Identity authentication method based on Hyperledger network
An identity authentication and authentication algorithm technology, applied in the blockchain field, can solve the problems of reducing communication efficiency, increasing communication costs and energy consumption, and achieving the effect of ensuring non-tampering and authentication security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
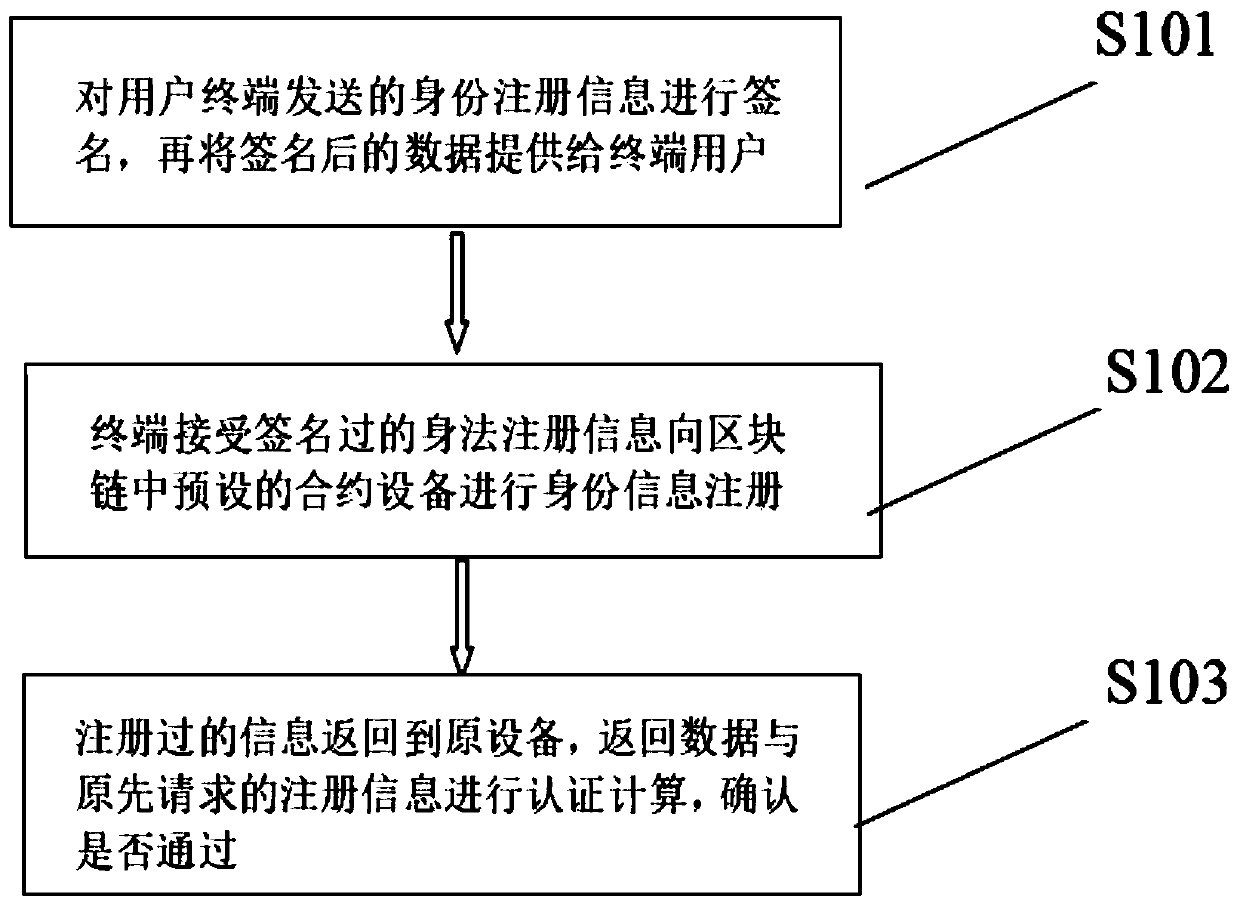
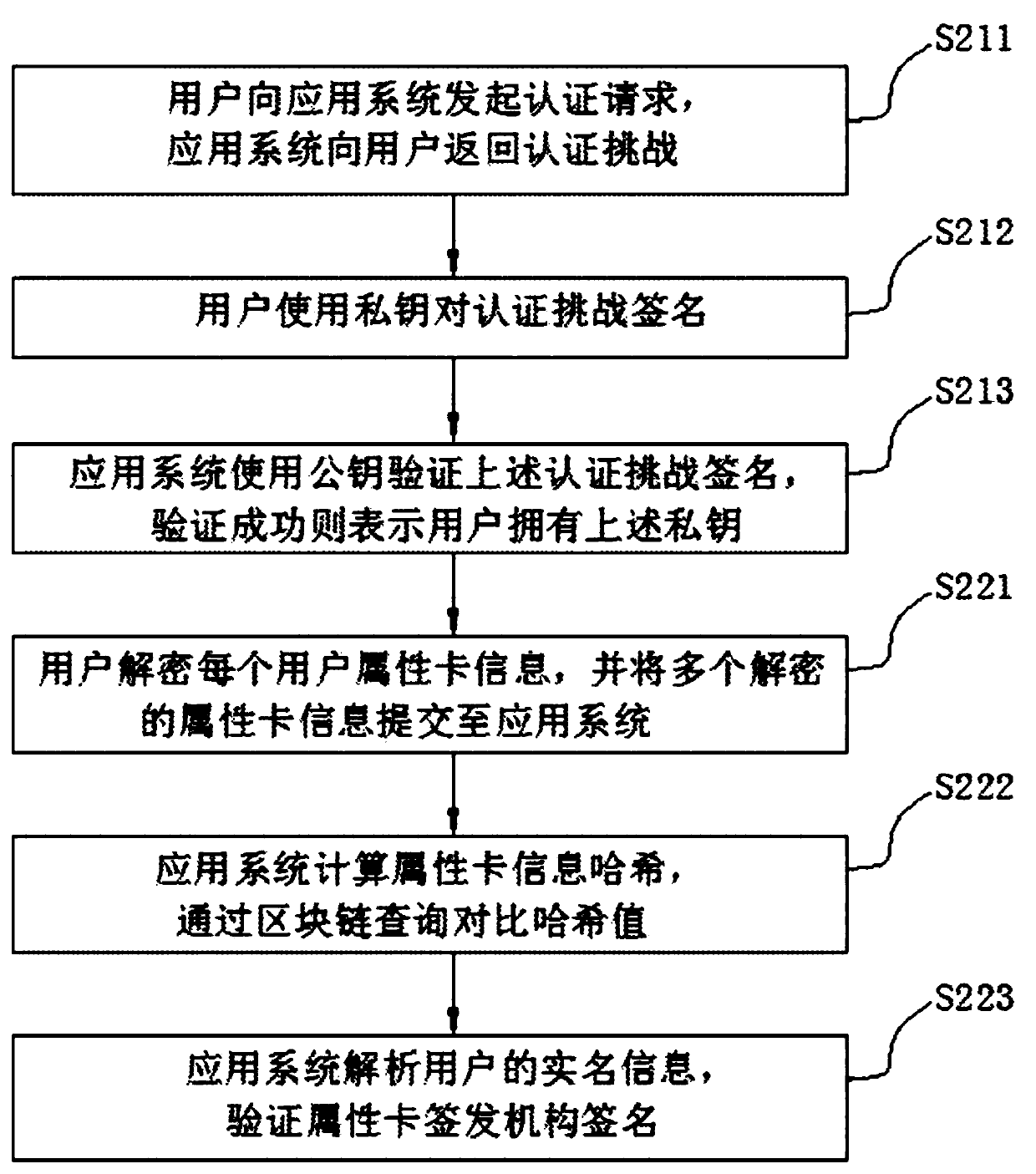
[0028] (1), user registration:
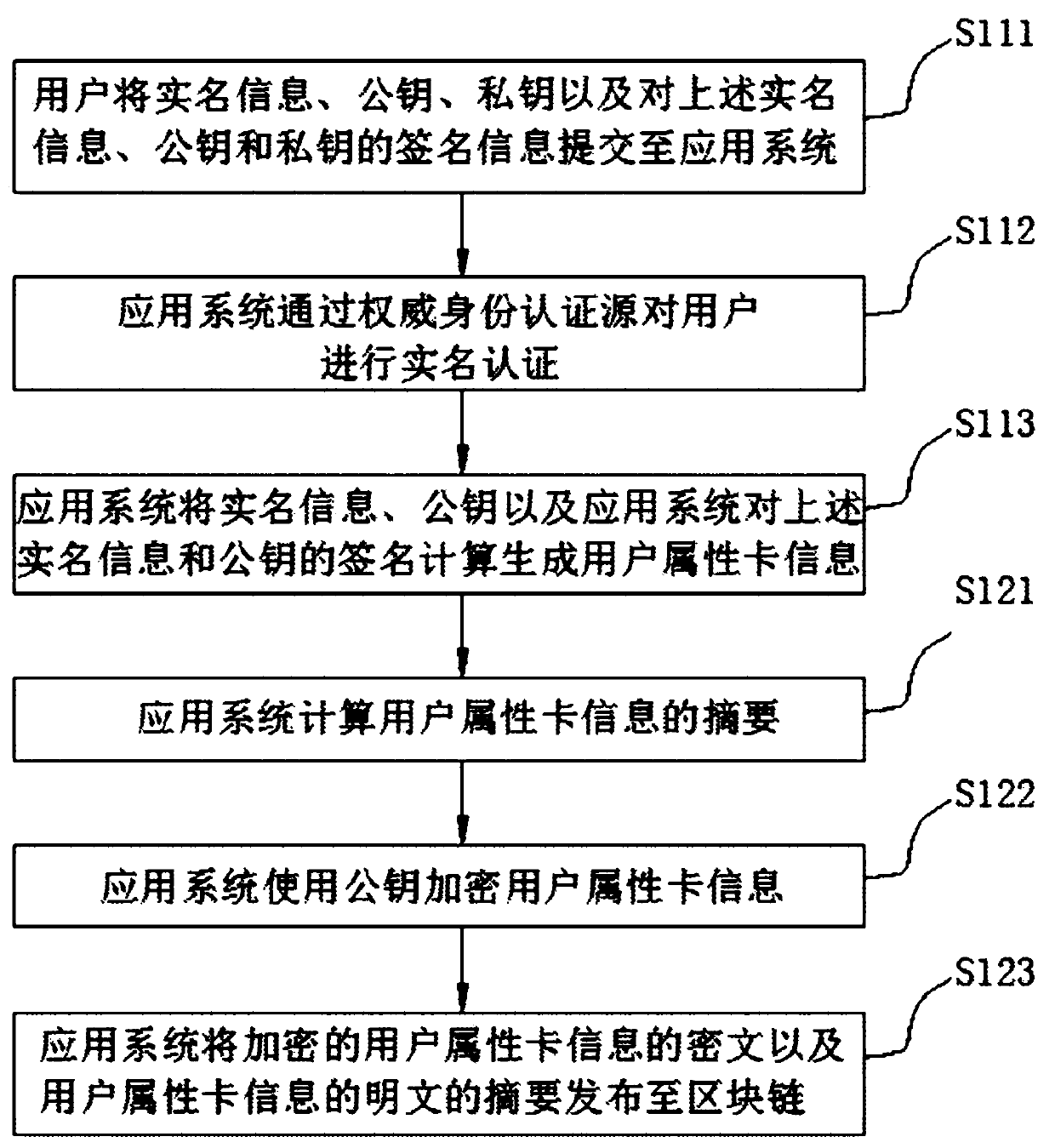
[0029] (1.1), the user generates a public key and a private key when registering for the first time, and initiates a registration request to the application system;
[0030] (1.2), the user submits the real name information, public key, private key and signature information on the above real name information, public key and private key to the application system;
[0031] (1.3), the application system performs real-name authentication on the user through the authoritative identity authentication source;
[0032] (1.4), the application system calculates the real-name information, public key, and the signature of the application system on the above-mentioned real-name information and public key to generate user attribute card information. The user attribute card information includes: user ID, real-name information, source of real-name authentication, public key, The identity of the attribute card issuing institution, the public key of the attribu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com