Patents
Literature
198 results about "Identification scheme" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In metadata, an identification scheme is used to identify unique records in a set. If a data element is used to identify a record within a data set, the data element uses the Identifier representation term.
Content Metadata Directory Services
ActiveUS20070156726A1Improve interoperabilityIncrease the number ofMultimedia data indexingDigital data processing detailsContent IdentifierSystems management
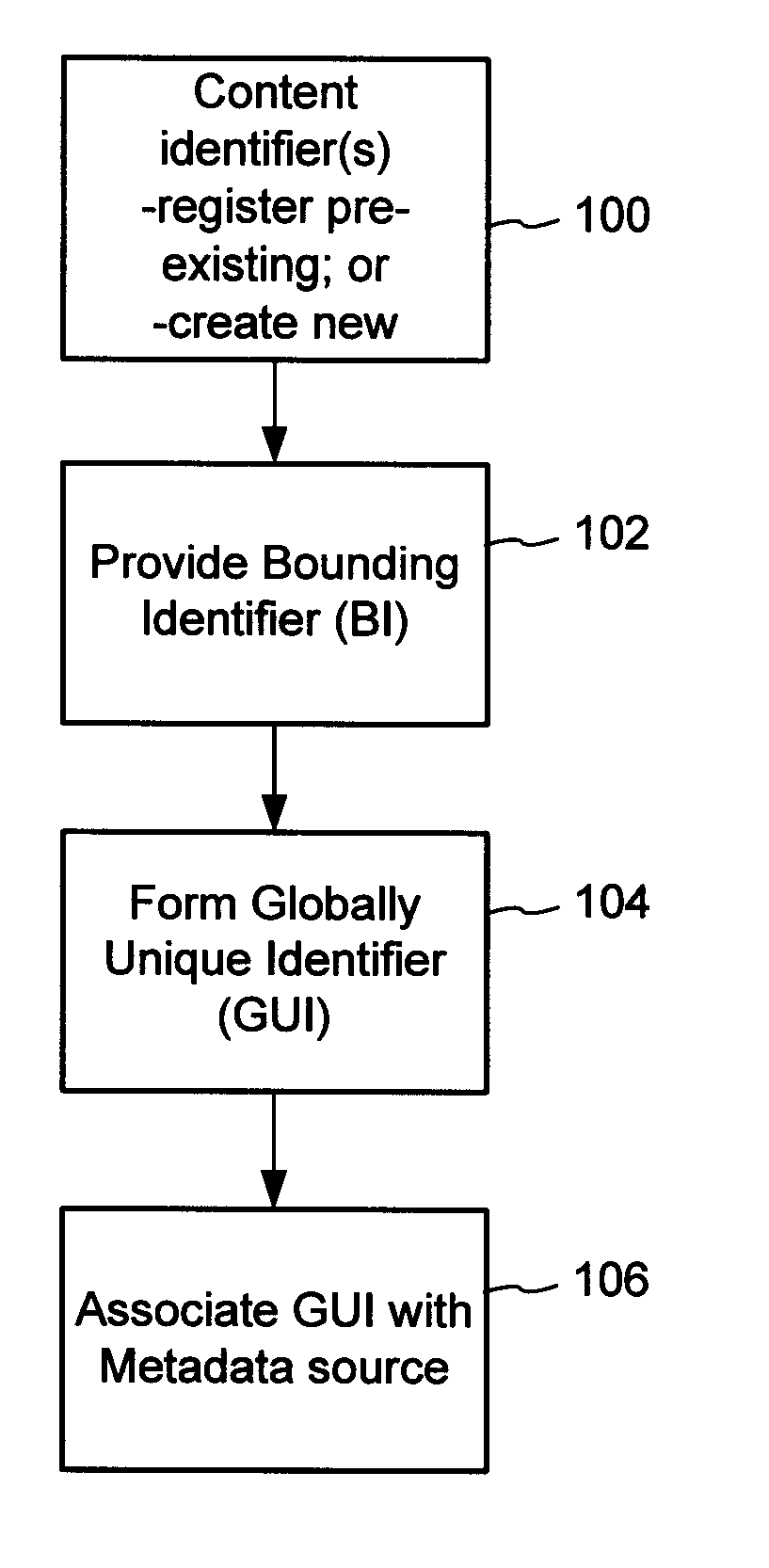
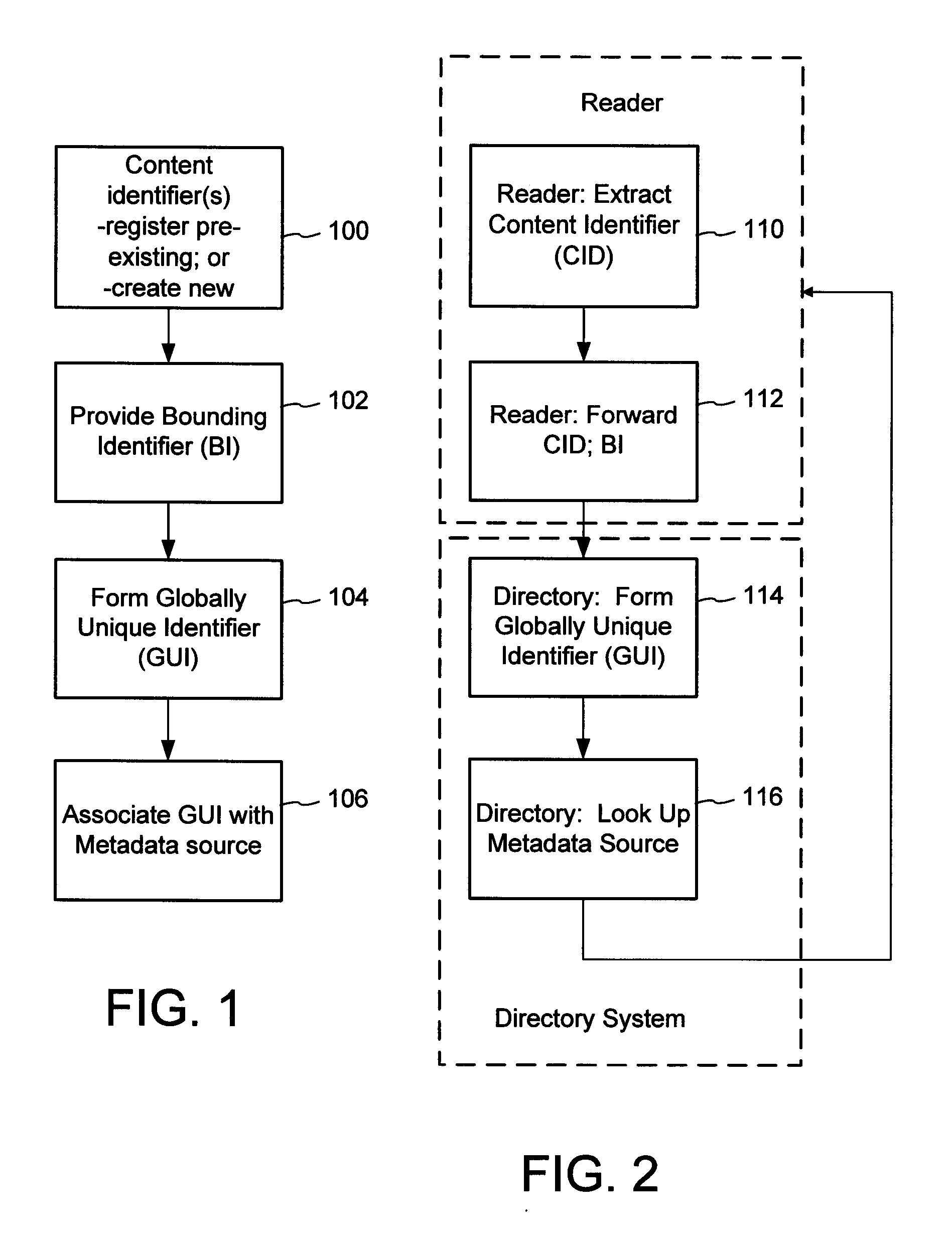
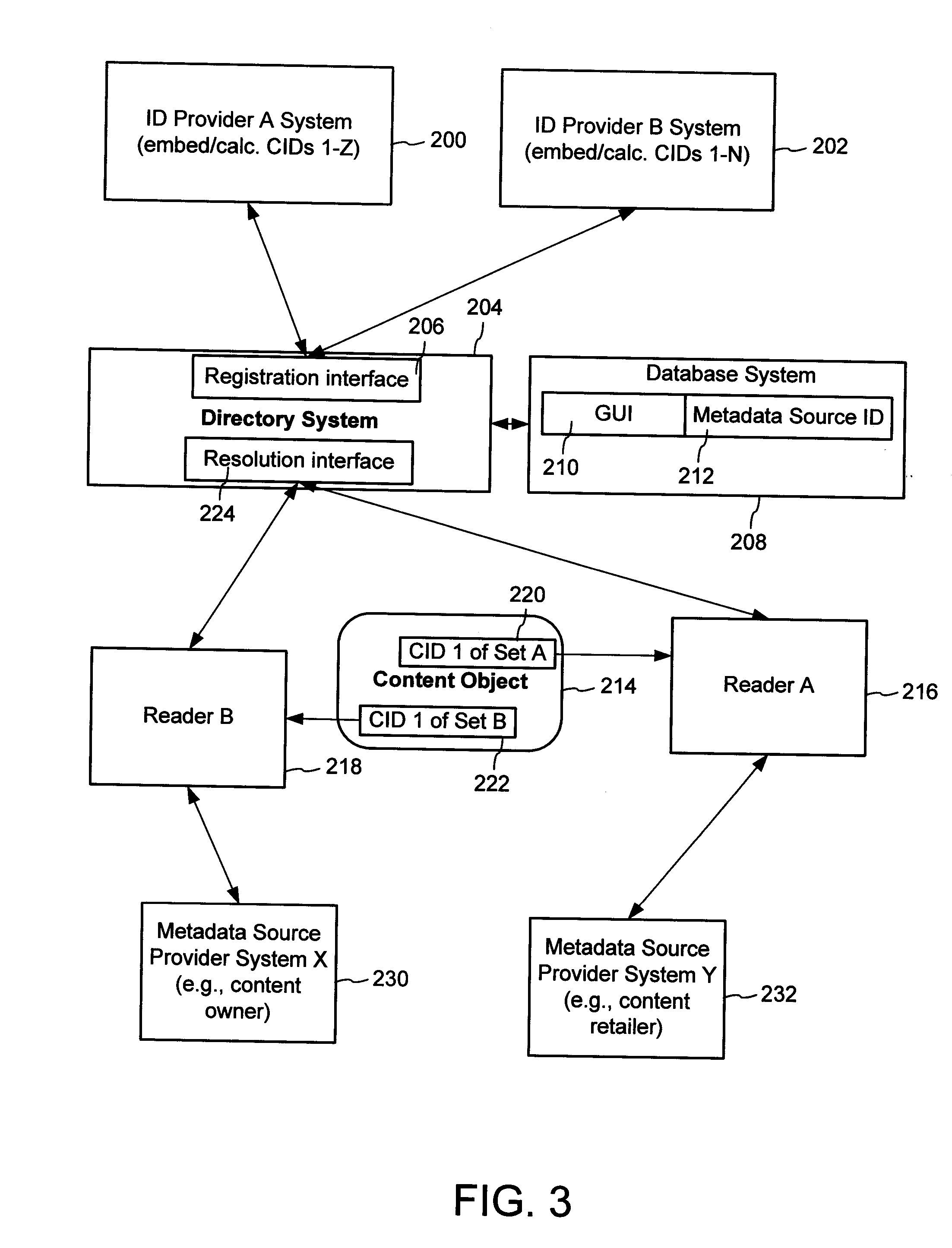
The content metadata directory system connects consumers of identified content to managed metadata databases and other digital resources. The system manages links between identifiers in content objects and metadata sources. It supports a variety of different type of content identifiers and allows for overlap among different content identification schemes. One method of associating a content object with metadata uses a combination of a content identifier and a bounding identifier to enable handling of disparate sets of content identifiers for content objects with potentially conflicting content identifiers. The method receives a content identifier for a content object from among a set of content identifiers and provides a unique bounding identifier for the set of content identifiers. This unique bounding identifier is used in combination with the content identifier to form a globally unique identifier for the content object. This globally unique identifier is associated with a metadata source, which enables routing of a user to the metadata source.
Owner:DIGIMARC CORP
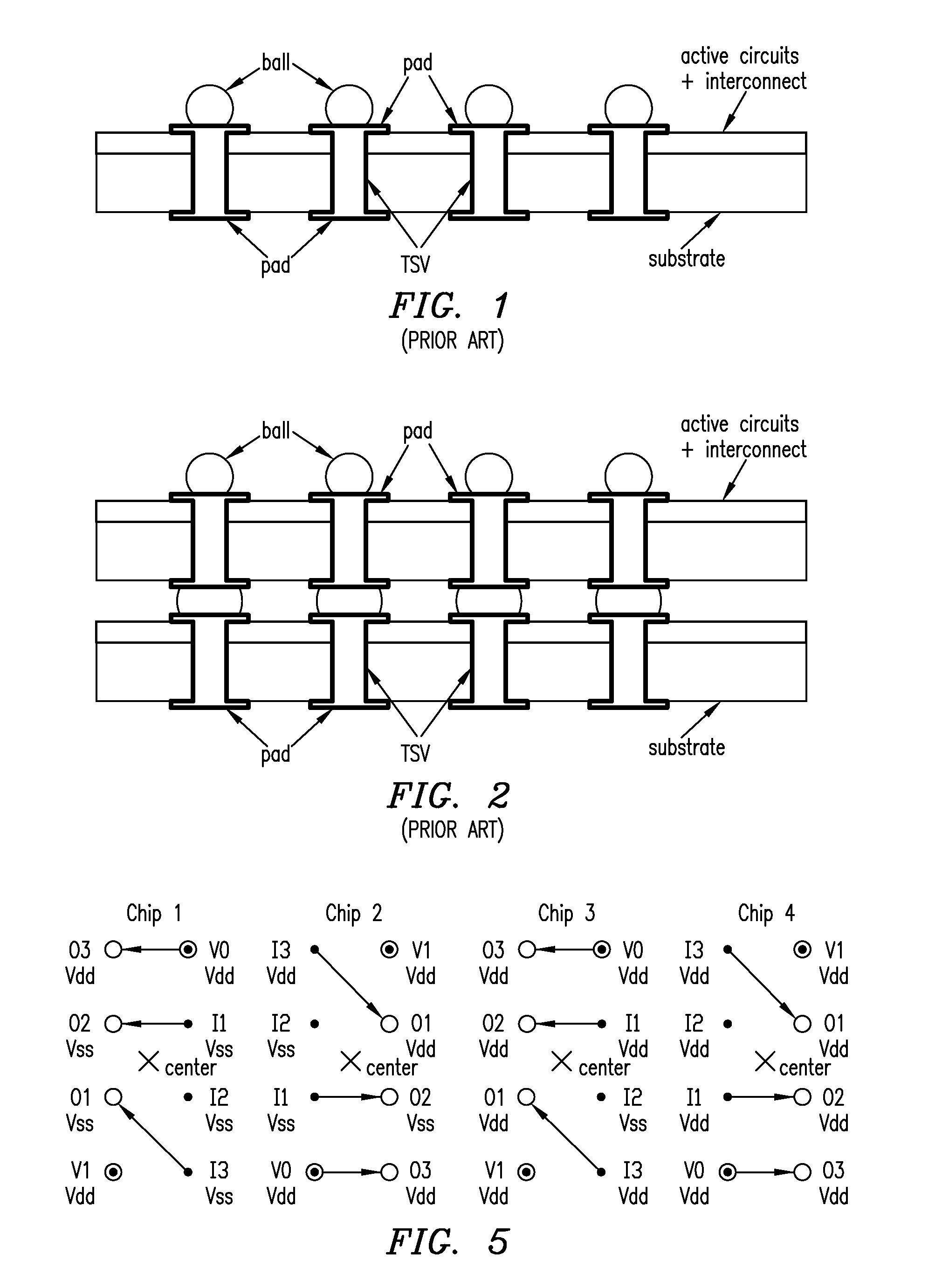
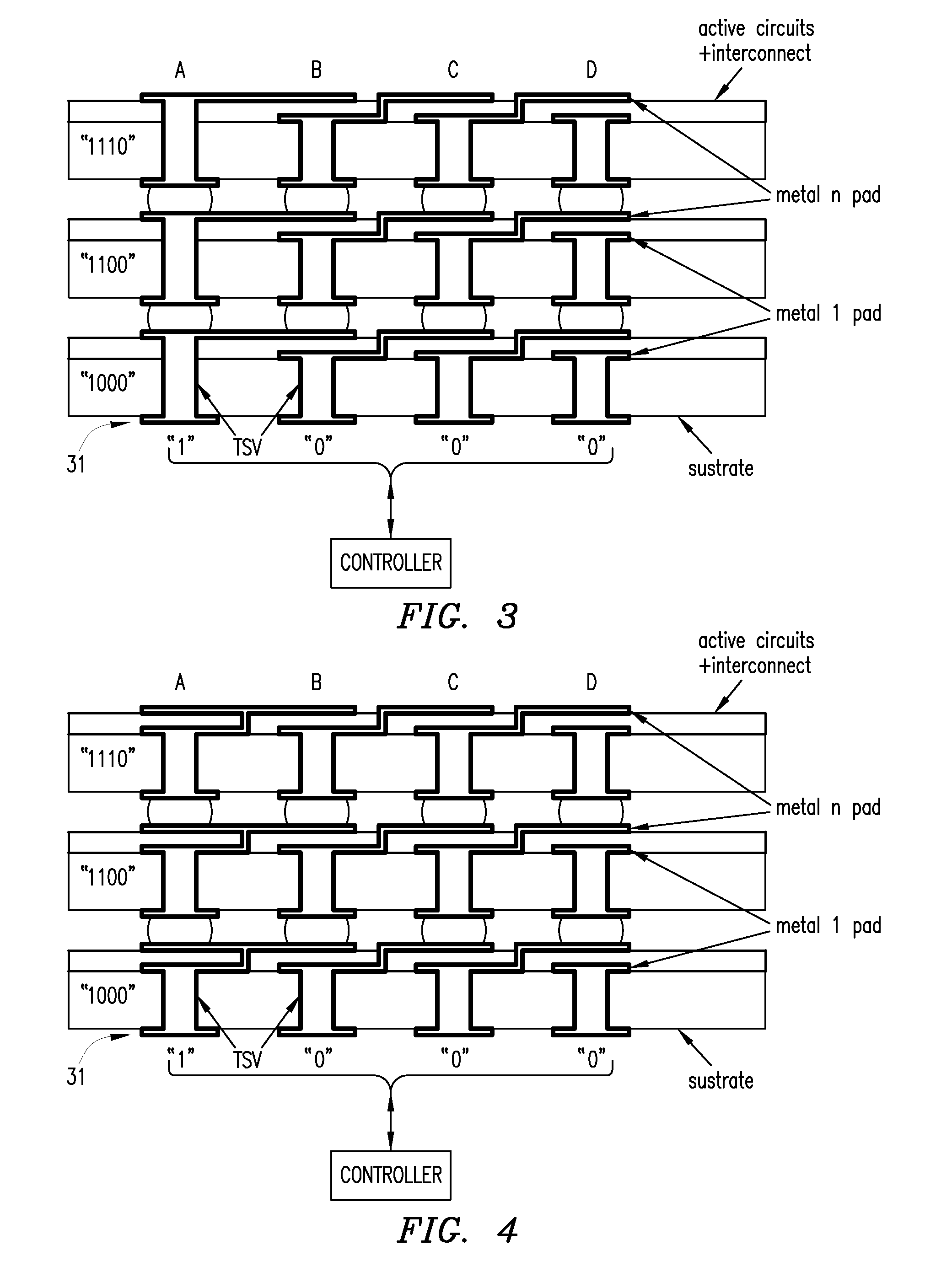
Using interrupted through-silicon-vias in integrated circuits adapted for stacking
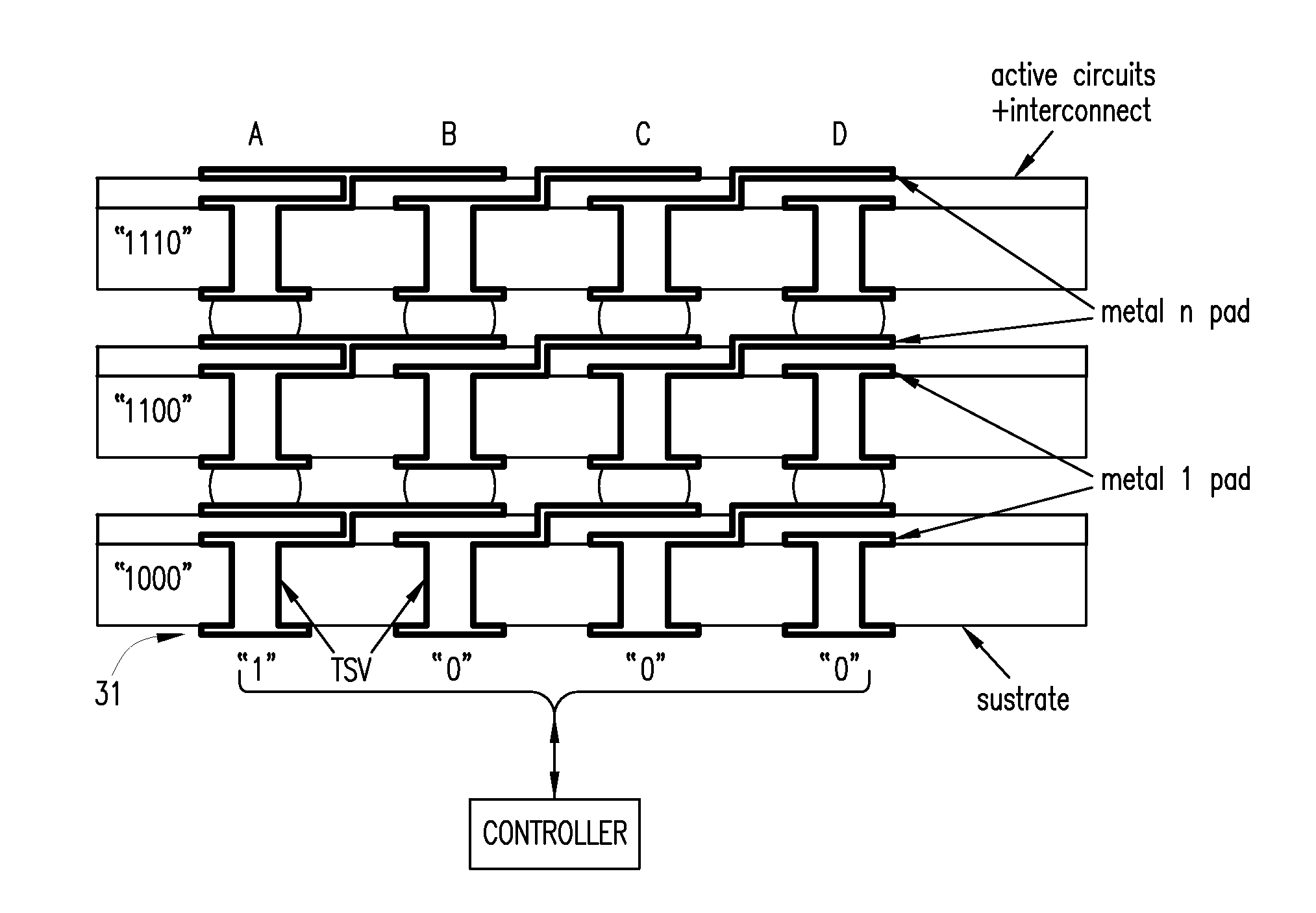
In an integrated circuit (IC) adapted for use in a stack of interconnected ICs, interrupted through-silicon-vias (TSVs) are provided in addition to uninterrupted TSVs. The interrupted TSVs provide signal paths other than common parallel paths between the ICs of the stack. This permits IC identification schemes and other functionalities to be implemented using TSVs, without requiring angular rotation of alternate ICs of the stack.
Owner:MOSAID TECH
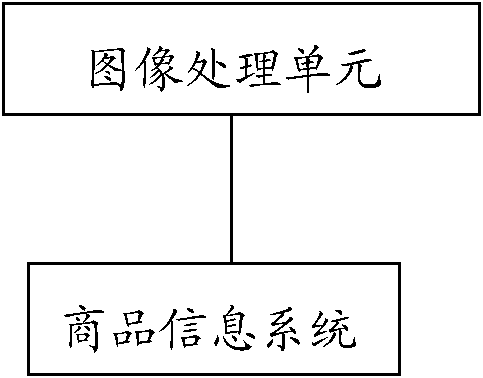
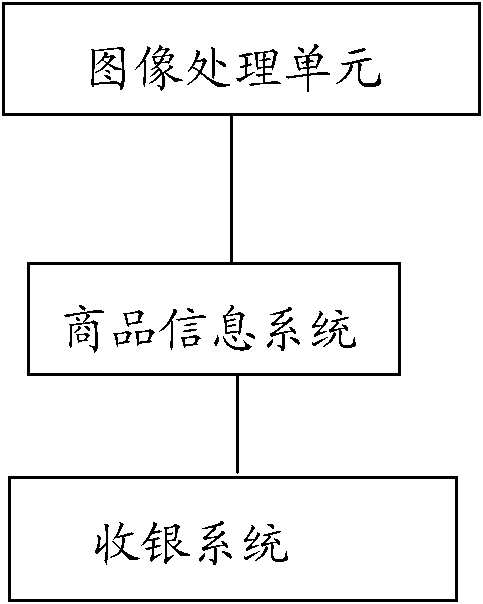
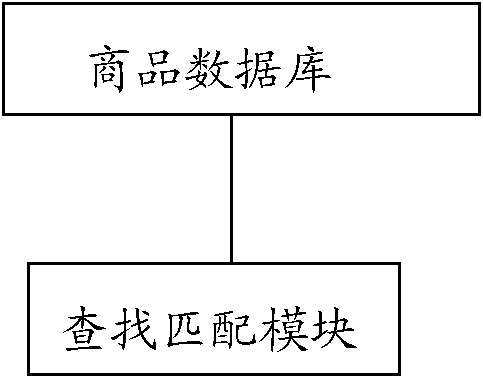
Automatic identification system and method for commodities based on image feature matching
InactiveCN102063616AFast recognitionHigh precisionCharacter and pattern recognitionImaging processingBarcode
The embodiment of the invention discloses an automatic identification system and method for commodities based on image feature matching, which are used in the field of information systems and are used for overcoming the defect of the traditional bar code process for commodity feature identification in a commodity sales system so as to provide an accurate real-time commodity feature identification scheme. The system comprises an image processing unit and a commodity information system, wherein the image processing unit is used for collecting the image data of the current commodity in real time and processing the image data of the current commodity to extract image feature information; the commodity information system is used for storing the image feature information of the commodity, and looking up and matching the image feature of the current commodity according to the image feature information of the commodity, which is collected in real time, and the current commodity is identified. In the automatic identification system, the image processing unit is used for collecting commodity images, processing and communicating, the commodity price is synchronously identified by the image identification process, and thus the automatic identification system has the advantages of high identification speed, high precision and favorable popularization and application values.
Owner:SHANGHAI DIANJI UNIV
System and method for immutably cataloging electronic assets in a large-scale computer system
InactiveUS20070260476A1Data processing applicationsDigital data information retrievalSurvivabilityObsolescence
Systems and / or methods for storing and / or retrieving assets in connection with an extremely large scale computer storage system are provided. An asset catalog may comprise a plurality of asset catalog entries stored according to at least one schema and corresponding to a plurality of assets. A storage architecture may be capable of storing the plurality of assets, with the storage architecture comprising a storage locator and a federator. An item identification scheme may be capable of providing identifiers to reference, locate, and / or access said assets and / or said asset catalog entries stored in the asset catalog in the storage architecture. The computer storage system may be scalable essentially without limitation while maintaining asset storage and retrieval flexibility and substantially obsolescence-proof survivability of assets.
Owner:LOCKHEED MARTIN CORP +1
Method and system for identifying transient process of non-intrusive load
ActiveCN106786534AAdaptableImprove accuracyAc network circuit arrangementsNear neighborSample sequence
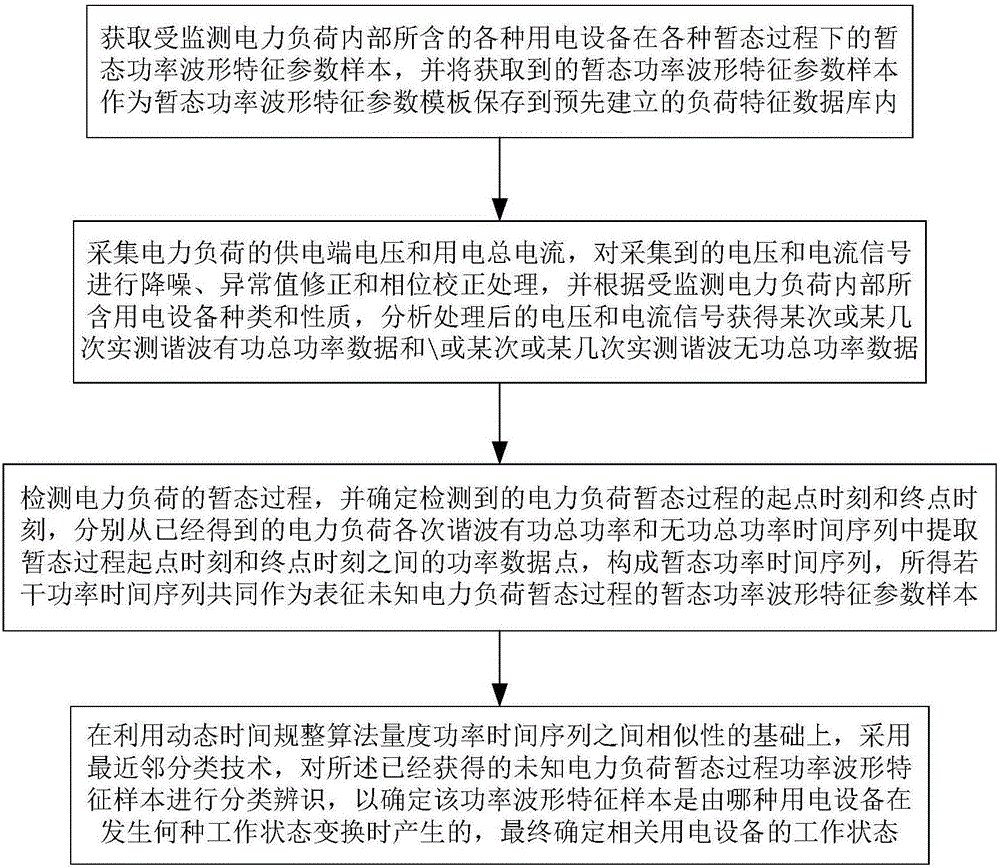
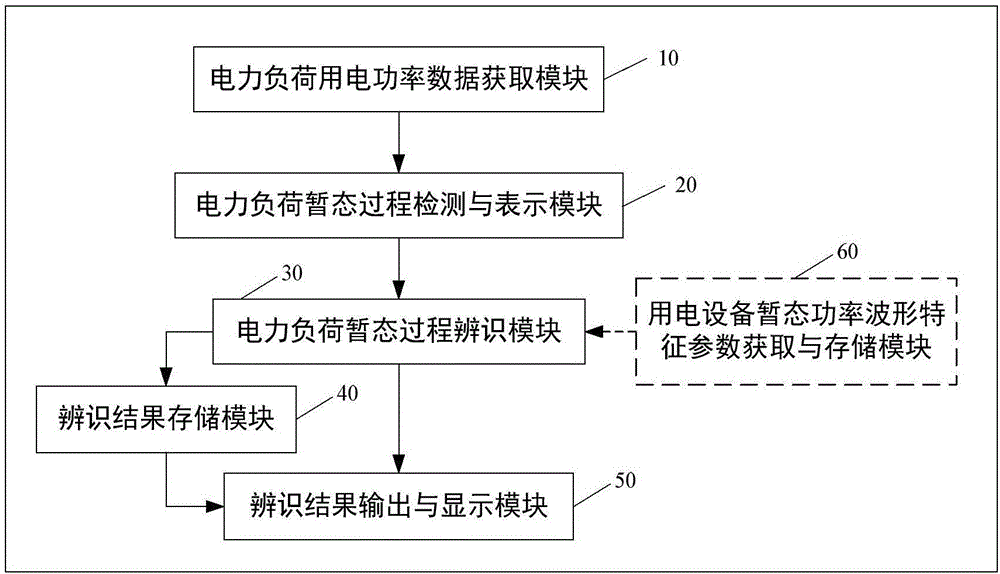
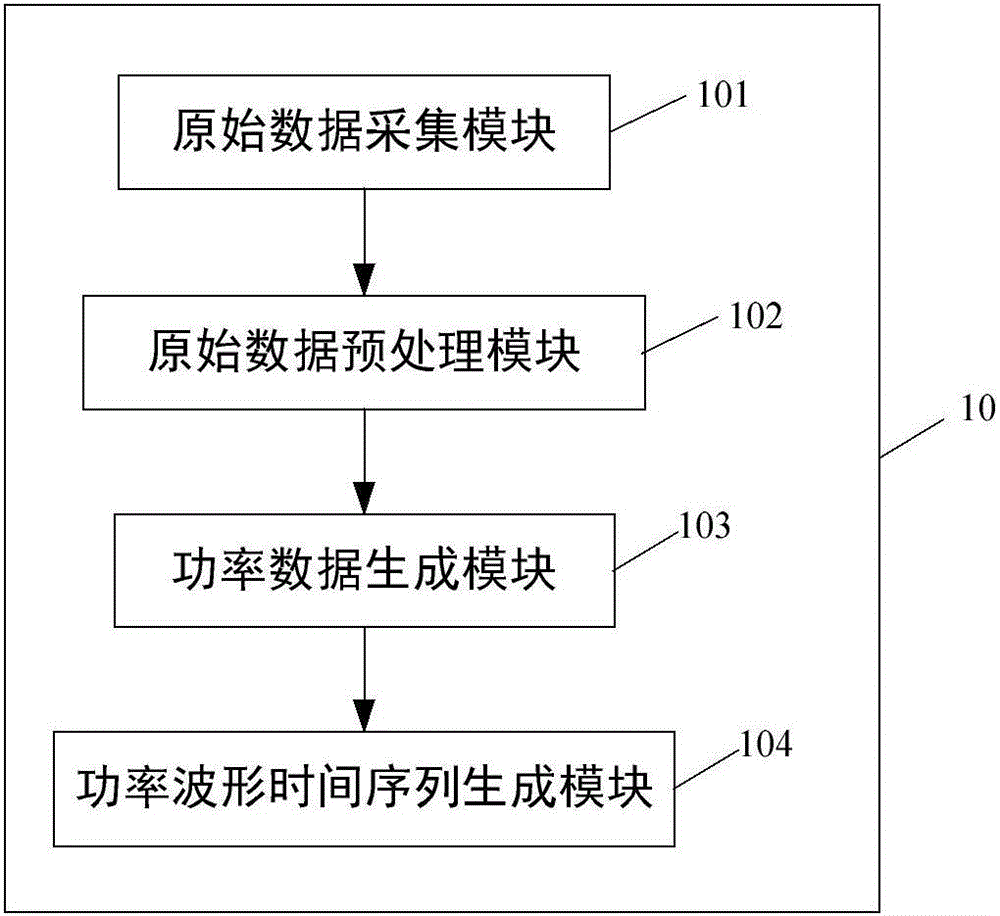
The invention belongs to the field of load power use monitoring and energy management, and particularly relates to a method and system for identifying transient process of a non-intrusive load. The method comprises the following steps: by virtue of transient power waveform characteristics of multiple types, measuring similarity of a transient power waveform characteristic parameter sample sequence of an unfixed length and a template sequence by using a dynamic time warping algorithm within a time domain, on the basis, establishing a load transient process classification identification scheme based on a nearest neighbor classification strategy, and confirming power use equipment with the load transient process, thereby achieving artificial working state identification on the non-intrusive type power use equipment. The method and the system have the beneficial effects that accuracy and robustness of power load transient process identification can be improved, the cost of a monitoring system can be effectively controlled, and the practicability of the monitoring system can be effectively improved, therefore, practical popularization of an NILM (Non-Intrusive Load monitoring) technique can be greatly improved.
Owner:TIANJIN TRANSENERGY TECH
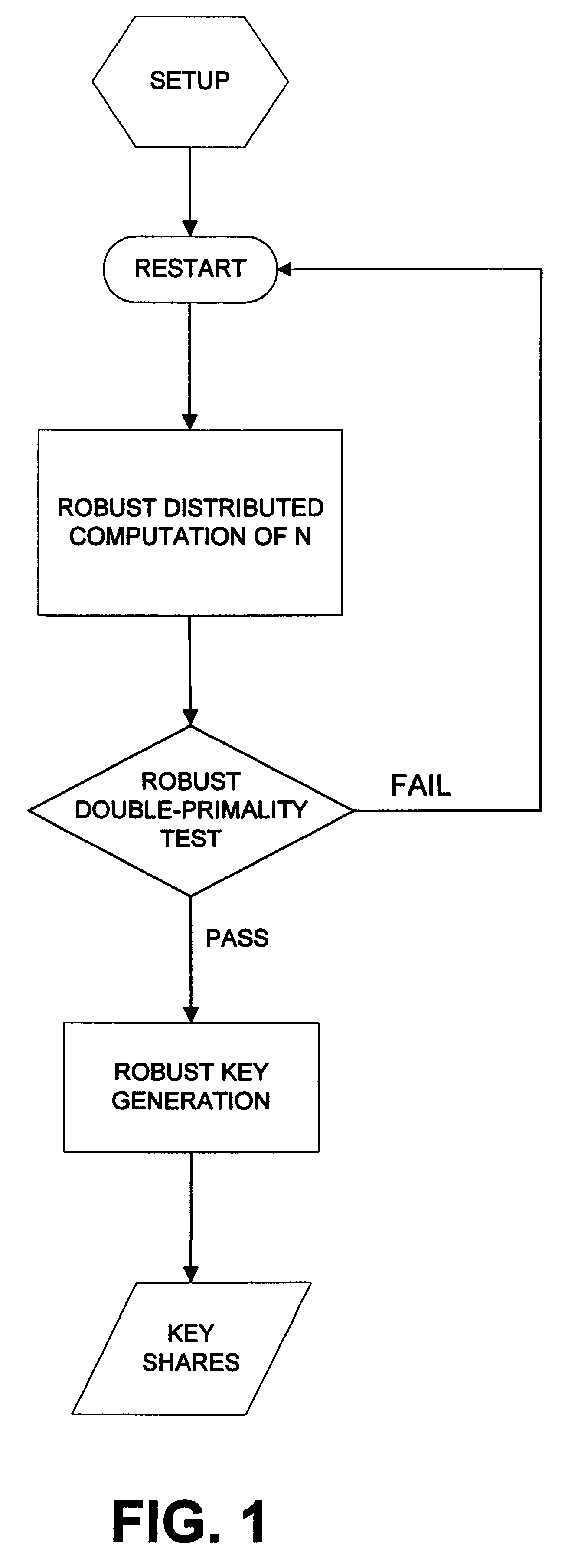
Robust efficient distributed RSA-key generation
InactiveUS6237097B1Reduce in quantityConfidenceKey distribution for secure communicationPublic key for secure communicationParallel computingEngineering
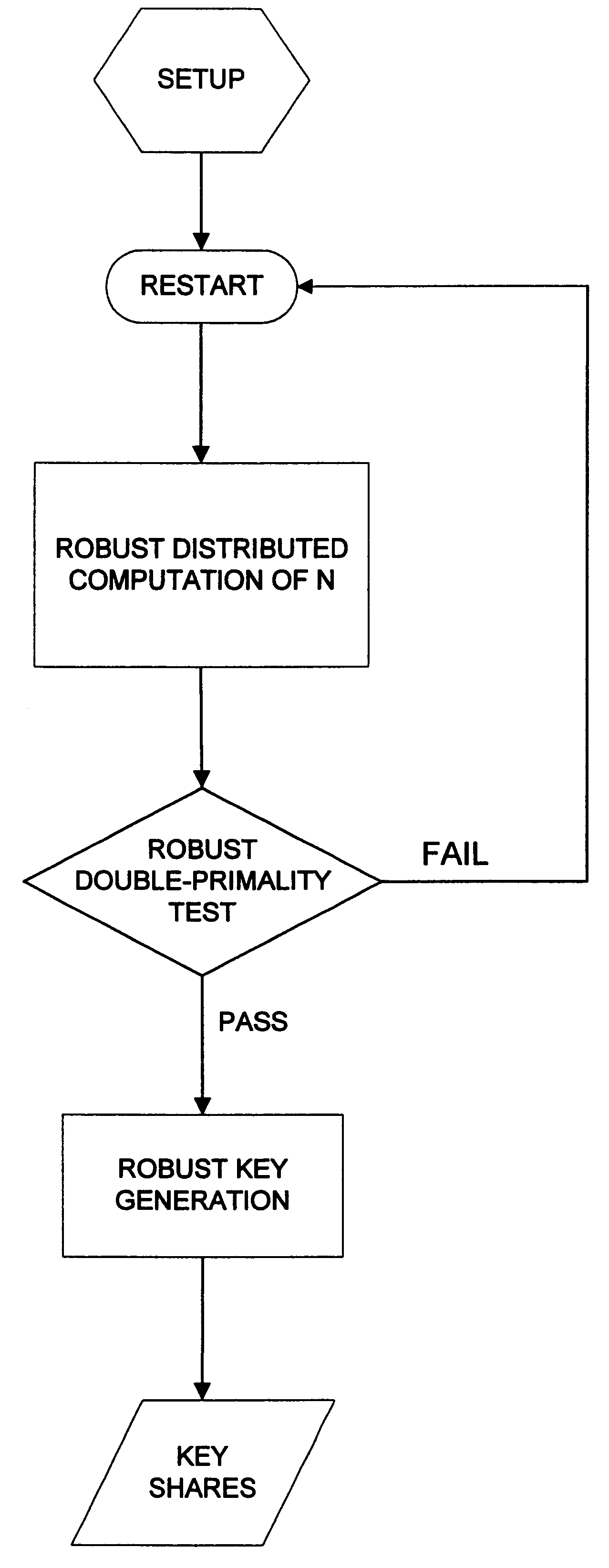
The invention provides for robust efficient distributed generation of RSA keys. An efficient protocol is one which is independent of the primality test "circuit size", while a robust protocol allows correct completion even in the presence of a minority of arbitrarily misbehaving malicious parties. The disclosed protocol is secure against any minority of malicious parties (which is optimal). The disclosed method is useful in establishing sensitive distributed cryptographic function sharing services (certification authorities, signature schemes with distributed trust, and key escrow authorities), as well as other applications besides RSA (namely: composite ElGamal, identification schemes, simultaneous bit exchange, etc.). The disclosed method can be combined with proactive function sharing techniques to establish the first efficient, optimal-resilience, robust and proactively-secure RSA-based distributed trust services where the key is never entrusted to a single entity (i.e., distributed trust totally "from scratch"). The disclosed method involves new efficient "robustness assurance techniques" which guarantee "correct computations" by mutually distrusting parties with malicious minority.
Owner:CERTCO
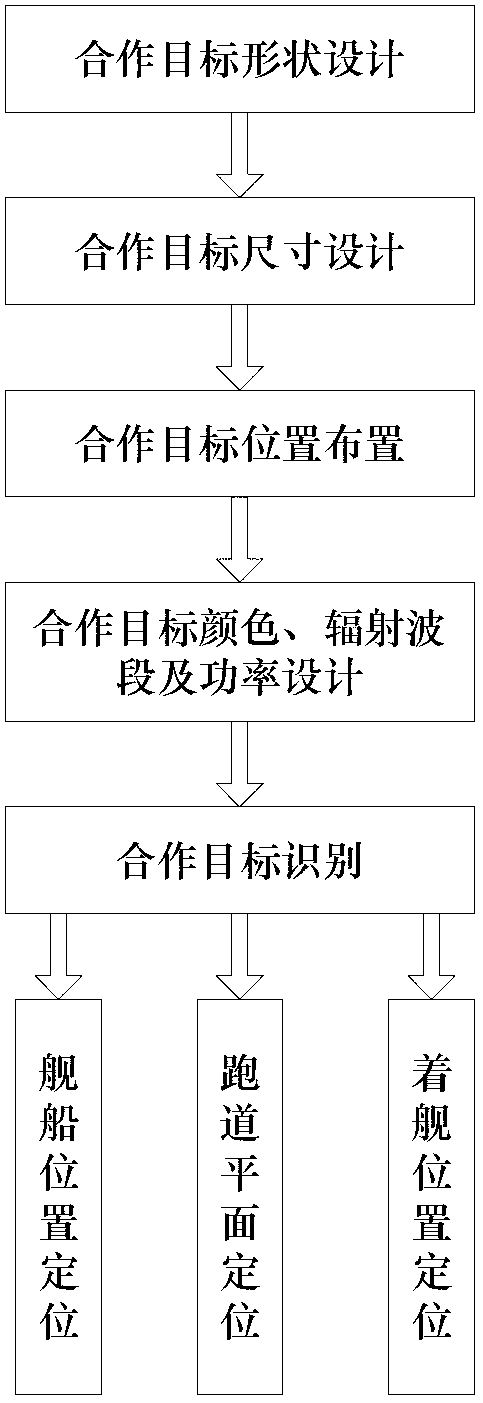
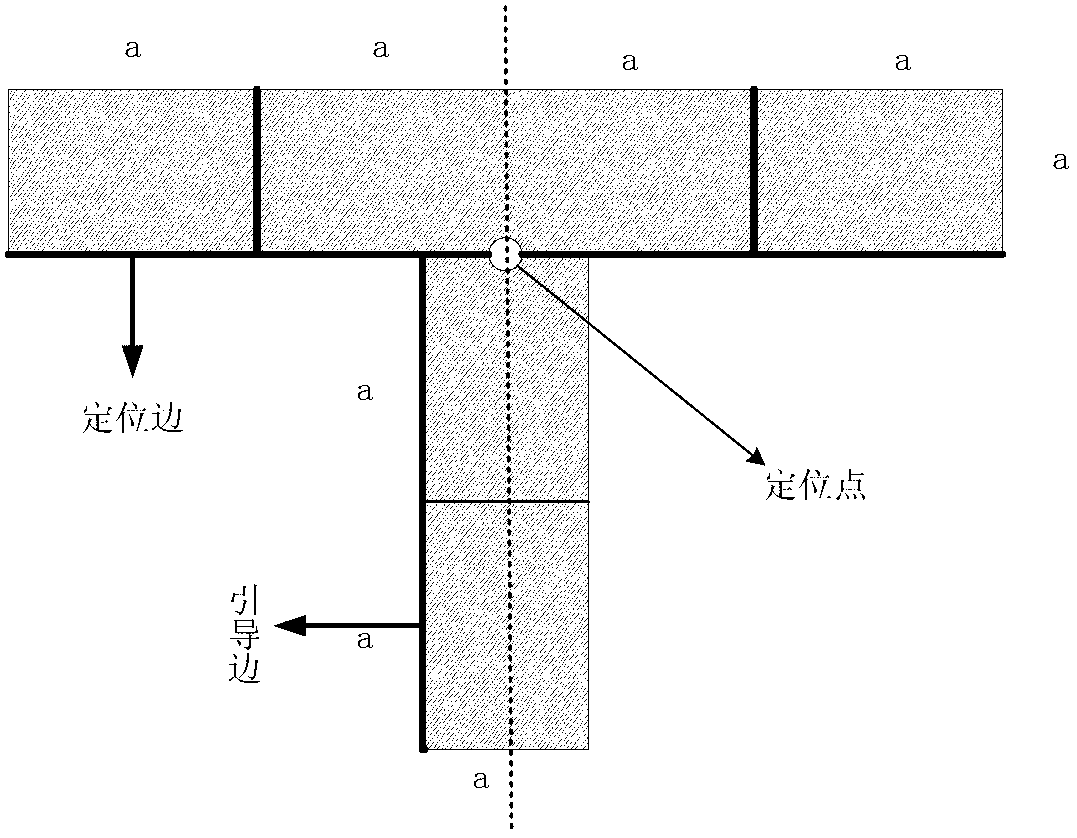
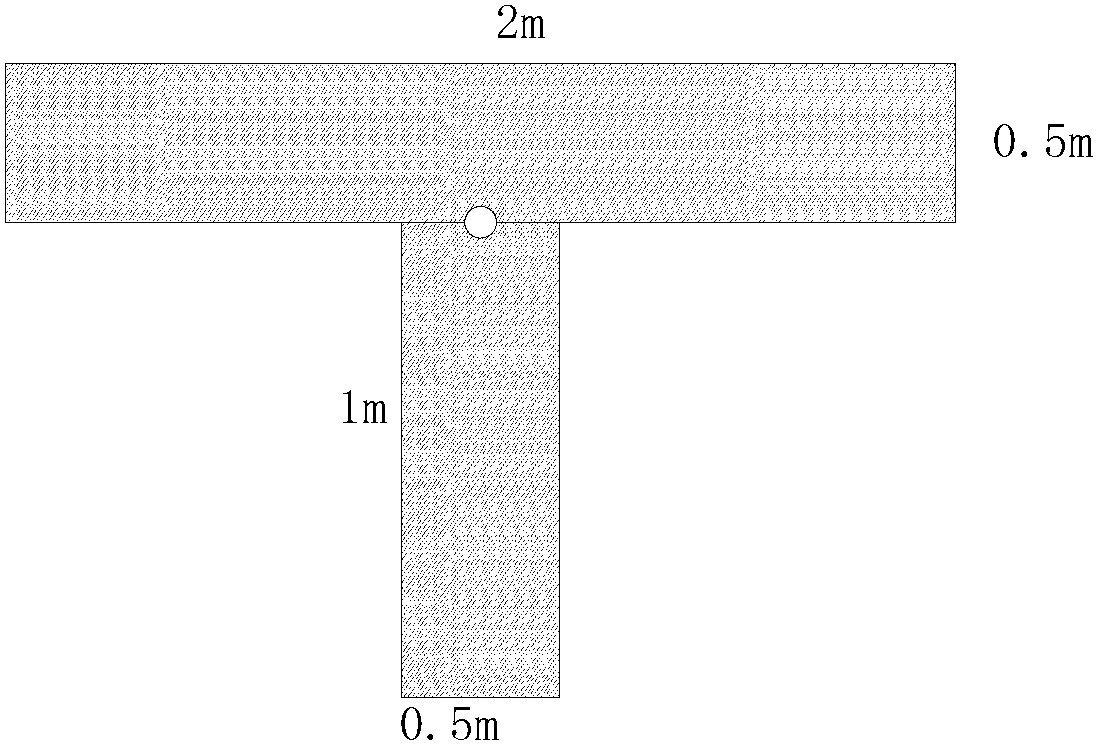
Cooperative target designing and locating method for unmanned aerial vehicle autonomous landing
ActiveCN103218607AEasy to identifyImprove robustnessCharacter and pattern recognitionFar distanceUncrewed vehicle
The invention belongs to the filed of visual navigation, and discloses a cooperative target designing and locating method for unmanned aerial vehicle autonomous landing. The method is based on the principle of being simple in structure and convenient to identify, having direction guidance, and facilitating accurate locating under the affine transformation condition, the shape, size, color, position arrangement and radiation band and power of the cooperative target are designed, and then an identification scheme of the cooperative target is designed. The identification scheme comprises 5000-meter far distance naval vessel position detection, 1000-meter middle distance runway plane locating and 500-meter near distance vessel landing position locating. By means of the cooperative target designing and locating method, safety and success rate of unmanned aerial vehicle autonomous landing can be improved, and the designed cooperative target is convenient to identify and locate and high in robustness. By means of computer view, the cooperative target can be fast identified, and unmanned aerial vehicle autonomous landing is achieved.
Owner:北京北航天宇长鹰无人机科技有限公司
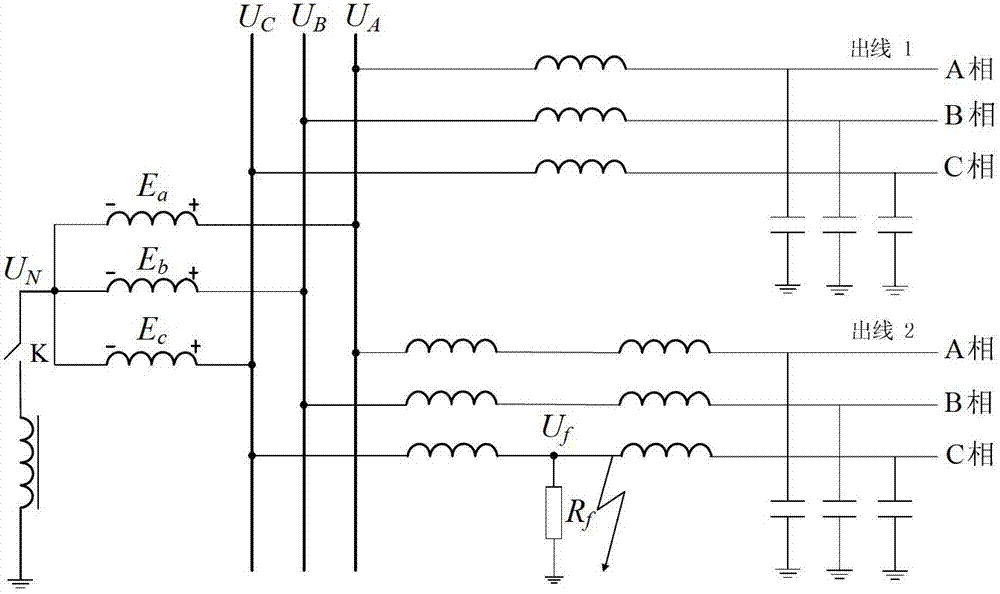
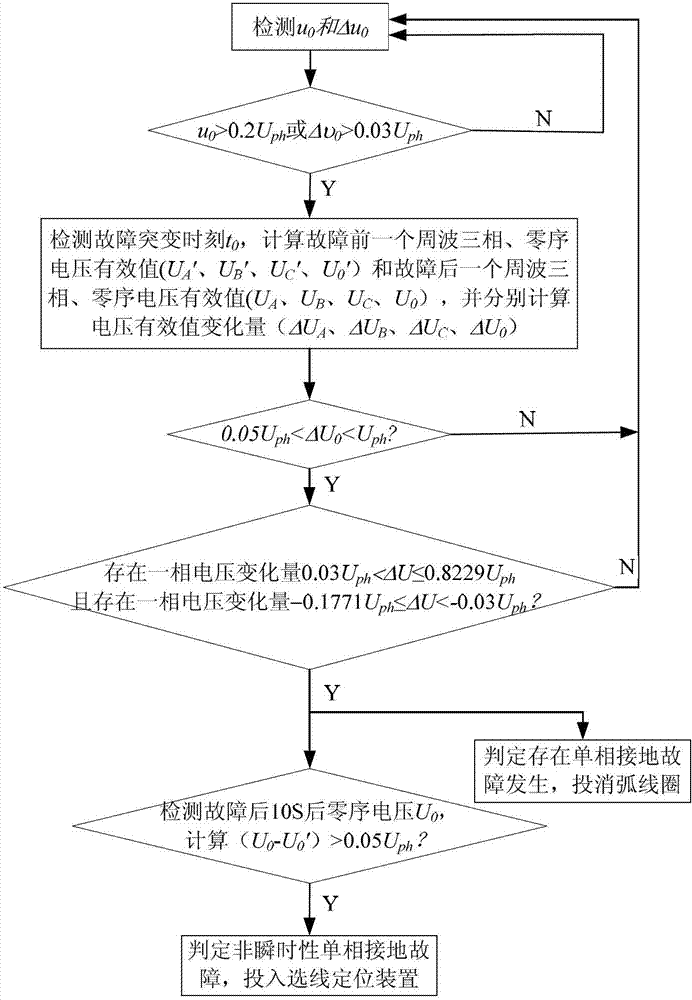
Neutral point non-effective earthing system single-phase earthing fault identification method
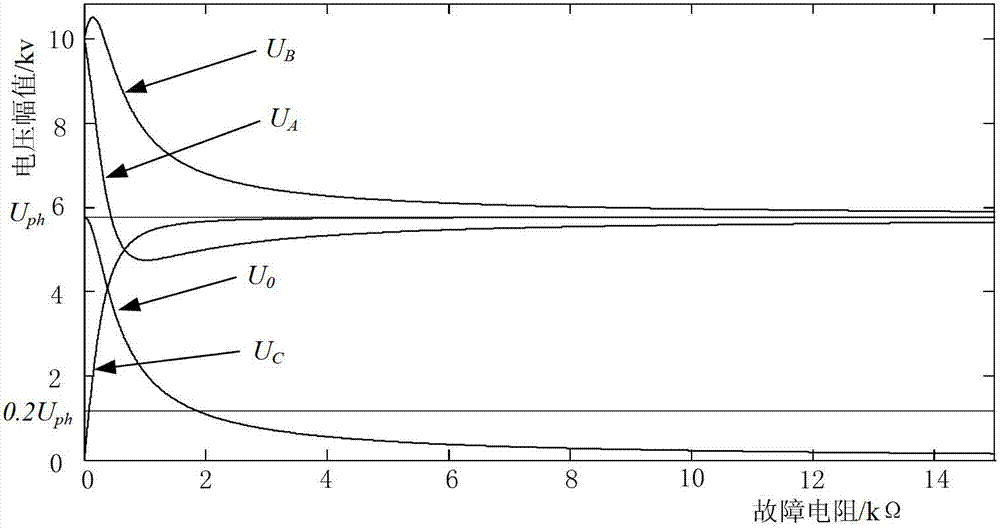
ActiveCN102955098AEfficiently reflects mutationsGuaranteed reliabilityFault locationThree-phaseEngineering
The invention discloses a neutral point non-effective earthing system single-phase earthing fault identification method which includes the steps that a zero sequence voltage instantaneous value and a instantaneous saltation value are taken as the startup criteria of an identification scheme; when any of the above values is out of the limit, an identification process is started, a saltation moment is determined according to a signal saltation point, and the effective values of the zero sequence voltages and the three-phase voltages in cycles before and after the signal saltation point and the variations of the effective values are calculated; and a single-phase earthing fault is judged to have happened only when the variation of the zero sequence voltage and the variations of all phases of voltage all satisfy all the criteria. The method takes voltage variation for identification, and the saltation of the state of the system can be reflected; a low threshold value scheme is adopted in the method, so the system can be started sensitively under a high impedance fault; and the multiple criteria scheme of zero sequence voltage and three-phase voltage are adopted, so the method has high reliability. The method is simple and easy to realize.
Owner:ZIYANG POWER SUPPLY COMPANY STATE GRID SICHUAN ELECTRIC POWER +2
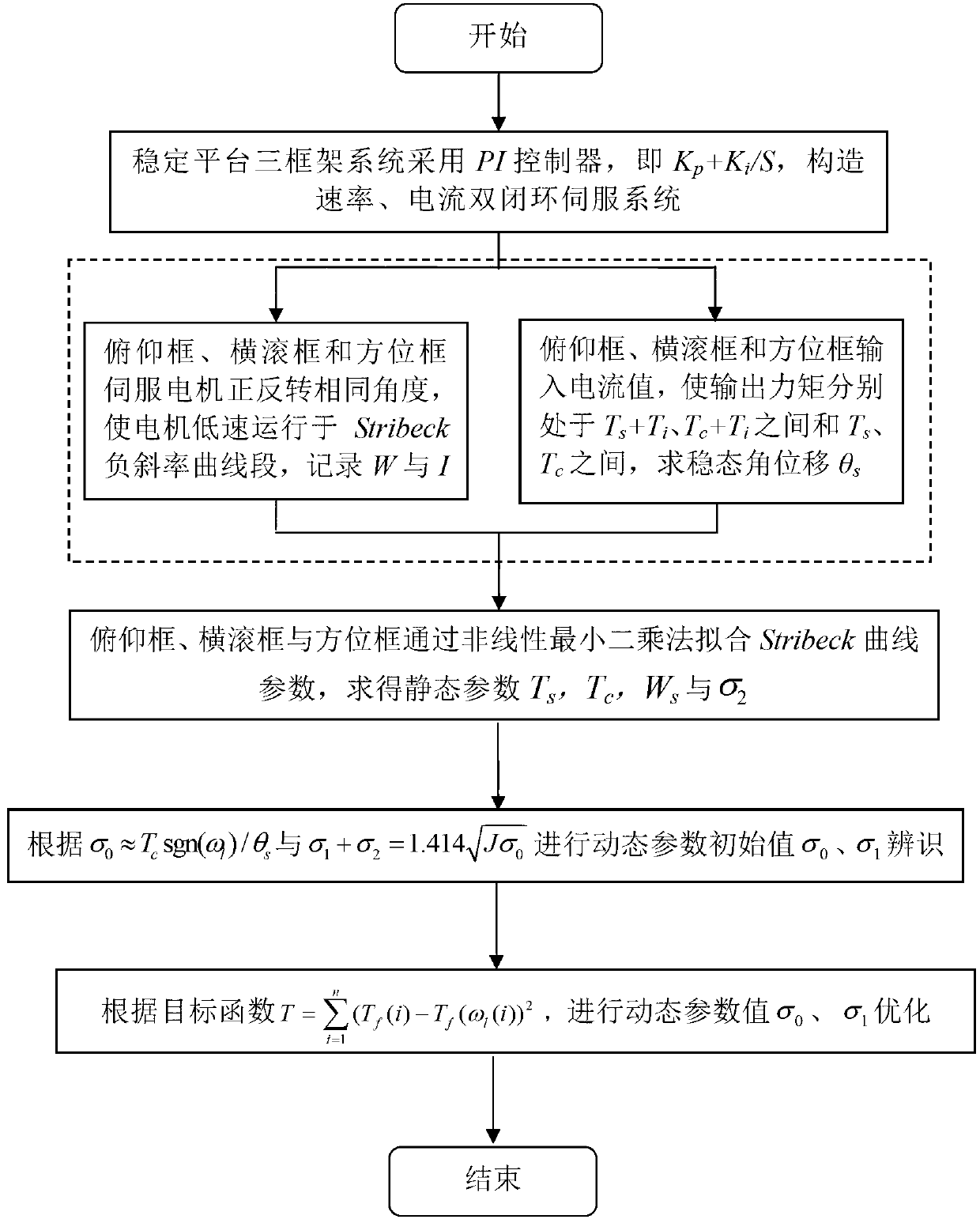
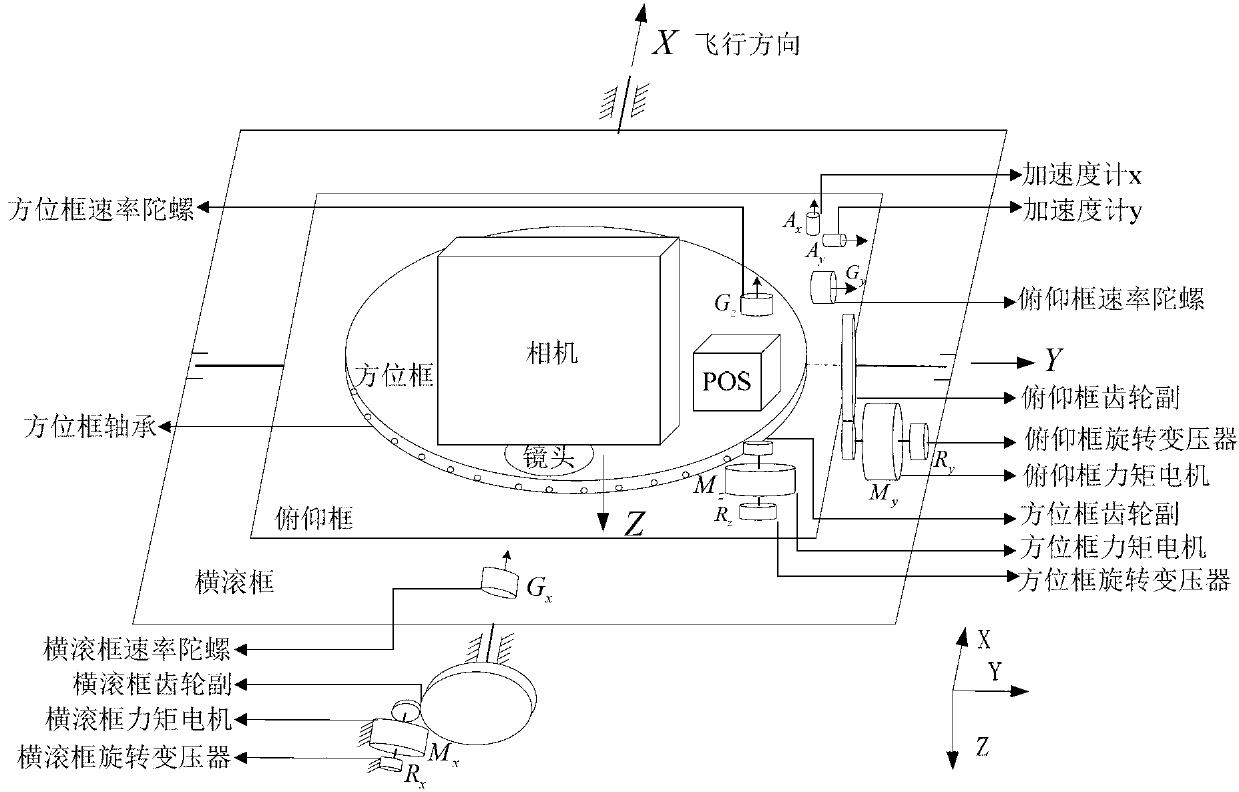
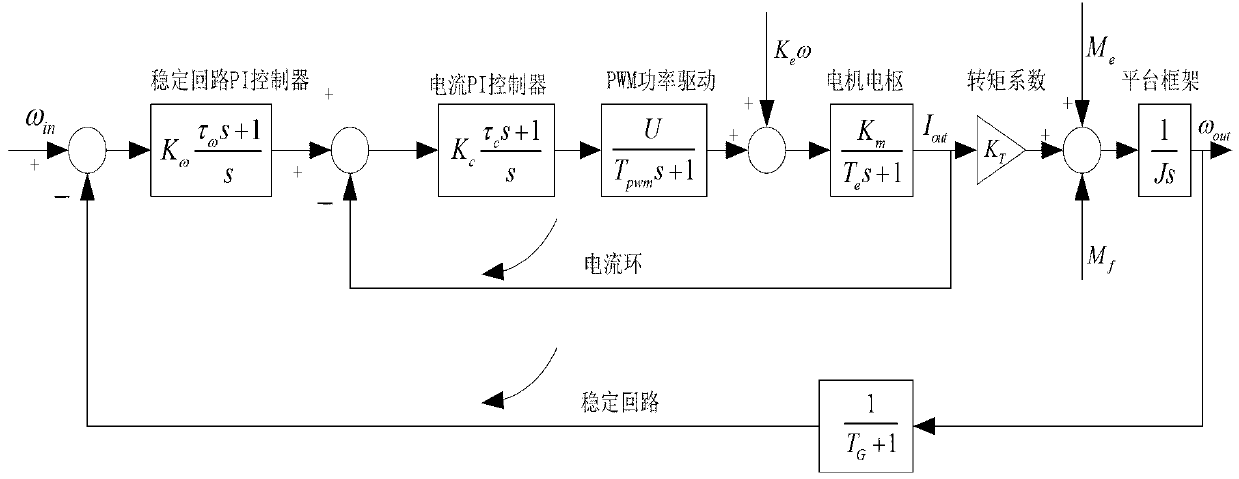
Friction parameter identification method for aerial remote-sensing inertial stabilization platform
InactiveCN103344243AHigh resolutionHigh precisionNavigation by speed/acceleration measurementsAdaptive controlAviationEngineering
Owner:BEIHANG UNIV
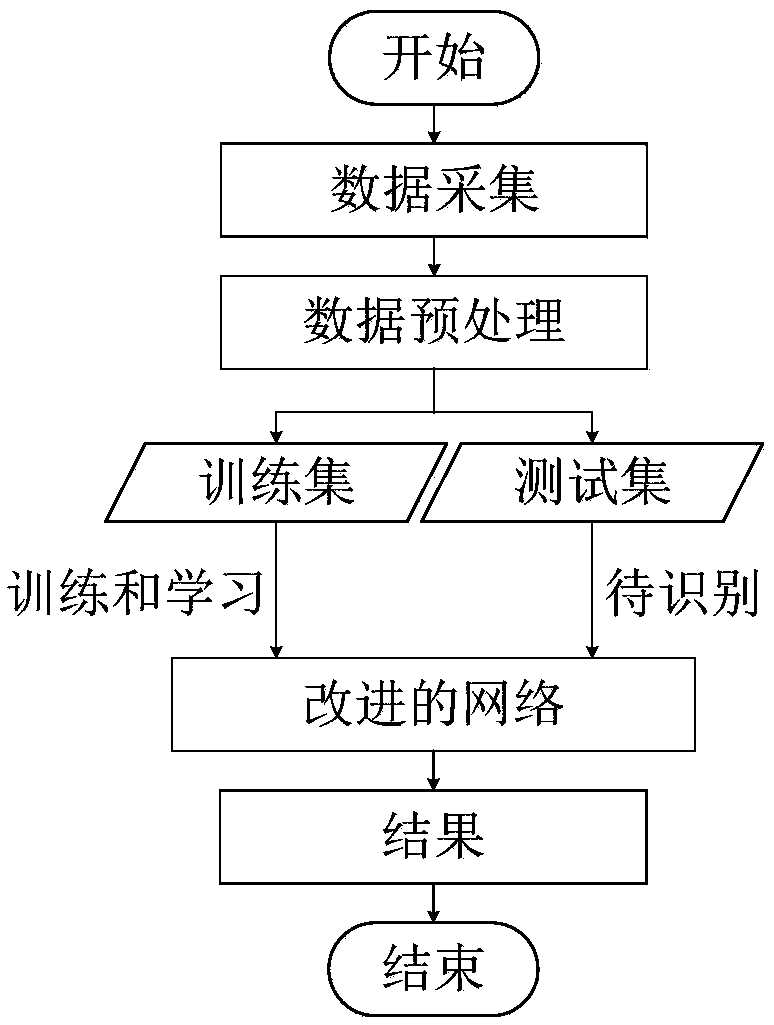
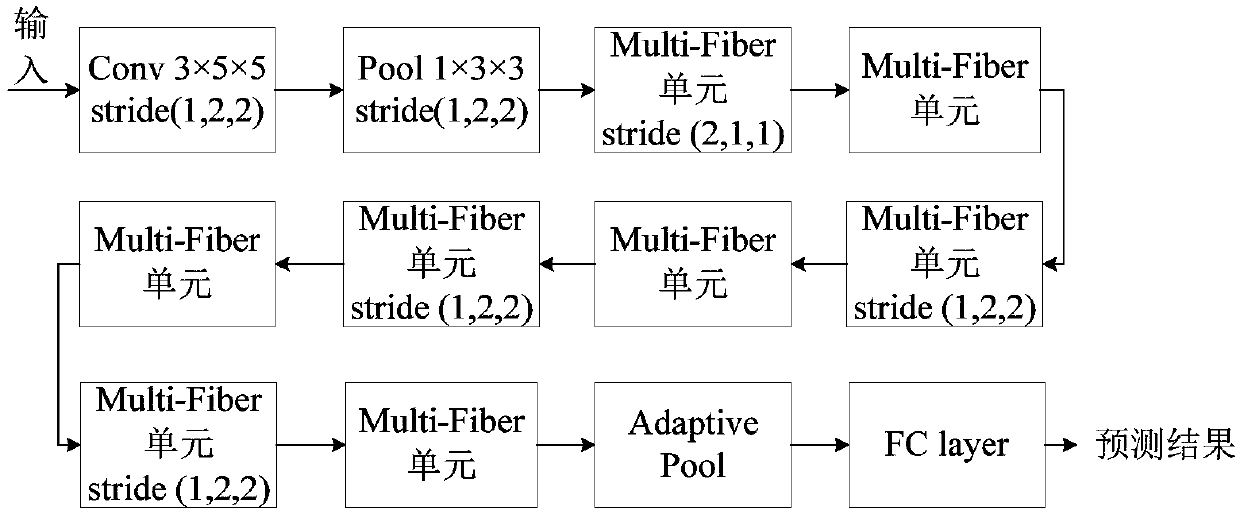
A pedestrian abnormal behavior identification method based on 3D convolution
PendingCN109635790AStay recognizableReduce computing costCharacter and pattern recognitionNeural architecturesNerve networkData set
The invention discloses a pedestrian abnormal behavior identification method based on 3D convolution. The pedestrian abnormal behavior identification method comprises the steps of S1, creating a dataset containing abnormal behaviors such as fighting, dog walking and falling; S2, in combination with the latest video behavior identification scheme, constructing a 3D convolutional neural network considering both precision and speed; S3, preprocessing the images in the data set, and sending the preprocessed images into a 3D convolutional neural network to obtain a video abnormal behavior recognition model; And S4, inputting a tested pedestrian monitoring video, and outputting an abnormal behavior type. According to the identification method provided by the invention, the lightweight 2D convolutional network MobileNet idea is migrated to the 3D network, so that the calculation cost can be reduced on the basis of maintaining the identification performance; Meanwhile, a self-adaptive poolinglayer and a sparse time sampling strategy are adopted, so that a large amount of redundant information and fuzzy noise contained in continuous frames can be reduced.
Owner:HANGZHOU DIANZI UNIV
System and method for an immutable identification scheme in a large-scale computer system
ActiveUS20070260621A1FlexibilityMaintenanceDigital data information retrievalData processing applicationsSurvivabilityObsolescence
Systems and / or methods for storing and / or retrieving assets in connection with an extremely large scale computer storage system are provided. An asset catalog may comprise a plurality of asset catalog entries stored according to at least one schema and corresponding to a plurality of assets. A storage architecture may be capable of storing the plurality of assets, with the storage architecture comprising a storage locator and a federator. An item identification scheme may be capable of providing identifiers to reference, locate, and / or access said assets and / or said asset catalog entries stored in the asset catalog in the storage architecture. The computer storage system may be scalable essentially without limitation while maintaining asset storage and retrieval flexibility and substantially obsolescence-proof survivability of assets.
Owner:LOCKHEED MARTIN CORP +1
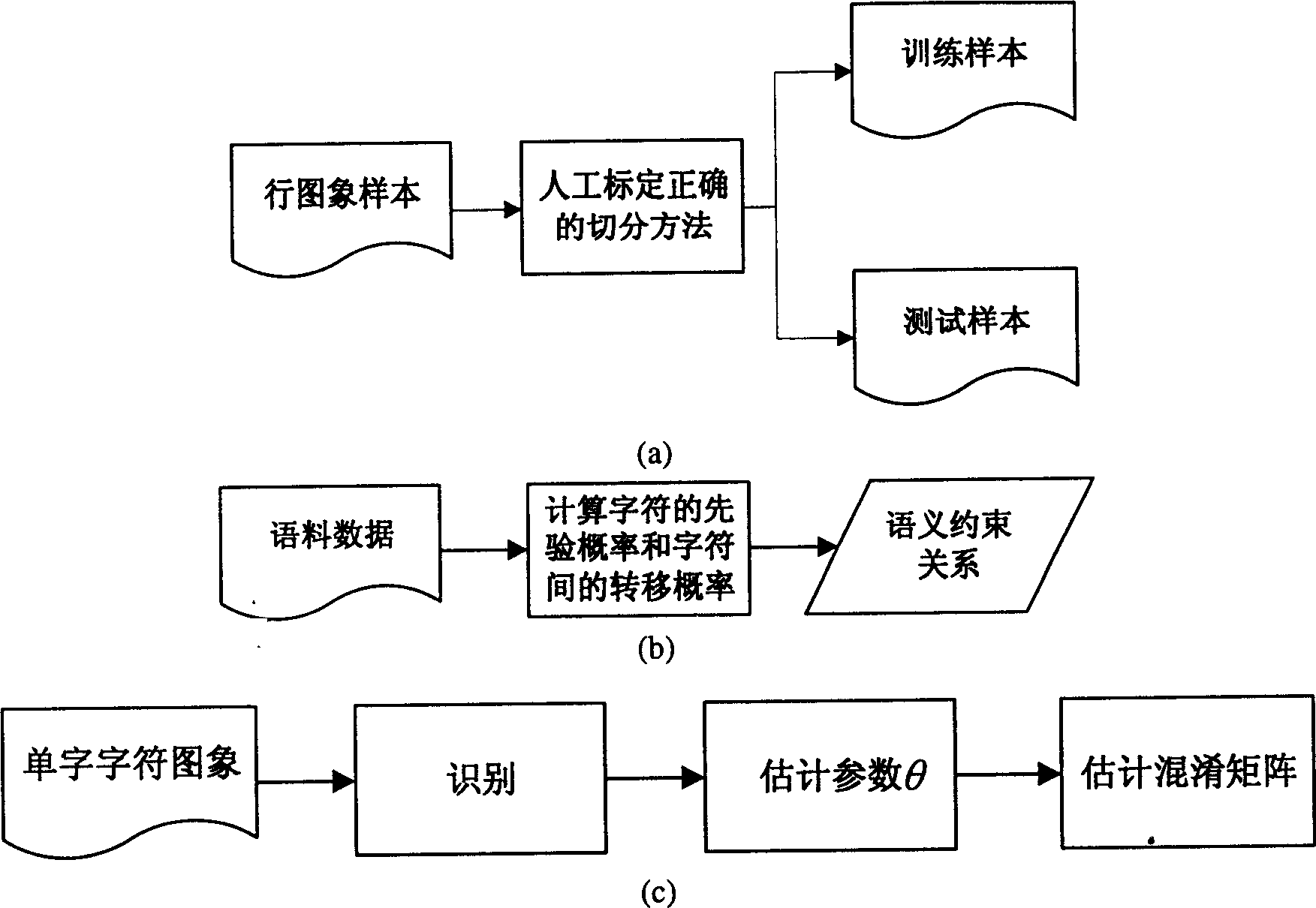
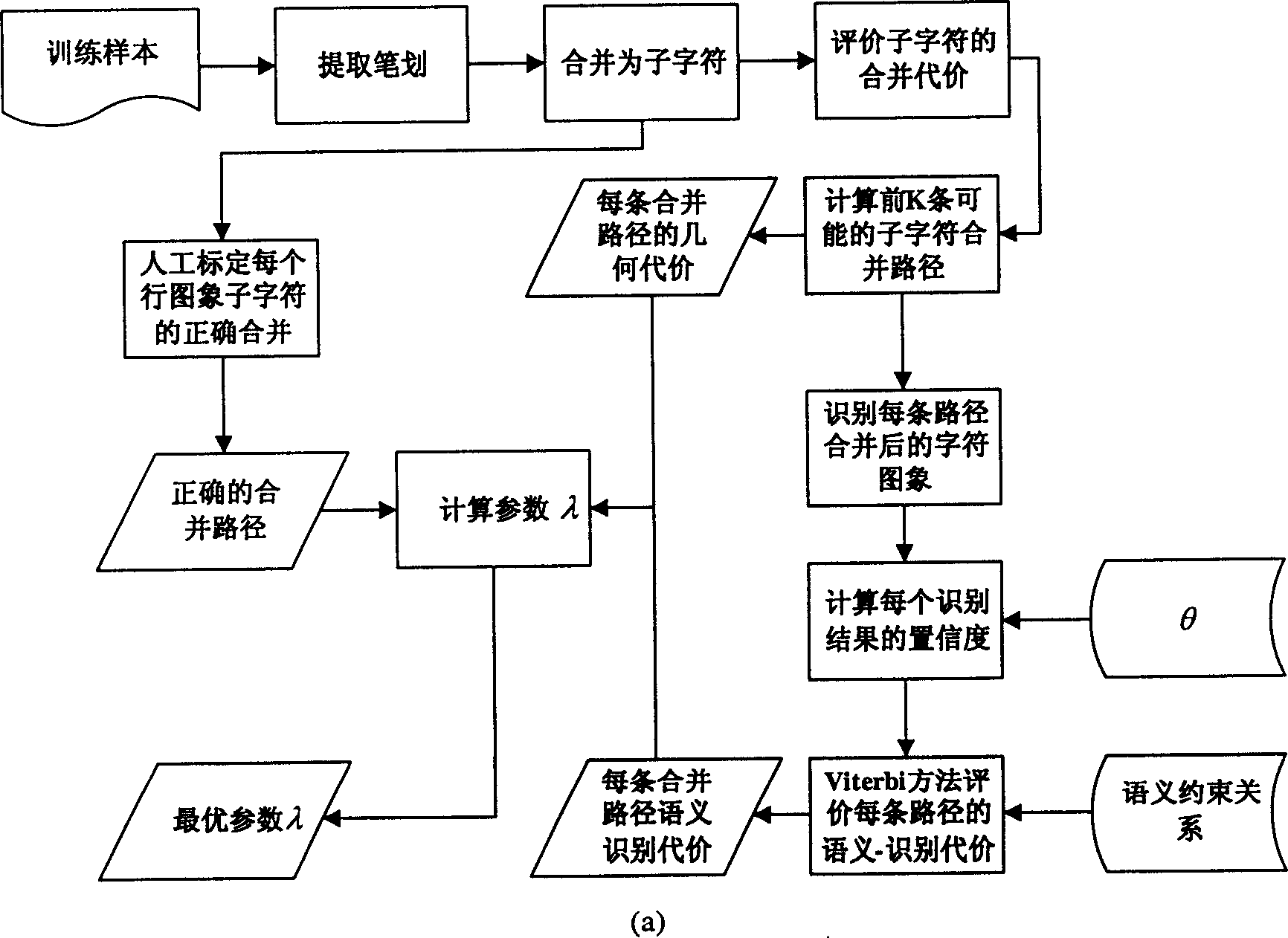
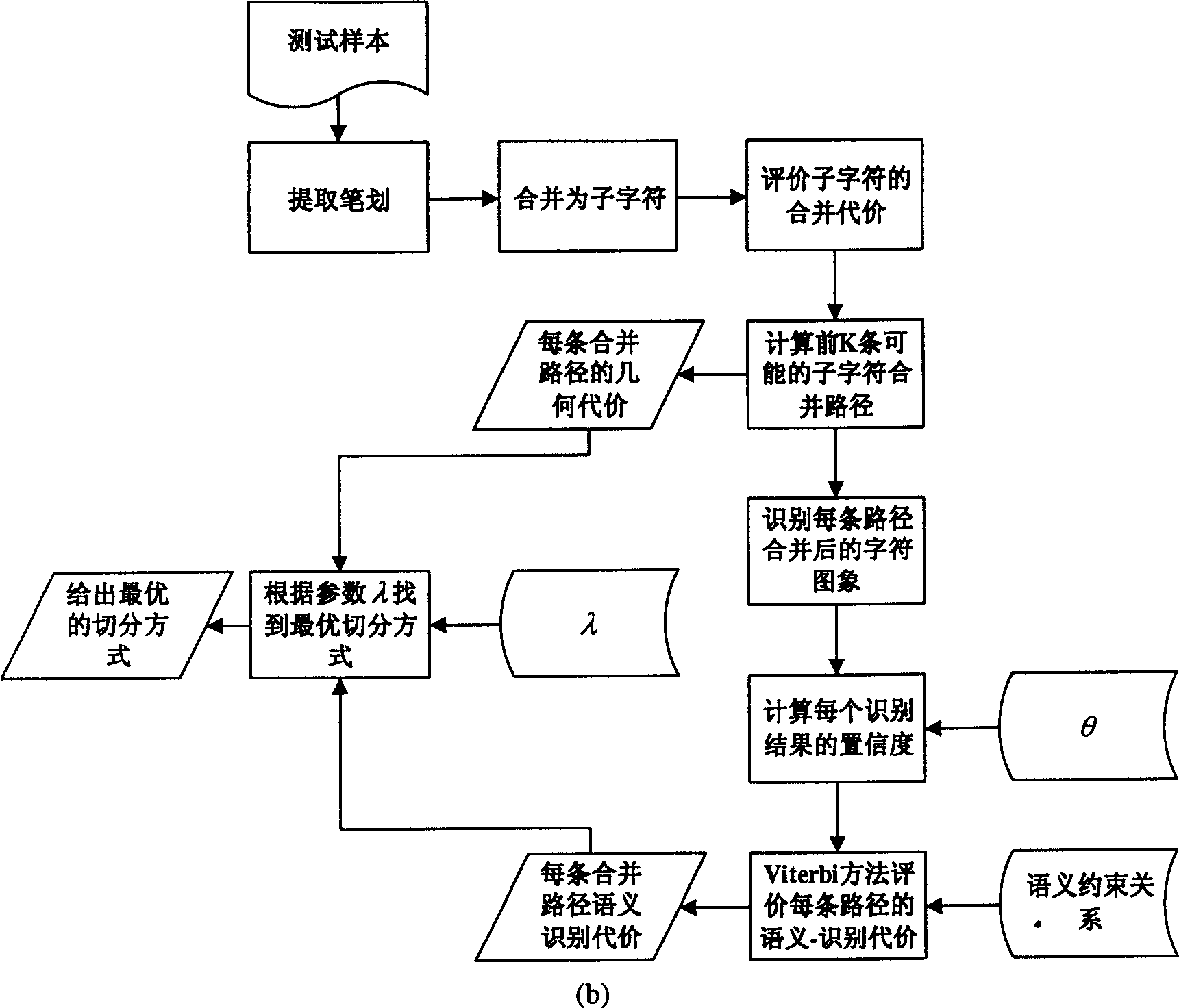
Off-line hand writing Chinese character segmentation method with compromised geomotric cast and sematic discrimination cost
InactiveCN1719454ASolve adhesionReflect intimacyCharacter and pattern recognitionChinese charactersText recognition
The geometric cost-semantic identification cost amalgamated off-line hand-written Chinese character segmentation method belongs to the field of character identification technology. Said method includes the following steps: firstly, analyzing row image of inputted off-line hand-written Chinese character, extracting stroke segment, combining stroke segments into subcharacter block, at the same time giving out subcharacter blocks combined geometric cost, utilizing these geometric costs to generate several possible candidate segmentation methods, evaluating every method by using binary syntactic model of language to obtain semantic-identification cost of every segmentation method, finally integrating geometric and semantic identification costs to obtain optimum segmentation identification scheme.
Owner:TSINGHUA UNIV
System and method for immutably storing electronic assets in a large-scale computer system
InactiveUS20070260620A1Large scaleExtreme flexibilityData processing applicationsDigital data information retrievalSurvivabilityObsolescence
Systems and / or methods for storing and / or retrieving assets in connection with an extremely large scale computer storage system are provided. An asset catalog may comprise a plurality of asset catalog entries stored according to at least one schema and corresponding to a plurality of assets. A storage architecture may be capable of storing the plurality of assets, with the storage architecture comprising a storage locator and a federator. An item identification scheme may be capable of providing identifiers to reference, locate, and / or access said assets and / or said asset catalog entries stored in the asset catalog in the storage architecture. The computer storage system may be scalable essentially without limitation while maintaining asset storage and retrieval flexibility and substantially obsolescence-proof survivability of assets.
Owner:LEIDOS INNOVATIONS TECH INC +1
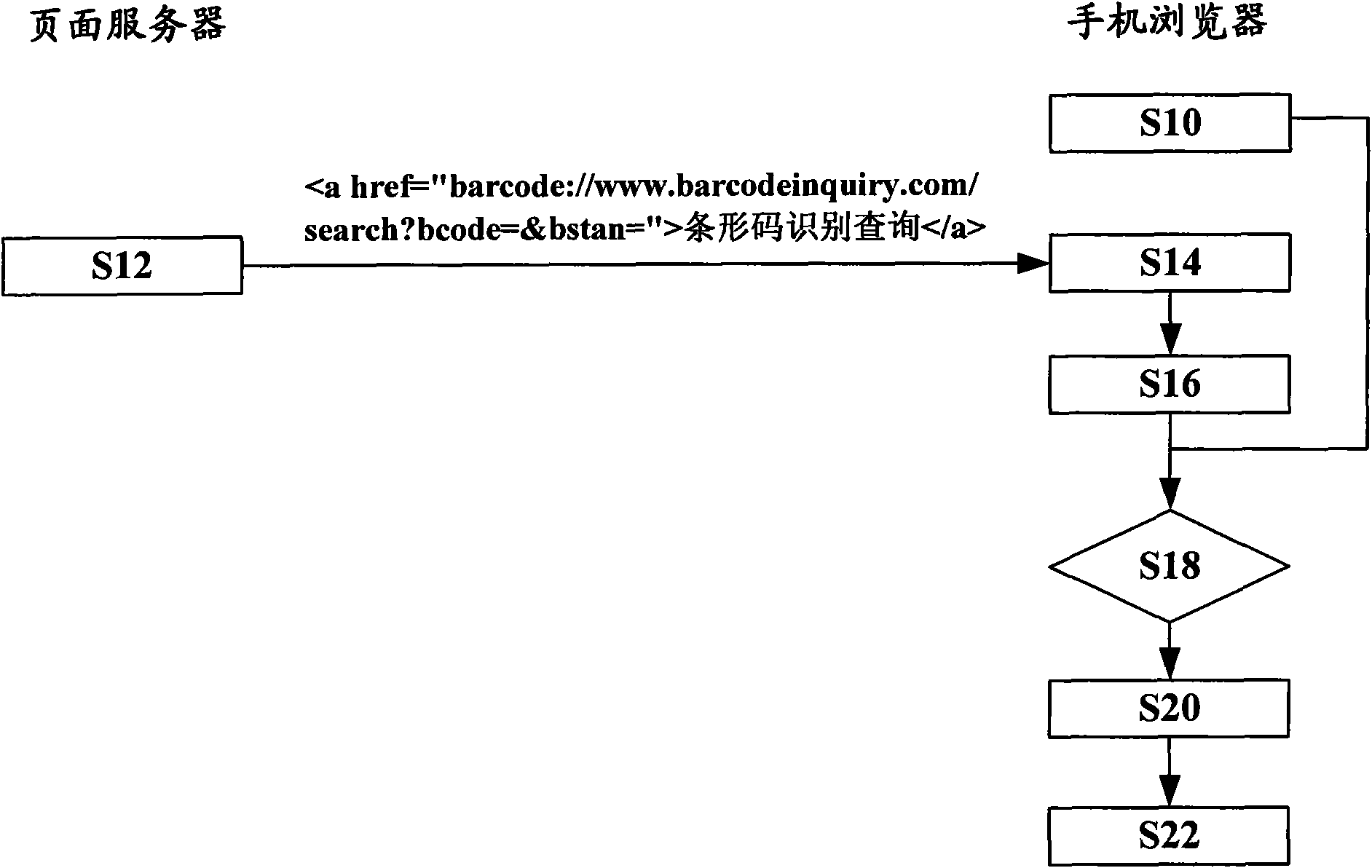
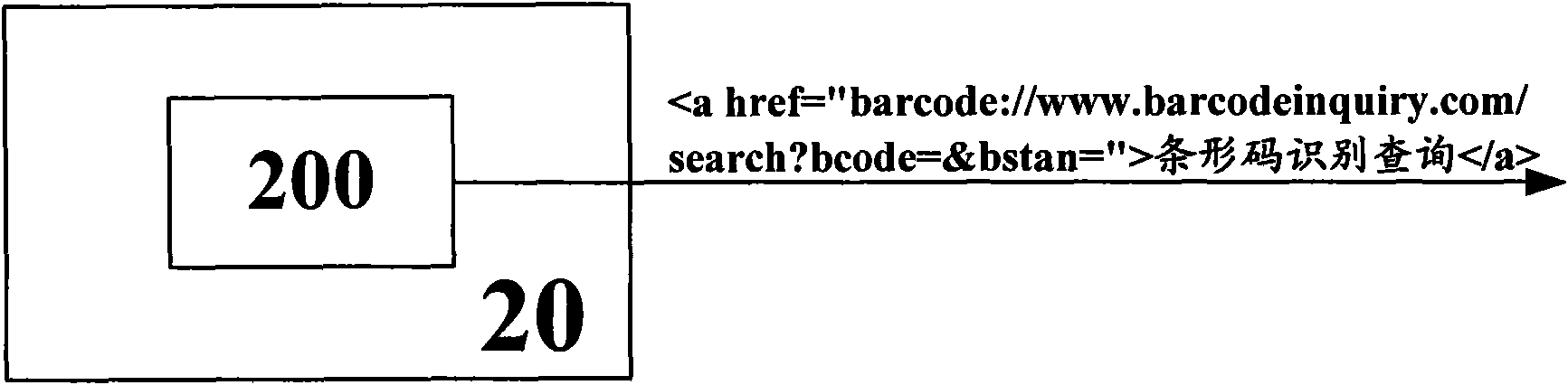
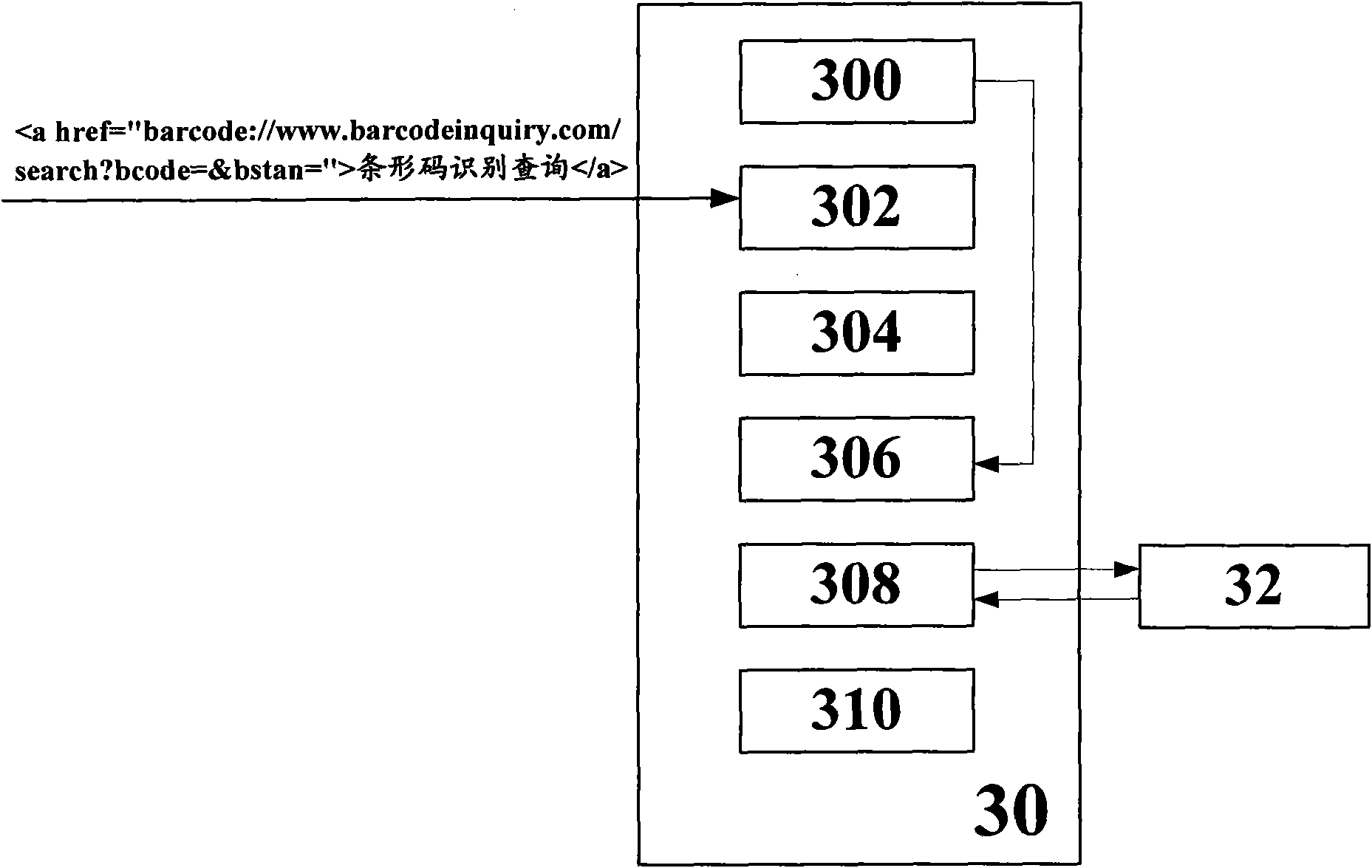
Method and device for acquiring bar code from browser of mobile phone
ActiveCN101964044AImprove experienceReduce development and maintenance costsSubstation equipmentTransmissionBarcodeMobile phone
The invention provides technology which is simple and convenient to operate and can easily maintain and expand a bar code acquired by a mobile phone and discloses a method and a device for acquiring the bar code from a browser of the mobile phone, wherein the mobile phone comprises a functional part capable of acquiring the bar code. The method comprises the following steps that: a page server sends a page code (S12) to the browser, wherein the page code comprises a command for indicating the browser to call the functional part to acquire the bar code; and the browser receives a page code (S14), judges that the command is triggered (S18), and calls the functional part to acquire a bar code (S20) according to the command. Preferably, the command is realized by a uniform resource identity scheme. According to the method and the device, the related application of the bar code and hypertext markup language (HTML) pages and the like are conveniently and easily developed; adjustment and expansion of application and service functions can be realized by upgrading the page code on the server, so that the maintenance and upgrading of the mobile phone are avoided; and a user directly acquires the bar code by using the browser, the learning threshold is low, the bar code is acquired quickly and conveniently, and the user experience is improved.
Owner:WOCHACHA INFORMATION TECH SHANGHAI CO LTD
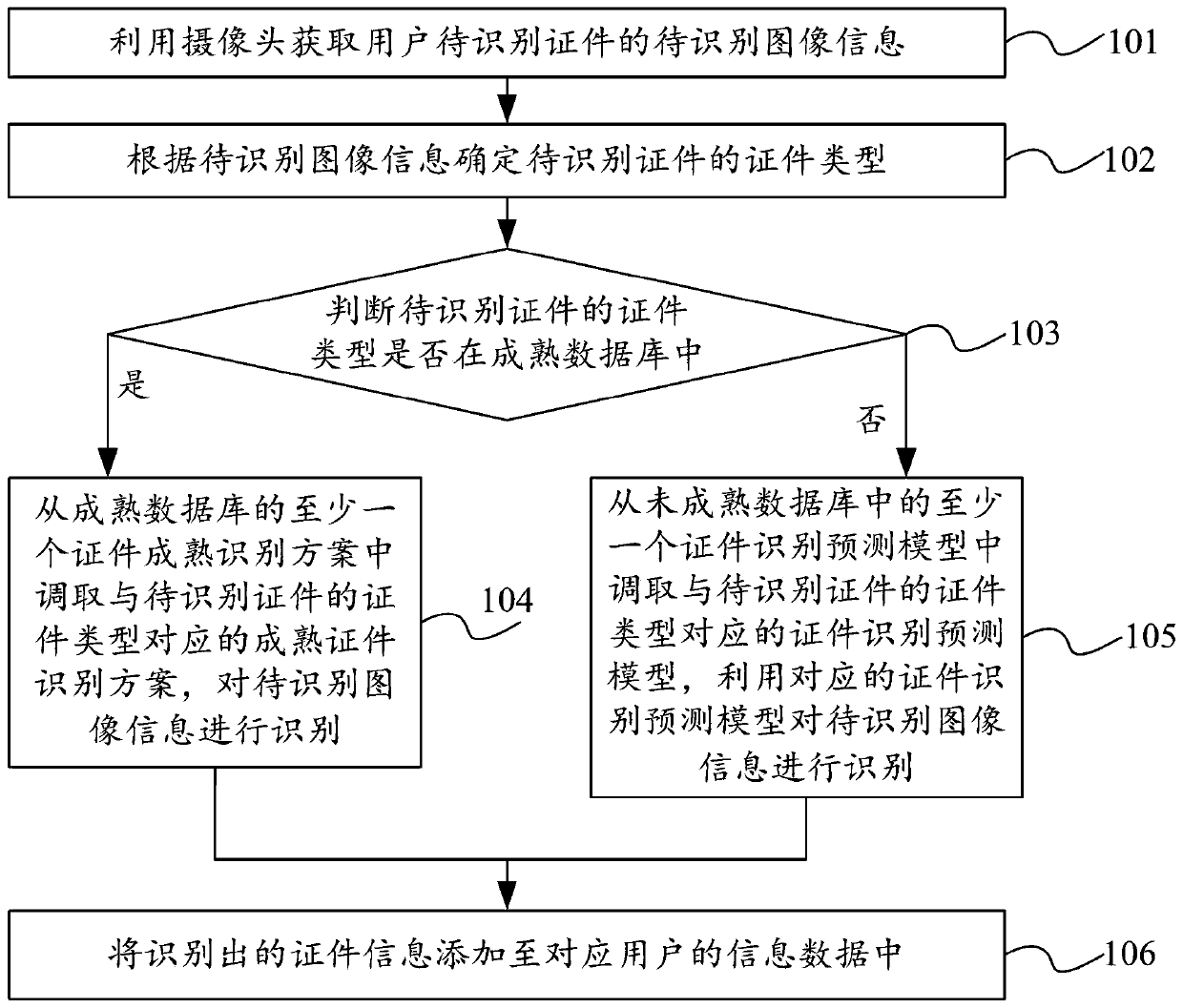
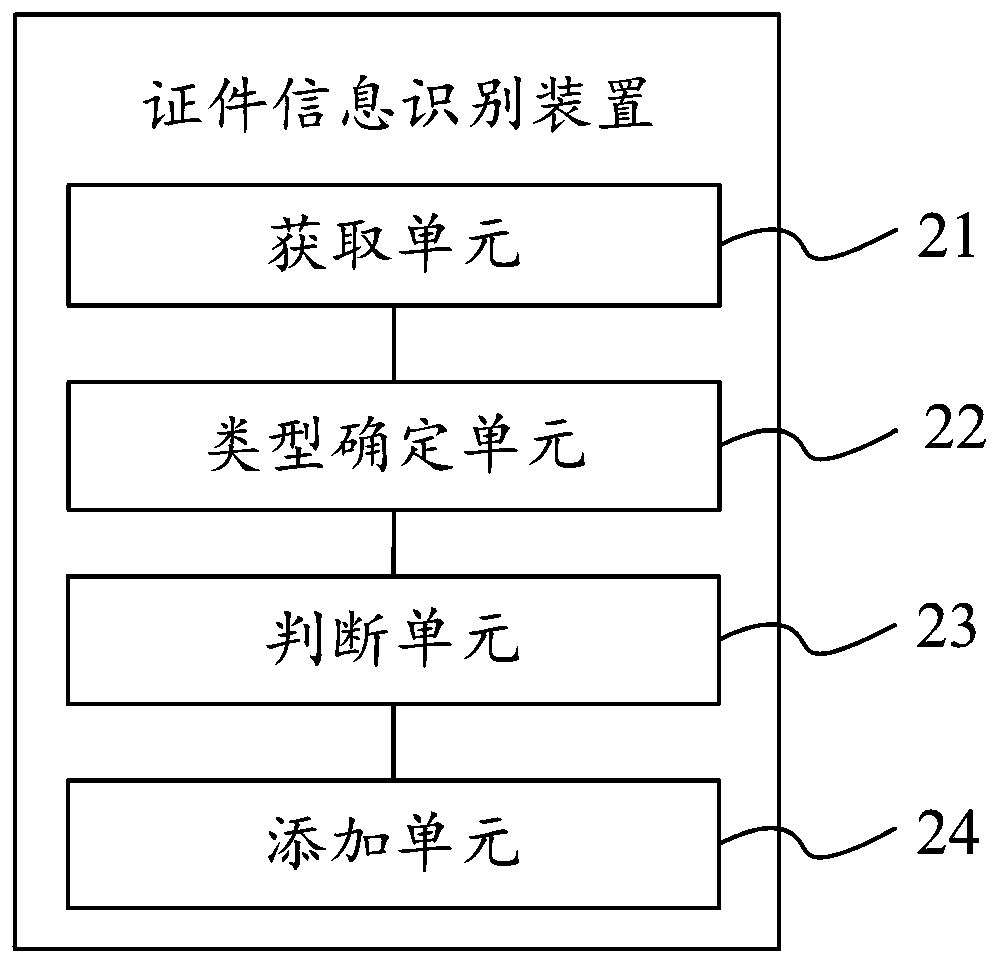
Certificate information identification method, device and equipment
PendingCN109815976AShorten the timeImprove recognition efficiencyCharacter and pattern recognitionIdentification schemeInformation data
The invention belongs to the field of artificial intelligence, and discloses a certificate information identification method, device and equipment, and the method comprises the steps: obtaining to-be-identified image information of a to-be-identified certificate of a user through a camera; determining the certificate type of the to-be-identified certificate; when the certificate type of the to-be-identified certificate is in the mature database, calling a mature certificate identification scheme corresponding to the certificate type of the to-be-identified certificate from the mature database,and identifying the to-be-identified image information; when the certificate type is not in the mature database, calling a certificate identification prediction model corresponding to the certificatetype of the to-be-identified certificate from the immature database, and identifying the to-be-identified image information; And adding the identified certificate information to the information dataof the corresponding user. The certificate type identified by the scheme is relatively comprehensive, manual participation is not needed in the identification process, the certificate identification time is saved, and the certificate identification efficiency is improved.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
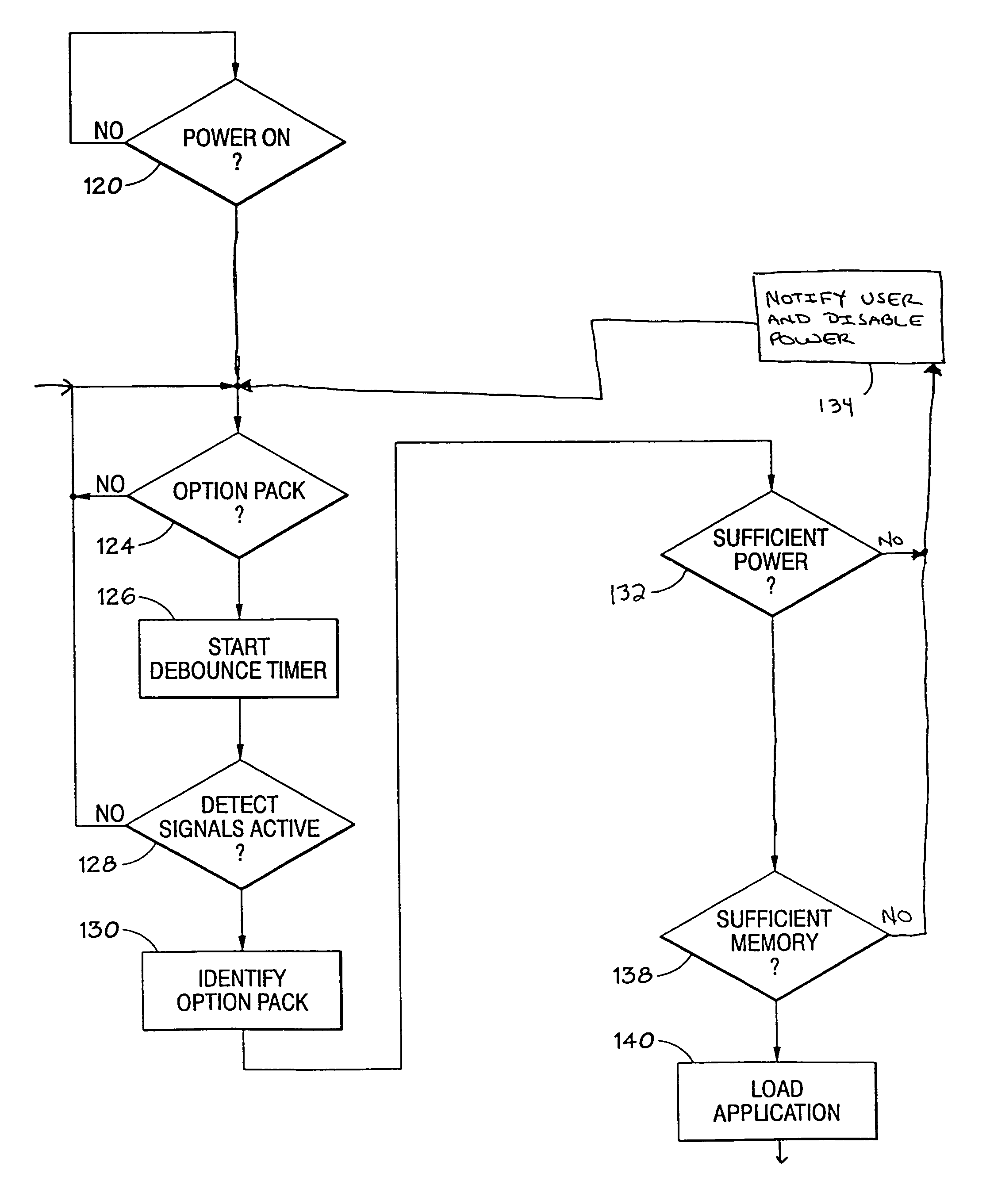
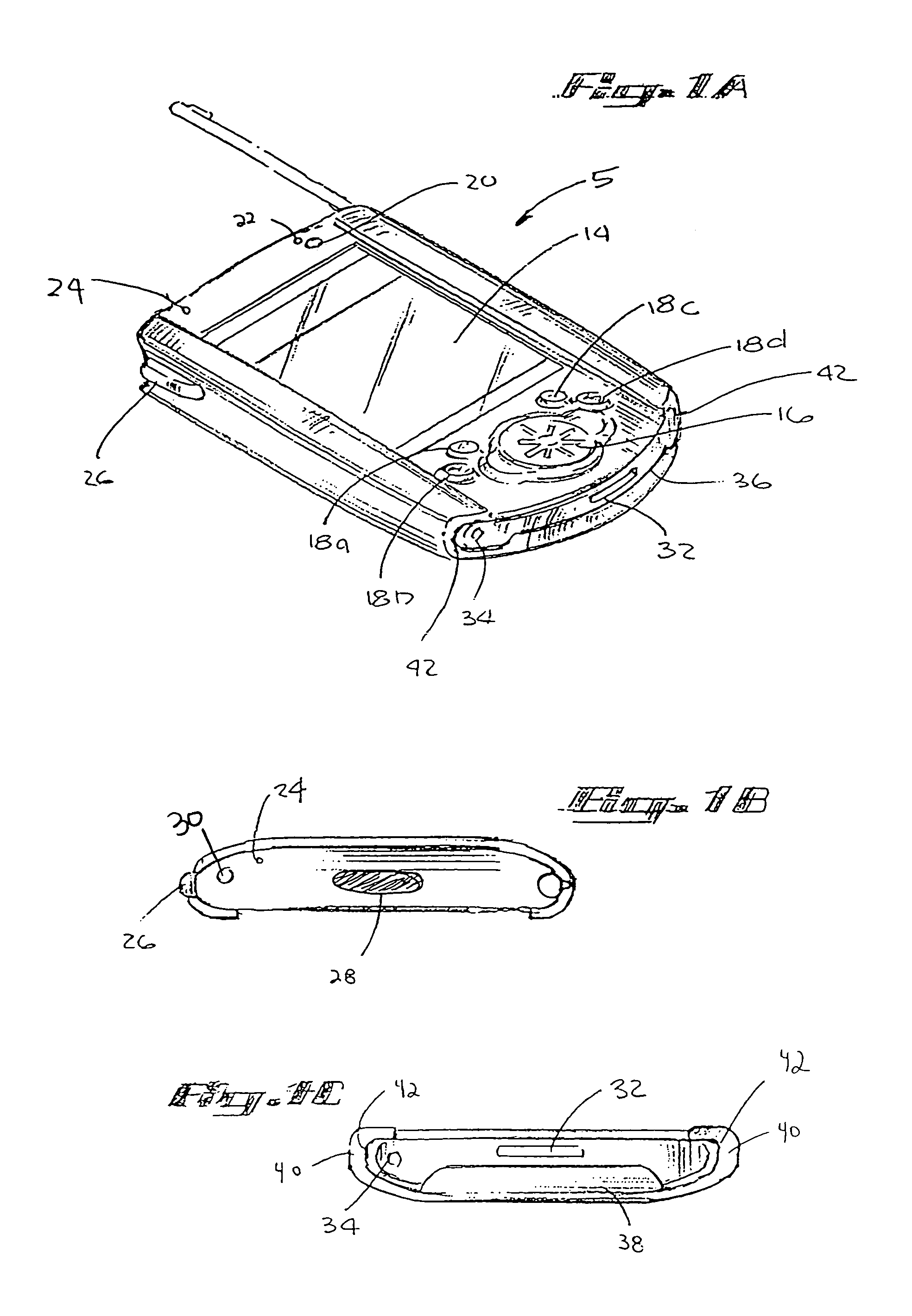
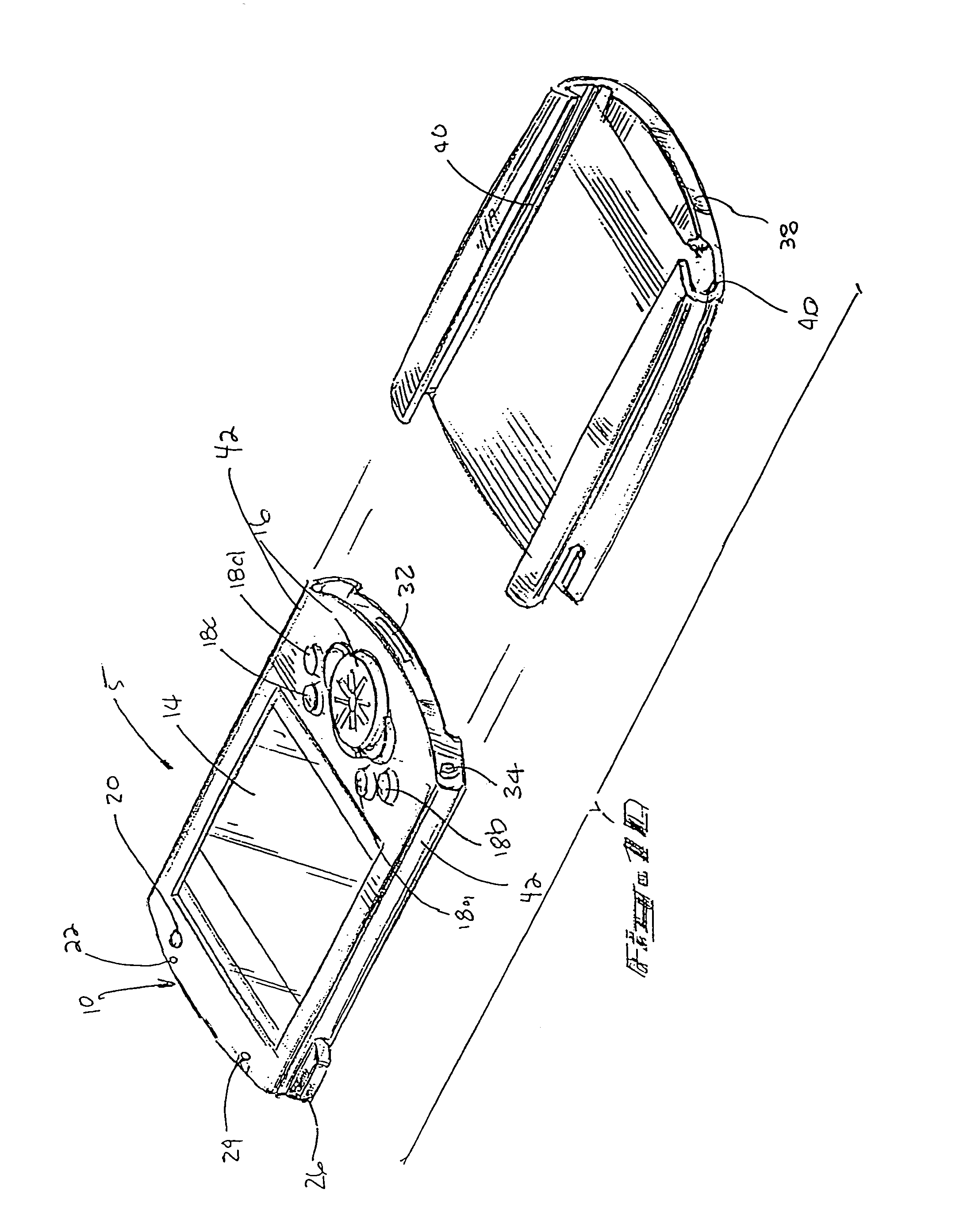
Handheld option pack identification scheme
An insertion and identification scheme between the main unit of a Personal Digital Assistant (PDA) or handheld device and an option pack. Upon insertion, the hardware interface invokes a device manager on the main unit that interrogates the option pack on its features without significantly impacting battery life. The interrogation includes data on drivers, applications, configuration and miscellaneous requirements of the option pack. This identification process allows the option pack to store information, drivers and applications on the option pack, so the main unit does not have to use its memory to store information on a large number of option packs. Further, the insertion scheme provides a means of checking the power availability in the main unit before allowing the option pack to fully power-on.
Owner:QUALCOMM INC
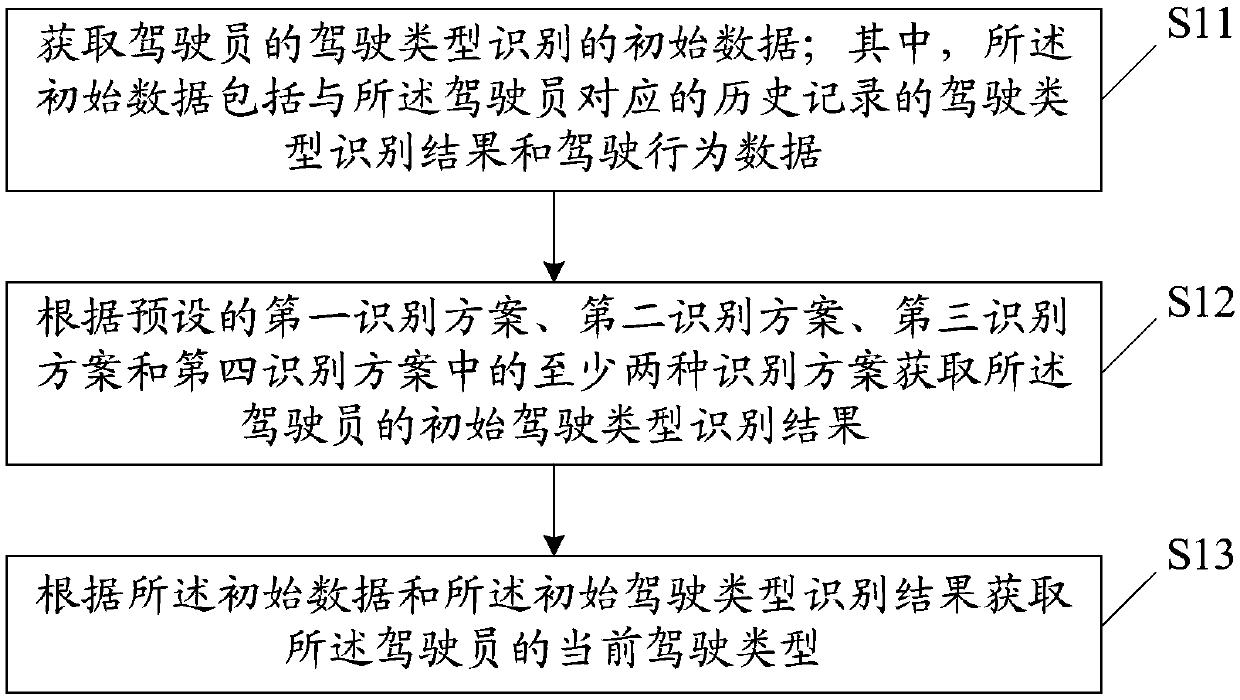
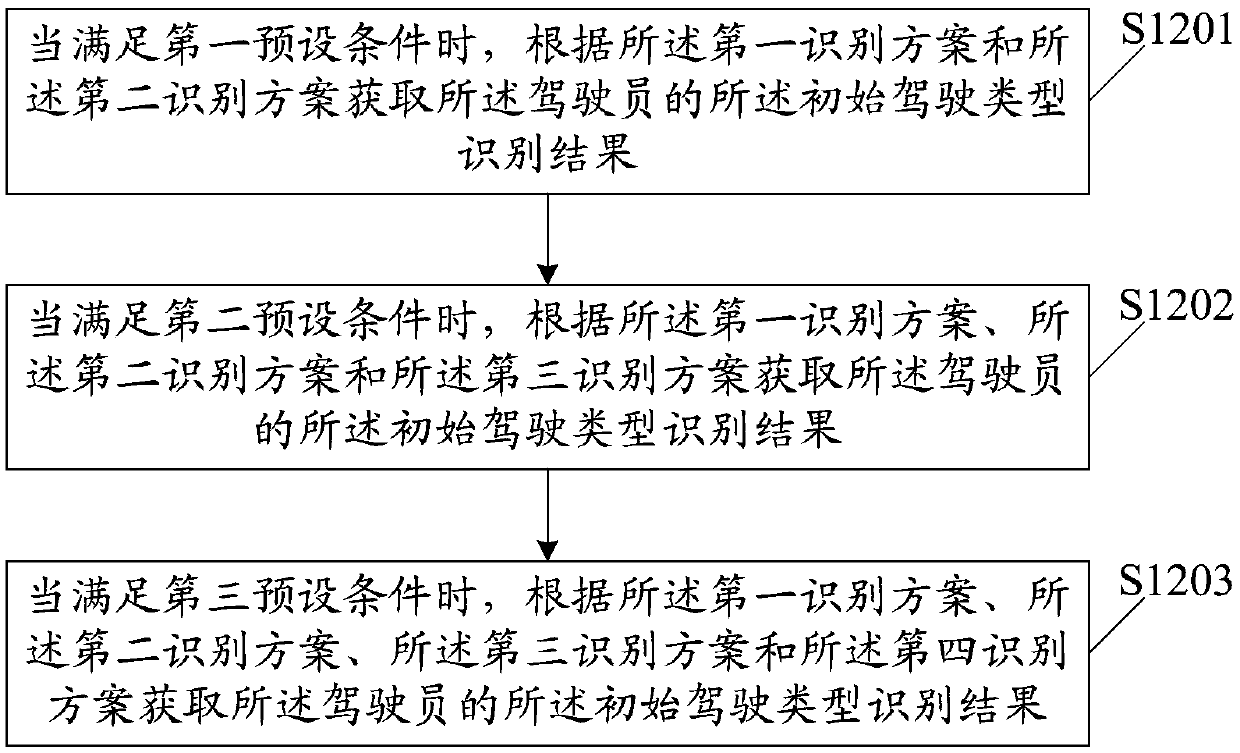
Driver driving type identification method and device, storage medium and terminal equipment
The invention discloses a driver driving type identification method and device, a storage medium and a terminal device. The method comprises: obtaining initial data of driving type identification of adriver; obtaining an initial driving type recognition result of the driver according to at least two of a preset first recognition scheme, a second recognition scheme, a third recognition scheme anda fourth recognition scheme, wherein the first identification scheme is to identify the driving type according to the dynamic information of the vehicle, the second identification scheme is used for identifying the driving type according to the operation information of the driver under the preset working condition, the third identification scheme is used for identifying the driving type accordingto a pre-trained machine learning network, and the fourth identification scheme is used for identifying the driving type according to a pre-trained deep learning network; and obtaining a current driving type of the driver according to the initial data and the initial driving type identification result. According to the invention, the accuracy and real-time performance of driver driving type identification can be improved.
Owner:GUANGZHOU AUTOMOBILE GROUP CO LTD
Identification method and device of cheating application program
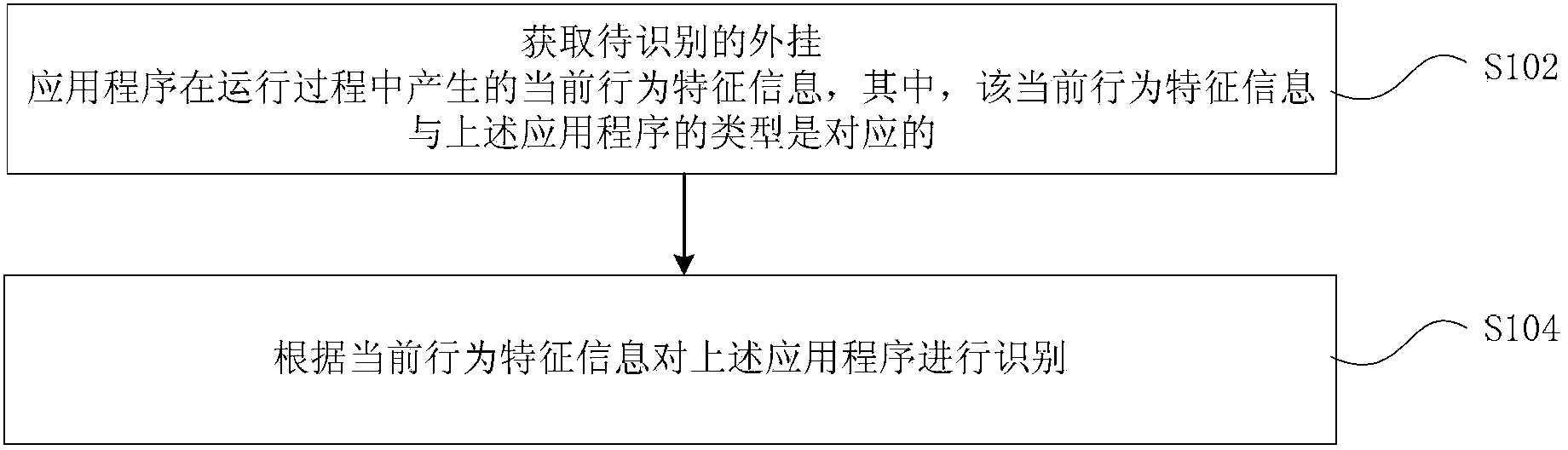
ActiveCN104252592ARealize precise identificationResolve identifiabilityIndoor gamesPlatform integrity maintainanceApplication softwareIdentification scheme
The invention provides an identification method and a device of a cheating application program. The method comprises obtaining current behavior characteristic information produced by the cheating application program to be identified during operation, and identifying the cheating application program according to the current behavior characteristic information, wherein the type of the current behavior characteristic information corresponds to the type of the cheating application program. By adopting the technical scheme, the problems that cheating application program identification schemes have difficulty in identifying cheating application programs and are likely to make erroneous judgment in relevant technologies are solved, so that precise identification of cheating application programs is realized.
Owner:BEIJING CHEETAH MOBILE TECH CO LTD +4
Robust efficient distributed RSA-key generation
InactiveUS20010038696A1ConfidenceMore efficiencyKey distribution for secure communicationPublic key for secure communicationEncrypted functionKey escrow
Owner:CQR CERT
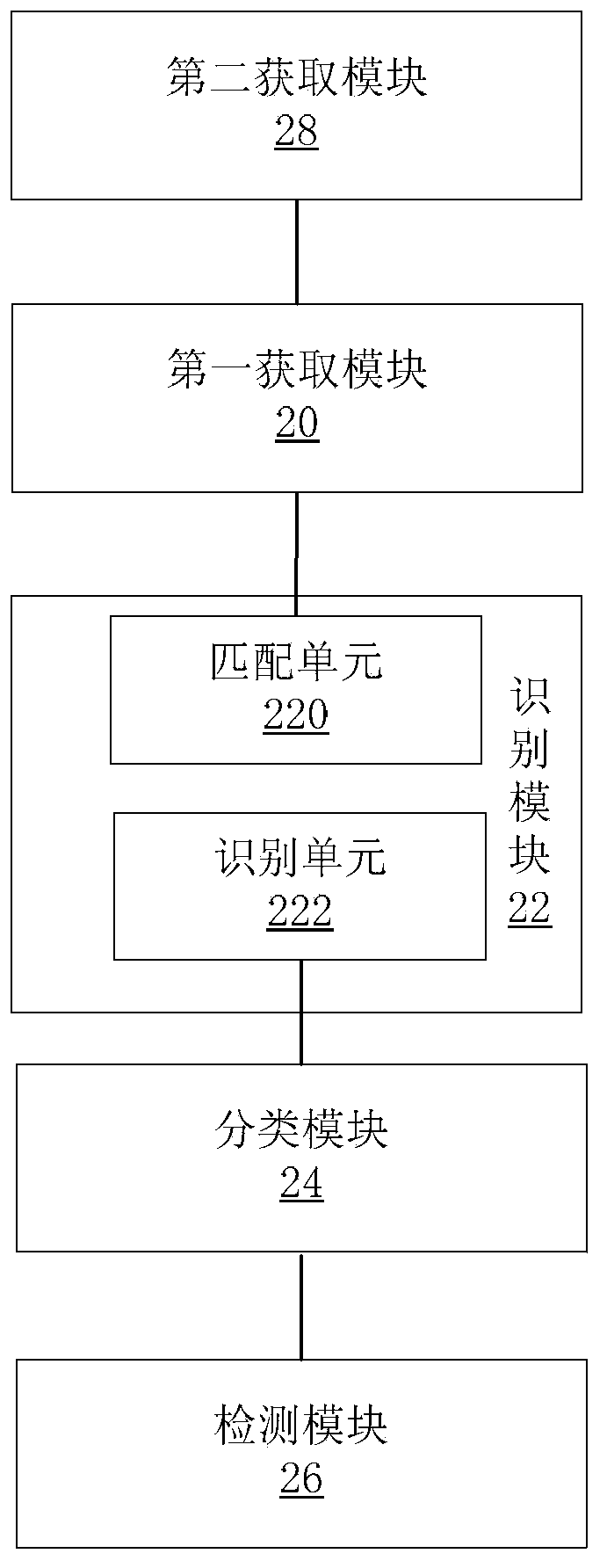
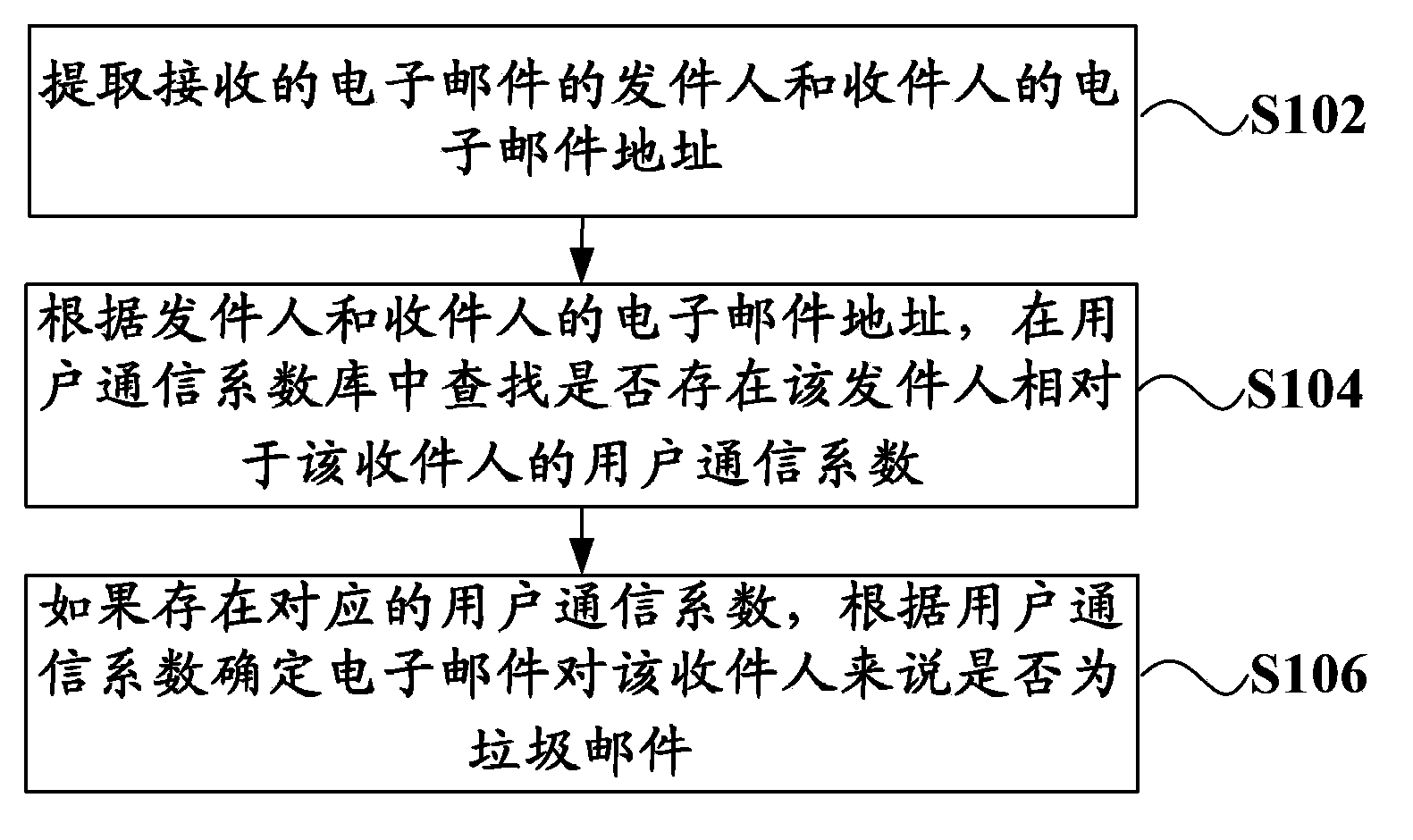
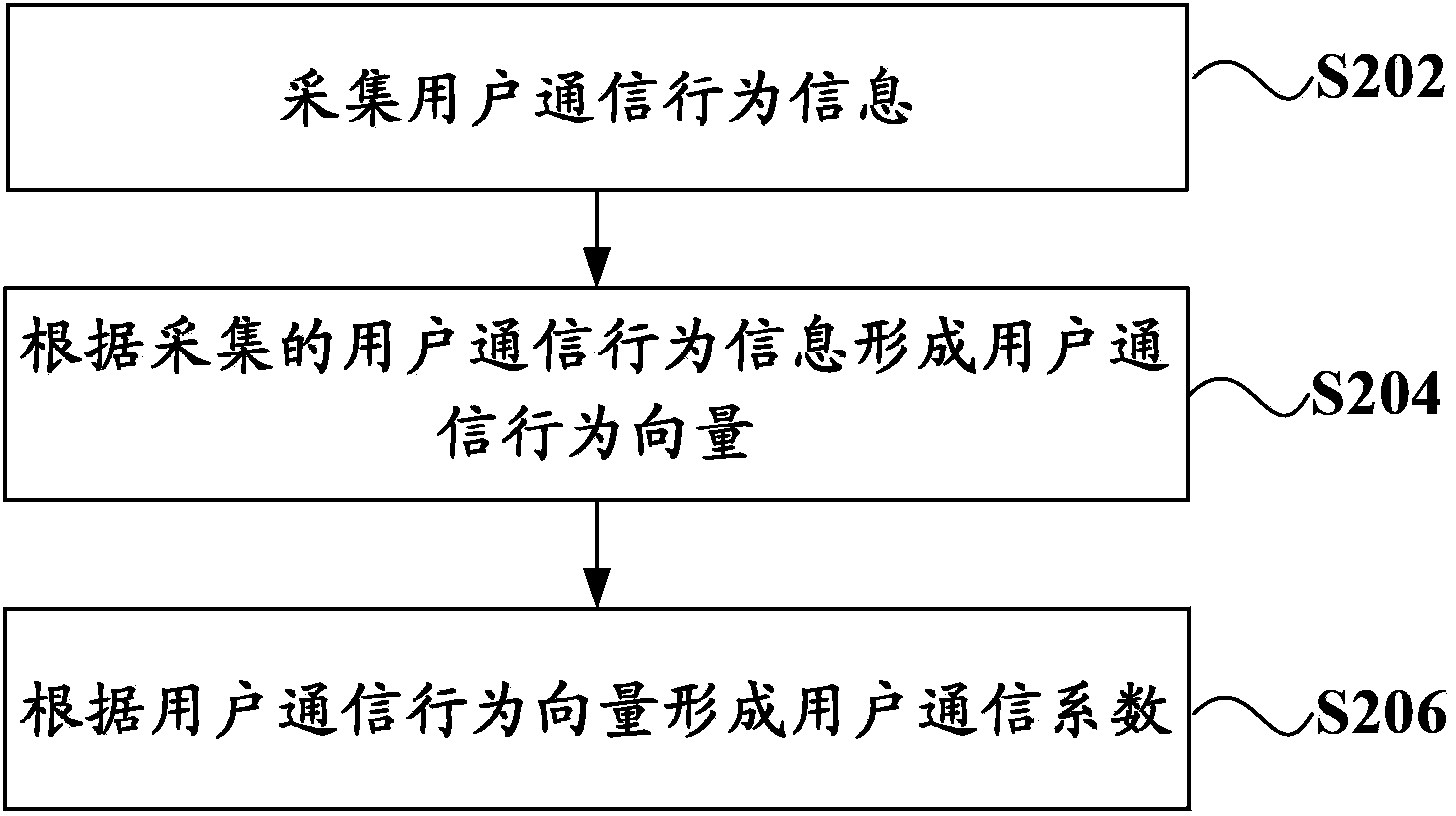
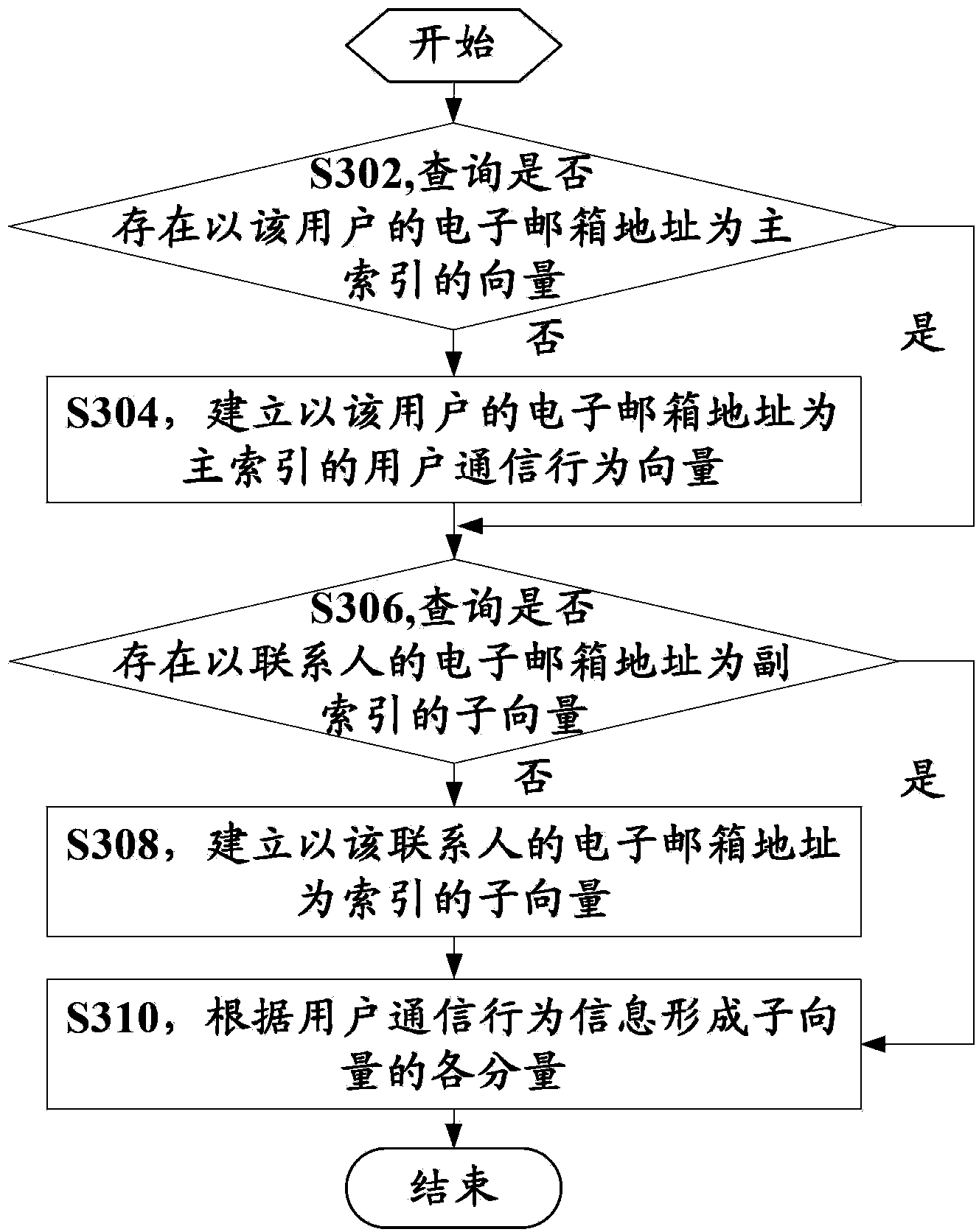
Identification method, identification system, and filter system of spam mail
The invention, which relates to the field of the anti-spam mail technology, discloses a user communication behavior-based identification method, identification system, and filter system of a spam mail. The method comprises the following steps that: e-mail addresses of an addresser and an addressee of a received e-mail are extracted; according to the e-mail addresses of the addresser and the addressee, whether a user communication coefficient of the addresser relatively to the addressee exists is searched in a user communication coefficient database, wherein the user communication coefficient is constructed based on the user communication behavior and expresses a connection degree between the addresser and the addressee; if the corresponding user communication coefficient exists, whether the e-mail is a spam mail for the addressee is determined according to the user communication coefficient. According to the user communication behavior-based spam mail identification scheme, the easy avoidance can be prevented; the individual communication relation of the user is fully considered; and the accuracy of identification and filtering of the spam mail is improved.
Owner:CHINA TELECOM CORP LTD
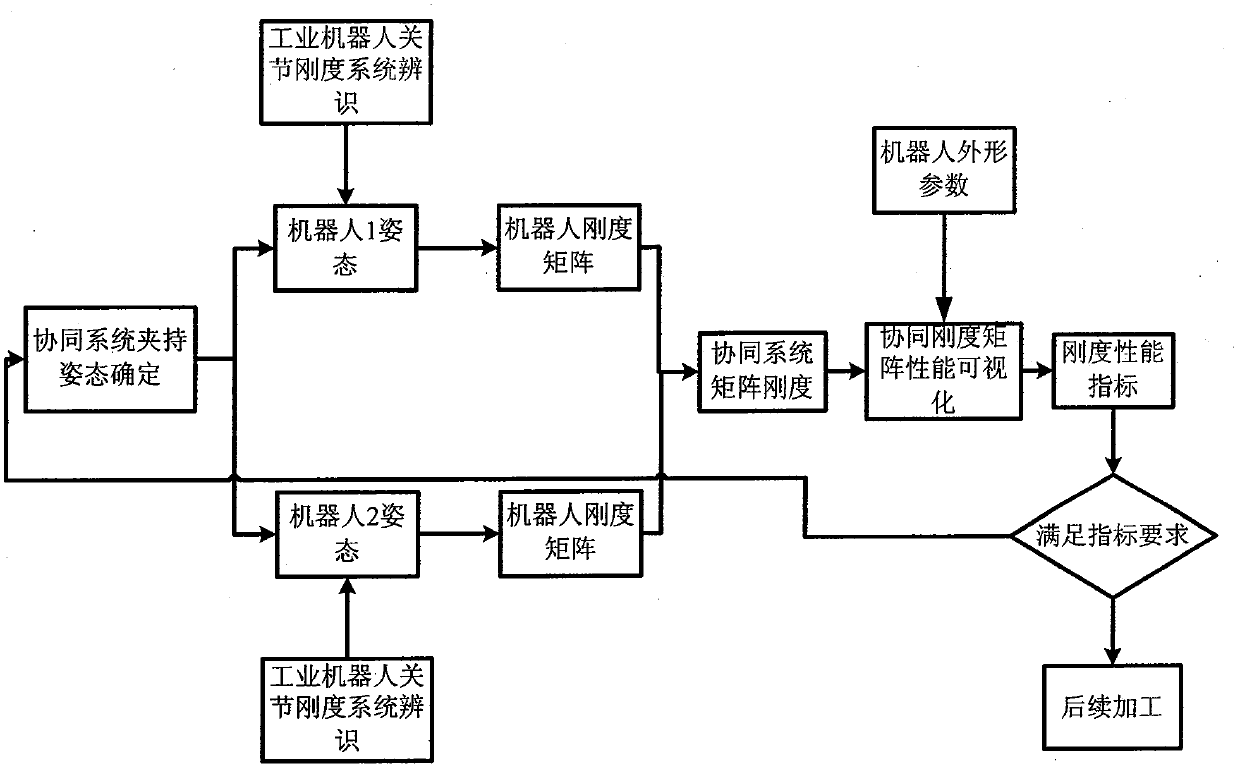
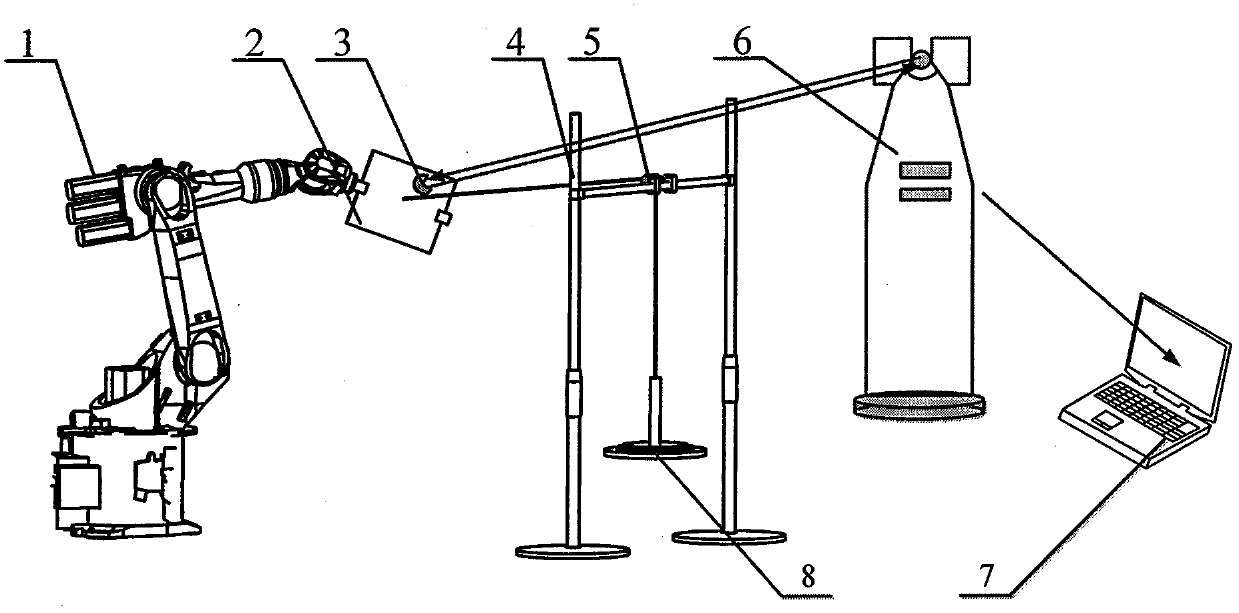
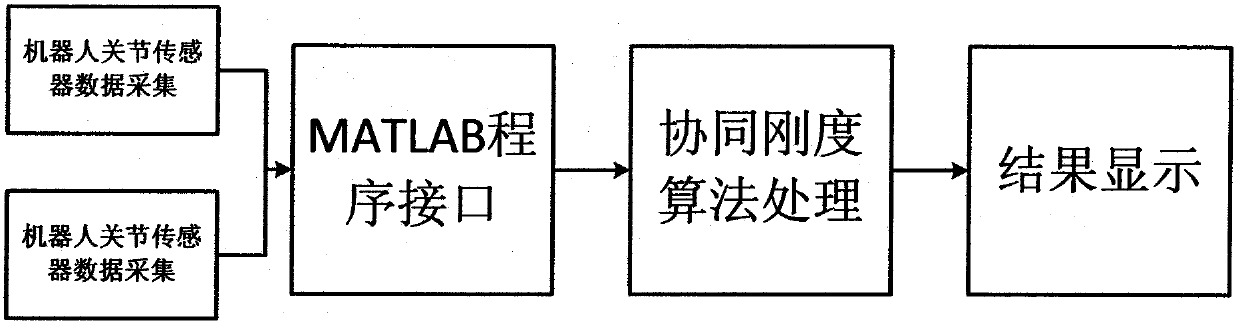
Multi-robot synergistic system static stiffness real-time performance evaluation method
InactiveCN107414834AImprove machining accuracyThe method steps are simpleProgramme controlProgramme-controlled manipulatorSimulationJoint stiffness
The invention provides a multi-robot synergistic system static stiffness real-time performance evaluation method without additional devices. The method comprises the steps that based on a robot kinematics transfer matrix and a robot end operation stiffness matrix, a robot joint stiffness identification scheme is established and implemented, and accurate robot practical joint stiffness is acquired; by employing robot system software to feed back real-time joint angles, a robot jacobian matrix is established, and a multi-robot synergistic system overall stiffness matrix is formed through the robot jacobian matrix and joint stiffness parameters identified by a robot; robot real-time stiffness is subjected to visual characterization through robot stiffness matrix ellipsoids, and the maximum value of system stiffness matrix characteristic values is selected as an evaluation index for carrying out robot stiffness evaluation; finally, through a GUI design interface, a stiffness performance evaluation visual interface is designed based on a double-KUKA KR-16 robot synergistic system.
Owner:SHANGHAI UNIV
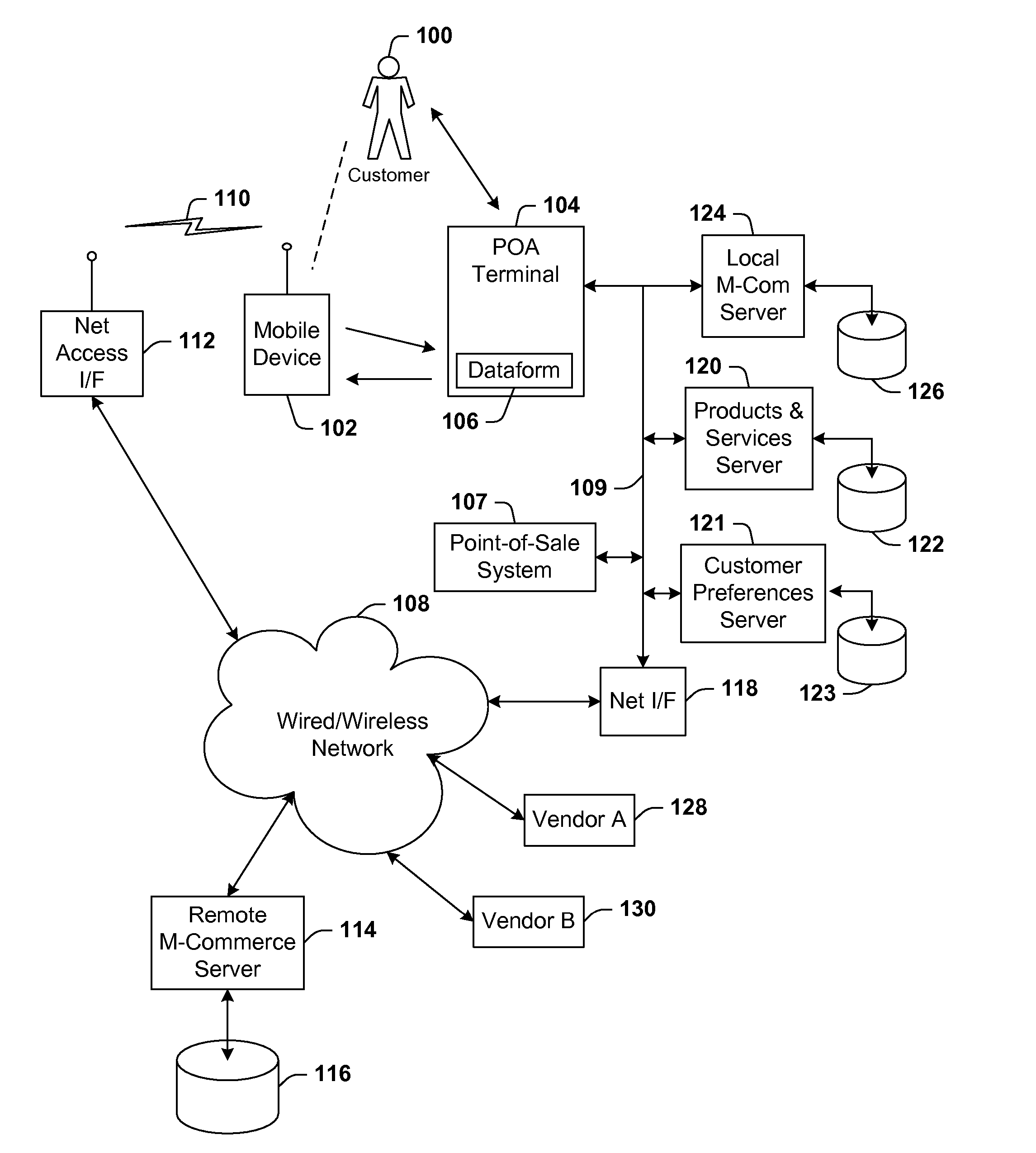
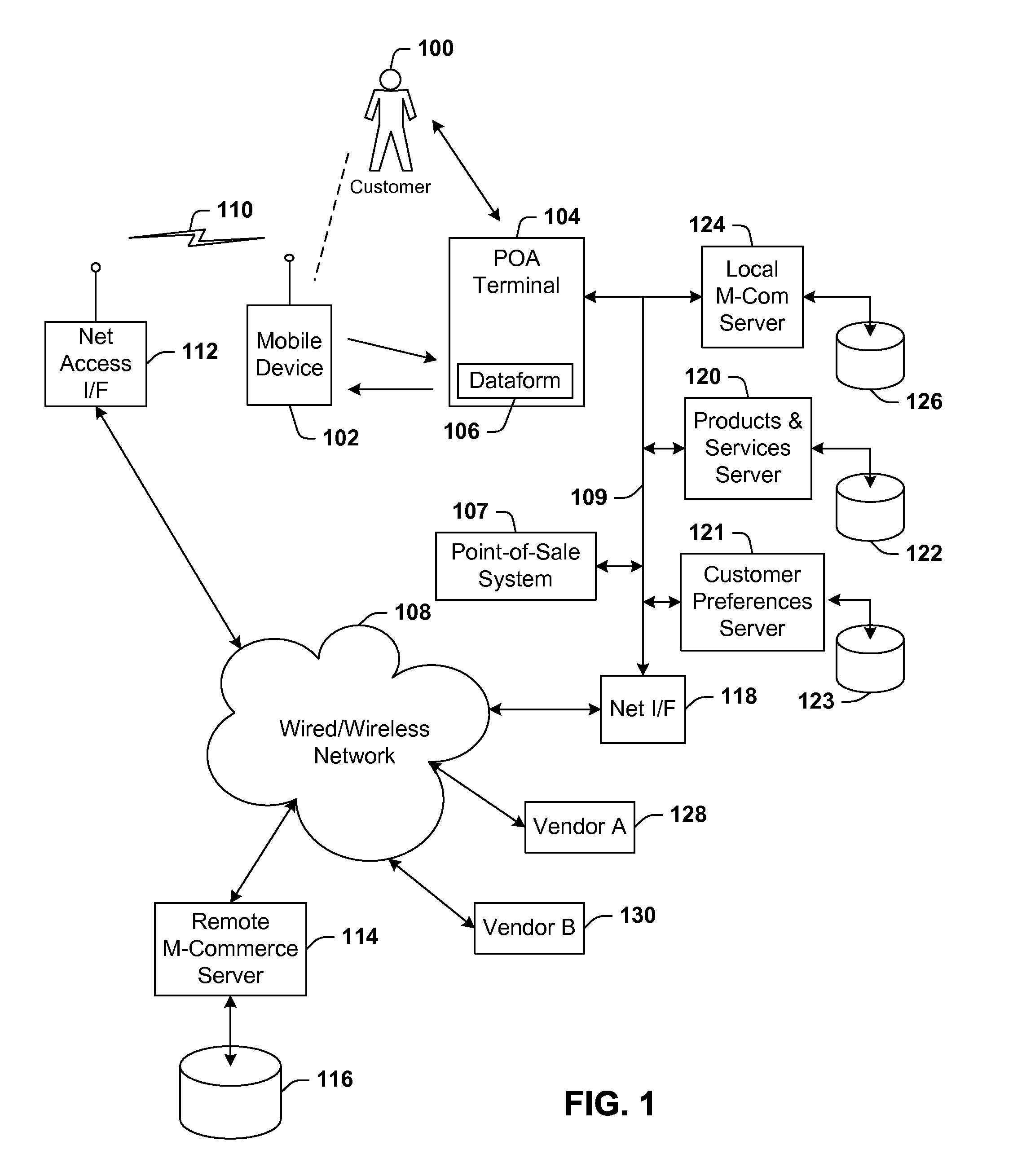
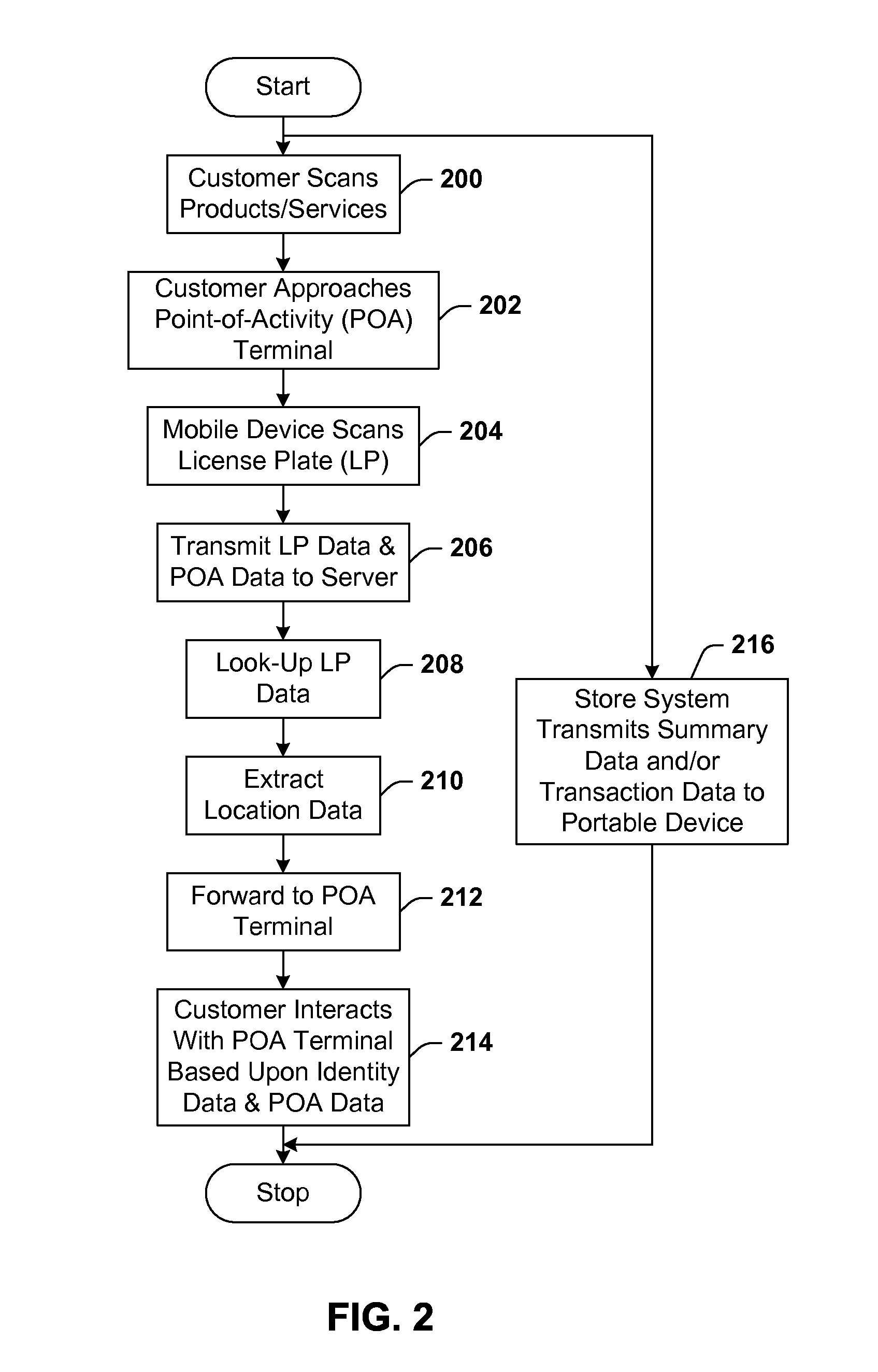
Identification scheme for a communication device
ActiveUS20070083439A1Easy to identifyEasy to viewCash registersVisual presentationTransaction dataComputer terminal
Architecture for presenting m-commerce transaction data to a user. An m-commerce device includes a device reading apparatus adapted to read a dataform. At least one item for purchase has associated therewith an item dataform readable by the m-commerce device, the item dataform linked to item information of the item. A terminal is provided for interactive presentation of information to the user. The m-commerce device and terminal are in communication over a network such that item information input to the m-commerce device is transmitted to the terminal for interactive presentation to the user.
Owner:SYMBOL TECH LLC
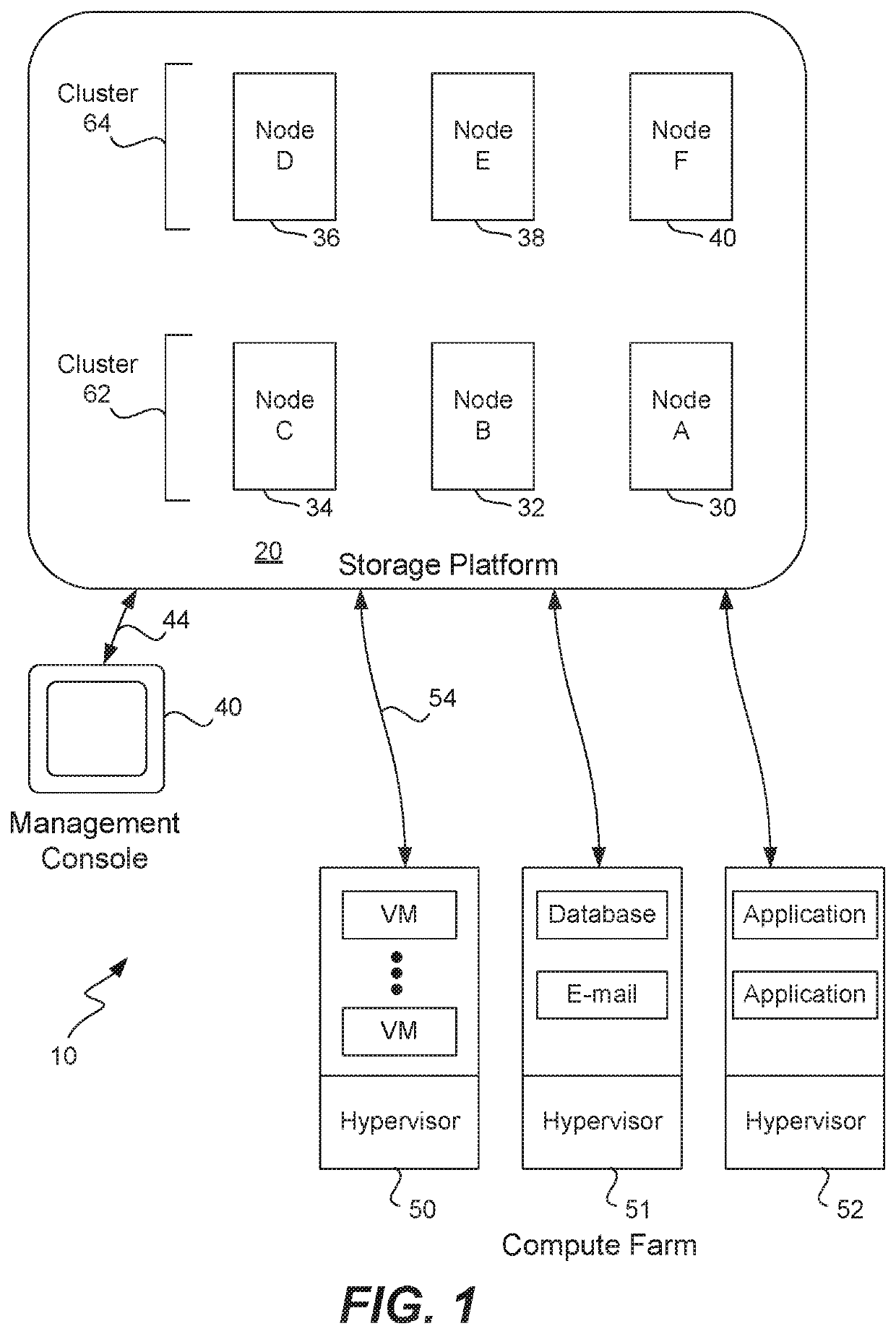
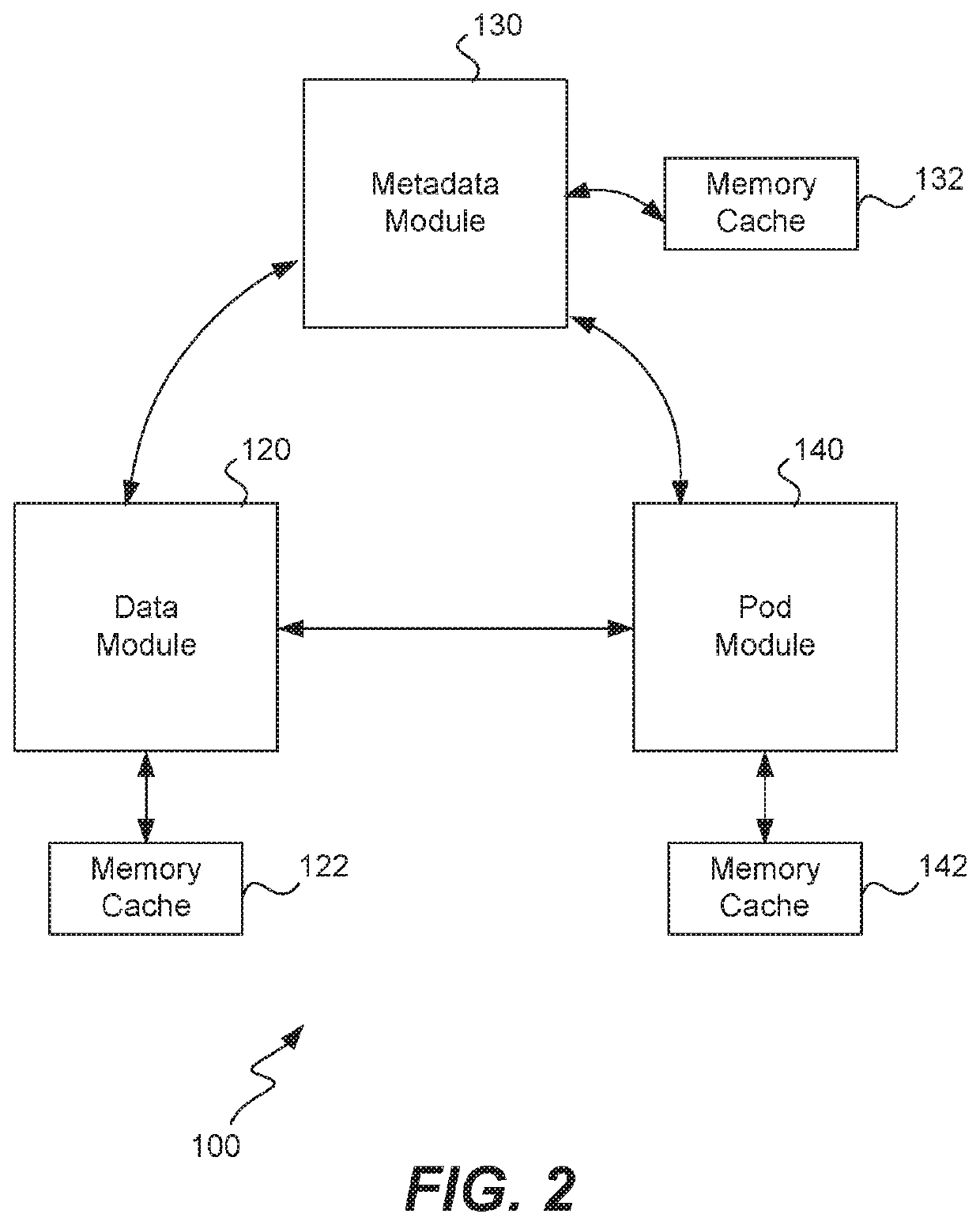
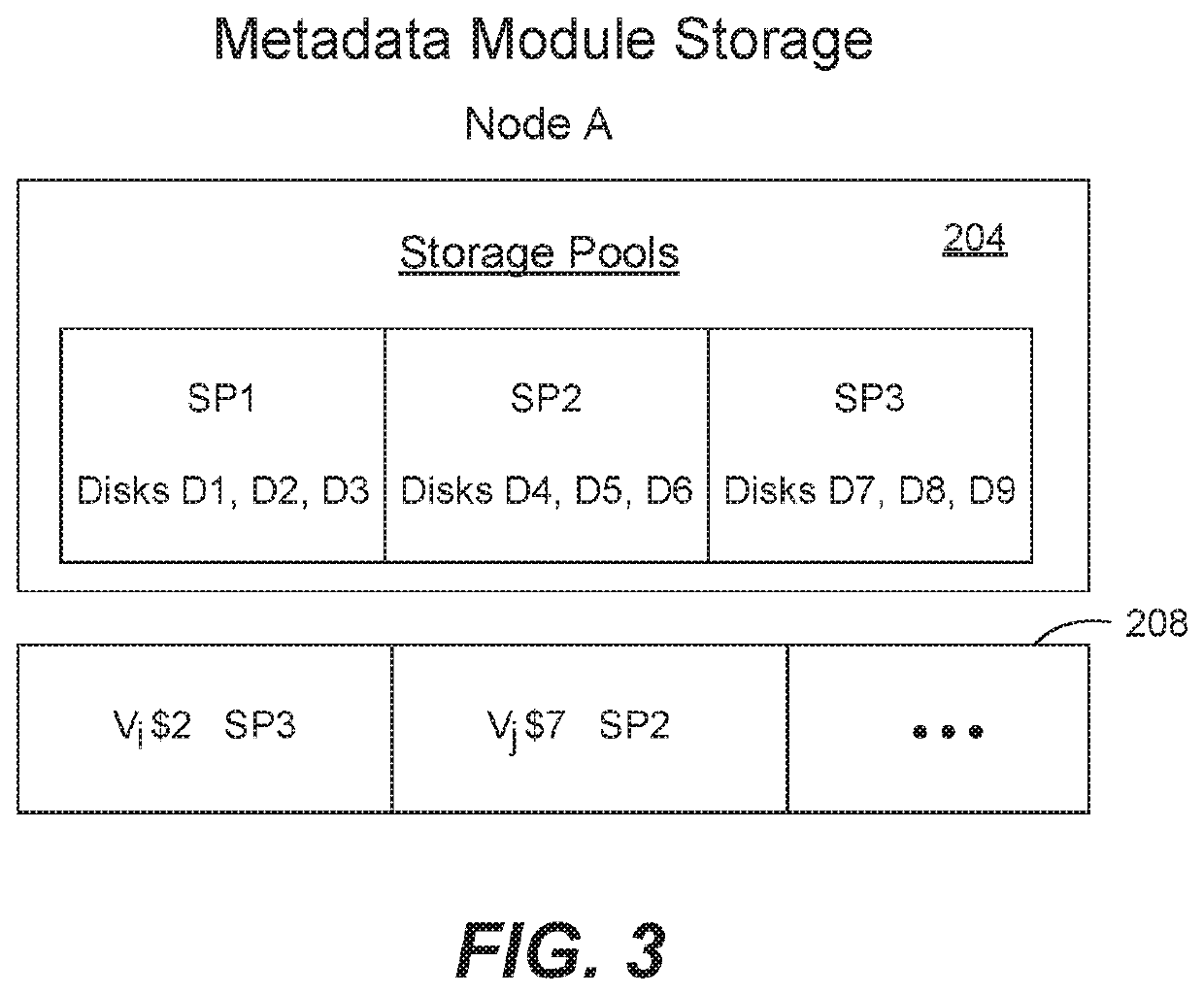
Synchronization of metadata in a distributed storage system
ActiveUS10740300B1Faster and efficient synchronization processImprove reliabilityDigital data processing detailsDatabase distribution/replicationParallel computingTheoretical computer science
A client machine writes to and reads from a virtual disk on a remote storage platform using a storage protocol. Metadata is generated and is stored in replicas on different metadata nodes of the storage platform. A modified log-structured merge tree is used to store and compact string-sorted tables of metadata. During file storage and compaction, a consistent file identification scheme is used across all metadata nodes. A fingerprint file is calculated for each SST file on disk that includes hash values corresponding to regions of the SST file. To synchronize, the fingerprint files of two SST files are compared, and if any hash values are missing from a fingerprint file then the key-value-timestamp triples corresponding to these missing hash values are sent to the SST file that is missing them in the SST file is compacted with the missing triples to create a new version of the SST file. The other fingerprint file is then analyzed the same way.
Owner:COMMVAULT SYST INC
Inventory management system based on strategy module
ActiveCN108846621AAvoid difficultiesReduce computationCo-operative working arrangementsCharacter and pattern recognitionAcquisition SchemeComputer science
The invention relates to an inventory management system based on a strategy module. The system comprises an image collection unit, an image identification unit, calculation equipment and a strategy unit, wherein the image identification unit responds to the state of goods held by an access mechanism to identify the change of at least one inventory position of a goods shelf around the absolute position of the access mechanism and / or positioned on a preset relative position; the calculation equipment judges a corresponding relationship between the changes of the goods and the inventory positionto generate inventory information; the calculation equipment records the inventory information of each type of goods in the historical information of each type of goods in a certain period; in addition, after analysis is carried out on the basis of the historical information and the inventory information, the inventory state information of each type of goods is obtained; and the strategy unit triggers and regulates the collection scheme of the image collection unit and / or the identification scheme of the image identification unit on the basis of the inventory state information.
Owner:HUNAN UNIV OF HUMANITIES SCI & TECH
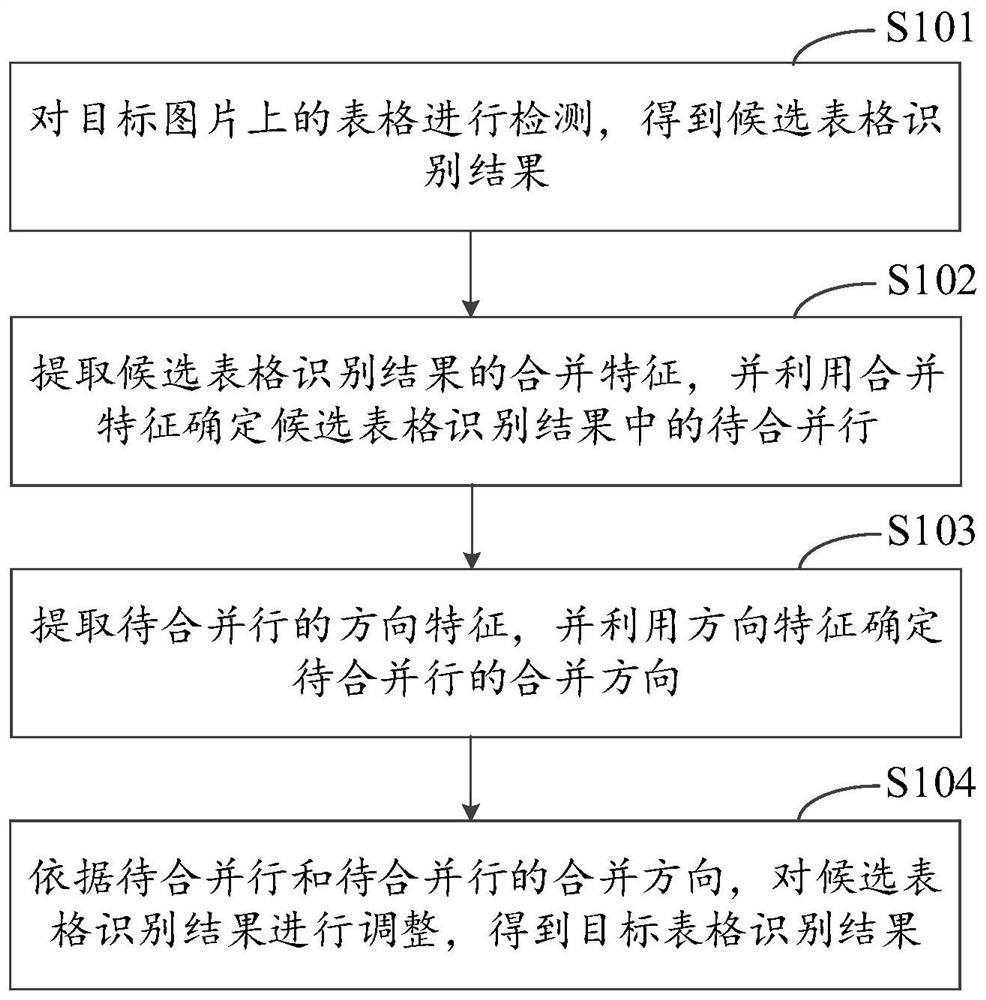
Table identification method and device, equipment and medium
ActiveCN111695553AImprove accuracySolve inaccurateNatural language data processingNeural architecturesAlgorithmEngineering
The embodiment of the invention discloses a table identification method and device, equipment and a medium, and relates to the field of data processing technologies and cloud computing. The table identification method comprises the following steps: detecting a table on a target picture to obtain a candidate table identification result; extracting a merging feature of the candidate table identification result, and determining to-be-merged rows in the candidate table identification result by utilizing the merging feature; extracting direction features of the to-be-merged rows, and determining amerging direction of the to-be-merged rows by utilizing the direction features; and according to the to-be-merged rows and the merging direction of the to-be-merged rows, adjusting the candidate tableidentification result to obtain a target table identification result. According to the embodiment of the invention, the problem that the identification result is inaccurate in the existing table identification scheme is solved, and the table identification accuracy is improved.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
Collision arbitration method and apparatus for reading multiple frequency identification tags
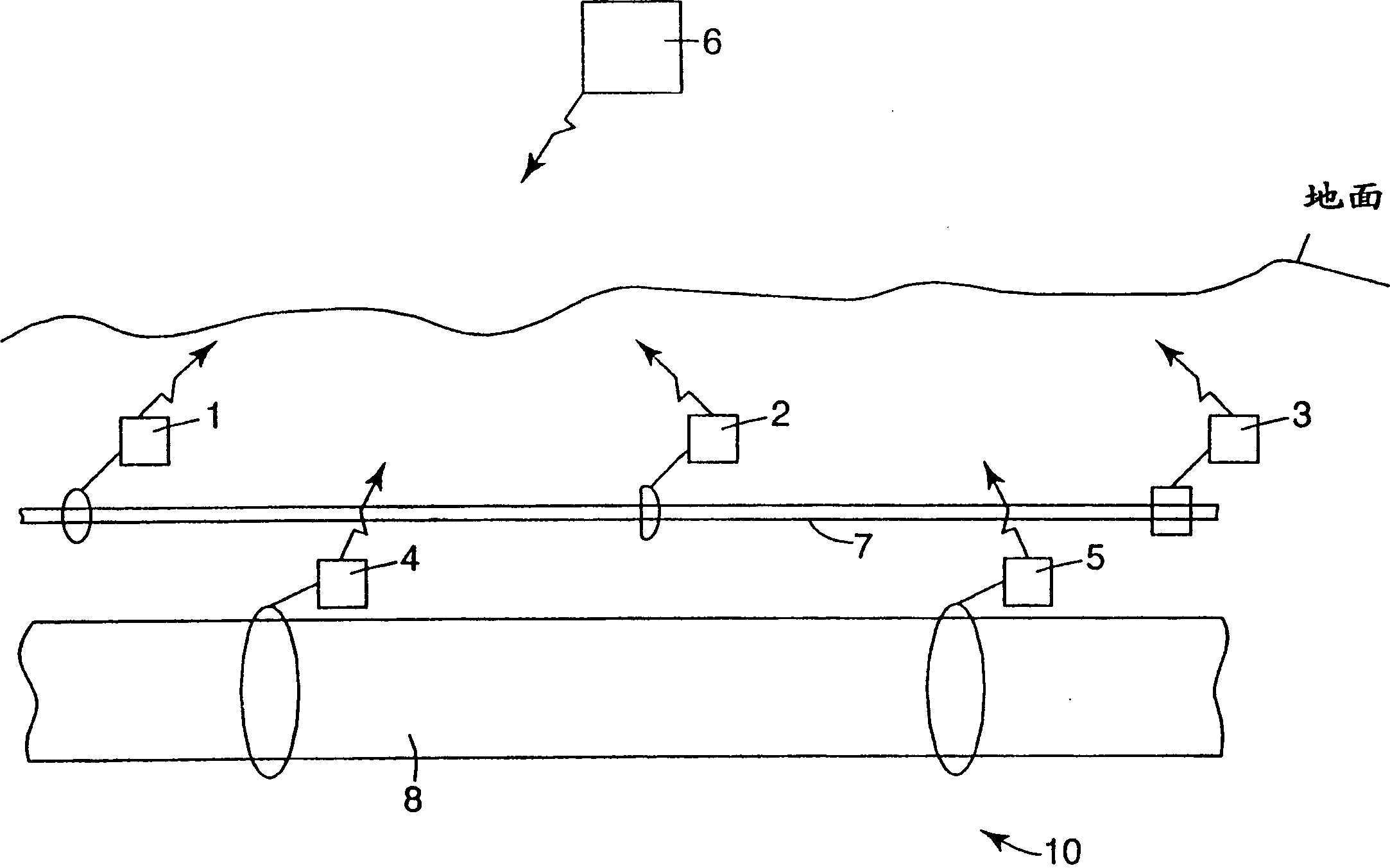
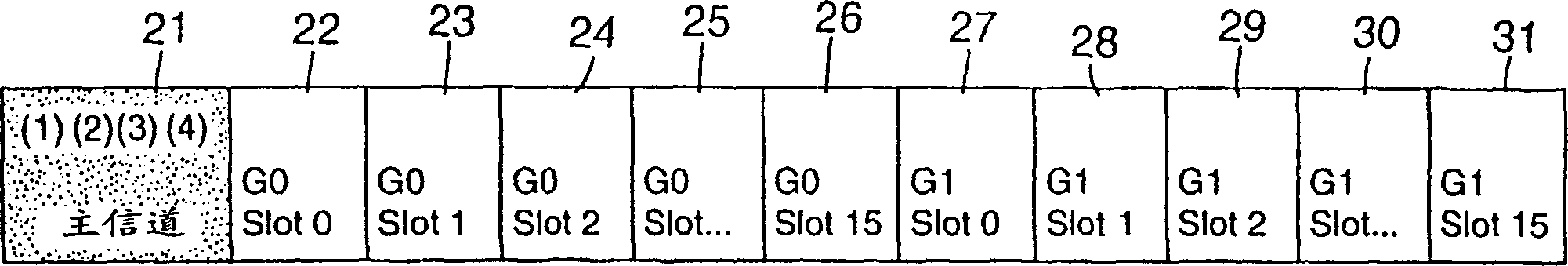
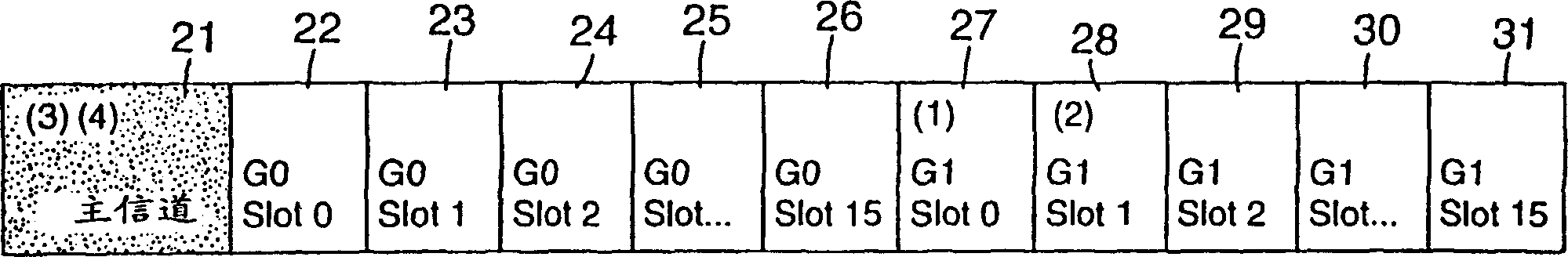
InactiveCN1433555AMemory record carrier reading problemsCo-operative working arrangementsRadio frequencyPrimary channel
A method for simultaneously reading a serial number and / or other information from multiple colliding RF signals from RF identification tags (1-5) requires minimal additional logic in the tag's processor and provides for a powerful and rapid sorting and identification scheme. This technique employs a primary communication channel and multiple secondary channels, A locator or reader unit (6) interrogates the tags (1-5), which respond with an RF signal. Upon receiving multiple signals, the locator or reader unit (6) commands the RFID tags (1-5) and requires them to transmit another response, which is transmitted in one of the secondary channels based on a portion of their unique serial identification number, thereby forcing the tags (1-5) to sort in the secondary channels. These secondary channels are assigned using a portion of the unique serial identification numbers for the tags. The reader (6) then detects an acknowledgment in the occupied secondary channels and commands a tag (1-5) in a particular channel to move to the primary channel. Once the signal is transmitted in the primary channel, the reader (6) reads the identification number. If there is further collision, the collided tags are returned to the secondary channel and sorted again using a different portion of their ID number. This process continues until all the tags (1-5) are sorted and identified. Once the tags (1-5) are all sorted, the tags (1-5) are assigned yet another channel distinct from the secondary channels that are used for sorting.
Owner:3M INNOVATIVE PROPERTIES CO
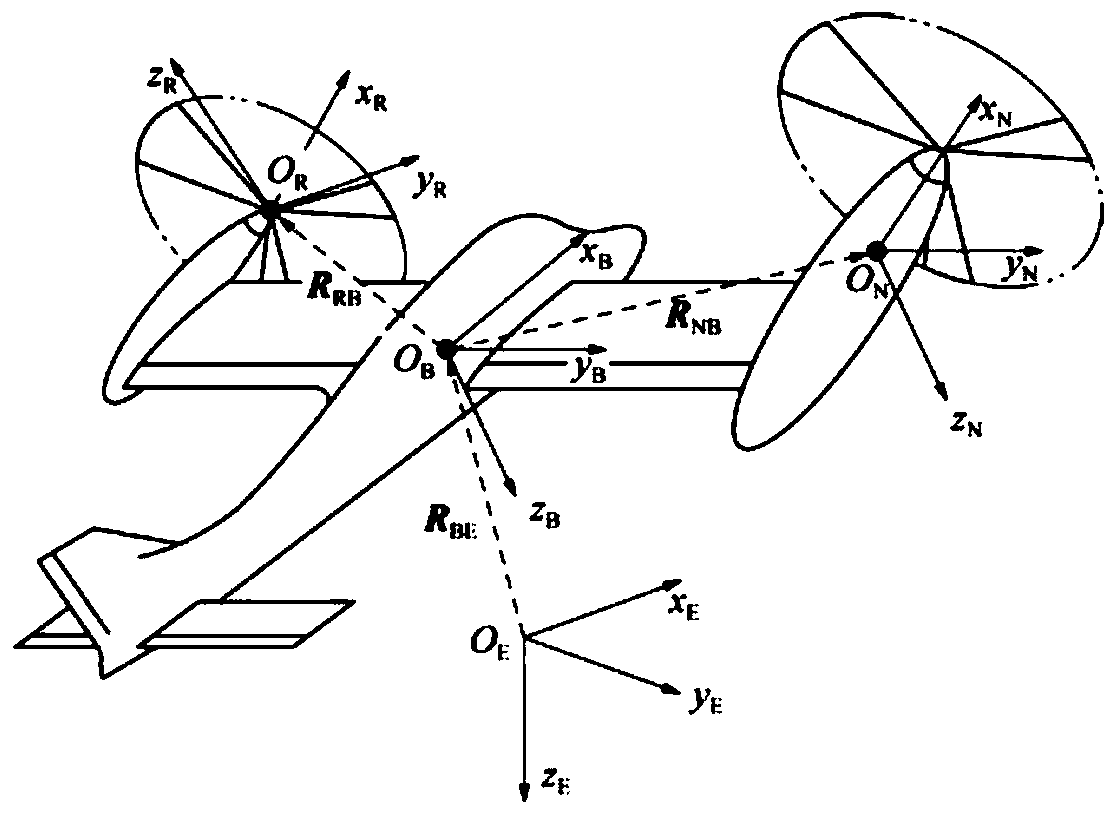
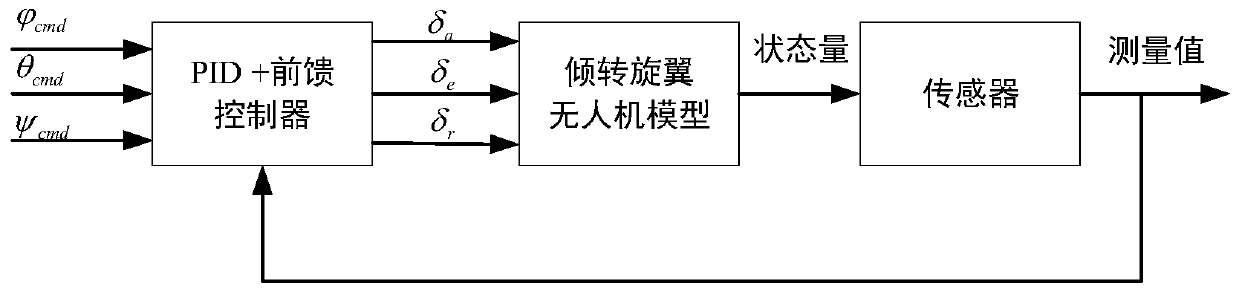
Tilting rotor wing unmanned aerial vehicle nonlinear shallow grey model identification and correction method
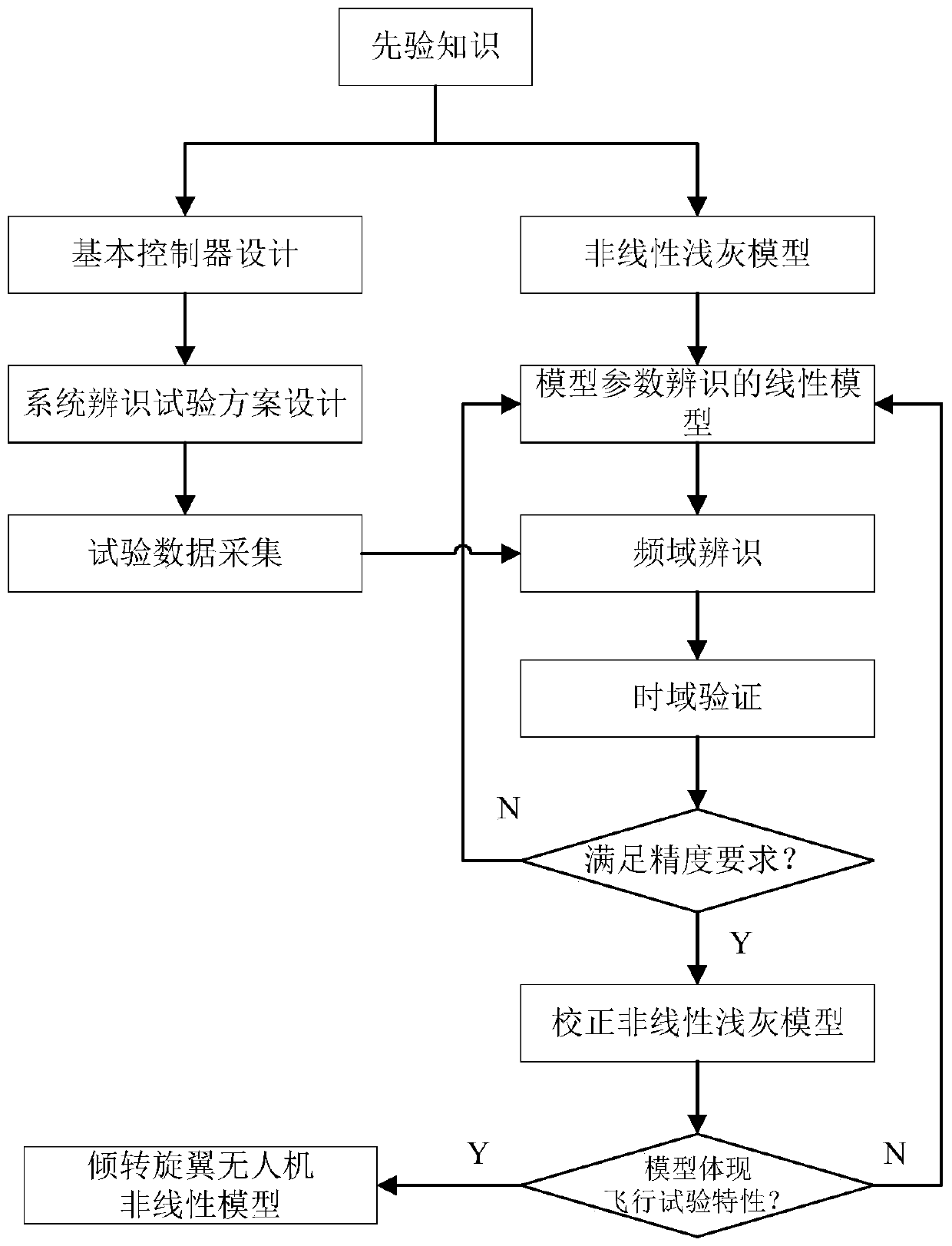
ActiveCN111538237AAccurate nonlinear light gray modelTrue reflection of flight responseAdaptive controlNonlinear modelClassical mechanics
The invention belongs to the field of unmanned aerial vehicle flight control, and relates to an unmanned aerial vehicle shallow grey model correction method, particularly to a method for correcting atilting rotor wing unmanned aerial vehicle nonlinear shallow grey model by combining mechanism modeling and identification modeling. The method comprises the steps: providing a nonlinear light grey model of a tilting rotor wing unmanned aerial vehicle through mechanism analysis, and after linearization, determining an identification model structure according to identification requirements; designing an identification scheme including designing an input signal and selecting a data sampling frequency and a data length, and preprocessing acquired flight test data; based on the flight test data, utilizing CIFER software to obtain a linear model of the tilting rotor wing unmanned aerial vehicle in each mode; and finally correcting the non-linear model by utilizing an identification result, andif necessary, continuously iterating the process until the linearized parameters of the non-linear model are consistent with the structure and the identification model. By means of the method, the accurate nonlinear model of the tilting rotor wing unmanned aerial vehicle can be obtained.
Owner:BEIHANG UNIV
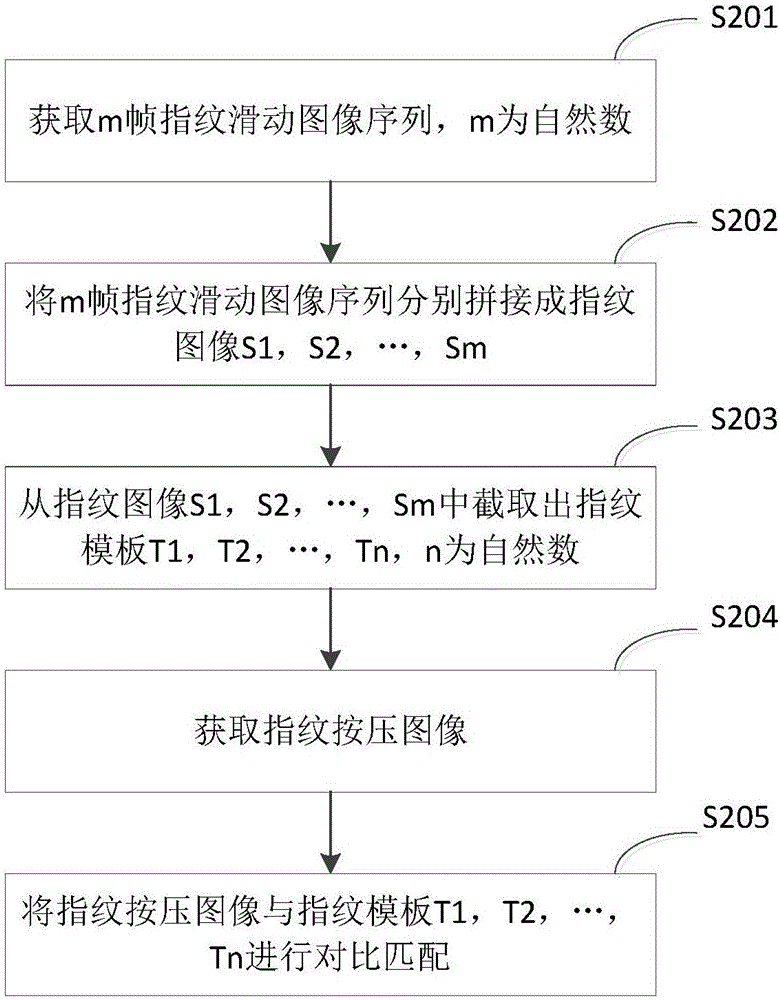
Fingerprint identification method, device and terminal
The invention provides a fingerprint identification method, device and terminal. The fingerprint identification method comprises the following steps: acquiring m pieces of fingerprint sliding image sequences; splicing m pieces of fingerprinting image sequences into fingerprint images S1, S2, ..., Sm; the fingerprint templates T1, T2, ..., Tn are obtained by matching the fingerprint image with the fingerprint templates T1, T2, ..., Tn. The invention combines sliding registration and pressing recognition, sliding registration and then merging the acquired fingerprint image sequence into large fingerprint images S1, S2, ..., Sm, and then fingerprints used for pressing recognition are cut out in these fingerprint images. The user can finish the registration of the fingerprint template by sliding the finger at the time of registration, and only need to press the fingerprint once to complete the fingerprint recognition, and the organic integration of the prior art fingerprint identification scheme is realized.
Owner:SHENZHEN GOODIX TECH CO LTD
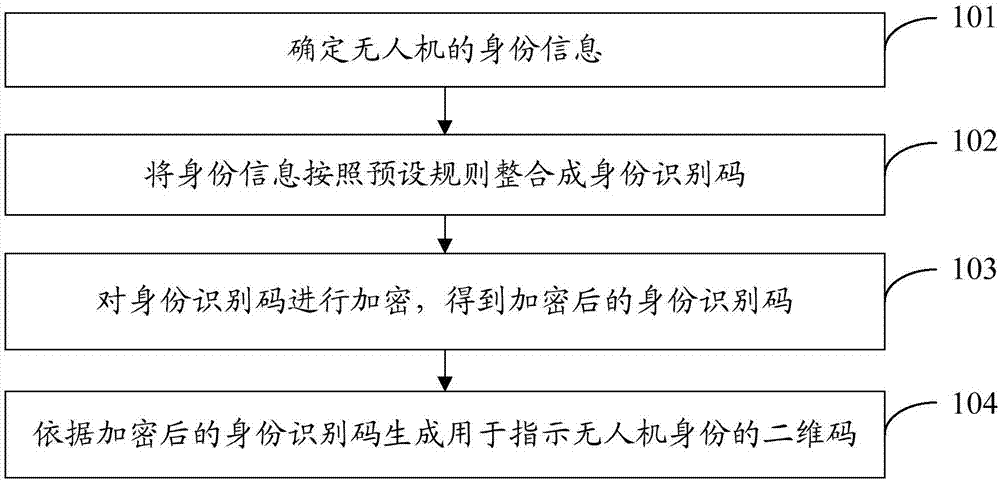
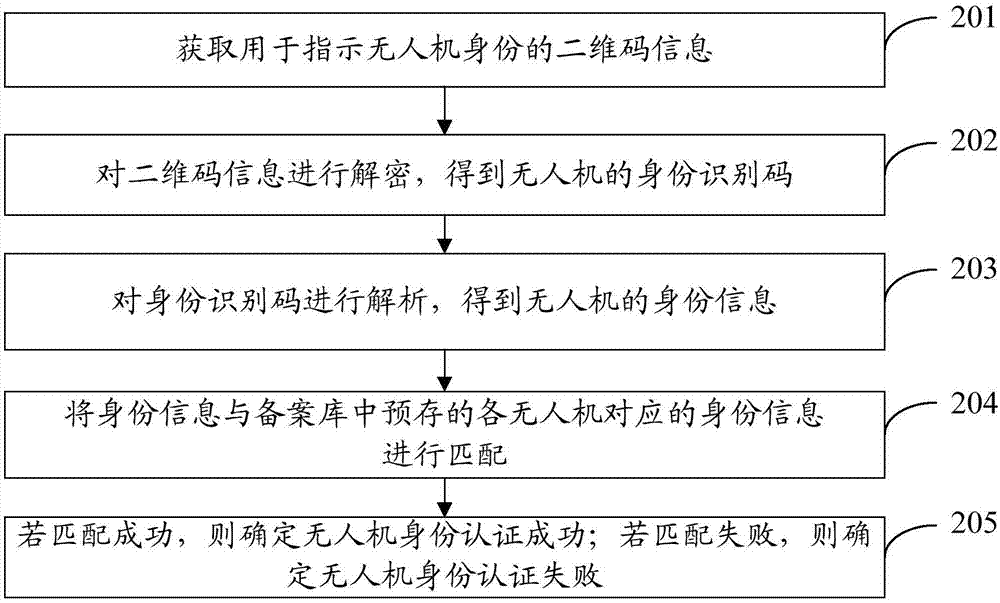
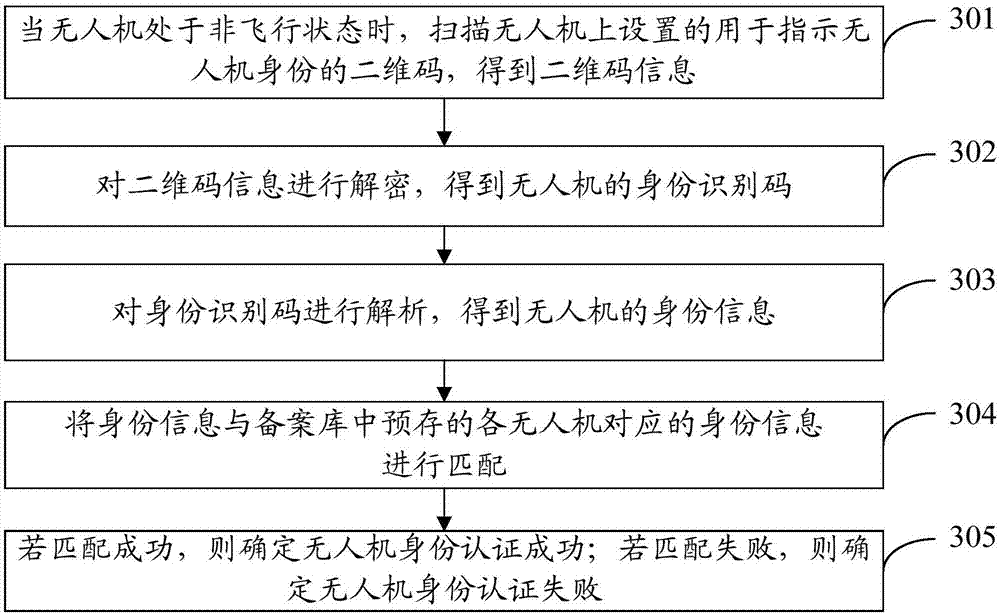
Unmanned aerial vehicle identity identification method and management platform system
ActiveCN107291097AGuaranteed to fly legallyBlack fly effectiveDigital data authenticationPosition/course control in three dimensionsUncrewed vehicleIdentification scheme
The invention provides an unmanned aerial vehicle identity identification method and a management platform system. The unmanned aerial vehicle identity identification method comprises steps that two-dimensional code information used for indicating an unmanned aerial vehicle identity is acquired; the two-dimensional code information is decoded, and the identity identification code of the unmanned aerial vehicle is acquired; the identity identification code is parsed to acquire the identity information of the unmanned aerial vehicle; the identity information is matched with the identity information corresponding to the various unmanned aerial vehicles pre-stored in a record database; when the matching succeeds, the successful unmanned aerial vehicle identity identification is determined; when the matching fails, the failed unmanned aerial vehicle identity identification is determined. By adopting an unmanned aerial vehicle identity identification scheme provided by the invention, illegal flight and disordered flight are effectively struck, and the legal flight of the unmanned aerial vehicle is guaranteed.
Owner:北京明朝万达科技股份有限公司
Identification method of DFIG wind farm equivalent parameter
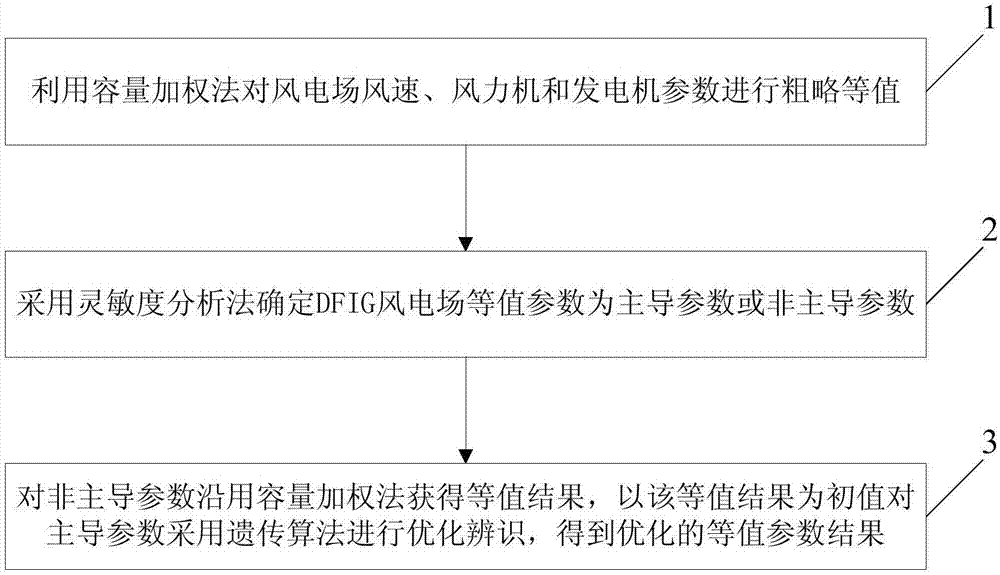
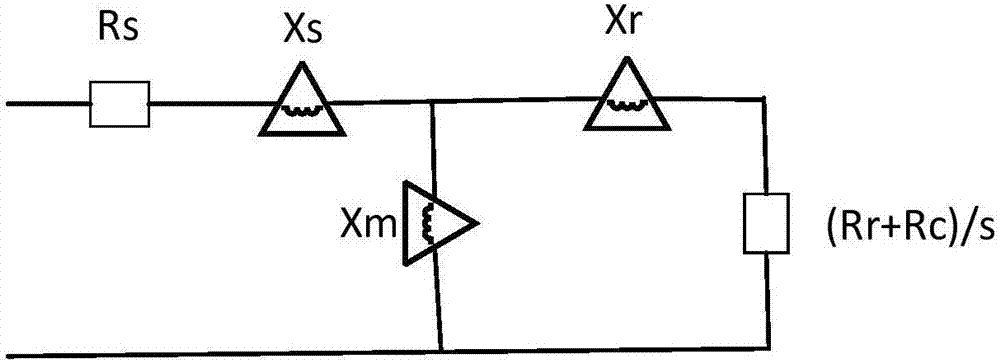
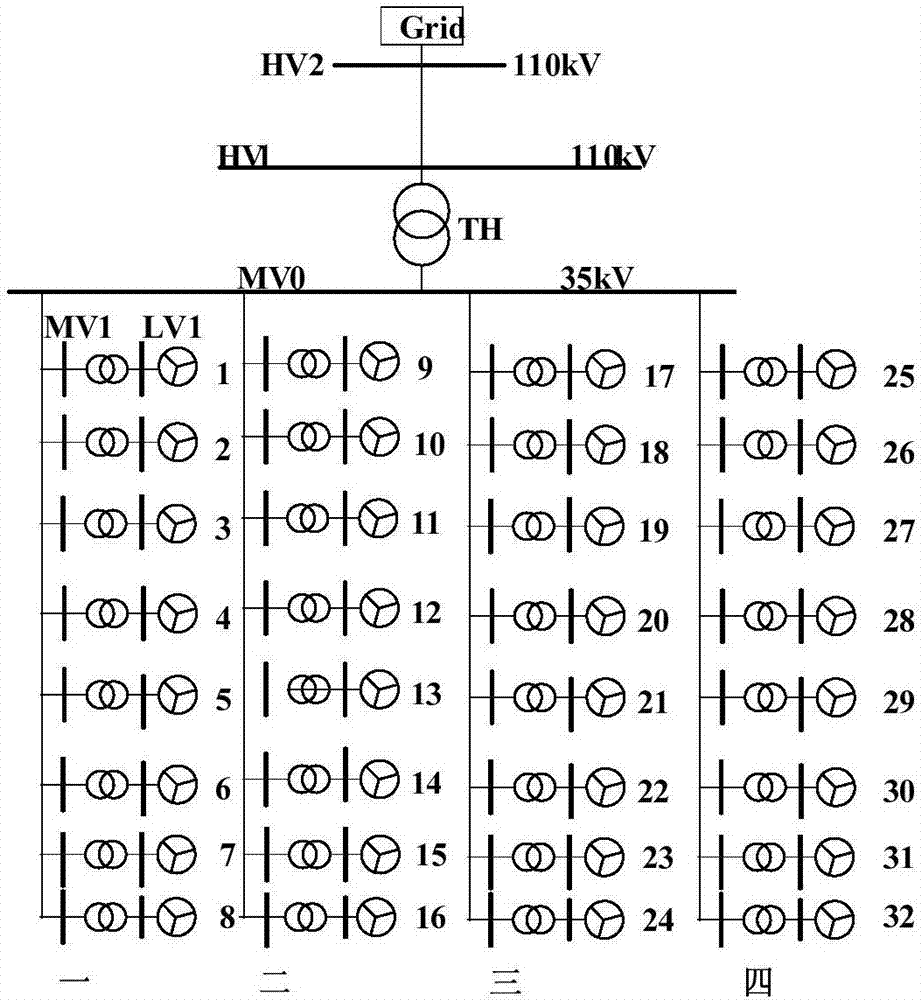
ActiveCN107451364AIncrease credibilityDesign optimisation/simulationSpecial data processing applicationsGenetic algorithmEngineering
The invention discloses an identification method of DFIG wind farm equivalent parameter. The identification method includes the following steps: firstly, a volume weighting method is used to equate parameters of wind speed, wind turbines and electric generators in a wind farm roughly; Then whether a DFIG wind farm equivalent parameter is a dominant parameter or a non-dominant parameter is determined by using a sensitivity analysis method; Then the volume weighting method continues to be used to obtain an equivalent result of the non-dominant parameters, the equivalent result is taken as an initial value and the dominant parameters are optimized and identified by using genetic algorithm, and an optimized result of the equivalent parameters is acquired. The identification method is a final identification scheme of parameters equivalence, which can obtain a more accurate equivalent model of DFIG wind farm and further improve the credibility of simulation results.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com