Patents
Literature
66results about How to "Prevent replay" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
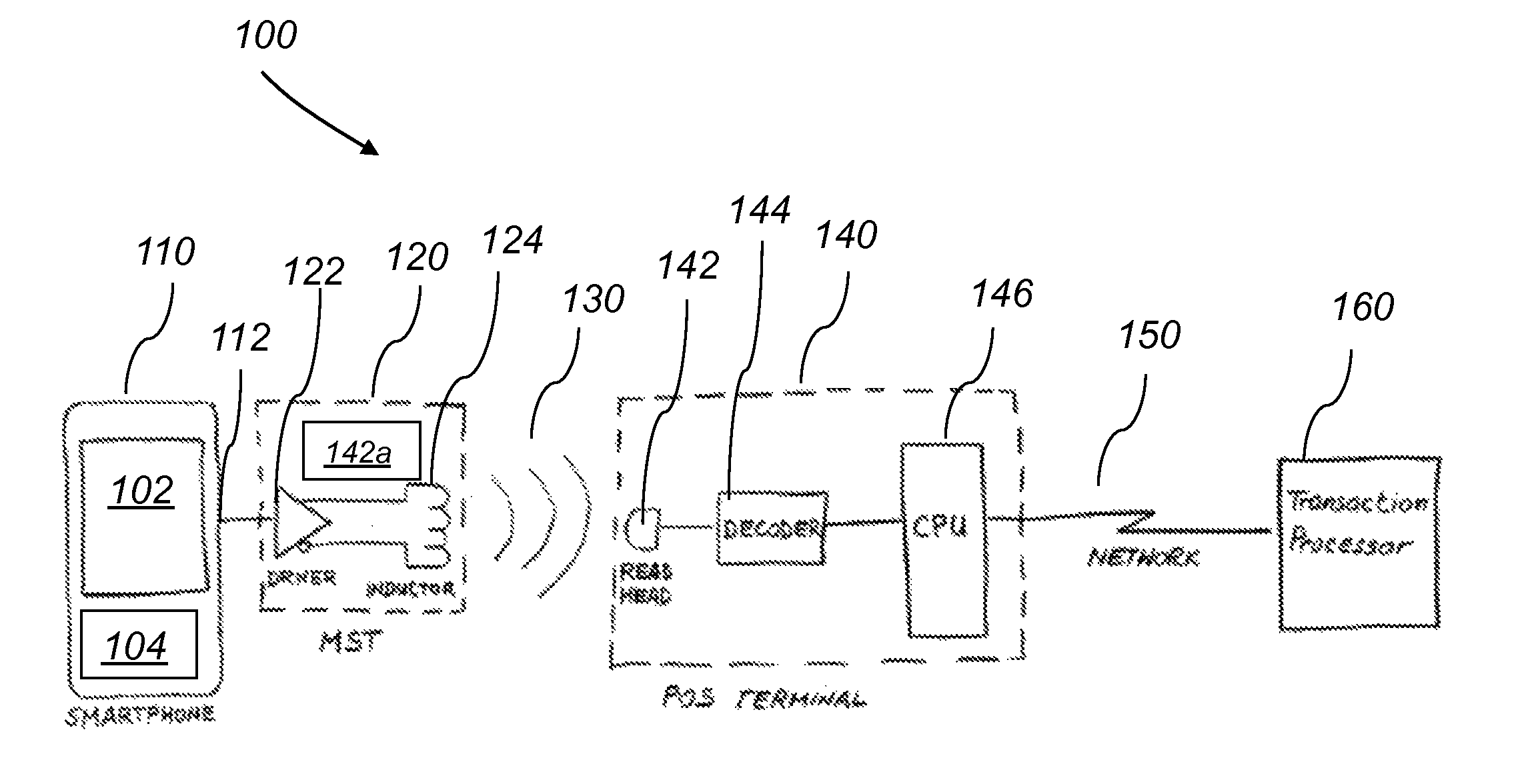
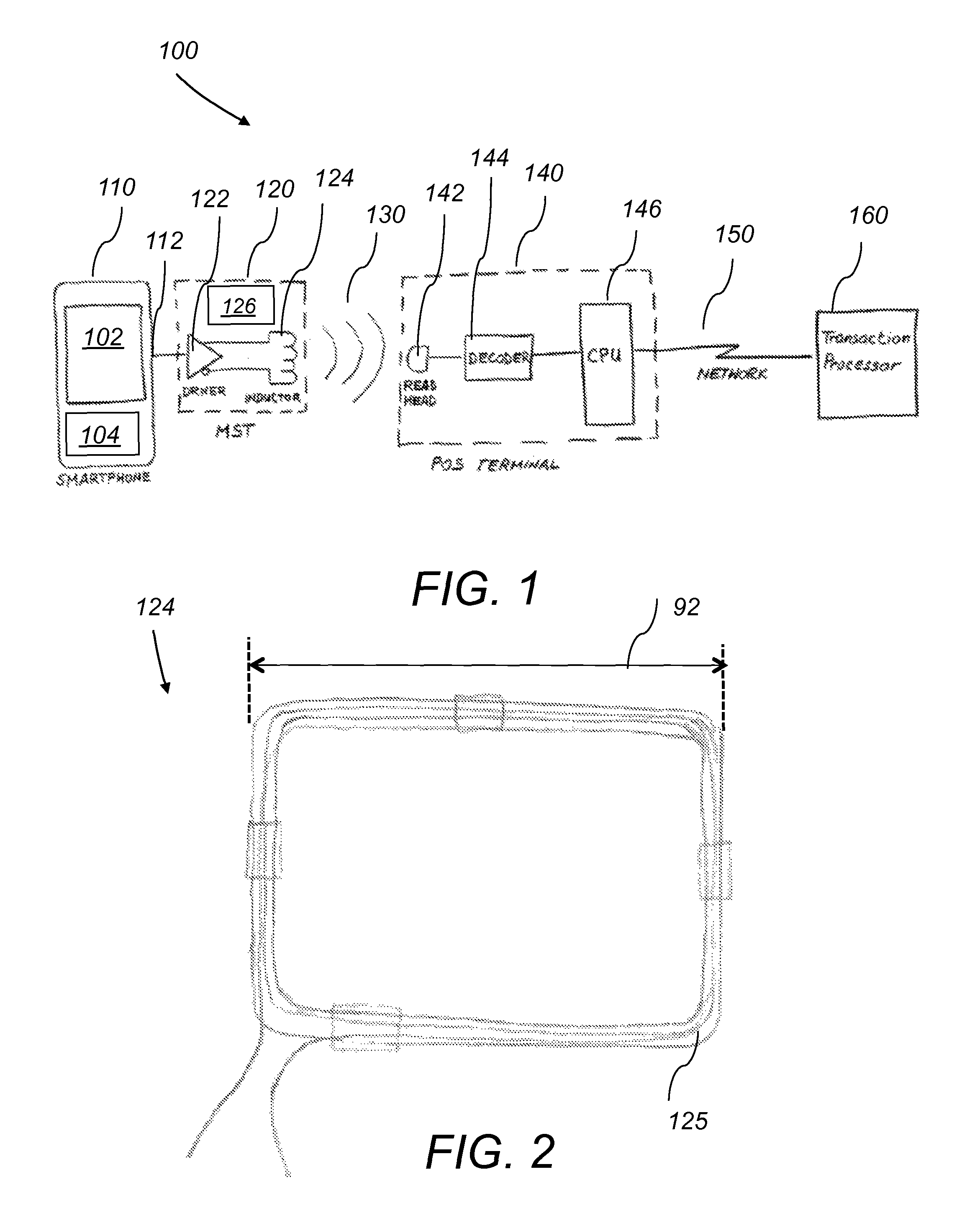
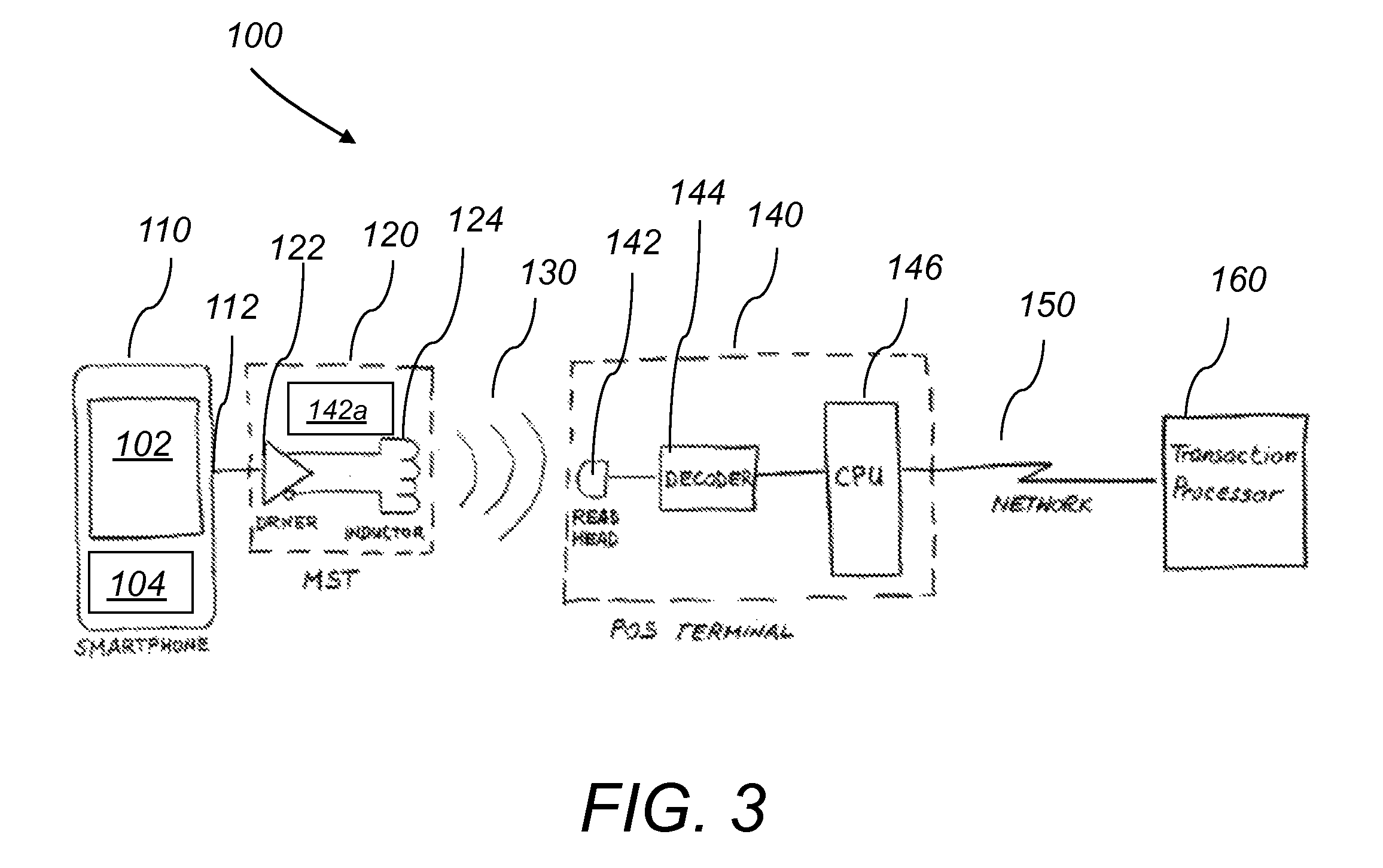
System and method for a baseband nearfield magnetic stripe data transmitter
ActiveUS8814046B1Prevent replayPrevents copy attackNear-field transmissionPayment architectureHigh energyWaveform shaping
A system for a baseband near field magnetic stripe data transmitter includes a mobile phone and a magnetic stripe transmission (MST) device. The mobile phone transmits a stream of pulses including magnetic stripe data of a payment card. The magnetic stripe transmission (MST) device includes a wave shaper, a driver and an induction device. The MST device receives the stream of pulses from the mobile phone, shapes and amplifies the received stream of pulses and generates and emits high energy magnetic pulses including the magnetic stripe data. The emitted high energy magnetic pulses are picked up remotely by a magnetic read head. The MST device shapes the stream of pulses to compensate for shielding, eddy current losses and limited inductance value of the magnetic read head.
Owner:SAMSUNG ELECTRONICS CO LTD
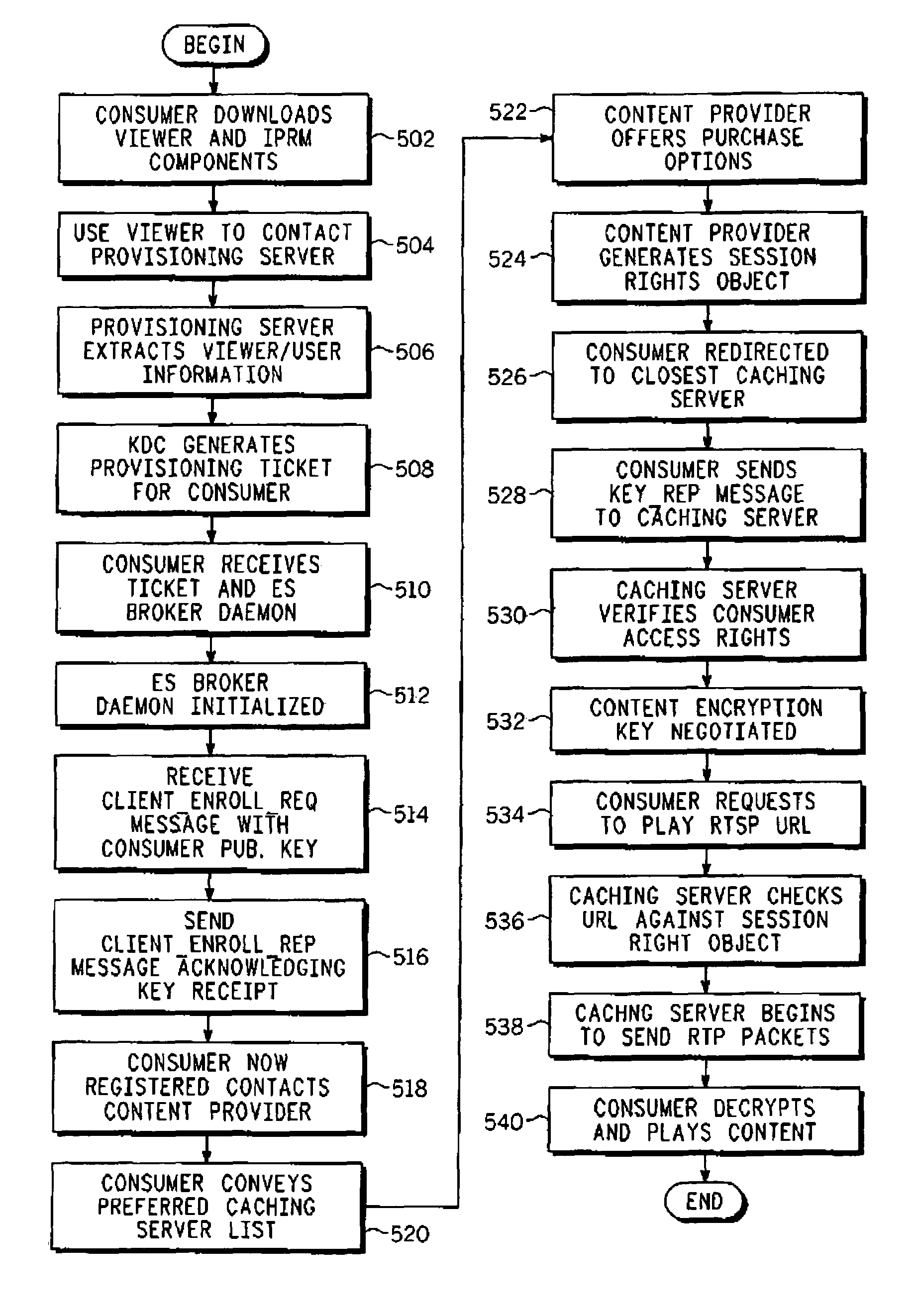
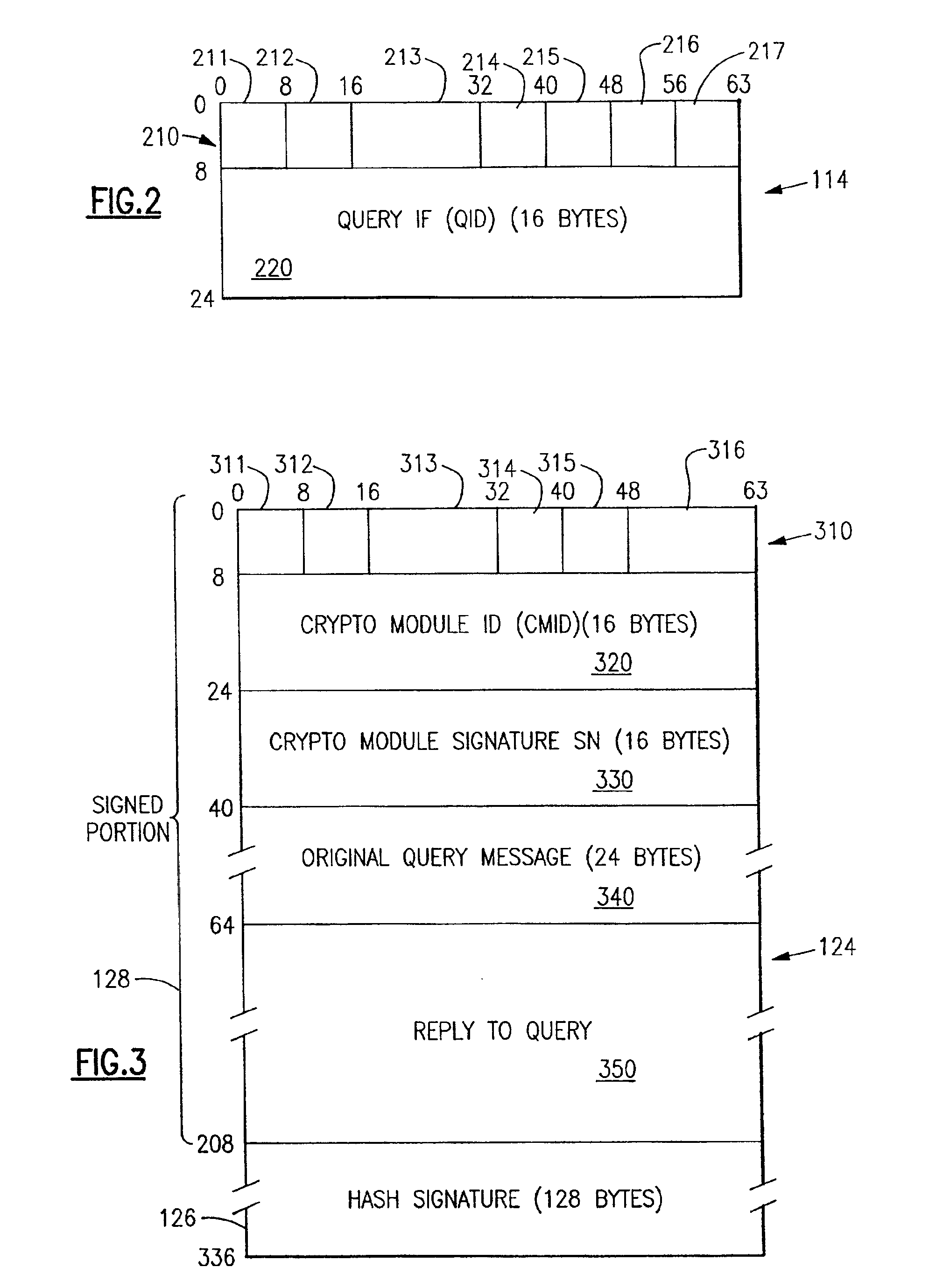
Encryption of streaming control protocols and their headers
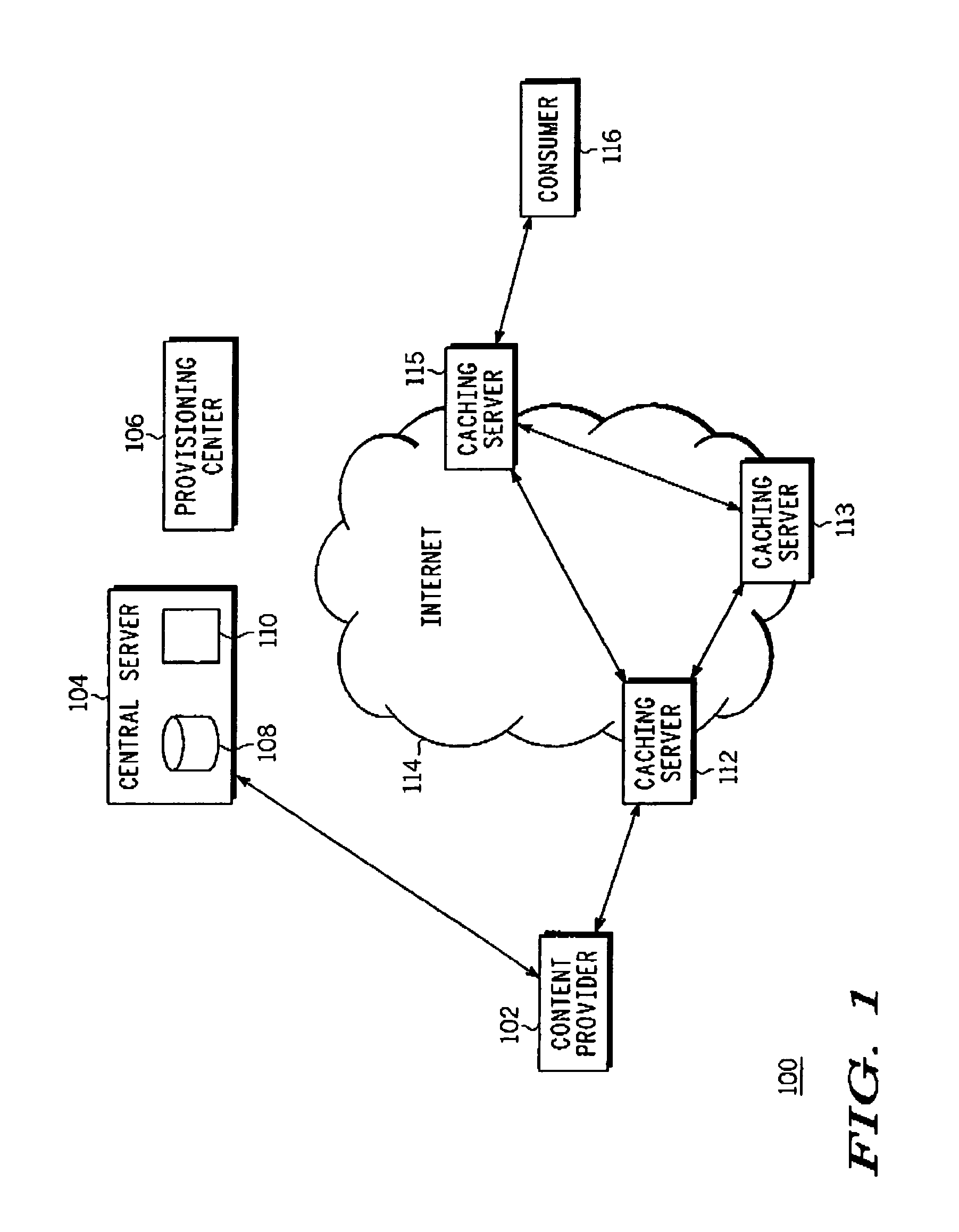
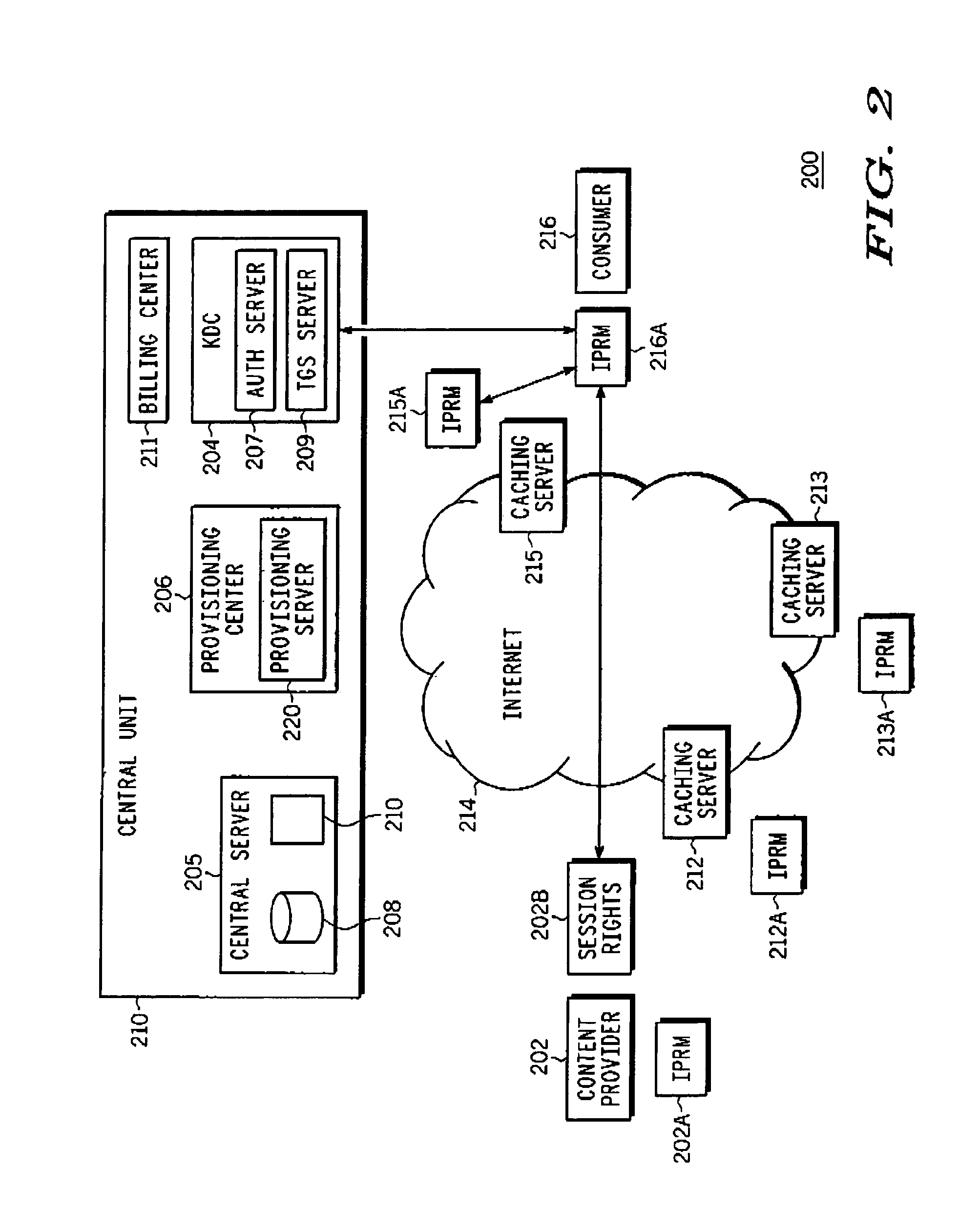
InactiveUS7237108B2Prevent replayTelevision systemsProgram/content distribution protectionCache serverRTP Control Protocol
A method for securely streaming real-time content from a caching server to an authorized client. The method includes the steps of encrypting an RTSP (real-time streaming protocol) message having a header and a payload, the RTSP message being encrypted in its entirety; and providing a first clear header for the encrypted RTSP message. Further, the method includes the steps of encrypting an RTCP (real-time control protocol) message having a header and a payload, the RTCP message being encrypted in its entirety; and providing a second clear header for the encrypted RTCP message. Thereafter, the encrypted RTSP message and the first clear header are transmitted, and the encrypted RTCP message and the second clear header are transmitted in order to securely stream the real-time content from the caching server to the authorized client.
Owner:GOOGLE TECH HLDG LLC
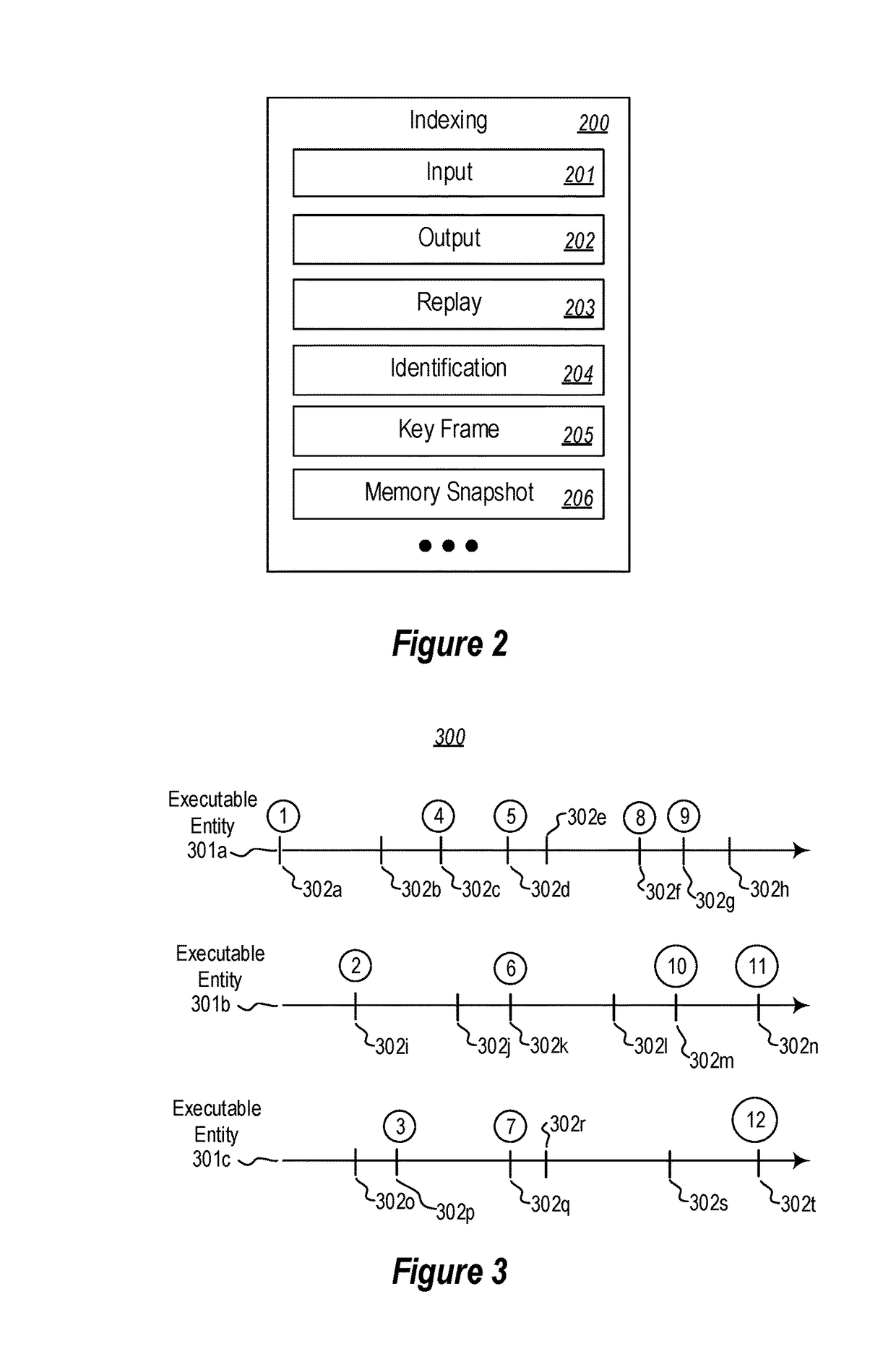
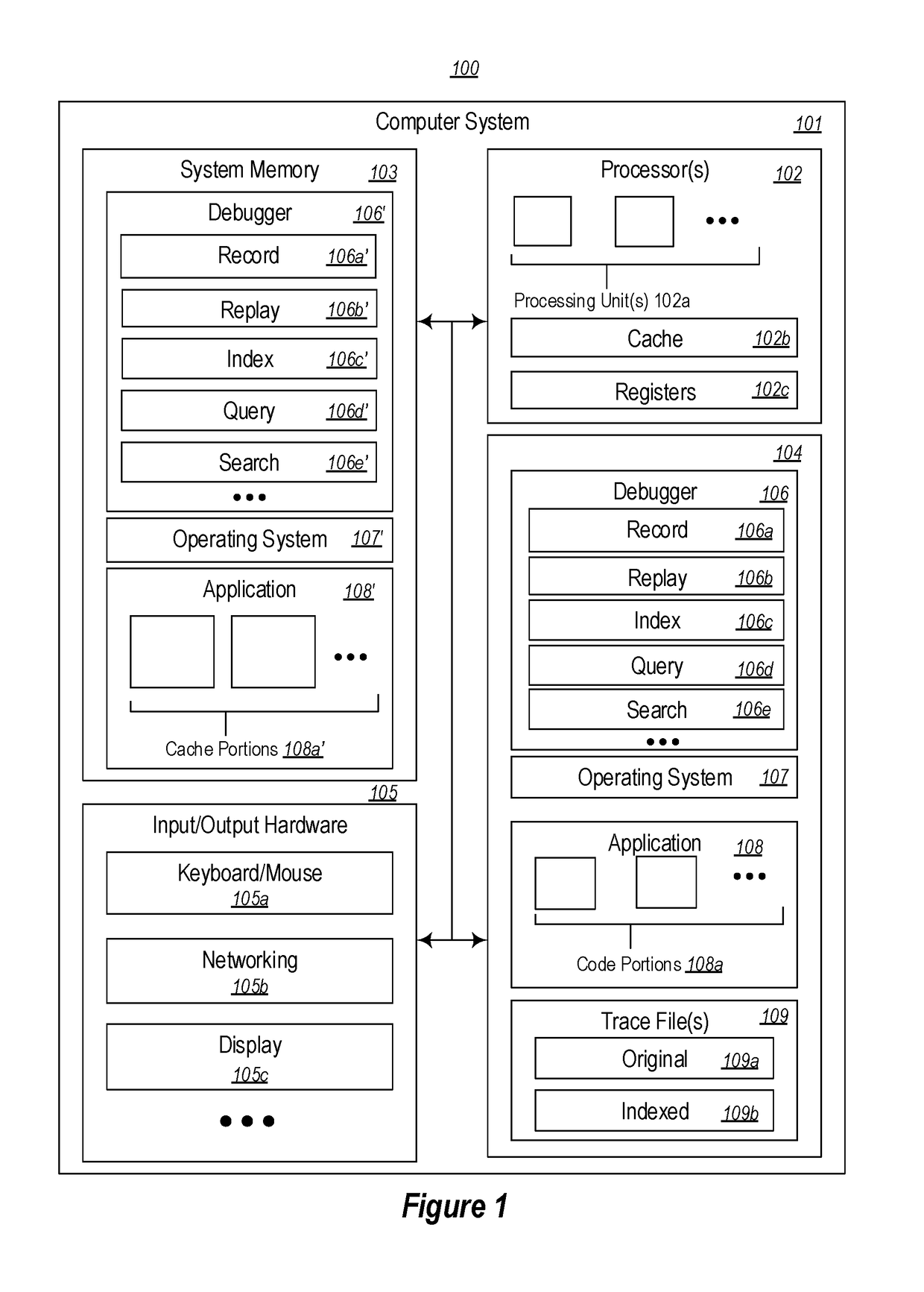
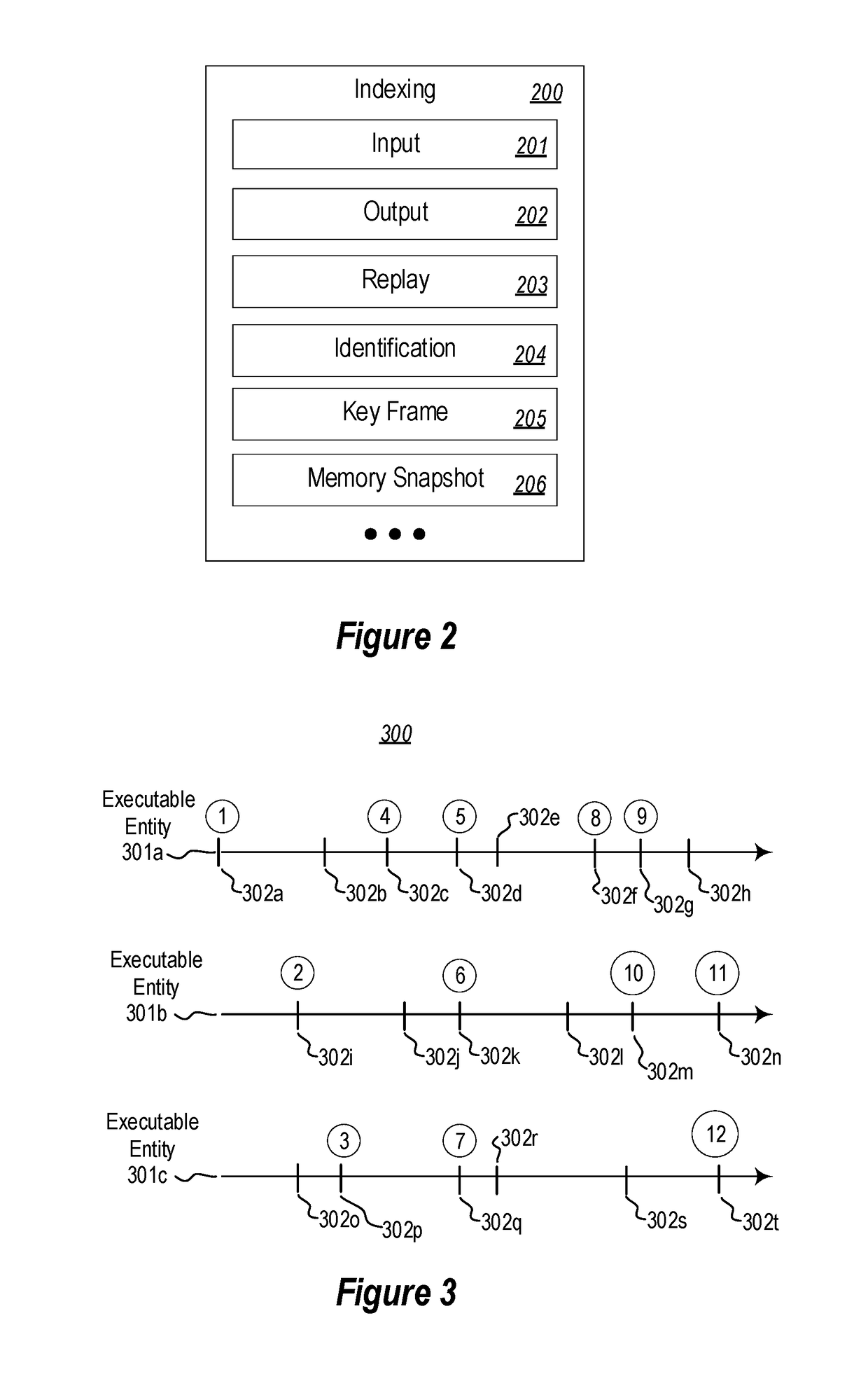
Indexing a trace by insertion of memory snapshots for replay responsiveness
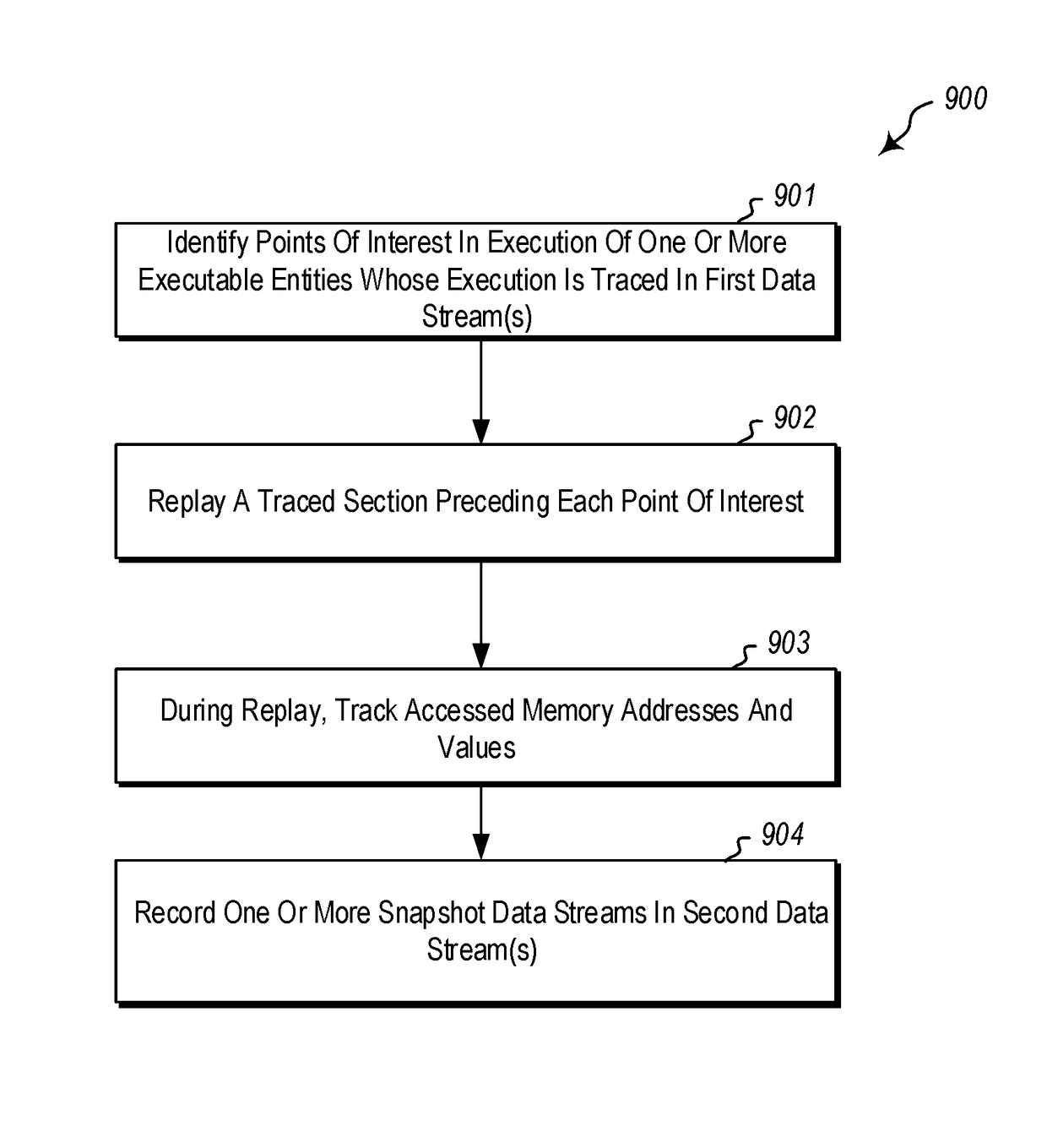
ActiveUS9959194B1Avoid the needPrevent replayInput/output to record carriersHardware monitoringMemory addressParallel computing
Inserting memory snapshots during indexing of a trace for responsive trace replay. A method includes identifying a plurality of points of interest in execution of executable entit(ies) whose execution is traced in first data stream(s). Based on the first data stream(s), a traced section of execution of the executable entit(ies) preceding each point of interest is replayed. During replay of each traced section of execution, memory addresses that are accessed by the executable entit(ies) during replay of the section, and a most recent value encountered at each memory address, is tracked. Second data stream(s) are recorded, which includes recording a plurality of memory snapshots in connection with the plurality of points of interest into the second data stream(s). Each memory snapshot summarizes memory addresses and values encountered in at least one section of execution preceding each point of interest.
Owner:MICROSOFT TECH LICENSING LLC
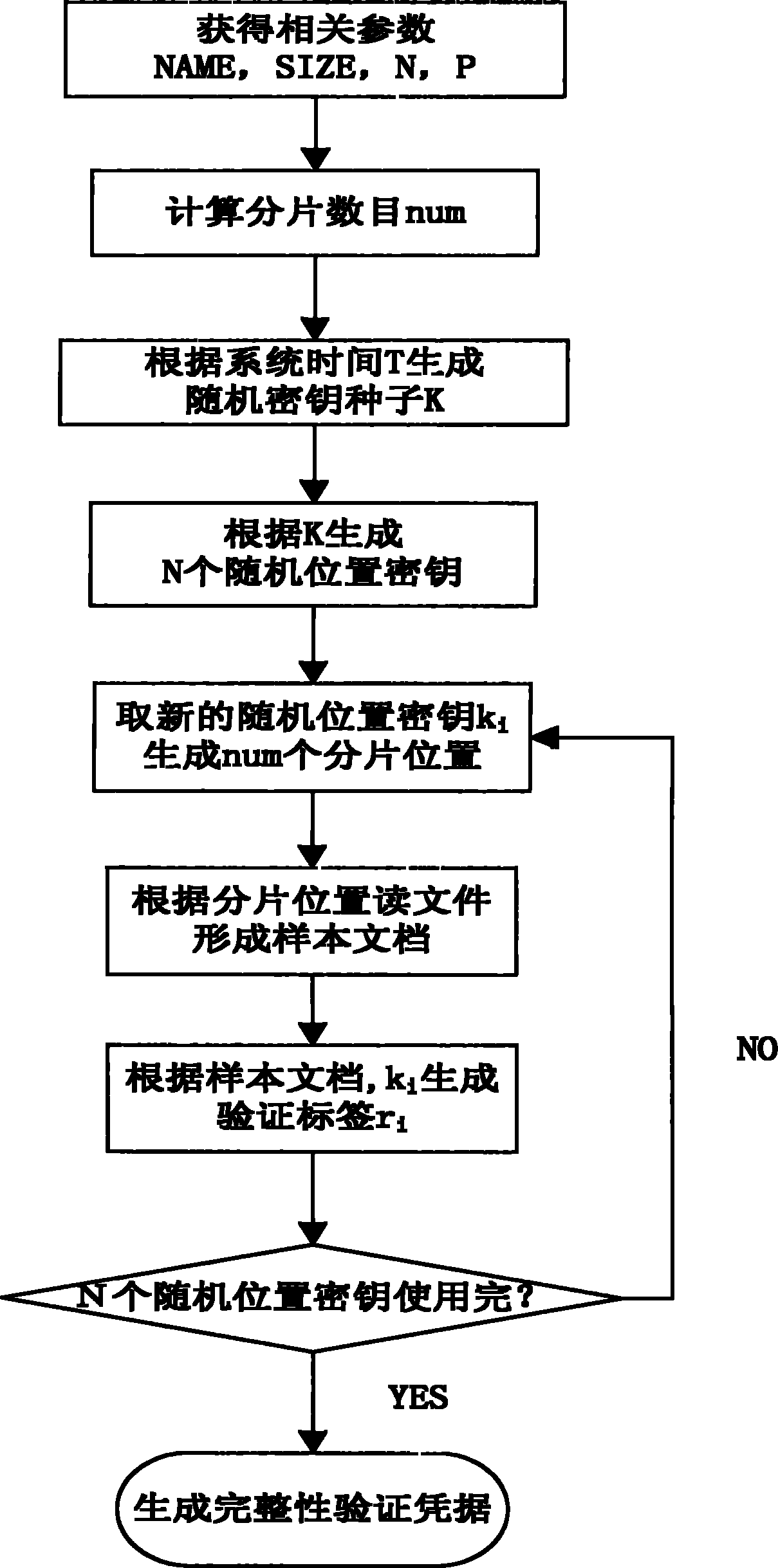
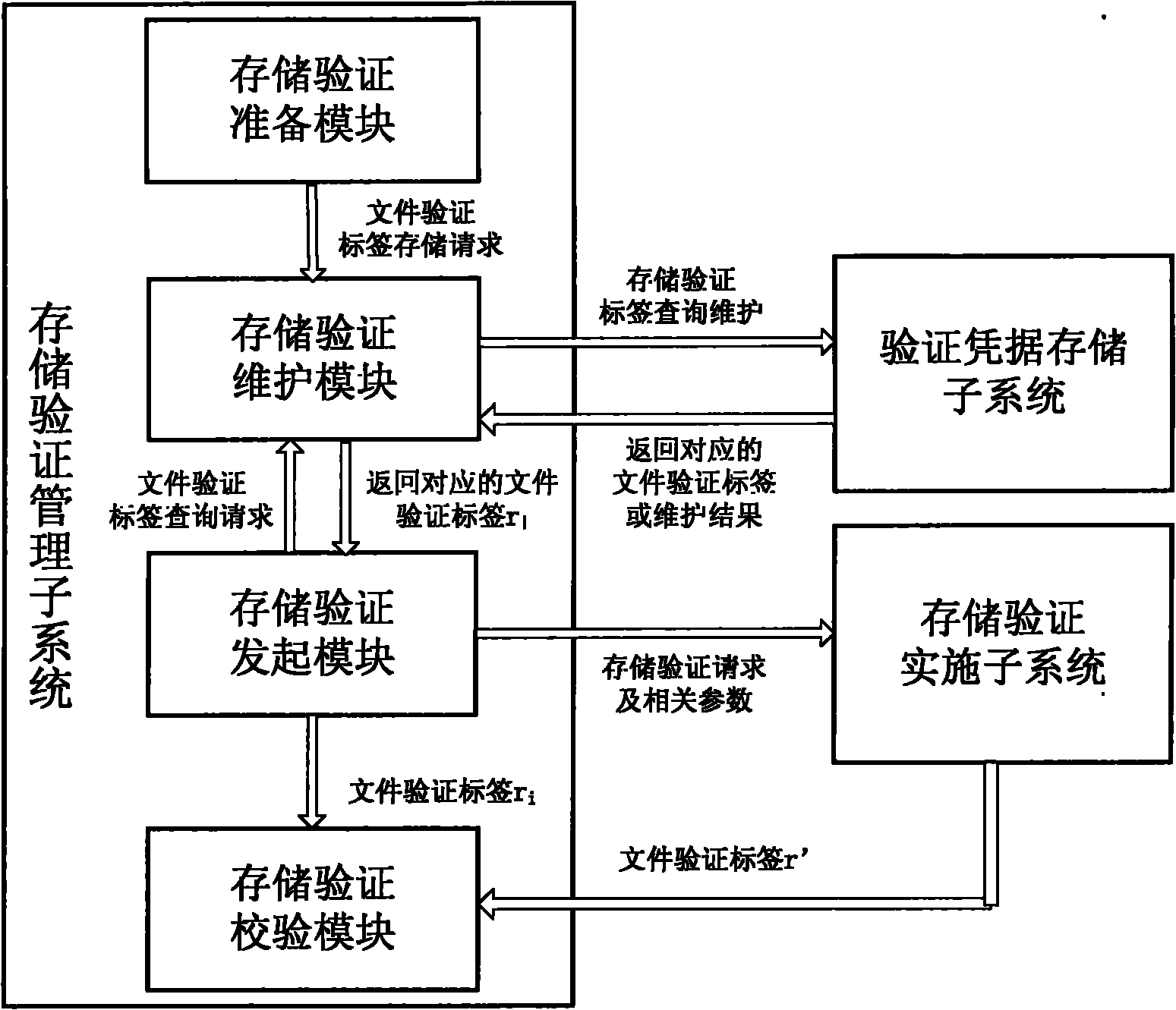
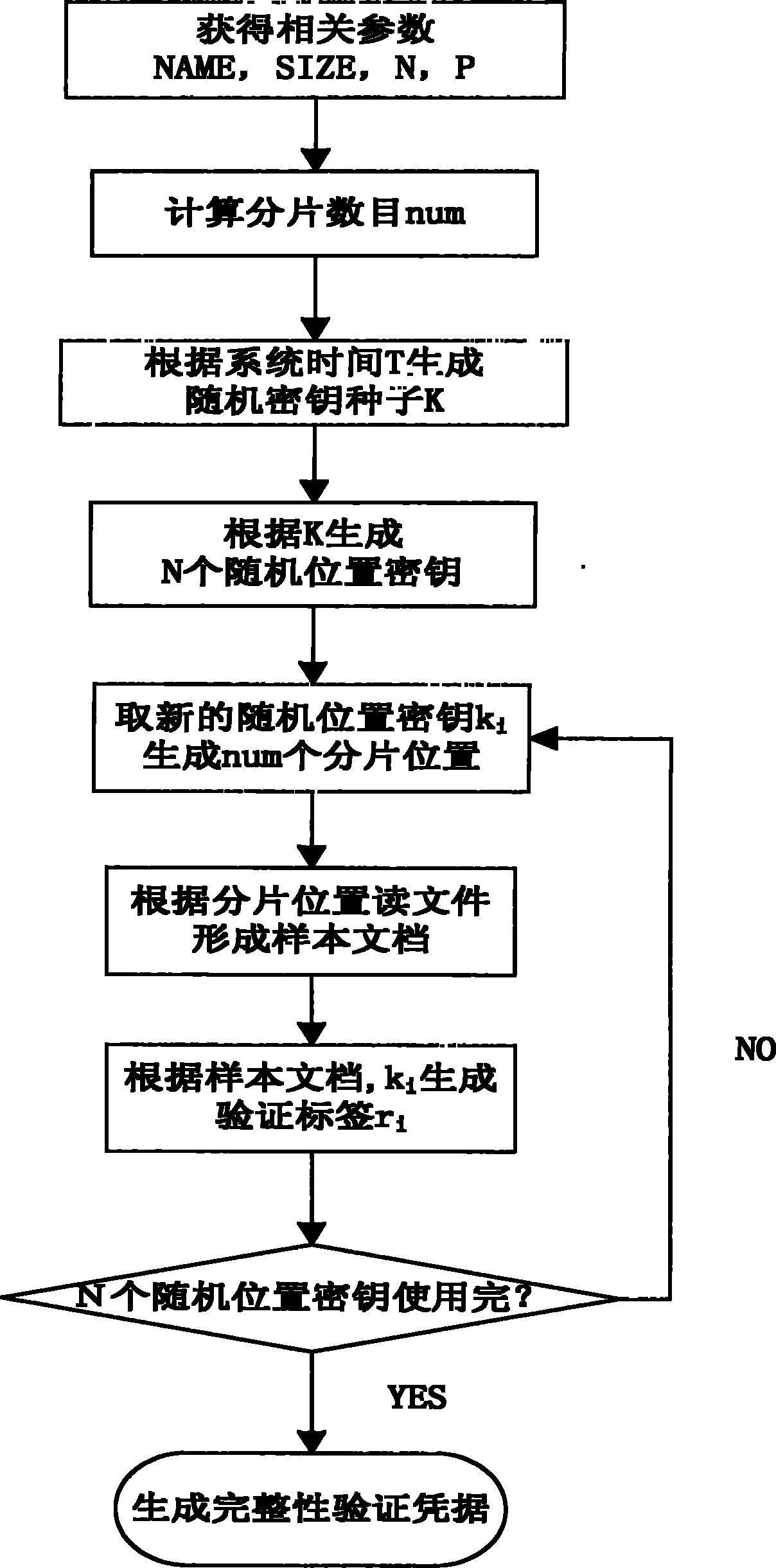
Cloud-storage-oriented trusted storage verification method and system
ActiveCN102045356AAvoid consumptionReduce consumptionTransmissionValidation methodsCloud storage system
The invention discloses a trusted storage verification method and a trusted storage verification system for cloud storage and belongs to the technical field of computer software. In the method and the system, before a file is transmitted to an untrusted cloud storage server, a series of random positions are generated according to the key held by a user and other generated related verification parameters, the contents at the random positions in the file are read, a plurality of verification labels are generated for the file, and all necessary parameters are stored and maintained; and when the storage state of the file is required to be checked, a user can initiate an interaction process with a cloud storage system according to related parameters, and the cloud storage system can generate new verification labels again according to parameters corresponding to the verification. In the method disclosed by the invention, a higher verification reliability can be acquired at a lower computingcost, the contents at different positions in the file are selected at each time of generation of the file verification labels, and different keys are adopted to prevent a server from generating a correct signature by using a stored correct signature or by storing the file contents at a specific position.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
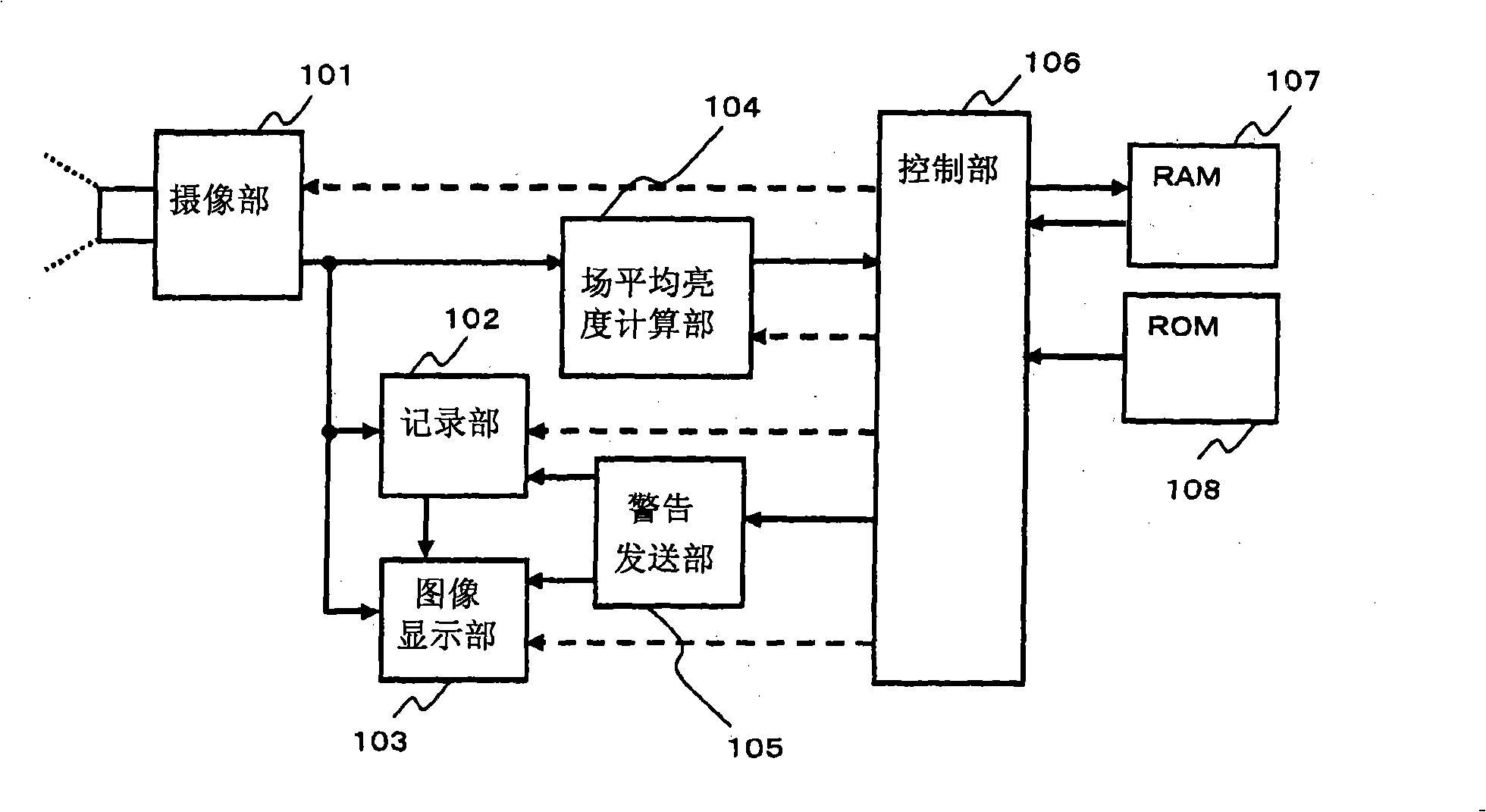
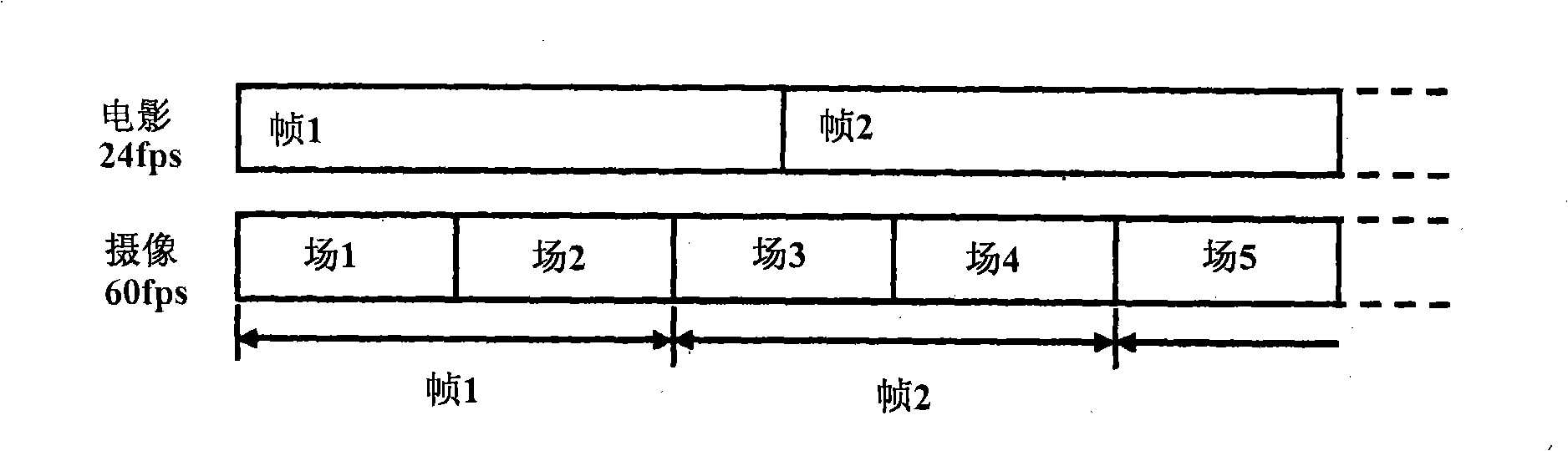
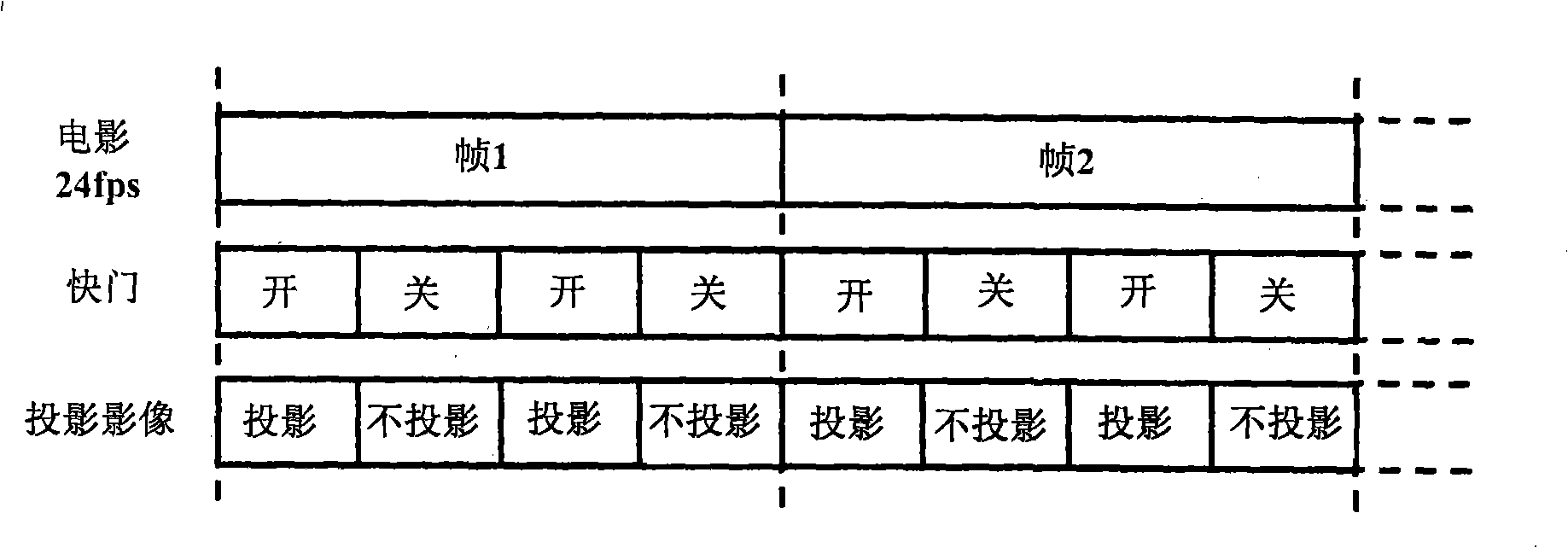
Imaging apparatus and reproducing apparatus
ActiveCN101257575ACandid behavior preventionPrevent candid behaviorTelevision system detailsColor television detailsComputer hardwareImage signal
The invention provides an imaging apparatus which can prevent the candid for detecing the imaging signal for shooting the film projected picture in the theater for presenting the film and the line, wherein after the image shot by an image part (101), the average brightness for shooting the image is figured in a field average brightness figuring part. A control part (106) measures the field average brightness of five continuous shooting fields, the candid of the film is detected through judging the ratio of the max brightness and the minimum brightness. When detecting the candid of the film, the warning information is displayed in the image display part (103) by the transmitting part (105), and the recording data of the recording medium is deleted by the recoding part (102), or the warning information and the image are recorded to the recording medium.
Owner:VICTOR CO OF JAPAN LTD
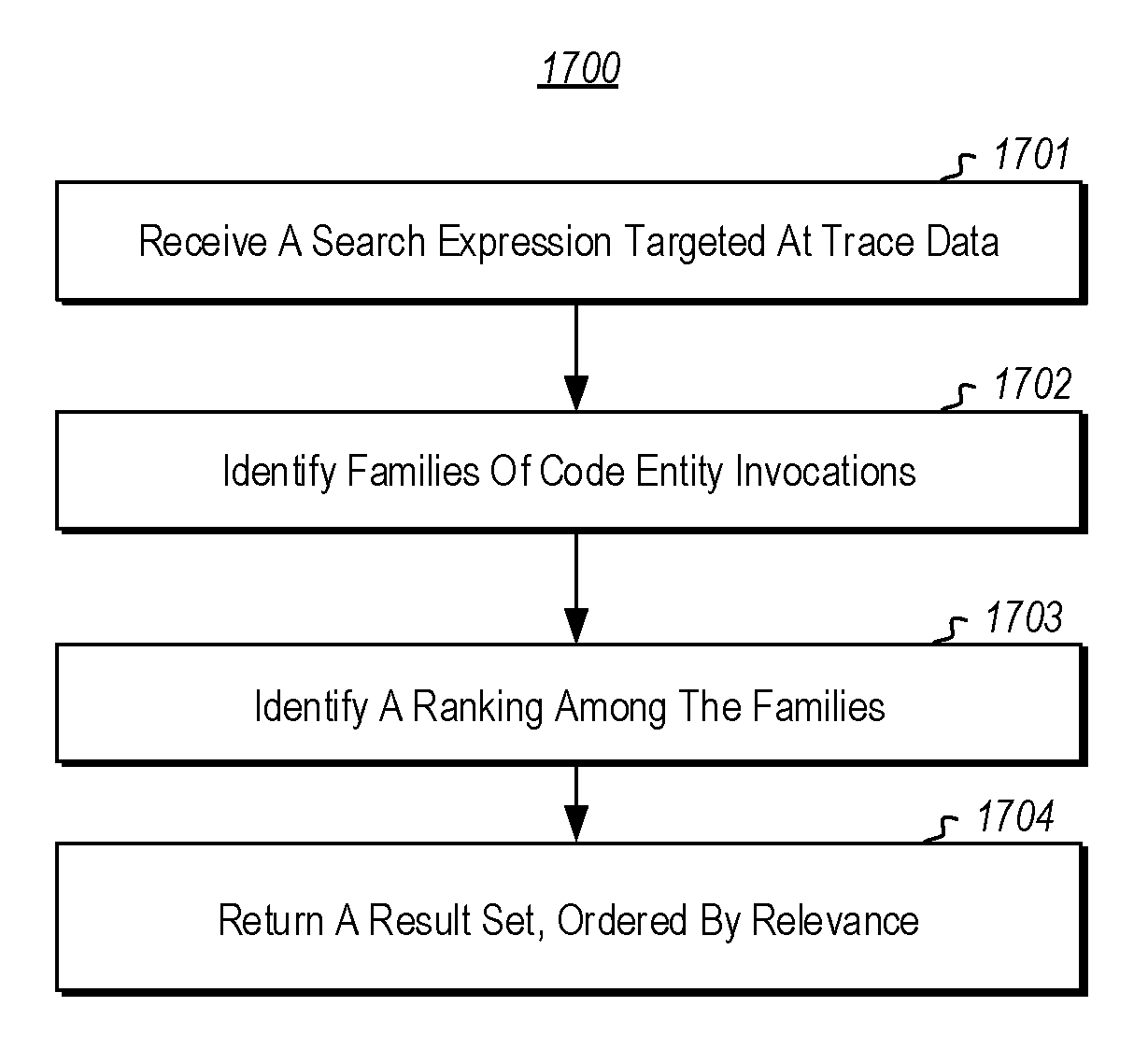
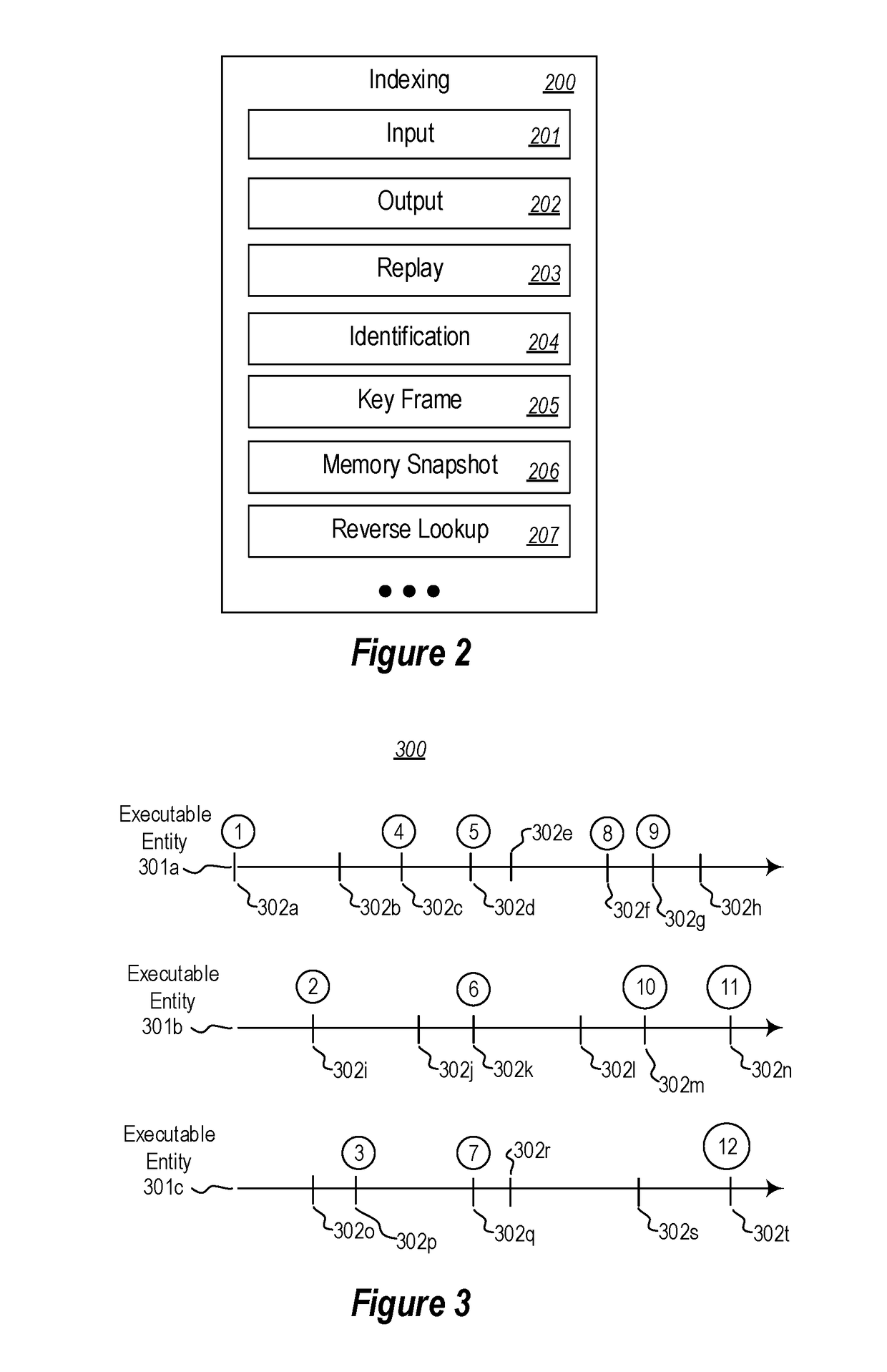
Searching an indexed time-travel trace
ActiveUS9940369B1Avoid the needPrevent replayDigital data information retrievalDigital data processing detailsData streamRanking
Performing a search over a trace of program execution. A method includes receiving a search expression including one or more search criteria. The search expression is targeted at one or more trace data streams storing a trace of program execution. Based on the one or more search criteria, a plurality of families of code entity invocations are identified. Each family identifies a plurality of code entity invocations that are related to each other, and that are identified based in on one or more trace data streams. A ranking among the plurality of families of code entity invocations is identified, and based at least on the ranking a set of code entity invocations determined to meet the one or more search criteria is returned. The set of code entity invocations is ordered by a relevance determined based at least on the ranking among the plurality of families.
Owner:MICROSOFT TECH LICENSING LLC
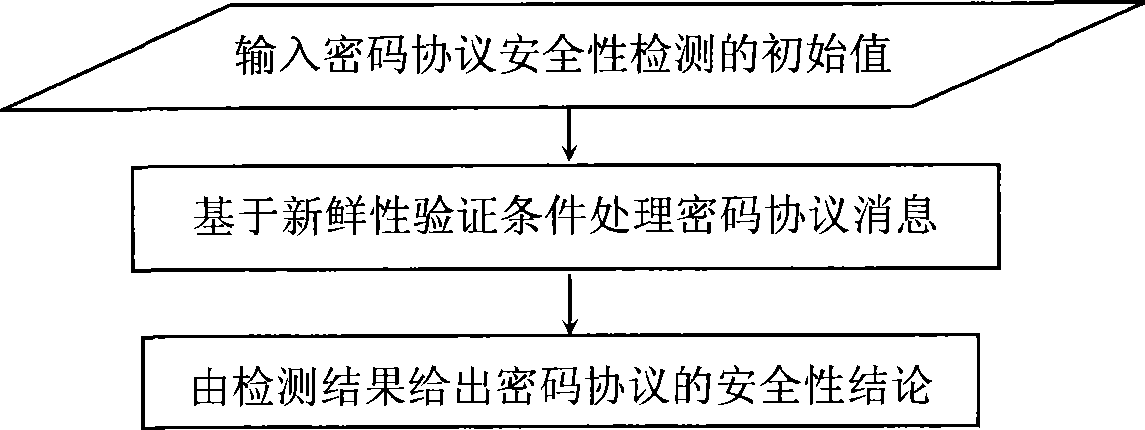
Password protocol safety detection method based on novelty verification condition
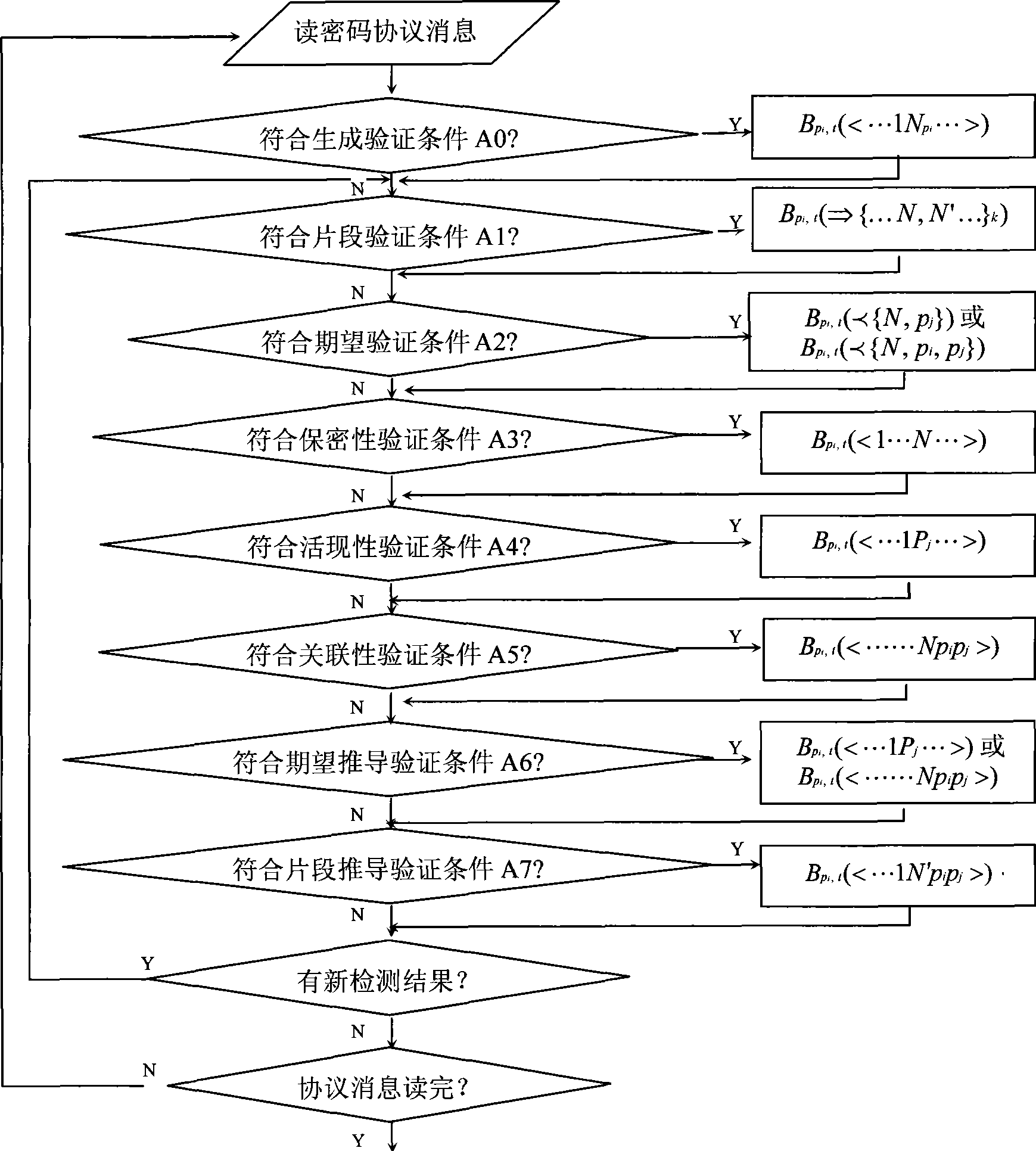
InactiveCN101459509APrevent replay and obfuscation attacksEffectively distinguish whether it is fresh or notKey distribution for secure communicationPublic key for secure communicationCODE protocolPassword
The invention relates to a code protocol security detecting method based on freshness verification conditions in the field of information security, which comprises the steps that: inputting the initial value of a code protocol security detecting result, generating a new fact after a communication agent sends or receives each message, obtaining a new security detecting result through operating the freshness verification condition of a confidence multi-collection method based on the new fact and the built security detecting result until to process the protocol information, obtaining the security conclusion of the code protocol through the code protocol security detecting result, or displaying that the code protocol is safe, or leading out an attack structure for the code protocol with security hidden dangers. The detecting method not only can effectively differentiate whether the message is fresh, but also substantially prevents the attacks of replaying and confusing, and is not related to the specific descriptions of a multi-protocol operation environment and the ability of an attacker. In addition, the invention not only is a method of proving the code protocol correctness, but also is a method of searching protocol errors.
Owner:SHANGHAI JIAO TONG UNIV
Unauthorized deice detection device, unauthorized device detection system, unauthorized device detection method, program, recording medium, and device information update method
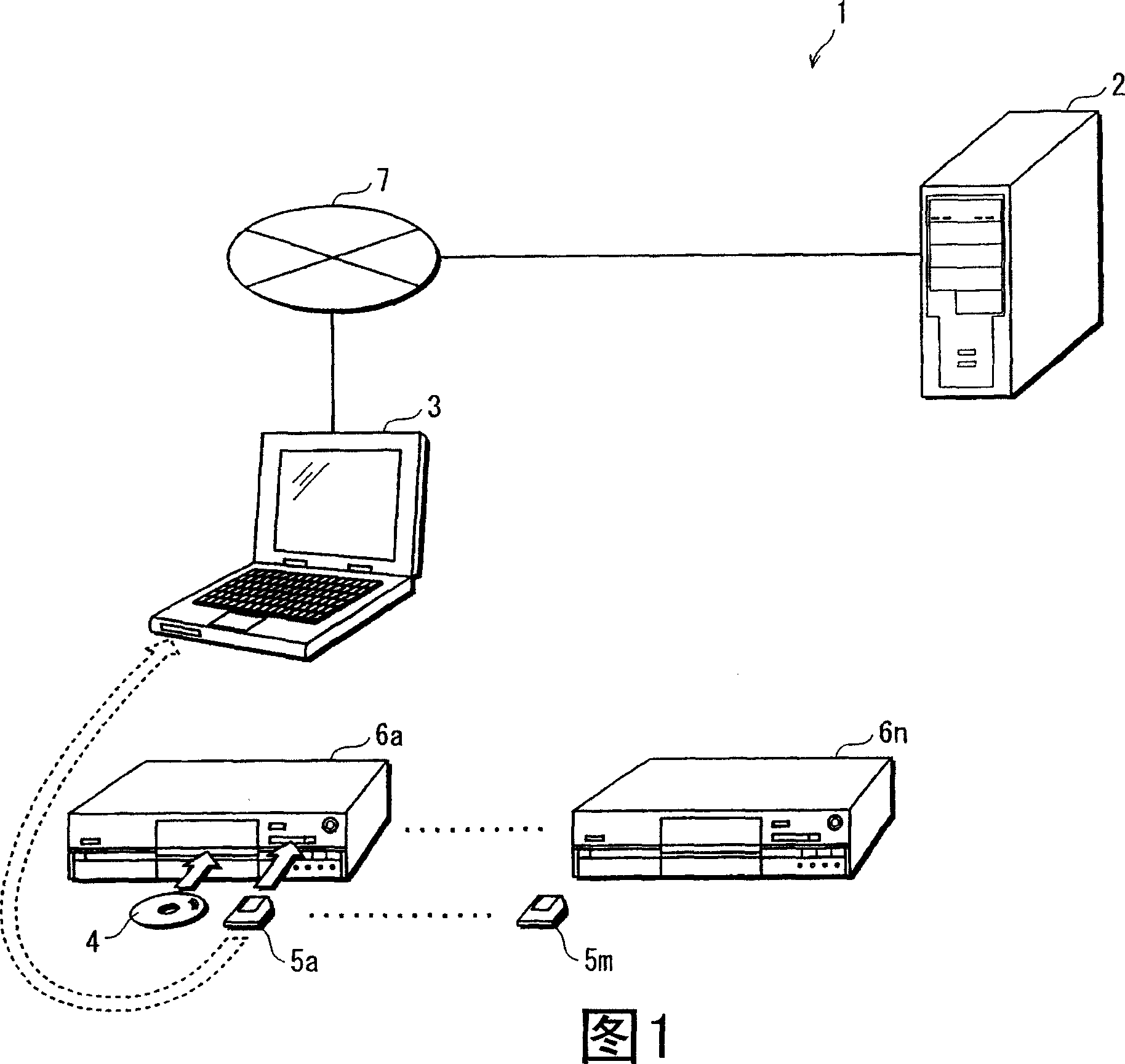
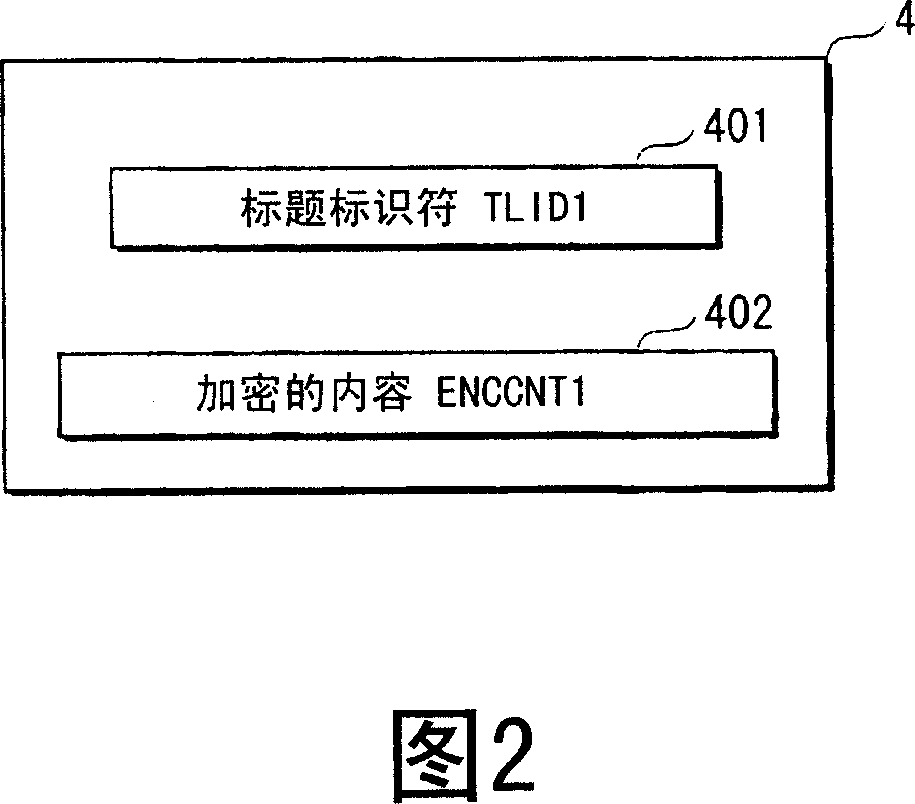
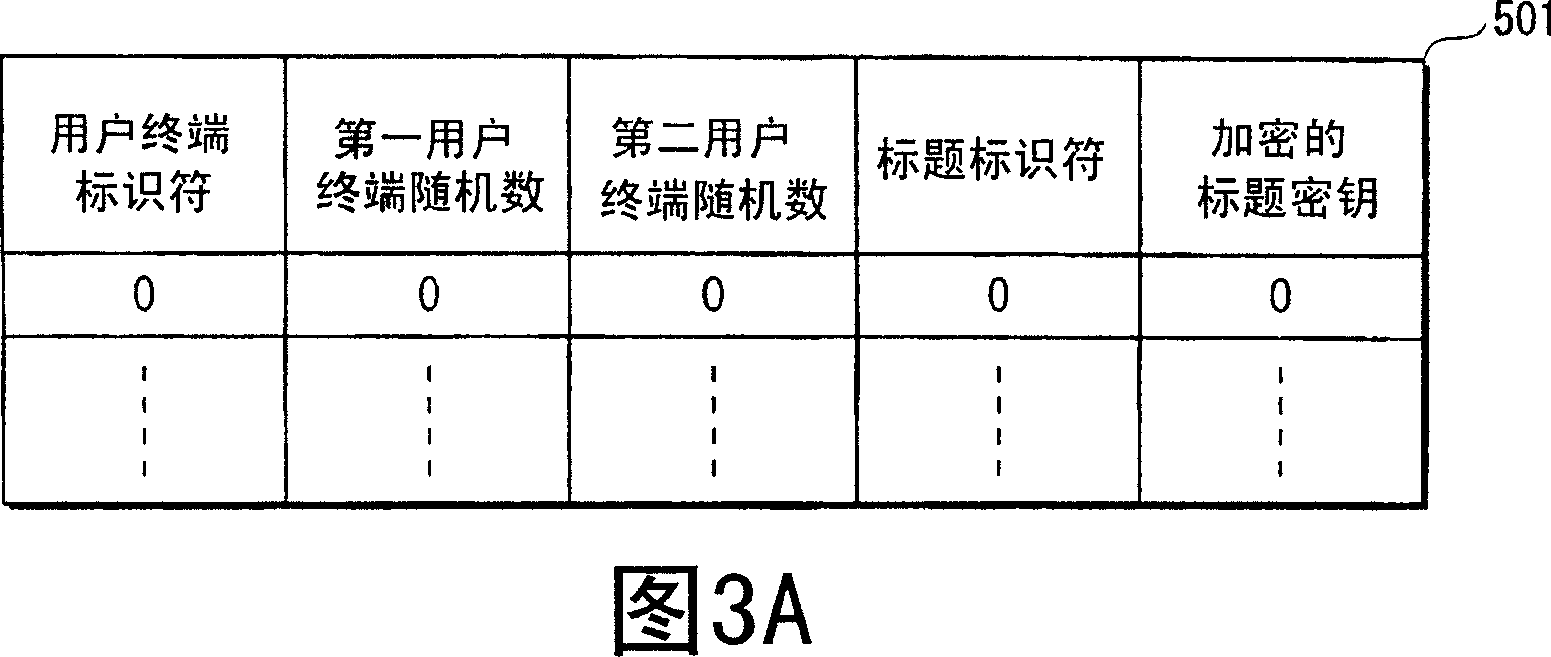
ActiveCN1957356APrevent replayAvoid misjudgmentKey distribution for secure communicationAnalogue secracy/subscription systemsIntegrated circuitRecording media
There are provided an unauthorized device detection device, a content reproduction device, an unauthorized device detection system, an information collection device, an unauthorized device detection method, a program, a recording medium, a device information update method, and an integrated circuit capable of detecting a clone device associated with a content reproduction device. In a management server (2), a reception processing unit (241) acquires a user terminal identifier and a first user terminal random number from a user terminal as an unauthorized device detection object and judges whether a second management server random number corresponding to the user terminal held in a recording unit (23) coincides with the first user terminal random number. If they do not coincide, a display unit (22) displays a message indicating that a clone terminal exists. If they coincide, a terminal information generation unit (243) generates a new random number and overwrites the generated random number on the second management server random number in the recording unit (23). Moreover, a transmission processing unit (246) transmits the generated random number via a transmission / reception unit (21) to the user terminal so that the user terminal updates the first user terminal random number to the generated random number.
Owner:PANASONIC CORP +1
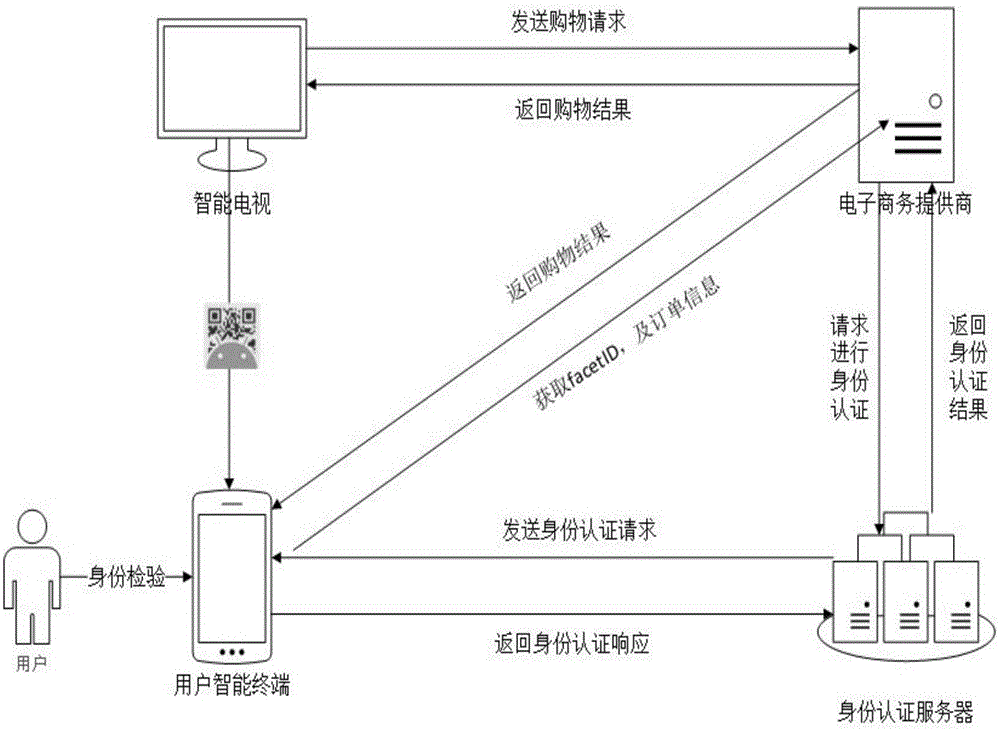
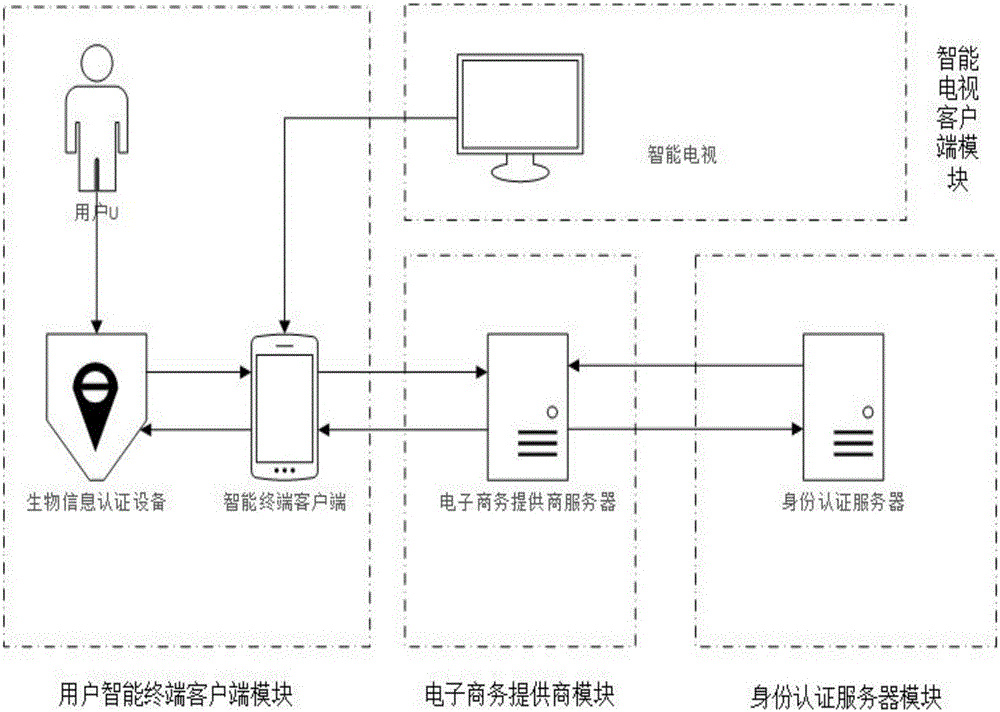
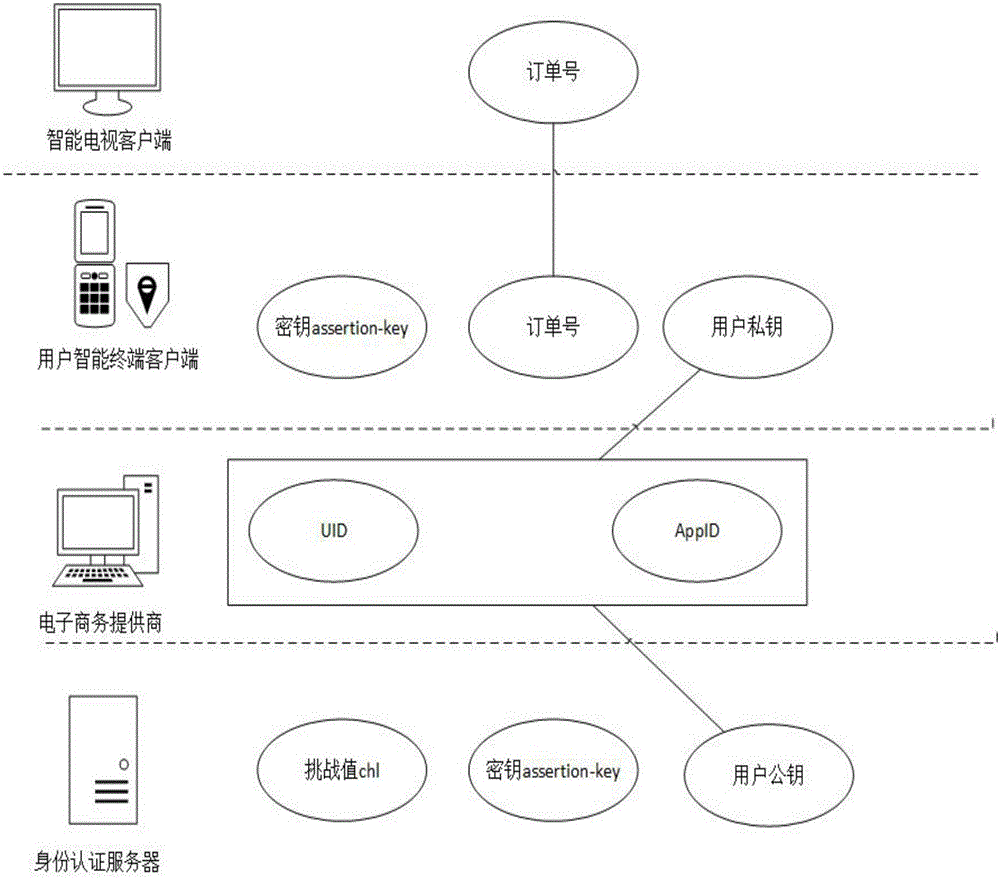
Safety payment system and method based on smart TV multi-screen interaction
InactiveCN105049945AImprove securityGuaranteed experienceTransmissionSelective content distributionPasswordAuthentication server
The invention discloses a safety payment system and method based on smart TV multi-screen interaction. A business delegate method is introduced to relegate an identity authentication requirement at a smart TV terminal to a user smart terminal, which is higher in security and supports a plurality of physiological information authentications, to process through a multi-screen interaction concept, and a processing result is finally returned to the smart TV terminal. Through the adoption of the user smart terminal, a built-in or external physiological information authentication device and an identity authentication server are combined through an asymmetrical secret key mode to perform the negotiation authentication, thereby realizing the safety payment system at the smart TV terminal. Through the adoption of the method disclosed by the invention, a user can finish the identity authentication and the affair confirmation of the smart TV terminal by means of the convenient and safe physiological information authentication device at the smart terminal, and the traditional user name password identity authentication mode is substituted. The information security in the authentication process is greatly improved while the user experience is guaranteed.
Owner:INST OF INFORMATION ENG CAS
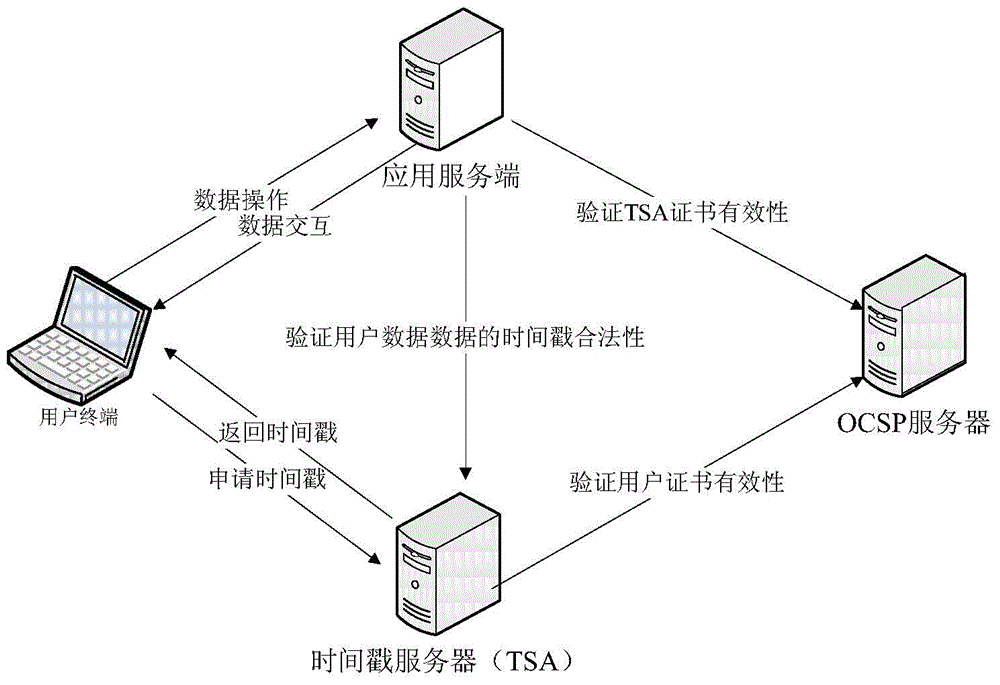
Identity authentication method and system for mobile terminal based on WPKI and timestamp
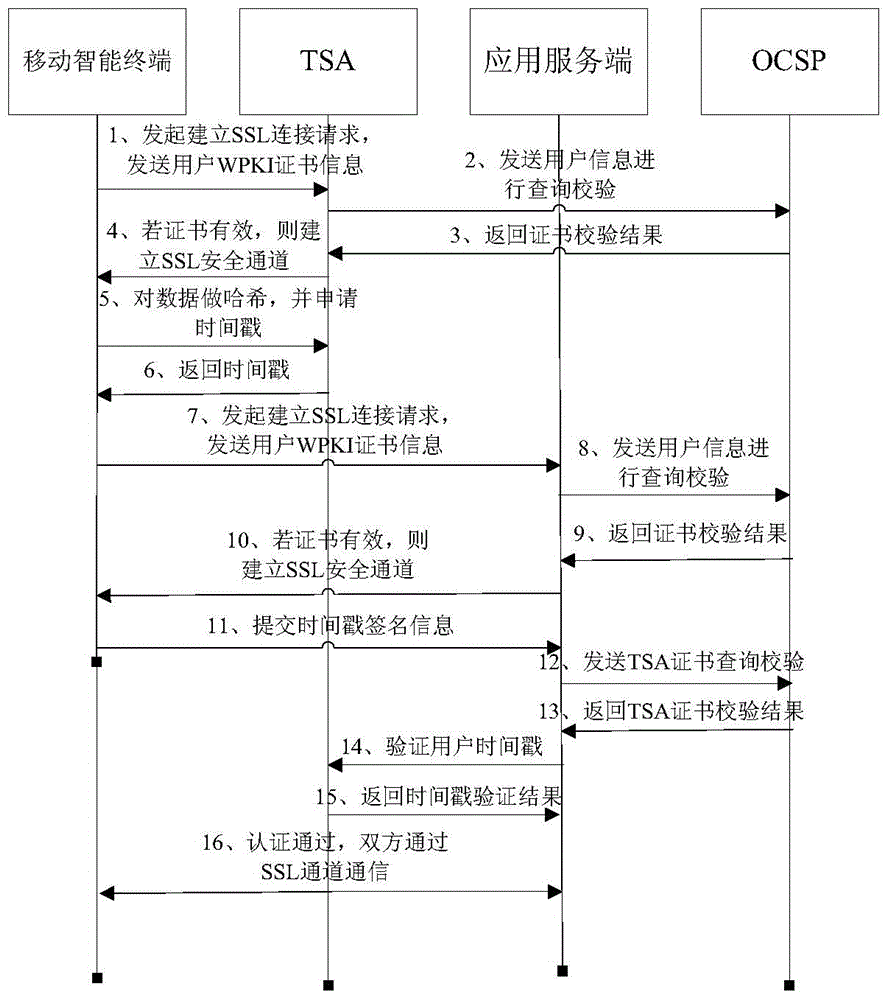
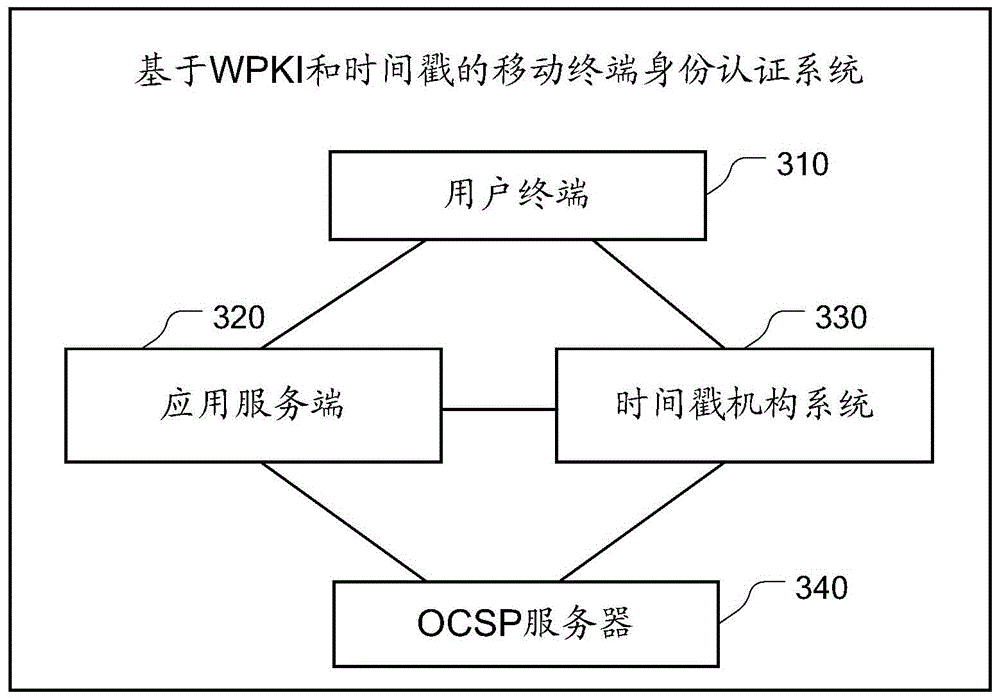
ActiveCN104579662AValid authenticationEnsure safetyUser identity/authority verificationTimestampApplication server
The embodiment of the invention provides an identity authentication method and an identity authentication system for a mobile terminal based on a WPKI and a timestamp. The method mainly comprises the steps that a user terminal acquires the timestamp from a timestamp mechanism system and establishes a safety data channel with an application server by adopting the WPKI; the application server receives the timestamp sent by the user terminal through the safety data channel and authenticates the timestamp through the timestamp mechanism system; after authentication of the timestamp is passed, data are transmitted between the application server and the user terminal by utilizing the safety data channel. According to the embodiment of the invention, a mobile intelligent terminal communicates with the application server by adopting a WPKI technology, and the safety of the whole link is guaranteed by adopting an SSL communication protocol based on an ECC algorithm; by using the timestamp service of a trusted third party, various attacks to a group key exchange protocol can be resisted, so that the effective identity authentication of the mobile terminal is achieved, and the data safety of wireless services of the mobile terminal is guaranteed.
Owner:AEROSPACE INFORMATION
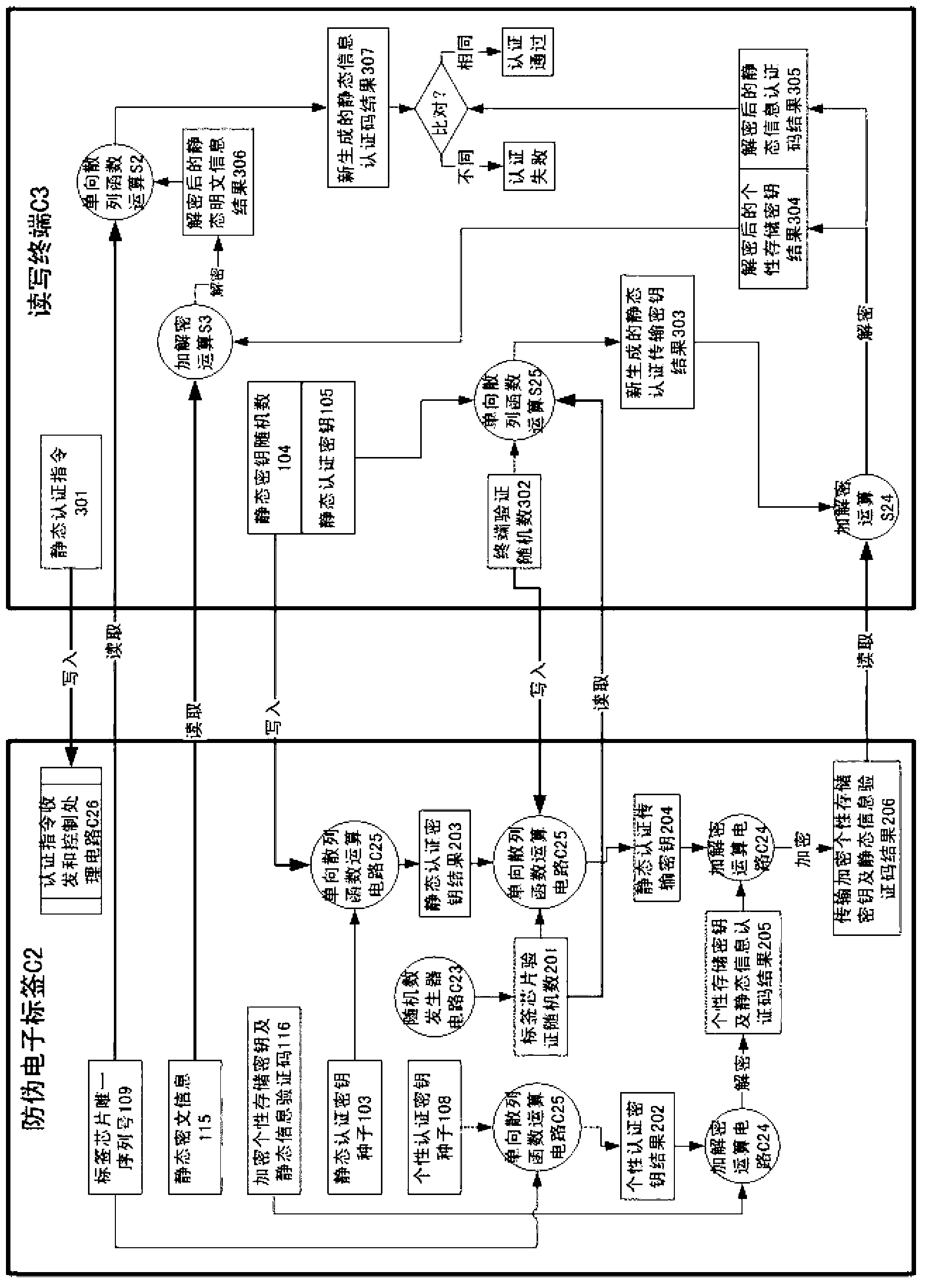
Electronic tag anti-fake authentication method
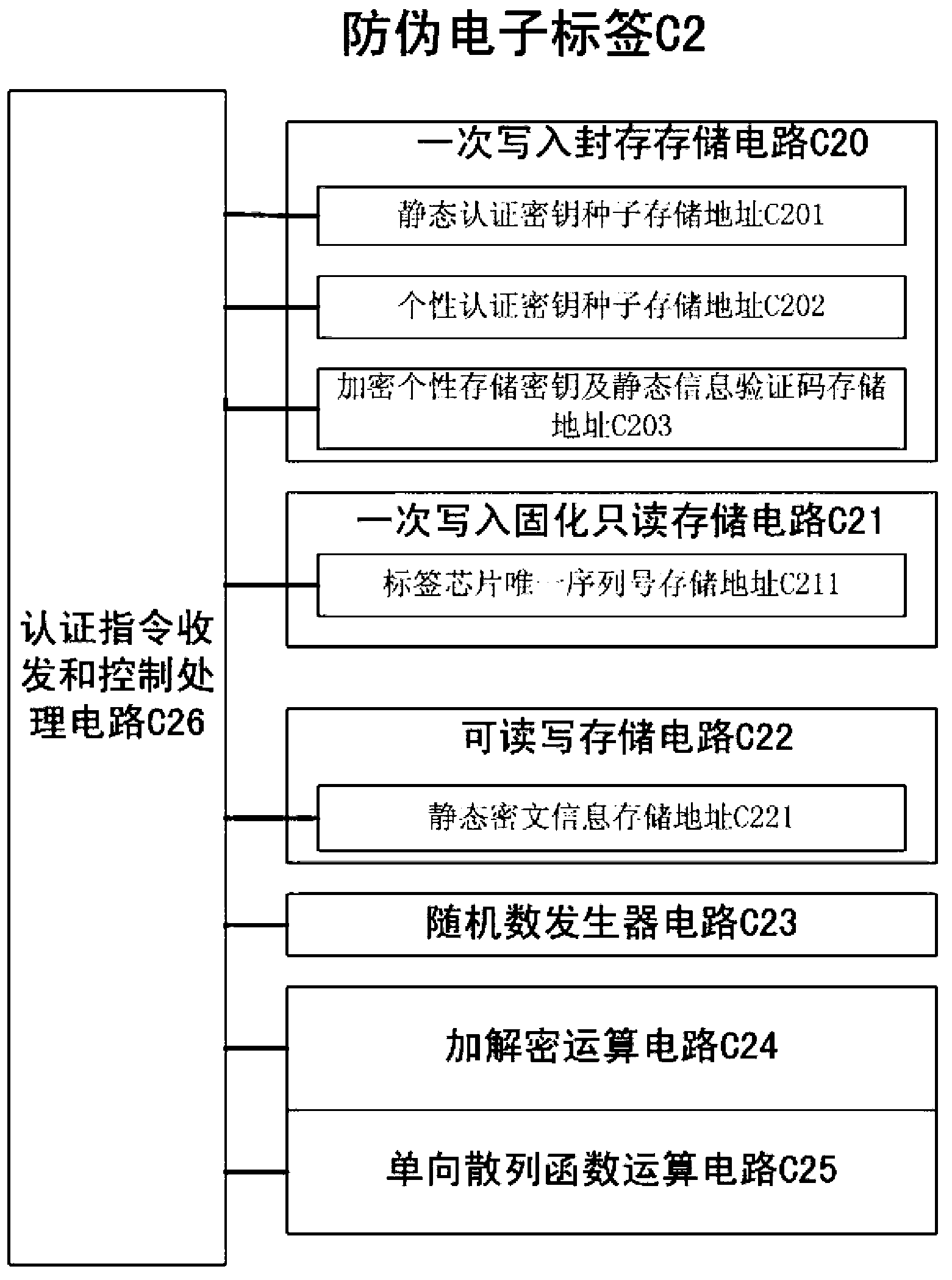
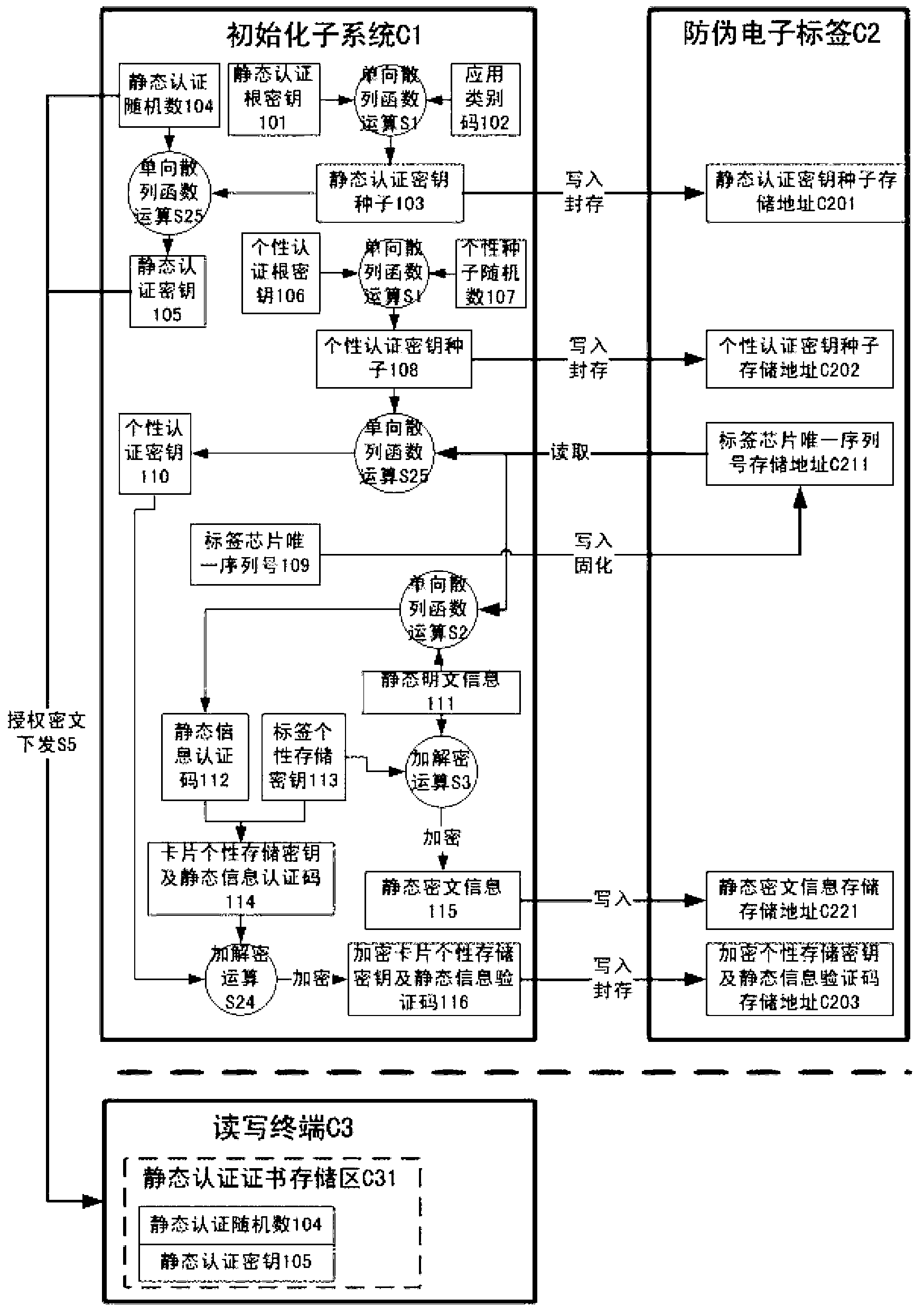
ActiveCN103326864AEasy to be illegally copiedPrevent replayUser identity/authority verificationSensing by electromagnetic radiationAuthentication systemEavesdropping
The invention discloses an electronic tag anti-fake authentication method. A logic system in an electronic tag chip comprises an authentication order receiving, sending and control processing circuit, a one-time write-in sealing storage circuit, a one-time write-in read-only storage circuit, a read-write storage circuit, a random number generator circuit, an encryption and decryption operational circuit and a one-way hash function operational circuit. An anti-fake authentication system comprises an initializing sub system and an authentication sub system. The anti-fake electronic tag can pass the authentication of the authentication sub system only after the successful initialization of the initializing sub system. According to the electronic tag anti-fake authentication method, the problems that a low-cost logically encrypted electronic tag is prone to illegal copying, internal storage information is prone to illegal falsification and steal, and space transmission data are prone to illegal eavesdropping and resetting are solved.
Owner:詹万泉
Querying an indexed time-travel trace
ActiveUS9983978B1Avoid needPrevent replayMultimedia data queryingHardware monitoringResult setTheoretical computer science
Performing a query over a trace of program execution. A method includes receiving a query expression targeted at least a portion of a trace of program execution. A data structure that represents the query expression is built. The data structure has a plurality of data elements representing concepts and operations of the query. Based on the data structure, an order for evaluating the data elements is identified. The plurality of data elements is evaluated. Based on the evaluation, at least a portion of a result set is conveyed for consumption.
Owner:MICROSOFT TECH LICENSING LLC
Authorization system based on oauth2 protocol enhancement and method thereof
PendingCN113079175AImprove experienceImprove efficiencyUser identity/authority verificationDigital data authenticationEngineeringProtocol for Carrying Authentication for Network Access
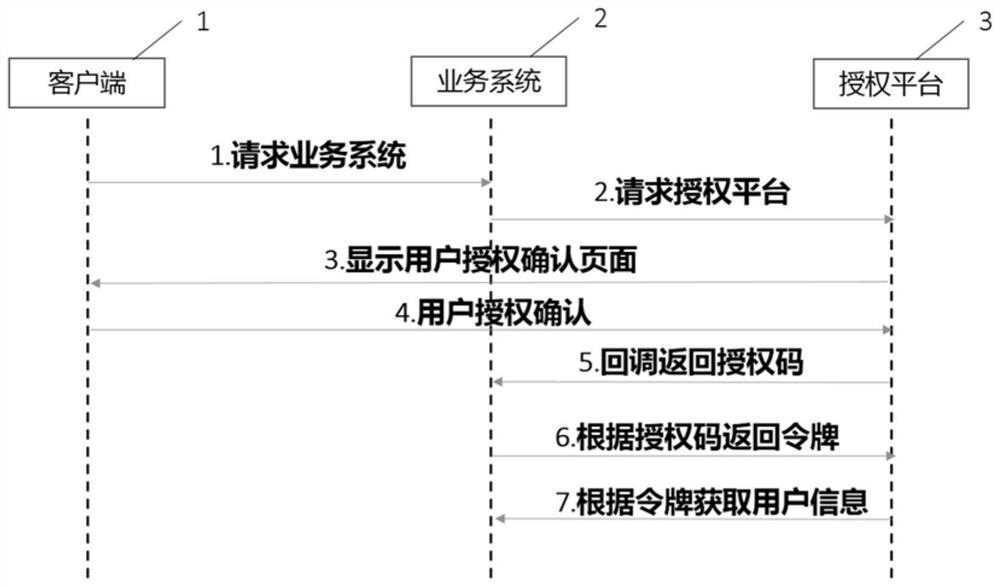
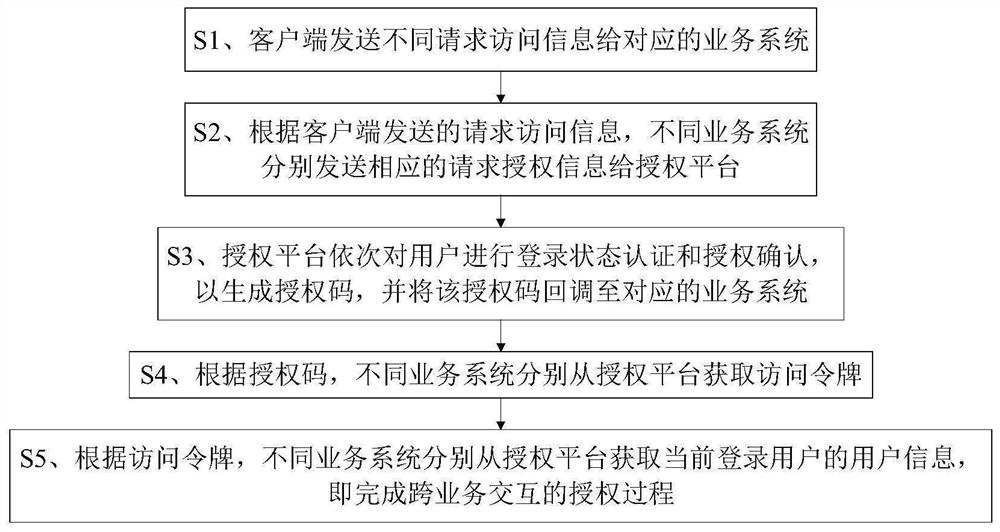
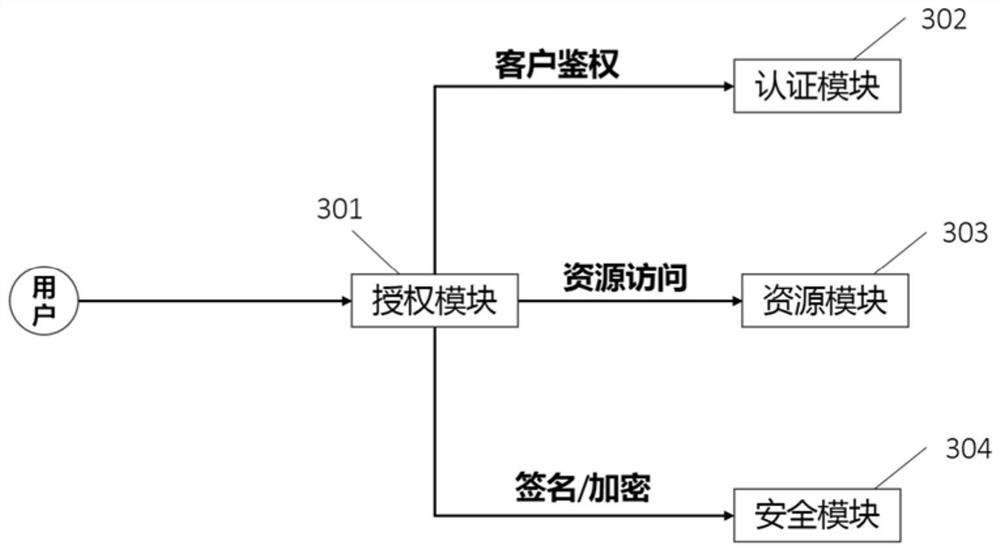
The invention relates to an authorization system and method based on oauth2 protocol enhancement, the system comprises a client and an authorization platform, the client is unidirectionally connected to a plurality of different service systems so as to send access request information to the corresponding service systems from the client, and the client and the plurality of service systems are respectively bidirectionally connected with the authorization platform. The authorization platform is used for pushing an authorization confirmation page to the client and returning an authorization code to the corresponding service system, the client is used for executing user login operation and sending authorization confirmation information to the authorization platform, and the service system is used for sending authorization request information to the authorization platform, and acquiring the token from the authorization platform according to the authorization code, and acquiring the user information from the authorization platform according to the token. Compared with the prior art, the user operation in the cross-service interaction process can be simplified, and the user does not need to repeatedly carry out login operation; and meanwhile, data security is ensured, user information does not need to be transmitted between service systems, and interception by rogue program information is avoided.
Owner:SHANGHAI PUDONG DEVELOPMENT BANK
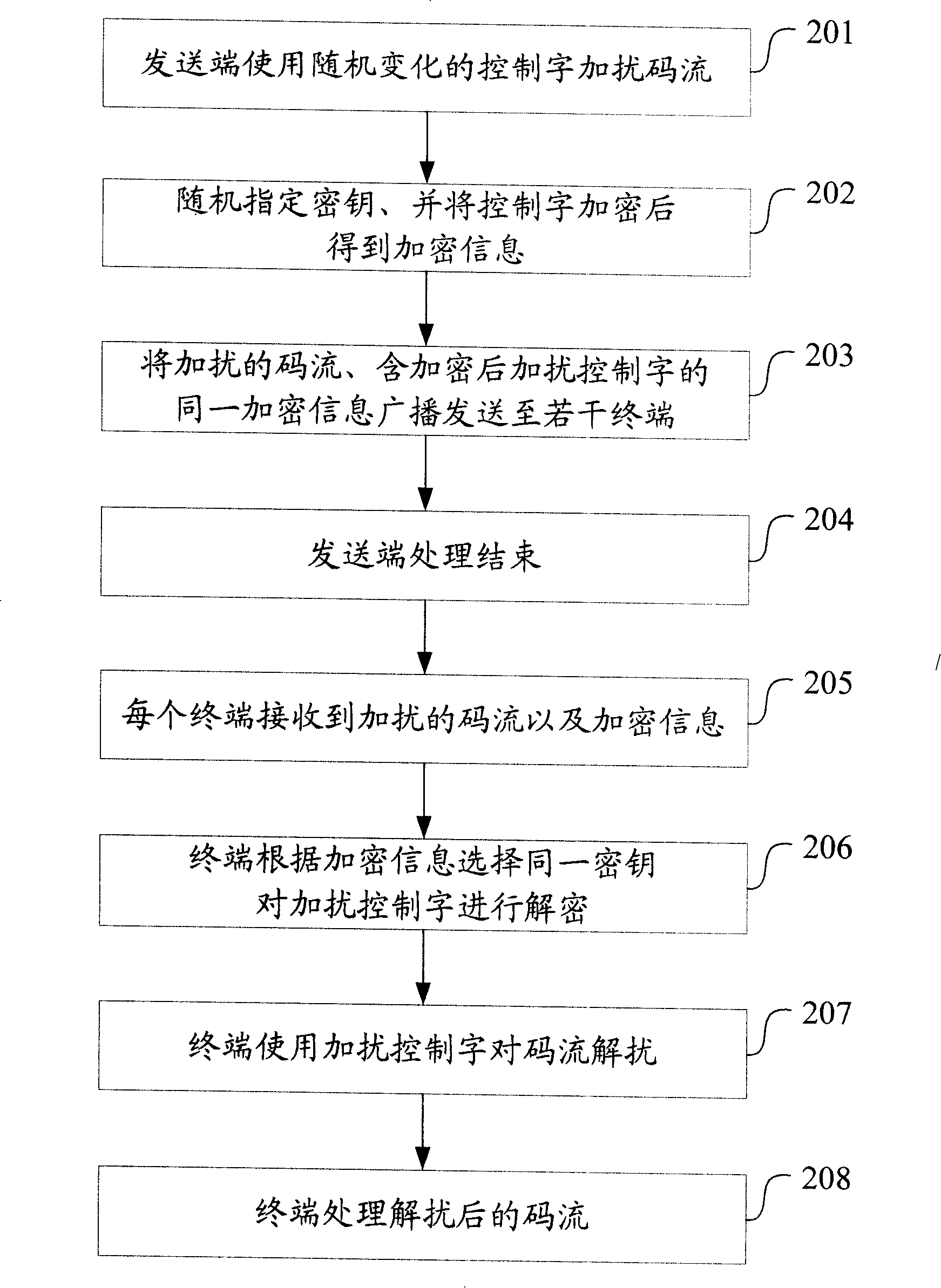
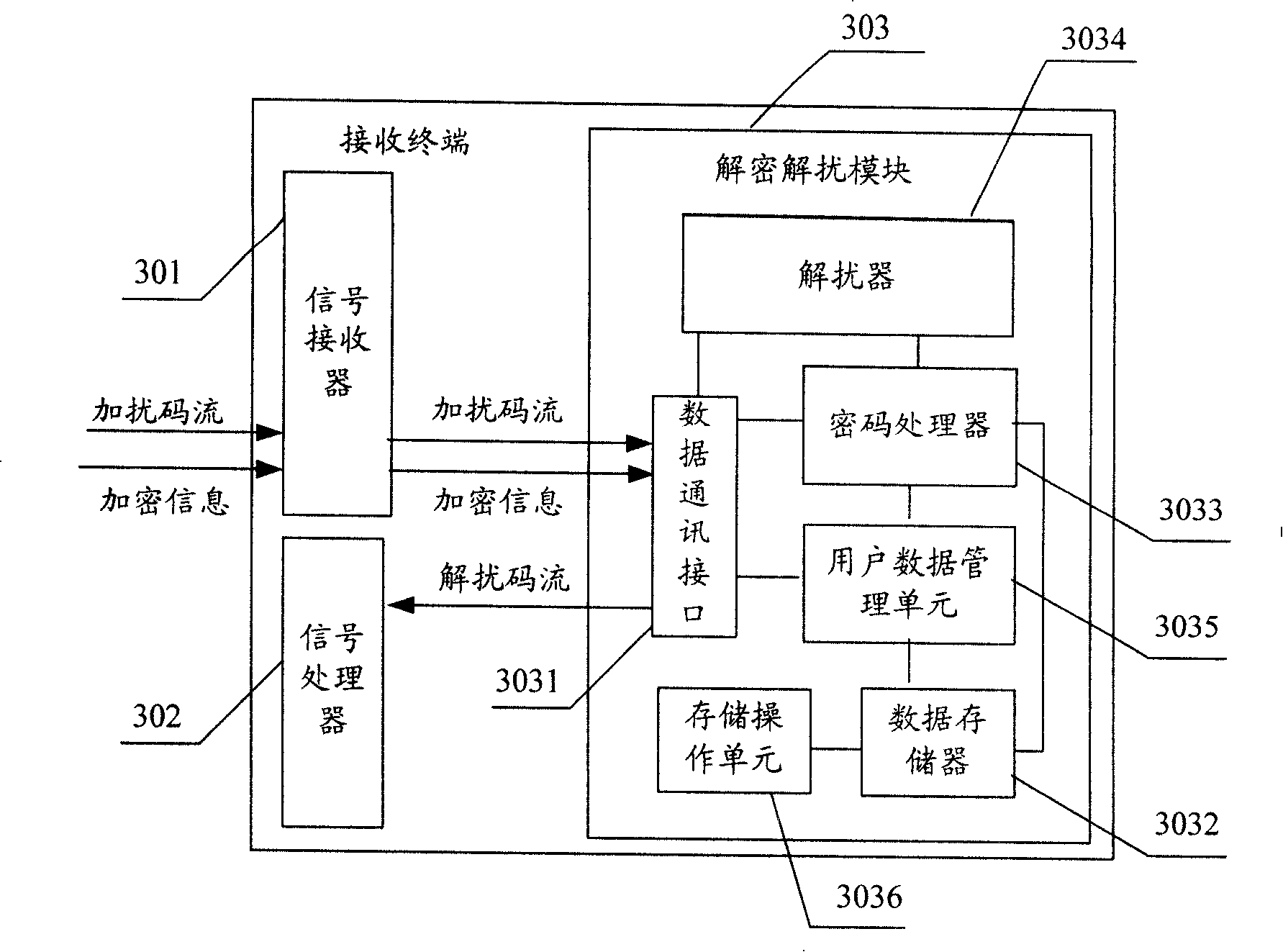
Broadcast signal processing method, system, and receiver
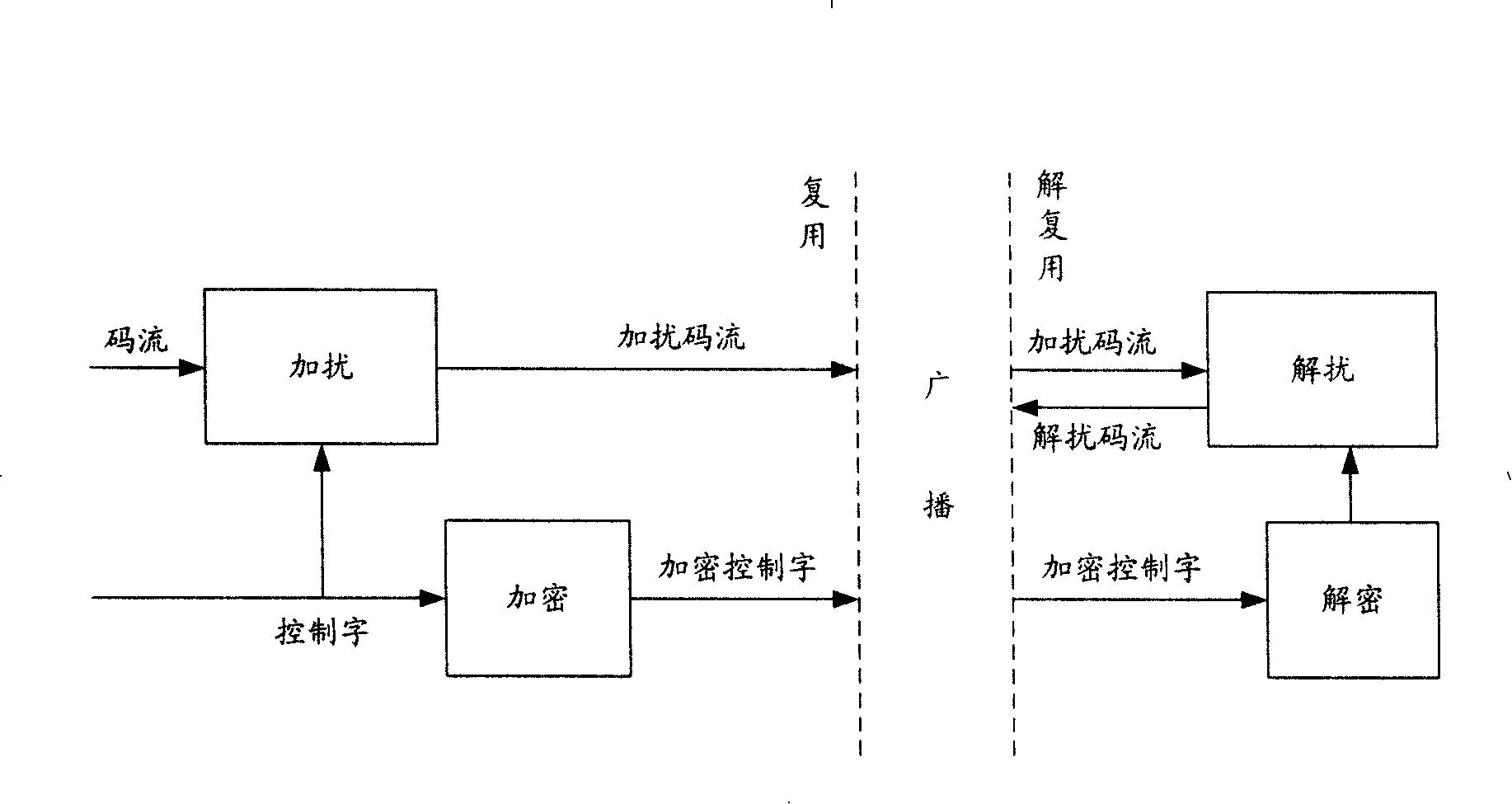
InactiveCN101212642AImplement conditional access servicesConvenient and flexible managementAnalogue secracy/subscription systemsSelective content distributionRadio broadcastingData stream
Owner:BEIJING WATCH DATA SYST
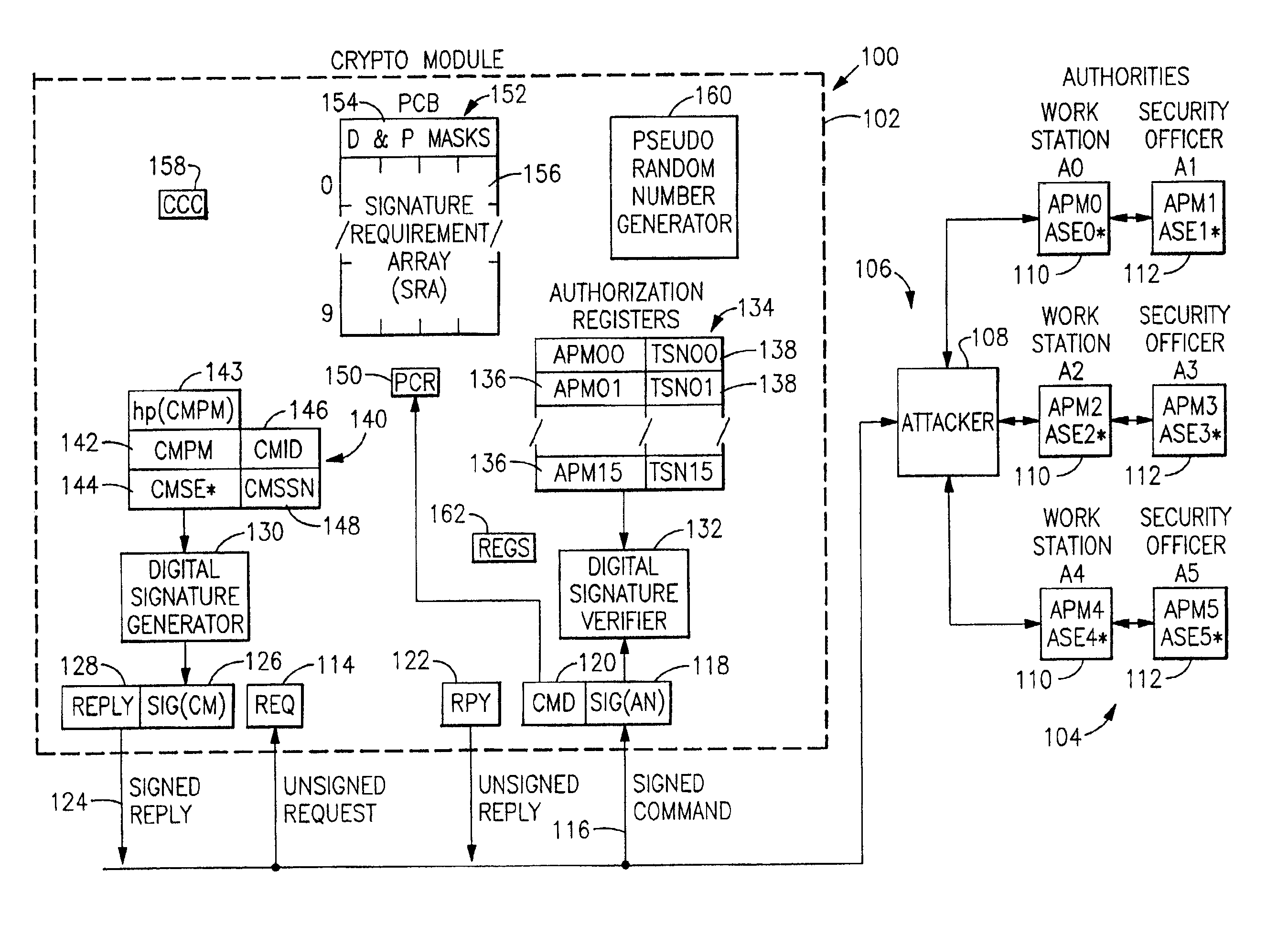
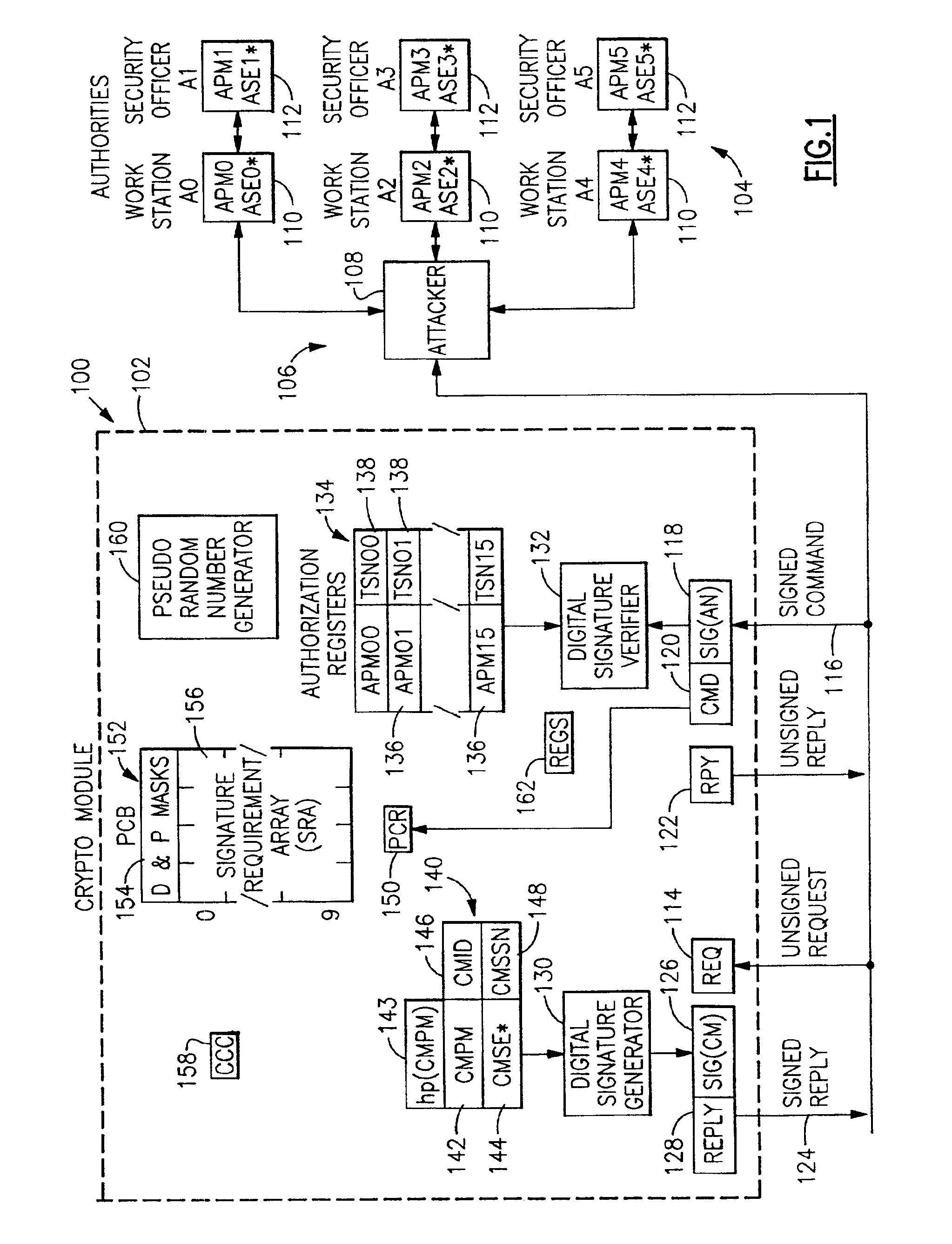
Method and apparatus for providing public key security control for a cryptographic processor
InactiveUS6948064B2Improve securityGreat confidencePublic key for secure communicationDigital data processing detailsArray data structureDigital signature
Owner:IBM CORP
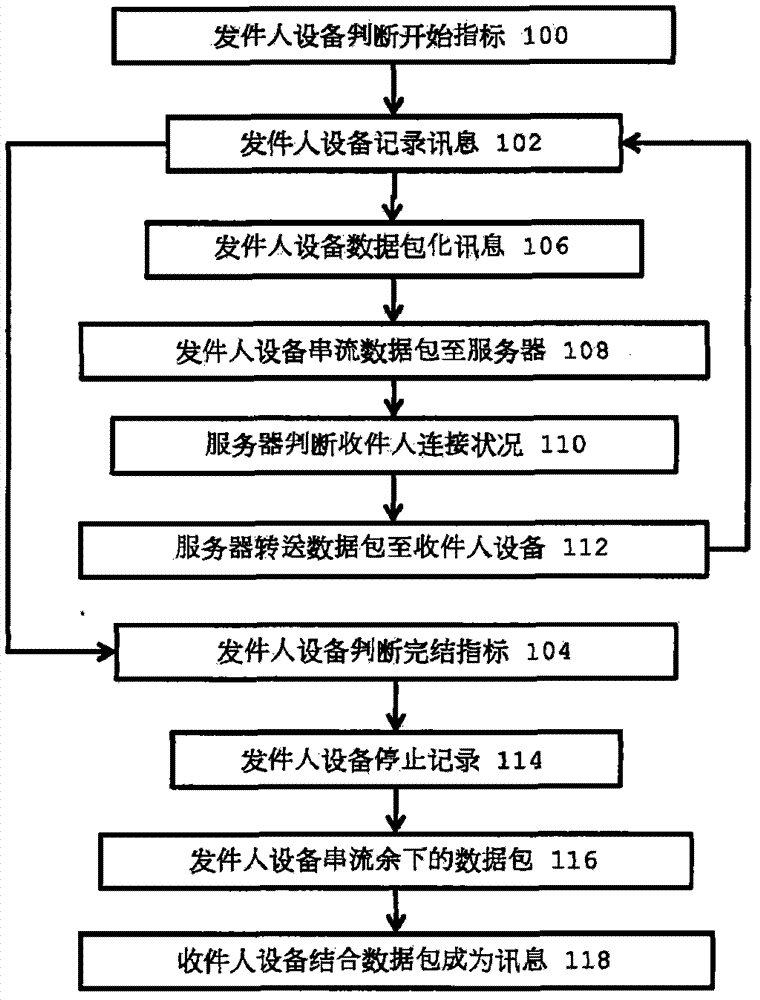
System and method for real-time transmission of multimedia messages
The present invention discloses a system and a method for real-time transmission of a multimedia message. The method records the multimedia message upon receiving a start indication from a sender at a sender device. The method then divides the multimedia message into a plurality of packets, streams the plurality of packets from a sender device to a server during recording of the multimedia message. The method then determines whether at least one recipient of the multimedia message is connected to the server. If the recipient is connected to the server, the method then streams the plurality of packets from the server to a recipient device during recording of the multimedia message. A system for real-time transmission of a multimedia message is also disclosed.
Owner:TALKBOX
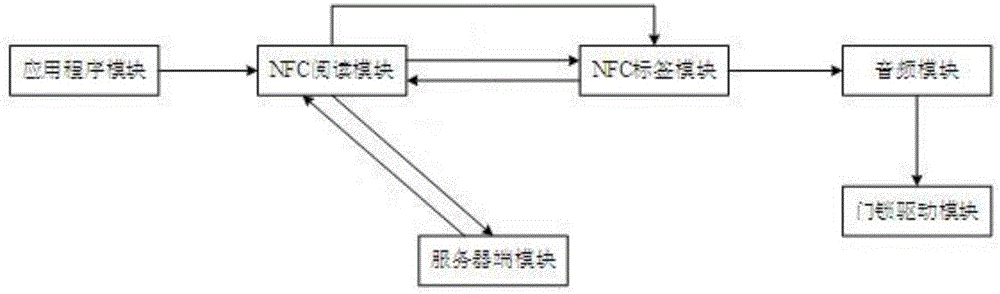
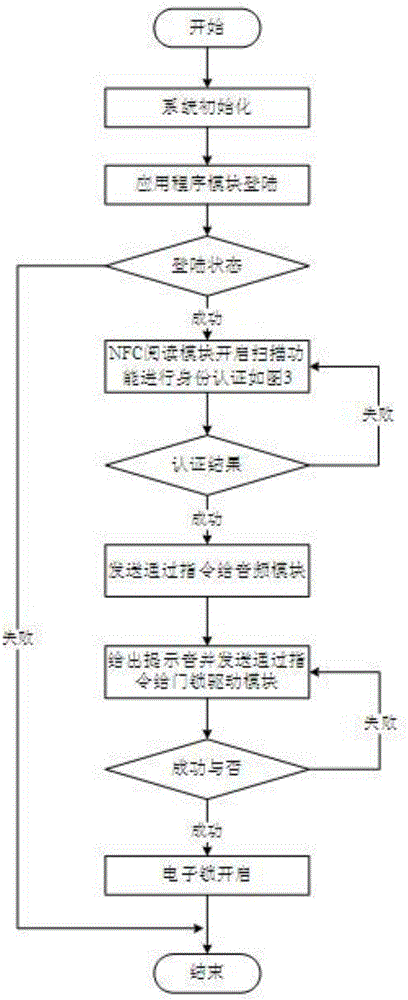
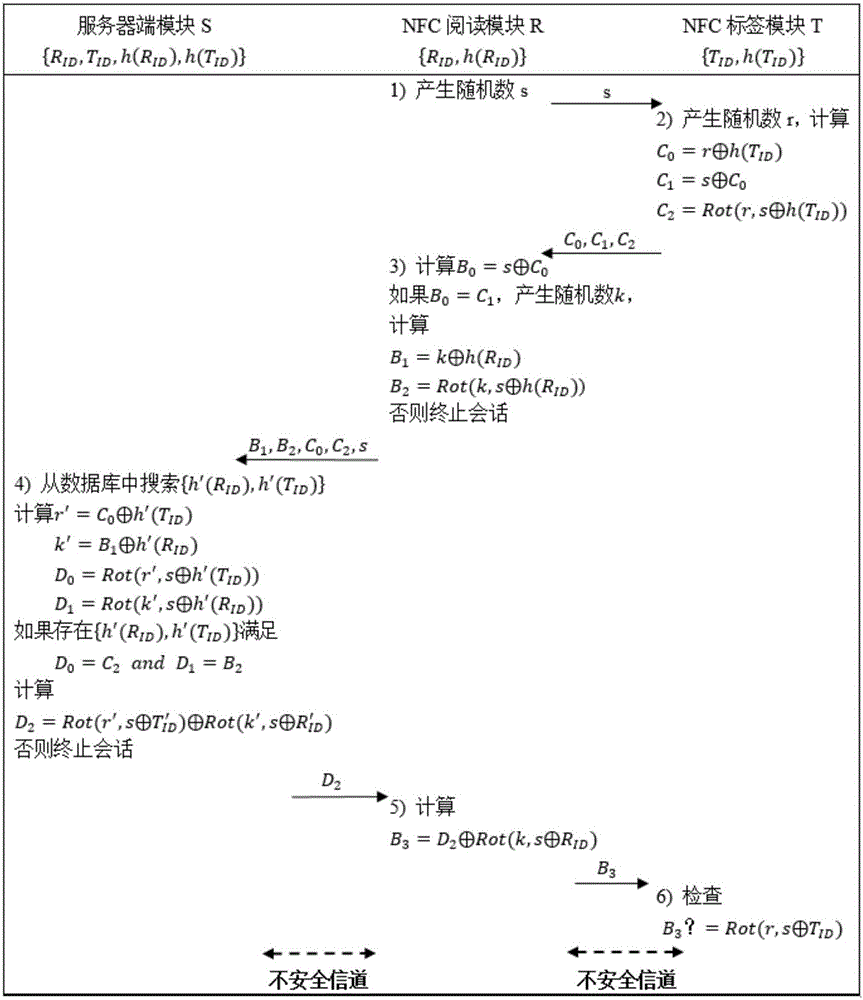
NFC (Near Field Communication) mobile intelligent terminal security access control system and control method thereof
ActiveCN106683245AGuaranteed freshnessPrevent data replayIndividual entry/exit registersSecurity arrangementServer-sideNear field communication
The invention discloses a NFC (Near Field Communication) mobile intelligent terminal security access control system and a control method thereof. The NFC mobile intelligent terminal security access control system comprises a NFC mobile intelligent terminal, an access controller, a server and an electronic lock, wherein the NFC mobile intelligent terminal is internally provided with an application program module and a NFC reading module; the access controller is internally provided with a NFC labeling module, a door lock driving module and an audio module; the server is internally provided with a server side module; the server side module is used for identifying the NFC reading module and the NFC labeling module, and meanwhile, the NFC labeling module is also used for identifying the server side module and the NFC reading module; the door lock driving module drives the electronic lock to open after the NFC labeling module passes the identification. During an identification process, identity labels of the NFC reading module and the NFC labeling module are hidden, and hash processing is carried out on the identity labels, so that eavesdrop and forgery attacks can be prevented; meanwhile, random numbers are added in interaction information, and shift operation is carried out, so that attacks of data replay, data tampering and the like can be prevented.
Owner:GUIZHOU AEROSPACE INST OF MEASURING & TESTING TECH
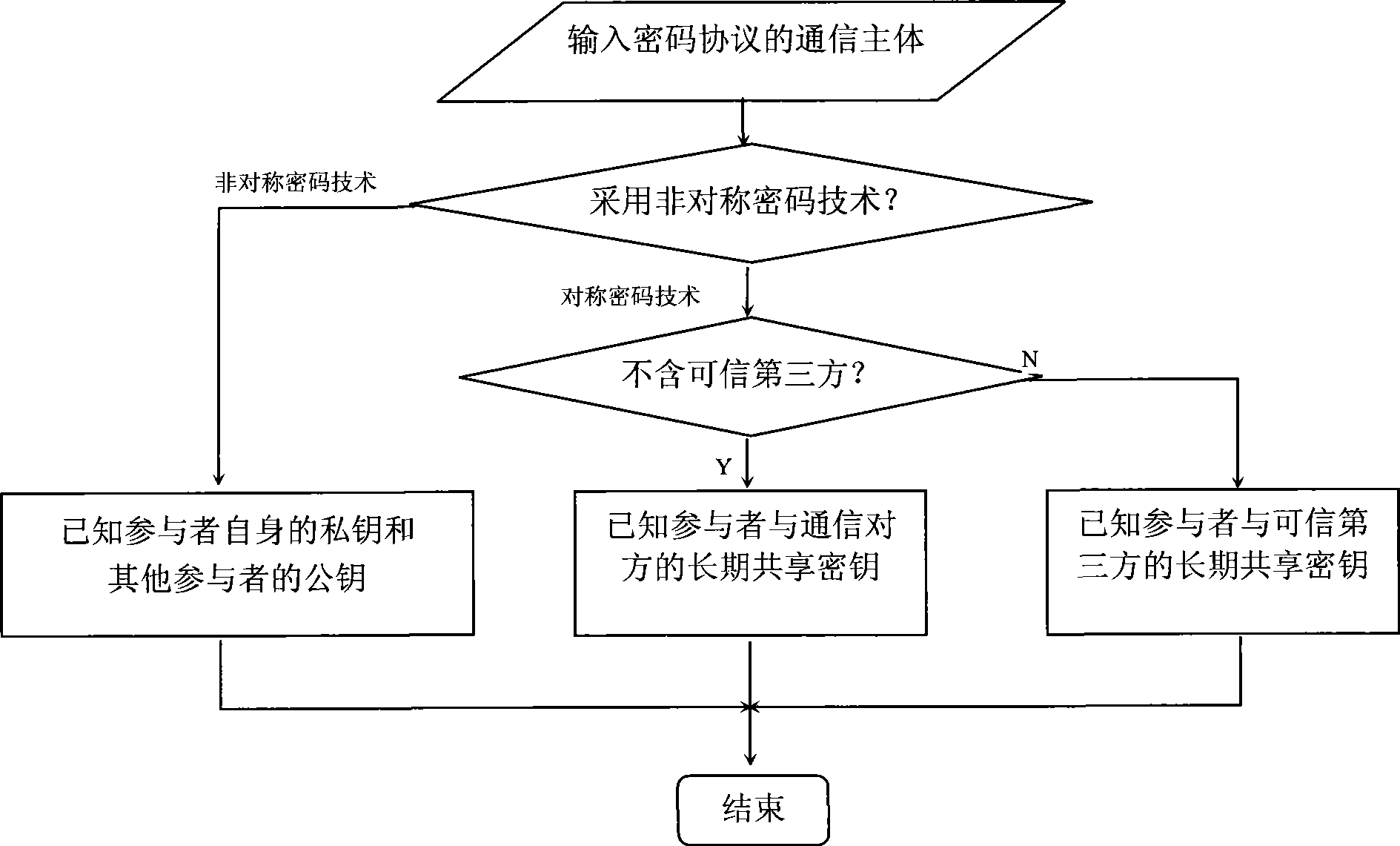
Method for establishing cipher protocol security based on trustful greenness
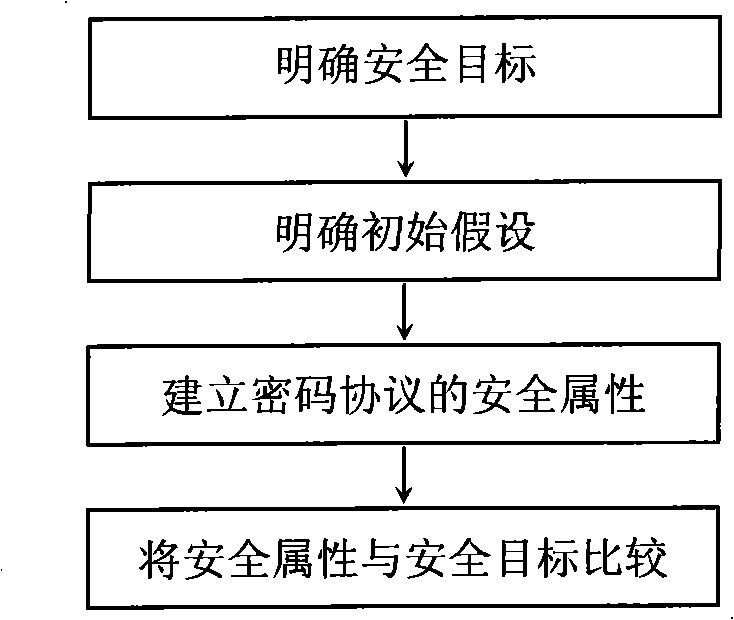
InactiveCN101299752ASafety verification is actually feasibleSignificant progressUser identity/authority verificationCryptographic protocolSecurity properties
A method for building the cryptographic protocol security based on the novelty in the information safety domain, including: determining the safe target of the cryptographic protocol to be concluded; determining the initial hypothesis of the cryptographic protocol security validation; building the cryptographic protocol security attribute obtained by the communication participating main body based on the initial hypothesis and the novelty principle of the cryptographic protocol security after transmitting or receiving each information, till the end of the protocol operation; comparing the obtained cryptographic protocol security attribute with the expected safe target. The invention effectively differentiates whether the information is novel, prevents the attack of the playback and confusion essentially, independent of the security validation and the intercurrent operating environment and the specific formalization description of the attacker's ability, which is of great efficiency to the validation cryptographic protocol, further to be expanded, applied to a plurality of validation of the cryptographic protocol security attribute.
Owner:SHANGHAI JIAO TONG UNIV
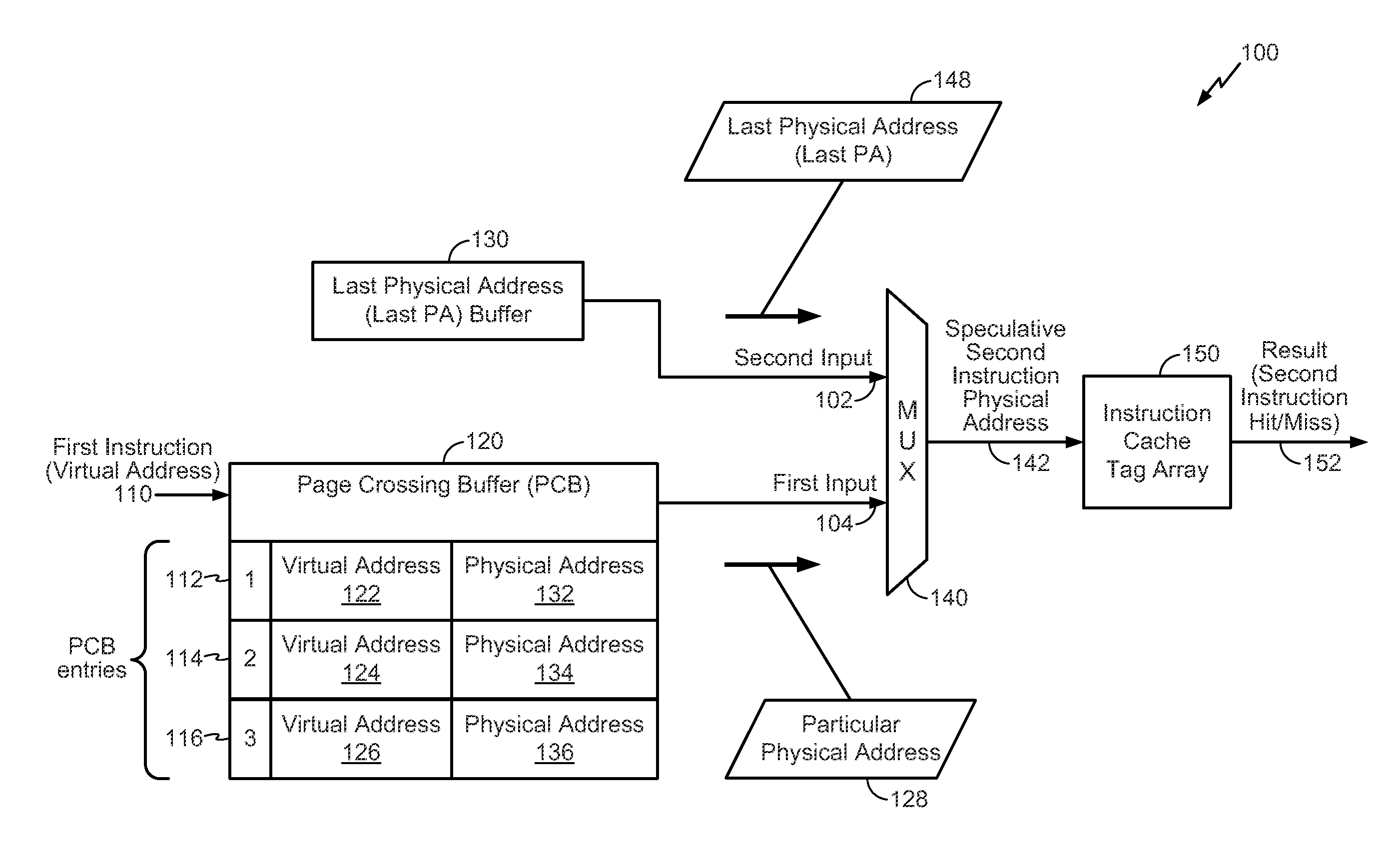
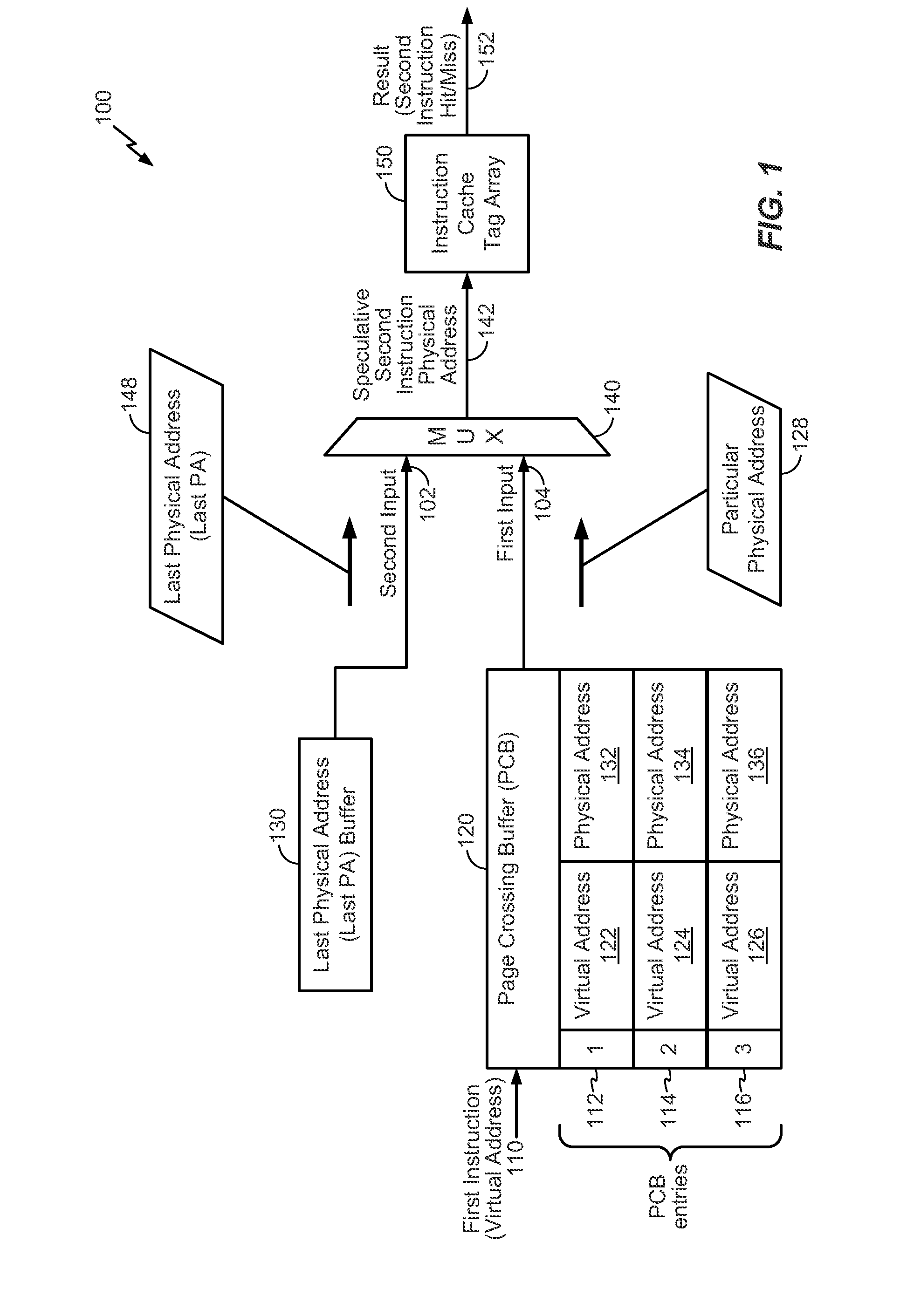
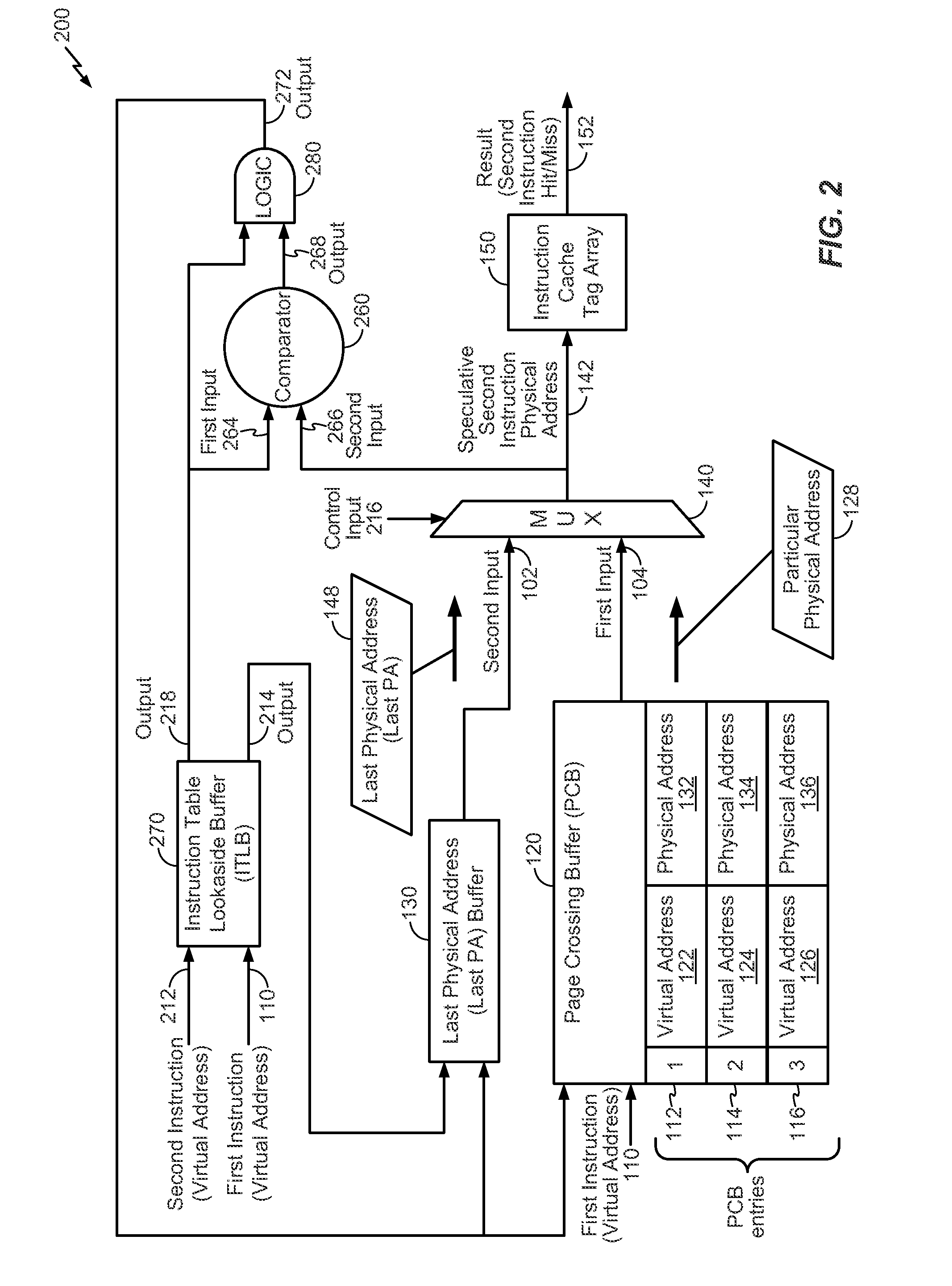
Speculative addressing using a virtual address-to-physical address page crossing buffer
InactiveUS20140181459A1Reduce processing delayImprove speculative addressingMemory architecture accessing/allocationMemory adressing/allocation/relocationData bufferOperating system
A method includes receiving an instruction to be executed by a processor. The method further includes performing a lookup in a page crossing buffer that includes one or more entries to determine if the instruction has an entry in the page crossing buffer. Each of the entries includes a physical address. The method further includes, when the page crossing buffer has the entry in the page crossing buffer, retrieving a particular physical address from the entry in the page crossing buffer.
Owner:QUALCOMM INC
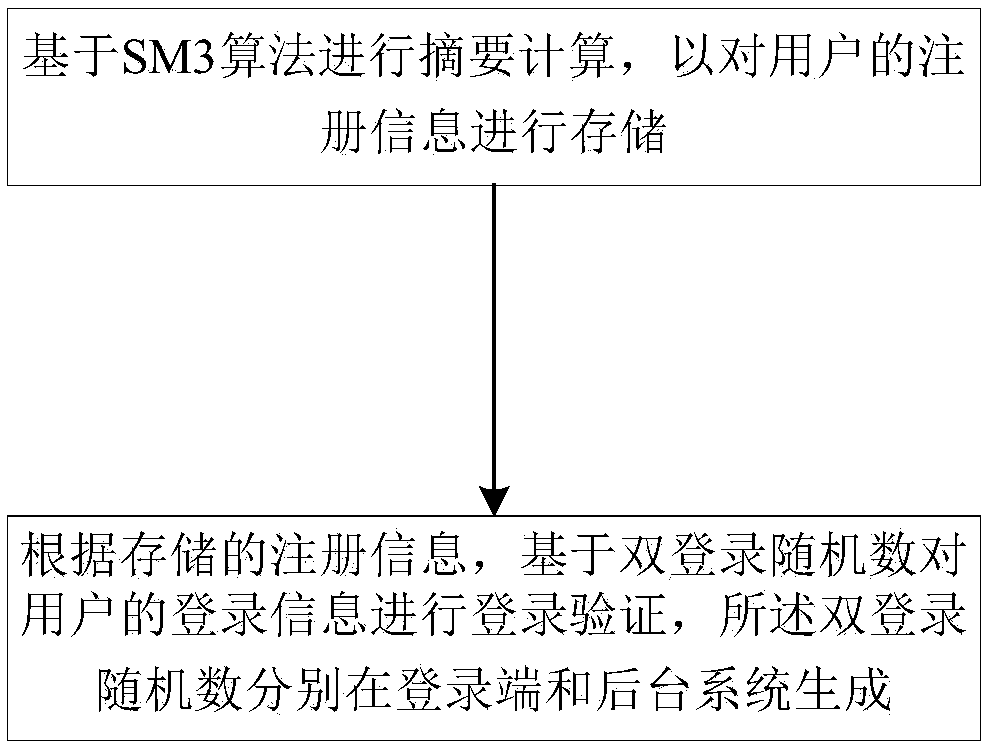
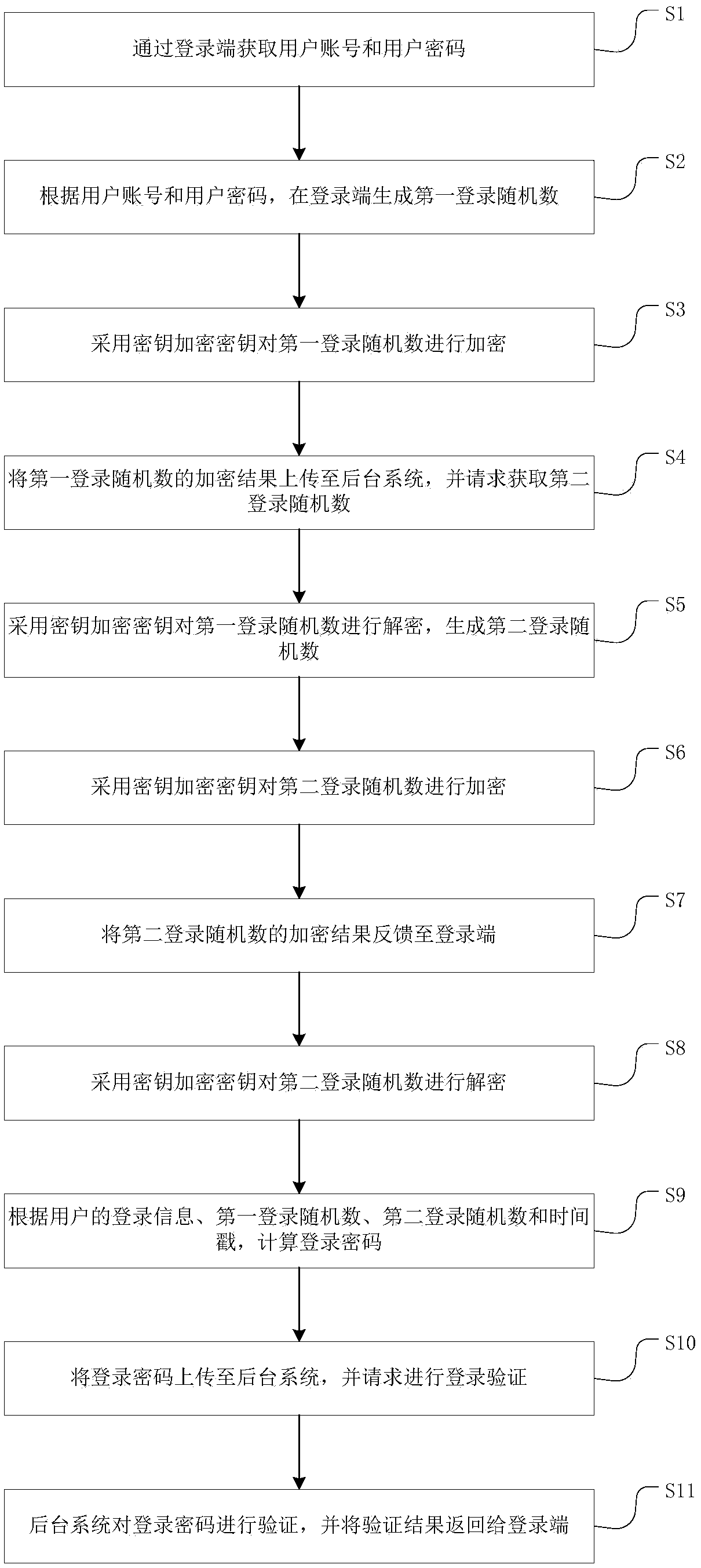
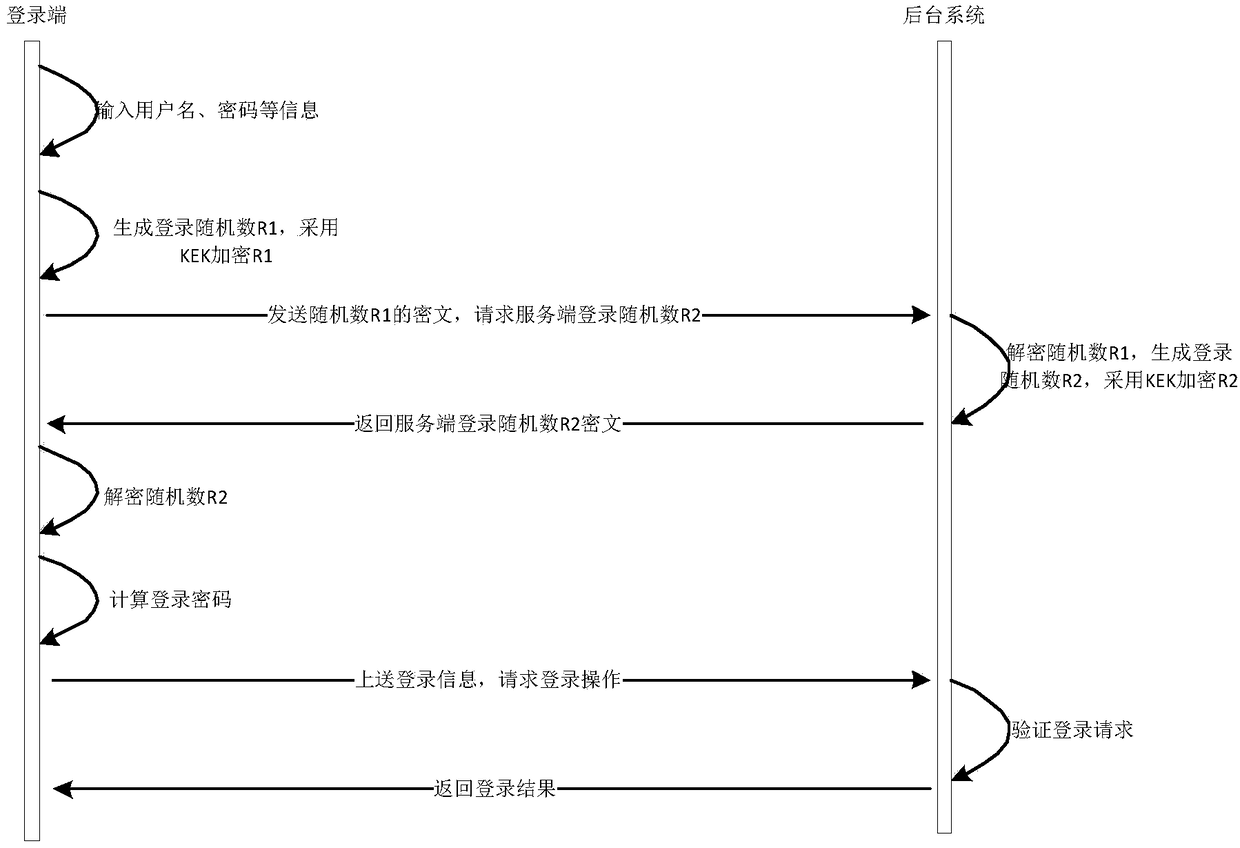
Login verification method and system based on SM3 algorithm and random challenge code
InactiveCN108347335APrevent replayImprove securityEncryption apparatus with shift registers/memoriesUser identity/authority verificationValidation methodsInformation security
The invention discloses a login verification method and system based on an SM3 algorithm and a random challenge code. The method comprises the following steps: performing summary calculation based onthe SM3 algorithm to store registration information of a user; and based on the stored registration information, performing login verification on the login information of the user based on double login random numbers. The system comprises a storage module and a verification module. According to the login verification method and system, the registration information of the user is stored based on the SM3 algorithm, compared with the existing international algorithms such as MD5, the irreversible SM3 algorithm can avoid the playback of the user login data and improve the security of the login data. In addition, based on the stored registration information, the login verification is performed on the login information of the user based on double login random numbers, thus improving the randomness and one-time of the login data, further preventing the replay attack, the data randomness and the security are high, and the login verification method and system can be widely applied to the information security field.
Owner:广州江南科友科技股份有限公司
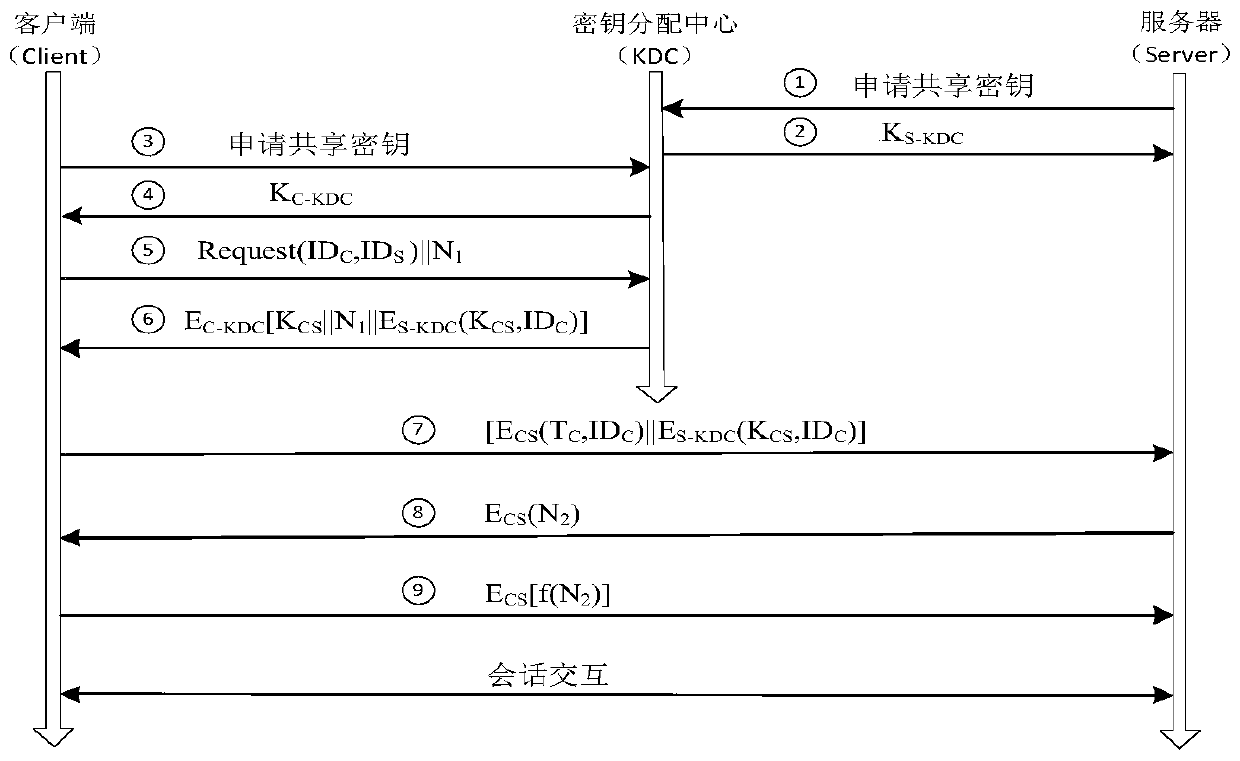
SSH authentication method based on key distribution center
ActiveCN110808829AIncrease flexibilityImprove convenienceKey distribution for secure communicationInformation technology support systemInternet privacyEngineering
The invention discloses an SSH authentication method based on a key distribution center. The SSH authentication method comprises the following steps: providing the key distribution center; the clientdoes not need to store all the host public keys to be connected, the generation, distribution and cancel operations of the used keys are completed by the key distribution center, manual participationis not needed, and the flexibility and convenience of key management are improved. The client obtains the encrypted session key through the key distribution center, and the key distribution center completes the authentication of the server identity. Moreover, the client can confirm that the obtained secret key and identity information are sent by the secret key distribution center through the unique recognition code returned by the secret key distribution center, thereby preventing the sent application from being tampered and preventing the response information from being replayed.
Owner:NARI TECH CO LTD
System and method for resisting physical attacks of printer
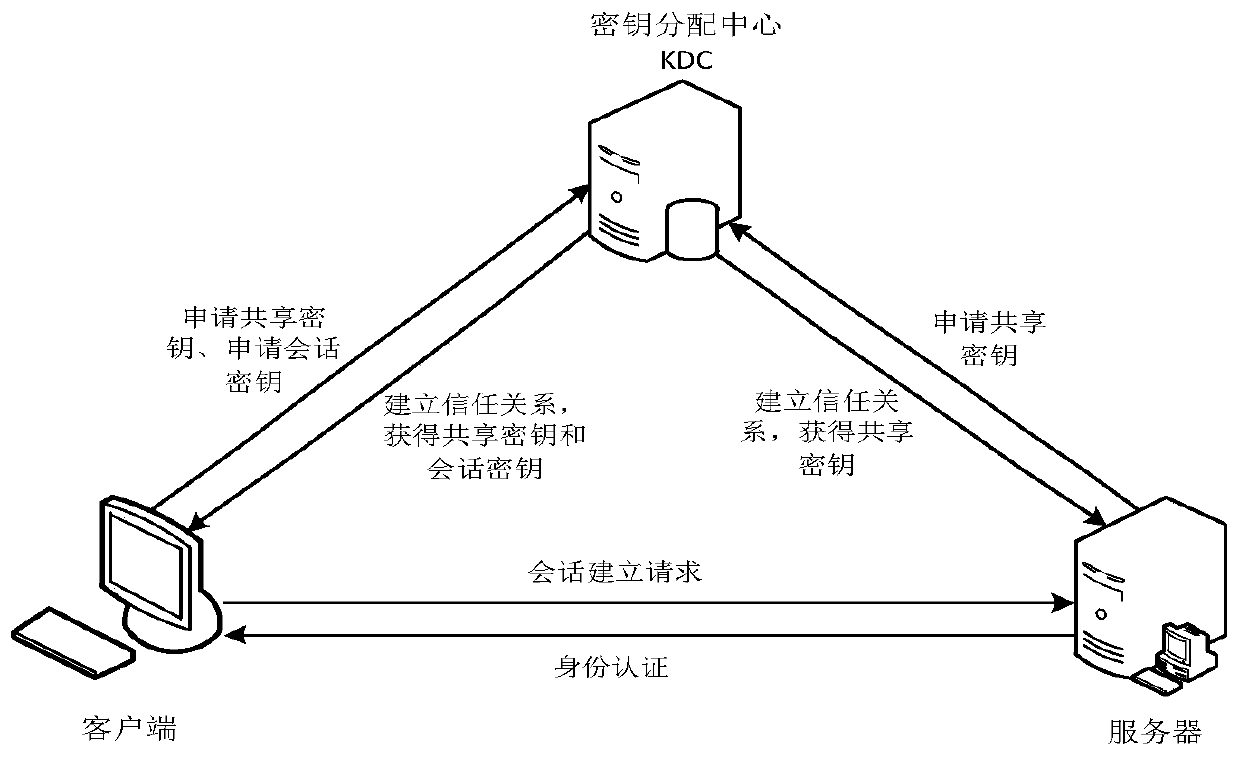
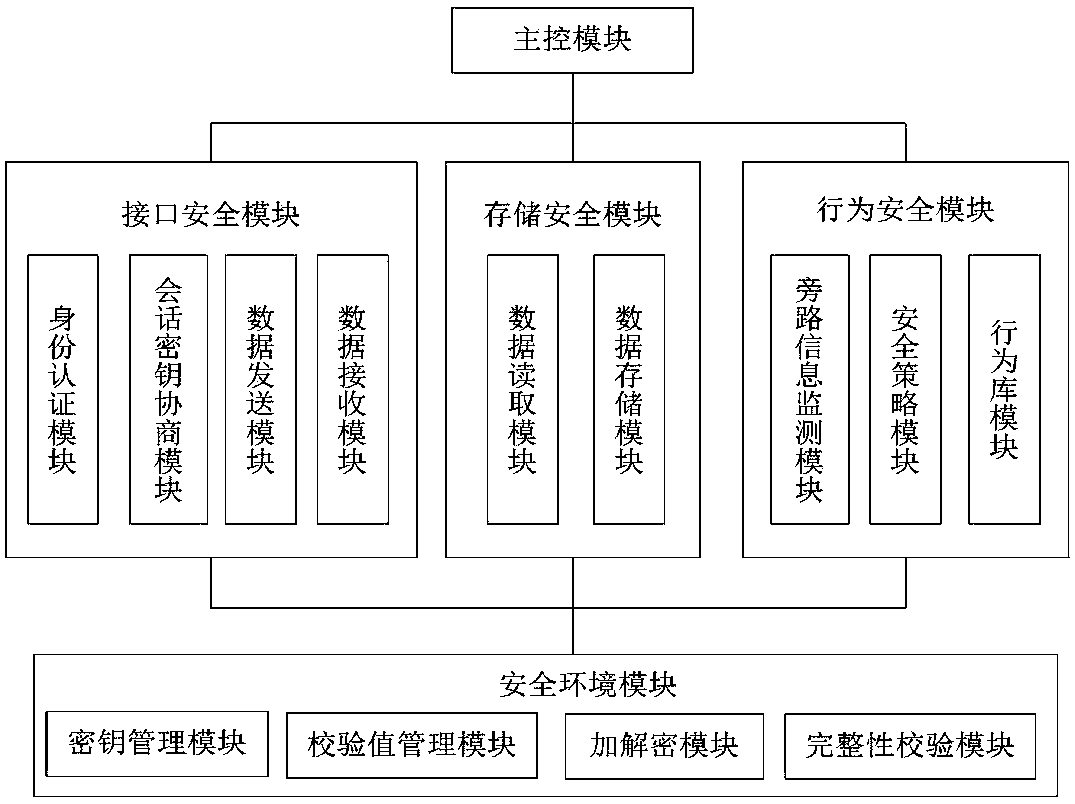
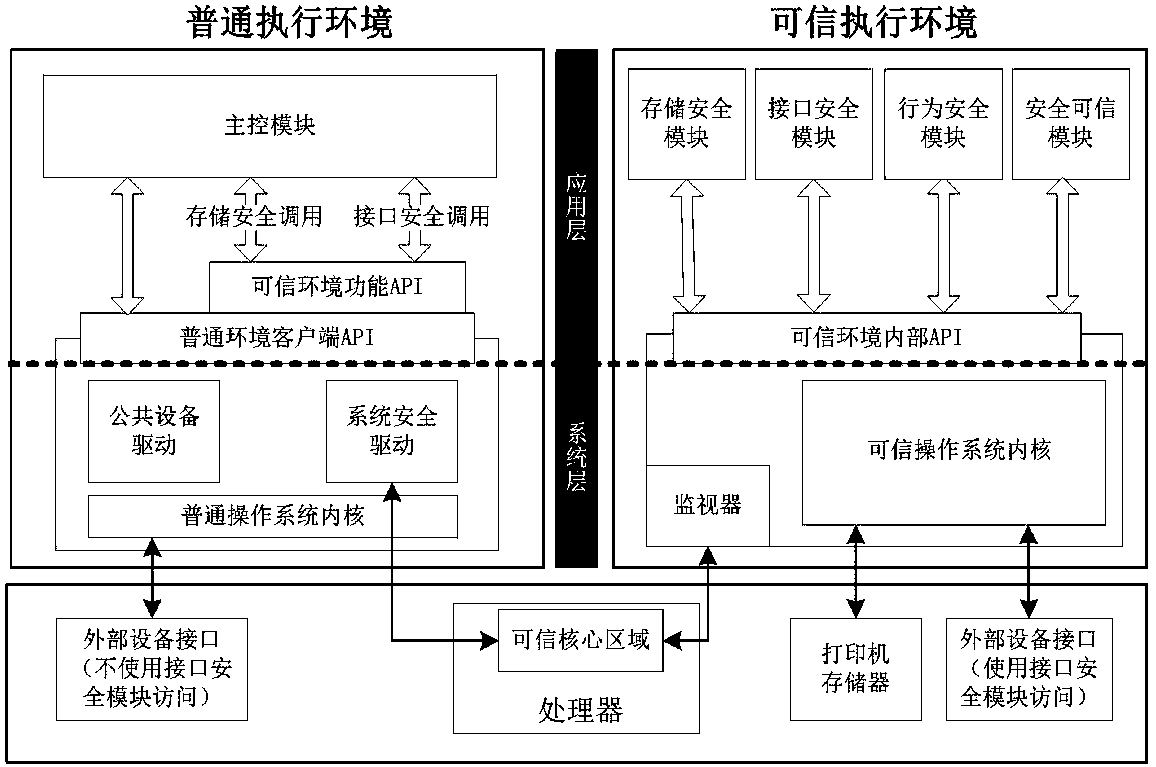
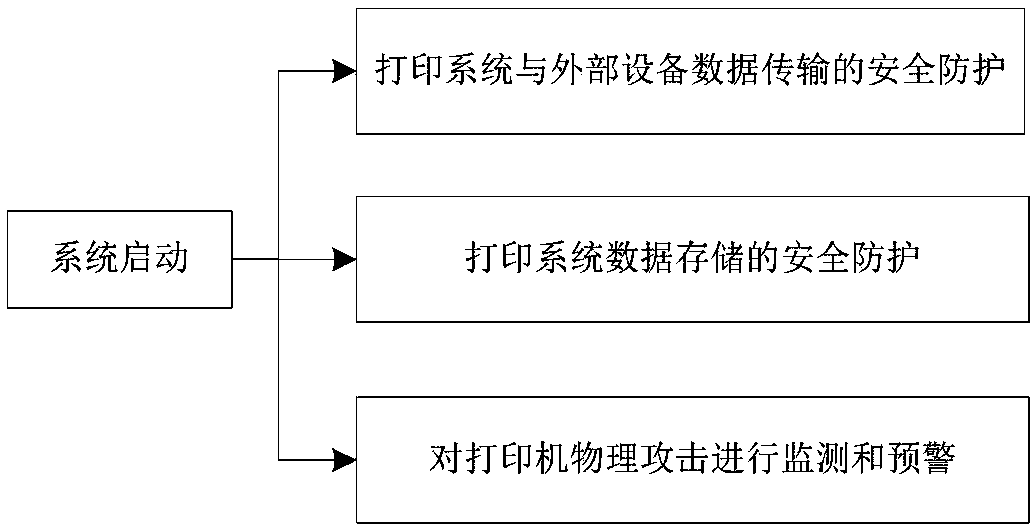
ActiveCN107911567AReal-time monitoring statusImprove securityTransmissionPictoral communicationPlaintextStorage security
The invention provides a system and method for resisting physical attacks of a printer. By encrypting and verifying plaintext data of a printer storage and an interface and monitoring behaviors of theprinter in real time to achieve early warning on the potential attack behaviors, the purpose of improving the security of the printer is achieved; a main control module achieves a security protectionfunction on the printer storage through a storage security module, achieves a security protection function on the interface through an interface security module and conducts monitoring and early warning on the physical attacks through a behavior security module; and a security trusted module is used for managing encryption keys, decryption keys and verification values which are used in the storage security module and the interface security module and conducting encryption, decryption and integrity verification on used data. According to the system and method, the physical attacks such as tapping, counterfeiting and resetting for the interface and the storage of the printer system are effectively resisted, the security of the printer is improved, the encryption efficiency of the printer storage is high, and the system and method can be applied to the printer system requiring high confidentiality.
Owner:XIDIAN UNIV
Key management method
InactiveCN101159538APrevent forgeryPrevent replayUser identity/authority verificationData switching by path configurationMessage integrityMaster key
The invention relates to a key management method which is an enhanced RSNA four-stage handshake protocol, which comprises the following steps: step 1, an authenticator adds a key negotiation ID (KNID) and a message integrity code (MIC) to a message (1) and then sends the message to a requester; step 2, the requester receives the message (1) and then checks whether the MIC character field container therein is correct, if incorrect, the requester directly discard the message, otherwise performs other checks, and sends a message (2) to the authenticator after the check succeeds; step 3, the authenticator checks the message (2) after reception and sends a message (3) to the requester after the check succeeds; step 4, the requester checks the message (3) after reception and sends a message (4) to the authenticator after the check succeeds; step 5, the authenticator checks the message (4) after reception, if the check succeeds, the four-stage handshake protocol is completed, and the authenticator and the requester reach an agreement after negotiation to produce a unicast temporal key (UTK) and obtain the group multicast master key (GMK) of the other party. The invention solves the DoS attack problem of the key management protocol in the existing RSNA security mechanism.
Owner:CHINA IWNCOMM
Grain information management method and system
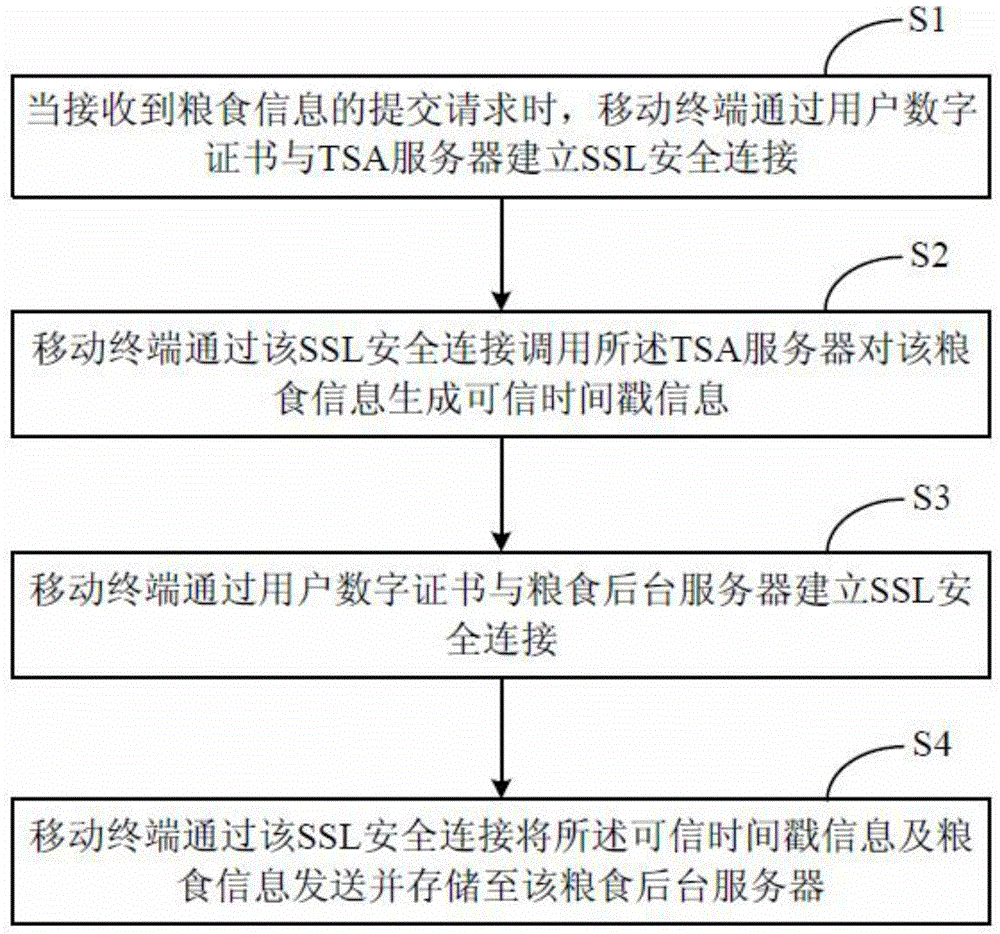
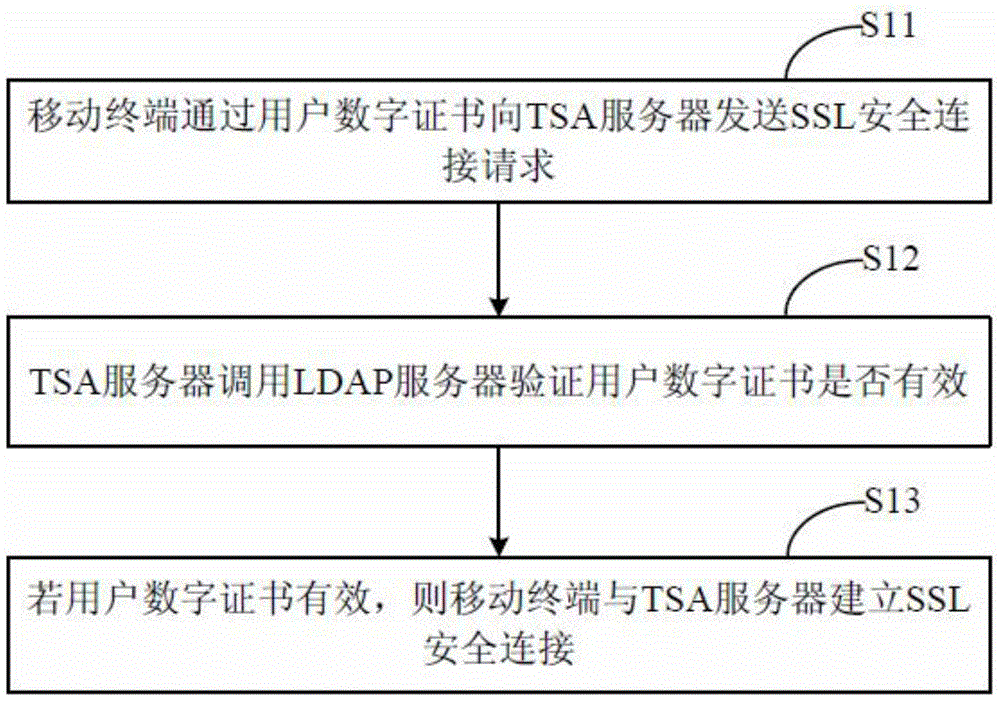
InactiveCN105763506AImprove securityNot interceptedTransmissionTelecommunicationsTrusted timestamping
The invention relates to a grain information management method, and the method comprises the steps that a mobile terminal builds safe cup-joint layer safety connection with a credible time stamp through a user digital certificate when a grain information submitting request is received; the mobile terminal carries out the call of the credible time stamp through the safe cup-joint layer safety connection, so as to generate credible time stamp information for the grain information; the mobile terminal builds safe cup-joint layer safety connection with a grain background server through the user digital certificate; and the mobile terminal enables the credible time stamp information and the grain information to be transmitted and stored in the grain background server through the safe cup-joint layer safety connection. The invention also provides a grain information management system. The method and system can provide reliable basis for the tracking of the quality safety of grains.
Owner:AEROSPACE INFORMATION
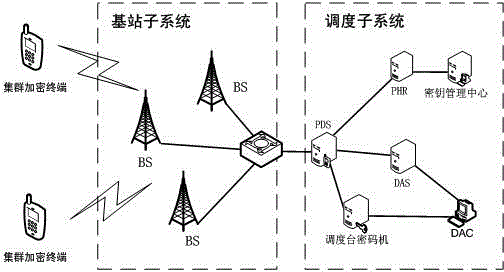
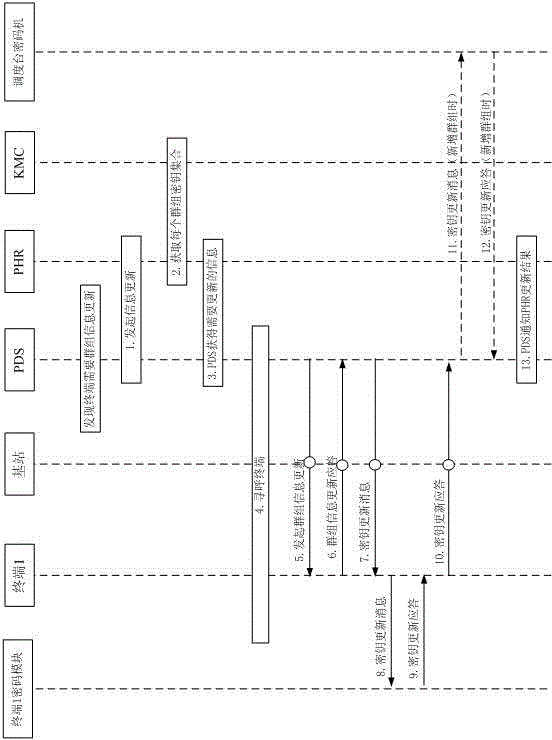
Dynamic restructuring method in cluster encryption communication
ActiveCN104539428APrevent theftPrevent counterfeitingUser identity/authority verificationCode moduleInformation needs
The invention relates to a dynamic restructuring method in cluster encryption communication. The method specifically includes the following steps that firstly, group information updating is started; secondly, a key set of a group corresponding to terminals is acquired; thirdly, a key management center KMC judges whether the terminals are registered or not and whether the updated group exists or not and according to a judgment result, group keys of the terminals are issued to a home location register PHR; fourthly, the home location register PHR issues group information needing to be updated and the key set of the group to a dispatch server PDS, and the dispatch server PDS pages the terminals and sends updating messages of the group information to the terminals through base stations; fifthly, the terminals update the group information and then send responses back; sixthly, key updating messages are sent to the terminals, if code modules of the terminals verify that the received key updating messages successfully, group key updating is finished, and response messages are sent back to the terminals; seventhly, the terminals send the key updating response messages to the dispatch server PDS through the base stations. By the adoption of the method, encrypted group calling is achieved.
Owner:成都三零瑞通移动通信有限公司
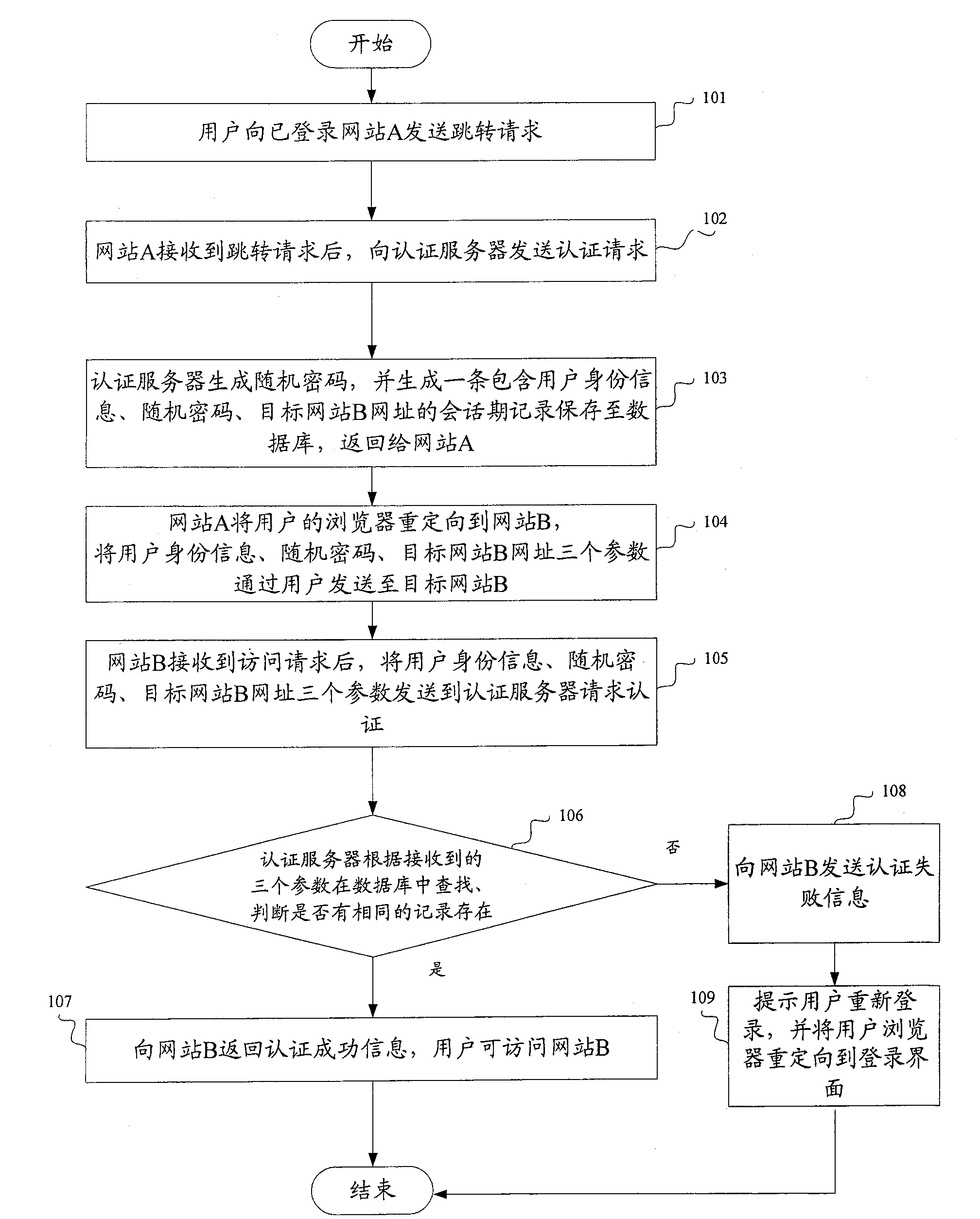
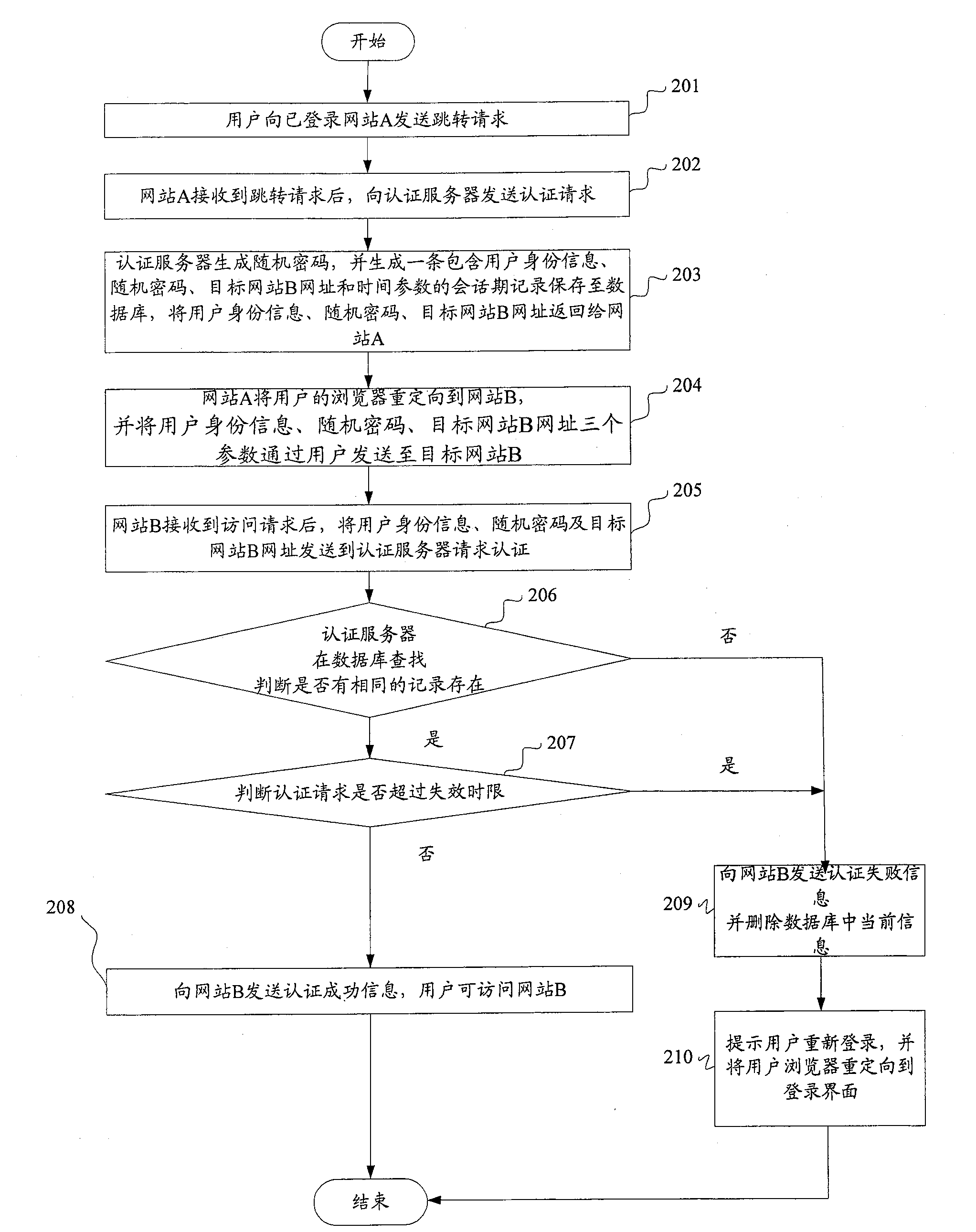
System and method for realizing single-point login
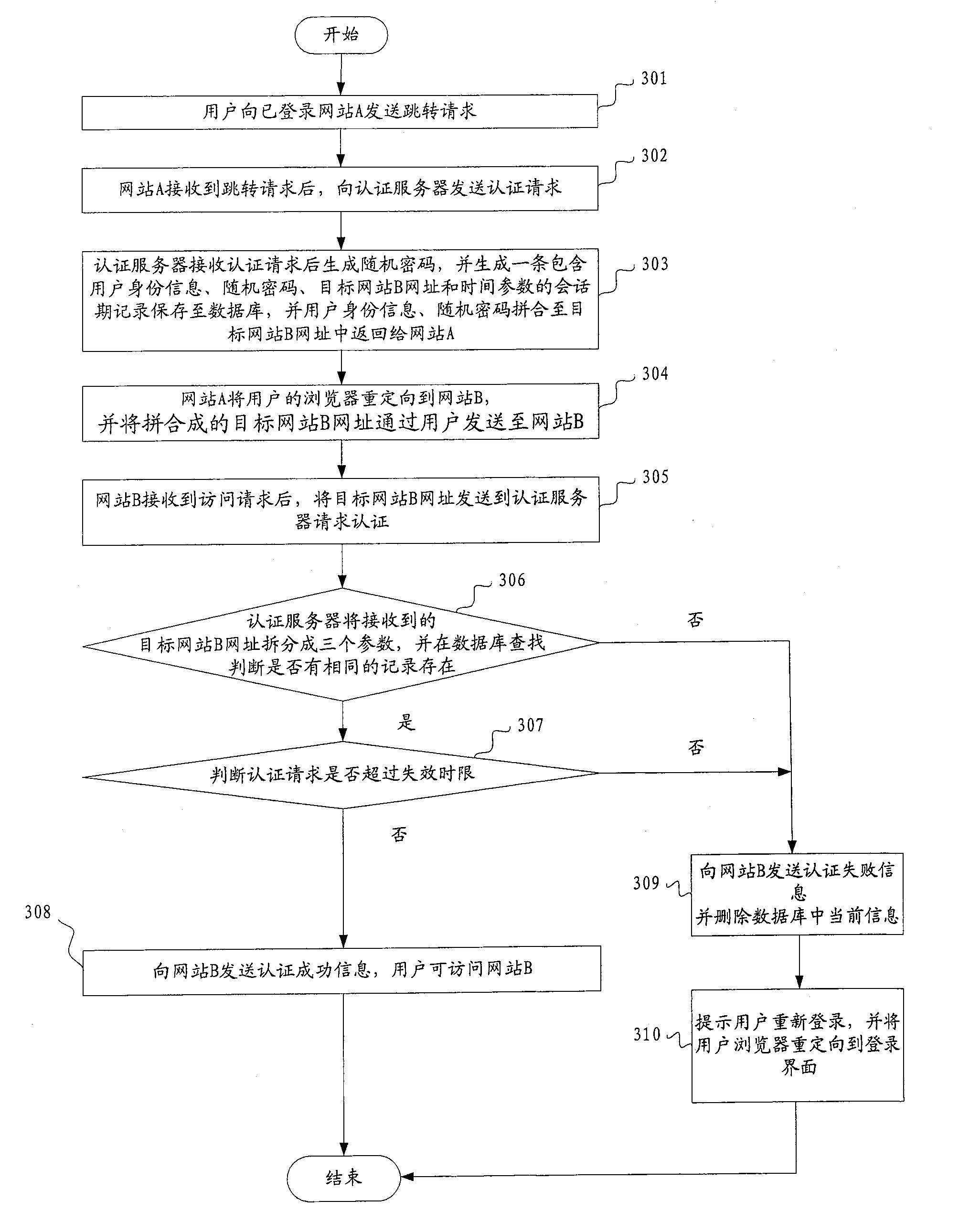
ActiveCN100586066CPrevent replaySmall modificationUser identity/authority verificationData switching by path configurationInternet privacyAuthentication server
The method comprises: user sends a jump request with its identification information and the website B address expected to login to the authentication server from a website A already logged in; the authentication server receives the jump request and generate a random cipher, and then generates the user ID information, random cipher and destination website B address, and then saves them; the user ID information, random cipher, destination website B address are returned to the website A; the website A redirects the user's browser to the destination website B, and transmits the user ID information, random cipher, and destination website B address to the authentication server through user and website B; the authentication server makes search to decide if there is a identical user's ID information, destination website B address and random cipher sent from the website B; if yes, then returning a successfully login sign to the website B, and permitting user login. The system thereof comprises: the website A already logged on and the website expected to log in.
Owner:BEIJING KINGSOFT SOFTWARE
Cooperative spectrum sensing location privacy protection method based on blockchain
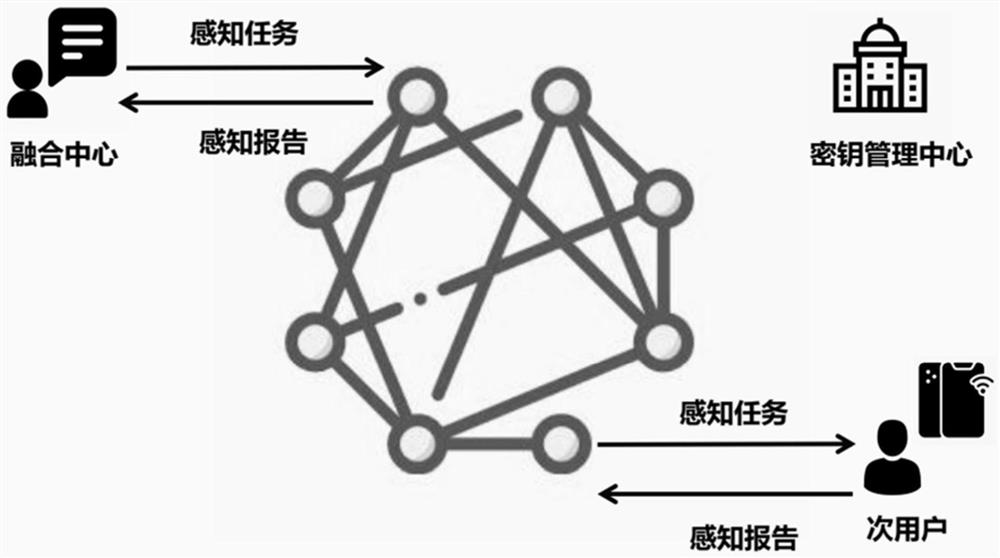
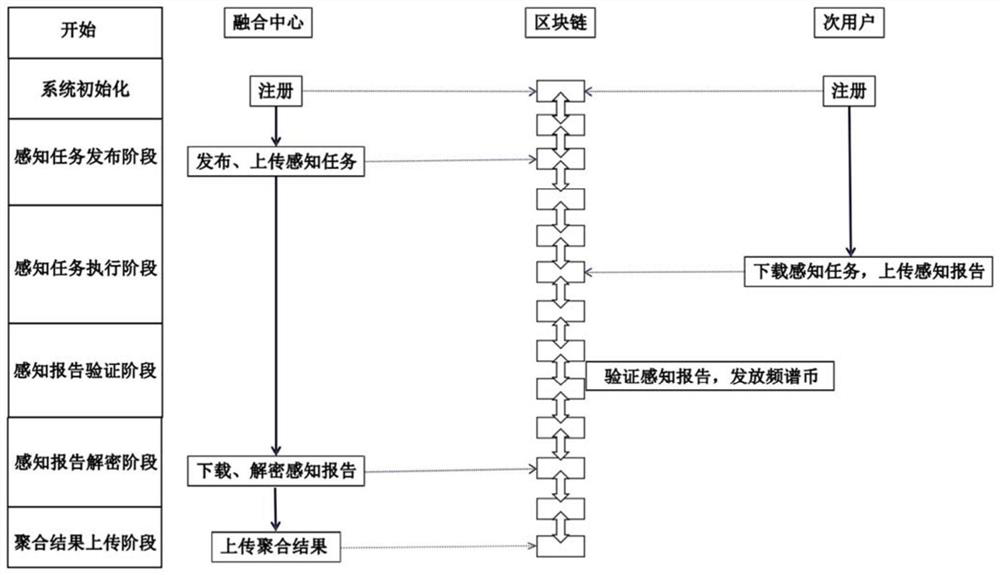
ActiveCN113079140AProtection securityPrevent theftKey distribution for secure communicationPublic key for secure communicationFusion centerTimestamp
The invention discloses a cooperative spectrum sensing location privacy protection method based on a blockchain, which utilizes the anonymity of the blockchain to enable a secondary user to anonymously upload a sensing report to the blockchain, avoids the relevance between the sensing report and the secondary user, prevents a fusion center from associating the sensing report with the secondary user during decryption, and protects the security of the sensing report in the fusion process. The secondary user encrypts and signs the sensing report by using the elliptic curve cryptography technology, so that the sensing report is prevented from being stolen and tampered in the transmission process, and the confidentiality and integrity of the sensing report in the transmission process are ensured. According to the method, the sensing report is prevented from being replayed in the transmission process by using the timestamp, and the timeliness of the sensing report in the transmission process is ensured. According to the method, the automatic verification characteristic of a smart contract is utilized, and the smart contract, instead of the fusion center, automatically verifies the digital signature of the sensing report, so that the calculation overhead of the fusion center is reduced.
Owner:FUJIAN NORMAL UNIV
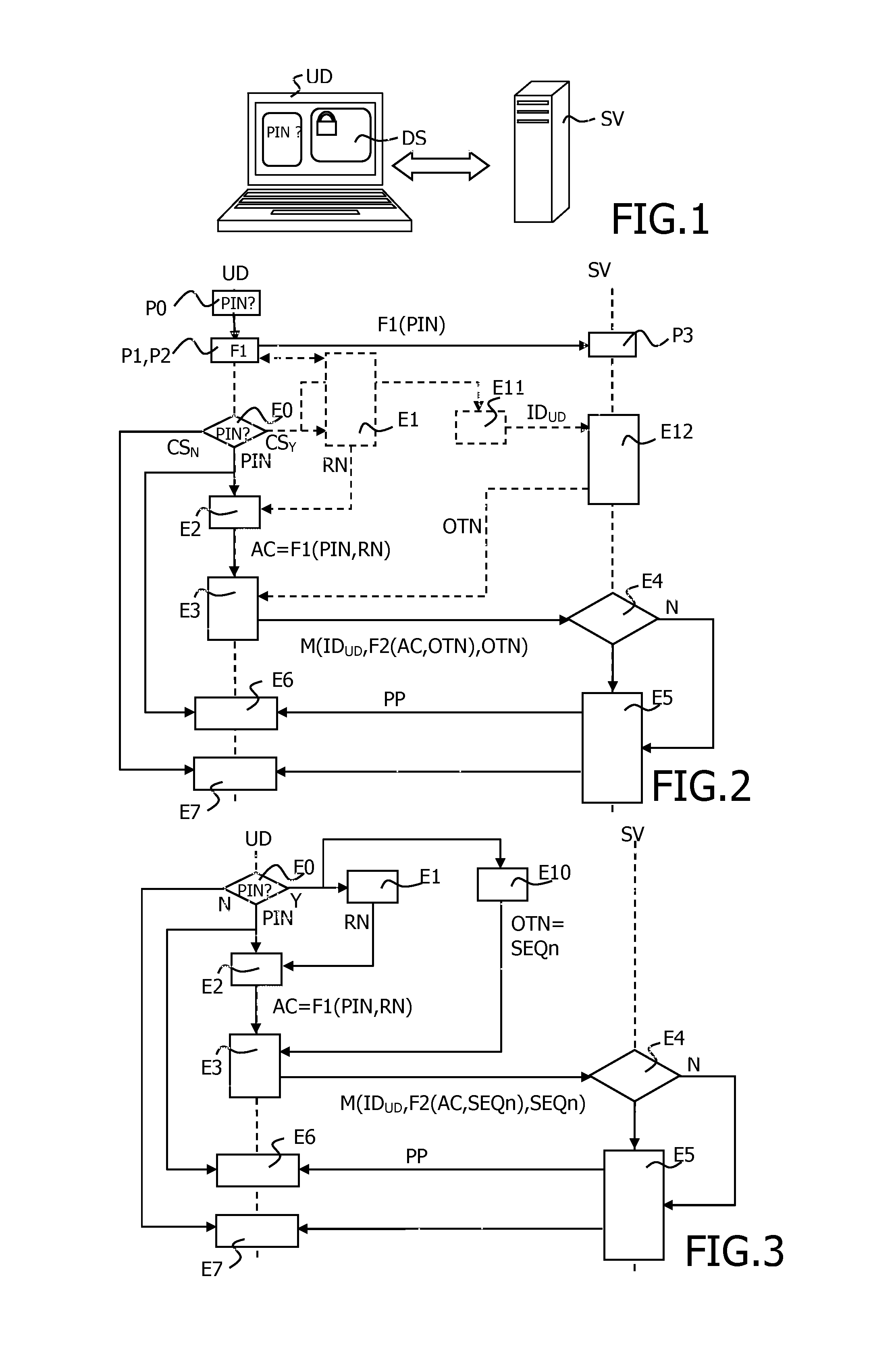
Method for server assisted keystore protection
ActiveUS20150318992A1Avoid retrievingAvoids replays of requestsKey distribution for secure communicationUser identity/authority verificationPassphraseUser input
The present invention relates to a method to access a data store previously locked using a passphrase from a device. The method includes the following steps, when the user requests access to the data store: requesting the user to enter the personal code; generating an access code by applying a first function to at least the entered personal code; sending out, to the server, at least an identifier of the device and the access code; for the server, comparing the access code with the preliminary received first function; for the server, if the access code is correct, returning the passphrase to the device; and for the device, unlocking the data store using the received passphrase in combination with the entered personal code.
Owner:GEMPLU
Indexing a trace by insertion of key frames for replay responsiveness
ActiveUS20180260299A1Avoid the needPrevent replaySoftware testing/debuggingSpecial data processing applicationsData streamParallel computing
Creating key frames during indexing of a trace for responsive trace replay. A method includes identifying responsiveness goal(s) for trace replay, including identifying a target trace section replay time. A portion of execution of executable entit(ies) is replayed based on trace data stream(s). While replaying execution of the executable entit(ies), and based on the identified target trace section replay time, points of interest in execution of the executable entit(ies) are identified. At least one key frame is created for each of the identified plurality of points of interest. Each key frame enables replay of at least one of the one or more executable entities beginning at the key frame.
Owner:MICROSOFT TECH LICENSING LLC
Disk apparatus, video/audio data processor, and video/audio control method
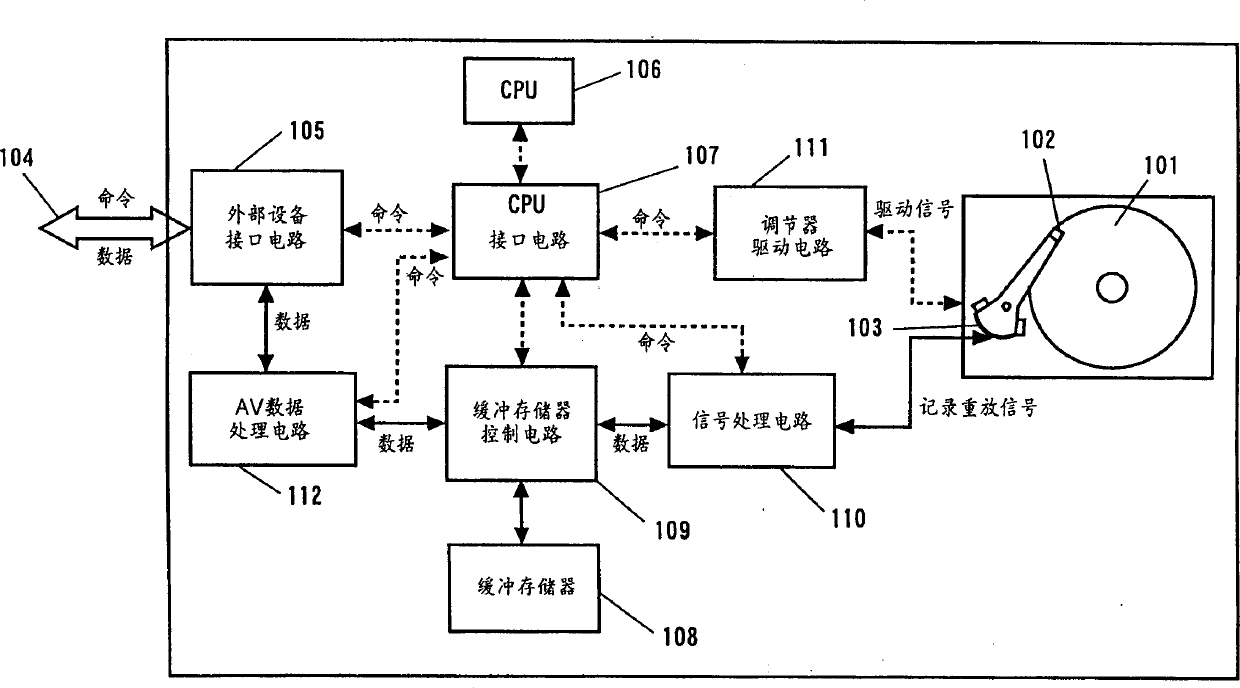
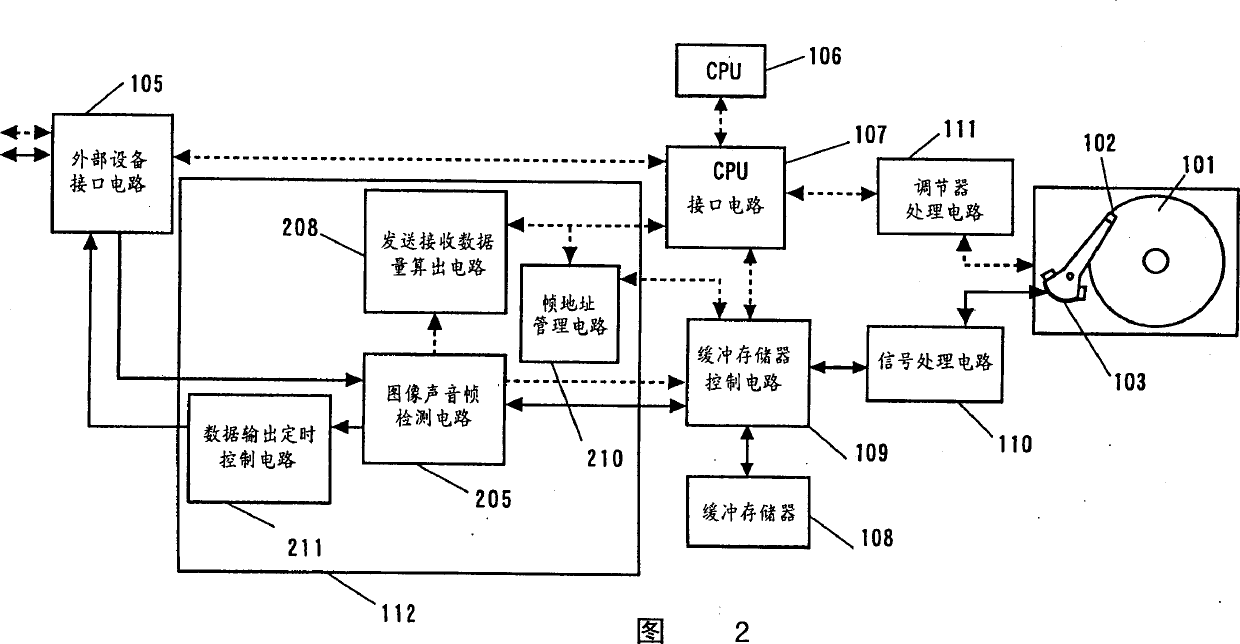
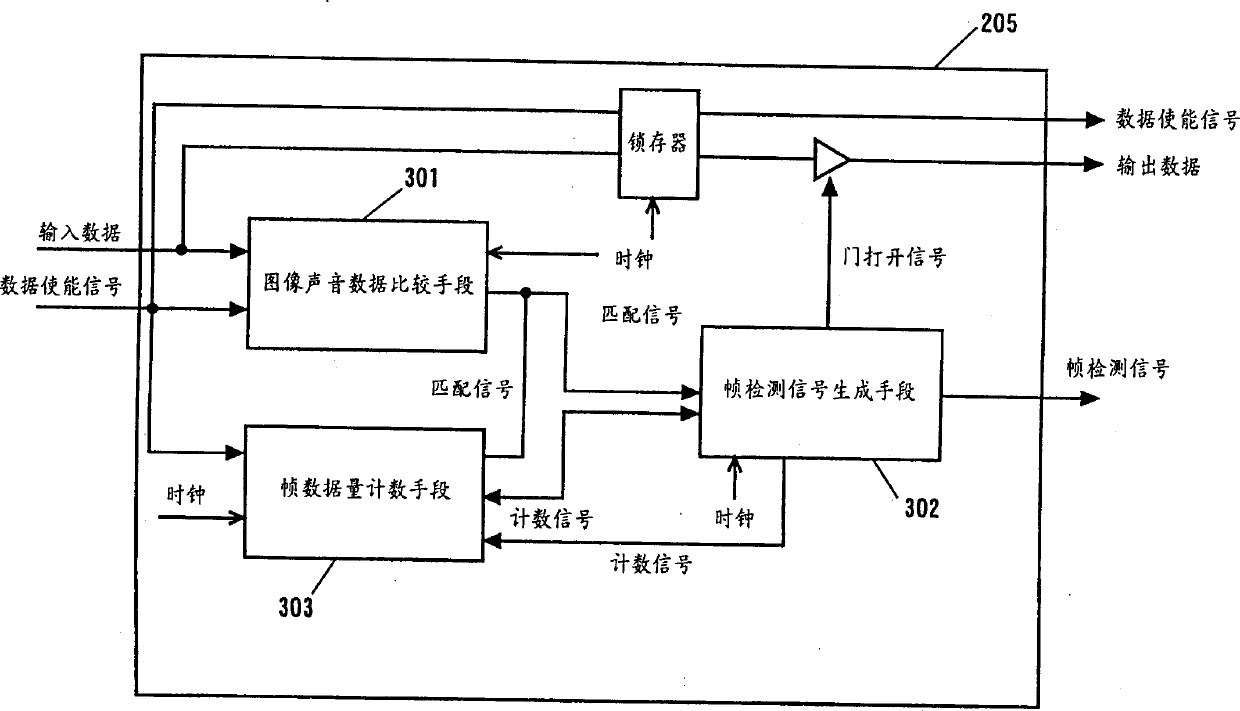
InactiveCN1275232AImprove data transfer efficiencyReduce functionTelevision system detailsInput/output to record carriersStream dataData treatment
A disk apparatus and video / audio data processor having a function of processing stream data, virtually having a function of processing commands in a digital VCR, and adaptable to respond to various processing requests from an external apparatus, wherein a video / audio frame boundary of video / audio data is detected, the video / audio data continuously received from outside is divided into video / audio frame units according to the detected video / audio frame boundary, and the divided data is stored on a disk medium and controlled. A video / audio control method comprising detecting a video / audio frame boundary of video / audio data, dividing the video / audio data continuously received from outside into video / audio frame units according to the detected video / audio frame boundary, and controlling the divided data.
Owner:PANASONIC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com