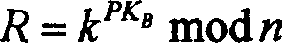High performance and quick public pin encryption
A public key encryption and fast technology, applied in the field of information security, can solve the problems of slow running speed, impracticality, and impractical application of data encryption system, etc., and achieve the effect of fast encryption speed, strong practicability, and fast encryption speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
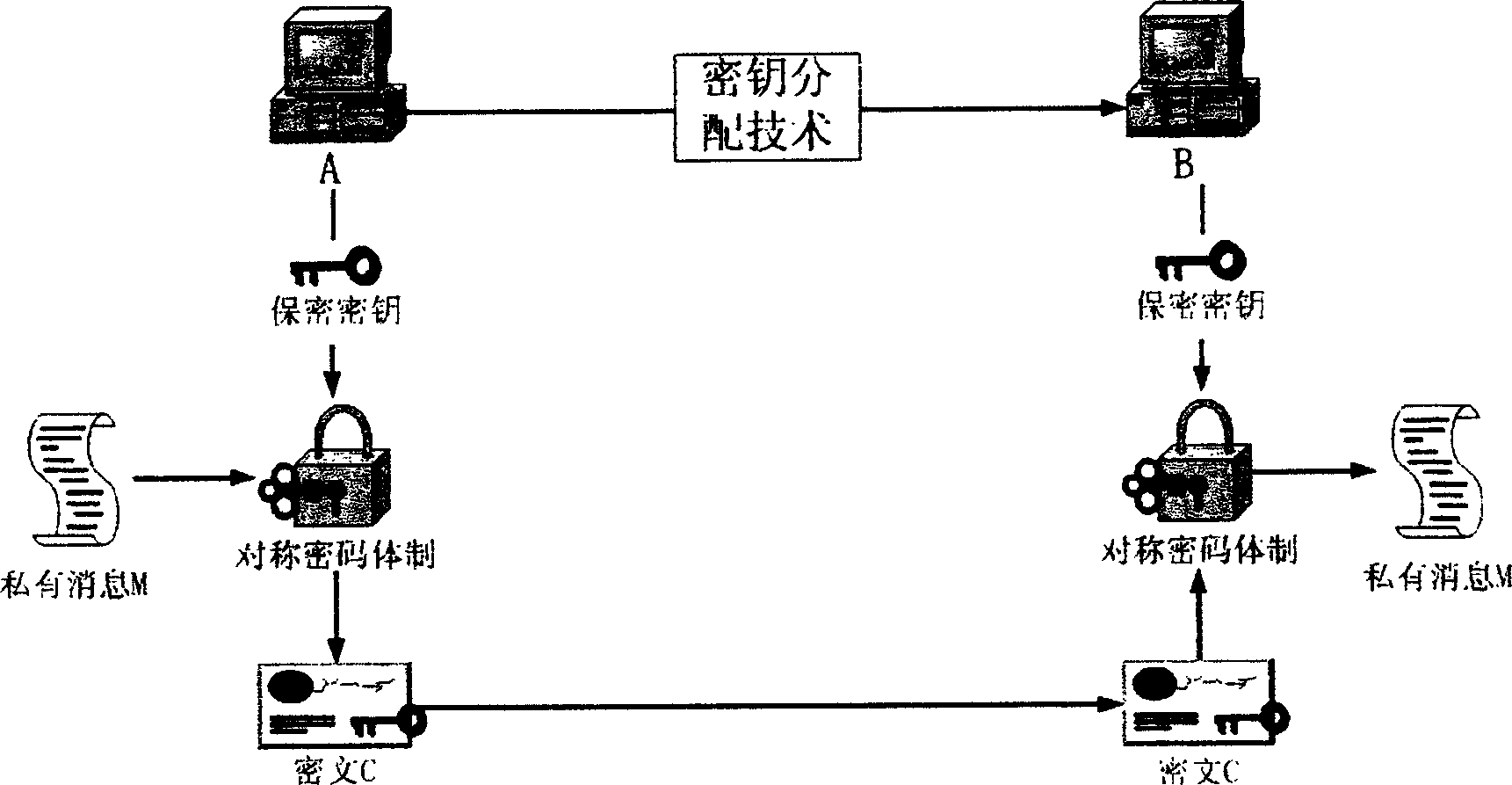
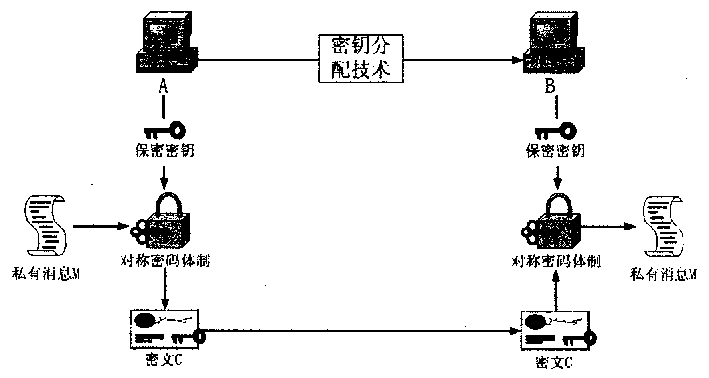
[0016] When the public key key distribution technology is the XECDA key distribution technology based on the elliptic curve discrete logarithm problem, and when the symmetric cryptosystem selects AES, the specific implementation of the present invention is as follows:
[0017] System parameters: Randomly select a large prime number p, elliptic curve E(GF(p):y 2 =x 3 +ax+b(mod p) is a secure elliptic curve defined on the finite field GF(p), on which the base point randomly selected is G, let n=#E(GF(p) be the order of the elliptic curve E, r is a large prime factor of n. The private key SK of A and B A and SK B is a random positive integer less than r-1. Then the public key PK A and PK B Get it as follows:
[0018] And placed in a trusted third-party certification center. Then the data encryption process is as follows:
[0019] a) A randomly selects an integer k∈[1, r-1], calculates K=k×G, then K is the secret key used in the symmetric cryptosystem AES in this data en...
Embodiment 2
[0022] The implementation method when the public key cryptosystem chooses RSA and the symmetric cryptosystem chooses DES:
[0023] System parameters: randomly select two large prime numbers p, q (need to be kept secret), calculate their product n=pq, as the public modulus of the system, randomly select an integer as the public key PK of the communication party A (B) A (PK B ), then its private key SK A (SK B ) can be obtained as follows:
[0024] in,
[0025] (n)=(p-1)×(q-1)
[0026] At the same time, the public key PK A (PK B ) placed in a trusted third-party certification center, the data encryption process is as follows:
[0027] a) A randomly selects a positive integer k∈[1.n-1], then K=k is the secret key used in the symmetric encryption system DES in this data encryption process, and at the same time, use the secret key K to The sent private message M is encrypted with DES symmetric encryption technology, and the ciphertext C is obtained. And...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com