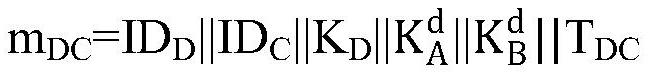Patents
Literature
47results about How to "Ensure security and confidentiality" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
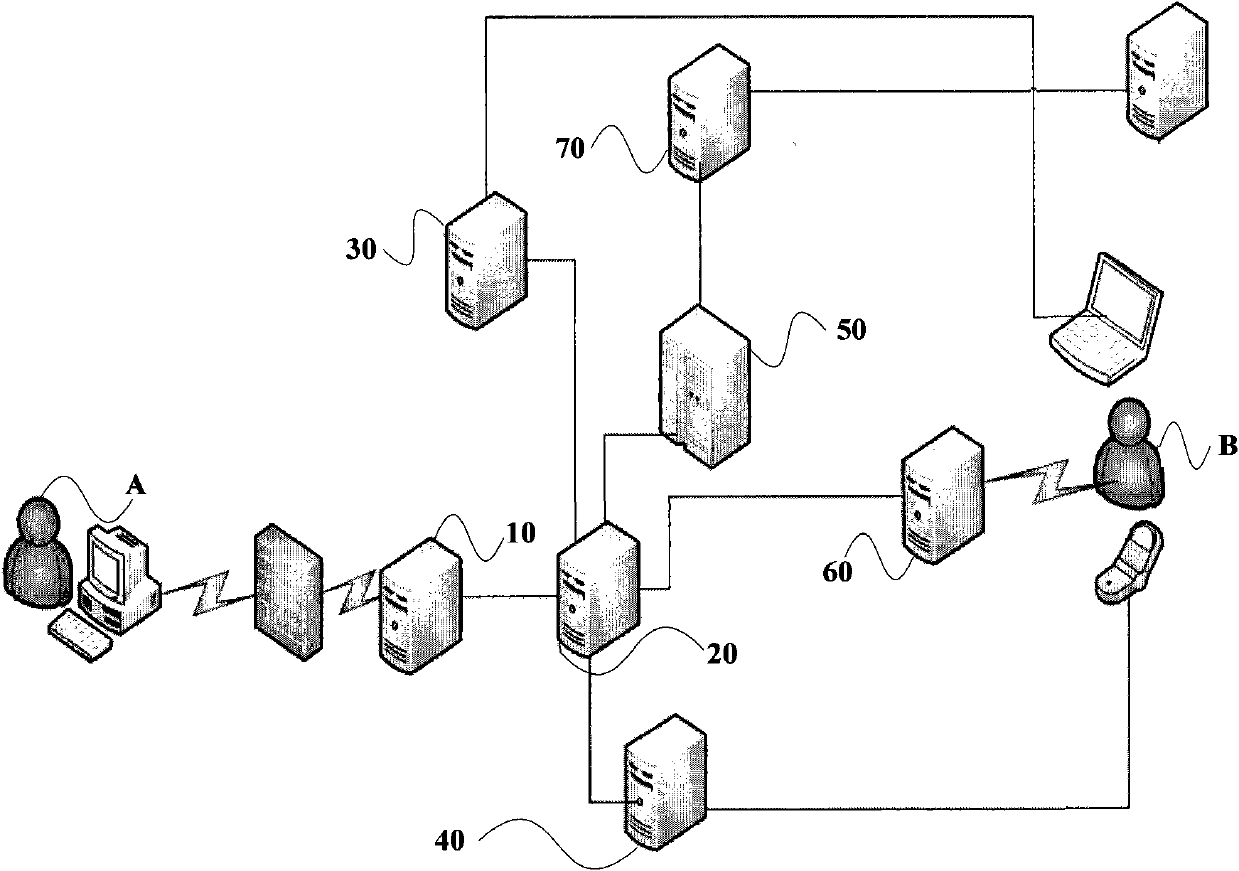
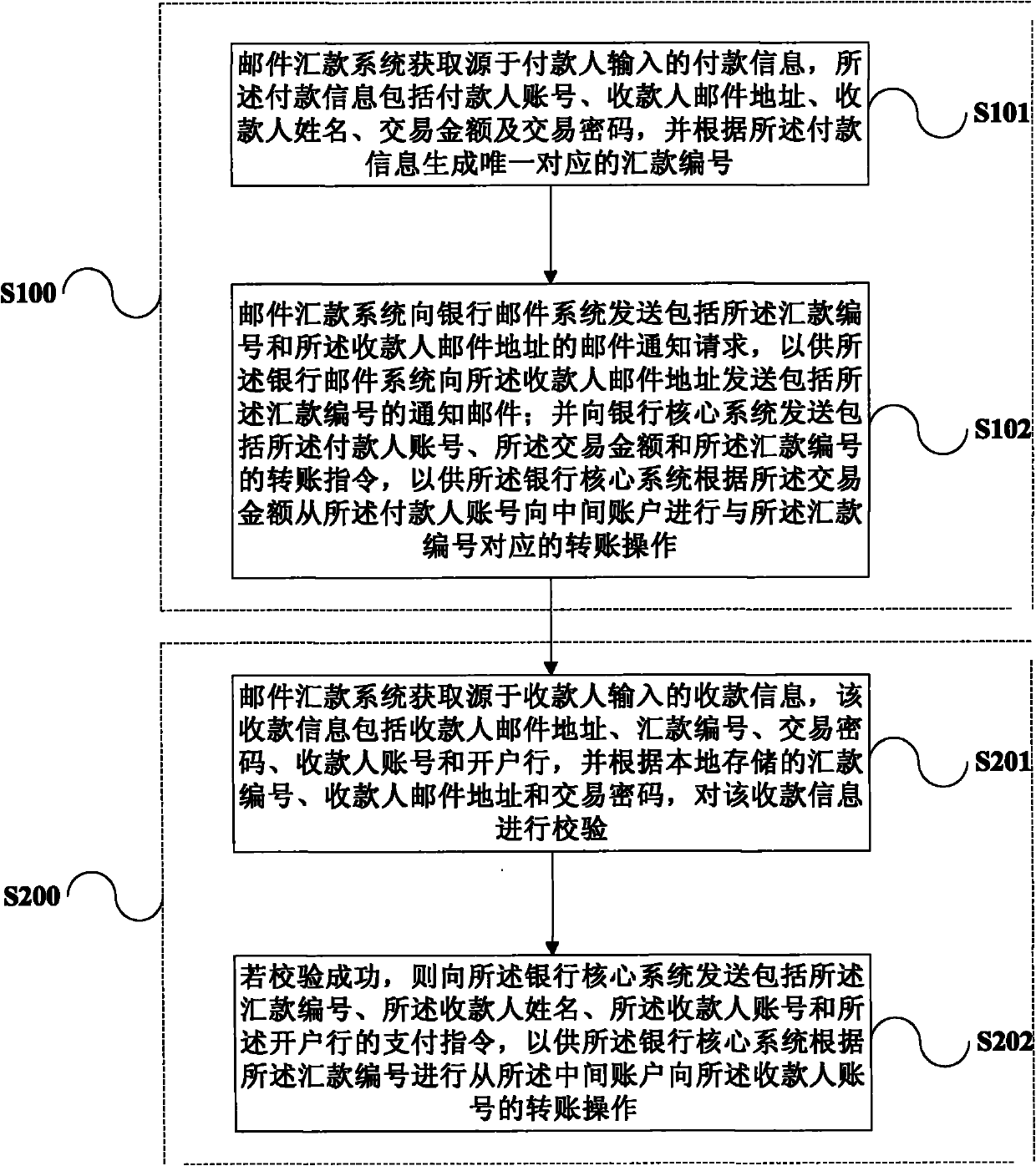
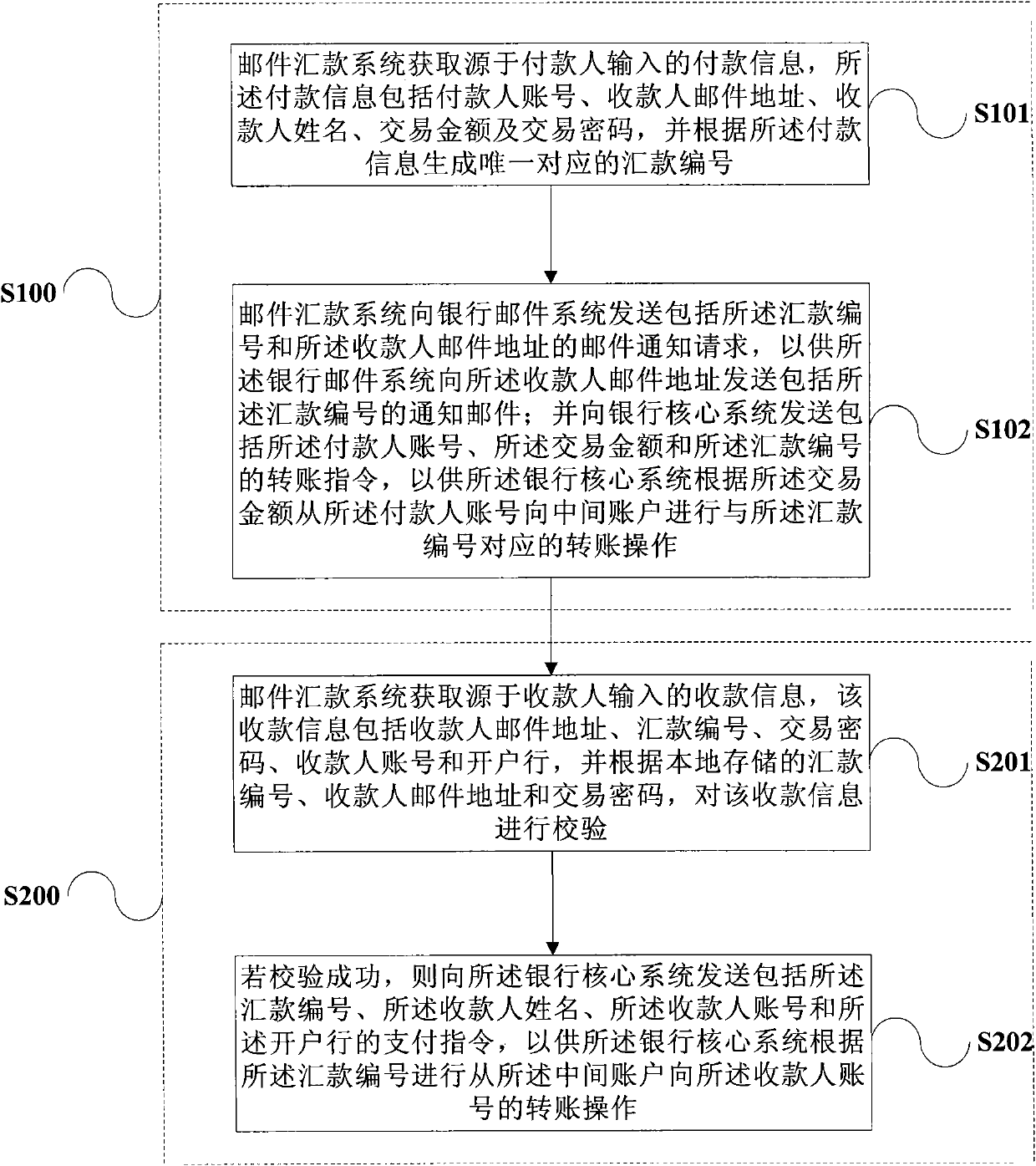
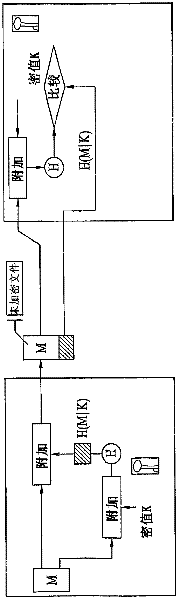
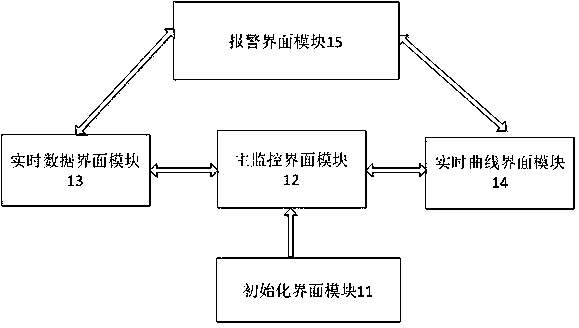
Method and system for processing collection and payment among bank accounts
InactiveCN101950451ASimplify the payment processEnsure security and confidentialityComplete banking machinesCore systemMonetary Amount
The invention provides a method and a system for processing collection and payment among bank accounts. The method comprises the following steps that: a mail remittance system acquires payment information comprising a payer account number, a payee email address, a payee name, a transaction amount and a transaction password which are input by a payer, and generates a remittance number according to the payment information; the mail remittance system sends a mail notification request to a bank mail system so as to allow the bank mail system to send a notification mail; the mail remittance system sends a transfer instruction to a bank core system so as to allow the bank core system to perform transfer operation corresponding to the remittance number from a payer account to an intermediate account; the mail remittance system acquires collection information comprising a payee mail address, the remittance number, the transaction password, a payee account and an opening bank which are input by the payee, and checks the collection information according to local storage information; and the mail remittance system sends a payment instruction to the bank core system if the checking is successful so as to allow the bank core system to perform the transfer operation from the intermediate account to the payee account.
Owner:MINSHENG BANKING CORP
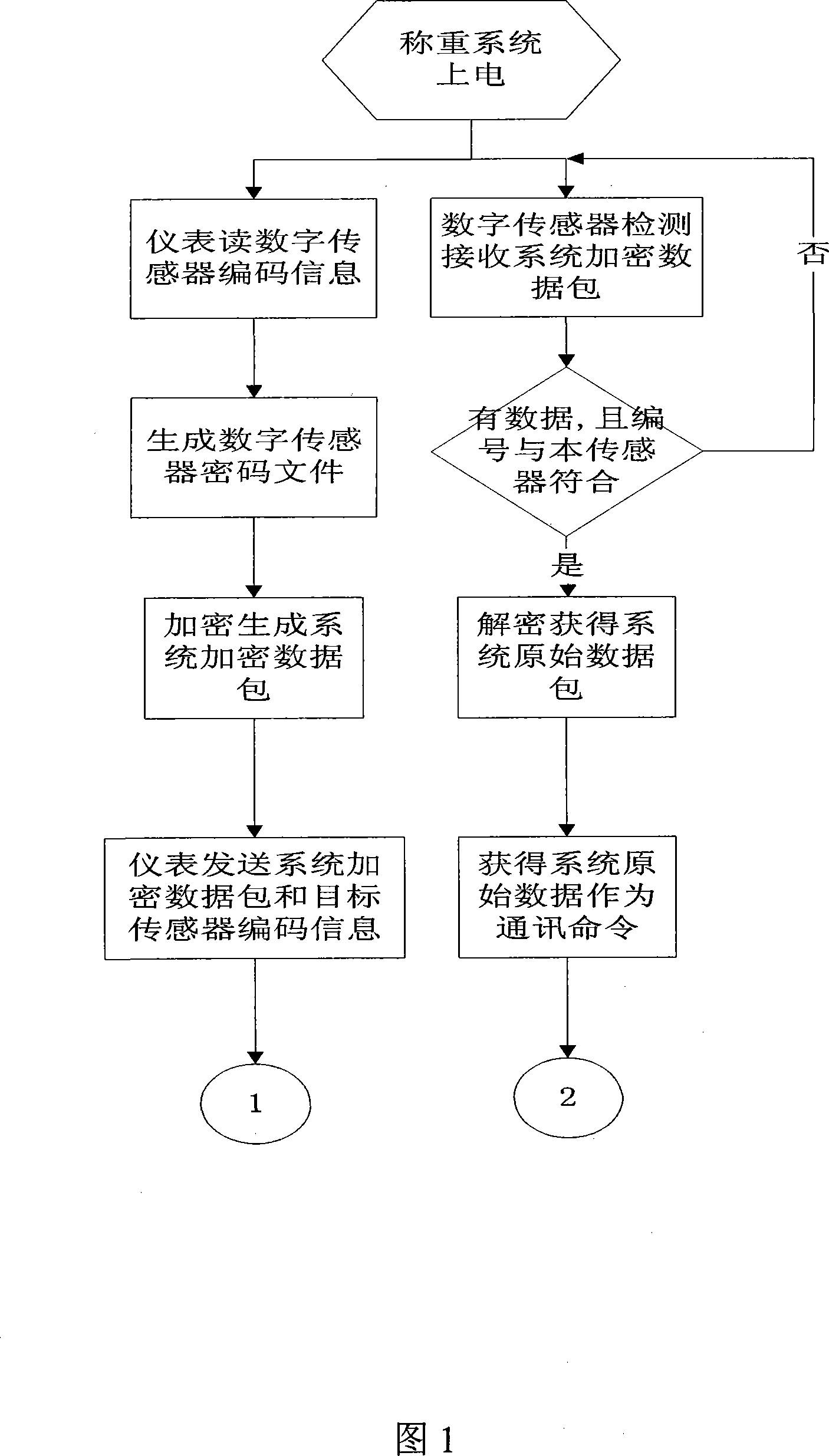
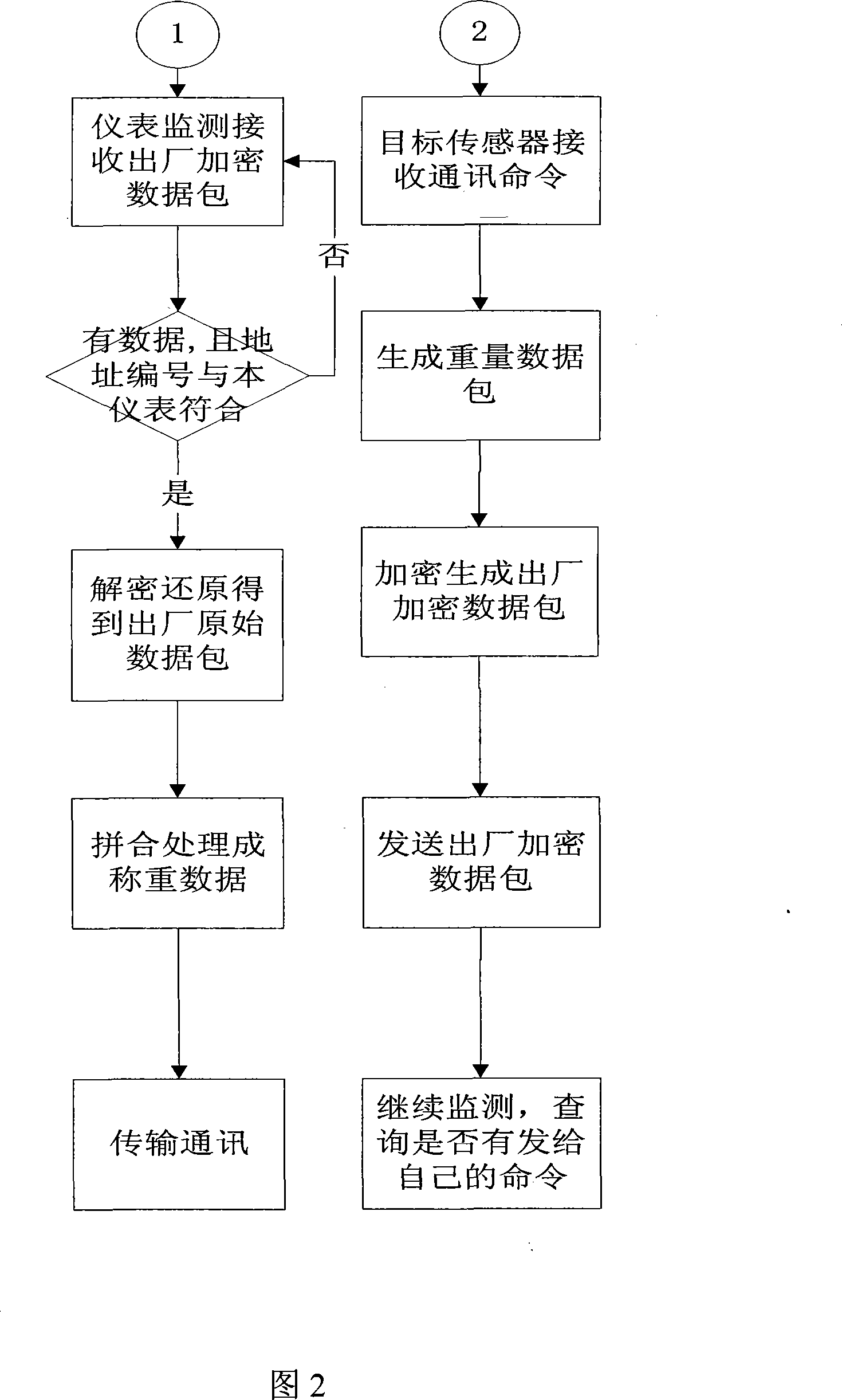
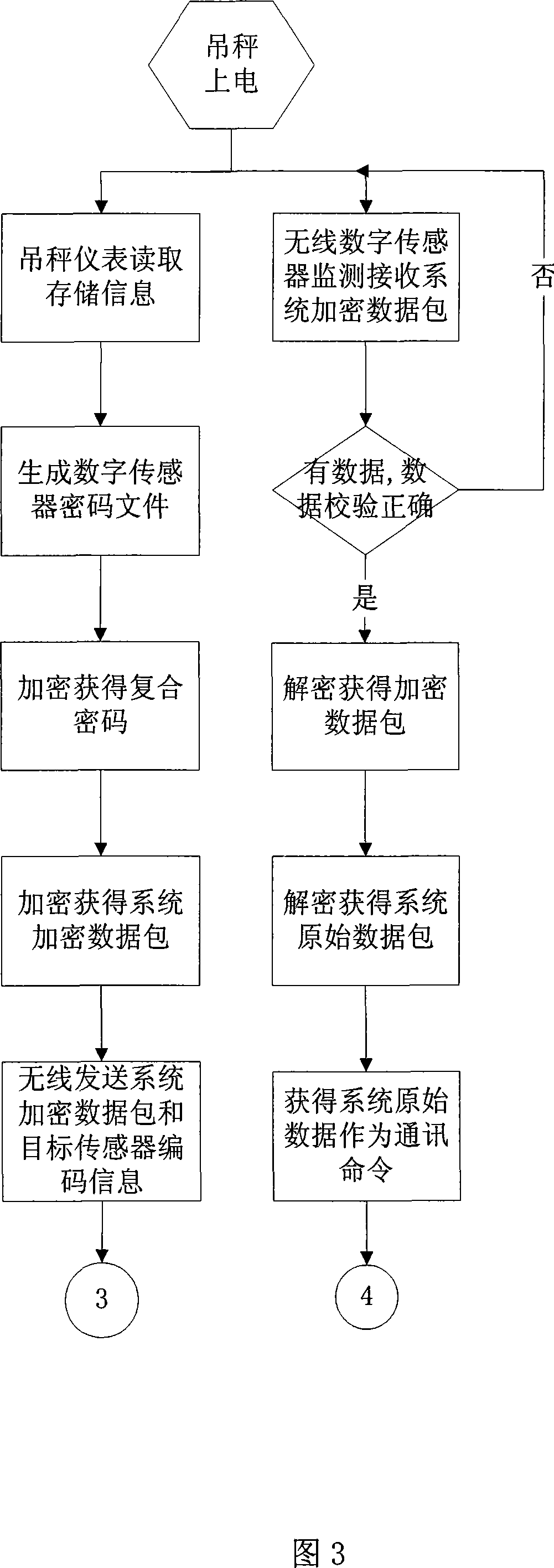
Weighing system communication method based on digital sensor
ActiveCN101140692AAvoid inaccuraciesGuaranteed accuracy and reliabilityTransmission systemsSecuring communicationComputer hardwareData stream
The invention relates to a communication method for weighing system based on digital sensor, which requires files building of a key and its password on release date as well as a key for digital sensor. The process of the said method is that: firstly, the key and its password for the storage system of the weighing instrument are downloaded to the digital sensor, from which the key and its password on release date can be obtained; secondly, the weighing instrument sends the communication orders to the target digital sensor, and the encrypted data packet, encrypted and generated through key files of digital sensor, data flow and system cipher, is sent to the target digital sensor; thirdly, after monitoring and receiving the packet, the target digital sensor will make a deciphering and recovery to obtain the system raw data by system key and key on release date, and then take it as the communication order; fourthly, after receiving the communication order, the target digital sensor will make a data packet of the sampled weights, and the data packet, the key on release date and the system cipher, encrypted and generated as the release encrypted data packet, will be sent to the weighing instrument; lastly, after monitoring and receiving the release encrypted data packet, the weighing instrument will make a encryption to obtain the weight data by system cipher and key on release date. Thus the transmission and communication of weight data is achieved. The invention ensures a security and reliability of the channels for weight data transmission.
Owner:METTLER TOLEDO CHANGZHOU PRECISION INSTR +2
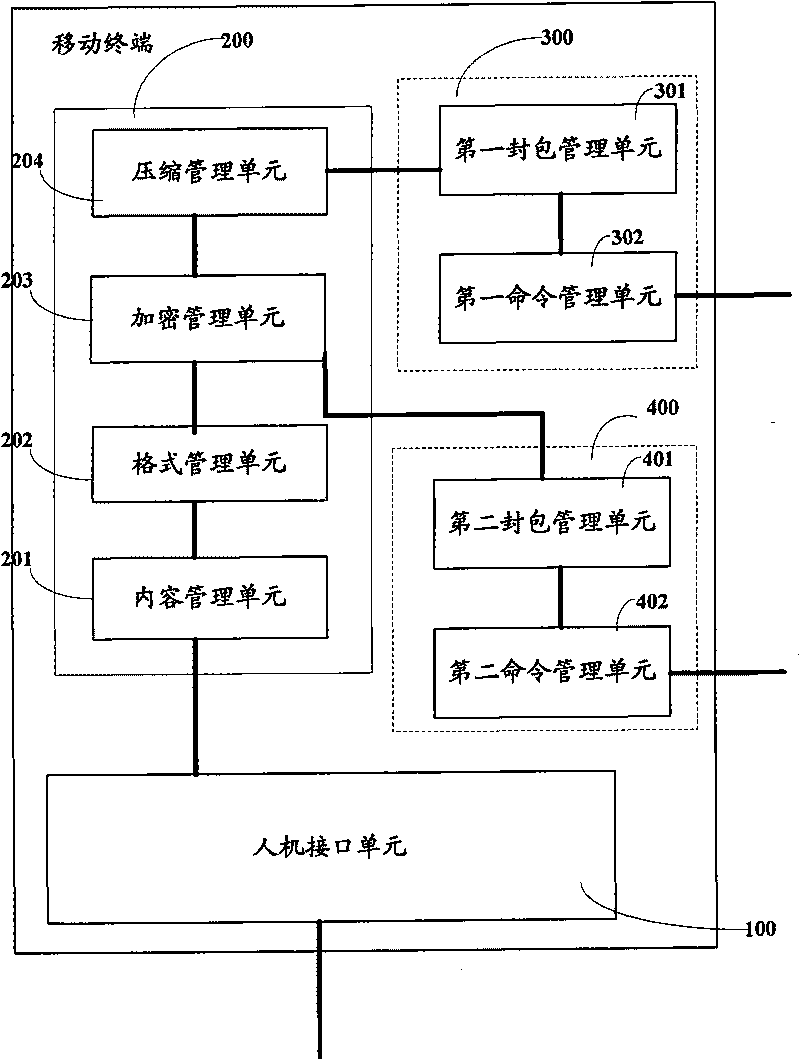
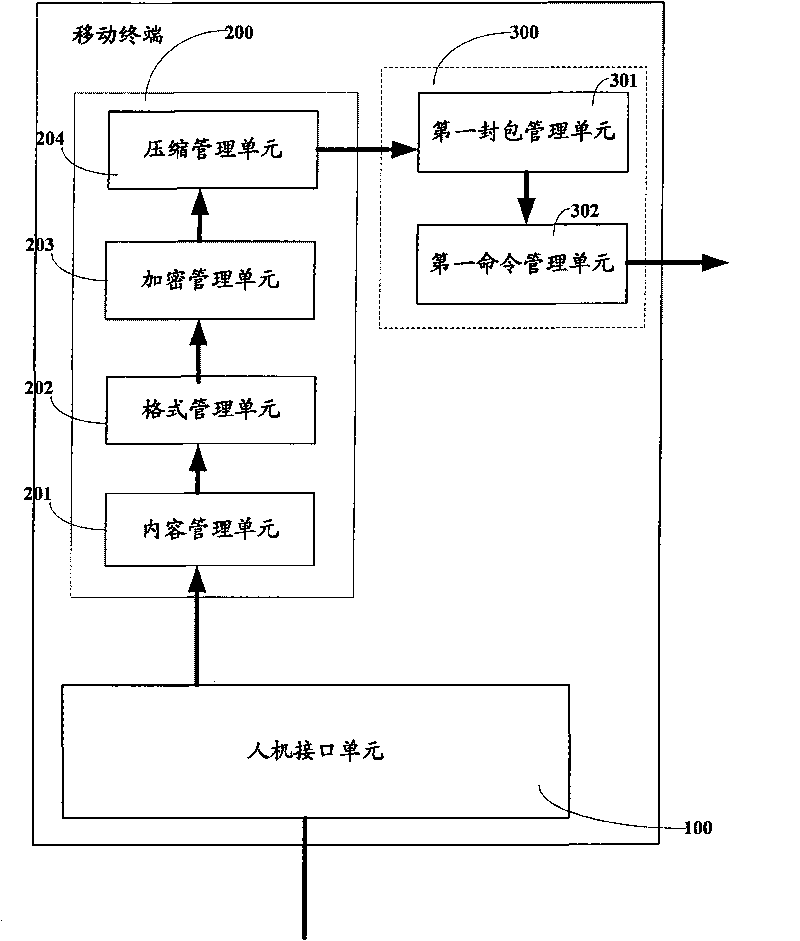
Mobile terminal, method and server for realizing data management
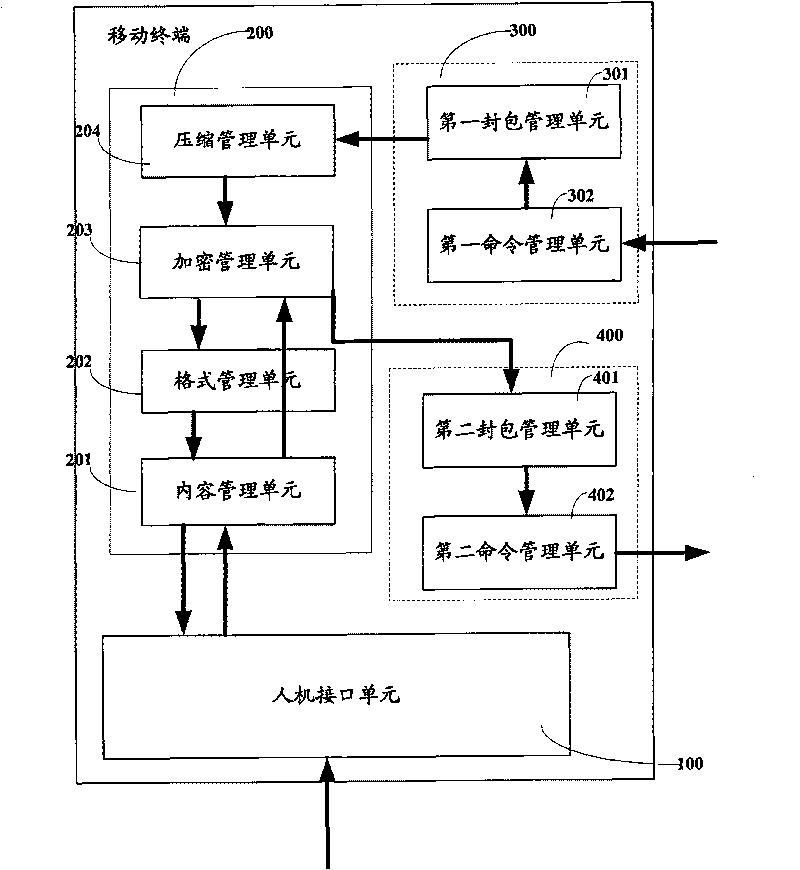
InactiveCN101730297AEnsure security and confidentialityImprove experienceSubstation equipmentWireless communicationManagement unitConfidentiality
The invention provides a mobile terminal, a method and a server for realizing data management. The mobile terminal comprises a human-computer interface unit, a data management unit and a multimedia information service unit, wherein the human-computer interface unit is used for inputting a backup command and extracting data to be backed up from data information in the mobile terminal according to the backup command; the data management unit is used for preprocessing the data to be backed up after receiving the data to be backed up from the human-computer interface unit; and the multimedia information service unit is used for encapsulating the preprocessed data to be backed up into a multimedia information service message body and transmitting the multimedia information service message body in which the preprocessed data to be backed up is encapsulated to the server. The embodiment of the invention has the following advantages that: data backup technology and data recovery technology provided by the invention can be realized across platforms on different mobile terminals, which sufficiently ensure the security and confidentiality of the data, and simultaneously, provides a variety of selections for manufacturers and enhances user experience.
Owner:北京摩软科技有限公司
Independent link type communication processing method and system based on isolated IP (Internet Protocol) address
ActiveCN106027491AReduce management costsSuppression of broadcast stormsTransmissionProtocol for Carrying Authentication for Network AccessIp address
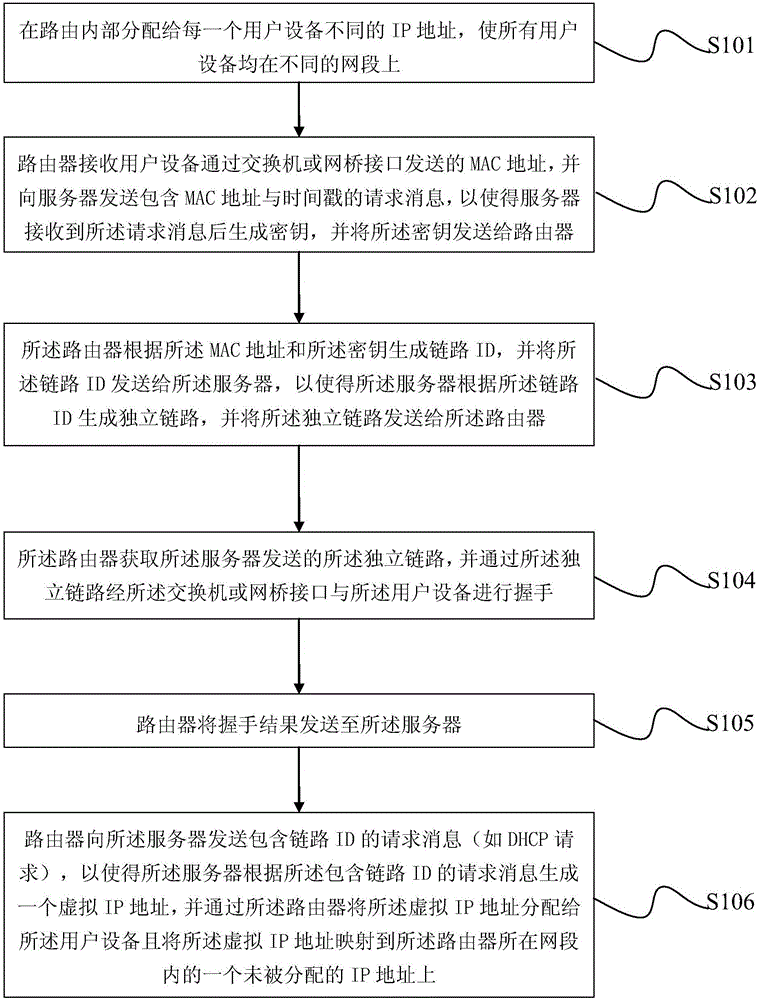
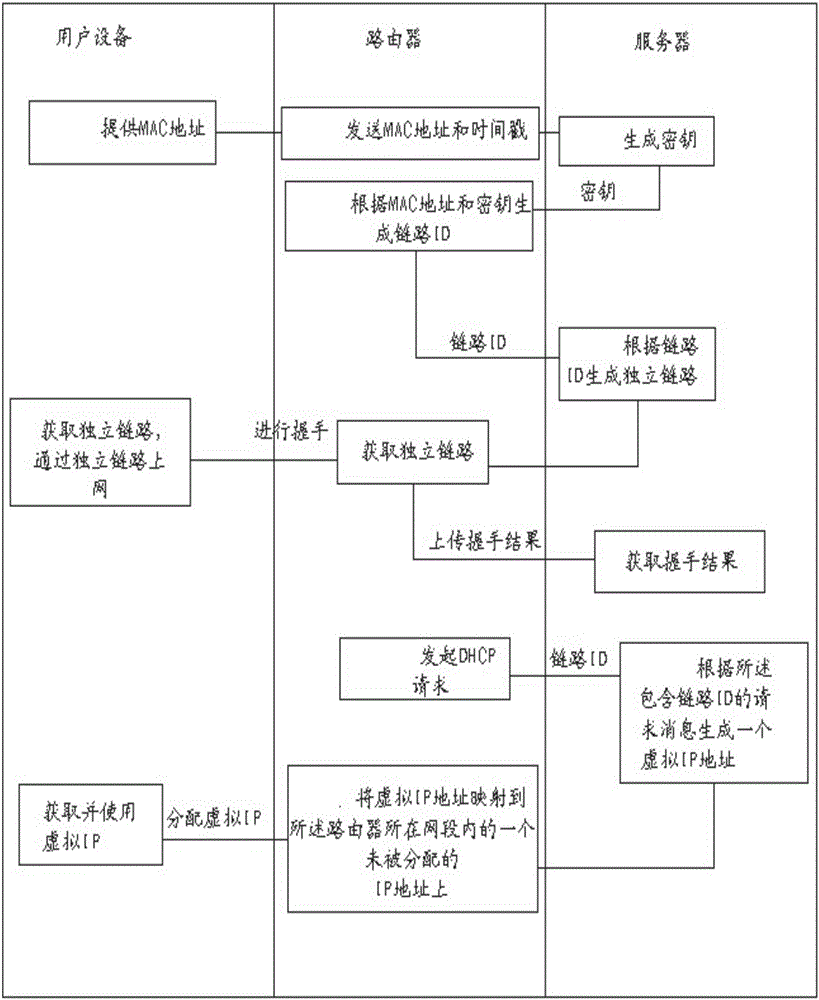
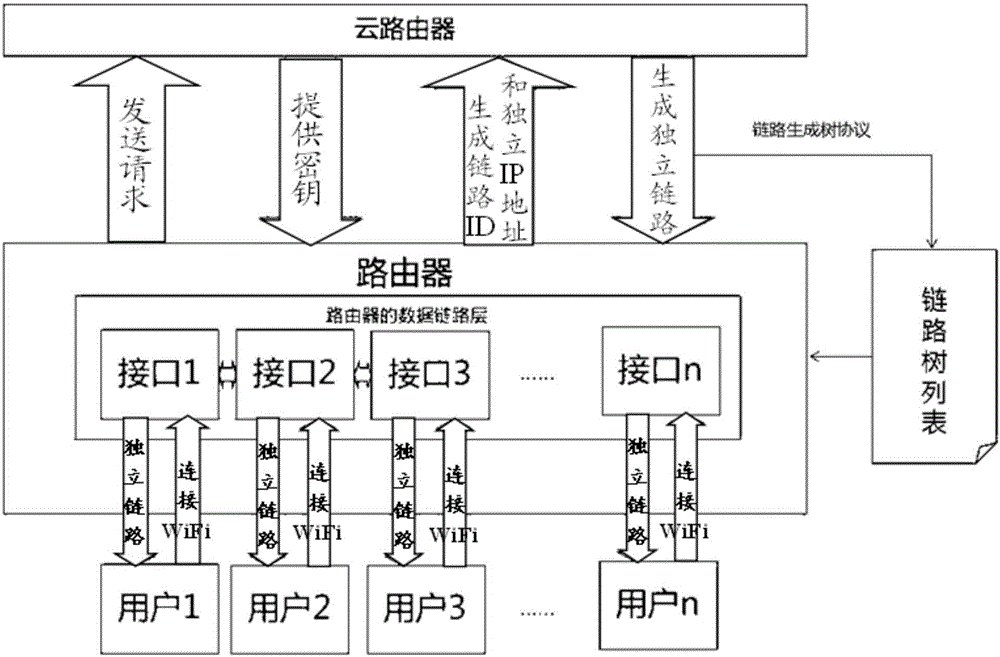
The invention discloses an independent link type communication processing method based on an isolated IP (Internet Protocol) address. The method comprises the following steps: allocating different IP addresses to user equipment inside a router in order that all the user equipment is on different network segments; and configuring link generating tree protocols on switches and / or network bridge interfaces between the router and the user equipment. Through adoption of the independent link type communication processing method, communications in network segments among users are blocked completely, and the security is enhanced. Moreover, through the link generating tree protocols, the flexibility and security of network connections are enhanced; broadcast storm is restrained; and the network stability and reliability are enhanced.
Owner:TIANJIN ZANPU TECH
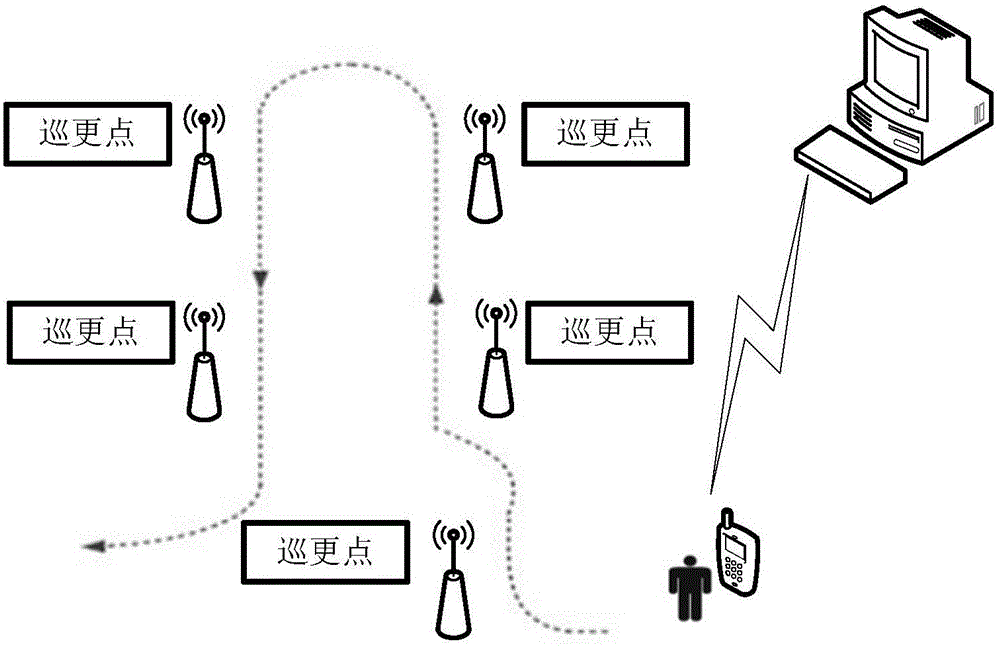
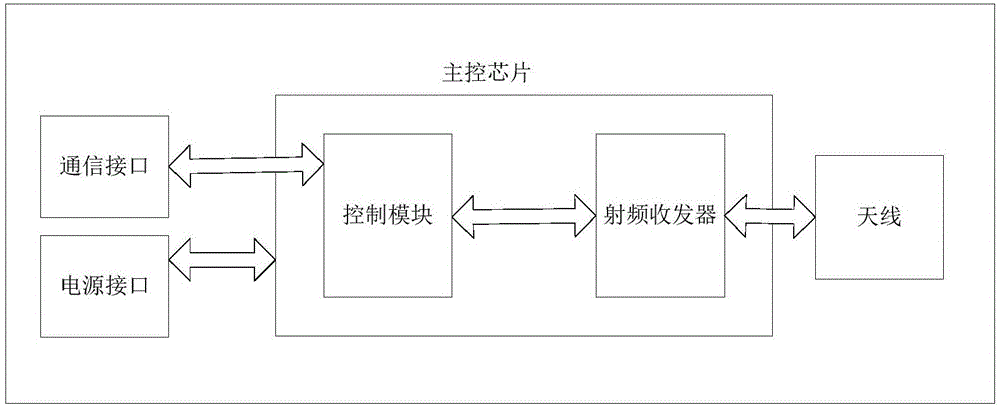
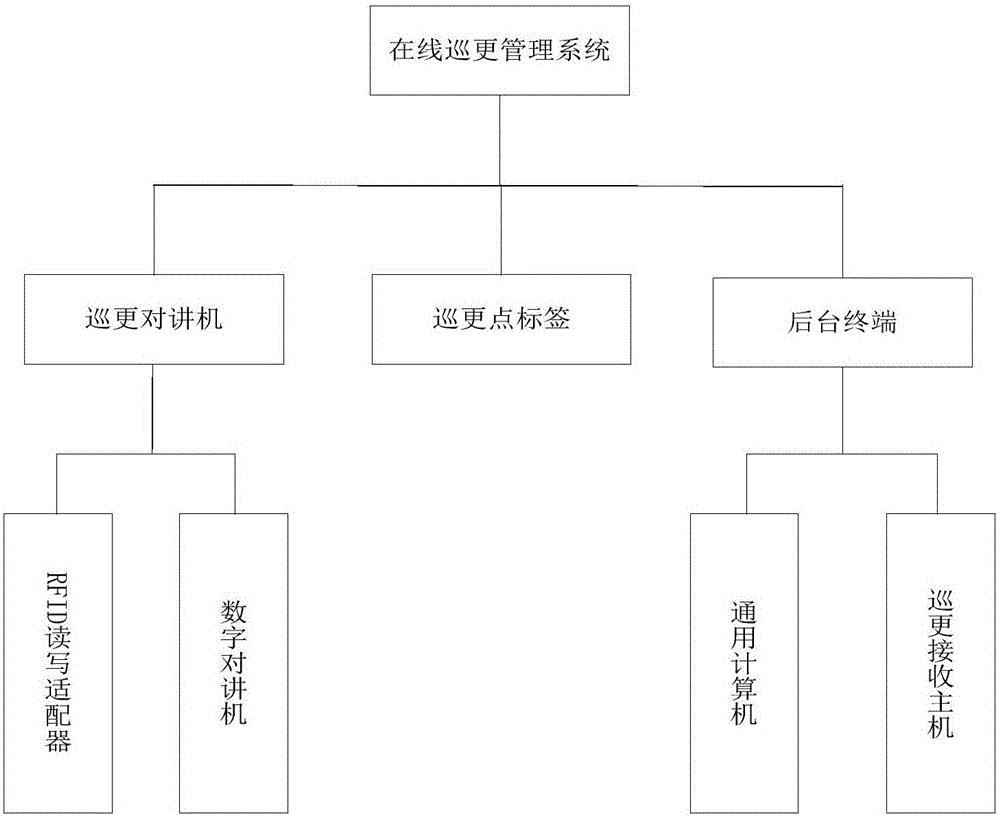
Online patrol management system
InactiveCN106710022ARealize scientific managementEasy to viewChecking time patrolsCo-operative working arrangementsComputer terminalReal time display
The present invention provides an online patrol management system including a patrol interphone, a patrol point label and a backstage terminal, the patrol interphone and the patrol point label are in wireless connection; the patrol interphone and the backstage terminal are in wireless connection; the patrol point label is arranged on a patrol route, and is used for marking patrol point information; the patrol interphone is used for receiving the patrol point information of the patrol point label, and sending the patrol point information to the backstage terminal, and the backstage terminal is used to collect the patrol point information and display supervision in real time. The online patrol management system adopts RFID technology, wireless data transmission technology, database information management technology and the like to achieve access of the patrol point information and real-time sending of the patrol point information to the backstage terminal, and the online patrol management system has the advantages of no wiring, easy installation, convenient operation, portability, stable performance and the like, and is not affected by humidity, temperature and normal working range, and system expansion and line change are easy to maintain.
Owner:SHANGHAI WULING SHENGTONG INFORMATION TECH CO LTD
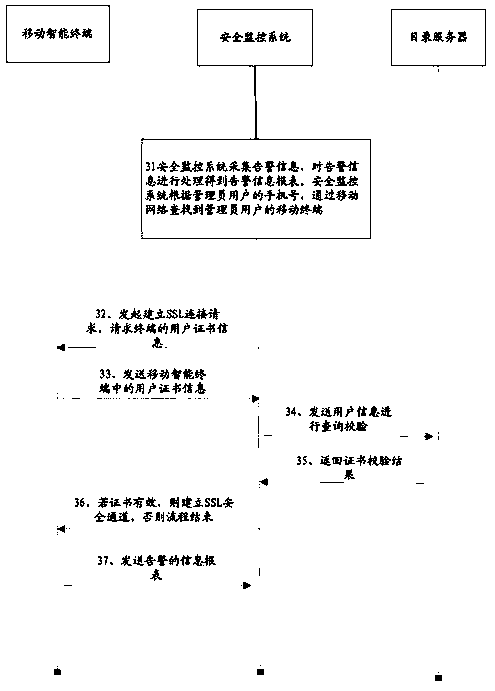
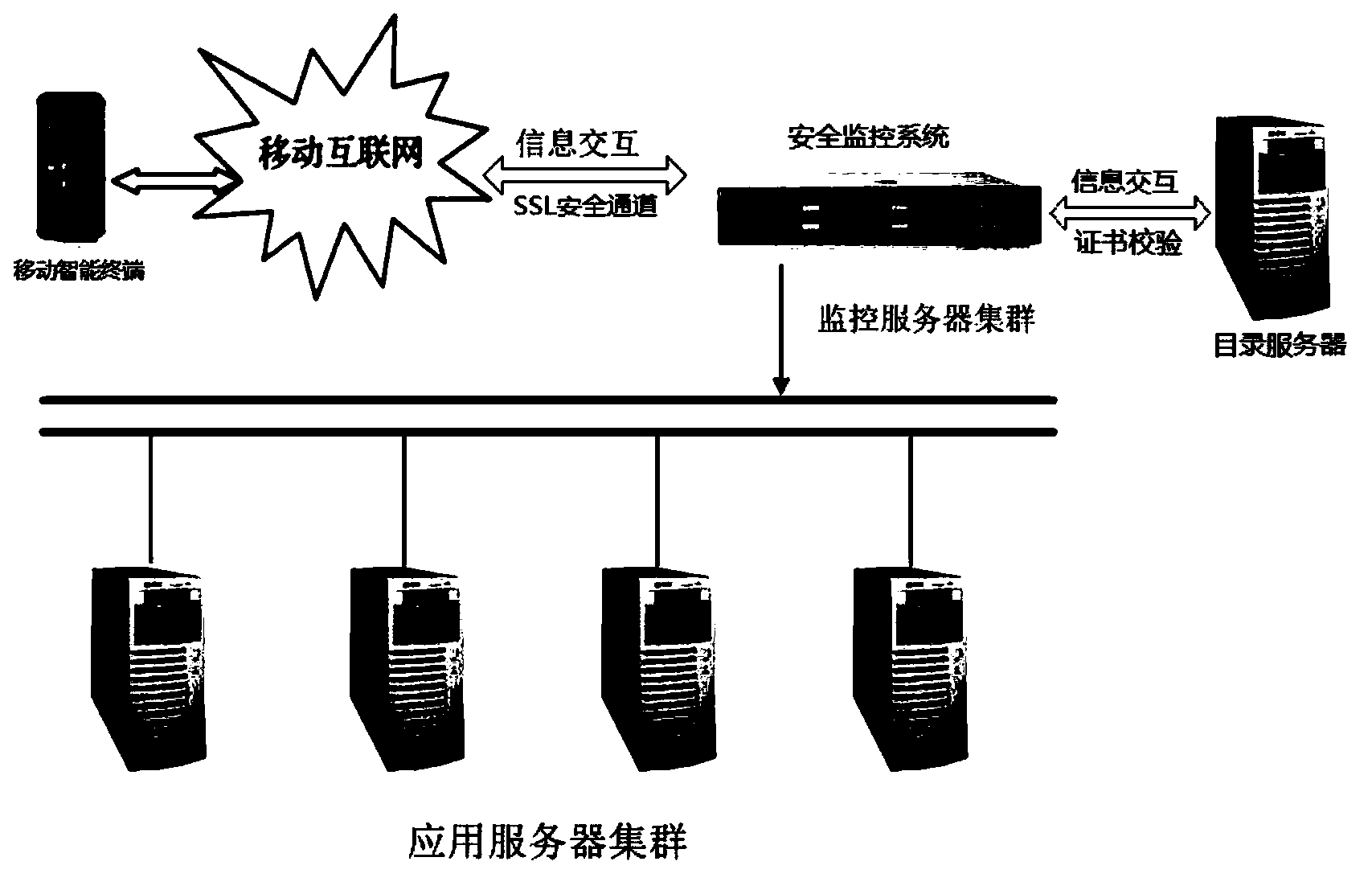
WPKI security monitoring and control method and system based on mobile terminal
InactiveCN103906050AEnsure security and confidentialityCommunication securitySecurity arrangementEncryptionConfidentiality
The embodiment of the invention provides a WPKI security monitoring and control method and system based on a mobile terminal. The method mainly includes the steps that the mobile terminal of a user sends a connection request to the security monitoring and control system, wherein the connection request carries digital certificate information of a user terminal; the security monitoring and control system verifies a digital certificate of the user terminal through a catalog server and returns a connection response to the mobile terminal after the digital certificate passes verification; an SSL connection channel is set up between the mobile terminal and the security monitoring and control system through the digital certificate, an operation inquiry request is sent to the security monitoring and control system through the SSL connection channel, and the security monitoring and control system returns an information report to the mobile terminal through the SSL connection channel. According to the method and the system, encryption is conduced on transmitted data in a wireless network, security and confidentiality of information are ensured, and user information can not be obtained or tampered by lawbreakers even under the condition that the user information is cut out by the lawbreakers.
Owner:AEROSPACE INFORMATION
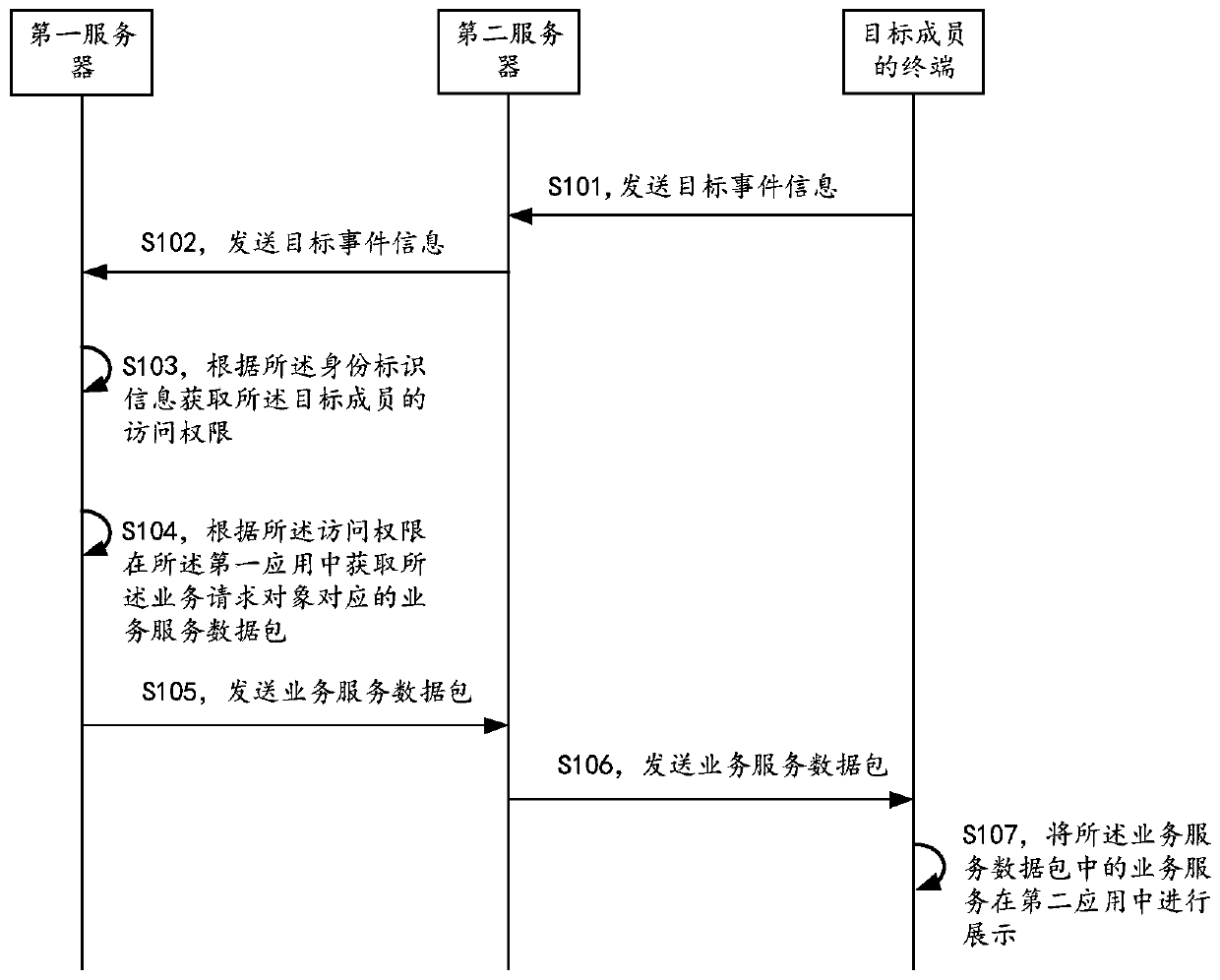
Application interaction processing method and device
ActiveCN111352740AEnsure security and confidentialityWays to enrich messagesInterprogram communicationDigital data protectionData packBusiness enterprise
The embodiment of the invention discloses an application interaction processing method and device, and the method comprises the steps: enabling a first server corresponding to a first application to obtain target event information sent by a second server corresponding to a second application, wherein the target event information comprises a service request object based on the first application andthe identity information of a target member; obtaining an access permission of the target member according to the identity identification information, and obtaining a service service data packet corresponding to the service request object in the first application according to the access permission; sending the service service data packet to a second server, so as to enable the second server to forward the service service data packet to a terminal of a target member corresponding to the second application; and transmitting the service data associated with the service service data packet to theterminal of the target member through the second server. By adopting the method and the system, the enterprise internal information can be published to enterprise internal members, so that the privacy and the security of the enterprise internal information are guaranteed.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Digital anticounterfeiting system and method based on IP telephone operation system
InactiveCN101483686ASecurity and Confidentiality GuaranteeImprove anti-counterfeiting reliabilityData processing applicationsPrepayment telephone systemsSpeech soundComputer module
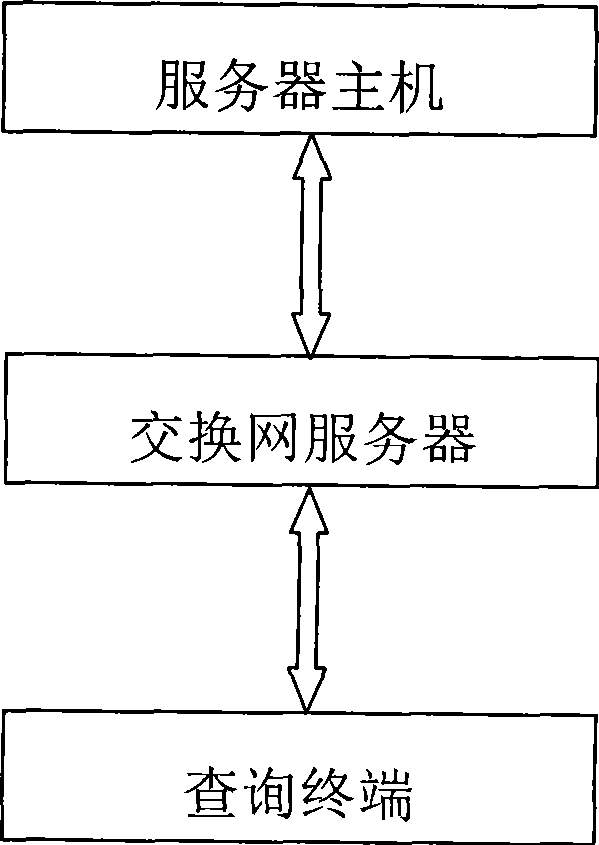
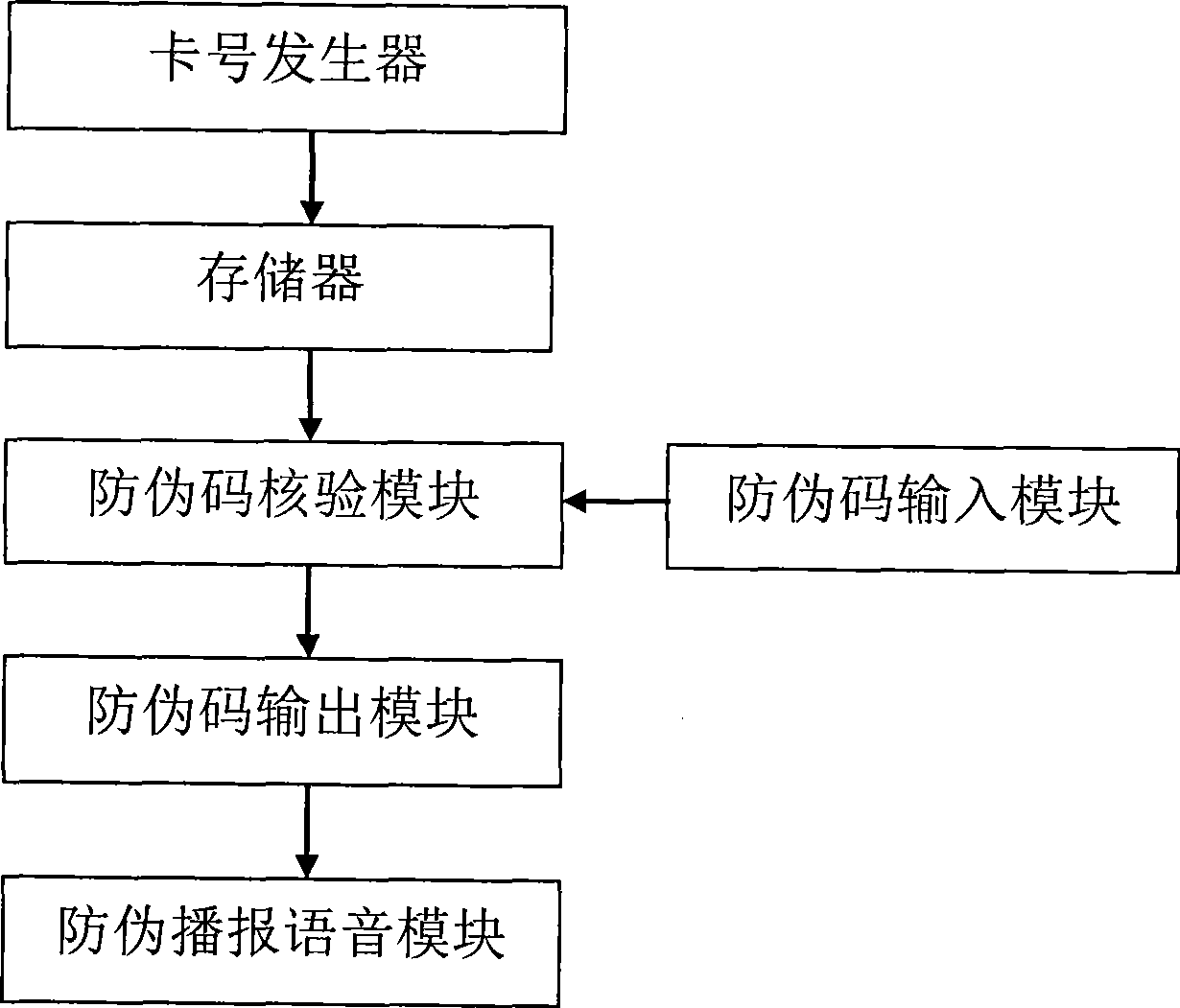
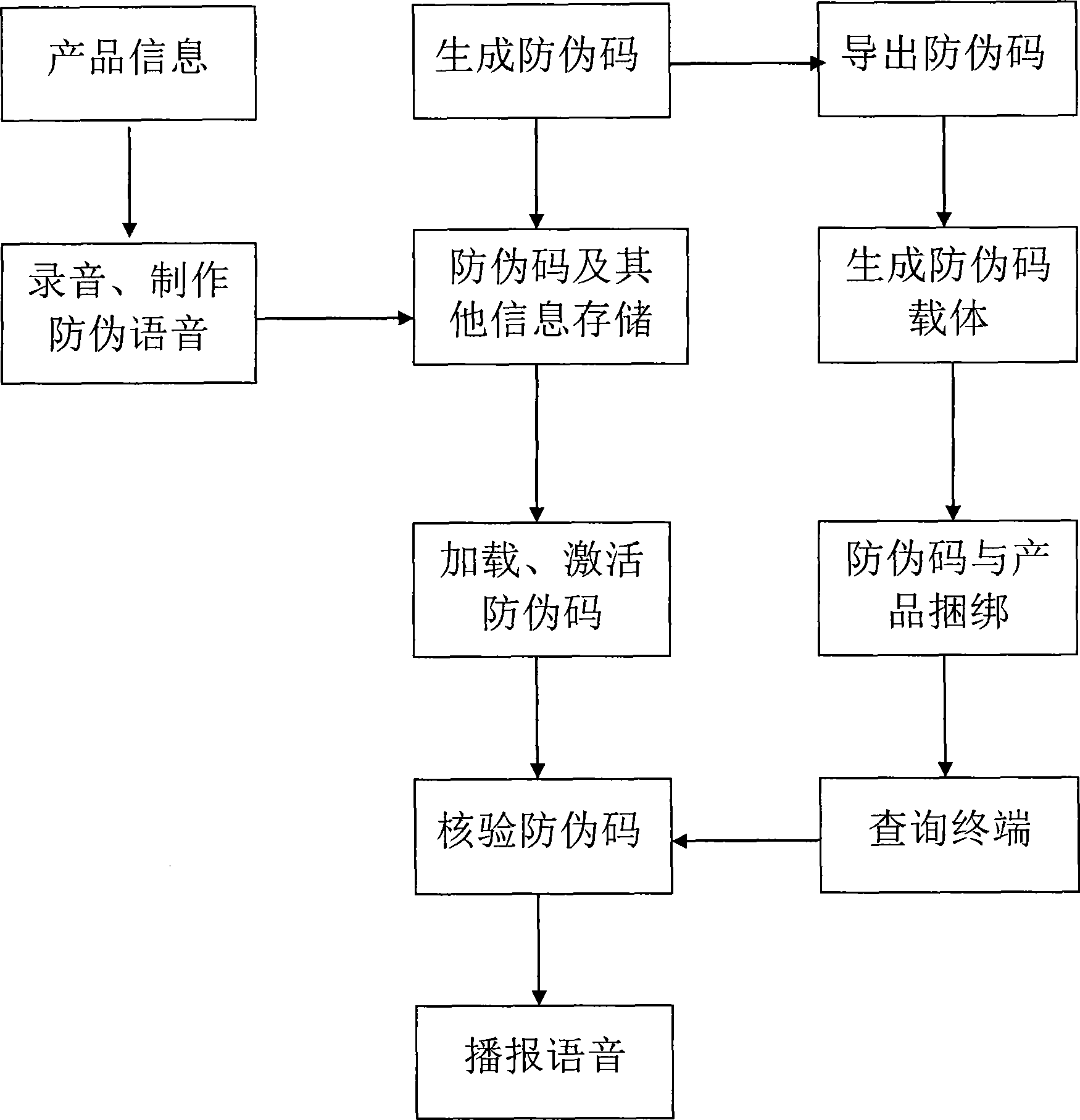
The invention discloses a system and method having double verification anti-fake based on IP telephone operation system, which is easy to operate and verify but not easy to be copied by fake producers. Anti-fake codes and anti-fake face values of products are firstly generated in the IP telephone operation system, and then the enter inquiry verification for the anti-fake codes and the check verification for the anti-fake face values and the information of products are carried out by dialing the IP telephone according to the anti-fake codes and anti-fake face values of products. The system comprises an inquiry terminal, a switching network server and a server host; the inquiry terminal is connected with the server host via the switching network server; and the server host comprises a card number generator for generating and exporting the anti-fake codes and anti-fake face values, a memory, an input and output module for anti-fake codes, a verification module for anti-fake codes, and a voice module for anti-fake reporting.
Owner:杭州华科通信设备有限公司
Method of encrypting control signaling
InactiveCN102100030AEffective securityEnsure security and confidentialityData stream serial/continuous modificationRadio transmission for post communicationControl signalEngineering
A method of protecting control signaling transceived between a mobile station and a base station in a wireless access system is disclosed. And, a method of encrypting control signals selectively is disclosed. The present invention defines new control signal encryption key (CSEK) and group control signal encryption key (GCSEK) for encrypting a control signal and discloses methods of protecting a control signal using the control signal encryption keys. Moreover, although the new control signal encryption key and the like are not used, the present invention efficiently protects control signaling by selectively encrypting control signals.
Owner:LG ELECTRONICS INC
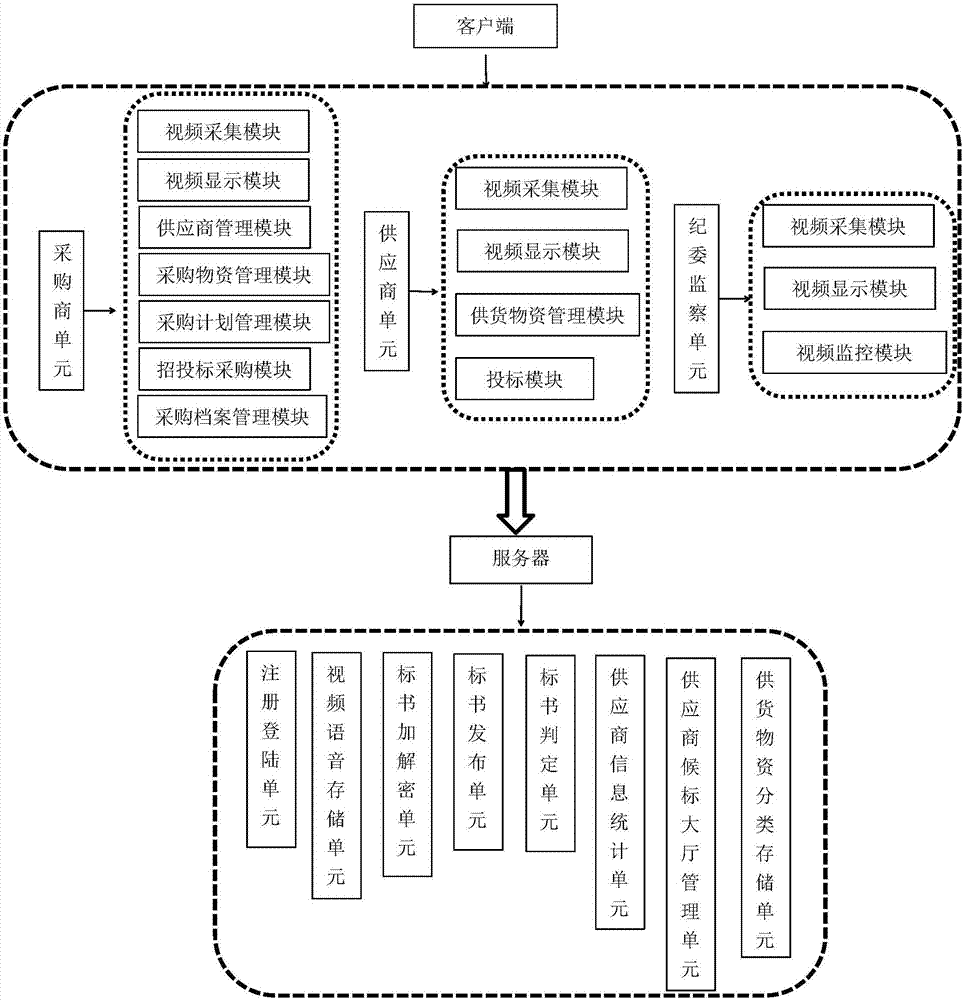
Remote audio and video technology-based e-commerce purchase management platform
ActiveCN107516266AEnsure security and confidentialityImprove procurement efficiencyKey distribution for secure communicationDigital data protectionMaterial classificationManagement unit
The invention discloses a remote audio and video technology-based e-commerce purchase management platform. The platform is characterized by comprising a client and a server, wherein the client comprises a purchaser unit, a supplier unit and a supervision unit; and the server comprises a registration login unit, a video and voice storage unit, a bidding document encryption and decryption unit, a bidding document release unit, a bidding document judgment unit, a supplier information statistics unit, a supplier bidding hall management unit and a supplied material classification storage unit. An electronic bidding document of the platform uses an asymmetric encryption and decryption algorithm, a CA authentication encryption and decryption algorithm and an electronic signing algorithm; a bid inviter can remotely control the electronic bidding document to be decrypted during bid opening; a supplier inserts a CA Key for performing verification and decryption; after the electronic bidding document is encrypted, the security of a bidding process can be ensured; and the supplier and a purchaser of the platform perform communication negotiation through videos and voices, so that the purchase efficiency can be improved.
Owner:合肥明信软件技术有限公司
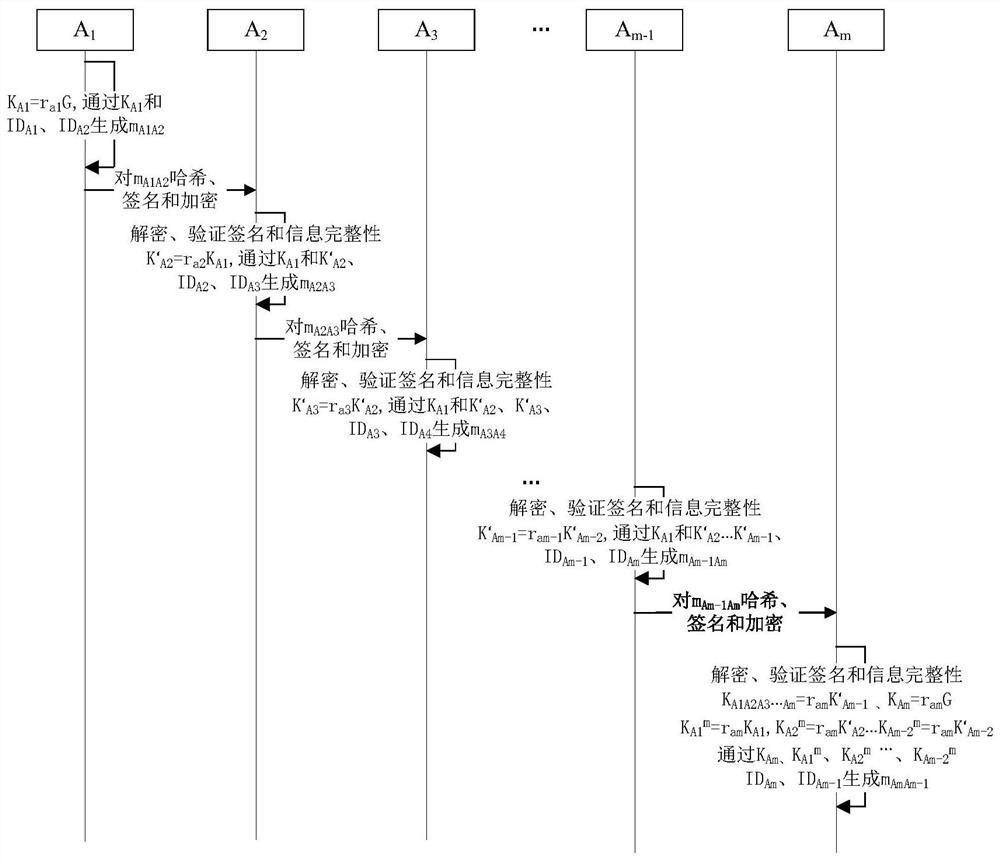
Method and system for realizing multi-party key agreement
ActiveCN112422276AEnsure security and confidentialityPrevent replay attacksKey distribution for secure communicationEncryption apparatus with shift registers/memoriesConfidentialityDiscrete logarithm
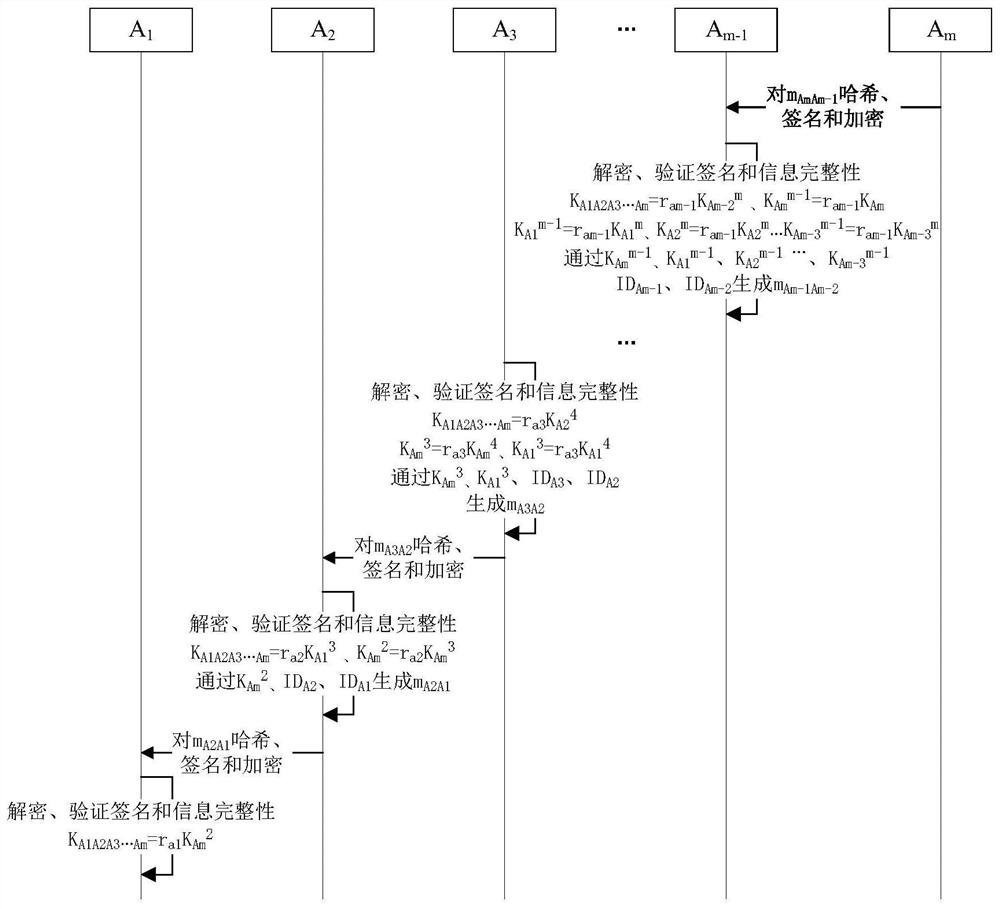
The invention provides a method and a system for realizing multi-party key agreement. The method comprises the following steps that: after generating a key parameter, a member A1 generates key negotiation information with member information and sends the key negotiation information to a member A2; the member A2 generates random number calculation, generates key agreement information with the member information and sends the key agreement information to the member A3; continuously, the member Am generates a random number to calculate and obtain a secret key; key agreement information is generated through calculation and the member information and sent to the member Am-1; and in this way, the key negotiation information is sequentially transmitted, and the final member A1 calculates to obtain the key. According to the method, key agreement of multiple members can be effectively realized, a safe elliptic curve is selected, and on the basis of the safe elliptic curve, the security and confidentiality of key parameters in the communication process can be effectively ensured through the difficulty in solving discrete logarithms on the elliptic curve.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Secure and confidential offline software registration authorization method
InactiveCN109858202ASolve operational problemsTime consuming to solvePlatform integrity maintainanceProgram/content distribution protectionConfidentialitySoftware engineering
Confidential software products installed and used by a confidential host in a national security and confidentiality place basically need to be authorized and verified. The invention provides a secureand confidential offline software registration authorization method. Authorization software registration information can be managed at a management end in a unified manner, the whole process is physically isolated from a host, and the potential safety hazard that a storage medium is in direct contact with a secret-related machine in the authorization process is avoided. The security and confidentiality offline software registration authorization method comprises: when the software needs registration authorization, obtaining a unique identifier of the equipment, performing special splicing, reversible and irreversible encryption to generate a registration two-dimensional code, performing local analysis and identification on the two-dimensional code by using physical equipment, performing analysis and decryption by using a management end, performing encryption by using a private algorithm to generate a registration code, and inputting the registration code by the software to perform registration verification authorization; when software needs to migrate or replace hardware equipment, a logout two-dimensional code is generated through encryption, the two-dimensional code is locally analyzed and recognized through physical equipment, a management end analyzes and recovers software authorization, the hardware equipment is migrated or replaced after success, and the hardware equipment can be reused after re-registration.
Owner:JIANGSU BOZHI SOFTWARE TECH CO LTD
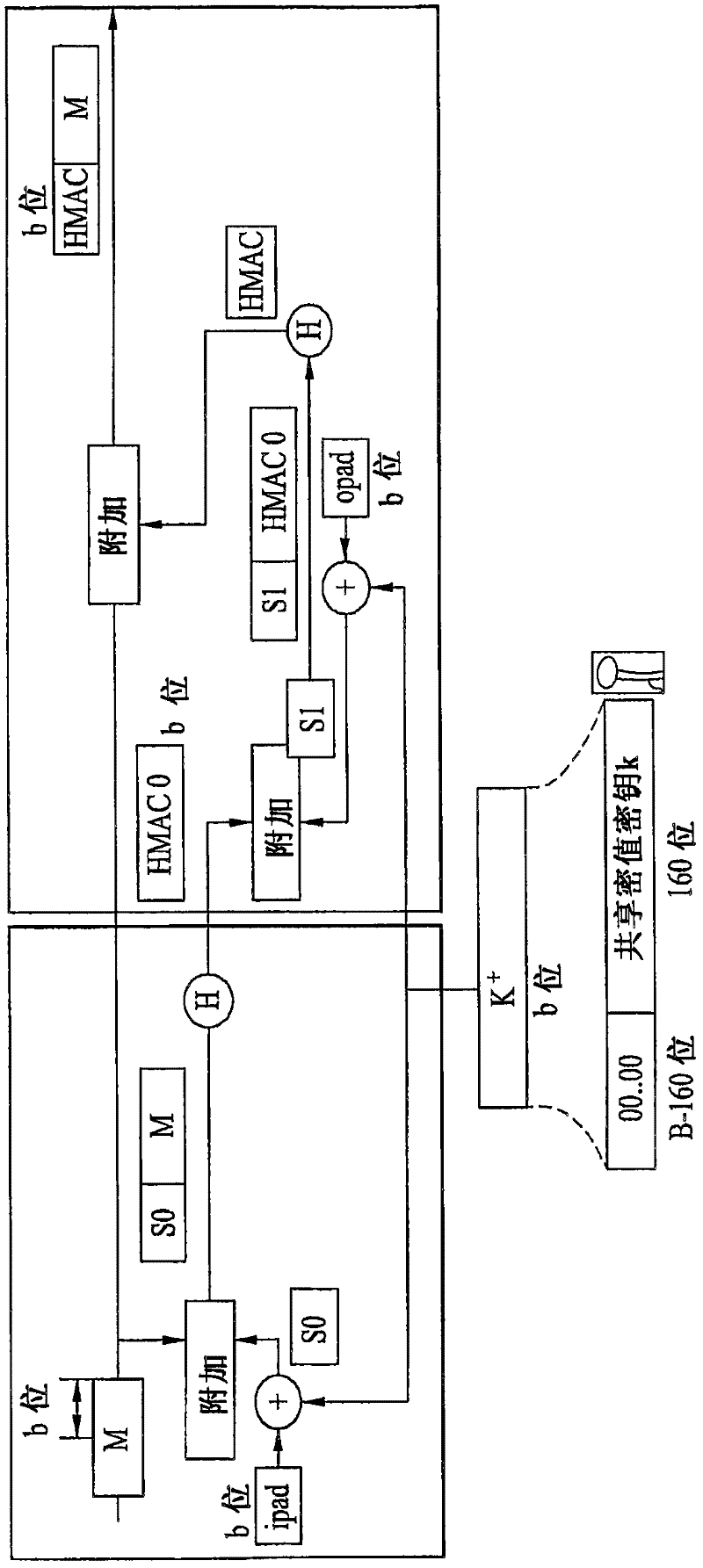
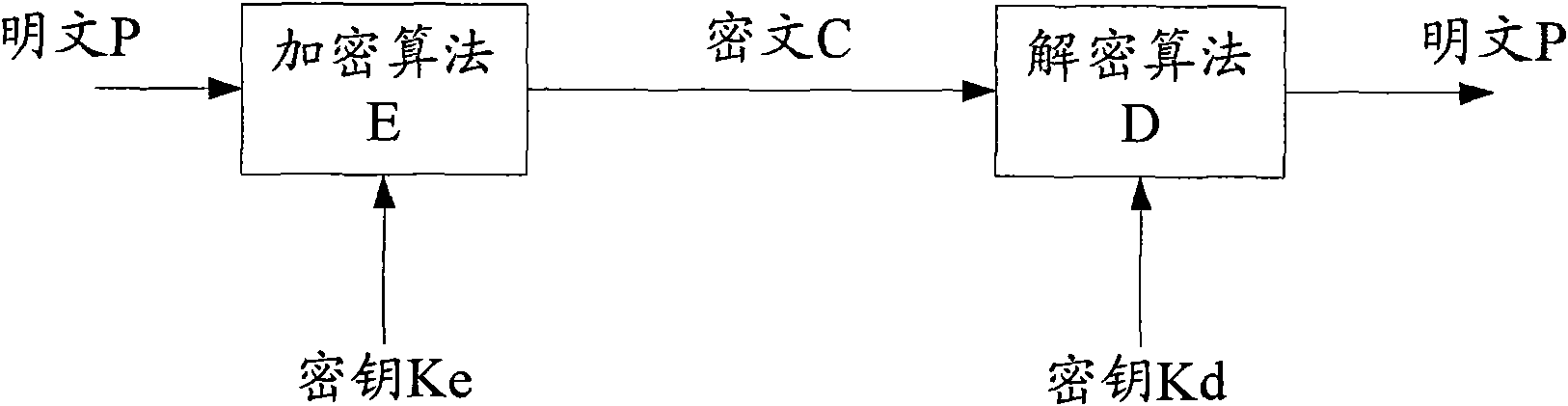
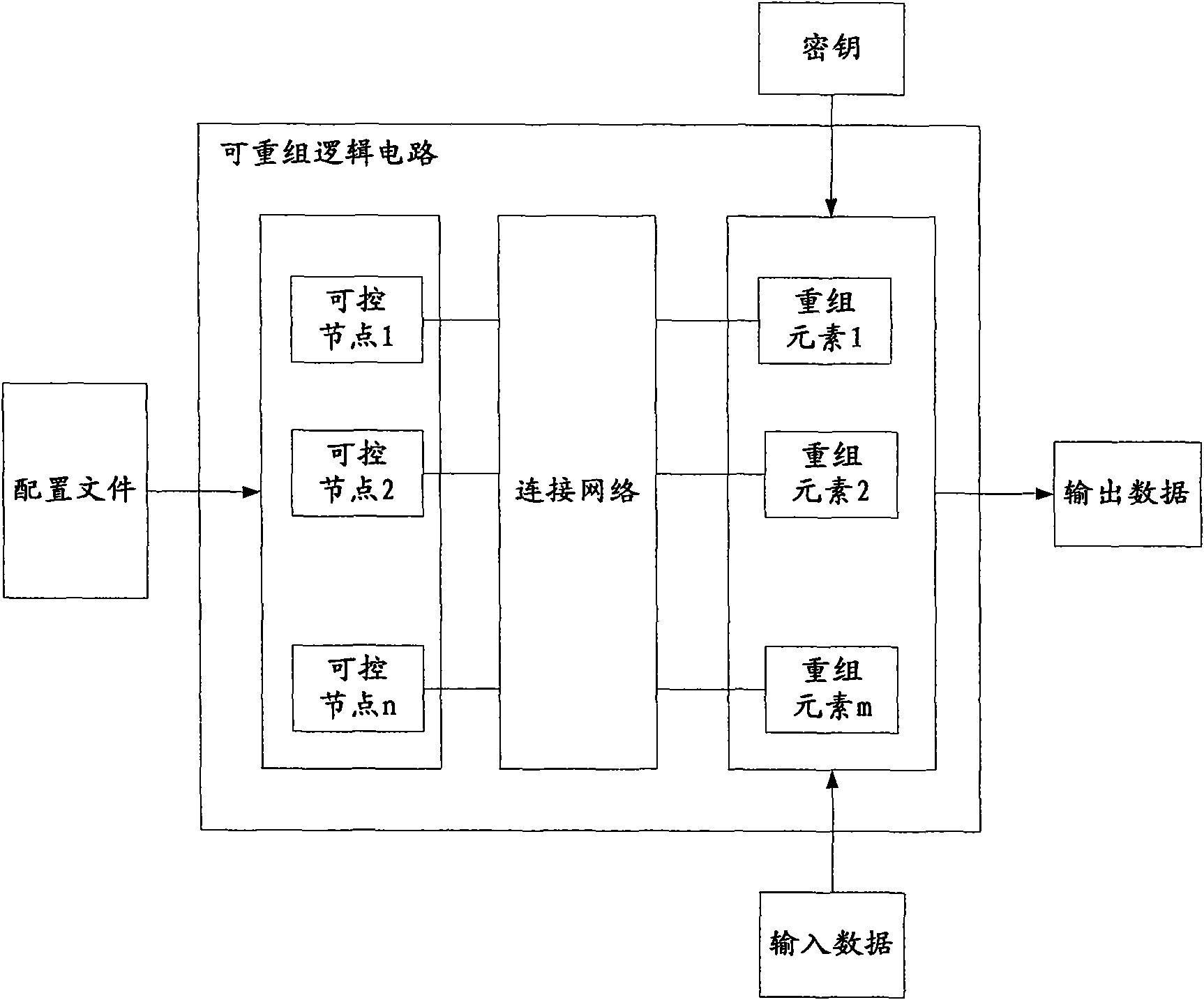
Encrypted communication method, encrypted/decrypted communication device, encryption device and decryption device
InactiveCN101997674AImprove securityEasy to replaceEncryption apparatus with shift registers/memoriesPublic key for secure communicationComputer hardwareCommunication device
The invention discloses an encrypted communication method, an encrypted / decrypted communication device, an encryption device and a decryption device which can enhance the security of encrypted communication. In the encrypted communication method, a first device is provided with a first reconfigurable logic circuit, a second device is provided with a second reconfigurable logic circuit, the first reconfigurable logic circuit and the second reconfigurable logic circuit have the same structure, and an encryption configuration file and a decryption configuration file for realizing a cryptographic algorithm are determined between the first device and the second device; the first device controls the first reconfigurable logic circuit according to the encryption configuration file to constitute an encryption logic circuit, encrypts data by utilizing the encryption key and the encryption logic circuit, and transmits the encrypted data to the second device; and the second device receives the encrypted data from the first device, controls the second reconfigurable logic circuit according to the decryption configuration file to constitute the decryption logic circuit, and decrypts the decryption data by using a decryption key and the decryption logic circuit.
Owner:BEIJING DUOSI TECH DEV
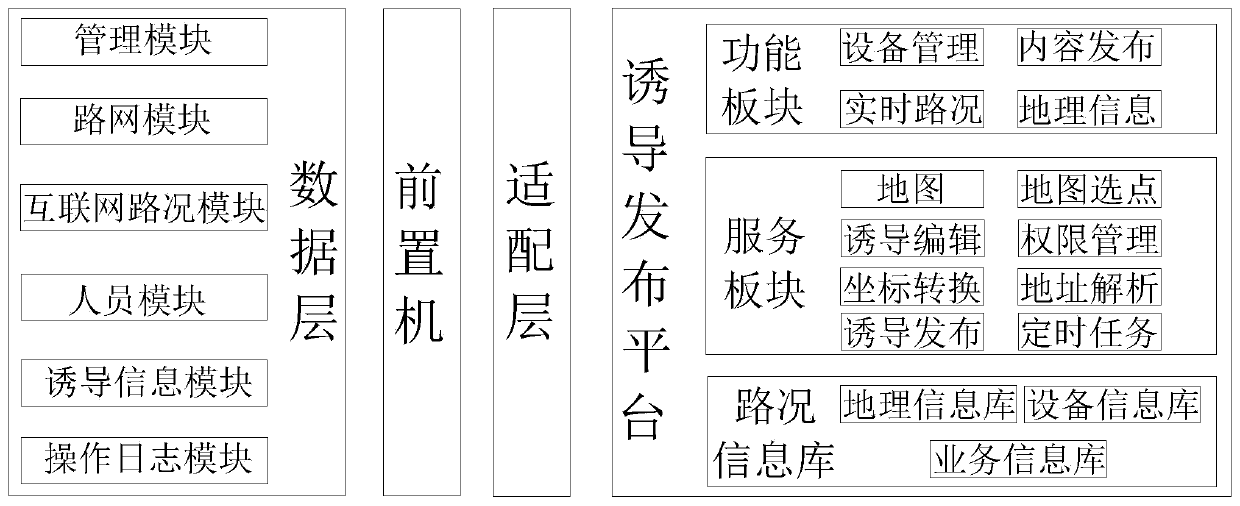
Traffic guidance information publishing system with standardized interface
InactiveCN111462494AEnsure security and confidentialityDetection of traffic movementTransmissionCollection analysisData transport
The invention discloses a traffic guidance information publishing system with a standardized interface. The traffic guidance information publishing system comprises a data layer, a front-end processor, an adaptation layer and a guidance publishing platform. The front-end processor comprises a plurality of data acquisition devices and an induction publishing device. The data layer collects trafficroad condition data through the plurality of data acquisition devices. The adaptation layer performs standardized connection on the data layer and the induction publishing platform through a data transmission protocol. The induction publishing platform performs fusion processing on the traffic road condition data acquired by the data layer to generate comprehensive traffic information, and publishes the traffic information through an induction publishing device. According to the invention, a traditional traffic guidance information publishing system and a data acquisition and analysis system are integrated, one-stop management of acquisition, analysis and publishing of traffic information is realized, and the system is high in reliability, good in maintainability and high in safety.
Owner:SUZHOU IND PARK SURVEYING MAPPING & GEOINFORMATION CO LTD
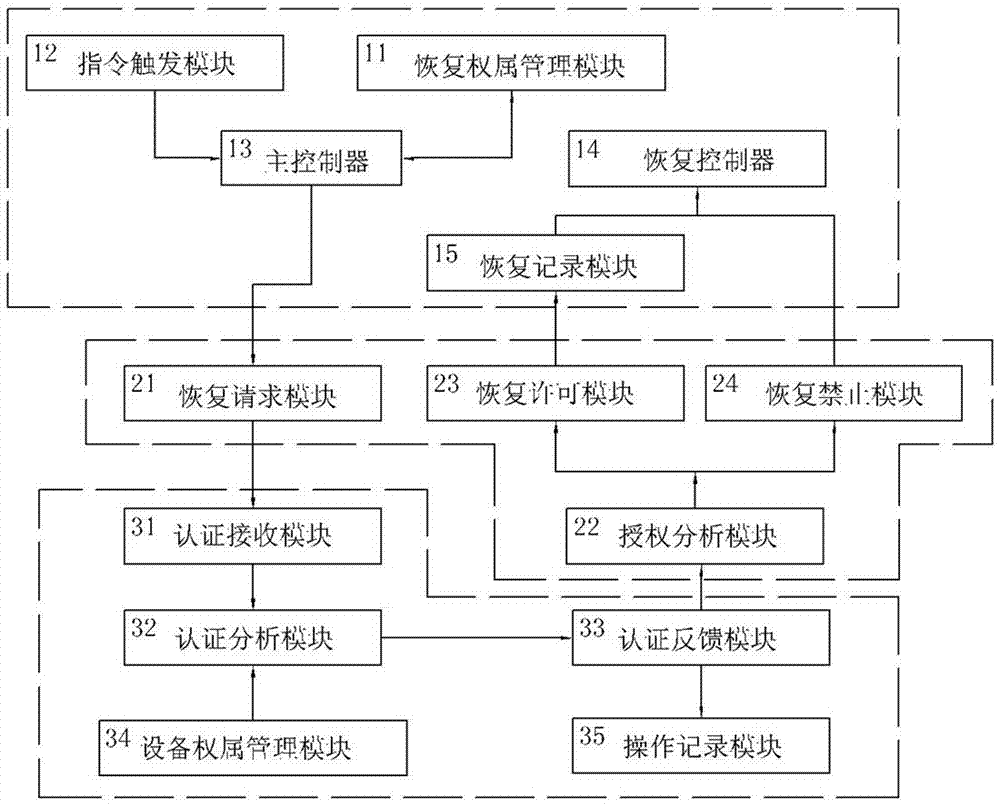
System for factory setting recovery of information safety equipment and method for same
InactiveCN107480485AEnsure security and confidentialityAvoid random tampering and deletionDigital data authenticationConfidentialitySafety Equipment
The invention discloses a system for factory setting recovery of information safety equipment and a method for the same. An instruction triggering module sends safety alarm information to a main controller when the module receives an operator's request for a factory setting recovery operation; the main controller collects a unique authentication code in an ownership recovery management module and sends the unique authentication code to a recovery authentication manager; the recovery authentication manager transmits the unique authentication code to a remote permission server by an authentication receiving module, and an authentication analysis module analyzes whether matching is successful; and finally, the recovery authentication manager acquires feedback information transmitted by an authentication feedback module, gives a result of authentication permission or authentication prohibition and decides whether factory setting recovery of the equipment needs to be conducted. The factory setting recovery system disclosed by the invention is characterized in that through remote running authentication, a malignant operator is prevented from conducting tampering and deletion at will without authentication, so that user's safety and confidentiality during use of the information safety equipment can be ensured.
Owner:深圳市波普安创技术有限公司
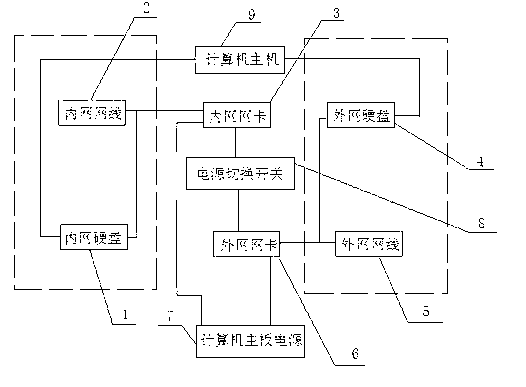
Network security isolating device
The invention discloses a network security isolating device, which comprises an intranet hard disk, an intranet wire and an intranet network card, wherein an extranet hard disk, an extranet wire and an extranet network card are additionally arranged in a computer mainframe; the extranet network card and the intranet network card are both connected with the power supply of a computer main board; and a power supply switch is arranged between the intranet network card and the extranet network card. The network security isolating device is simple in structure and very convenient to use, realizes physical isolation, can ensure the security and confidentiality of the system, and also facilitate the user of a user, so that the intranet and the extranet are switched in real time.
Owner:XUZHOU YINGDONG NETWORK TECH
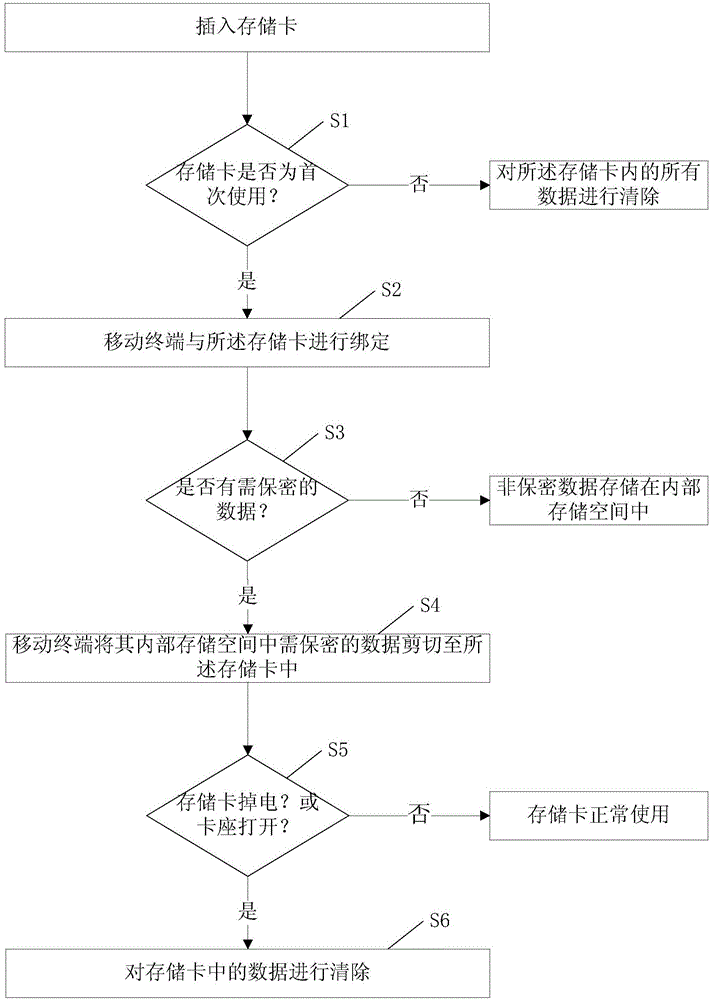
Data security method of memory card
InactiveCN104463032AEffective isolationEnsure security and confidentialityInternal/peripheral component protectionElectricityComputer terminal
The invention relates to a data security method of a memory card. The data security method includes that a mobile terminal acquires identity of the inserted memory card so as to judge whether the memory card is used for the first time or not, if yes, the mobile terminal can be bound with the memory card, if not, all data in the memory card can be eliminated; the mobile terminal can cut the data to be secured in the internal storage space into the memory card. When the mobile terminal monitors power failure of the memory card, the data in the memory card can be eliminated. By the data security method, data on the mobile terminal can be effectively isolated, and data security and safety are ensured.
Owner:GUANGZHOU YUXI INFORMATION TECH
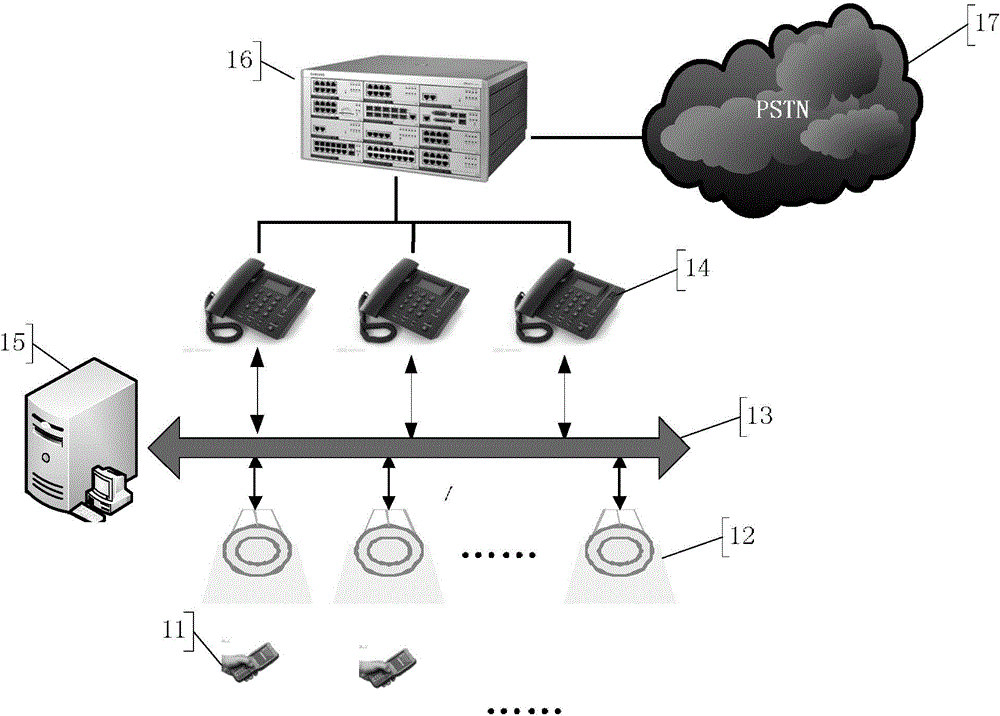
Cordless telephone system
ActiveCN104954584AReduce work delaysEnsure security and confidentialityCordless telephonesExchange networkTelephone network
A cordless telephone system comprises a house phone network formed by multiple telephones, a public phone switching network, a switch connected between the two networks and a visible light communication network, wherein each telephone is a child-mother telephone consisting of a mother telephone and a child telephone which are in wireless communication connection through the visible light communication network. According to the cordless telephone system, each mother telephone and the corresponding child telephone are communicated on the basis of the visible light communication network, so that security and secrecy of the communication can be guaranteed, and mobile connection can be realized on occasions such as underground facilities, mines, tunnels and the like where electromagnetic wave propagation is not facilitated.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
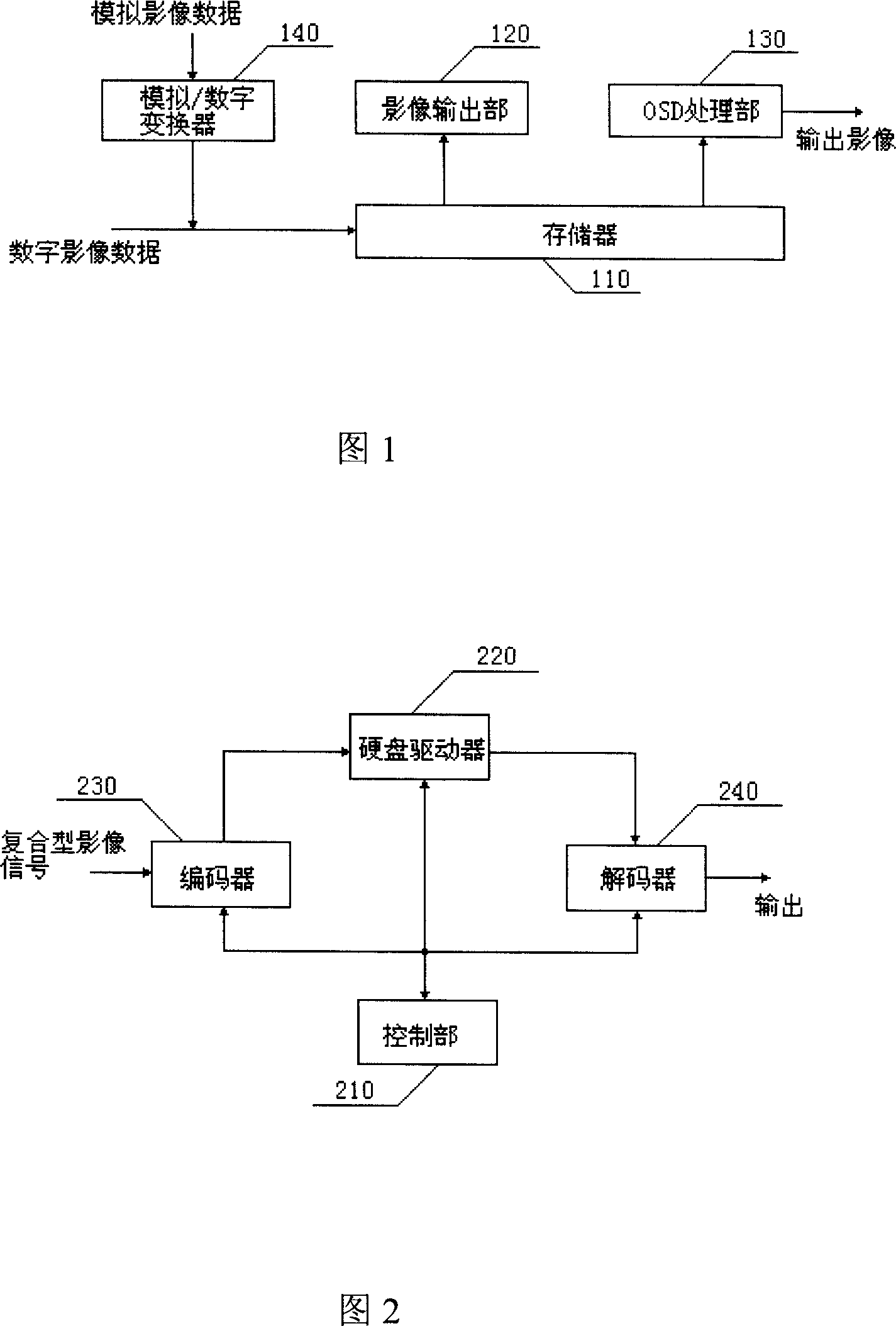
Apparatus for recording and playing composite image information and its method
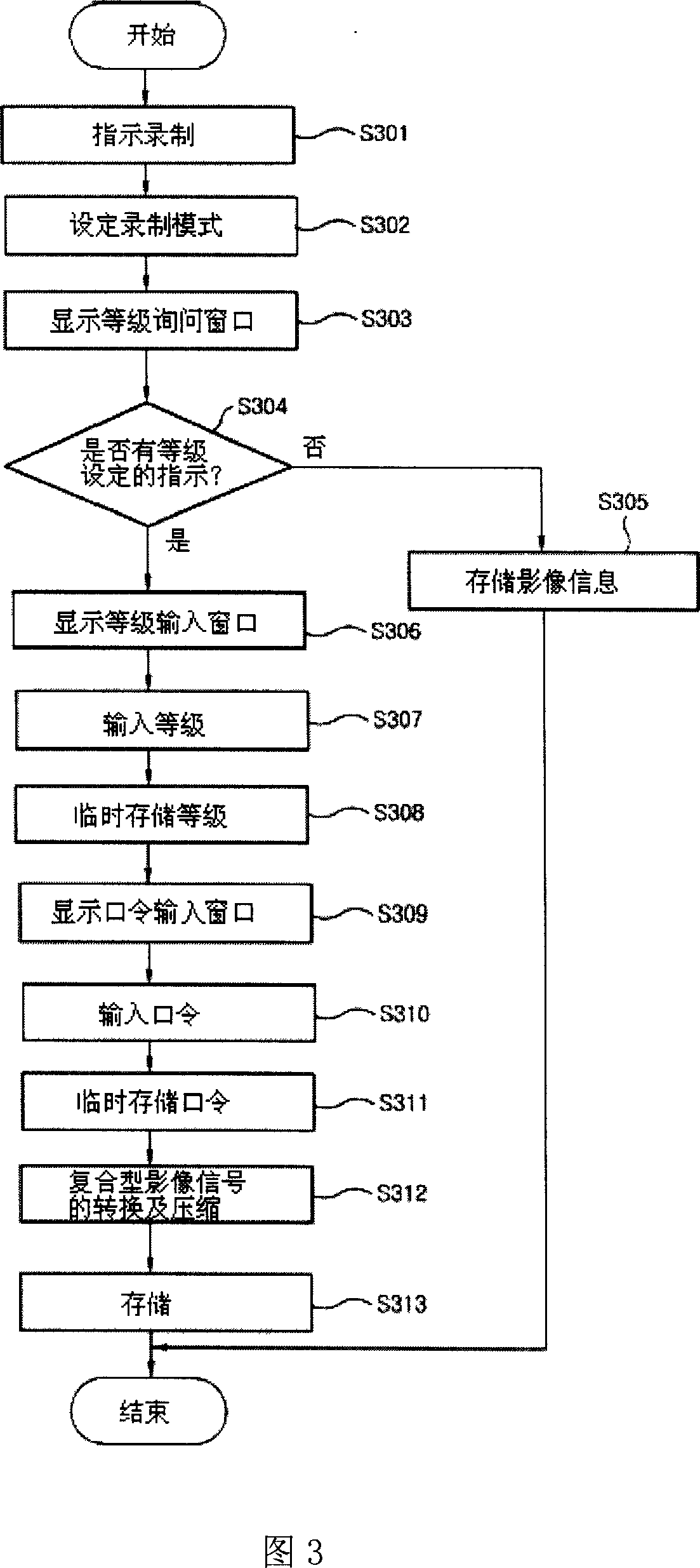
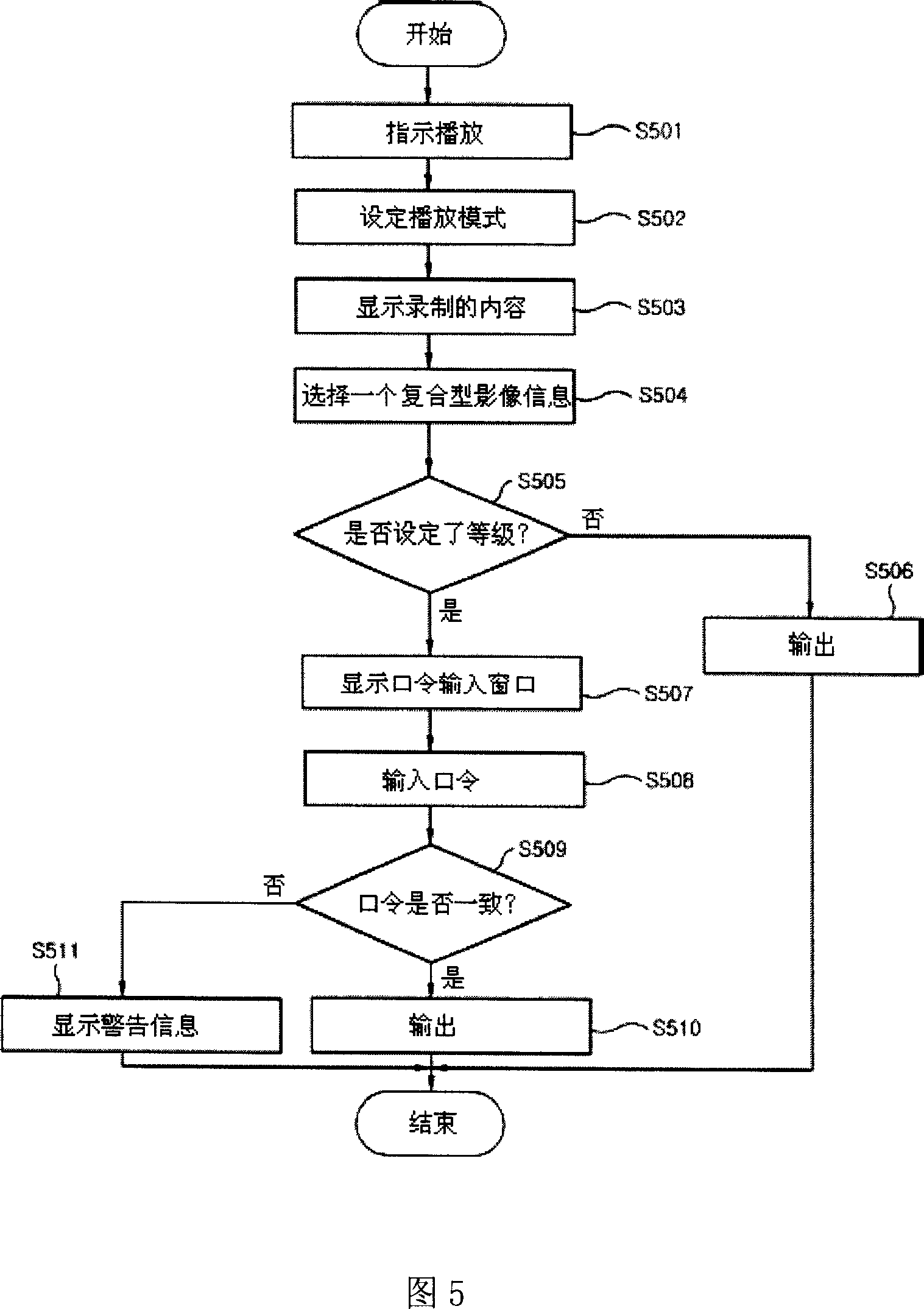
InactiveCN1972418APrevent watchingPrevent viewingTelevision system detailsColor television detailsInformation controlHard disc drive
This invention discloses one compound video information record and play device and method, wherein, the device is set on hardware driver of television or top box and divides each kinds of video signal degree for recording under record or play control orders and it comprises each kinds of compound video information control part for different recording and the memory part for each compound video information and coder and decoder.
Owner:LEIJIN ELECTRONIC SHENYANG CO LTD
Intelligent monitoring and control system for prison perimeter high voltage power grid
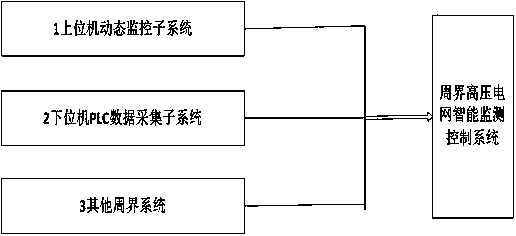
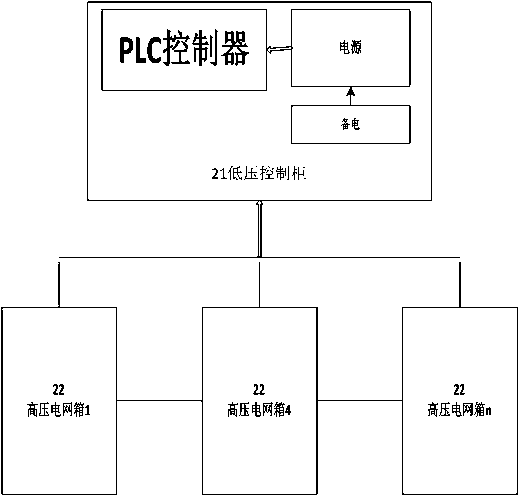
ActiveCN107621580ASafe and reliable workEnsure safetyElectrical testingAlarmsDynamic monitoringPower grid
The invention belongs to the technical field of intelligent power grid monitoring and control, and particularly relates to an intelligent monitoring and control system for a prison perimeter high voltage power grid, which comprises a lower computer PLC data acquisition subsystem and an upper computer dynamic monitoring subsystem, wherein the lower computer PLC data acquisition subsystem is used for acquiring various state parameters of operation of the power grid and transmitting the well-processed power grid parameters to the upper computer dynamic monitoring subsystem; the upper computer dynamic monitoring subsystem is used for carrying out early warning processing on the power grid operation parameters, making corresponding feedback according to the early warning information, being linked with other perimeter systems and ensuring the safety of the prison perimeter; and the other perimeter systems comprise a video monitoring system, a door access system, an interphone system and an infrared system. Functions of high voltage power grid intelligent detection, intelligent striking, process recording, region linkage and the like are integrated, the perimeter high voltage power grid and other devices are not mutually independent but operate cooperatively, and prison perimeter safety management intelligence is thus realized.
Owner:QILU UNIV OF TECH
Multifunctional safeguard vehicle capable of providing camping for multiple persons
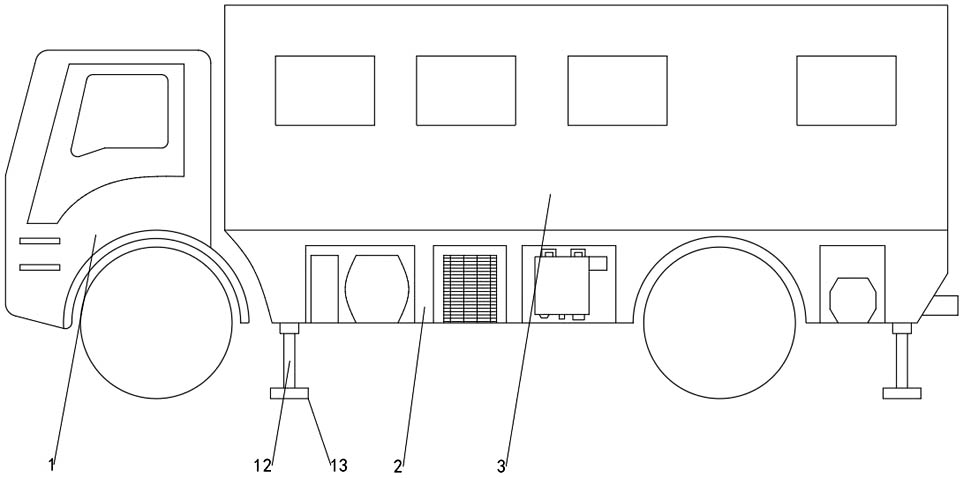
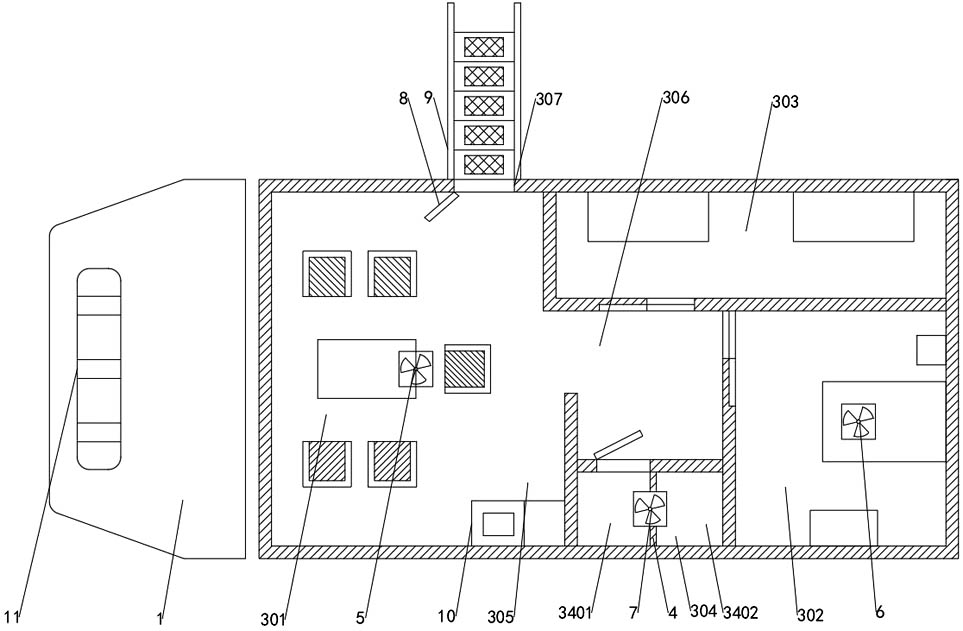
PendingCN112550121AEnsure a normal dietLeft functionVehicle fittings for liftingVehicle with living accommodationMedicineArchitectural engineering
The invention discloses a multifunctional safeguard vehicle capable of providing camping for multiple persons. According to the technical scheme, the multifunctional safeguard vehicle is characterizedby comprising a vehicle head, a support is arranged at the right end of the vehicle head, a carriage is fixedly arranged at the upper end of the support, the carriage is divided into a meeting area,a first rest area, a second rest area, a bathing area and a leisure area, and the meeting area is located at the left end of the carriage; a conference table and conference chairs are arranged in theconference area, the first rest area is located at the right end of the carriage, the second rest area is located behind the first rest area, the bath area is located at the left end of the first restarea, a passageway is formed between the second rest area and the bath area, the bath area is divided into a toilet and a shower room through a partition plate, and the shower room is located at theright end of the toilet. A first air purification system is fixedly arranged at the top end of the conference area, a second air purification system is fixedly arranged at the top end of the first rest area, and the multifunctional conference table has multiple functions in use and is comfortable and practical.
Owner:JIANGSU ZHENXIANG VEHICLE EQUIP
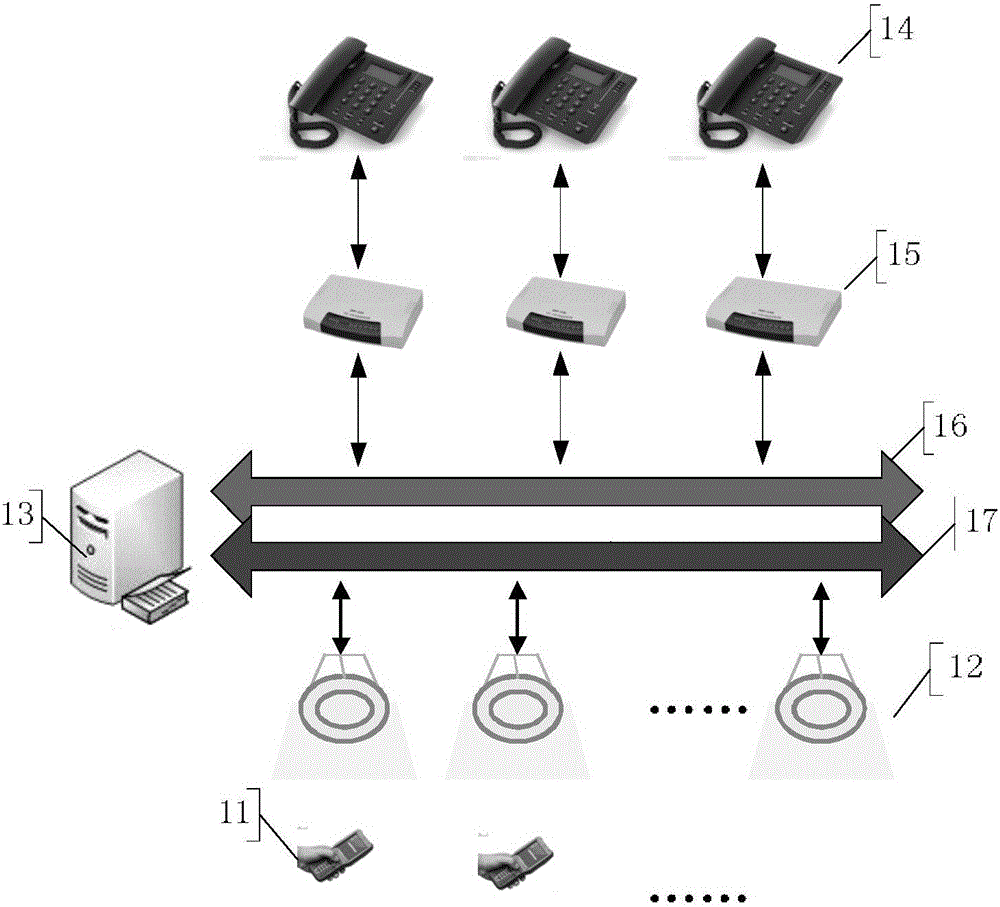
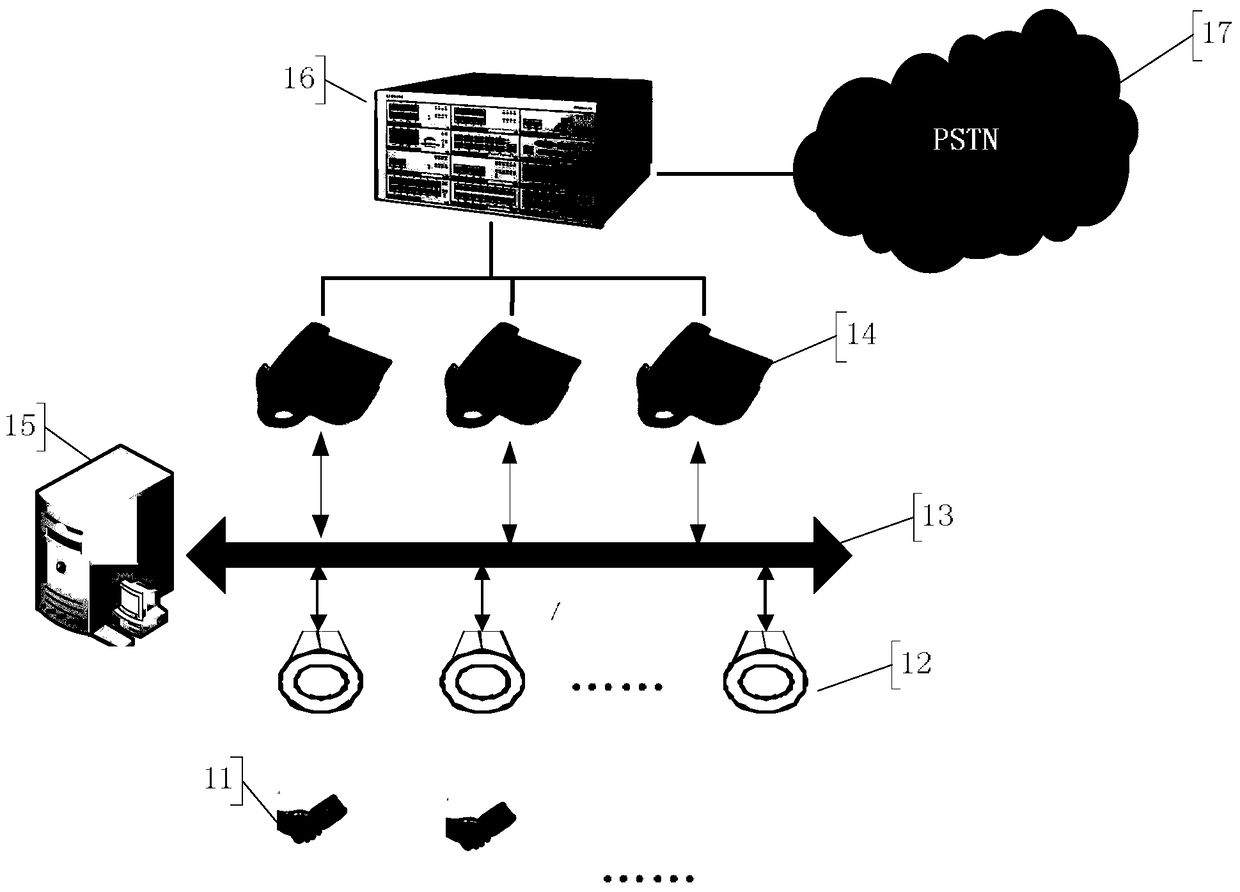
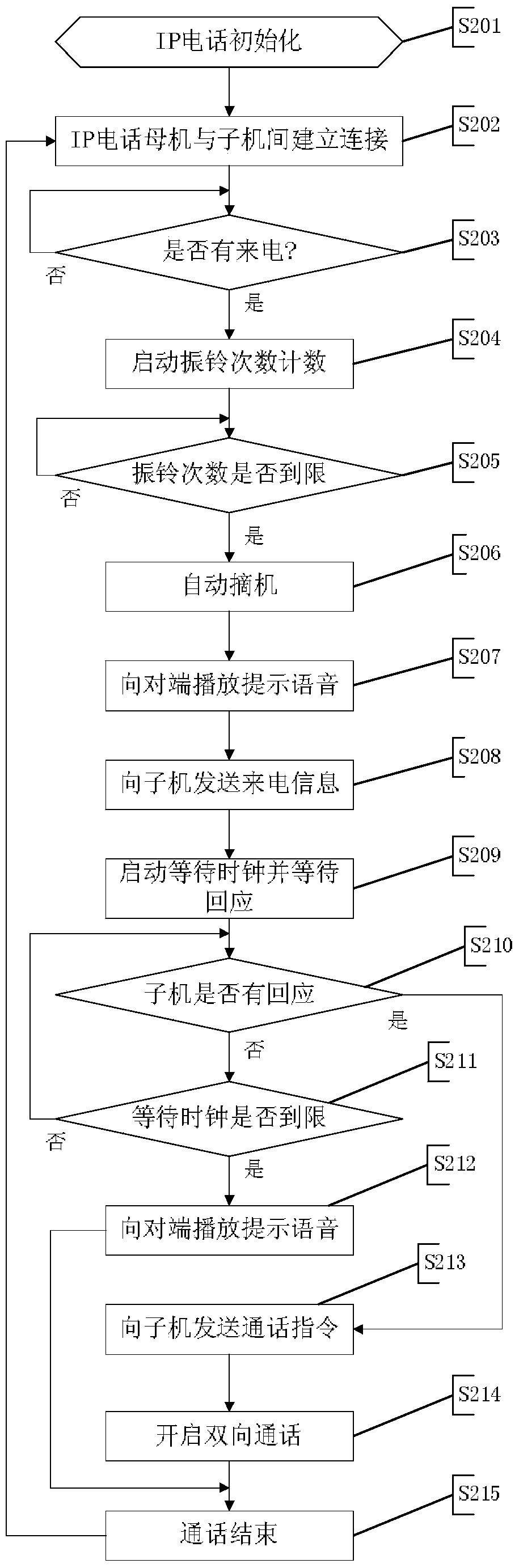
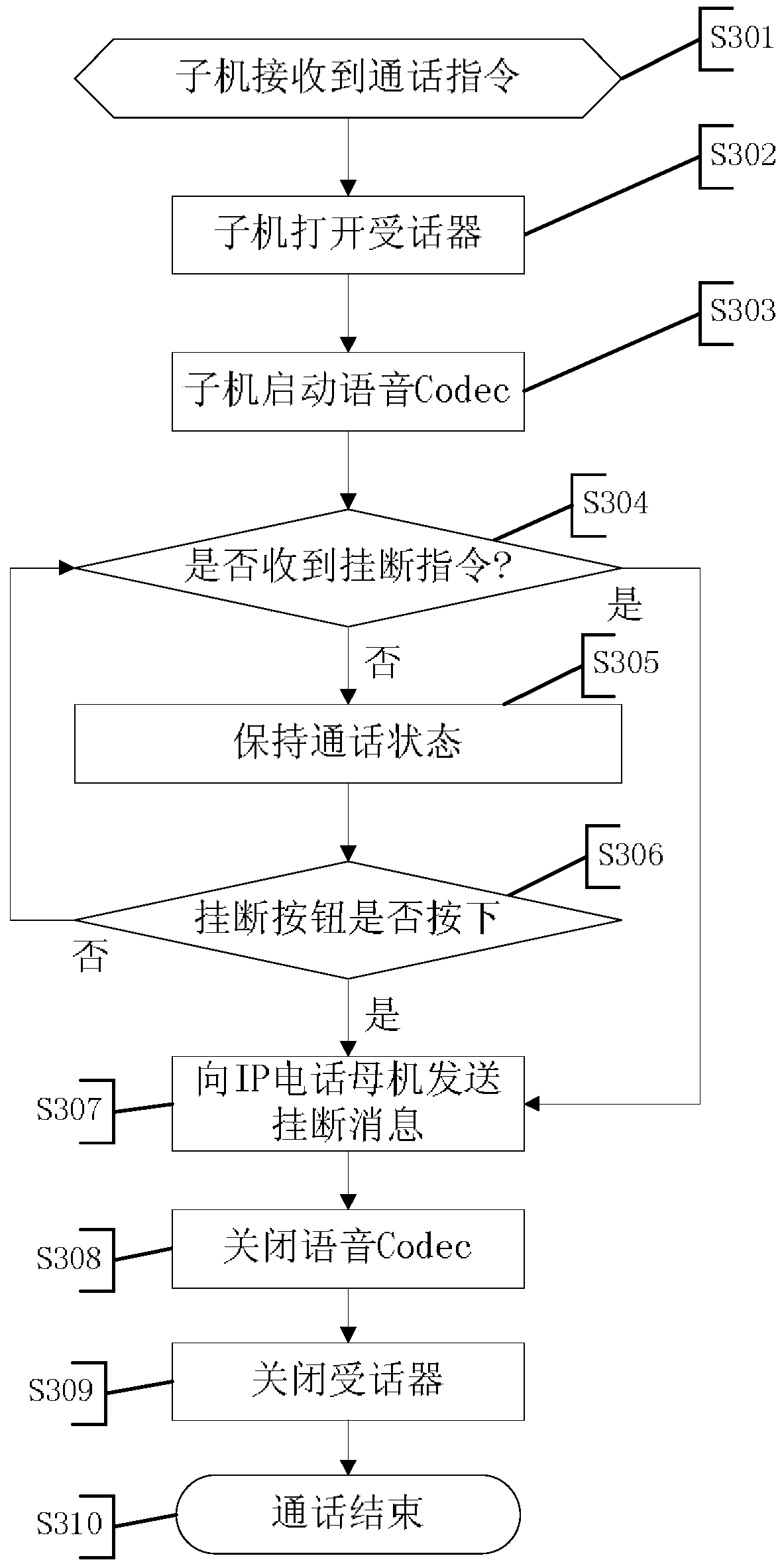
Fixed-line telephone extension method and system
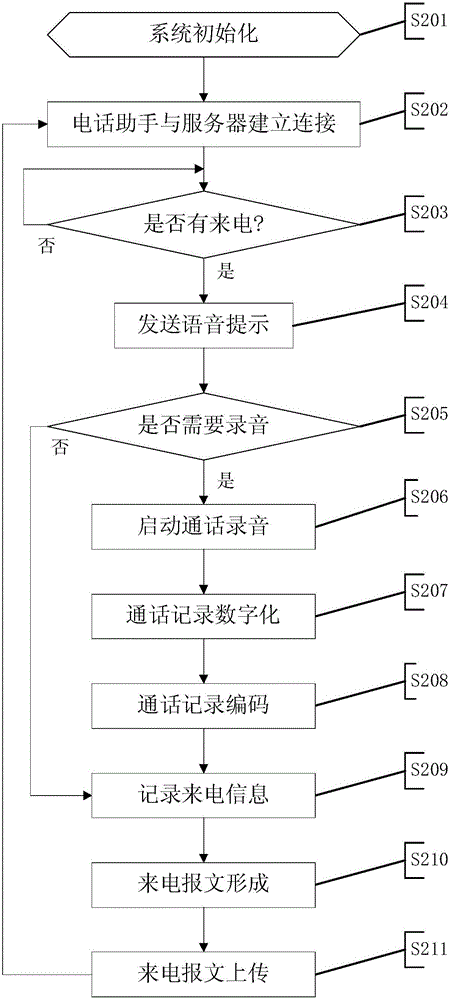
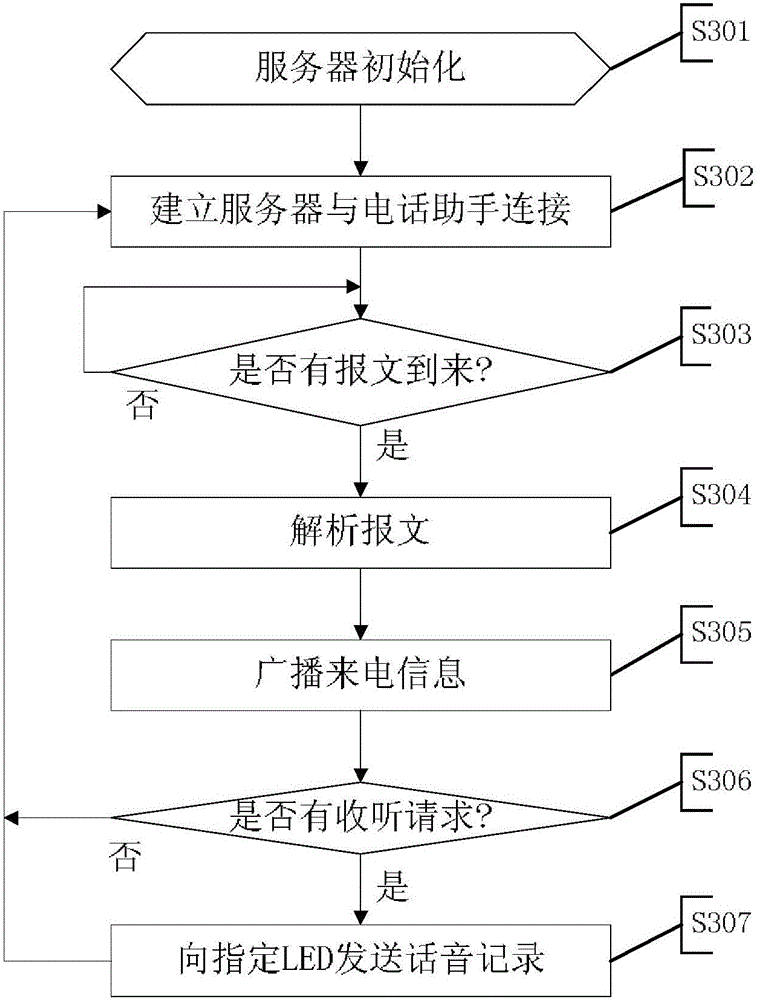
ActiveCN104993868AReduce work delaysEnsure security and confidentialitySpecial service for subscribersClose-range type systemsLED lampVisible light communication
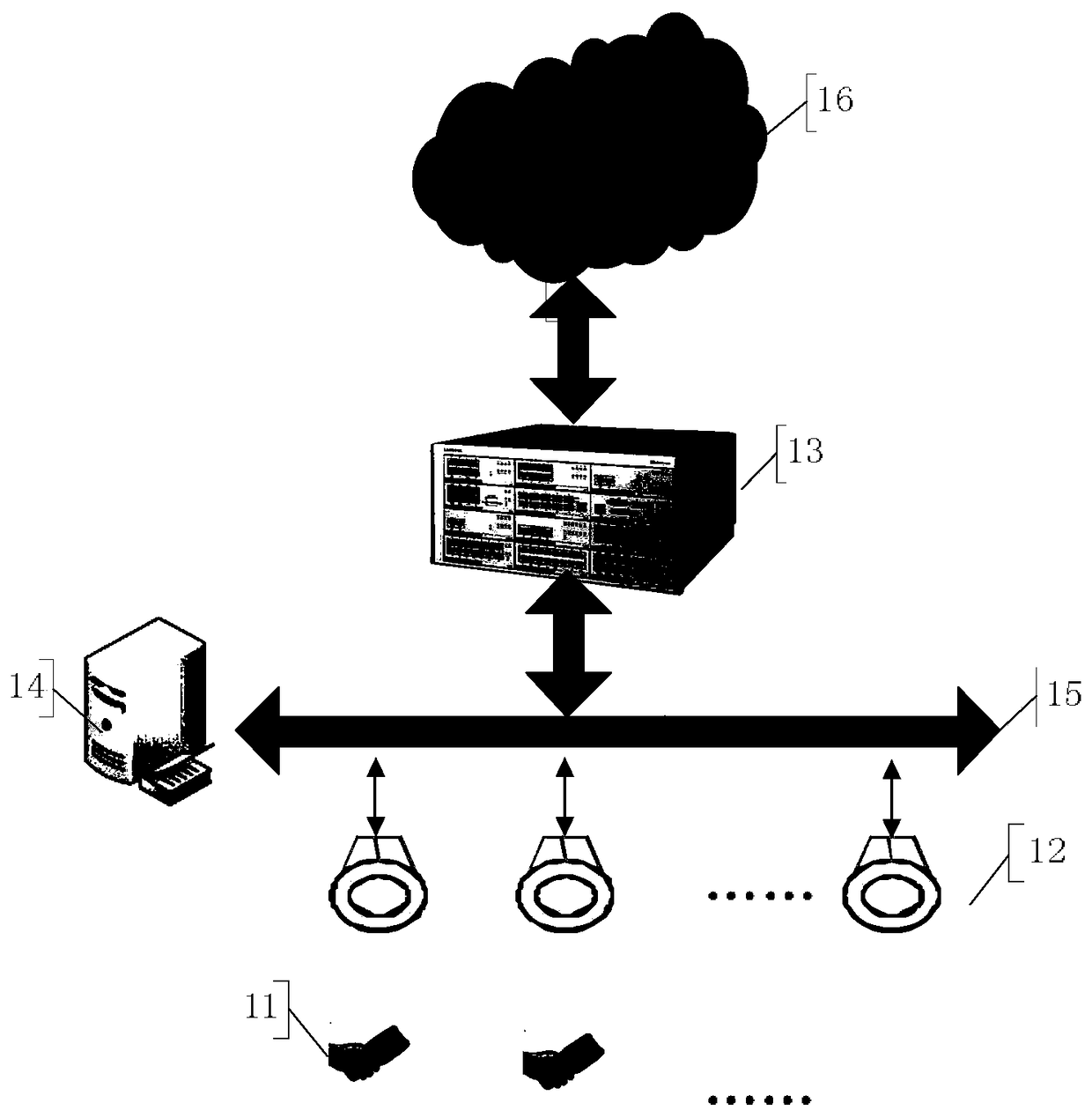
The invention provides a fixed-line telephone extension method and system. The system comprises a server, a plurality of auxiliary devices which are connected with a plurality of fixed-line telephones in a one-to-one correspondent manner and are connected with the server through a telephone subnet, a plurality of LED lamps which are connected with the server through an LED subnet and a plurality of user terminals which are connected with the LED lamps through visible light communication. The method comprises: the auxiliary devices detect incoming calls of the fixed-line telephones, generate incoming information and contents into a message and report the message to the server; after receiving the message, the server stores the message and broadcasts the incoming information to the user terminals on an application occasion in a visible light form through the LED subnet and the LED lamps; after receiving a listening request fed back by the user terminal, the server dispatches a corresponding incoming call content and sends the incoming call content to the user terminal in the visible light form through the LED subnet and particular LED lamps; and the user terminal broadcasts the incoming call content. The method and the system can be used for achieving mobile communication on occasions where mobile phones cannot be used.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
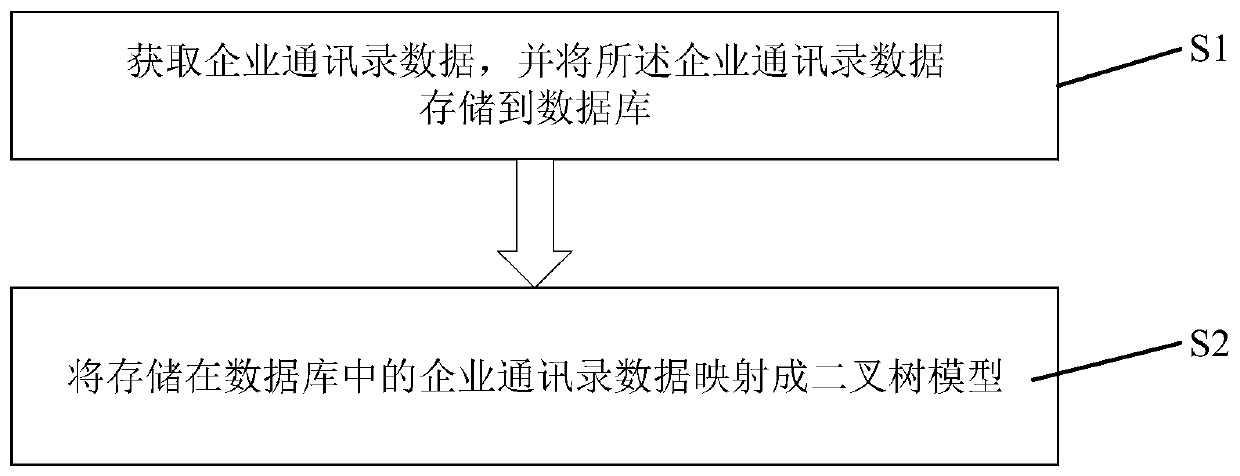
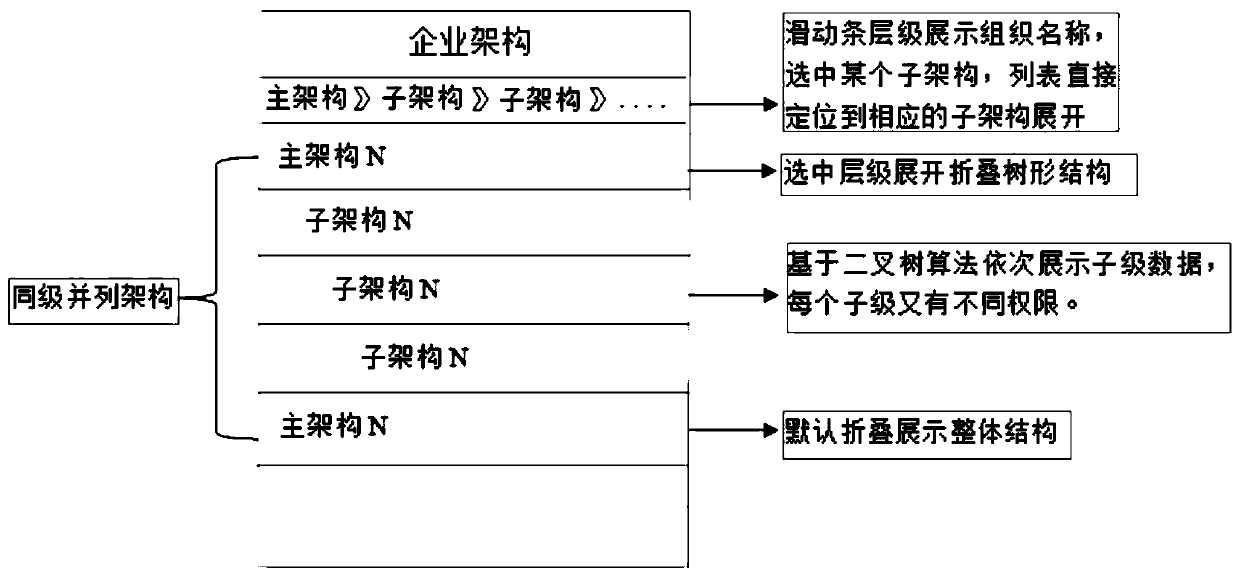
Enterprise address book hierarchical architecture mode method and system
PendingCN110532240ADisplay is clear and intuitiveEnsure security and confidentialityVisual data miningStructured data browsingBinary treeAddress book
The invention discloses an enterprise address book hierarchical architecture mode method and system, and the method comprises the steps: S1) obtaining enterprise address book data, and storing the enterprise address book data in a database; s2) mapping the enterprise address book data stored in the database into a binary tree model, wherein the enterprise organization ID of the main architecture is used as a Node node in the binary tree model to perform downward extension, the parallel enterprise center sub-architecture IDs are used as a left sub-tree L and a right sub-tree R to perform downward extension, the enterprise center sub-architecture ID is used as a Node node to bifurcate all levels of departments to serve as a left sub-tree L and a right sub-tree R, and the IDs of all levels ofdepartments are used as Node nodes to bifurcate personnel IDs of all departments to serve as L nodes.
Owner:FIBRLINK NETWORKS +1
Safety protective server refer to secrete
InactiveCN1588841AEnsure security and confidentialityDoes not take up practical spaceCharacter and pattern recognitionSecuring communicationComputer imageOpto electronic
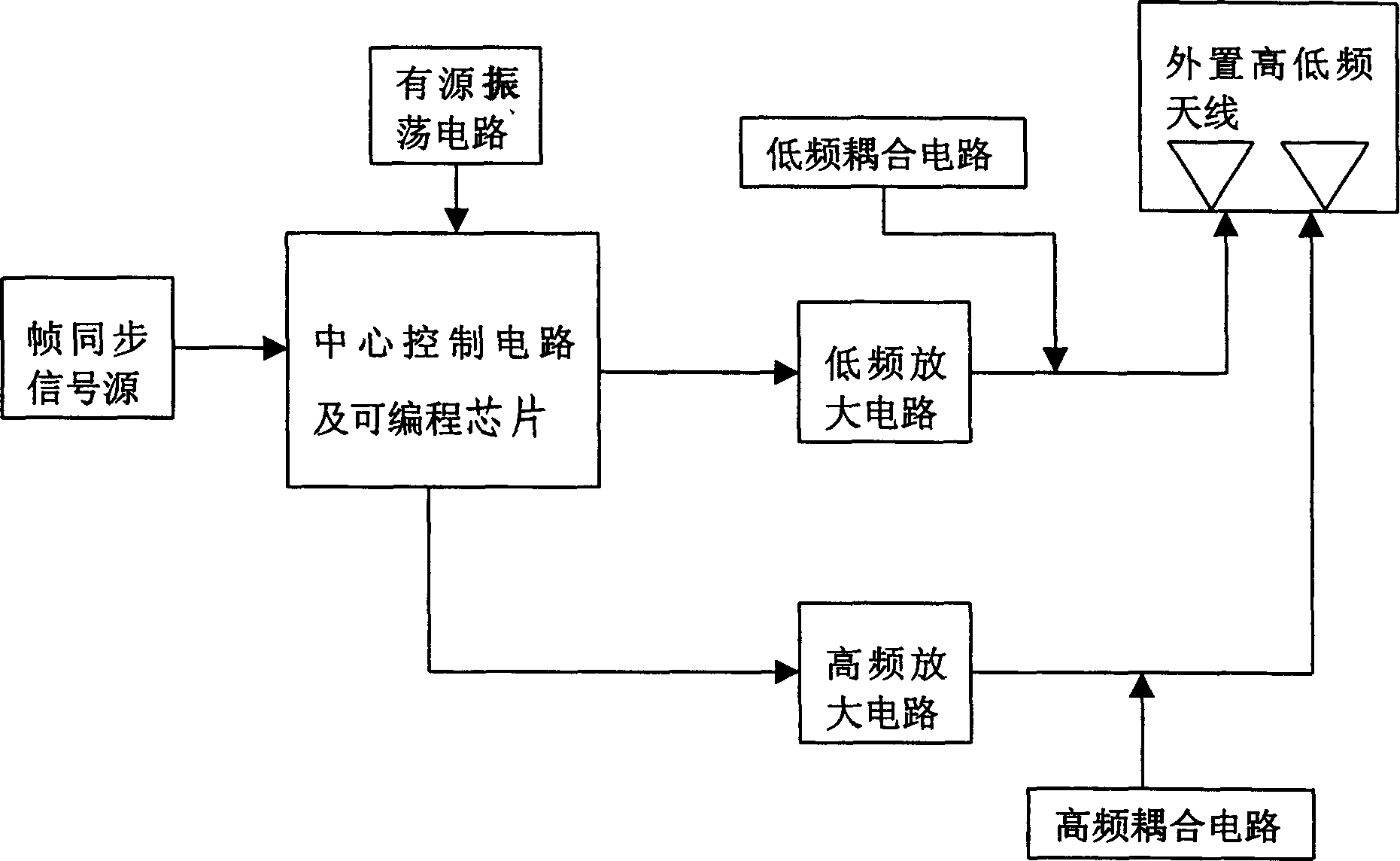
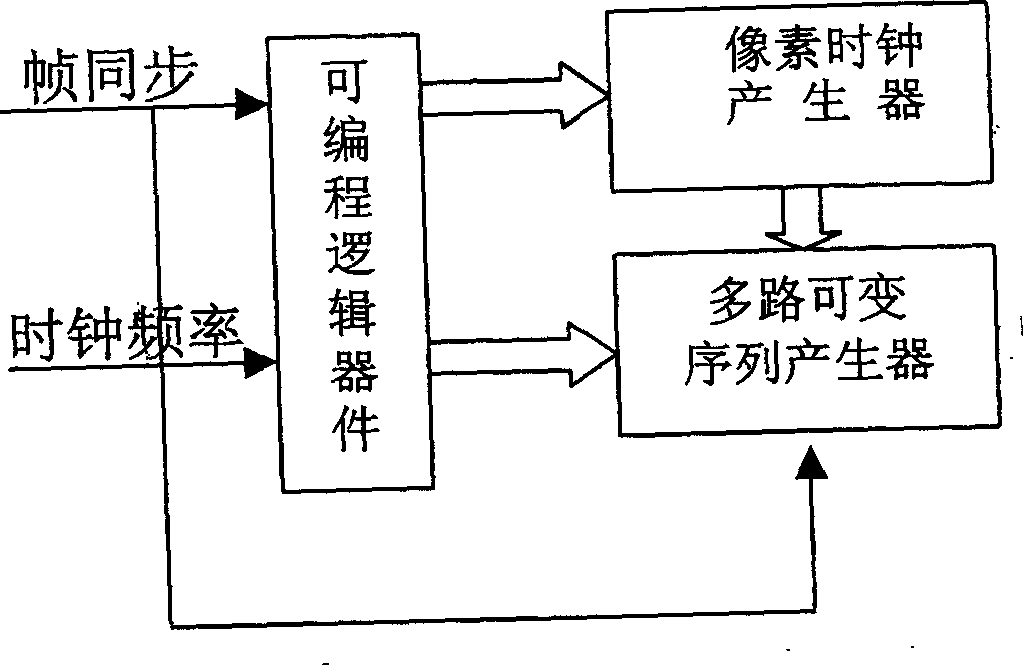
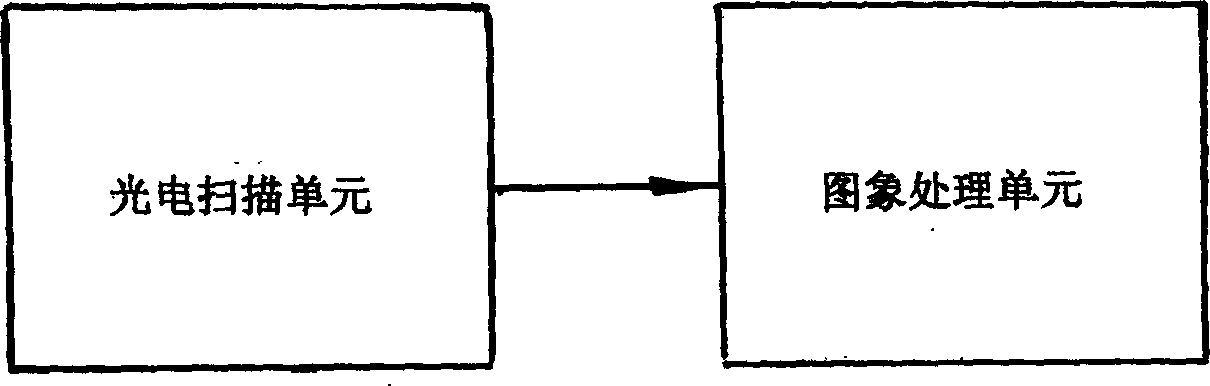
This invention relates to a safety protection server characterizing having an information anti-disclosure part including a frame synchronous signal source an active oscillation circuit, a central control circuit, a programmable chip, a low frequency amplifying circuit, low frequency couple circuit, a high frequency amplifying circuit, a high frequency couple circuit and an outside high / low frequency antenna. The server has a fingerprint management part including a photoelectric scan unit and a computer image process unit. The data cipher part includes a USB interface, USB control chip MCU, EPROM1, ROM+RAM, CPU, EEPROM2, flash and fix disk / photo drive / CF care. It also has a dial part including a dial detection end, a monitor, a database, short message warning platform, a browser and a manager.
Owner:李大东
Data analysis and diagnosis system, device and method, and storage medium
ActiveCN109214202AEnsure security and confidentialityAnalysis and Diagnosis RealizationDigital data protectionTransmissionPrivate networkConfidentiality
The embodiment of the invention discloses a data analysis and diagnosis system, device and method, and a storage medium. The system comprises a private network platform device for receiving field datafrom the field device, extracting keywords capable of describing the field data according to the field data when the field data is judged to be abnormal data, and sending the extracted keywords to apublic network platform device; and receiving a data analysis algorithm returned by a public network platform device, performing data analysis on the abnormal data and related field data by using thedata analysis algorithm, and outputting an analysis result; and a public network platform device for receiving a keyword from the private network platform device, searching a corresponding data analysis algorithm according to the keyword, and sending the searched data analysis algorithm to the private network platform device. The technical proposal of the invention can realize the data analysis and diagnosis of the sensitive data under the condition of ensuring the safety and confidentiality of the sensitive data.
Owner:SIEMENS CHINA
Combined security U disk device
InactiveCN107491807AEasy to useEnsure security and confidentialityInternal/peripheral component protectionRecord carriers used with machinesUser needsUSB
The invention provides a combined security U disk device. A casing and a plug are separately placed. When a user needs to use the device, the user opens and removes an encryption lock, and inserts the plug rod of the plug into a fixation slot, which is corresponding to the plug rod, of the casing. A connection block and a connection port are connected together, so that a USB connector and the U disk body are connected together to be used. The plug can be inserted into an insertion channel through the plug rod, so that the plug and the casing are combined together. The combined security U disk device is convenient to use. The device can be used when the casing and the plug are available at the same time, which further ensures security and secrecy.
Owner:WUHU ZHENHUA RONGKE INTELLIGENT TECH
paging system
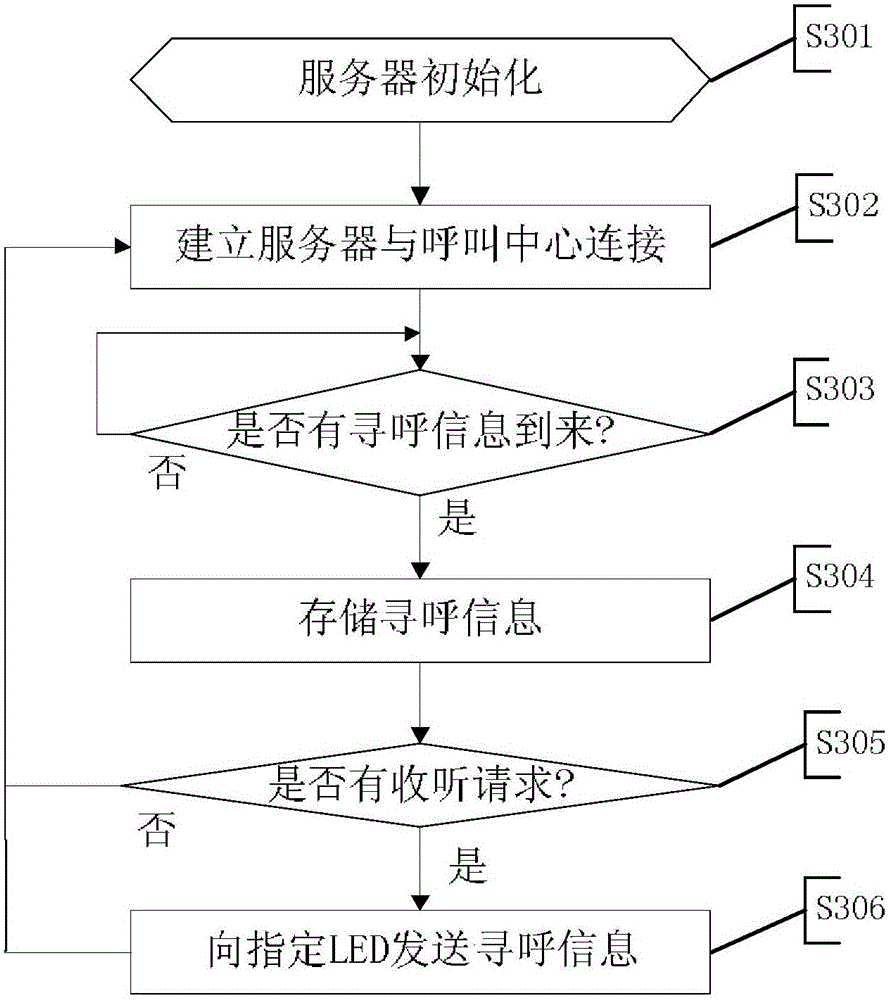
ActiveCN105050183BReduce work delaysEnsure security and confidentialityClose-range type systemsWireless communicationPagerLED lamp
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
Material work order auditing method, device and equipment and storage medium
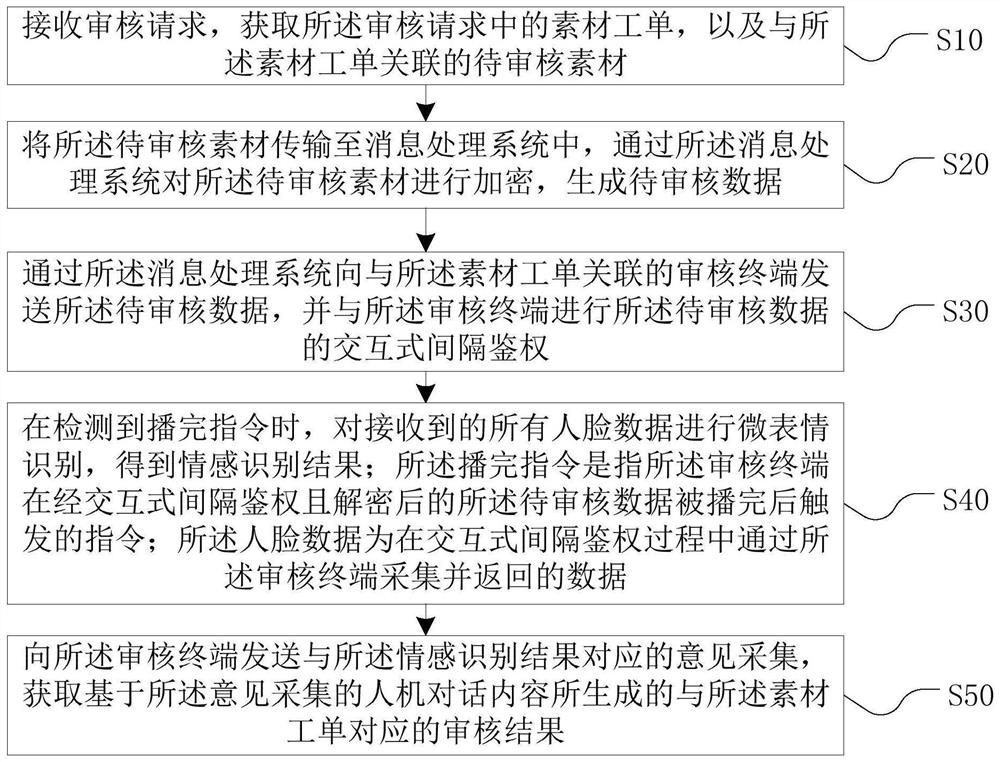
PendingCN114282882AEnsure security and confidentialityImprove confidentialityCharacter and pattern recognitionDigital data protectionEngineeringData processing
The invention relates to the technical field of data processing, and discloses a material work order auditing method, device and equipment and a storage medium, and the method comprises the steps: receiving an auditing request, and obtaining a material work order in the auditing request and a to-be-audited material associated with the material work order; transmitting the to-be-audited material to a message processing system, encrypting the to-be-audited material through the message processing system, and generating to-be-audited data; sending the to-be-audited data to an auditing terminal associated with the material work order, and performing interactive interval authentication on the to-be-audited data with the auditing terminal; when a playing completion instruction is detected, performing micro-expression recognition on all the received face data to obtain an emotion recognition result; and sending opinion collection corresponding to the emotion recognition result to an auditing terminal, and obtaining a generated auditing result corresponding to the material work order. Therefore, the confidentiality and security of the to-be-audited data are improved, and the experience satisfaction degree of customers is improved.
Owner:DONSON TIMES INFORMATION TECH CO LTD
Paging system
ActiveCN105050183AReduce work delaysEnsure security and confidentialityClose-range type systemsWireless communicationPagerLED lamp
Provided is a paging system. The paging system comprises a call center, a plurality of pagers and a paging network connected with the call center and the plurality of pagers. The paging network comprises a plurality of LED lamps arranged in application places and an IP network connected with the plurality of LED lamps and the call center. Signal reception devices of the plurality of pagers are optical signal receiving elements. Paging information is transmitted to the pager through the IP network, the LED lamp and the optical signal receiving element of the pager. Visible light communication and a preset paging system are combined, on one side, security and secrecy of paging information are ensured, on the other side, mobile connection can be achieved in places, where mobile phone cannot be used, such as underground working places or the like.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
cordless phone system
ActiveCN104954584BReduce work delaysEnsure security and confidentialityCordless telephonesClose-range type systemsVisible light communicationMobile phone
A cordless telephone system comprises a house phone network formed by multiple telephones, a public phone switching network, a switch connected between the two networks and a visible light communication network, wherein each telephone is a child-mother telephone consisting of a mother telephone and a child telephone which are in wireless communication connection through the visible light communication network. According to the cordless telephone system, each mother telephone and the corresponding child telephone are communicated on the basis of the visible light communication network, so that security and secrecy of the communication can be guaranteed, and mobile connection can be realized on occasions such as underground facilities, mines, tunnels and the like where electromagnetic wave propagation is not facilitated.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com