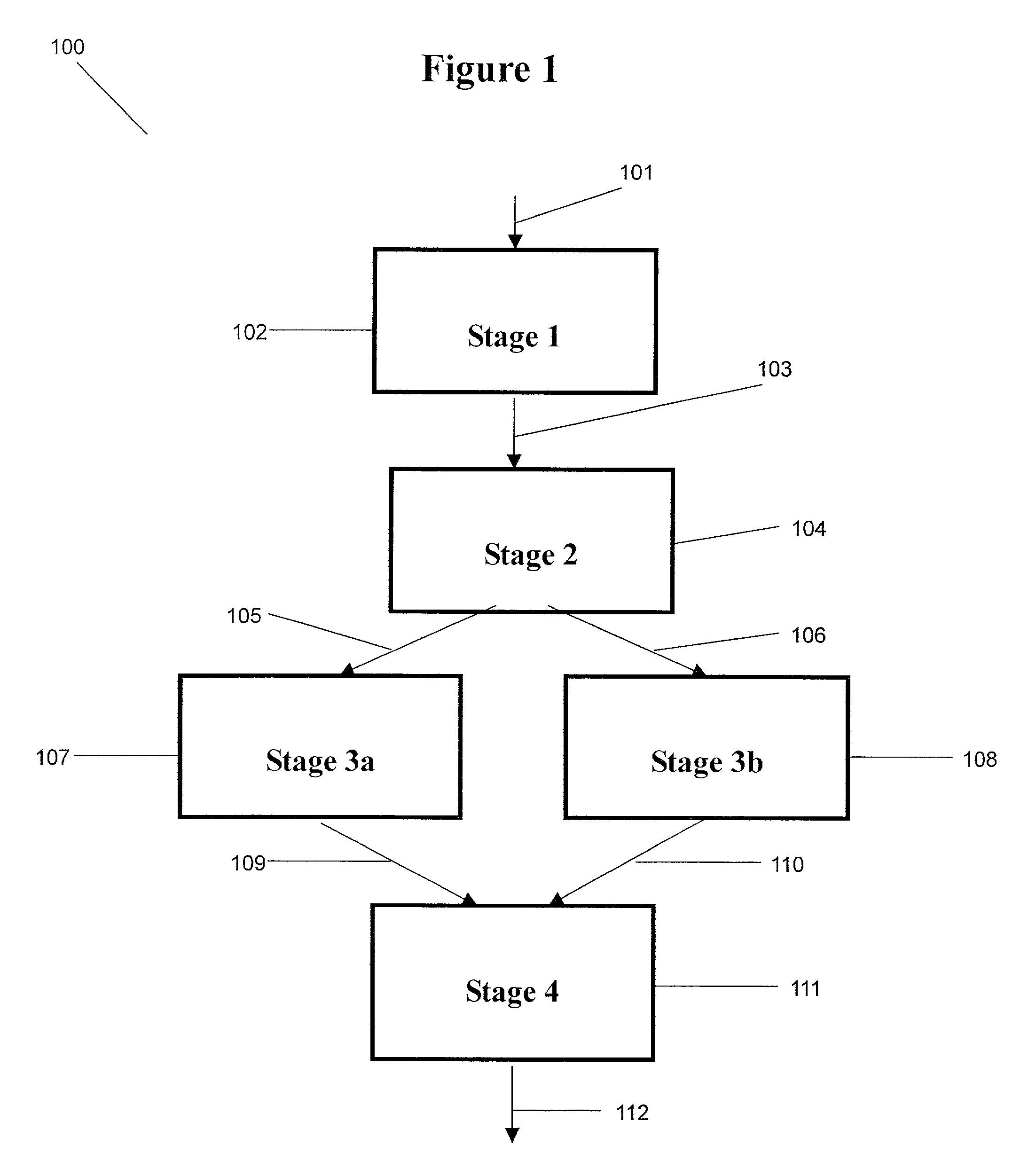
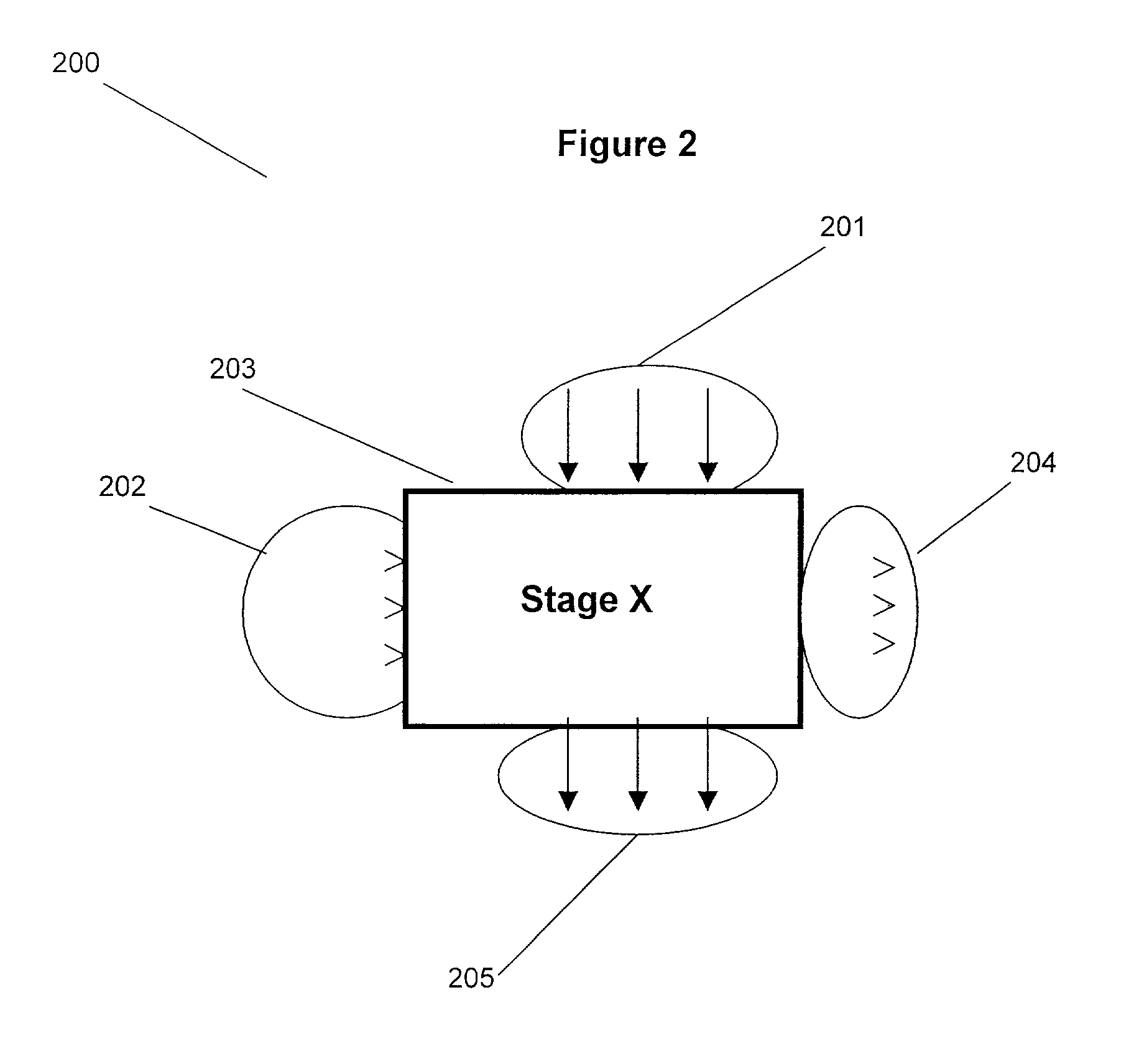
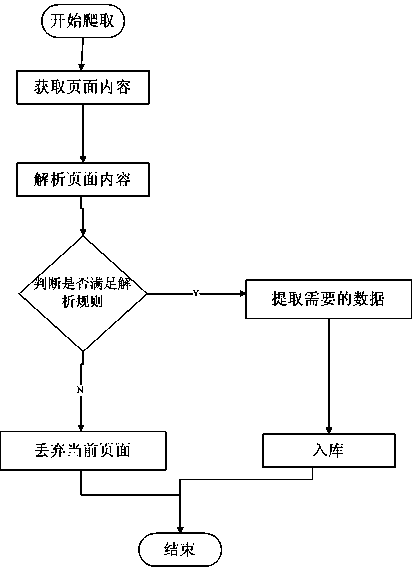
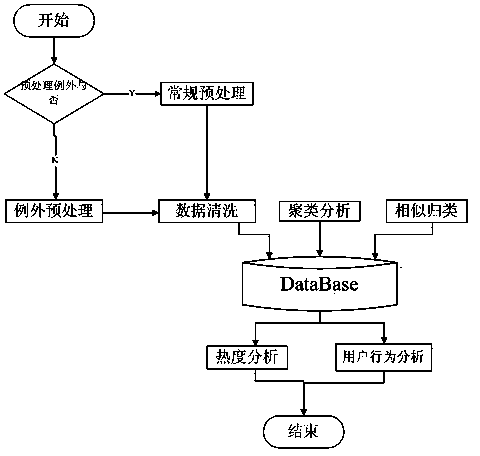
Patents
Literature
156 results about "Strategy method" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
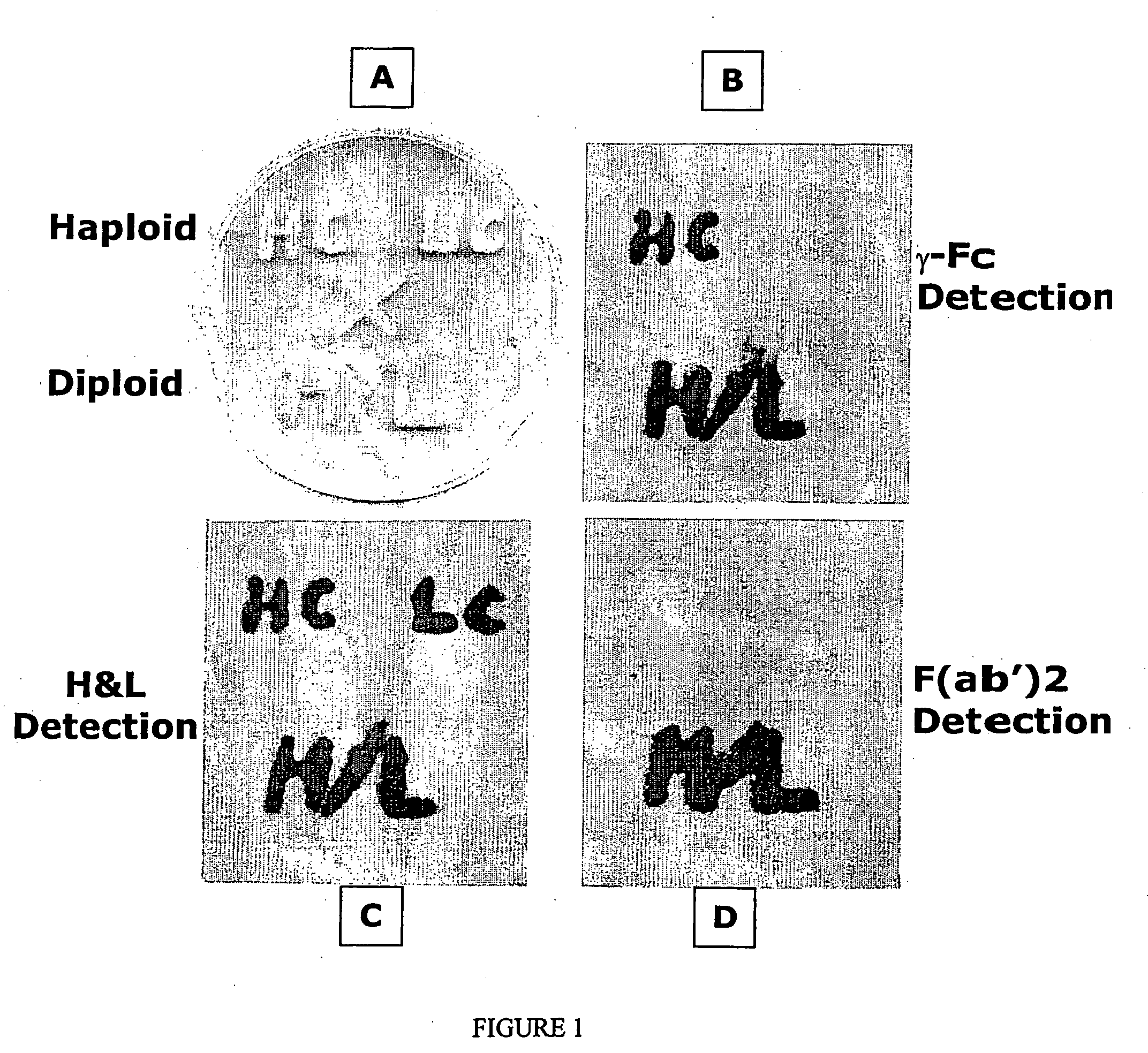
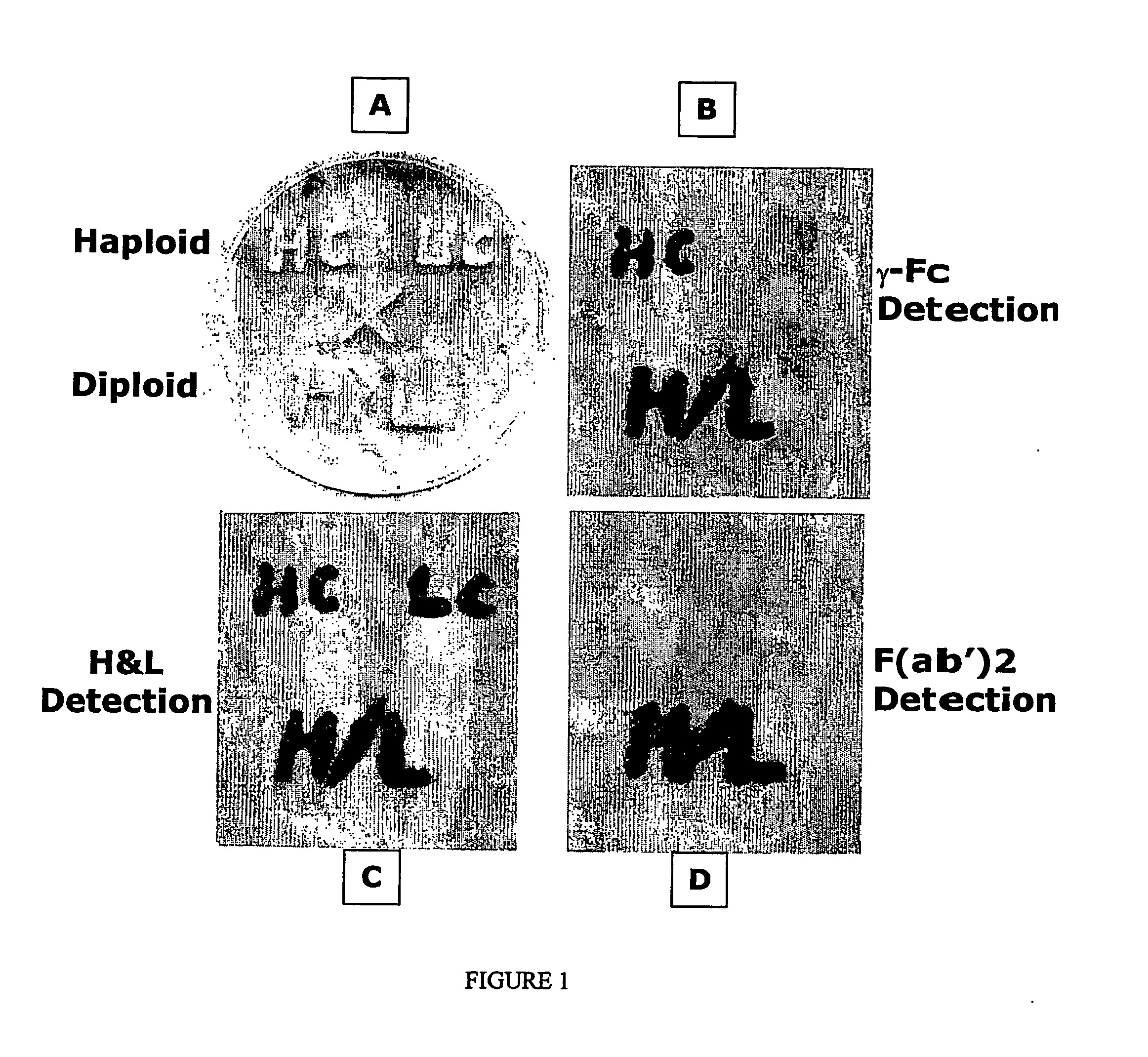
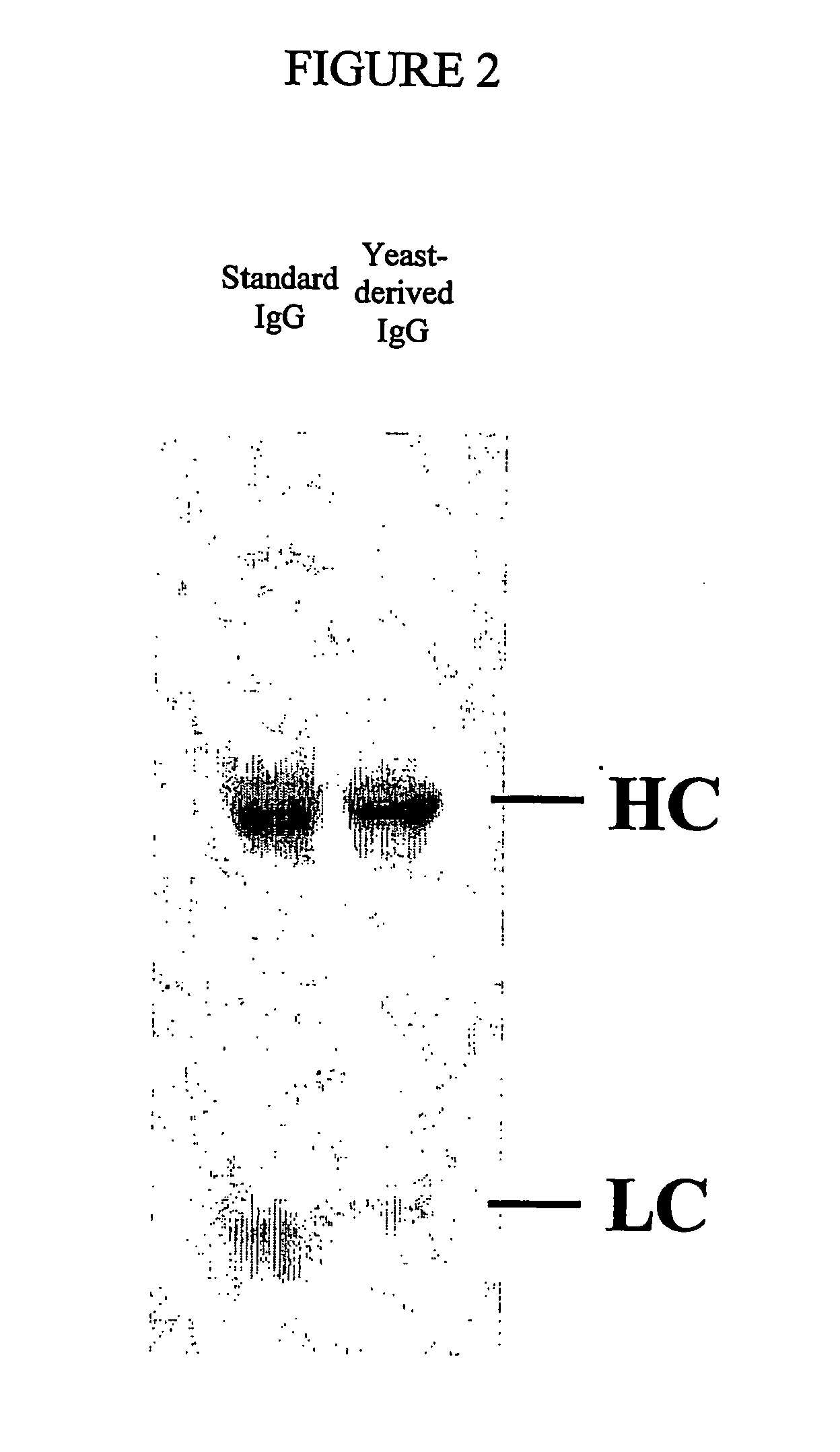
Methods of synthesizing heteromultimeric polypeptides in yeast using a haploid mating strategy
ActiveUS20060270045A1Enhance full-length product generationIncrease secretionFungiMicrobiological testing/measurementBiotechnologyMating
Methods are provided for the synthesis and secretion of recombinant proteins preferably large mammalian proteins or hetero-multimeric proteins at high levels and for prolonged time in polyploid, preferably diploid yeast. These methods use various mating competent yeast, including Pichia. In a preferred embodiment, a first expression vector is transformed into a first haploid cell; and a second expression vector is transformed into a second haploid cell. The transformed haploid cells, each individually synthesizing a non-identical polypeptide, are identified and then genetically crossed or fused. The resulting diploid strains are utilized to produce and secrete fully assembled and biologically functional hetero-multimeric protein.
Owner:KECK GRADUATE INST OF APPLIED LIFE SCI +1
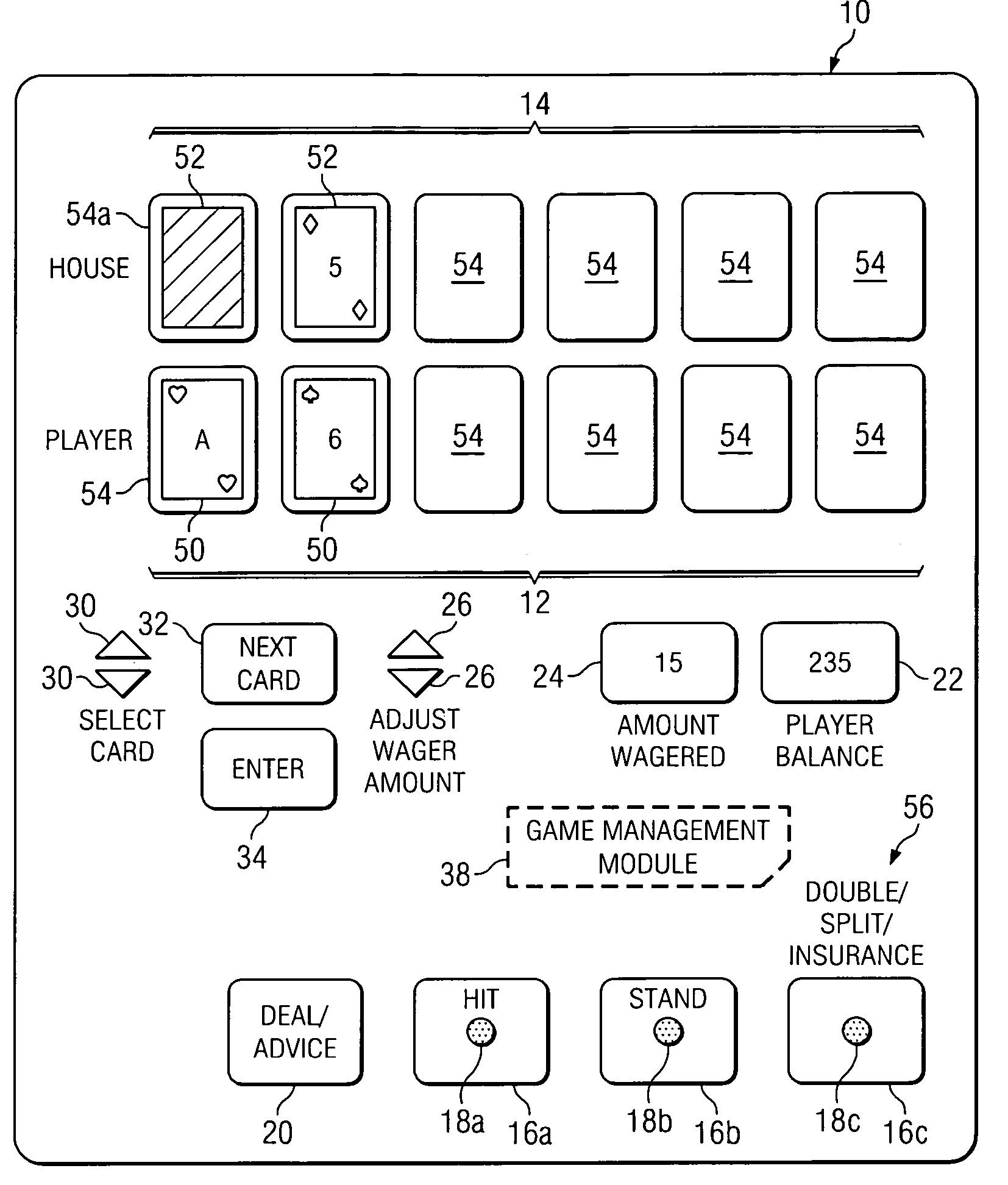
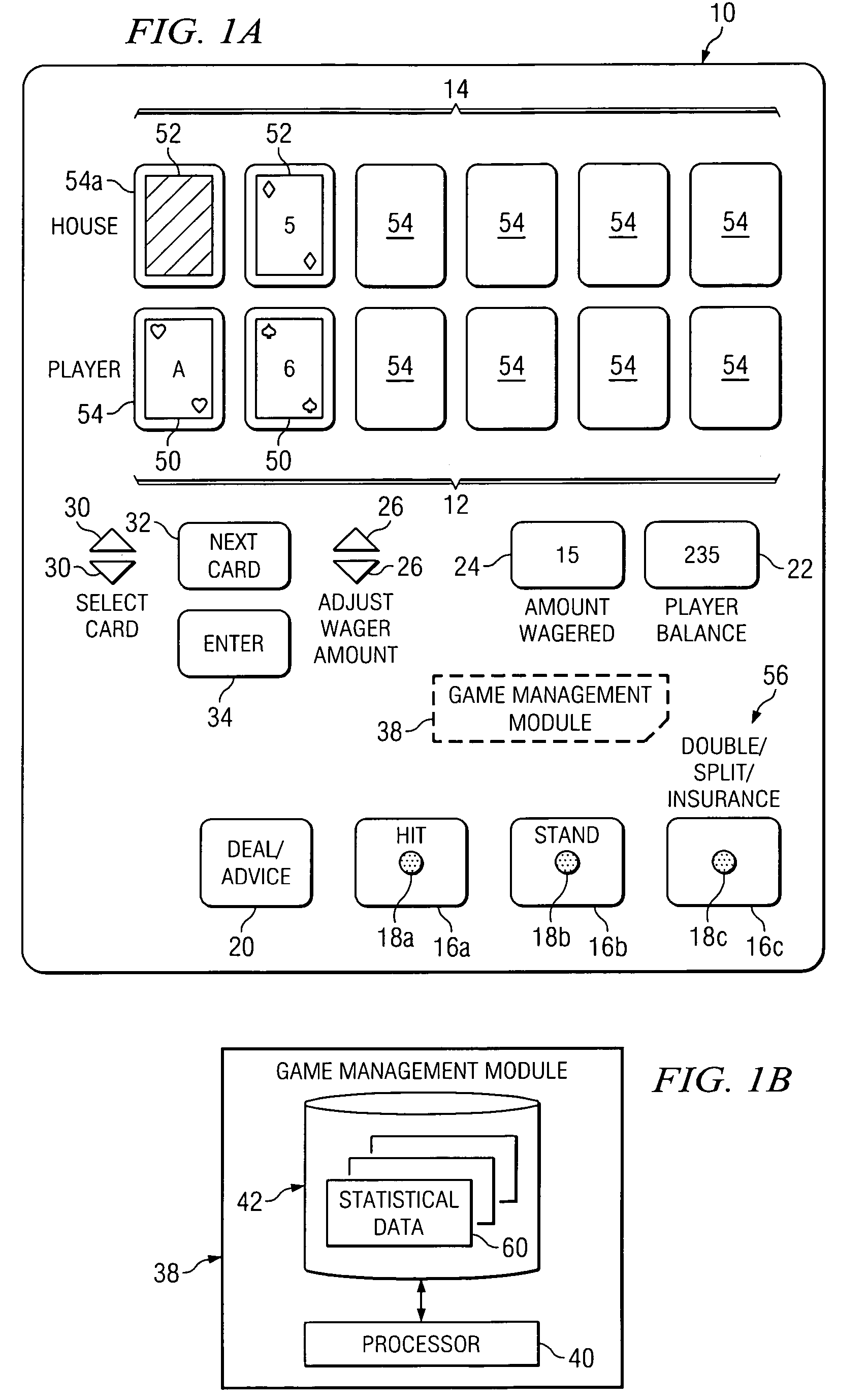
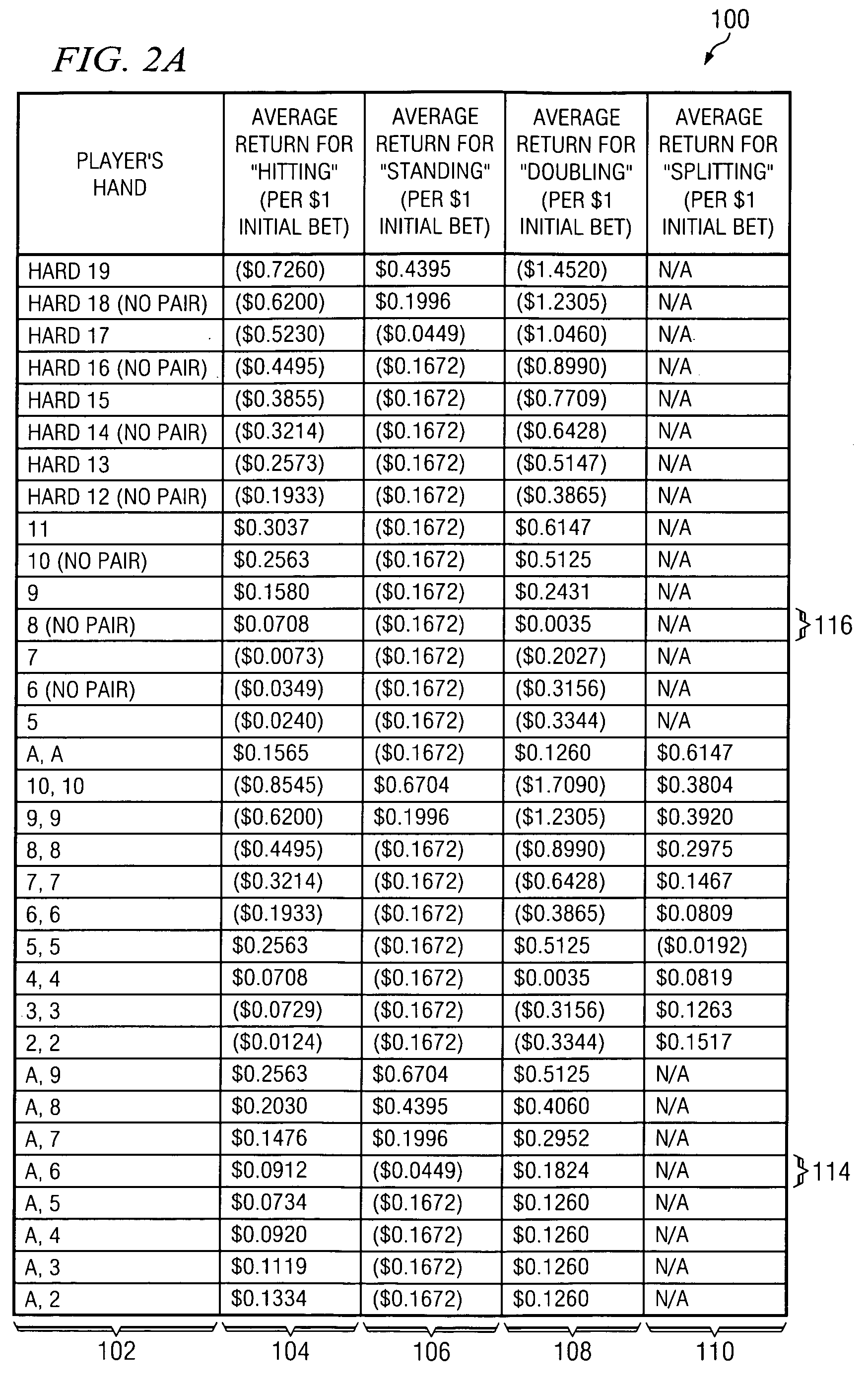
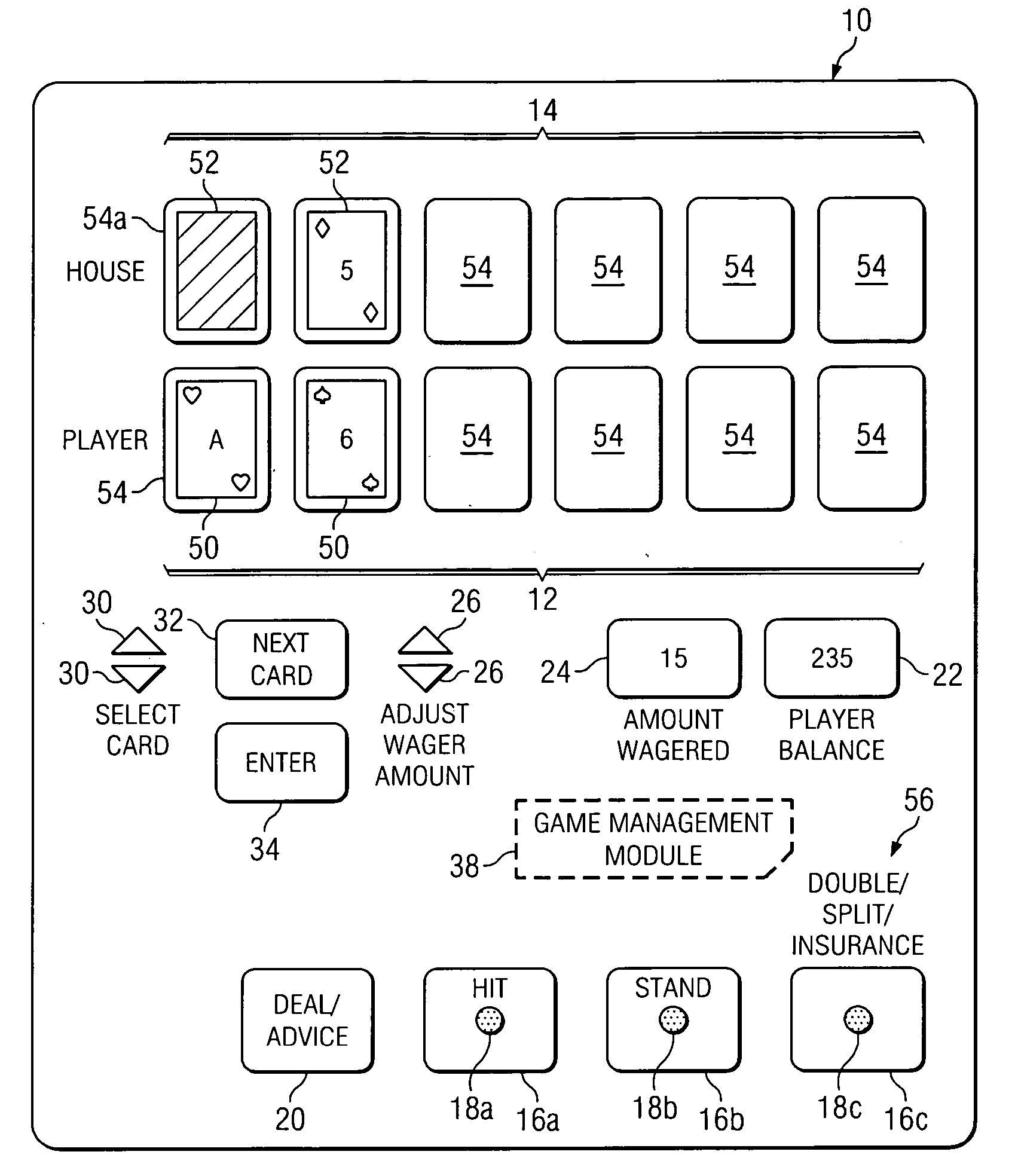
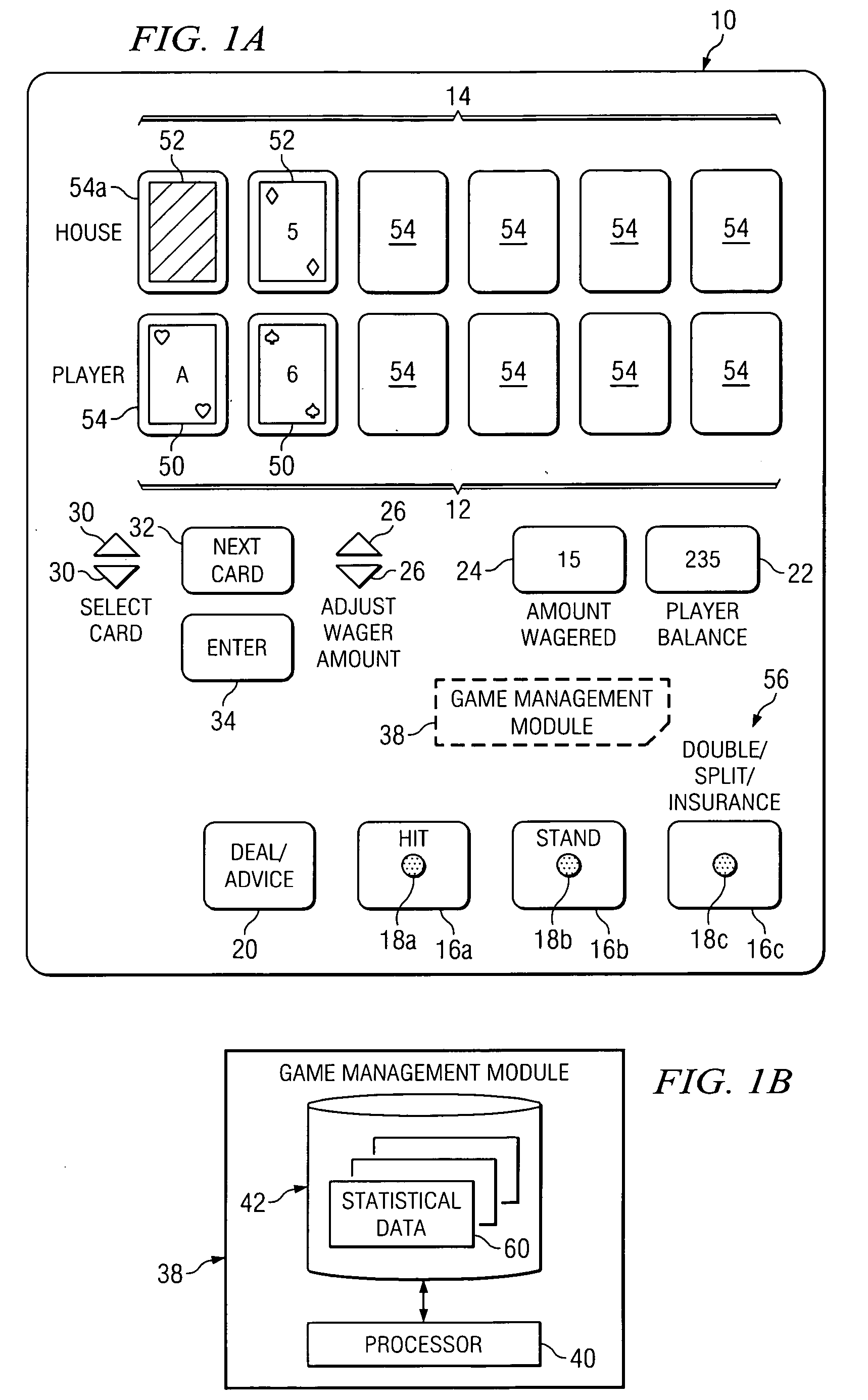
Method and apparatus for providing advice regarding gaming strategies
InactiveUS7452273B2Increase opportunitiesBoard gamesCard gamesHuman–computer interactionStrategy method
Owner:CANTOR INDEX
Method and apparatus for providing advice regarding gaming strategies
InactiveUS20050181851A1Increase opportunitiesIncrease chanceBoard gamesCard gamesHuman–computer interactionStrategy method
Owner:CANTOR INDEX
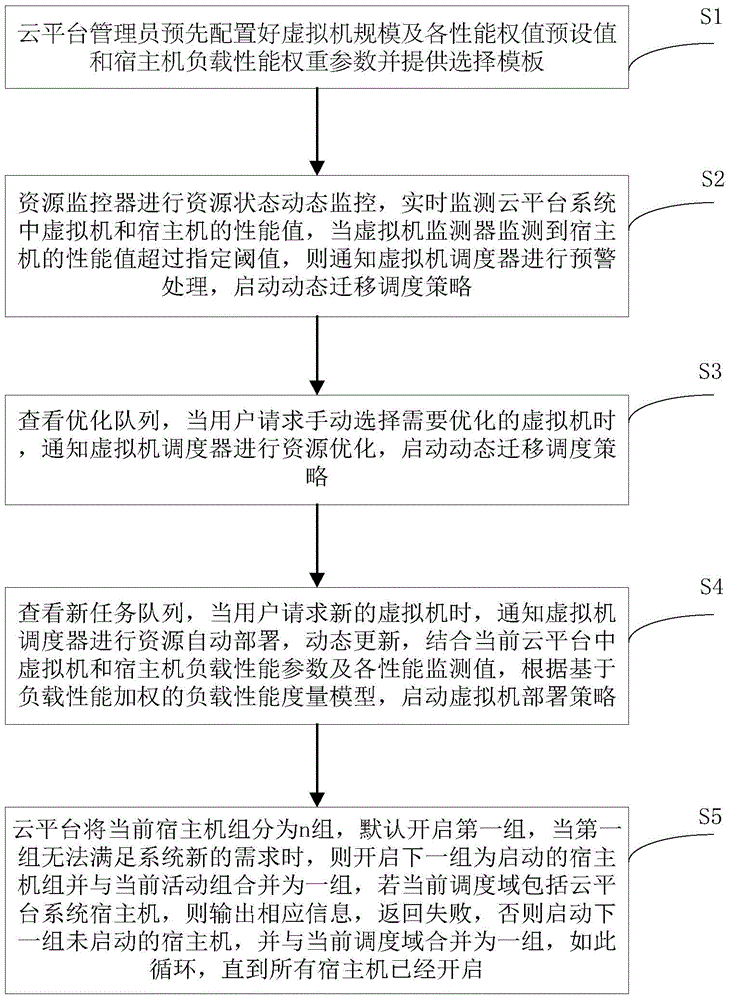
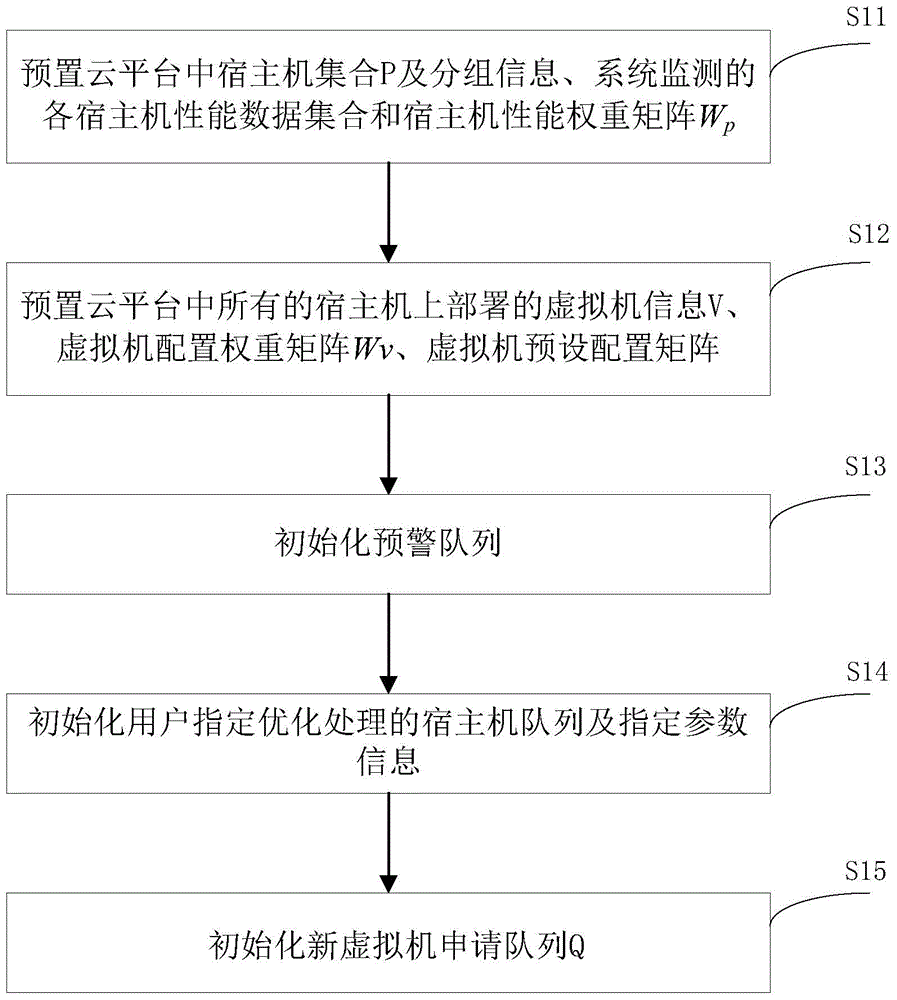
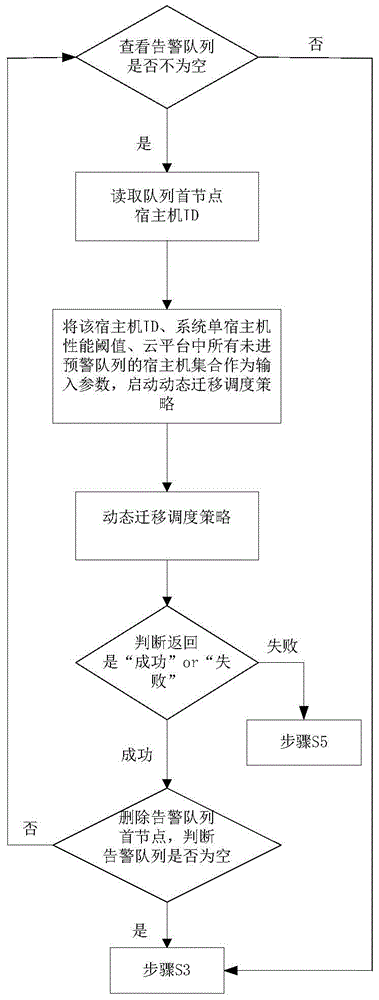
Dynamic virtual resource management strategy method for performance weighting under cloud platform
InactiveCN104010028AMaximize loadMinimize the number of physical servicesData switching networksUser needsPersonalization
The invention relates to the technical field of cloud computing, in particular to a dynamic virtual resource management strategy method for performance weighting under a cloud platform. According to the method, at first, contrast matrixes of various request resources and performance weighting values are configured, according to the needs of users and real-time monitoring data of the cloud platform, a load performance metric model based on load performance weighting is provided, and then the dynamic virtual resource management strategy method under the cloud platform is provided according to the model. The method comprises a virtual machine deployment strategy and a virtual machine transfer strategy, on the condition of meeting the existing load request, the cloud platform ensures that the load degree of a physical server in each scheduling area to be maximized, and on the basis, the number of the physical servers, needing to be started, of the cloud platform can be minimized. According to the method, the needs of the users are taken into consideration, data of individuation weight setting and cloud platform system real-time performance monitoring are given, the needs of QoS can be met, resources of the cloud platform system are utilized reasonably, and the load performance of the cloud platform is ensured.
Owner:SOUTH CHINA UNIV OF TECH
Method for constructing three-dimensional map by mobile robot in unknown environment
ActiveCN109341707AIntegrity guaranteedAchieve a full buildInstruments for road network navigationPosition/course control in two dimensionsDecision modelInformation gain
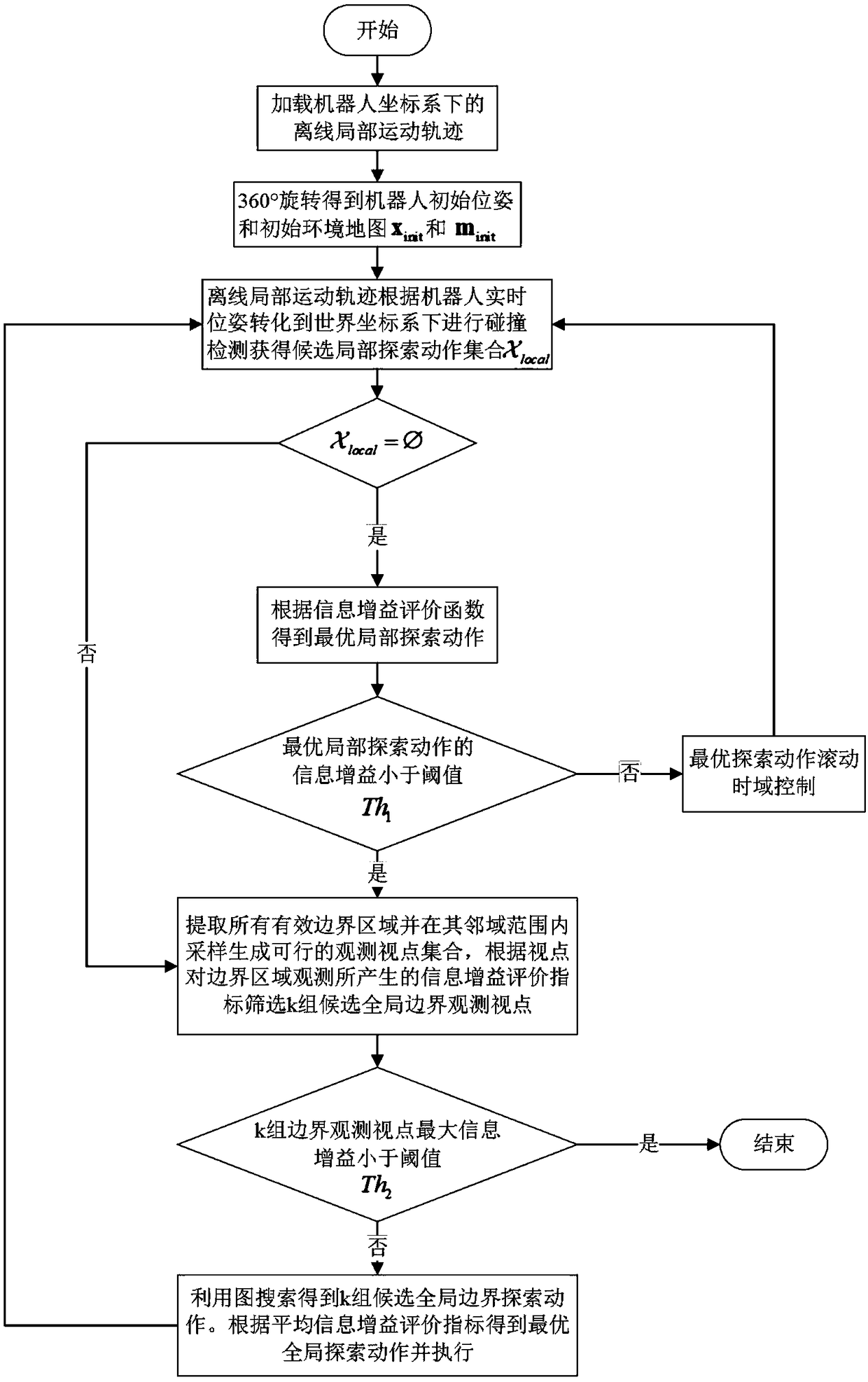
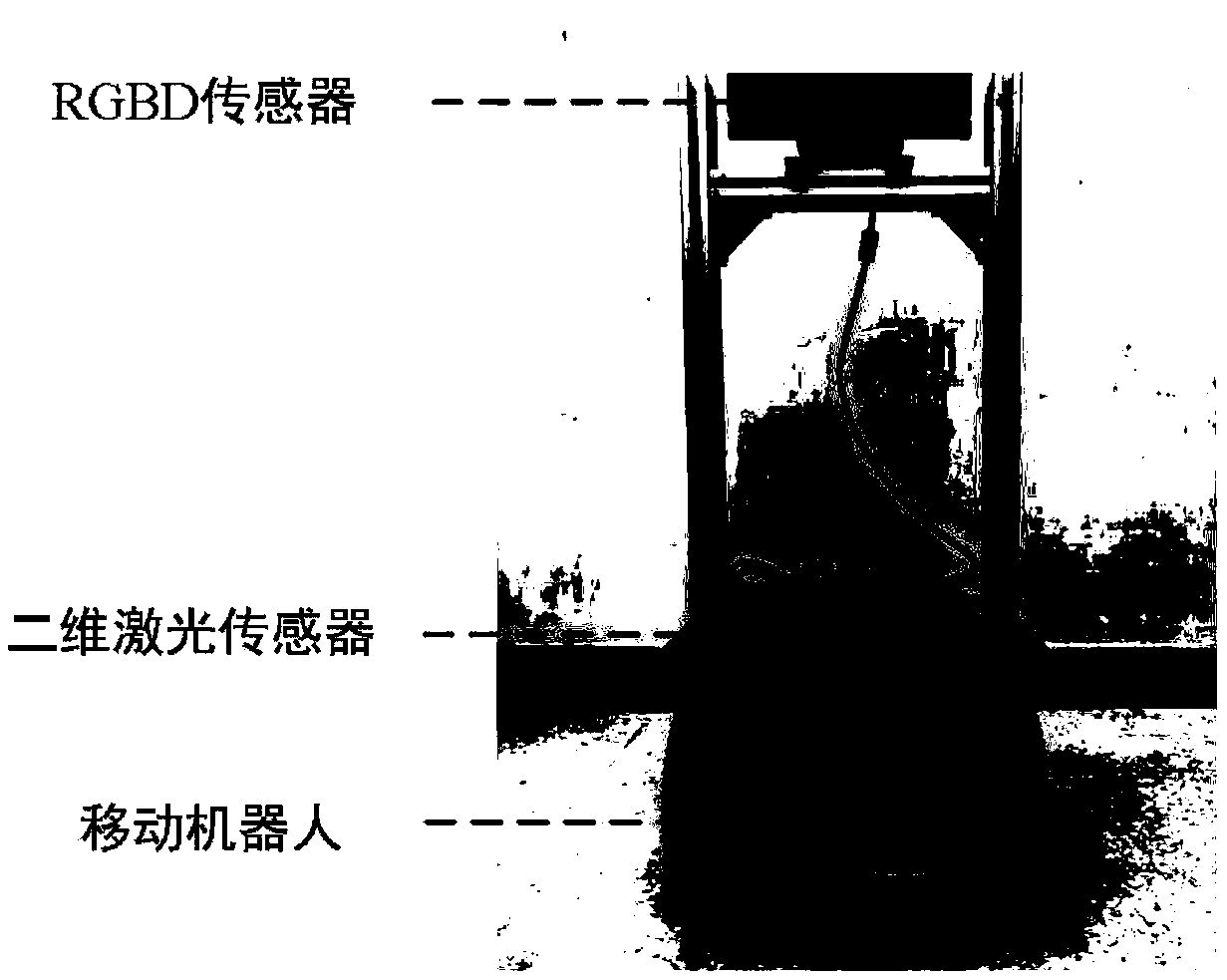
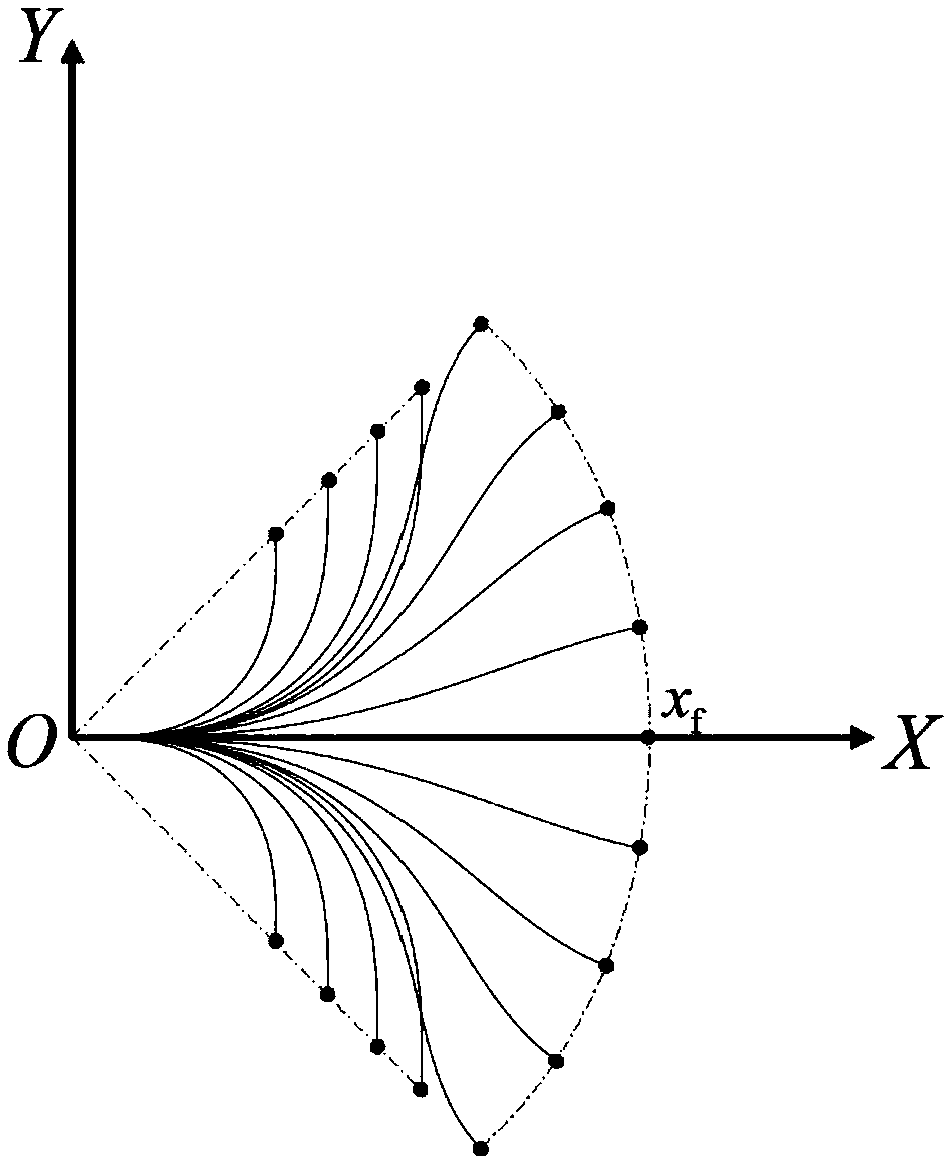
The invention discloses a method for constructing a three-dimensional (3D) map by a mobile robot in an unknown environment, and proposes a multi-exploration strategy method combining information gainguided local exploration strategy and global boundary exploration strategy for a problem of constructing a map of an indoor unknown 3D environment. The method comprises the following steps: firstly, constructing an autonomous exploration and 3D map construction system framework of the mobile robot, which comprises a map construction module and an exploration decision planning control module; secondly, establishing an information gain guided decision model based on a Shannon information theory and designing an information gain objective function calculation applied to multi-step exploration action evaluation; and finally, constructing a local exploration strategy by using an offline local motion trajectory, realizing a multi-strategy exploration method by combining with the information gainguided global boundary exploration strategy, and dynamically switching the two strategies during exploration according to real-time construction situations of the 3D map. Experimental results show that the method provided by the invention ensures integrity of map construction while rapidly constructing the 3D map.
Owner:NANKAI UNIV
Strategic method for process control
InactiveUS7461040B1Increase productivityImprove efficiencySpeech analysisSound input/outputData setValidation methods
A strategic method for process control wherein the method includes, for a predetermined process juncture, the steps of: (A) defining an interconnection cell having associated therewith (i) at least one set of input data or at least one set of process control parameters, and (ii) at least one set of output data; (B) assigning at least one boundary value to at least one set of the sets associated with the defined interconnection cell; (C) using the assigned at least one boundary value, forming a plurality of discrete respective set combinations, and (D) for the interconnection cell, processing data from the plurality of respective formed set combinations into respective corresponding data record clusters.The strategic method for process control is a continuation-in-part of a Knowledge-Engineering Protocol-Suite, (U.S. patent application Ser. No. 09 / 588,681 filed on 7 Jun. 2000) incorporated herein by reference, that generally includes methods and systems, apparatus for search-space organizational validation, and appurtenances for use therewith. The protocol-suite includes a search-space organizational validation method for synergistically combining knowledge bases of disparate resolution data-sets, such as by actual or simulated integrating of lower resolution expert-experience based model-like templates to higher resolution empirical data-capture dense quantitative search-spaces. The protocol-suite includes facile algorithmic tools for use with the method.
Owner:ADA ANALYTICS ISRAEL
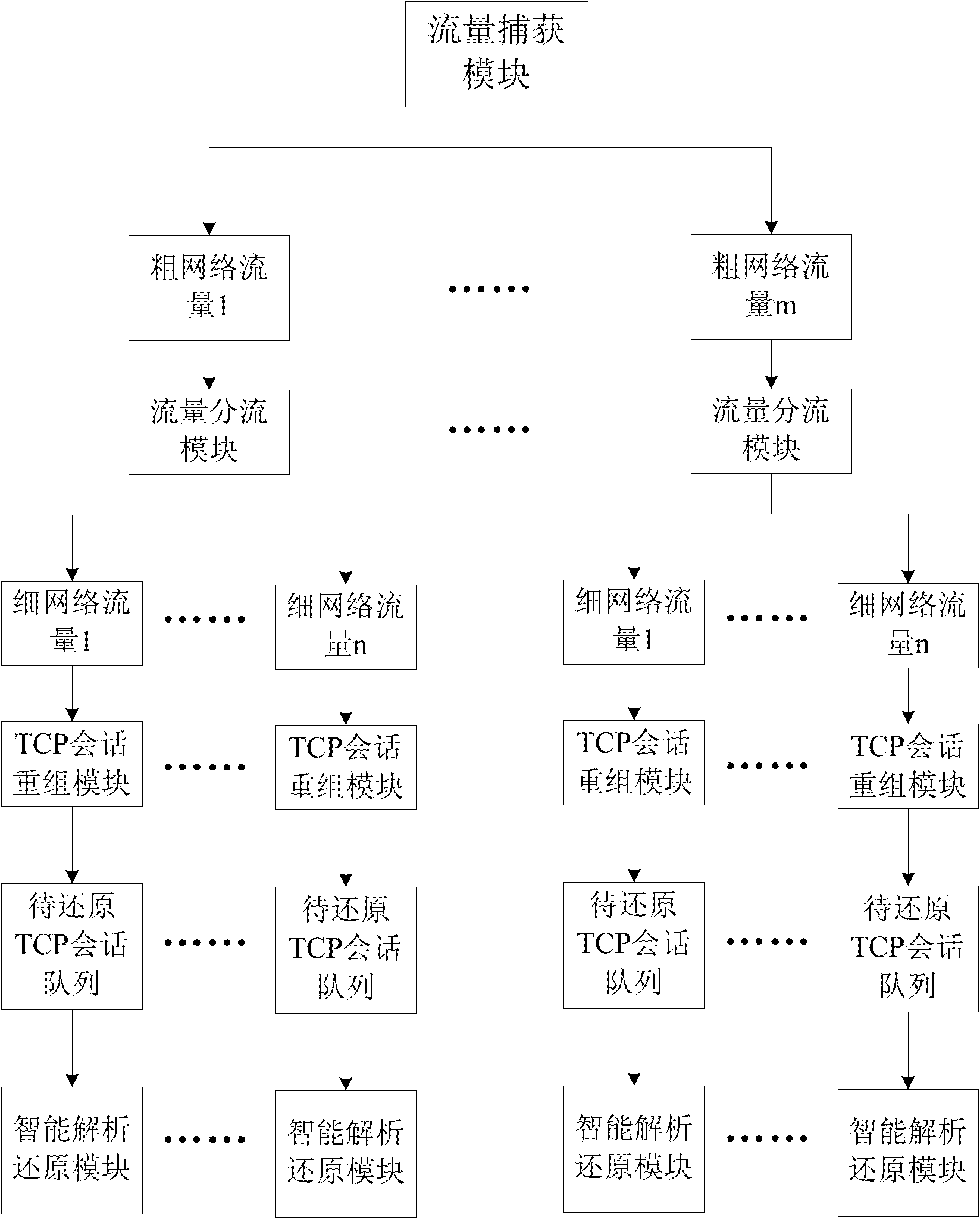
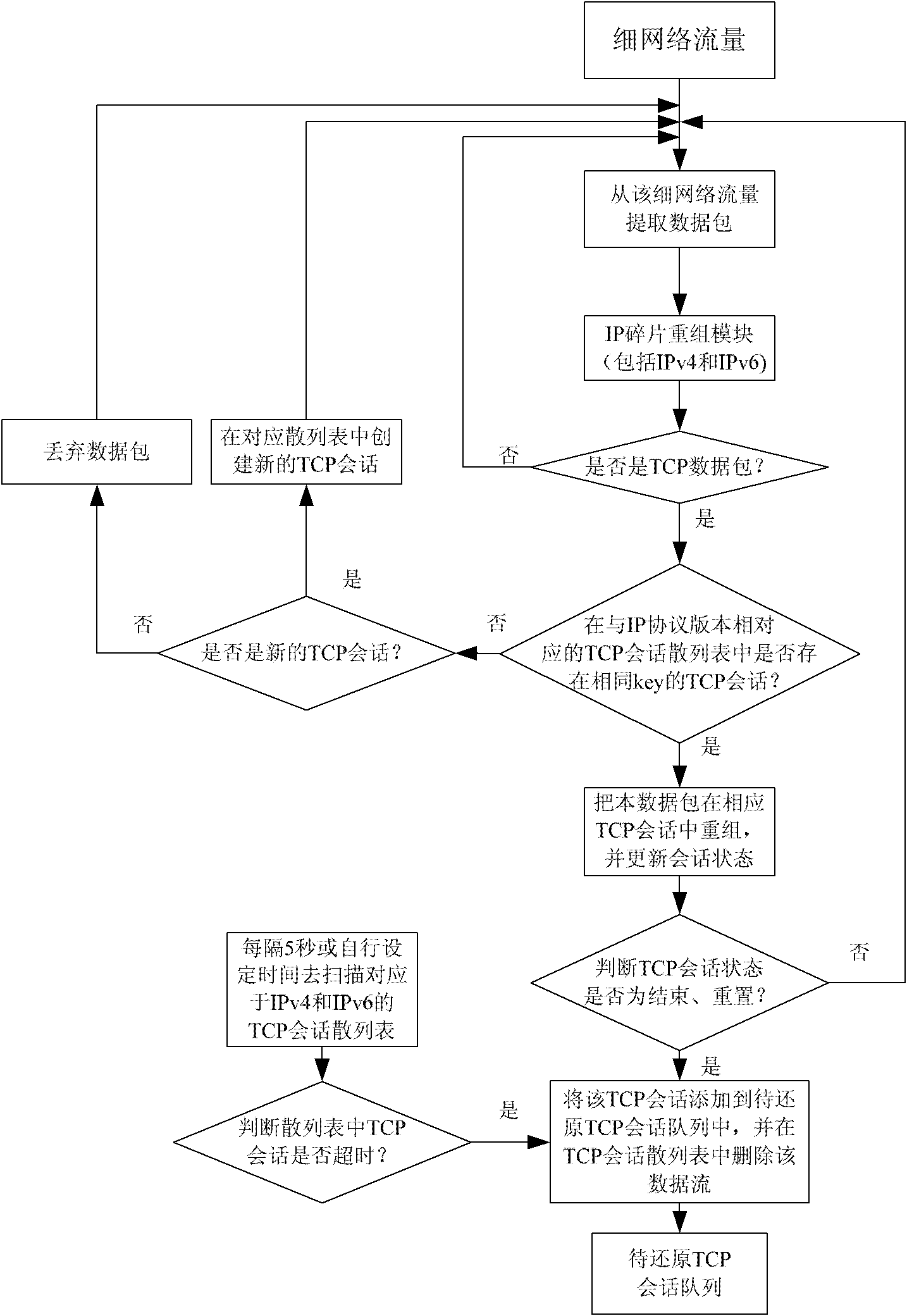
Network flow recovery method
The invention relates to a network flow recovery method, which belongs to the technical field of Internet and discloses a method for recovering network flow to a file. The method adopts a two-stage parallel strategy method to fully make the best of the processing efficiency of a multi-core computer, which comprises the following steps: firstly acquiring high-speed flow, adopting a Mac address xor and IP address xor method to split flow twice, and resolving the acquired initial flow into a plurality of thin flows to realize the two-stage parallel resolution of the flow; then adopting a 'producer-consumer model' loose coupling multithreading framework between working modules with data transfer in a thin flow recovery flow path to realize parallel on a threading level. In addition, the method realizes load balancing on each thin flow, and supports IPv4 and IPv6 protocols simultaneously. The invention aims to solve the problem of converting 'invisible' network flow into information which can be directly processed by a computer under high-speed network bandwidth, and provides technical support for identifying and blocking illegal network information transmission.
Owner:XI AN JIAOTONG UNIV
Low-orbit satellite routing strategy method based on deep reinforcement learning architecture
ActiveCN110012516AReduce complexityReduce storage overheadRadio transmissionNeural architecturesDependabilityOrbit
The invention discloses a low-orbit satellite routing strategy method based on a deep reinforcement learning architecture, and belongs to the field of wireless communication. Firstly, an iridium constellation network is established, and a deep reinforcement learning framework is established in combination with a Markov decision process; and for a certain satellite node A, a HELLO packet is periodically sent to a neighbor node, and an adjacent node communicated with the link state of the current node A is searched, a next hop node of a current node is obtained by inputting a destination node coordinate, a link state of the current node and a link state of a neighbor node into a deep reinforcement learning architecture, and a next hop node is continuously obtained in the same way; and when aspecial routing condition (such as open circuit, loop and congestion) occurs, a link state is repeatedly input into the deep reinforcement learning architecture by adopting a corresponding solution strategy until a destination node is reached, and a path planning process is finished. According to the method, the system complexity and the storage overhead are reduced, the effect of detecting the satellite link state in real time is achieved, and satellite routing is more stable and reliable.
Owner:BEIJING UNIV OF POSTS & TELECOMM
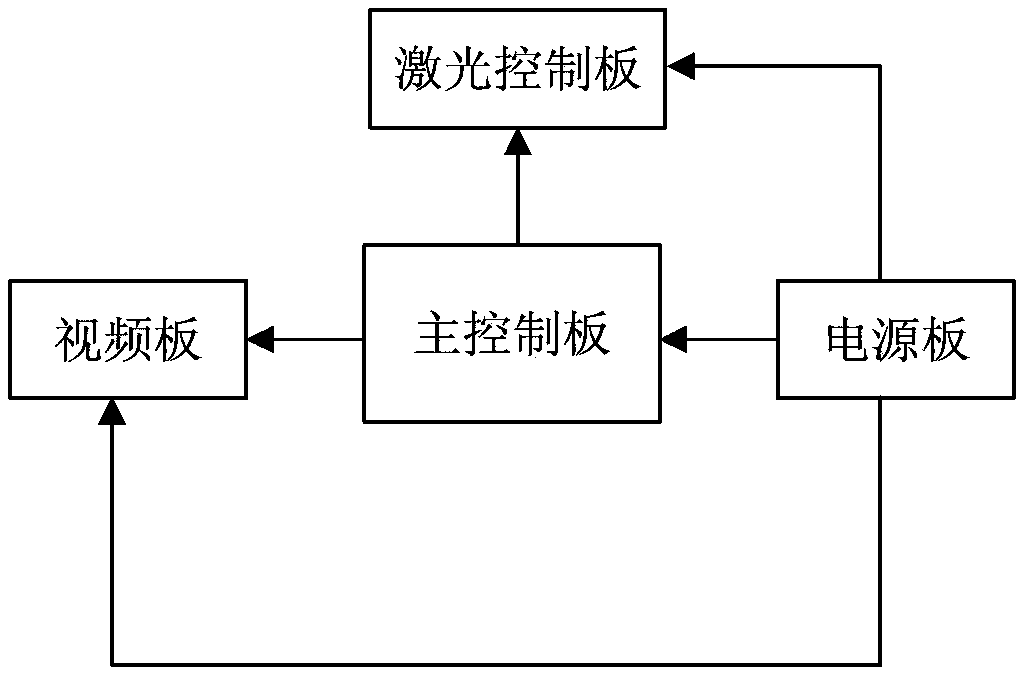
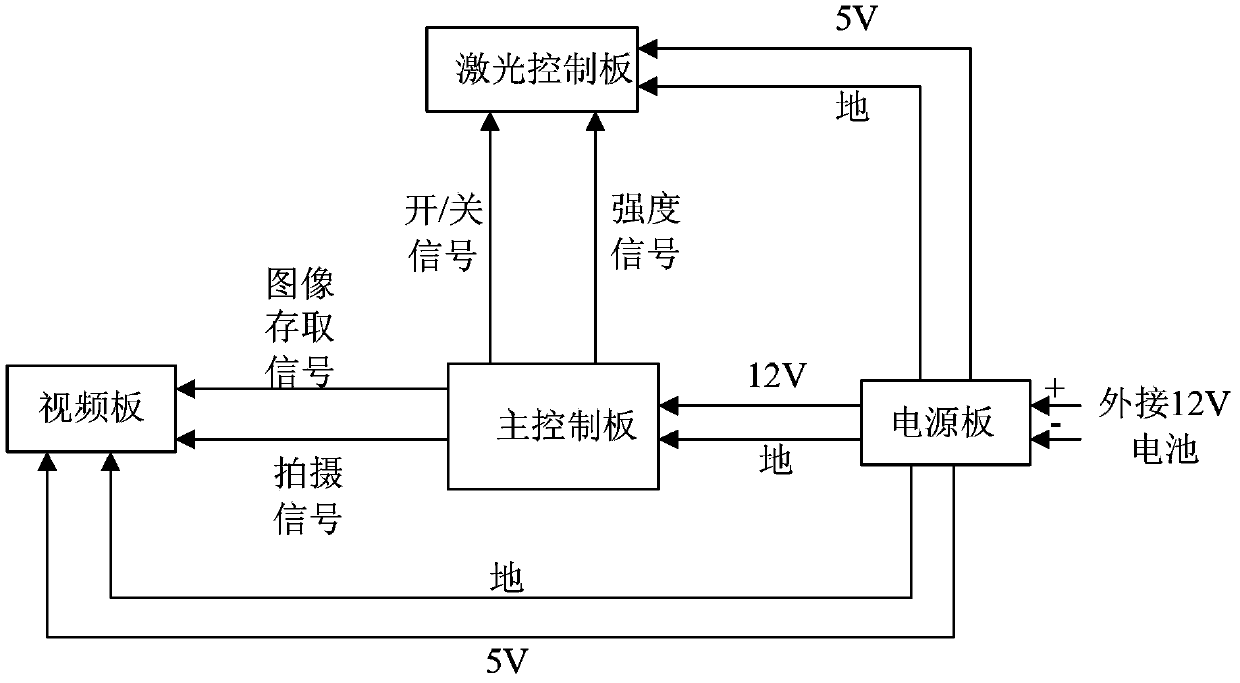
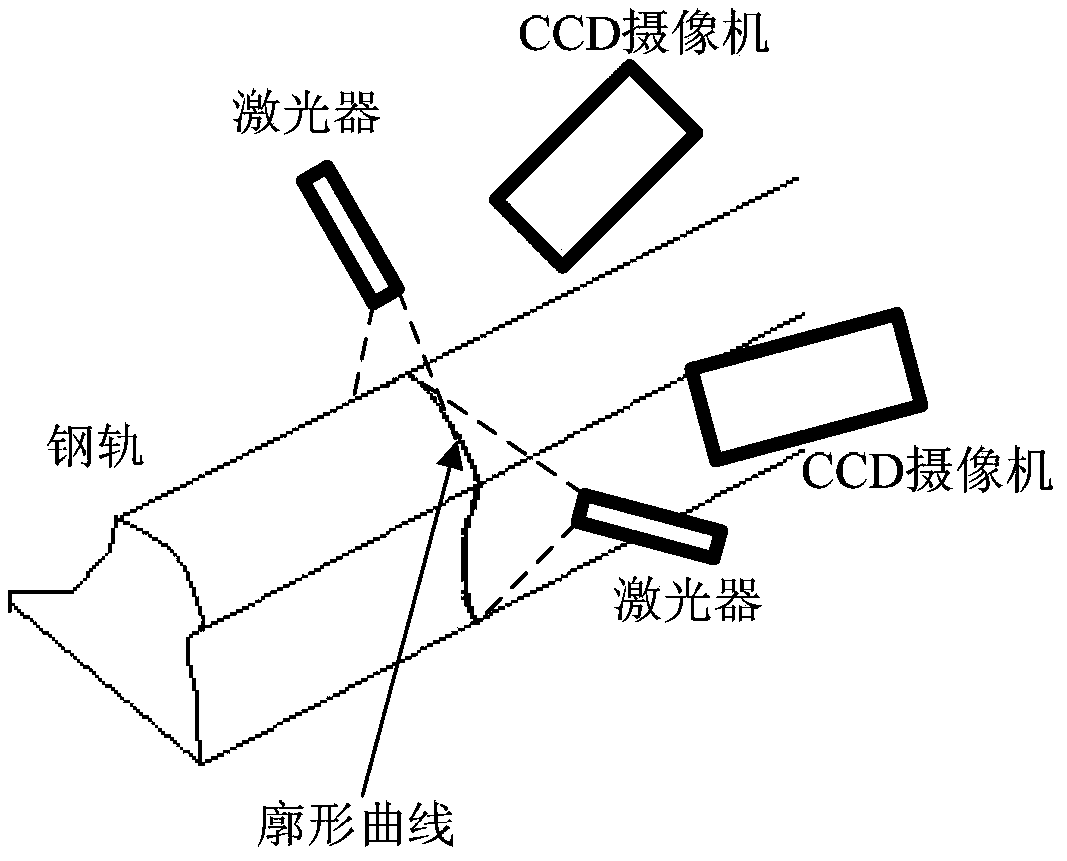
Steel-rail wear measurement device based on machine vision and grinding strategy method thereof
InactiveCN104180767AMeet the selection needsGrinding feed controlUsing optical meansMeasurement deviceHigh power lasers
The invention provides a steel-rail wear measurement device based on machine vision, which comprises a main control panel, a power panel, a laser control panel, and a video panel. The power panel is used for providing a stable direct-current voltage for the main control panel, the laser control panel and the video panel. The laser control panel is electrically connected with two high-power lasers. The video panel is electrically connected with two CCD cameras. The main control panel is connected with the power panel, the laser control panel, and the video panel, and used for controlling the on-off and intensities of the two high-power lasers and controlling the shooting actions of the two CCD cameras. The invention also provides a grinding strategy method for steel-rail wear according to the measurement device. According to a planned grinding quantity, a proper grinding speed of a steel-rail grinding car, the grinding power, and the motor distribution of different angles are calculated, and the steel rail is grinded. The steel-rail wear measurement device based on machine vision has the beneficial effects that the planned grinding area of the steel rail on side can be calculated according to different zones, and shortcomings of large amount of labor, poor environment, low efficiency and the like of the measurement mode of manual and mechanical contact can be overcome.
Owner:中国铁路武汉局集团有限公司武汉大型养路机械运用检修段 +1
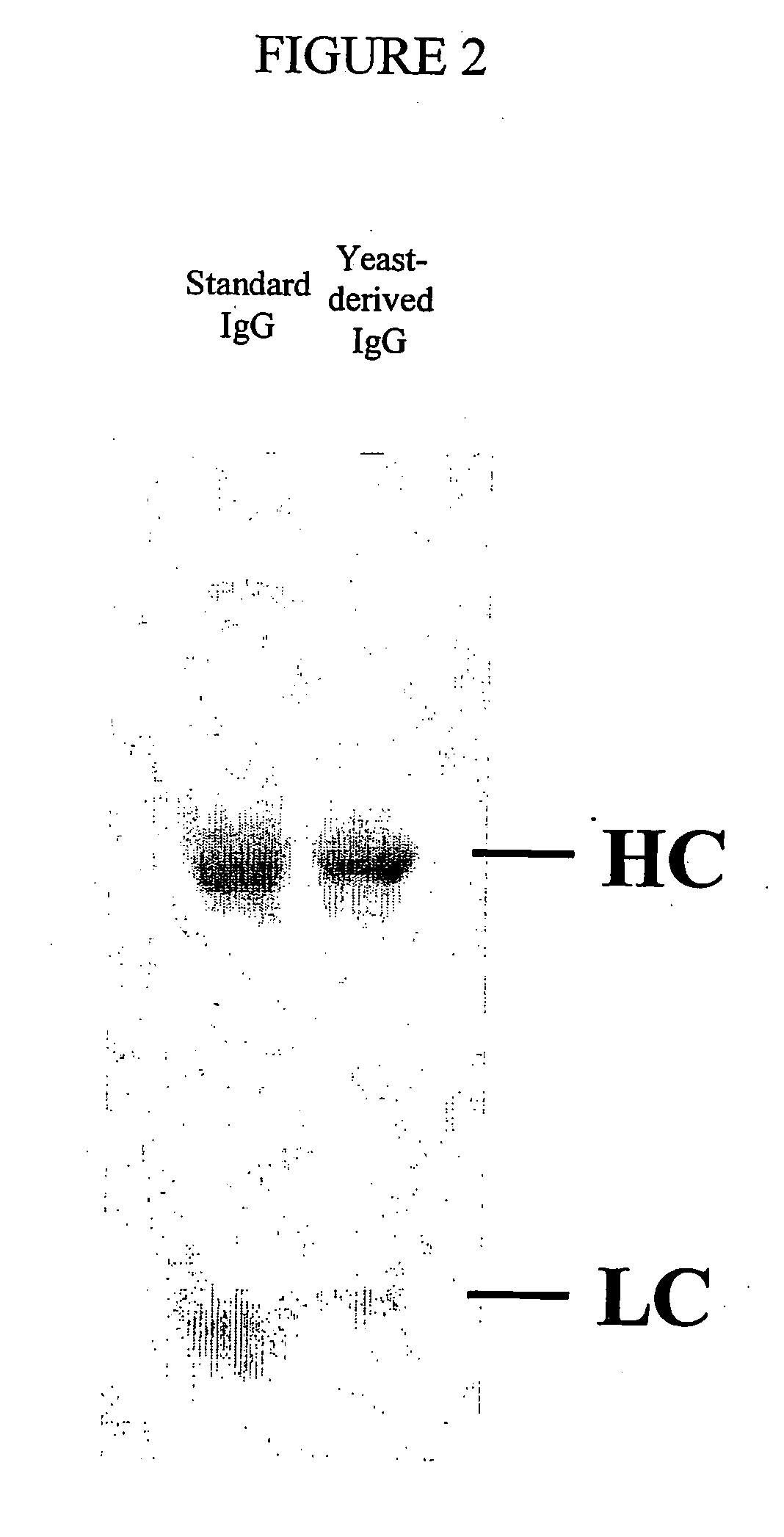
Methods of Synthesizing Heteromultimeric Polypeptides in Yeast Using a Haploid Mating Strategy
ActiveUS20080003643A1Enhance generationIncrease secretionMicroorganismsImmunoglobulins against cell receptors/antigens/surface-determinantsBiotechnologyYeast
Methods are provided for the synthesis and secretion of recombinant hetero-multimeric proteins in mating competent yeast. A first expression vector is transformed into a first haploid cell; and a second expression vector is transformed into a second haploid cell. The transformed haploid cells, each individually synthesizing a non-identical polypeptide, are identified and then genetically crossed or fused. The resulting diploid strains are utilized to produce and secrete fully assembled and biologically functional hetero-multimeric protein.
Owner:H LUNDBECK AS +1
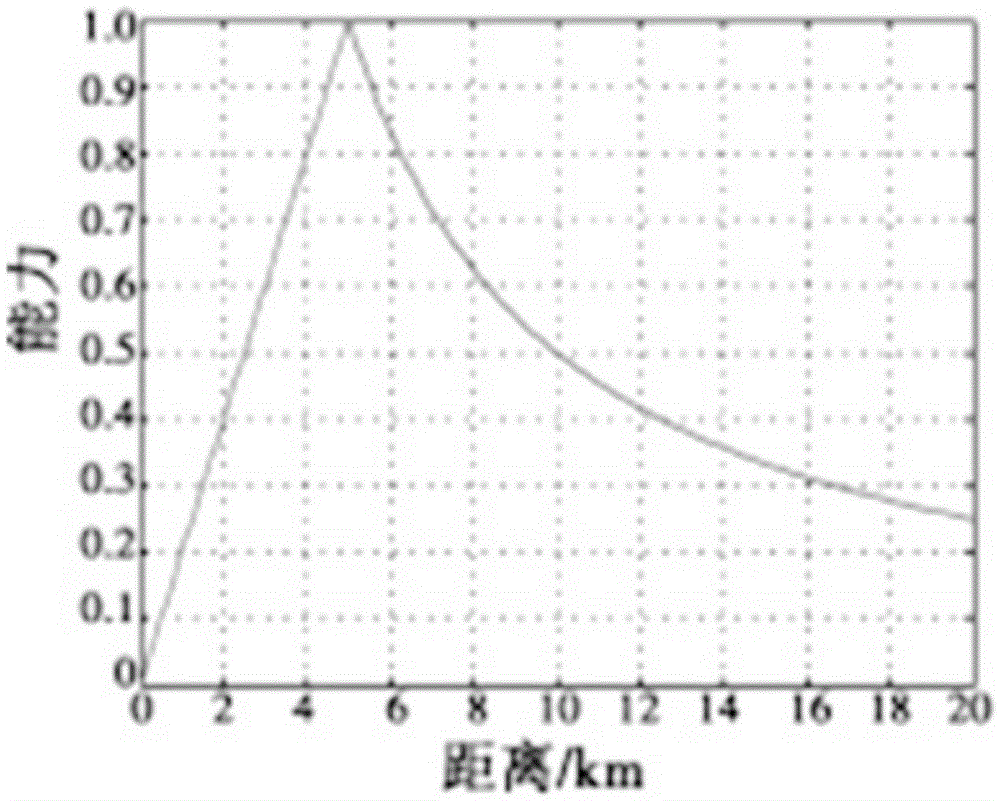
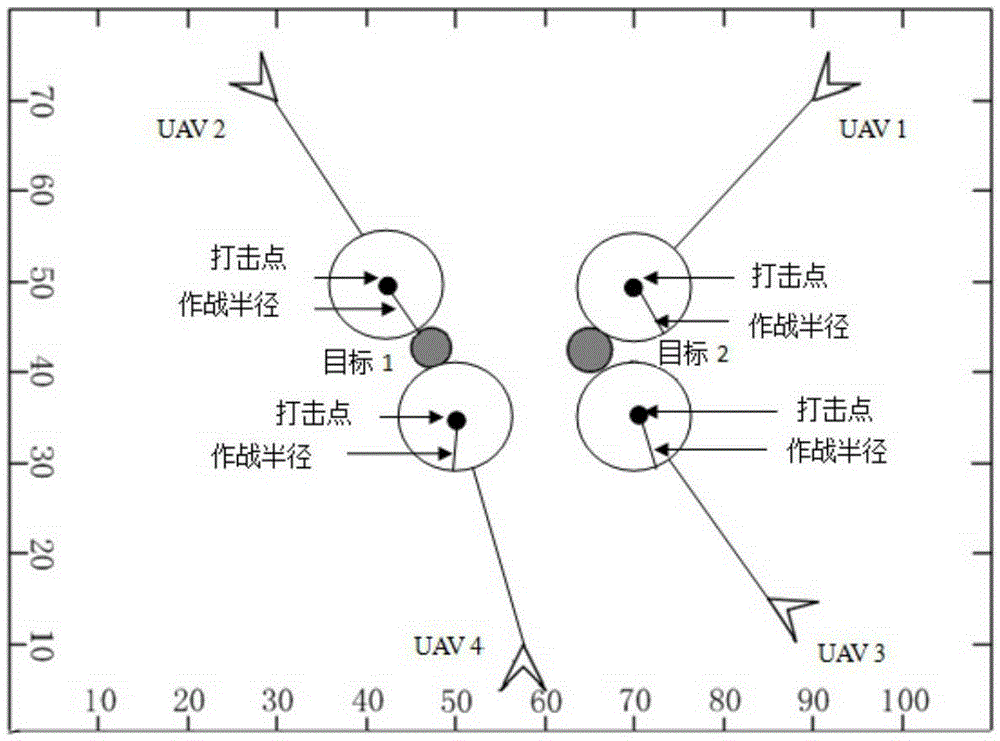
Counter-attack countermeasure optimal strategy method for multi-unmanned plane cooperative strike task
InactiveCN105278542AImprove coordinated strike capabilityEstimated benefit value is largeAdaptive controlPosition/course control in three dimensionsCountermeasureSimulation
The invention aims to solve the problem of a counter-attack countermeasure optimal strategy for a multi-unmanned plane cooperative strike task and belongs to the technical field of multi-unmanned plane cooperative control. The invention combines a capability function with a multi-unmanned plane cooperative strike counter-attack countermeasure model and provides a counter-attack countermeasure method for the multi-unmanned plane cooperative strike. Firstly, the capability function of an unmanned plane is established; then by means of a jacobian matrix of the capability function, a calculation method for the position of the multi-unmanned plane cooperative strike is created; and the multi-unmanned plane cooperative strike counter-attack countermeasure model is established further, and a solving method for a n-person limited strategy static counter-attack countermeasure model and the pure-strategy nash equilibrium is created. The invention achieves the counter-attack countermeasure optimal strategy for the multi-unmanned plane cooperative strike, obtains great assessment profit value and strike strike efficiency, and improves the multi-unmanned plane cooperative strike capability.
Owner:SHENYANG AEROSPACE UNIVERSITY
Cache strategy method in D2D network based on deep reinforcement learning
ActiveCN109639760AAccurately predict mobilityAccurately Predict PopularityTransmissionNeural learning methodsEcho state networkReinforcement learning algorithm
The invention discloses a cache strategy method in a D2D network based on deep reinforcement learning. The method comprises the steps of acquiring position information of each user at a next moment via an echo state network algorithm by using the historical position information of each user in the cached and enabled D2D network as input data; acquiring content request information of each user at the next moment via the echo state network algorithm according to the position information of each user at the next moment in combination with the context information of each user at a current moment;caching the content request information into a cache space of the corresponding user; and acquiring an optimal strategy for delivering the content request information between the users in the cached and enabled D2D network via a deep reinforcement learning algorithm by minimizing the transmission power of the user transmitting the content request information and minimizing the delay of the user receiving the content request information as targets. According to the method provided by the invention, the problems that in the cached and enabled D2D network, the placement hit rate of the cached content is low and the consumed energy is large and the delay is long during a cache delivery process are solved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
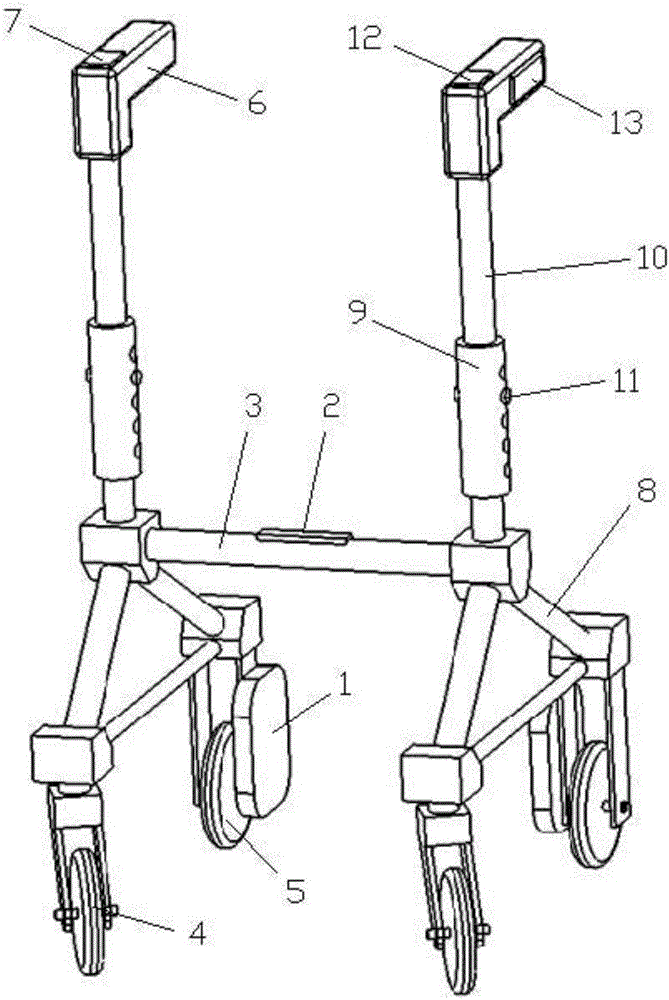
Intelligent wheeled walking assistant platform and control strategy method thereof
The invention discloses an intelligent wheeled walking assistant platform and a control strategy method thereof. The intelligent wheeled walking assistant platform comprises a supporting frame body, a driving device, an integration module and a power source, the driving device comprises a motor, a transmission device and a coder for detecting rotating speed of the motor, the integration module comprises radar, a main controller and a gyroscope for detecting inclination degree of the walking assistant platform, and a walking control panel is arranged on an armrest. The control strategy method includes: executing a dynamic compensation walking assistant control strategy; executing a safe fall-preventive strategy. The intelligent wheeled walking assistant platform realizes autonomous walking assistance and is easy to operate, labor-saving and simple; a user can autonomously control moving speed of the walking assistant platform according to own conditions, and the intelligent wheeled walking assistant platform is convenient to brake and high in using safety. The control strategy method provides control schemes under different moving circumstances, and the user can be ensured to safely use the walking assistant platform under different moving circumstances.
Owner:GUANGZHOU ZUBU MEDICAL TECH CO LTD
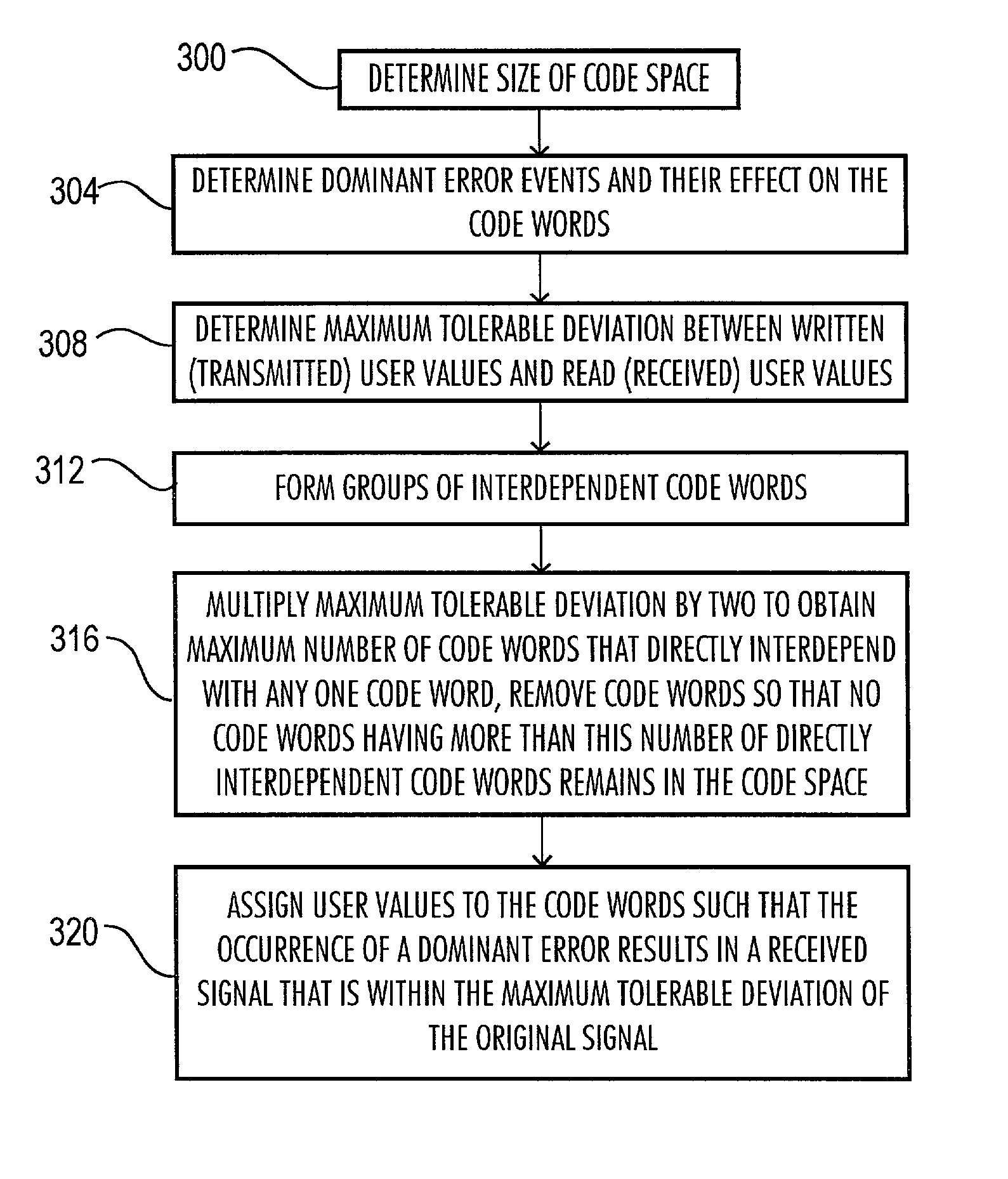
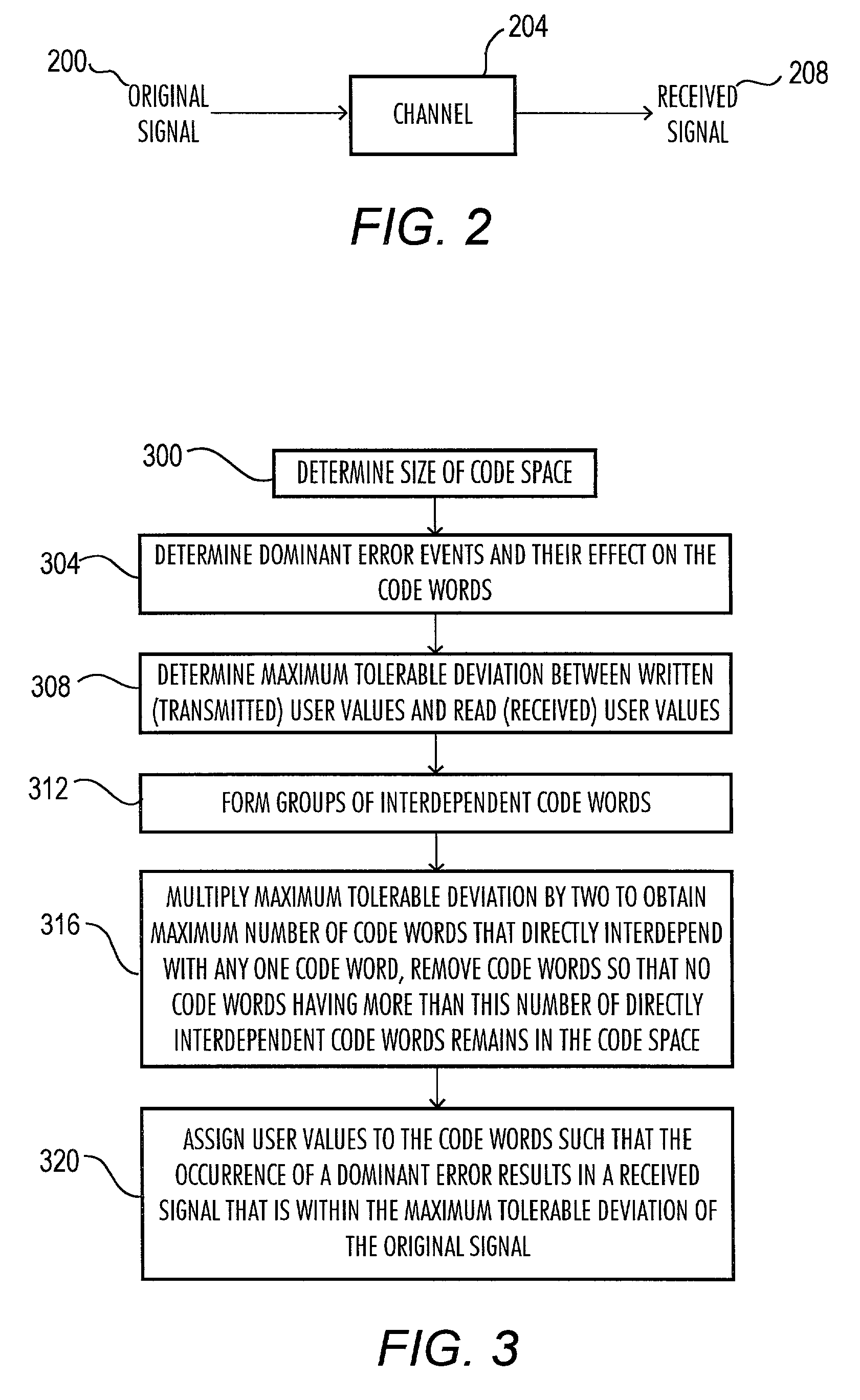
High efficiency, error minimizing coding strategy method and apparatus
InactiveUS7404131B2Improve efficiencyError minimizing strategyError preventionTransmission systemsHigh effectivenessComputer science
A method for creating a high efficiency, error minimizing code is provided. In addition, an apparatus having a high efficiency, error minimizing code is provided. In particular, the present invention provides a high efficiency, error minimizing code for use in connection with systems having a communication channel in which identifiable dominant errors occur, and that is used to transmit data that may be usefully applied in the system even though the received signal is not exactly equal to the original signal. Furthermore, the present invention provides a code that may be used to constrain the effects of dominant errors in a communication channel.
Owner:MAXTOR
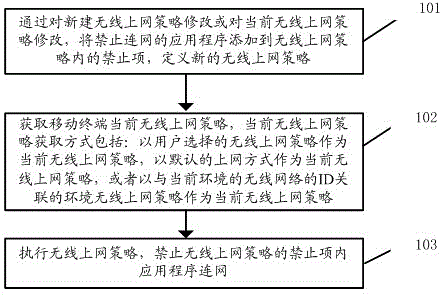
Wireless internet access strategy method, system and definition method for mobile terminal
InactiveCN104066088ATo ensure the safety of interestsReduce trafficSubstation equipmentSecurity arrangementTraffic capacityPayment
The invention discloses a wireless internet access strategy method, system and definition method for a mobile terminal. Firstly, the wireless internet access strategy is made for the mobile terminal, when the mobile terminal is connected with the wireless network, a user can select the wireless internet access strategy to serve as the current wireless internet access strategy, can modify the current wireless internet access strategy as well to make a wireless internet access strategy associated with the current wireless network IP. A user can execute different wireless internet access strategies in different wireless networks by setting the wireless internet access strategies, for example, operation of instant messaging software is forbidden in the working environment, and work efficiency can be improved; operation of an internet payment application is forbidden in the market shopping process, and safety of user benefits can be guaranteed; furthermore, the user can add the application which is forbidden from being networked to the wireless internet access strategy forbidding item to forbid the application from being networked, network traffic can be saved for the user, the network traffic consumption due to background operation of some applications can be avoided, applications can also be added to the permitted item, only the applications in the permitted item is allowed to be networked, and the number is prevented from being stolen by Trojan viruses.
Owner:TCL COMM NINGBO
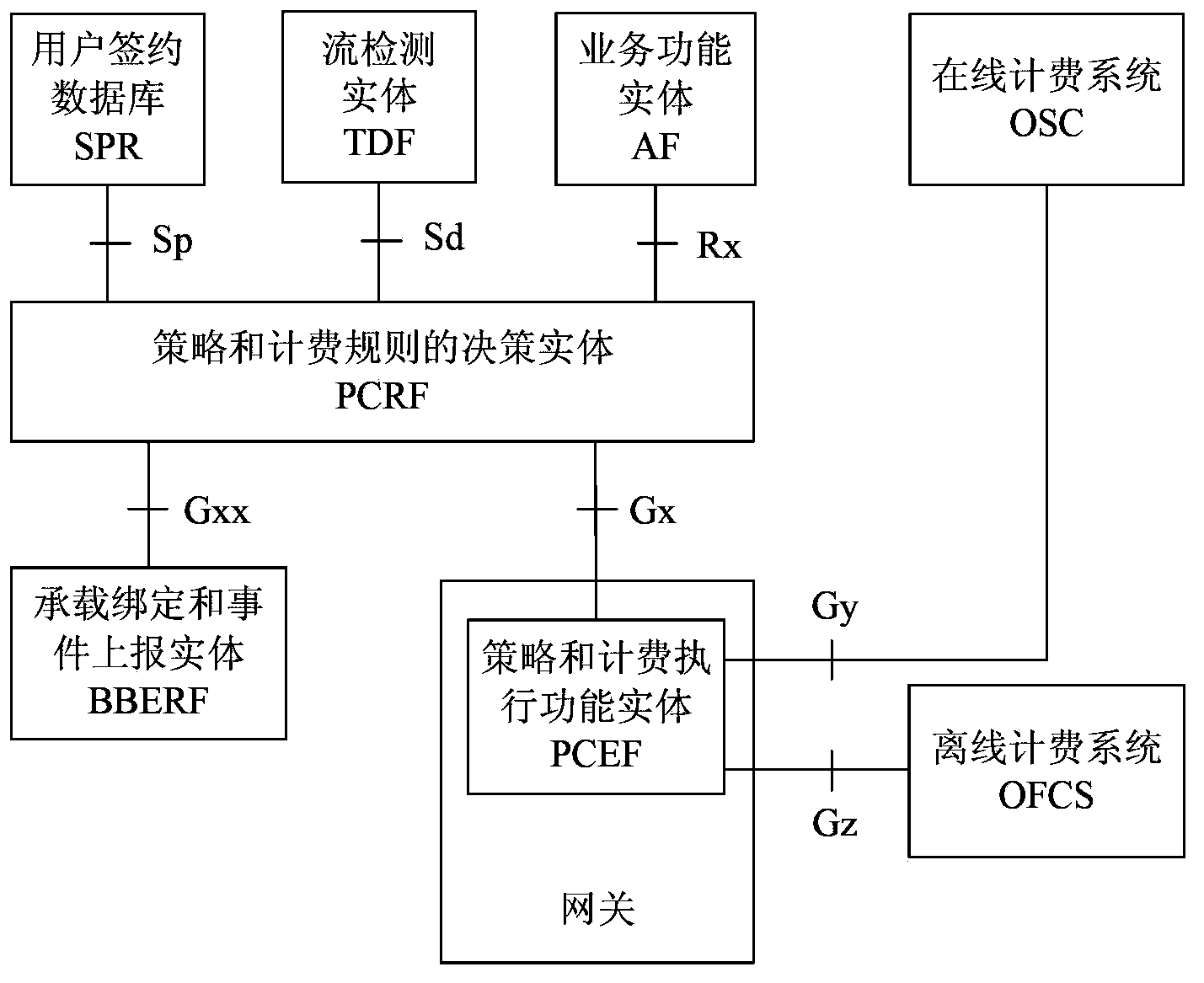
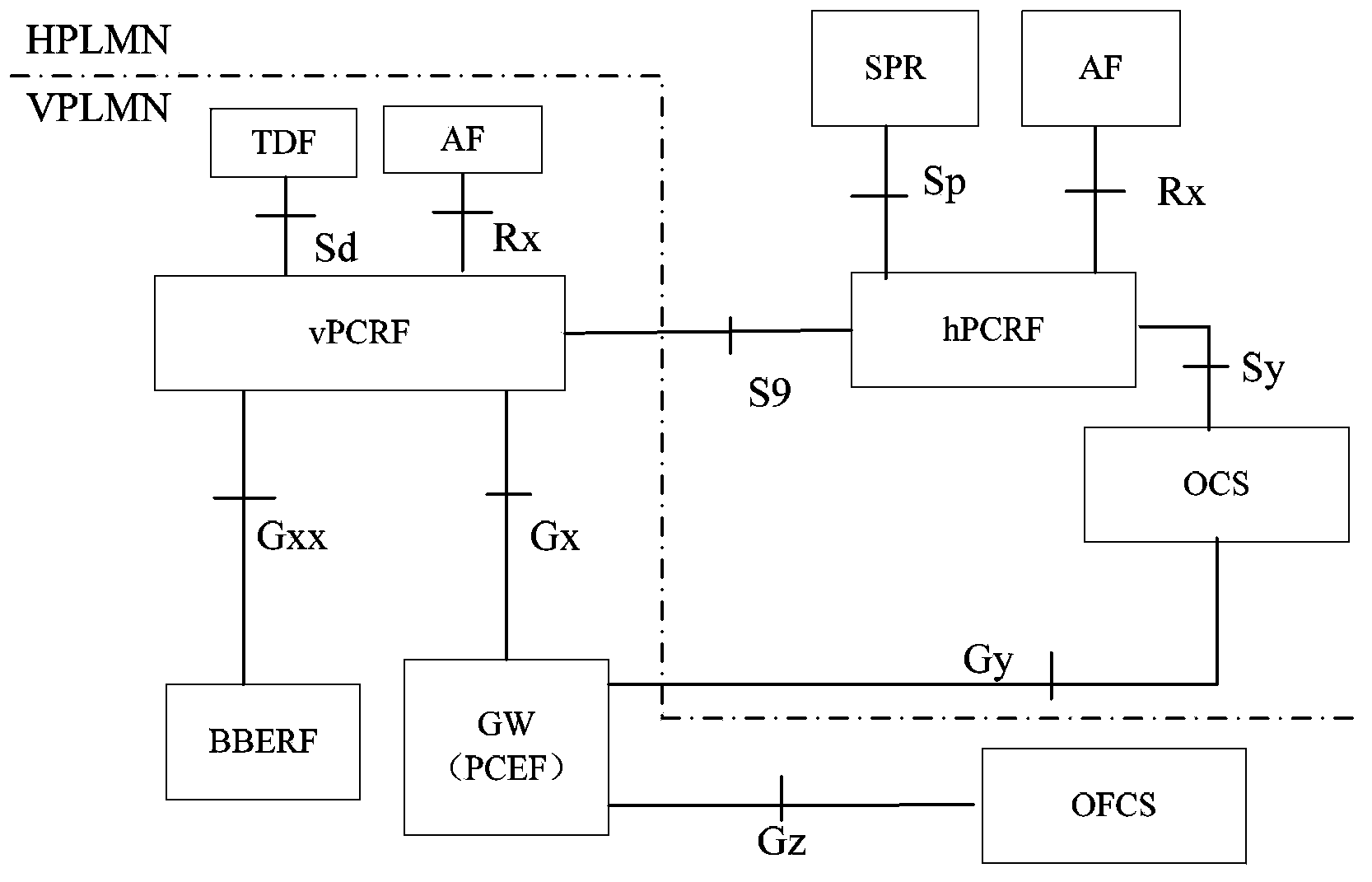
Charging strategy method and apparatus of roaming local services
InactiveCN103888926AEasy session creationEasy to implement modificationAccounting/billing servicesTelephonic communicationTelecommunicationsThreshold response
The invention discloses a charging strategy method and apparatus of roaming local services. The method comprises: a V-OCS receiving a credit control request message sent by a PCEF, the credit control request message being used for requesting the PCEF to execute a current user' credit quota needing to be used during charging; the V-OCS, according to the credit control request message, determining whether services requested by the current user are the roaming local services, if it is determined so, sending a credit threshold request message to an H-OCS, and receiving a credit threshold response message returned by the H-OCS, the credit threshold response message carrying a credit threshold authenticated by a home network for use in a visit network by the user; and the V-OCS, according to the credit threshold, determining the credit quota, and sending the credit quota carried in a credit control response message to the PCEF for executing charging. By using the method and apparatus provided by the invention, the effects of easily realizing session creating, modification and terminating flow processing of roaming local services are achieved.
Owner:ZTE CORP
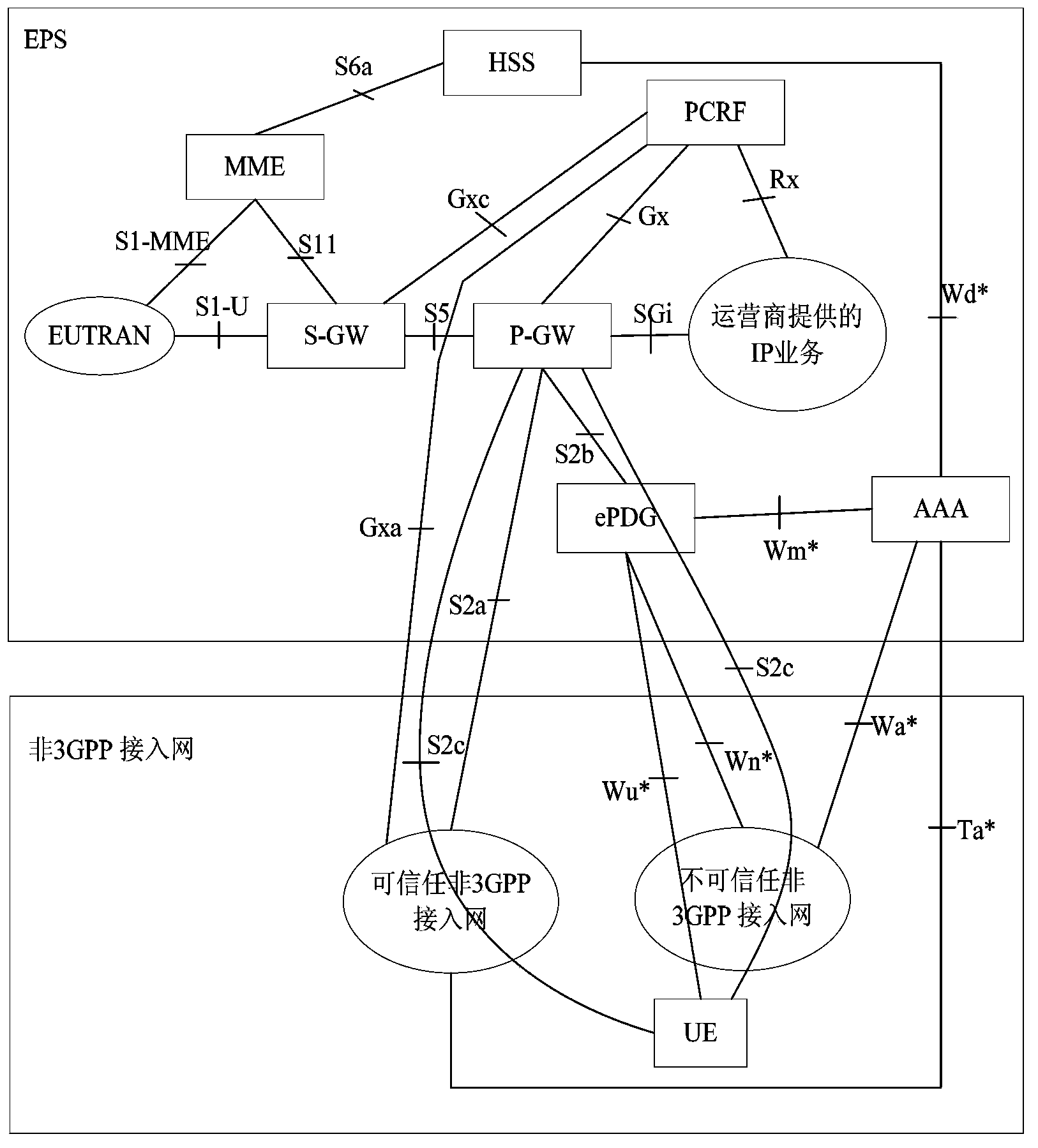
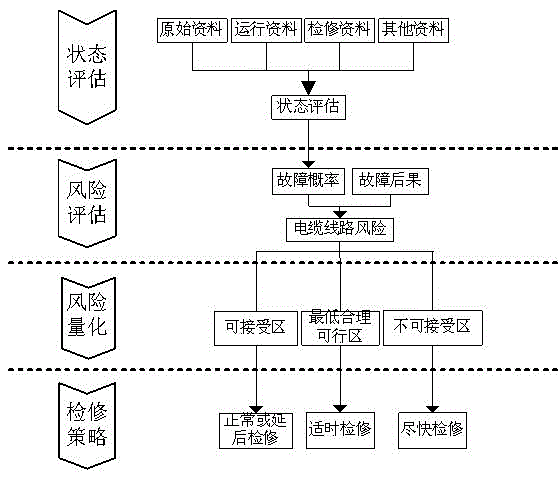
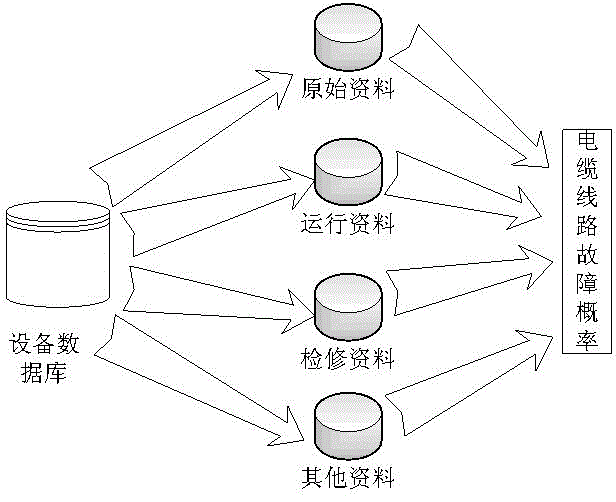
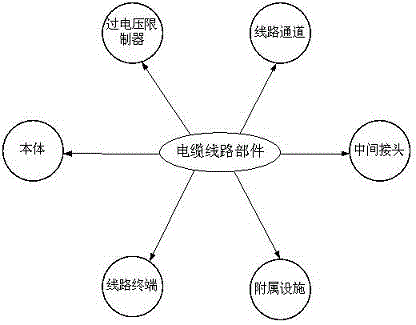
Risk evaluation based cable overhaul strategy method
The invention provides a risk evaluation based cable overhaul strategy method. The method specifically comprises the steps of proposing a risk evaluation based cable line overhaul strategy according to the overhaul characteristics of a cable line; considering the portability of the fault of the cable line and the severity of the fault consequence; evaluating a cable line unit according to the real-time information; calculating the healthy indexes of the whole cable line by the analytic hierarchy process; then calculating the portability of the fault of the cable line; determining the comprehensive risk of the cable line according to the assets loss risk and operation loss risk of the cable line; deciding the cable line overhaul strategy according to the risk grade of the comprehensive risk of the cable line. According to the method, the risk evaluation is further performed for the cable line based on the cable line state evaluation; in addition, the cable line overhaul strategy is prepared according to the ALARP rule, and therefore, a new concept is provided for the overhaul of the cable line.
Owner:江西汇能电力工程技术有限公司
Low-delay communication system
ActiveCN108289063ALower latencyLearning to use zero costFinanceData switching networksCommunications systemLow delay
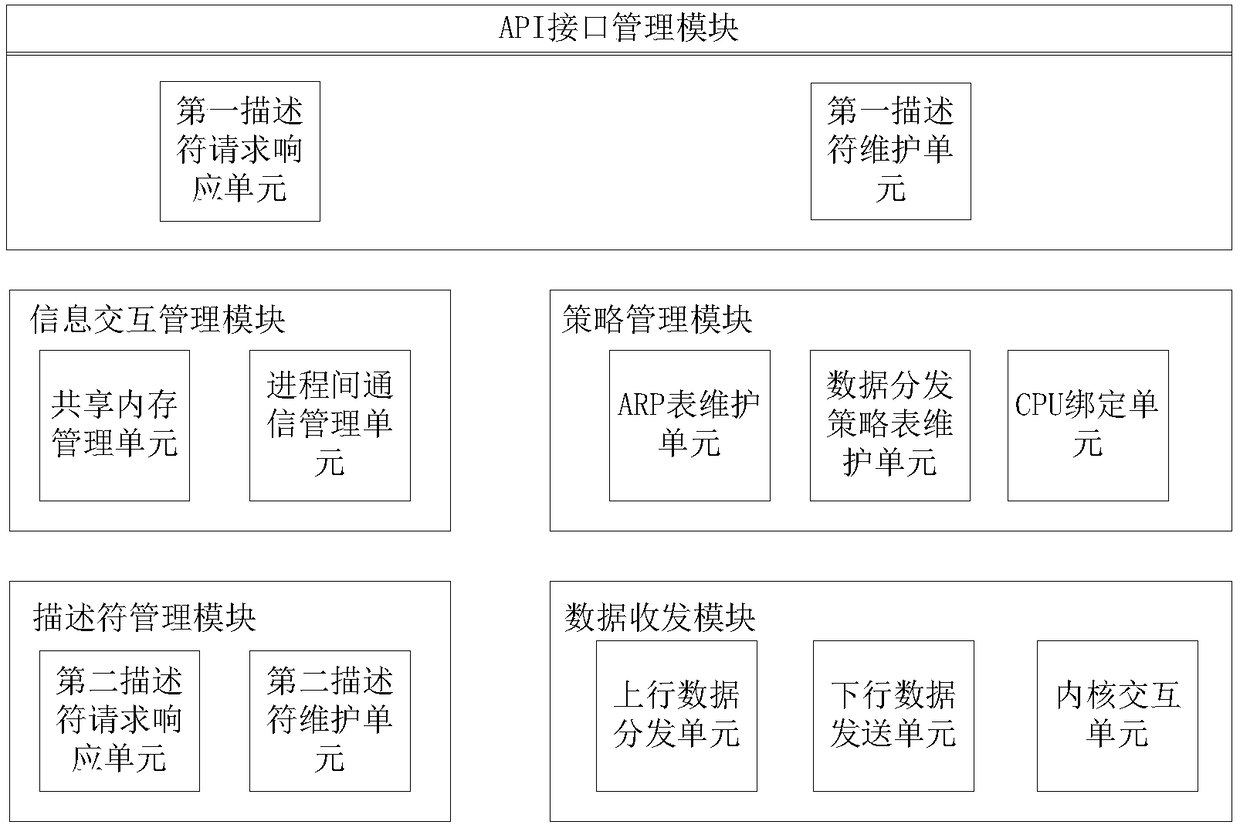
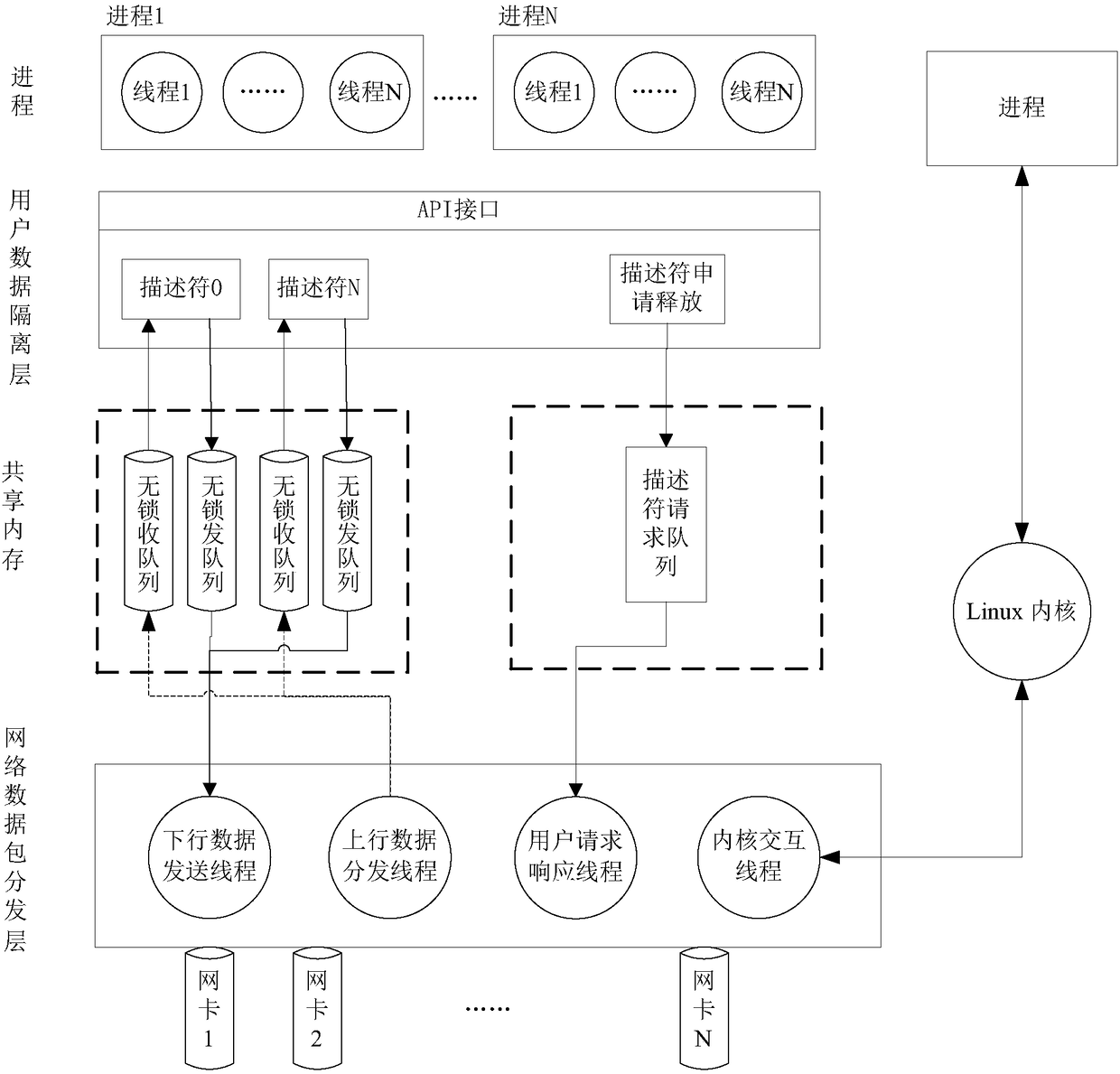
The invention discloses a low-delay communication system, which can effectively reduce the system delay problems in a financial derivative transaction system without additional procurement of networkhardware, and is simple to use. The technical scheme is as follows: the system comprises an API interface management module, an information interaction management module, a policy management module, adescriptor management module and a data transceiving module, wherein the API interface management module is used for providing a data transceiving interface to a user application; the information interaction management module is used for managing a communication mechanism between different processes; the policy management module is used for maintaining a data distribution strategy method; the descriptor management module is used for managing descriptors applied by all user processes; and the data transceiving module is used for the data transceiving between a user layer, a kernel and a network card.
Owner:上海金融期货信息技术有限公司
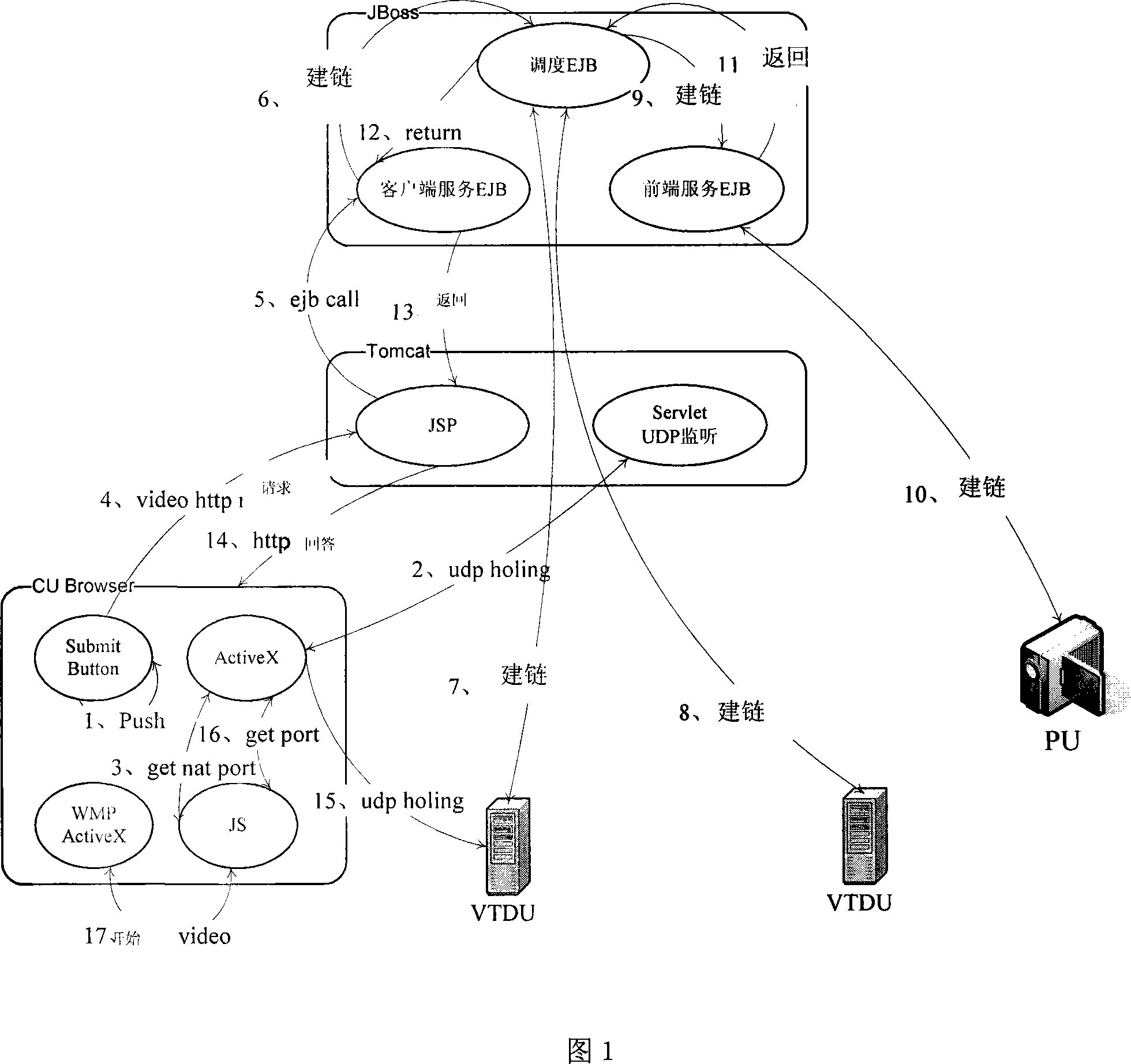
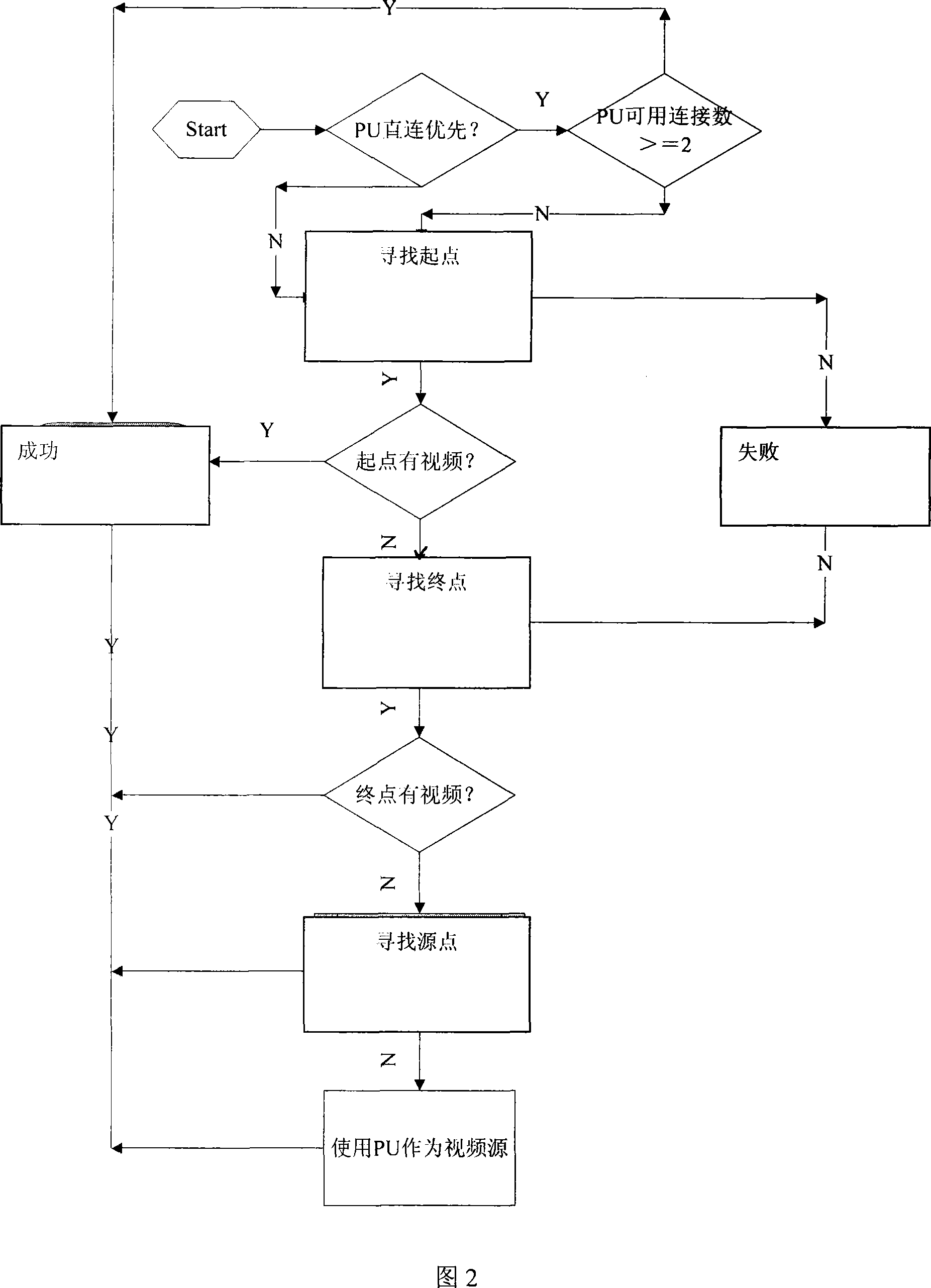
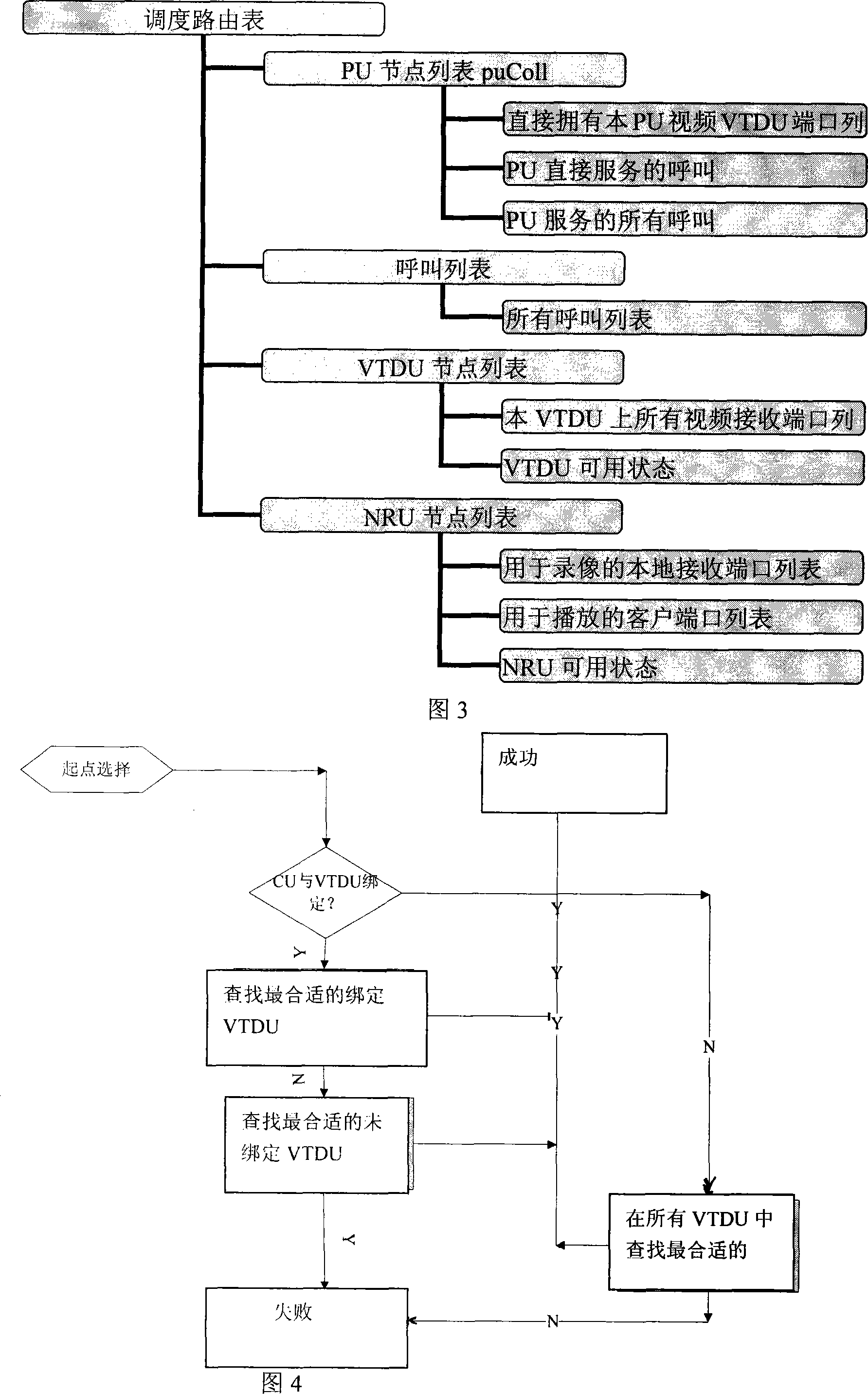
Strategy method for video binding thin resources of diversiform video exchange routes
ActiveCN101094391AAvoid the disadvantages of upper limit on the number of householdsAvoid the disadvantages of unreasonable resource allocationClosed circuit television systemsTransmissionComputer scienceMulti path
The invention comprises: when user uses the peripheral unit (PU) and the video transfer distribute unit (VTDU), dynamically calculating the proper video forwarding and distributing route, namely using the VTDU to make multi-path forwarding for the single video point so as to realize the reasonable transmission of video stream. It is used for realizing the following policies; making binging between user (CU) and PU; the PU is set to directly send video stream to CU; making binding between PU and VTDU; the VTDU is set to only distribute the video stream from appointed PU; binding CU and VTDU; the special VTDU is set to only provide service for the appointed customer; binding CU and NRU; the special NRU is set to only provide server for appointed customer; binding PU and NRU; the special NRU is set to only provide the recording service for appointed NRU.
Owner:LINKAGE SYST INTEGRATION
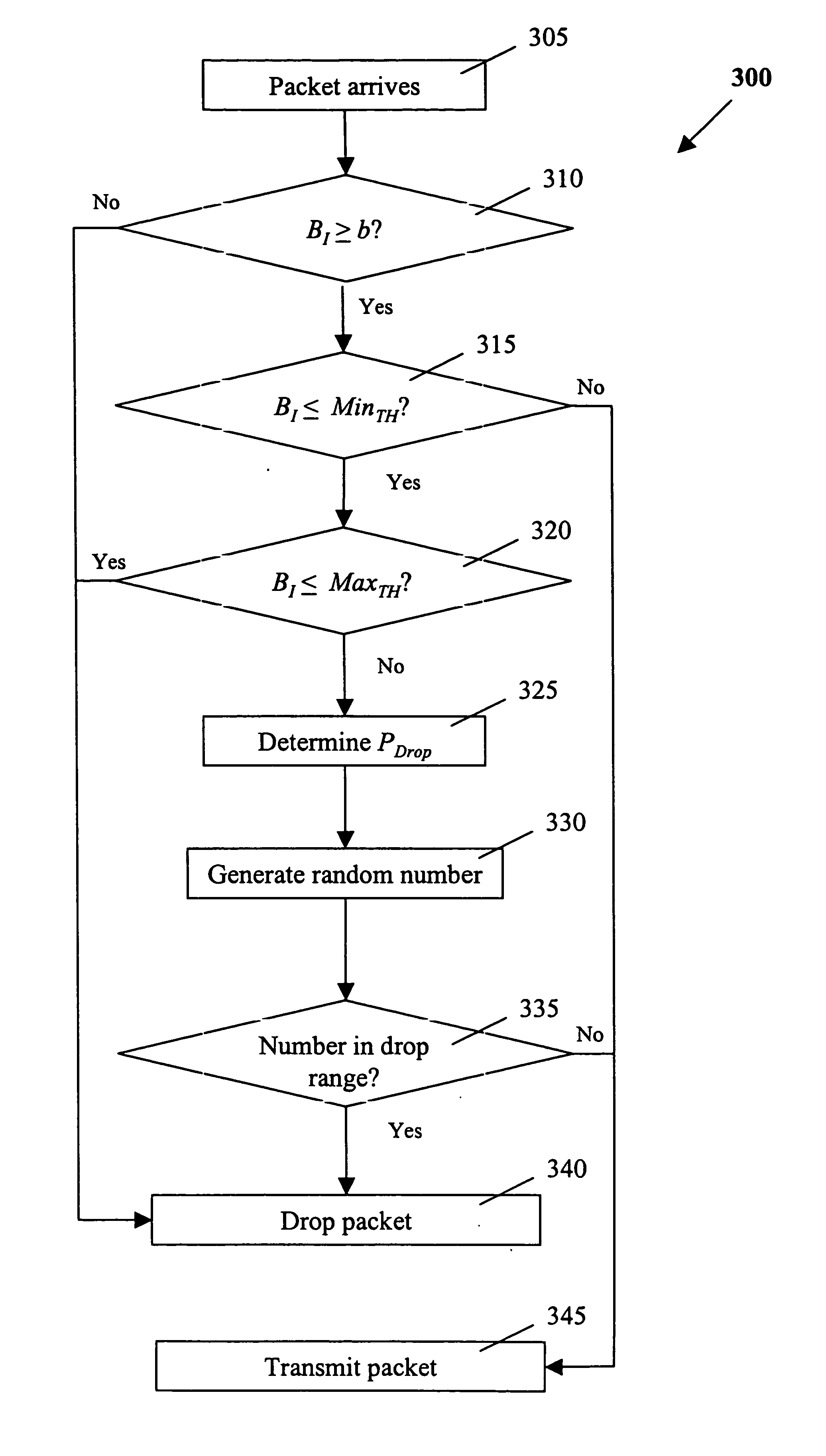
Modification of policing methods to make them more TCP-friendly
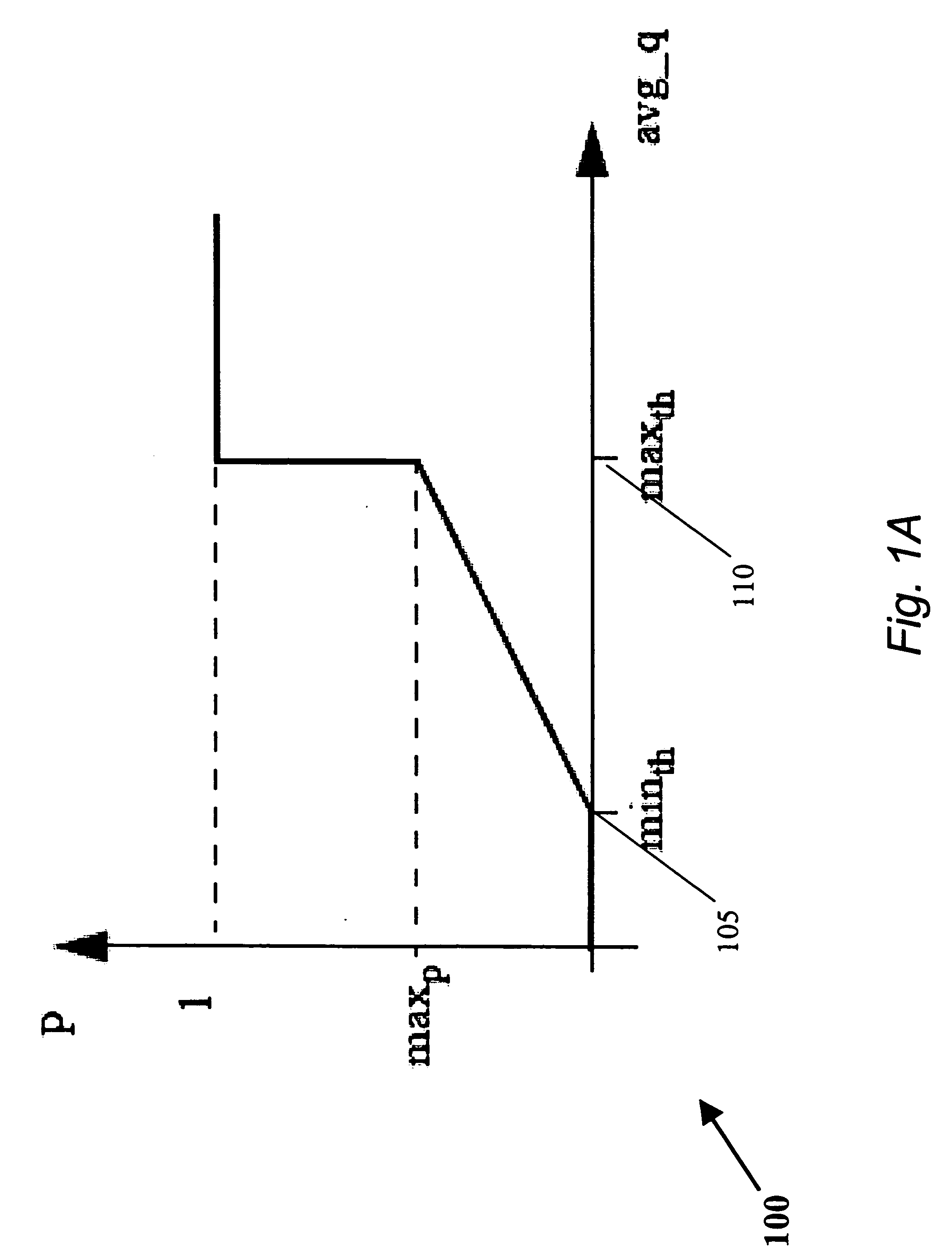
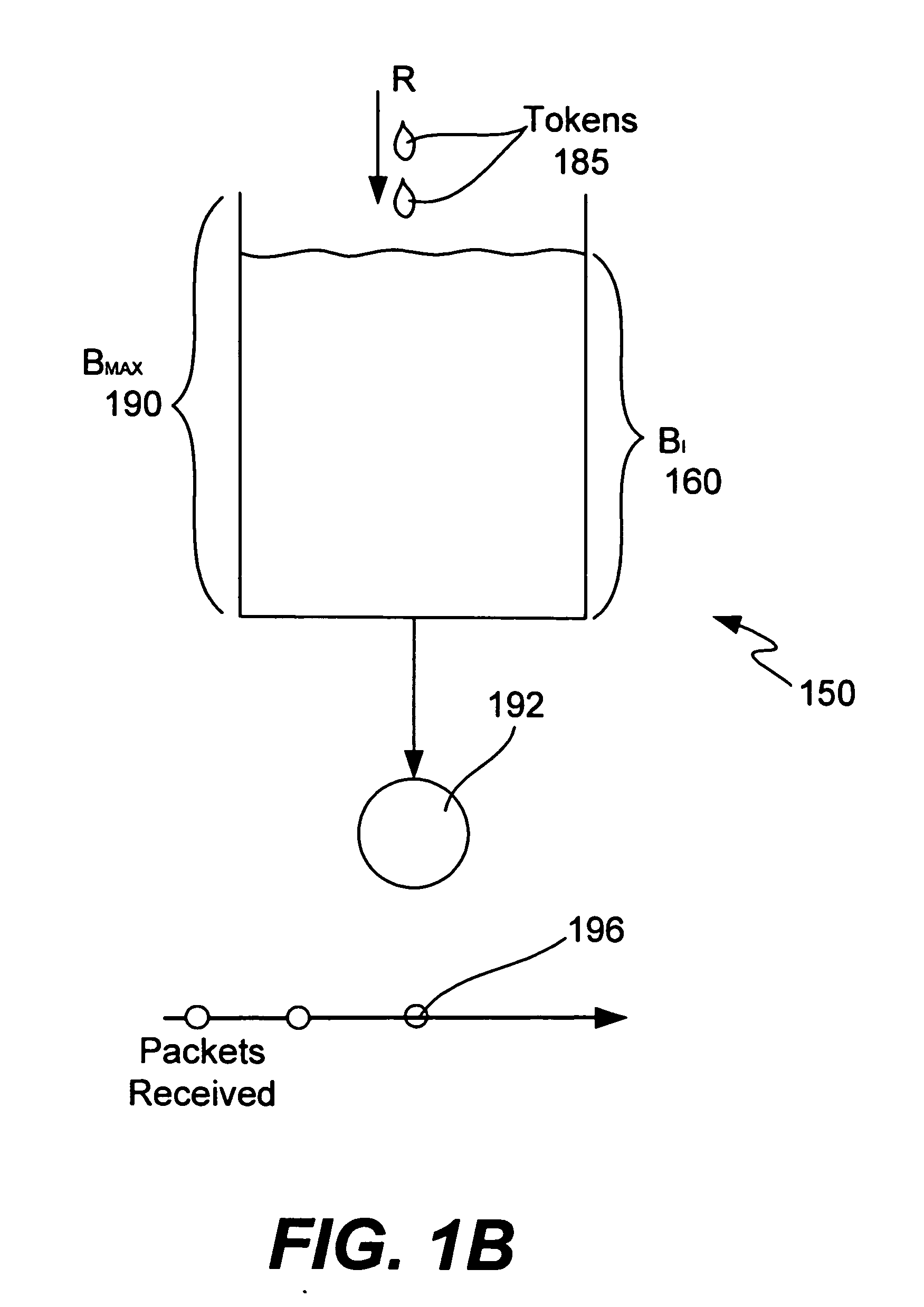
Various improvements are provided for prior art policing methods, including token bucket methods and virtual time policing methods. Some preferred methods of the invention involve assigning a non-zero drop probability even when the packet would otherwise have been transmitted according to a prior art policing method. For example, a non-zero drop probability may be assigned even when there are sufficient tokens in a token bucket to allow transmission of the packet. A non-zero drop probability may be assigned, for example, when a token bucket level is at or below a predetermined threshold or according to a rate at which a token bucket is being emptied. Some implementations involve treating a token bucket as a virtual queue wherein the number of free elements in the virtual queue is proportional to the number of remaining tokens in the token bucket. Such implementations may involve predicting a future virtual queue size according to a previous virtual queue size and using this predicted value to calculate a drop probability.
Owner:CISCO TECH INC
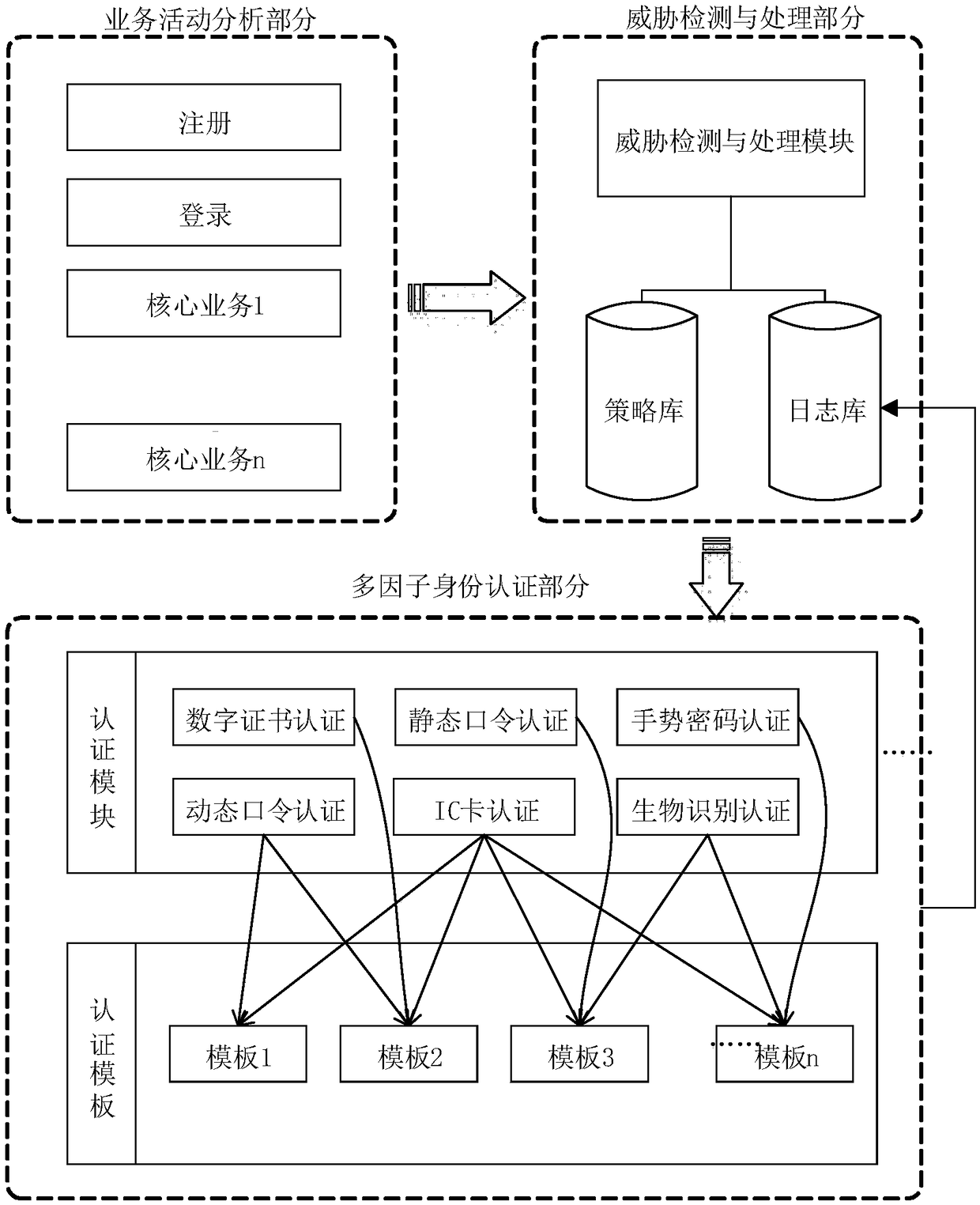
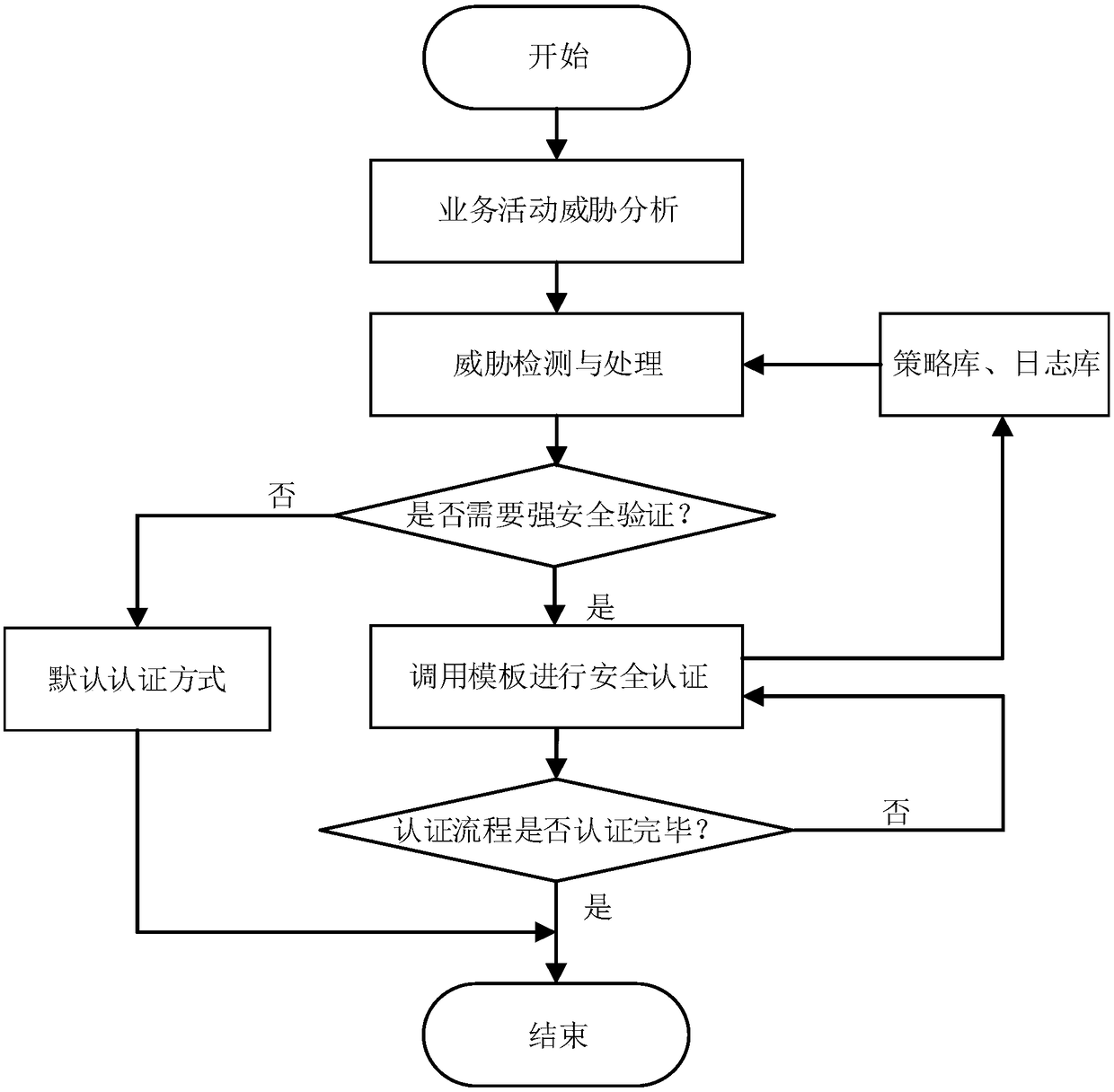
Threat level-based multi-factor identity authentication method
InactiveCN109450959AFlexible authenticationThe certification process is fastTransmissionFlexible MechanismsInterface design
The invention discloses a threat level-based multi-factor identity authentication method, which comprises the following steps: building an identity authentication model; performing service activity threat analysis; generating an authentication strategy; and performing security authentication. The invention provides the threat level-based multi-factor identity authentication method for defects of acurrent identity authentication mode. During application, a corresponding identity authentication strategy method is formulated according to different security threat levels in an application scene;a multi-factor identity authentication model with a flexible mechanism is provided according to the identity authentication strategy; the model adopts a modularized design, and can be flexibly replaced as required; an authentication template method is provided according to parameter weights in the authentication strategy; the method takes a comprehensive consideration of the threat level, the authentication strength, the computing cost, the time, the convenience and other factors to adaptively dynamically select corresponding authentication modules; and multi-factor identity authentication meeting requirements at different security levels is flexibly performed through standard interface design and integration.
Owner:SICHUAN JIUZHOU ELECTRIC GROUP
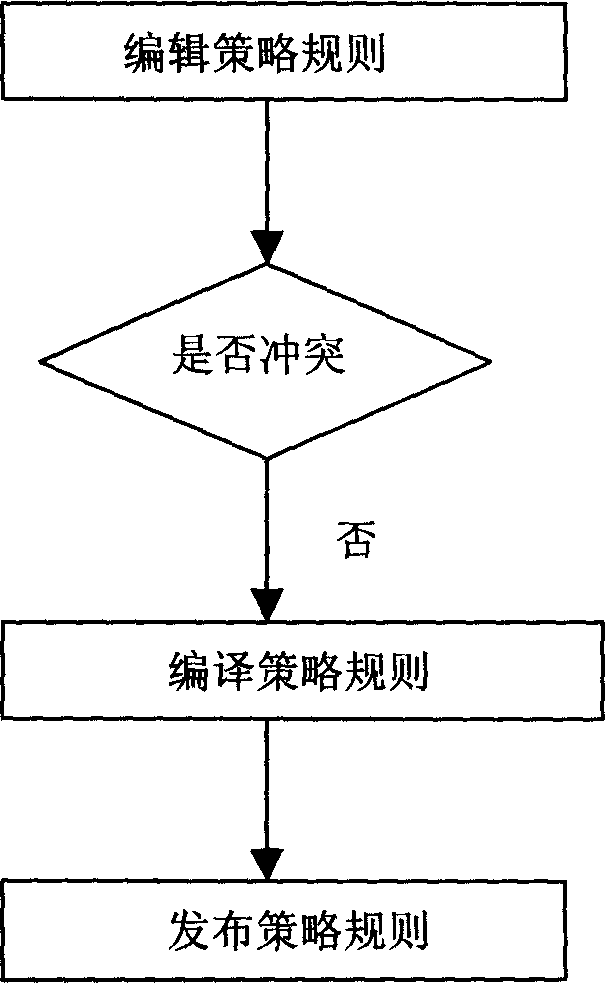
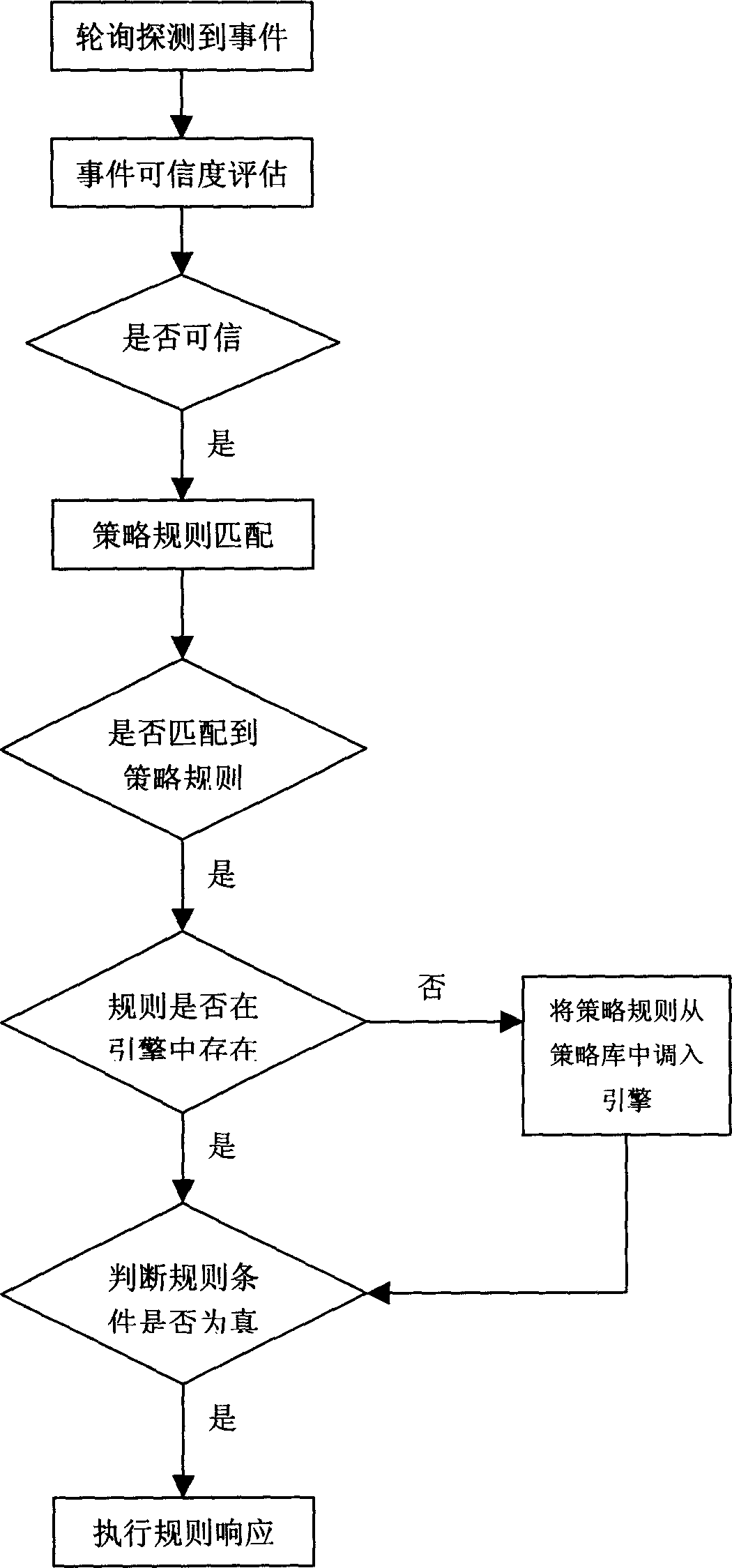
Confidential active type strategy linkage method
InactiveCN1556613AEnsure consistencyReduce the risk of linkageData switching networksSpecial data processing applicationsData miningInformation security
The invention relates to a credible active linked tactic method, which belongs to the information security field. It carries on the tactic rule distribution according to the distribution flow through the tactic managing device, the event adapter is used to detect the security event warning information, carries on the credible analysis flow of the warning information to acquire the credence parameter, sends information notice to the static engine, at the same time, waits for the response of the tactic engine, the event adapter transmits the warning event to the tactic rule localizer, the tactic rule localizer searches the event index table, the rule localizer finds out and activates the distributed tactic rules, the tactic engine calls the tactic rule executer to execute the tactic condition matching and tactic response according to the tactic condition, , realizes the link of tactic rules.
Owner:SHANGHAI JIAO TONG UNIV
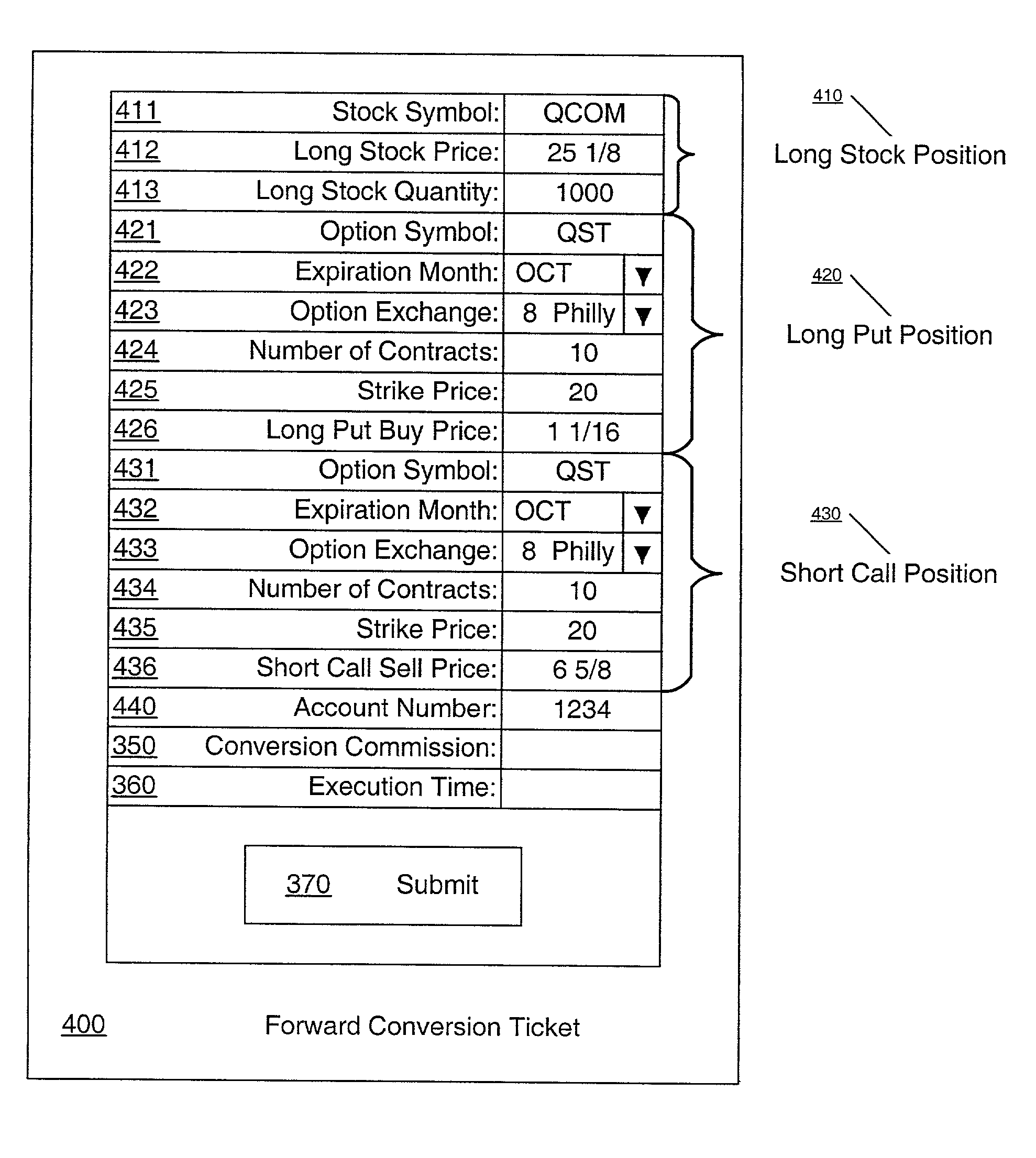
Methods and systems for reconciling a forward conversion securities strategy
Methods and systems for reconciling a forward conversion strategy are provided. A forward conversion strategy may include a long stock order, a long put order, and a short call order, for at least one security. The method may include automatic calculation of the following items / values for each forward conversion strategy in an account: a cost basis, multiple present values, and multiple unrealized gain / loss values. The method may include automatic display of the values described above on a first computer system. The present value may be determined on a periodic basis (e.g., daily, at user configurable times, and / or in real-time). A forward conversion strategy that is missing at least one of its parts may be automatically restored by automatically acquiring of the at least one missing securities position (e.g., buying the stock long, buying the long put, or selling the short call).
Owner:PROTRADER TECH +2
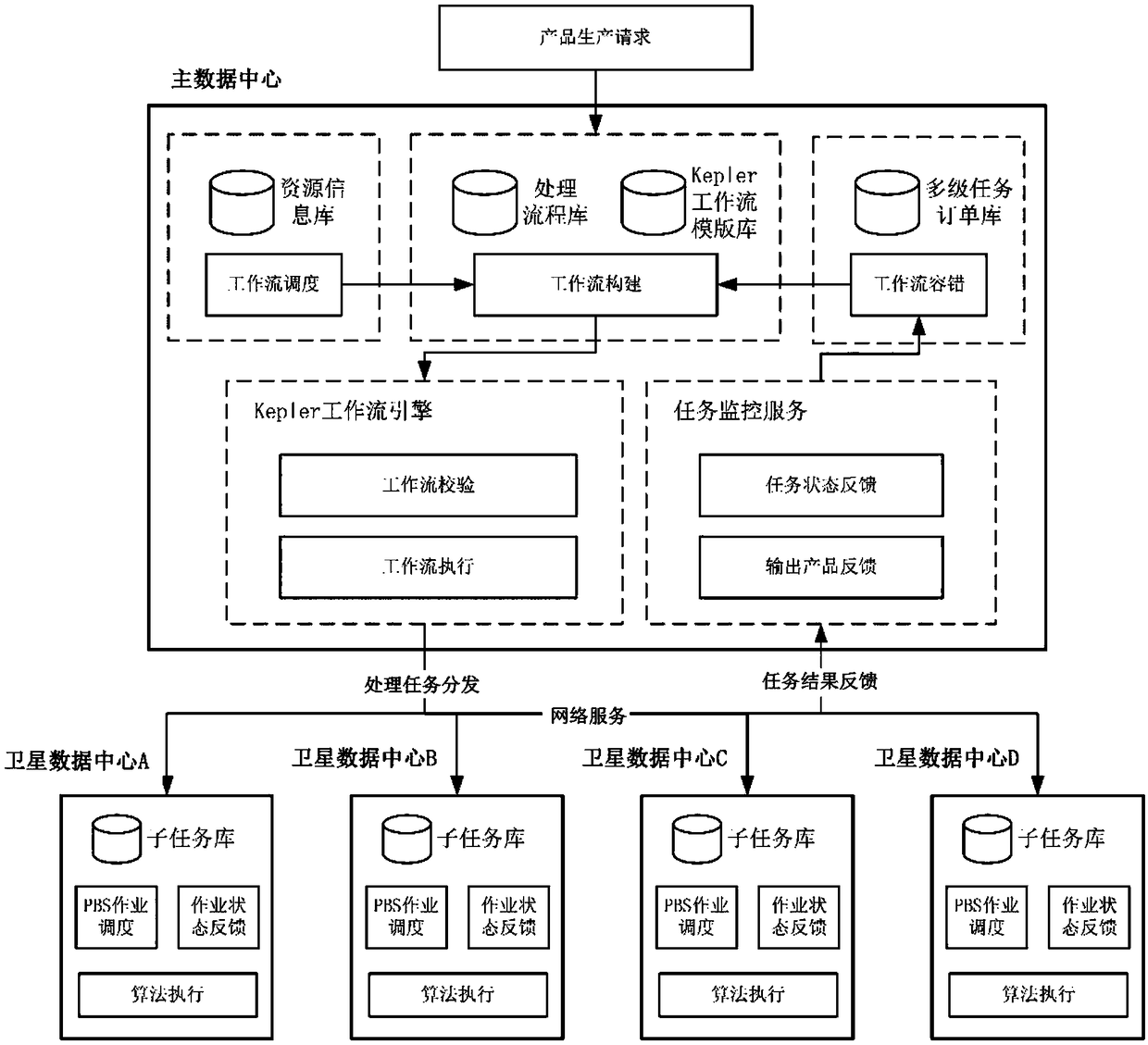
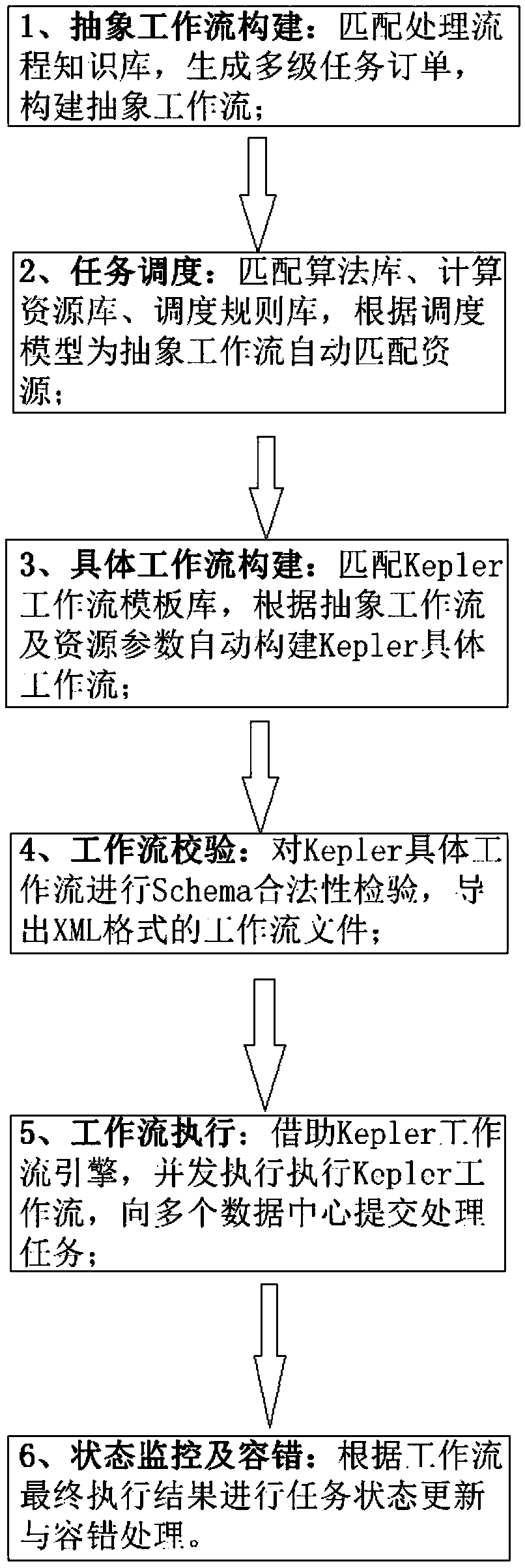
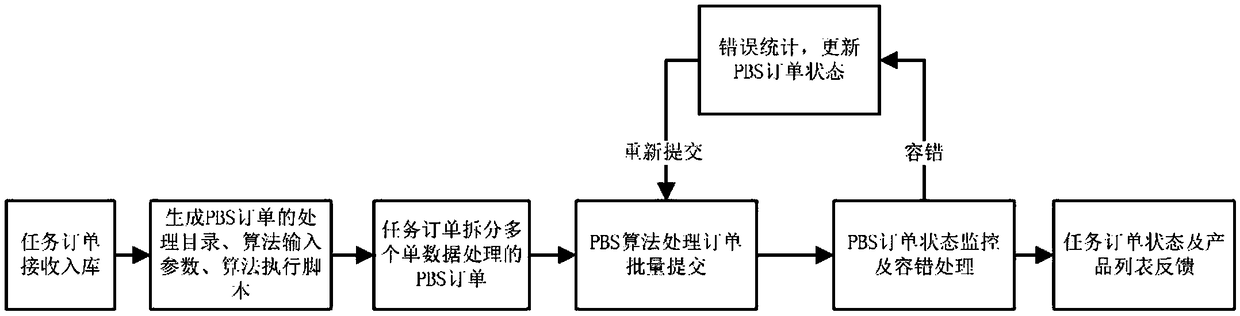
Workflow management method for collaborative remote sensing product production of multi-satellite data center
InactiveCN108985709ARealize dynamic scalable managementImprove performanceOffice automationResourcesData centerSatellite remote sensing
The invention discloses a workflow management method for collaborative remote sensing product production of a multi-satellite data center, the method comprising the following steps: constructing a remote sensing product production processing flow base, constructing a multi-source remote sensing data processing flow knowledge base, and constructing a multi-level task order base; according to Keplerdynamic workflow system and PBS job scheduling system, automatically constructing the specific task workflow with different granularity for remote sensing product production; formulating a heuristicworkflow dynamic scheduling strategy method; formulating a multi-level task status monitoring strategy related to remote sensing product production, and a fault tolerant strategy based on retry, checkpoint recovery and timeout; constructing a dynamic process library and algorithm library to realize the dynamic and scalable management of multi-satellite remote sensing workflow in a multi-satellitedata center.
Owner:INST OF REMOTE SENSING & DIGITAL EARTH CHINESE ACADEMY OF SCI
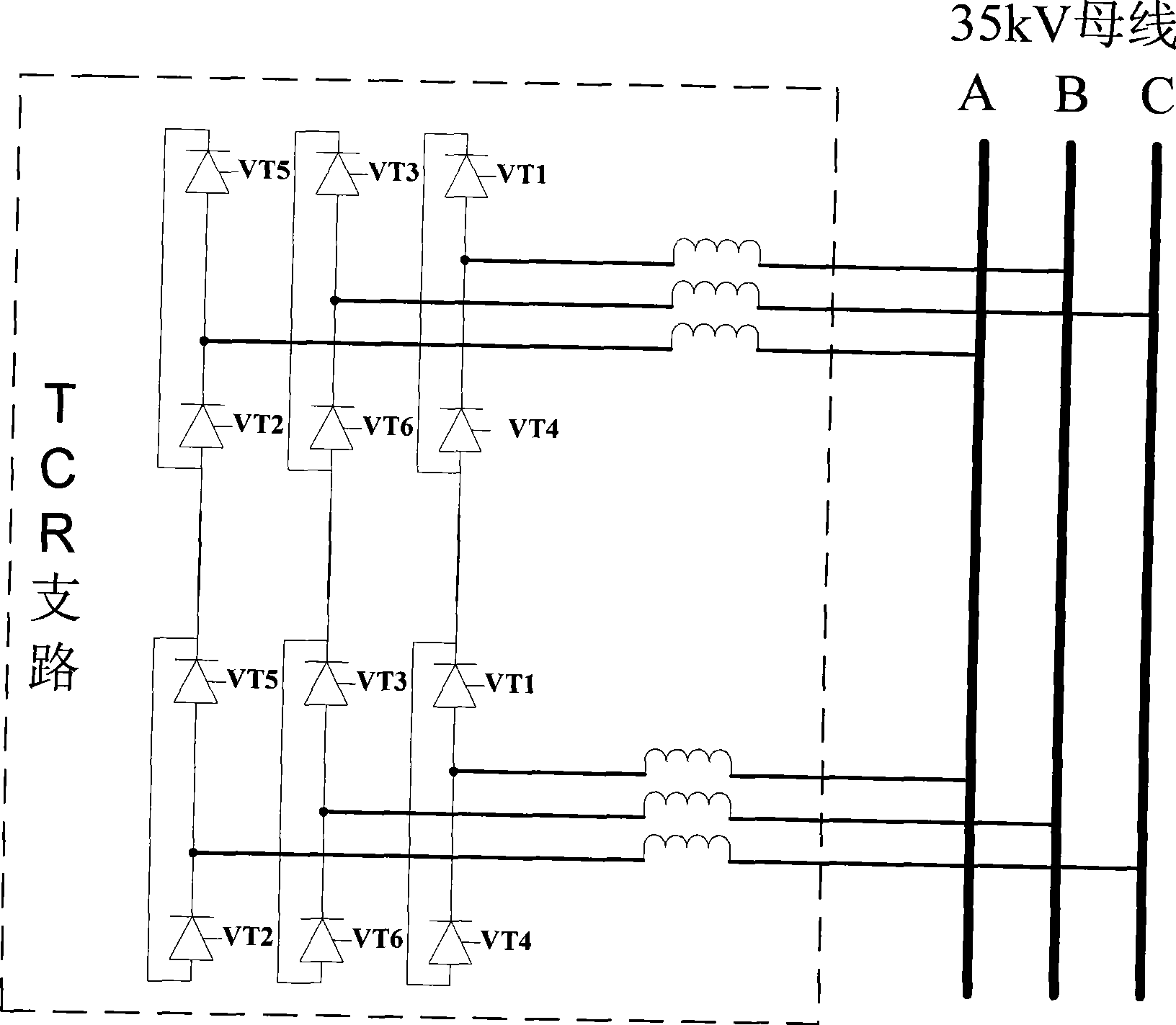
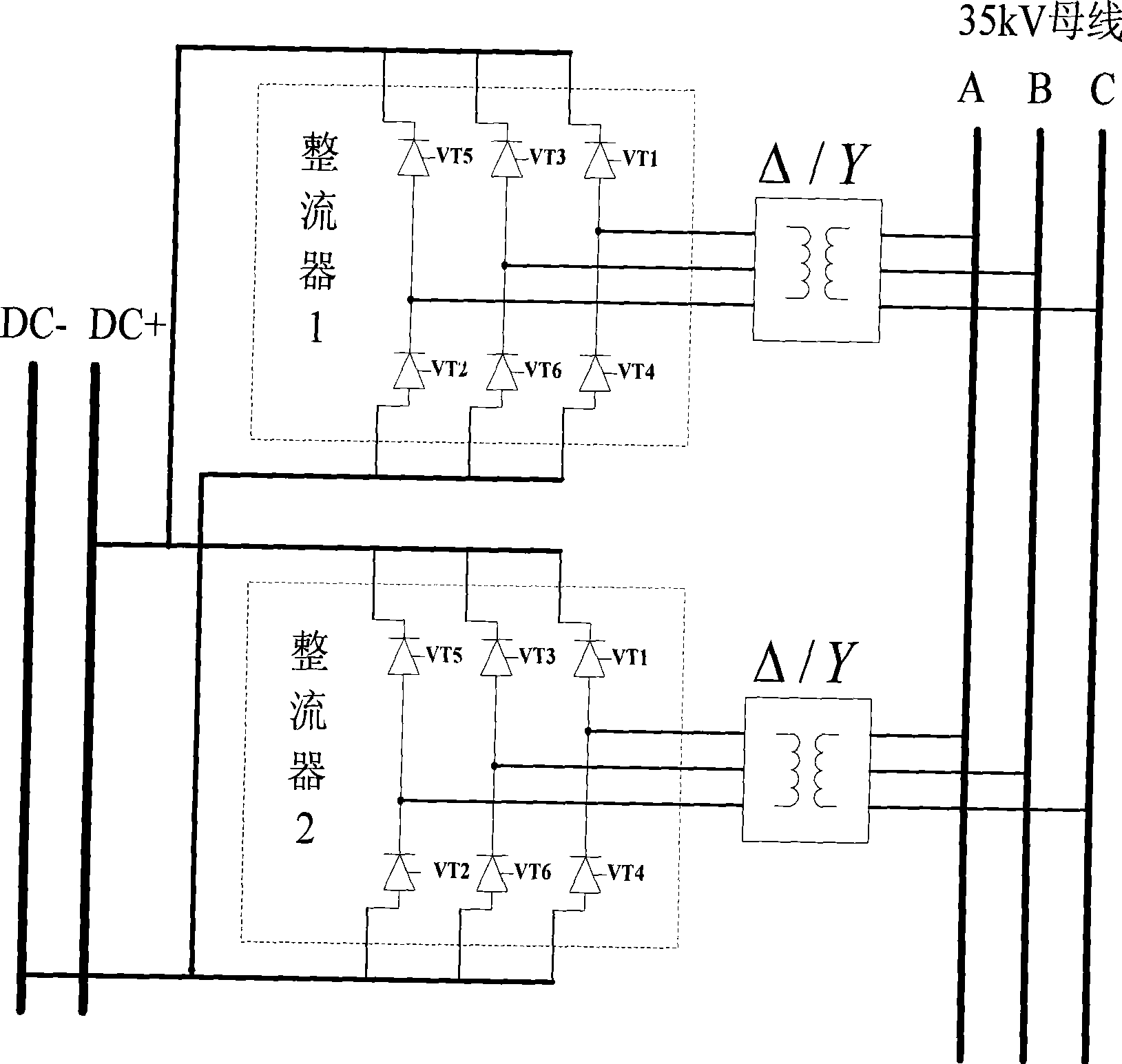
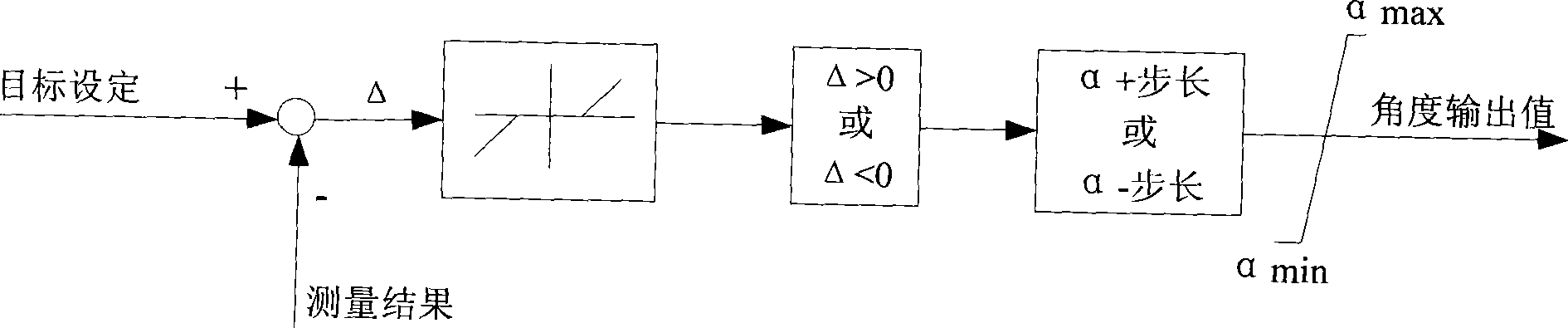
Regulation control method of reconfigurable static reactive-power compensation/DC de-icing composite apparatus
InactiveCN101369731AReliable trackingLow investment costOverhead installationReactive power adjustment/elimination/compensationPower compensationOperation mode
The invention relates to a method for regulating and controlling a reconfigurable static reactive compensation / DC ice-melting composite apparatus, wherein a complete set of controller completes the judgment of operation mode based on the difference of the primary equipment wire connection, and implements the whole switch of analog acquisition, triggering synchronization, tactical control and regulation, and the tactical regulation uses various regulation methods based on the operation mode. combined regulation control of the reconfigurable power electronic device with two different operation modes is implemented, and the complete set of regulation control policy method is completed on a same control hardware platform, which ensure the method be stabile and reliable as well as save hardware cost.
Owner:STATE GRID CORP OF CHINA +2
Multi-Android-client service sharing method and system
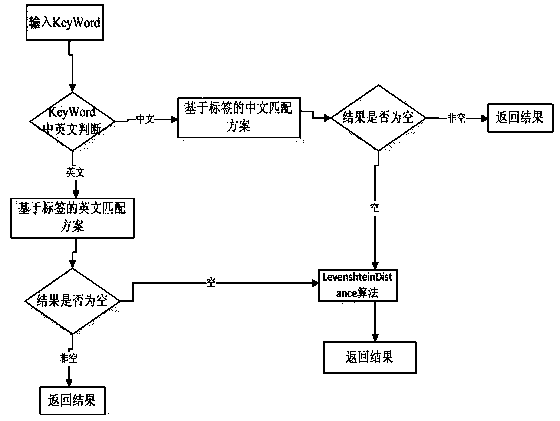
ActiveCN103399877AImprove the search experienceEasy to findSpecial data processing applicationsWeb siteData analysis system
The invention provides an android application based vertical search method and system. The whole strategy method is supported by a crawler system, and core platforms of the system include a data analysis system, an intelligent search algorithm core and an interface project. The process of the whole system includes that the crawler system crawls effective data of specified websites regularly every day and archives; then the data analysis system preprocesses newly stored data every day, preprocessing includes detail processing of a large amount of applications, and preparation for searching basic search data is finished so far; after the interface project receives an http request, servlet node configuration information is distributed to corresponding classes to perform search processing; the core is to call an intelligent search algorithm and return a result set; data are provided to the outside through the interface project in a josn form. The method and system can help users to discover and acquire content more conveniently and better, really becomes an expressway linking the users with content websites including all big application stores and brings better search experience to the users.
Owner:四川公用信息产业有限责任公司
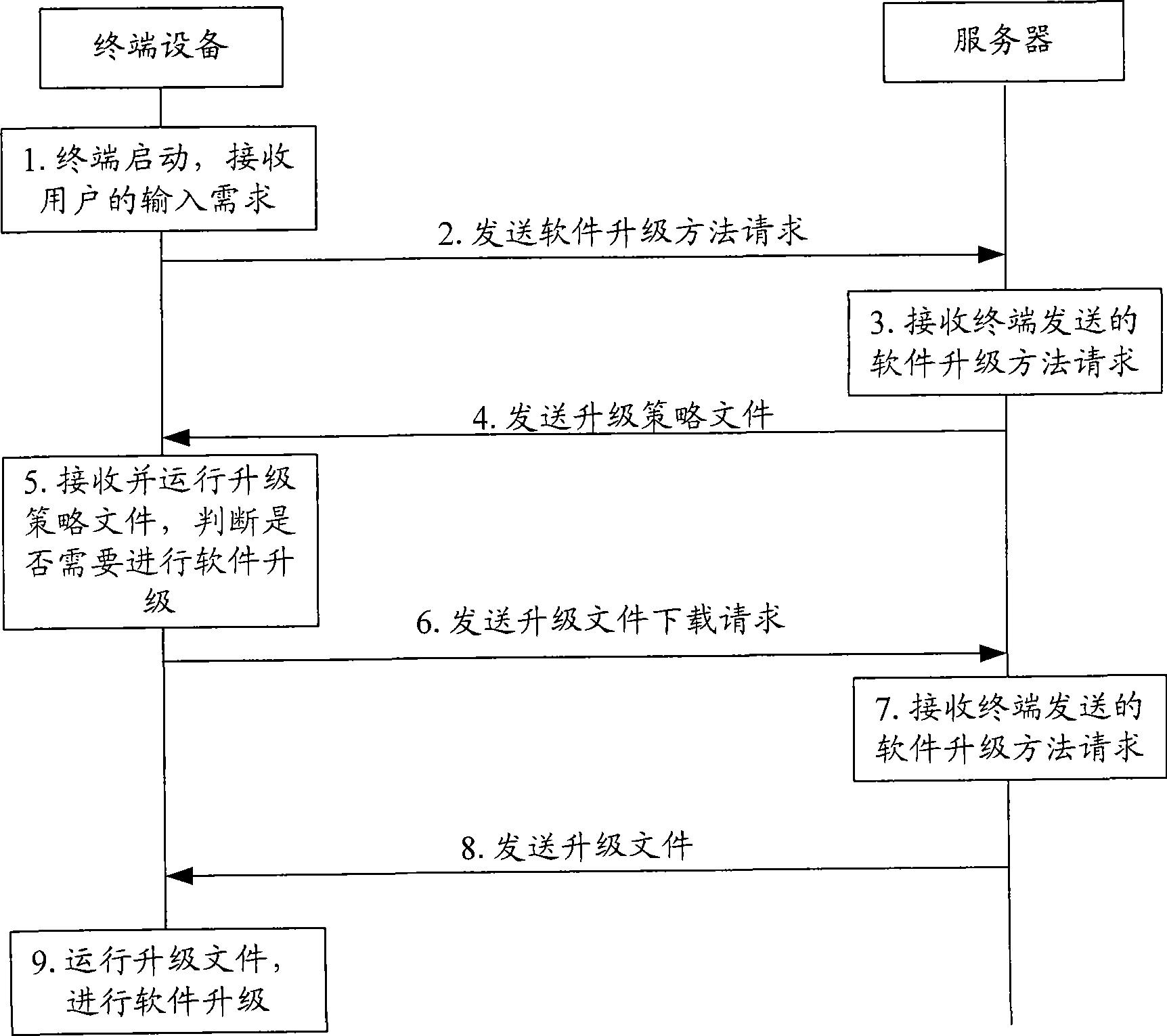
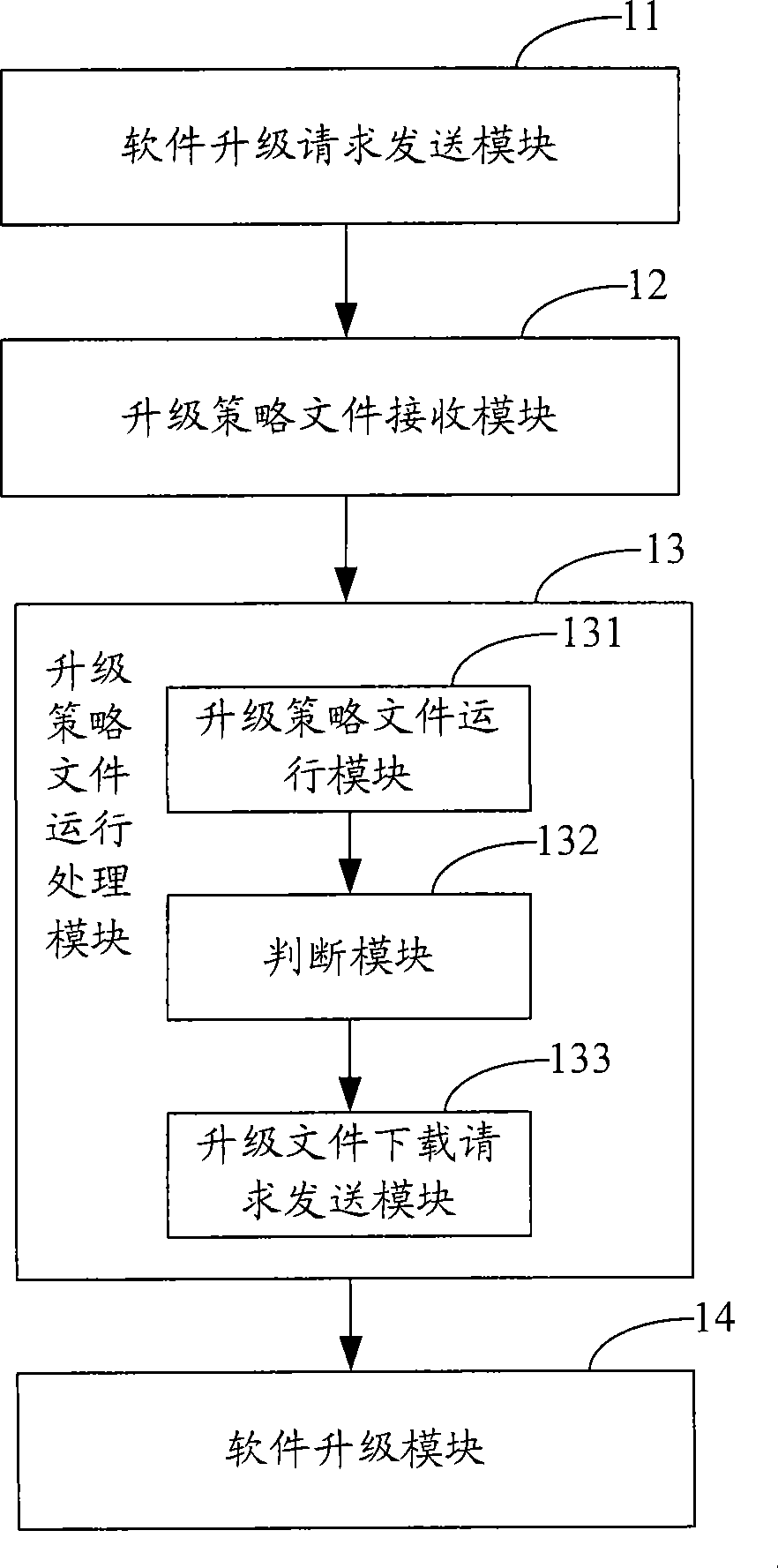
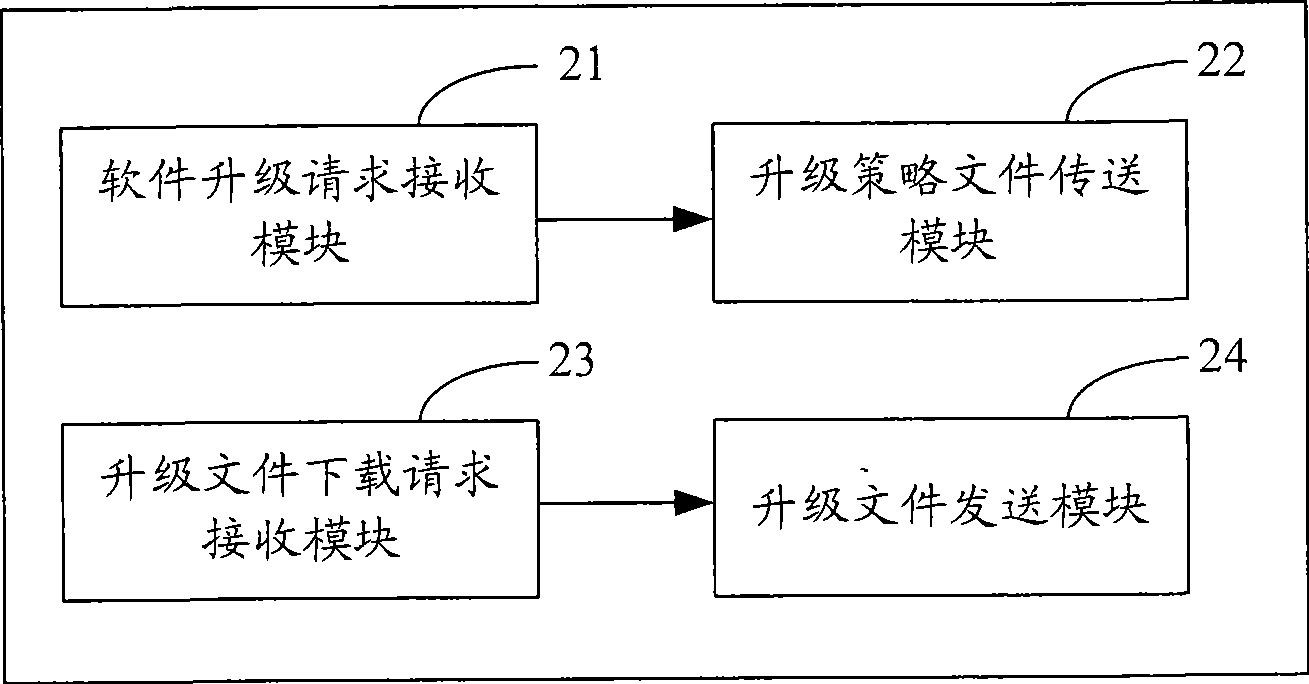
Method and system for updating software, digital television receive terminal and server
InactiveCN101472050AFlexible upgradeSecurity upgradeTelevision system detailsColor television detailsSoftware updateTerminal equipment
The invention is suitable for the digital television field, and provides a software updating method, a system, a digital television receiving terminal and a server. The method comprises the following steps: a software upgrading request is transmitted to the server according to the input request from the user; an upgrading strategy file sent by the server is received; the upgrading strategy file runs, and an upgrading file downloading request is transmitted to the server; and the upgrading file sent by the server is received, and the data updating and the software upgrading are performed. In the embodiment of the invention, since the software updating strategy method is obtained from the server, the upgrading file is downloaded from the server, the stability of the terminal device is enhanced, the time of leaving the factory for the terminal device is reduced, and meanwhile, the invention can perform software upgrading flexibly and safely.
Owner:TCL CORPORATION
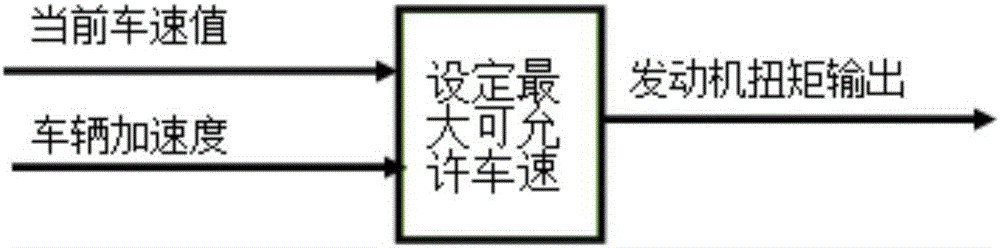
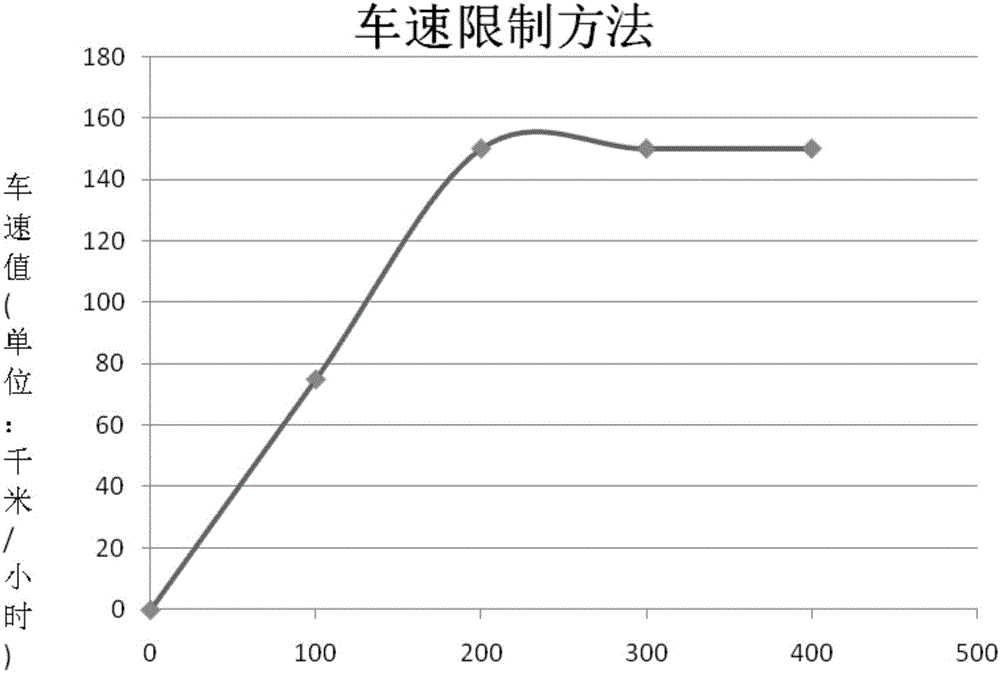
Vehicle speed limit system having active speed limit function and method
InactiveCN106515449ALow costGuaranteed uptimeVehicle fittingsSpeed/accelaration controlEmbedded systemSpeed limit
The present invention discloses a vehicle speed limit system having an active speed limit function. The system is provided with a key. The key outputs a key signal to a combination instrument, the combination instrument communicates with an ECU via a wire harness, and the combination instrument and the ECU acquire a vehicle speed signal. The vehicle speed limit system having the active speed limit function has the advantages that only a few key inputs need to be added, and the existing system sensor is used, the purpose is realized through optimizing the control target method, the equipment cost is low, the operation is stable and reliable, and the maximum limited speed can be adjusted according to the requirement.
Owner:CHERY AUTOMOBILE CO LTD
Beam exposure writing strategy system and method
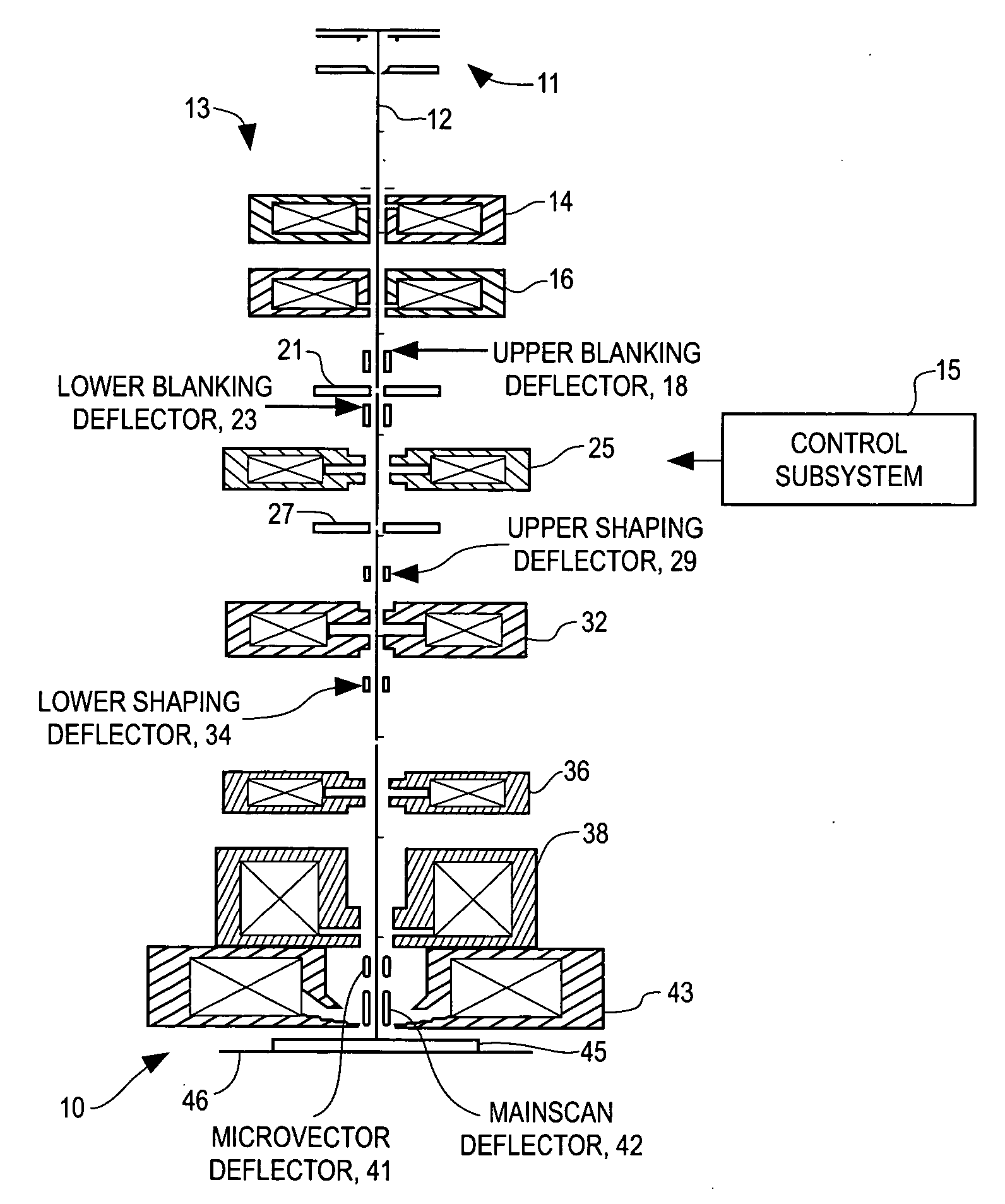
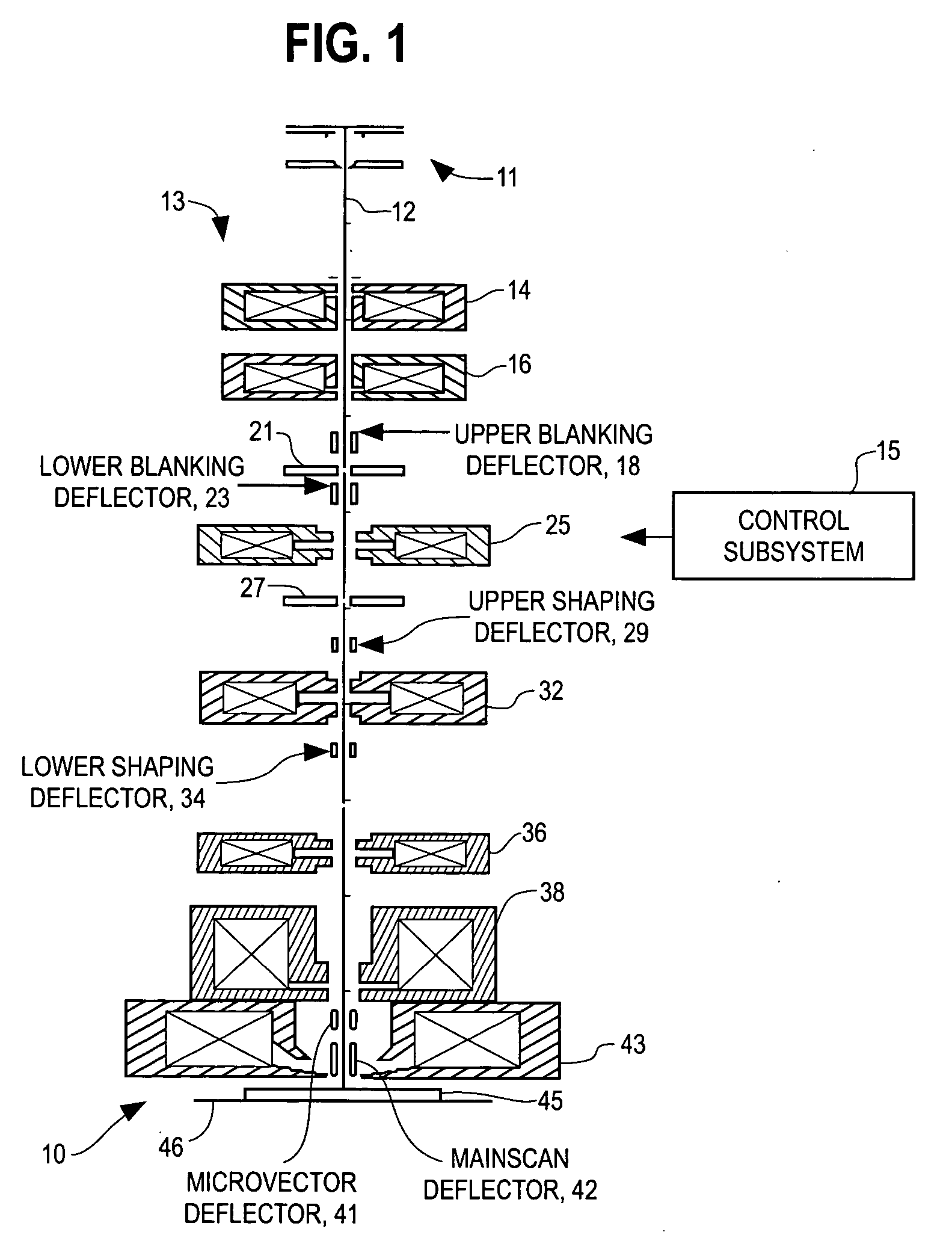
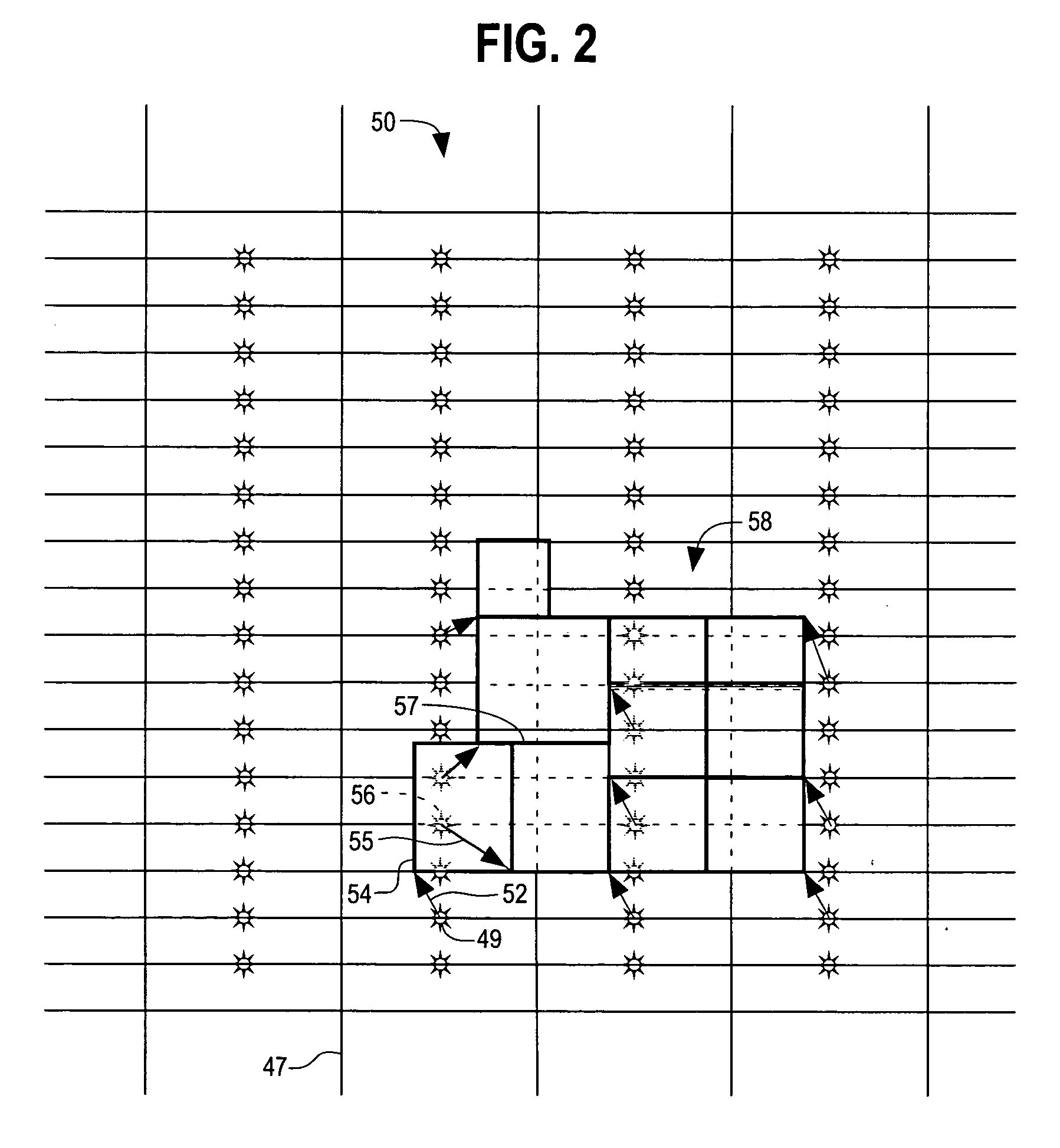
A beam exposure writing strategy method and system are disclosed for exposing a desired pattern on a substrate, by raster scanning a beam such as a particle beam, across a major field on the substrate. The beam is also vector scanned across a minor field of the substrate superimposed along the major field raster scan. The beam is selectively blanked and unblanked as the beam is being scanned. The unblanked flashes of the beam are modulated in coordination with the raster and vector scanning to expose the desired pattern on the substrate. The disclosed system and method generating an adjustable length microvector having a maximum range of at least about N time a nominal length λ, where N is equal to four and λ is substantially equal to a dimension of a nominal flash area, the nominal flash location dimension being substantially greater than a major field cell dimension.
Owner:APPLIED MATERIALS INC
Data center network flow balancing method and device oriented to software definition
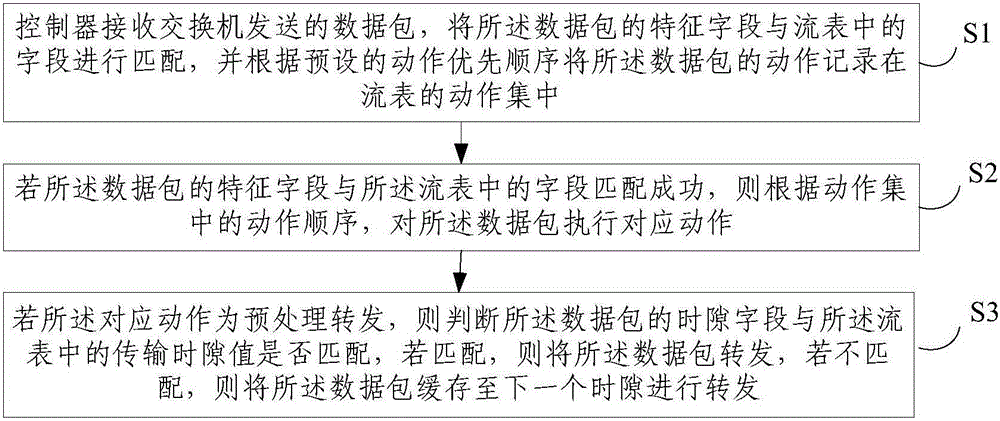
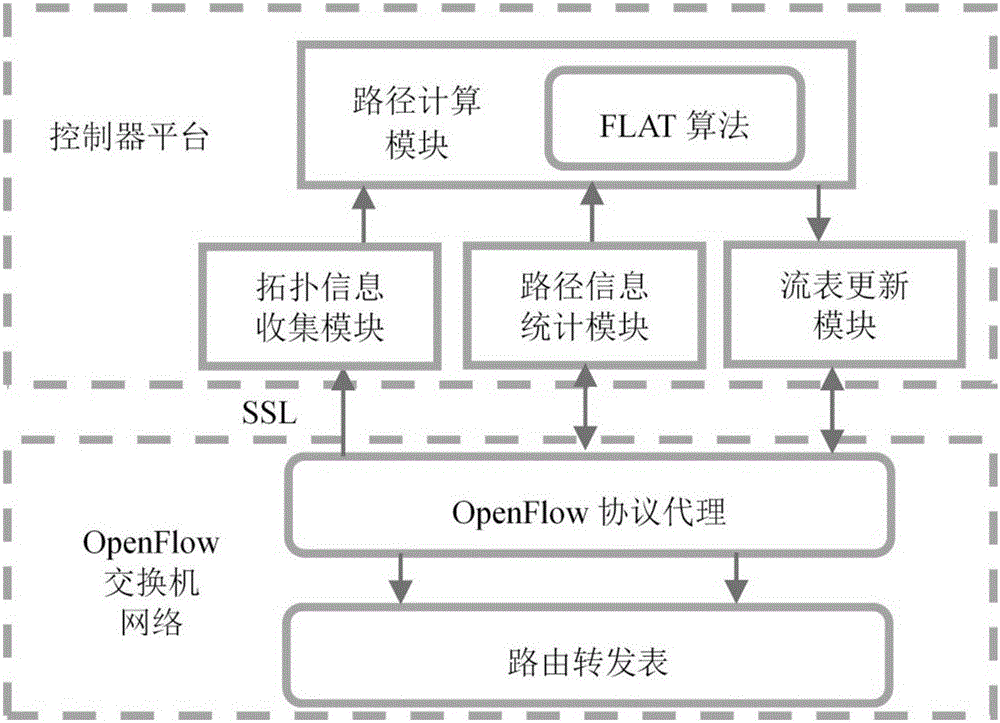
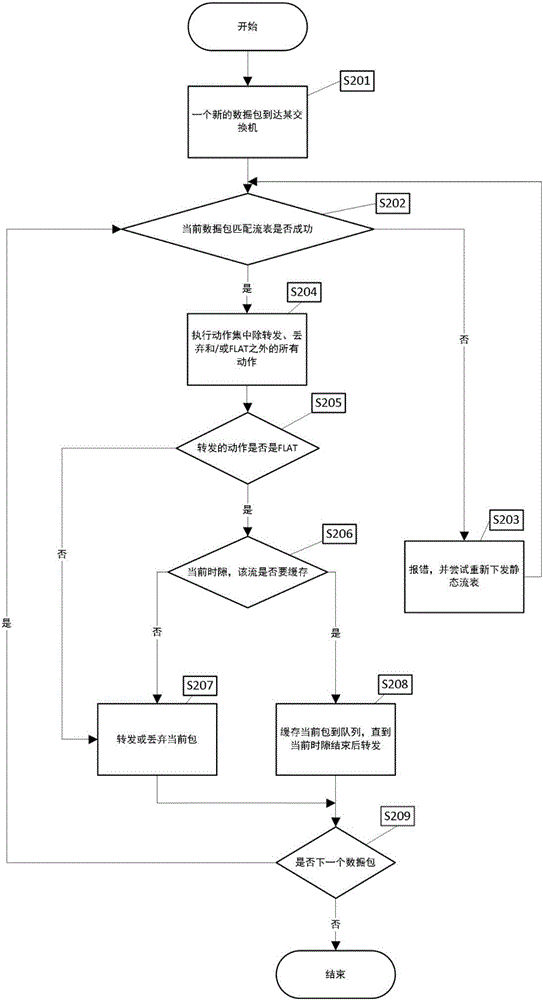
ActiveCN105915467AAvoid disorderImprove scalabilityData switching networksExtensibilityTraffic capacity
The invention discloses a data center network flow balancing method and a data center network flow balancing device oriented to software definition. The data center network flow balancing method comprises the steps that: a controller receives a data packet transmitted by a switch, matches feature fields of the data packet with fields in a flow table, and records actions of the data packet in an action set of the flow table according to a preset action priority; a corresponding operation is carried out on the data packet according to the action sequence in the action set if the feature fields of the data packet are successfully matched with the fields in the flow table; and whether a time slot field of the data packet is matched with a transmission time slot value in the flow table is judged if the corresponding operation is pretreatment forwarding, if so, then the data packet is forwarded, and if not, the data packet is cached to a next time slot for forwarding. The data center network flow balancing method and the data center network flow balancing device simplify deployment, enhance network expandability, and solve the problems of data flow packet loss during the strategy implementation process and disorder of data packets which may occur at a receiving end.
Owner:TSINGHUA UNIV +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com