SSH authentication method based on key distribution center
A key distribution center and authentication method technology, which is applied in the field of power system network security, can solve problems such as manual, inflexible and convenient, and the danger of host deception, so as to prevent tampering and replay of response information, improve flexibility and convenience effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] A method for managing the reception of various operation and maintenance indicator data based on memory queues in the present invention will be further described in detail below in conjunction with the accompanying drawings.
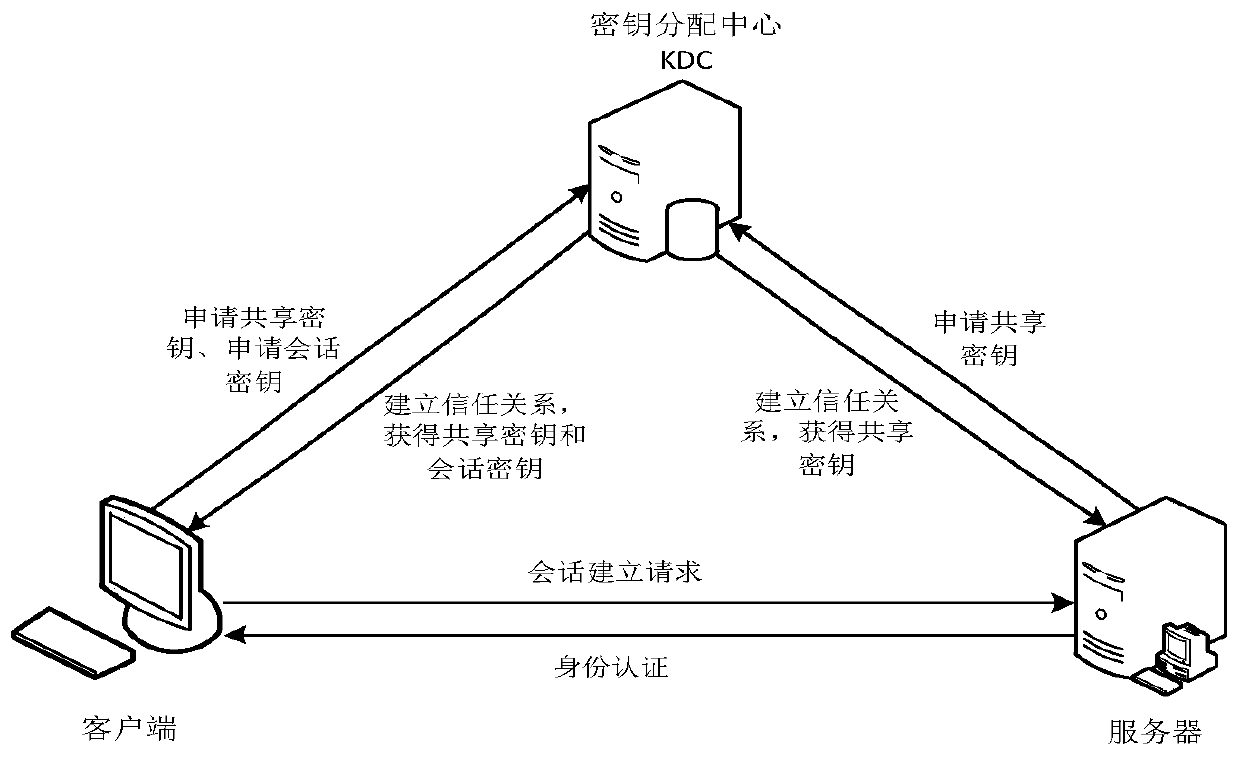
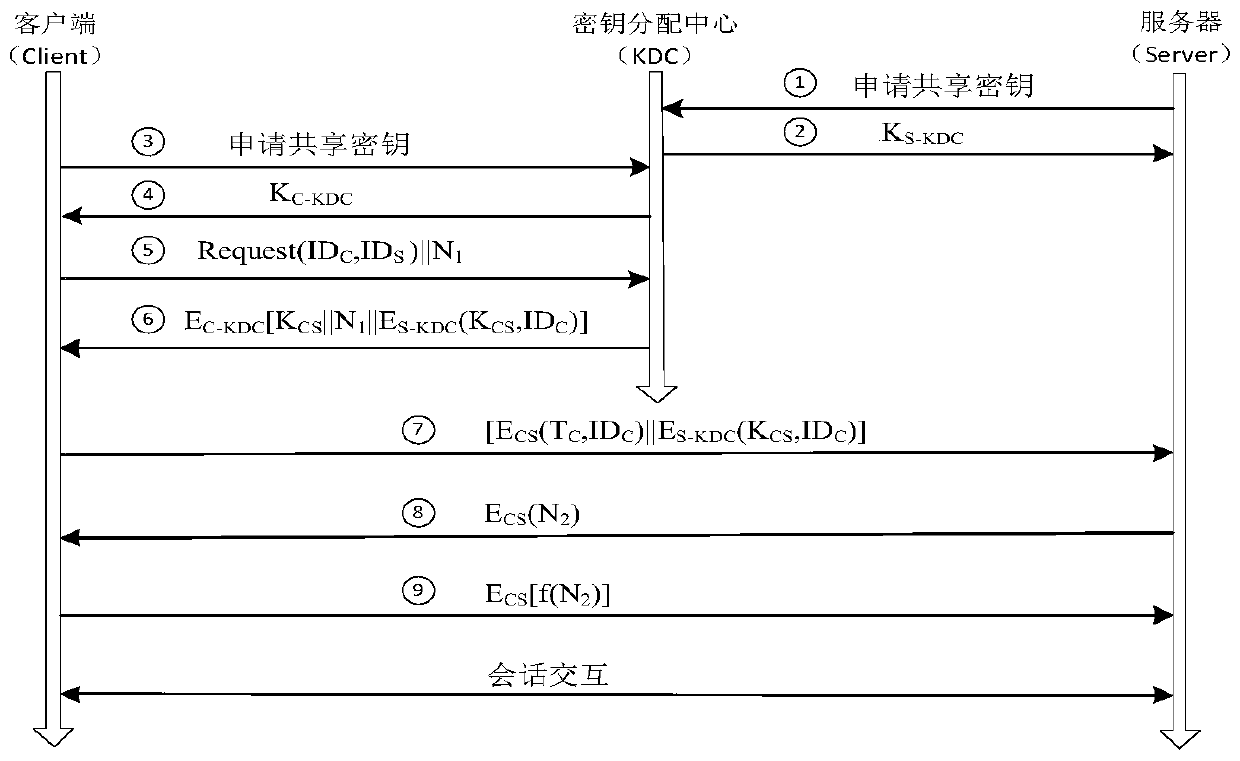
[0038] The Key Distribution Center (KDC, Key Distribution Center) is a service running on a physical security server, and the KDC maintains a database of account information of all security principals in the domain. The KDC stores an encryption key that only the security principal and the KDC know. This key is also called a long-term key, that is, the master key, and is used for exchanging between the security principal and the KDC. KDC is a third party trusted by both the initiator and receiver because it maintains an account database that stores all accounts in the domain, that is, it manages the name belonging to each account and the master key derived from the account password . The session key used for mutual authentication between the clien...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com