User authentication method, device and system
A user authentication and user technology, applied in the communication field, can solve problems such as account management server and authentication server bottlenecks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
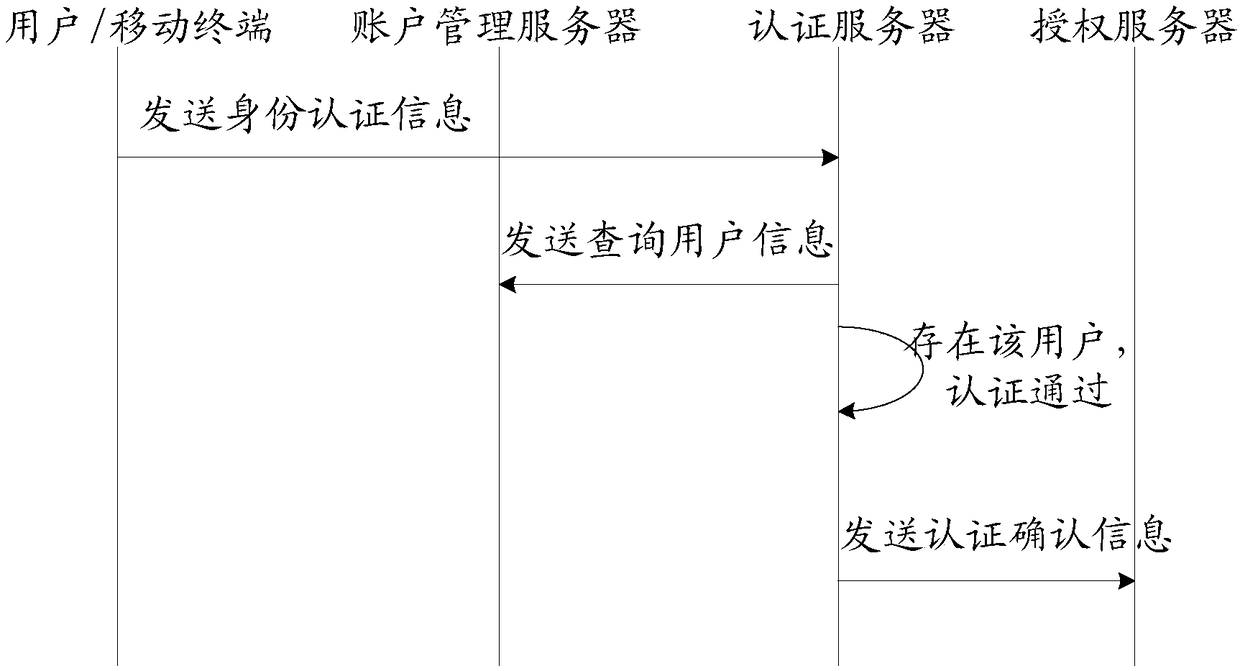
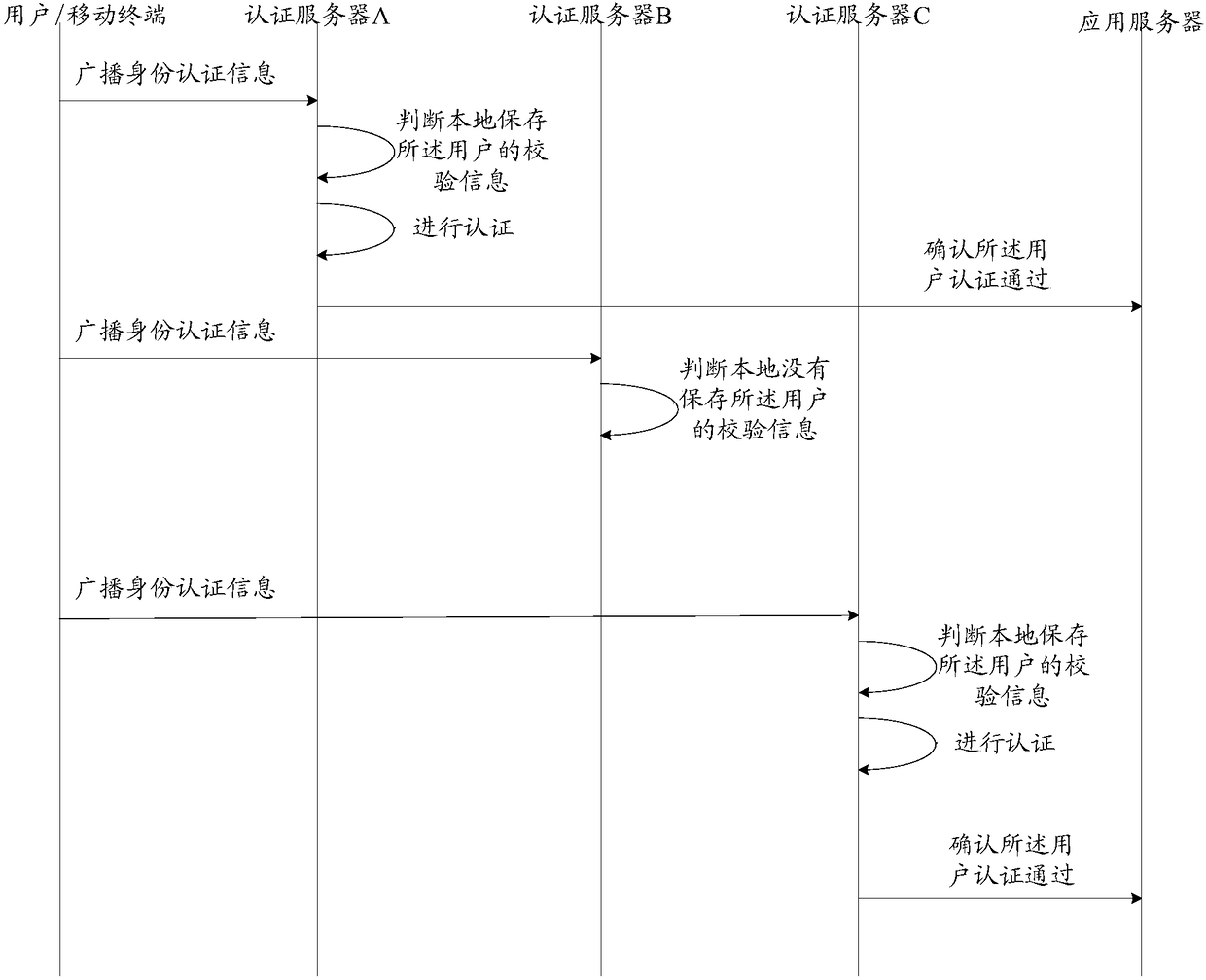
[0087] An embodiment of the present invention provides a user authentication system, the system includes: an application server and at least two authentication servers; wherein,
[0088] At least two authentication servers, configured to receive the identity authentication information broadcast by the mobile terminal, judge whether the verification information of the user is stored locally according to the user identification information carried in the identity authentication information, and if so, according to the Verifying the information and the identity authentication information to authenticate the user, and if the authentication is passed, sending authentication confirmation information to the application server;
[0089] The application server is configured to receive authentication confirmation information sent by the authentication server, determine whether the number of authentication servers sending authentication confirmation information for the user reaches a set ...
Embodiment 2
[0101] In the prior art, the authentication information of all users is stored in the account management node and stored in plain text. If the account management node is cracked, it means that the authentication information of all users in the user authentication system has been leaked. , so that the security of user authentication information is greatly reduced. In order to improve the security of user identity authentication information, on the basis of the above-mentioned embodiments, in the embodiments of the present invention,
[0102] The at least two authentication servers are used to receive the identity authentication information encrypted by the private key broadcast by the mobile terminal, and determine whether the identity authentication information encrypted by the private key of the user is stored locally, and if so, use the The saved public key decrypts the identity authentication information encrypted by the user's private key stored locally and the received id...
Embodiment 3
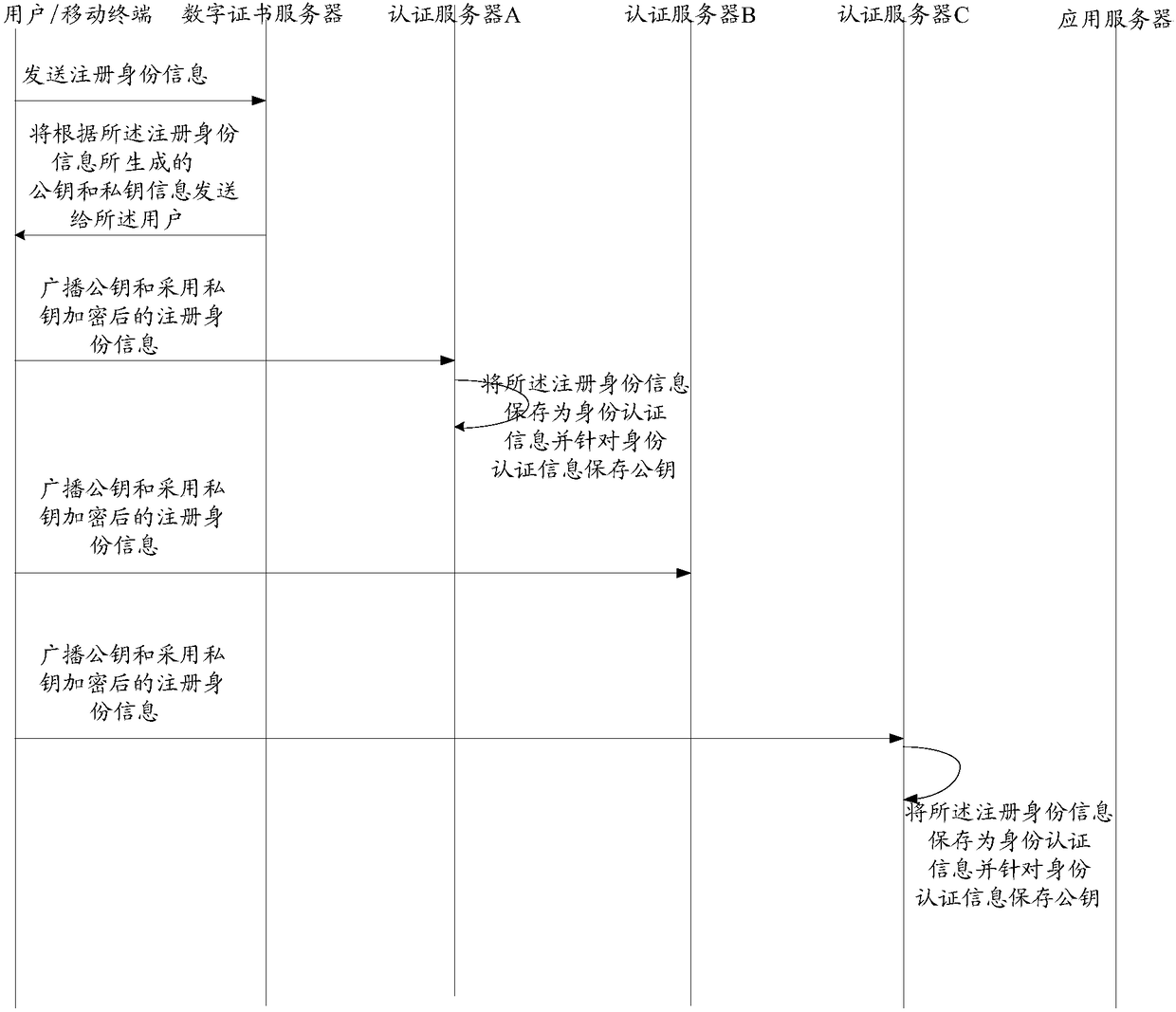
[0109] In order to improve the security of user authentication information, on the basis of the above-mentioned embodiments, in the embodiment of the present invention, the user authentication system further includes:
[0110] The digital certificate server is configured to receive the registration identity information sent by the mobile terminal, wherein the registration identity information carries the identification information of the user, generates a public key and a private key according to the registration identity information, and converts the public key and the private key sending information to the mobile terminal;
[0111] The at least two authentication servers are further configured to receive the public key sent by the mobile terminal and the registered identity information encrypted with the private key, save the registered identity information as identity authentication information, and The authentication information holds the public key.
[0112] In order to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com