Secure and confidential offline software registration authorization method
A software registration, security and confidentiality technology, applied in the direction of program/content distribution protection, platform integrity maintenance, etc., can solve the problems of unable to uniformly manage authorized software registration information, easy to lose, waste of manpower, etc., to achieve encryption and transmission mode guarantee, Easy to see the effect of supervision
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] Below in conjunction with accompanying drawing, the present invention is further elaborated:
[0021] A safe and confidential off-line software registration and authorization method, its specific implementation examples are as follows:
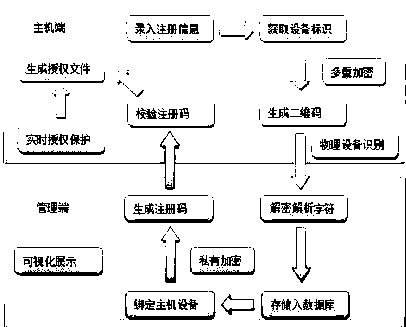
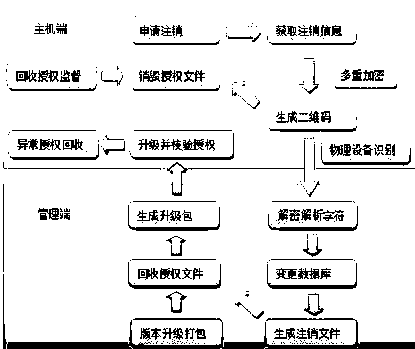
[0022] Such as figure 1 As shown, the working steps are as follows: (1) Generate registration information: obtain multiple unique identification information of the host device and perform special splicing, the user enters the registration information such as the company name and then splices with the unique host ID; the above information data Use RSA to encrypt AES key + AES encrypted text, which is a combination of irreversible and reversible encryption; the encrypted string generates a QR code image and displays it on the interface; use physical devices to analyze and identify the QR code locally ;(2) Generate registration code: When the registration management terminal receives the need to register the software, it will enter the en...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com