An agile authentication access method for third-party effective identity hosting based on account concealment
A technology of identity trusteeship and identity authentication, applied in the field of identity verification, can solve problems such as unguaranteed security, inability to distinguish, and impact on company operations, so as to eliminate false network traffic and false access, prevent false traffic, and improve high security attributes Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0072] The specific embodiments provided by the present invention will be described in detail below in conjunction with the accompanying drawings.
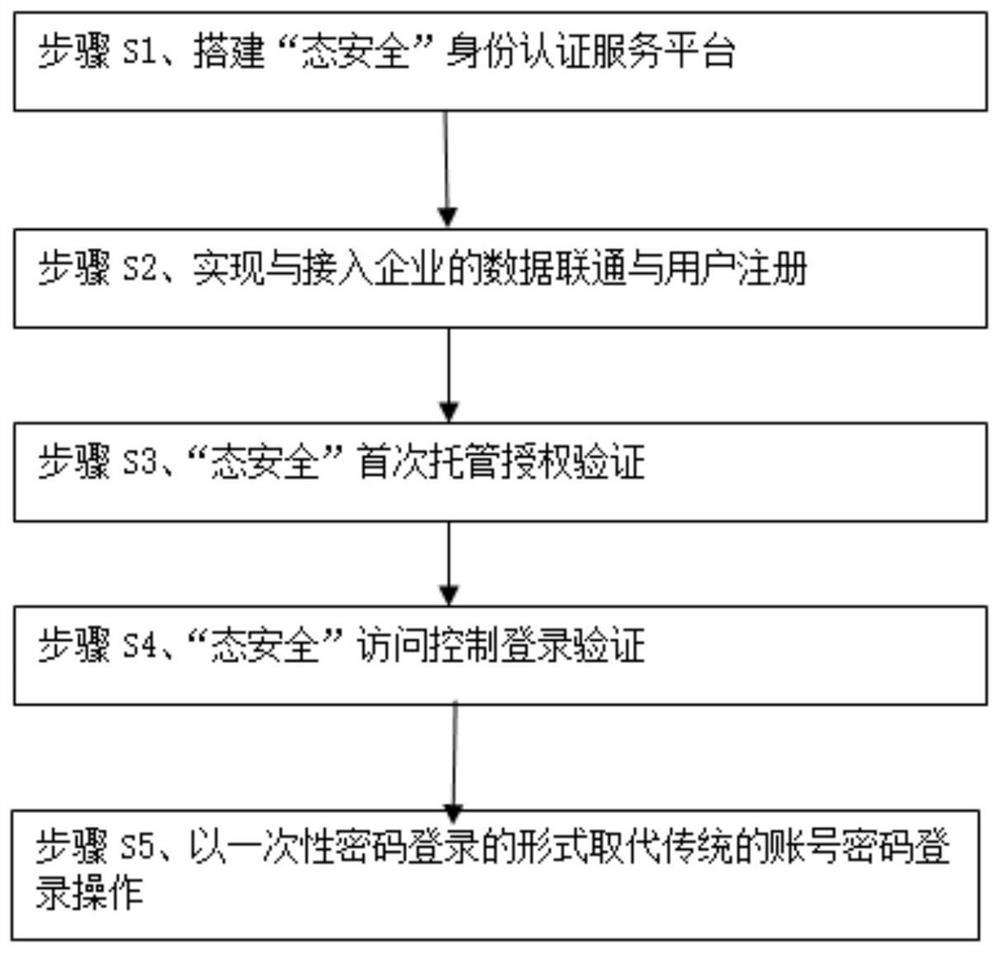
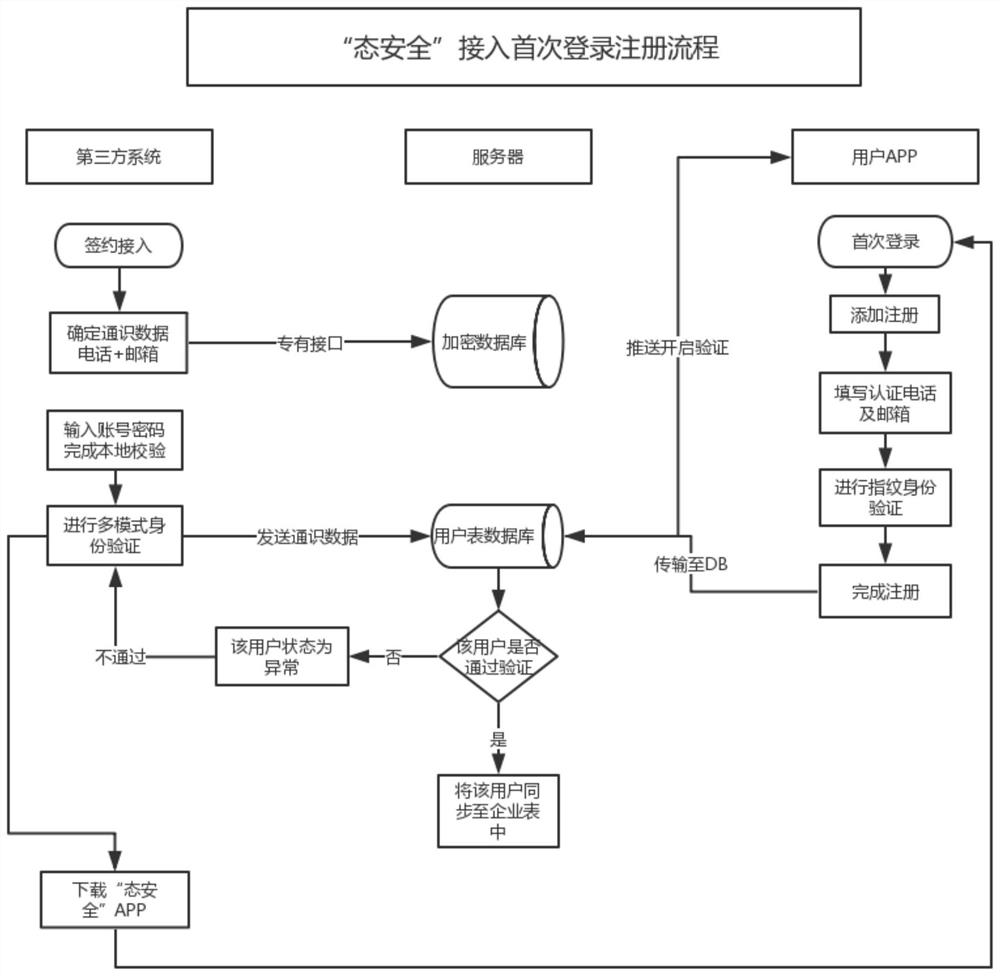
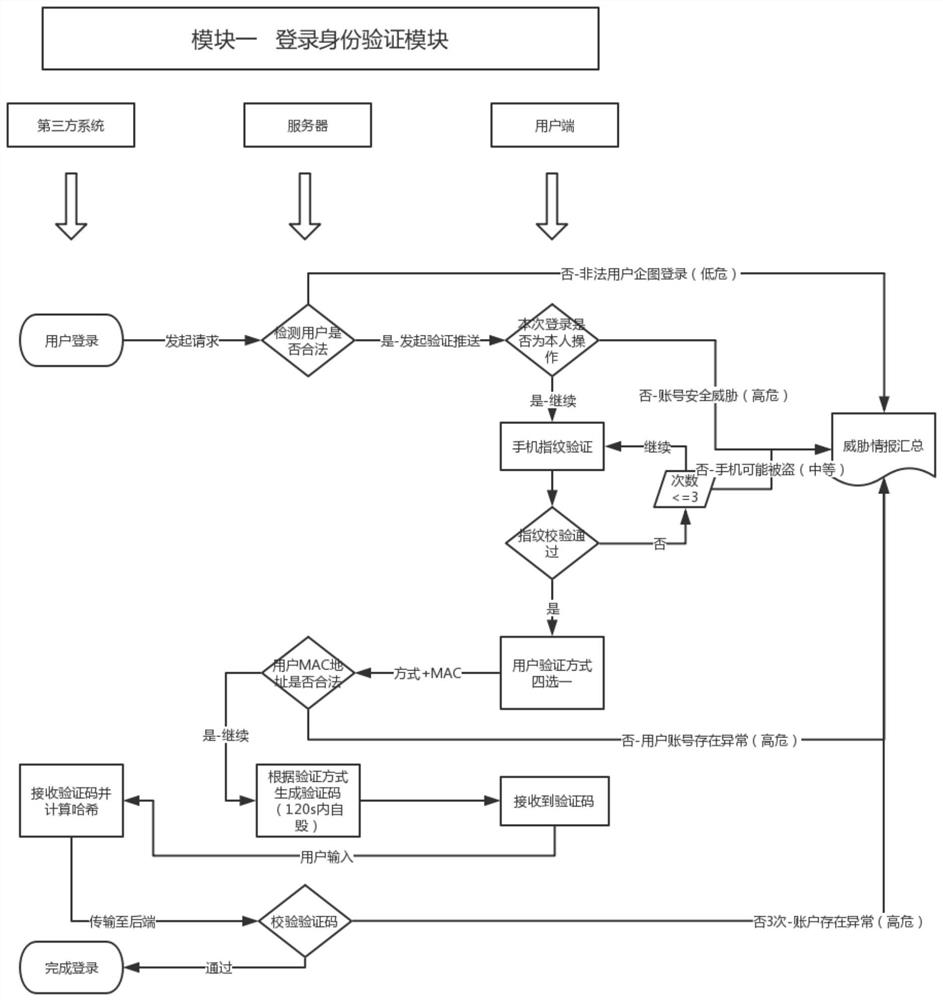
[0073] Please refer to Figure 1-Figure 6 , this technical solution adopts the principle of "two minimums and one maximum". And to minimize the access to the operation data of the enterprise, only the account name in the enterprise account login system is required, and any other data about the user account will not be requested to obtain and store; to minimize the acquisition of user privacy data, only to obtain the user's registration The phone, mailbox and mobile phone hardware address are used for data docking, and any data of other users except high-authority authentication users will not be stored; it maximizes the access control security and operational security of access enterprises and enterprise users.
[0074] 1 Build an identity authentication service platform of "Ecology Security"
[0075] By building a unified "stat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com