Block chain-based access control management method and device and access control equipment
A management method and blockchain technology, applied in the field of access control equipment and access control management based on blockchain, can solve the problems of privacy information leakage and high requirements on the network speed of equipment terminals, achieve efficient transmission, reduce network traffic usage, avoid The effect of personal privacy leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
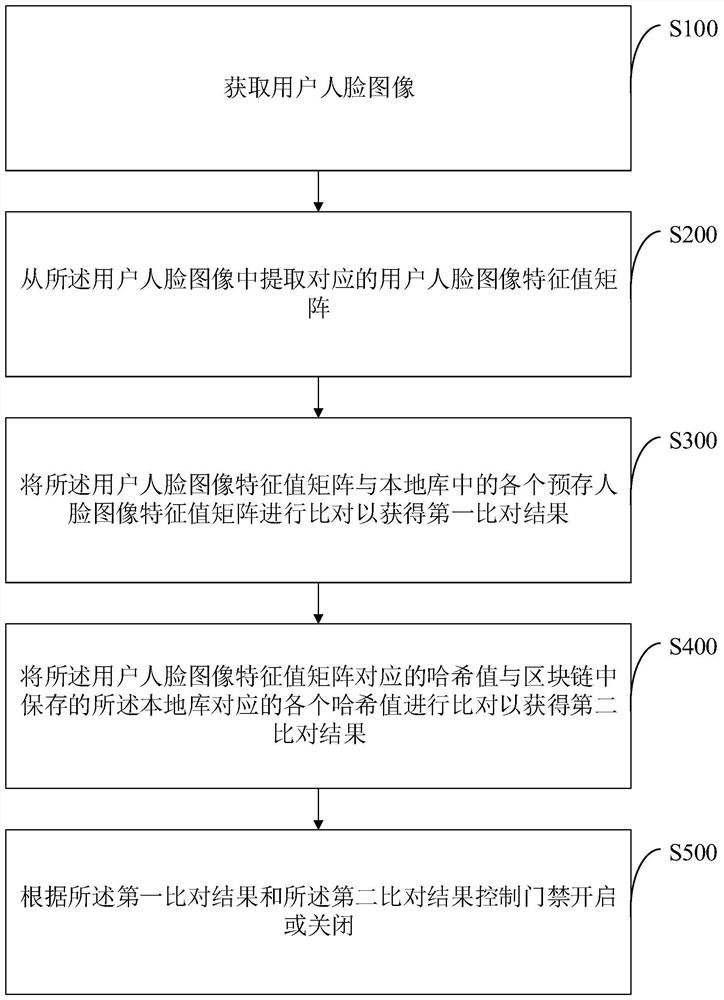
[0064] An example of this application, such as figure 1 As shown, a blockchain-based access control management method includes the following steps:
[0065] S100: Acquire a user face image.
[0066] When the user requests to open the access control, the access control device starts its own face acquisition unit, for example, a camera, uses the camera to acquire the current user's face image, and judges whether the acquired user's face image meets the requirements, for example, whether it is covered by sunglasses, masks Wait for the blocking object to block, if the acquired user's face image is not blocked and the picture is clear, then execute step S200.
[0067] S200: Extract a corresponding feature value matrix of the user's face image from the user's face image.
[0068] Since the face eigenvalue matrix is irreversible (that is, the face eigenvalue matrix obtained by the knowledge-based extraction method and the algebraic feature-based extraction method cannot be restor...
Embodiment 2
[0083] Furthermore, an embodiment of the present application also proposes to delete the user's face image immediately after the access control device obtains the user's face image and extracts the corresponding user's face image eigenvalue matrix from the user's face image. The access control device only stores the eigenvalue matrix of the face image, and does not save the user's face image. On the one hand, it can avoid the face image from occupying too much memory, and a smaller storage module can be set for the access control device to reduce the hardware cost of the access control device. On the other hand, the user's face image is immediately deleted, and the eigenvalue matrix of the face image stored in the access control device is irreversibly restored to the face, thereby effectively preventing the leakage of the user's face information.
Embodiment 3
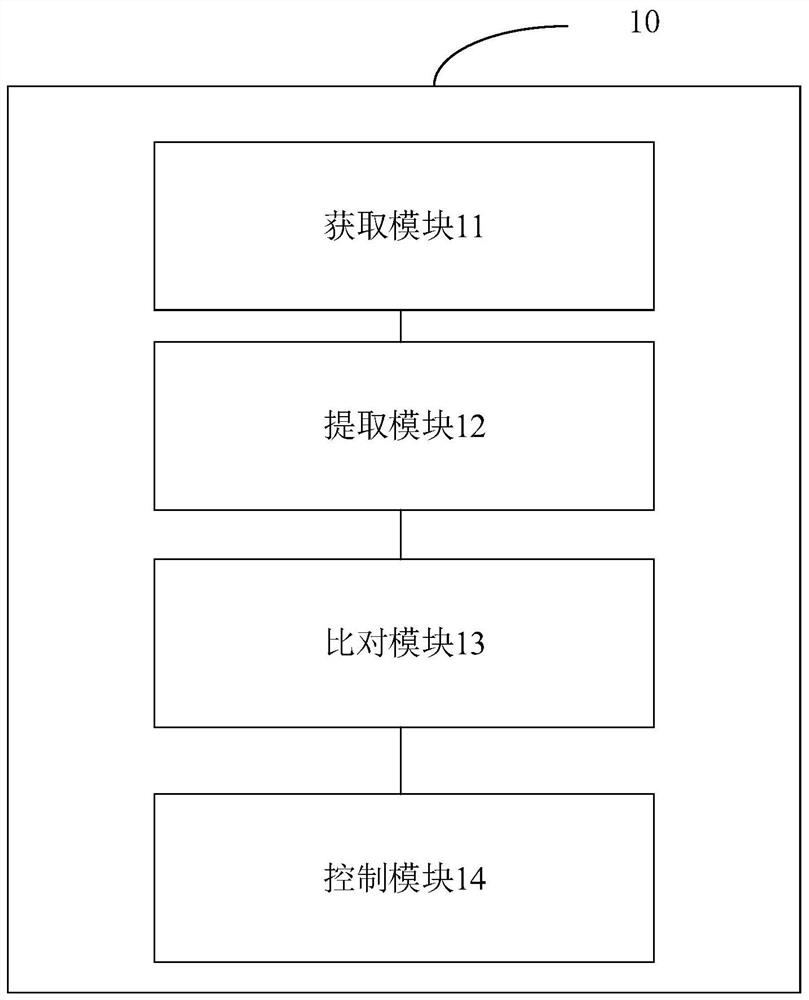
[0085] An example of this application, such as figure 2 As shown, a blockchain-based access control management device 10 is proposed including: an acquisition module 11 , an extraction module 12 , a comparison module 13 and a control module 14 .
[0086]Obtaining module 11, is used for obtaining user's face image; Extraction module 12, is used for extracting corresponding user's face image eigenvalue matrix from described user's face image; Comparison module 13, is used for described user's face The image eigenvalue matrix is compared with each pre-stored face image eigenvalue matrix in the local library to obtain the first comparison result; it is also used to compare the hash value corresponding to the user's face image eigenvalue matrix with the block chain The respective hash values corresponding to the local library stored in are compared to obtain the second comparison result; the control module 14 is used to control the opening or closing of the gate according to t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com