Data security method of memory card
A data security and storage card technology, applied in the direction of internal/peripheral computer component protection, etc., can solve the problems of poor data security and security, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] In the following, the present invention will be further described in conjunction with the drawings and specific embodiments.
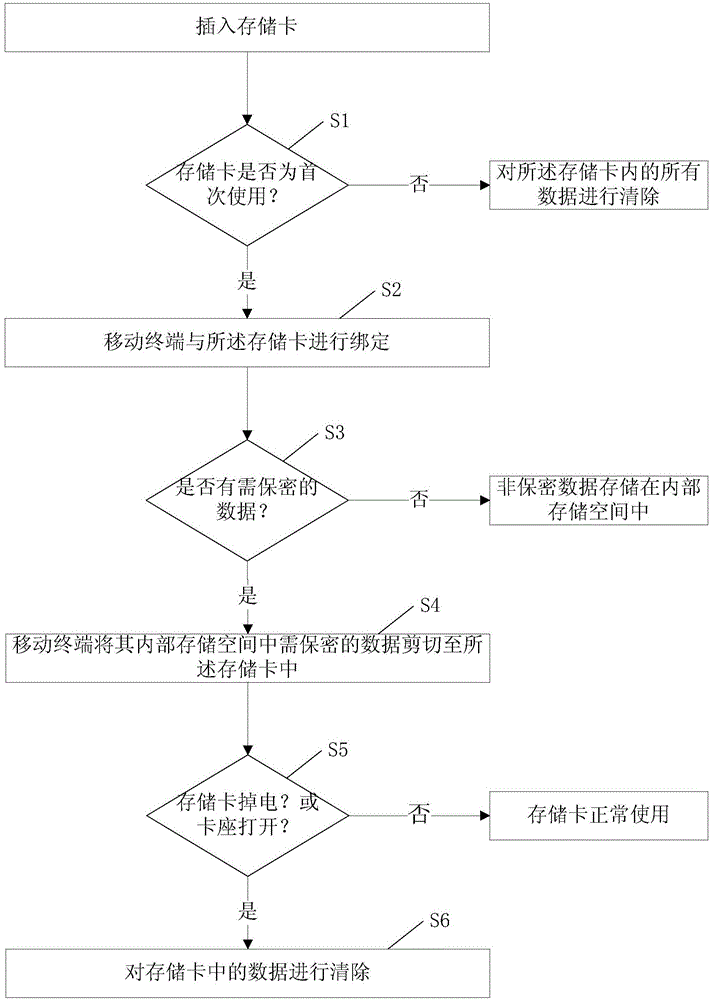
[0026] Such as figure 1 As shown, a data security method of a memory card, when the memory card is inserted into the mobile terminal, the following steps are performed:
[0027] Step S1, the mobile terminal acquires the identity information of the inserted memory card, which may be empty or may be an International Mobile Subscriber Identification Number (IMSI, International Mobile Subscriber Identification Number), to determine whether the memory card is the first If yes, execute step S2, if not, clear all data in the memory card, and stop using the memory card.
[0028] Specifically, the process of judging whether the memory card is used for the first time is: the mobile terminal compares its International Mobile Subscriber Identification Number with the identity information in the memory card, if they do not match, it means that the IMSI numb...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com