Method of encrypting control signaling
A control signal and group control technology, which is applied in the direction of encryption devices with shift registers/memory, wireless communication, security communication devices, etc., can solve the problems of not performing key exchange, etc., and achieve security weaknesses that prevent the destruction of confidentiality, Reduce the effect of excessive load
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 2 example
[0208]
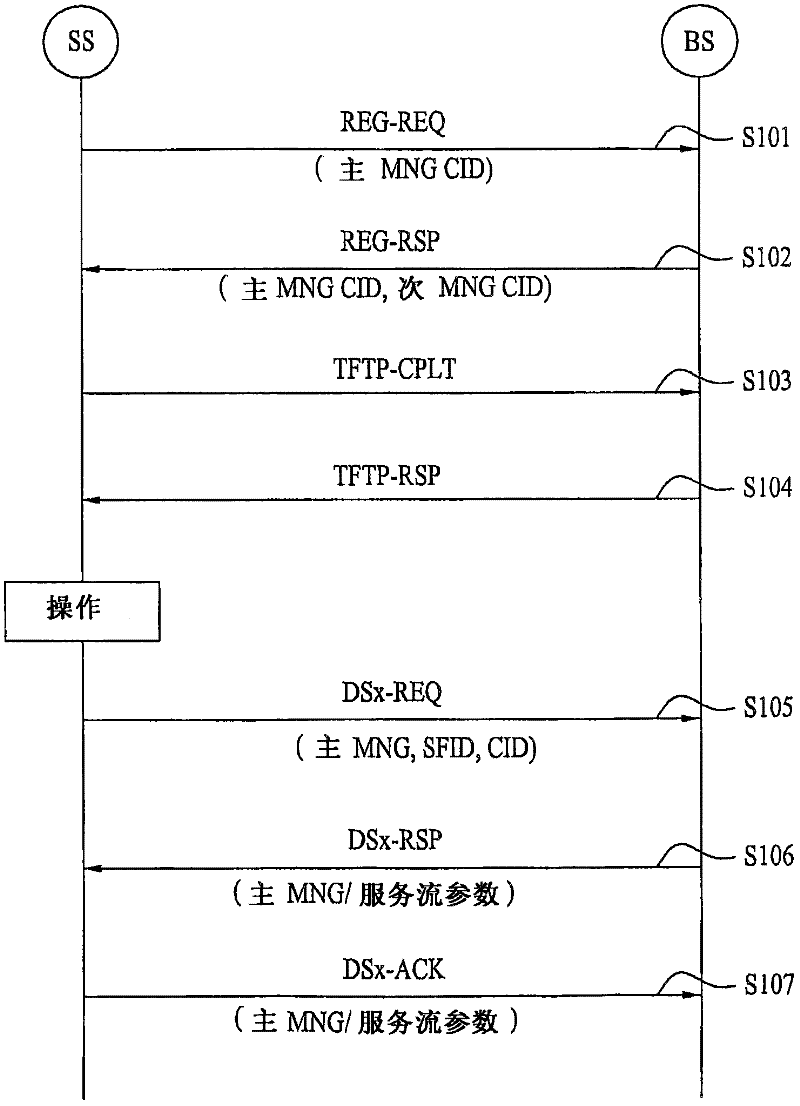
[0209] In the following description, a method of selectively encrypting a control signal applicable to an embodiment of the present invention is explained.
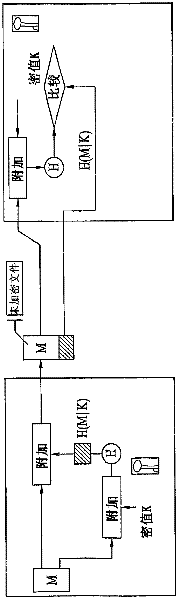
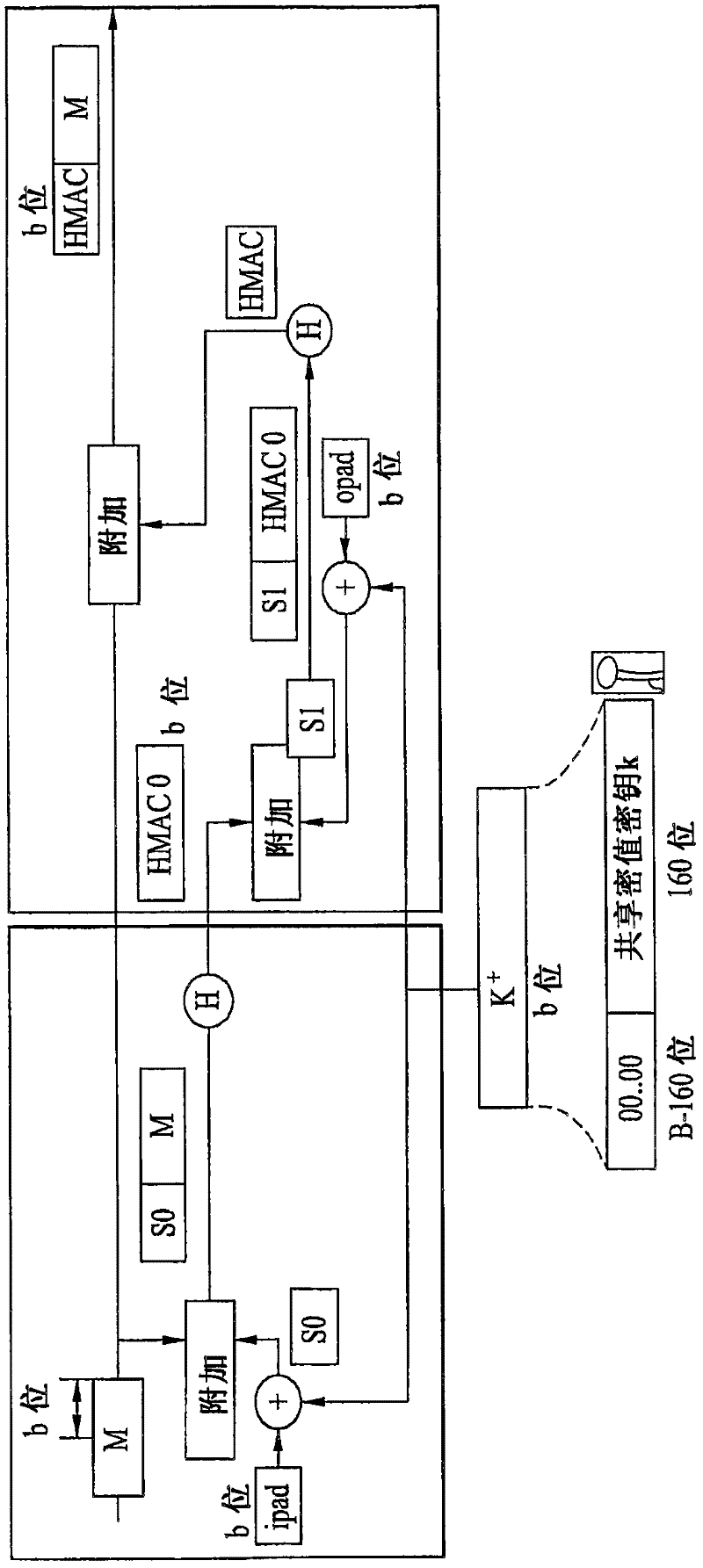
[0210] In the IEEE 802.16e system, the mobile station and the base station use the authorization key shared by both the mobile station and the base station to generate CMAC (cipher-based message authentication code) keys and HMAC (hash message authentication code) keys for control signaling protection. code) key.
[0211] Each of the mobile station and the base station can generate a message authentication code (MAC) using a CMAC key and / or a HAMC key. Also, the mobile station and the base station can ensure the integrity of the corresponding control signal by exchanging the control signal in a manner of attaching a message authentication code (MAC) to the control signal.
[0212] Meanwhile, in case the base station and the mobile station use AES-CCM, the mobile station and the base station can ensure the inte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com