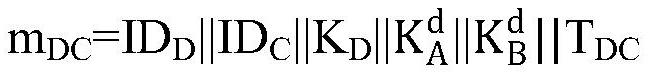Method and system for realizing multi-party key agreement
A technology of key negotiation and implementation method, which is applied in the field of implementation methods and systems of multi-party key negotiation, and can solve the problem that the security of information exchanged by key negotiation members cannot be effectively guaranteed.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
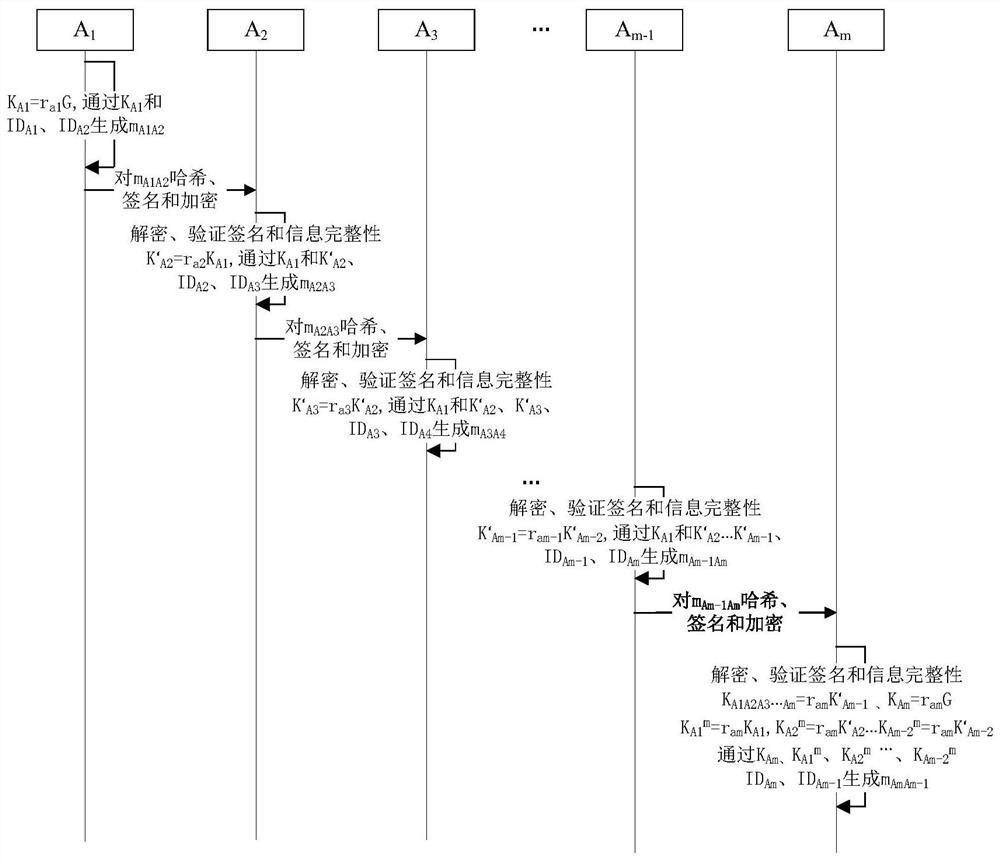
[0052] The embodiment of the present invention proposes a method for implementing multi-party key negotiation, including m key negotiation members {A 1 ,A 2 ,...,A m}, the method includes a forward transfer process and a reverse transfer process; where:
[0053] The forward transmission process includes:
[0054] key agreement member A 1 Generate random numbers Then generate the key parameters pass Generate key agreement information with member information and sent to key agreement member A 2 ; G is the base point on the elliptic curve whose order is a prime number n; random number
[0055] key agreement member A 2 Generate random numbers Calculate key parameters pass Generate key agreement information with member information and sent to key agreement member A 3 ;random number
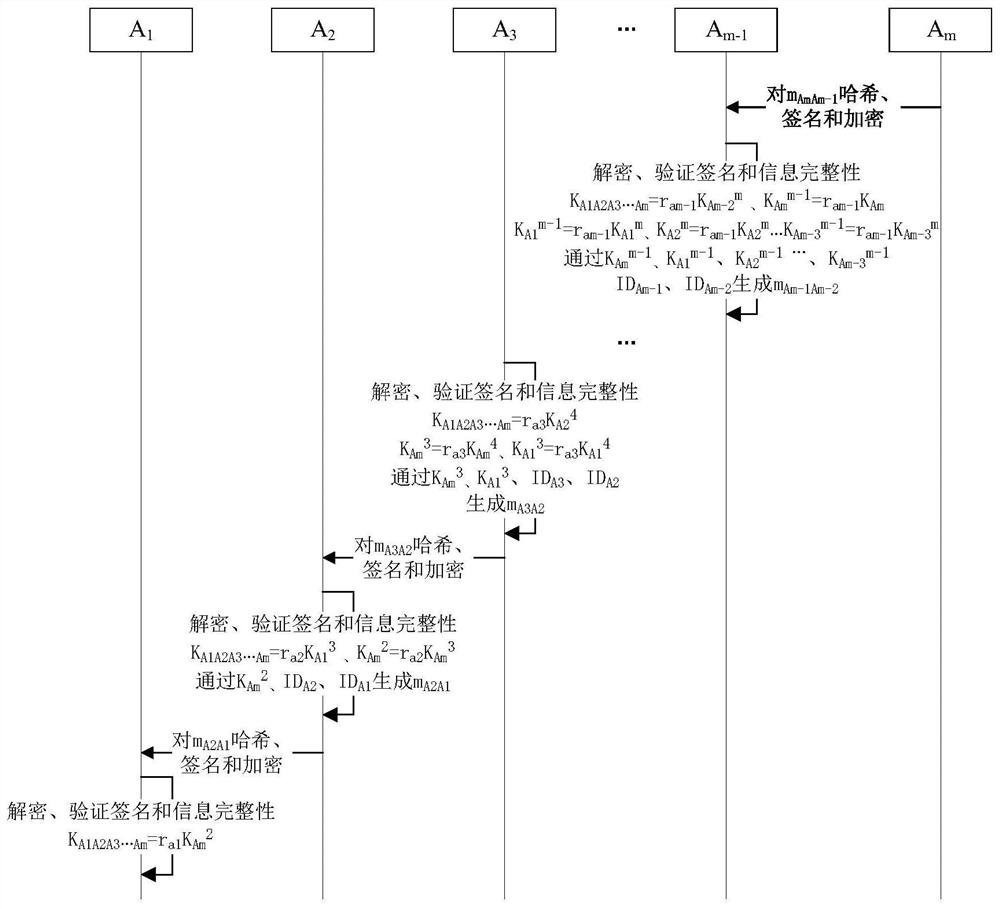
[0056] Continuing in this way, the key agreement member A i Generate random numbers Member A according to the key agreement i-1 The key parameter of Compute its key par...
Embodiment 2
[0066] On the basis of the above-mentioned embodiment 1, this embodiment of the present invention provides another implementation method of multi-party key agreement, which is different from the above-mentioned embodiment 1 in that the method further includes the following steps:
[0067] Before each key agreement member sends the key agreement information to its corresponding next key agreement member, digest, sign and encrypt the key agreement information;
[0068] Specifically, performing digest, signature, and encryption processing on the key agreement information specifically includes: performing a hash operation on the key agreement information through a hash algorithm to generate a first hash operation result; using each key through a signature algorithm The private key of the negotiating member signs the first hash operation result to generate signature information; encrypts the signature information and the key negotiation information through an encryption and decrypti...
Embodiment 3
[0075] On the basis of the above-mentioned embodiment 1 or embodiment 2, this embodiment of the present invention also provides a method for implementing multi-party key negotiation, which is different from the above-mentioned embodiment 1 or embodiment 2 in that:
[0076] The key agreement information also includes a time stamp when the sender sends information to the receiver;
[0077] For example, to negotiate member A with key i To key agreement member A j The key agreement information sent For example, at this time, the key agreement member A i As the sender, the key agreement member A j is the receiver, the key agreement information Including key agreement member A i To key agreement member A j Timestamp when the message was sent
[0078] Correspondingly, after receiving the timestamp, the receiver first verifies the timestamp, and then calculates the key or key parameters.
[0079] For example, to negotiate member A with key j Received key agreement member ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com