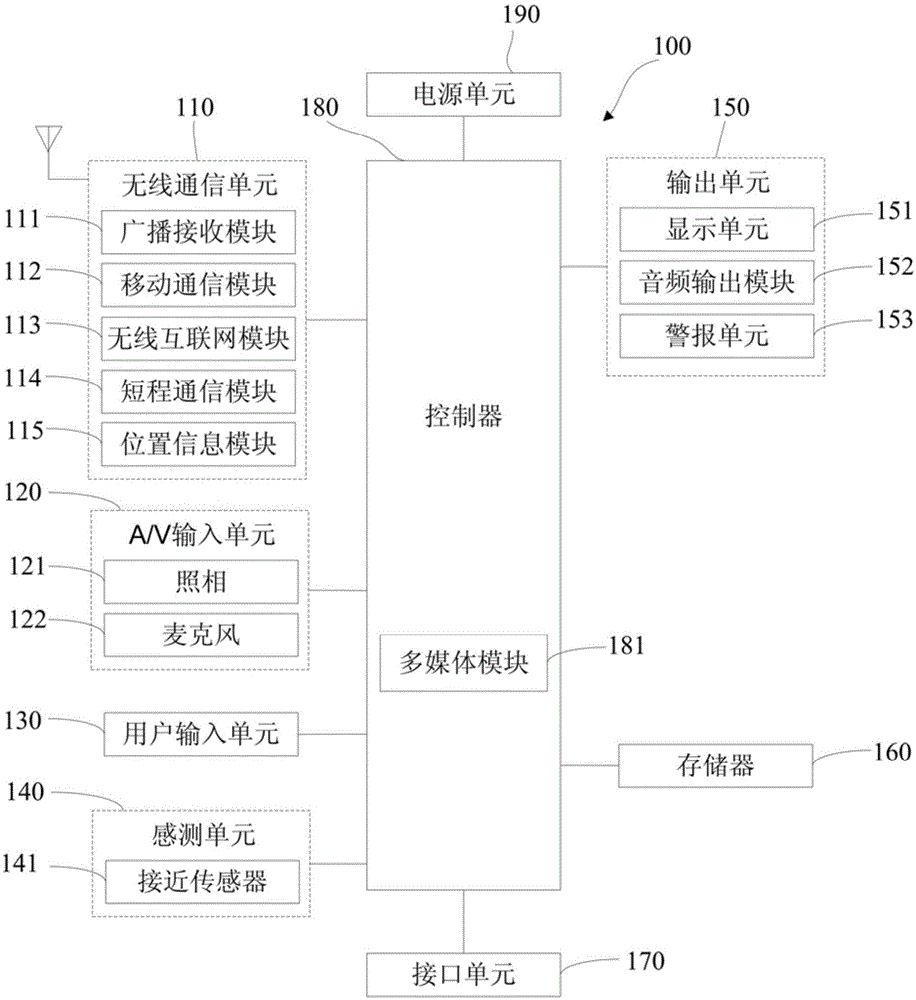
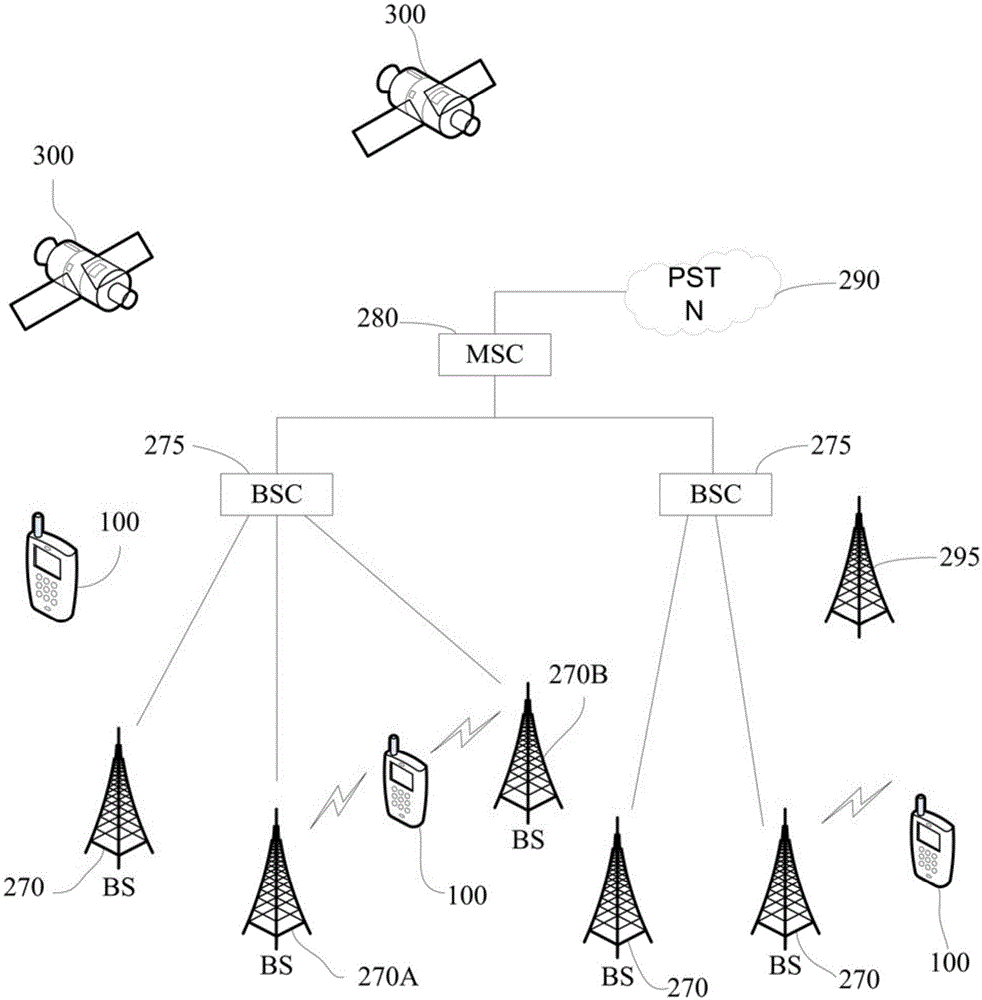
Patents
Literature
46results about How to "Security upgrade" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
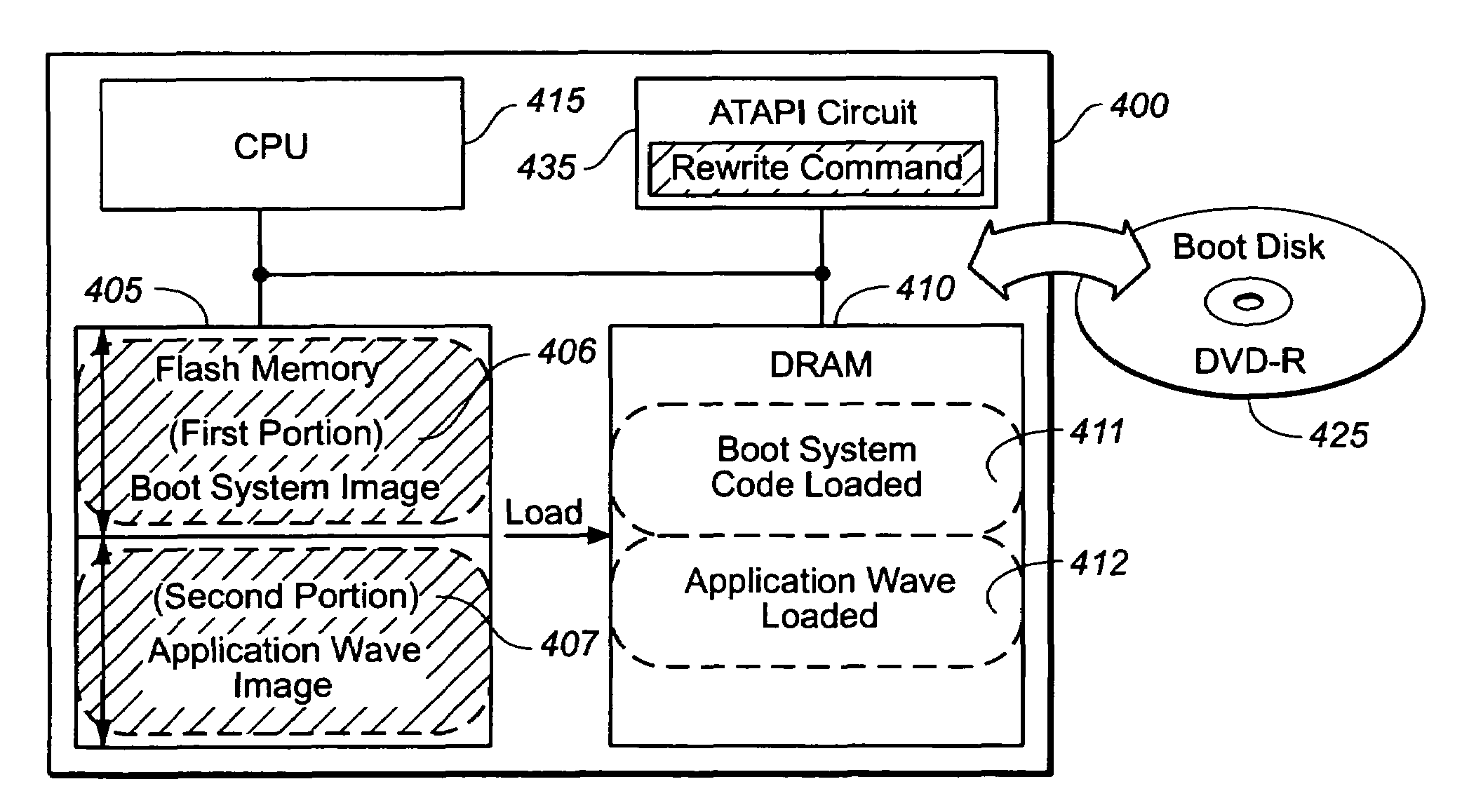
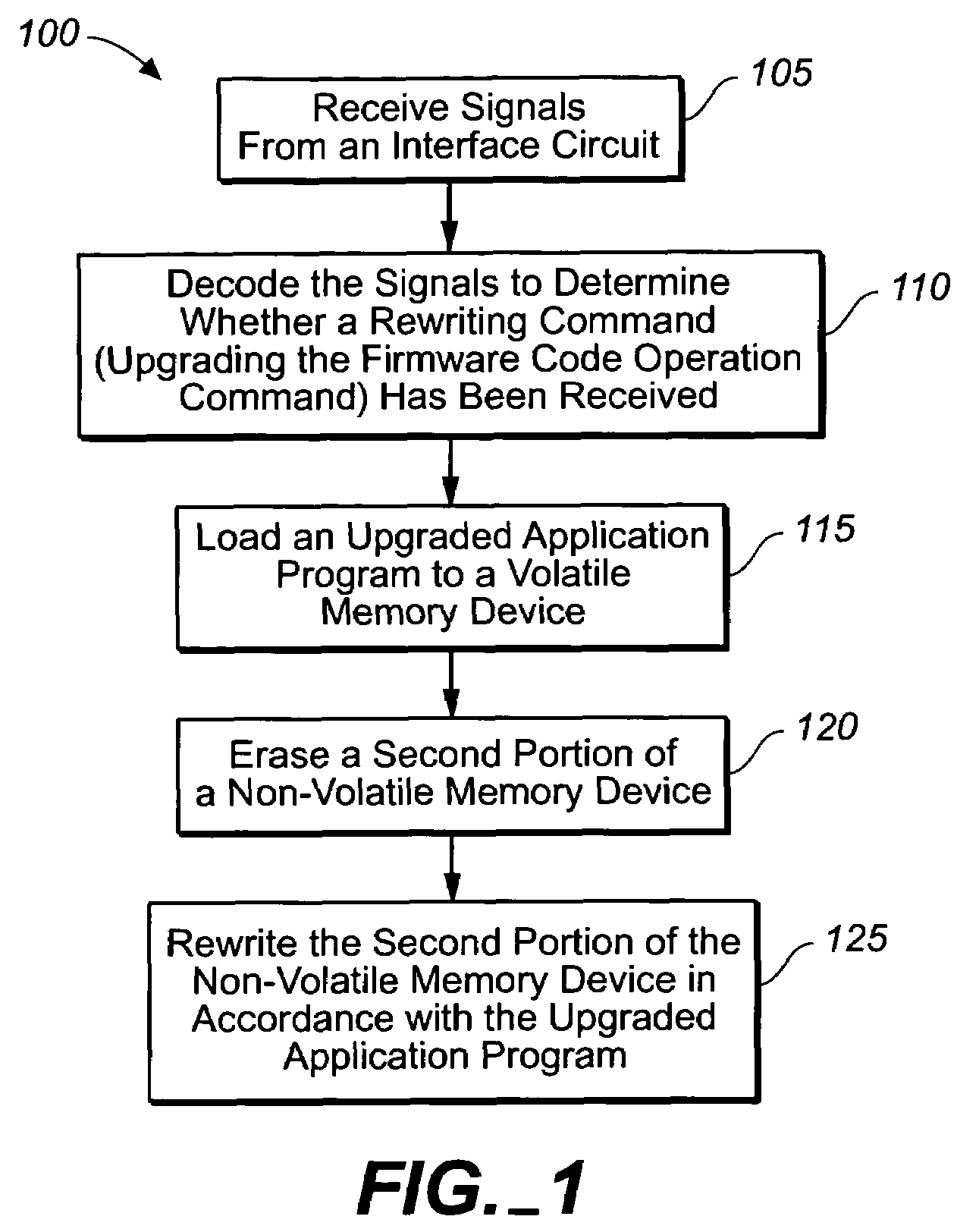
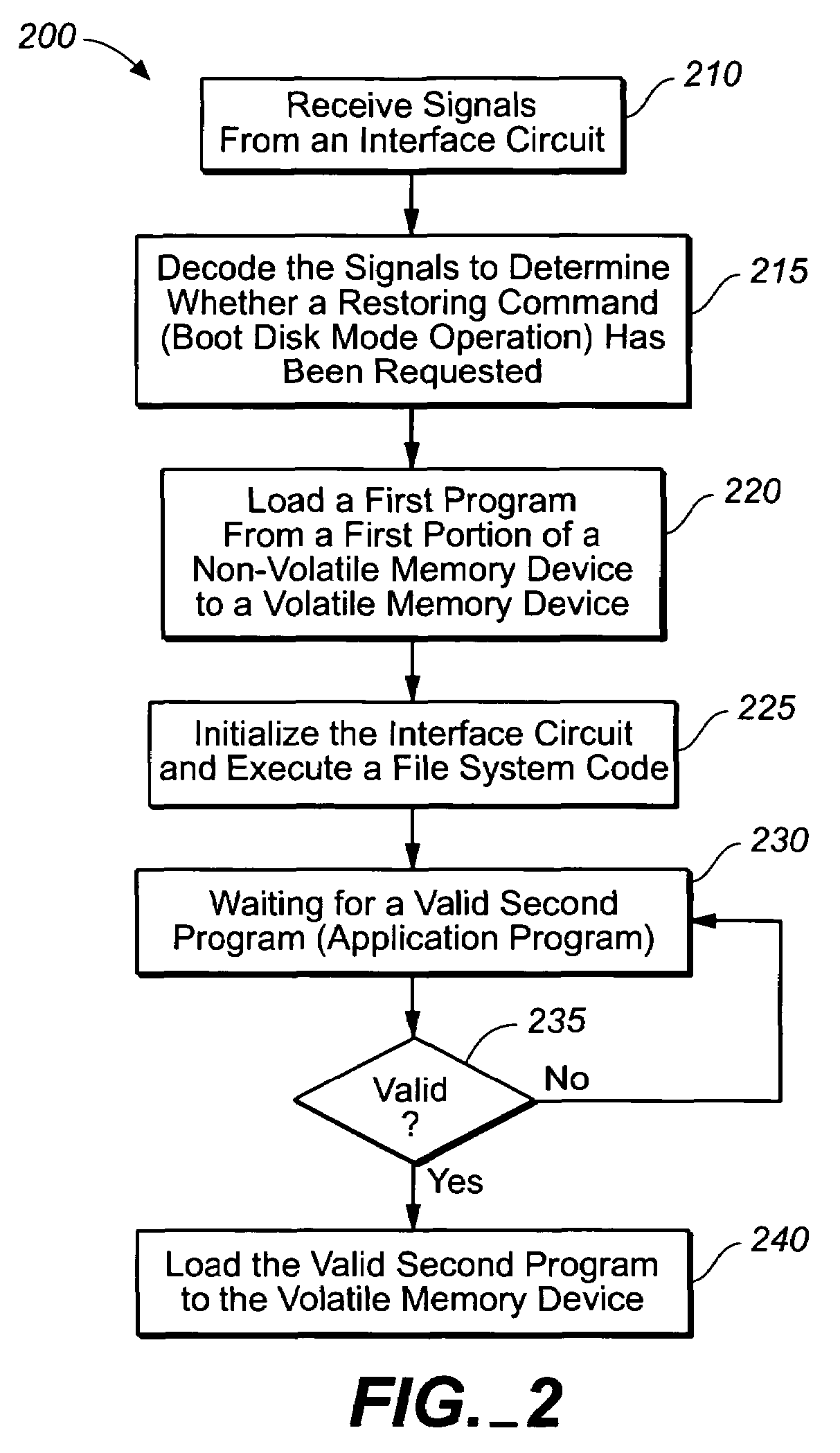
Safe method for upgrading firmware of optical disk product
ActiveUS20050138645A1Method securitySecurity upgradeError detection/correctionProgram loading/initiatingCompact discSystem failure
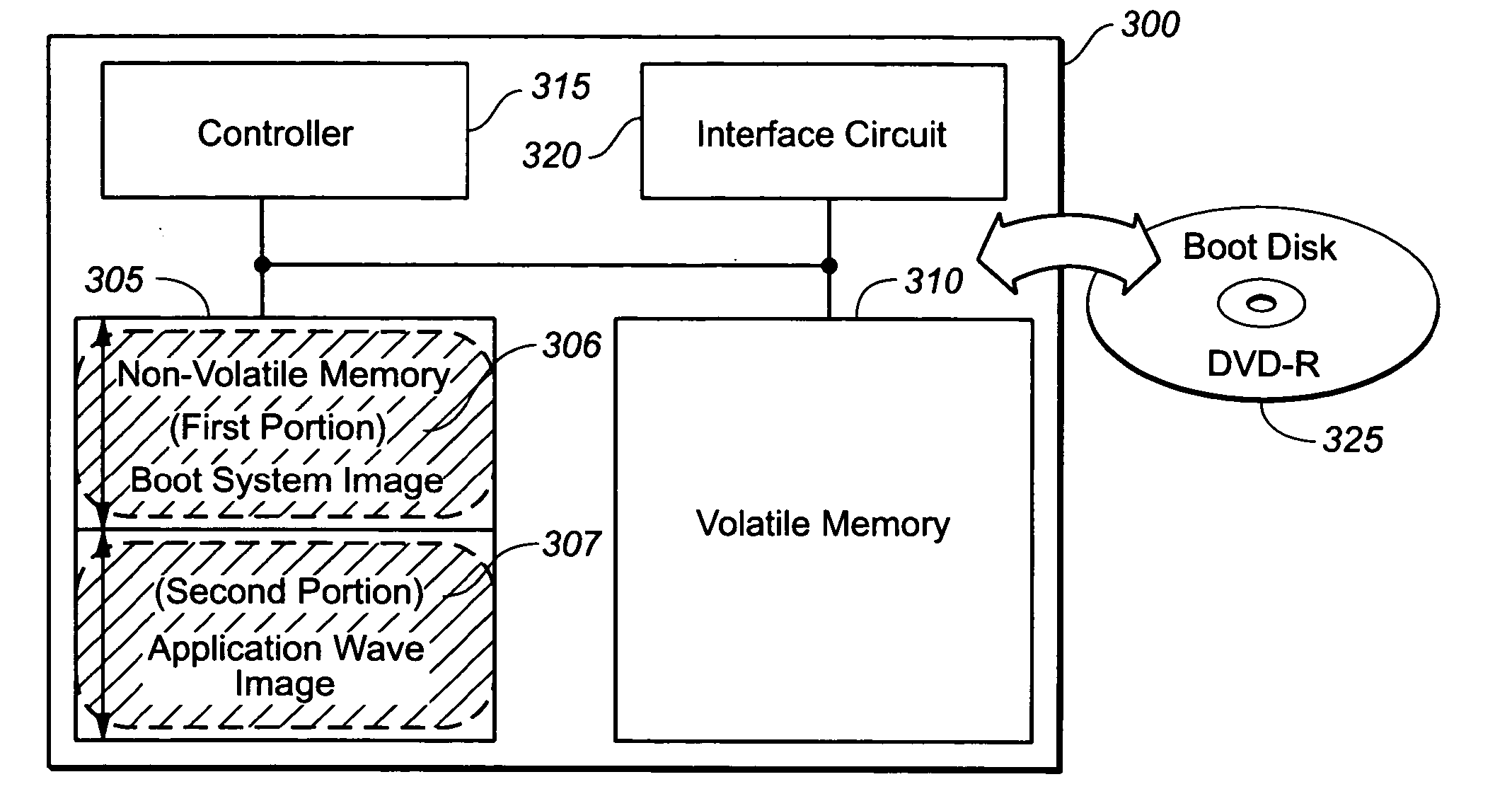
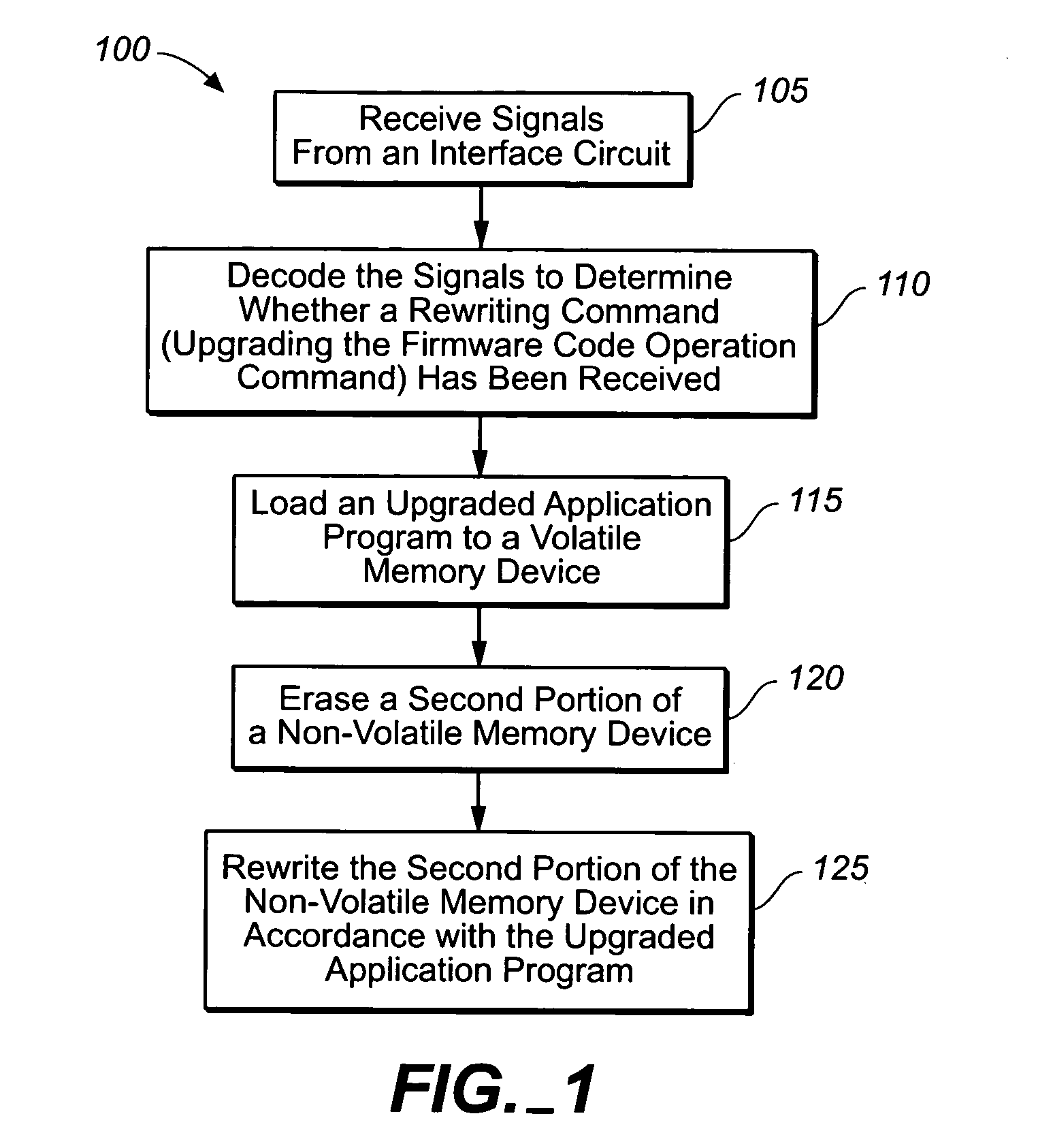
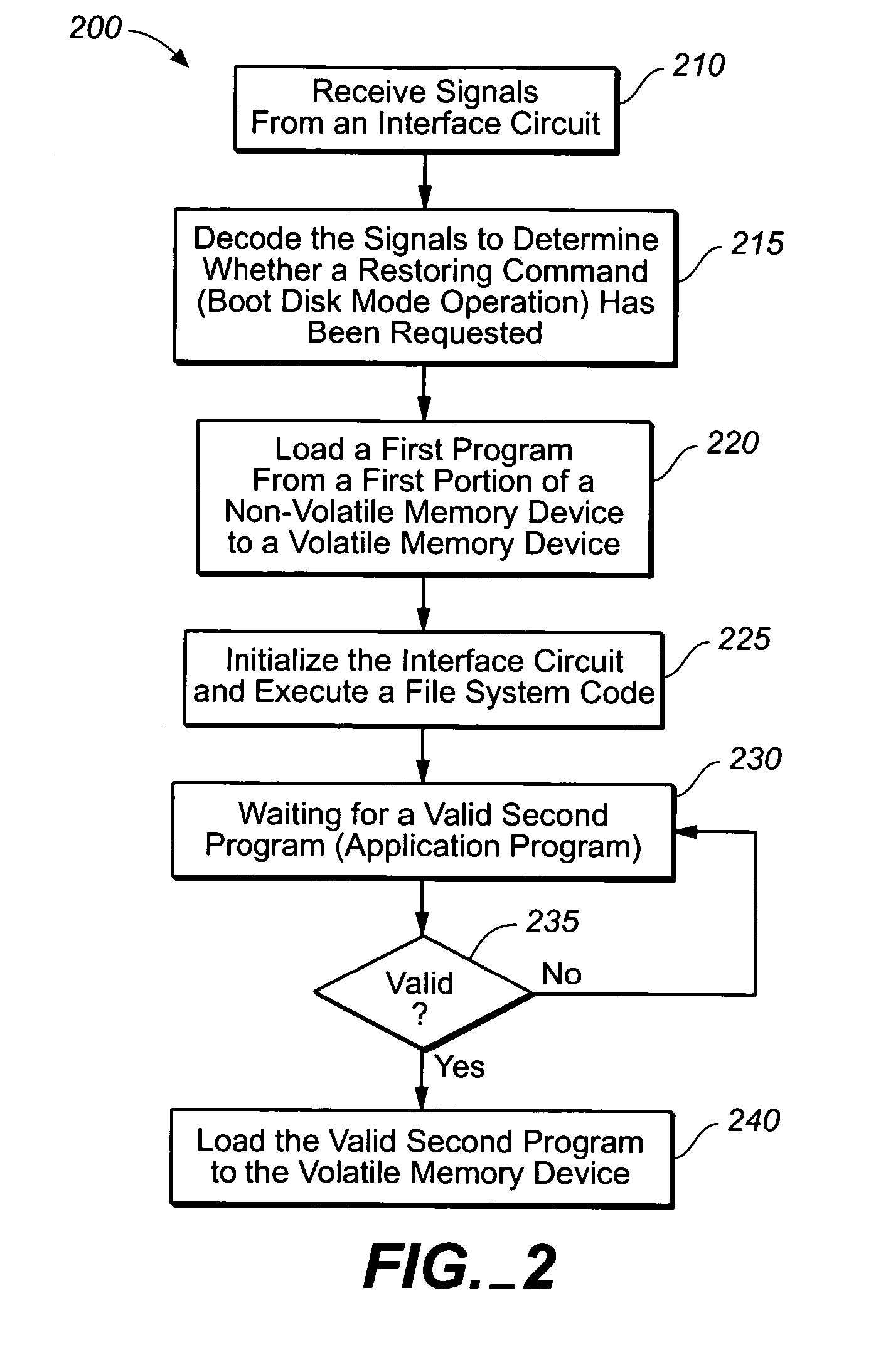
The present invention provides a safe method for upgrading firmware code for optical disk products without corrupting firmware even if an abnormality occurs during a upgrading a firmware process. A nonvolatile memory device of the present invention may store a boot system image and an application ware image separately. End users may update the application ware image by executing an upgraded application program. However the boot system image stored in the nonvolatile memory device may not be modified at any event and it may be used to restore the optical disk product from a system failure caused by a corrupted firmware.
Owner:AVAGO TECH INT SALES PTE LTD
Reconfigurable software unit upgrading method
InactiveCN101290579ASave bandwidthConfigurableTelevision system detailsColor television detailsComputer moduleEmbedded software
The invention relates to the embedded software field, in particular to a configurable software unitization upgrading method aiming at digital television set-top boxes. The invention puts forward a configurable, flexible, efficient and safe software on-line upgrading method. The method comprises the following steps that: a. upgradeable software and data having fixed storage addresses are marked into individual unit modules, and module configuration information is established for each unit module and stored on a terminal; b. the upgrading data and configuration information of all the unit modules needing to be upgraded are packaged to generate upgrade files and configuration files; c. a code stream generation tool is used to form code streams of the upgrade files and configuration files and send the code streams out; d. the terminal downloads the configuration files to judge which modules are needed for upgrading the terminal, and then downloads the upgrade files of the modules needing to be upgraded so as to carry out upgrading. The upgrading method is flexible in upgrade, high in efficiency, good in safety and suitable for the upgrade of embedded software.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
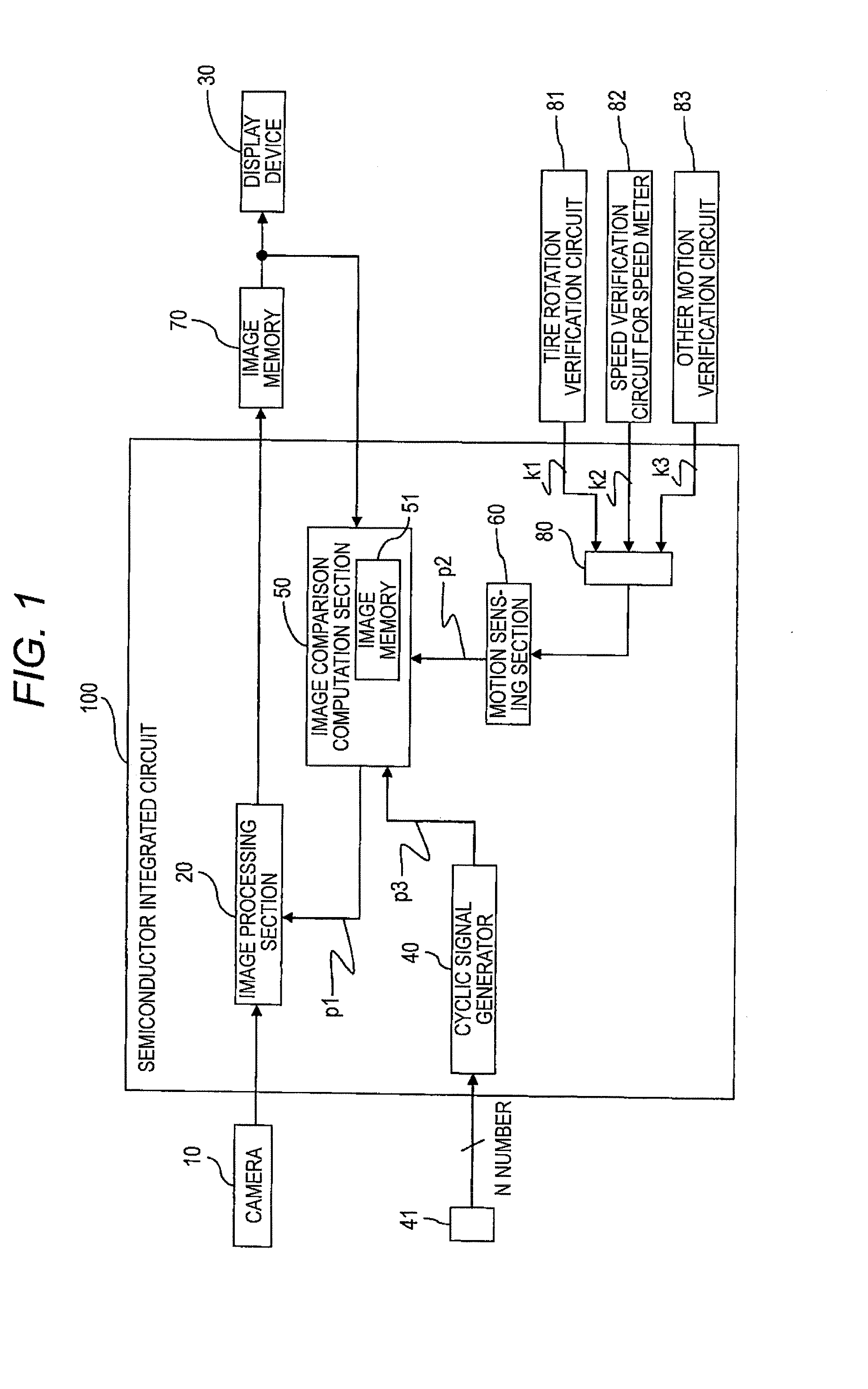
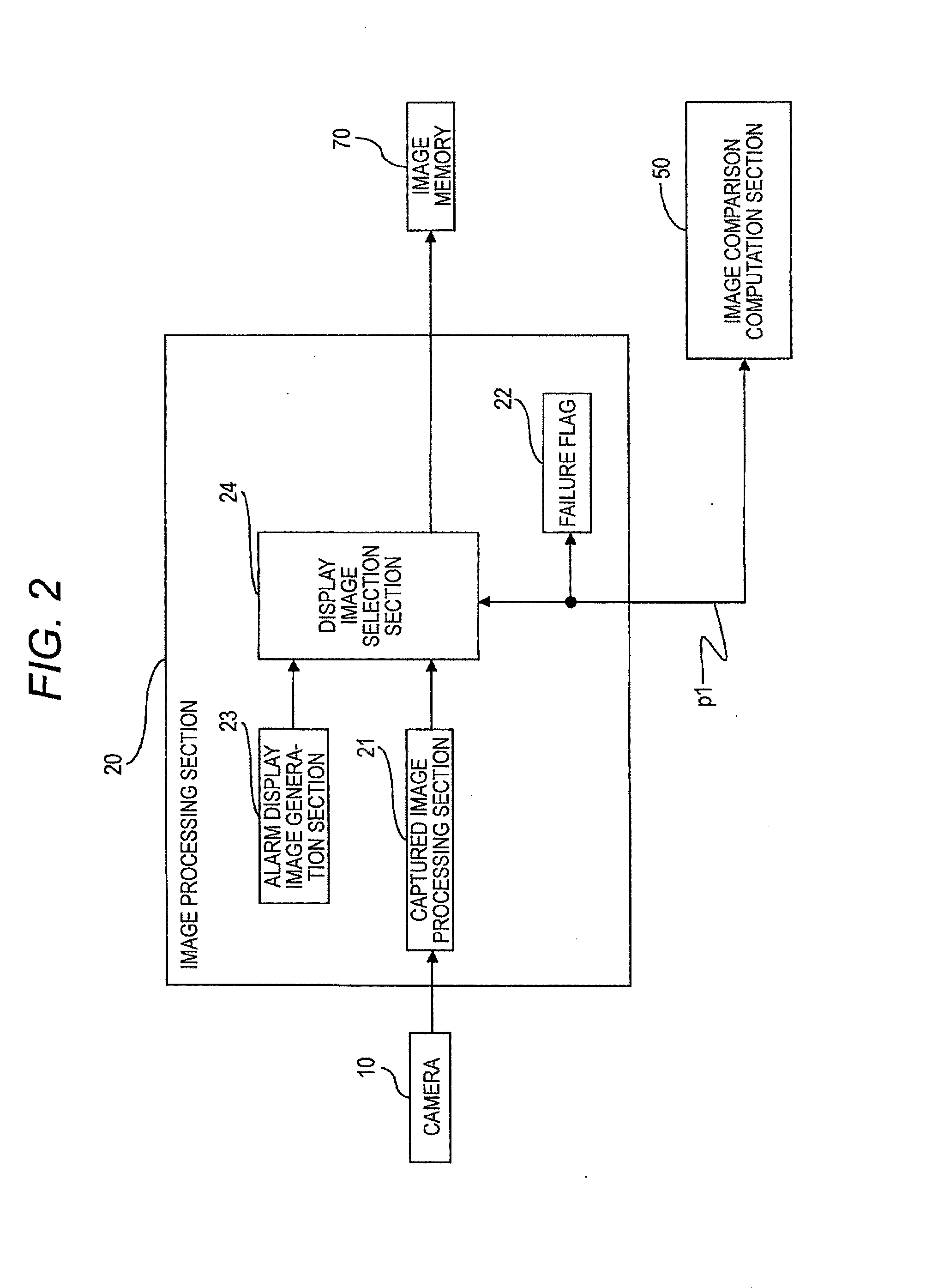
Monitoring system, method for controlling the same, and semiconductor integrated circuit for the same
InactiveUS20130088596A1Avoid accidentsImplement the buildColor television detailsClosed circuit television systemsImaging processingDisplay device
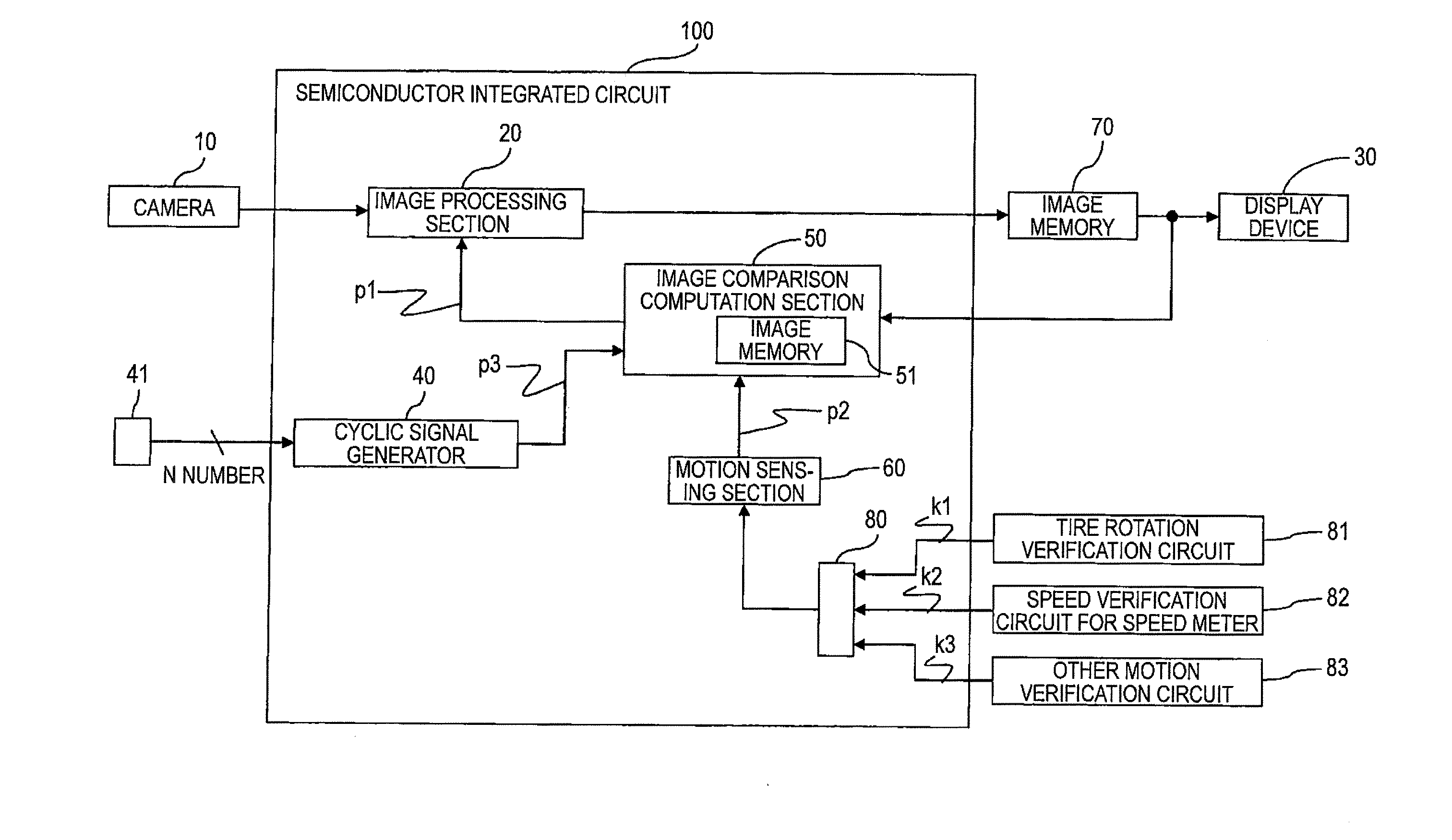
An image comparison section provided in a monitoring system compares current image data with past image data acquired in at least one preceding cycle when a vehicle is determined to be in motion on the basis of an output signal input from a motion sensing section. On the basis of a comparison result, the image comparison section determines whether or not a camera or an image processing section broke down. When there is a failure, the image comparison section outputs an output signal reporting the failure to the image processing section. Upon receipt of the output signal, the image processing section performs image processing intended for the event of a failure, and transmits failure information while superimposing the failure information on an image signal, thereby changing a display device to a monochrome display or an alarm display.
Owner:PANASONIC CORP
Safe method for upgrading firmware of optical disk product
ActiveUS7376943B2Method securitySecurity upgradeError detection/correctionProgram loading/initiatingApplication program softwareSystem failure
The present invention provides a safe method for upgrading firmware code for optical disk products without corrupting firmware even if an abnormality occurs during a upgrading a firmware process. A nonvolatile memory device of the present invention may store a boot system image and an application ware image separately. End users may update the application ware image by executing an upgraded application program. However the boot system image stored in the nonvolatile memory device may not be modified at any event and it may be used to restore the optical disk product from a system failure caused by a corrupted firmware.
Owner:AVAGO TECH INT SALES PTE LTD
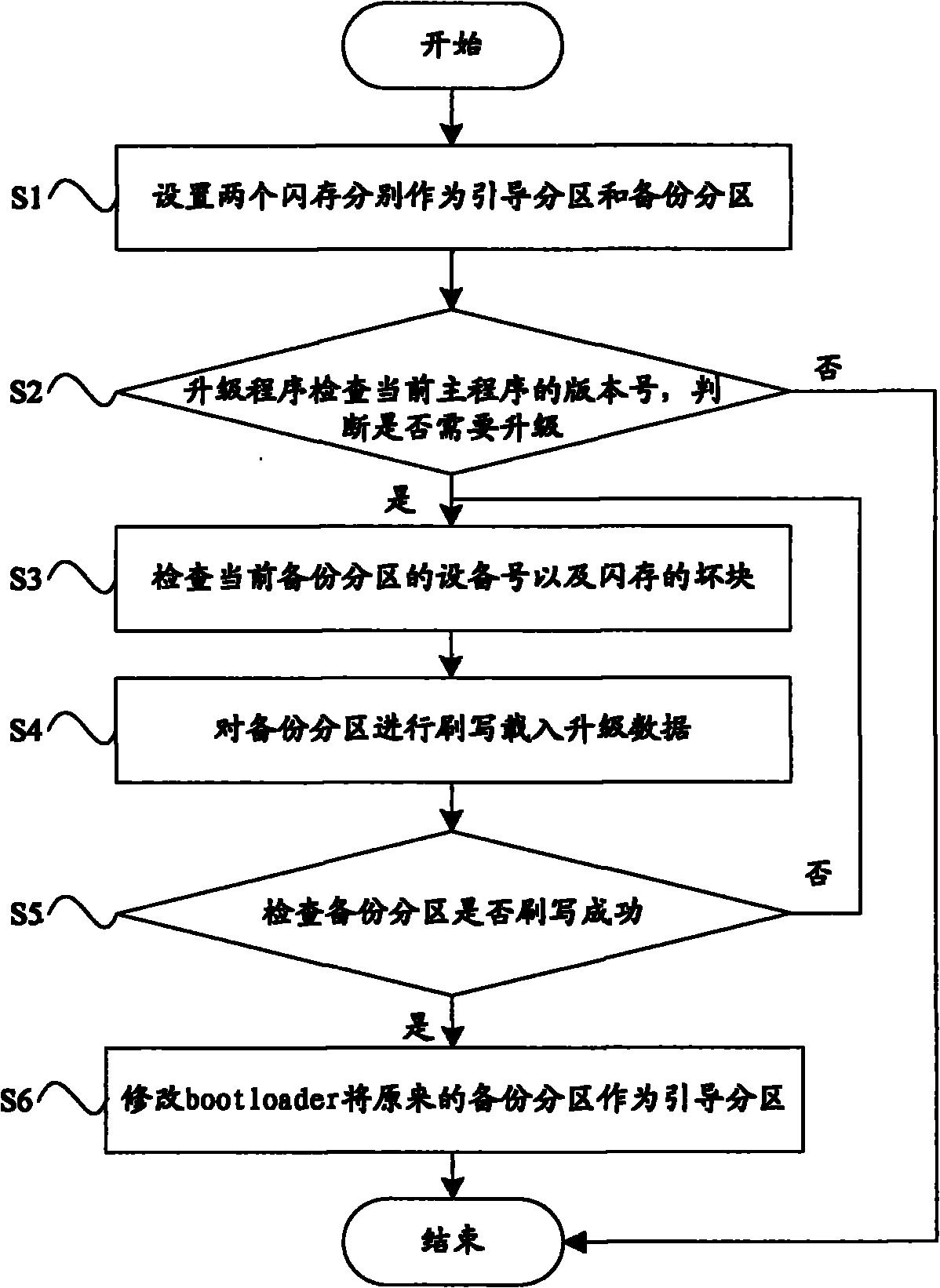
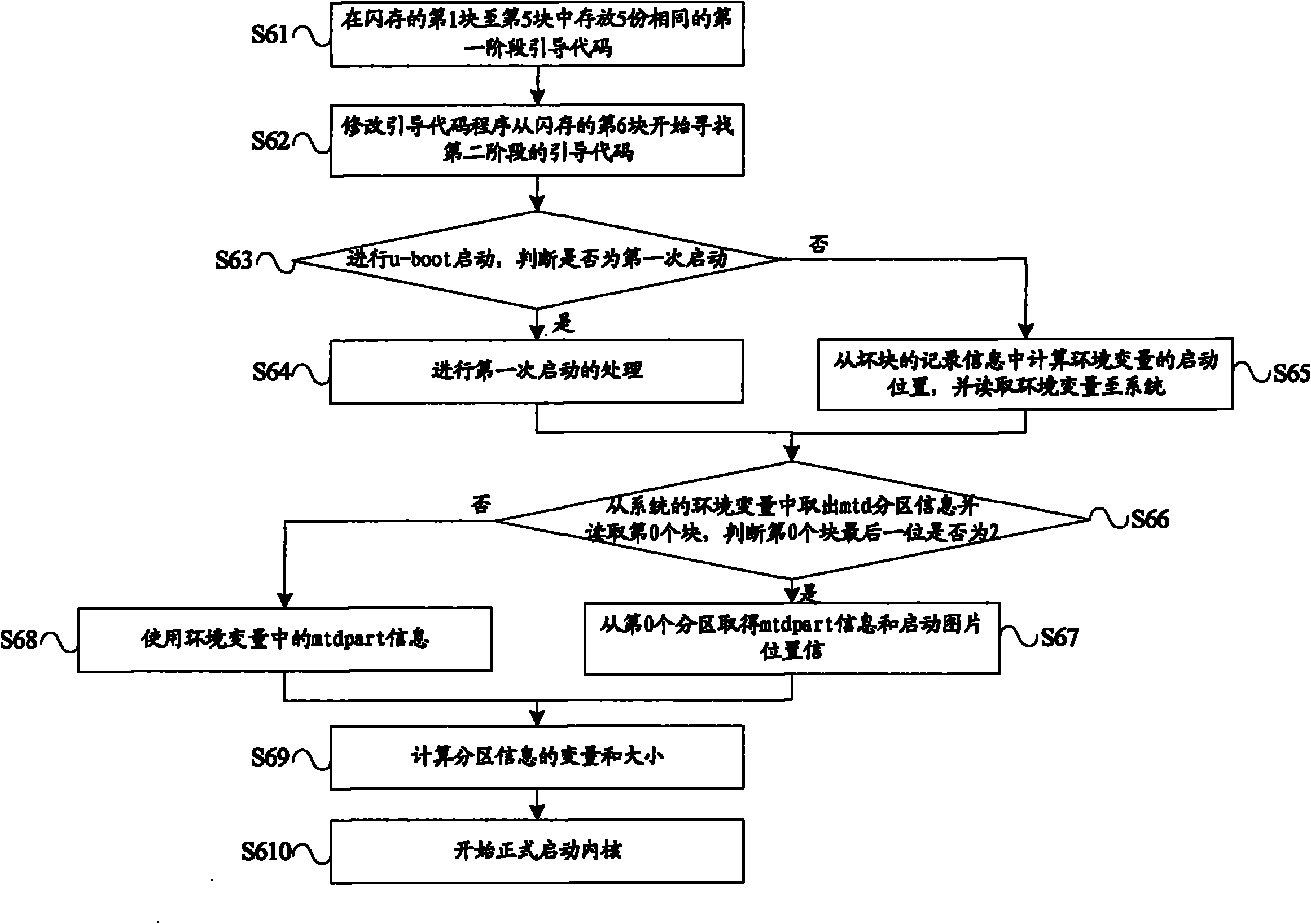
Method for automatically upgrading network television
ActiveCN102104750ASecurity upgradeImprove reliabilityTelevision system detailsColor television detailsUpgradeCable television
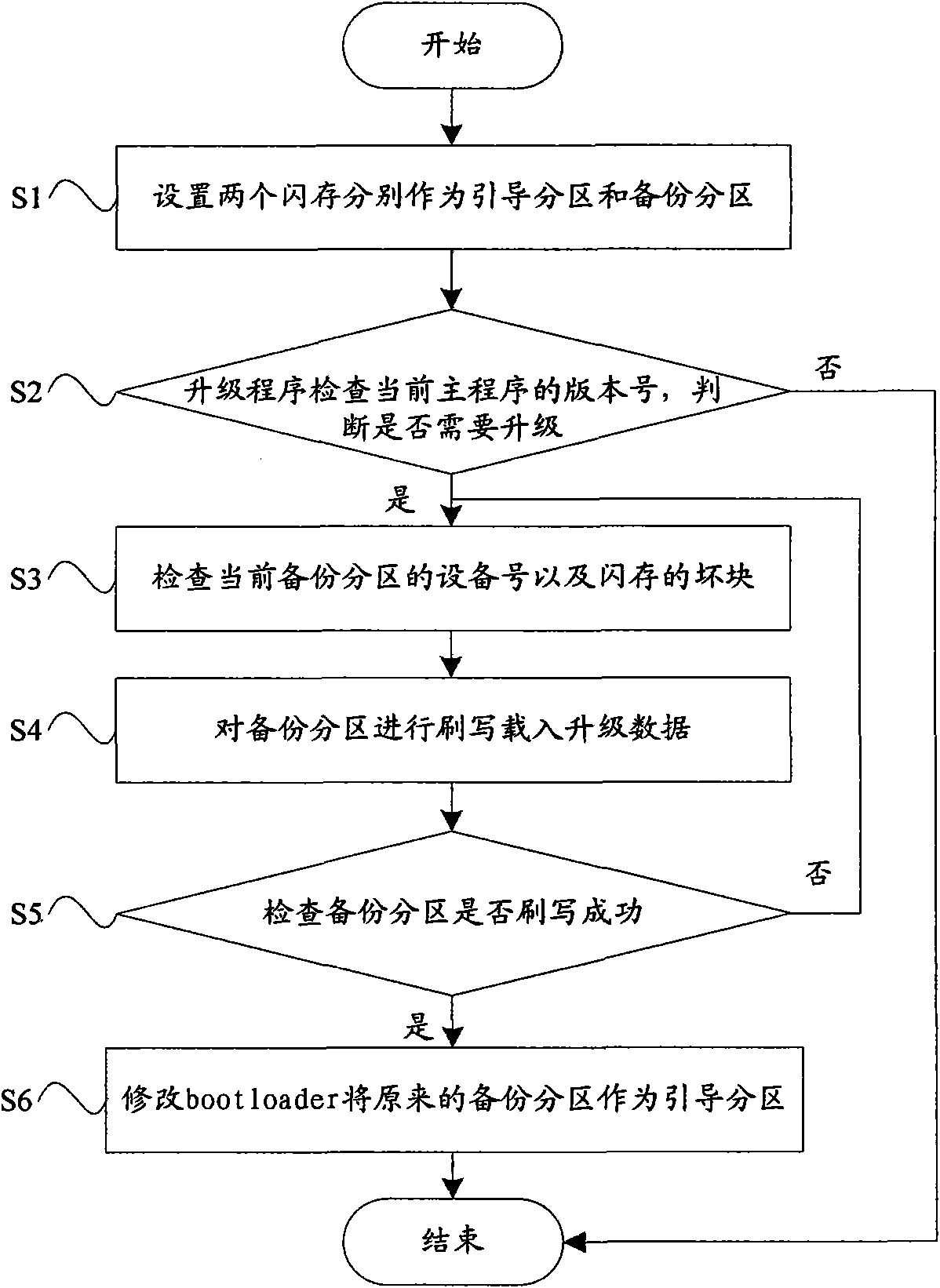
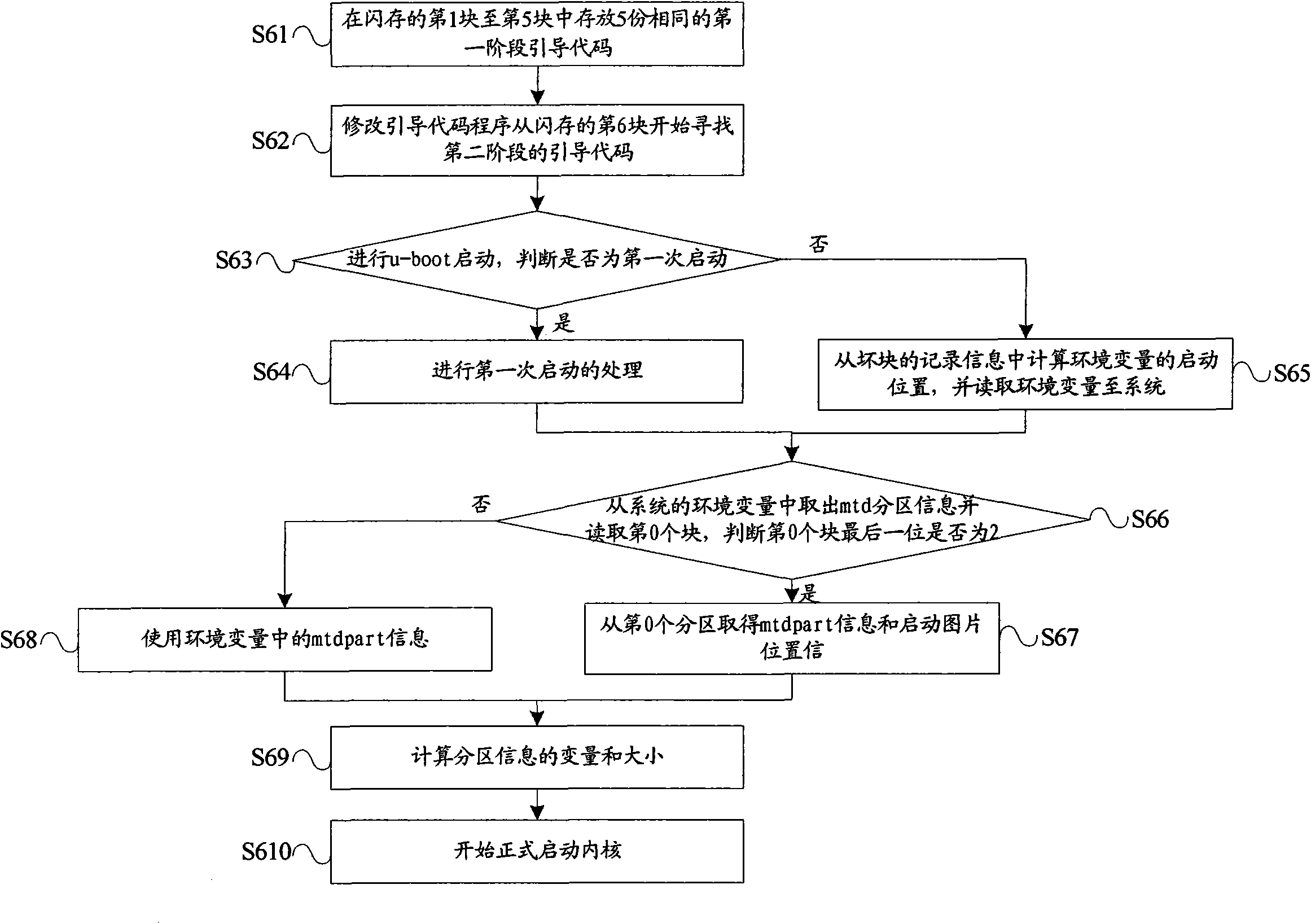
The invention relates to a method for automatically upgrading a network television, which comprises the following steps of: S1, setting one flash memory for a boot subarea to store a current used main program and setting the other flash memory for a backup subarea to store the backup of the current used main program in a bootloader; S2, checking the version number of the current main program by an upgrade program, judging whether upgrade is needed, if so, turning to a step S3, otherwise, ending; S3, checking the equipment number of the current backup subarea and the bad block of the flash memories; S4, flashing the backup subarea to load upgrade data; S5, checking whether the backup subarea is flashed successfully, if so, turning to a step S6, otherwise, turning to the step S3; and modifying the bootloader to change the original backup subarea into the boot subarea. The method for automatically upgrading the network television ensures that the network television cannot be upgraded safely by adopting a double-machine hot backup mode, and reduces the cost of home maintenance.
Owner:KONKA GROUP
Method and system for updating software, digital television receive terminal and server
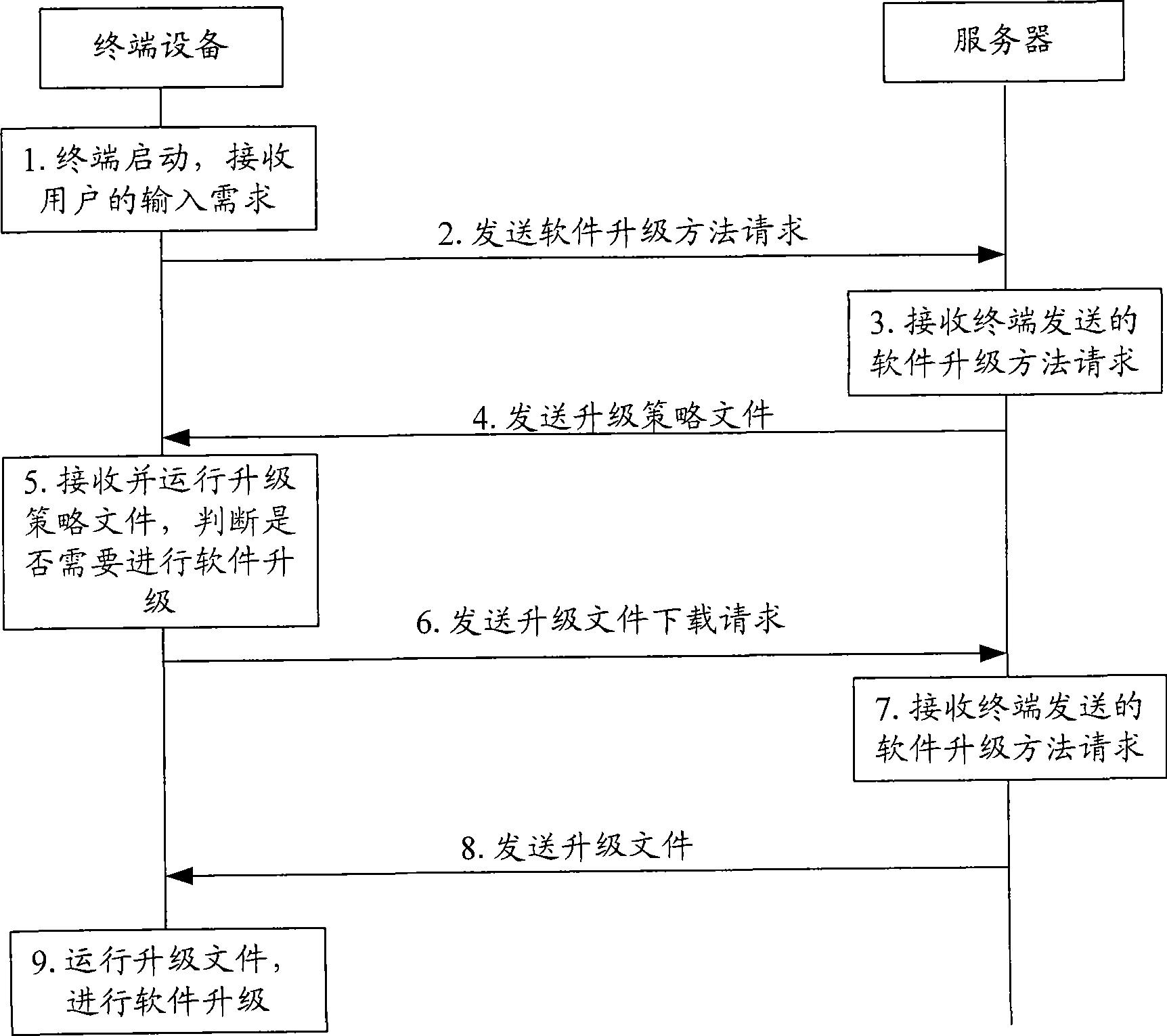
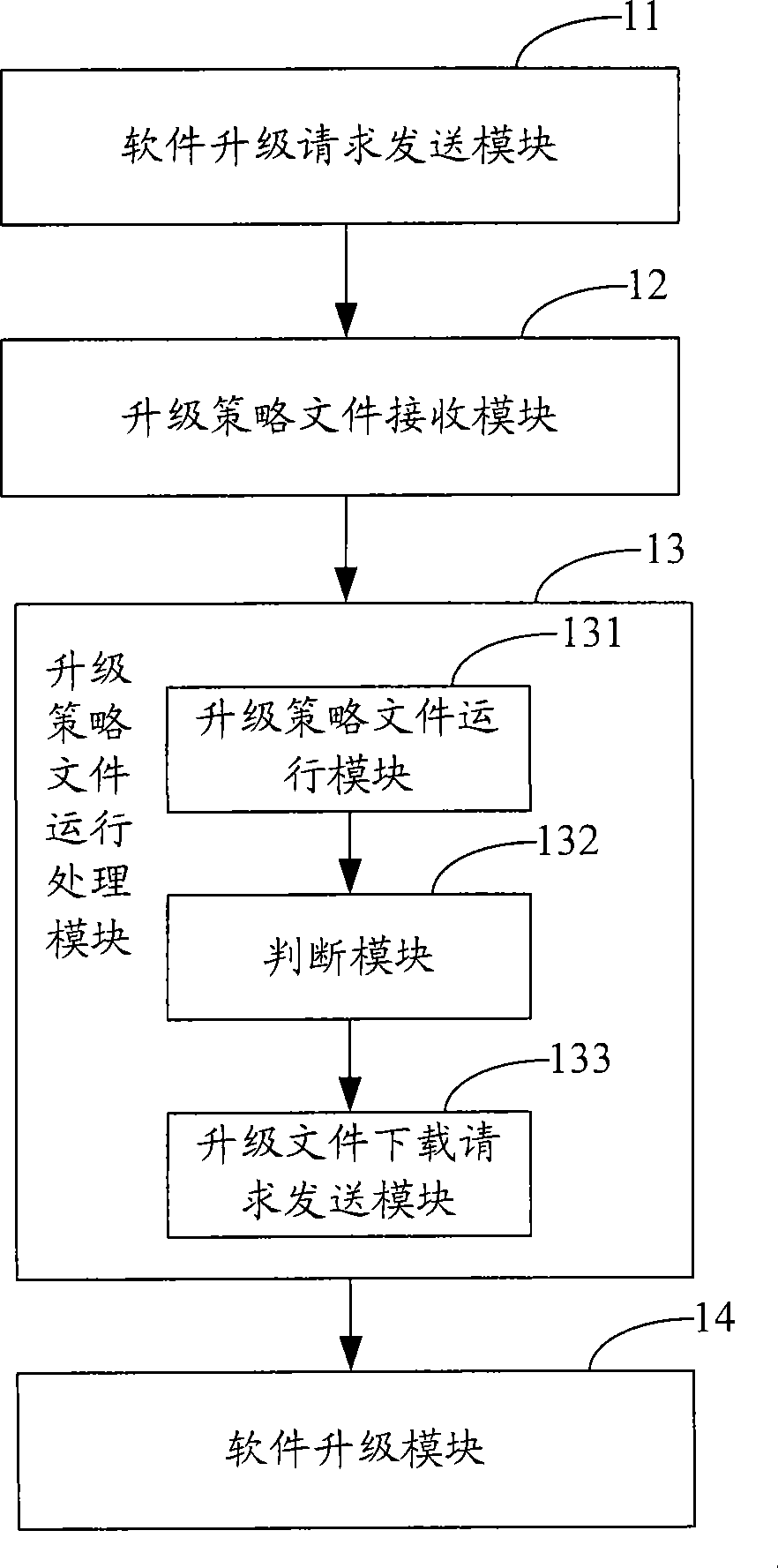
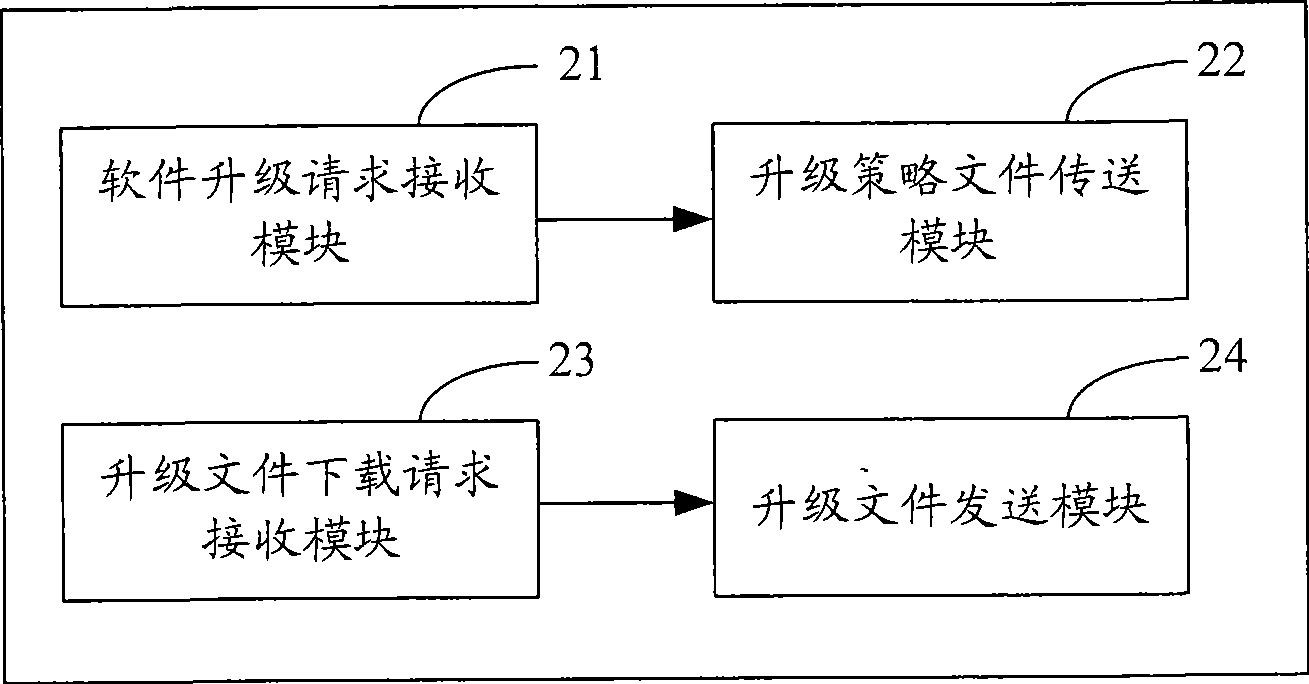
InactiveCN101472050AFlexible upgradeSecurity upgradeTelevision system detailsColor television detailsSoftware updateTerminal equipment
The invention is suitable for the digital television field, and provides a software updating method, a system, a digital television receiving terminal and a server. The method comprises the following steps: a software upgrading request is transmitted to the server according to the input request from the user; an upgrading strategy file sent by the server is received; the upgrading strategy file runs, and an upgrading file downloading request is transmitted to the server; and the upgrading file sent by the server is received, and the data updating and the software upgrading are performed. In the embodiment of the invention, since the software updating strategy method is obtained from the server, the upgrading file is downloaded from the server, the stability of the terminal device is enhanced, the time of leaving the factory for the terminal device is reduced, and meanwhile, the invention can perform software upgrading flexibly and safely.
Owner:TCL CORPORATION
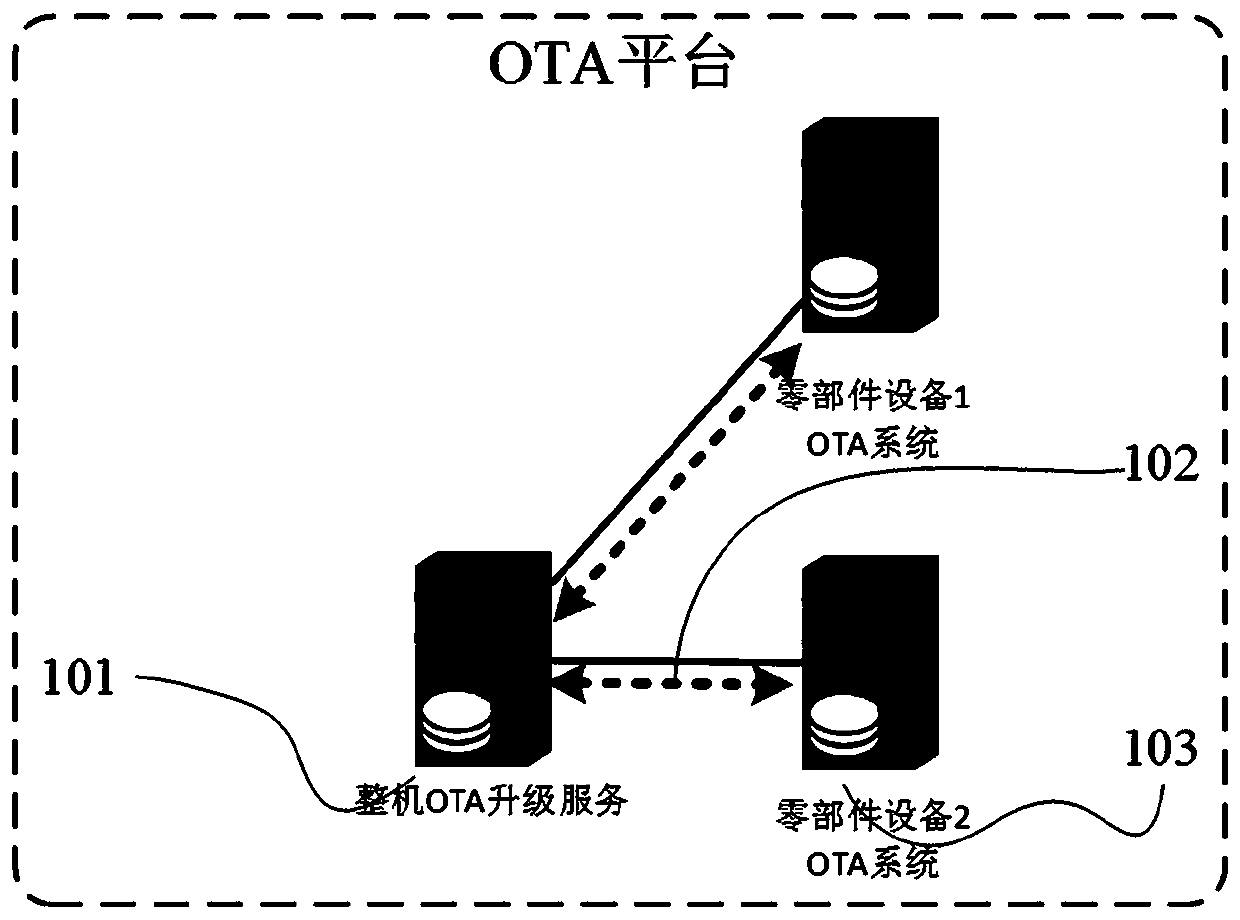
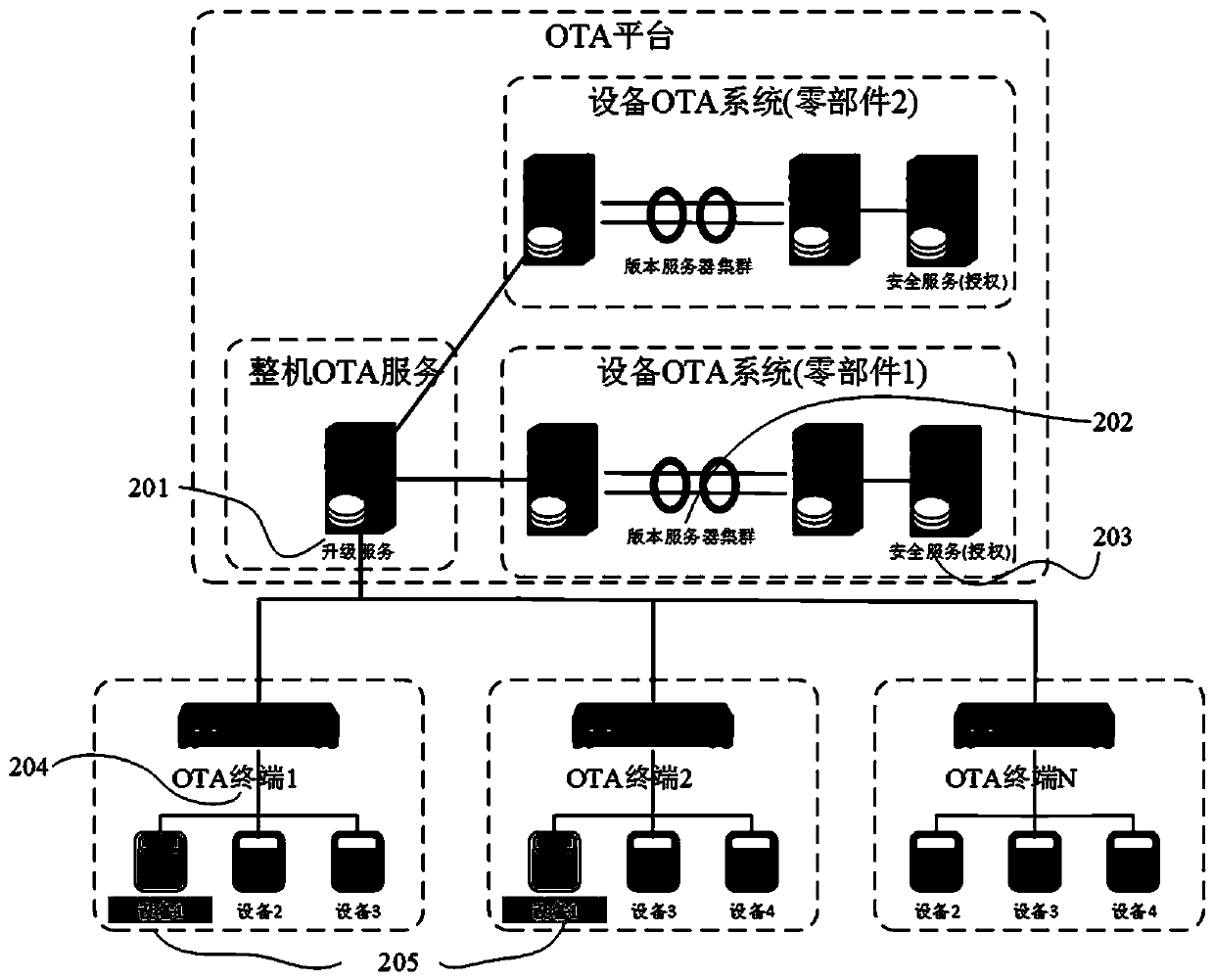
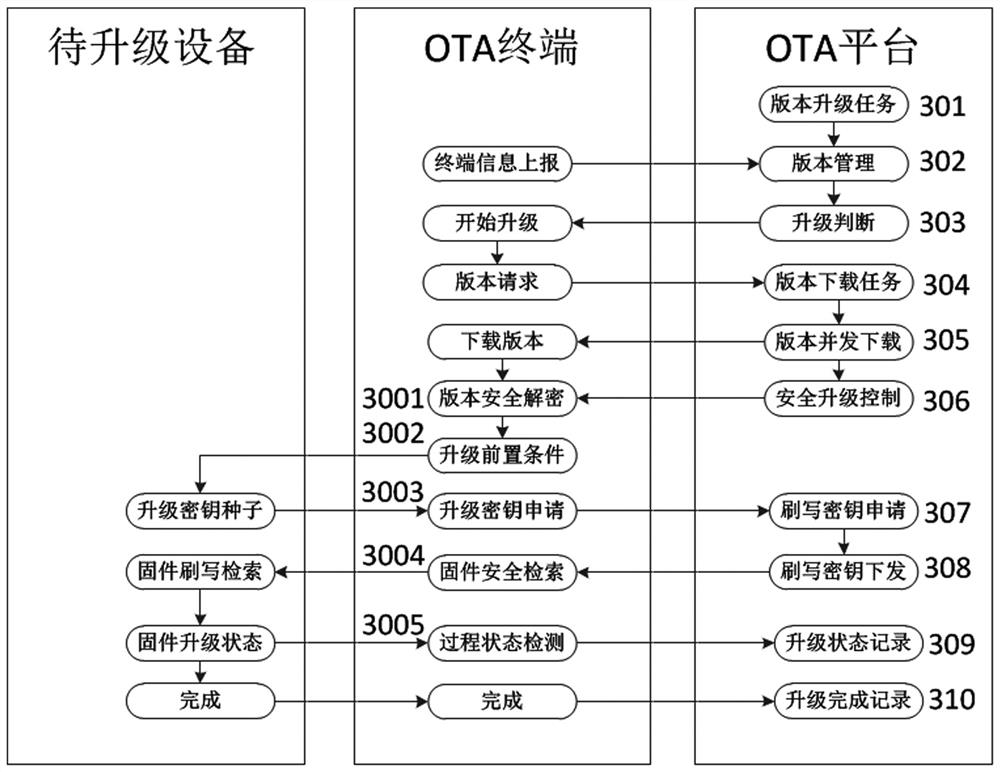
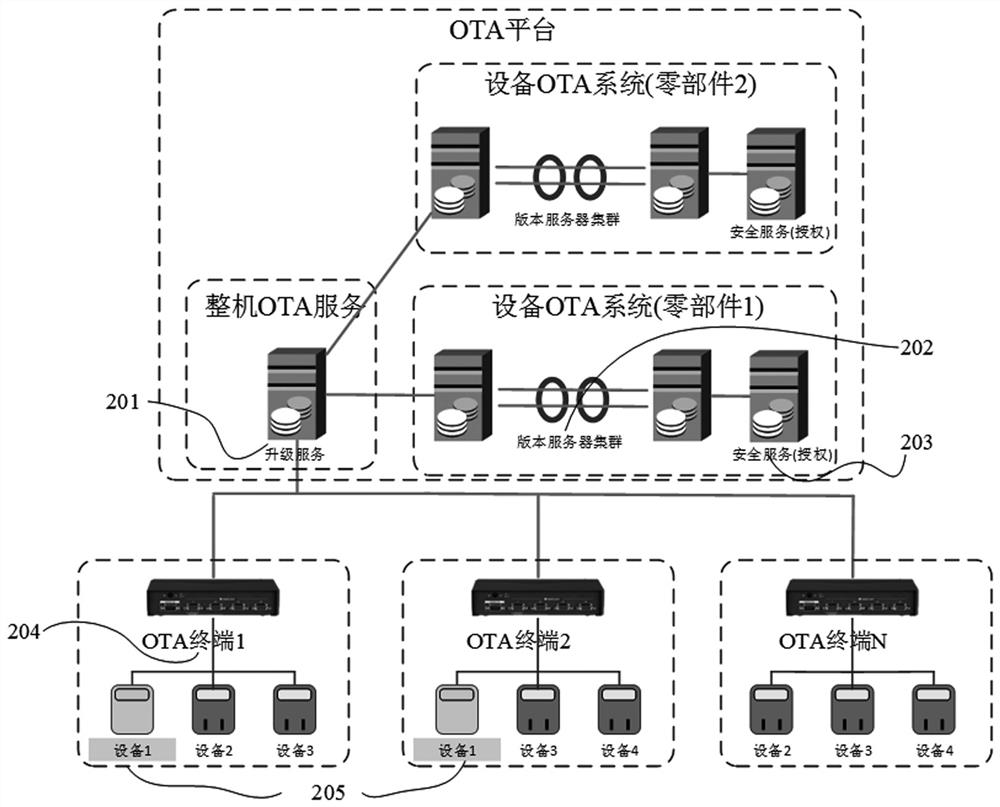
OTA security upgrading system and upgrading method thereof
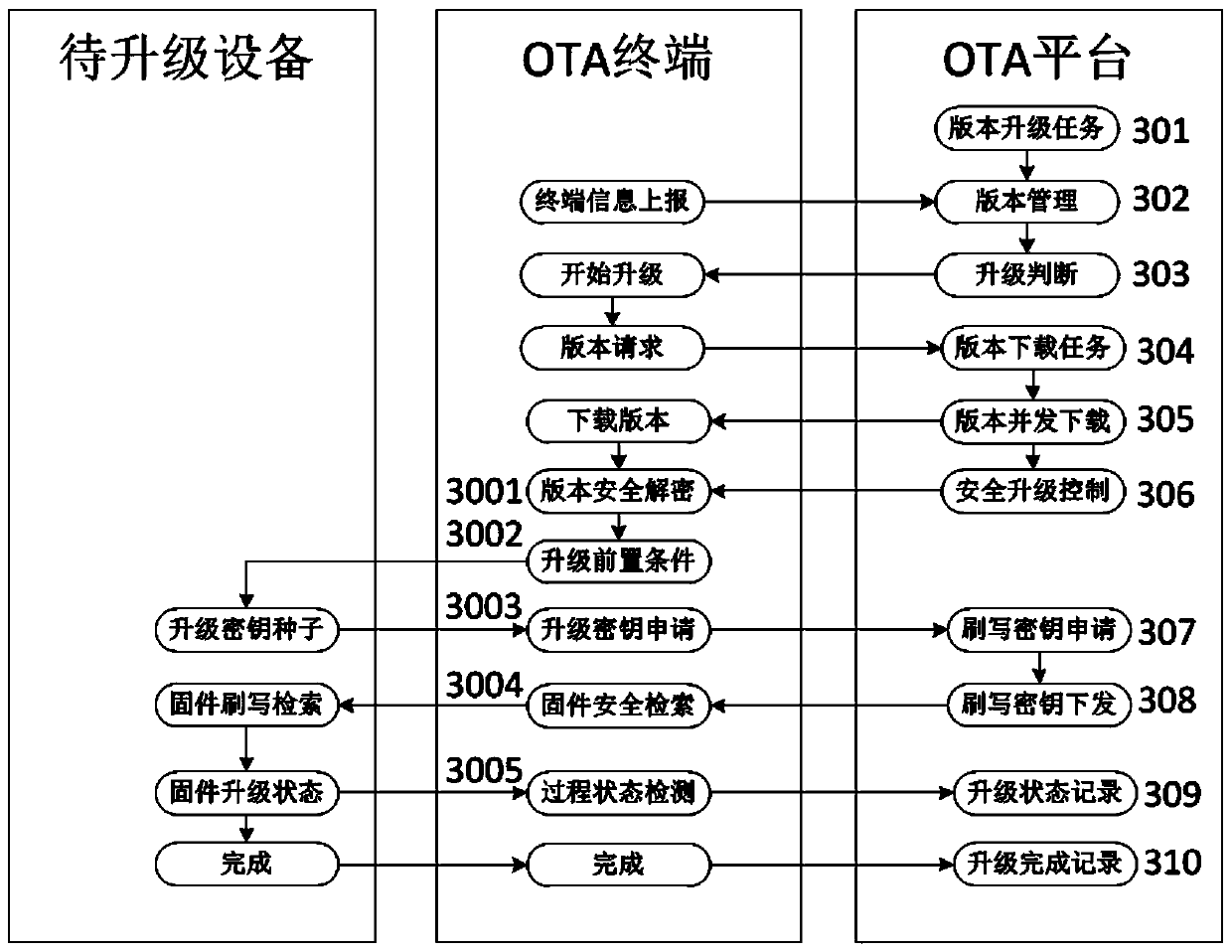
ActiveCN111562935AEnsure safetySecurity upgradeVersion controlDigital data protectionComputer scienceOperating system
The invention belongs to the technical field of communication, and particularly relates to an OTA security upgrading system and method. The OTA platform upgrading method comprises an OTA platform upgrading method and an OTA terminal upgrading method. The OTA platform upgrading method comprises security upgrading management, security version management, version downloading management and security control. The OTA terminal upgrading method is matched with an OTA platform function. Corresponding upgrade version file secret key acquisition and processing, upgrade precondition judgment and preorderoperation, safety secret key request management and upgrade process state detection rule functions are provided for upgrading of each intelligent part device, and the OTA terminal integrates and manages upgrade operation of a plurality of intelligent parts. Through standardized equipment upgrading process management, OTA safety upgrading of multiple types of intelligent parts is achieved for a large complete equipment integration party, the requirements for privacy and safety of upgrading of various intelligent parts are met, and the upgrading safety and stability are effectively improved.
Owner:江苏海平面数据科技有限公司
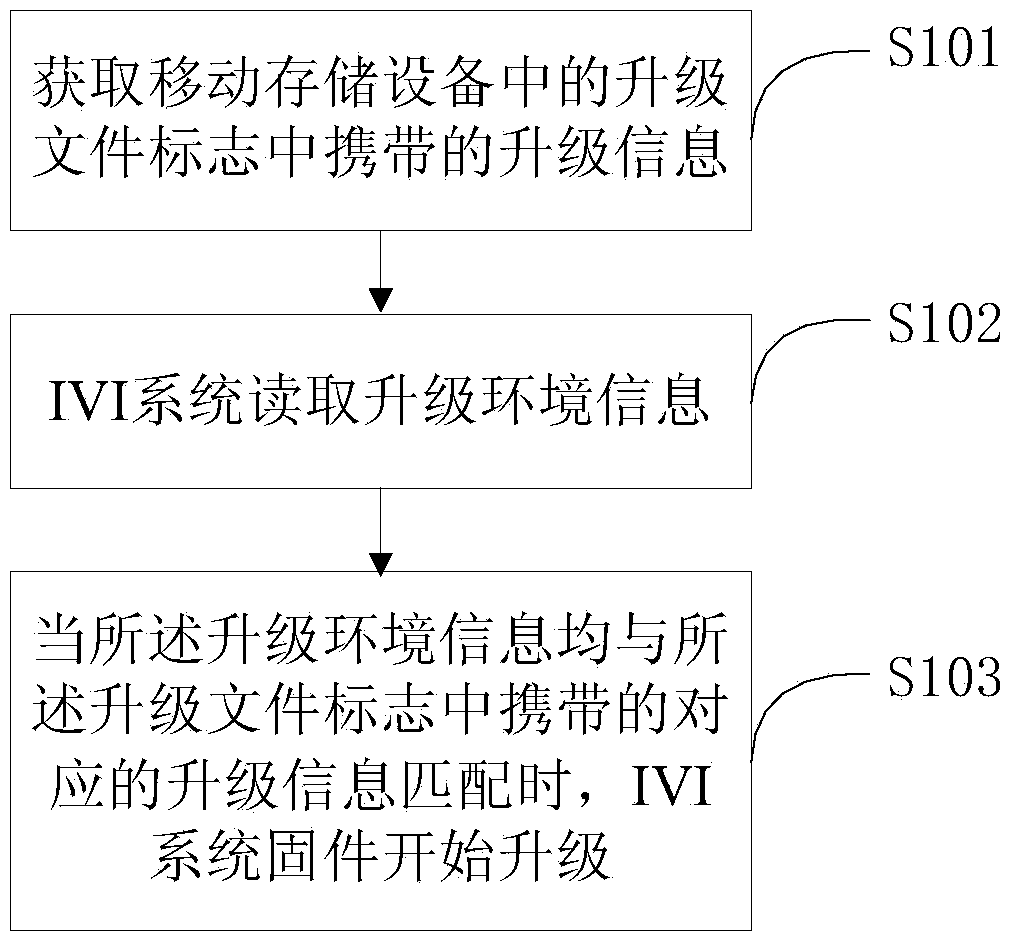
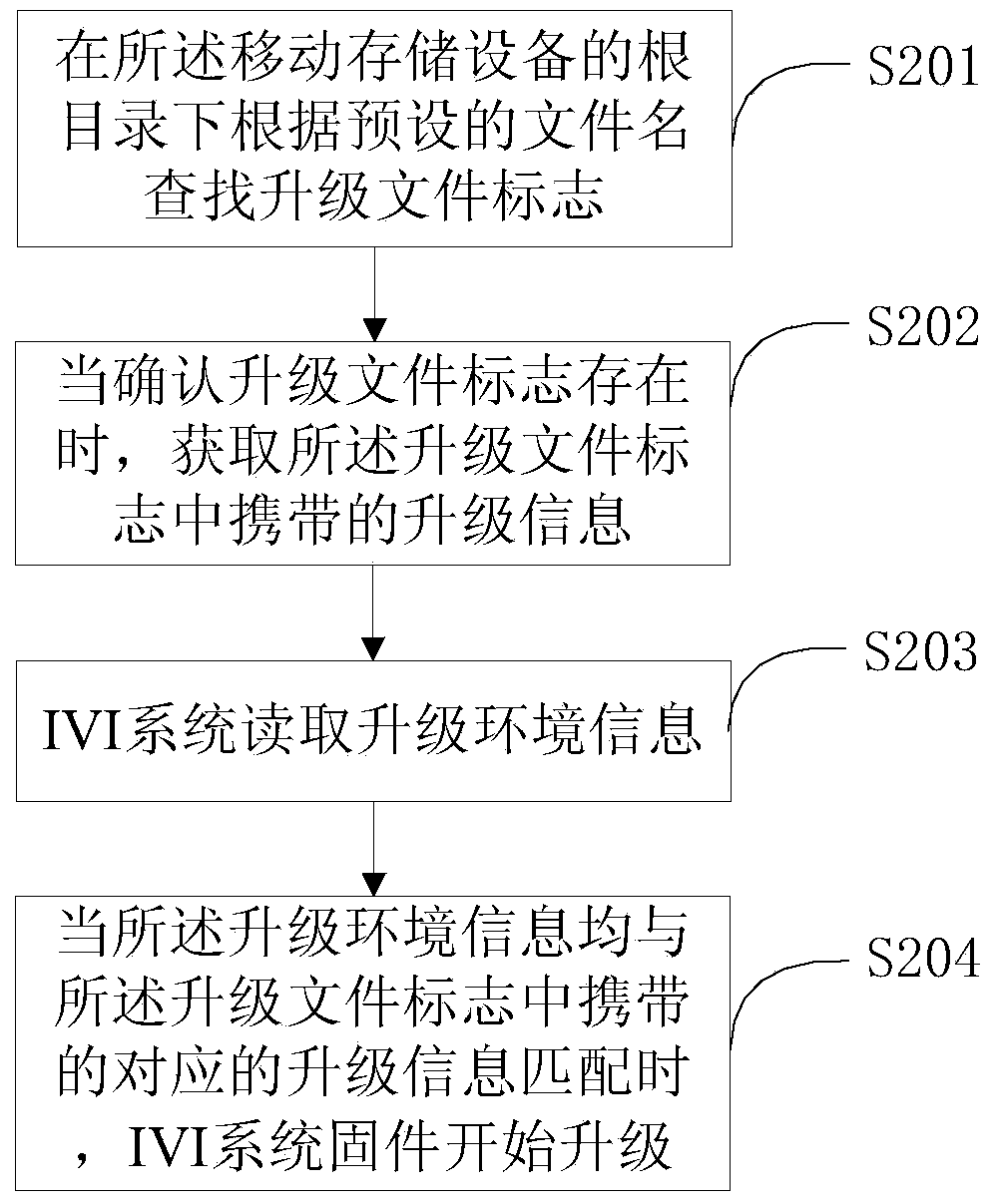
IVI system firmware updating method and device based on mobile storage equipment
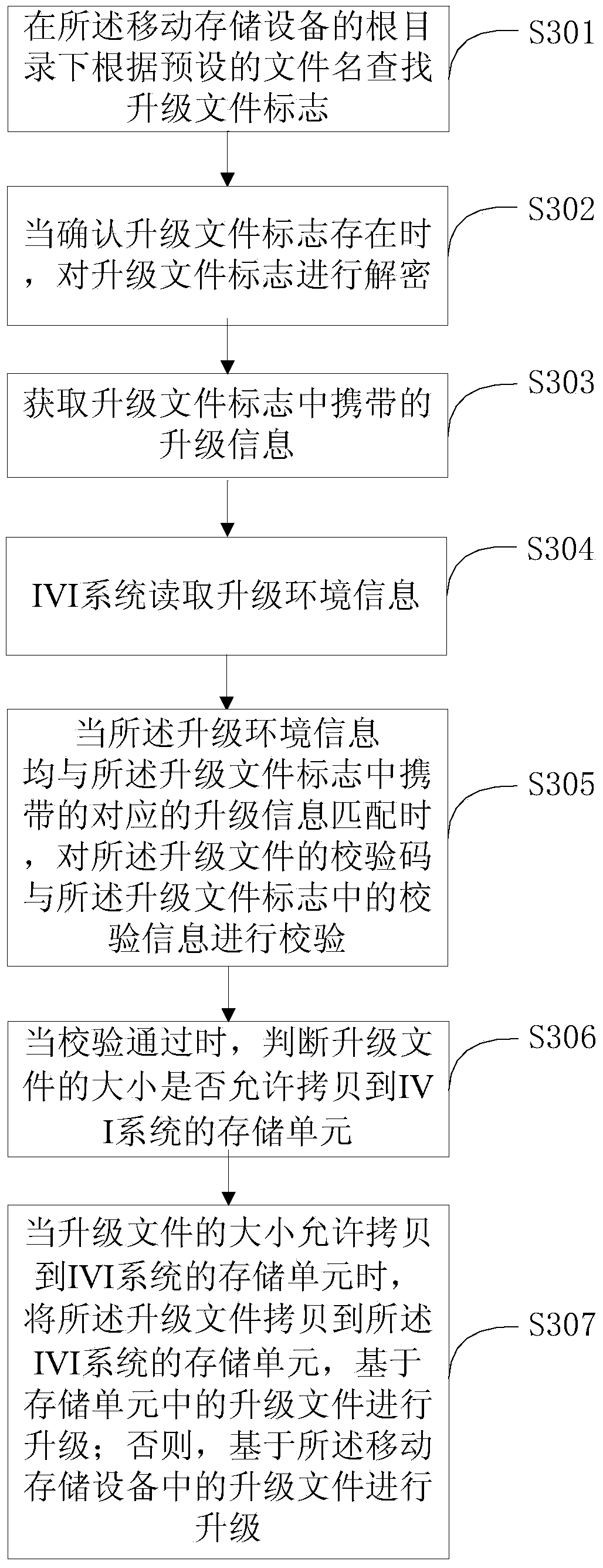
ActiveCN103995723AThe upgrade source and upgrade purpose are accurateGuaranteed checkSoftware engineeringProgram loading/initiatingControllabilityRemovable media
The invention discloses an IVI system firmware updating method and device based on mobile storage equipment. The method comprises the steps that updating information carried in an updating file mark in the mobile storage equipment is obtained; an IVI system reads updating environment information which comprises the serial number of the mobile storage equipment, the file list of updating files in the mobile storage equipment and the UUID of the IVI system; and when the updating environment information and the corresponding updating information carried in the updating file mark are matched, IVI system firmware updating is started. The updating file mark is set, related updating information of the UUID of the IVI system, the file list and the serial number of the mobile storage equipment is recorded in the updating file mark, when the read updating environment information and the recorded updating information are matched, updating is started, full-course information verifying during a whole updating process is guaranteed, controllability and safety of the whole updating process are guaranteed, and an updating source and an updating purpose are accurate.
Owner:FORYOU GENERAL ELECTRONICS
Intelligent infant anti-theft system based on IOT (Internet of Things)
The invention discloses an intelligent infant anti-theft system based on the IOT (Internet of Things), and the system comprises a mobile terminal, a communication gateway device, a signal receiver, a signal repeater, a long distance reader, a wrist ring, a wristband, a temperature sensing probe, an infrared detector, a heart rate sensor, a wrist ring body, a battery unit, a wrist buckle, a display, an electronic tag, an access controller, an audio device, a touch screen, an exit monitor, a management server, an alarm device and a camera. According to the invention, a signal receiving device and the exit monitor are installed in a monitoring area of a hospital, and an electronic tag which can emit a radio frequency signal and causes no harm to the human body is installed on a baby, thereby achieving the safety monitoring function. The signal receiving device can receive the signals emitted by the electronic tag on the baby at any time so that the state of the baby can be judged according to the signals, thereby achieving the timely alarm against the behavior of trying to steal the baby, and tracking the signals. Moreover, the system senses whether the wrist ring is taken down through an infrared induction probe. Once the wrist ring is detected to be separated from a wrist, the system can directly give an alarm for prompt.
Owner:刘哲
Method and device for BMC (Baseboard Management Controller) with external upgrading
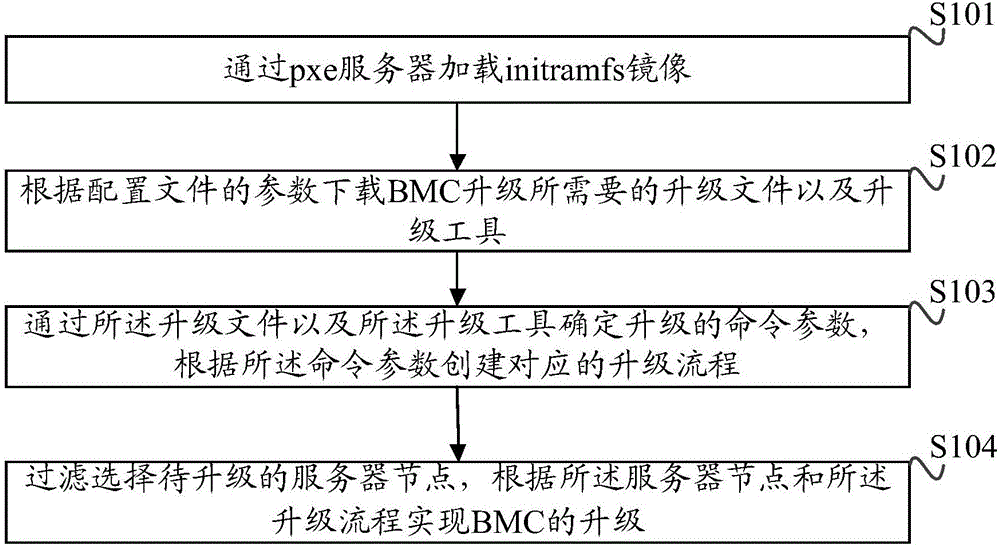
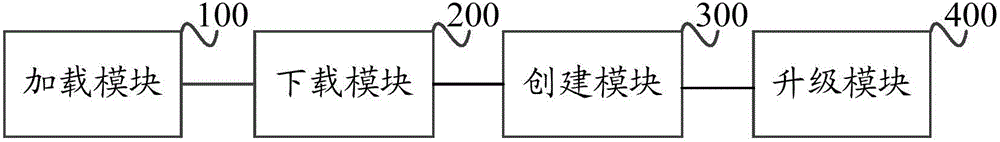
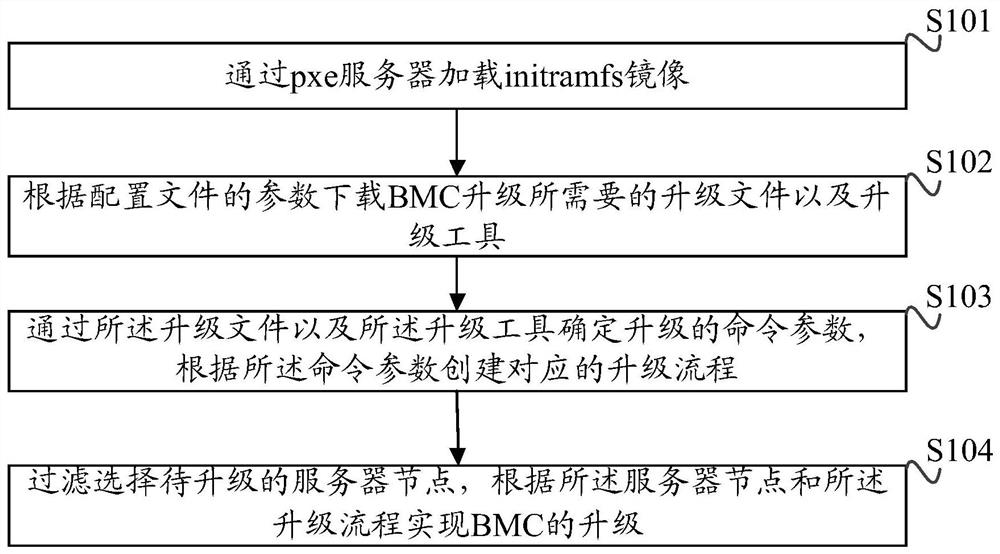
ActiveCN106445580AQuick upgradeSecurity upgradeProgram loading/initiatingSoftware engineeringMirror image
The invention discloses a method and a device for a BMC (Baseboard Management Controller) with external upgrading. The method comprises the steps of: loading an initramfs mirror image through a pxe server; downloading an upgrading file and an upgrading tool needed for upgrading of the BMC according to parameters of a configuration file; determining a command parameter for upgrading through the upgrading file and the upgrading tool, and establishing a corresponding upgrading process according to the command parameter; and filtering and selecting a to-be-upgraded server node, and realizing the upgrading of the BMC according to the server node and the upgrading process. According to the method and the device for the BMC with external upgrading provided by the invention, the upgrading of the BMC can be rapidly and safely realized in batches. Through batch upgrading of the BMC, an error caused by manual operation is avoided and the reliability of the upgrading of the BMC is improved.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
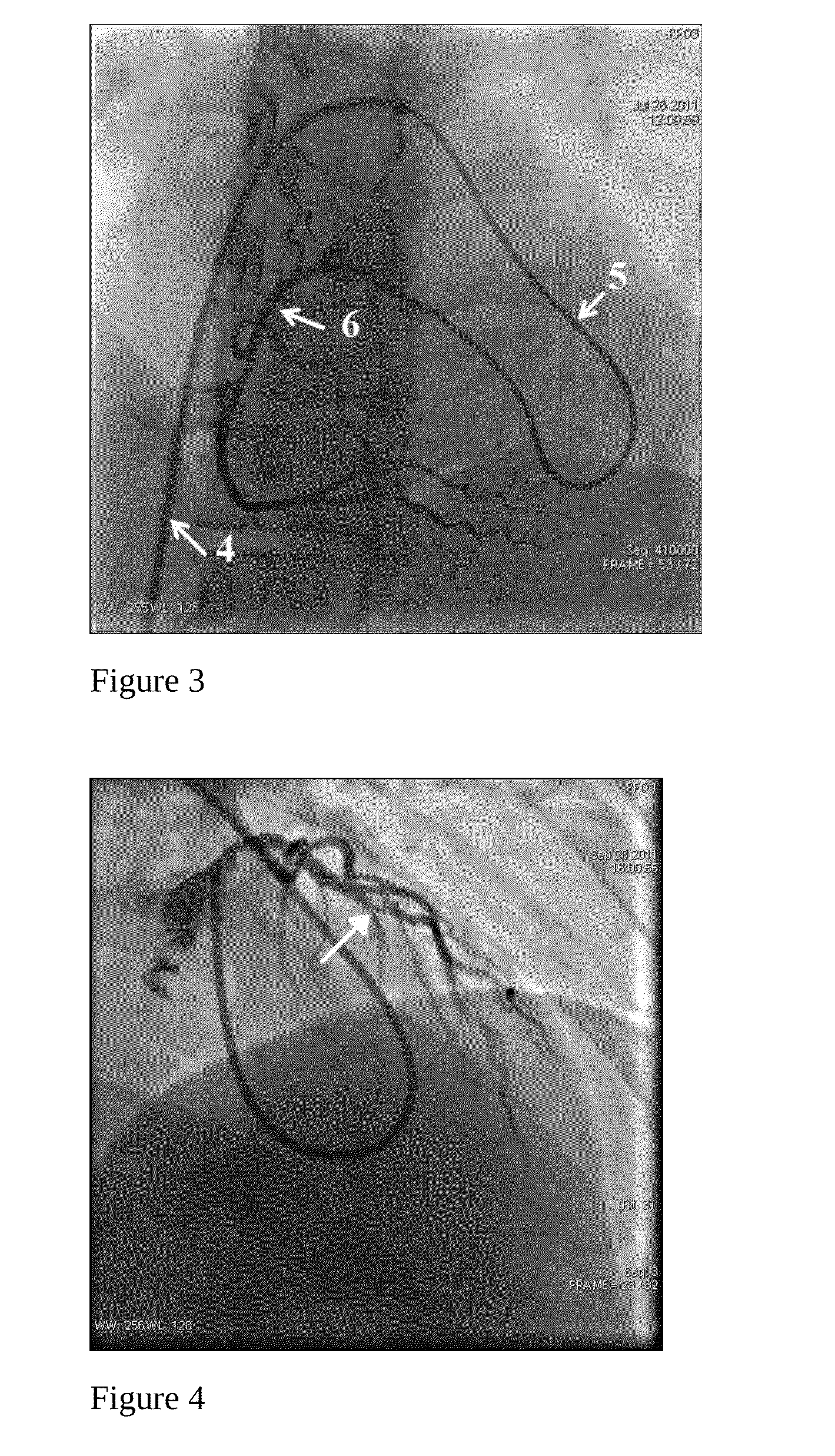
Method for the catheterization of the coronary arteries and catheter for the implementation thereof
InactiveUS20150273136A1Improve processing efficiencySecurity upgradeMedical devicesCatheterAscending aortaCoronary arteries
What is proposed is a method for the catheterization of the coronary arteries in which a catheter is introduced via the venous system into the right atrium, then passed through the interatrial septum and introduced into the left atrium, followed by the left ventricle, and into the ascending aorta to the opening of the coronary arteries, and also a catheter for the implementation of this method.
Owner:OSIEV ALEKSANDR GRIGORIEVITCH
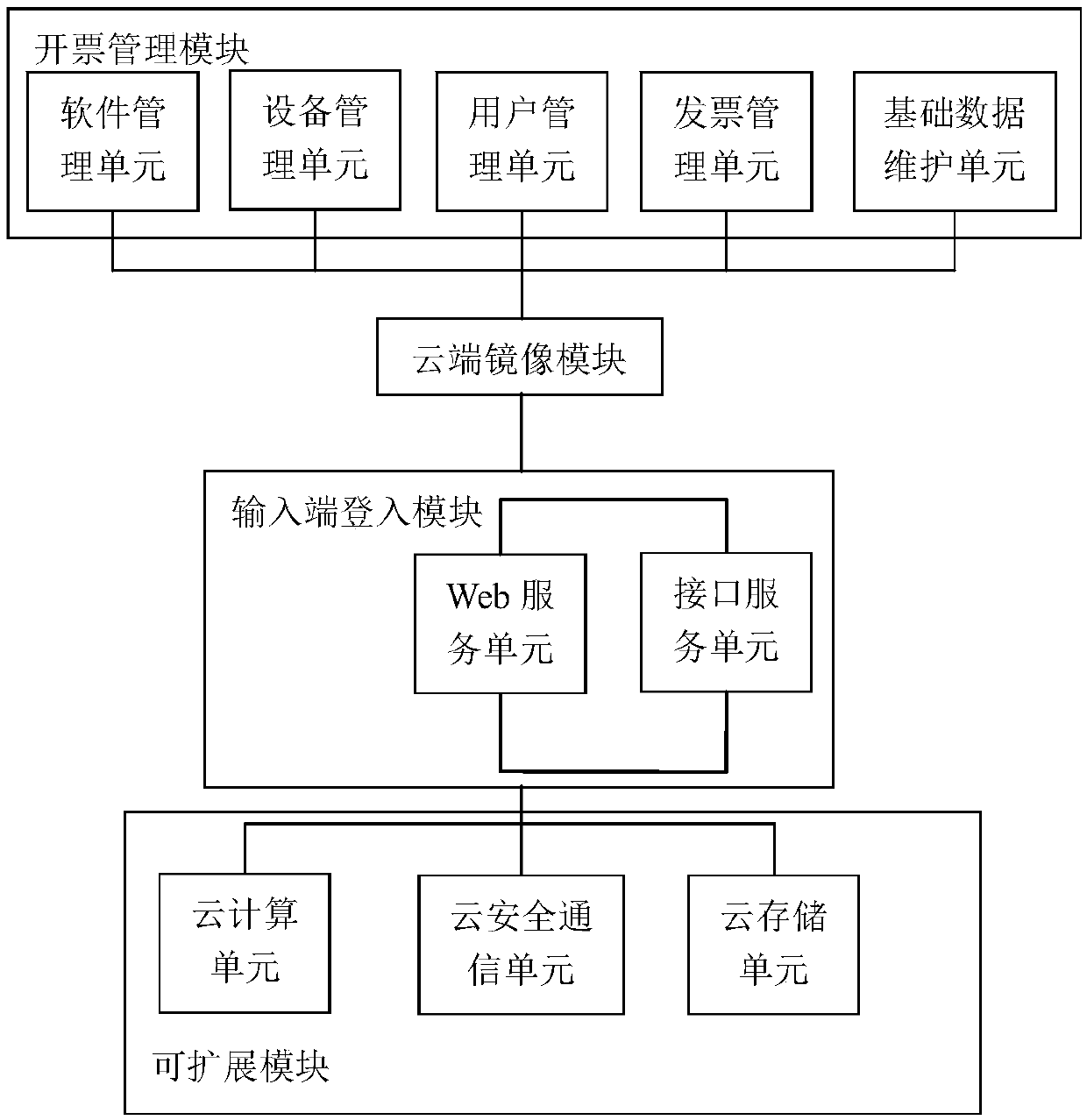
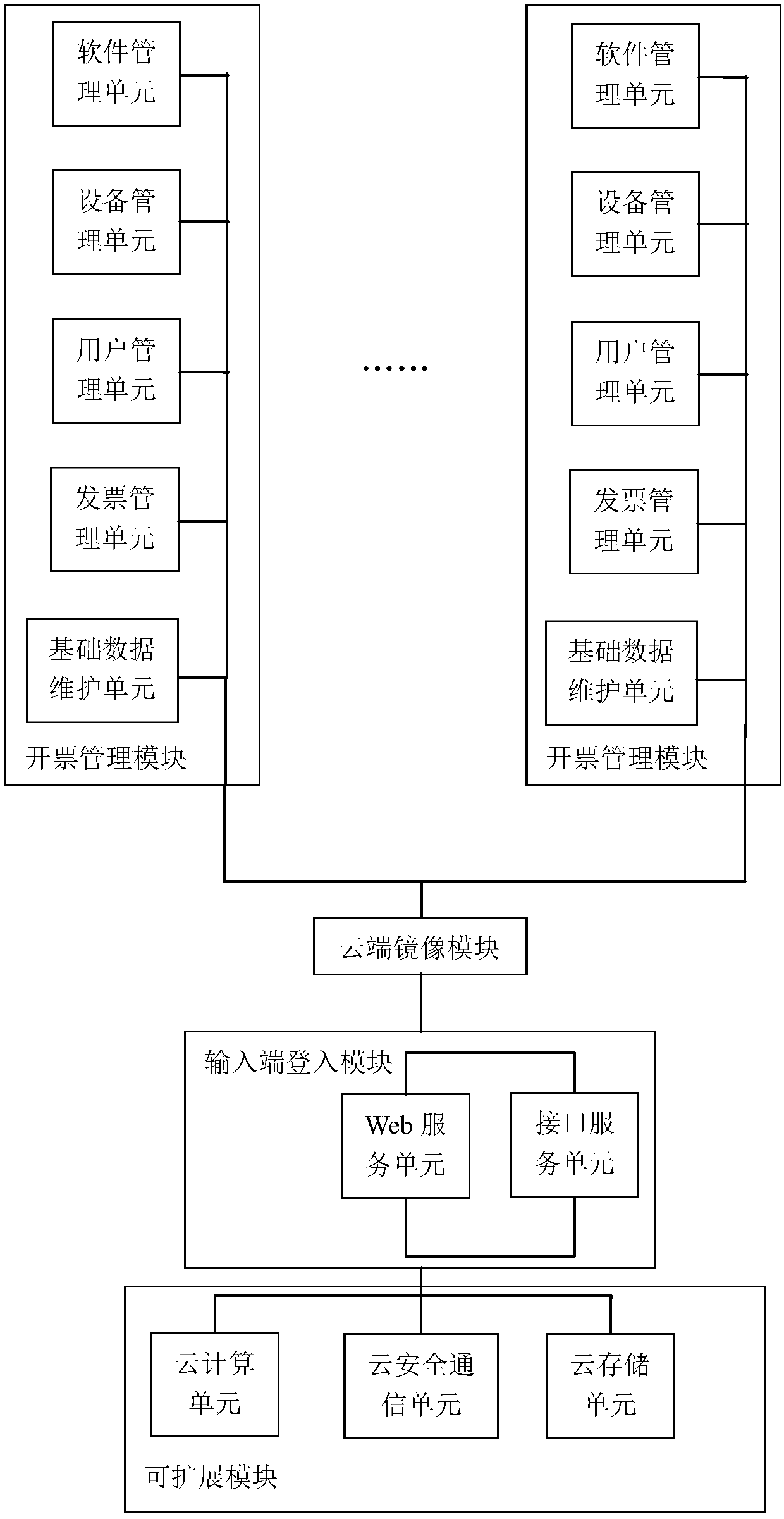
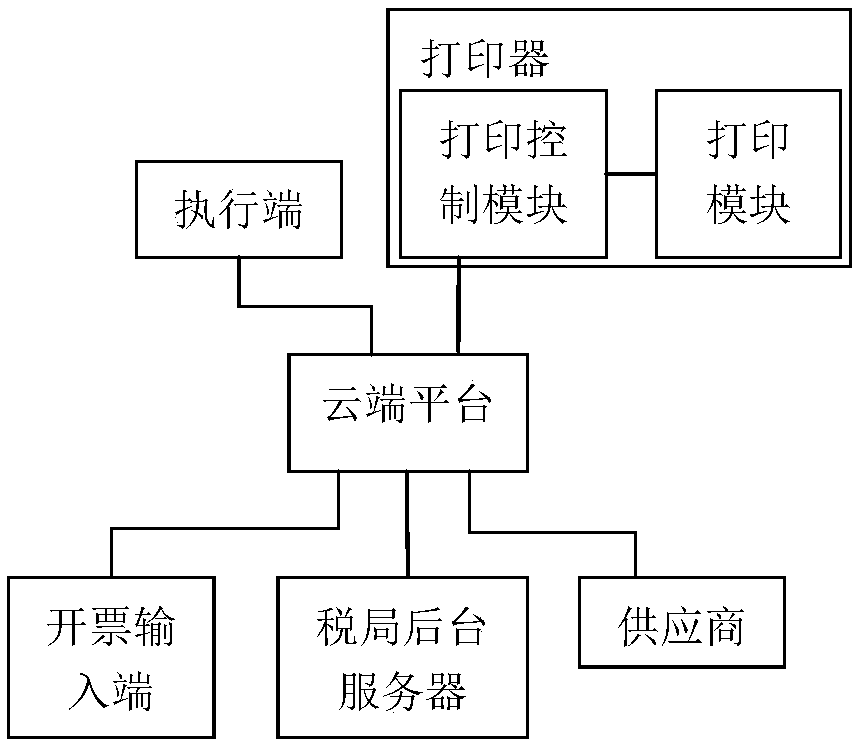
Cloud platform for billing, cloud system for billing, and cloud billing method
InactiveCN107818485AEasy accessRealize remote billingBilling/invoicingBuying/selling/leasing transactionsInvoice
The present invention relates to a cloud platform for billing, a cloud system for billing, and a cloud billing method. The cloud platform comprises: a billing management module configured to receive login account registration information, establish a login account, perform matching and binding of the login account and an execution terminal, open an authority for the login account having matched and bound with the execution terminal to receive the login account and audit the authority of the login account, inquire and connect with the execution terminal bound with the login account after the auditing passes for receiving billing information and sending the billing information to the execution terminal and for receiving electronic invoice data and performing feedback of the electronic invoice data to the login account for the login account to inquire and print; and a cloud mirror image module configured to receive login account registration information input by an input terminal, the login account and billing information input by the input terminal and send the login account registration information input by the input terminal, the login account and billing information input by the input terminal to the billing management module.
Owner:百望金赋科技有限公司
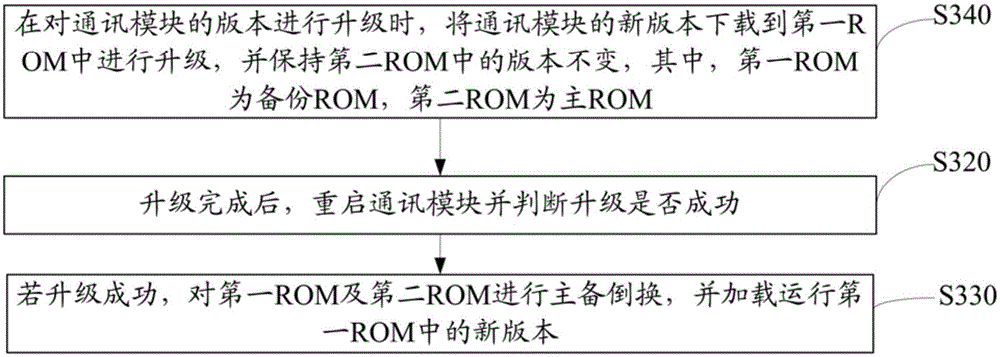
Communication module upgrading method and communication module upgrading device
InactiveCN105049633ASecurity upgradeReduce maintenance costsSubstation equipmentProgram loading/initiatingRead-only memory
The invention discloses a communication module upgrading method and a communication module upgrading device, belonging to the technical field of communication. The method process comprises the following steps of: while upgrading version of a communication module, downloading a new version of the communication module to a first ROM (Read Only Memory) for upgrading, and keeping the version in a second ROM unchanged, wherein the first ROM is a standby ROM, and the second ROM is a main ROM; after finishing upgrading, resetting the communication module and judging whether upgrading is successful; if upgrading is successful, performing main-standby switch on the first ROM and the second ROM, and loading and running the new version in the first ROM. With the method and the device, even if upgrading is failed or upgrading failure happens during the upgrading process for the reason of emergencies, such as power failure, the communication module can be recovered to the original version, and failure of upgrading cannot cause failure of the communication module.
Owner:高新兴物联科技股份有限公司
Method, system and equipment for enhancing MQTT protocol identity authentication by using symmetric cryptographic technology
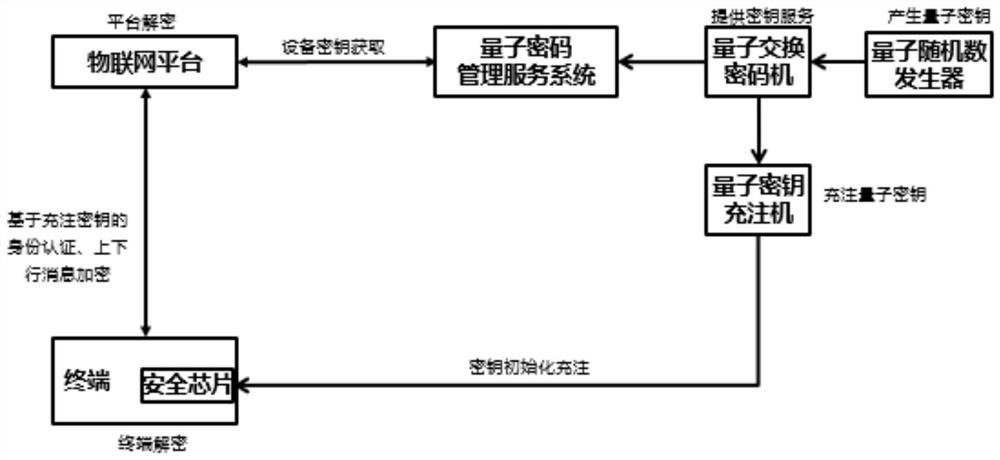
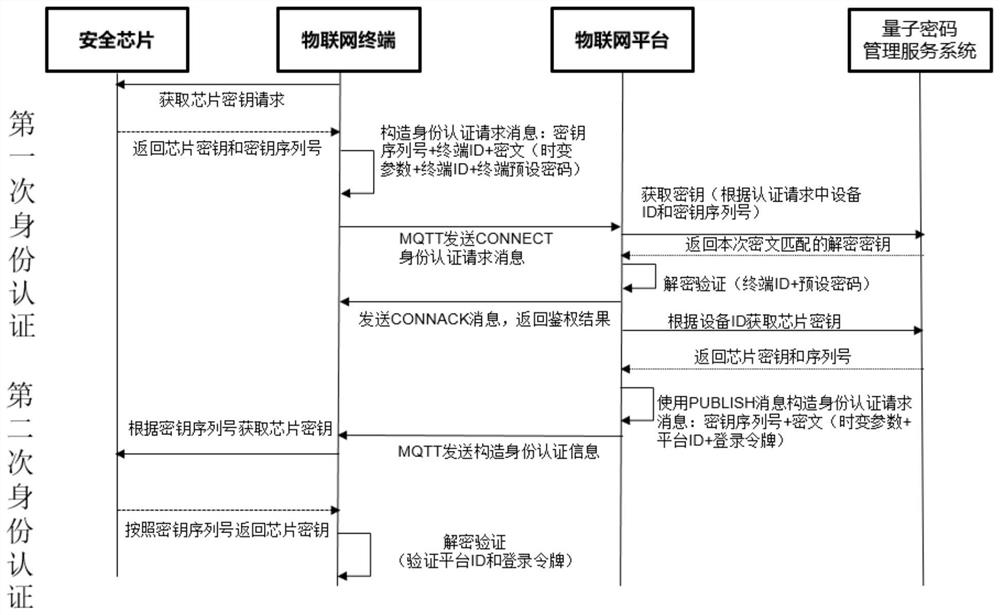
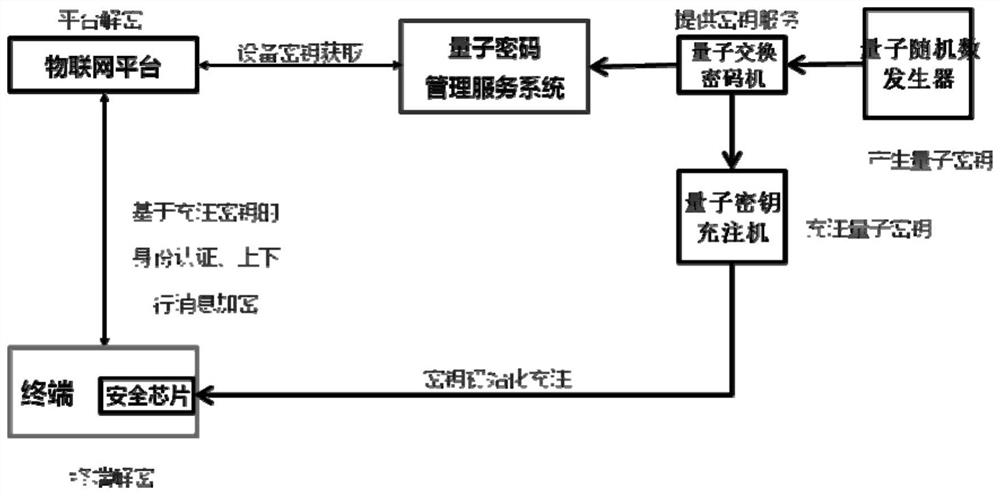
PendingCN113612605AImprove safety performanceReduce the risk of tripartite agreementsKey distribution for secure communicationUser identity/authority verificationProtocol for Carrying Authentication for Network AccessThird party
The invention provides a method for enhancing MQTT protocol identity authentication by using a symmetric cryptographic technology, which comprises the following steps of: performing first identity authentication from an Internet of Things terminal to an Internet of Things platform: charging a quantum key into a quantum safety chip by a quantum key charging machine, and recording and storing a corresponding relationship between the charging safety chip and the key, the Internet of Things terminal calls a quantum key in a chip to construct an identity authentication request message to the Internet of Things platform, the Internet of Things platform obtains symmetry, carries out decryption and identity comparison, generates a login token after successful authentication, and returns a verification message to the terminal; second identity authentication: the Internet of Things platform applies for a key according to the terminal ID and constructs an identity authentication request message to the terminal; and the terminal decrypts and verifies the platform ID and the login token. The invention further provides a system and equipment corresponding to the method. The invention has the advantages that identity authentication is performed by using a key set symmetric algorithm in the quantum safety chip, one key is pad at a time, a third party does not need to issue and authenticate a digital certificate. Therefore, the safety is improved.
Owner:中电信量子科技有限公司
High-reliability upgrading method of unmanned system
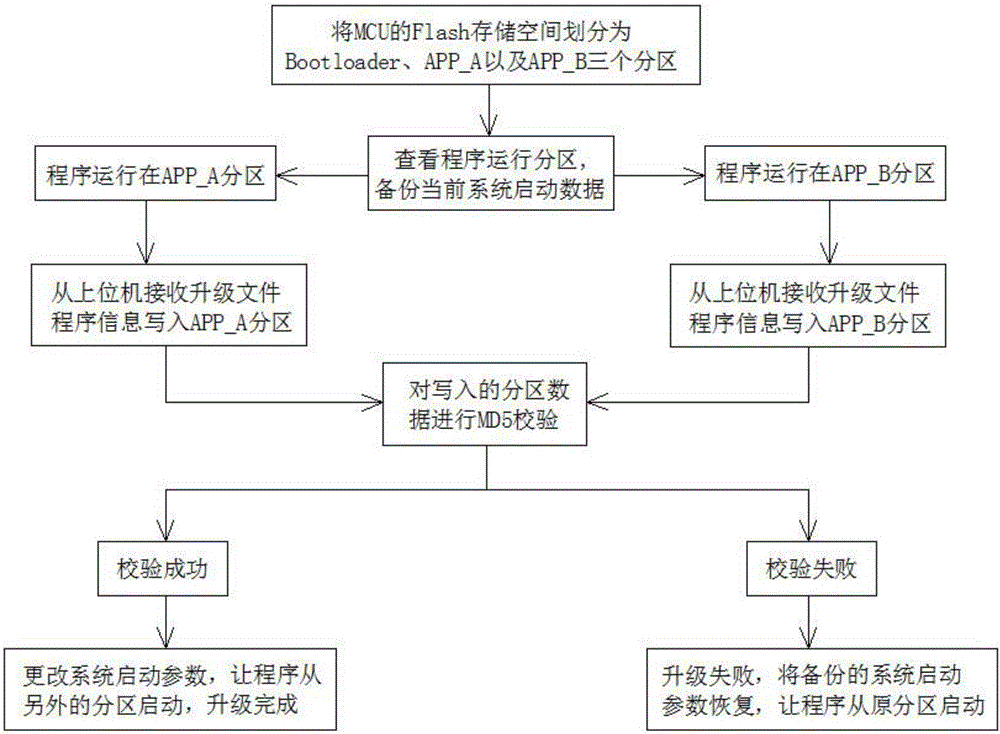
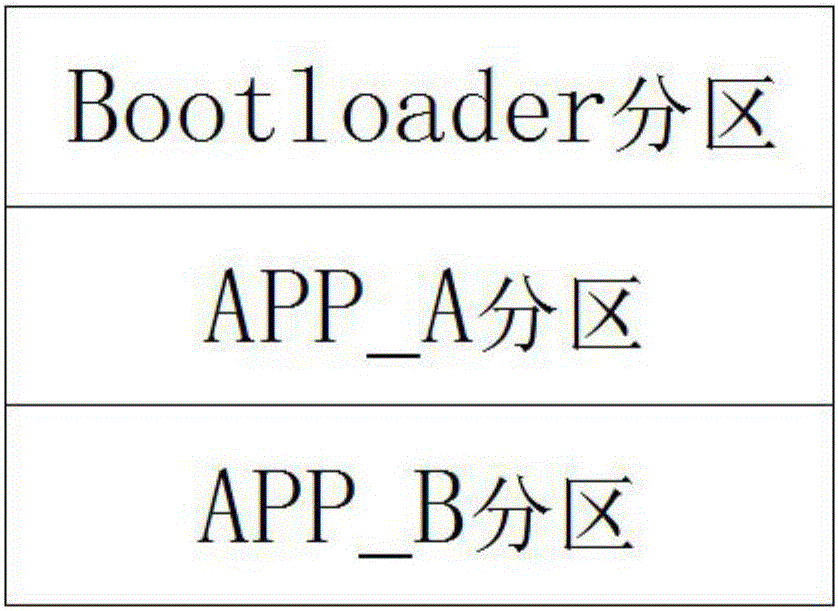
InactiveCN107436778ASecurity upgradeSafe and reliable upgradeSoftware engineeringProgram loading/initiatingData integritySystem failure
The invention discloses a high-reliability upgrading method of an unmanned system. By adopting the storage space inside an MCU, the three-partition mode is adopted, the system is divided into three portions including one BootLoader partition and two function partitions, upgrading is performed in different partitions, new partitioning data is written in, the partition safety is ensured, MD5 checking is performed after data is written into the novel partition, the partition data writing integrity is ensured, upgrading of the unmanned system is safer and reliable, and absolute upgrading safety is achieved truly, system failure under various abnormal conditions is avoided, and the functions of changing an upgrading protocol and achieving upgrading can be achieved.
Owner:安徽科微智能科技有限公司
Firmware upgrading method, device and computer readable storage medium
PendingCN112346759ASecurity upgradeImprove securityDigital data protectionProgram/content distribution protectionComputer engineeringUpgrade
Owner:SHENZHEN GONGJIN ELECTRONICS CO LTD
Remote dynamic upgrading method and method for embedded software of power system
ActiveCN108196873ASecurity upgradeReliable upgradeSoftware engineeringElectric power systemSoftware engineering
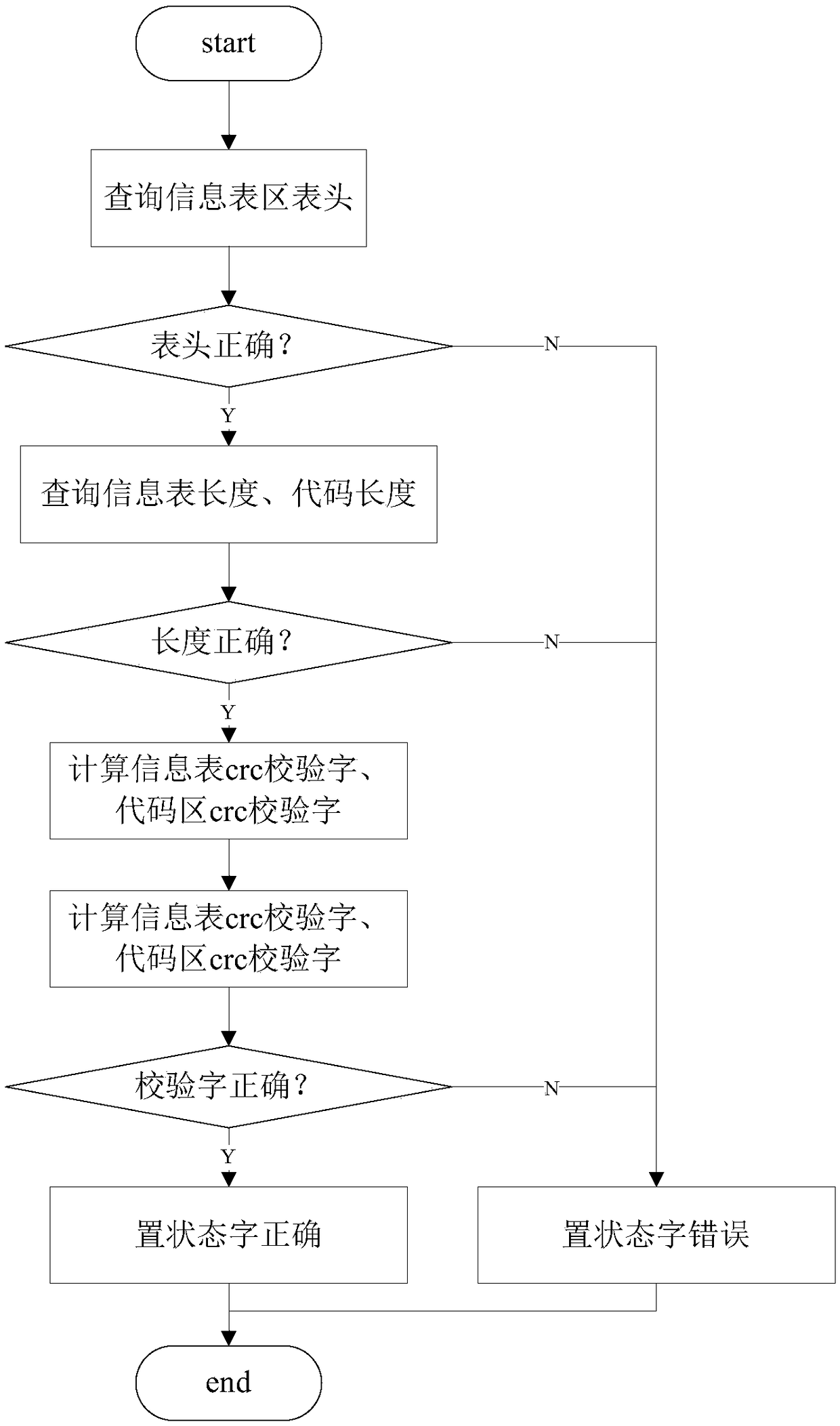
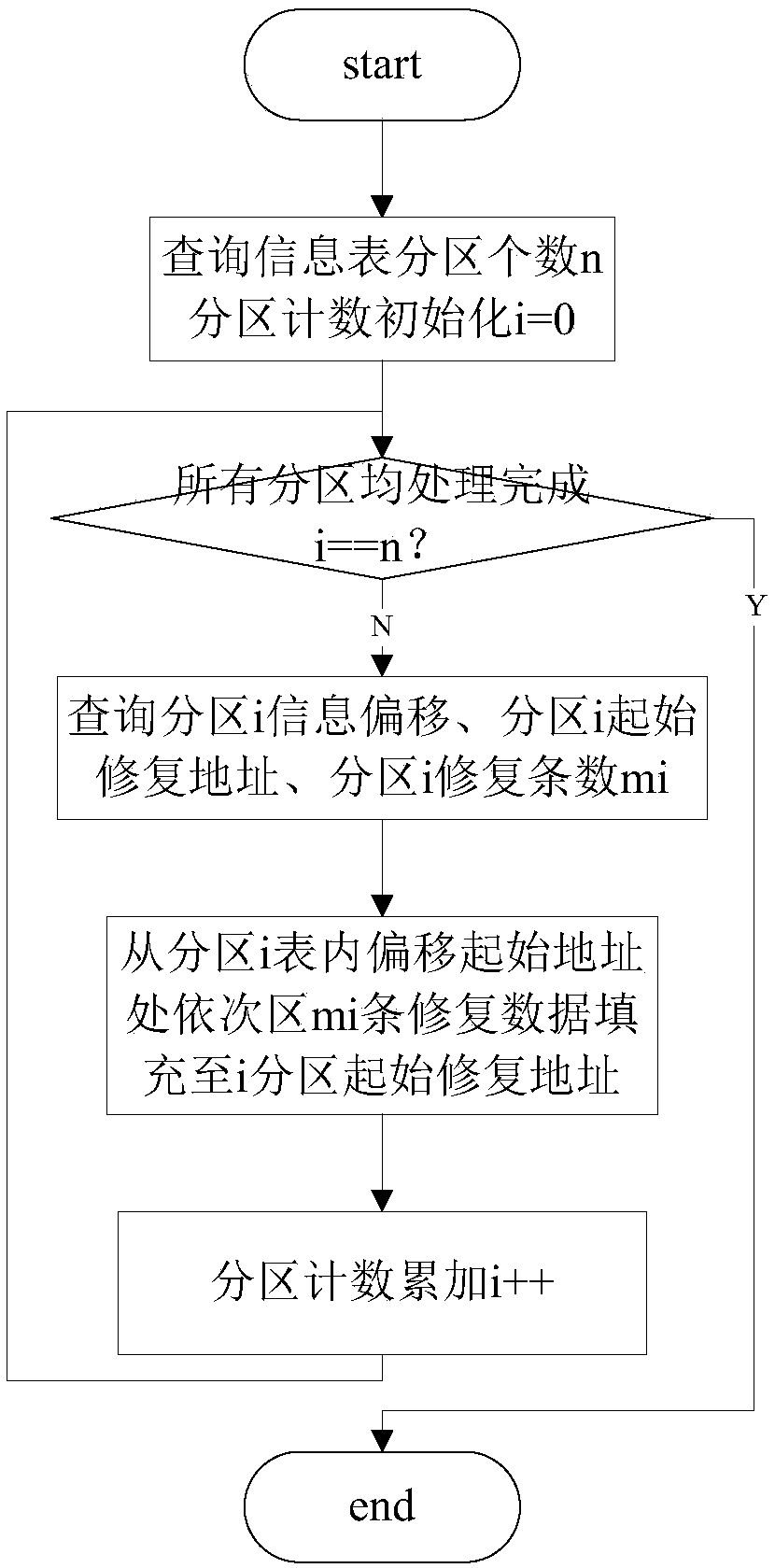
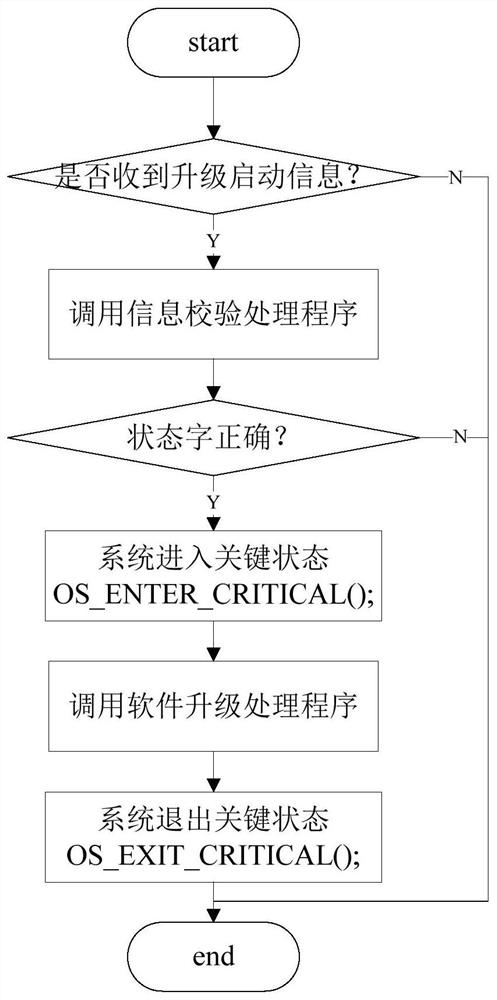
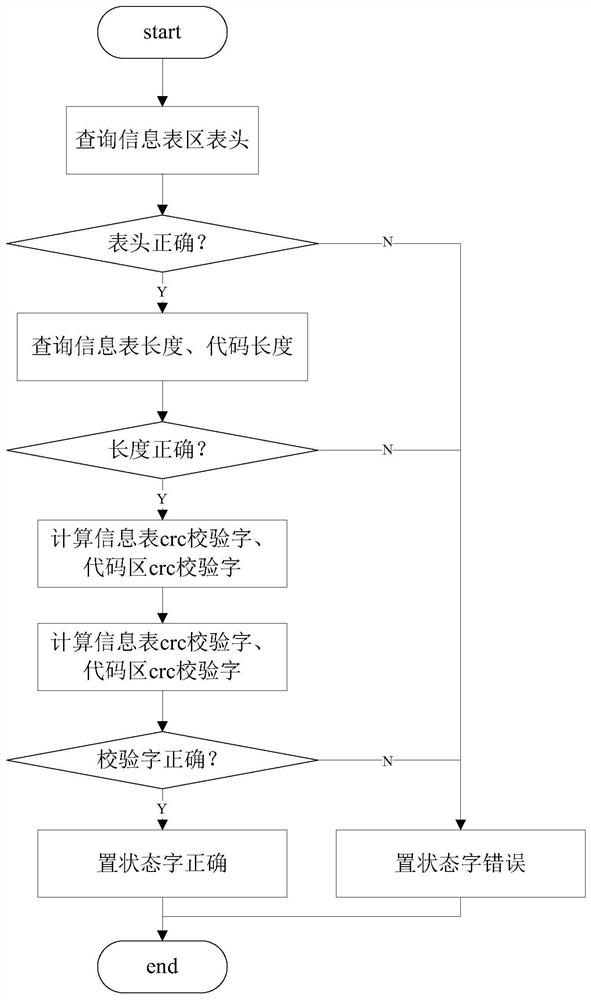
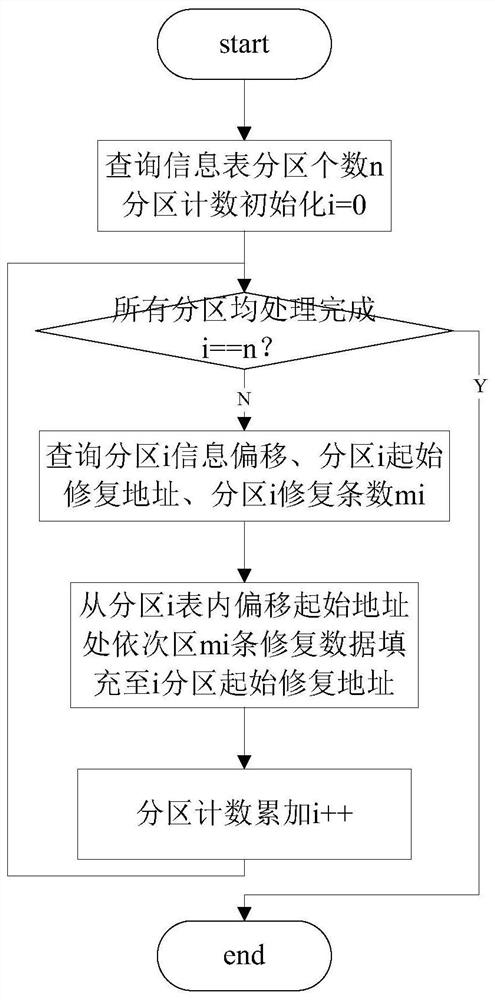
The invention discloses a remote dynamic upgrading method and method for embedded software of a power system. The method comprises the steps of remotely loading a software upgrade information table and a software upgrade code to the power system's equipment node to be upgraded; when an 'idle' task runs in the equipment node (all system tasks are idle), performing information check on the softwareupgrade information table, and executing dynamic software upgrading if the information check shows a positive result. Through information check and interruption control, a software upgrading process of good safety and reliable is guaranteed.
Owner:SHANDONG UNIV OF SCI & TECH
Cross-communication protocol data forwarding network communication system, method and device thereof
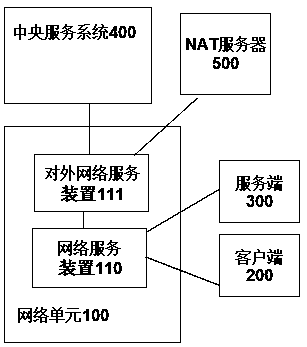
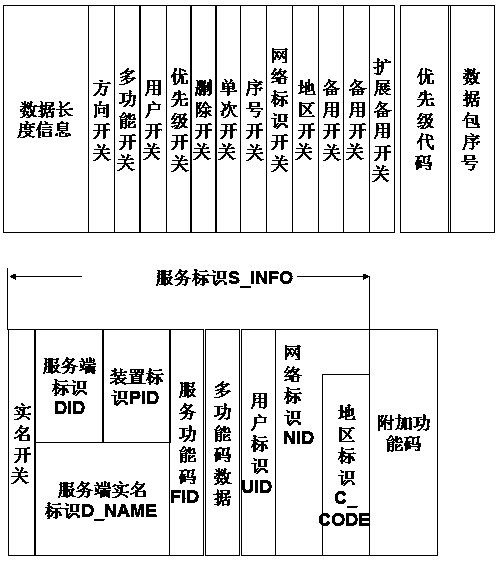
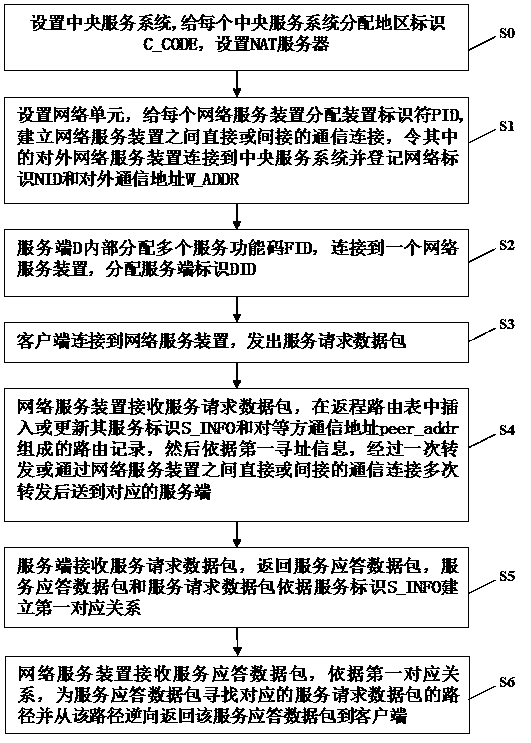
PendingCN111464573ARealization of communication capabilitiesGuaranteed communication performanceTransmissionHigh level techniquesTelecommunicationsServer-side
The invention relates to a cross-communication protocol data forwarding network communication system, a method and a device thereof. A service identifier S_INFO in a service request data packet sent to a server side by a client side through a network service device comprises at least one of first addressing information of the server side and a plurality of service function codes FIDs provided in the server side; one or more network service devices forward the service request data packet to the server for the client; and a first corresponding relation is established between the service responsedata packet responded by the server and the service request data packet according to the service identifier S_INFO, and according to the first corresponding relation, the network service device searches a path of the corresponding service request data packet for the service response data packet to return the service response data packet to the client. The system provided by the invention can spana plurality of countries and regions to deploy network units of ten billion orders of magnitudes to form a complete system, so that any two endpoints in the system have a communication capability.
Owner:胡俊喜
Method and system for enhancing MQTT protocol transmission security by using symmetric cryptographic technology
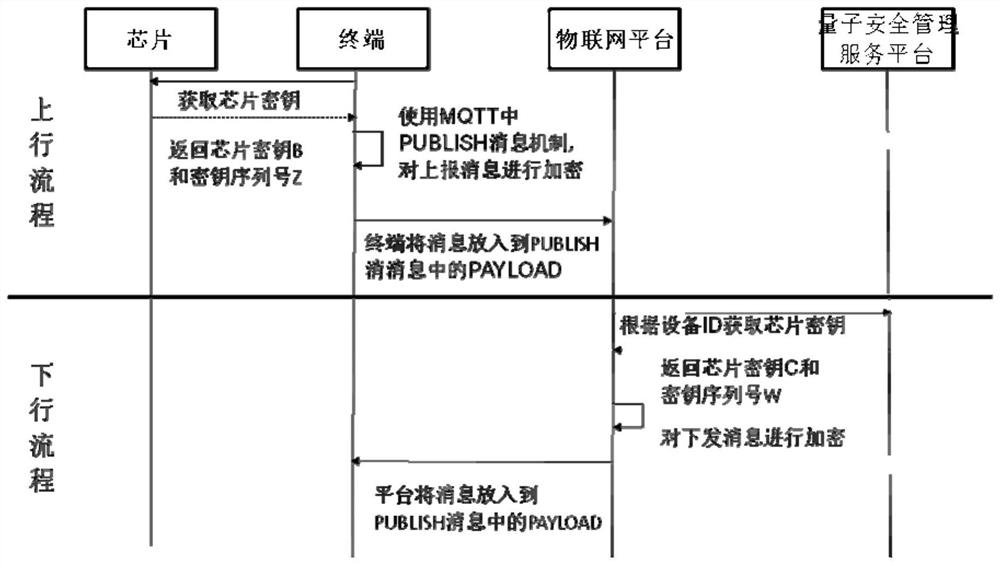
ActiveCN113630407AAvoid security impactSolve authentication problemsKey distribution for secure communicationUser identity/authority verificationProtocol for Carrying Authentication for Network AccessEngineering
The invention provides a method for enhancing MQTT protocol transmission security by using a symmetric cryptographic technology, and the method comprises the steps: carrying out the encryption and decryption of data: carrying out the encryption and decryption from an Internet of Things terminal to an Internet of Things platform, and carrying out the encryption and decryption from the Internet of Things platform to the Internet of Things terminal; in encryption and decryption, employing a quantum key filling machine for filling a symmetric key of a quantum security chip arranged in or outside the Internet of Things terminal and a key stored in a quantum exchange cipher machine, and enabling the quantum exchange cipher machine to record and store a corresponding relation between the filled quantum security chip and the key. The method has the advantages that the quantum key is used for protecting uplink and downlink information of the MQTT, and the problems that the key is reused in the transmission process of uplink and downlink information of the Internet of Things terminal, and the security is reduced along with use are solved by using a quantum security chip and a symmetric cryptographic technology.
Owner:中电信量子科技有限公司
Embedded multi-system upgrading method based on Hypervisor and computer readable storage medium
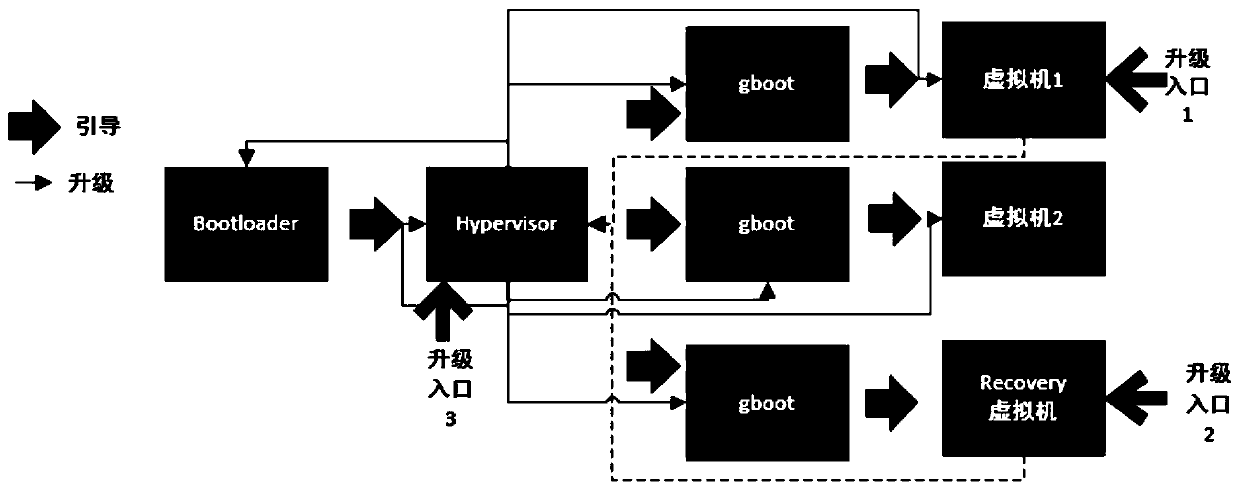
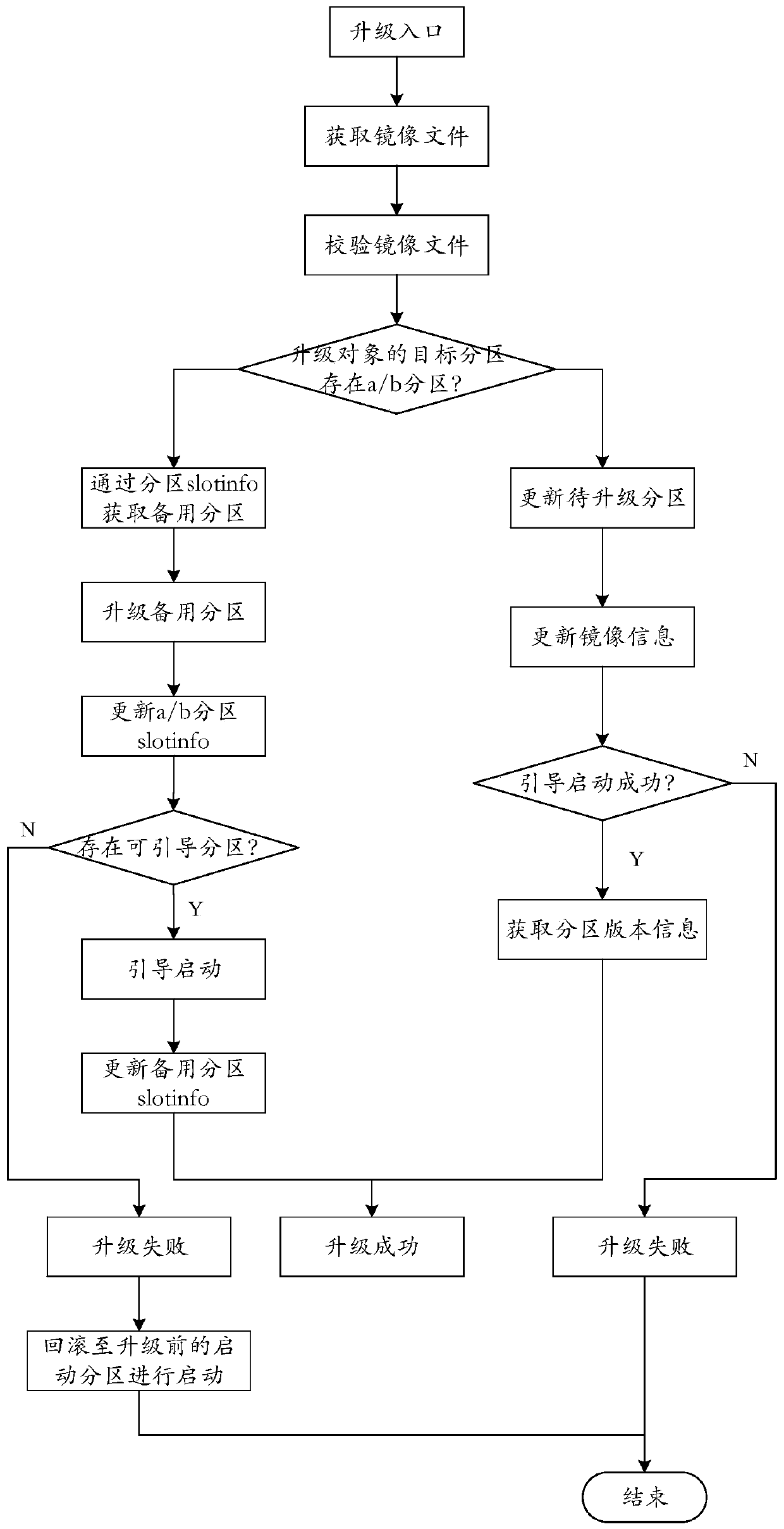
ActiveCN111522569ASecurity upgradeVersion controlSoftware simulation/interpretation/emulationSoftware engineeringMirror image
The invention relates to the technical field of computers. The invention specifically discloses an embedded multi-system upgrading method based on the Hypervisor. When the Hypervisor carries out upgrading operation on a target partition of an upgrading object, if the target partition has a standby partition, the mirror image file is written into the standby partition, and slot information of the standby partition is updated to be in a bootable state after verification succeeds; when the Hypervisor updates the mirror image file, the mirror image file is sent to the Hypervisor; the target partition is guided and started by the upgrading object; wherein if the standby partition exists in the target partition and the booting is successful, slot information of the target partition is in a successfully bootable state, and the booting fails, the booting continues to be tried, and when the number of tried booting times is zero, the effective booting partition before upgrading is rolled back tobe booted. Therefore, all the mirror images can be upgraded through the Hypervisor, and the target partition can be started by rolling back the effective starting partition before upgrading even if upgrading fails by configuring the backup partition, so that upgrading is safer.
Owner:中瓴智行(成都)科技有限公司
Vehicle rear bumper structure
The invention provides a vehicle rear bumper structure, which comprises a rear bumper main body, wherein the rear bumper main body is provided with a rear trailer cover plate, a left side lower wrap angle, a right side lower wrap angle, a left side welding support, a right welding support, a left side ventilating decoration bar, a right side ventilating decoration bar, an inner skeleton, a lower protection plate, a left side outer mounting support, a right side outer mounting support, a left side inner mounting support, a right side inner mounting support, a rear fog lamp left mounting support, a rear fog lamp right mounting support, a square tail pipe left mounting support, a square tail pipe right mounting support, a round tail pipe mounting support, a round tail pipe right mounting support and a prevention and protection bar. The rear bumper structure provided herein has high prevention and protection performances and safety performance.
Owner:JIANGSU GAOBIAO TECH DEV
Method and system for monitoring credible counting device
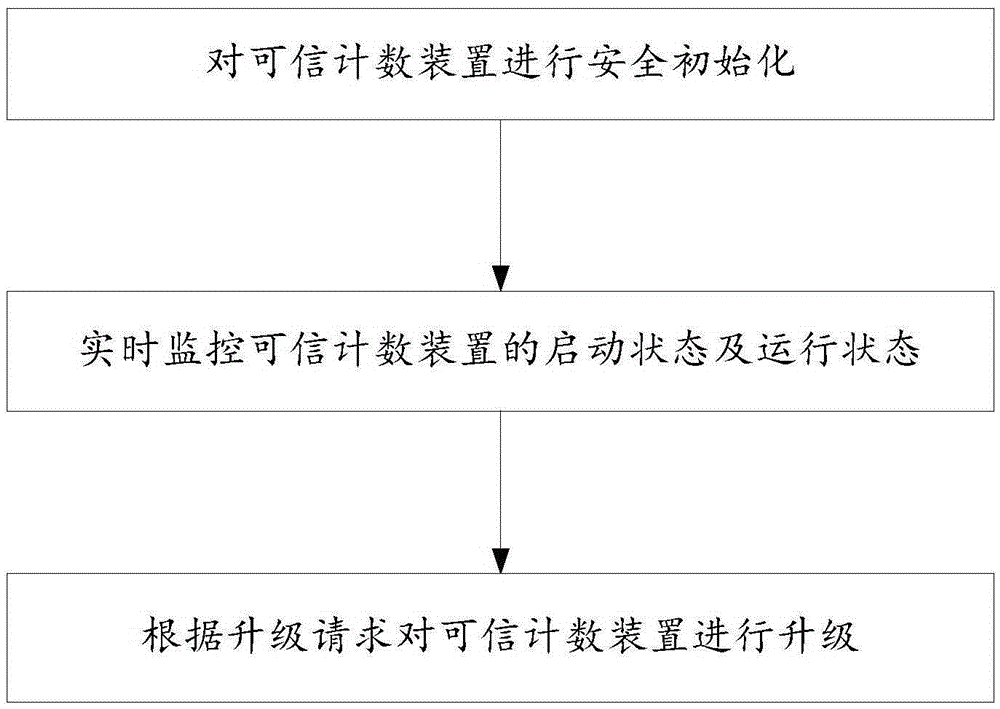
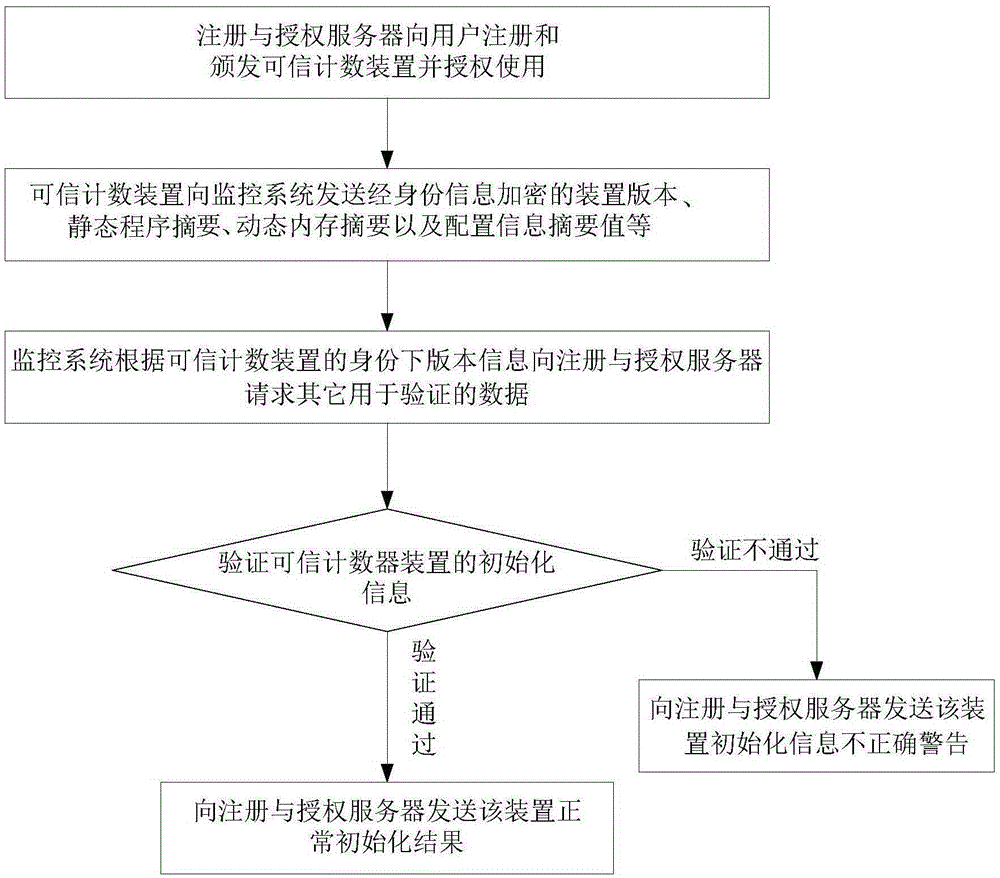
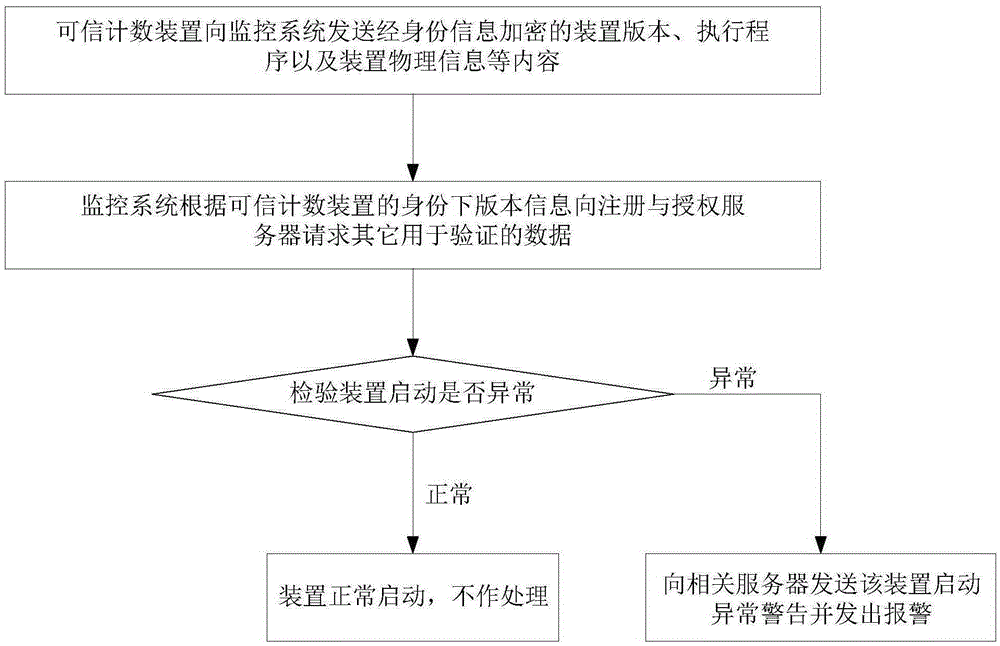
ActiveCN105306301AThe configuration information is legalRealize monitoringData switching networksComputer scienceCounter device
The invention relates to a method and a system for monitoring a credible counting device. The method comprises the following steps of carrying out security initialization on the credible counting device; monitoring running status of the credible counting device in real time; and upgrading the credible counting device according to an upgrading request. The method and the system have the beneficial effects that through monitoring security initialization of the device, the to-be-started device can be guaranteed to be issued, unmodified and authorized, and the loaded configuration information is legal. Through operation monitoring and abnormal alarm functions of the device, the real-time status of the device can be monitored; when the device is abnormal, an alarm is given, so that the anomaly is timely processed. Through the security upgrading function of the device, security upgrading of the legal operation device can be guaranteed, so that the illegal device cannot be upgraded to the legal device, and the legal device can be available after upgrading.
Owner:BEIJING ELECTRONICS SCI & TECH INST +1
Hoisting wire pulley device for crane
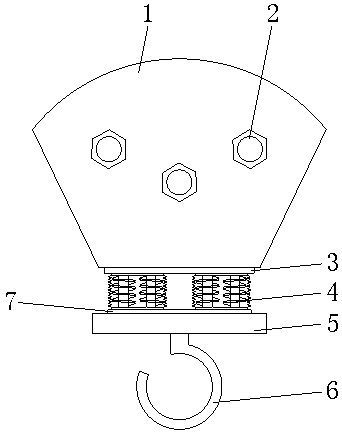
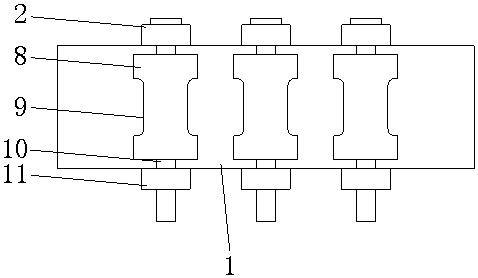
The invention discloses a hoisting wire pulley device for a crane. The device comprises a shell, a connecting plate is welded to the lower end of the shell, a base plate is connected to the lower endof the connecting plate through spring assemblies, a hook lock is fixed to the lower end of the base plate, three shaft rods are sequentially arranged in the shell, pulley bodies are connected to theouter parts of the three shaft rods in a rotating mode, grooves are formed in the outer surfaces of the pulley bodies, meanwhile, each spring assembly comprises spring bodies and two spring seats, andthe two spring seats are fixed to the two ends of the corresponding spring bodies. The device has the advantage that the shell, screw caps, the connecting plate, the spring assemblies, the base plate, a damping pad, the pulley bodies, the shaft rods, nuts, the spring bodies, the spring seats and protective covers are arranged, so that the problems that the safety of a hoisting wire pulley devicefor a crane at the present stage is low in the using process, and goods are prone to shake due to the fact that a pressure buffering device is not arranged can be solved.
Owner:新乡市圣元起重机有限公司
A kind of OTA security upgrading system and upgrading method thereof
ActiveCN111562935BEnsure safetySecurity upgradeVersion controlDigital data protectionSoftware engineeringOperating system
The invention relates to an OTA security upgrade system and an upgrade method thereof, which belong to the technical field of communication, and in particular relate to a system and a method for OTA security upgrade. Including the OTA platform upgrade method and the OTA terminal upgrade method; the OTA platform upgrade method includes security upgrade management, security version management, version download management and security control; The upgrade provides corresponding upgrade version file key acquisition and processing, upgrade pre-condition judgment and pre-order operation, security key request management and upgrade process status detection rules functions, and the OTA terminal integrates the upgrade operation management of multiple intelligent parts. Through standardized equipment upgrade process management, OTA security upgrades of multiple types of intelligent components can be realized for large-scale equipment integrators, meeting the privacy and security requirements of various intelligent component upgrades, and effectively improving the security and stability of upgrades .
Owner:江苏海平面数据科技有限公司
Casting molding high-performance alloy casting ceramic lining plate
The invention relates to the field of lining plates, and particularly discloses a casting molding high-performance alloy casting ceramic lining plate. The casting molding high-performance alloy casting ceramic lining plate comprises an alloy matrix and an anti-wear body, and the alloy matrix and the anti-wear body are integrally cast. The ceramic casting lining plate is formed by integrally casting the steel alloy base body and the anti-wear ceramic body, the lining plate is connected to a mother plate in a welded or bolted mode and cannot fall off, and the reliability is higher compared with a lining plate which is mechanically connected or bonded through glue. The ceramic casting lining plate is an alloy composite material, is high in high temperature resistance and has longer service life than a common lining plate. The ceramic casting lining plate is cast according to a mold, can be subjected to secondary machining according to shape requirements, and has higher plasticity and higher adaptability to process requirements compared with a ceramic lining plate.
Owner:唐山贵金甲科技有限公司
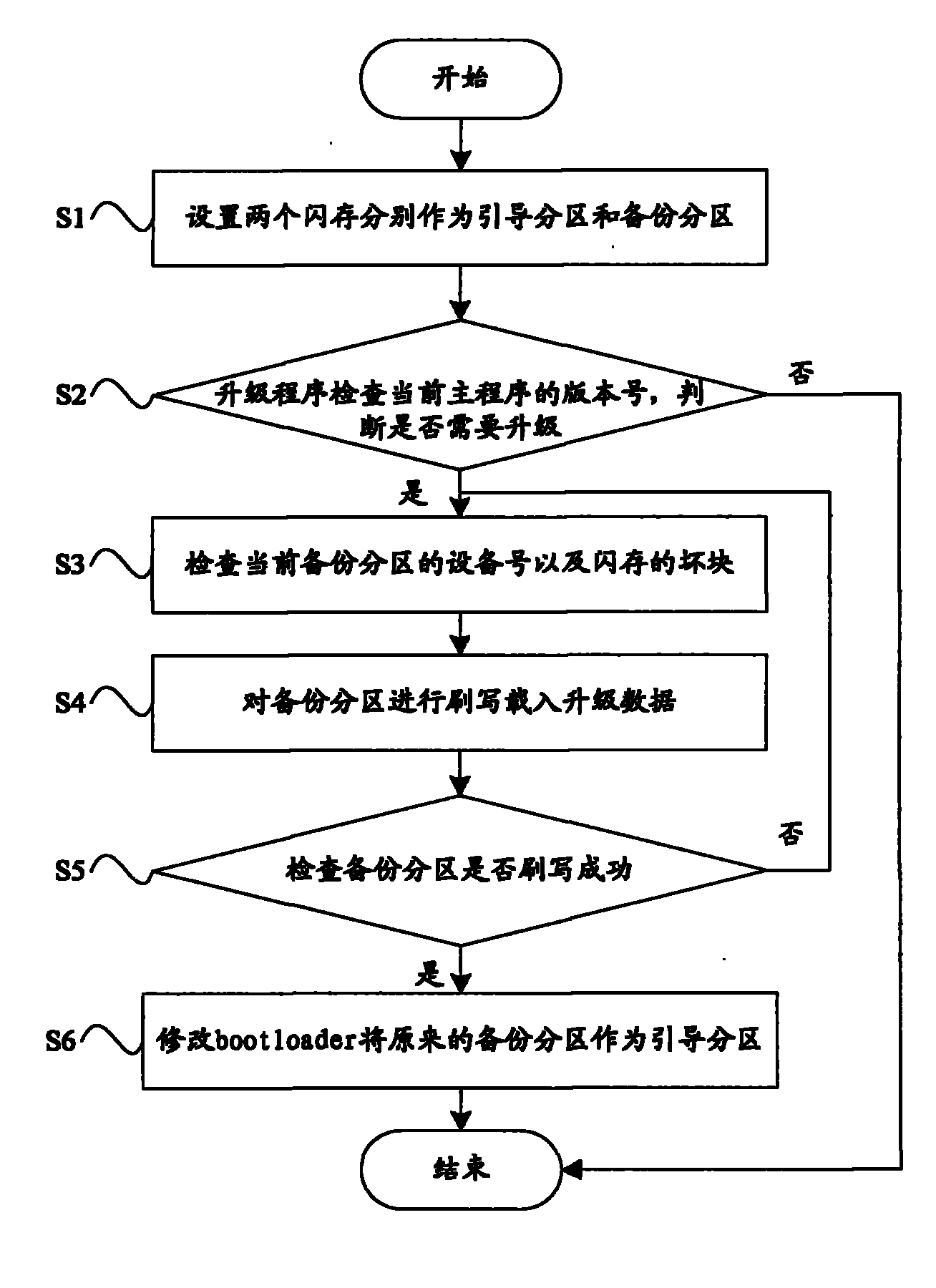
Method for automatically upgrading network television
ActiveCN102104750BSecurity upgradeImprove reliabilityProgram loading/initiatingSelective content distributionUpgradeComputer engineering
The invention relates to a method for automatically upgrading a network television, which comprises the following steps of: S1, setting one flash memory for a boot subarea to store a current used main program and setting the other flash memory for a backup subarea to store the backup of the current used main program in a bootloader; S2, checking the version number of the current main program by an upgrade program, judging whether upgrade is needed, if so, turning to a step S3, otherwise, ending; S3, checking the equipment number of the current backup subarea and the bad block of the flash memories; S4, flashing the backup subarea to load upgrade data; S5, checking whether the backup subarea is flashed successfully, if so, turning to a step S6, otherwise, turning to the step S3; and modifying the bootloader to change the original backup subarea into the boot subarea. The method for automatically upgrading the network television ensures that the network television cannot be upgraded safely by adopting a double-machine hot backup mode, and reduces the cost of home maintenance.
Owner:KONKA GROUP
A kind of out-of-band upgrade method and device of BMC
ActiveCN106445580BQuick upgradeSecurity upgradeProgram loading/initiatingSoftware deploymentProcess engineeringServer
The invention discloses a method and a device for a BMC (Baseboard Management Controller) with external upgrading. The method comprises the steps of: loading an initramfs mirror image through a pxe server; downloading an upgrading file and an upgrading tool needed for upgrading of the BMC according to parameters of a configuration file; determining a command parameter for upgrading through the upgrading file and the upgrading tool, and establishing a corresponding upgrading process according to the command parameter; and filtering and selecting a to-be-upgraded server node, and realizing the upgrading of the BMC according to the server node and the upgrading process. According to the method and the device for the BMC with external upgrading provided by the invention, the upgrading of the BMC can be rapidly and safely realized in batches. Through batch upgrading of the BMC, an error caused by manual operation is avoided and the reliability of the upgrading of the BMC is improved.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
Power system embedded software remote dynamic upgrade method and system
ActiveCN108196873BSecurity upgradeReliable upgradeSoftware engineeringElectric power systemSoftware engineering
The invention discloses a method and system for remote dynamic upgrading of embedded software in a power system, which includes the following steps: remotely loading a software upgrade information table and a software upgrade code to a device node to be upgraded in the power system; when the device node " When the "idle" task is running (when all system tasks are not running), the information is verified according to the software upgrade information table, and if the verification is correct, the software dynamic upgrade is performed. The invention ensures the safety and reliability of the software upgrading process through the control of information verification and interruption.
Owner:SHANDONG UNIV OF SCI & TECH
Front bumper of automobile
The invention discloses a front bumper of an automobile. The front bumper comprises a front bumper body. A front bumper lower decoration plate is arranged on the edge of the lower side of the front bumper body. A front bumper middle grating is arranged above the front bumper lower decoration plate. A front bumper left grating and a front bumper right grating are symmetrically arranged on the left side and the right side of the front bumper middle grating correspondingly. A front bumper lower left wrapping corner and a front bumper lower right wrapping corner are symmetrically arranged on the edges of the lower portions of the left side and the right side of the front bumper body correspondingly. A front bumper left framework and a front bumper right framework are symmetrically arranged on the upper portions of the left side and the right side of the front bumper body correspondingly. A radar left support and a radar right support are symmetrically arranged on the front bumper left framework and the front bumper right framework correspondingly. A left daytime running light and a right daytime running light are arranged on the left side and the right side of the front bumper body. A left daytime running light decoration frame and a right daytime running light decoration frame are arranged on frames of the left daytime running light and the right daytime running light correspondingly. The front bumper of the automobile has high practical performance and safety performance.
Owner:JIANGSU GAOBIAO TECH DEV
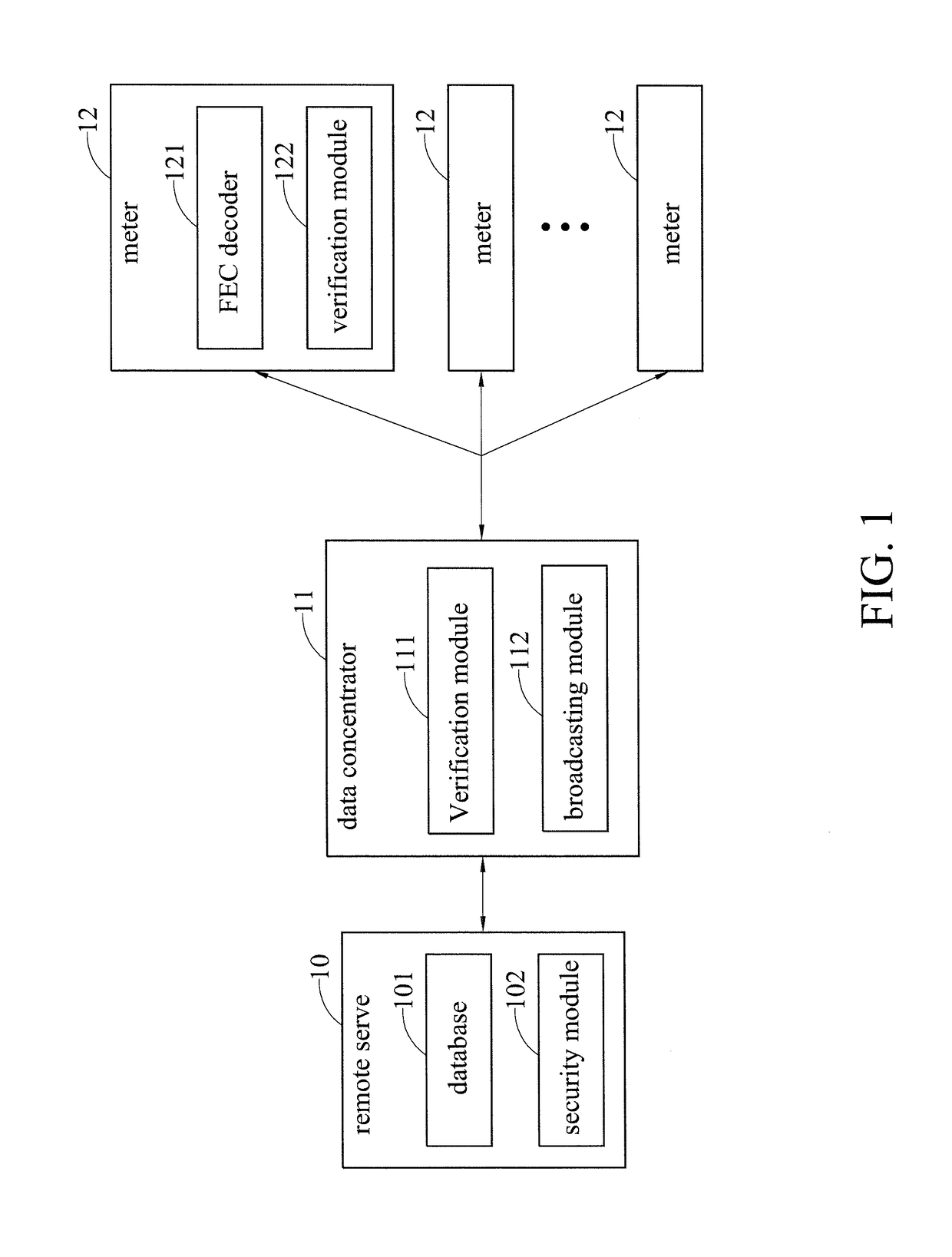
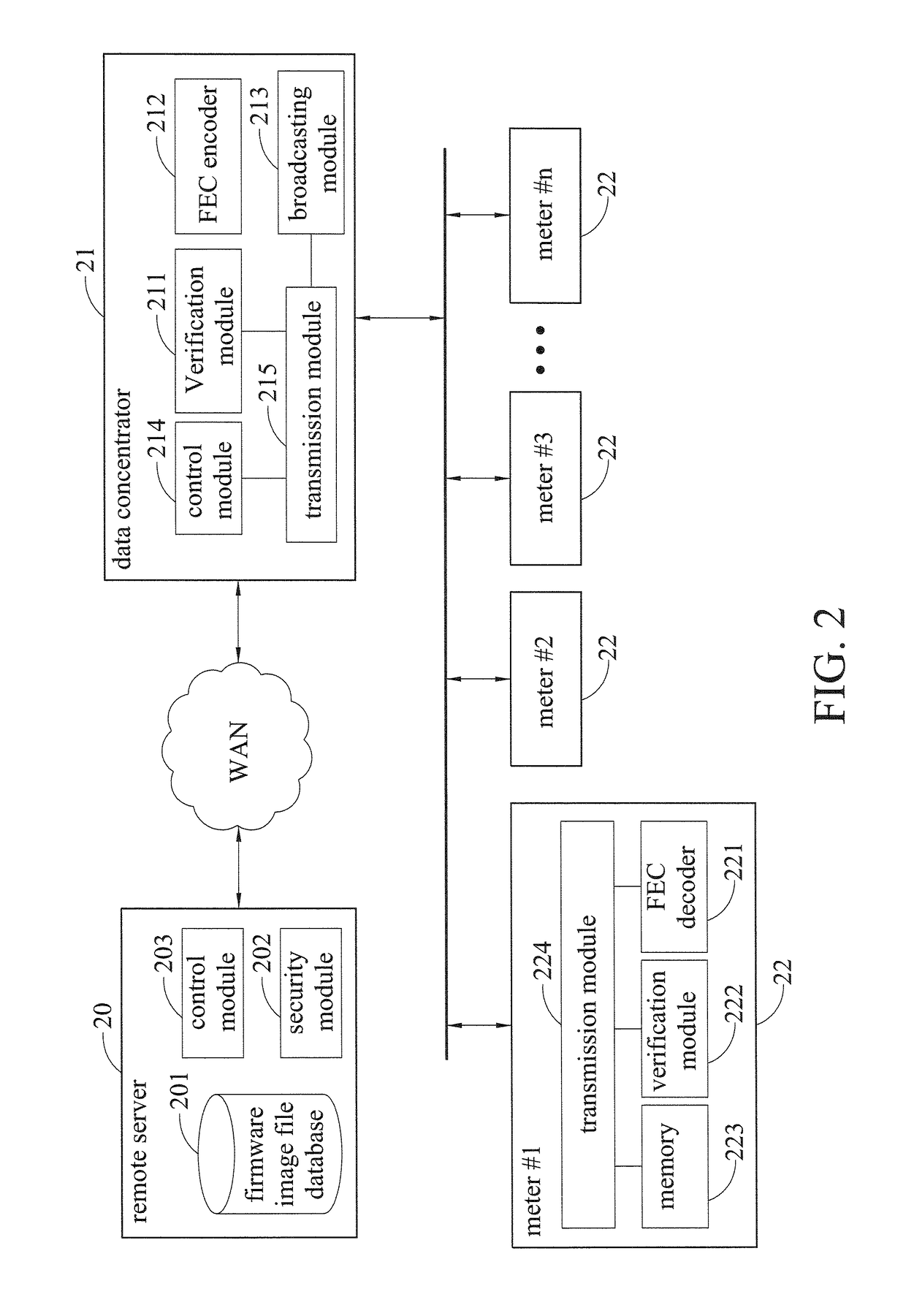
System for firmware upgrade in AMI and method thereof
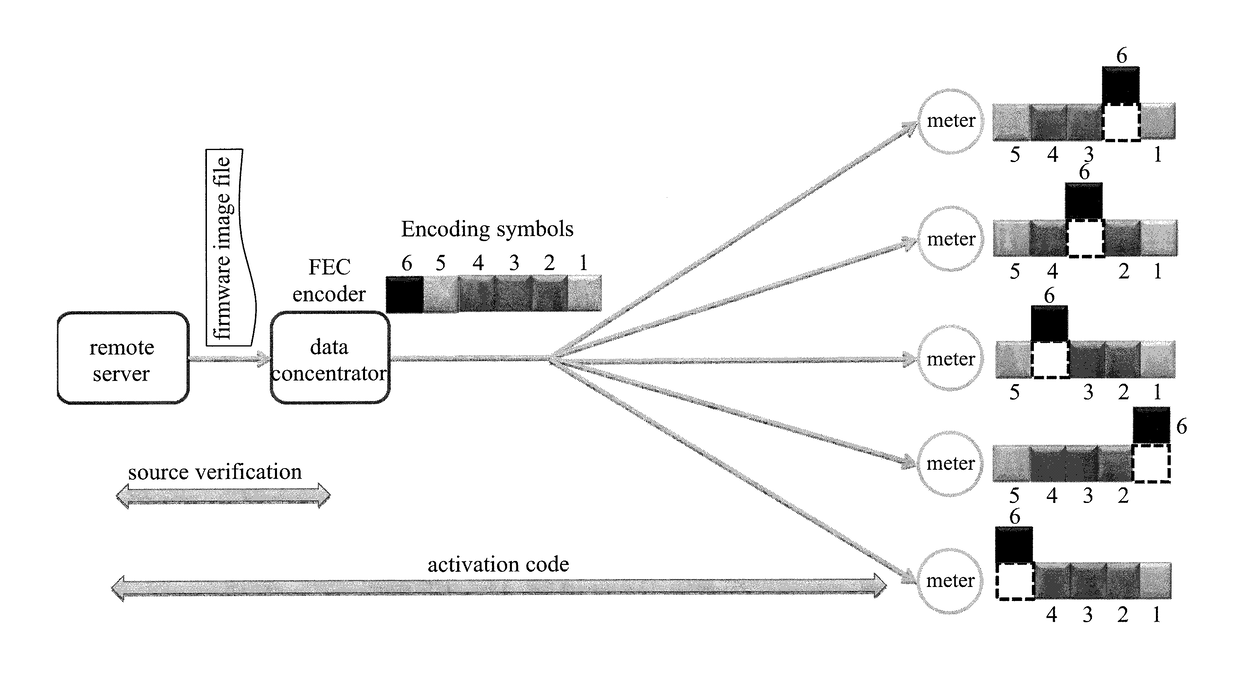
ActiveUS9645887B2Improve upgrade efficiencySecurity upgradeSoftware engineeringUser identity/authority verificationBiological activationBroadcasting
A system and method for firmware upgrade in an AMI are provided. A remote server provides a firmware image file. After receiving the firmware image file and verifying the remote server, a data concentrator transmits at least one encoding symbol generated from the firmware image file to at least one meter through broadcasting and a retransmission mechanism of minimum retransmission contents. Upon receiving a predetermined number of encoding symbols, each meter recovers the original firmware image file from the received encoding symbols. Then, each meter receives and verifies an activation code generated by the remote server before carrying out the firmware upgrade.
Owner:IND TECH RES INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com