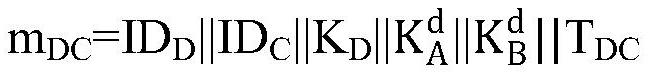Patents
Literature
43results about How to "No tampering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
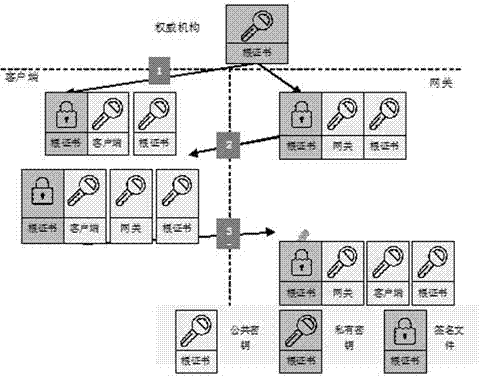
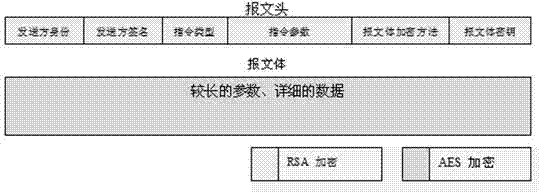
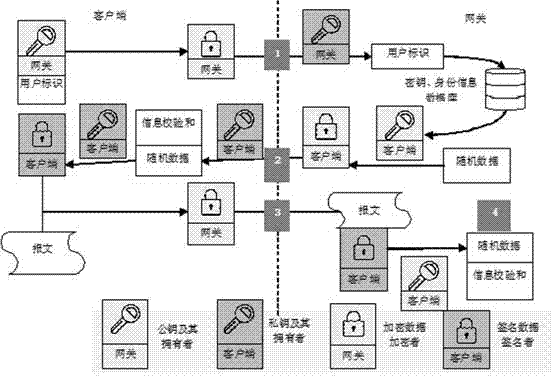
Information safety algorithm based on energy information gateway in smart power grid
ActiveCN103618610AGuaranteed correspondenceNo tamperingUser identity/authority verificationData transmissionSmart grid
The invention relates to an information safety algorithm based on an energy information gateway in a smart power grid, ad an introduced safety mechanism is divided into an identity verification process, an encryption information message format and an information communication process according to a connecting flow path. Based on an RSA encryption algorithm, an advanced encryption standard (AES), digital signature and other technologies, the safety mechanism with instruction information transmission confidentiality, integrity and non-repudiation is achieved. By using the respective advantages of the three technologies, the condition that a smart electricity using network transmits sensitive information in a public network is combined, the situations of identify forging, data stealing, repeated attack sending and the like are considered sufficiently, and a bi-directional identity verification and safe instruction transmission mechanism is provided, so that the data attacks are effectively prevented, and traceability of instructions is ensured. A practicable and reliable solution is provided for safe data transmission in the demand response and home automation technology in China.
Owner:SHANGHAI SHANGTA SOFTWARE DEV CO LTD
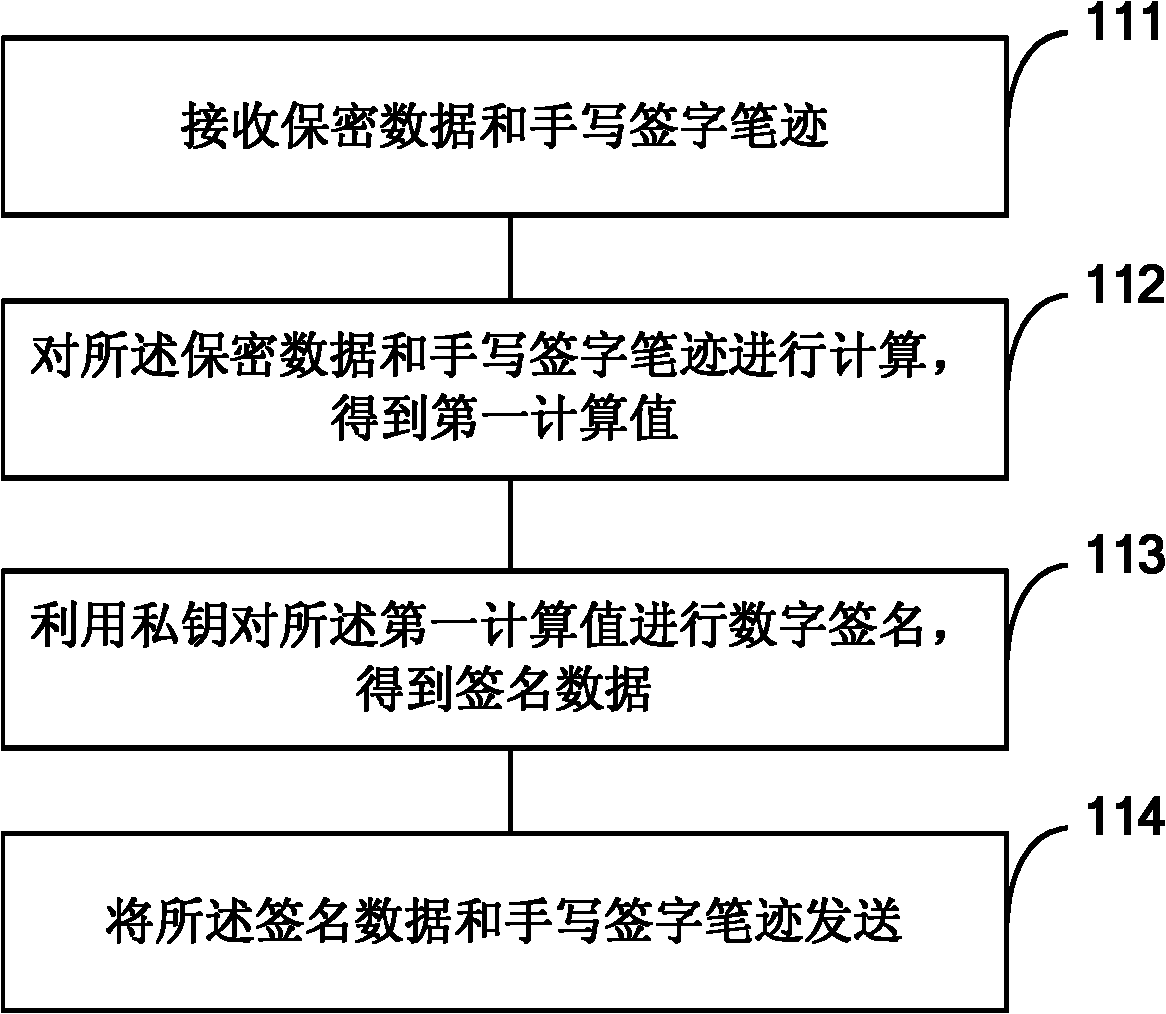
Identity authentication method, identity authentication equipment, server and identity authentication-based encryption method
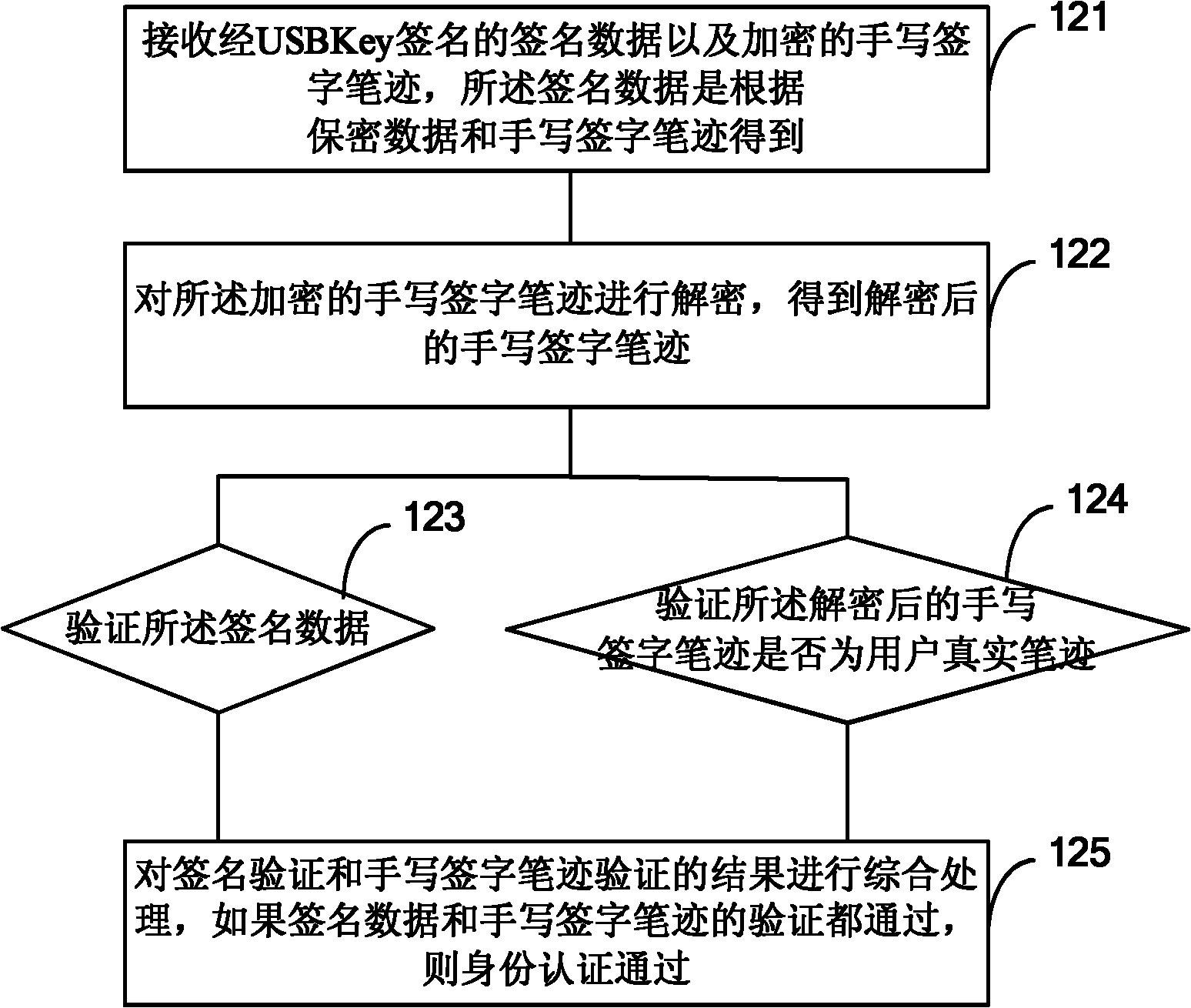
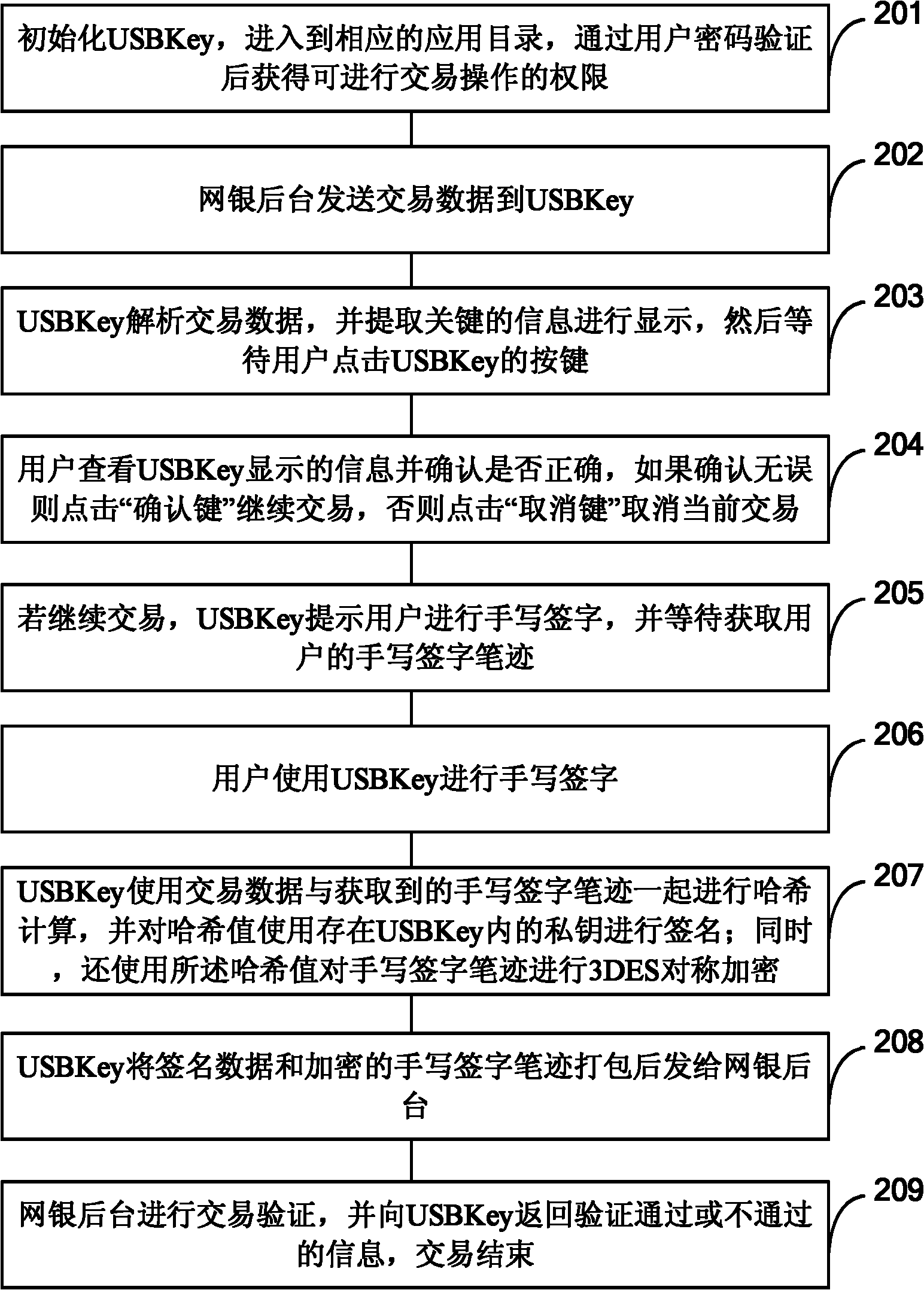
ActiveCN102035654ANo tamperingSolve the anti-counterfeiting problemUser identity/authority verificationHandwritingDigital signature
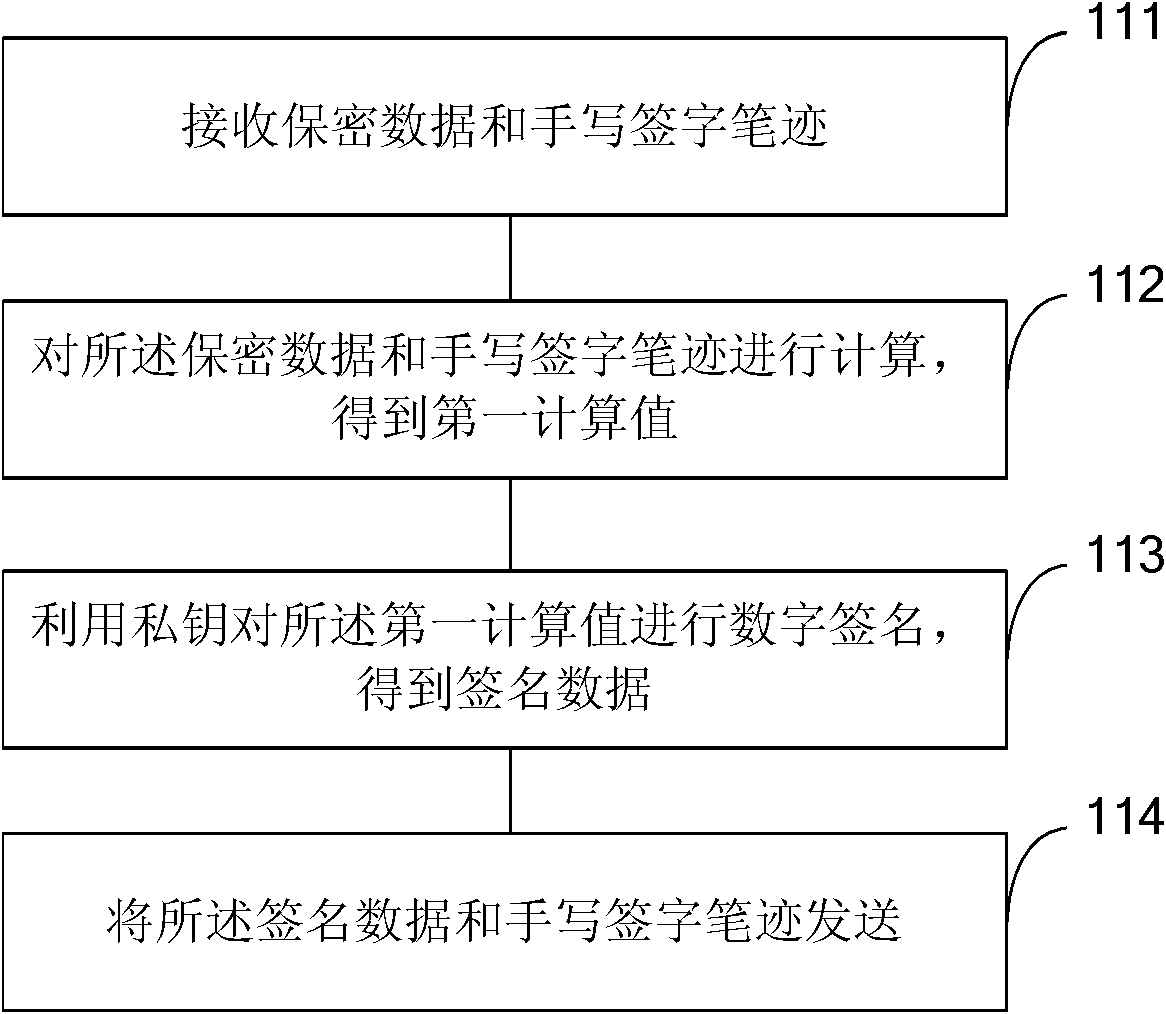
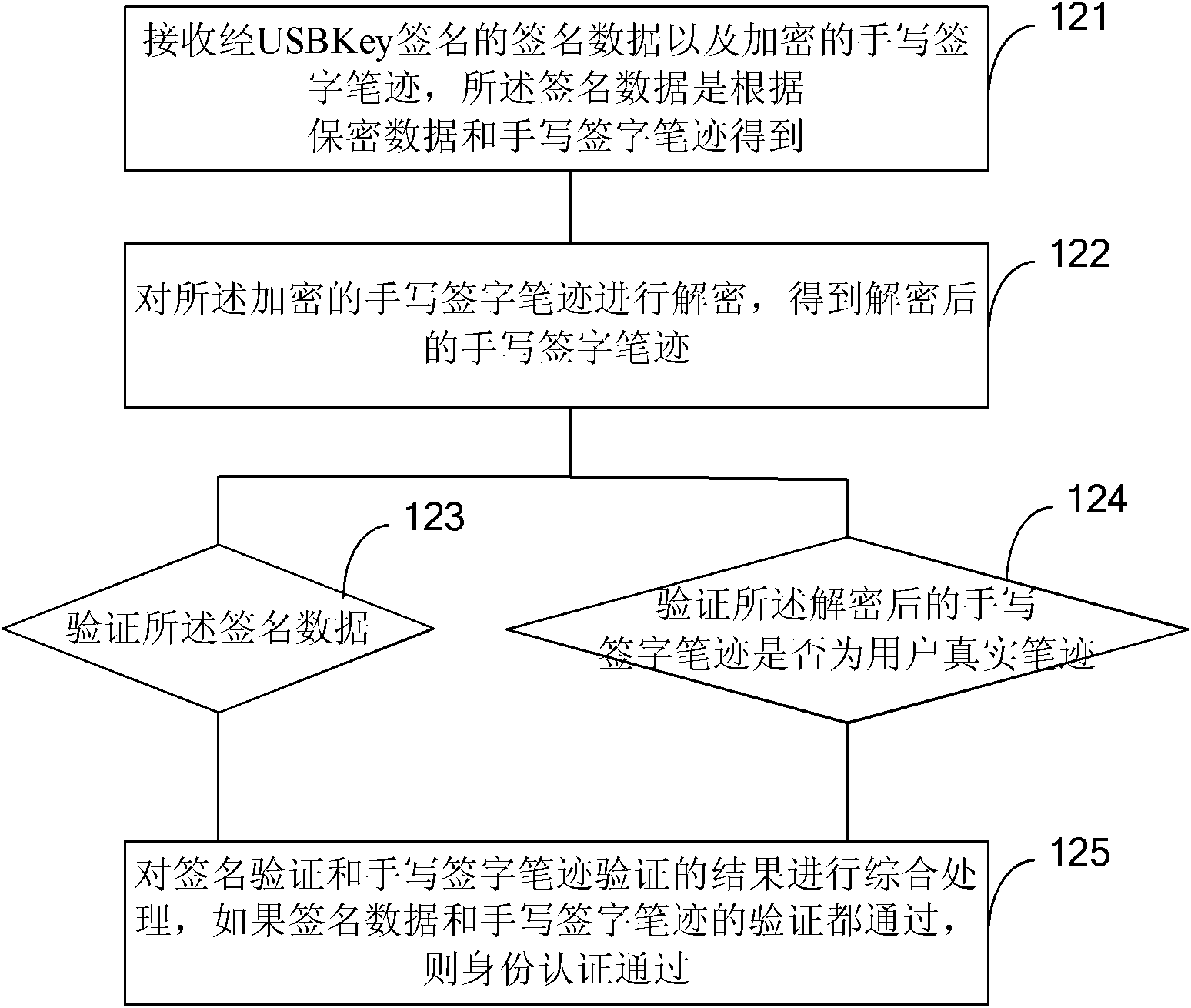
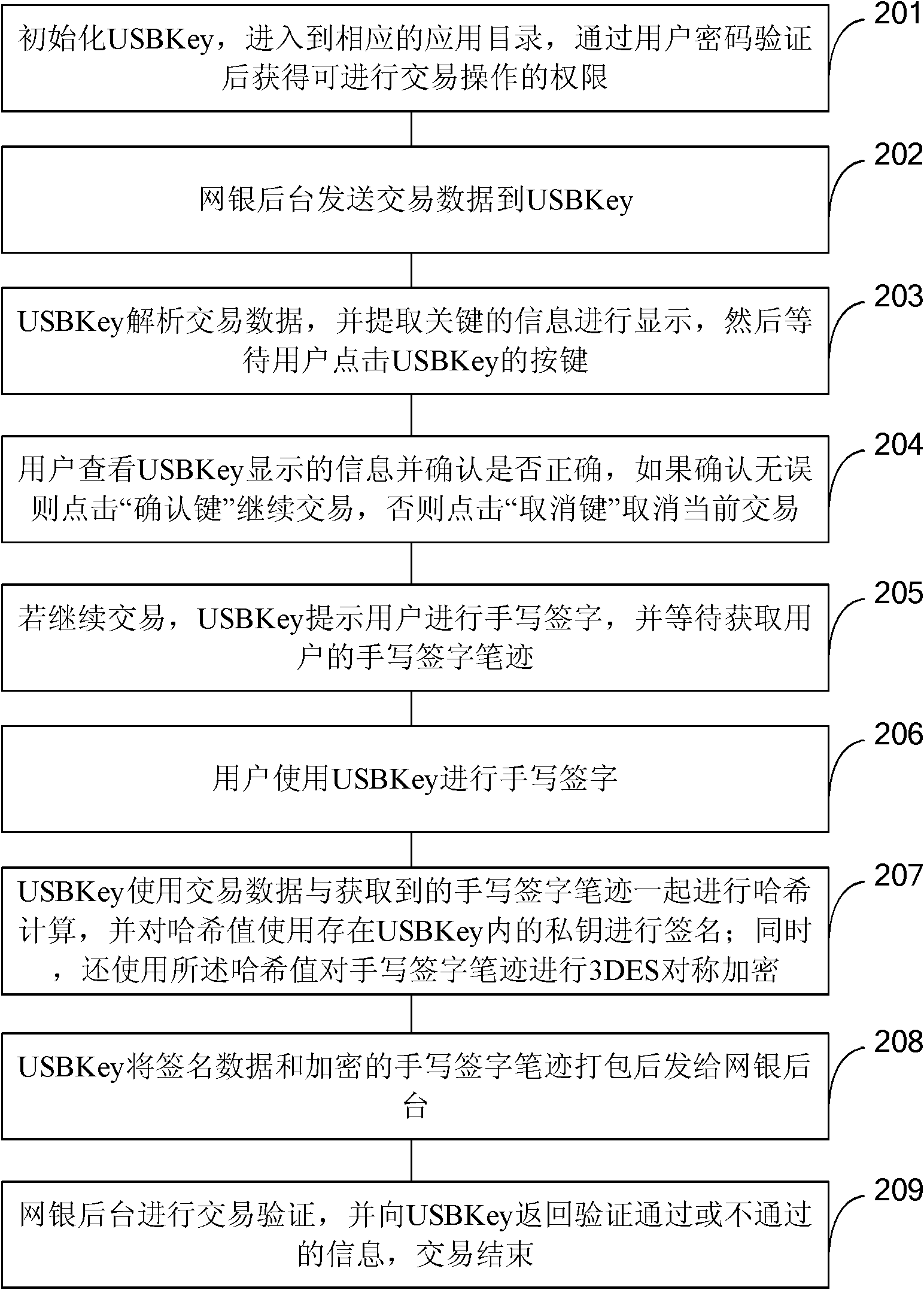
The invention provides an identity authentication method, identity authentication equipment, a server and an identity authentication-based encryption method and aims to solve the counterfeiting and repudiation prevention problems of identity authentication. The method comprises the following steps of: combining a written signature with a digital signature; acquiring the written signature handwriting of a user through the identity authentication equipment such as a universal serial bus (USB) key; combining the written signature handwriting with transaction data and performing digital signing; and transmitting signature data and the encrypted written signature handwriting to a verification party (such as an Internet bank background system). The signature data is verified by the verification party, so that the written signature handwriting and confidentiality data are not tampered in a transmission process; simultaneously, the truth of the written signature handwriting is verified by the verification party, so that the signature of the written signature handwriting by a user is ensured.
Owner:BEIJING WATCH DATA SYST
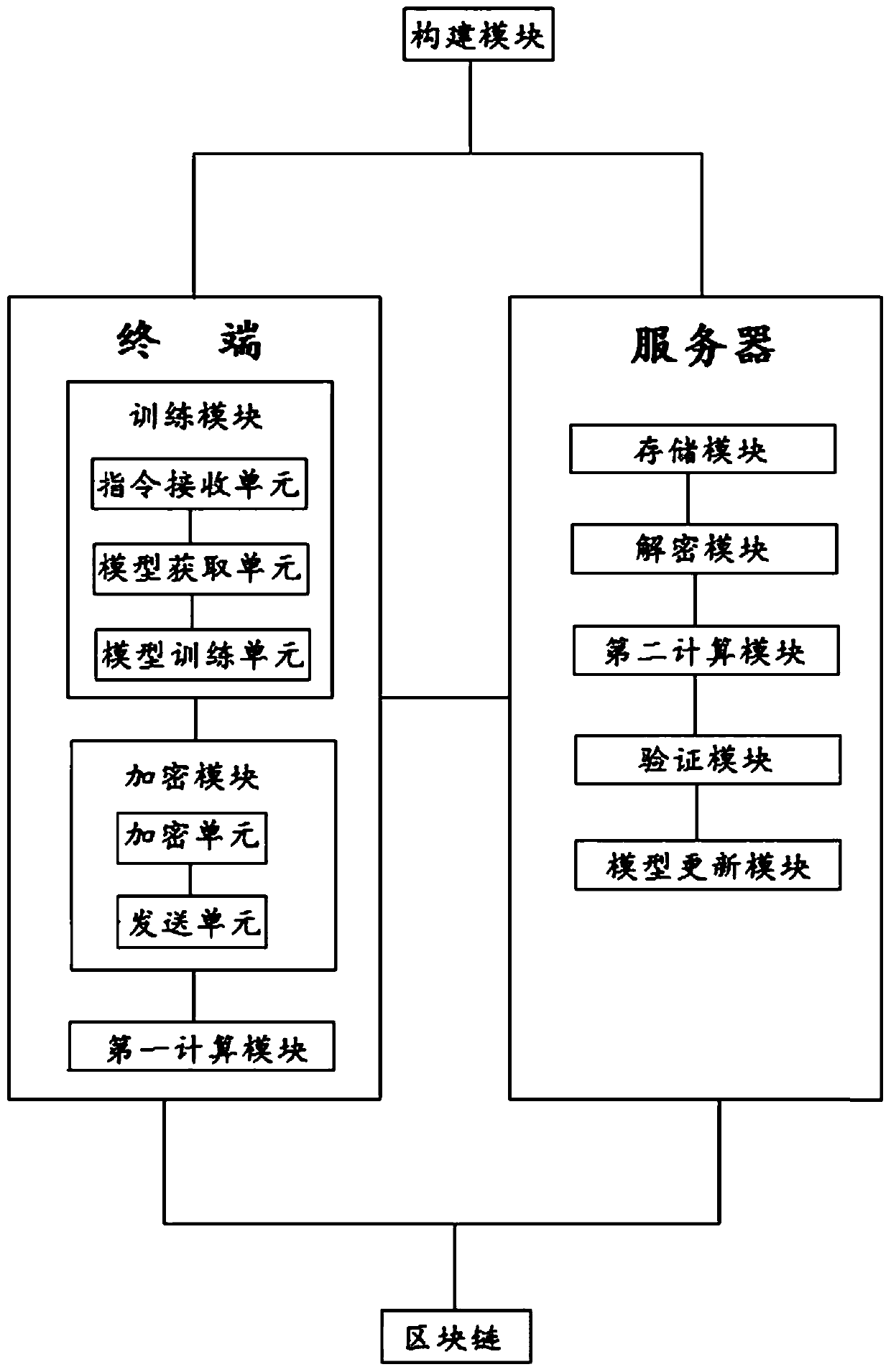
A joint learning method and system based on a public block chain and an encrypted neural network
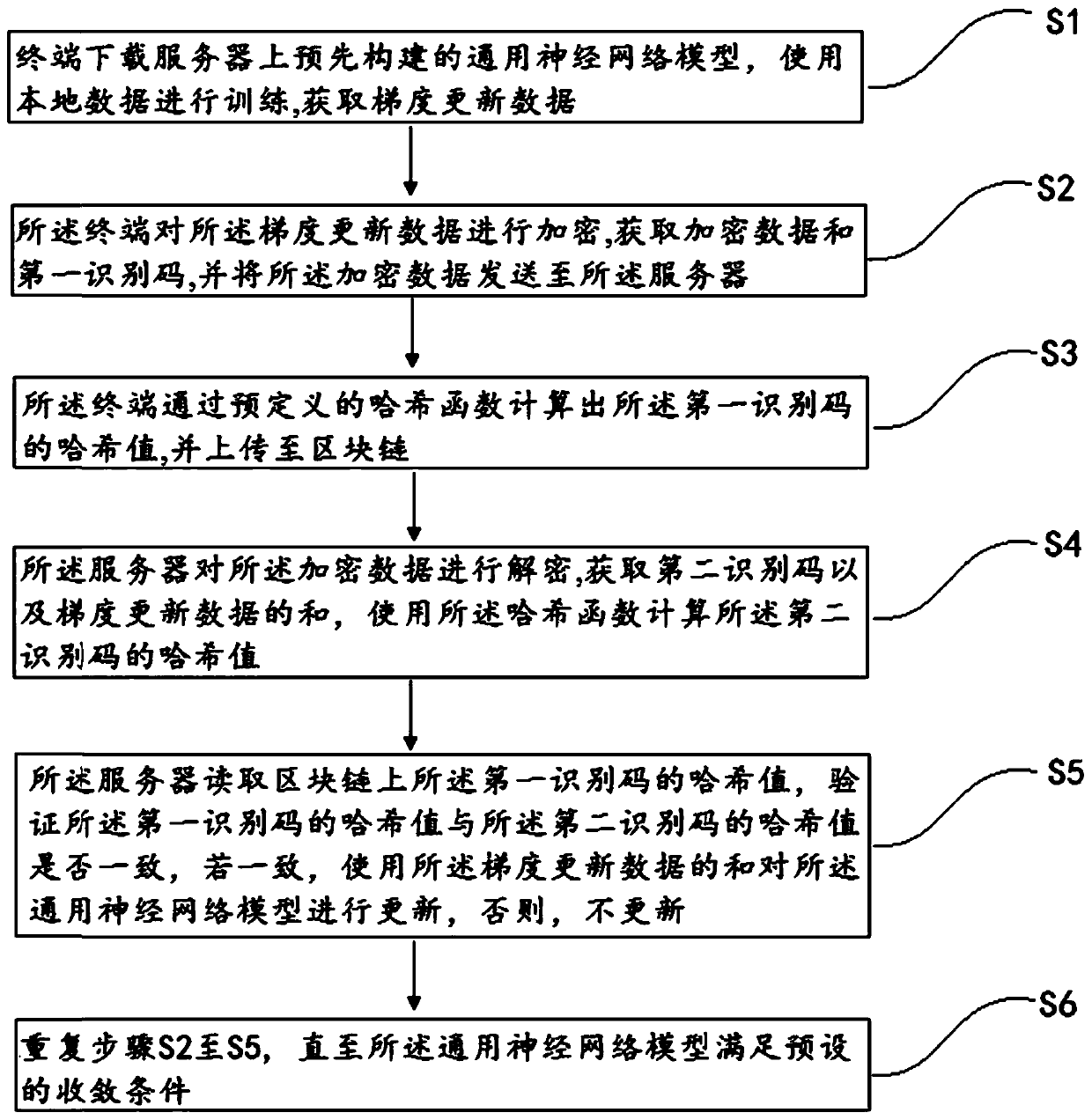
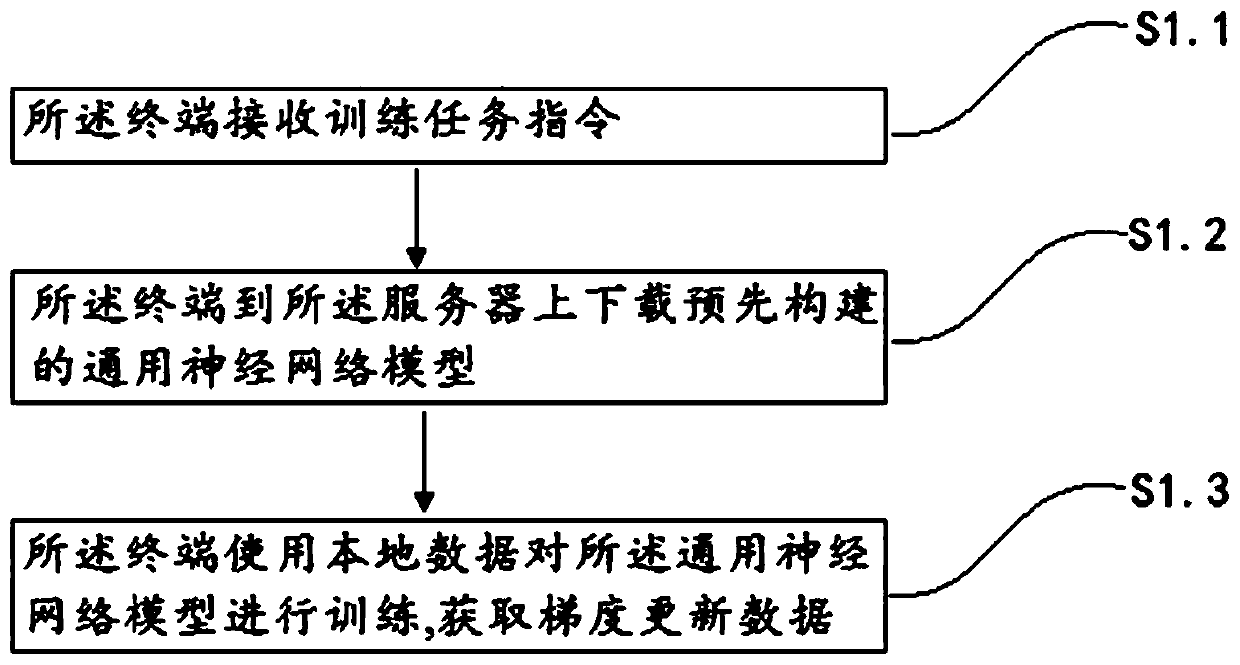
InactiveCN109698822APrevent leakageGradient update data protectionUser identity/authority verificationNeural architecturesComputer terminalNetwork model
The invention discloses a joint learning method and system based on a public block chain and an encrypted neural network. The method comprises the following steps of: enabling the terminal to downloada universal neural network model pre-constructed on the server; performing Training using local data, obtaining gradient updating data and encrypting the gradient updating data; acquiring encrypted data and a first identification code, sending the encrypted data to a server; calculating a hash value of the first identification code and uploading the hash value to the block chain; enabling a server to decrypte encrypted data, obtaining the sum of the second identification code and the gradient updating data, calculating the hash value of the second identification code, then verifying whether the hash value of the first identification code is consistent with the hash value of the second identification code or not, if yes, updating the universal neural network model by using the sum of the gradient updating data, otherwise, not updating, and repeating the above steps until the model meets a preset convergence condition. In the process of completing deep network training, user informationcan be prevented from being leaked, and it is guaranteed that transmission data are not leaked or tampered.
Owner:ZHONGAN INFORMATION TECH SERVICES CO LTD
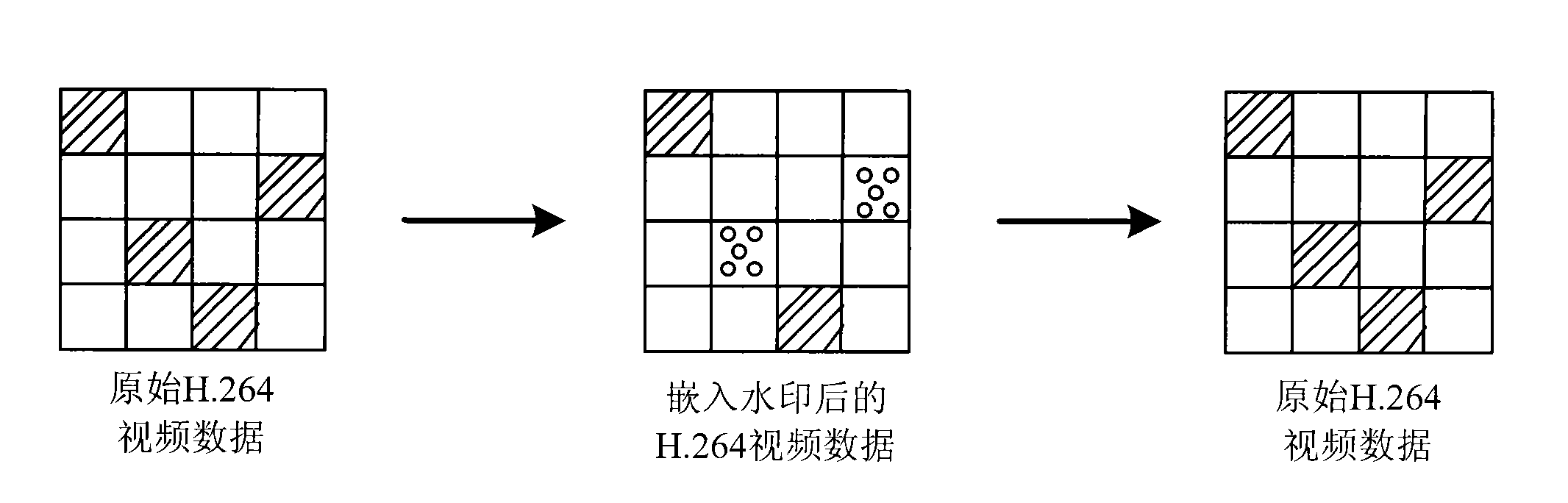
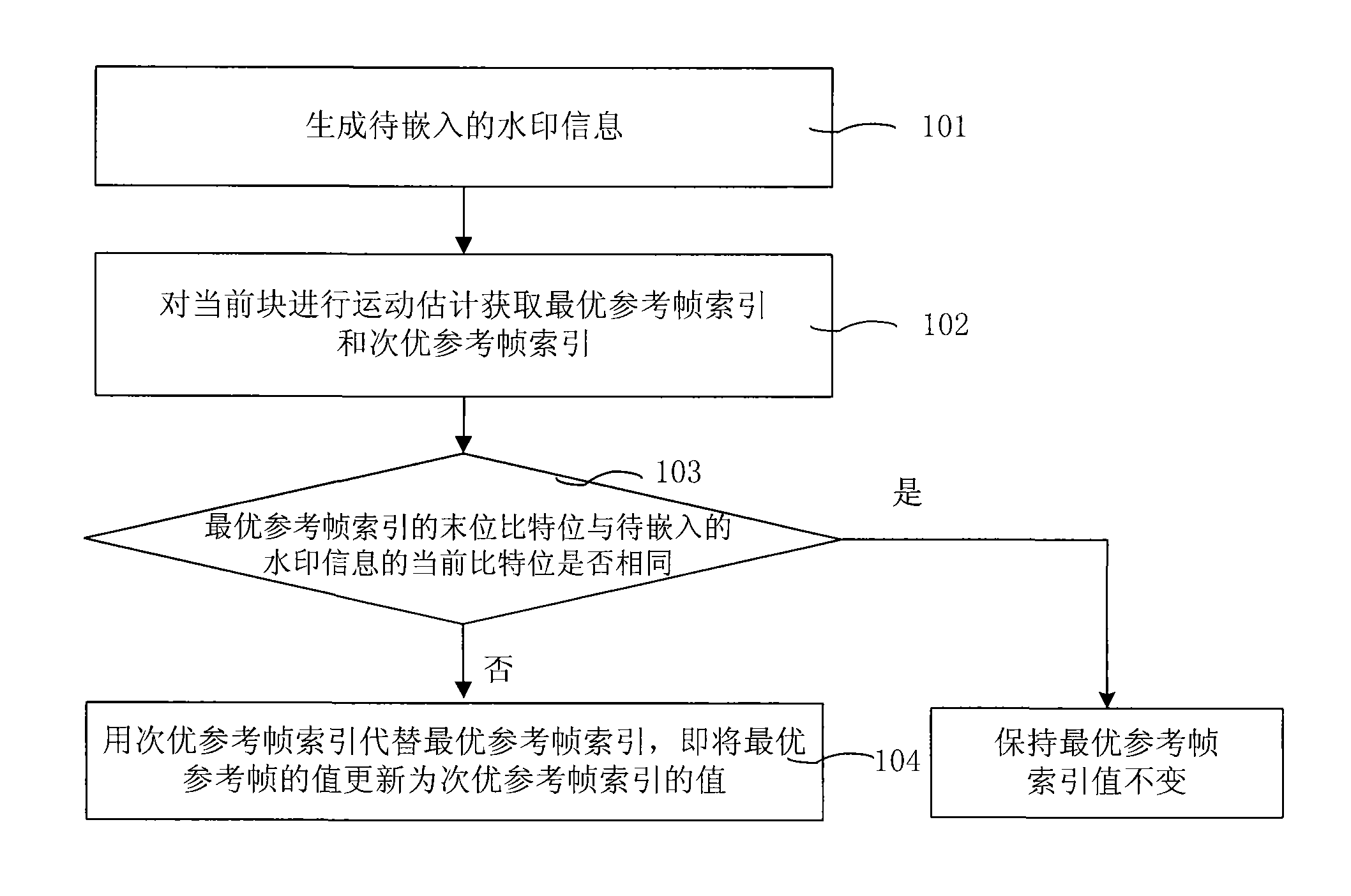
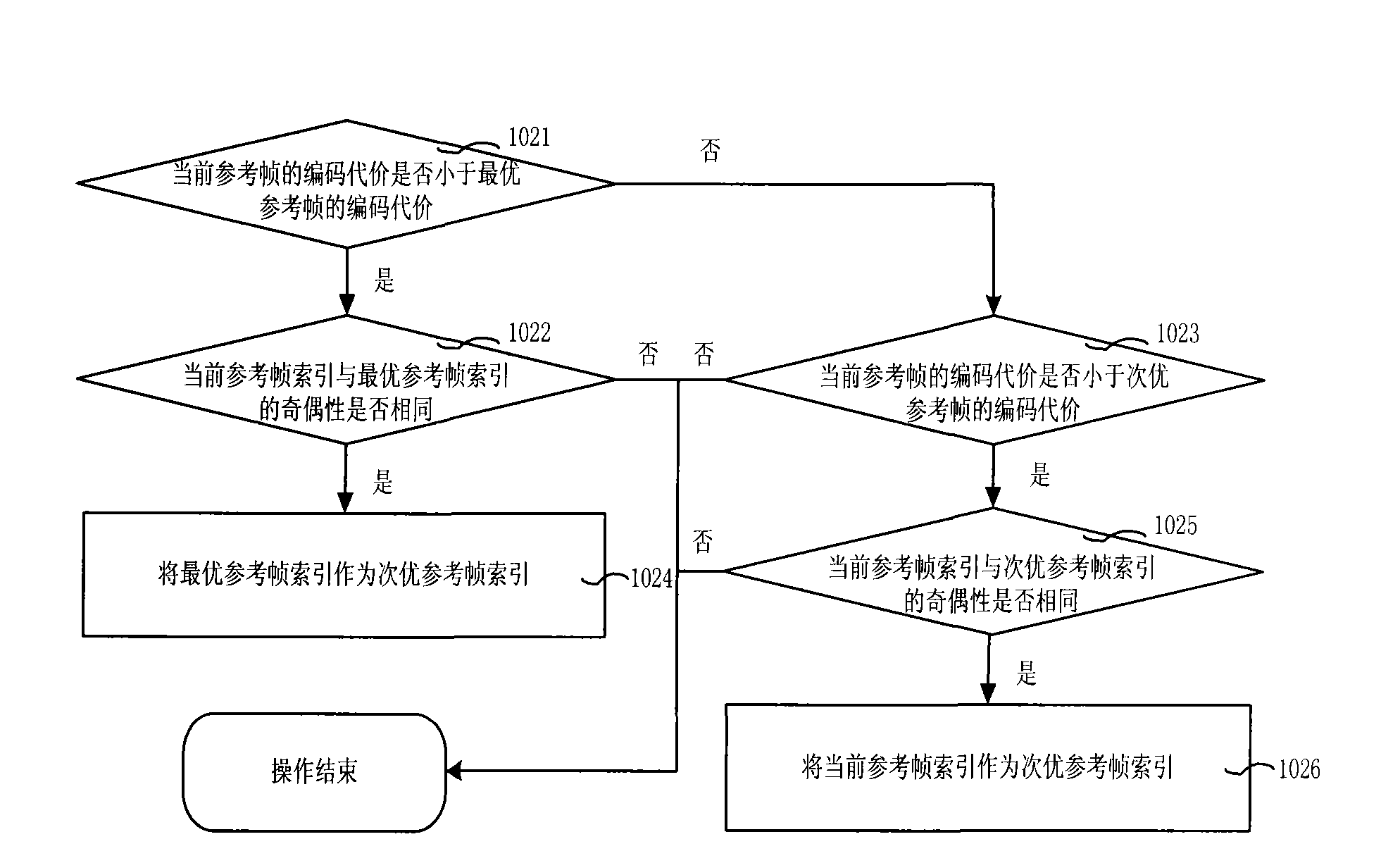
Method and device for embedding watermarking information and method and device for authenticating watermarking information
InactiveCN101527830ANo tamperingValid certificationPulse modulation television signal transmissionImage data processing detailsVideo qualityComputer science
The embodiment of the invention relates to a method and a device for embedding watermarking information and a method and a device for authenticating the watermarking information. The method for embedding the watermarking information comprises the following steps: generating watermarking information to be embedded; acquiring a reference frame index of a current macro block in video data; and embedding the watermarking information into the reference frame index. The method and the device for embedding the watermarking information and the method and the device for authenticating the watermarking information can better utilize the watermarking information to protect and authenticate video content, are easy to realize, and have little influence on video quality.
Owner:HUAWEI TECH CO LTD +1
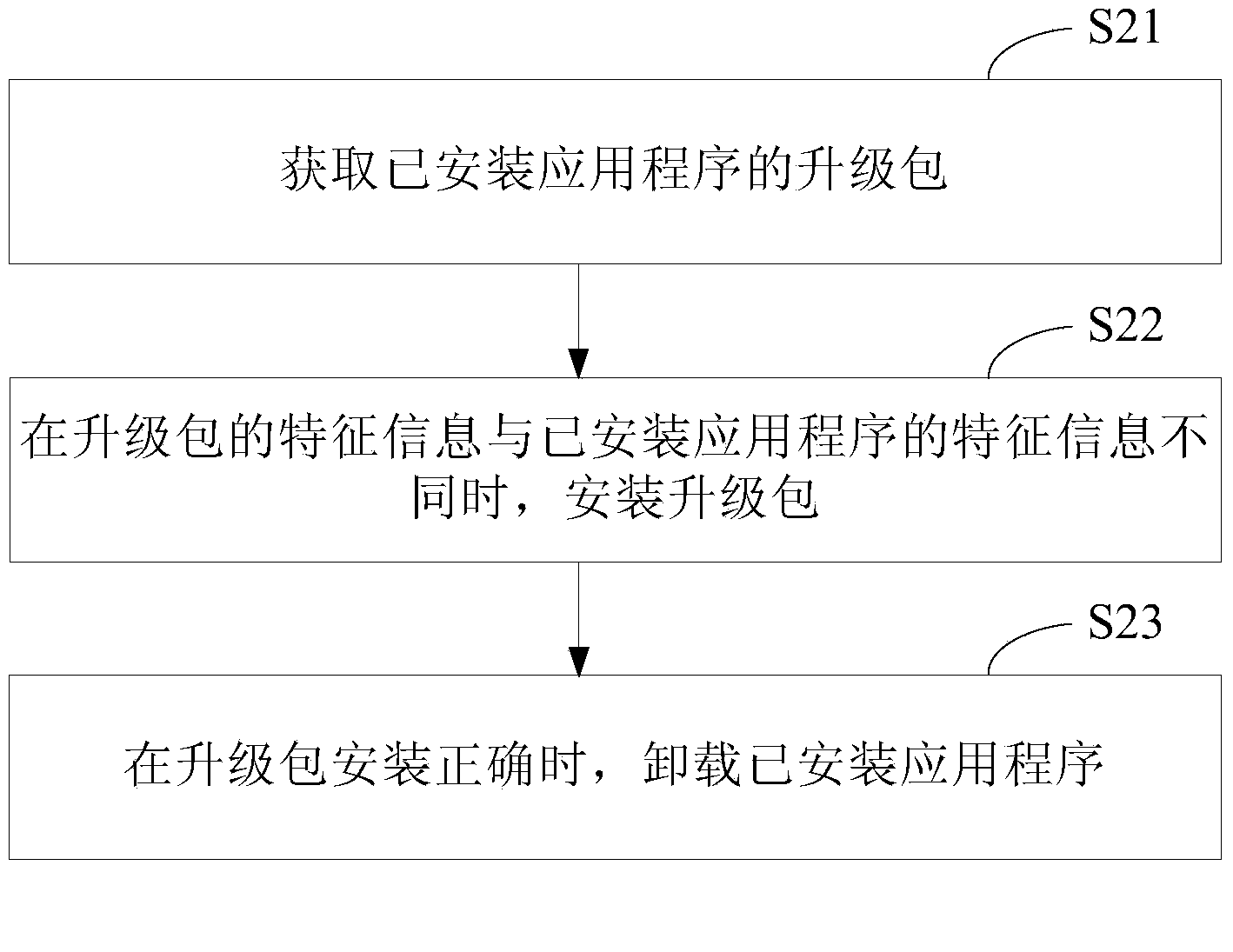
Root privilege based procedure upgrading method and device
ActiveCN104391729ANo tamperingAvoid churnPlatform integrity maintainanceProgram loading/initiatingApplication softwareUpgrade
The invention provides a Root privilege based procedure upgrading method which comprises steps as follows: an upgrade package of an installed application is acquired; the upgrade package is installed when characteristic information of the upgrade package is different from characteristic information of the installed application; and the installed application is uninstalled when the upgrade package is installed correctly. The invention further provides a Root privilege based procedure upgrading device. With adoption of the scheme, when Root privilege is provided, the application can be subjected to package name and / or signature upgrading, and loss of users is avoided.
Owner:BEIJING QIHOO TECH CO LTD
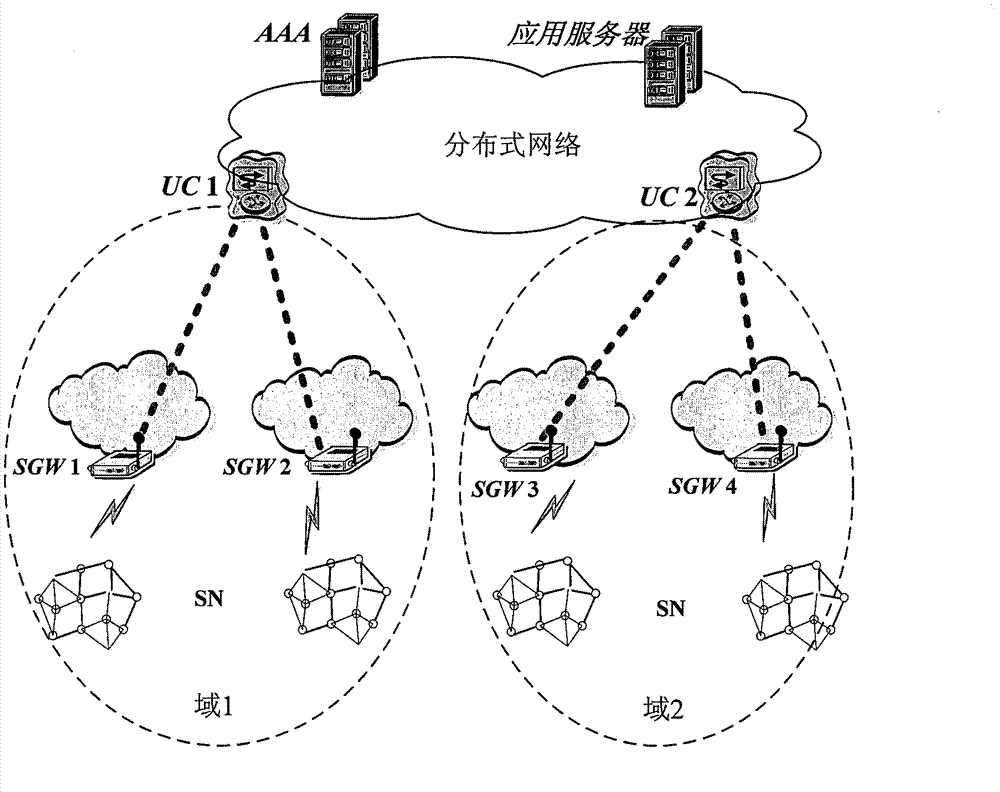
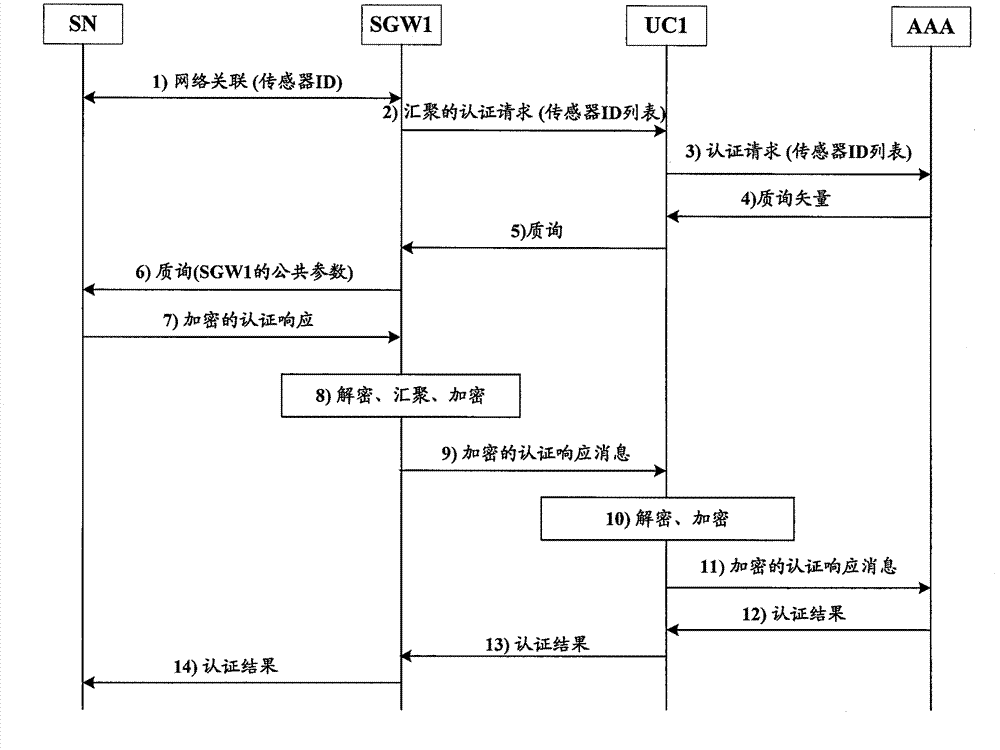
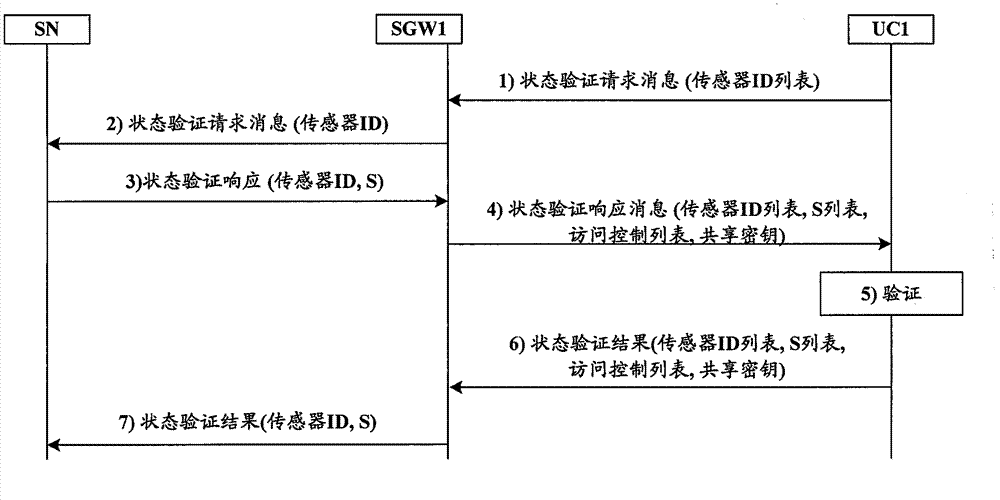
Methods for SN (sensor node) equipment authentication and state authentication, as well as security protocol method
ActiveCN103249043ANo tamperingEnsure safetyNetwork topologiesWireless network protocolsCryptographic protocolSensor node
The invention provides a security protocol method in a sensor network. A plurality of SNs in the sensor network are connected to sensor network gate ways SGWs, at least on gate way is connected to a controller UC which is connected to an authentication server AAA. The methods comprise the steps as follows: in an SN equipment authentication process, the gate ways collect requests sent by the plurality of SNs respectively and send the requests to the controller; and after the SN equipment authentication, the controller initiates a state verification process to verify the states of each SN and the sensor network. The invention achieves the SN equipment authentication and the state authentication of the SNs and the sensor network, and provides the complete security protocol.
Owner:ALCATEL LUCENT SHANGHAI BELL CO LTD
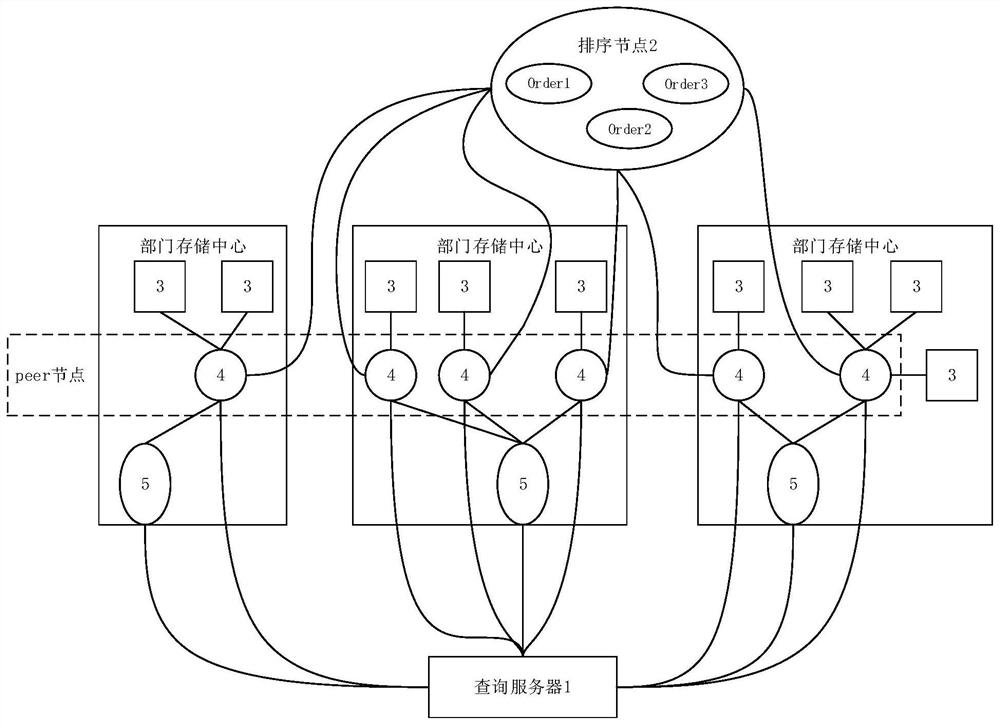
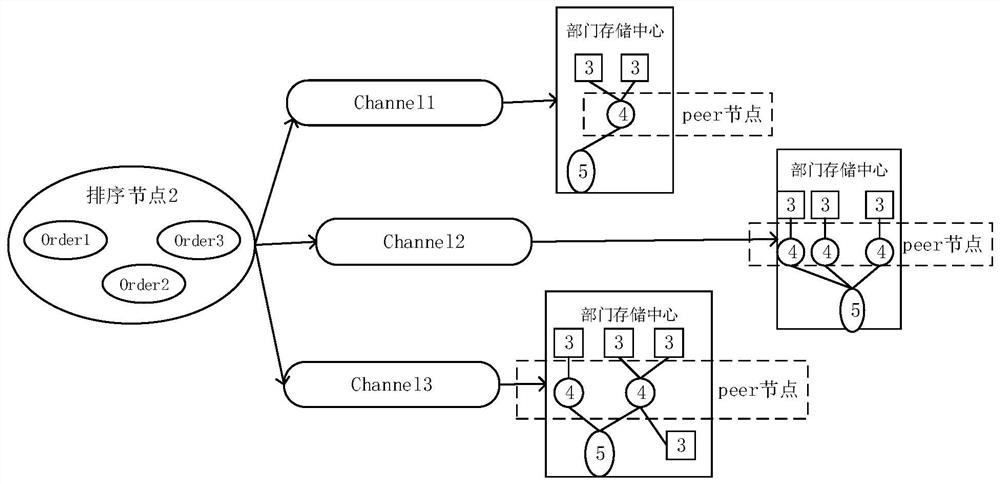
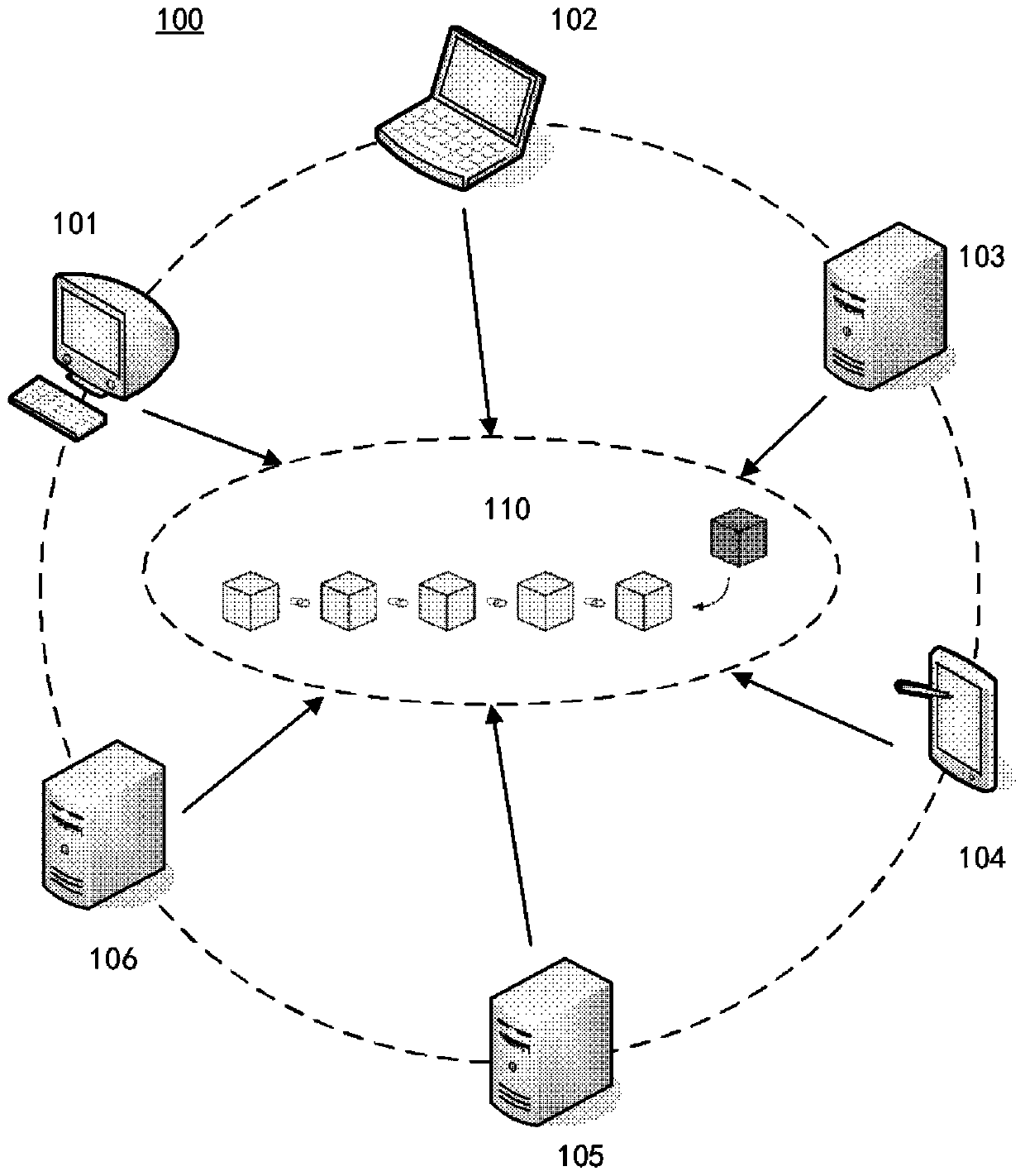
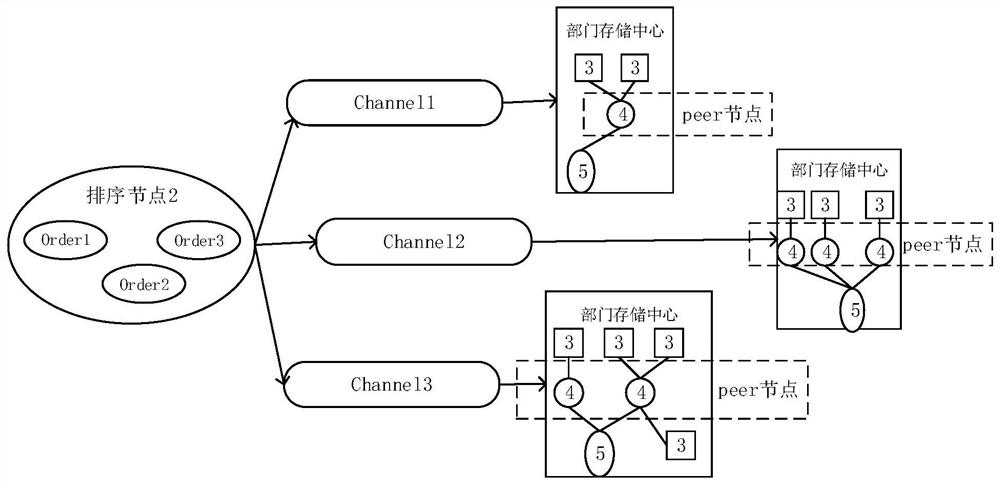
Cross-department data sharing system and method based on block chain technology
ActiveCN112671840ANo tamperingLimit tamperingFinanceDigital data protectionInformation transmissionData acquisition
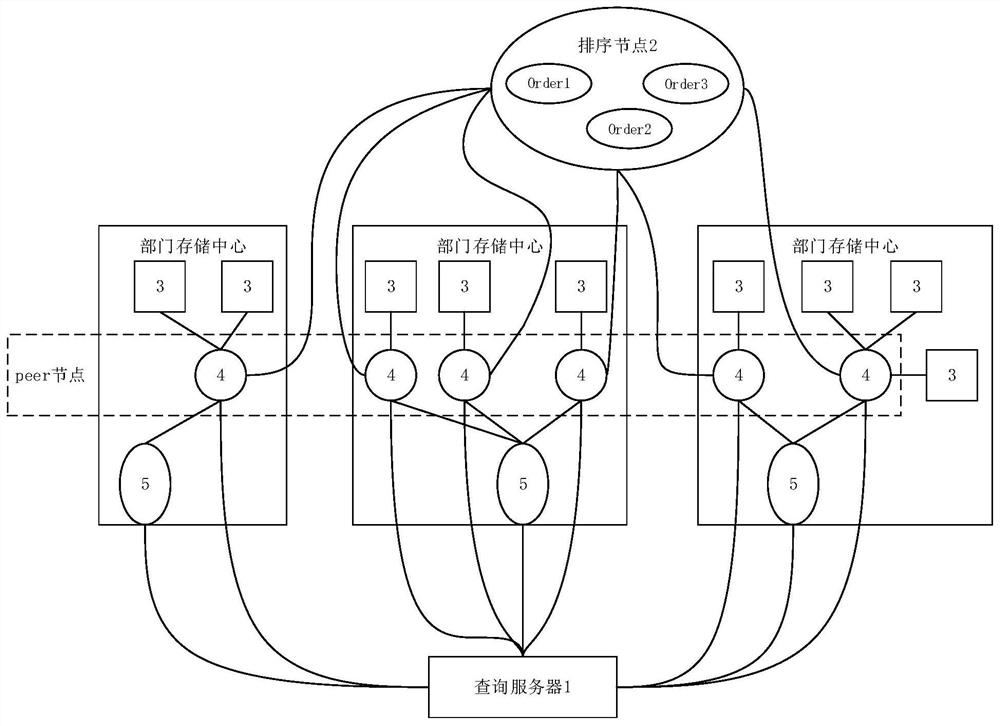
The invention relates to a cross-department data sharing system and method based on a block chain technology, the system comprises a query server, a sorting node and a plurality of department storage centers, in each department storage center, a data acquisition module is connected with a data processing server, the data processing server is connected with a distributed storage system and the query server, and the distributed storage system is connected with the query server; and the data processing server is used as a peer node of the block chain, and the sorting node performs information transmission with each department storage center through a message channel. Compared with the prior art, through the blockchain technology, the structured data is directly uploaded and stored, it can be guaranteed that the data cannot be tampered, the original hash value of the unstructured data is uploaded and stored, hash value verification is carried out during subsequent data query, tracing can be carried out, the behavior of tampering the data is further limited, and the security and credibility of the data sharing system are improved.
Owner:TONGJI UNIV
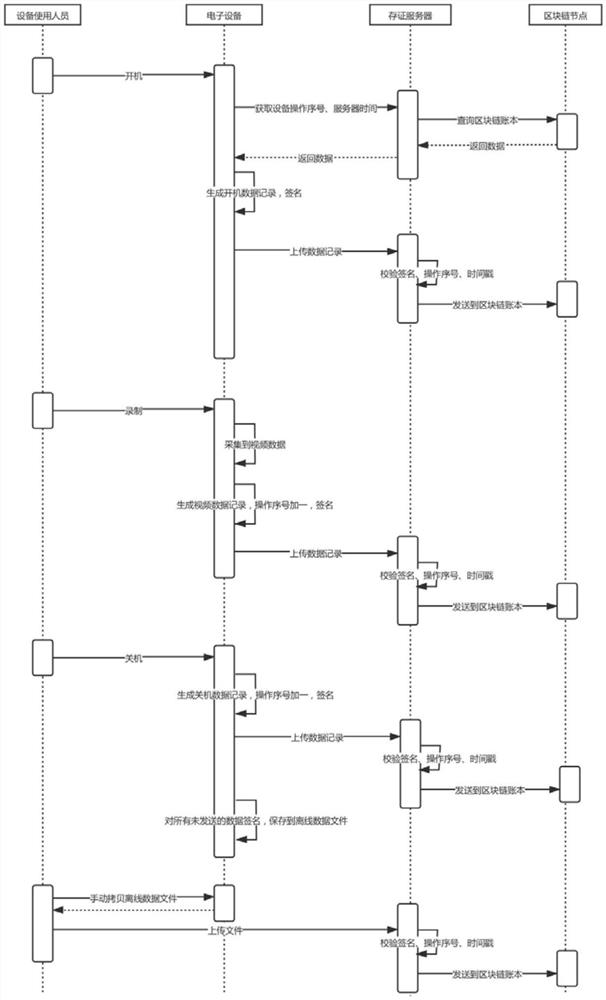
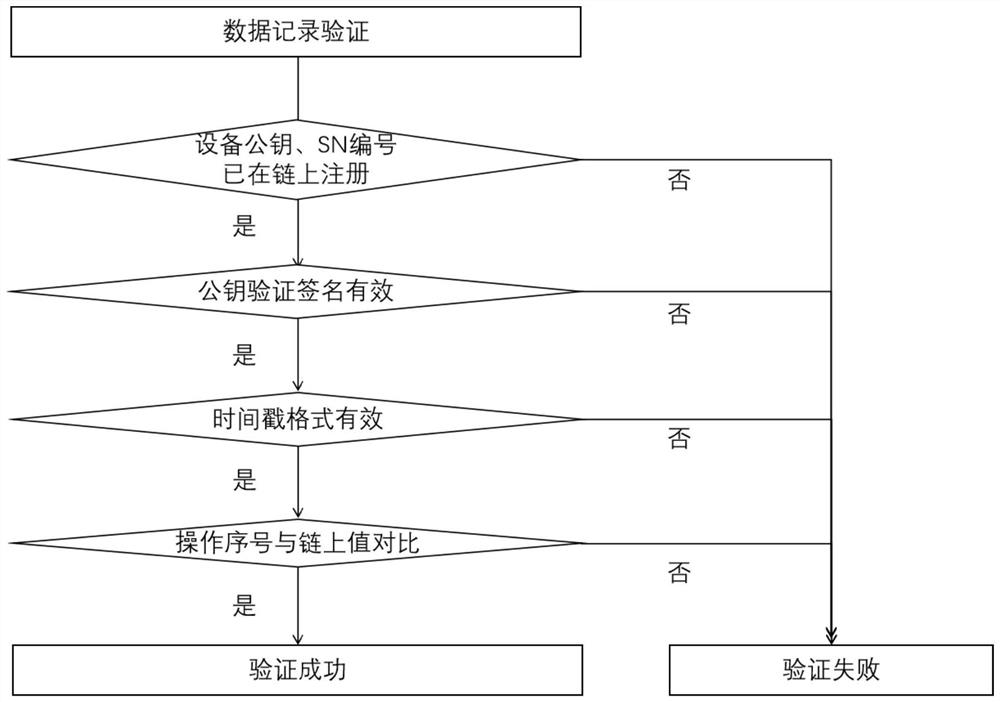
Electronic equipment data credible acquisition and evidence storage method based on blockchain technology
The invention discloses an electronic equipment data credible acquisition and evidence storage method based on the blockchain technology, and the method comprises the steps: generating a unique public and private key pair for electronic equipment according to an equipment manufacturer name, an equipment model and an equipment SN number; through a private key signature and public key signature verification mode, guaranteeing that the server can confirm the identity of the device when the data collected by the device is sent to the server in real time, and guaranteeing that the data is not tampered. A strict progressive increase operation sequence number is maintained for each device, and a timestamp synchronization mode is adopted, so that the data uploading sequence of the devices is consistent with the collection sequence. And the data uploaded by the equipment is not lost or deleted in an offline period in a mode of maintaining a strict progressive increase operation sequence number for each piece of equipment. And the server stores the public key of the electronic equipment and is bound with the information of the electronic equipment. The whole process of data from collection to storage is transparent, credible and non-tampering through the block chain and encryption technology.
Owner:HANGZHOU VASTCHAIN TECH CO LTD
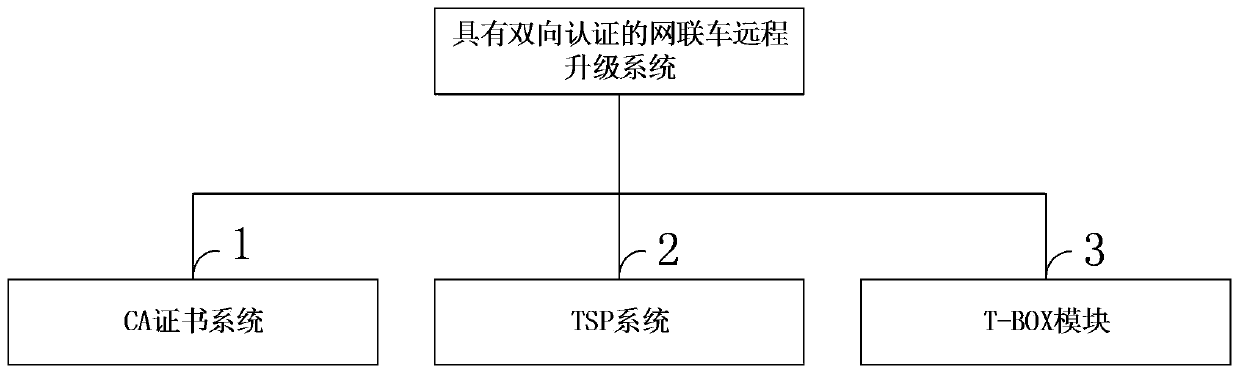
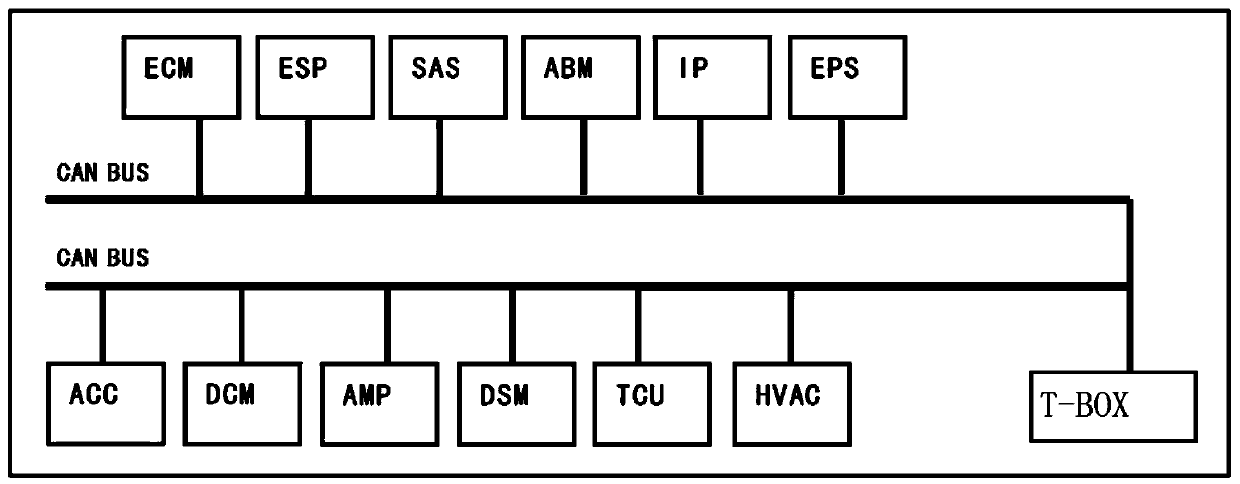
Networked vehicle remote upgrading system and method with anti-attack bidirectional authentication
ActiveCN110891257AAchieving Reliability CertificationPrevent counterfeitingEncryption apparatus with shift registers/memoriesParticular environment based servicesData packSecurity rule
The invention belongs to the technical field of systematic safety of Internet of Vehicles, and discloses a networked vehicle remote upgrading system and method with anti-attack bidirectional authentication, a CA certificate system is used for performing identity authentication on a vehicle through a digital certificate in an Internet of Vehicles network, and supporting bidirectional authenticationbetween a TSP and a networked vehicle. A TSP system is used for supporting remote upgrading of vehicles. A T-BOX system is used for detecting the IP of the TSP during upgrading; wherein the IP is notthe IP of the TSP, and the data packet of the IP is discarded; and in a non-upgrading state, external communication is compared according to rules in the security rule base of the firewall, and rulesof the rule base are updated through TSP real-time operation. According to the invention, the reliability authentication of the bidirectional identity between the networked vehicle T-BOX and the vehicle remote service provider TSP is realized, and the identity counterfeiting is prevented; reliability of data transmission between the T-BOX and the TSP is achieved, and illegal stealing and tampering of automobile upgrading software in the transmission process are prevented.
Owner:CHENGDU UNIV OF INFORMATION TECH
Contract executing method and system based on organism information
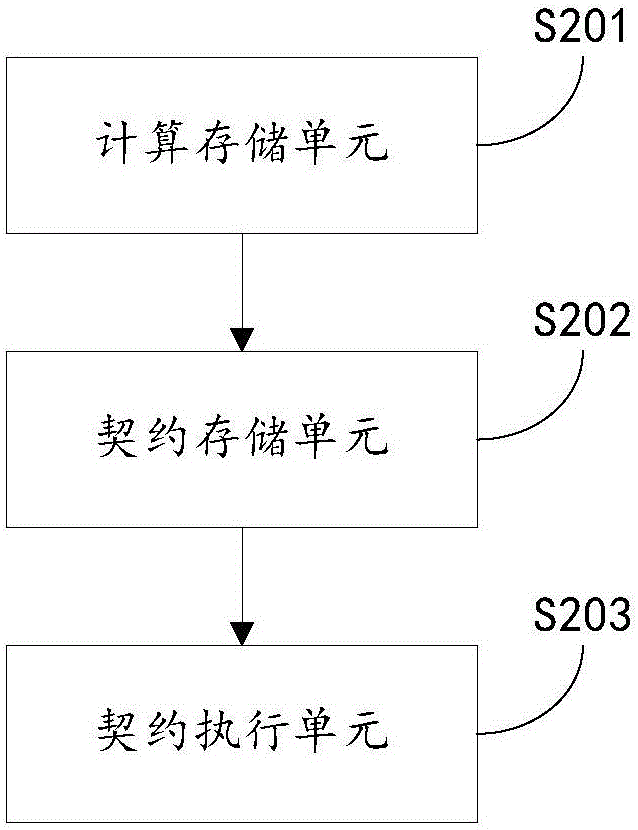
ActiveCN106096443AEnsure safetyPrevent leakageDigital data protectionDigital data authenticationBiological bodyComputer hardware
The invention discloses a contract executing method and system based on organism information. The method includes the steps of calculating collected biological information of an organism and a preset security code through a preset encrypting algorithm, obtaining a preset security identification code corresponding to the organism, and storing the preset security identification code into an identification code database; storing contract content and contract trigger conditions related to the preset security identification code in the contract database, wherein the contract content includes a plurality of contract terms; receiving monitoring information sent by a monitor, and executing the contract terms corresponding to the contract trigger conditions when it is judged that the monitoring information meets the contract trigger conditions. By means of the method and system, whether the preset contract trigger conditions are met or not can be automatically judged according to the monitoring information, if yes, the contract terms corresponding to the contract trigger conditions are automatically executed, the fair execution of a contract is ensured, the contract content can not be revealed, and security and convenience are achieved.
Owner:杨鹏
Internet data verification method and system
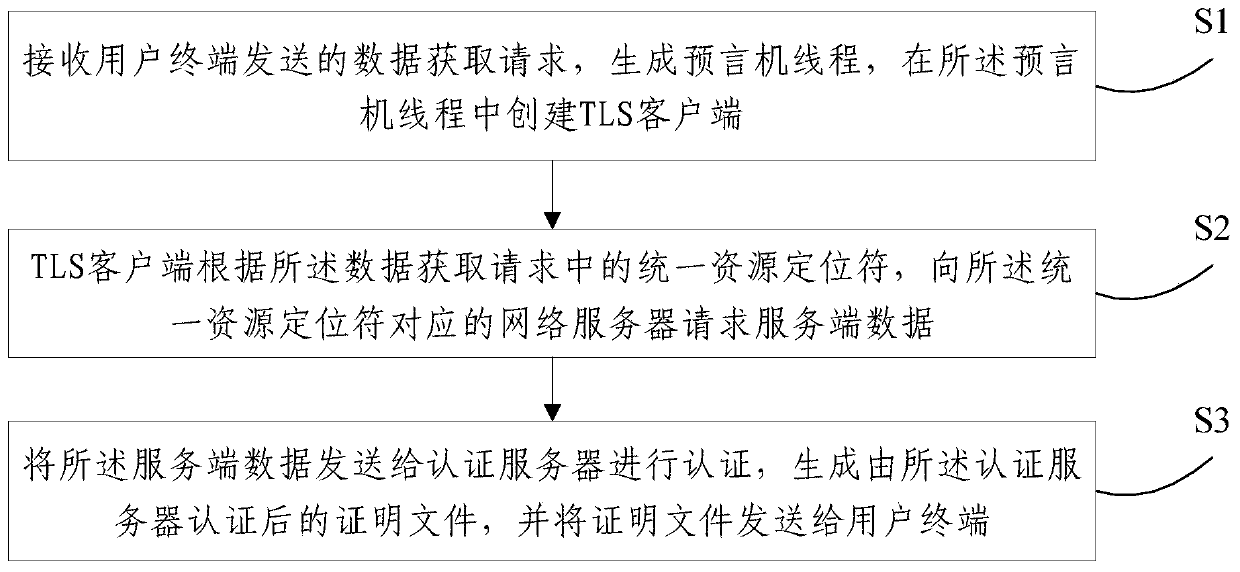
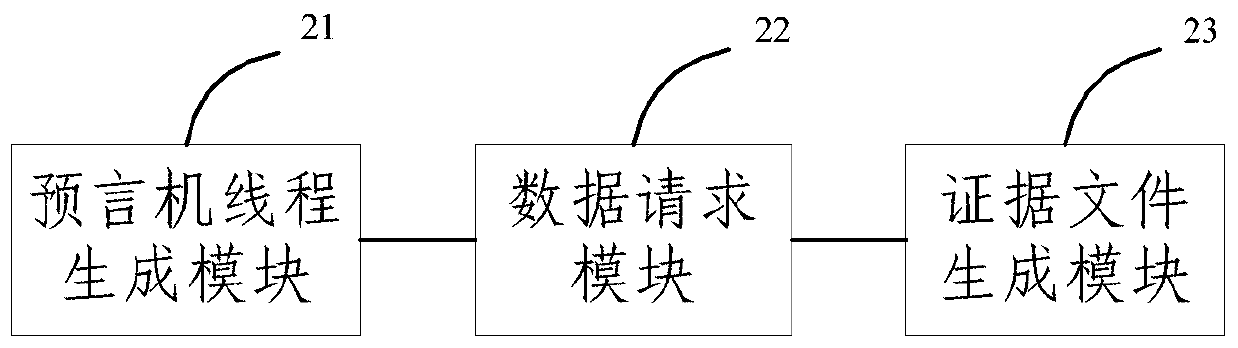
ActiveCN109995776ASafe and reliable accessImplement the validatorTransmissionData verificationClient-side
The embodiment of the invention provides an Internet data verification method and system, and the method comprises the steps: receiving a data obtaining request sent by a user terminal, generating a predictor thread, and creating a TLS client in the predictor thread; the TLS client requests server side data from a network server corresponding to a uniform resource locator in the data acquisition request according to the uniform resource locator in the data acquisition request; the server side data is sent to an authentication server for authentication, a proof file authenticated by the authentication server is generated, and the proof file is sent to a user terminal; wherein the TLS client operates in a flying place. The embodiment of the invention provides a method. The TLS client runs inthe trusted secure computing environment enclave, so that codes of the TLS client and the symmetric key in the obtained TLS connection can be ensured not to be tampered, the authenticity of data obtained by the TLS client from the Server is ensured, and the data can be provided for any third party to verify the reliability of the evidence file.
Owner:西安纸贵互联网科技有限公司
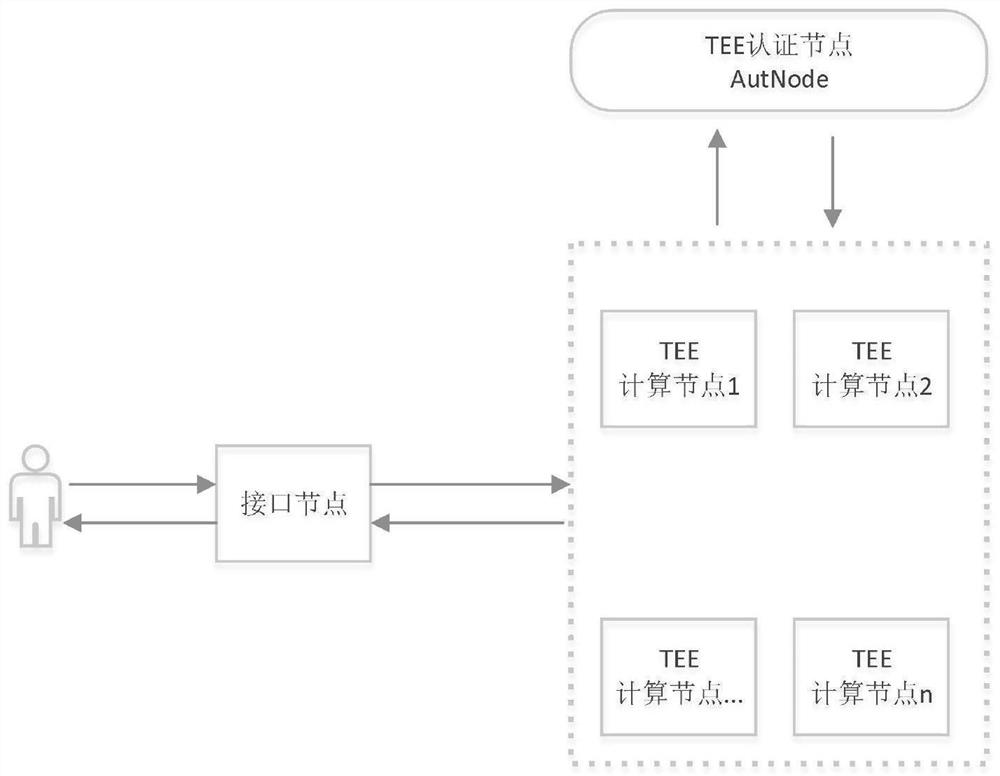
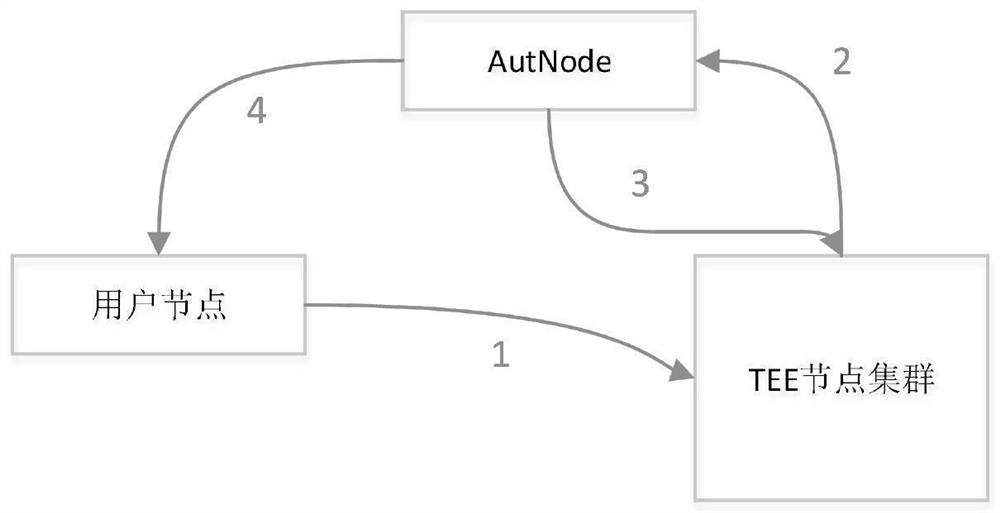
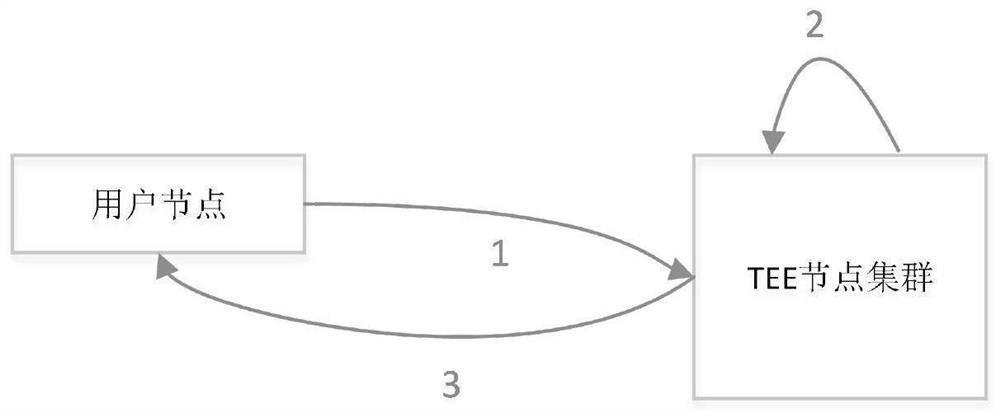
Multi-node authentication method for trusted execution environment
PendingCN113904806ARealize security protectionRealize privacy protectionUser identity/authority verificationResource poolResource Management System
The invention discloses a trusted execution environment (TEE) multi-node authentication method, which comprises the following steps of: assuming that a plurality of TEE computing nodes form a computing resource pool, and uniformly distributing computing resources by a computing resource management system; and setting a unified access and authentication node (AuthNode) for the the resource pool, wherein the node assists a user in completing the remote authentication process of all distributed TEE computing nodes. The method has the following advantages: 1, a user can authenticate the code security in the cloud computing environment, and realizes security protection on the computing process through the TEE; 2, the privacy protection of user data can be achieved, the user data are uploaded to the cloud environment in an encrypted state, and the data are only decrypted and used in the TEE; 3, the user can authenticate the correctness of the calculation result to ensure that the calculation result is not tampered; and 4, complete remote authentication is only carried out in a program deployment stage, the TEE authentication process is completed in the cloud environment, the user only needs to carry out simple local verification in the calculation process, and the execution efficiency is high.
Owner:TIANYI ELECTRONICS COMMERCE
Security processing method, device and processing chip, network equipment
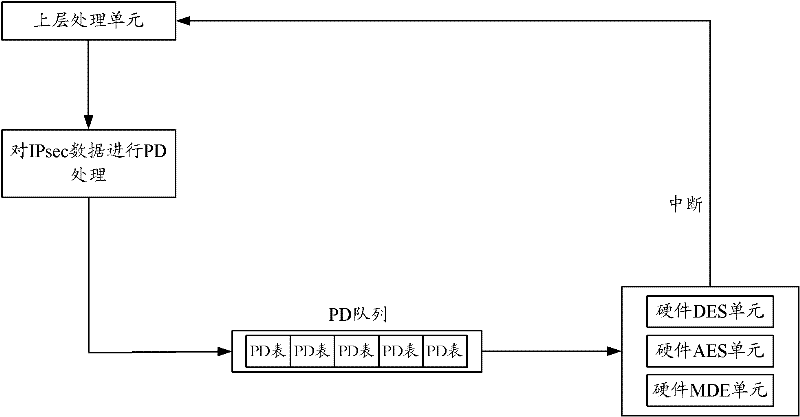
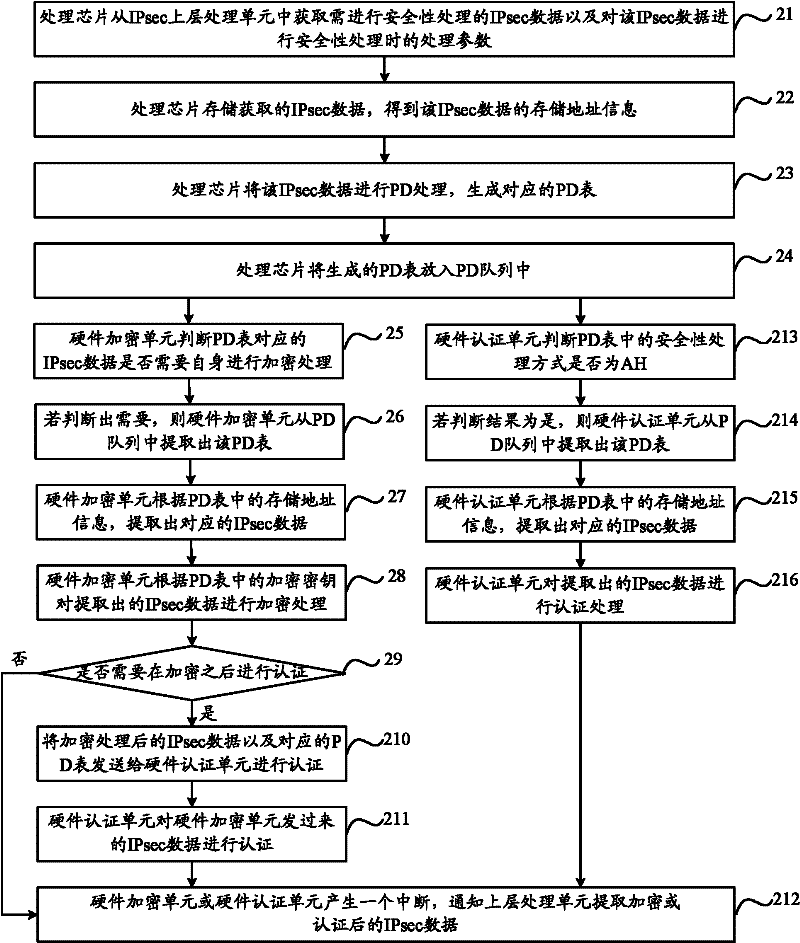
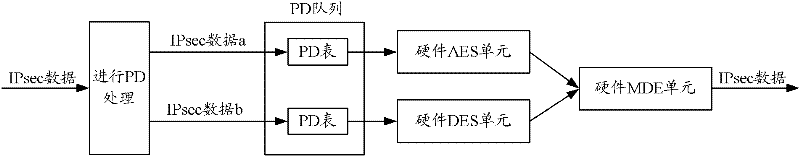
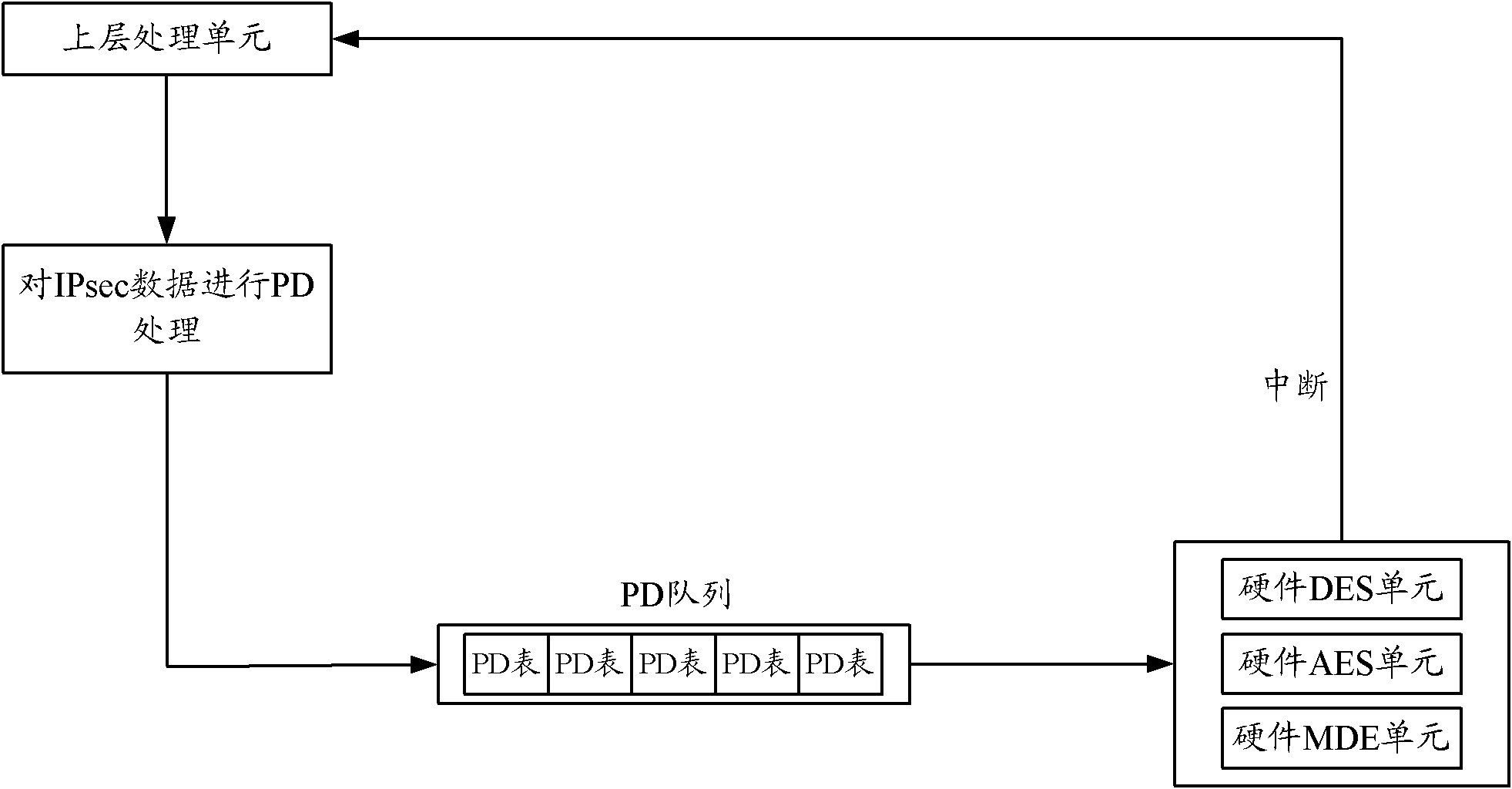
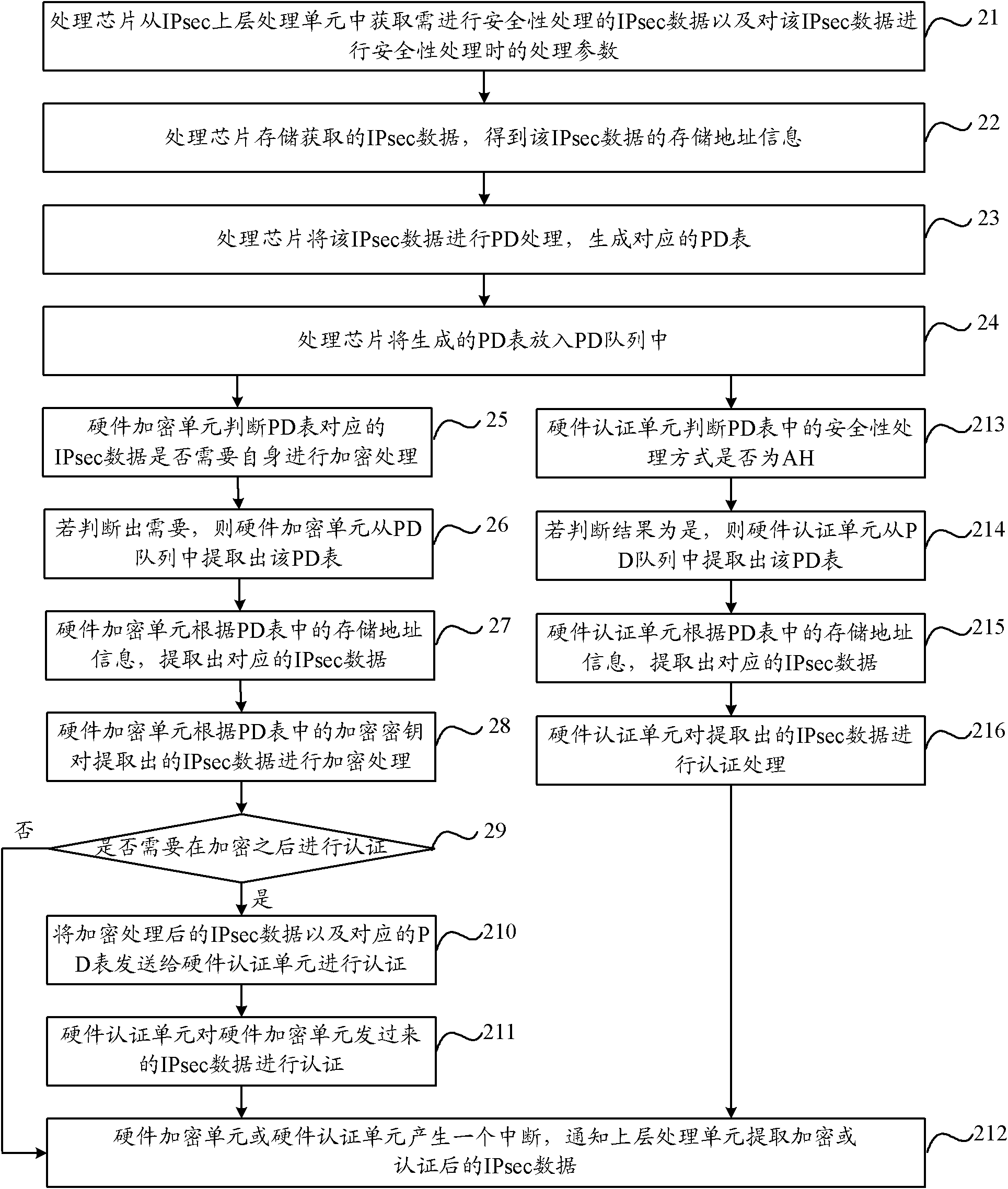
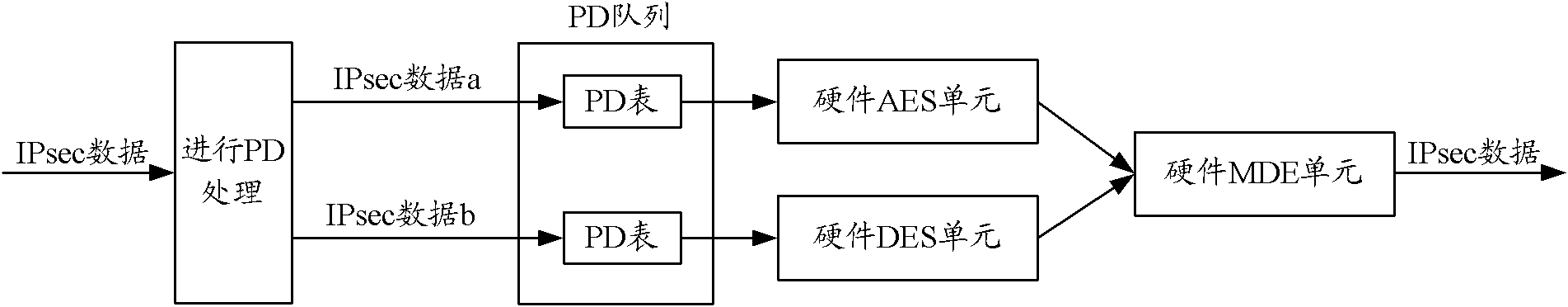
ActiveCN102263794AIntegrity guaranteedNo tamperingEncryption apparatus with shift registers/memoriesIPsecHardware authentication
The invention discloses a security processing method, a security processing device, a processing chip and network equipment. The method comprises the following steps of: obtaining a security processing way for Internet protocol security (IPsec) data requiring security processing; if authentication processing is determined to be required after encryption processing is performed on the IPsec data according to the security processing way, obtaining an encryption algorithm for the encryption processing of the IPsec data; determining an authentication processing way for the authentication processing of the IPsec data according to the obtained encryption algorithm, wherein the authentication processing way comprises a software authentication processing way and a hardware authentication processing way; performing hardware encryption processing on the IPsec data according to the obtained encryption algorithm; and performing the authentication processing on the hardware-encrypted IPsec data according to the determined authentication processing way. By the technical scheme provided by the invention, the problem of relatively lower processing efficiency in the authentication processing of the IPsec data in the prior art is solved.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
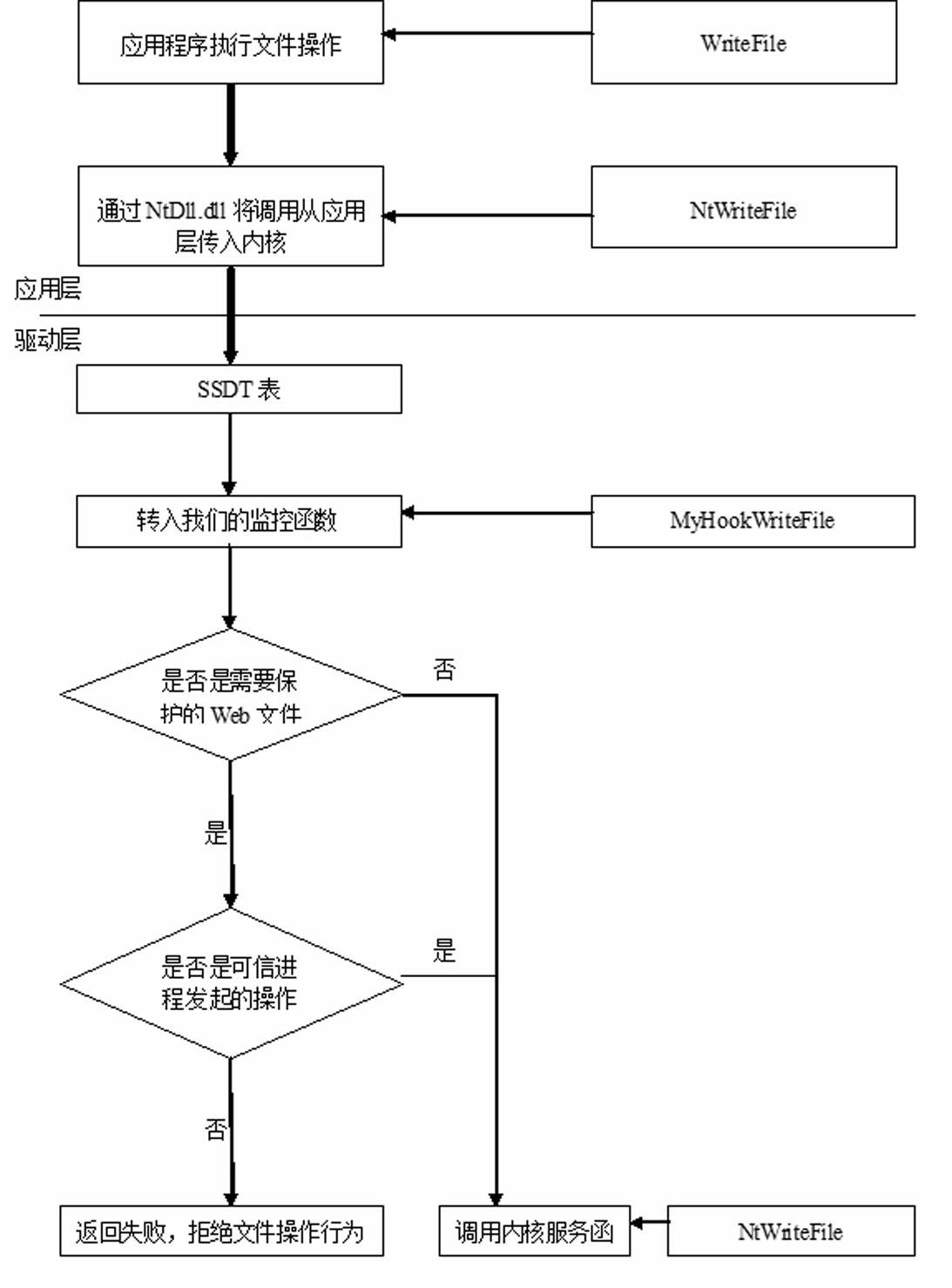
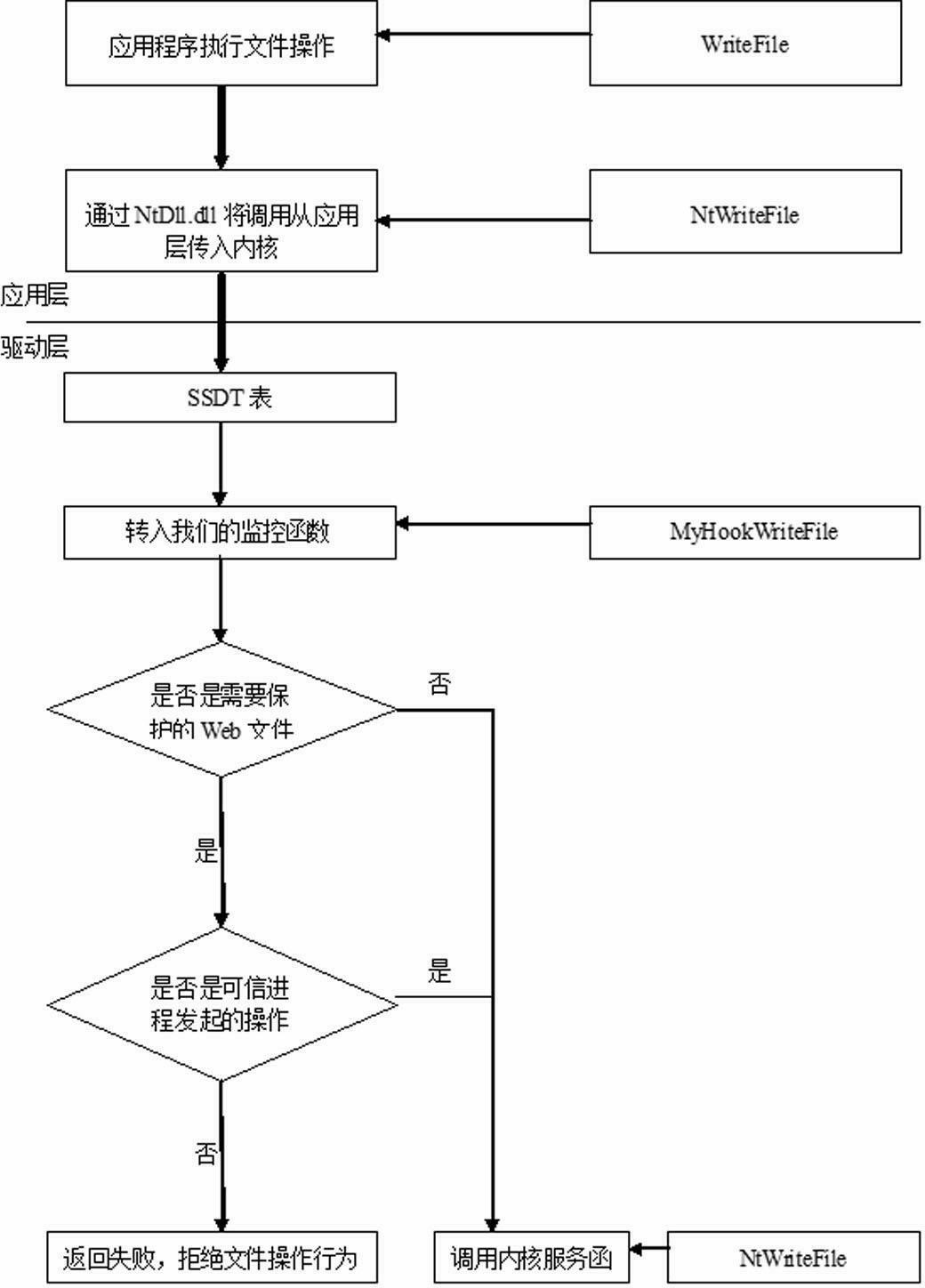
Webpage tamper proofing method realized by windows driver layer
InactiveCN102693383AReduce resource usageQuick responseHardware monitoringProgram/content distribution protectionTamper resistanceEvent trigger
Owner:西安交大捷普网络科技有限公司
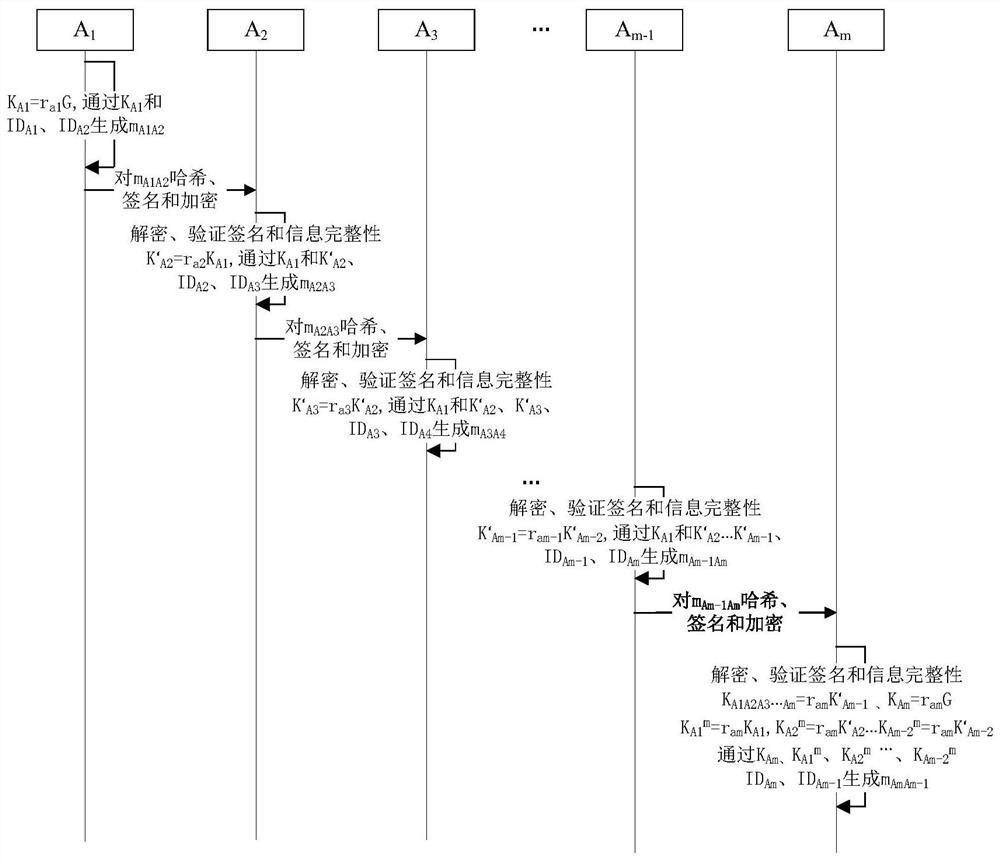
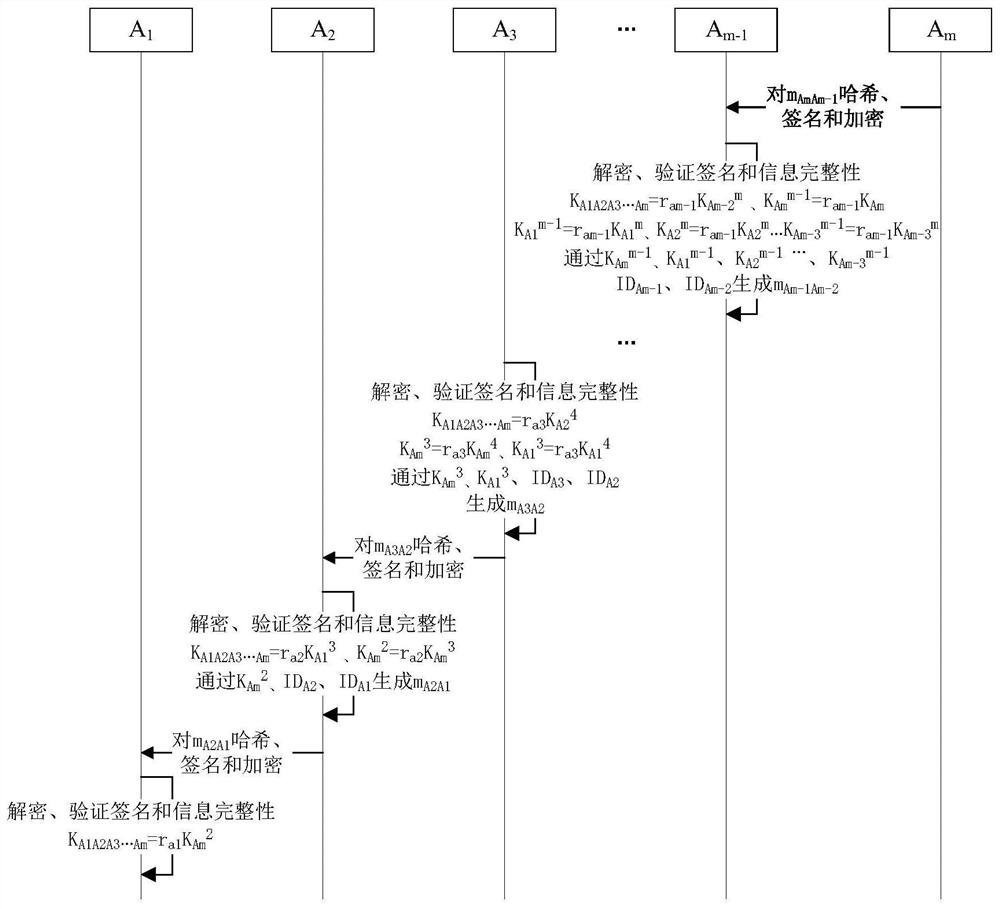
Method and system for realizing multi-party key agreement
ActiveCN112422276AEnsure security and confidentialityPrevent replay attacksKey distribution for secure communicationEncryption apparatus with shift registers/memoriesConfidentialityDiscrete logarithm
The invention provides a method and a system for realizing multi-party key agreement. The method comprises the following steps that: after generating a key parameter, a member A1 generates key negotiation information with member information and sends the key negotiation information to a member A2; the member A2 generates random number calculation, generates key agreement information with the member information and sends the key agreement information to the member A3; continuously, the member Am generates a random number to calculate and obtain a secret key; key agreement information is generated through calculation and the member information and sent to the member Am-1; and in this way, the key negotiation information is sequentially transmitted, and the final member A1 calculates to obtain the key. According to the method, key agreement of multiple members can be effectively realized, a safe elliptic curve is selected, and on the basis of the safe elliptic curve, the security and confidentiality of key parameters in the communication process can be effectively ensured through the difficulty in solving discrete logarithms on the elliptic curve.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
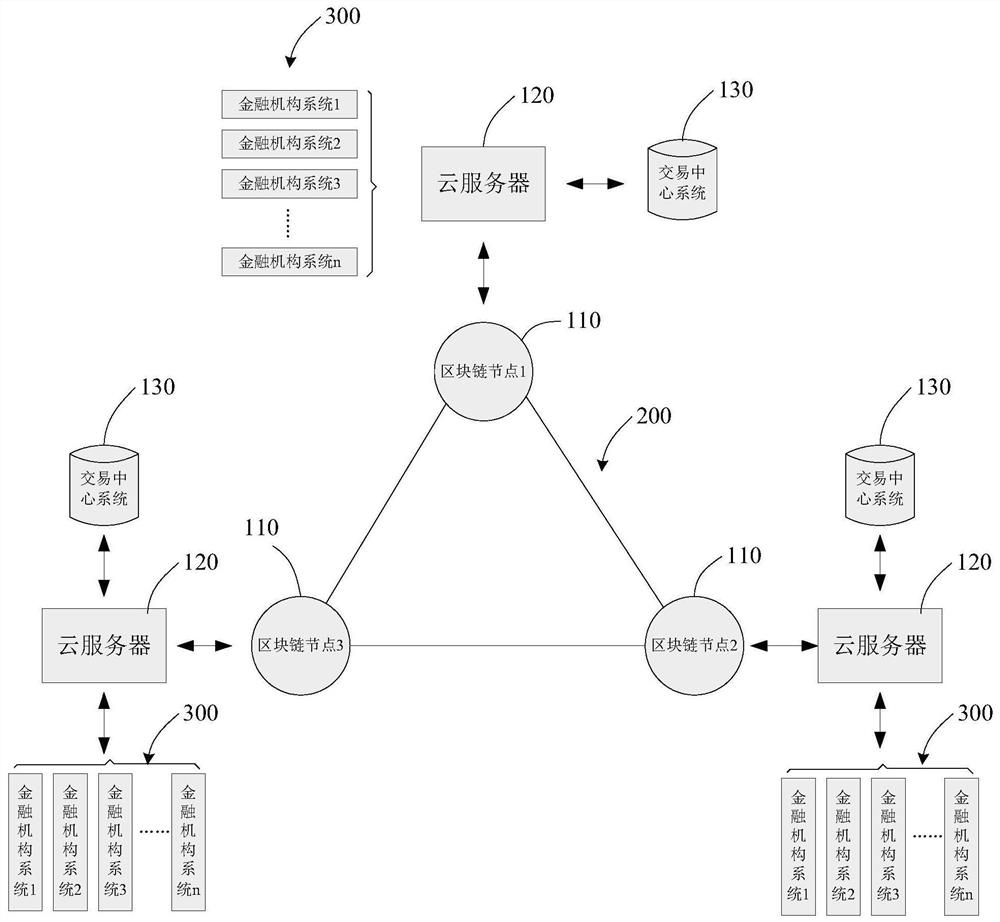
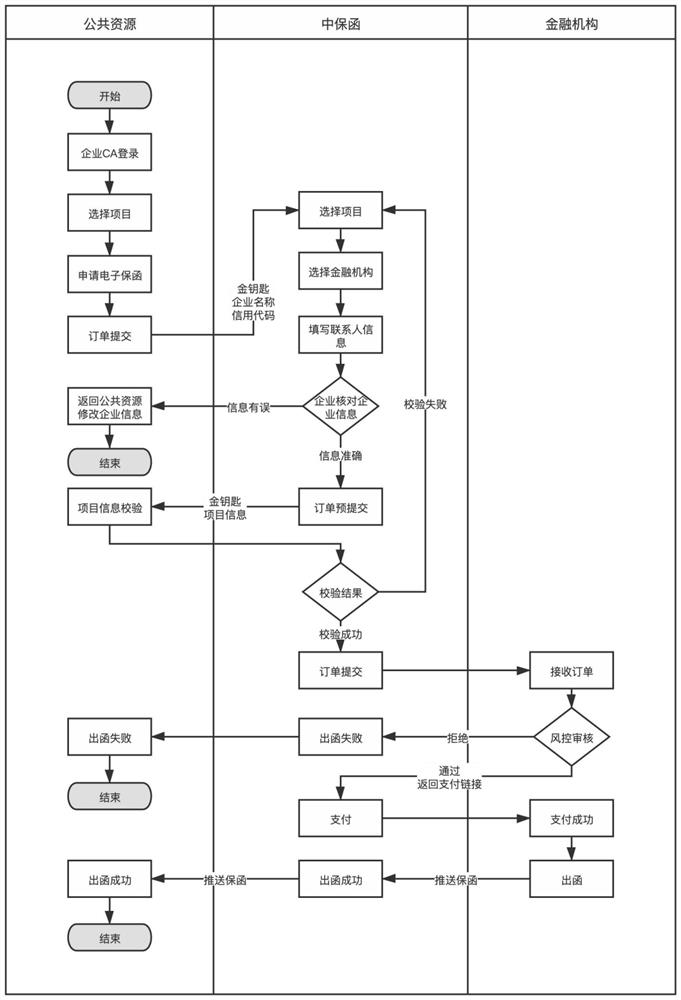
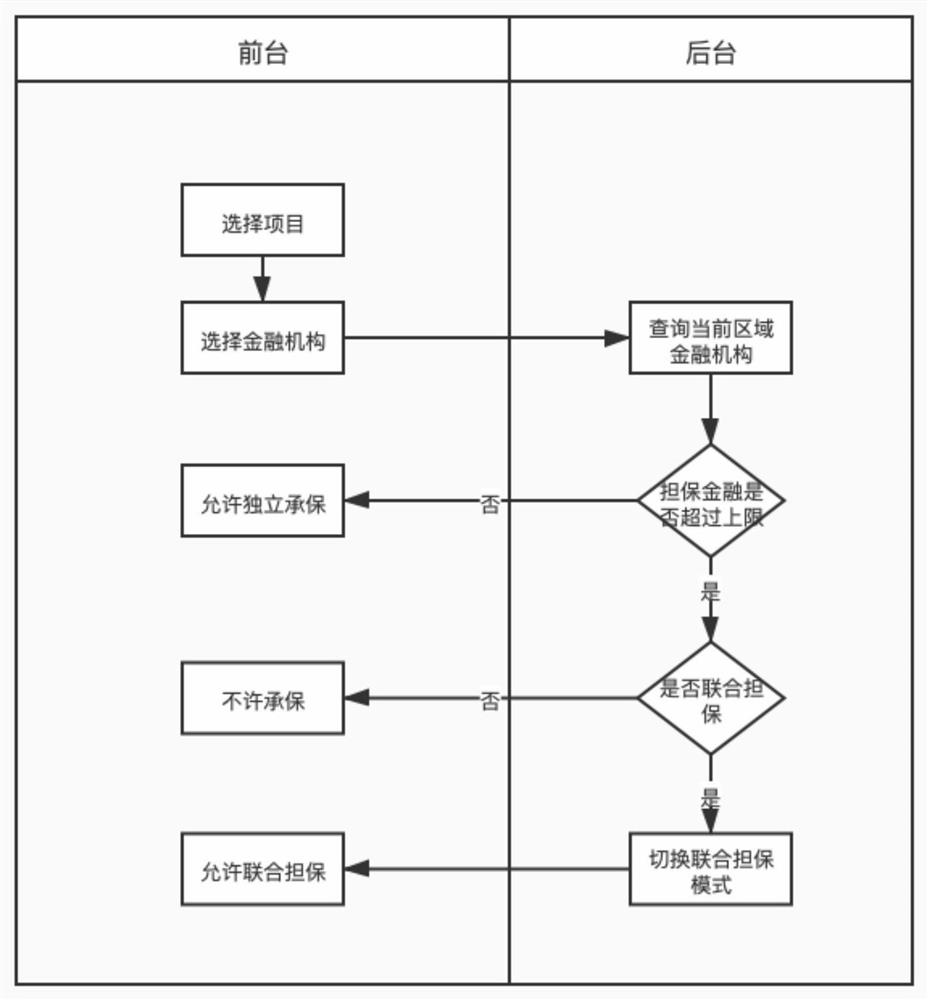
Electronic warrant issuing method, cloud server and electronic warrant system
PendingCN113077233AOptimize the business environmentOptimize the market environmentFinanceDatabase distribution/replicationBusiness enterpriseOperations research
The invention discloses an electronic warrant issuing method, a cloud server and an electronic warrant system. The method comprises the following steps of pushing a project list according to order data and a project selection request; receiving the selected items and primarily screening a financial institution based on the attributes of the items to obtain a primarily reviewed financial institution list; based on the bid amount of the selected item, interacting with the transaction center system to obtain a guarantee residual responsibility and a guarantee upper limit of the financial institution; carrying out secondary screening on the first-review financial institution list; when the guarantee residual responsibility of the financial institution exceeds the guarantee upper limit and joint guarantee exists, or when the guarantee residual responsibility of financial institutions does not exceed the guarantee upper limit, the financial institutions being reserved; generating a final financial institution list based on the reserved financial institutions and feeding back the final financial institution list; and receiving the selected financial institution, generating a warranty order and sending the warranty order to the selected financial institution system. More financial institutions with the qualification of dealing are provided for enterprises for selection, market business is expanded for guarantee companies, financial industry chains are expanded, and insurance companies obtain associated business.
Owner:李冬
Method and system for bill circulation, computer equipment and medium
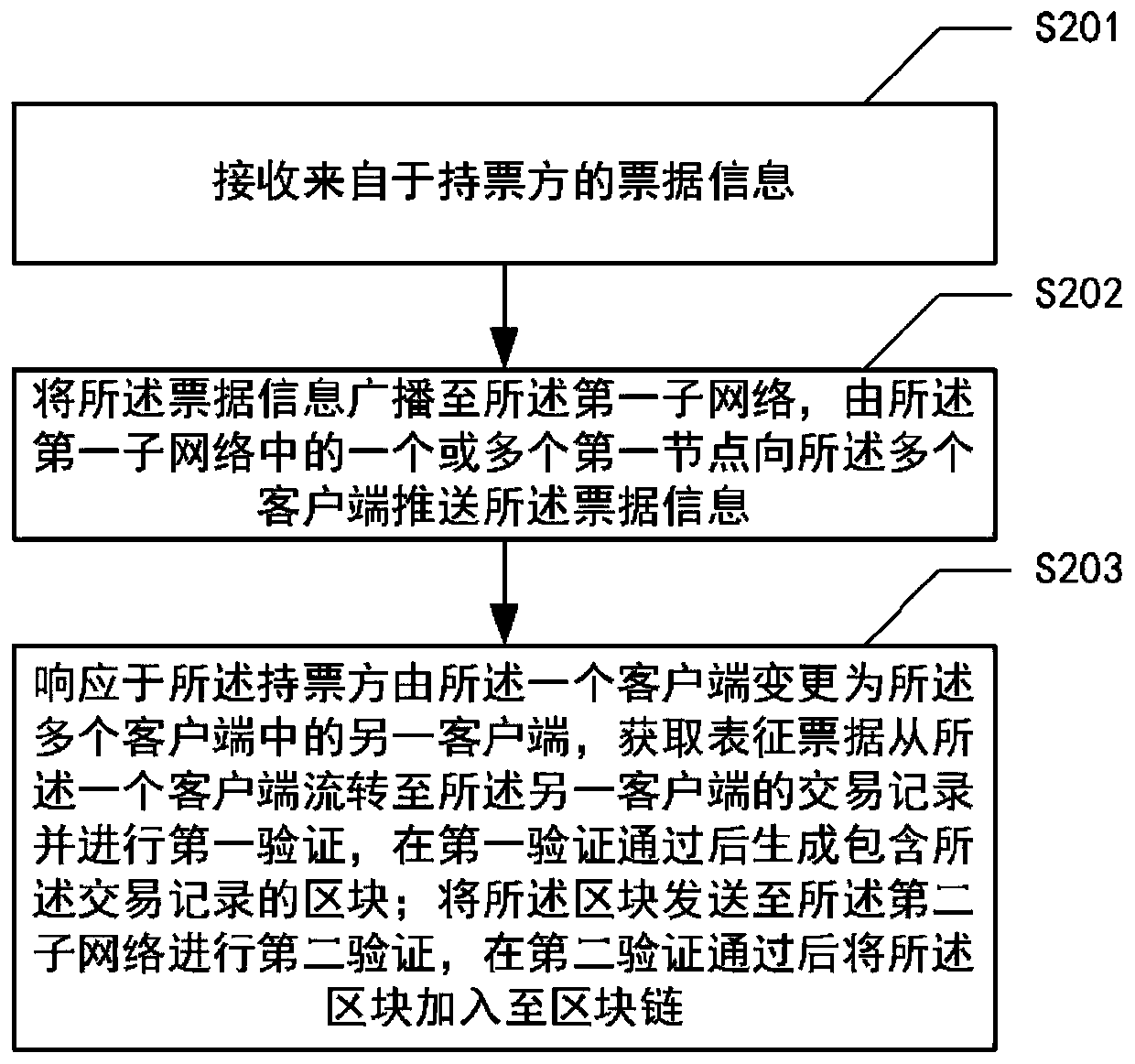
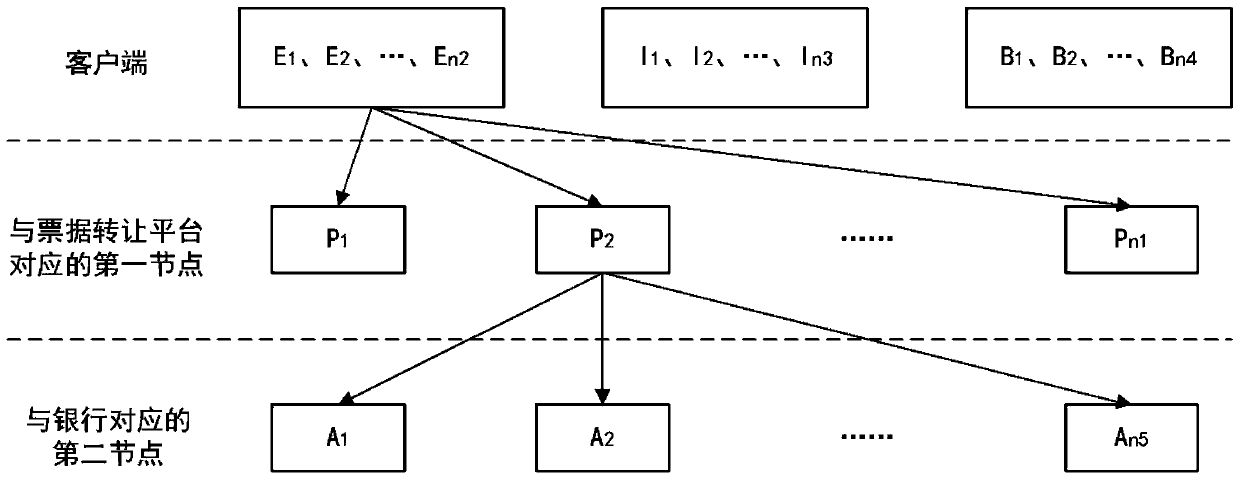
ActiveCN110417917AImprove efficiencyNo tamperingFinanceUser identity/authority verificationComputer engineeringComputer equipment
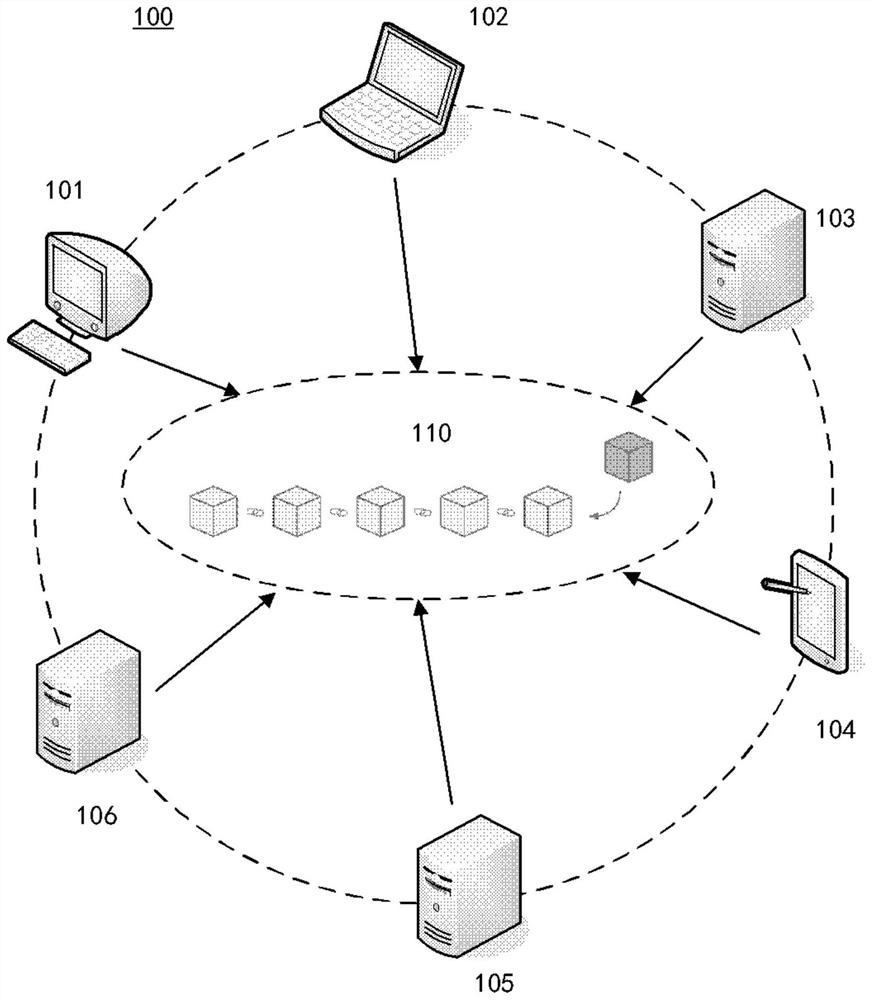
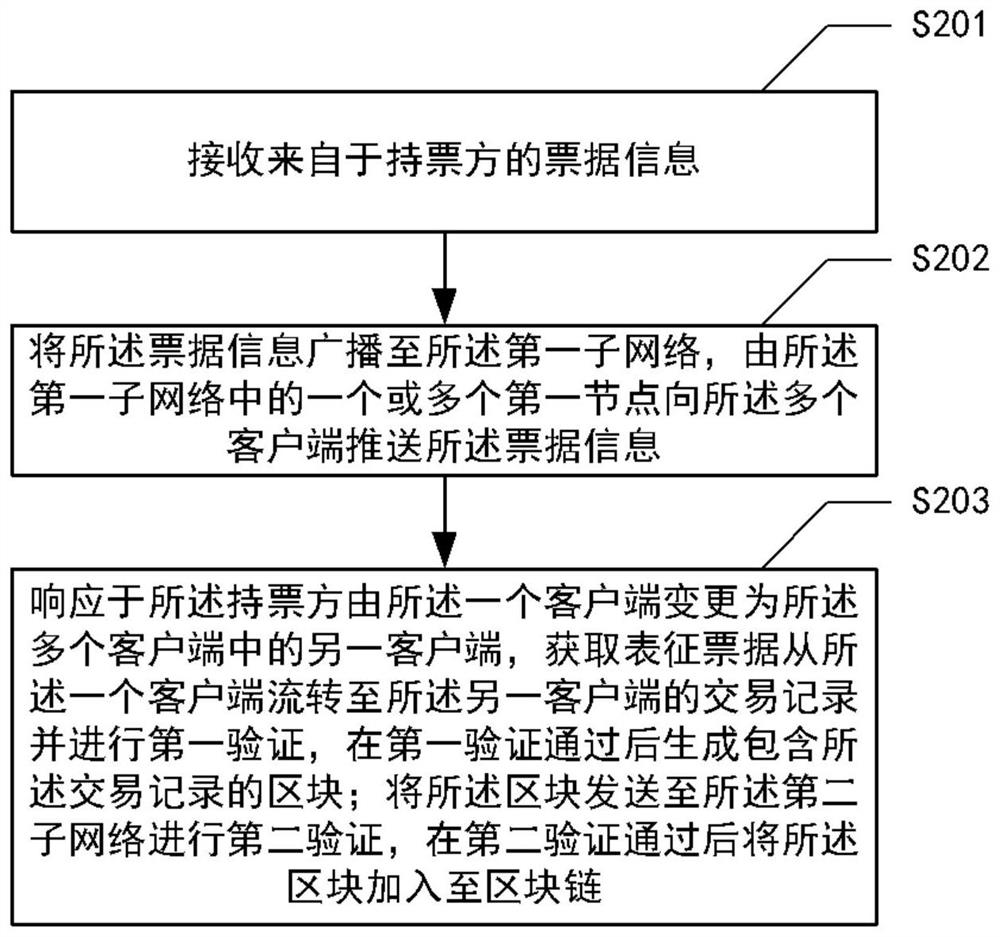
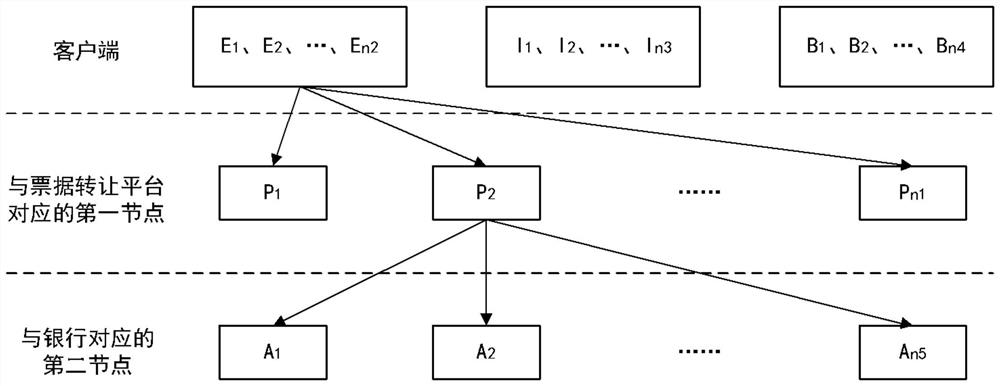
The invention provides a method for bill circulation. The method is applied to a main node of a first sub-network. The first sub-network comprises a plurality of first nodes including the main node, the plurality of first nodes correspond to a plurality of bill transfer platforms, the second sub-network comprises a plurality of second nodes corresponding to a plurality of bill discount banks, themethod comprises the following steps: receiving bill information from a bill holder, wherein the bill holder is one of a plurality of clients; broadcasting the bill information to the first sub-network; in response to the fact that the ticket holder is changed from one client to another client, obtaining a transaction record and performing first verification, and generating a block containing thetransaction record after the first verification is passed; and sending the block to the second sub-network for second verification, and adding the block to a block chain after the second verificationis passed. The invention further provides a system for bill circulation, computer equipment and a computer readable storage medium.
Owner:JINGDONG TECH HLDG CO LTD
Identity authentication method, identity authentication equipment, server and identity authentication-based encryption method
ActiveCN102035654BNo tamperingSolve the anti-counterfeiting problemUser identity/authority verificationHandwritingDigital signature
The invention provides an identity authentication method, identity authentication equipment, a server and an identity authentication-based encryption method and aims to solve the counterfeiting and repudiation prevention problems of identity authentication. The method comprises the following steps of: combining a written signature with a digital signature; acquiring the written signature handwriting of a user through the identity authentication equipment such as a universal serial bus (USB) key; combining the written signature handwriting with transaction data and performing digital signing; and transmitting signature data and the encrypted written signature handwriting to a verification party (such as an Internet bank background system). The signature data is verified by the verification party, so that the written signature handwriting and confidentiality data are not tampered in a transmission process; simultaneously, the truth of the written signature handwriting is verified by the verification party, so that the signature of the written signature handwriting by a user is ensured.
Owner:BEIJING WATCH DATA SYST
Education award teaching and learning assisting system based on blockchain
PendingCN111383148AGuaranteed Fair UsePrecise dockingData processing applicationsDatabase distribution/replicationData transmissionPrivacy protection
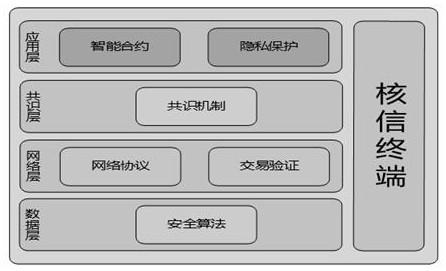
The invention discloses an education award teaching and learning assisting system, and relates to a blockchain, and the overall architecture of the system comprises an application layer, a consensus layer, a network layer, a data layer and an information checking terminal. The information checking terminal is respectively connected with the application layer, the consensus layer, the network layerand the data layer; the application layer comprises an intelligent contract module and a privacy protection module; the consensus layer comprises a consensus mechanism module; the network layer comprises a network protocol module and a transaction verification module; the data layer comprises a security algorithm module; the education award teaching and learning assisting system adopts a blockchain technology as a data transmission and distributed storage core service layer. According to the education award teaching and learning assisting system based on the blockchain, accurate docking, accurate management and accurate assistance can be realized. Through big data analysis, an assistant student tracking file is established, and the block chain records the real life condition of the student.
Owner:SHUNDE POLYTECHNIC
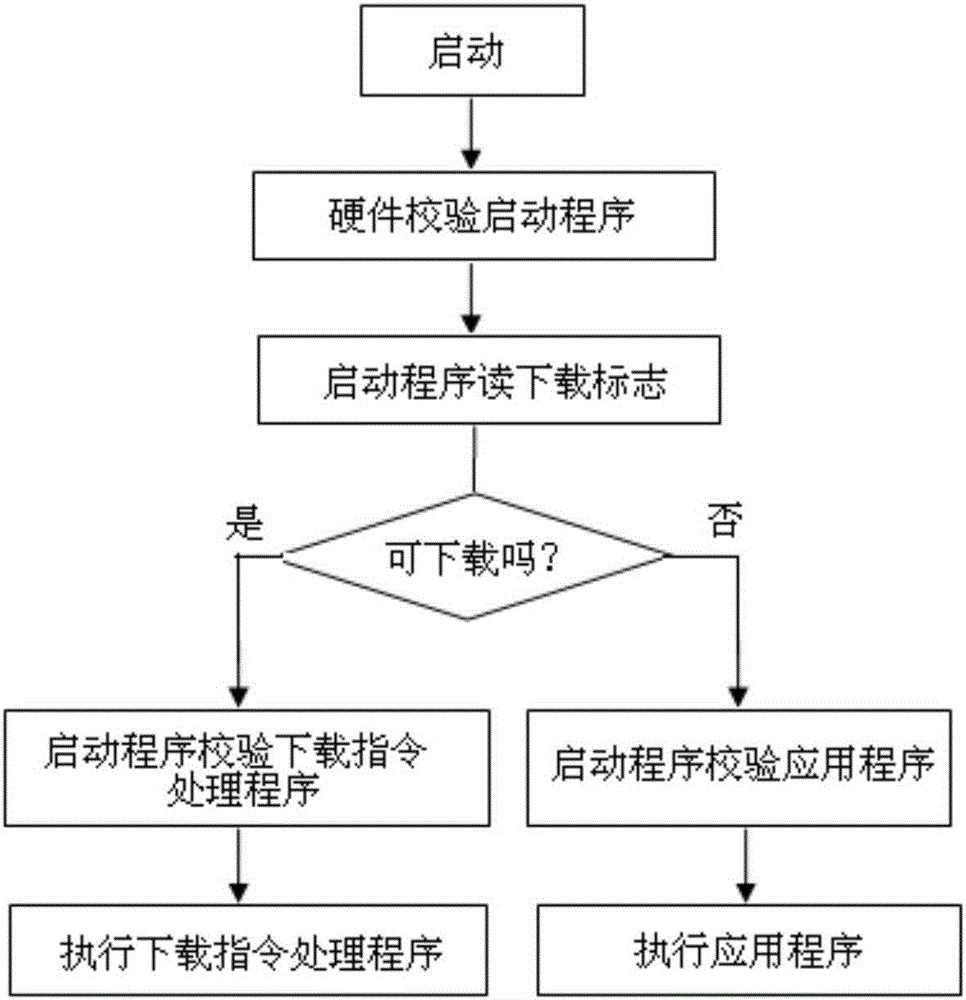
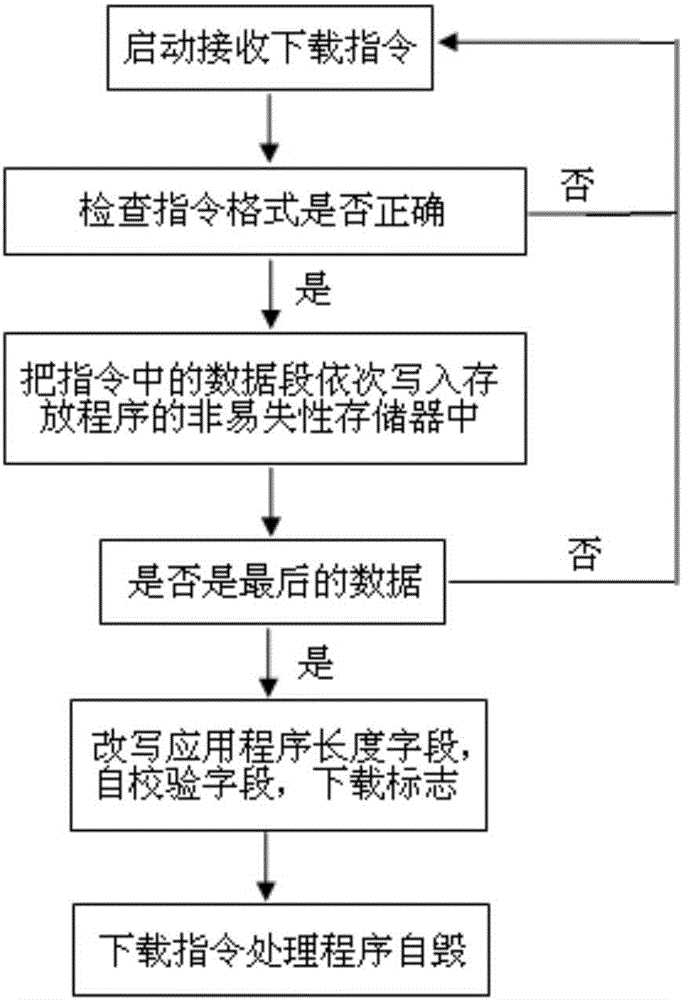
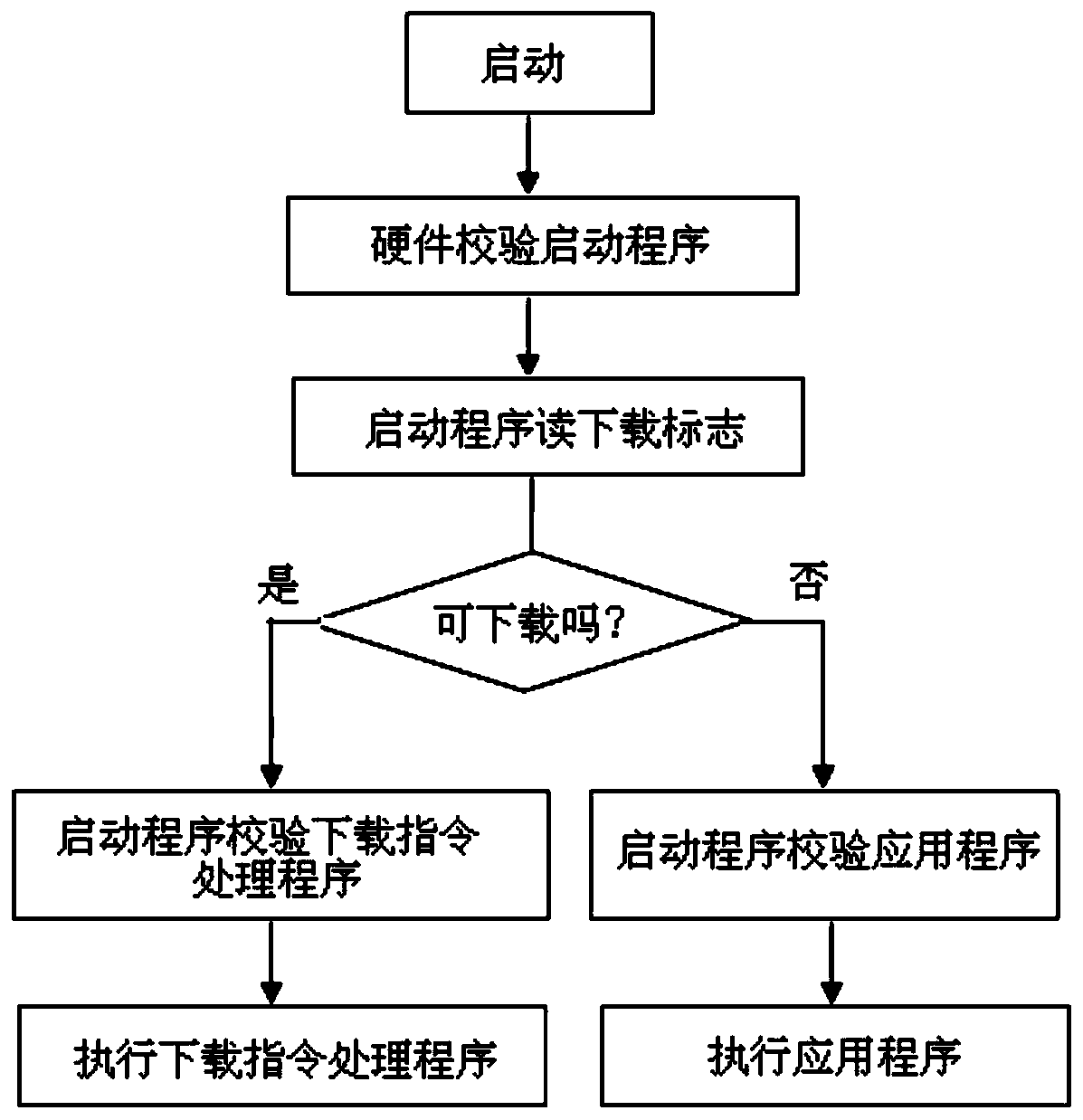
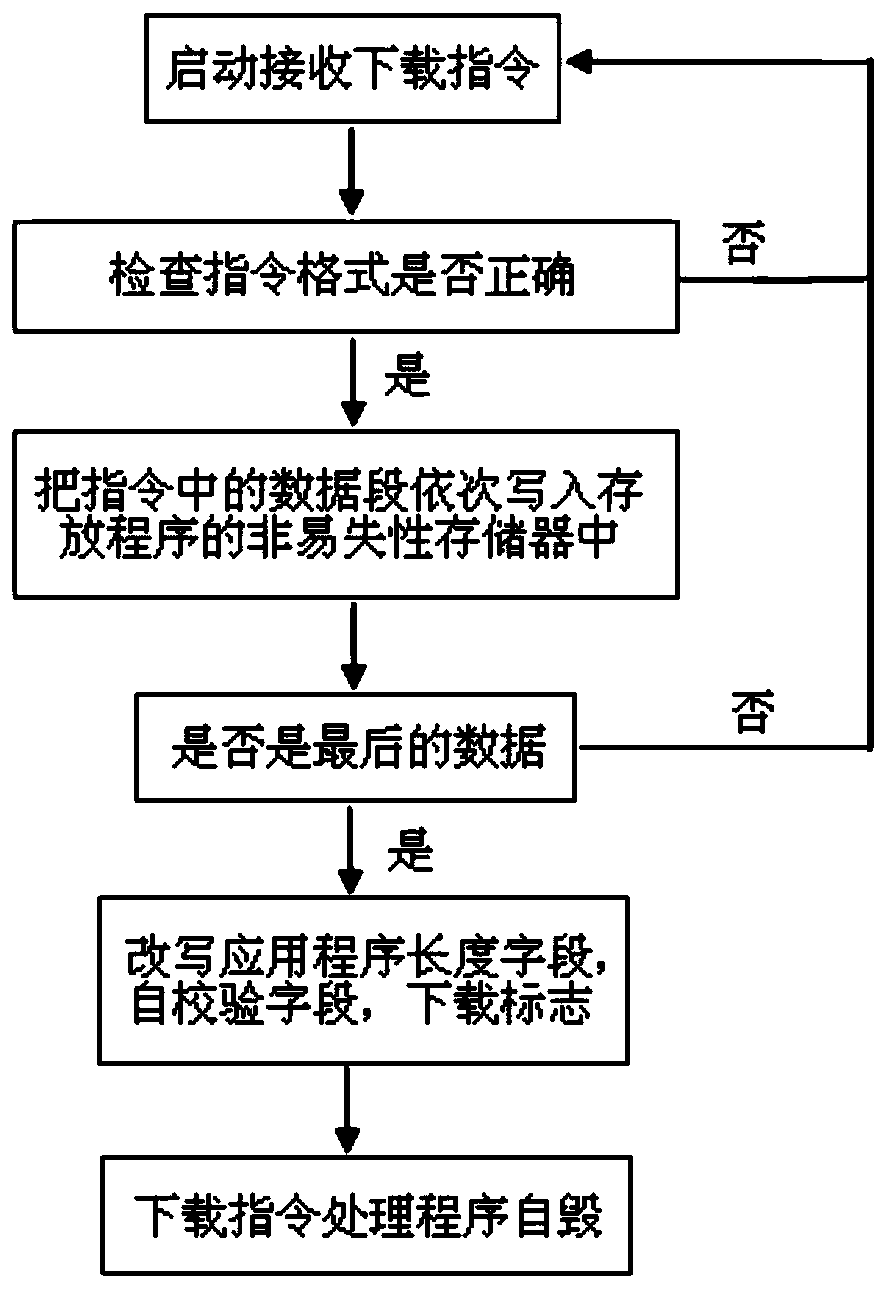
Secure software downloading and starting method
ActiveCN106484477ANo tamperingNot easy to attackDigital data protectionProgram loading/initiatingApplication softwareComputer science
The invention discloses a secure software downloading and starting method. The method comprises the following steps of 1, checking a startup program realized by software by adopting a hardware logic circuit; 2, reading a downloading flag field by the startup program or the hardware logic circuit; and 3, if the downloading flag field displays that an existing device is in an application downloadable stage, checking a downloading instruction processing program by the startup program, and then executing the downloading instruction processing program; and if the downloading flag field displays that the existing device is in an application non-downloadable stage, checking an application by the startup program, and then executing the application. According to the method, attacks performed on the device by attackers through adopting different means can be resisted, so that the device security is improved.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
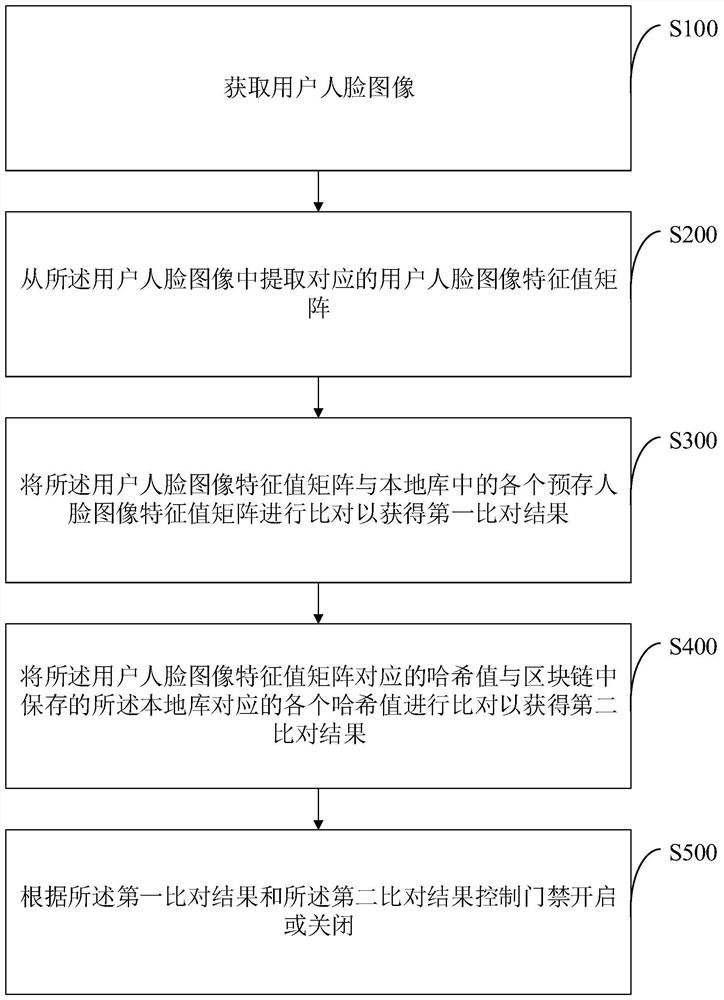
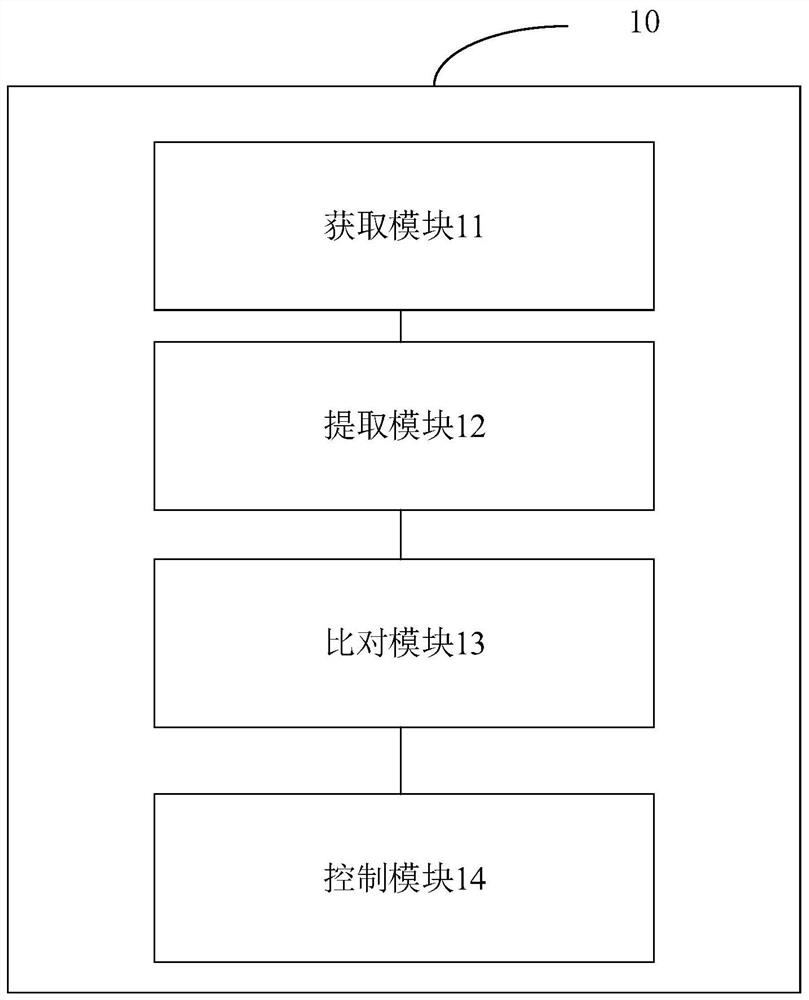
Block chain-based access control management method and device and access control equipment
PendingCN113516807AEnsure safe passageReduce dependenceDatabase distribution/replicationCharacter and pattern recognitionSystem verificationInternet traffic
The invention discloses an access control management method and device based on a block chain and access control equipment. When a user requests to open an access control, a face image is not transmitted by using a network, so that the leakage of personal privacy is avoided, the network traffic use of Internet of Things equipment is greatly reduced, the 4G / 5G traffic cost is reduced, and the transmission is more efficient; in addition, when the user requests to open the access control, an access control system verifies whether the user is legal or not, meanwhile, the block chain is used for conducting dual verification on the user, the safe passing of the user can be guaranteed, verification and troubleshooting can be conducted on a local library of the access control equipment, and the safety of the whole access control system is effectively improved.
Owner:SHENZHEN QINLIN TECH
A Method for Preventing Illegal Tampering of Program Content
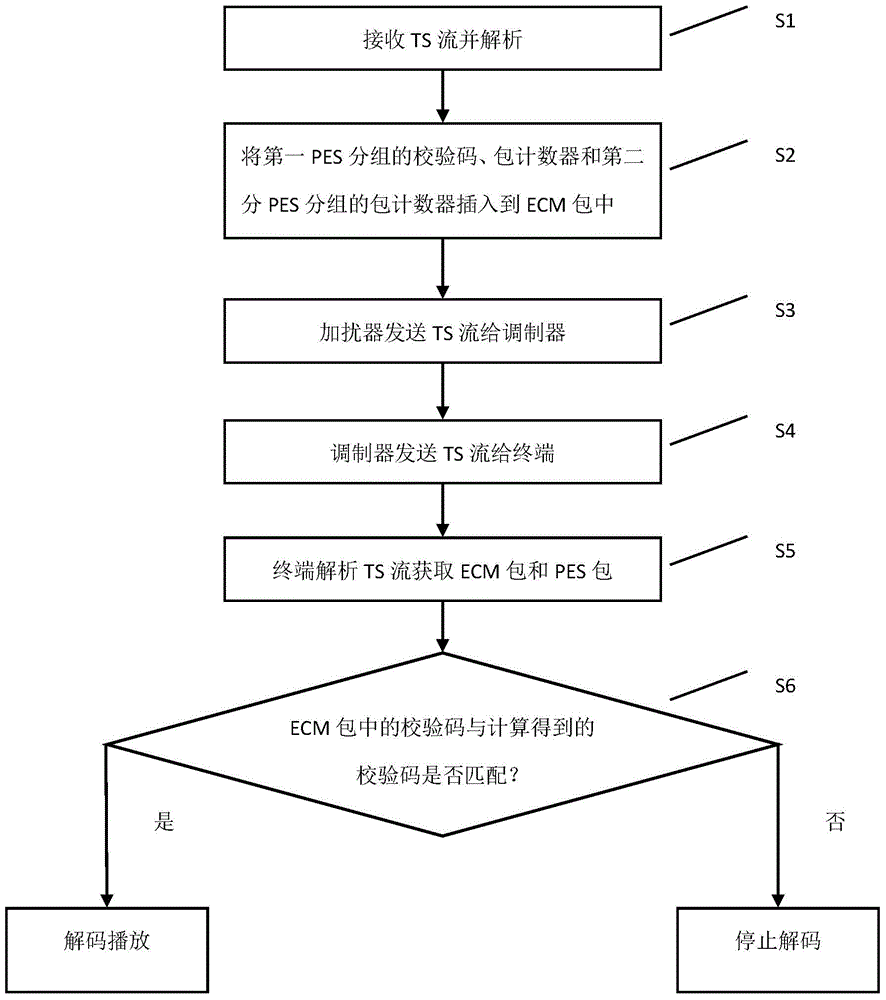
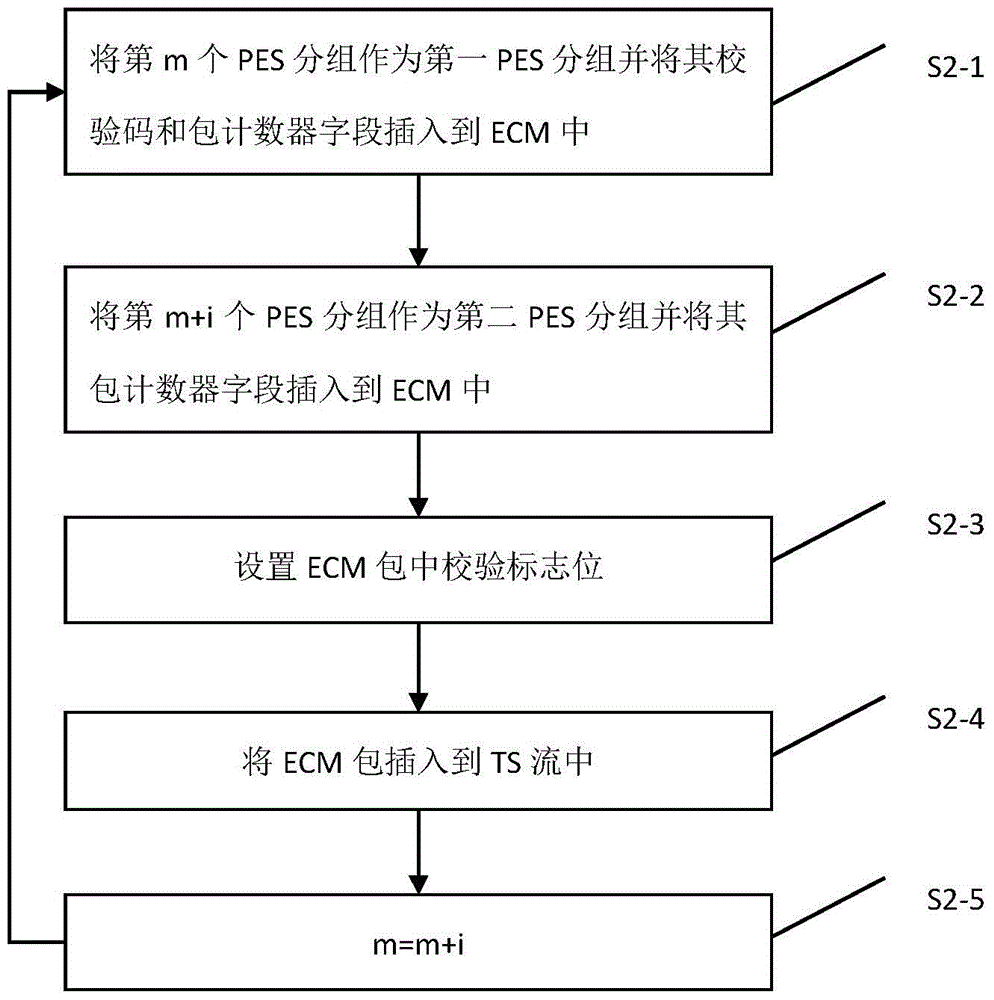
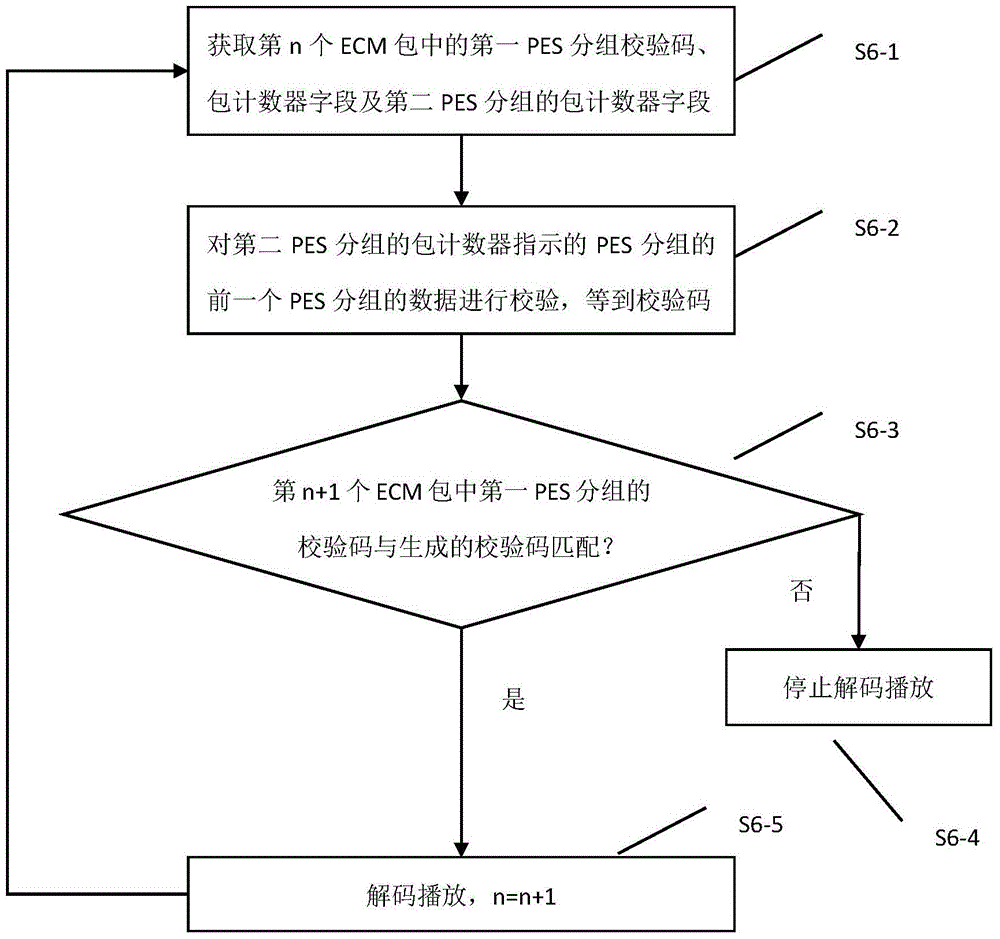
ActiveCN104320673BNo tamperingEnsure safetySelective content distributionContent securityDigital television
The invention discloses a method for program content illegal tampering preventing. The method comprises the steps that (1) a scrambler receives a TS, and PES groups are obtained by analysis; (2) the scrambler packages check codes and a package counter of a first PES group and a package counter of a second PES group to an ECM package, and the ECM package is inserted into the TS; (3) the scrambler sends the TS to a modulator; (4) the modulator modulates the TS and then sends the TS to a terminal; (5) the terminal receives the TS, and the ECM package and the PES groups are obtained by analysis; and (6) whether the check codes of the first PES group in the ECM package are matched with check codes generated by checking of the corresponding PES group is judged, if yes, the TS is subjected to decoding playing, otherwise, checking errors are hinted, and decoding is stopped. According to the method, program content illegal tampering can be effectively prevented, the content safety of a digital television is guaranteed, achieving is easy, and promoting is easy.
Owner:SHANDONG TAIXIN ELECTRONICS CO LTD
Method, system, computer device and medium for bill circulation
ActiveCN110417917BImprove efficiencyNo tamperingFinanceUser identity/authority verificationTicketFinancial transaction
Owner:JINGDONG TECH HLDG CO LTD
A Method of Traceable Data Security and Fidelity
ActiveCN109862002BMaintenance "trueMaintain "True"Encryption apparatus with shift registers/memoriesCommunications securityInformation processing
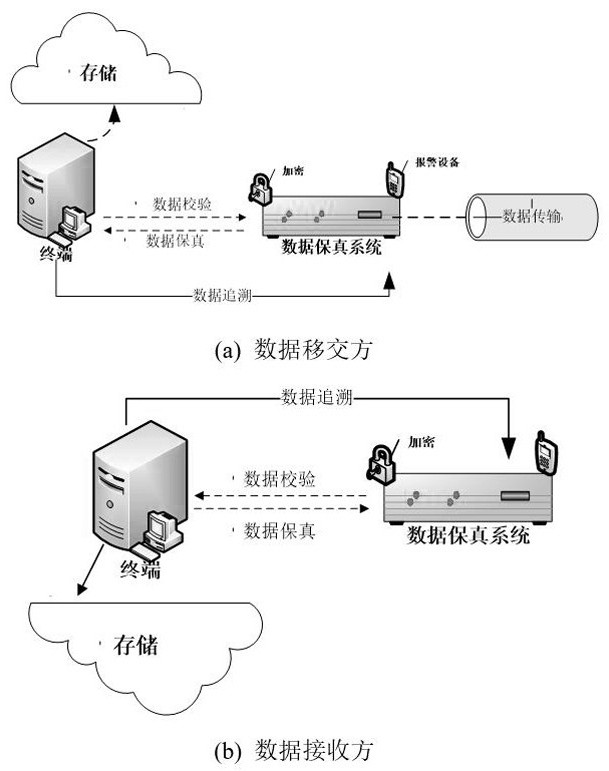
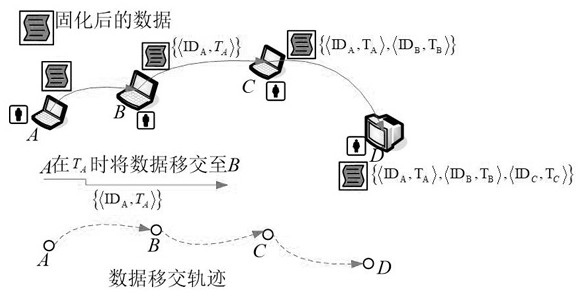
The invention relates to the field of communication security, in particular to a traceable data security fidelity method. Among them, the security strategy includes the security strategies in three aspects of the data fidelity stage, the data transmission stage and the data traceability stage; the strategy method of the data fidelity stage is to use the data fidelity system to perform data curing and data preservation on the data. Processing and recording data handover track information processing; the strategy method in the data transmission stage is that the user at the receiving end checks the data through the data fidelity system to determine the correctness of the data; the strategy method in the data traceability stage is that the user at the receiving end After discovering data errors, by querying the data transfer track information in the data fidelity system, the data reported with errors will be handed over and returned step by step according to the transfer track information. After each handover, the data will be re-verified at the upper-level node until the cause of the error is found .
Owner:SHANGHAI TAIYU INFORMATION TECH
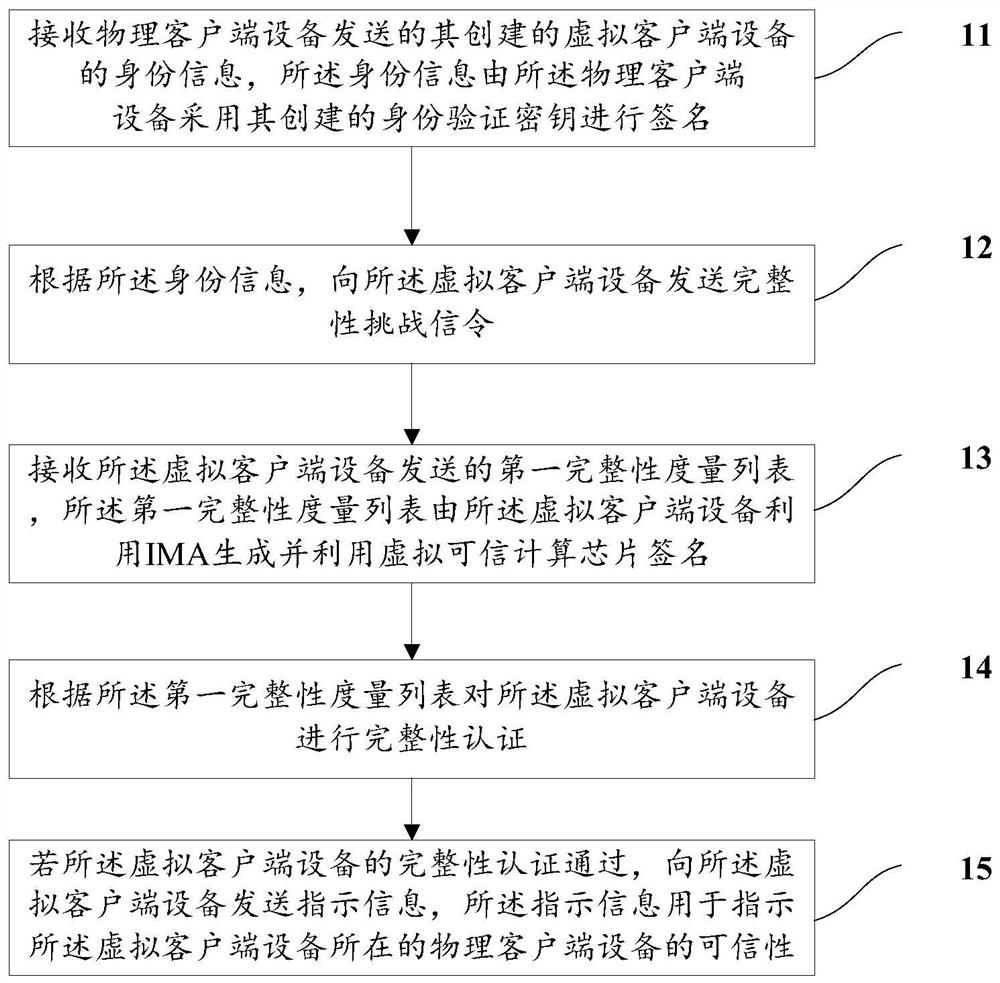
Integrity authentication method and device for virtual client device
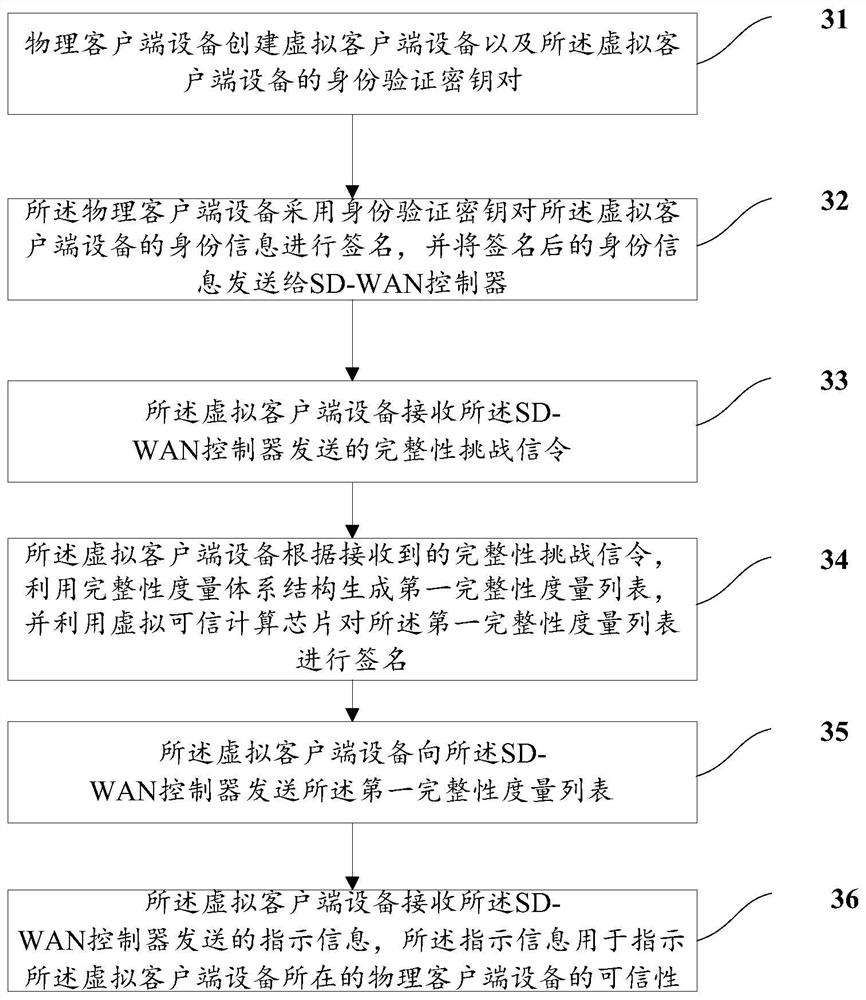
PendingCN114764367ANo tamperingEnsure predictabilityDigital data protectionSoftware simulation/interpretation/emulationOperational systemEngineering
The invention provides an integrity authentication method and device for virtual client equipment. The method comprises the following steps: an SD-WAN controller sends an integrity challenge signaling to the virtual client equipment; receiving a first integrity measurement list sent by the virtual client device, wherein the first integrity measurement list is generated by the virtual client device by using the integrity measurement system structure and signed by using the virtual trusted computing chip; performing integrity authentication on the virtual client device according to the first integrity measurement list; if the integrity authentication of the virtual client device is passed, indication information is sent to the virtual client device, and the indication information is used for indicating the credibility of a physical client device where the virtual client device is located. In the invention, the SD-WAN controller performs integrity authentication on the virtual client device, so that the virtual operating system of the virtual client device can be ensured not to be tampered, the predictability of the behavior of the virtual operating system is ensured, and the security of the system is improved.
Owner:CHINA MOBILE COMM LTD RES INST +1
A cross-departmental data sharing system and method based on blockchain technology
ActiveCN112671840BNo tamperingLimit tamperingFinanceDigital data protectionData acquisitionUnstructured data
The present invention relates to a cross-departmental data sharing system and method based on block chain technology. The system includes a query server, a sorting node, and multiple departmental storage centers. In each departmental storage center, a data acquisition module is connected to a data processing server, and the data The processing server is connected to the distributed storage system and the query server respectively, and the distributed storage system is connected to the query server; the data processing server acts as the peer node of the blockchain, and the sorting node transmits information to the storage centers of each department through the message channel. Compared with the existing technology, the present invention uses blockchain technology to directly store structured data on the chain, which can ensure that the data will not be tampered with. The hash value verification can also be traced, which further limits the behavior of tampering with the data and improves the security and credibility of the data sharing system.
Owner:TONGJI UNIV
Safe software download and launch method
ActiveCN106484477BNo tamperingNot easy to attackDigital data protectionProgram loading/initiatingApplication softwareSoftware download
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
A Secret Shared Cloud Storage Method for Outsourced Reconfigurable Electronic Medical Records
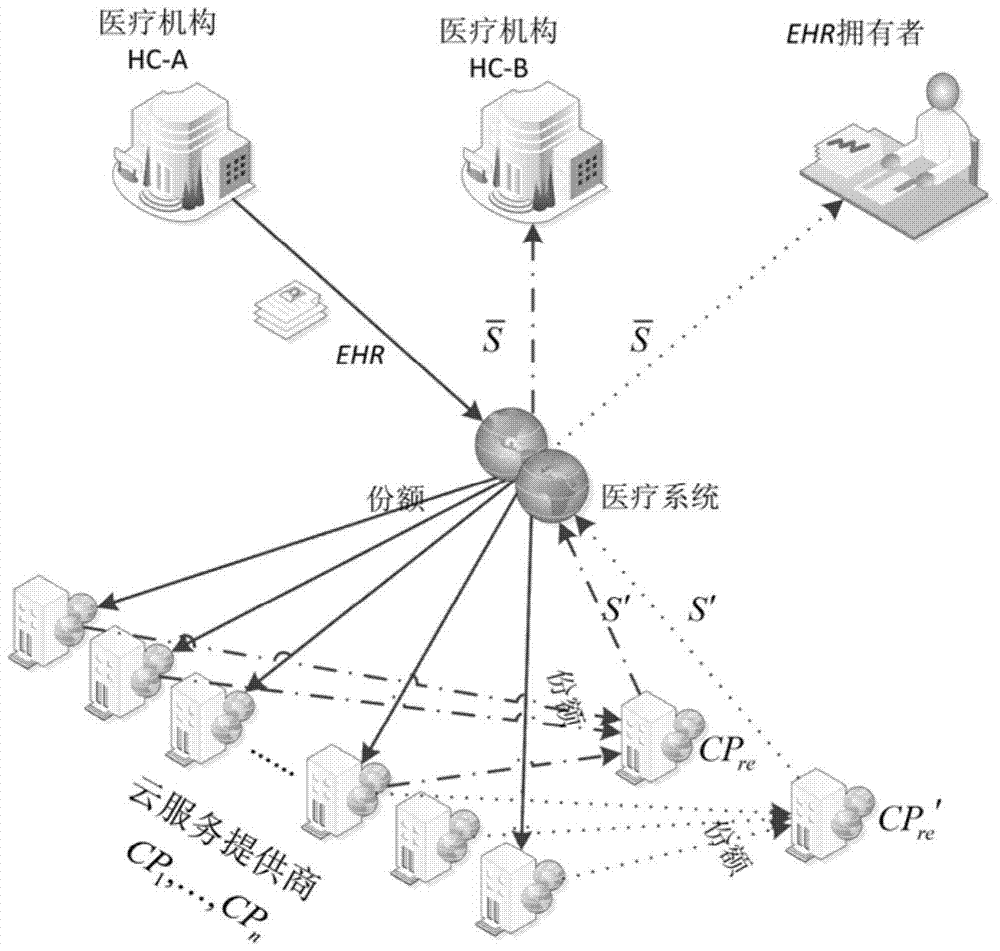
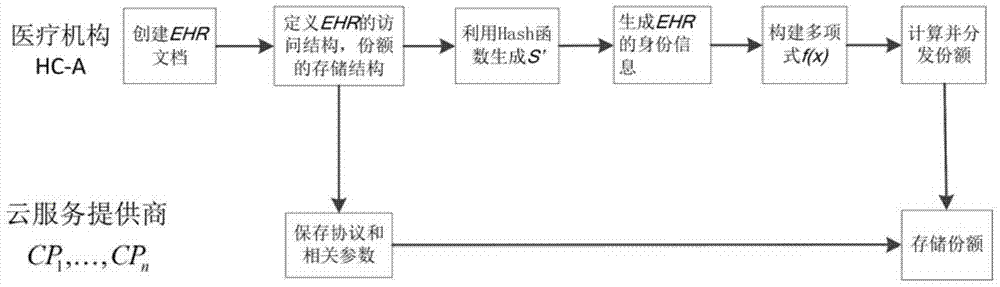
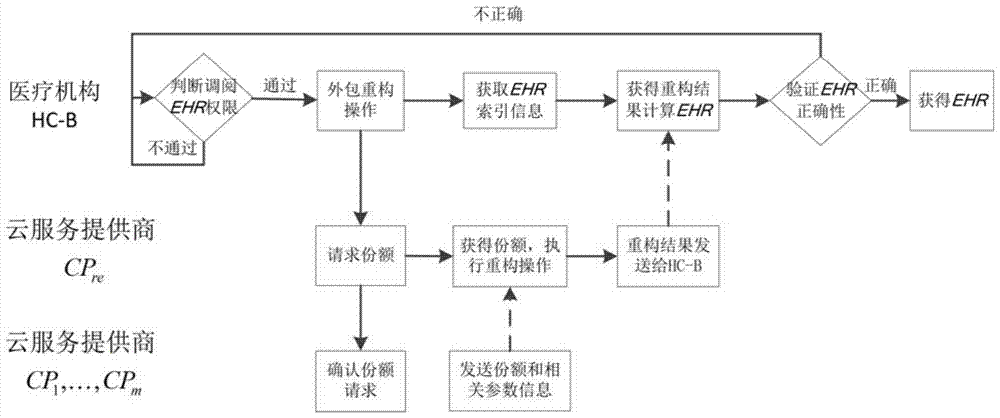
ActiveCN104270448BReduce data processing pressureNo tamperingData processing applicationsTransmissionSecret shareCloud storage
The invention provides a secret sharing cloud storage method. The method includes the preprocessing state, the distribution stage, the reconstruction stage and the recovery and verification stage. At the preprocessing stage, preprocessing is conducted on electronic medical records through the HC-A, and the preprocessing result is directly used for the distribution stage; at the distribution stage, n shares are generated through the HC-A and distributed to the CP1, the K and the CPn; at the reconstruction stage, the CPre obtains t or more shares from the CP1, the K and the CPn, and the preprocessing result of the electronic medical records are recovered and sent to the HC-B; at the recovery and verification stage, the electronic medical records are recovered through the HC-B, and the correctness of the electronic medical records is verified. According to the method, while it is ensured that the calculation cost of users is reduced, it can be ensured that neither cloud service providers storing the electronic medical records nor cloud service providers recovering the electronic medical records can obtain the records.
Owner:SHANDONG ZHENGZHONG COMP NETWORK TECH CONSULTING
Security processing method, device, processing chip and network equipment
ActiveCN102263794BIntegrity guaranteedNo tamperingEncryption apparatus with shift registers/memoriesComputer hardwareIPsec
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
A two-stage hash chain storage method for data or files
ActiveCN114154189BAvoid changeSimple pre-checkDigital data protectionTheoretical computer scienceComputation process
Owner:ZEU CRYPTO NETWORKS INC +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com