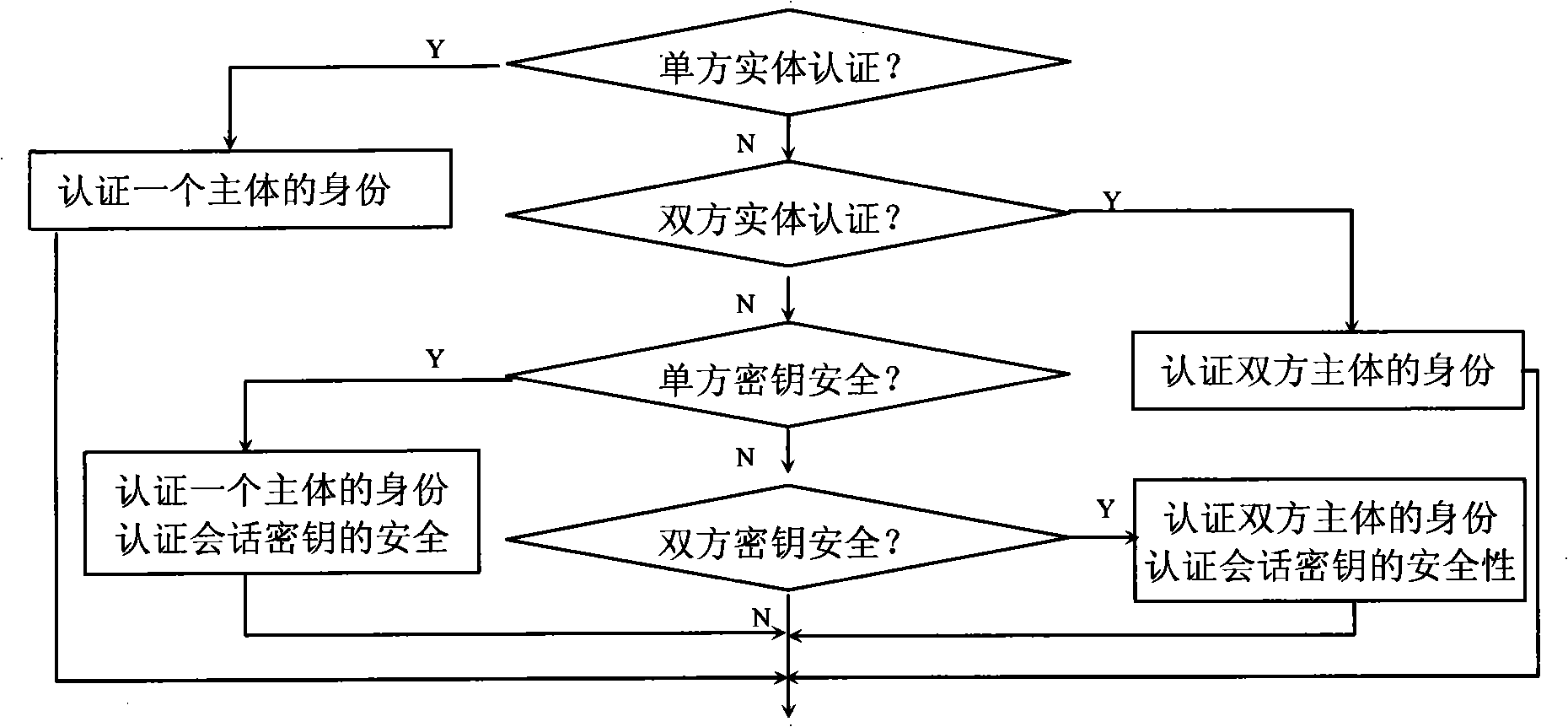
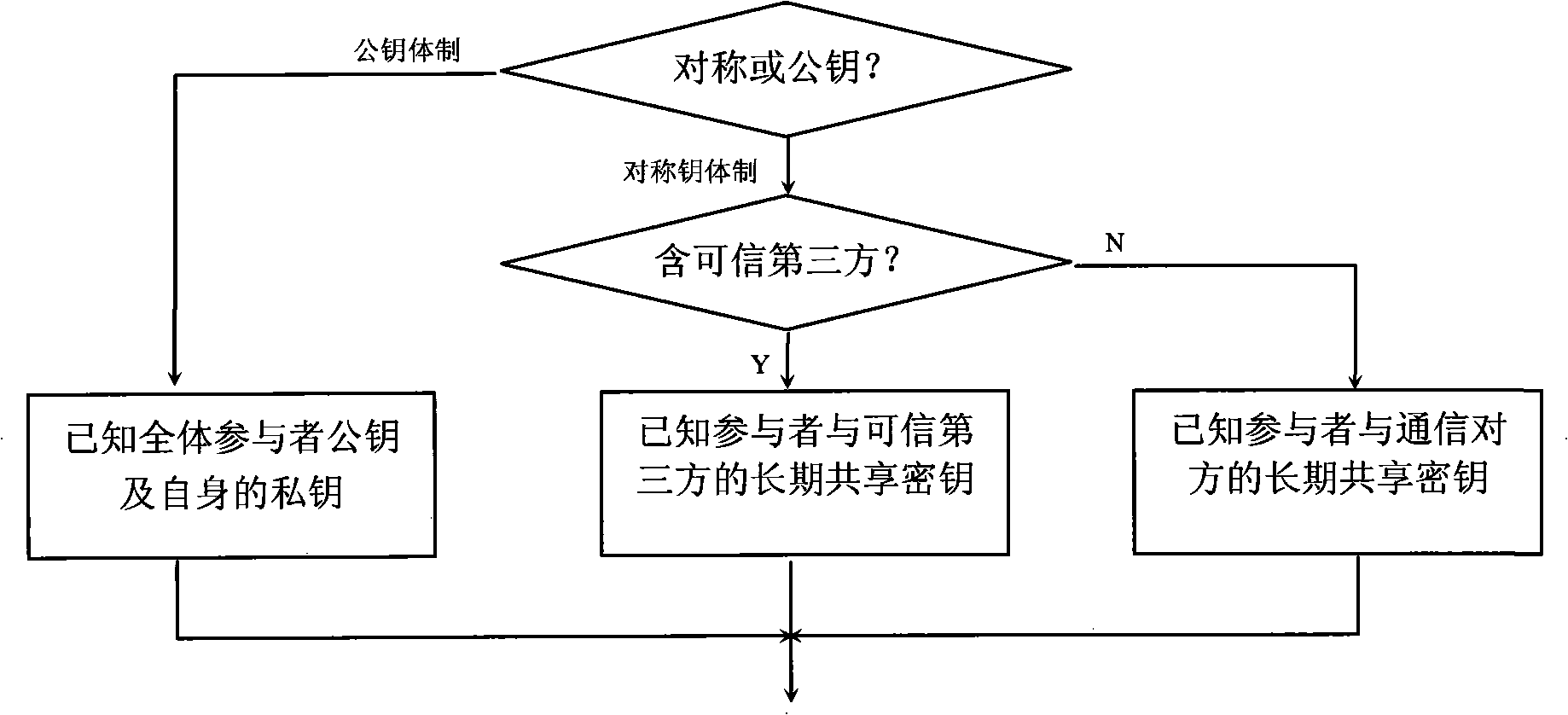
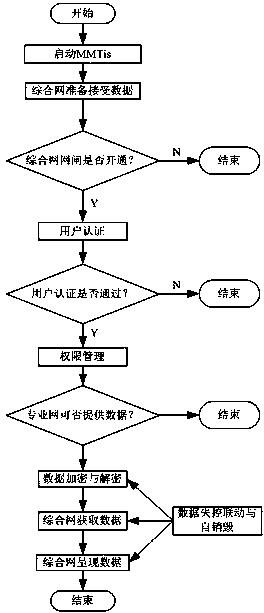
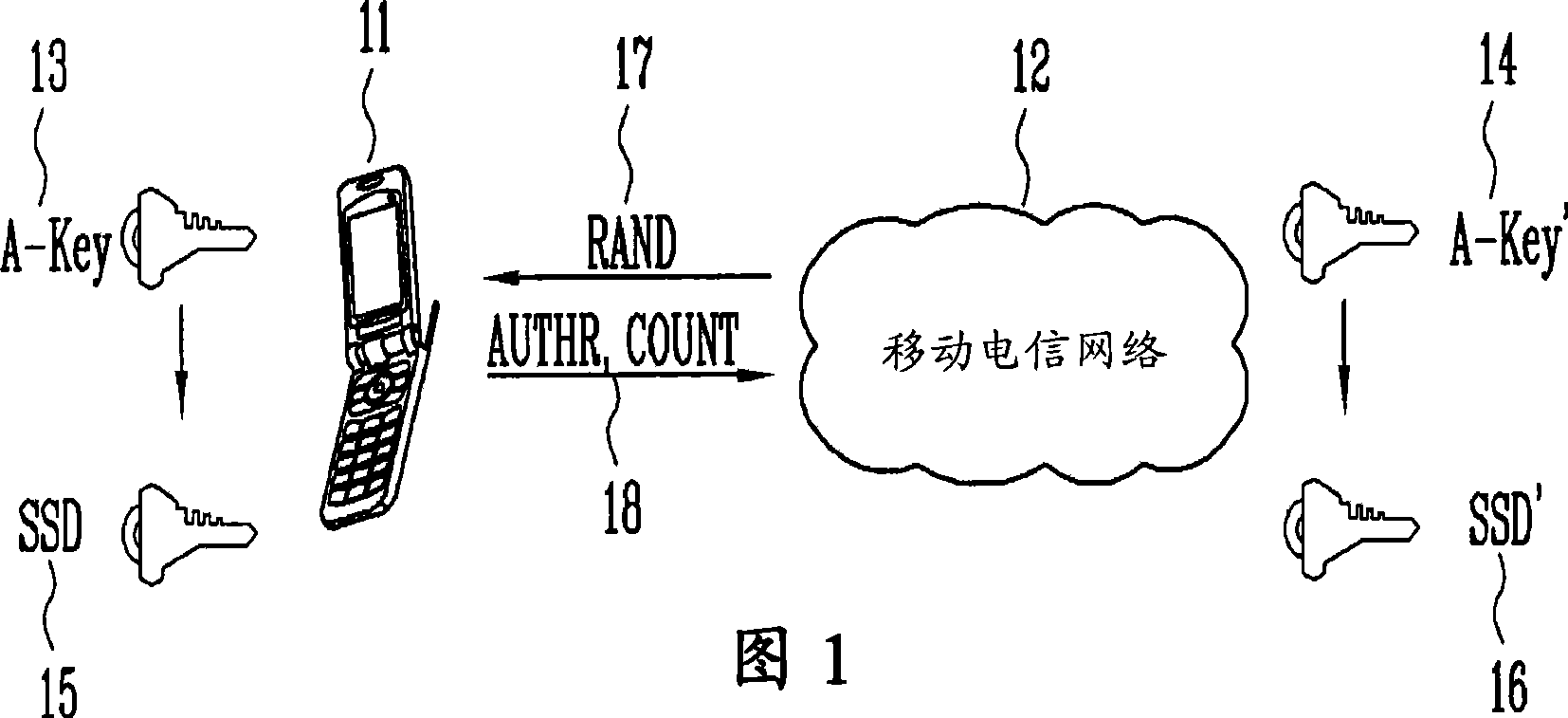
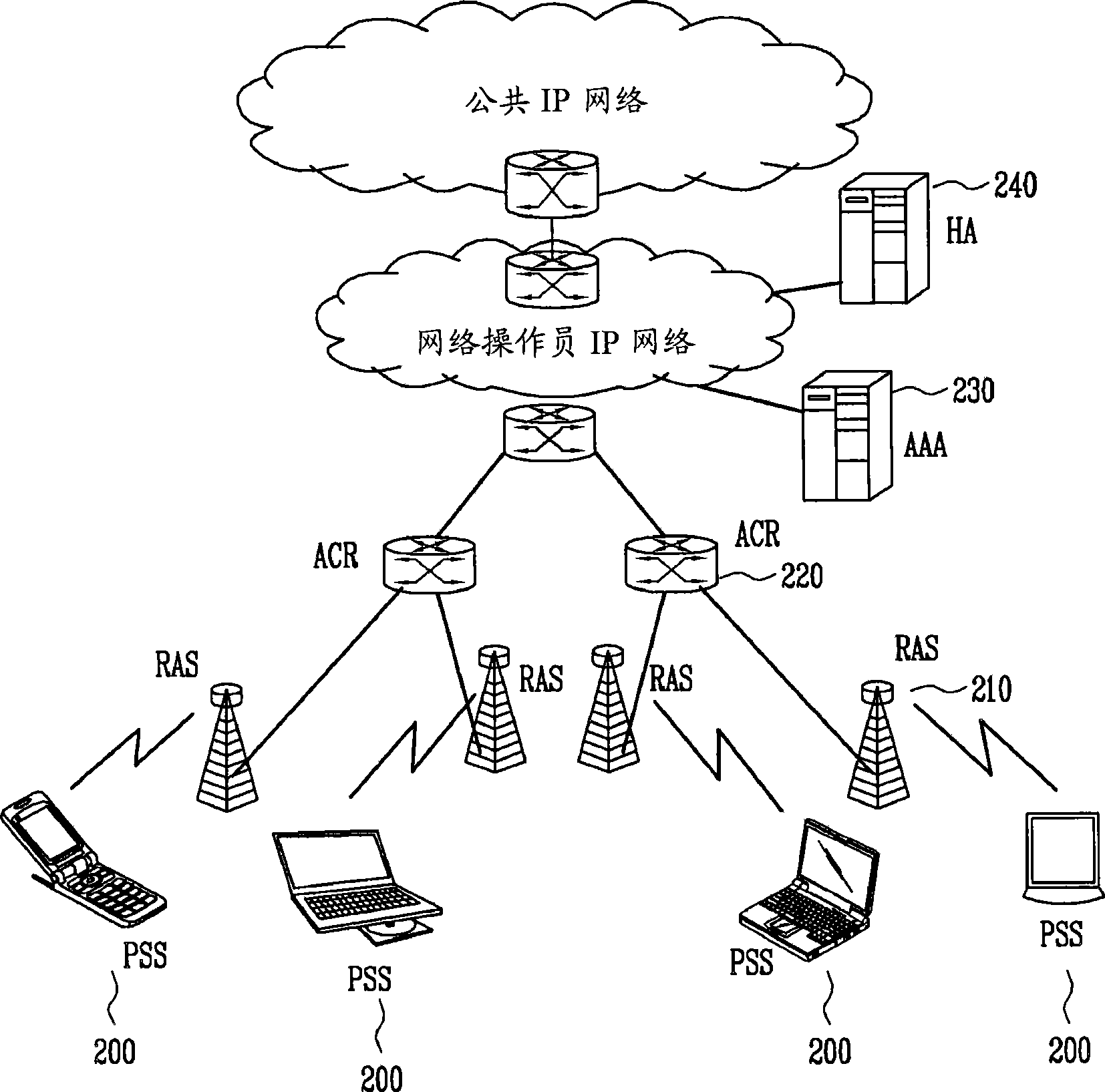
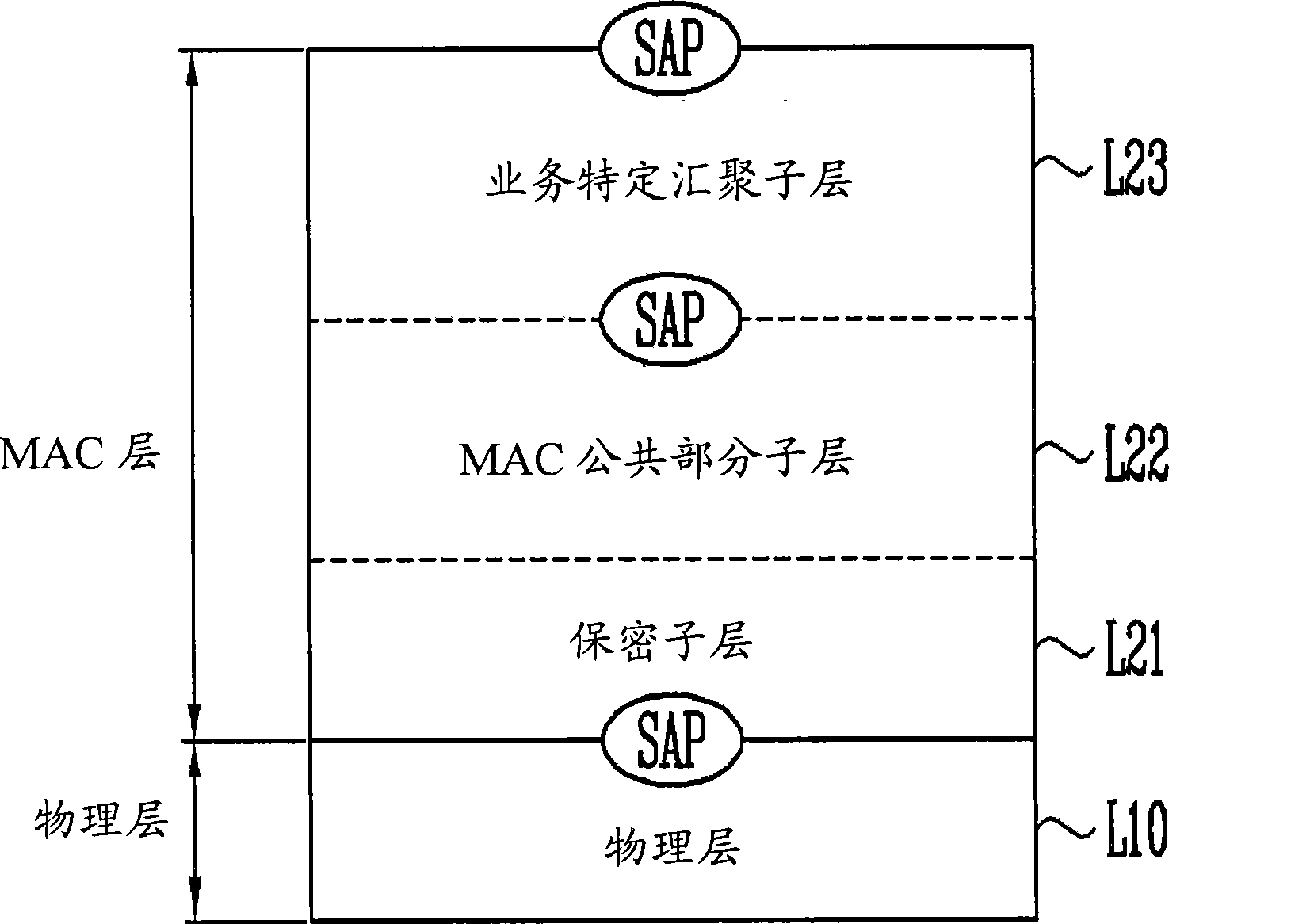
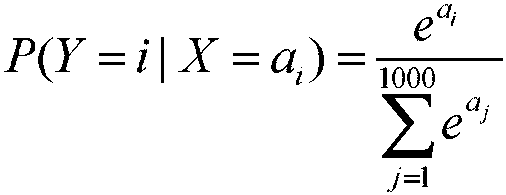Patents
Literature
41results about How to "Valid certification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
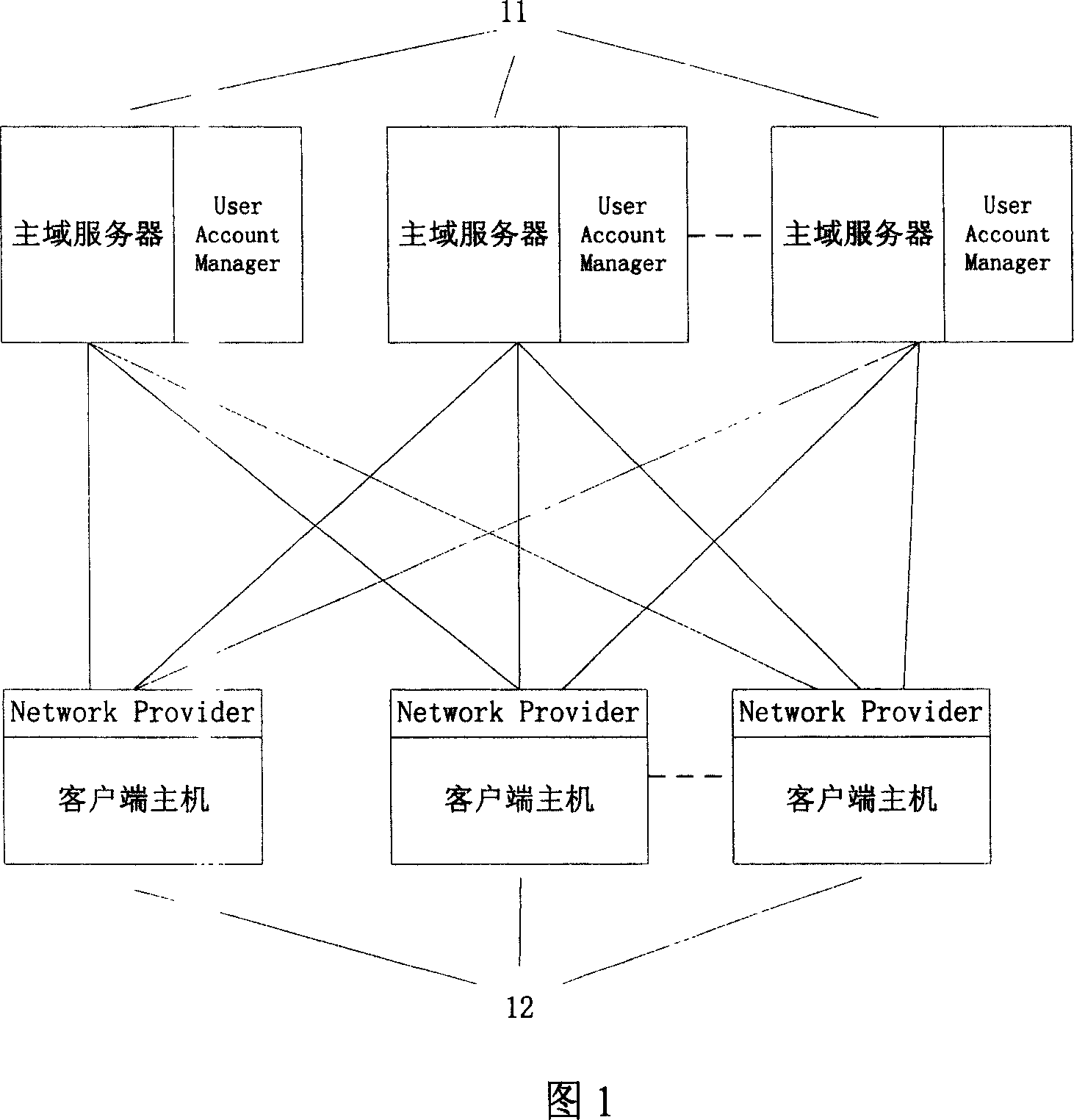
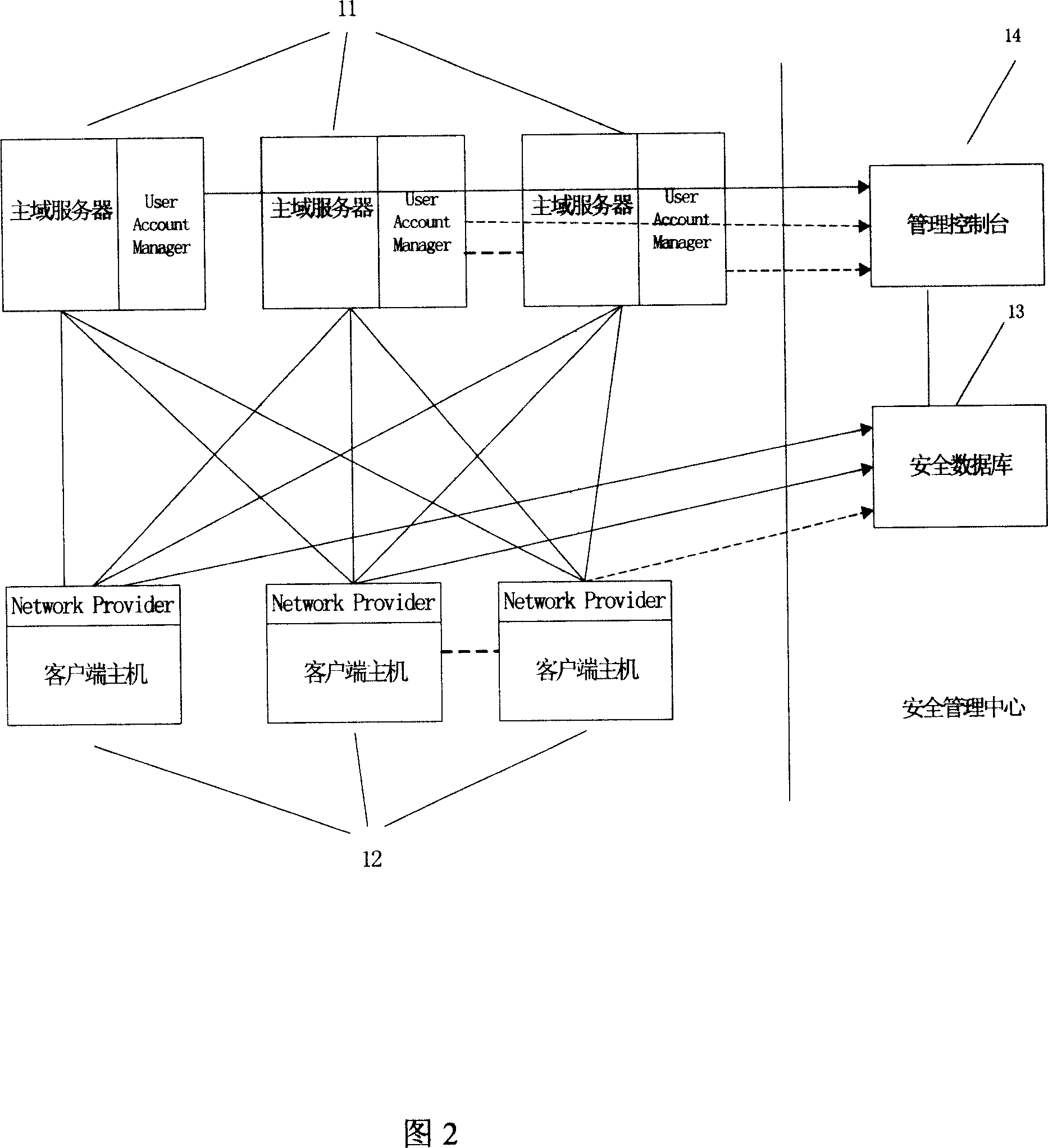
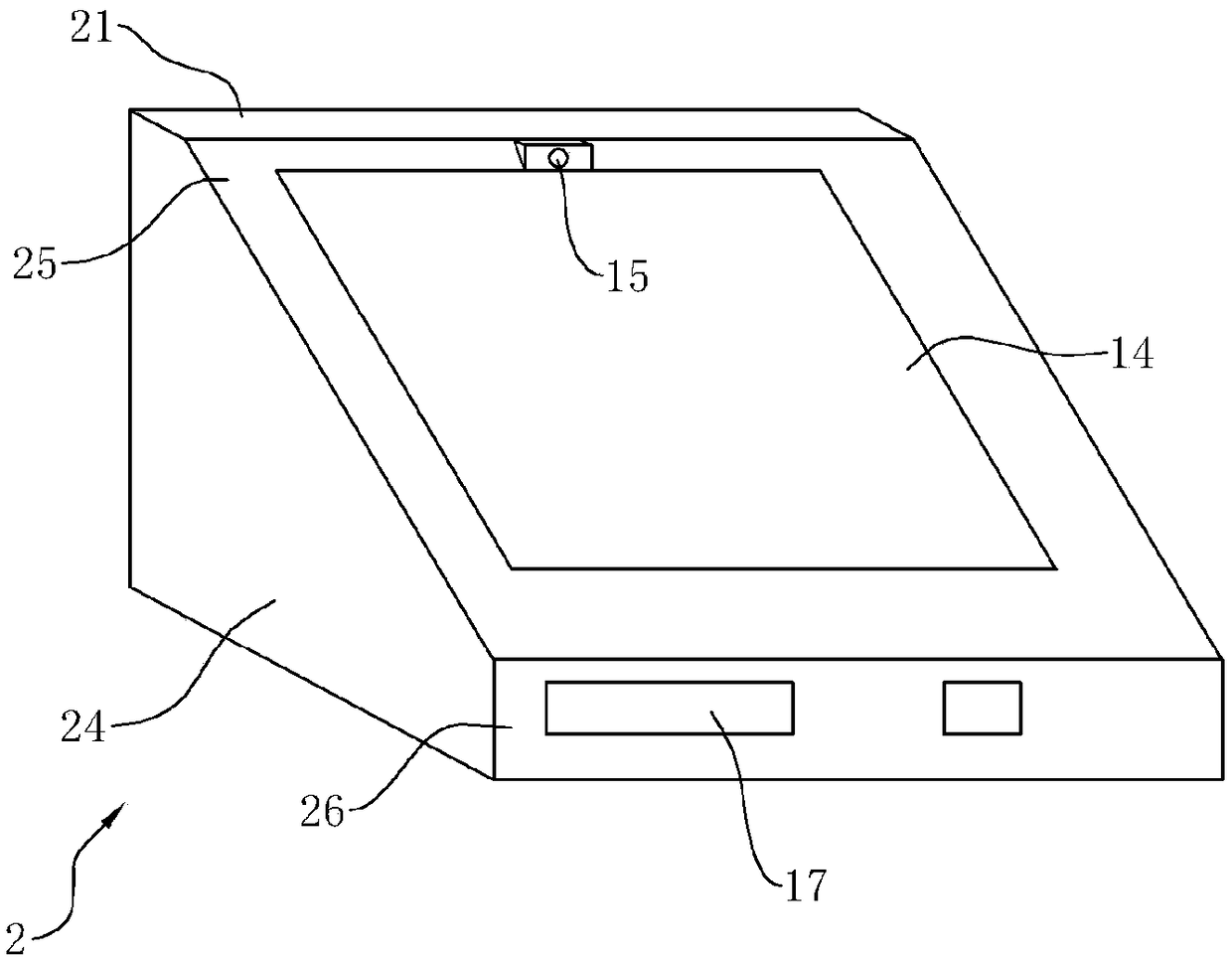
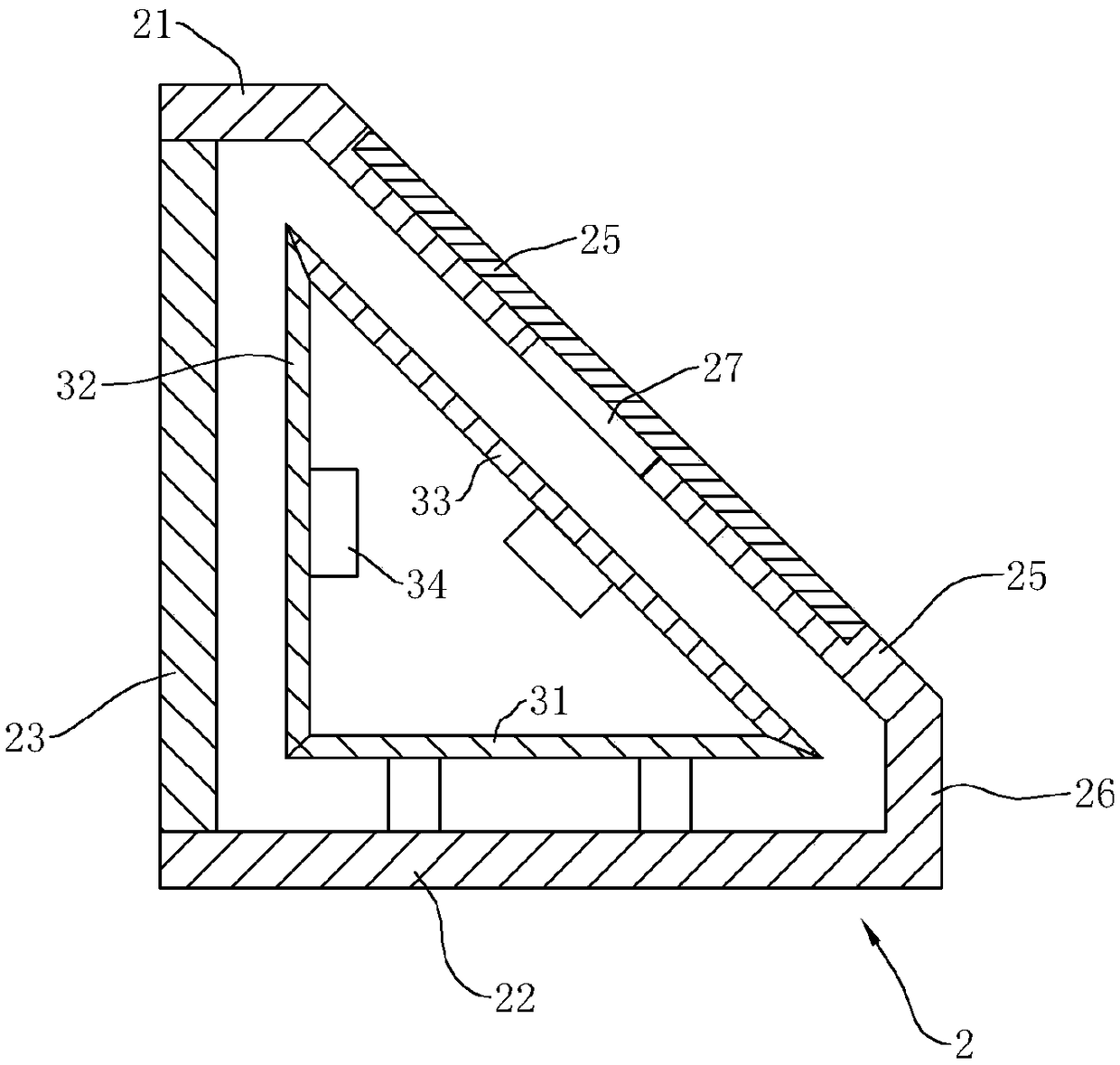
Novel express sending and receiving system
InactiveCN104850982AImprove qualityImprove resource utilizationLogisticsLogistics managementOperational costs
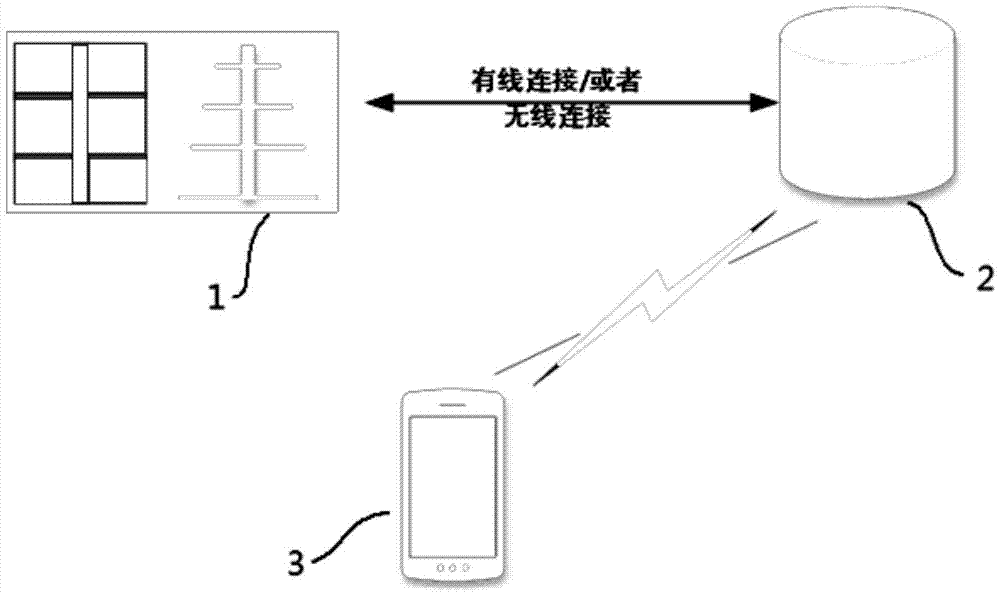
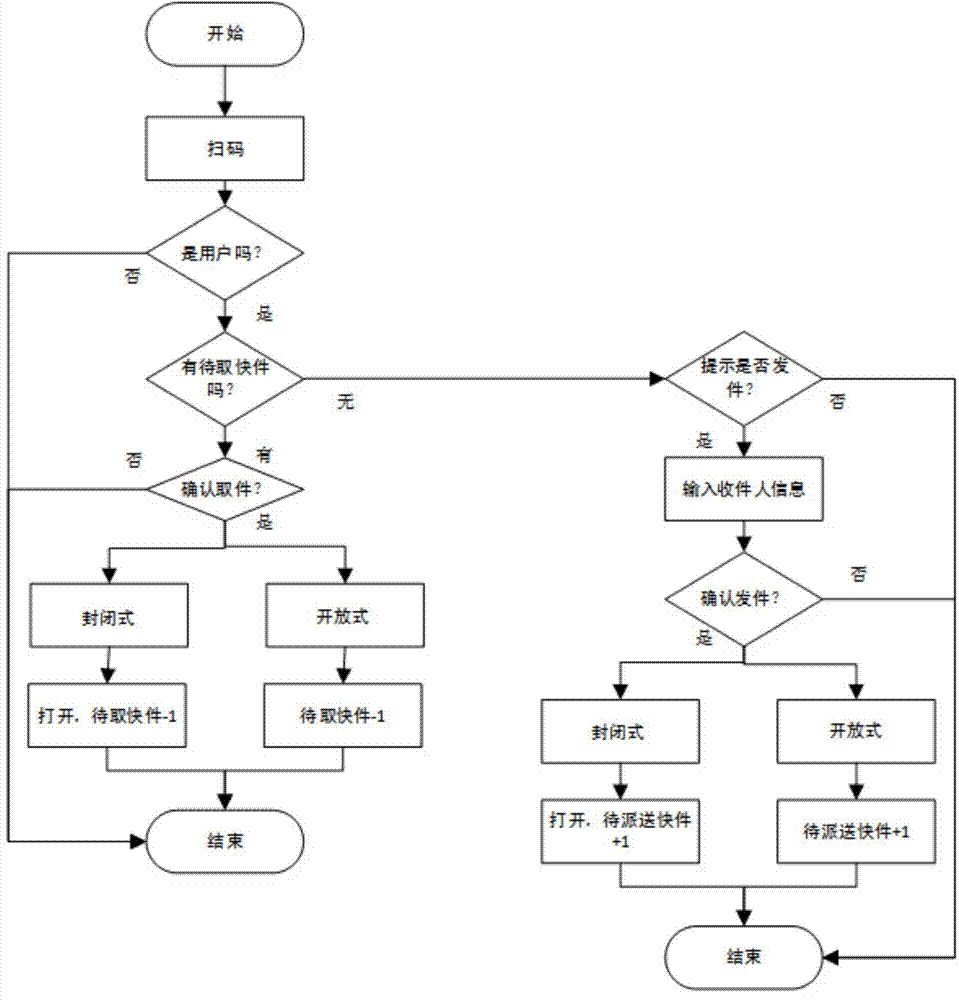
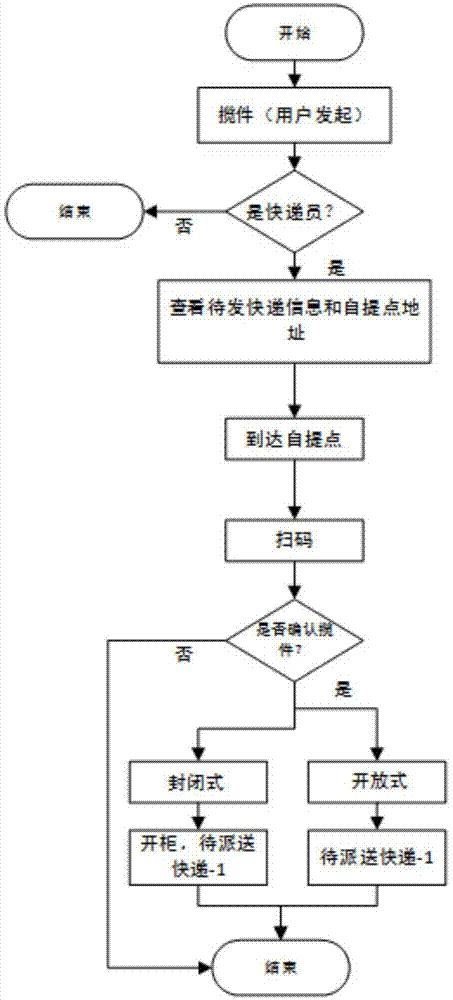
The invention relates to a novel express sending and receiving system, and the system comprises a self-fetching point, a hand-held intelligent terminal, and a background data server. The background data server is connected with the self-fetching point and the hand-held intelligent terminal through a network. The advantages of the system lie in that a self-fetching point system platform is deployed at a very low cost, and the system provides high-quality service; the system optimizes the utilization rate of resources, enables the functions of various types of convenience stores, exclusive shops and property management companies to be extended, enables all manpower to play a courier-like role, saves the social resources and logistics cost, and improves the efficiency; the system provides network authentication, achieves very quick and effective authentication, and saves the operation cost of an owner; the system provides a standard interface, thereby facilitating the concentration of other hardware providers, and achieving the purpose of saving cost.
Owner:吴方正
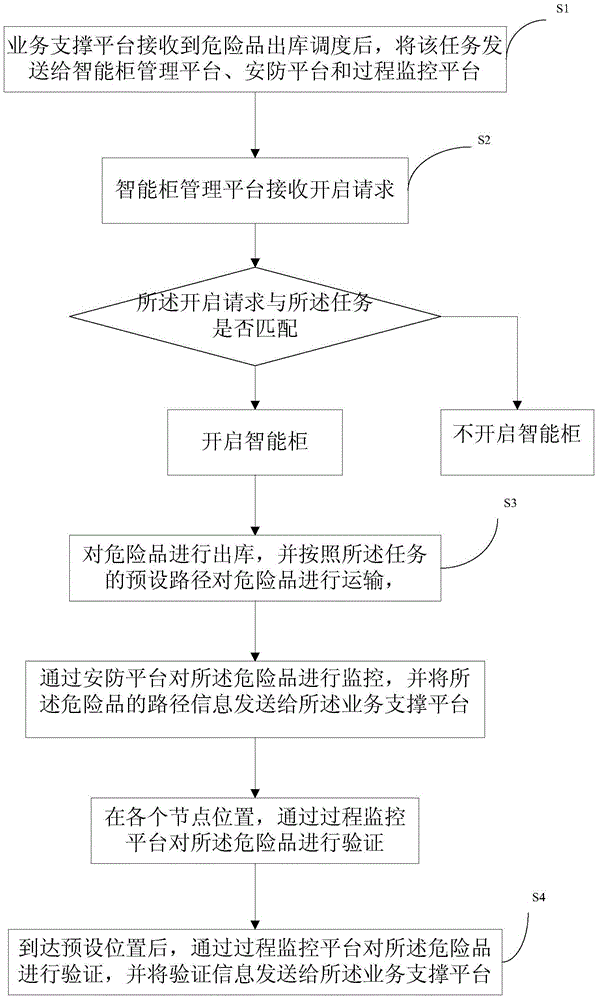
Hazardous material management system and method
InactiveCN105574700AImplement security managementImprove management levelLogisticsManagement systemSecurity management
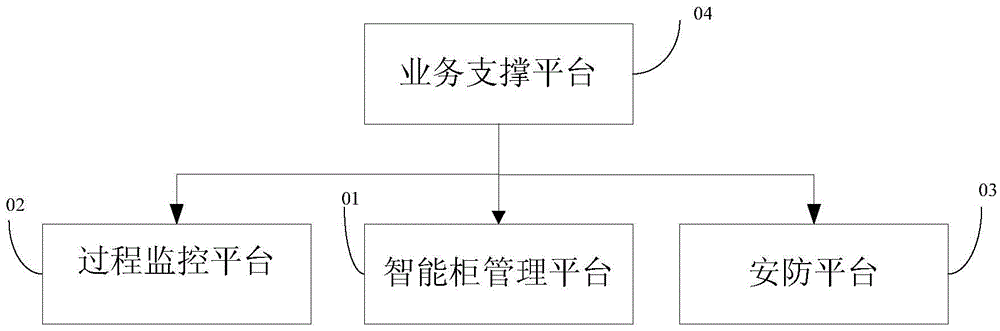
The invention provides a hazardous material management system and a method. The system comprises an intelligent cabinet management platform, a process monitoring platform, a security platform, and a business support platform, the intelligent cabinet management platform performs storage and storage management of the hazardous material, the security platform monitors the whole life cycle of the hazardous material, the hazardous material is verified in each important node via the process monitoring platform, and the business support platform receives data of the intelligent cabinet management platform, the process monitoring platform, and the security platform and manages the whole process of the hazardous material. According to the system and the method, the hazardous material is comprehensively managed in the whole life cycle, problems in any link can be monitored, the whole process of storage, usage, recycling, and management of the hazardous material in a plant area is effectively solved, comprehensive management is achieved, defects in the prior art are effectively overcome, and security management, process management, responsibility management, and tracking management of the hazardous material can be realized via an electronic monitoring method.
Owner:FOUNDER BROADBAND NETWORK SERVICE
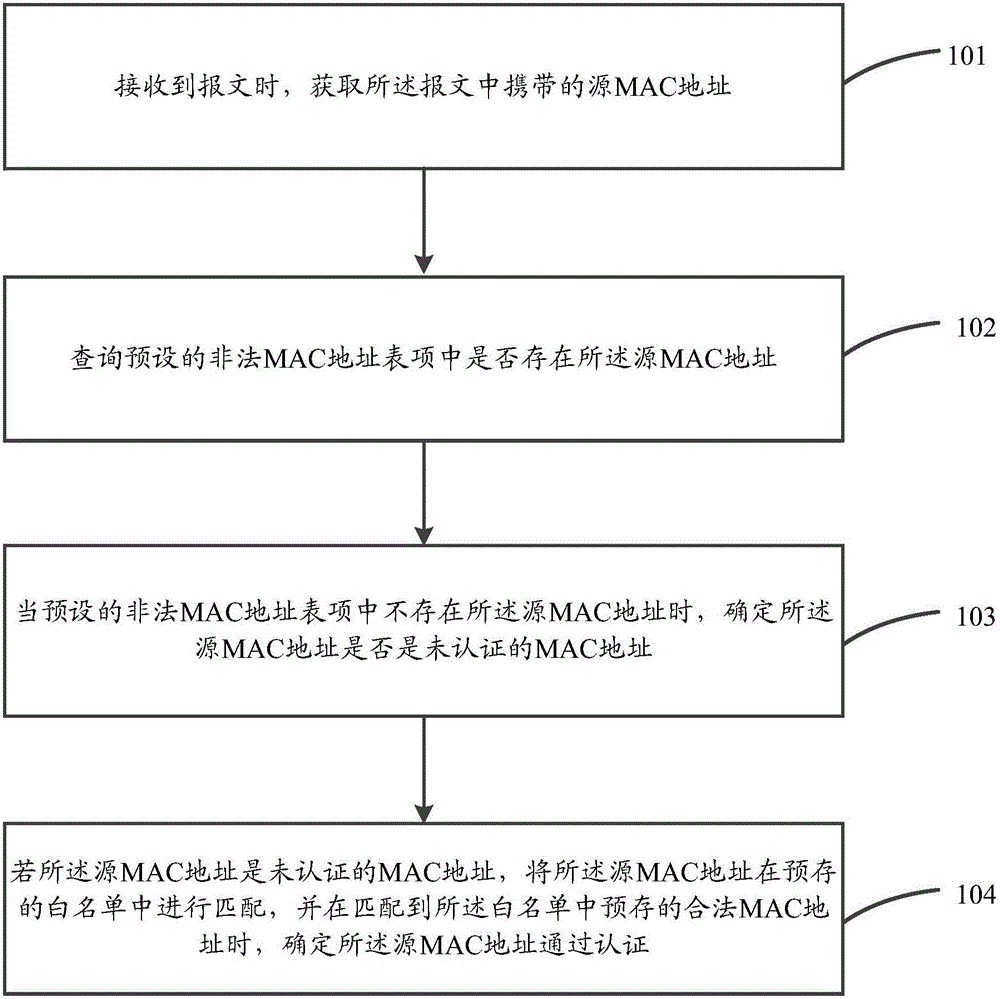
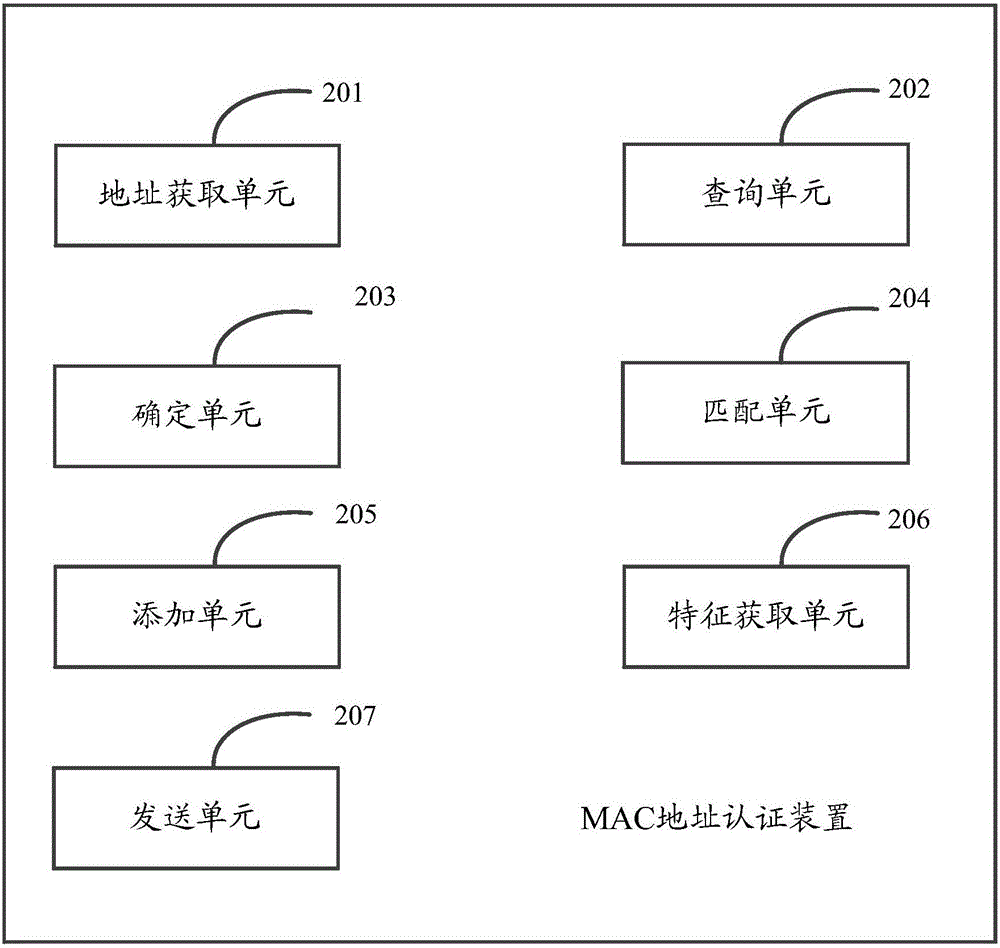
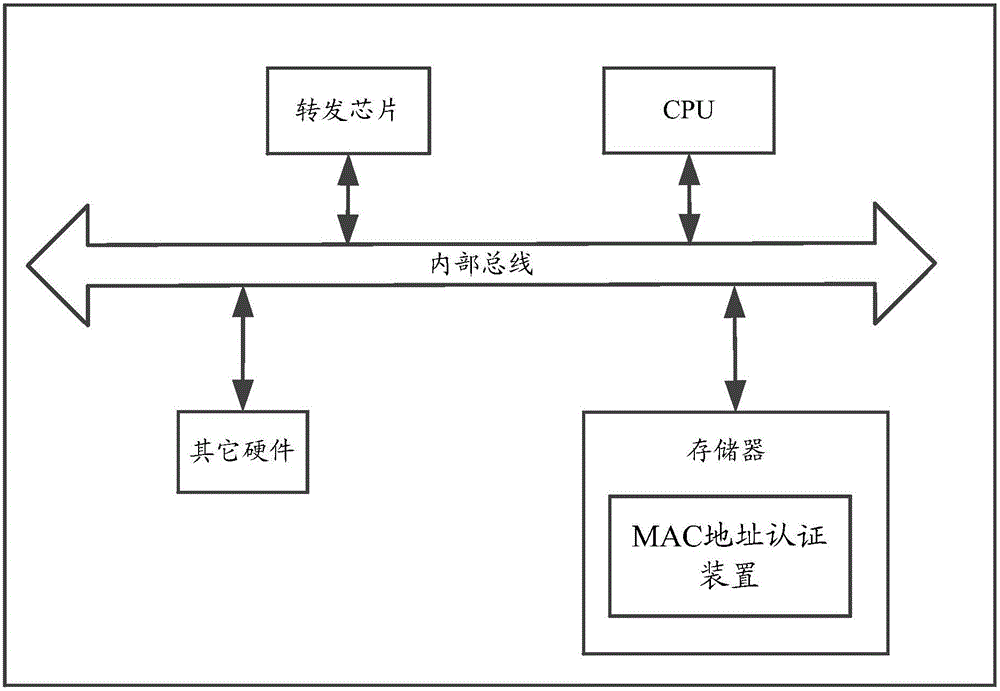
MAC address authentication method and apparatus
ActiveCN105939348AValid certificationAvoid attackClosed circuit television systemsTransmissionTraffic capacityUser authentication
The invention provides an MAC address authentication method and apparatus. The method comprises the following steps: when a message is received, obtaining a source MAC address carried by in the message; querying whether the source MAC address is present in a preset illegal MAC address table entry; if not, determining the source MAC address as an unauthenticated MAC address; if the source MAC address is the unauthenticated MAC address, matching the source MAC address in a pre-stored white list, and determining that the source MAC address is authenticated, when a pre-stored legal MAC address is matched in the white list. By adopting the invention, the processing pressure on a core switch can be reduced, and the overall processing efficiency is improved. According to the invention, effective user authentication can be provided for providing a network environment with better quality and higher efficiency for the transmission of video traffic, and network attacks can be blocked to improve the network security.
Owner:HANGZHOU DPTECH TECH
Method for identification of equipment validity
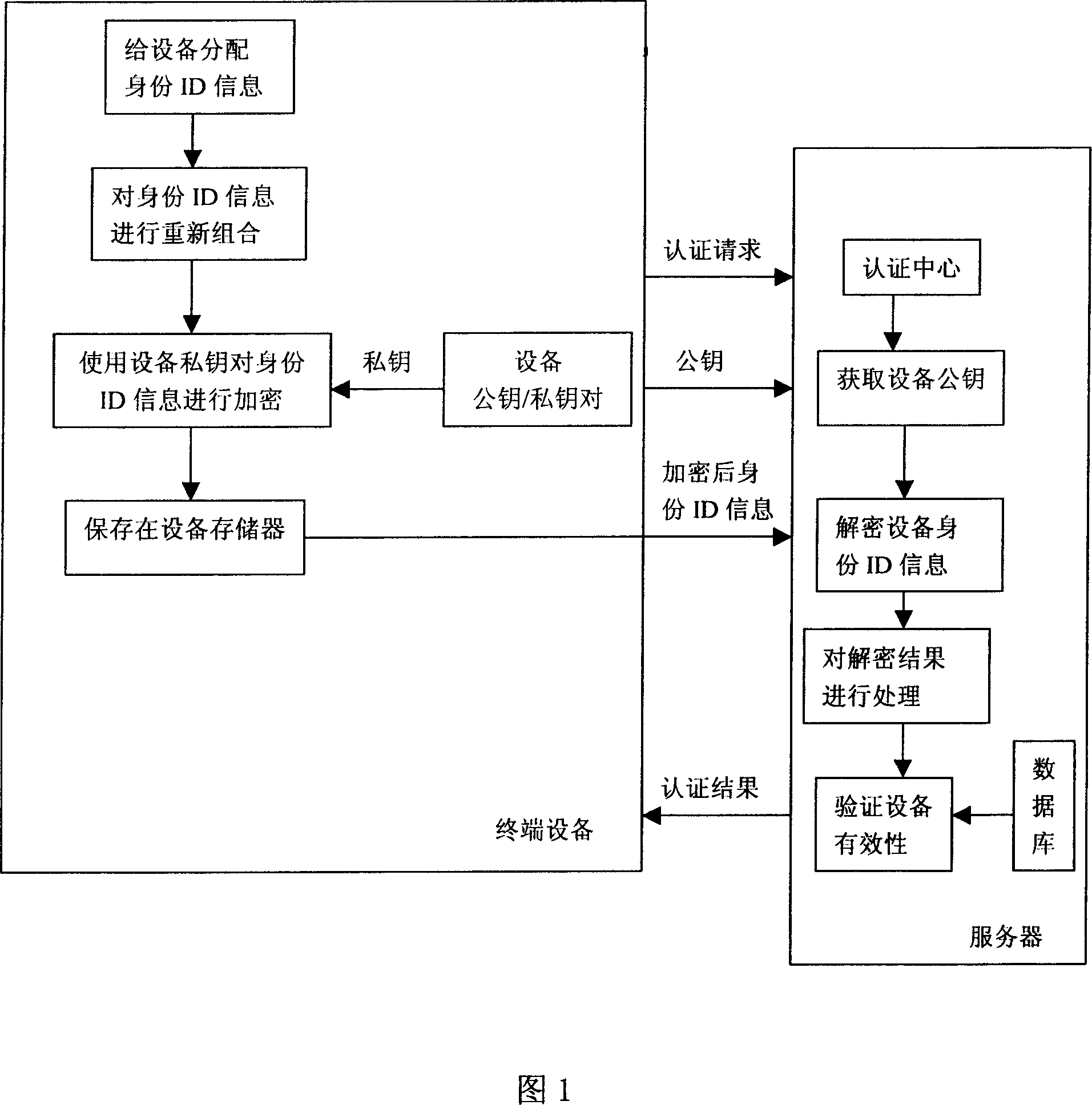
InactiveCN1925392AValid certificationIncrease the difficultyUser identity/authority verificationValidation methodsComputer science
This invention relates to digital copyright management system device legal identification or validation method and provides one device legal identification method, which comprises the following steps: a, device recodes original identification information to generate ID information; b, coding the ID information and then storing device memory; c, servo reading coded ID information to decode ID; d, servo restores codes identification; e, identifying servo ID information.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
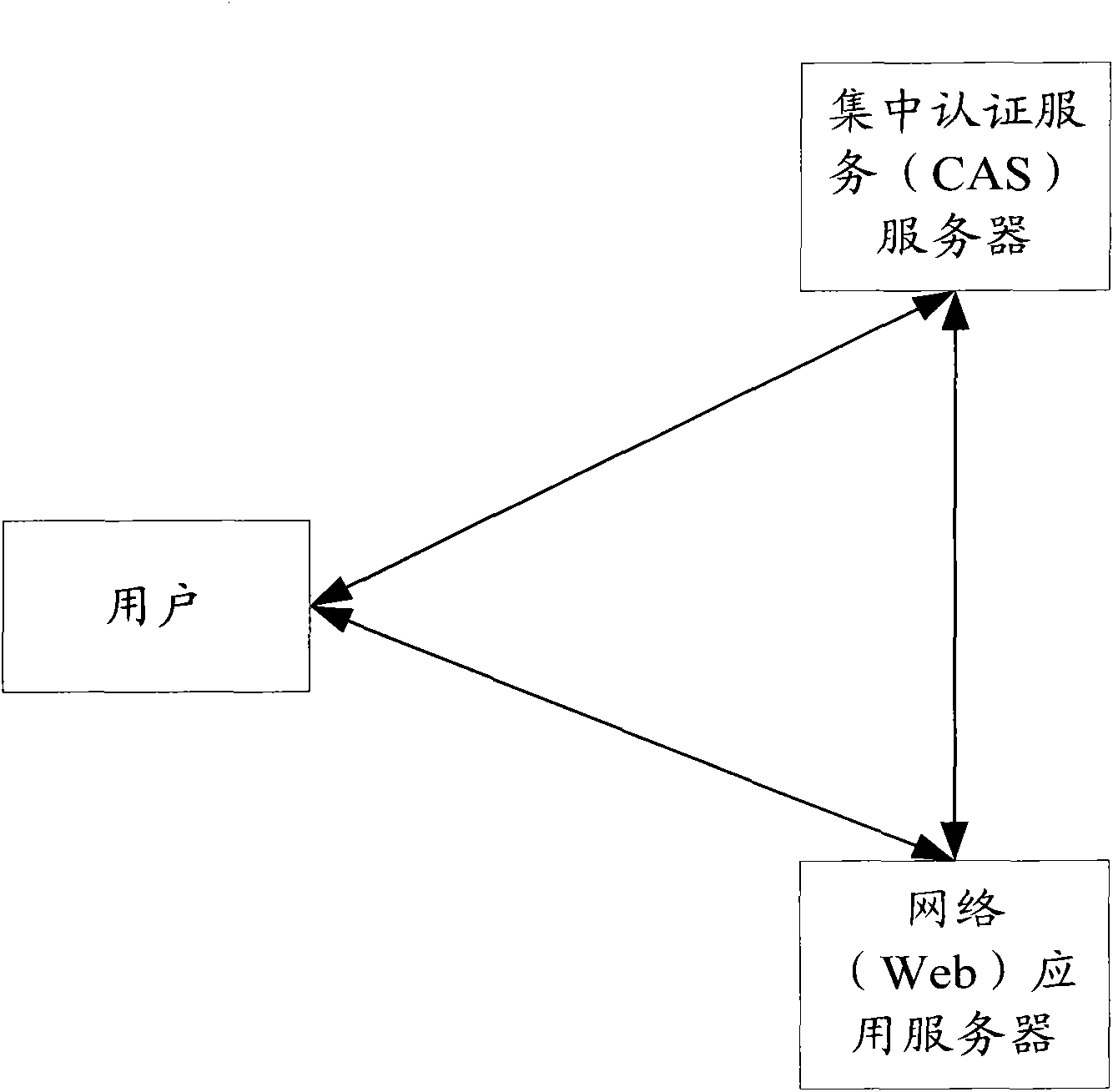
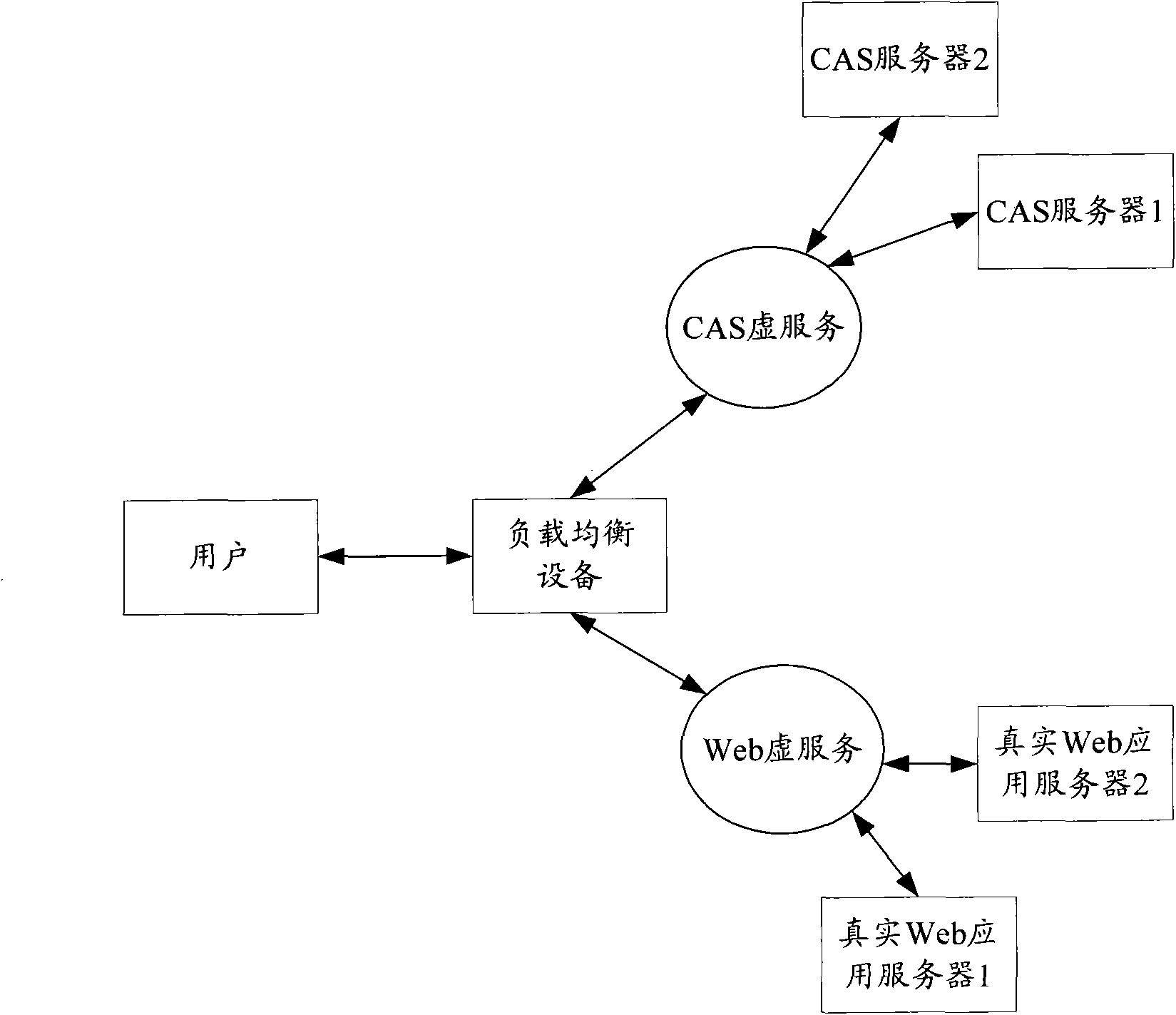
Single sign-on method, system and load balancing equipment based on load balance
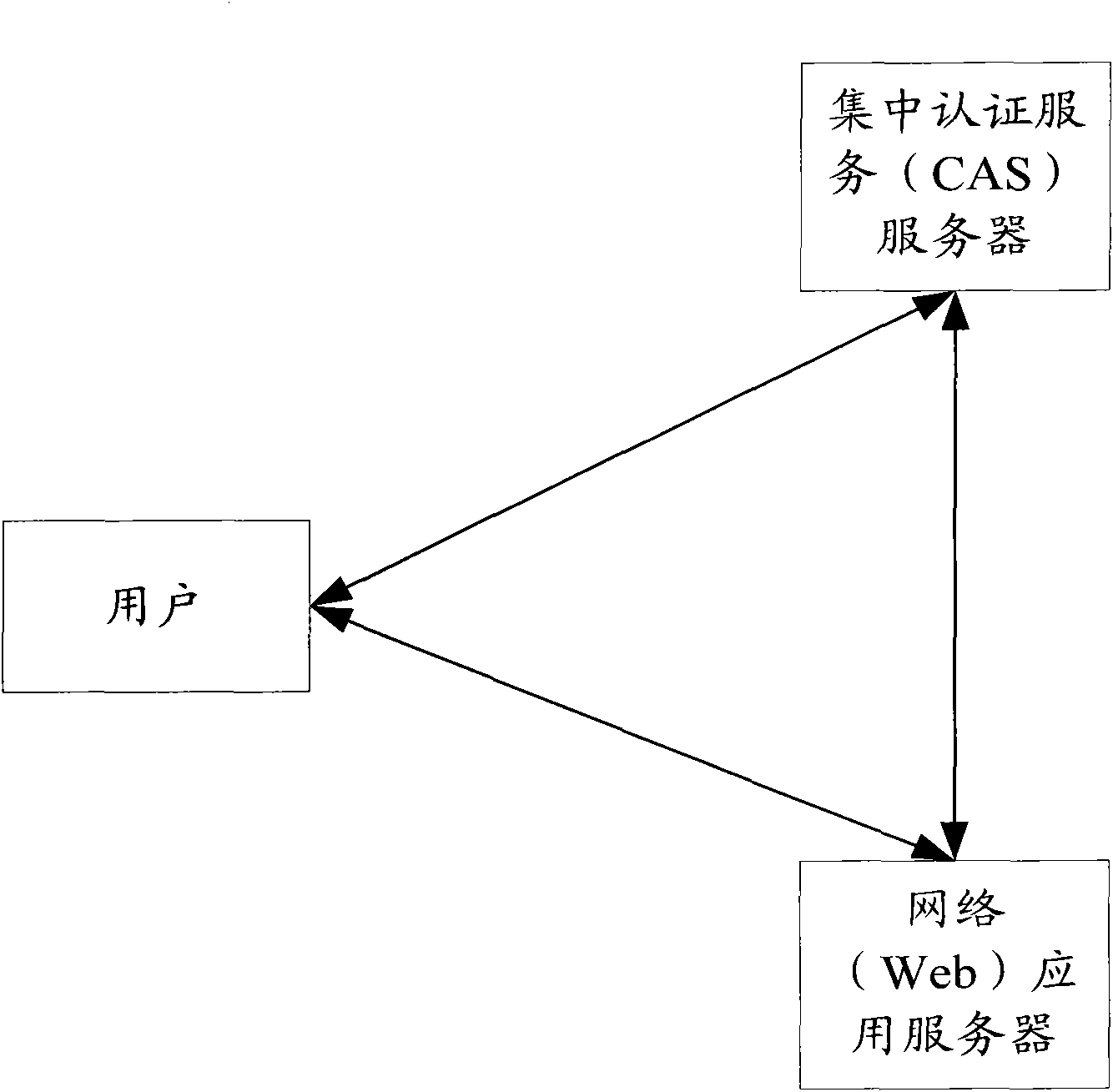
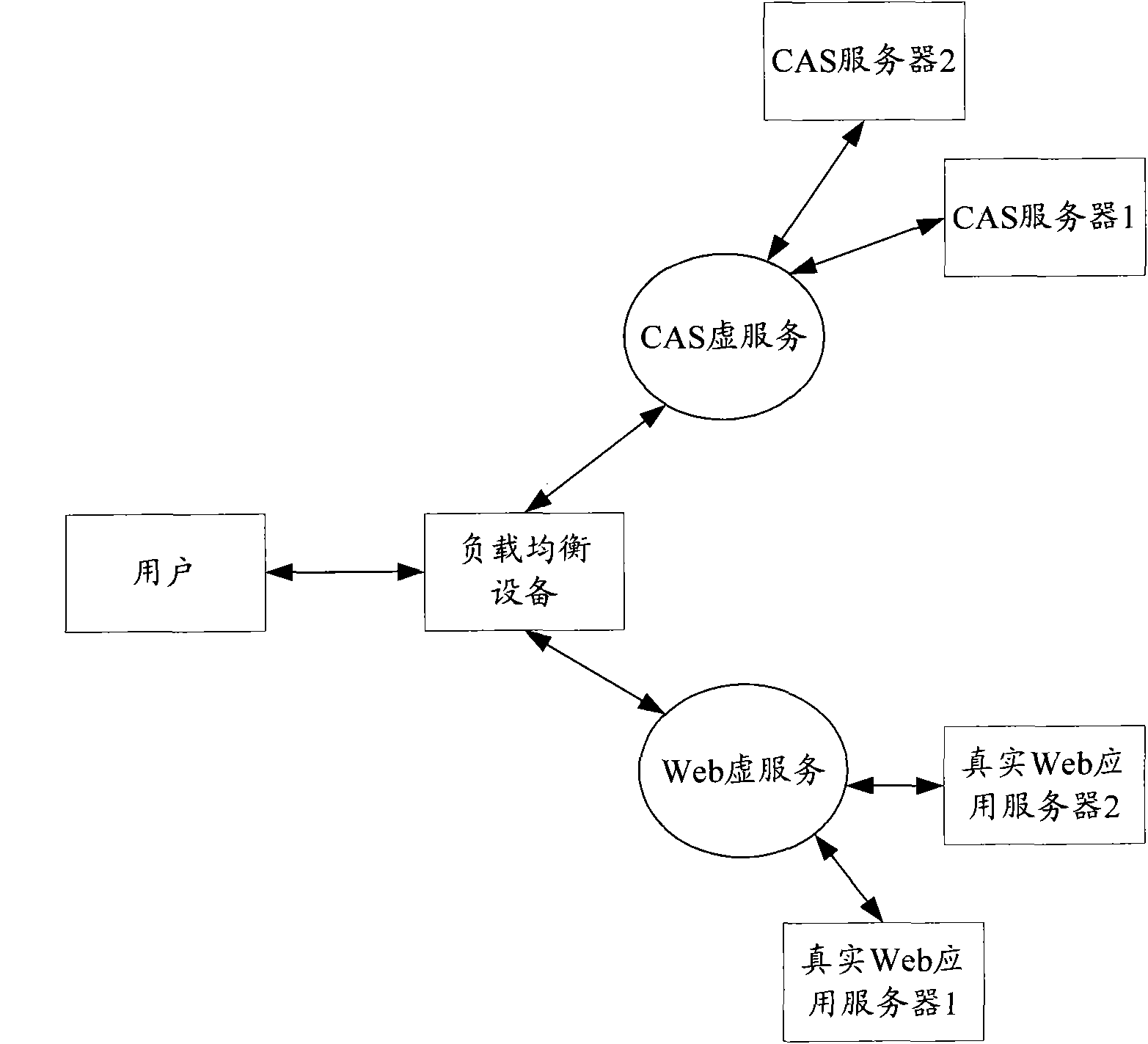
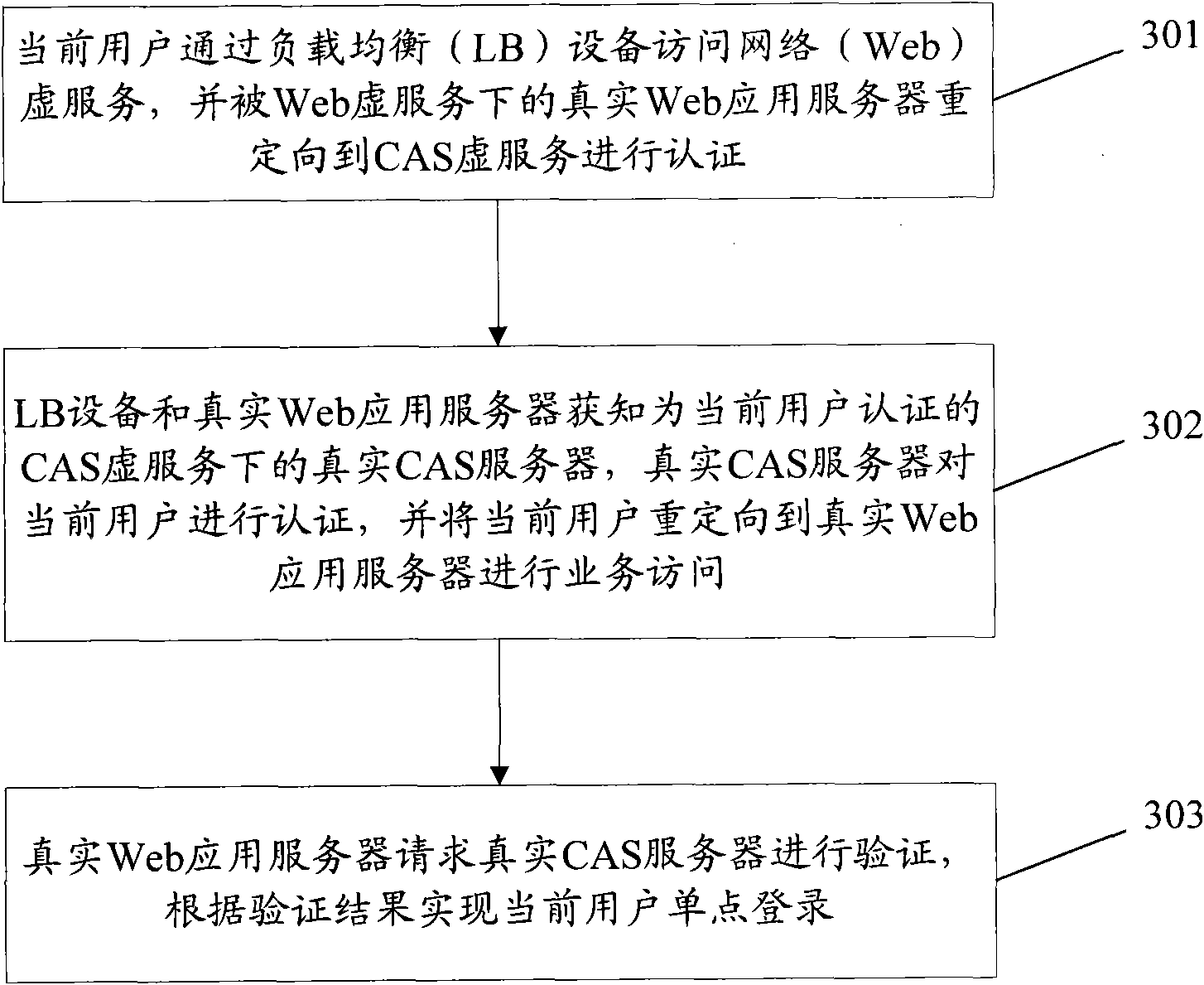
ActiveCN102104483AValid certificationImplement "sticky" accessUser identity/authority verificationWeb applicationDistributed computing
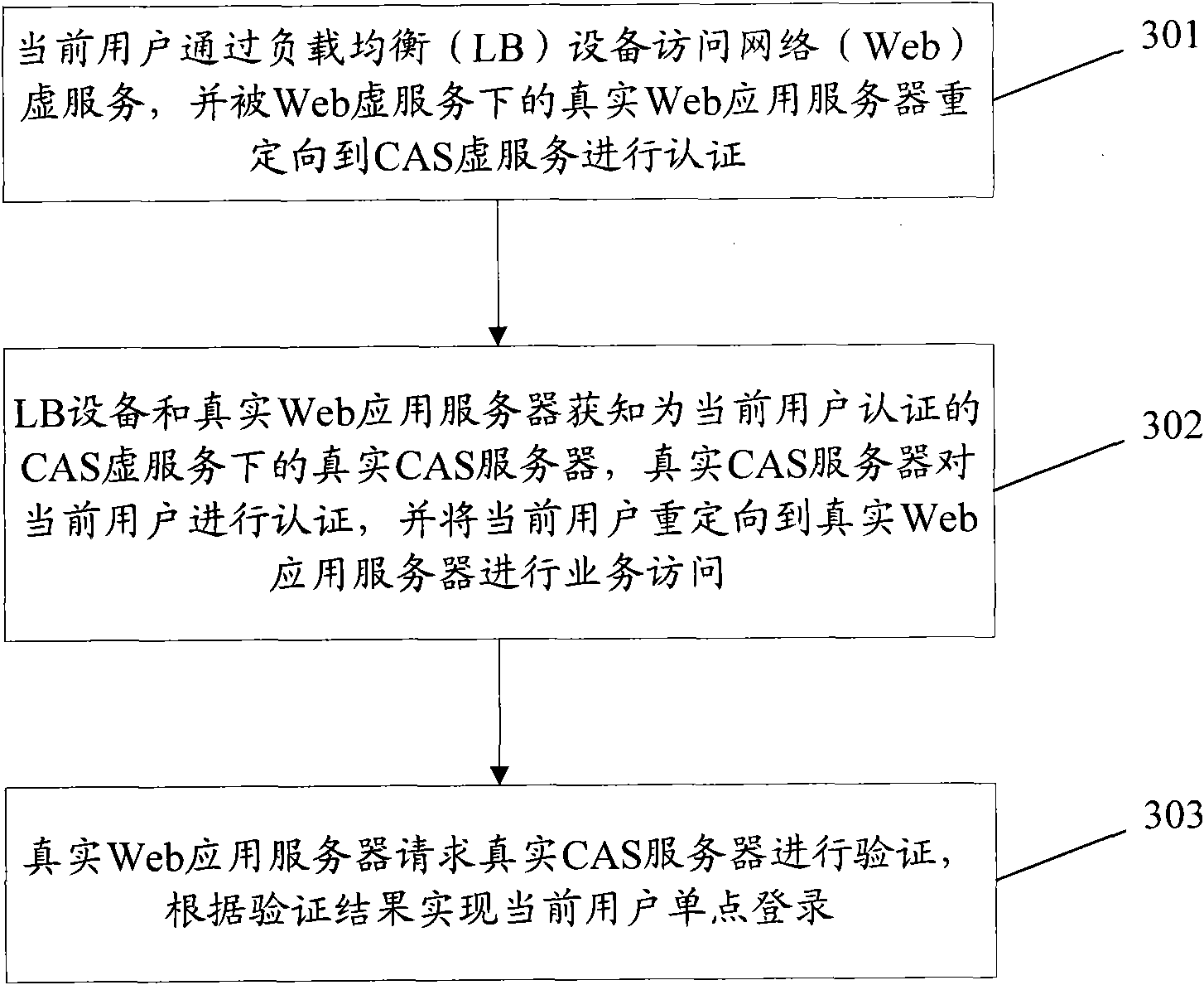
The invention provides a single sign-on method, system and load balancing equipment based on load balance, wherein a current user accesses a Web virtual server by load balancing (LB) equipment, and a real Web application server under the Web virtual server redirects the user to a centralized authentication service (CAS) virtual server for authentication; the LB equipment and the real Web application server obtain a real CAS server which authenticates the current user and redirects the current user to the Web virtual server for service access; and the real Web application server under the Web virtual server requests the real CAS server to perform verification, and realizes the single sign-on of the current user according the verification result. By the scheme provided by the invention, thecurrent user and the real Web application server both can accurately access the real CAS server which is in charge of the authentication of the current user, so that viscous access is realized, and the effective authentication and sign-on of users are ensured.
Owner:NEW H3C TECH CO LTD
Method and device for embedding watermarking information and method and device for authenticating watermarking information
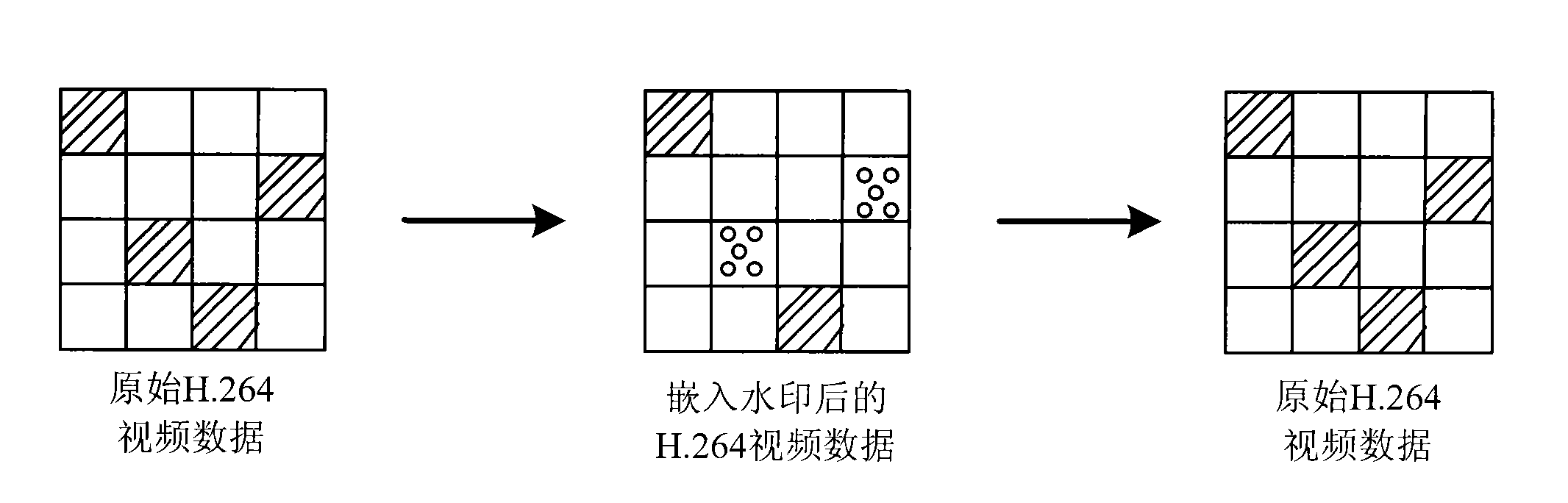
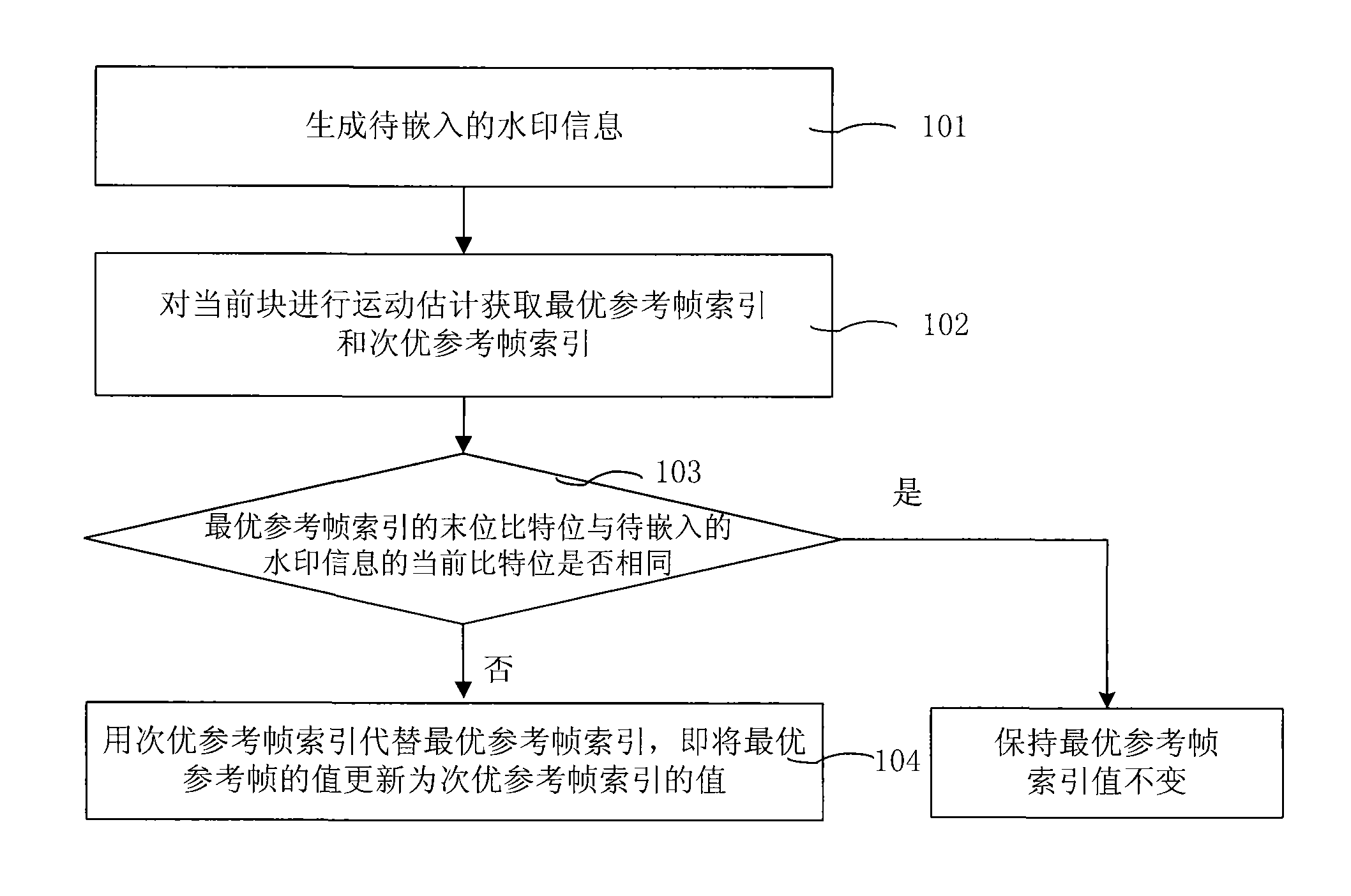
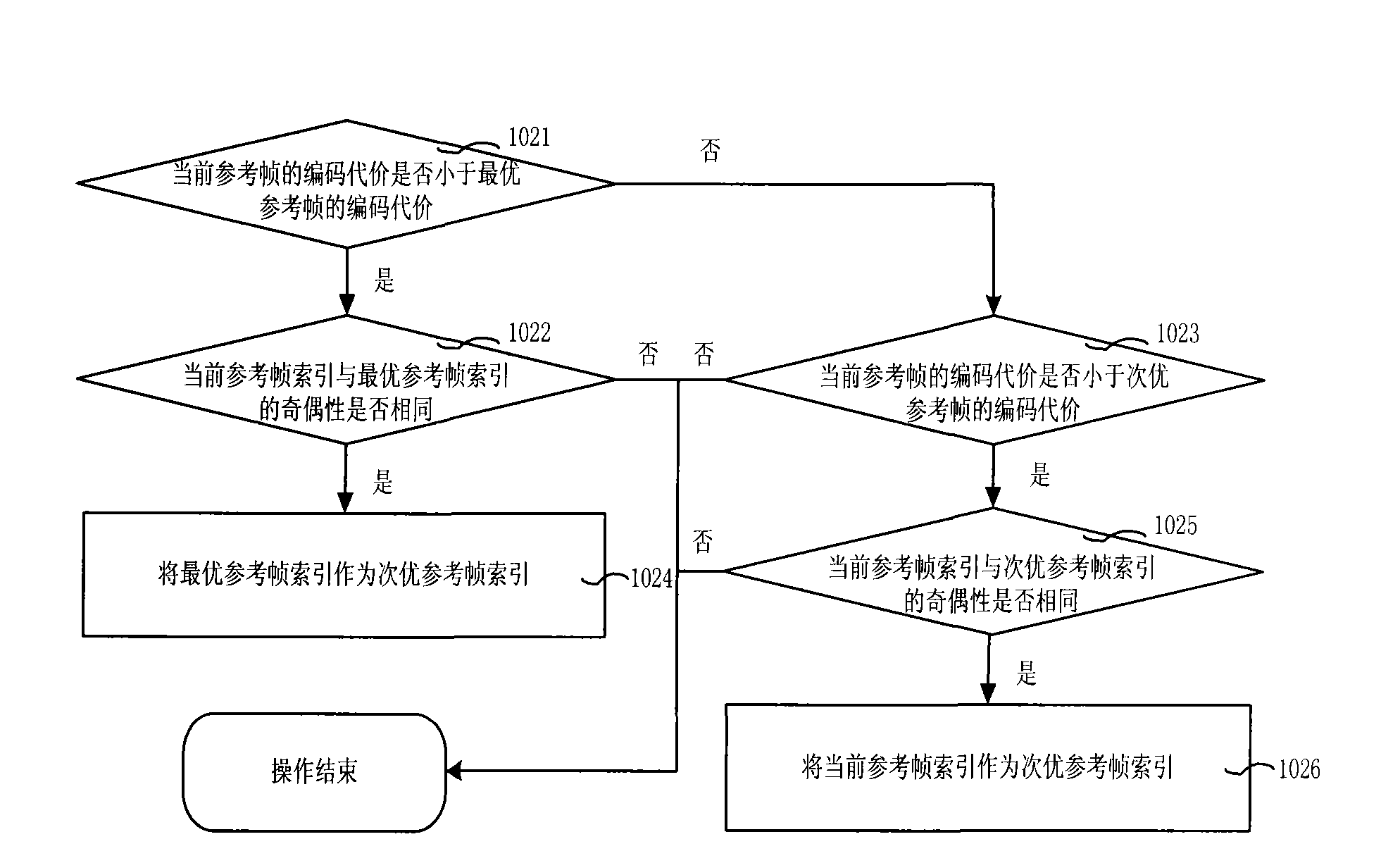
InactiveCN101527830ANo tamperingValid certificationPulse modulation television signal transmissionImage data processing detailsVideo qualityComputer science
The embodiment of the invention relates to a method and a device for embedding watermarking information and a method and a device for authenticating the watermarking information. The method for embedding the watermarking information comprises the following steps: generating watermarking information to be embedded; acquiring a reference frame index of a current macro block in video data; and embedding the watermarking information into the reference frame index. The method and the device for embedding the watermarking information and the method and the device for authenticating the watermarking information can better utilize the watermarking information to protect and authenticate video content, are easy to realize, and have little influence on video quality.
Owner:HUAWEI TECH CO LTD +1
User authentication method and device
ActiveCN103888436AValid certificationAvoid the risk of certification failureUser identity/authority verificationDigital data authenticationPasswordUser authentication
The invention relates to a user authentication method and device. According to the embodiment of the invention, information related to authentication is coded in an image of a two-dimensional code and the like. The image information and other authentication information are transmitted and decoded between one or more devices of a user and an authentication server, thus the authentication server can effectively authenticate the devices used by the user and the user, and at the same time authentication failure risk caused by password leakage in the prior art is avoided. According to the embodiment of the invention, the method and the device can be combined with the existing static password and / or dynamic password authentication, and have good compatibility.
Owner:EMC IP HLDG CO LLC
Third-party effective identity escrow agile authentication access mode based on account concealment
ActiveCN108989346AGuaranteed hands-onGuarantee safe and effectiveTransmissionThird partyInternet Authentication Service
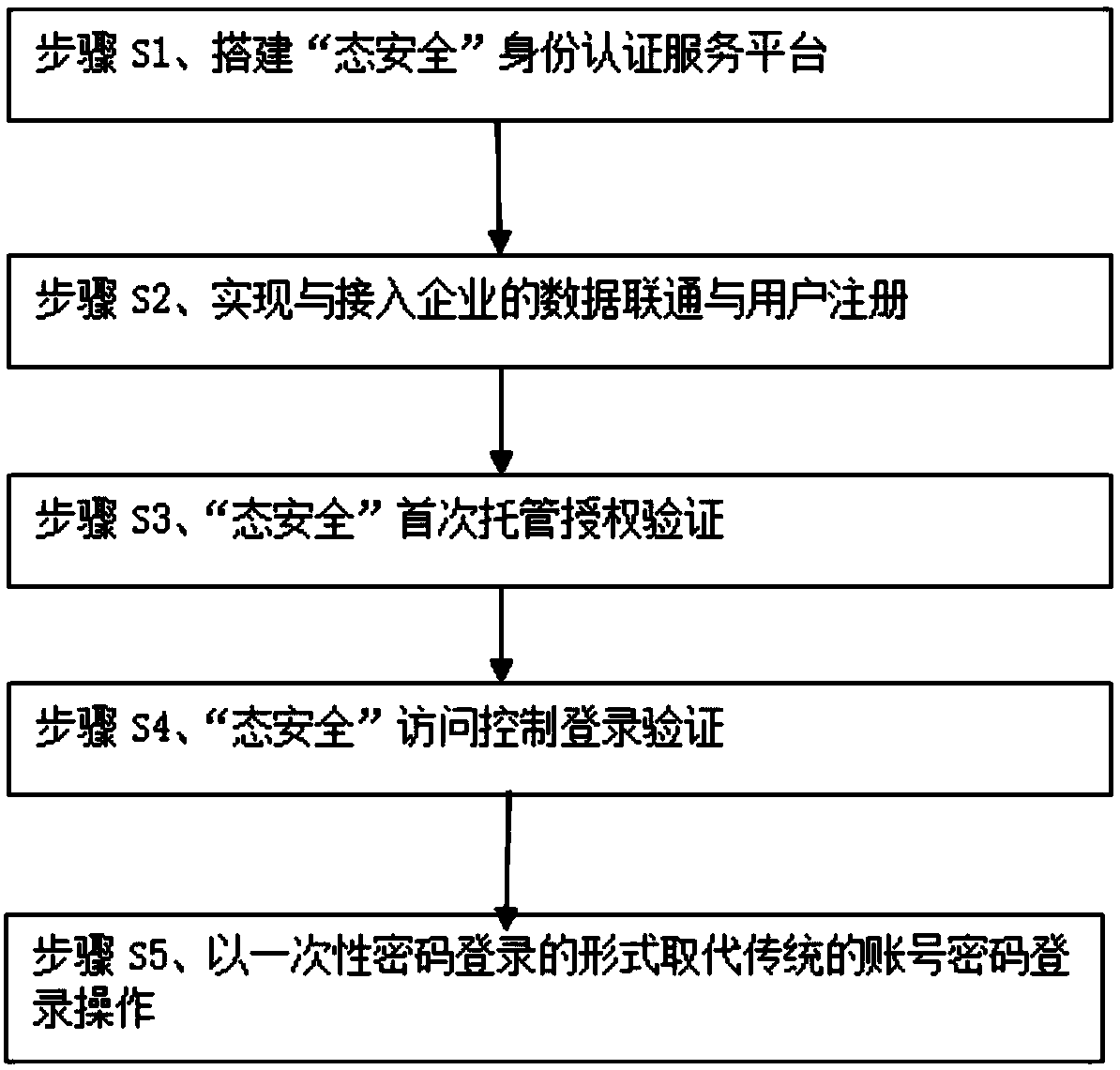
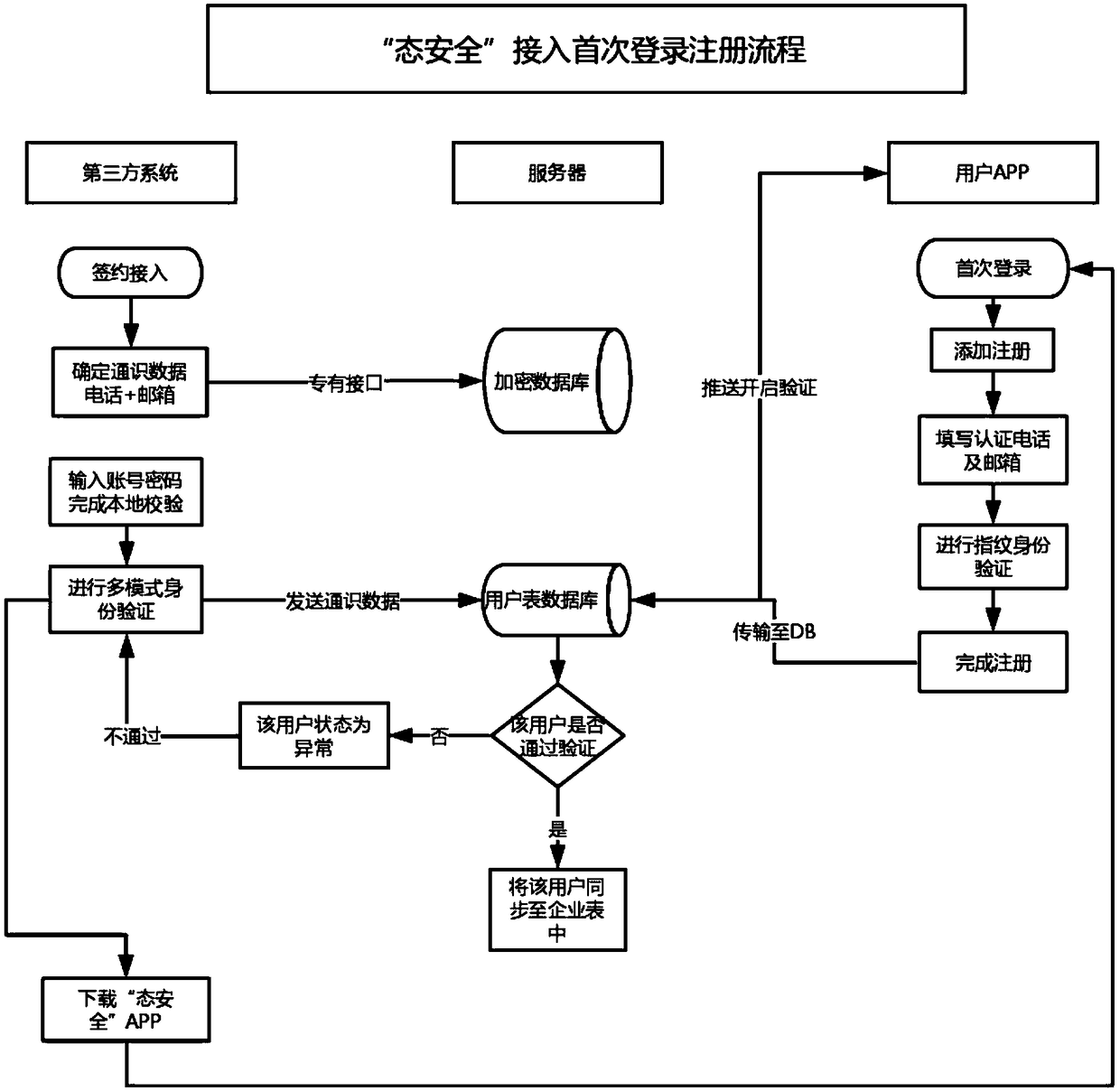
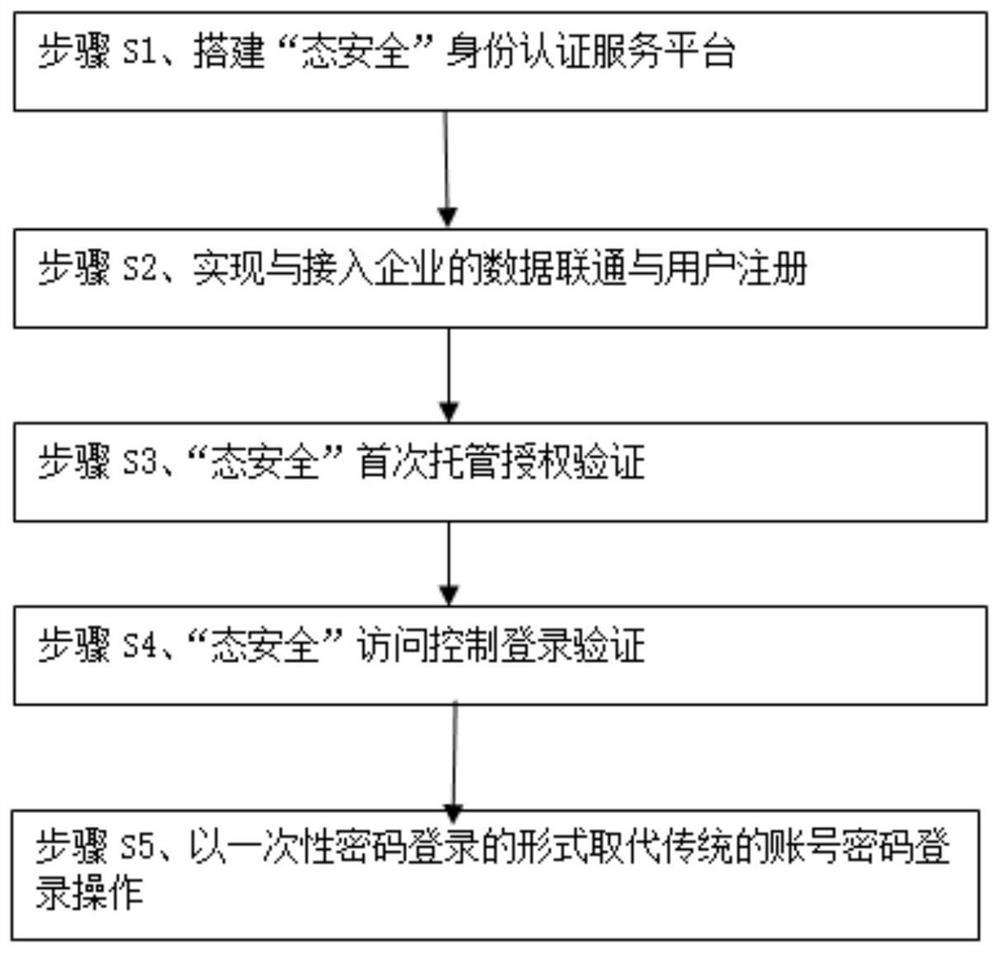
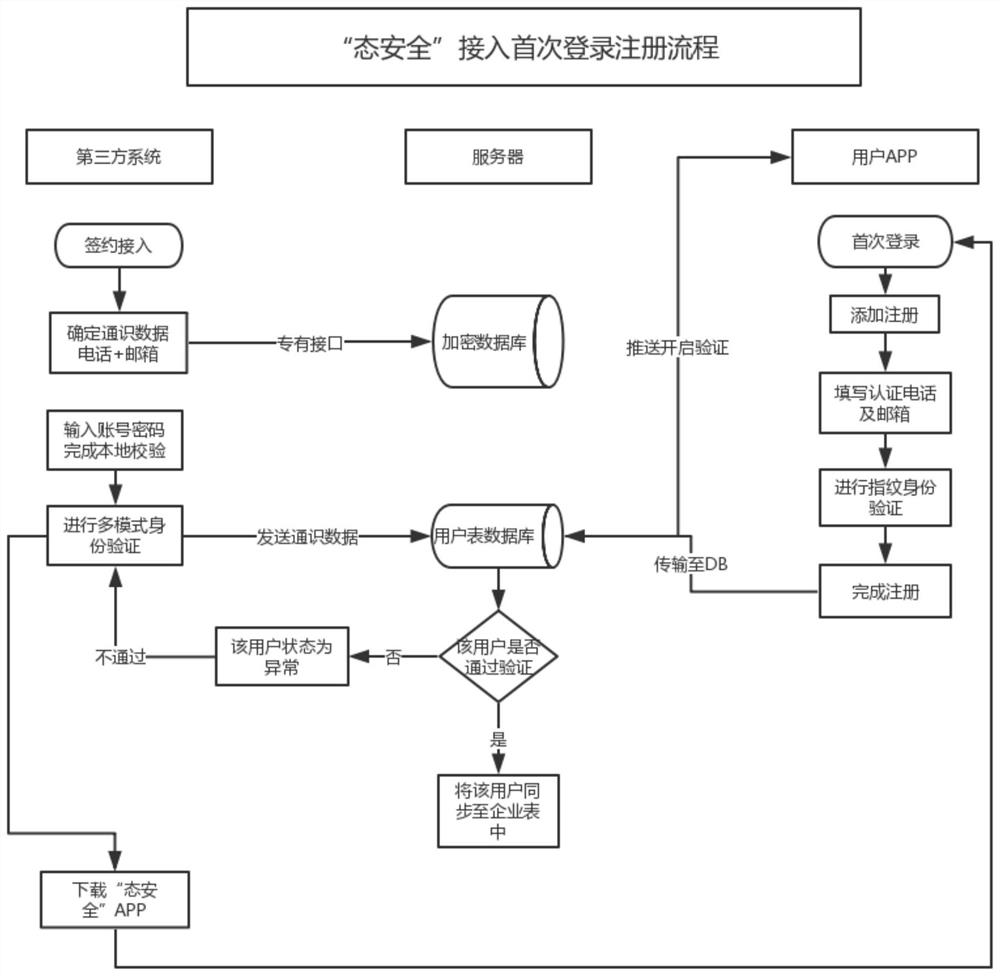
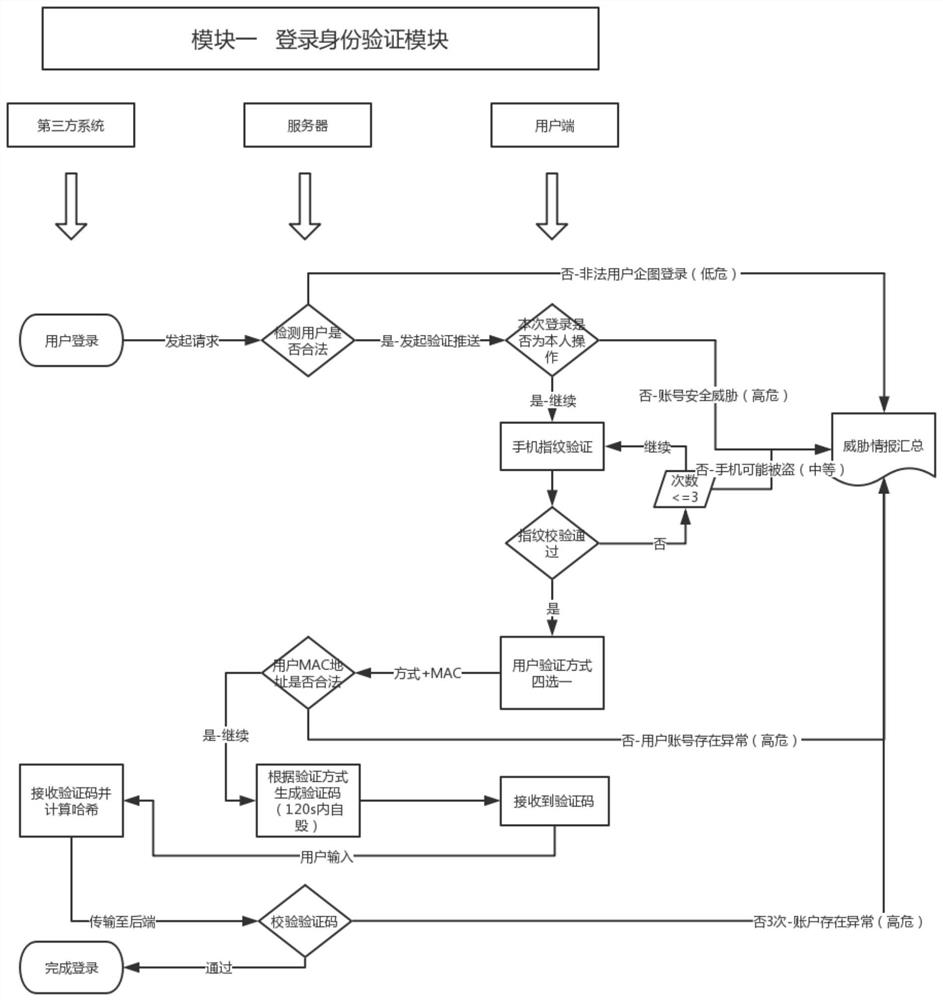
The invention relates to a third-party effective identity escrow agile authentication access mode based on account concealment. The third-party effective identity escrow agile authentication access mode comprises the following steps: step S1, establishing an identity authentication service platform of 'state security; Step S2, realizing data communication with the access enterprise and user registration; 3, performing first escrow authorization verification for 'state security'; 4, login authentication of that access control of 'state security'; Step S5, replacing the traditional account password login operation with a one-time password login form. The advantages are as follows: By building a third-party authentication service platform, with 'state security ' APP as the carrier of user operation, a unified multi-factor interactive authentication interface is established and provided to all companies for open use, and the authentication service is provided to the access company and theuser authentication result is provided to the access company in a verifiable form, so that the user can be authenticated and logged in in a more convenient and efficient form.
Owner:上海同态信息科技有限责任公司
System and method for key exchange based on authentication information
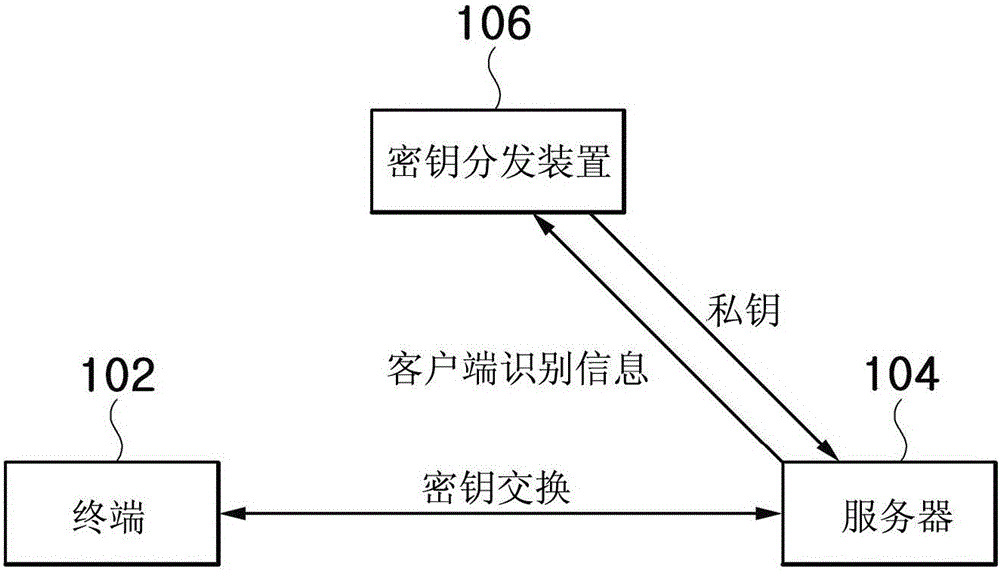
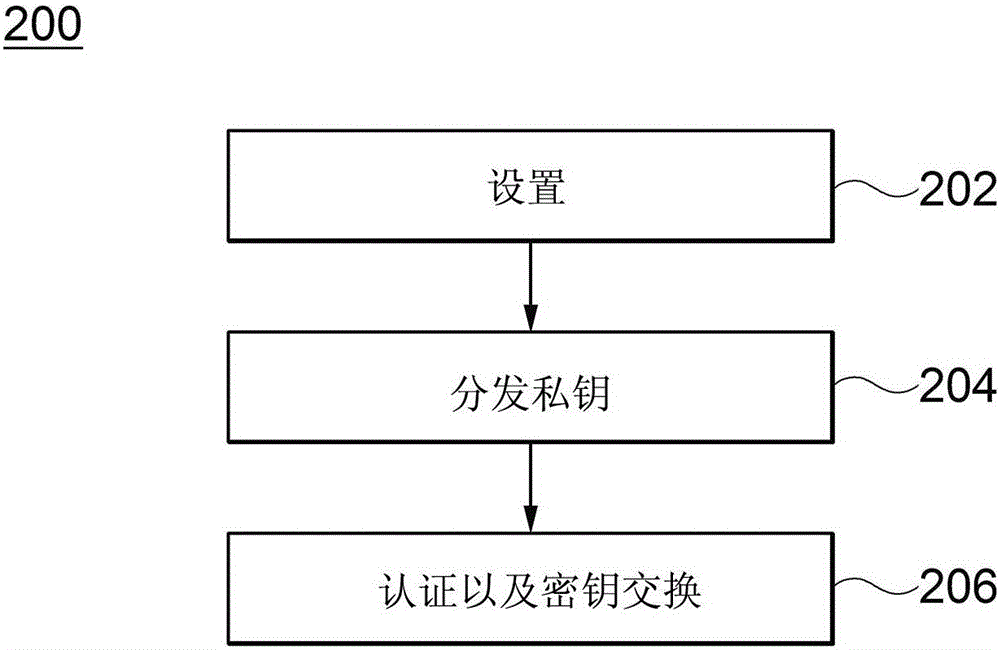
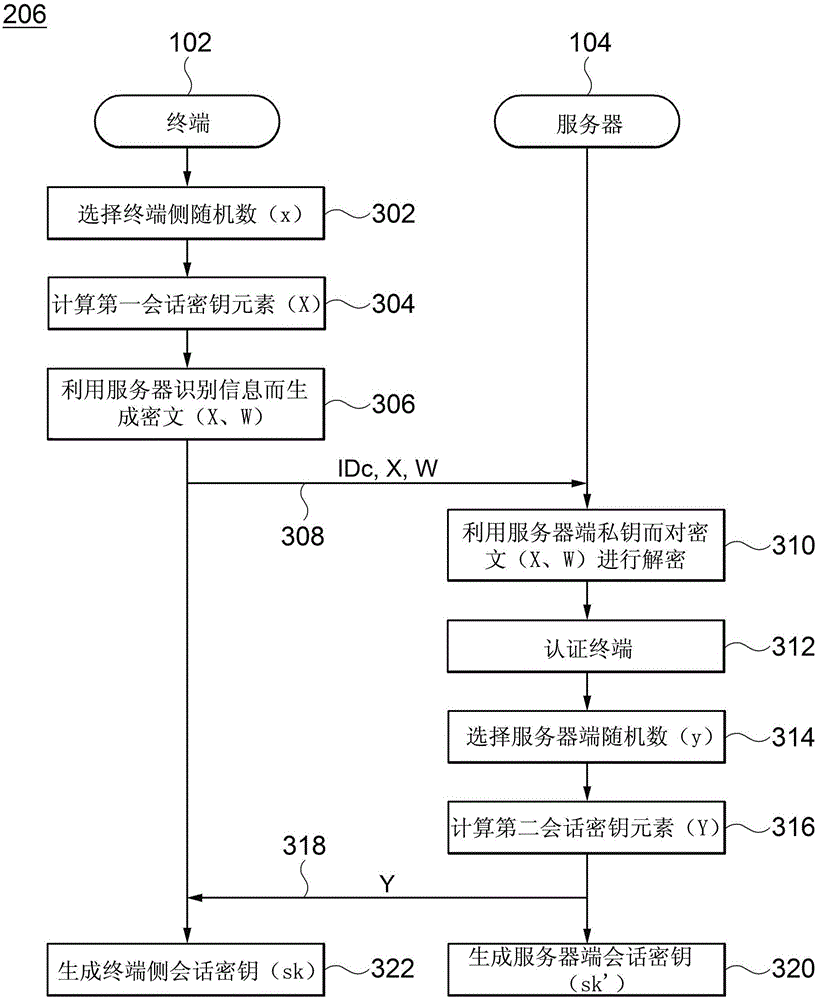
ActiveCN106130716AValid certificationEffective attackKey distribution for secure communicationEncryption apparatus with shift registers/memoriesKey exchangeCiphertext
Disclosed are a system and method for key exchange based on user authentication information. The system for key exchange based on user authentication information includes a terminal configured to generate ciphertext corresponding to authentication information of a user of the terminal using a random number for the client and server identification information, and a server configured to decrypt the ciphertext received from the terminal using a private key for the server corresponding to the server identification information to restore the authentication information, authenticate the terminal using the restored authentication information, and generate a session key for the server corresponding to the authenticated terminal.
Owner:SAMSUNG SDS CO LTD
Identification method and system used for identifying personal area network device
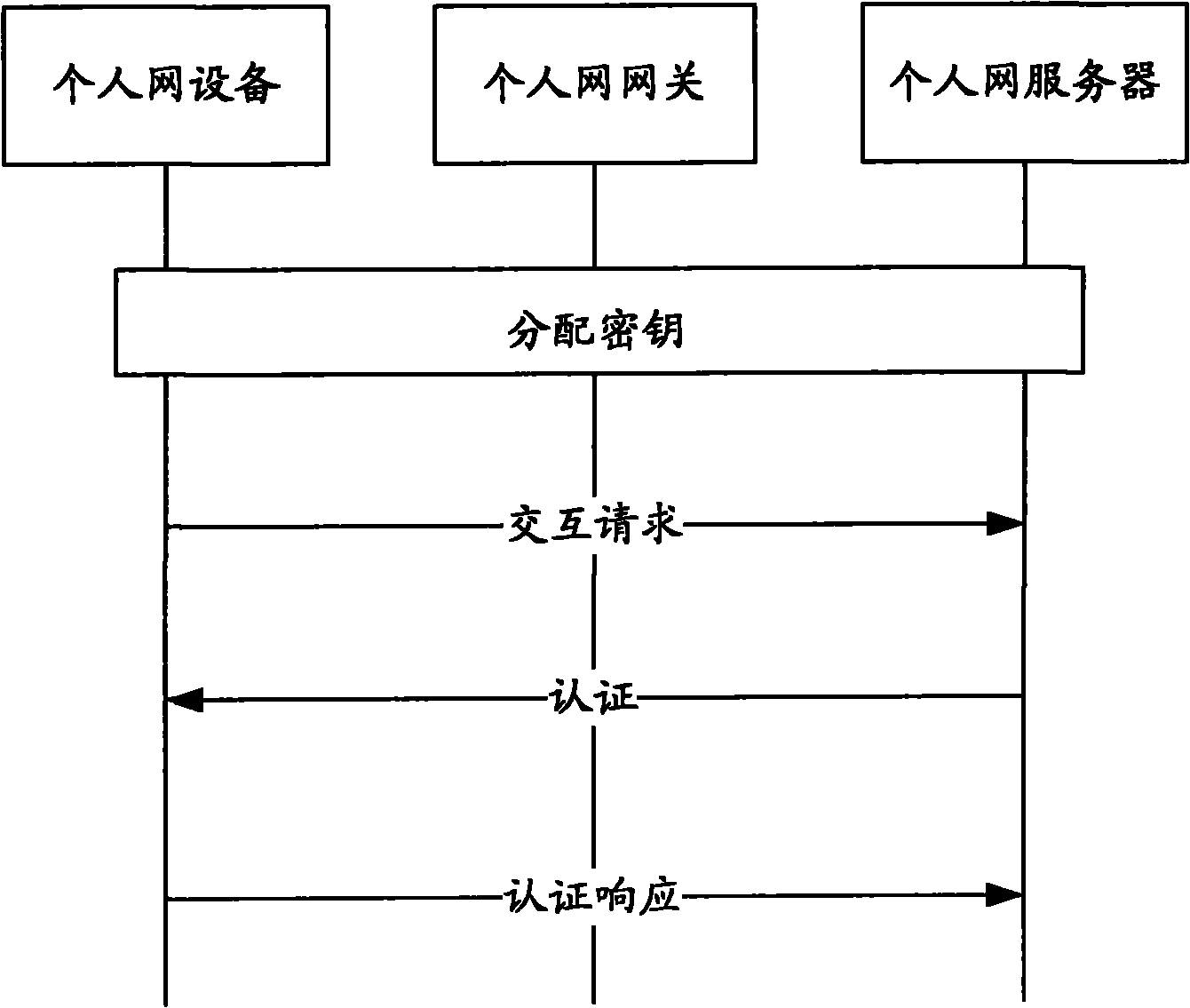
InactiveCN102377758AValid certificationEnsure safetyKey distribution for secure communicationUser identity/authority verificationComputer networkPersonal area network
The invention discloses an identification method used for identifying a personal area network device. The method comprises the steps of: identifying the personal area network device which initiates an interaction request by a personal area network gateway or a personal area network server when the personal area network device requires to perform interaction with the personal area network gateway or the personal area network server; and performing interaction between the personal area network device and the personal area network gateway or the personal area network server after passing of the identification. The invention further discloses an identification system used for identifying the personal area network device, an identification unit is used for identifying the personal area network device which initiates the interaction request by the personal area network gateway or the personal area network server when the personal area network device requires to perform interaction with the personal area network gateway or the personal area network server, and the interaction between the personal area network device and the personal area network gateway or the personal area network server is performed after passing of the identification. By adopting the method and the system disclosed by the invention, personal area network devices can be effectively identified in a personal area network when a large number of personal area network devices exist.
Owner:ZTE CORP
Method for establishing cipher protocol security based on trustful greenness
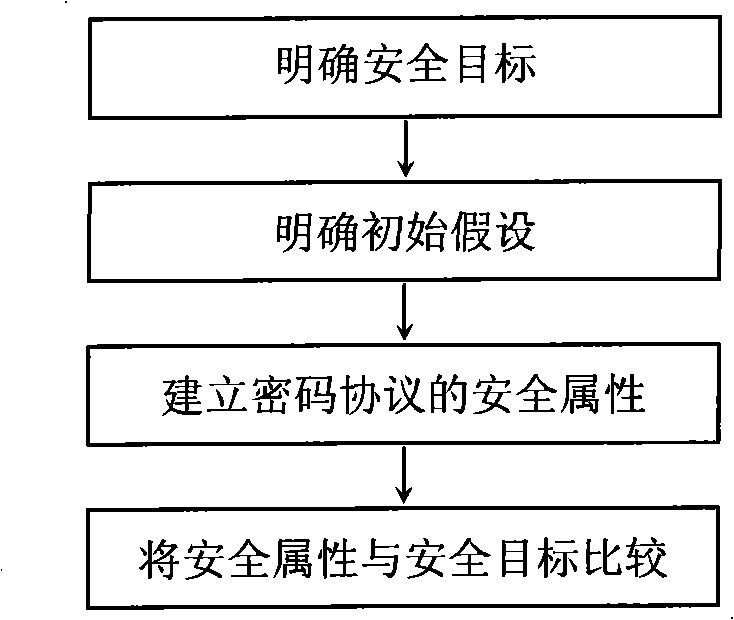
InactiveCN101299752ASafety verification is actually feasibleSignificant progressUser identity/authority verificationCryptographic protocolSecurity properties
A method for building the cryptographic protocol security based on the novelty in the information safety domain, including: determining the safe target of the cryptographic protocol to be concluded; determining the initial hypothesis of the cryptographic protocol security validation; building the cryptographic protocol security attribute obtained by the communication participating main body based on the initial hypothesis and the novelty principle of the cryptographic protocol security after transmitting or receiving each information, till the end of the protocol operation; comparing the obtained cryptographic protocol security attribute with the expected safe target. The invention effectively differentiates whether the information is novel, prevents the attack of the playback and confusion essentially, independent of the security validation and the intercurrent operating environment and the specific formalization description of the attacker's ability, which is of great efficiency to the validation cryptographic protocol, further to be expanded, applied to a plurality of validation of the cryptographic protocol security attribute.
Owner:SHANGHAI JIAO TONG UNIV
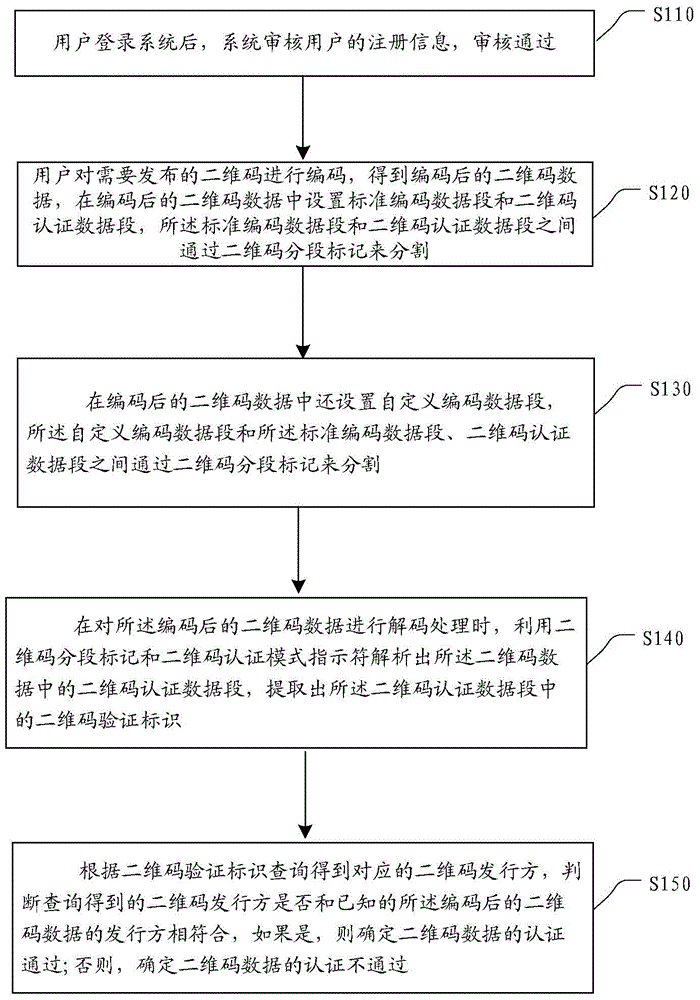
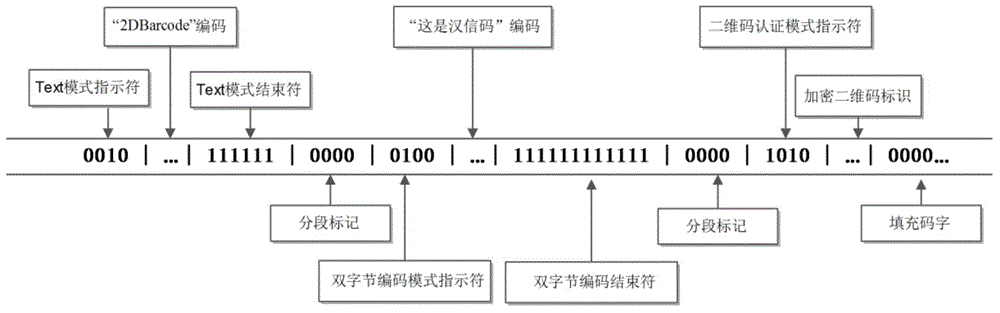
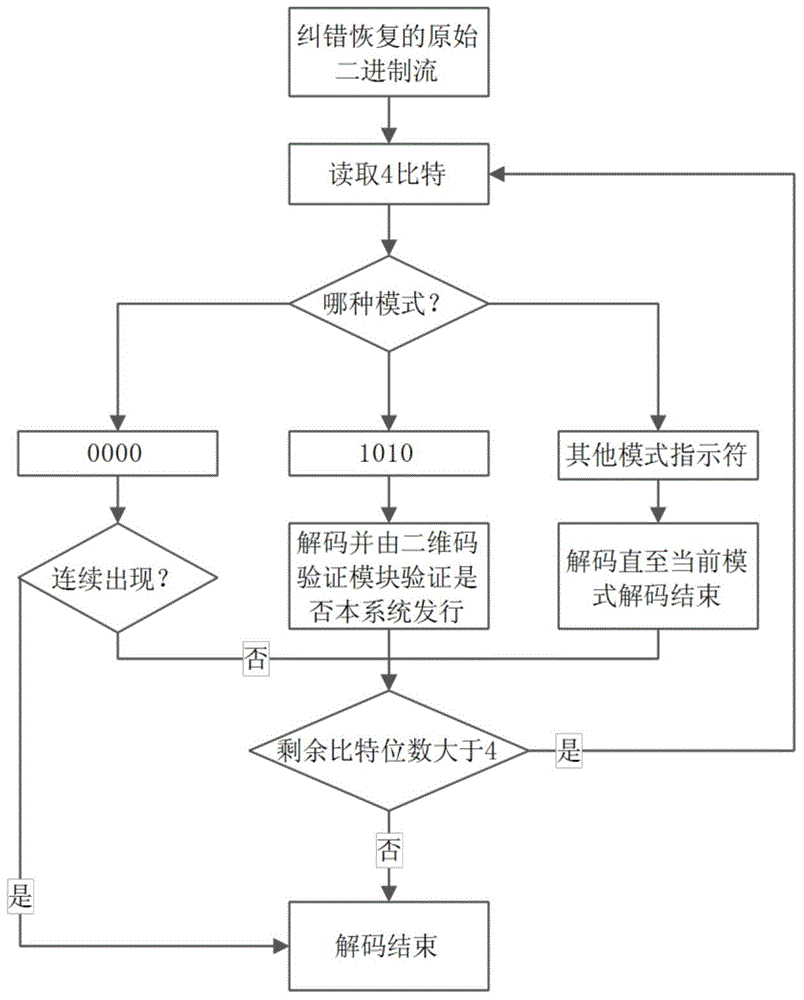
Two-dimensional code coding-and-decoding and authentication method and two-dimensional code coding-and-decoding and authentication device
InactiveCN105577376AImprove securityValid certificationUser identity/authority verificationRecord carriers used with machinesComputer hardwareData segment
An embodiment of the invention provides a two-dimensional code coding-and-decoding and authentication method and a two-dimensional code coding-and-decoding and authentication device. The two-dimensional code coding-and-decoding and authentication method mainly comprises the steps of setting a standard coded data segment and a two-dimensional code authentication data segment in coded two-dimensional code data, wherein the standard coded data segment is separated from the two-dimensional code authentication data segment through two-dimensional code segmenting marks; and setting a two-dimensional code verification mark in the two-dimensional code authentication data segment, wherein the two-dimensional code verification mark is used for verifying whether the coded two-dimensional code data are issued by a preset two-dimensional code issuing party. The two-dimensional code coding-and-decoding and authentication method and the two-dimensional code coding-and-decoding and authentication device have advantages of effectively improving safety in accessing the two-dimensional code, conveniently and effectively performing authentication on the validity of the two-dimensional code, simultaneously accommodating an open content and a private content in the two-dimensional code data, hiding the private content, and realizing no identification for existence of the private content, and realizing no use experience reduction.
Owner:AEROSPACE INFORMATION
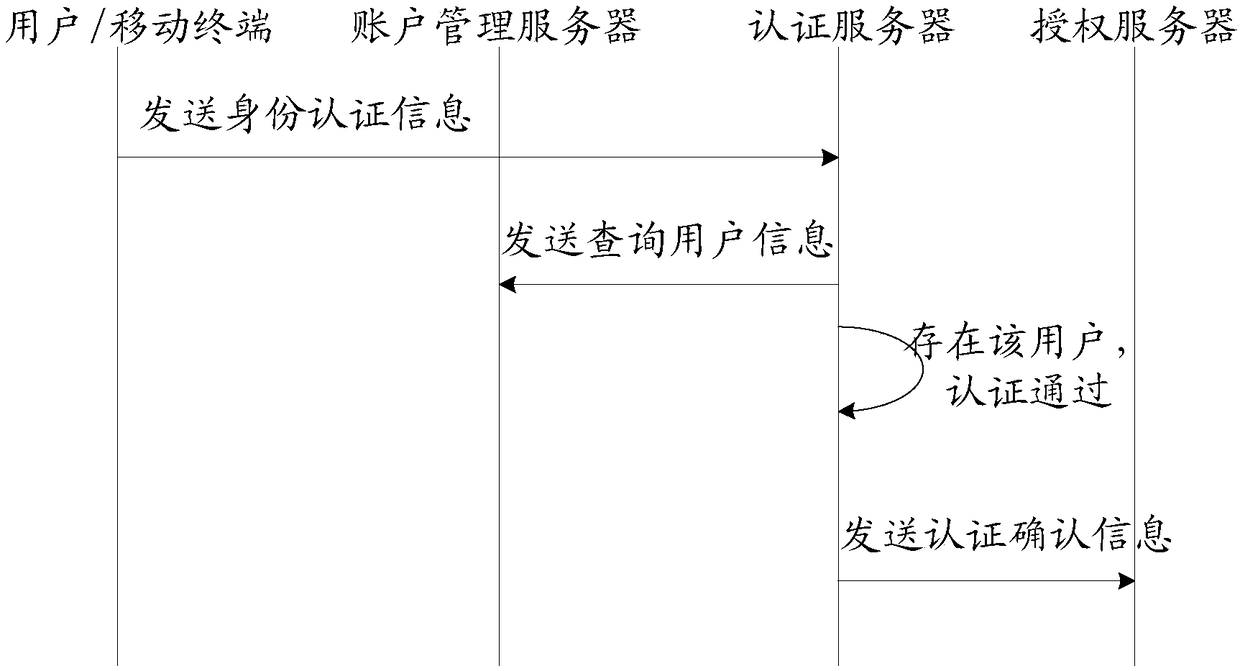
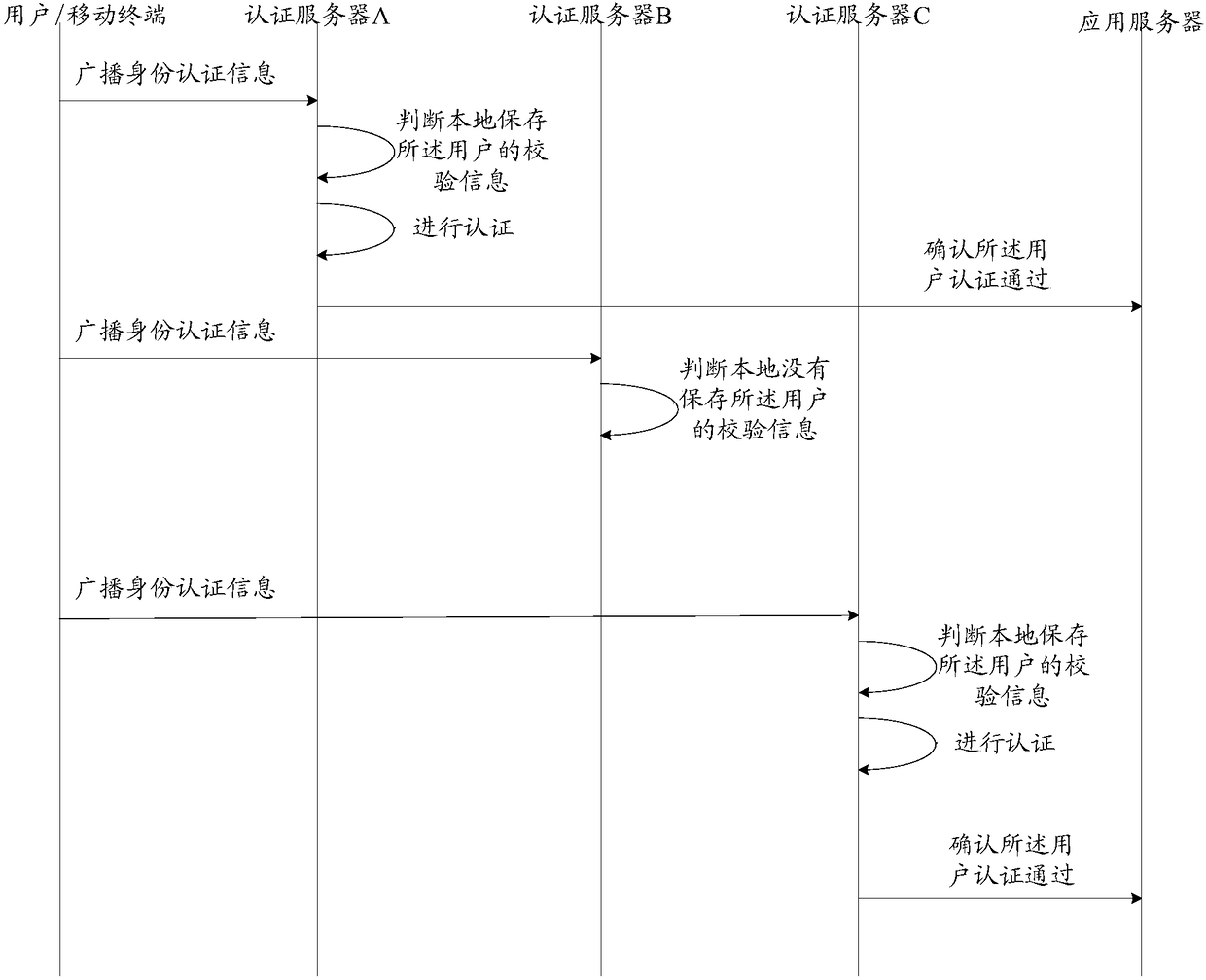
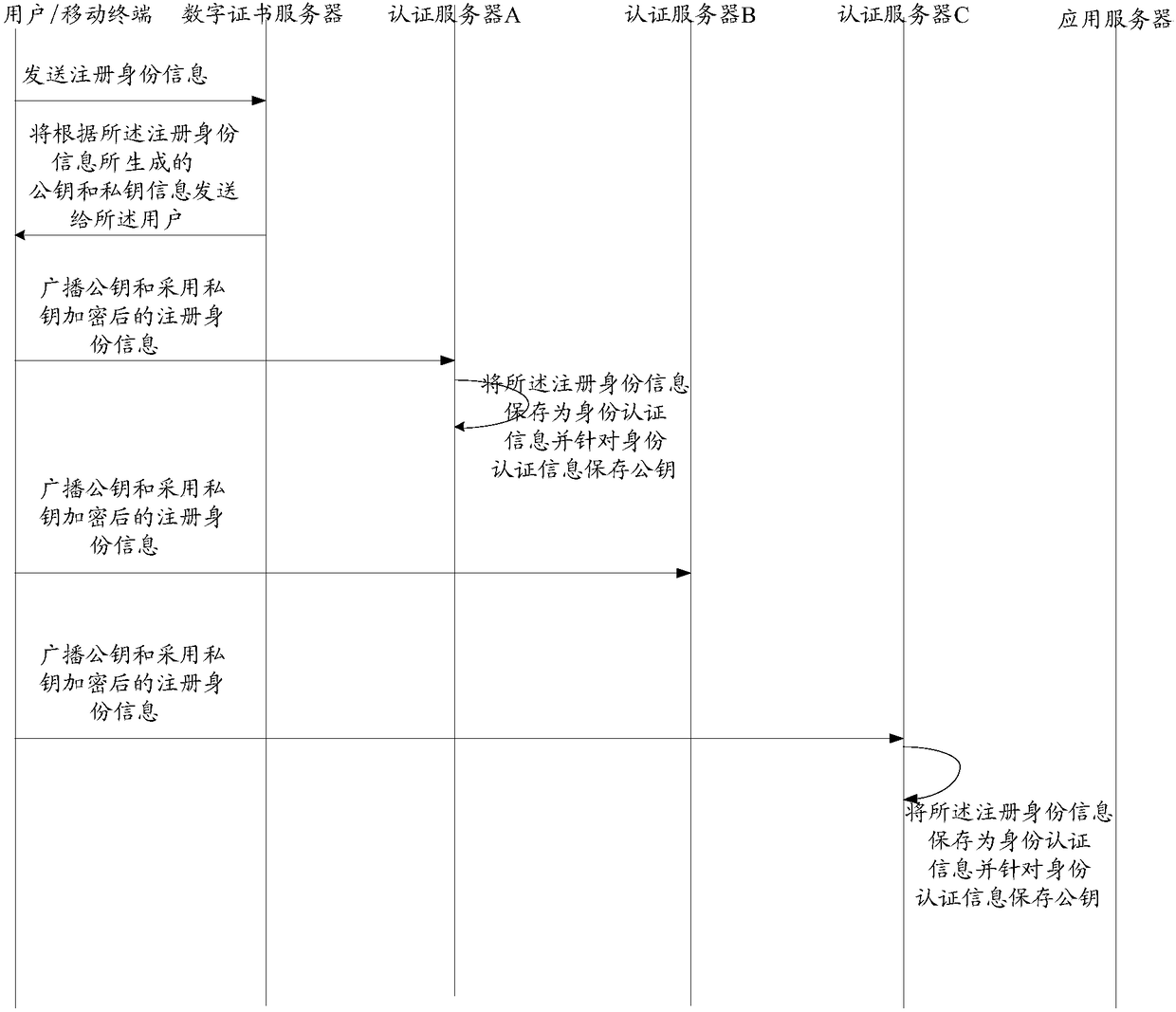
User authentication method, device and system
ActiveCN108063748AValid certificationReduce the burden onTransmissionUser authenticationApplication server
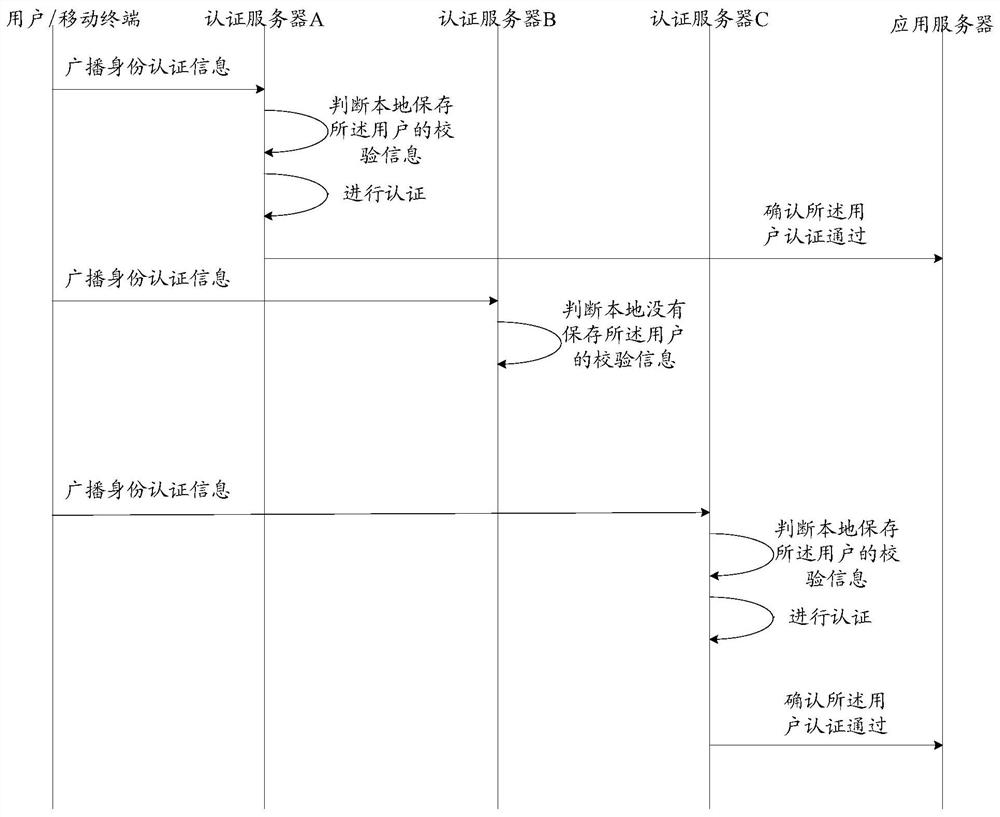
The invention discloses a user authentication method, device and system. The system comprises an application server and at least two authentication servers, wherein the at least two authentication servers are used for receiving identity authentication information broadcast by a user, judging whether verification information of the user is stored locally according to user identification informationcarried in the identity authentication information, if yes, performing authentication on the user according to the verification information and the identity authentication information, and if the authentication is passed, sending authentication confirmation information to the application server; and the application server is used for receiving the authentication confirmation information sent by the at least two authentication servers and judging whether the user, judging whether the number of the authentication servers sending the authentication confirmation information reaches a set frequency threshold value or not, and if yes, determining that the user authentication is passed and providing a corresponding service for the user. According to the method, the device and the system, a bottleneck problem of centralized authentication server processing when the user has too large concurrent page views is solved.
Owner:CHINA MOBILE COMM LTD RES INST +1
Method, device and electronic equipment for external equipment certification management
ActiveCN105787343AImprove securityImprove reliabilityDigital data authenticationEmbedded systemPeripheral
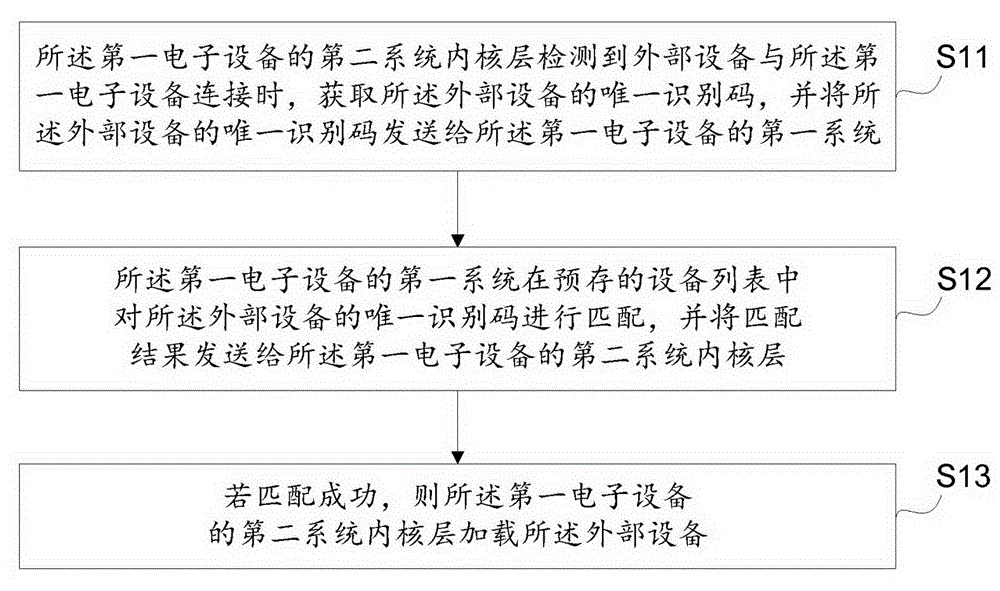
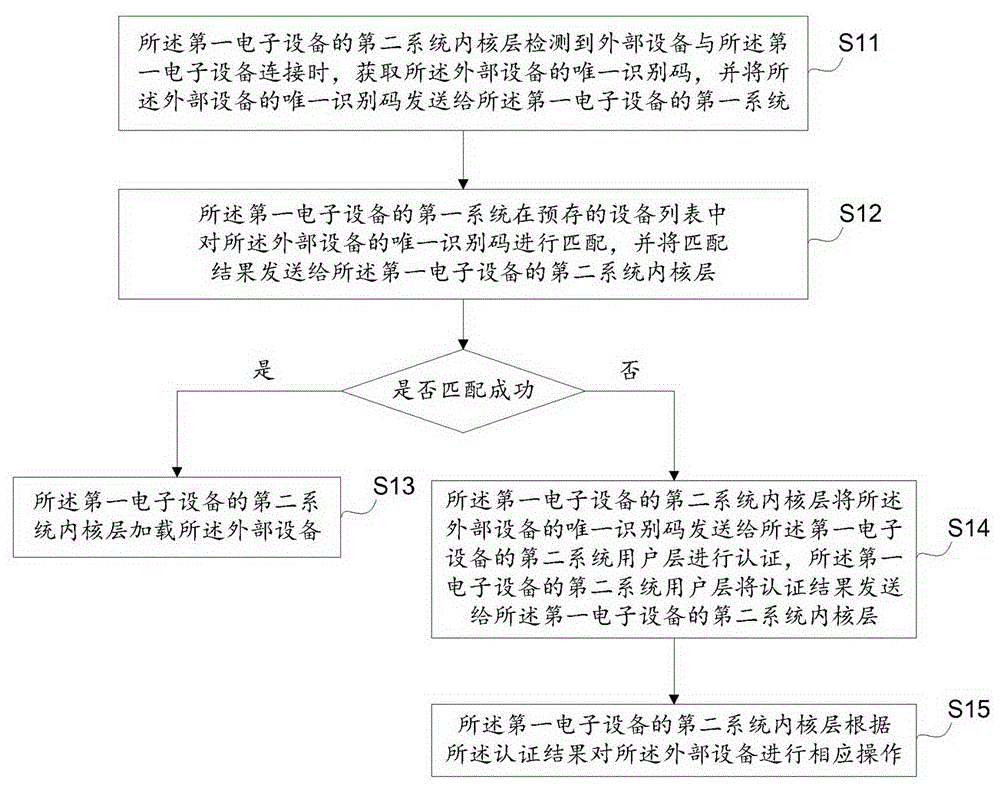
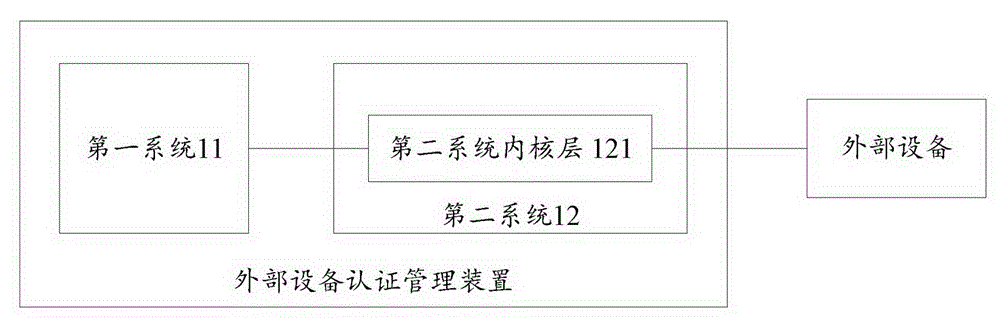
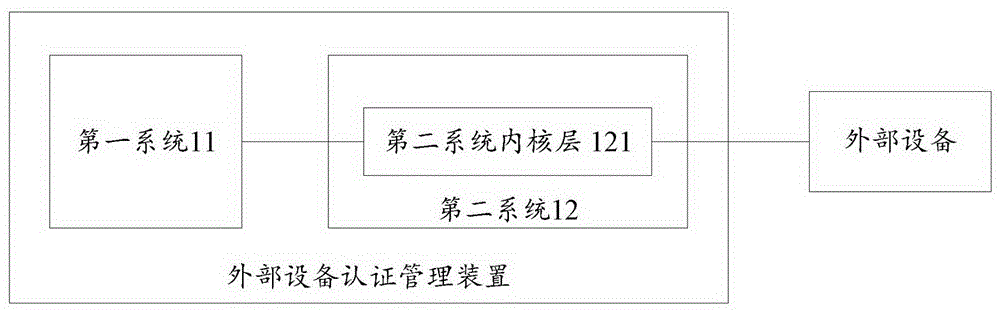
The embodiment of the invention provides a method, device and electronic equipment for external equipment certification management. The method, device and electronic equipment relate to the technical field of equipment certification and solve the problem that safety and reliability is not high for the external equipment certification in the prior art. The method for the external equipment certification management is applied in first electronic equipment and comprises the steps that when a second system kernel layer of the first electronic equipment detects connection between external equipment and the first electronic equipment, an unique identification code of the external equipment is acquired, and the unique identification code of the external equipment is sent to a first system of the first electronic equipment; the first system of the first electronic equipment matches the unique identification code of the external equipment in a pre-stored equipment list and sends a matching result to a second system kernel layer of the first electronic equipment; and if the matching succeeds, the second system kernel layer of the first electronic equipment loads the external equipment. The embodiment of the invention is applicable to the certification of the external equipment by a Linux system equipment.
Owner:LENOVO SHANGHAI INFORMATION TECH CO LTD
Identity authentication method based on Hyperledger network
InactiveCN110572392AGuaranteed not to be tampered withAuthentication securityUser identity/authority verificationDigital data authenticationChain networkBlockchain
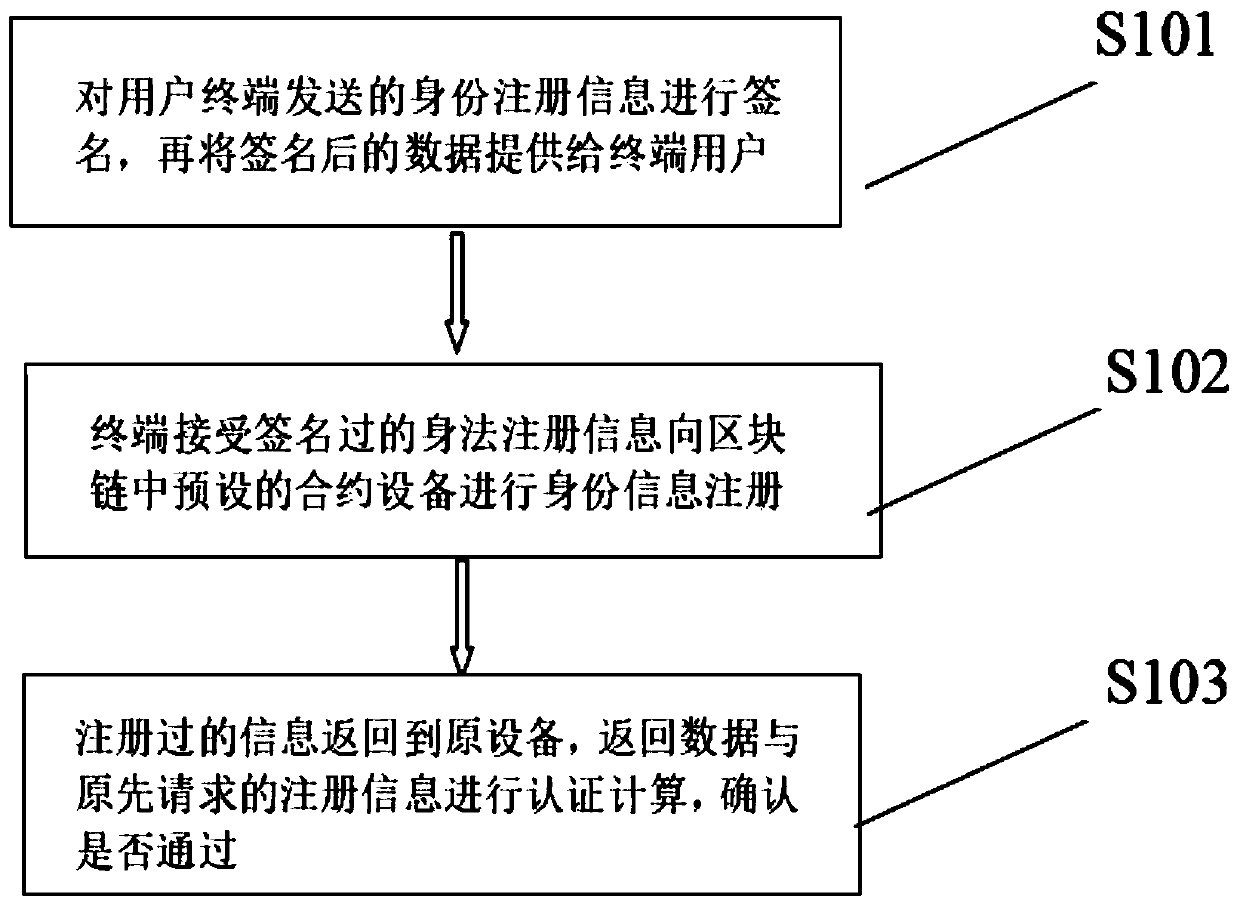
The invention discloses an identity authentication method based on a Hyperleder network. The identity authentication method is used for carrying out identity authentication on a terminal node in a block chain network. The method comprises the following steps that: enabling a terminal to receive signed body registration information and register identity information to preset contract equipment in ablock chain; and returning the registered information to the original equipment, performing calculation of an authentication algorithm on the returned data and the originally requested registration information by the original equipment, and then determining whether the identity authentication information is passed or not according to a calculated result. According to the invention, on the basis of blockchain identity authentication, the authentication security and the credit degree of the authentication process are improved.
Owner:河南戎磐网络科技有限公司
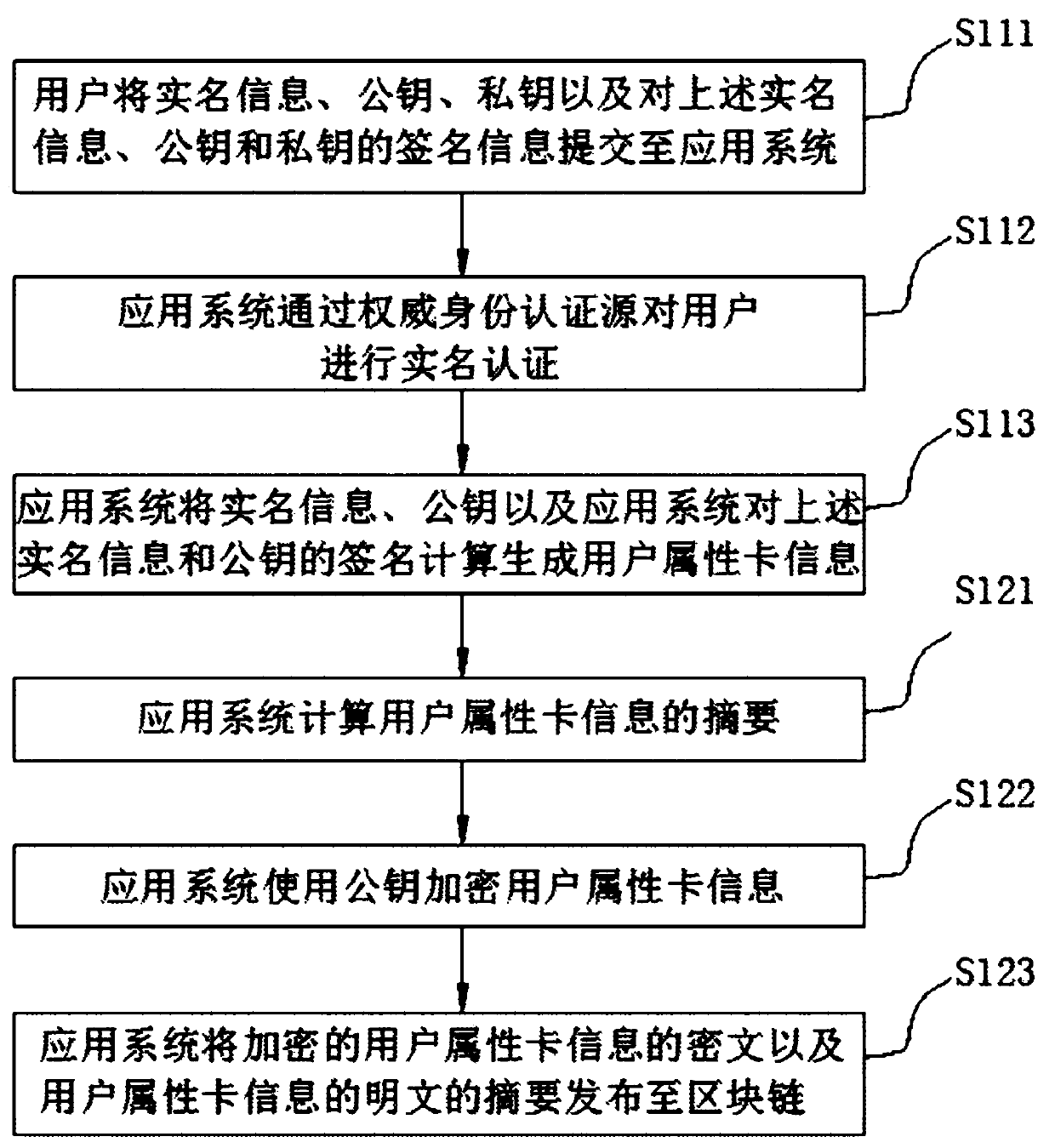
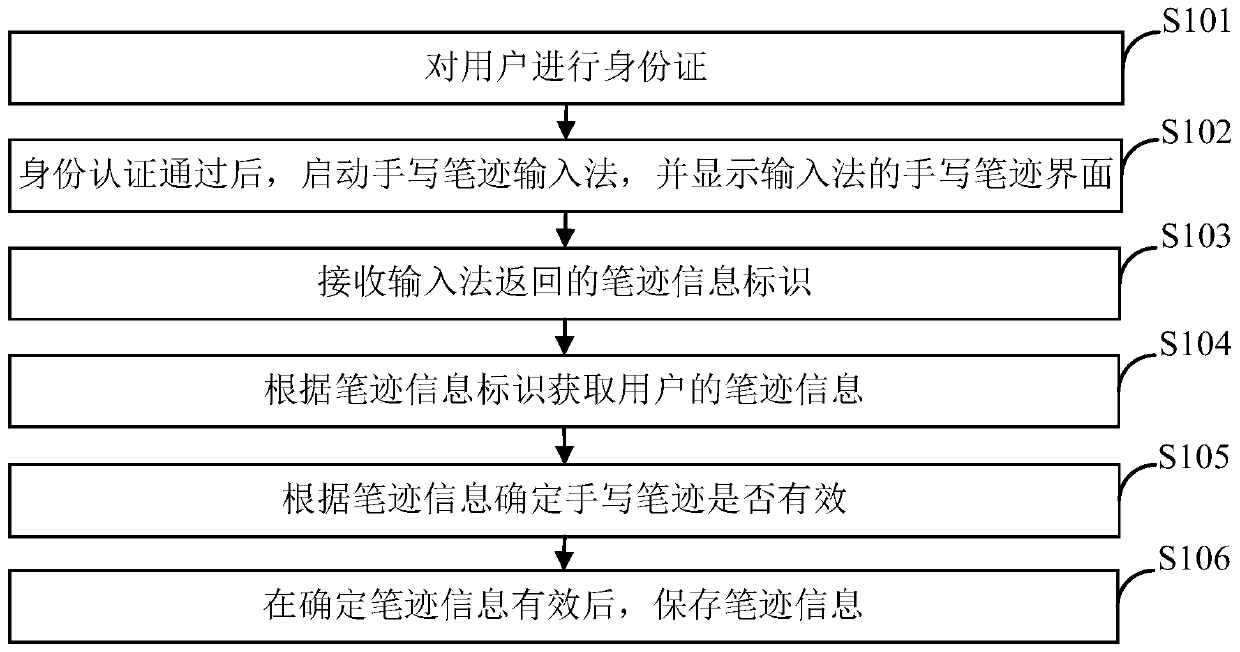
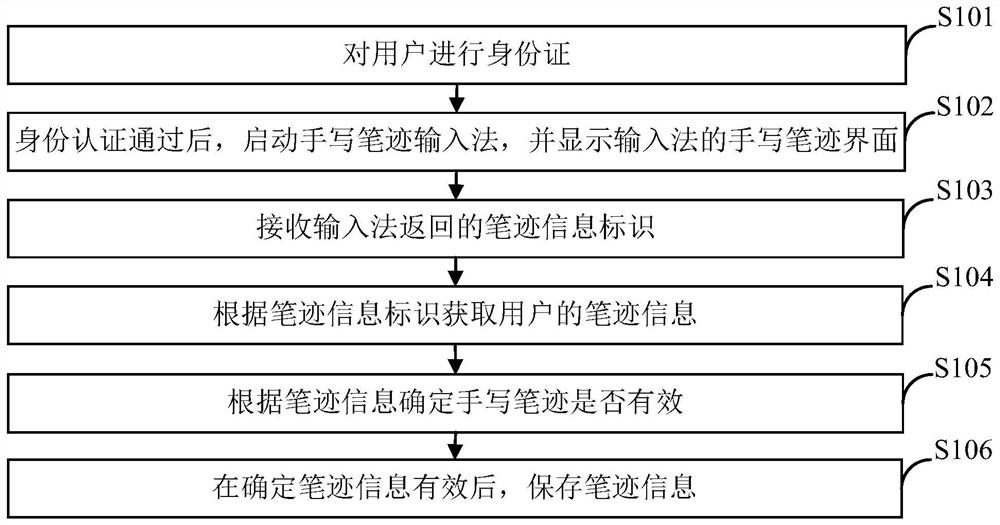
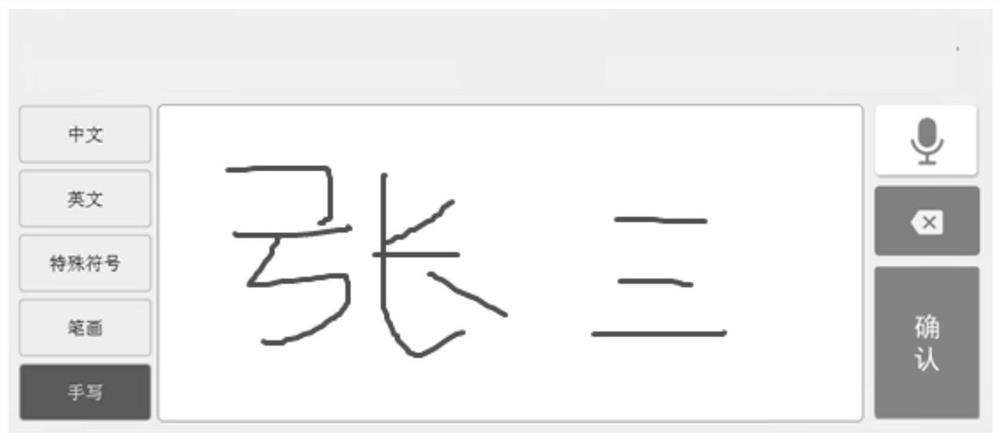
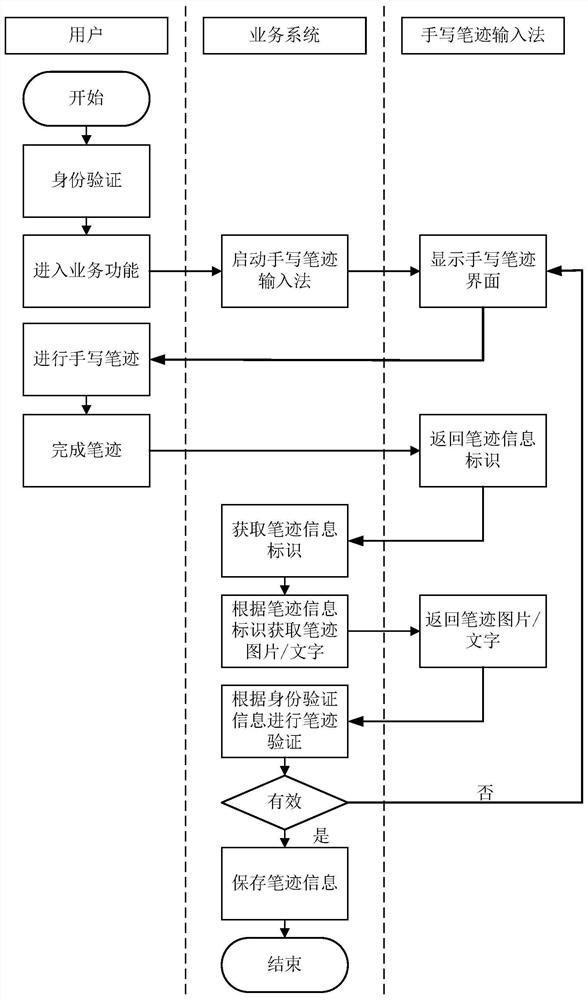
Handwriting authentication method and device based on self-service terminal and storage medium
ActiveCN109801076AValid certificationCharacter and pattern recognitionProtocol authorisationHandwritingInternet privacy
The invention relates to a handwriting authentication method and device based on a self-service terminal and a storage medium. The method carries out identity card processing on a user and comprises the following steps of after the identity authentication is passed, starting a handwriting input method, and displaying a handwriting interface of the input method; receiving a handwriting informationidentifier returned by the input method, wherein the handwriting information identifier is a unique identifier distributed after the input method obtains the picture corresponding to the handwriting of the user through the handwriting interface; obtaining handwriting information of the user according to the handwriting information identifier; determining whether the handwriting is effective or notaccording to the handwriting information; and after the handwriting information is determined to be valid, storing the handwriting information. After the identity authentication is passed, a handwriting input method is started, and a handwriting interface of the input method is displayed; Obtaining handwriting information of the user according to the handwriting information identifier; Determining whether the handwriting is effective or not according to the handwriting information; After the handwriting information is determined to be valid, the handwriting information is stored, and handwriting authentication of the self-service terminal is achieved.
Owner:GUANGDONG KAMFU TECH CO LTD
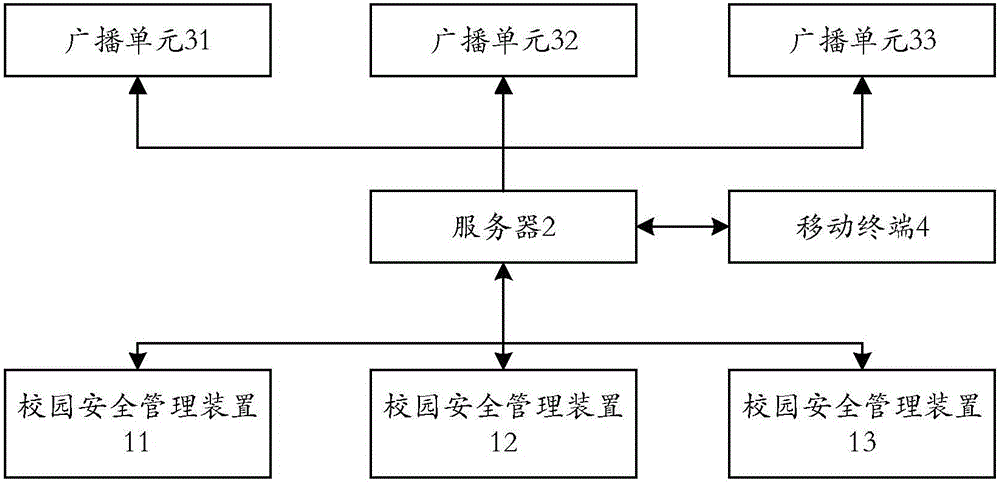
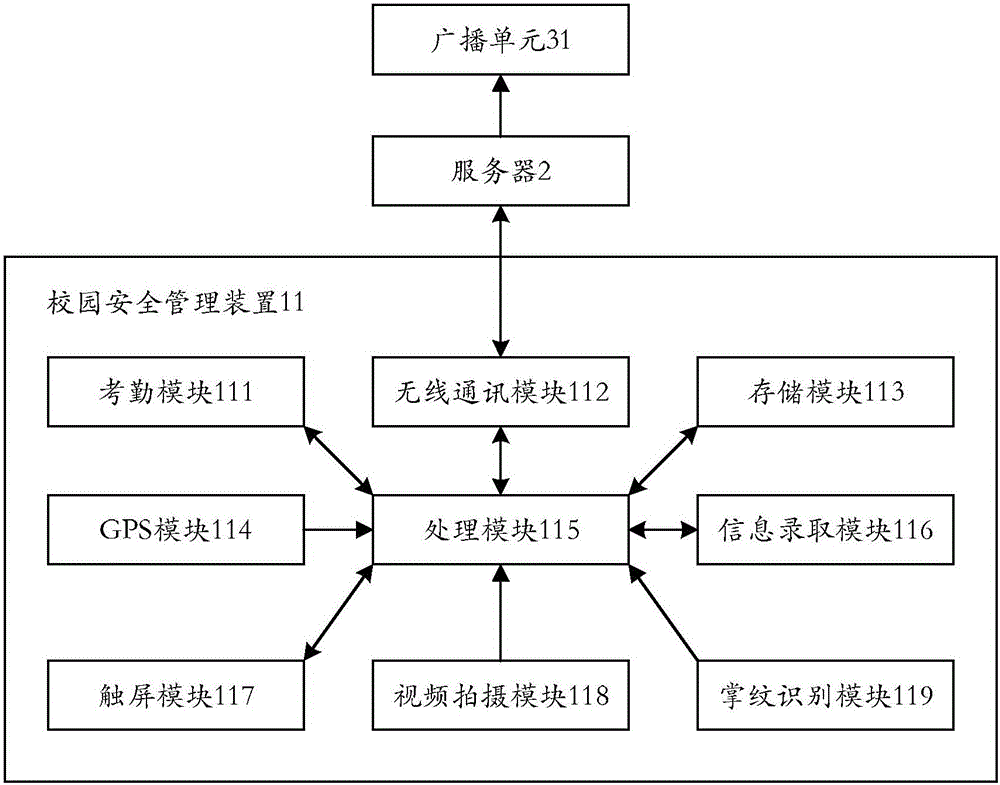
Campus safety management device and system thereof
InactiveCN105787840AValid certificationImprove convenienceData processing applicationsCharacter and pattern recognitionPalm veinIdentification scheme
The invention provides a campus safety management device and a system thereof. The campus safety management device comprises a palmprint identification module, a storage module, a processing module and a display module. The palmprint identification module is used for transmitting a palmprint identification signal to the processing module. The storage module stores identity information and basic palmprint information related to the identity information. The processing module is used for reading the identity information and the basic palmprint information. The processing module is also used for comparing the palmprint identification signal and the basic palmprint information. The processing module is further used for outputting an authentication signal. The display module is used for receiving and displaying the identity information outputted by the processing module. The palmprints and palm veins belong to biological characteristics and are not liable to lose so that safety can be greatly enhanced by the palmprint identification scheme, influence caused by loss of a pickup card can be avoided, safety hidden trouble of false pickup can also be avoided, and user convenience of the palmprint identification technology can be greatly enhanced in the aspect of identification.
Owner:湖南俊码邦科技有限公司
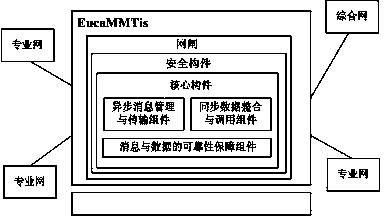
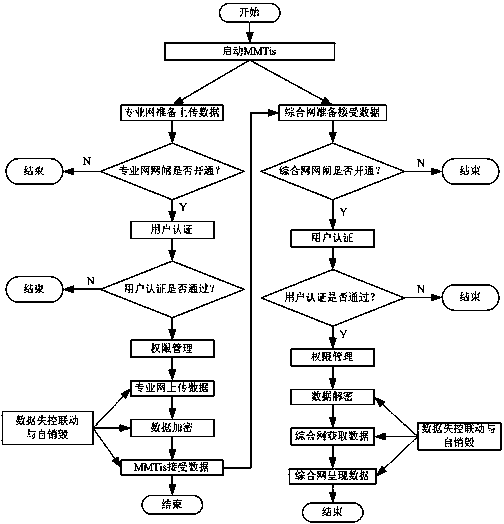
Message-oriented middleware transmission integration system based on Eucalyptus cloud platform
InactiveCN103401688AEffective isolationValid certificationUser identity/authority verificationMessage oriented middlewareEucalyptus
The invention discloses a message-oriented middleware transmission integration system based on a Eucalyptus cloud platform. The outside of the system is related with a plurality of professional networks and integrated networks. The system comprises a gatekeeper, a safety member and a core member which are stored at an Eucalyptus cloud, wherein the gatekeeper is positioned at the outermost layer of the system, can be in closed, one-way and two-way states and is used for controlling communication feasibility between subsystems; the safety member is positioned between the gatekeeper and the core member and used for identity authentication; the core member is positioned at the innermost layer of the system. The message-oriented middleware transmission integration system is suitable for being used by Chinese people, is simple and convenient to operate and is safe, stable and reliable.
Owner:PLA UNIV OF SCI & TECH
Apparatus and method for detecting duplication of portable subscriber station in portable internet system
InactiveCN101416543ADetection of illegal copyingReduce usageTransmissionSecurity arrangementThird partyPassword
Owner:POS DATA CO LTD
External equipment authentication management method, device and electronic equipment
ActiveCN105760742AImprove securityImprove reliabilityDigital data authenticationComputer hardwareCoupling
The invention embodiment provides an external equipment authentication management method, a device and electronic equipment, and relates to the equipment authentication technical field, thus solving the problems in the prior art that external equipment authentication is not high in security and reliability; the method is applied to the first electronic equipment, and comprises the following steps: entering the first system when the first electronic equipment starts, when the first system detects the external equipment is connected with the first electronic equipment, obtaining the unique identification code of the external equipment and storing the code into an equipment list of the first system; entering the second system, when the second system inner nuclear layer detects the external equipment is connected with the first electronic equipment, obtaining the unique identification code of the external equipment and sending the unique identification code to the first system; using the first system to couple the external equipment unique identification code in the equipment list, and sending the coupling result to the second system inner nuclear layer; the second system inner nuclear layer carries out corresponding operations on the external equipment according to the coupling result. The method, device and electronic equipment are suitable for Linux system equipment to carry out authentication for external equipment.
Owner:LENOVO SHANGHAI INFORMATION TECH CO LTD
An agile authentication access method for third-party effective identity hosting based on account concealment
ActiveCN108989346BWeaken the account conceptValid certificationTransmissionThird partyOne-time password
The invention relates to a third-party effective identity escrow agile authentication access mode based on account concealment. The third-party effective identity escrow agile authentication access mode comprises the following steps: step S1, establishing an identity authentication service platform of 'state security; Step S2, realizing data communication with the access enterprise and user registration; 3, performing first escrow authorization verification for 'state security'; 4, login authentication of that access control of 'state security'; Step S5, replacing the traditional account password login operation with a one-time password login form. The advantages are as follows: By building a third-party authentication service platform, with 'state security ' APP as the carrier of user operation, a unified multi-factor interactive authentication interface is established and provided to all companies for open use, and the authentication service is provided to the access company and theuser authentication result is provided to the access company in a verifiable form, so that the user can be authenticated and logged in in a more convenient and efficient form.
Owner:上海同态信息科技有限责任公司
CNN-based multi-sensor building elevator user identity verification system
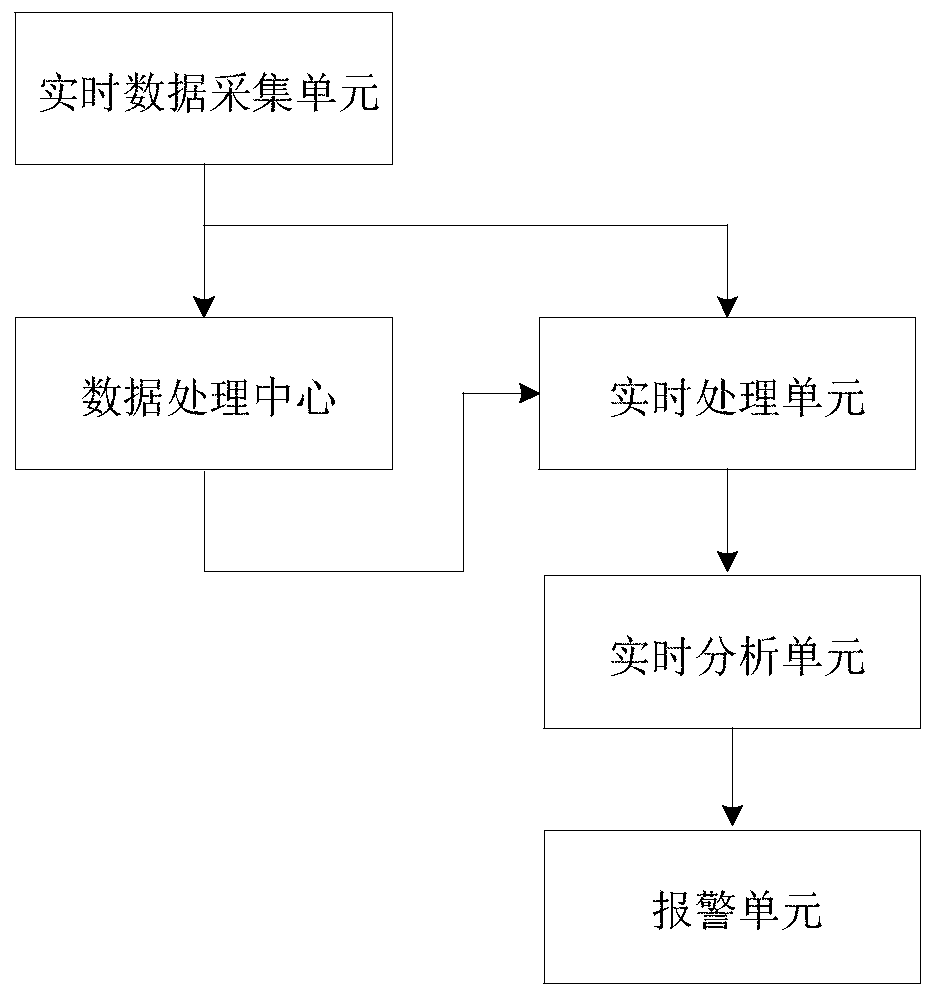
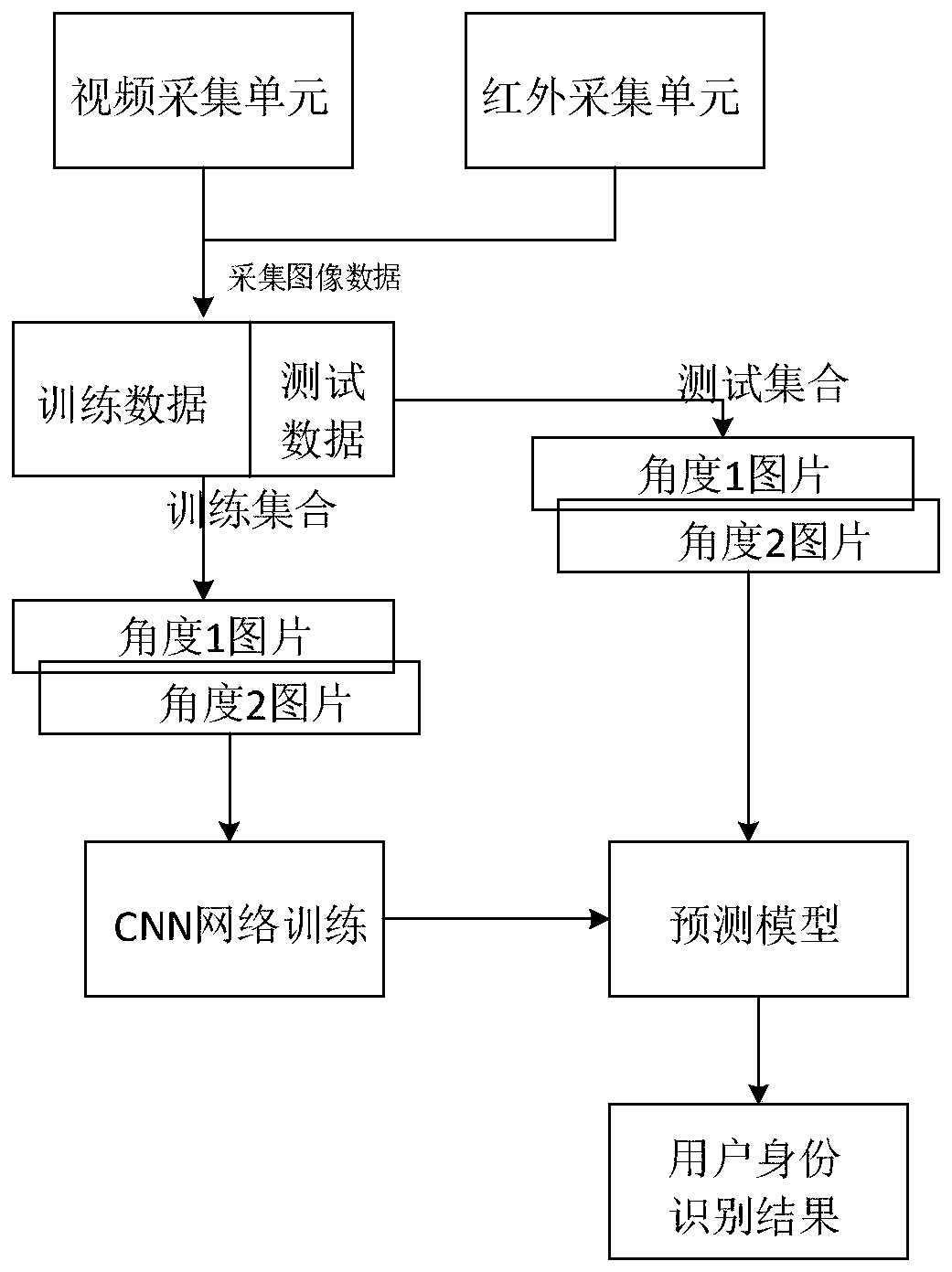
InactiveCN110309711AAccurate authenticationValid certificationCharacter and pattern recognitionElevatorsReal time analysisData information
The invention discloses a CNN-based multi-sensor building elevator user identity verification system, which comprises a real-time acquisition unit for acquiring multi-angle real-time image data of passengers in an elevator car, a data processing center which is used for carrying out technical analysis according to the passenger information transmitted by the real-time acquisition unit, respectively obtaining images and infrared information of multi-angle passengers containing passenger face information, forming a training set and a test set by the data information, and carrying out network training to obtain a proper weight of the CNN network, a real-time processing unit which is used for receiving and processing elevator passenger information in real time according to the trained CNN network and giving out a user identity recognition result so as to accurately verify the current passenger identity, and a real-time analysis unit which is used for judging the identity of the passenger according to the image information of the passenger, recording the information of the registered user if the passenger belongs to the registered user, and suggesting to pay attention to the external non-registered user if the user is judged to be the non-registered user.
Owner:ZHEJIANG NEW ZAILING TECH CO LTD
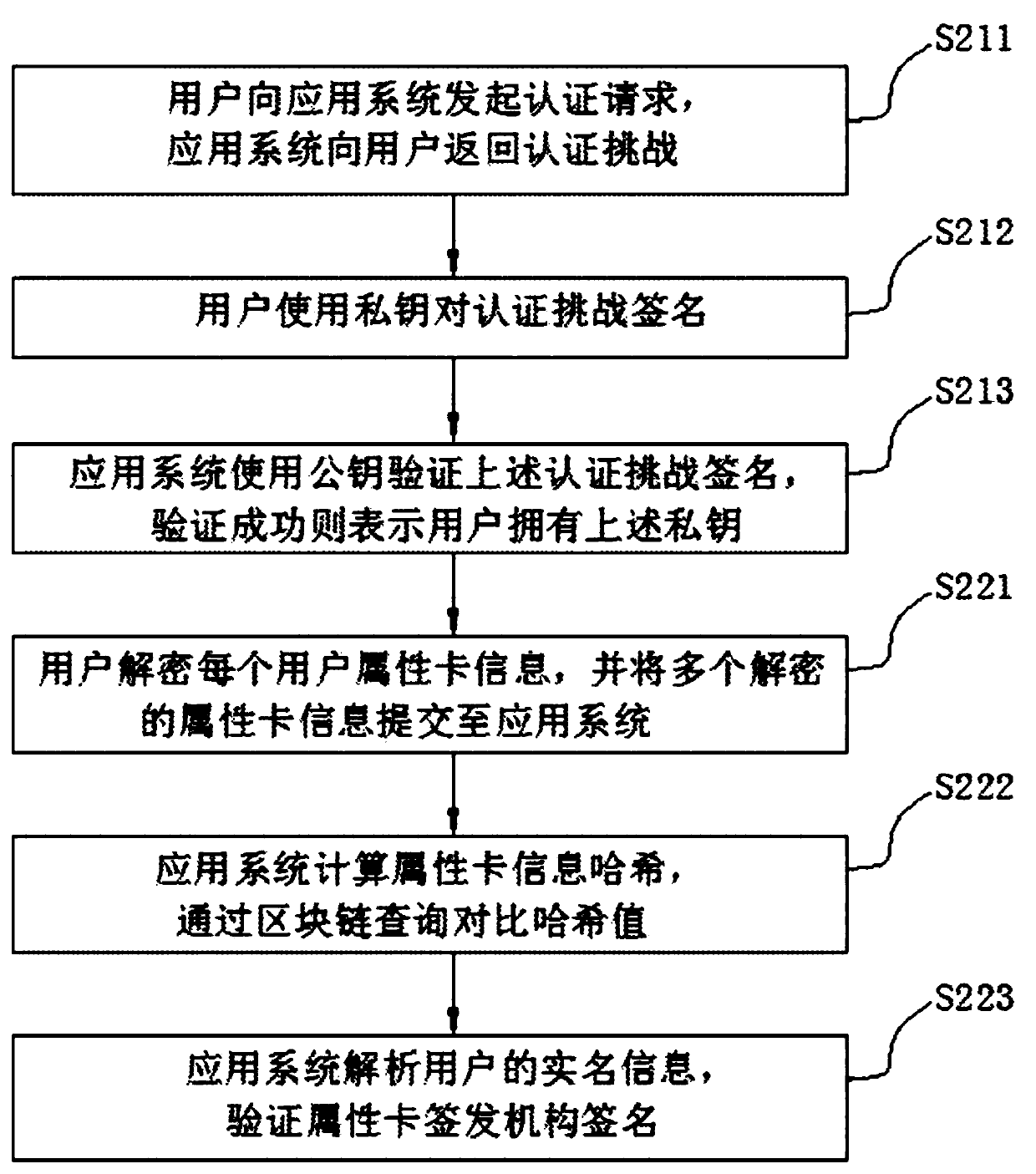
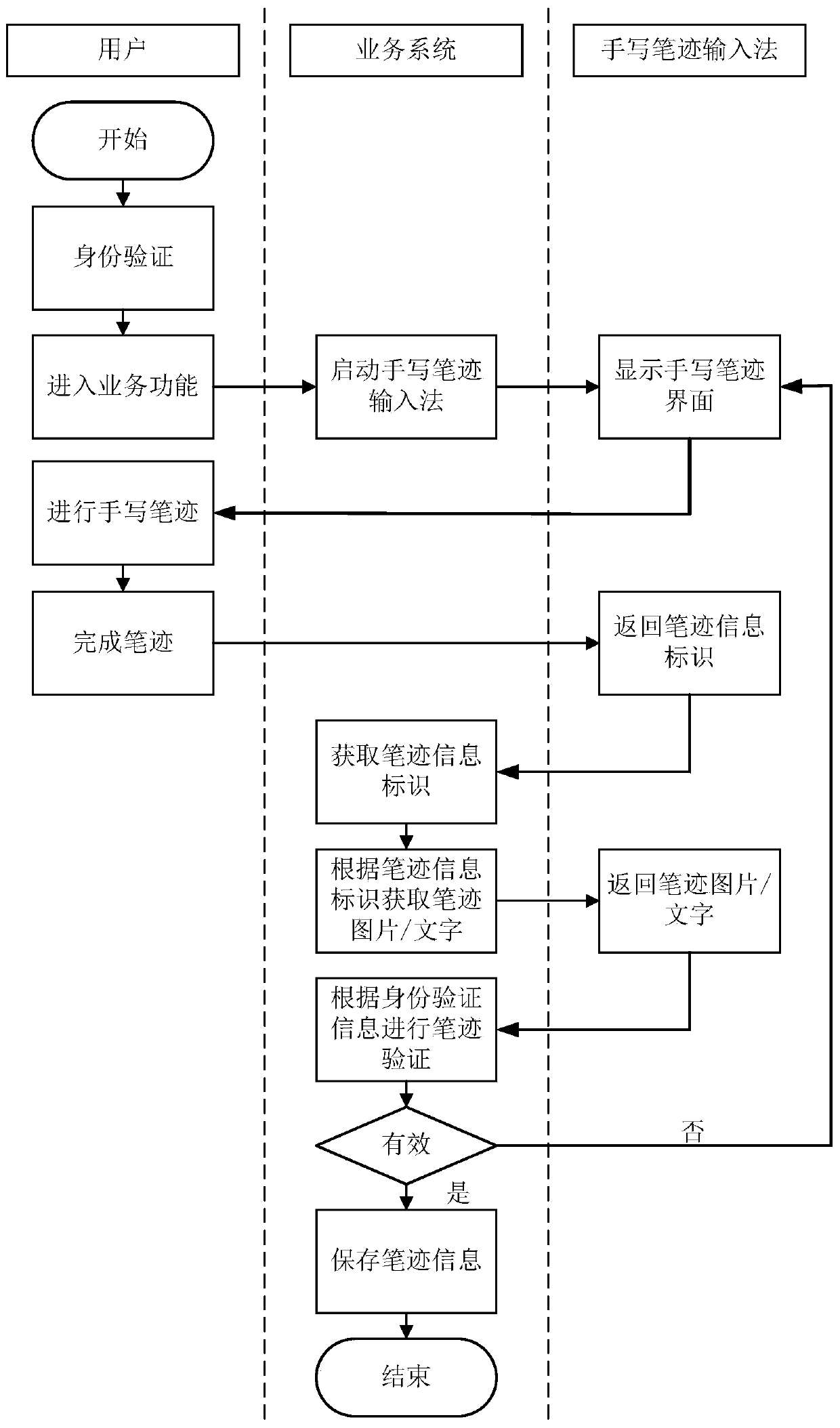
Handwriting authentication method, device and storage medium based on self-service terminal
ActiveCN109801076BValid certificationCharacter and pattern recognitionProtocol authorisationComputer hardwareHandwriting
The invention relates to a handwriting authentication method and device based on a self-service terminal and a storage medium. The method carries out identity card processing on a user and comprises the following steps of after the identity authentication is passed, starting a handwriting input method, and displaying a handwriting interface of the input method; receiving a handwriting informationidentifier returned by the input method, wherein the handwriting information identifier is a unique identifier distributed after the input method obtains the picture corresponding to the handwriting of the user through the handwriting interface; obtaining handwriting information of the user according to the handwriting information identifier; determining whether the handwriting is effective or notaccording to the handwriting information; and after the handwriting information is determined to be valid, storing the handwriting information. After the identity authentication is passed, a handwriting input method is started, and a handwriting interface of the input method is displayed; Obtaining handwriting information of the user according to the handwriting information identifier; Determining whether the handwriting is effective or not according to the handwriting information; After the handwriting information is determined to be valid, the handwriting information is stored, and handwriting authentication of the self-service terminal is achieved.
Owner:GUANGDONG KAMFU TECH CO LTD
Single sign-on method, system and load balancing equipment based on load balance
ActiveCN102104483BValid certificationImplement "sticky" accessUser identity/authority verificationWeb applicationVirtual servers
The invention provides a single sign-on method, system and load balancing equipment based on load balance, wherein a current user accesses a Web virtual server by load balancing (LB) equipment, and a real Web application server under the Web virtual server redirects the user to a centralized authentication service (CAS) virtual server for authentication; the LB equipment and the real Web application server obtain a real CAS server which authenticates the current user and redirects the current user to the Web virtual server for service access; and the real Web application server under the Web virtual server requests the real CAS server to perform verification, and realizes the single sign-on of the current user according the verification result. By the scheme provided by the invention, the current user and the real Web application server both can accurately access the real CAS server which is in charge of the authentication of the current user, so that viscous access is realized, and the effective authentication and sign-on of users are ensured.
Owner:NEW H3C TECH CO LTD
A user authentication method, device and system
ActiveCN108063748BValid certificationReduce the burden onTransmissionApplication serverInternet privacy
The invention discloses a user authentication method, device and system. The system includes: an application server and at least two authentication servers; wherein the at least two authentication servers are used to receive identity authentication information broadcast by users, and according to the identity The user identification information carried in the authentication information is used to determine whether the verification information of the user is saved locally, and if so, the user is authenticated according to the verification information and the identity authentication information, and if the authentication is passed, the user is sent to the The application server sends authentication confirmation information; the application server is configured to receive authentication confirmation information sent by at least two authentication servers, and determine whether the number of authentication servers sending authentication confirmation information for the user reaches a set number of times threshold, If yes, it is determined that the user has passed the authentication, and corresponding services are provided to the user. It solves the bottleneck problem of the centralized authentication server processing when the user's concurrent visits are too large.
Owner:CHINA MOBILE COMM LTD RES INST +1
Centralized domain user authorization and management system
InactiveCN1313950CReduce transplant costsGuaranteed irrelevanceMultiple digital computer combinationsProgram loading/initiatingClient-sideA domain
Owner:上海光华如新信息科技股份有限公司
A portable identity authentication system based on face recognition technology
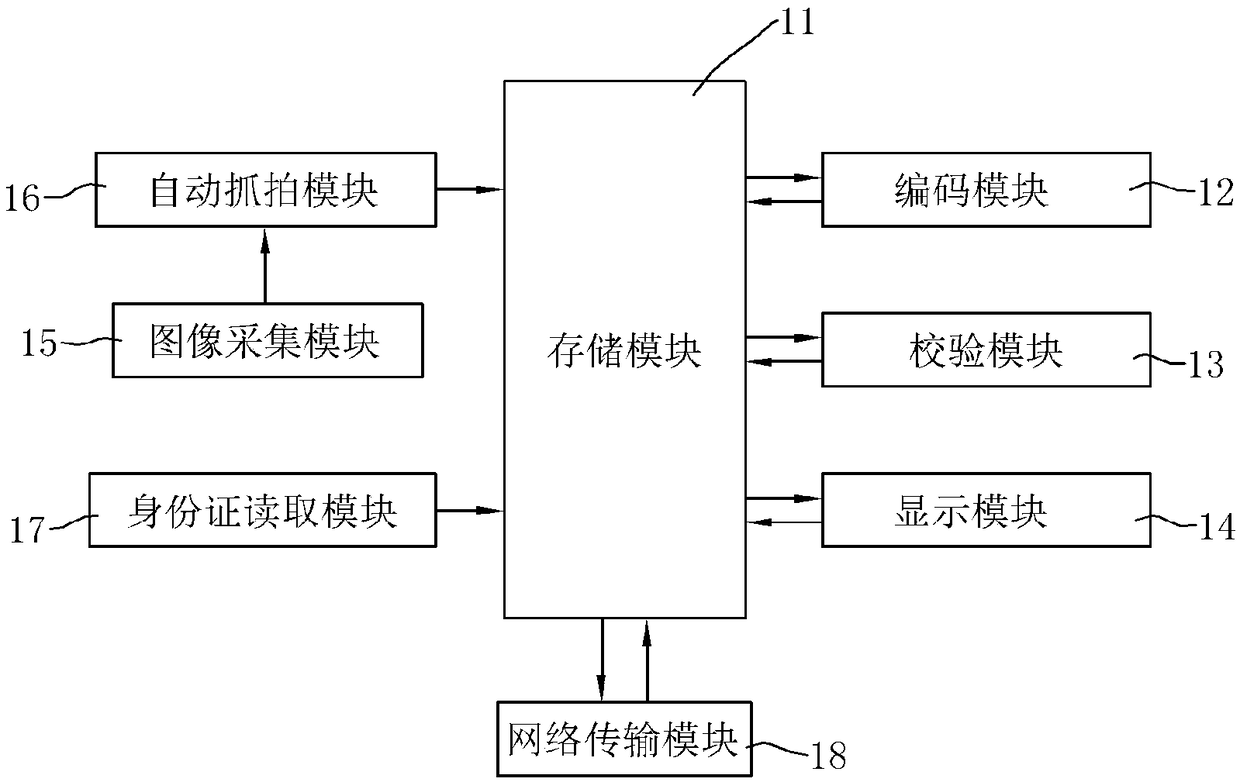
PendingCN109376723AUniqueness guaranteedPrevent taking the testData processing applicationsCharacter and pattern recognitionCode moduleComputer graphics (images)
The invention discloses a portable identity authentication system based on face recognition technology. The portable identity authentication system comprises a storage module, a coding module, a verification module, a display module, an image acquisition module, an automatic capture module and an ID card reading module. Through face recognition technology, For the frontal facial images of the candidates captured at the scene, The second-generation official ID card reads the image, the image consistency authentication when the examinee enrolls, In the prior art, invigilating teachers are required to identify examinee images with naked eyes. The scheme of the embodiment of the invention changes the mode of invigilating teachers identifying examinee images with naked eyes into a machine recognition mode, thereby effectively reducing the difficulty of teachers' work and improving the accuracy and effectiveness of identification. Through the automatic recognition of examinees' facial photographs to confirm the examinees' identity, the operation is convenient and the training intensity is reduced, the examinees will enter the field faster than before, and the workload of the invigilatorand the psychological pressure of the examinees when they enter the examination room will be lightened.
Owner:赵太方
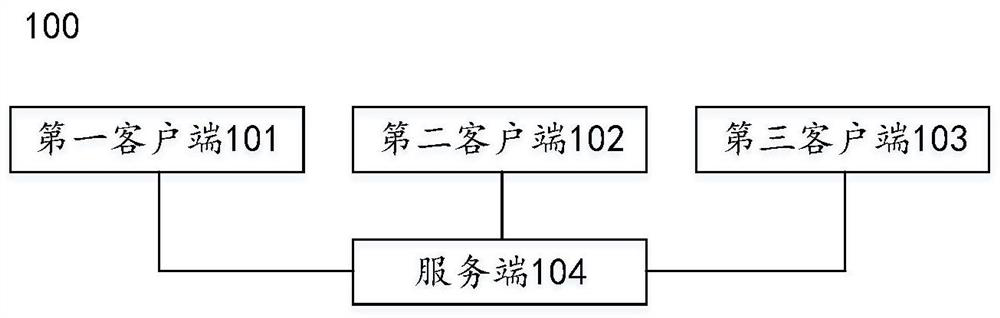
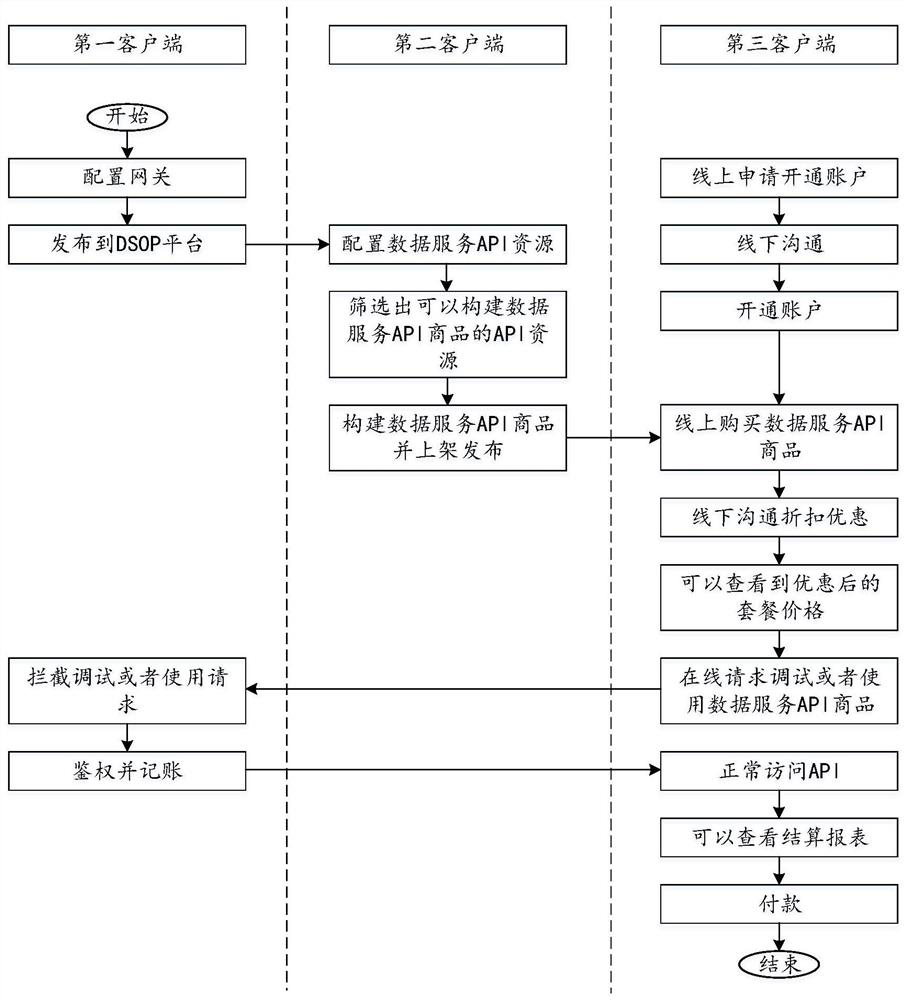
Data service operation platform
PendingCN113595789ASimplify platform integrationValid certificationData switching networksEngineeringDatabase access
The invention discloses a data service operation platform comprising a first client used for configuring gateway request information; a second client which is used for sending configuration request information of data service API resources and construction request information of data service API commodities to the server; a third client which is used for sending purchase request information or first use request information of the data service API commodity to the first client; a server which comprises a resource management module and an authentication module, wherein the resource management module is used for generating a target data service API resource and storing the target data service API resource to a database when the configuration request information is received; and the resource management module is also used for generating a target data service API commodity according to the target data service API resource and storing the target data service API commodity in a database when the construction request information is received. The method and the device at least solve the technical problems of how to simplify the integration mode of the data service operation platform, improve the calling safety of the API service and the accuracy of time counting and charging, and relieve the access pressure of the database.
Owner:深圳数鑫科技有限公司
A kind of SIP user authentication method and device
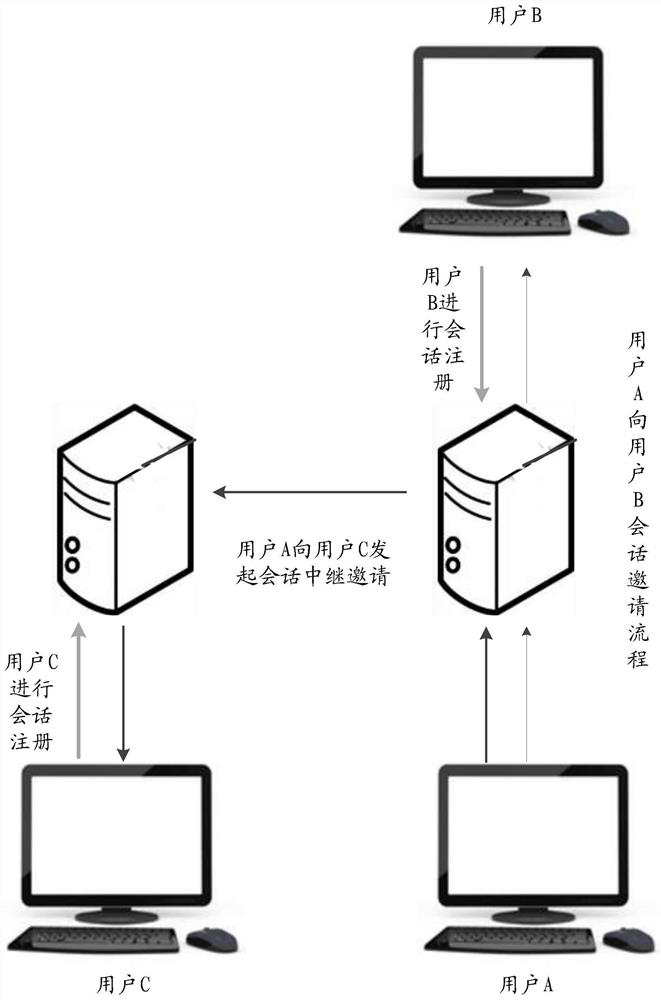
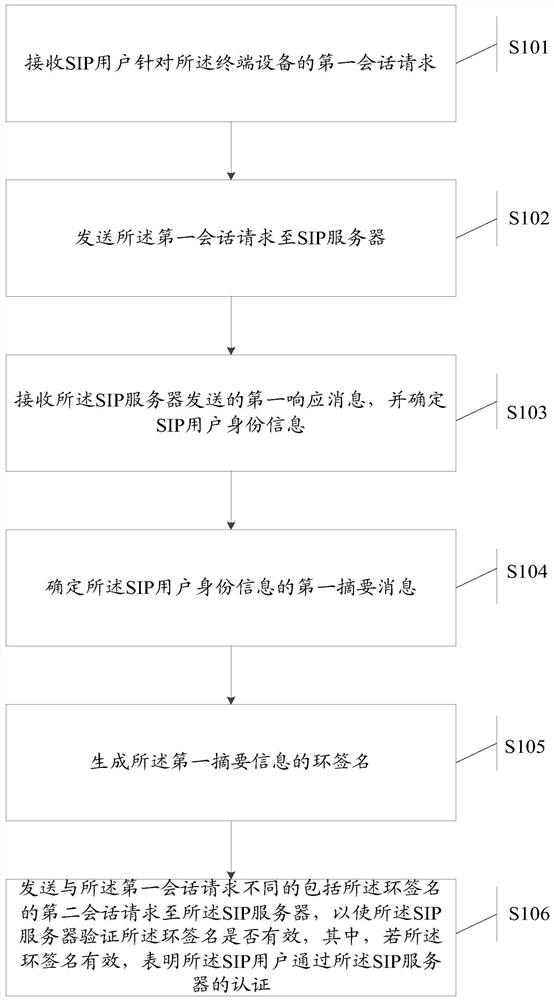
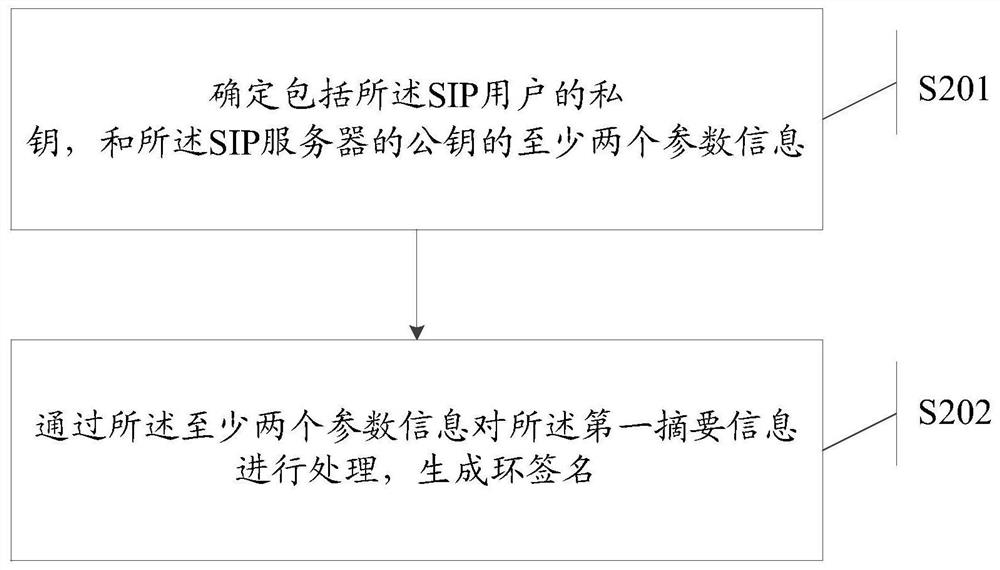
ActiveCN109995535BValid certificationSolve the technical problems of low certification efficiencyUser identity/authority verificationRing signatureTerminal equipment
Owner:CHINA MOBILEHANGZHOUINFORMATION TECH CO LTD +1
Game design cloud rendering system
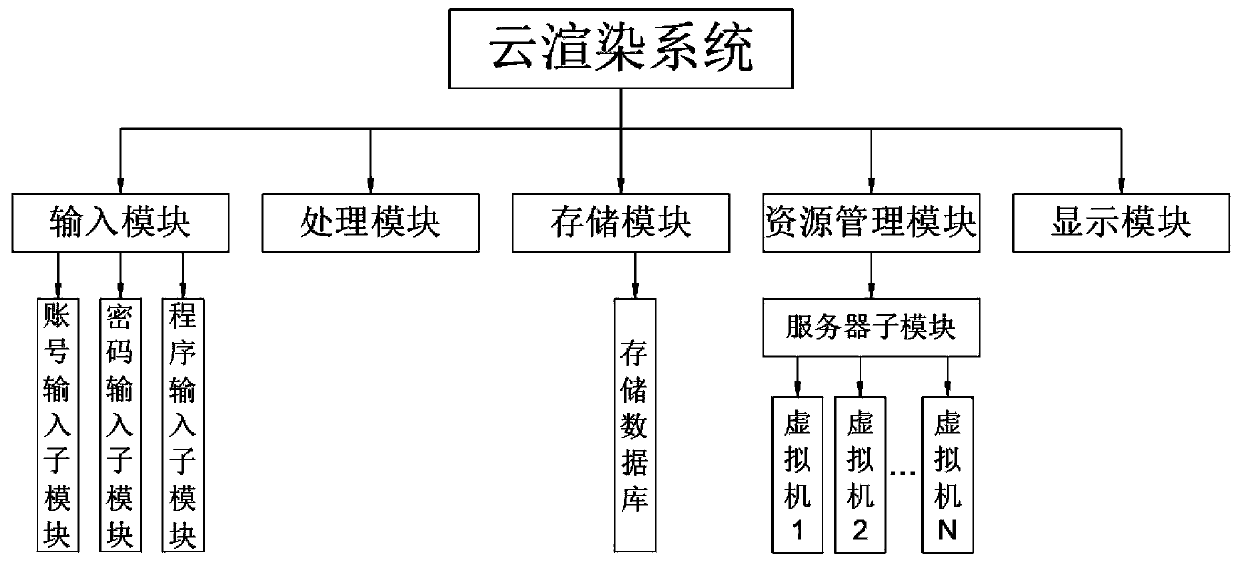
PendingCN111460402AValid certificationValid recordResource allocationSoftware engineeringVirtual machineResource management
The invention discloses a game design cloud rendering system. The cloud rendering system comprises an input module, a processing module, a storage module, a resource management module and a display module, and the input module comprises an account input sub-module, a password input sub-module and a program input sub-module. The storage module comprises a storage database, and the resource management module comprises a server sub-module. The server sub-module comprises a plurality of virtual machines. The system is scientific and reasonable, and has the advantage of safe and convenient use. Through the account number input sub-module and the password input sub-module, personnel logging in the cloud rendering system can be effectively authenticated and recorded, normal operation of the wholesystem is guaranteed, operation safety of the whole system is guaranteed, unified management of the whole system is facilitated, the rendering part of the game design program can be extracted throughthe processing module, and waste of network resources caused by overall rendering of the game design program is avoided.
Owner:广州问天信息技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com