Two-dimensional code coding-and-decoding and authentication method and two-dimensional code coding-and-decoding and authentication device
An authentication method and authentication device technology, applied in the field of two-dimensional codes, can solve problems such as defrauding users of phone charges, failing to solve the problem of two-dimensional code issuer authentication, and two-dimensional code standards are not easy to implement, so as to achieve improved security and effective authentication Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
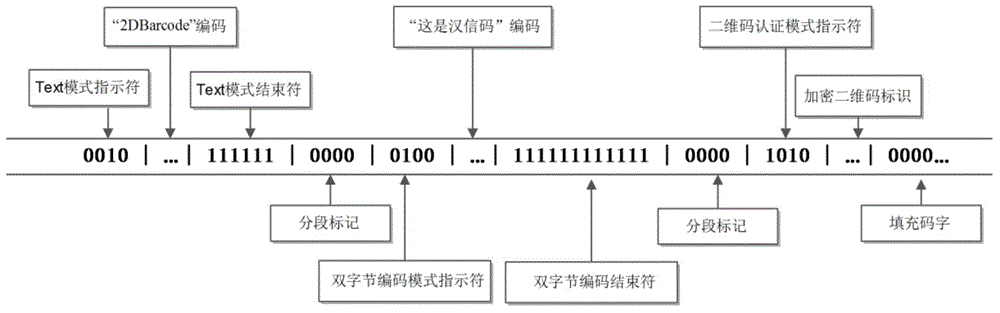
[0049] The embodiment of the present invention provides a multi-segment data encoding method in the two-dimensional code through a unique two-dimensional code generation and identification method, which can not only hide the data that does not want to be disclosed, realize the simultaneous preservation of public content and private content in the two-dimensional code, but also realize The legality of the two-dimensional code itself is certified, and it can provide two-dimensional code use services for customers who are unwilling to develop two-dimensional code generation certification or do not have the ability to develop it.
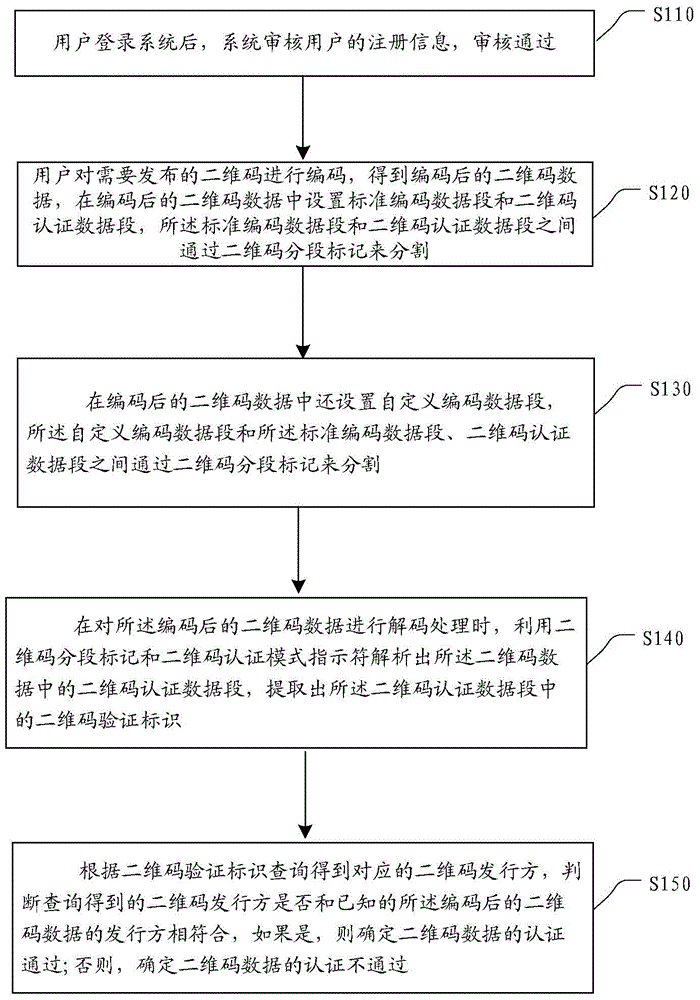
[0050] This embodiment provides a processing flow of a two-dimensional code codec and authentication method as follows: figure 1 As shown, the following processing steps are included:
[0051] Step S110, the two-dimensional code encoding and decoding and authentication method system in the embodiment of the present invention provides users with function...
Embodiment 2
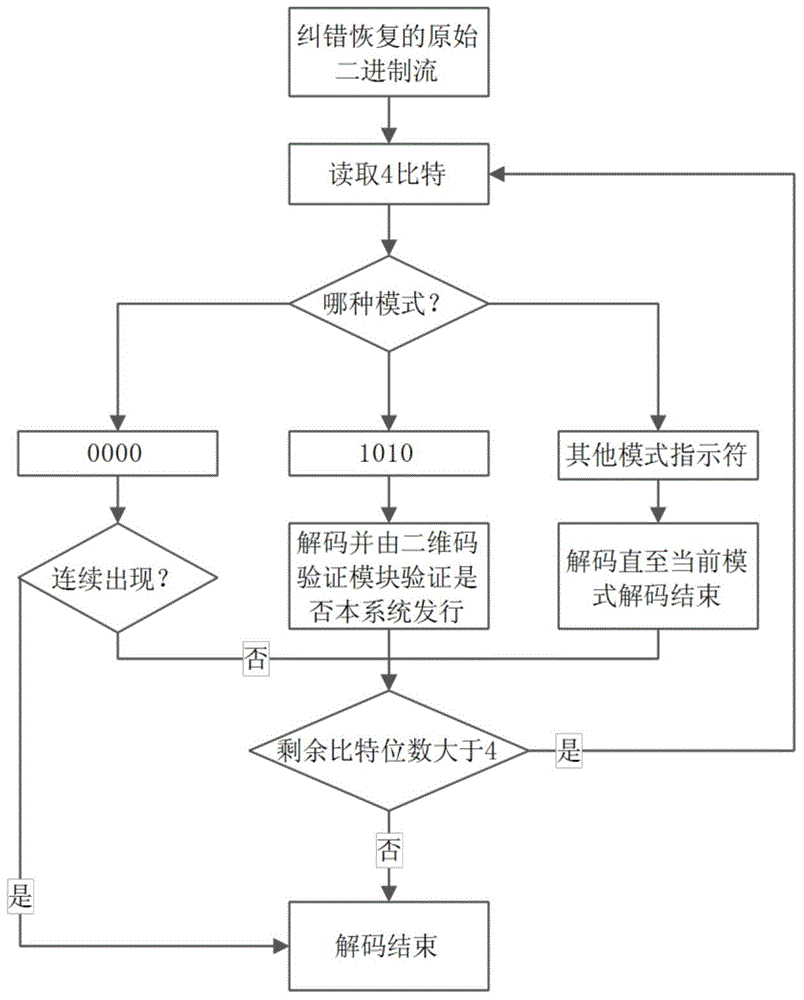
[0077] This embodiment provides a two-dimensional code encoding and decoding and authentication device, and its specific implementation structure is as follows: Figure 4 As shown, it can specifically include the following modules:
[0078] Standard data segment coding module 41, for setting standard coded data segment in the encoded two-dimensional code data;
[0079] The authentication data segment encoding module 42 is used to set the two-dimensional code authentication data segment in the encoded two-dimensional code data, and the standard encoded data segment and the two-dimensional code authentication data segment are divided by two-dimensional code segmentation marks ; Set a two-dimensional code verification identifier in the two-dimensional code authentication data segment, and the two-dimensional code verification identifier is used to verify that the encoded two-dimensional code data is issued by a designated two-dimensional code issuer.
[0080] Further, the authen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com