Encrypted communication method, encrypted/decrypted communication device, encryption device and decryption device
A technology for encrypting communication and communication devices, which is applied to encryption devices with shift registers/memory, public keys for secure communications, user identity/authority verification, etc., and can solve problems such as leaking encryption algorithms and security cannot be guaranteed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0107] Taking the encrypted communication process in which terminal A sends data to terminal B and terminal B receives data from terminal A as an example, the method of using reconfigurable logic circuits to realize encrypted communication is described below.
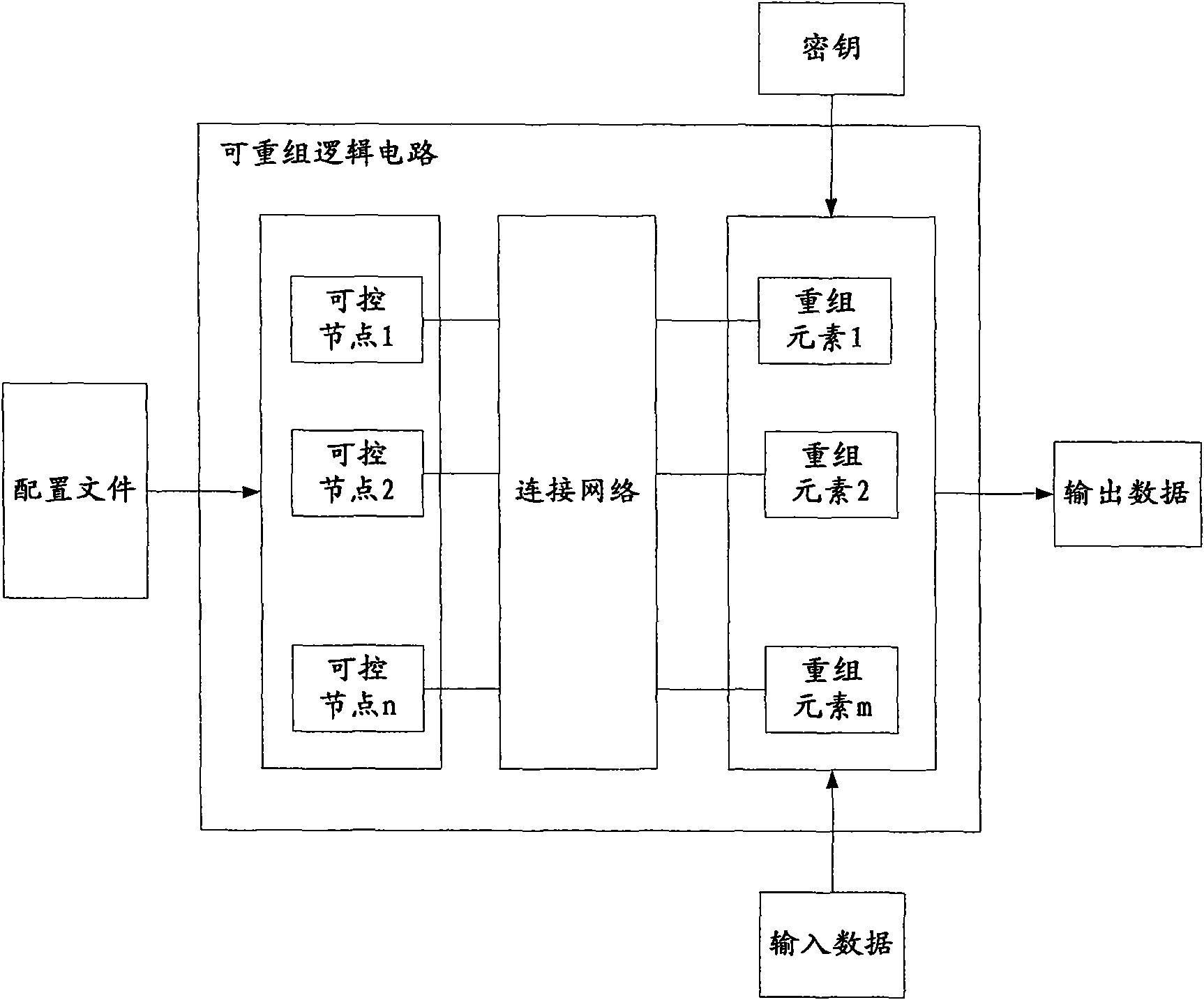
[0108] In the first embodiment, a reconfigurable logic circuit A is set in the terminal A, and a reconfigurable logic circuit B is set in the terminal B, and the reconfigurable logic circuit A and the reconfigurable logic circuit B have the same configuration. In the first embodiment, the process of implementing encrypted communication between terminal A and terminal B is as follows: Figure 5 shown, including the following steps.
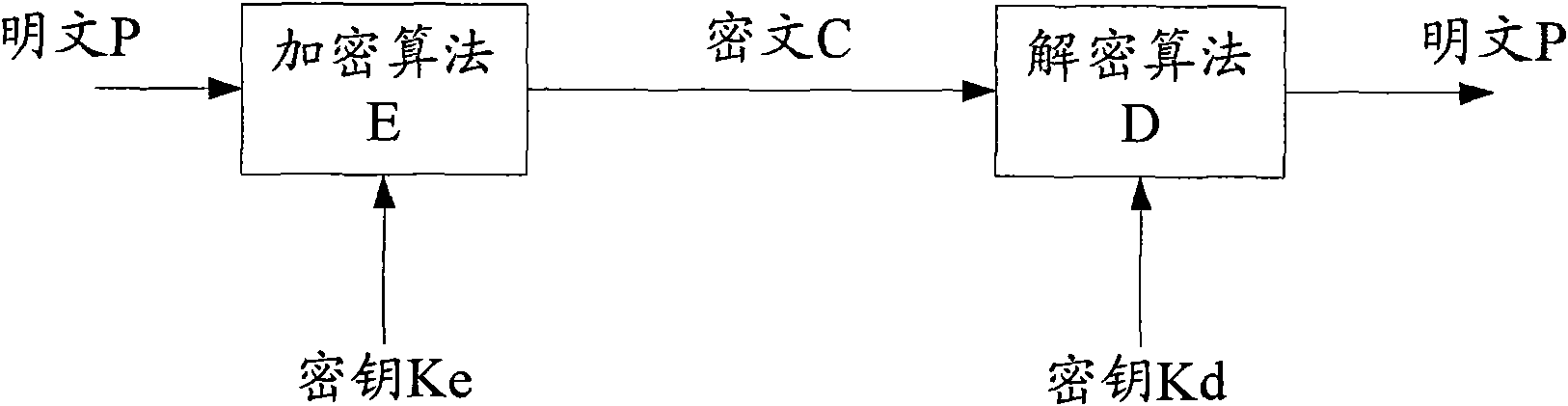
[0109] Step ST501: A key is determined between terminal A and terminal B, and the determined key includes an encryption key and a decryption key.
[0110] In the actual encrypted communication process, as keys, fixed encryption keys and decryption keys can be used. In order to improve the ...
Embodiment 2
[0134] In the second embodiment, a reconfigurable logic circuit A is set in the terminal A, and a reconfigurable logic circuit B is set in the terminal B, the reconfigurable logic circuit A and the reconfigurable logic circuit B have the same configuration, and in Terminal A is provided with a configuration file storage unit A for storing configuration files, and terminal B is provided with a configuration file storage unit B for storing configuration files.
[0135] There may be multiple ways to store configuration files in the configuration file storage unit, examples are as follows.
[0136] Storage method 1: Since the encryption algorithm and the decryption algorithm are in one-to-one correspondence in the cryptographic algorithm, the encryption configuration file and the decryption configuration file are also in one-to-one correspondence. Therefore, a different identifier is set for each cryptographic algorithm, and the cryptographic algorithm identifier, the encrypted co...
Embodiment 3
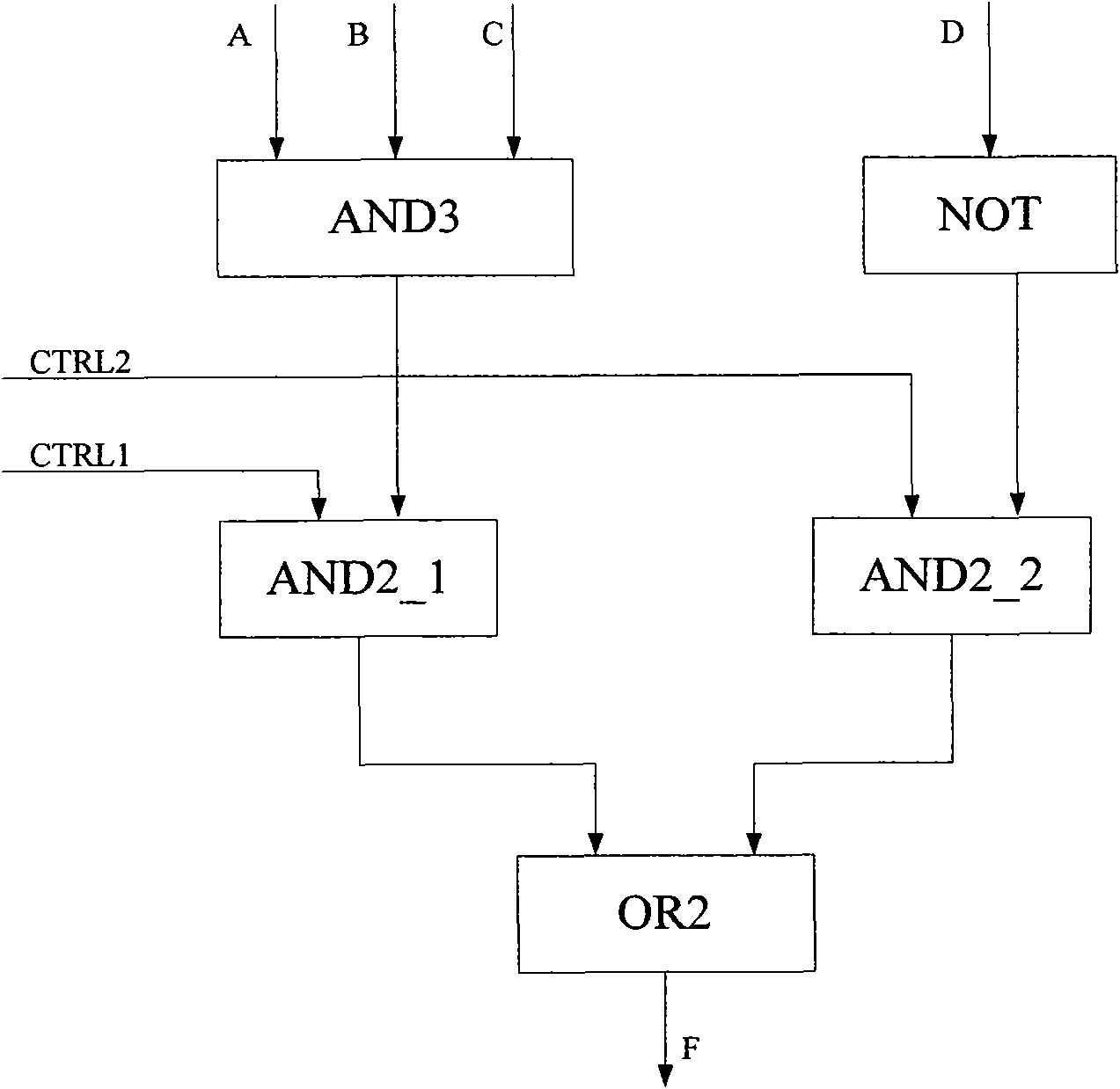
[0172] In the third embodiment, the difference from the second embodiment lies in step ST702.
[0173] In the third embodiment, if it is necessary to determine the cryptographic algorithm identifier used to represent the cryptographic algorithm between the terminal A and the terminal B in the above step ST702, then by Figure 10 The steps shown are determined: terminal A generates the first parameter Ra, sends the first parameter Ra to terminal B, and receives the second parameter Rb from terminal B; terminal B generates the second parameter Rb, and sends the second parameter to terminal A Rb, receiving the first parameter Ra from terminal A; terminal A determines the cryptographic algorithm identifier according to the first parameter Ra and the second parameter Rb in a prescribed manner; terminal B also determines the encryption algorithm identifier according to the first parameter Ra and the set The second parameter Rb determines the cryptographic algorithm identifier in a p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com