Cloud-storage-oriented trusted storage verification method and system
A verification method and cloud storage technology, applied in the field of computer software, can solve problems such as failure to access documents, potential safety hazards, signature results that cannot reflect the real situation of documents, etc., and achieve the effect of avoiding leakage and small calculation costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0074] In this embodiment, the user uploads the file file1 to the untrusted network storage server, and the file size is 100MB. The user requires storage verification of the file, which needs to be verified once a day for two years, so the maximum number of verifications is 730. The user requested a confidence level of "0.9" for storage verification.
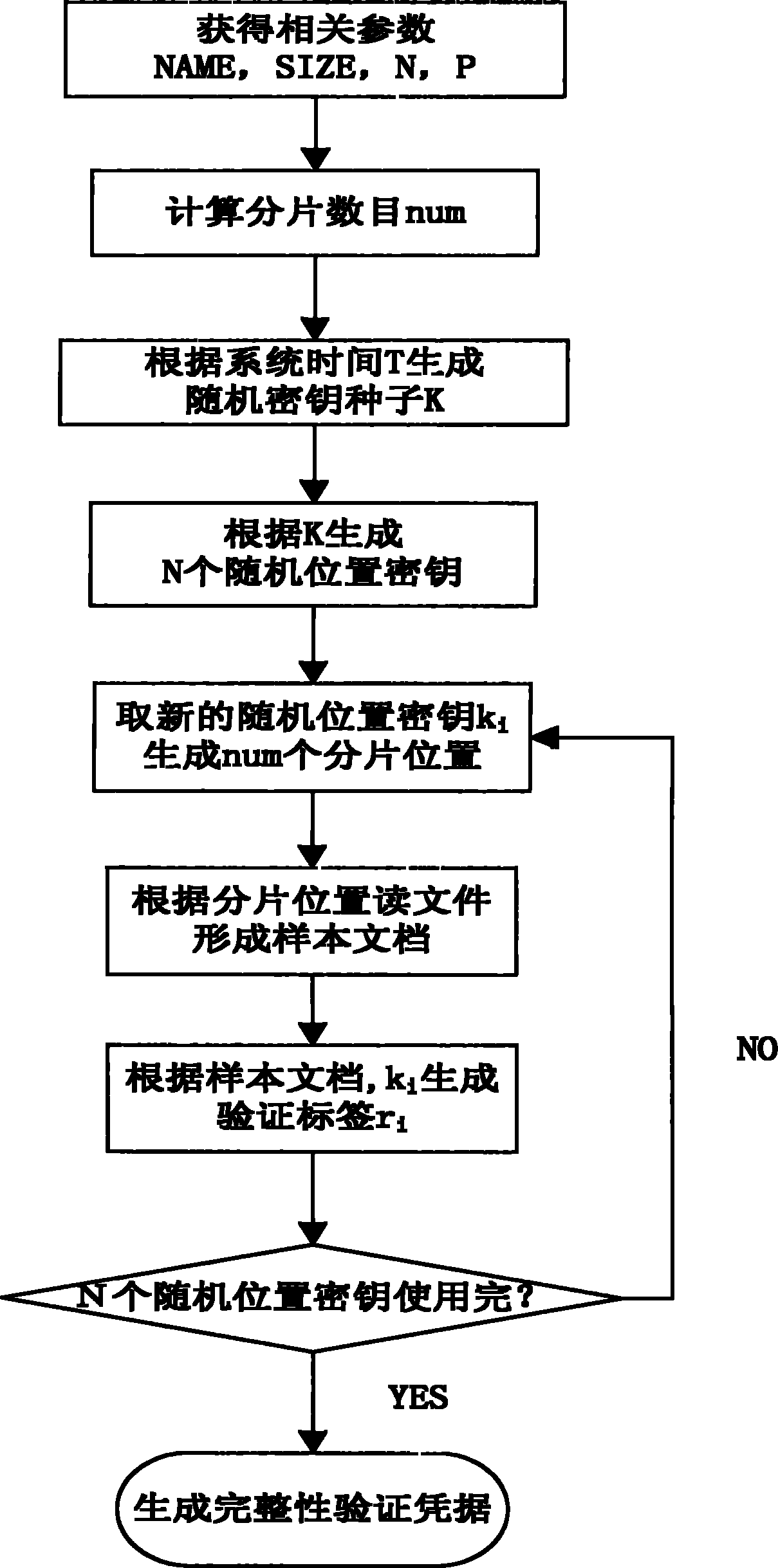
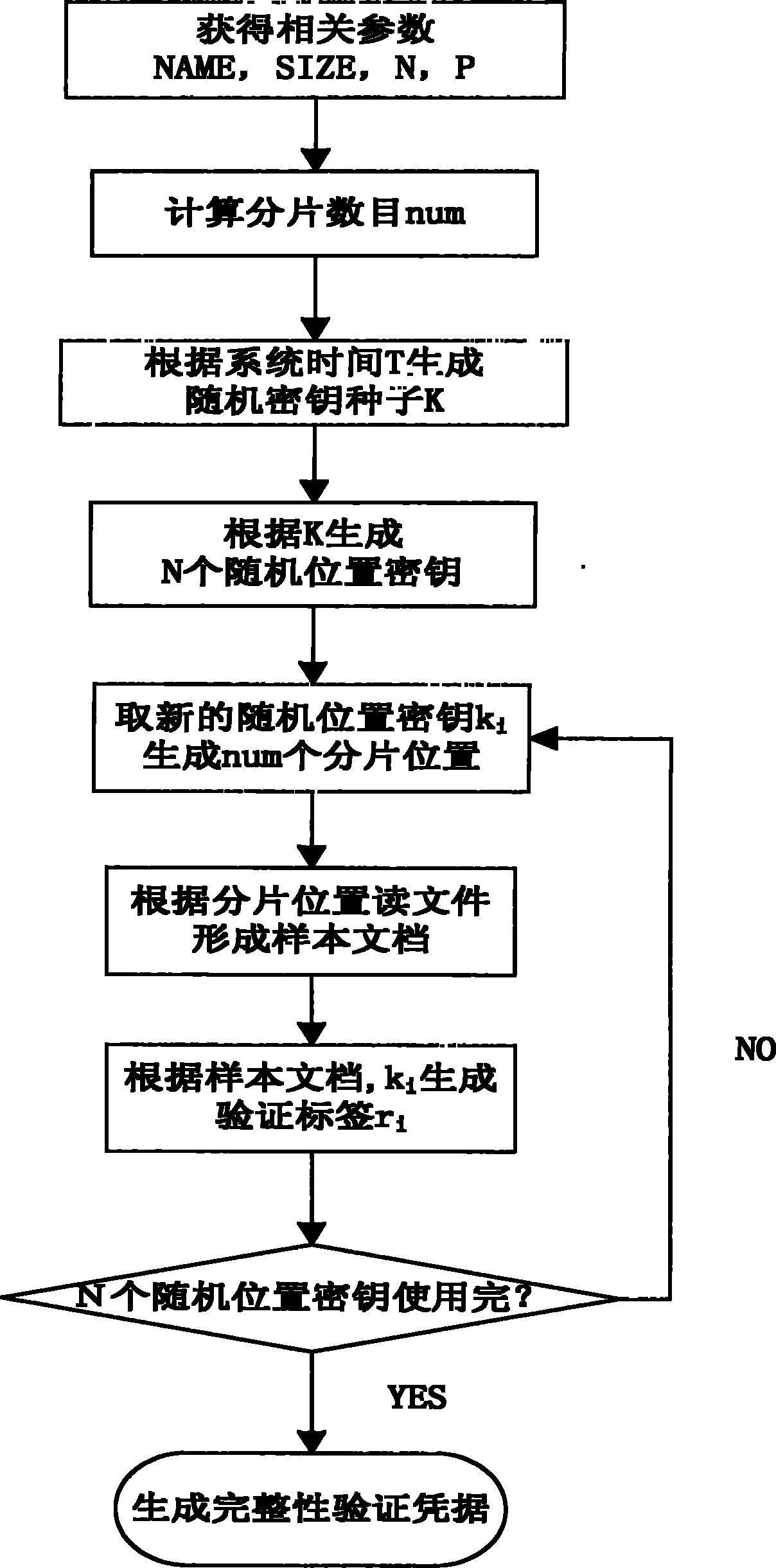
[0075] The flow process of the storage verification of the present invention is as follows,
[0076] 1) The user initiates a file storage verification preparation request
[0077] 2) The storage verification preparation module determines the file that the user needs to prepare for storage verification: NAME (file1);
[0078] 3) The storage verification preparation module determines the size of the file: SIZE (104857600Byte);
[0079] 4) The storage verification preparation module determines the number of times N that requires storage verification: 730;
[0080] 5) The storage verification preparation module determines the re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com