Method for establishing cipher protocol security based on trustful greenness
A cryptographic protocol and freshness technology, applied in the field of information security, can solve problems such as unconvincing security, inability to determine whether the protocol is correct enough and necessary, and inability to effectively determine whether a message is fresh, etc., to prevent replay and the effect of the obfuscated attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
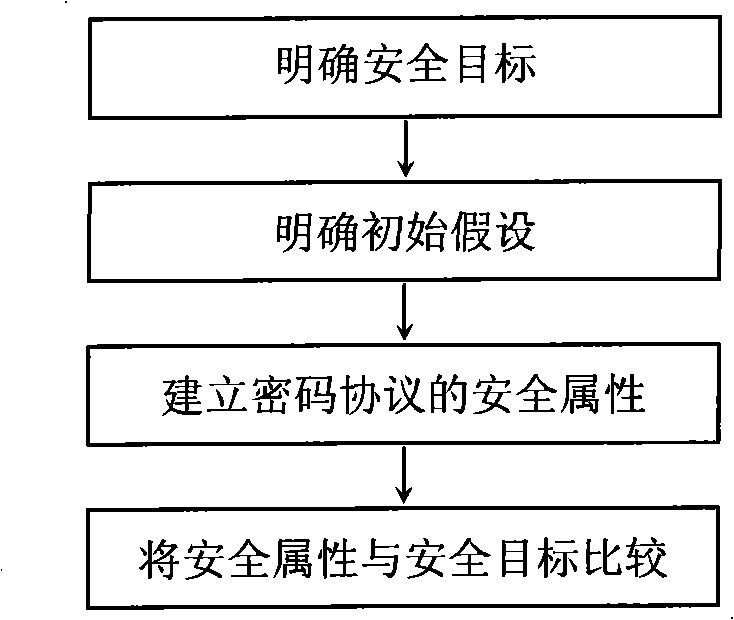
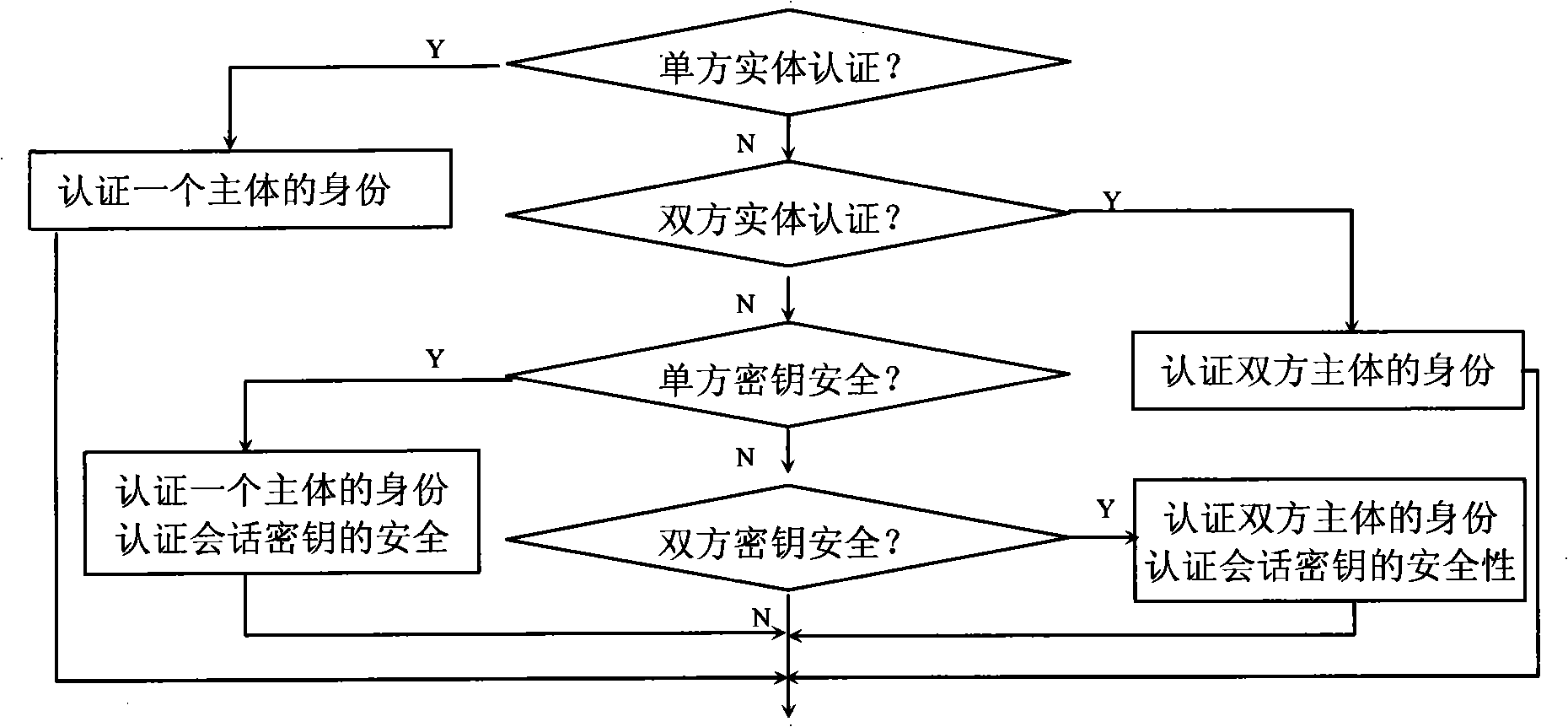
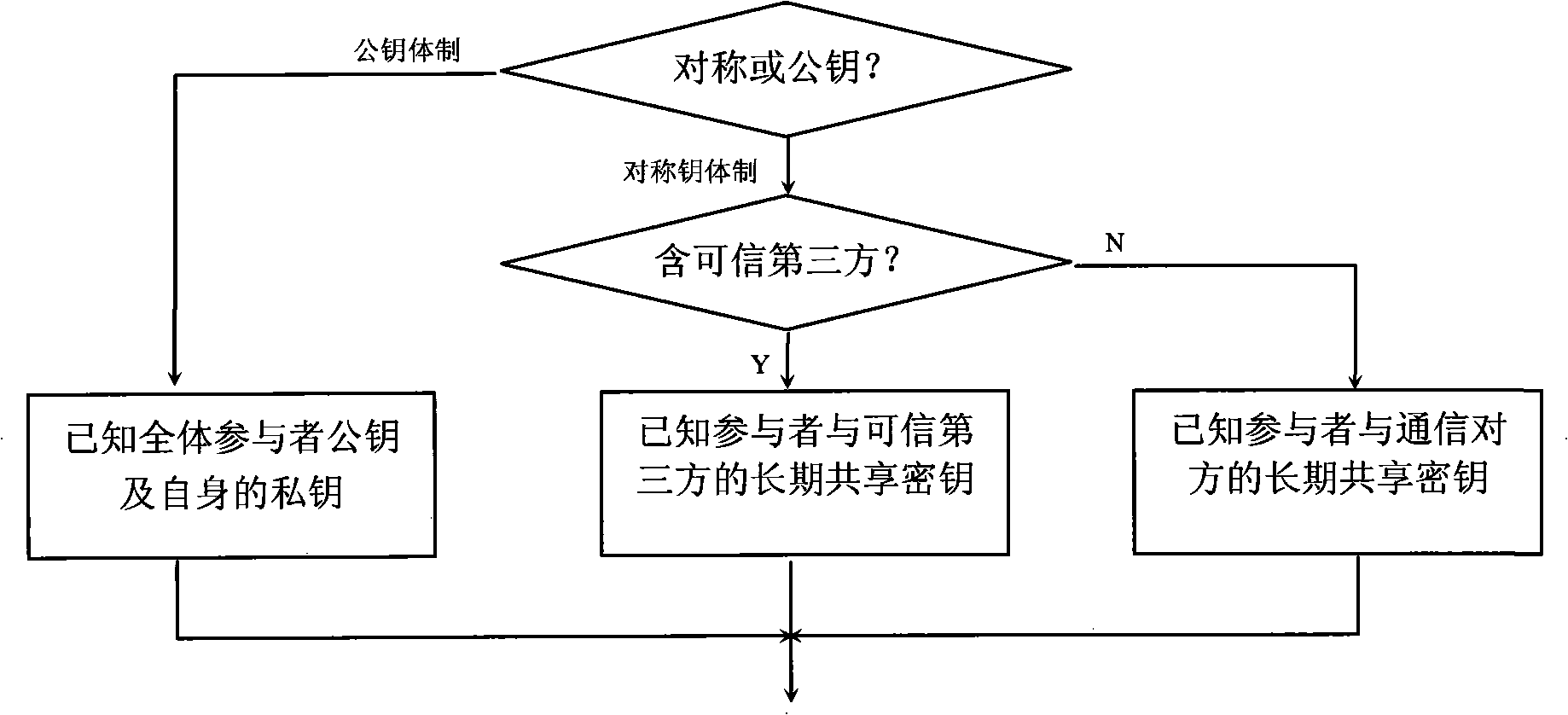
[0052] Below in conjunction with accompanying drawing, the embodiment of the present invention is described in detail: present embodiment implements under the premise of technical solution of the present invention, has provided detailed implementation and specific operation process, but protection scope of the present invention is not limited to following Example.
[0053] "The SSL Protocol Version 3.0" (SSL protocol version 3.0) published by Alan O. Freier et al. on the URL address http: / / wp.netscape.com / eng / ssl3 / draft302.txt is an asymmetric public protocol designed by Netscape. A key transfer protocol for key cryptography. K ab is a temporary session key randomly selected by subject A for the session between A and B, and CA is the public key certificate of subject A. The transmission of messages related to authentication in the SSL protocol is as follows:
[0054] Message 1 A→B: {K ab} Kb
[0055] Message 2 B→A: {N b}K ab
[0056] Message 3 A→B: {CA, {N b}K a -1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com