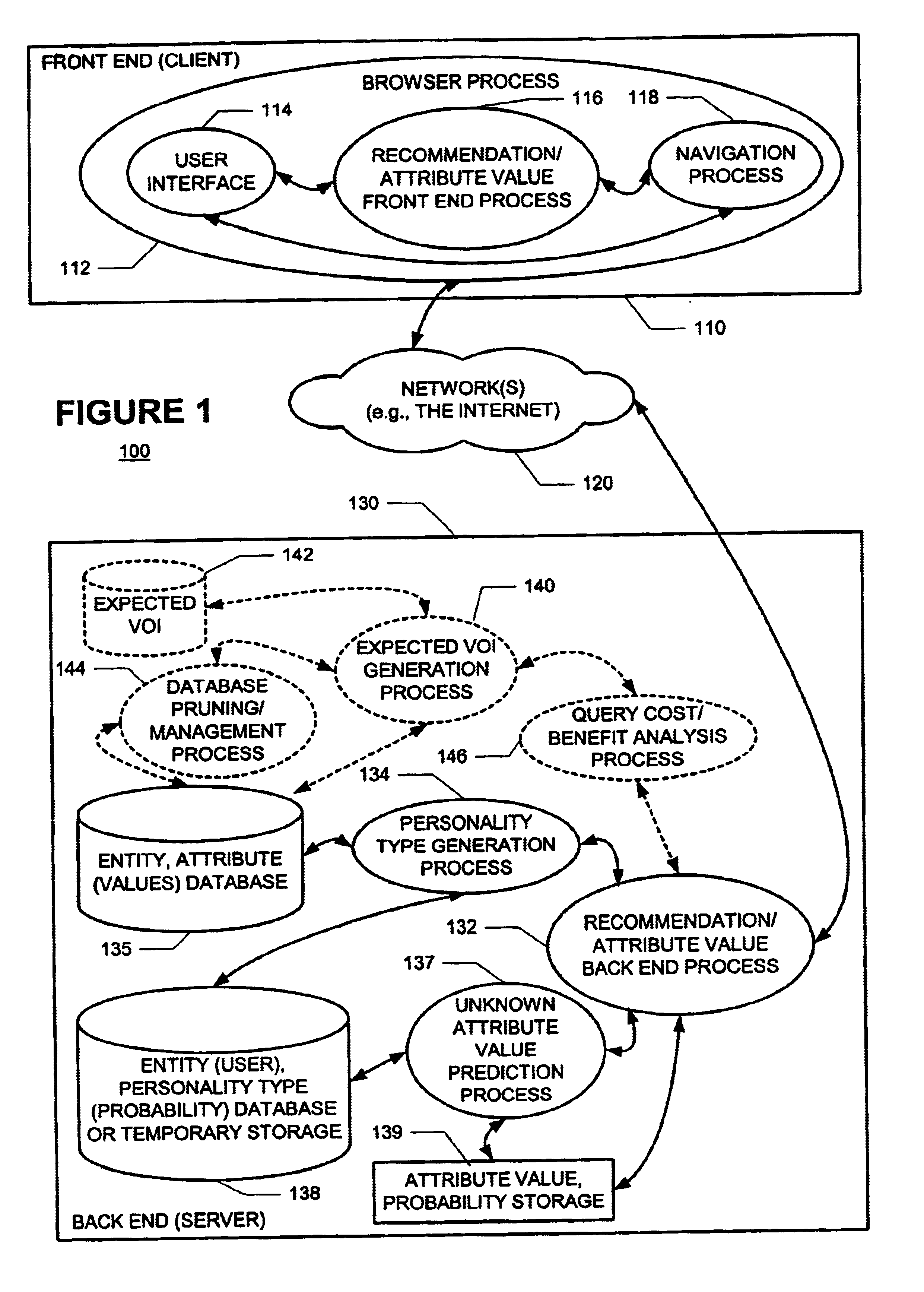
A new recommendation technique, referred to as "personality diagnosis", that can be seen as a hybrid between memory-based and model-based collaborative filtering techniques, is described. Using personality diagnosis, all data may be maintained throughout the processes, new data can be added incrementally, and predictions have meaningful probabilistic semantics. Each entity's (e.g., user's) reported attributes (e.g., item ratings or preferences) may be interpreted as a manifestation of their underlying personality type. Personality type may be encoded simply as a vector of the entity's (e.g., user's) "true" values (e.g., ratings) for attributes (e.g., items) in the database. It may be assumed that entities (e.g., users) report values (e.g., ratings) with a distributed (e.g., Gaussian) error. Given an active entity's (e.g., user's) known attribute values (e.g., item ratings), the probability that they have the same personality type as every other entity (e.g., user) may be determined. Then, the probability that they will have a given value (e.g., rating) for a valueless (e.g., unrated) attribute (e.g., item) may then be determined based on the entity's (e.g., user's) personality type. The probabilistic determinations may be used to determine expected value of information. Such an expected value of information could be used in at least two ways. First, an interactive recommender could use expected value of information to favorably order queries for attribute values (e.g., item ratings), thereby mollifying what could otherwise be a tedious and frustrating process. Second, expected value of information could be used to determine which entries of a database to prune or ignore-that is, which entries, which if removed, would have a minimal effect of the accuracy of recommendations.
Owner:MICROSOFT TECH LICENSING LLC
Methods and apparatus for predicting and selectively collecting preferences based on personality diagnosis
InactiveUS6655963B1Cumbersome processMinimal effectMarket predictionsBuying/selling/leasing transactionsProbabilistic semanticsData mining
A new recommendation technique, referred to as "personality diagnosis", can be seen as a hybrid between memory-based and model-based collaborative filtering techniques. Using personality diagnosis, all data can be maintained throughout the processes, new data can be added incrementally, and predictions have meaningful probabilistic semantics. Each entity's reported attributes can be interpreted as a manifestation of their underlying personality type. Personality type can be encoded simply as a vector of the entity's "true" values for attributes in the database. Given an active entity's known attribute values, the probability that they have the same personality type as every other entity can be determined. Then, the probability that they will have a given value for a valueless attribute can then be determined based on the entity's personality type. The probabilistic determinations can be used to determine expected value of information.
Owner:MICROSOFT TECH LICENSING LLC
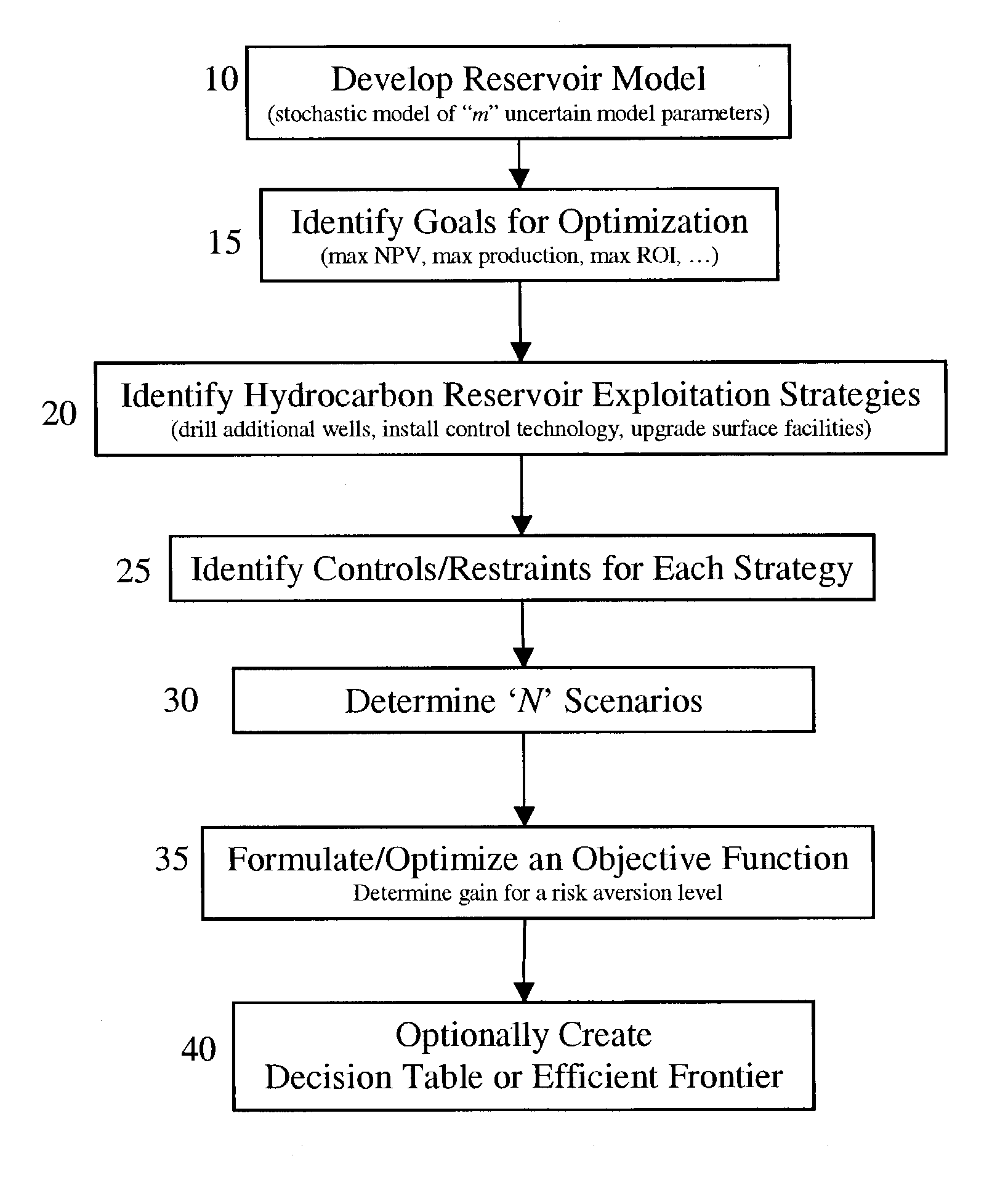
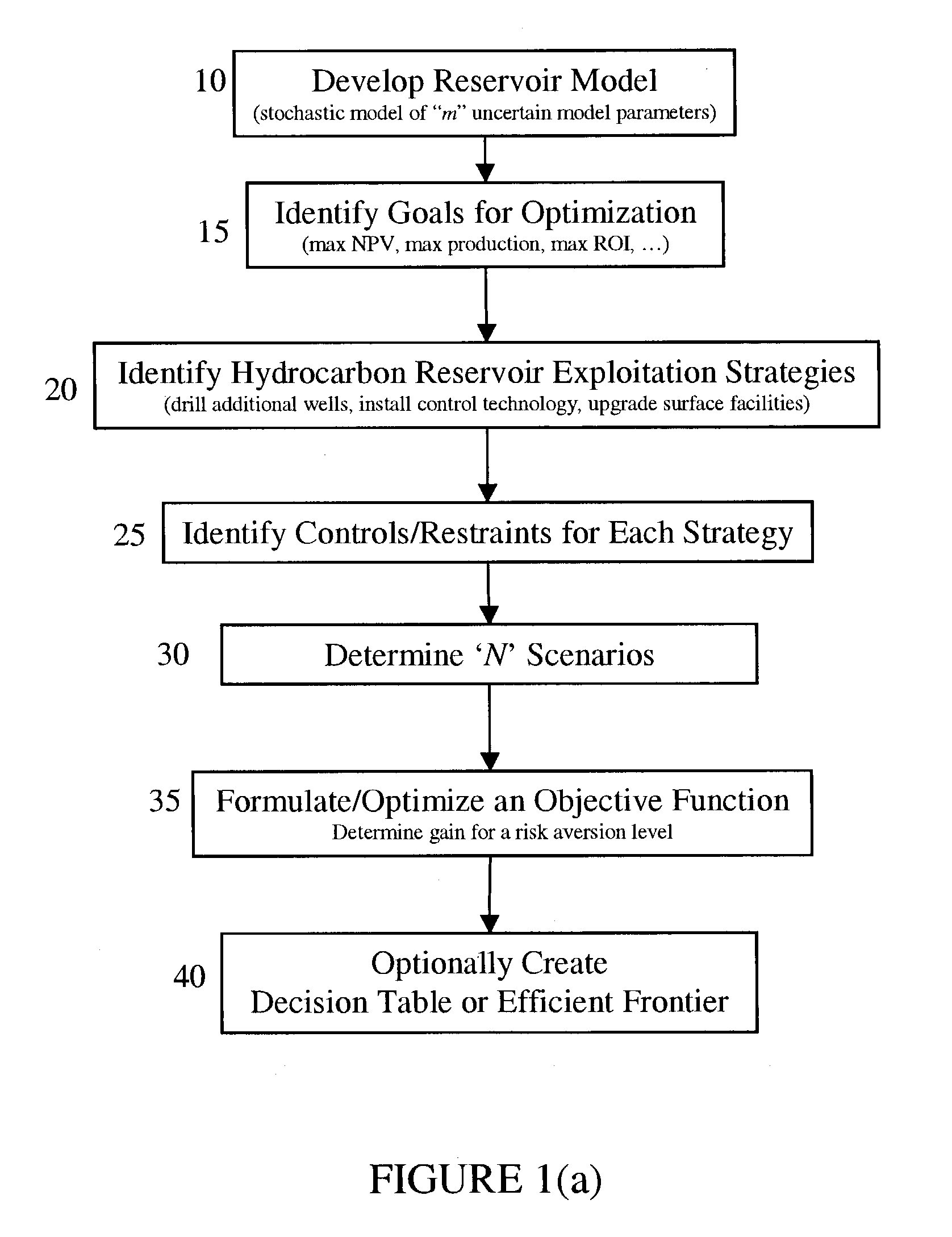
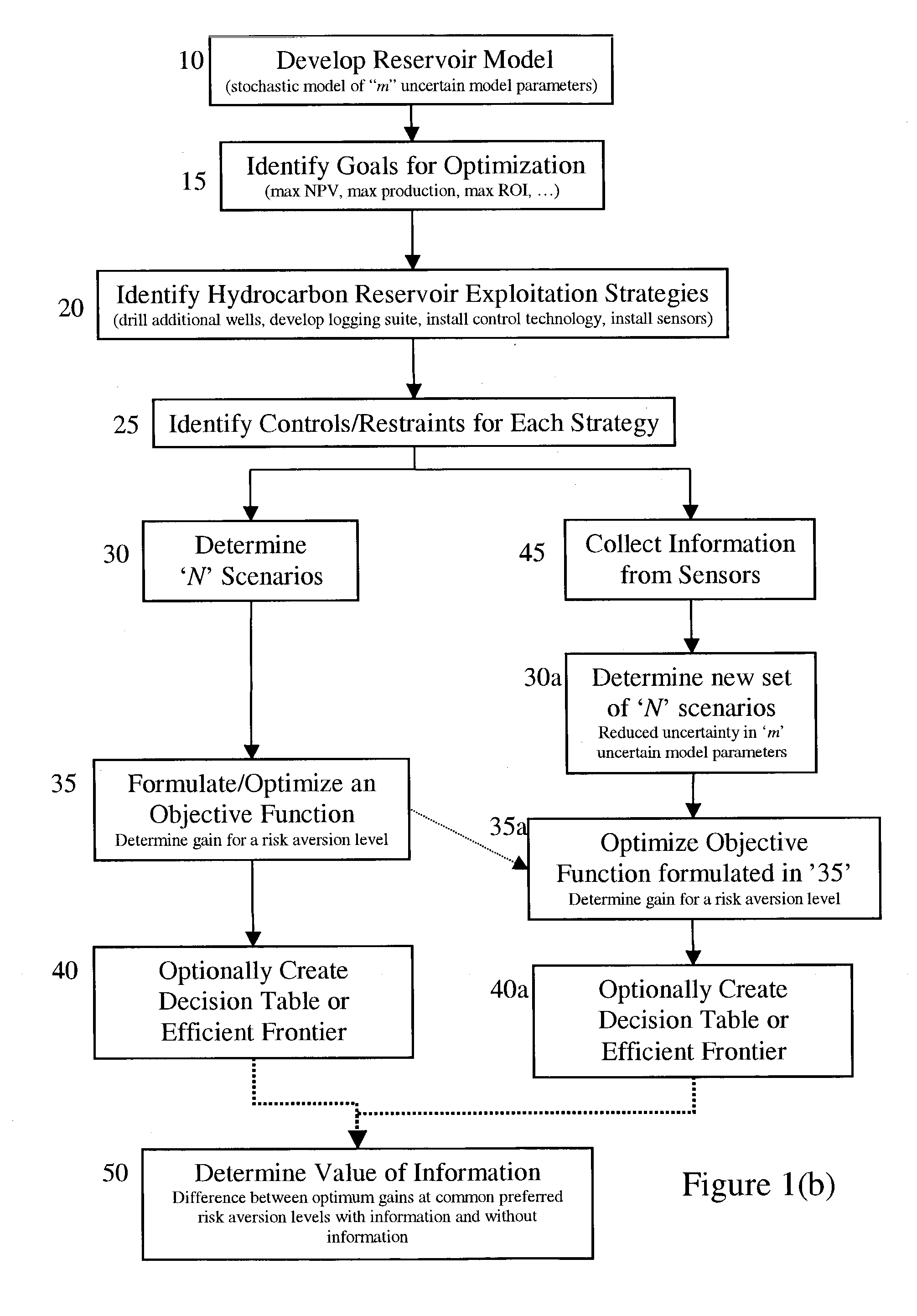
Tools for decision-making in reservoir risk management
ActiveUS20030225606A1FinanceComputation using non-denominational number representationEngineeringStochastic calculus
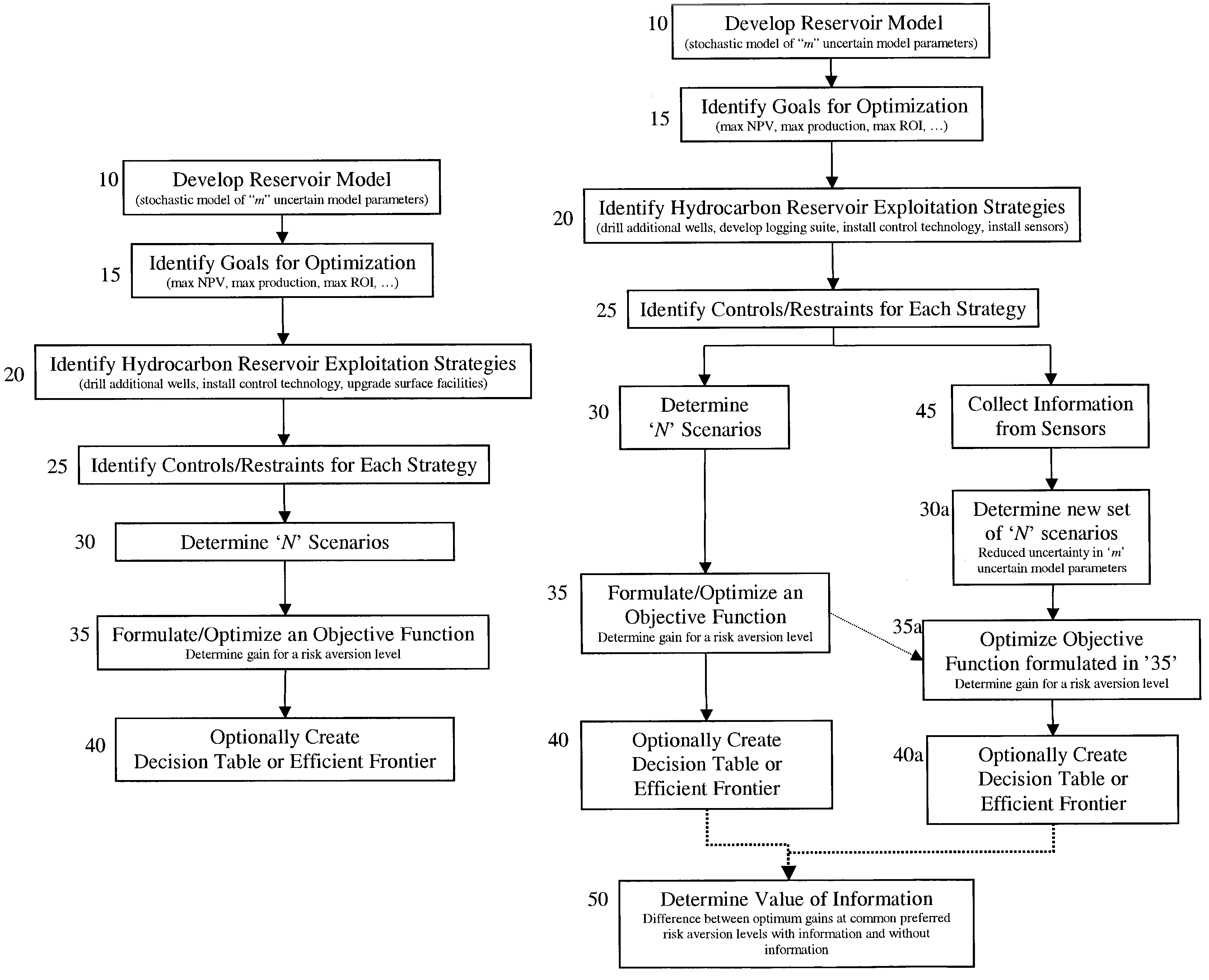
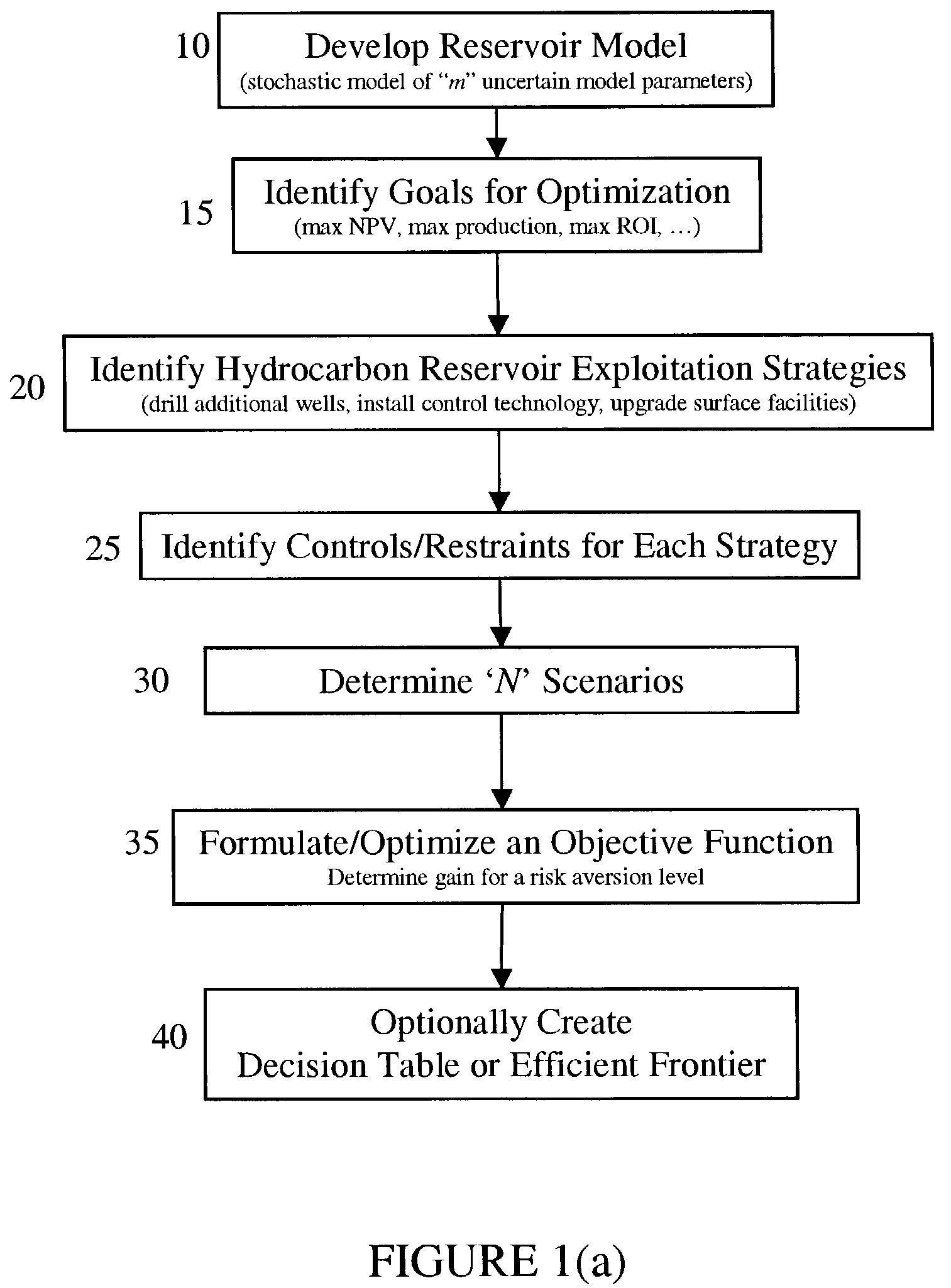
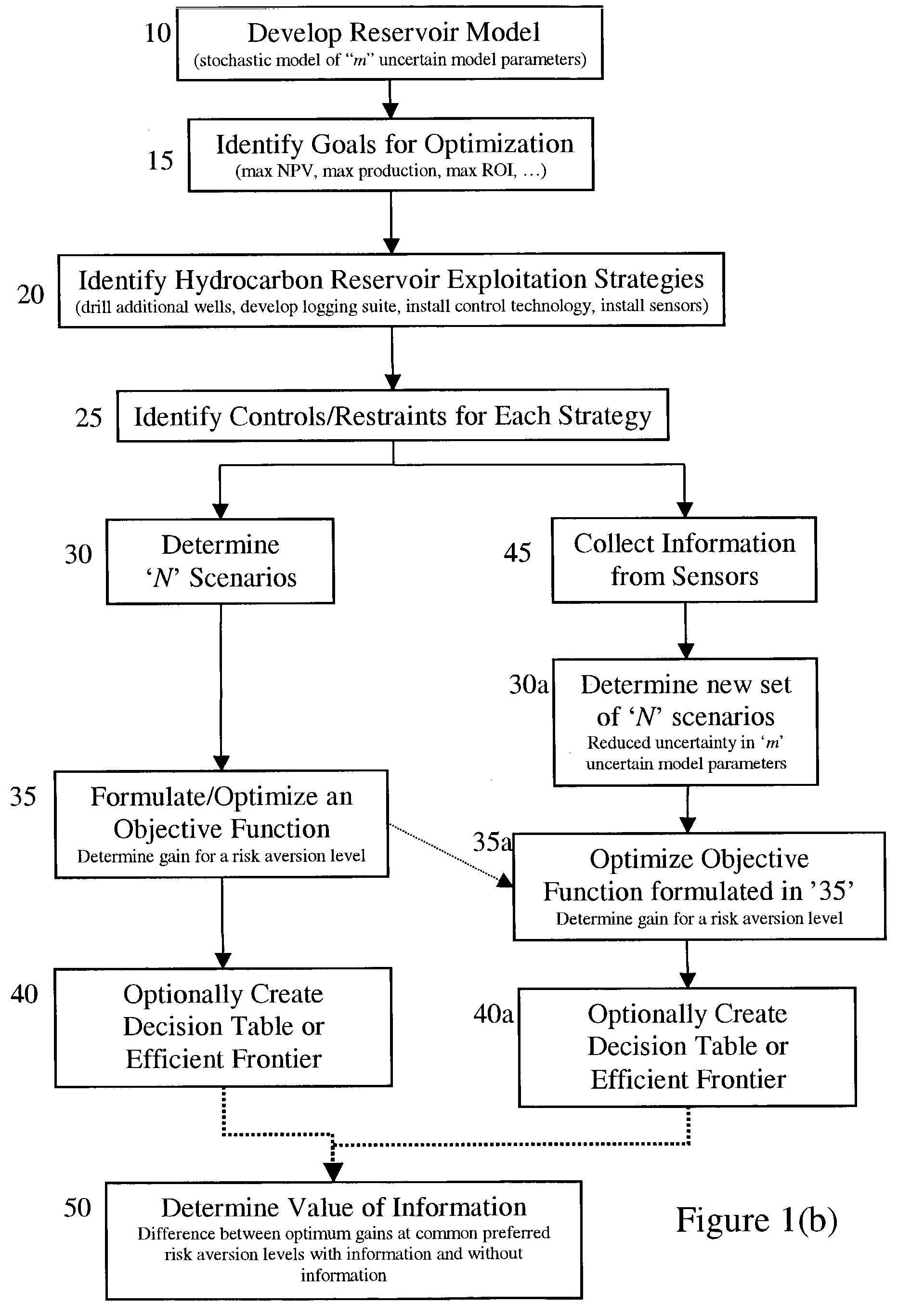
The present invention discloses a method for performing a stochastic analysis of one or more hydrocarbon reservoir exploitation strategies taking into consideration one or more uncertain parameters. The method optimizes an objective function that considers the gain in value of a reservoir management goal attributable to these exploitation strategies. The methodology may be used to decide whether or not to implement a strategy. Alternatively, it may be used to decide which competing strategy will yield the maximum benefit. In another embodiment of the present invention, the value of information obtained from the installation of additional sensors or new measurements is also considered.
Owner:SCHLUMBERGER TECH CORP
Computer based methods and systems for establishing trust between two or more parties
InactiveUS20110167059A1Improve trustPrevent fraudDigital data processing detailsMultiple digital computer combinationsProfessional relationshipValue of information
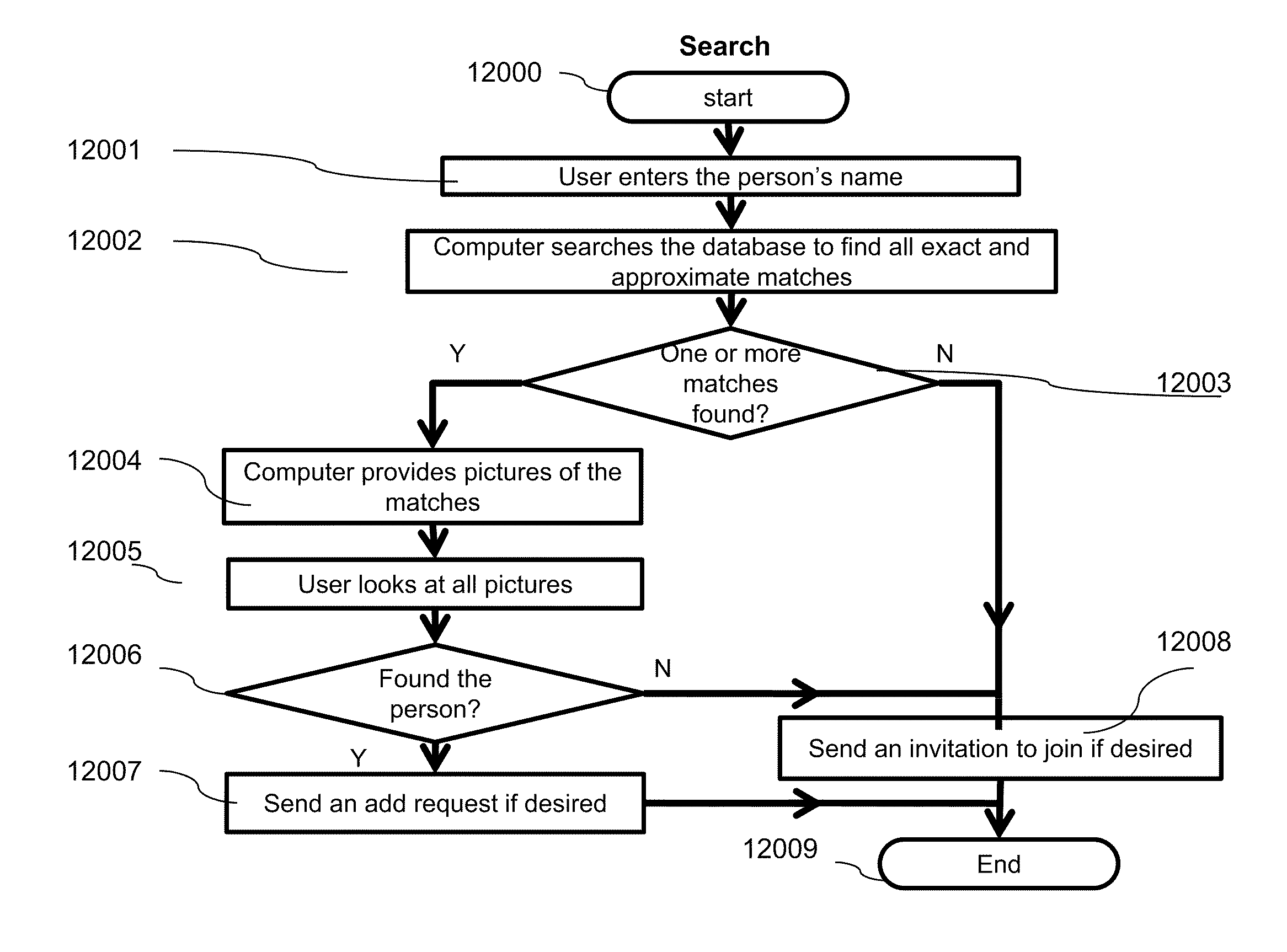
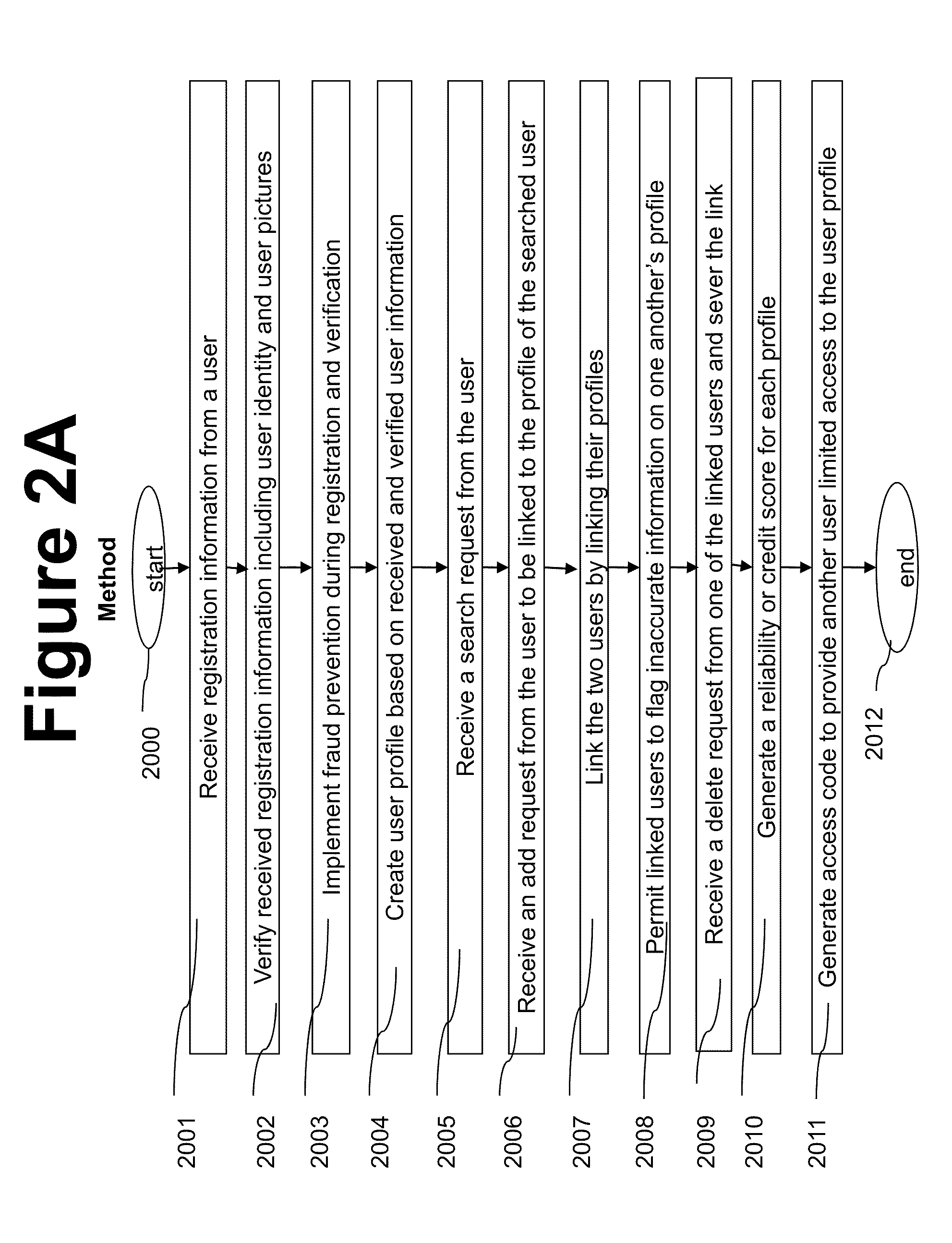
Methods, devices and systems for moderating and policing voluntarily established transparency regarding past and present, and personal and professional relationships via online networking services. Identity of a person or commercial entity is verified before registration as a user. Each user is permitted a single profile. A profile includes a record of all relationships entered in the profile, some of which may be hidden by user. Each user is capable of linking his profile to profiles of other consenting users. Owner of a profile may flag inaccurate information on other linked profiles. The reliability or value of information in a profile is measured as a function of duration of existence of profile, transparency of the information in the profile, periods of inactivation, and number of times the profile is correctly flagged. A code is generated and used to allow gradual exposing of the profile of a user to his prospective contacts.
Owner:IDELAN
Augmented processing of information objects in a distributed messaging framework in a computer network
InactiveUS6769032B1Data processing applicationsWeb data indexingInformation processingInformation object
Augmenting processing of information objects transferred among processors within a network. Processing is performed by a process, or processor, (called a "robot") at any point in the network where an information object is transferred, or where the object resides. By allowing processing at source, destination and at "interim" points between the source and destination, the ability to add functionality, services, control and management of objects and object transfers is greatly enhanced. The robots, can reside at any point in the system. A robot can be local to an end-user's computer, can reside on a content source server, or can be on another computer, processor, storage location or device on the network. Any type of processing can be performed by the robots. For example, access rights can be maintained so that certain attributes and values of information objects are restricted on a per user, per machine, chronological or other basis. Robots can use conditions which, when satisfied by attribute / value pairs within a specific object, or conditions which are satisfied by other, external, conditions, trigger specific processing. The processing can include one or more objects, other information processing, software or hardware control functions, etc. Information can be appended to objects. Statistics on object use, publication, subscription or transfers can be compiled. Groups of robots can operate in cooperation. Robots can share information.
Owner:EPIPHANY INC
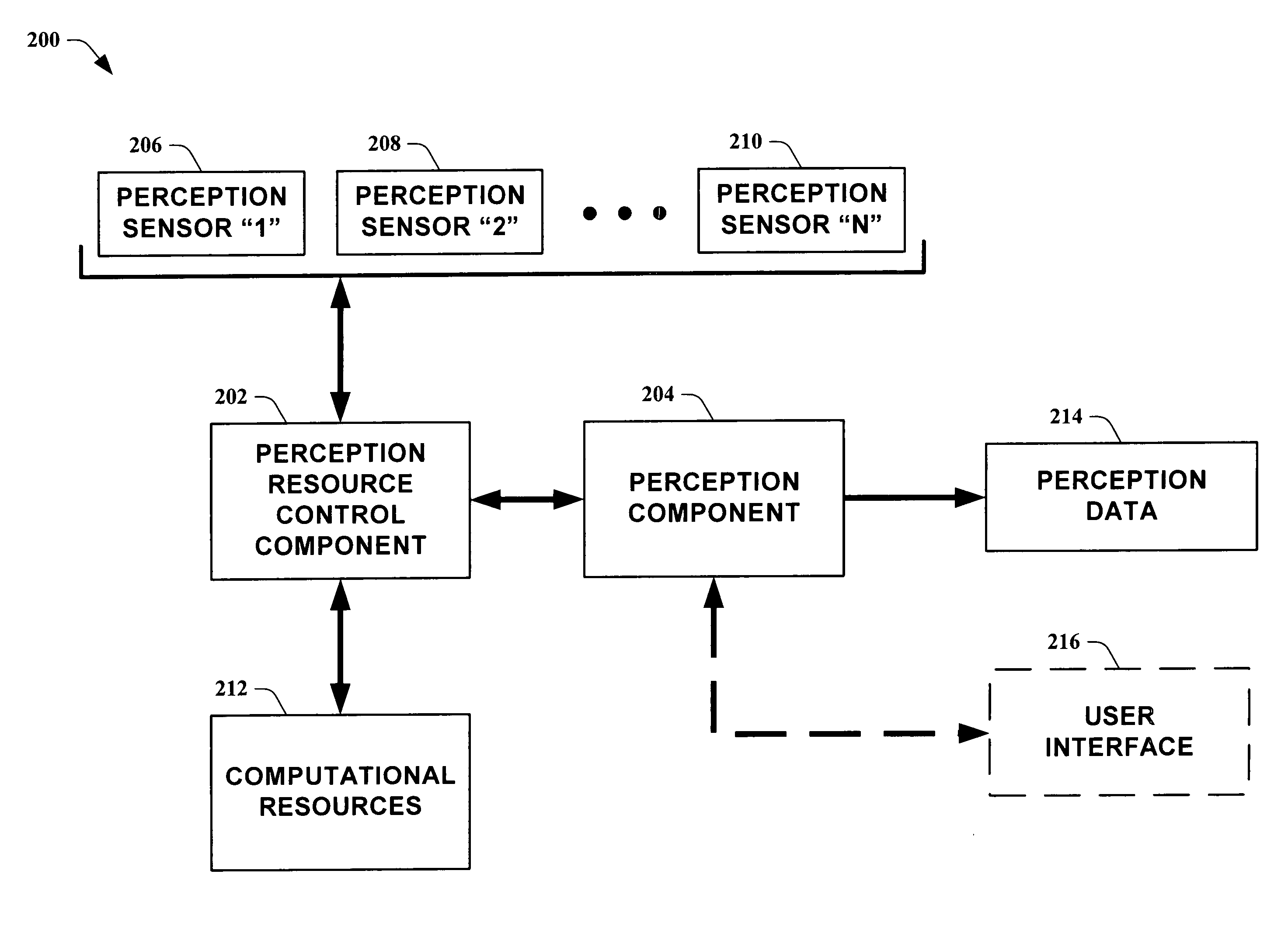
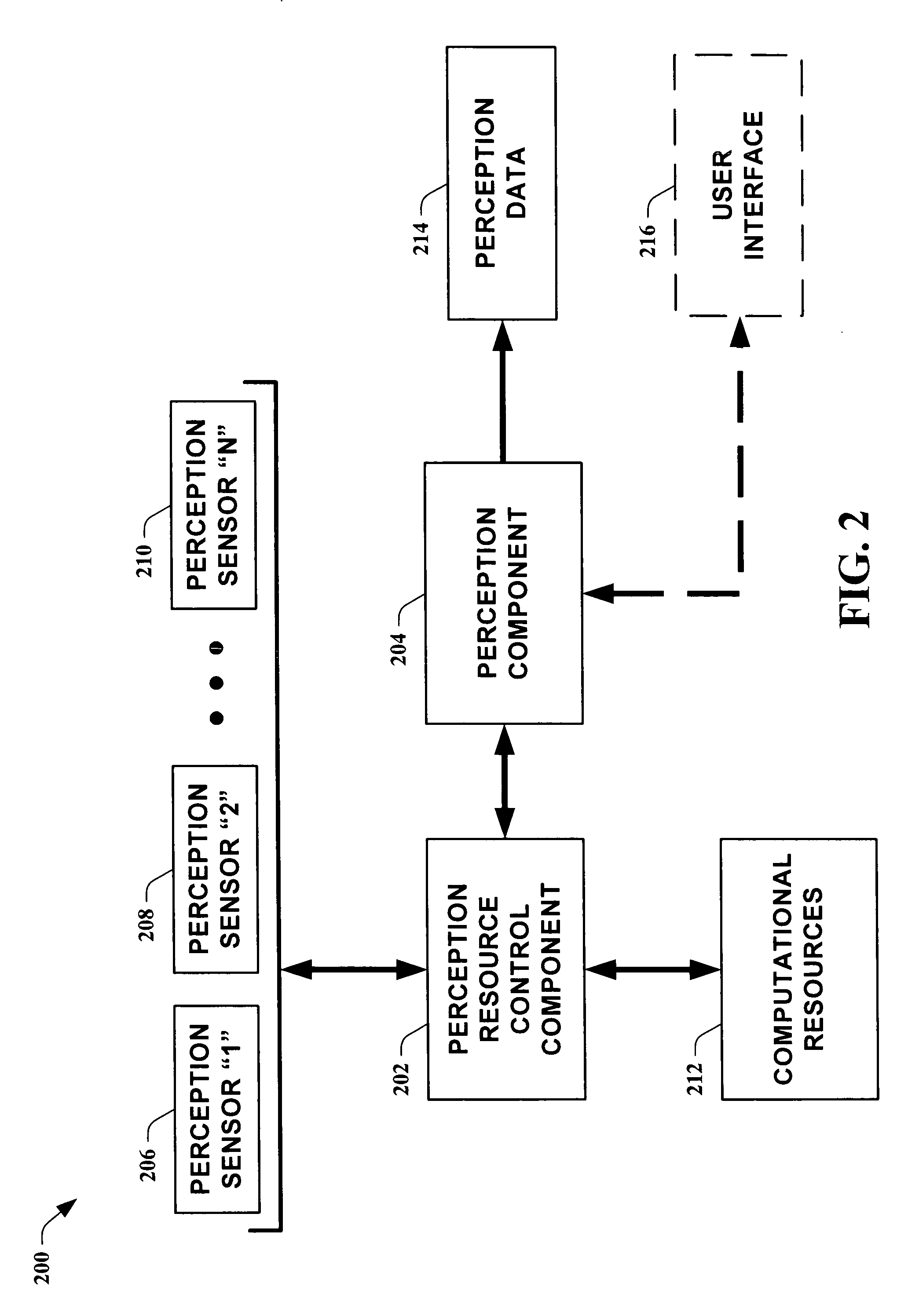
Systems and methods for guiding allocation of computational resources in automated perceptual systems
ActiveUS20050132378A1Facilitate in inferring human-centric notion of contextReducing computational resource burdenDigital computer detailsBiological neural network modelsPattern perceptionInformation Harvesting
The present invention leverages analysis methods, such as expected value of information techniques, rate-based techniques, and random selection technique, to provide a fusion of low-level streams of input data (e.g., raw data) from multiple sources to facilitate in inferring human-centric notions of context while reducing computational resource burdens. In one instance of the present invention, the method utilizes real-time computations of expected value of information in a greedy, one-step look ahead approach to compute a next best set of observations to make at each step, producing “EVI based-perception.” By utilizing dynamically determined input data, the present invention provides utility-directed information gathering to enable a significant reduction in system resources. Thus, of the possible input combinations, the EVI-based system can automatically determine which sources are required for real-time computation relating to a particular context.
Owner:MICROSOFT TECH LICENSING LLC
Media wall for displaying financial information
A system dynamically displays graphic identifier information, such as corporate logos, and value information for financial instruments, such as recent trade information, on a video wall having several monitors arranged to form a larger display. The system has input ports to receive feeds with identifiers and corresponding values of financial instruments, a filter to extract the identifiers and corresponding values of the financial instruments, a memory to store the extracted information and a table associating the financial instrument identifiers with graphic symbols, and processors to form a display signal with the graphic symbols and values.
Owner:IAMTECH +1
Tools for decision-making in reservoir risk management
ActiveUS7512543B2FinanceComputation using non-denominational number representationManagerial decisionStochastic calculus
The present invention discloses a method for performing a stochastic analysis of one or more hydrocarbon reservoir exploitation strategies taking into consideration one or more uncertain parameters. The method optimizes an objective function that considers the gain in value of a reservoir management goal attributable to these exploitation strategies. The methodology may be used to decide whether or not to implement a strategy. Alternatively, it may be used to decide which competing strategy will yield the maximum benefit. In another embodiment of the present invention, the value of information obtained from the installation of additional sensors or new measurements is also considered.
Owner:SCHLUMBERGER TECH CORP
Display and human-computer interaction for a notification platform
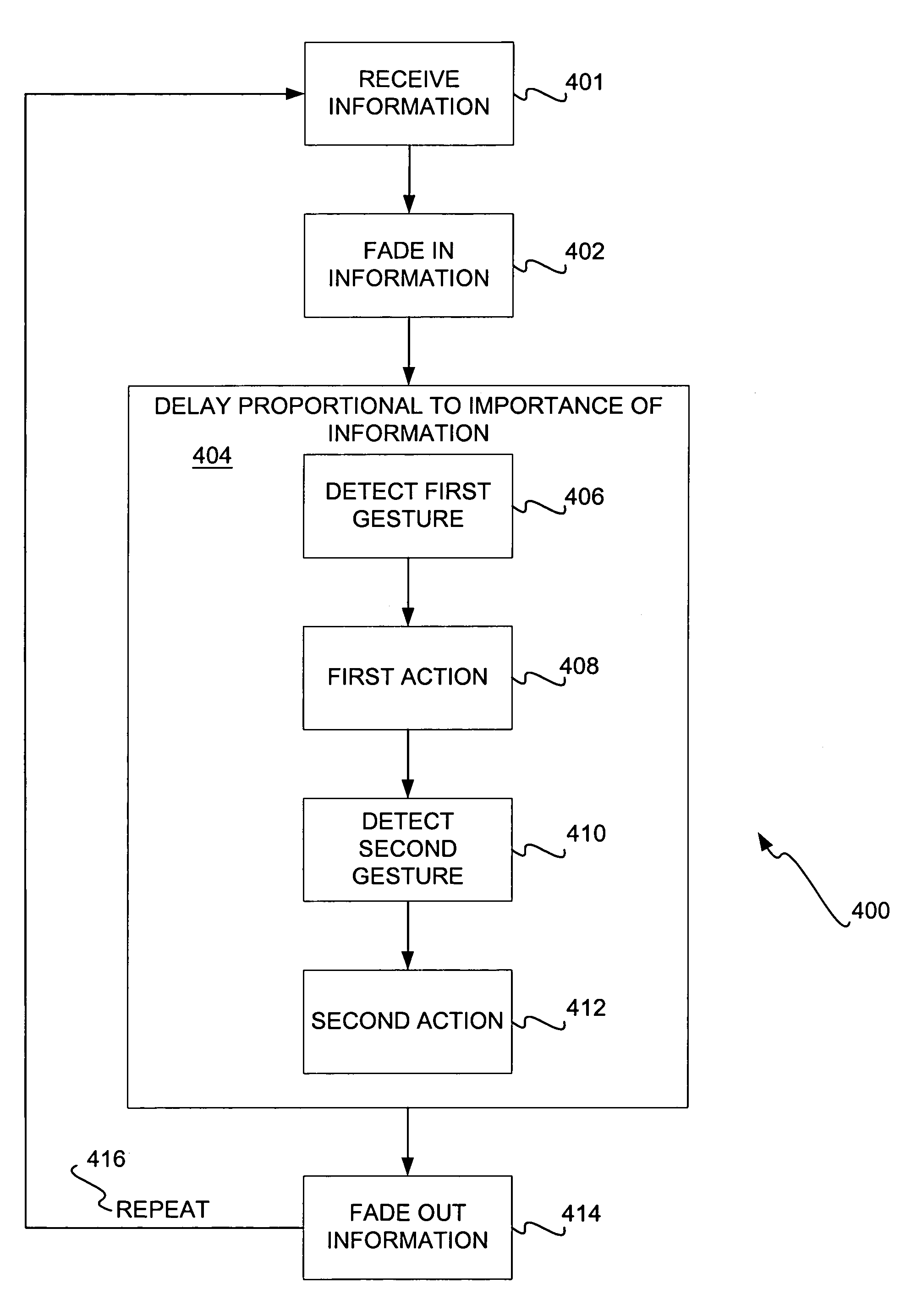
InactiveUS7417650B1Easily access more detailOffice automationExecution for user interfacesDisplay devicePulse mode
User interfaces for relaying notifications to users are disclosed. In a pulsing mode, information is faded into a predetermined area of a display, where the information has a net value greater than a predetermined or dynamically computed threshold. In a stream-cycling mode, for a number of different information sources, a display time is determined for each notification based on the information's importance. Each information is displayed in turn for a length of time equal to the display time, within the predetermined area of the display. In a stream-stacking mode, information from each of a number of sources is displayed in a corresponding source summary window. When the net value of information in a notification is greater than a predetermined or computed threshold, the information may be streamed in a main notification window and can be journaled in a journal window.
Owner:MICROSOFT TECH LICENSING LLC
Account abuse detection or prevention device, data collection device, and account abuse detection or prevention program
InactiveUS20090281816A1Easy to detectMemory loss protectionError detection/correctionMisuse detectionPublic network
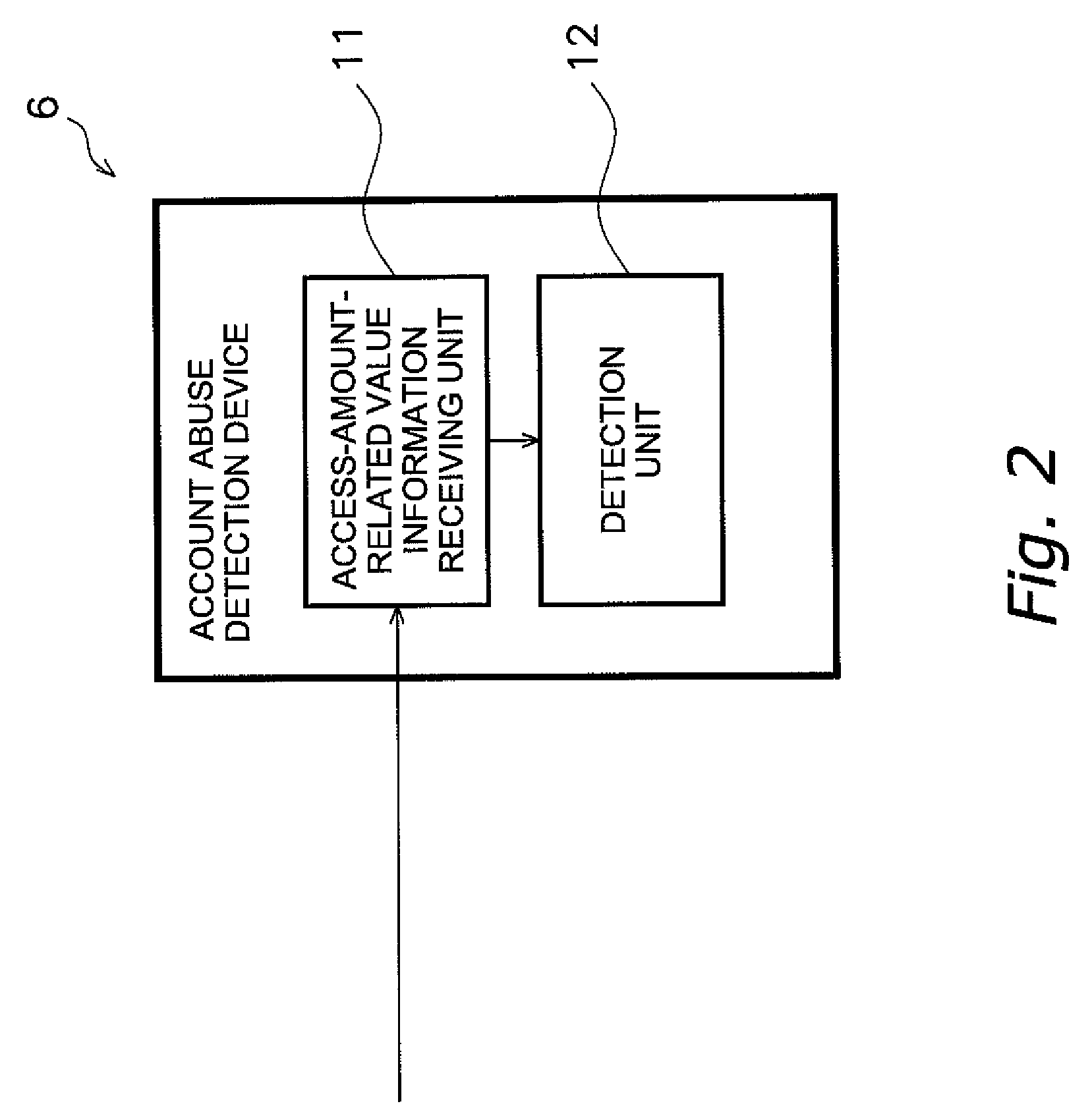
An account abuse detection or prevention device, a data collection device, and an account abuse detection or prevention program, which are capable of promptly detecting or preventing abuse of an account.An account abuse detection device (6) includes an access-amount-related value information receiving unit (11) and a detection unit (12). The access-amount-related value information receiving unit (11) receives access-amount-related value information from a management device (3). The management device (3) manages a specific account. The specific account is used when transmitting data from a plurality of data transmission devices (2) to a data collection device (5) via a public network. Access-amount-related value information is related to an access-amount-related value. The access-amount-related value is related to the amount of access by the public network (4) through the account. The detection unit (12) compares the access-amount-related value to a predetermined threshold value to detect abuse of the account.
Owner:DAIKIN IND LTD
Supercritical refrigeration cycle
InactiveUS20070125106A1Increase pressureReduce power consumptionEvaporators/condensersCompression machinesAir volumeAtmospheric air
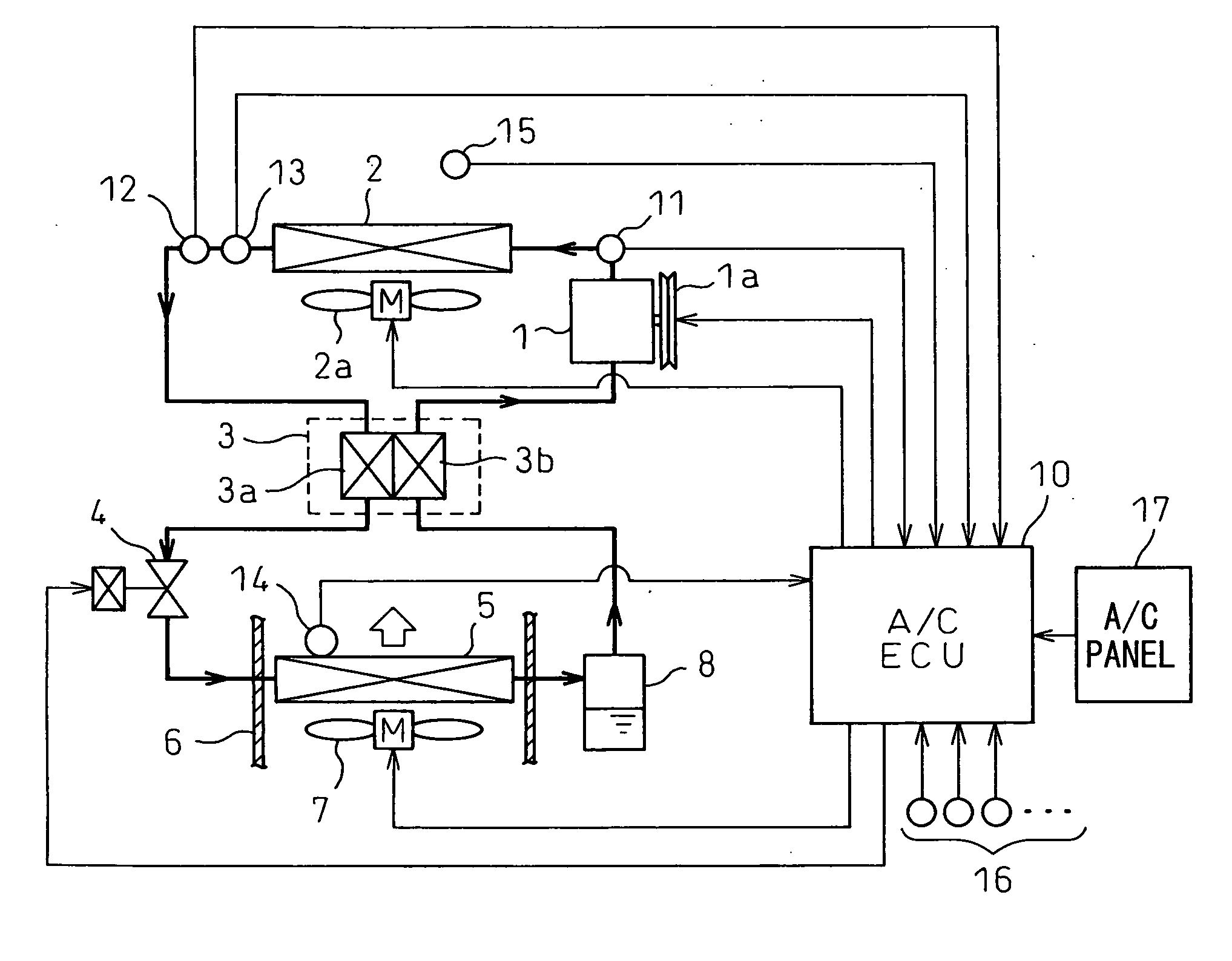
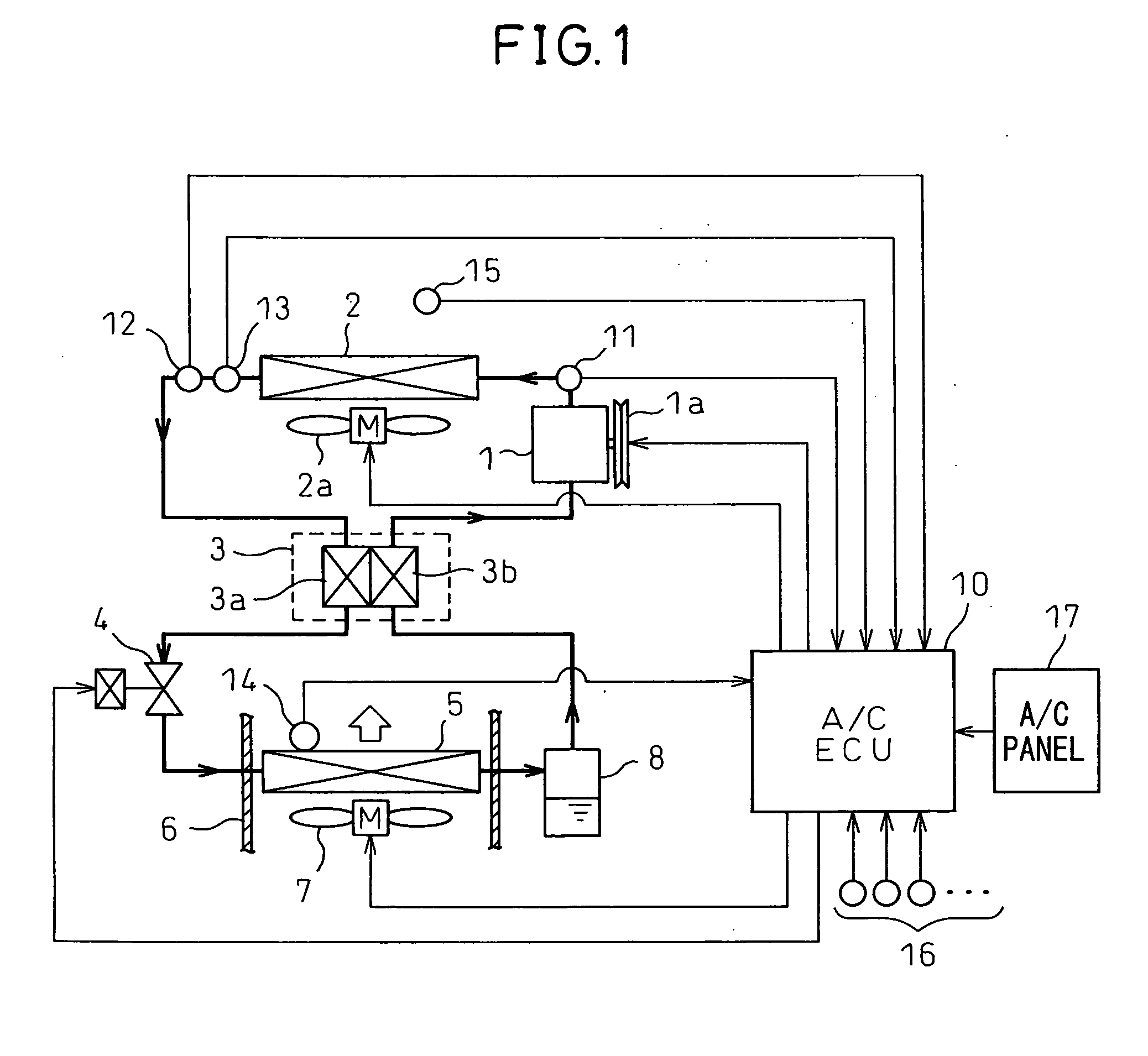
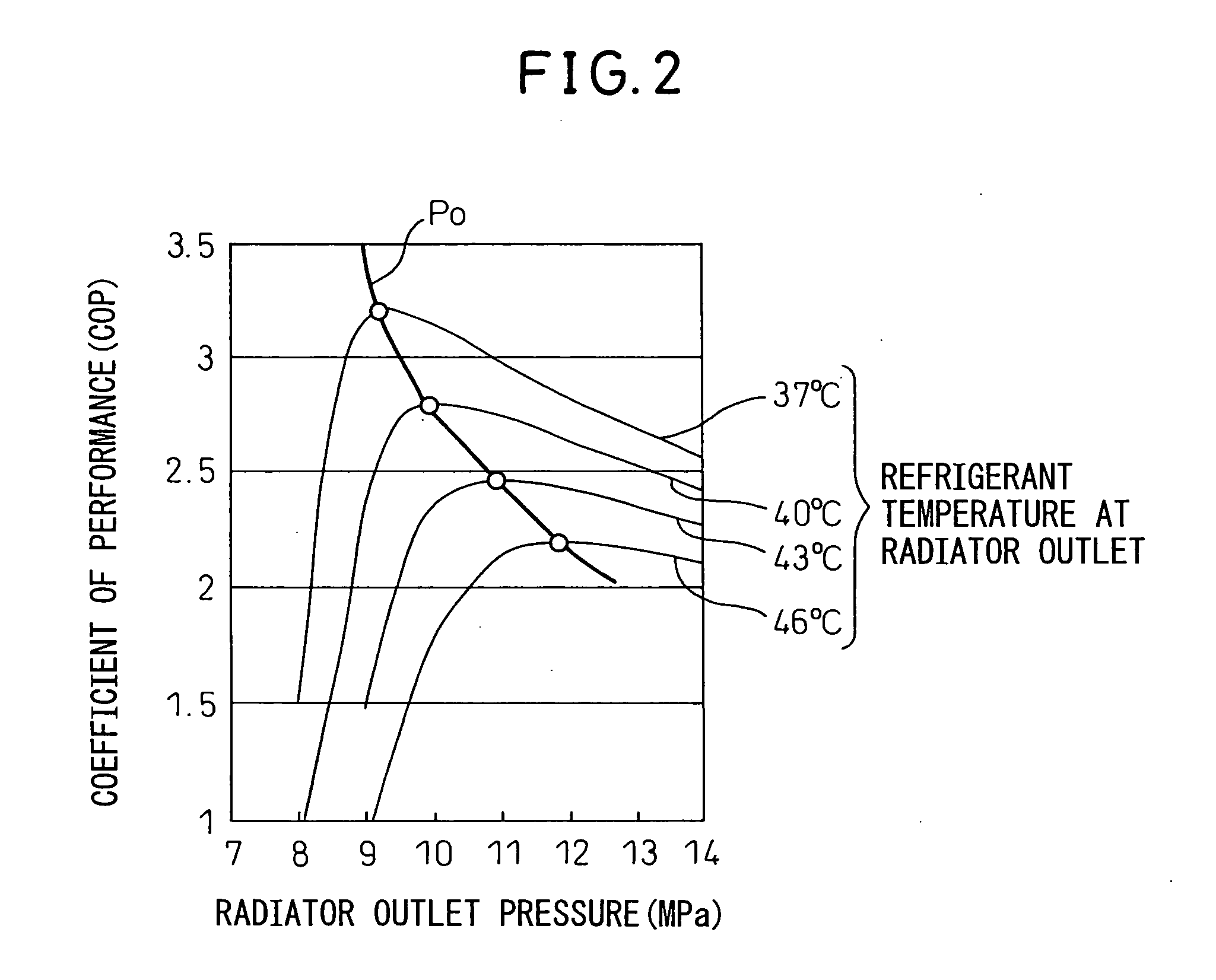
A supercritical refrigeration cycle comprises a radiator 2 for cooling the refrigerant discharged from a compressor 1, a cooling fan 2a for blowing the atmospheric air to the radiator 2, a decompression unit 4 for decompressing the refrigerant at the outlet of the radiator 2 and having the opening degree thereof controlled to achieve a target high pressure, and an evaporator 5 for evaporating the low-pressure refrigerant decompressed by the decompression unit 4. The high pressure exceeds the critical pressure of the refrigerant. A value of information representing the difference between the actual radiation state of the refrigerant at the outlet of the radiator 2 and the ideal radiation state determined by the atmospheric temperature is calculated, and based on this value of information, the air capacity of the cooling fan 2a is controlled to decrease the difference. Thus, the cooling fan of the high-pressure radiator can be properly controlled in the supercritical refrigeration cycle.
Owner:DENSO CORP
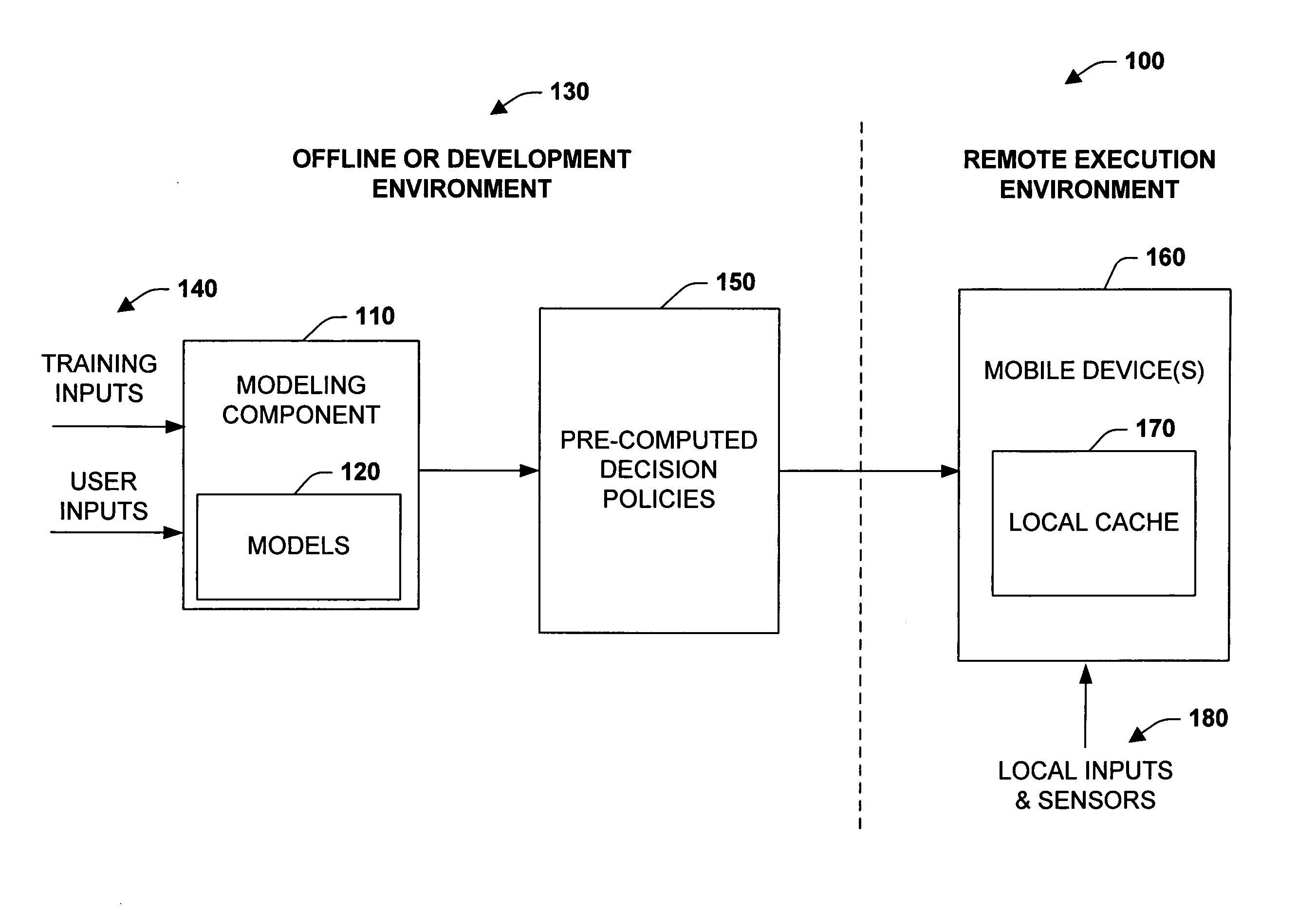
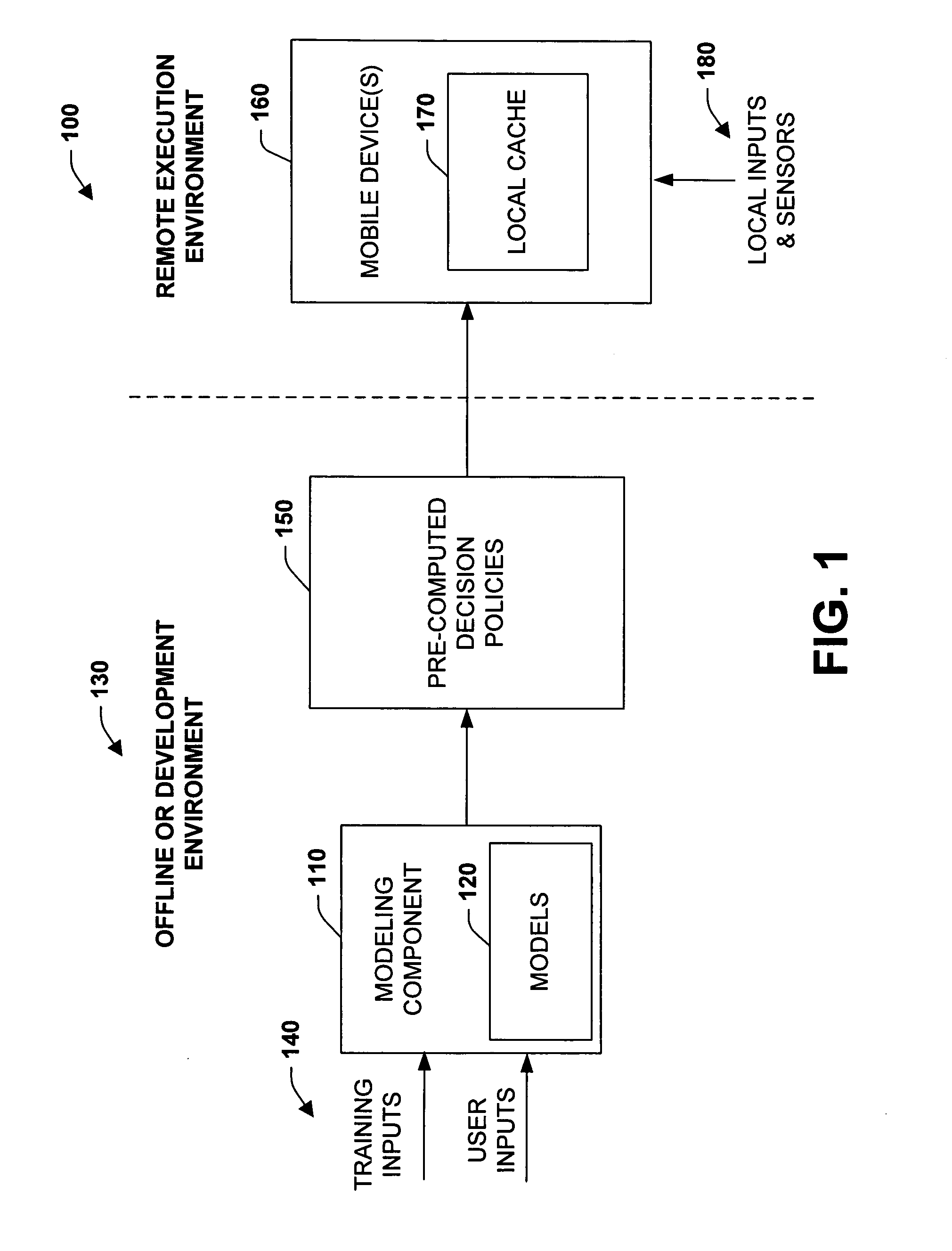
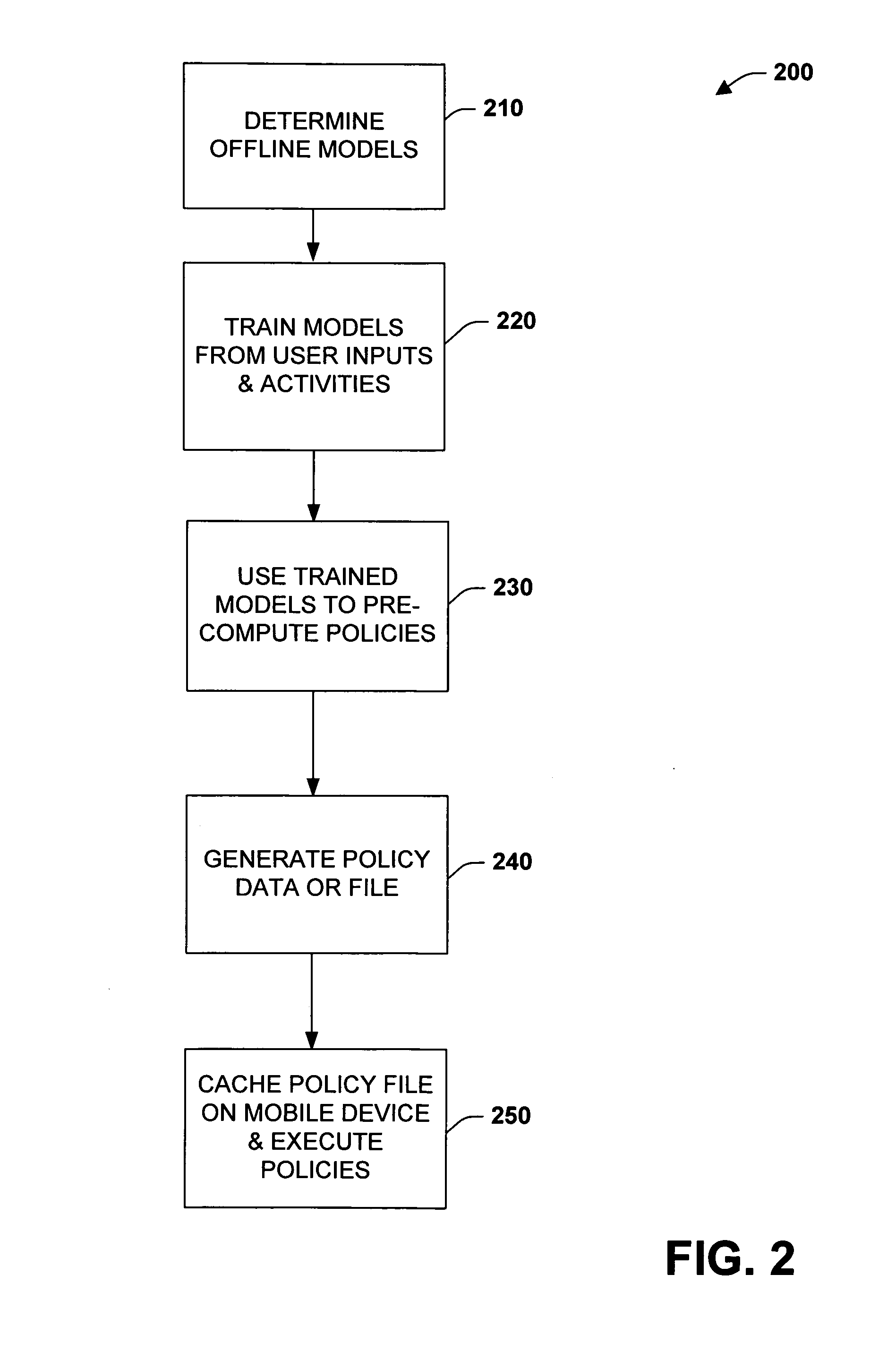
Precomputation of context-sensitive policies for automated inquiry and action under uncertainty
InactiveUS20070022075A1Enhance decision-making capability of deviceImprove device performanceProbabilistic networksFuzzy logic based systemsPrecomputationContext sensitivity
Learning, inference, and decision making with probabilistic user models, including considerations of preferences about outcomes under uncertainty, may be infeasible on portable devices. The subject invention provides systems and methods for pre-computing and storing policies based on offline preference assessment, learning, and reasoning about ideal actions and interactions, given a consideration of uncertainties, preferences, and / or future states of the world. Actions include ideal real-time inquiries about a state, using pre-computed value-of-information analyses. In one specific example, such pre-computation can be applied to automatically generate and distribute call-handling policies for cell phones. The methods can employ learning of Bayesian network user models for predicting whether users will attend meetings on their calendar and the cost of being interrupted by incoming calls should a meeting be attended.
Owner:MICROSOFT TECH LICENSING LLC
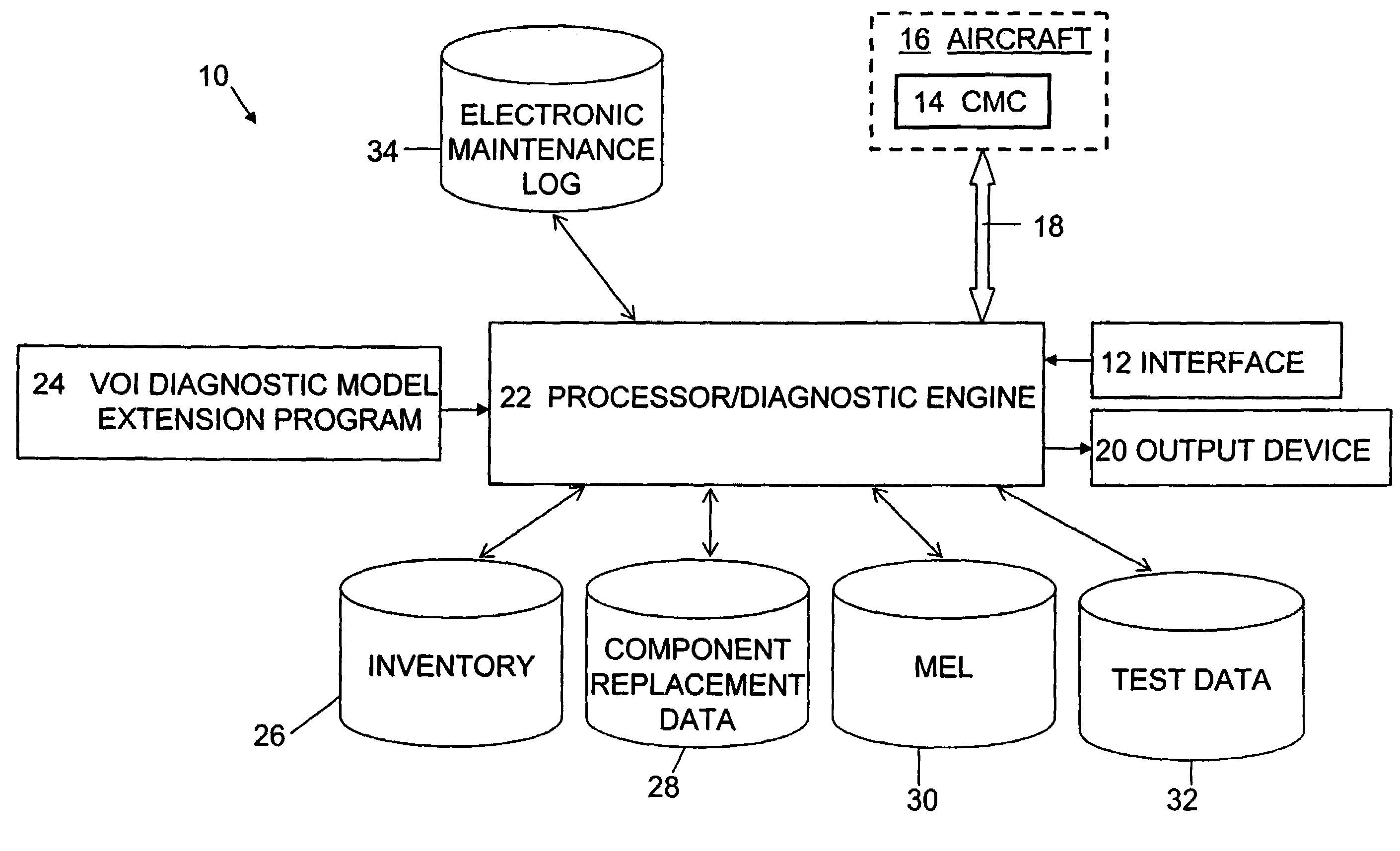
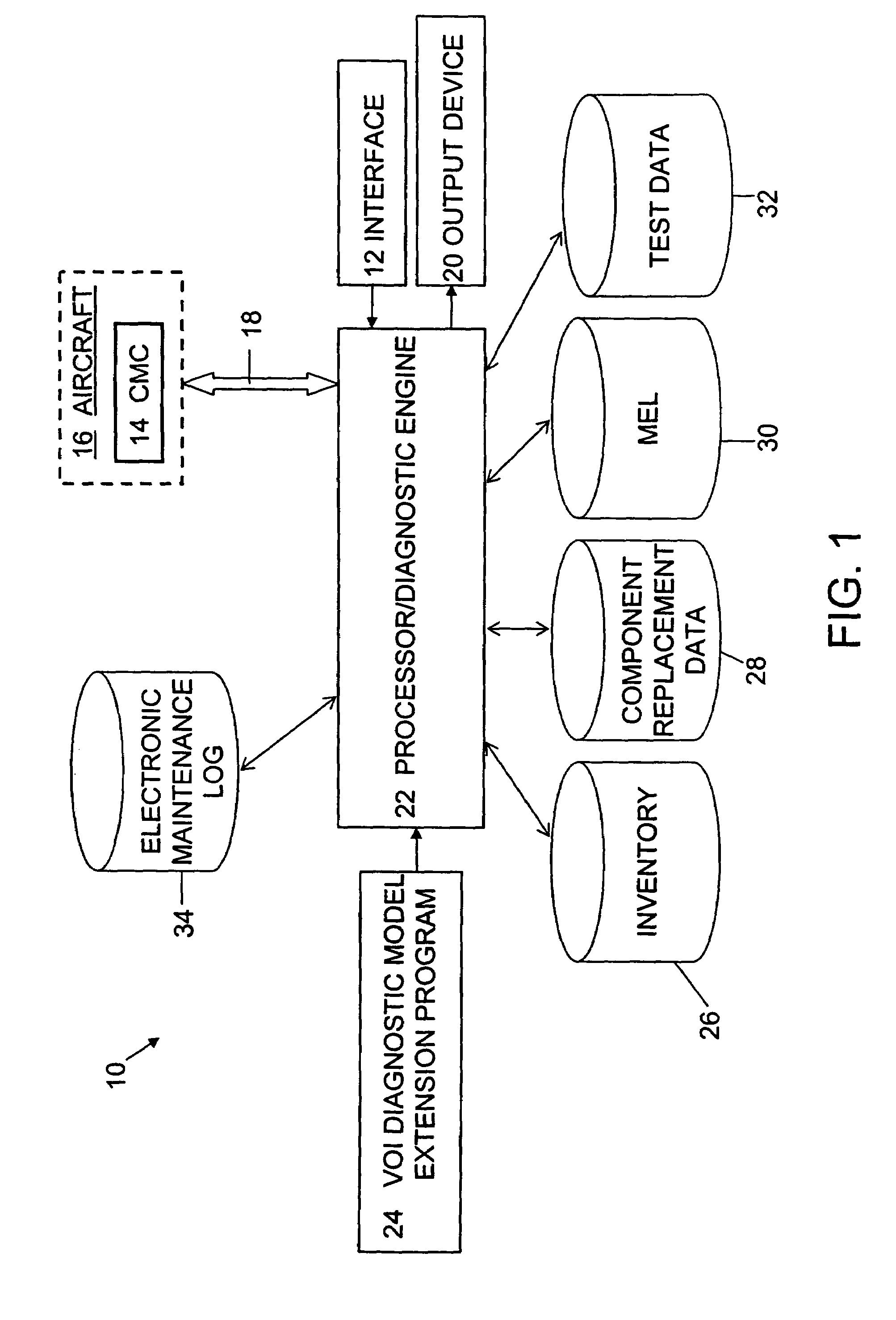
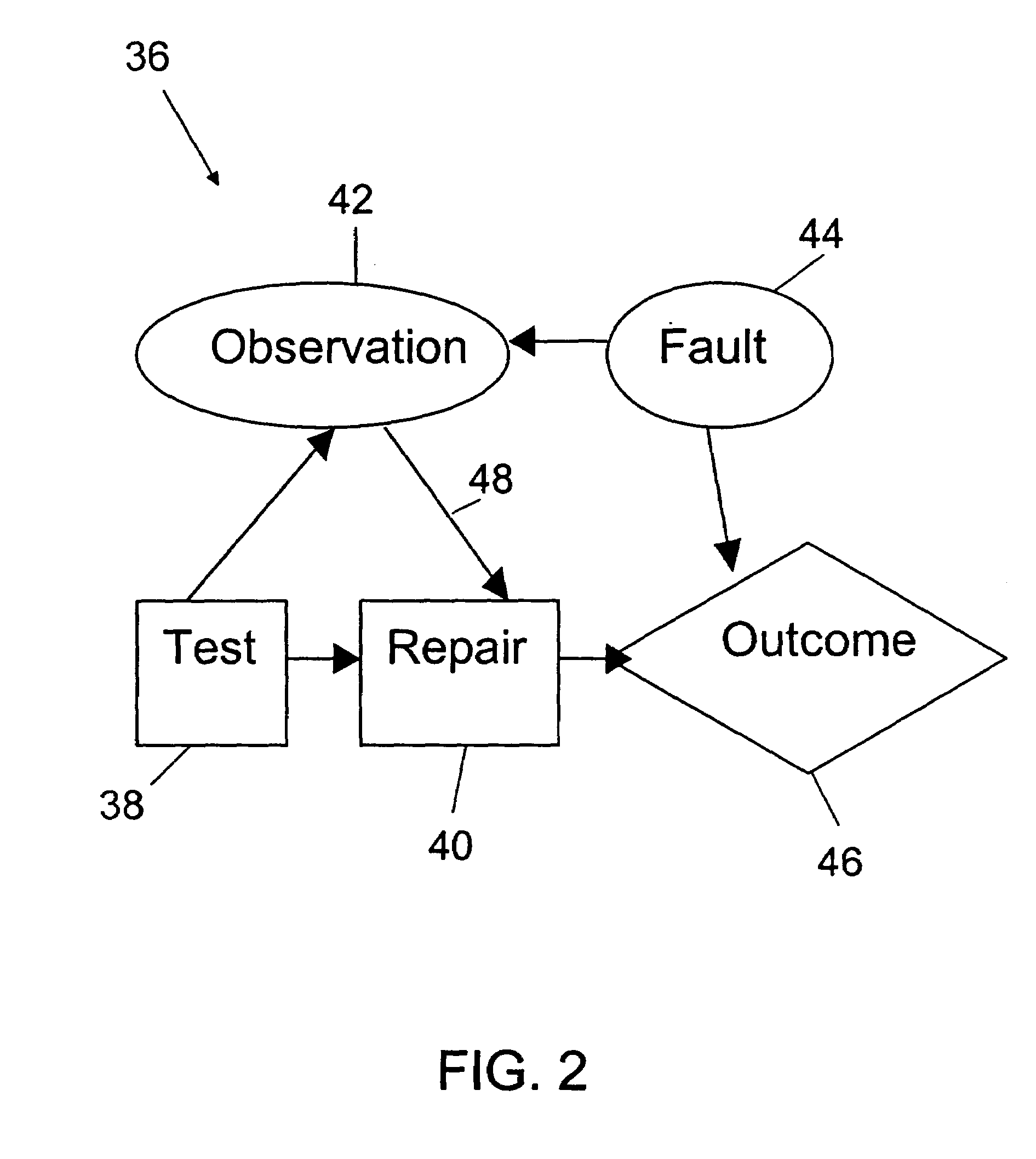
Diagnostic system and method for enabling multistage decision optimization for aircraft preflight dispatch
InactiveUS7209814B2Reduce maintenance costsEnable optimizationVehicle testingRegistering/indicating working of vehiclesDependabilityValue of information
A diagnostic system and method for enabling multistage decision optimization in aircraft preflight dispatch. The diagnostic system includes an interface for receiving one or more inputs relating to one or more observed symptoms indicative of a failed component in an aircraft. The diagnostic system extends an entropy-based value of information (VOI) diagnostic model by adding an explicit value function into the VOI diagnostic model to accommodate various variables associated with the aircraft preflight dispatch problem. The construction of the entropy-based VOI diagnostic model and thus the extended VOI diagnostic model are both based upon at least one of systemic information relating to aircraft components and input-output relationships of the aircraft components, experience-based information relating to direct relationships between aircraft component failures and observed symptoms, and factual information relating to aircraft component reliability.
Owner:THE BOEING CO
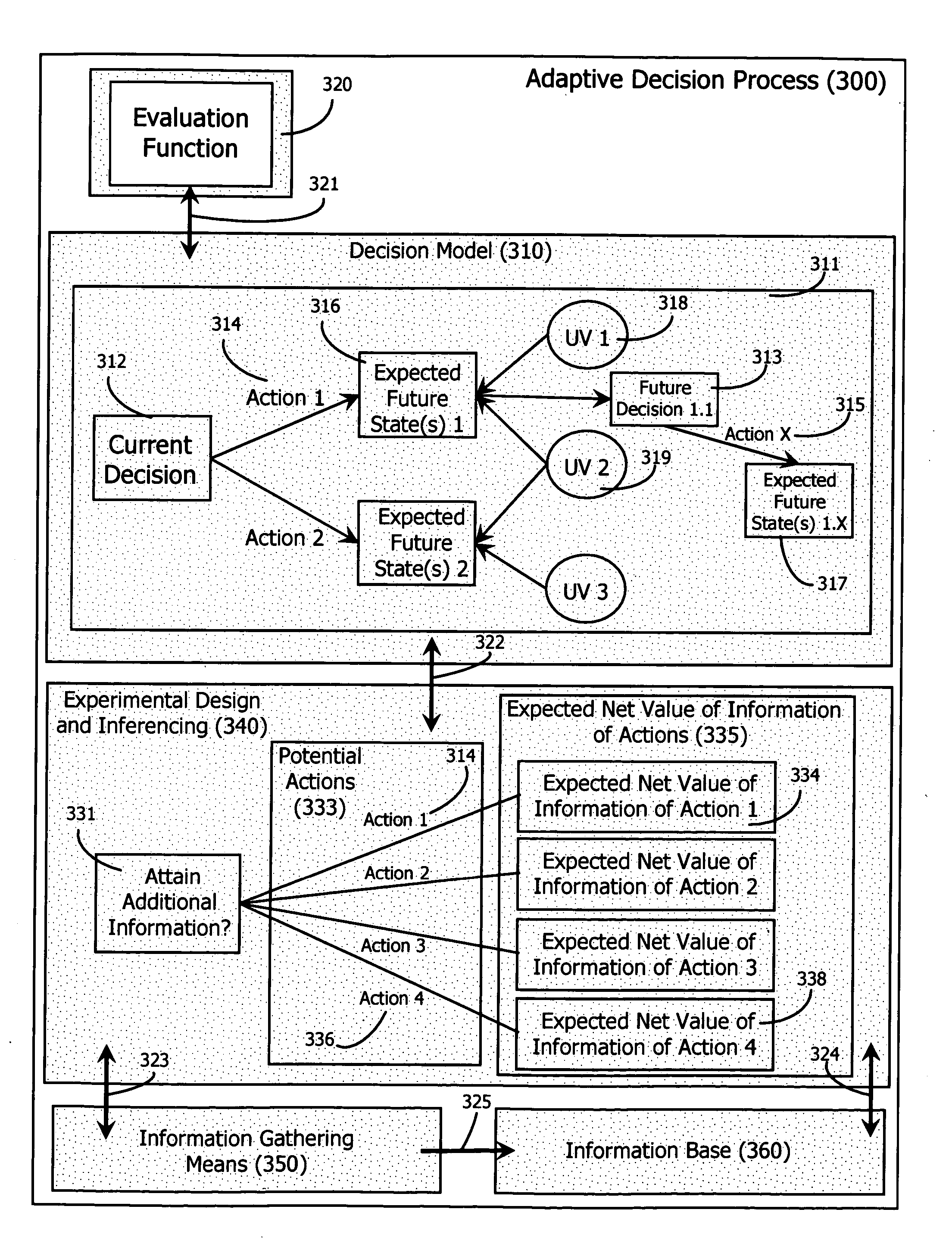
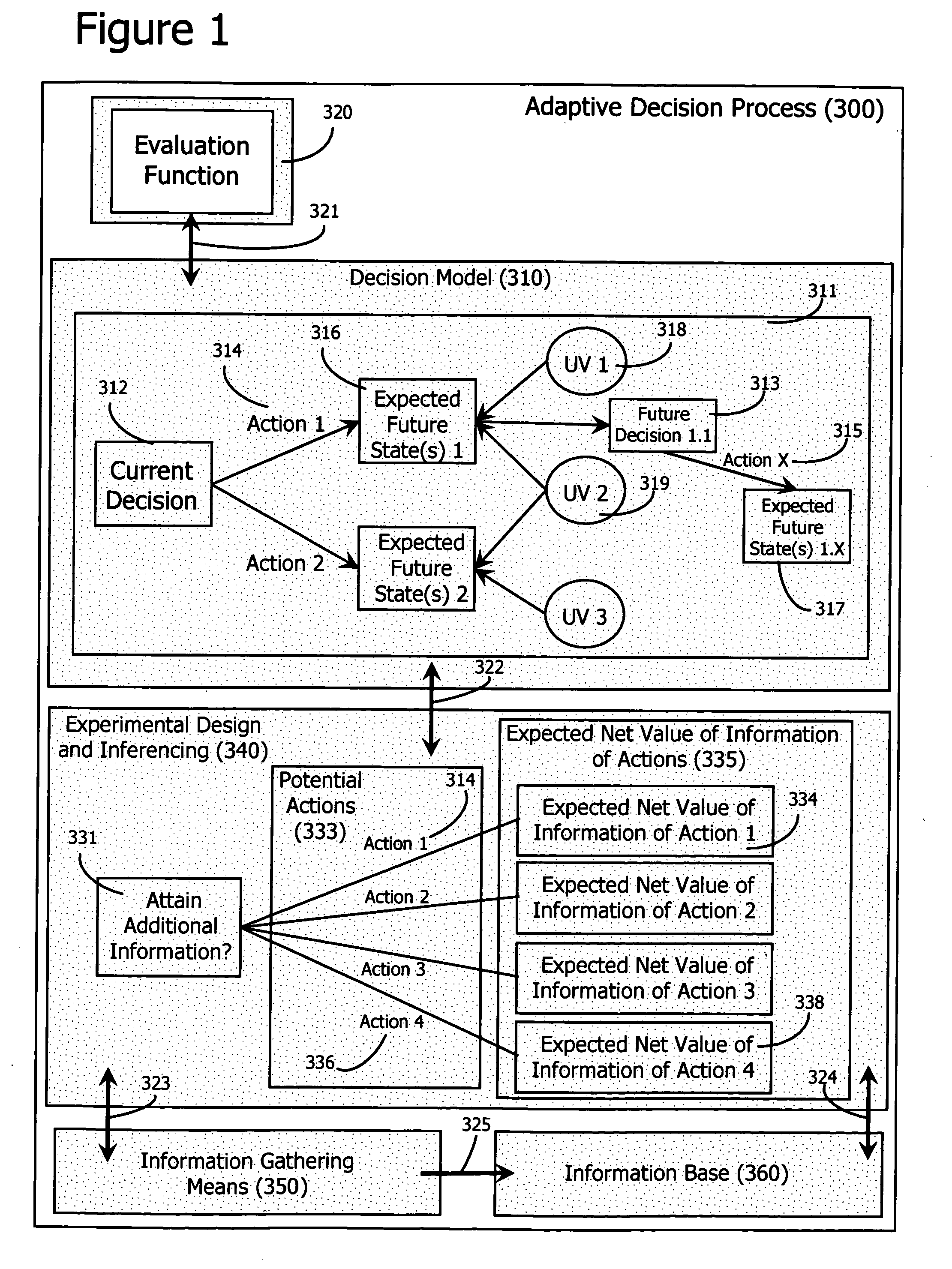
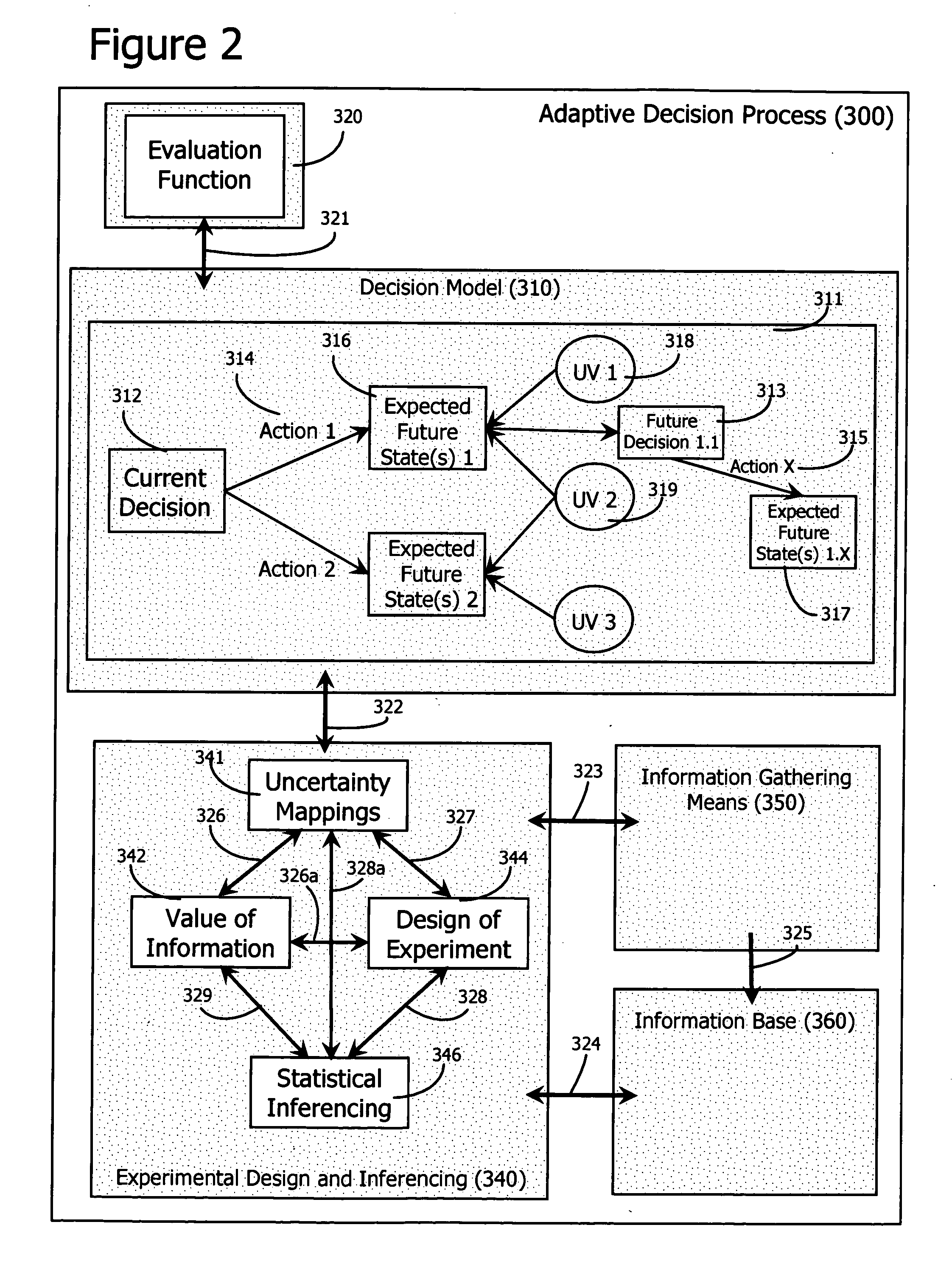
Adaptive decision process
InactiveUS20060184482A1Probabilistic networksSpecial data processing applicationsDecision modelClosed loop
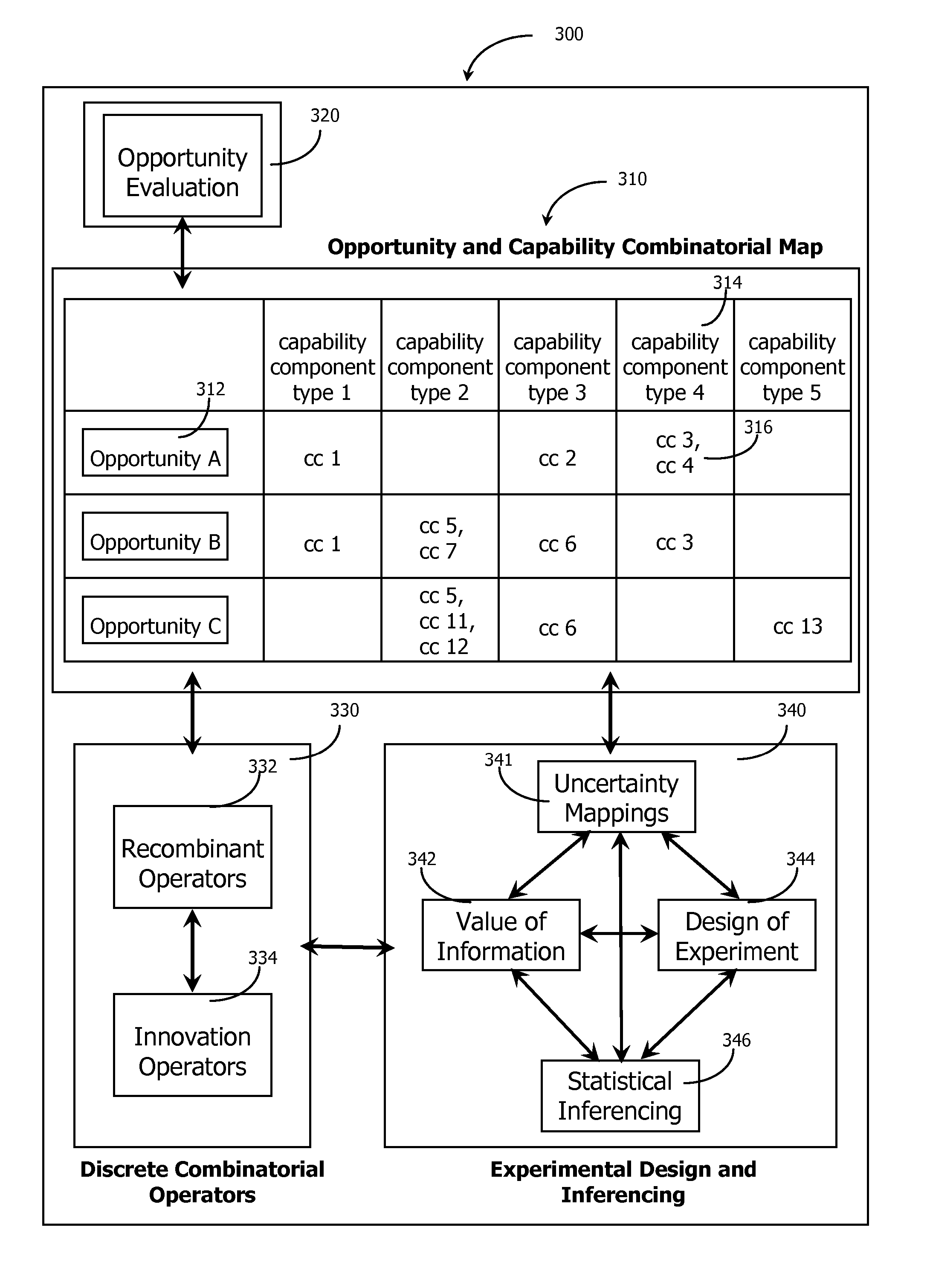
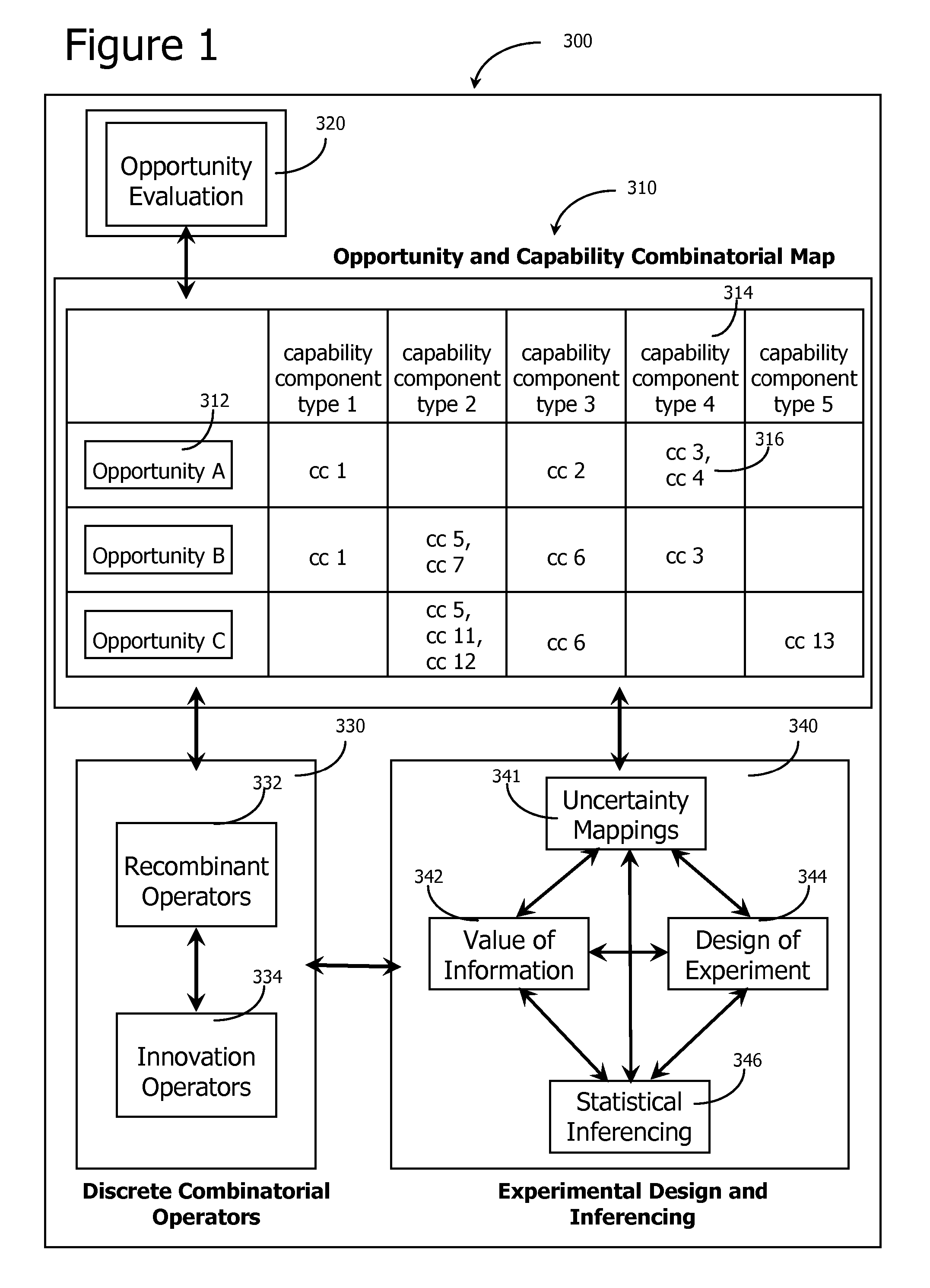
An adaptive decision process is disclosed for more effectively and efficiently determining and conducting information gathering and evaluation associated with decisions. The adaptive decision process integrates decision analysis, value of information analysis, design of experiment models, and the inferencing of gathered information, including experimental results. The process enables an automatic, adaptive, closed-loop process for attaining additional information and assimilating the attained information into the decision model.
Owner:MANYWORLDS CONSULTING
Body composition measuring device capable of comparing current measured value with past measured value
InactiveUS20050209528A1Easy to confirmCovering/liningsBuilding componentsData displayBody composition measure
In a display section, a measured value of information of a living body is displayed on a measured data display section, and a figure representing a human body including body parts such as arm and leg is displayed on a body display section. For example, a percentage of muscle and a percentage of body fat measured 30 days ago and a current percentage of muscle and percentage of body fat are compared with each other, and respective increase / decrease values are displayed on the measured data display section as well as the measured values. Further, a color of illumination in the background of the body display section is changed depending on a degree of the increase / decrease value. For example, the background of the body display section is illuminated in red when the percentage of muscle is decreased by a % or more, blue when increased by a % or more, and green when a percentage of variation is less than a % in comparing current data with data measured 30 days ago.
Owner:OMRON HEALTHCARE CO LTD
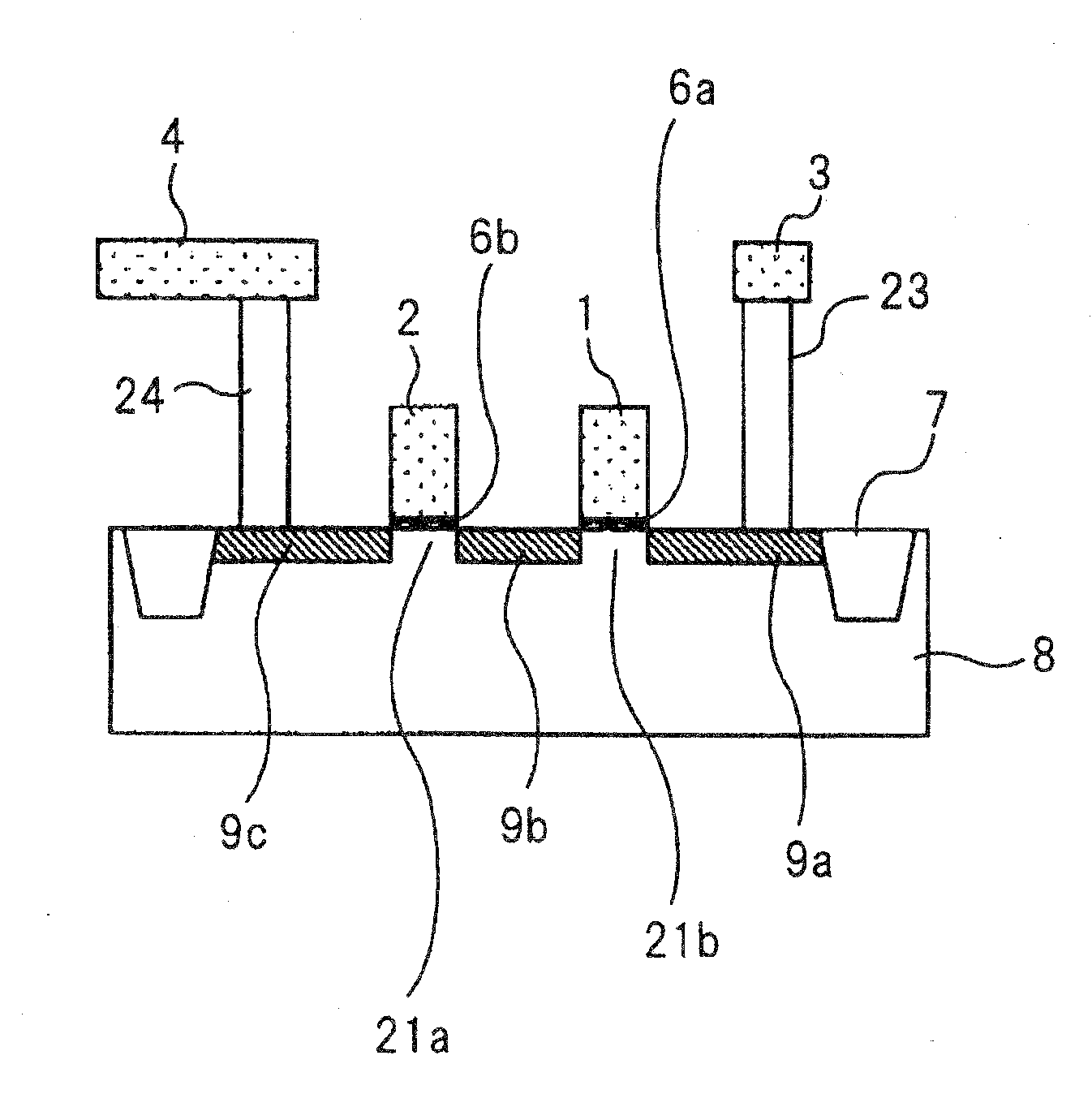
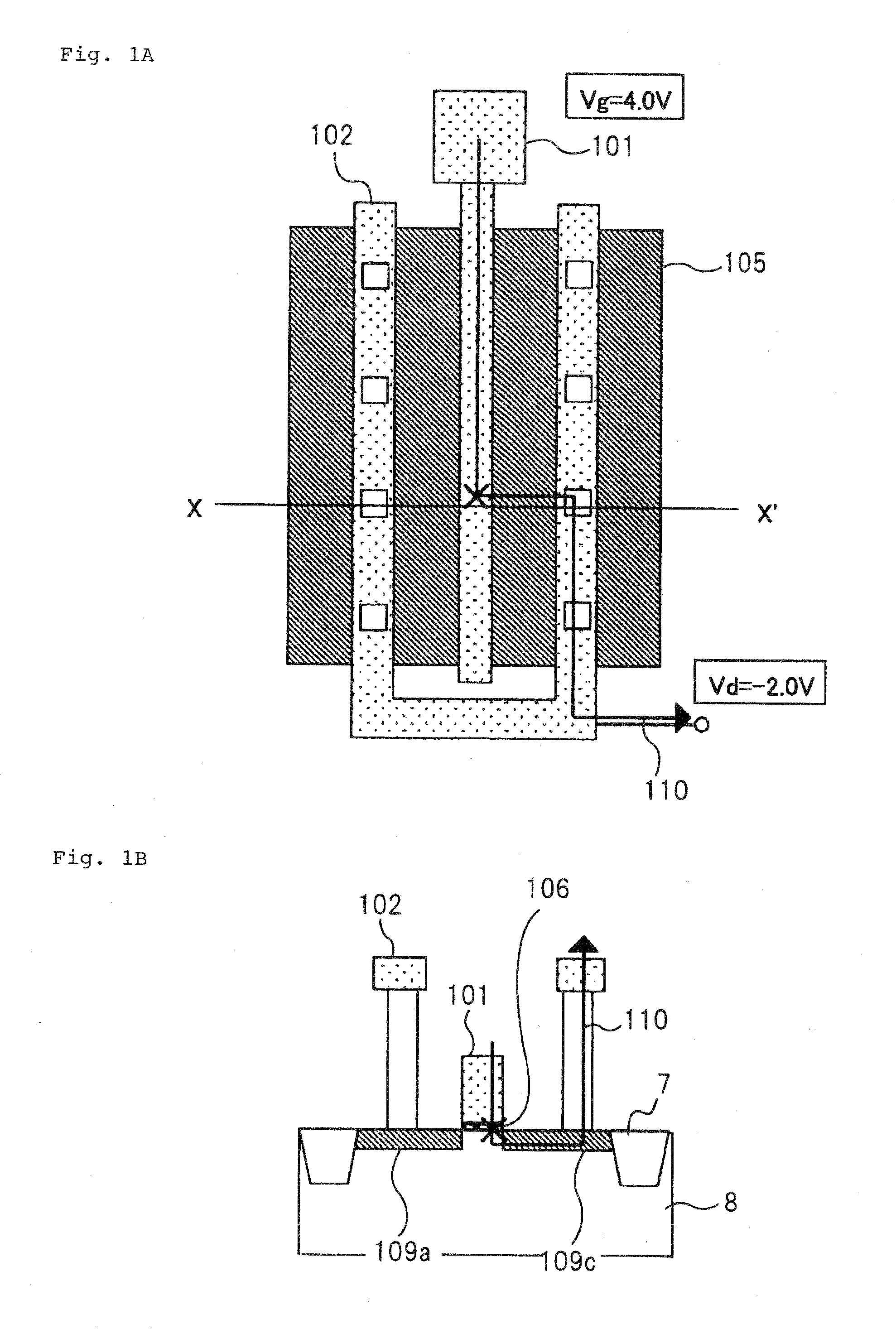
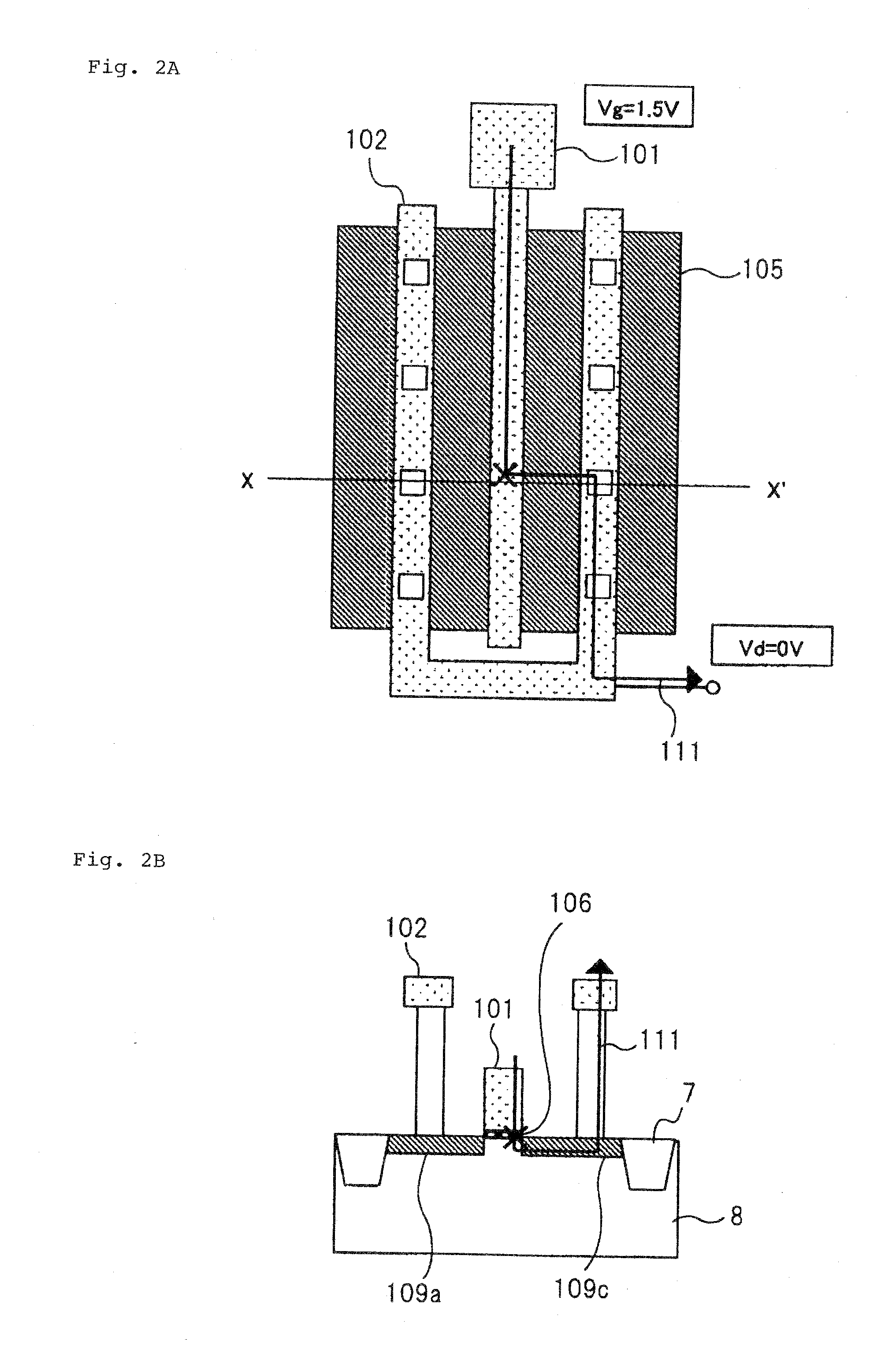
Antifuse element in which more than two values of information can be written
InactiveUS20090115021A1Semiconductor/solid-state device detailsSolid-state devicesEngineeringAntifuse
An antifuse element includes a plurality of MOS transistors; a first electrode to which source electrodes of the plurality of MOS transistors are commonly connected; a second electrode to which gate electrodes of the plurality of MOS transistors are commonly connected; a third electrode to which at least one of drain electrodes of the plurality of MOS transistors is capable of being connected; and an insulation film provided between the drain electrodes of the plurality of MOS transistors and the third electrode, wherein the insulation on at least one position in said insulation film and that corresponds to one of the drain electrodes is broken down.
Owner:ELPIDA MEMORY INC
Encryption device, encryption processing method and program, and information protection system employing the encryption device
InactiveUS20060120520A1Reduce the amount of calculationHigh encryption strengthMultiple keys/algorithms usageDigital data processing detailsComputer hardwareValue of information
An encryption device includes a first unit that acquires value information denoting a value of information to be encrypted, and a second unit that calculates a strength parameter denoting an encryption strength, based on the value information. It is thus possible to determine the strength parameter reasonably according to the information to be encrypted.
Owner:FUJIFILM BUSINESS INNOVATION CORP
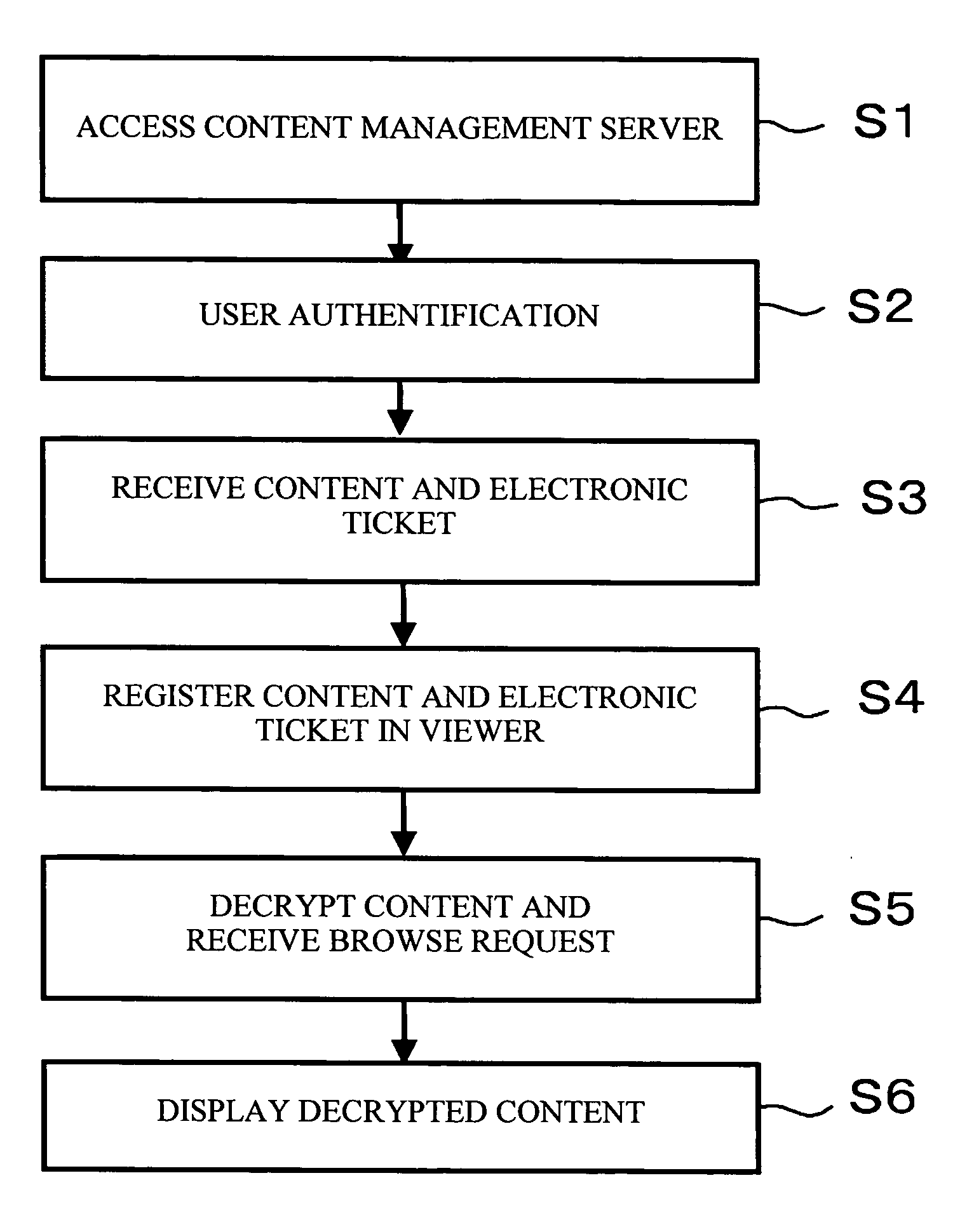
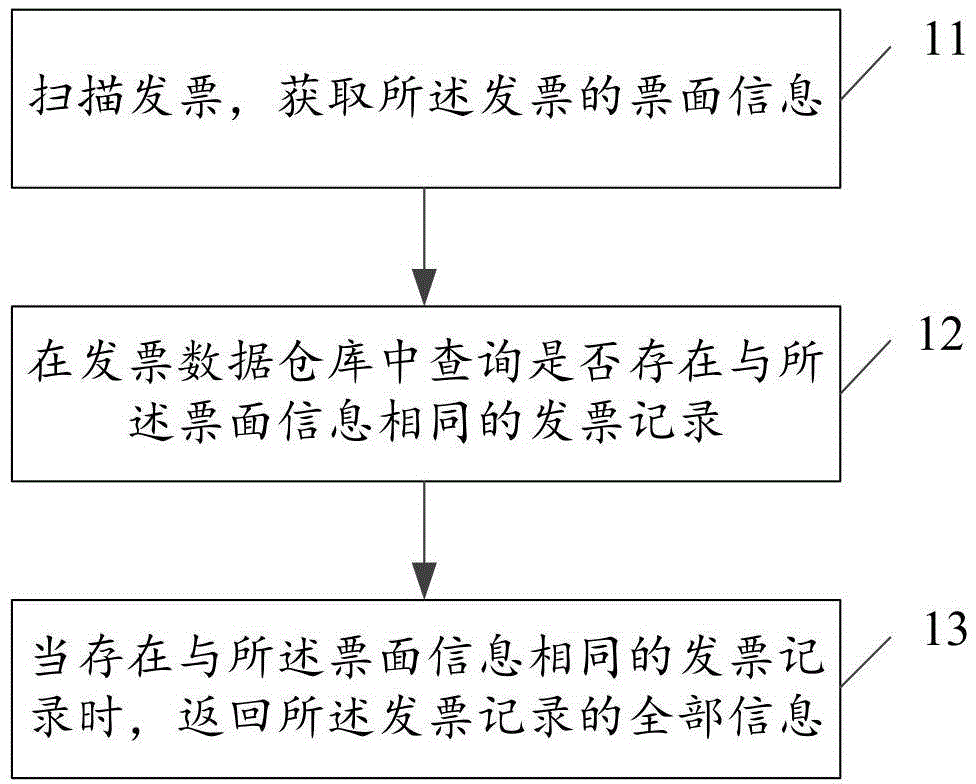
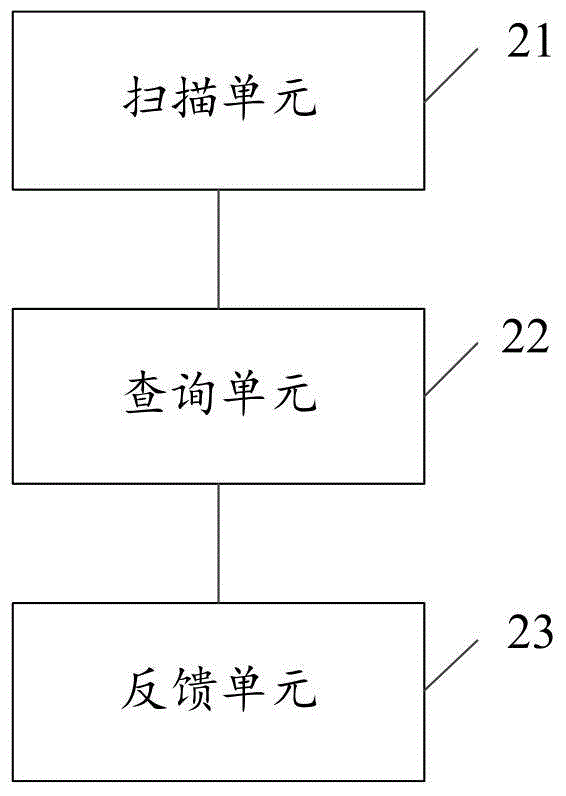
Invoice recognition method and system
InactiveCN105701905AImprove accuracyImprove efficiencyCharacter and pattern recognitionSensing by electromagnetic radiationData warehouseInvoice
An embodiment of the invention provides an invoice recognition method and an invoice recognition system. The invoice recognition method comprises the steps of: scanning an invoice, and acquiring face value information of the invoice; querying whether an invoice record identical with the face value information exists in an invoice data warehouse; and if the invoice record identical with the face value information exists, returning all information of the invoice record. The invoice recognition method and the invoice recognition system acquire the face value information of the invoice through scanning the invoice, the face value information comprises an invoice number, an invoice code, an invoicing date, amount of money and the like, and the face value information is combined for querying in the invoice data warehouse, the accuracy rate of invoice authenticity recognition is increased, when the face value information includes two-dimensional code information, the two-dimensional code information can be analyzed, the face value information obtained through analysis is further compared with the face value information obtained through scanning, and the invoice recognition efficiency and accuracy rate are improved.
Owner:AEROSPACE INFORMATION
Generative Investment Process
InactiveUS20060287937A1Optimizes synergy valueLow costFinanceInformation analysisValue of information
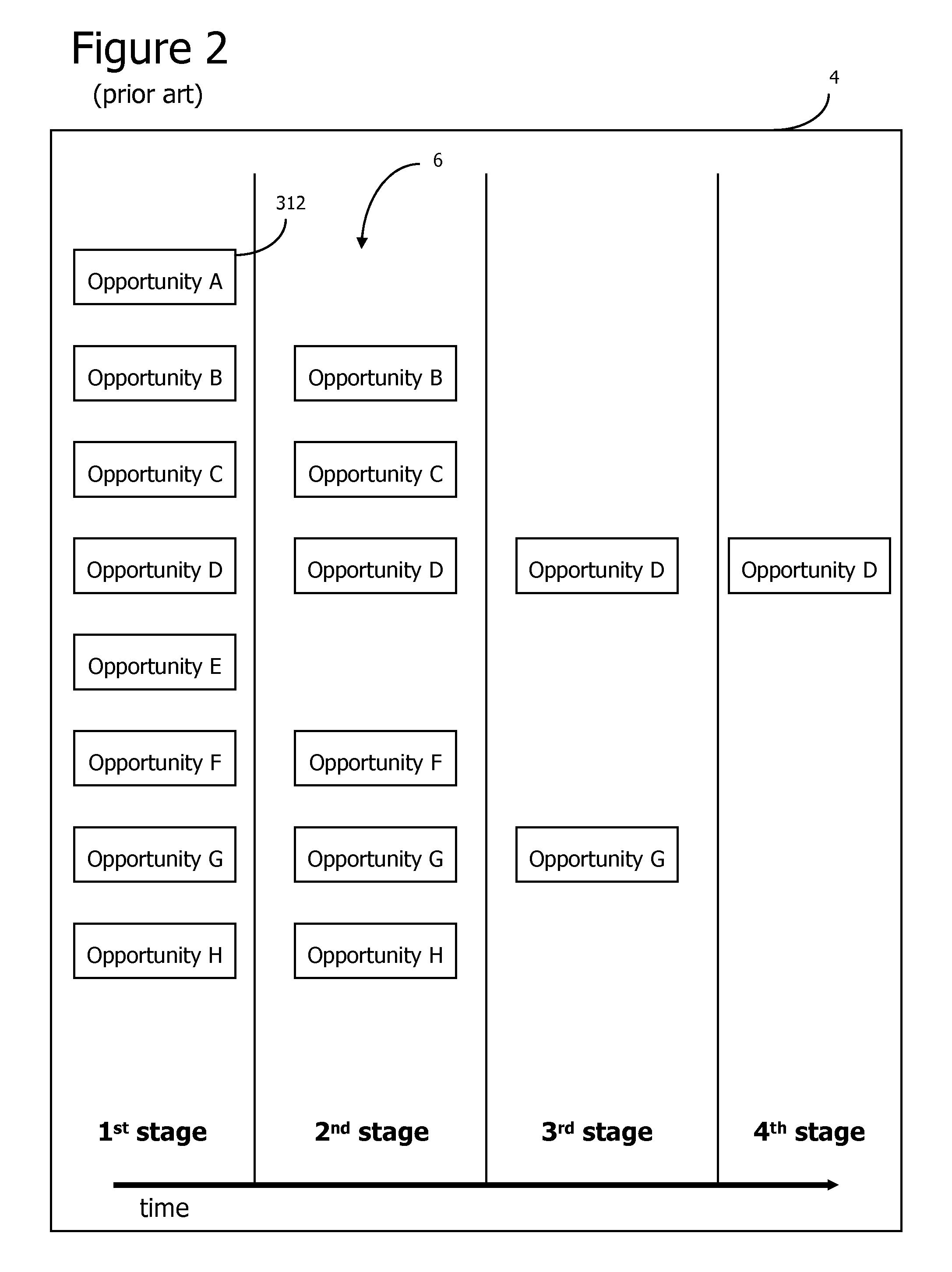
A generative investment process method and system is disclosed for managing investment opportunities. The process applies recursive decomposition to investment opportunities and applies a discrete combinatorial model to the resulting combinatorial investment portfolio, enabling evaluation of existing opportunities and generation of new opportunities. The process may apply decision analysis, value of information analysis, design of experiment models, and inferencing of gathered information, including experimental results. The process enables an efficient and adaptive approach to attaining additional information and assimilating the attained information into the investment opportunity decision process.
Owner:MANYWORLDS CONSULTING
Encoding/decoding method and apparatus using a tree structure
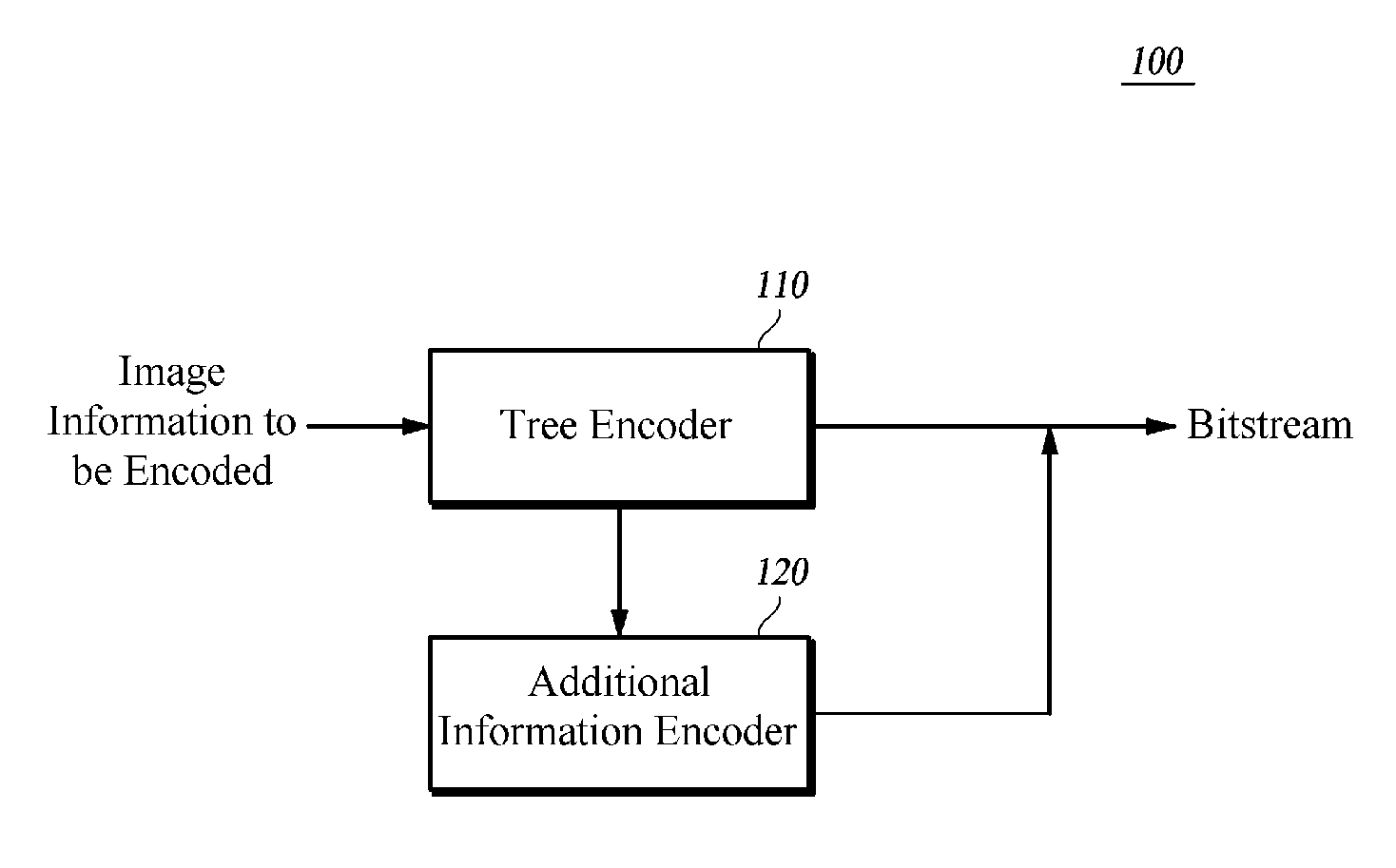
ActiveUS20120308148A1Efficient codingCharacter and pattern recognitionDigital video signal modificationDecoding methodsValue of information
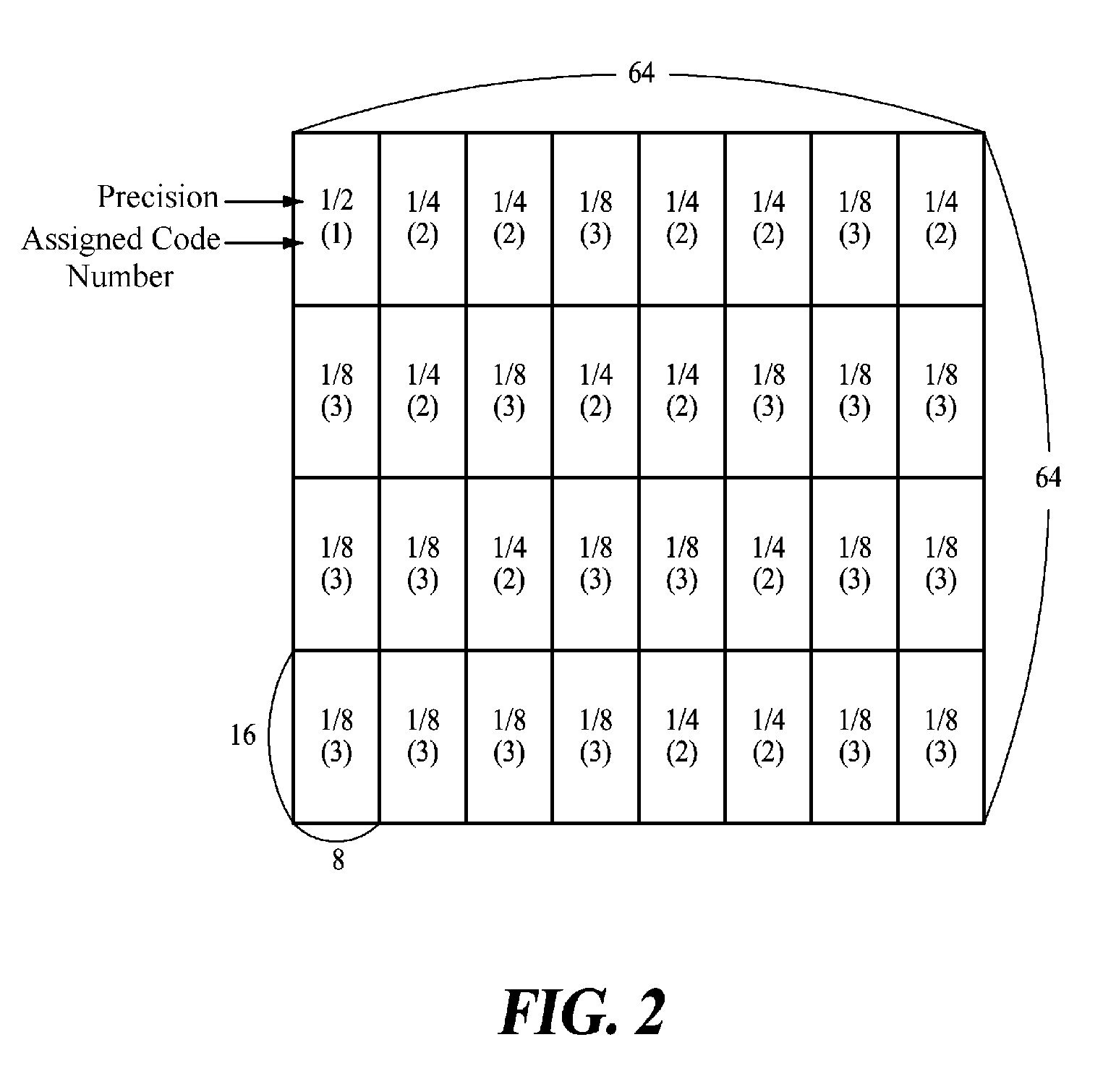
The present disclosure provides an encoding / decoding method using a tree structure. The encoding method for encoding image information includes: grouping predetermined areas having the image information into a plurality of groups, and generating a node value of each layer up to an uppermost layer by determining a minimum value or a maximum value of information to be encoded within grouped areas as information on the grouped areas; and encoding a difference value between the node value of each layer and a node value of an upper layer or a difference value between the node value of each layer and a value determined based on a preset criterion. Accordingly, the encoding efficiency and in turn the video compression efficiency are improved by using the tree structure in the encoding of various pieces of image information and the decoding of the resultant encoded data.
Owner:SK TELECOM CO LTD
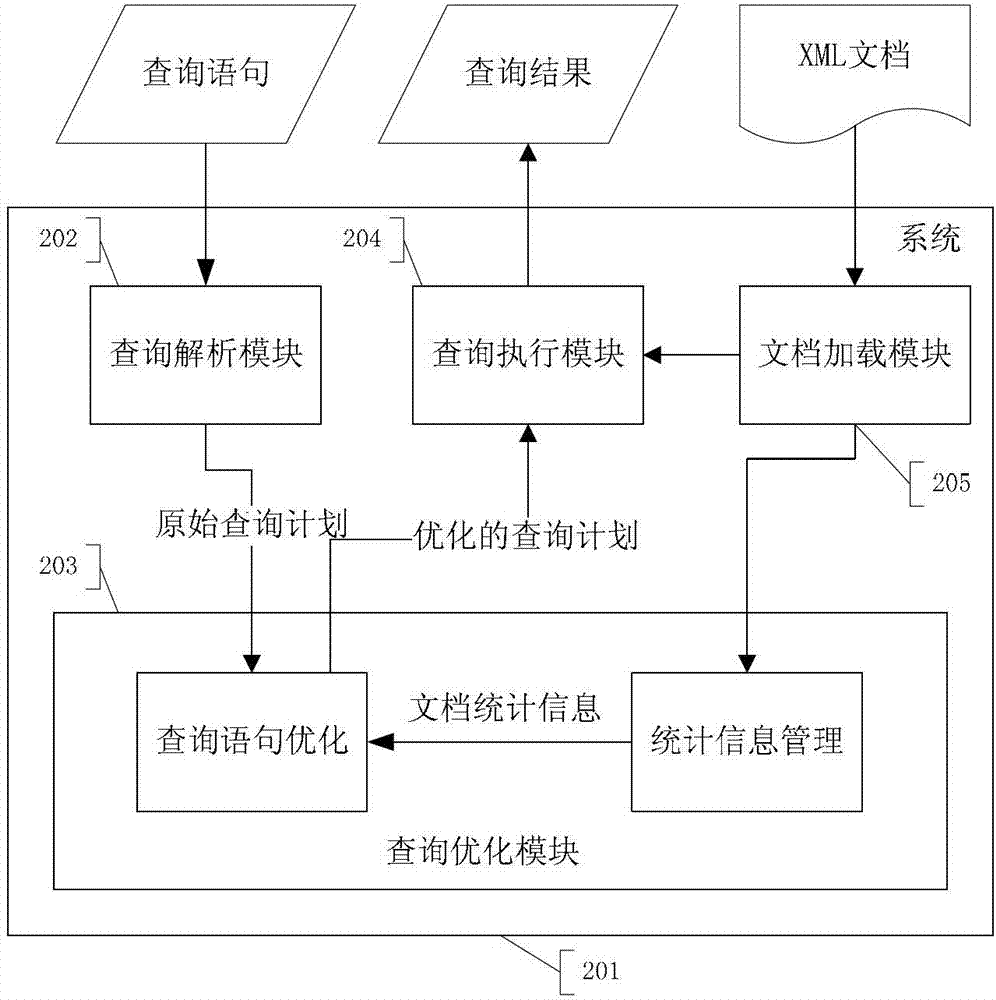
XPath query optimization method and system
ActiveCN102929996AEffective Structural Connection OrderOptimizing Query PlansSpecial data processing applicationsAlgorithmQuery optimization
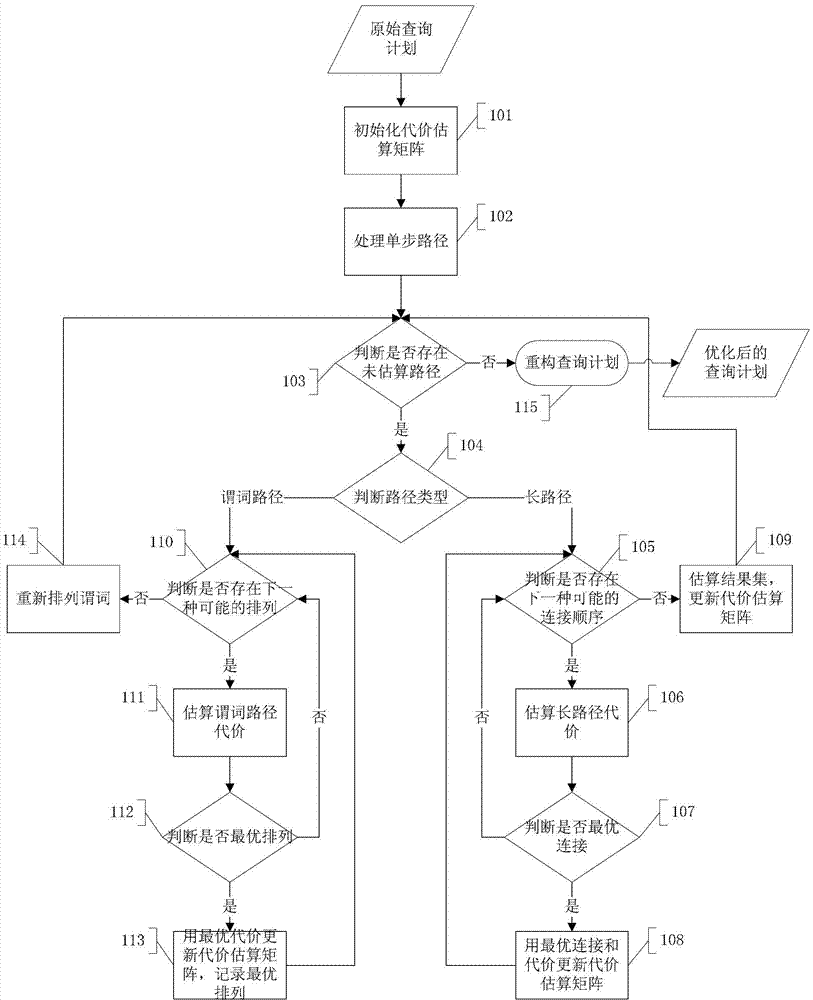
The invention discloses an XPath query optimization method and system. The method comprises the following steps of: counting structural summary information of an extensive makeup language (XML) document through hierarchical encoding; counting value summary information by using a value-coding histogram and RPST, and performing an optimization algorithm for query optimization on an XPath expression by utilizing the statistical information, wherein the query optimization algorithm comprises the following steps of: 101-102, initializing a data structure and processing a single-step path; 103, judging whether a non-estimated path exists; 104, judging the path type; 105-109, estimating connection with lowest cost in all possible connection of a long path, and updating a cost matrix and a result set matrix by using corresponding data; 110-114, estimating an arrangement sequence with lowest path in a predicate path, updating a cost matrix and a result set matrix by using the corresponding data, and resorting the predicates according to an optimized sequence; and 115, reconstructing a query plan. According to the XPath query optimization method and system, the XPath query sentences can be effectively optimized, and the execution efficiency of the XPath query sentences is greatly improved.
Owner:SOUTH CHINA UNIV OF TECH
Chart selection tooltip
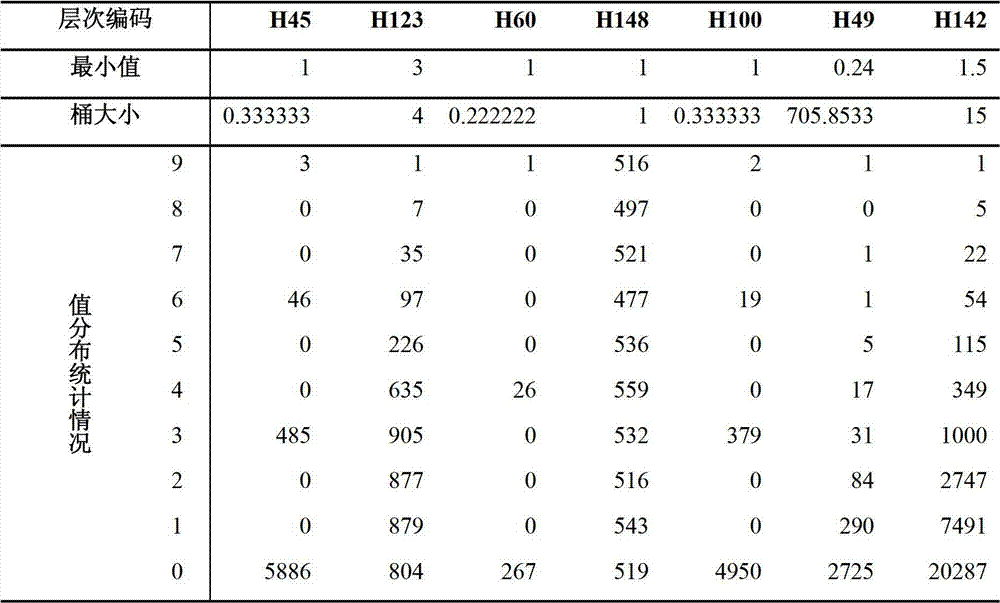
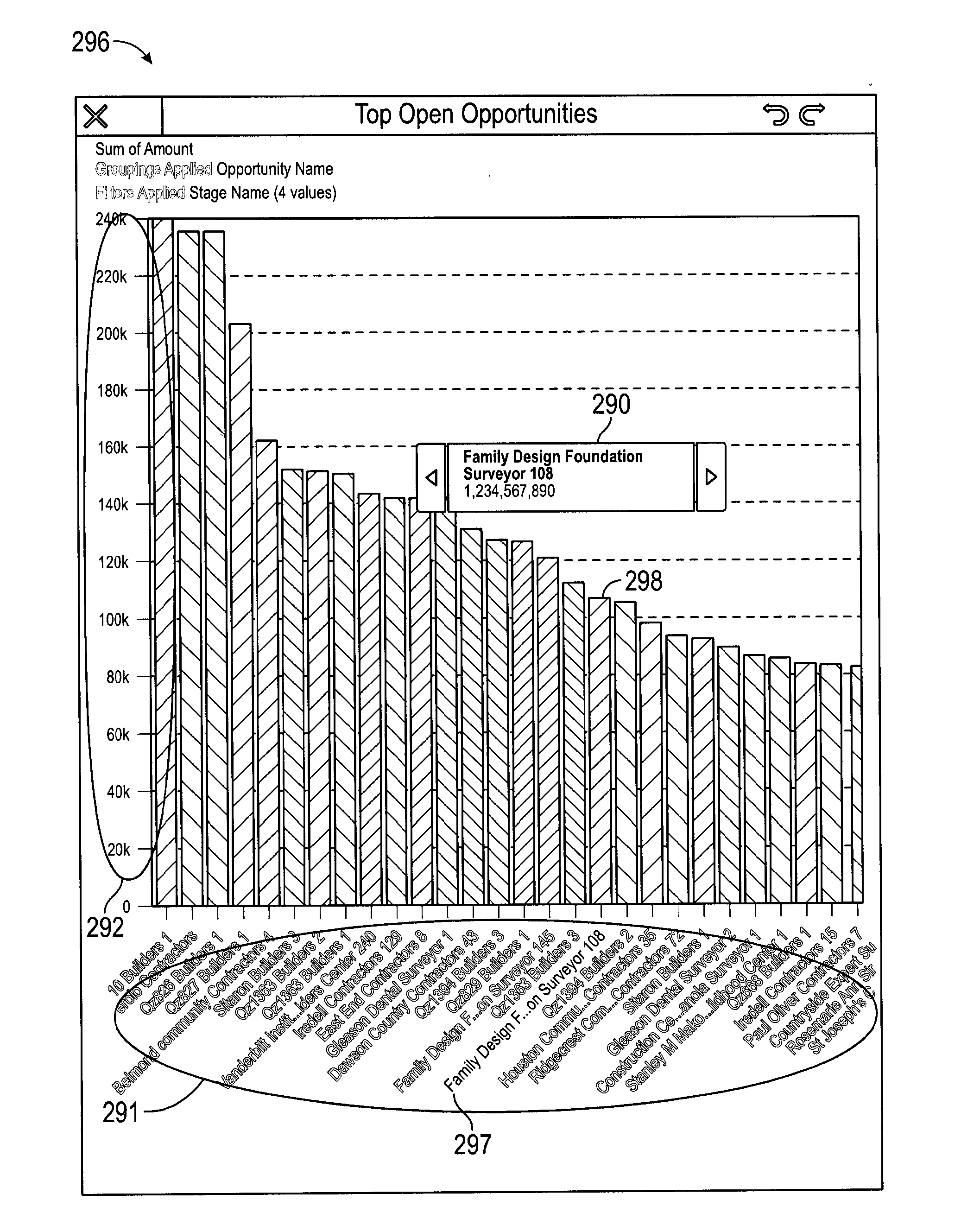
ActiveUS20160103581A12D-image generationInput/output processes for data processingData miningValue of information
Some embodiments of the present invention include an apparatus for enabling a tooltip to view information associated with portions of charts displayed on a display screen of a mobile computing device and include a processor, and one or more stored sequences of instructions which, when executed by the processor, cause the processor to display information associated with a chart on a display screen of a mobile computing system using a first chart type, the information including label information and value information Based on detecting a selection of a portion of the chart, cause the tooltip to be displayed on the display screen of the mobile computing system, the tooltip displaying label information and value information associated with the selected portion of the chart, the tooltip including a navigation tool to enable navigating and updating the tooltip with label information and value information associated with different portions of the chart.
Owner:SALESFORCE COM INC
Intelligent transformer substation relay protection inspection system
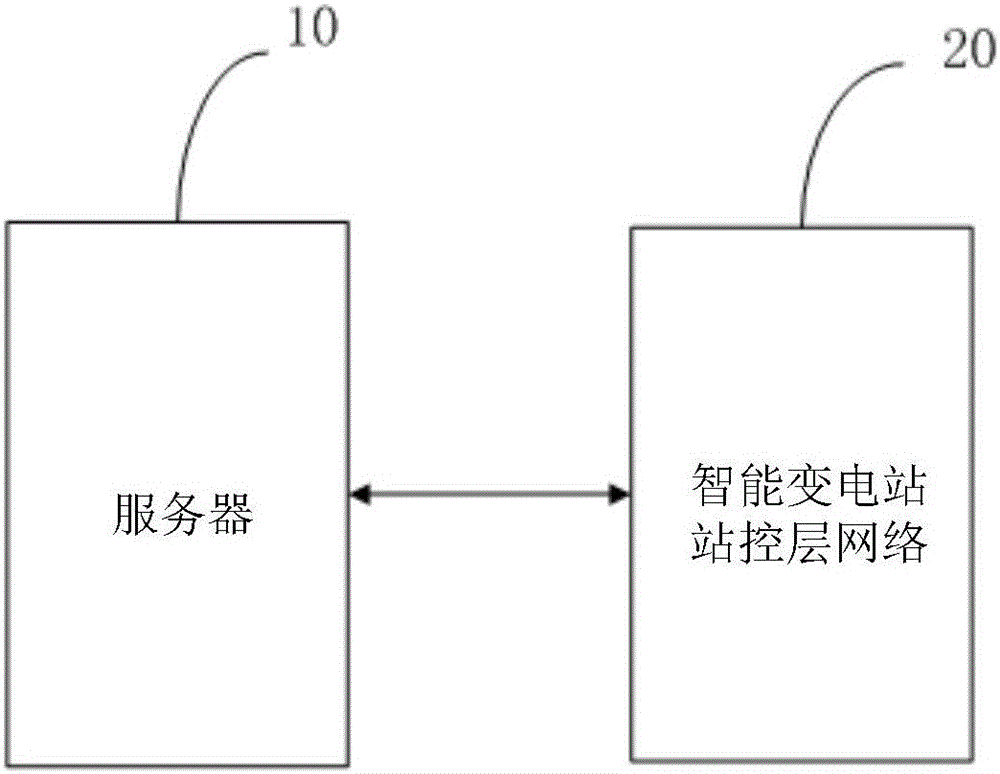
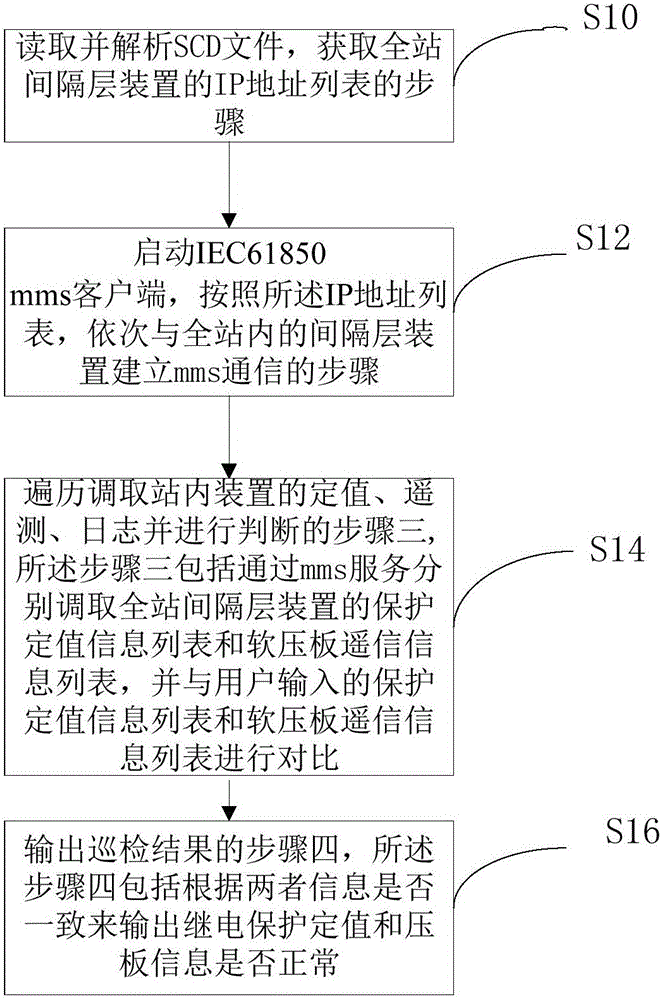
ActiveCN105790441AEliminate potential safety hazardsSafe and stable operationCircuit arrangementsInformation technology support systemControl layerSmart substation
The invention discloses an intelligent transformer substation relay protection inspection system. The system comprises a server connected to an intelligent transformer substation station control layer network. The server is used for executing a method comprising the following steps of reading and analyzing a SCD file and acquiring an IP address list of a full station spacing layer device; starting an IEC61850MMS client and successively establishing MMS communication with the spacing layer device in the full station according to the IP address list; traversing and taking a fixed value of the device in the station, remote metering and a log and carrying out determination, wherein the step includes taking a protection fixed value information list and a soft pressure plate remote communication information list and comparing to the information list input by a user; and outputting an inspection result, wherein the step includes whether an output relay protection fixed value and pressure plate information are normal. In the invention, relay protection fixed value checking is realized; checking efficiency of a relay protection equipment fixed value is increased; a problem of low efficiency is solved and inspection quality is greatly increased.
Owner:STATE GRID CORP OF CHINA +1
MIMO-SCMA system downlink design method based on STBC
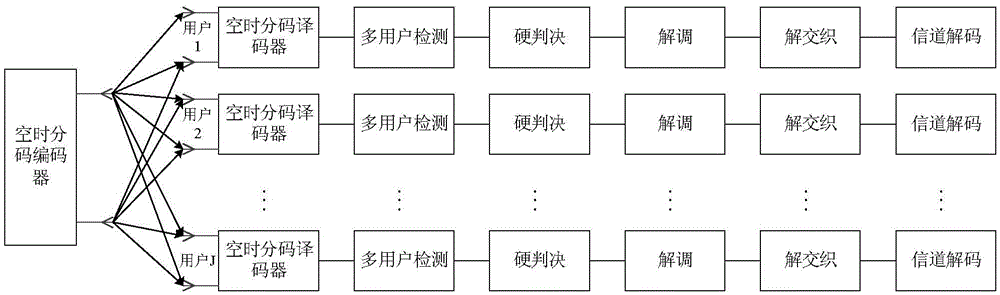
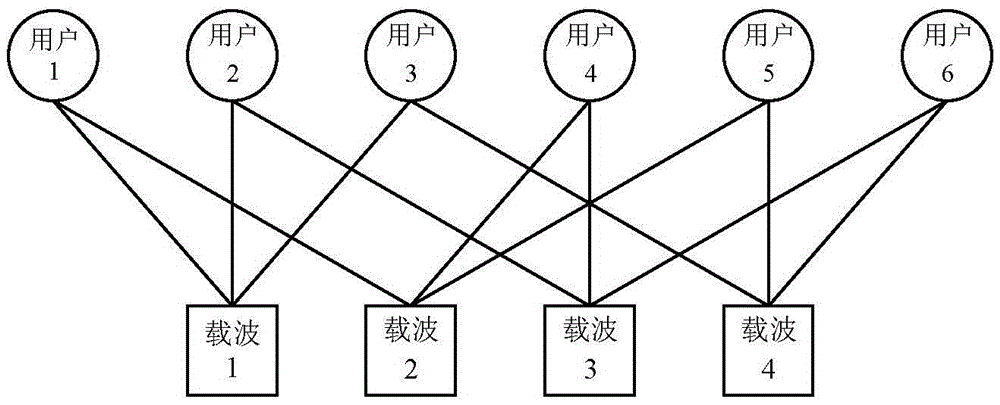
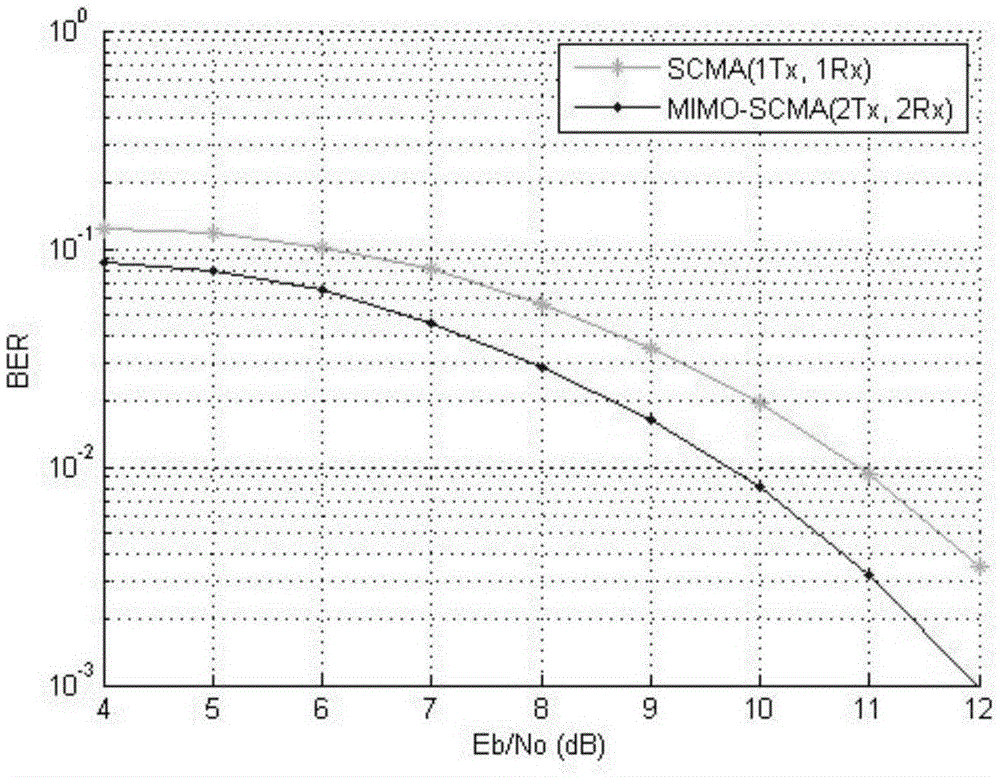
ActiveCN105554865AImprove spectrum utilizationImprove bit error rate performancePower managementCarrier signalEngineering
The invention provides an MIMO-SCMA system downlink design method based on STBC, and relates to the MIMO-SCMA system downlink design method. The MIMO-SCMA system downlink design method based on the STBC aims at the problems that error rate requires to be reduced by an SCMA technology and an MOMO-OFDM technology is difficult to meet the requirement of 5G for transmission rate. The method is realized by the steps that step one, two antennas of a base station are utilized to transmit TW and T'W; step two, user terminals are utilized to receive signals SW and S'W; step three, STBC decoding is performed on the signals SW and S'W received by each user terminal and then the decoded signals YW=[xw1xw2...xwK]T are obtained; step four, a factor graph is determined according to J users, occupation of K subcarriers, overload coefficient of J / K and a configuration matrix F; step five, the probability value of information transmitting of each user is obtained; and step six, information bits are obtained. The MIMO-SCMA system downlink design method based on the STBC is applied to the field of MIMO-SCMA system downlink design.
Owner:HARBIN INST OF TECH
Signature log storing apparatus
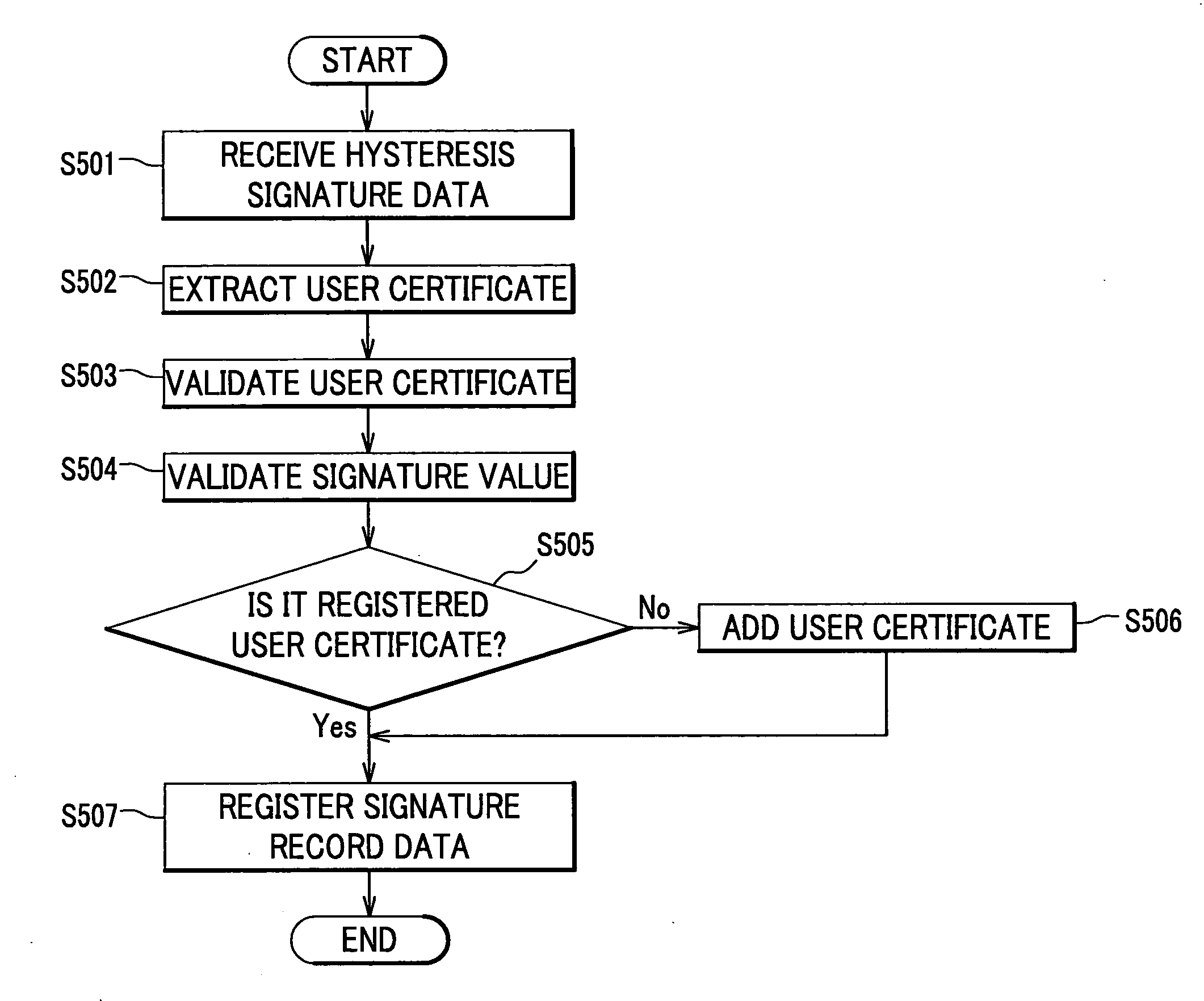
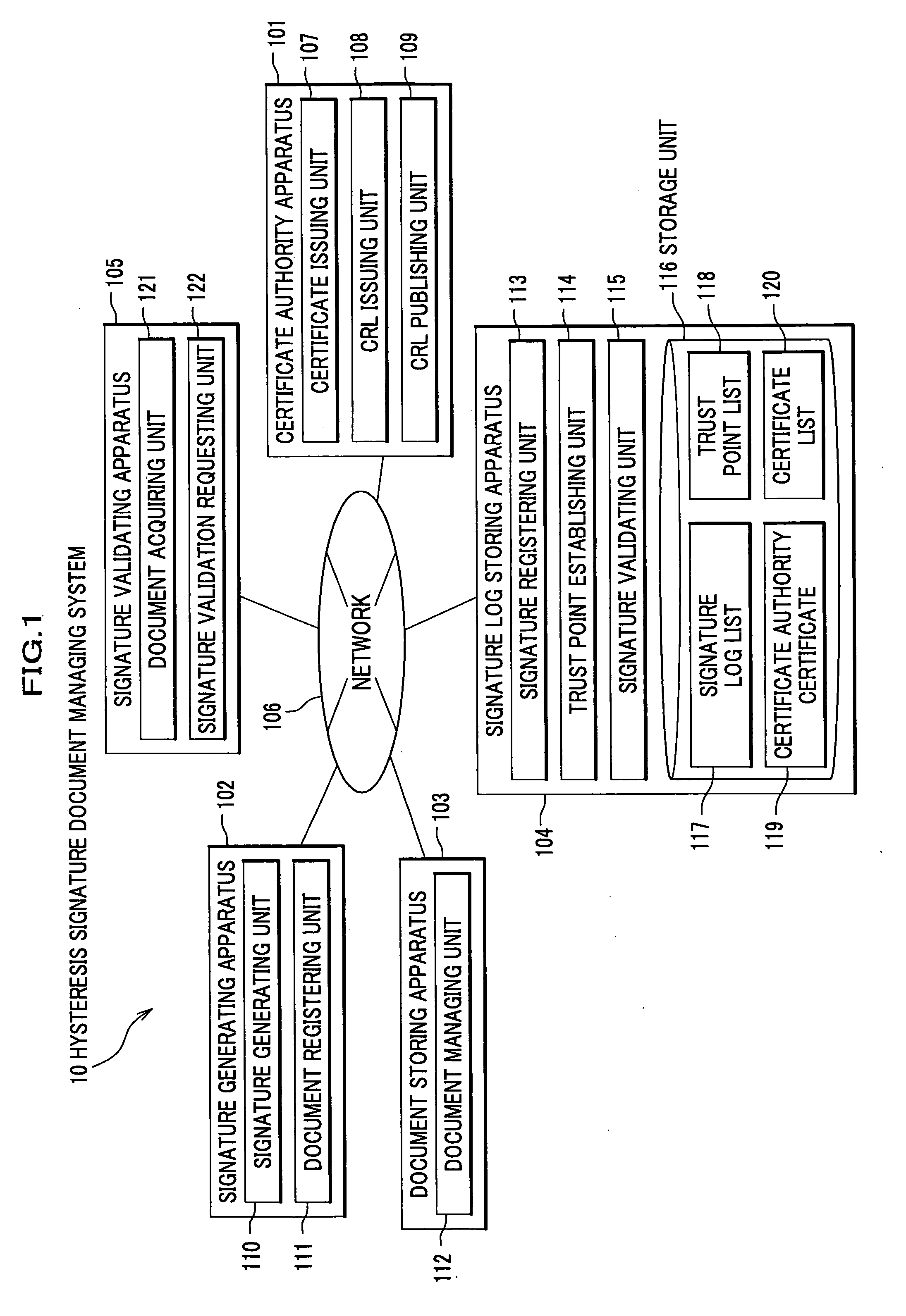
ActiveUS20070083763A1Reduce storage capacityReduce capacityUser identity/authority verificationValue of informationComputer security
A signature log storing apparatus includes a signature log list and a certificate list, and registers, in the signature log list, a part of signature information in generated hysteresis signature as a signature record and a part of a user certificate in the certificate list. The signature log storing apparatus further includes a trust point list and validates a signature records registered in the signature log list and registers identification information for identifying a latest signature record out of the validate signature record, evidence information for validating validity of the user certificate for a validated signature record, and a hash value of information derived by connecting the evidence information and the hash value as needed or before the user certificate expires.
Owner:HITACHI LTD
Method and device for correcting energy value
InactiveCN104035122AEliminate offsetDoes not reduce statsX/gamma/cosmic radiation measurmentScintillation crystalsPeak value
The invention provides a method and a device for correcting an energy value. The method comprises the following steps: presetting an energy correction coefficient table; calculating the product of the to-be-corrected energy value of each to-be-corrected single event and the energy correction coefficient of the each to-be-corrected single event to obtain the corrected energy value of the each to-be-corrected single event; counting an energy value-count value curve according to the corrected energy value. The energy correction coefficient is the ratio of a theoretical energy peak value in the energy valve-count value curve obtained by counting an extensive source radiation scintillation crystal array to a detected energy peak, thus the obtained corrected energy value of each to-be-corrected single event deviates towards the theoretical energy value of information about the position of the to-be-corrected single event, thereby eliminating the deviation between an energy value corresponding to a detected count peak value and an energy value corresponding to the theoretical count peak value on the premise of not reducing the statistical information of a scintillation crystal array edge single event.
Owner:NEUSOFT MEDICAL SYST CO LTD
Method for realizing information transmission security based on digital envelope technology
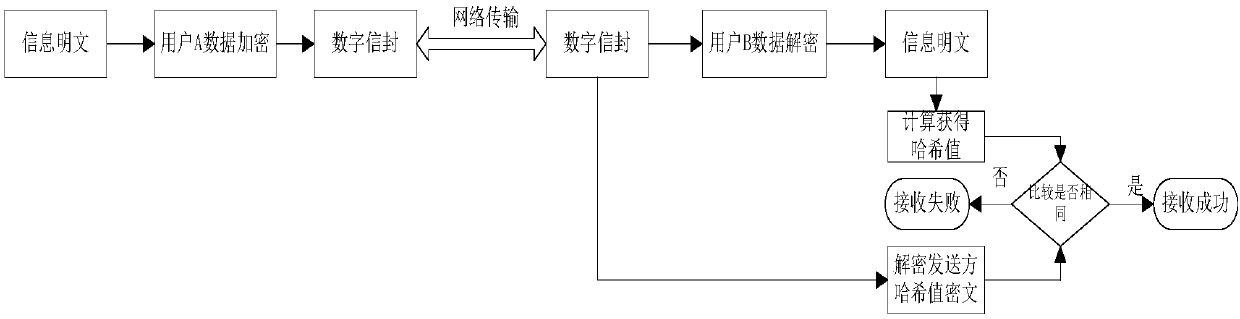
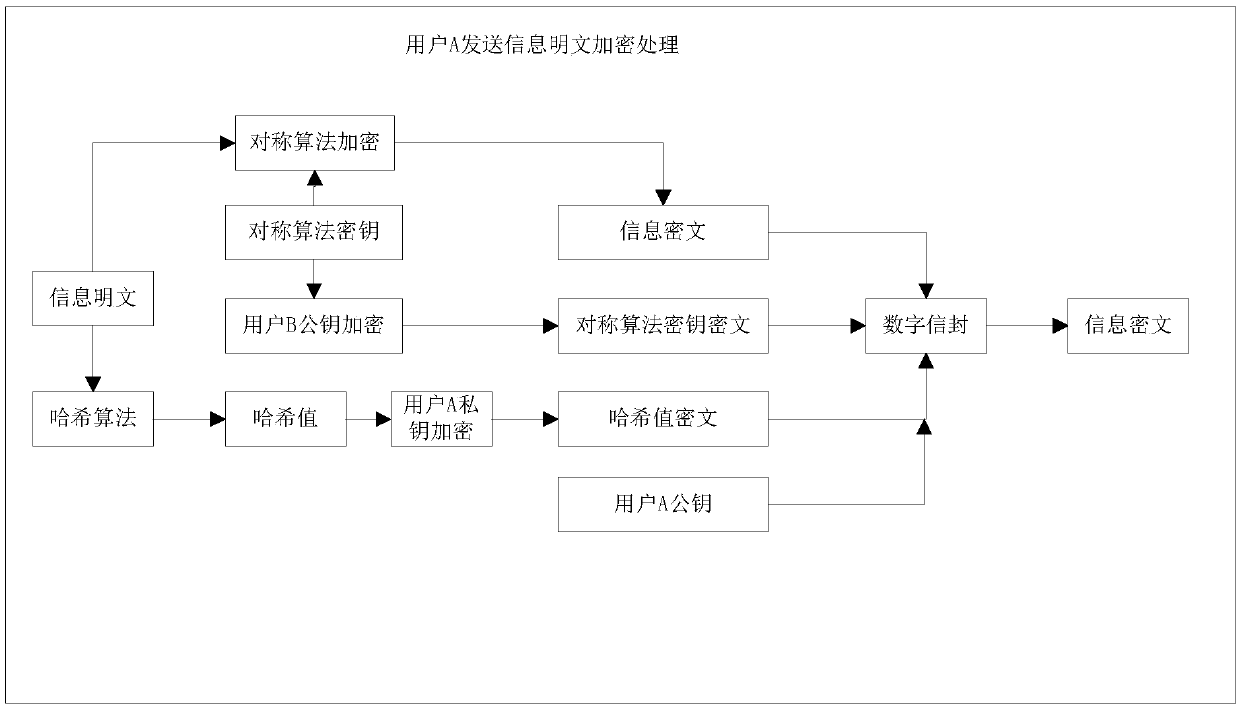
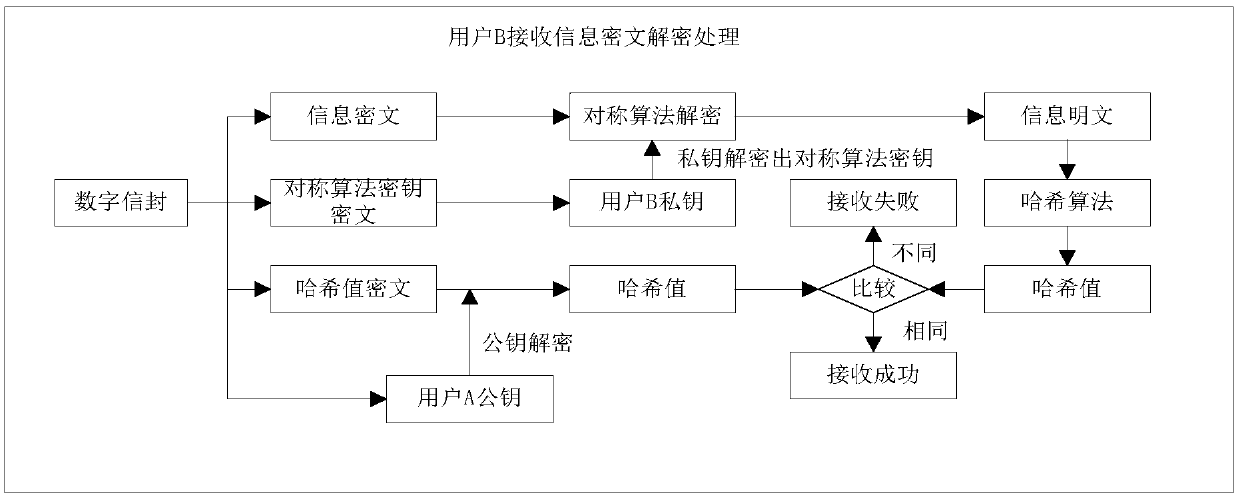
PendingCN108683688AAvoid inconsistenciesFast transmissionEncryption apparatus with shift registers/memoriesUser identity/authority verificationKey exchangePlaintext
The invention discloses a method for realizing information transmission security based on digital envelope technology. The method comprises the following steps: information plaintext of a user A is subjected to data encryption to output information ciphertext, symmetric algorithm key ciphertext, hash value ciphertext of information plaintext and user A public key which are processed by the digitalenvelope technology and then transmitted to a user B through a network; the user B receives inputs encapsulated by the digital envelope technology: information ciphertext, symmetric algorithm key ciphertext, hash value ciphertext of information plaintext and user A public key, and performs decryption to output information plaintext and hash value of information plaintext sent from the user A; andthe received information plaintext is subjected to hash calculation to obtain a hash value, and two hash values are compared to determine whether the information transmission is successful. The invention adopts the digital envelope technology to solve key exchange, synchronization and management problems, in real-time transactions, a large amount of information is encrypted by symmetric algorithm, and only a small number of symmetric encryption algorithm keys are encrypted and decrypted by asymmetric algorithm for exchanging keys and verifying the authenticity of information, which improves the speed of information transmission and reduces the consumption of resources.
Owner:CHINA CONSTRUCTION BANK
Mineralizing abnormal extraction method based on multifractal Krige method
InactiveCN102254095AExcellent interpolation resultImprove certaintySpecial data processing applicationsSkew normal distributionLower limit
The invention discloses a mineralizing abnormal extraction method based on a multifractal Krige method. The mineralizing abnormal extraction method is characterized by comprising the following steps of: performing the inspection of normal distribution on an exploration geochemical data set to be analyzed, calculating an experimental variance function value for the data set which submits to the normal distribution, and fitting the experimental variance function value by a theoretical variance function model to acquire relevant parameters in the theoretical variance function model; and solving an abnormal lower limit value effectively according to a multifractal Krige interpolation result on the basis of establishing local high-value information and highlighting weak anomaly to acquire a reliable mineralizing abnormal area for prospecting and exploration.
Owner:HEFEI UNIV OF TECH
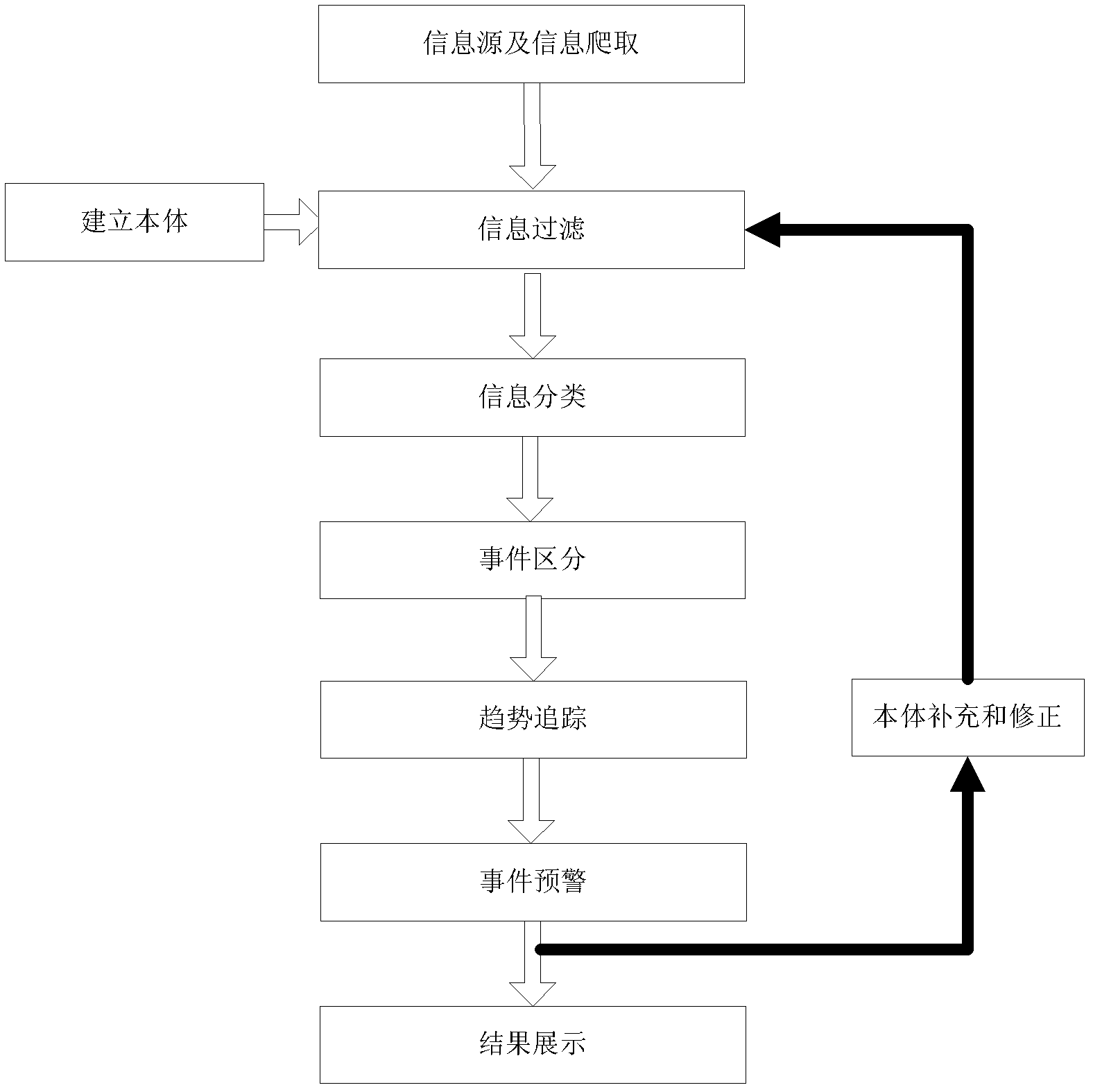
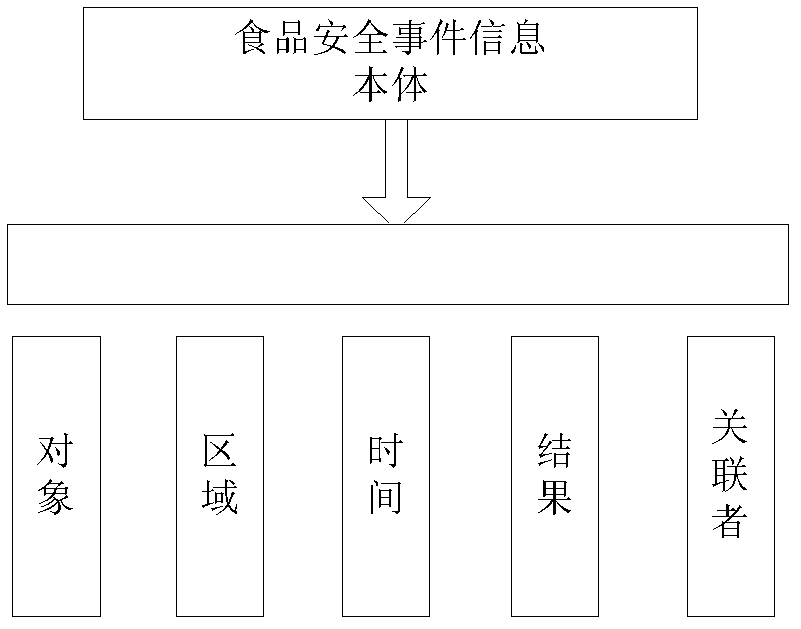
Event information mining and warning method
ActiveCN103176981AGuaranteed continuous improvementGuaranteed to be perfectForecastingSpecial data processing applicationsClassified informationWeb site
The invention discloses an event information mining and warning method, and belongs to the technical field of information. The method comprises the following steps: step 1, an event information ontology is built, obtained internet information is filtered, and information corresponding to an event is obtained; step 2, classification is conducted to the filtered information basing on the instance name and attribute in the event information ontology; step 3, clustering is conducted to the classified information according to set features, invents contained in each type of information are obtained; step 4, event feature parameter values of information page number, page views, page forward number, information source area number, information source web site number and the like of each event are calculated at fixed period; and step 5, if a difference value between the feature parameter values of a certain event and the mean value of the period time before exceeds a pre-set threshold value, alarming is conducted to the event. The event information mining and warning method ensures accuracy and comprehensiveness of information discovery and alarming of food safety events, and improves the efficiency of alarming of food safety risks.
Owner:COMP NETWORK INFORMATION CENT CHINESE ACADEMY OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com