A Method of Traceable Data Security and Fidelity
A data security and data technology, applied in the field of communication security, can solve the problems of inability to restore data, inability to trace data traces, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
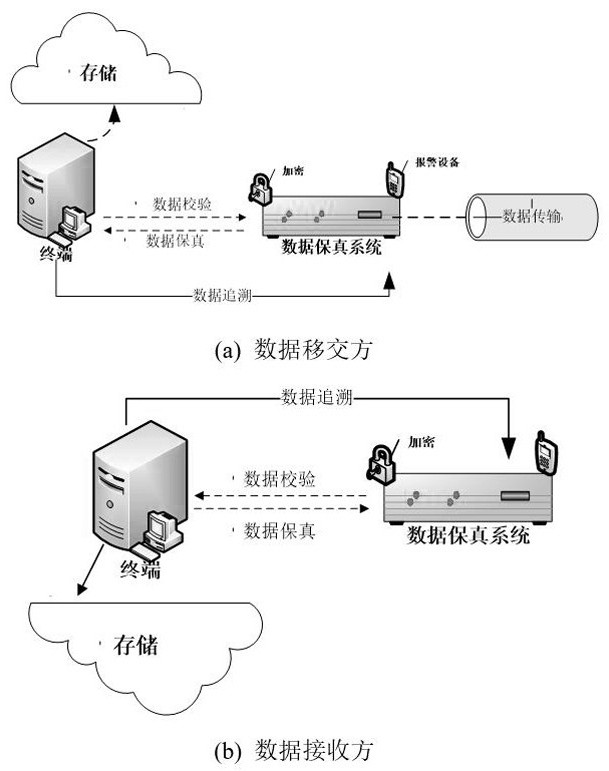
[0051] according to figure 1 As shown, a traceable data security system includes a data transfer party, a data receiver, and a data fidelity system; The guarantee method performs data exchange, thereby ensuring the completeness of the data.
Embodiment 2
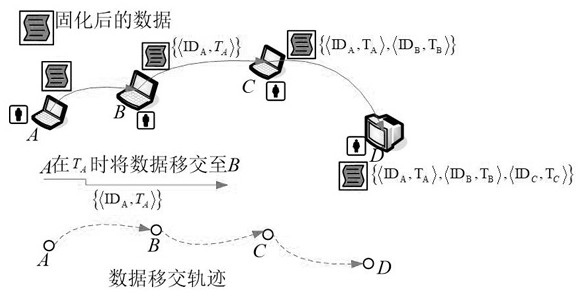
[0053] Under the traceable data security fidelity method, the steps of transferring data Data from node A to node B:
[0054] 1. Data solidification processing at node A:
[0055] 1) The data Data is used as the input of the Hash function, and the output is the data verification code H t ;
[0056] 2) Combine the data Data with the check code H t Perform lossless compression together to form data n_Data;
[0057] 3) Encrypt data n_Data using Advanced Encryption Standard (AES) to form ciphertext data (n_Data) AES , the ciphertext data is used as hardened data.
[0058] 2. Data preservation processing at node A:
[0059] 1) The curing data (n_Data) AES Fusion with timestamp Timestamp to form data {(n_Data) AES +Timestamp};
[0060] 2) put data {(n_Data) AES +Timestamp} for compression mapping and generate check code H time ;
[0061] 3) will solidify the data (n_Data) AES , timestamp Timestamp and check code H time merge into data {(n_Data) AES +Timestamp+H tim...
Embodiment 3
[0075] The difference from the above-mentioned embodiment 2 is that under the method of traceable data security and fidelity, another method of data preservation is adopted in the process of transferring data Data from node A to node B;
[0076] The steps are:
[0077] 1) Put the data (n_Data) AES Perform compression mapping to generate check code H;
[0078] 2) will solidify the data (n_Data) AES Combine the sum check code H into data {(n_Data) AES +H} back up together, and back up two copies.
[0079] Also, in the data transfer step: from data{(n_Data) AES +H} to reload the data and retransmit to node B.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com