Method and system for enhancing MQTT protocol transmission security by using symmetric cryptographic technology
A protocol transmission, symmetric encryption technology, applied in transmission systems, digital transmission systems, key distribution, and can solve problems such as reduced security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
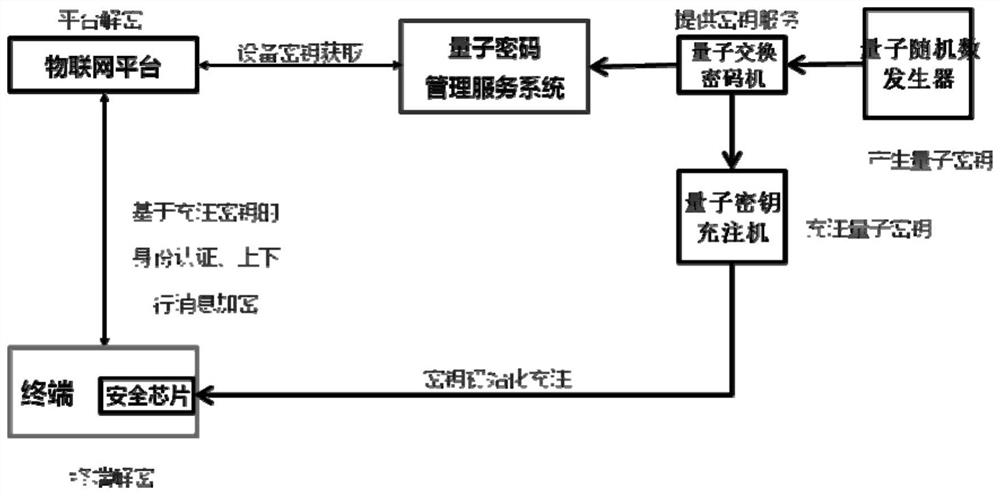
[0090] Such as figure 1 and figure 2 As shown, this embodiment provides a method for using symmetric cryptography to enhance MQTT protocol transmission security, including data encryption and data decryption, and is applied in the MQTT protocol transmission system. The MQTT protocol transmission system includes a quantum random number generator, a quantum exchange Cipher machines, quantum key filling machines, quantum cryptography management service systems, IoT terminals, security chips, and IoT platforms. The security chip can be in the form of a SIM card or a USB flash drive, and is built-in or externally connected to an IoT terminal or a device module of an IoT terminal.
[0091] The Internet of Things terminal can be a publisher in the MQTT protocol, or a subscriber in the MQTT protocol. The IoT platform can be a broker in the MQTT protocol. During the process of IoT terminal accessing the IoT platform, the IoT platform needs to authenticate the IoT terminal. If the a...
Embodiment 2
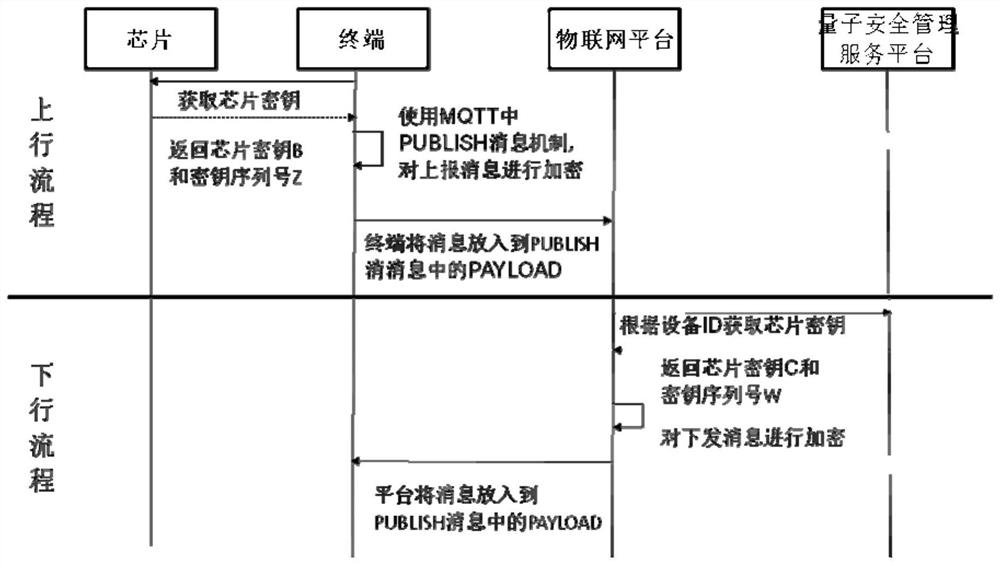
[0148] This embodiment provides a method for using symmetric cryptography to enhance MQTT protocol transmission security, including data encryption and data decryption, and is applied to an Internet of Things terminal in an MQTT protocol transmission system. The structure of the MQTT protocol transmission system is the same as that of Embodiment 1.
[0149] The IoT terminal first uses the key in the quantum security chip to complete the platform login authentication to the IoT platform, obtains the login token, and then performs the following MQTT protocol transmission steps:
[0150] encrypt data;
[0151] IoT terminal to IoT platform (uplink): the quantum security chip obtains the filling of the quantum key provided by the quantum key filling machine;
[0152] After obtaining the login token, the Internet of Things terminal calls the key in the quantum security chip to complete the encryption of the reported message. SM4 can be used for encryption, and the encrypted informat...
Embodiment 3
[0165] This embodiment provides a method of using symmetric cryptography to enhance MQTT protocol transmission security, including data encryption and data decryption, and is applied to the Internet of Things platform of the MQTT protocol transmission system. The structure of the MQTT protocol transmission system is the same as that of Embodiment 1.
[0166] The IoT platform first completes the login authentication of the IoT terminal, and then performs the following MQTT protocol transmission steps:
[0167] encrypt data;
[0168] IoT platform to IoT terminal (downlink): The IoT platform applies for a key to the quantum password management service system according to the IoT terminal identification, and the quantum password management service system fills the information with the previous quantum security chip through the quantum exchange cipher machine, returns and The quantum security chip integrated in the quantum terminal has already filled the available key symmetric key...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com