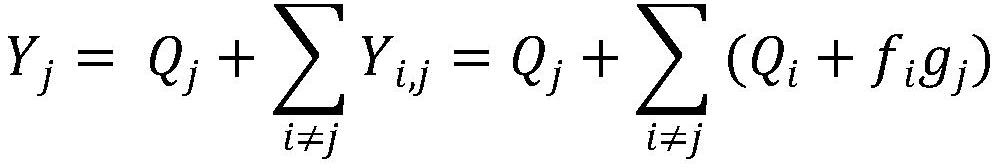Patents
Literature
85results about How to "Solve authentication problems" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
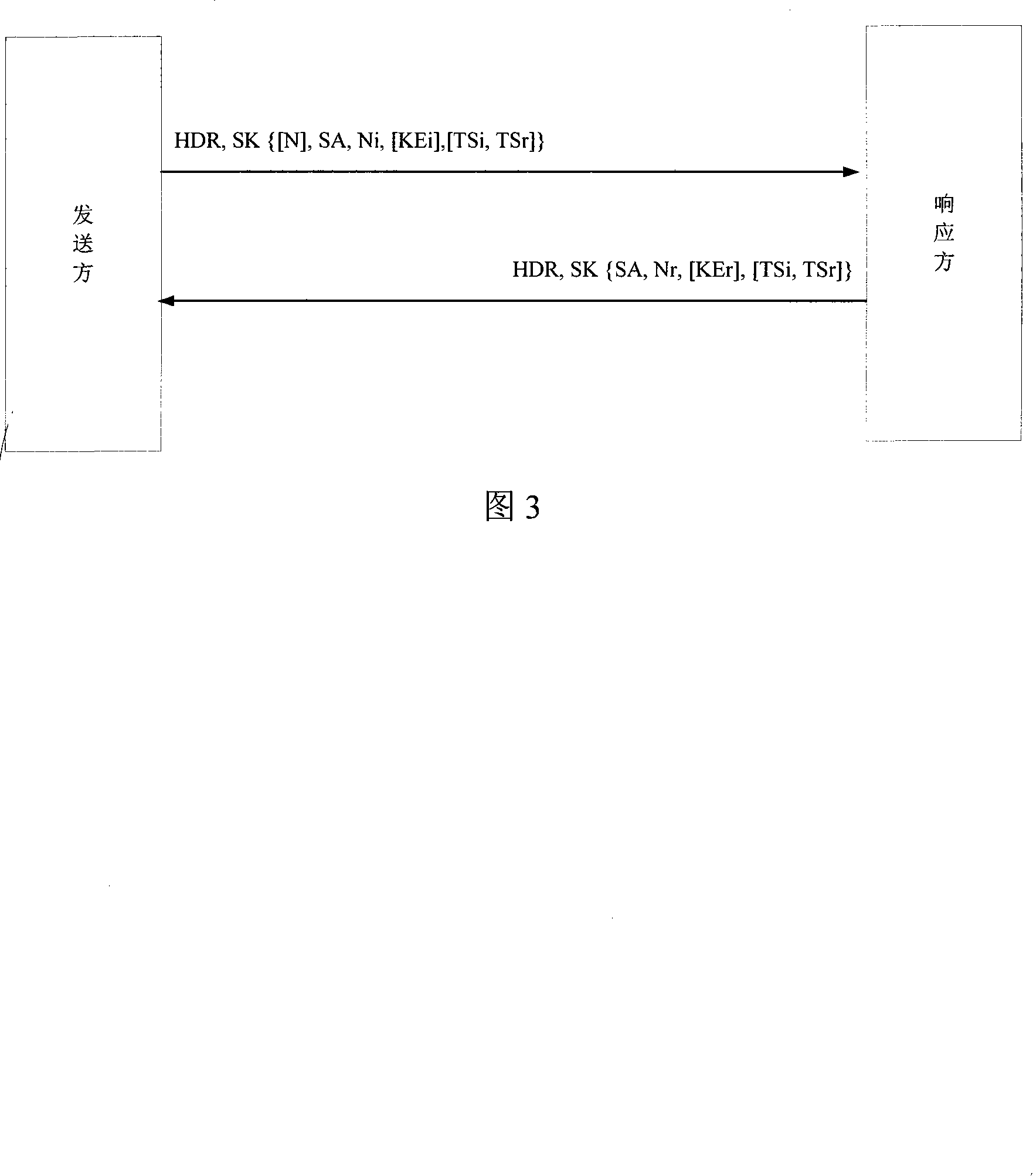
Mobile ad hoc authentication method, network and system
InactiveCN101192928AImprove efficiencyMake the most of processing resourcesEnergy efficient ICTUser identity/authority verificationNetwork structureMobile ad hoc network
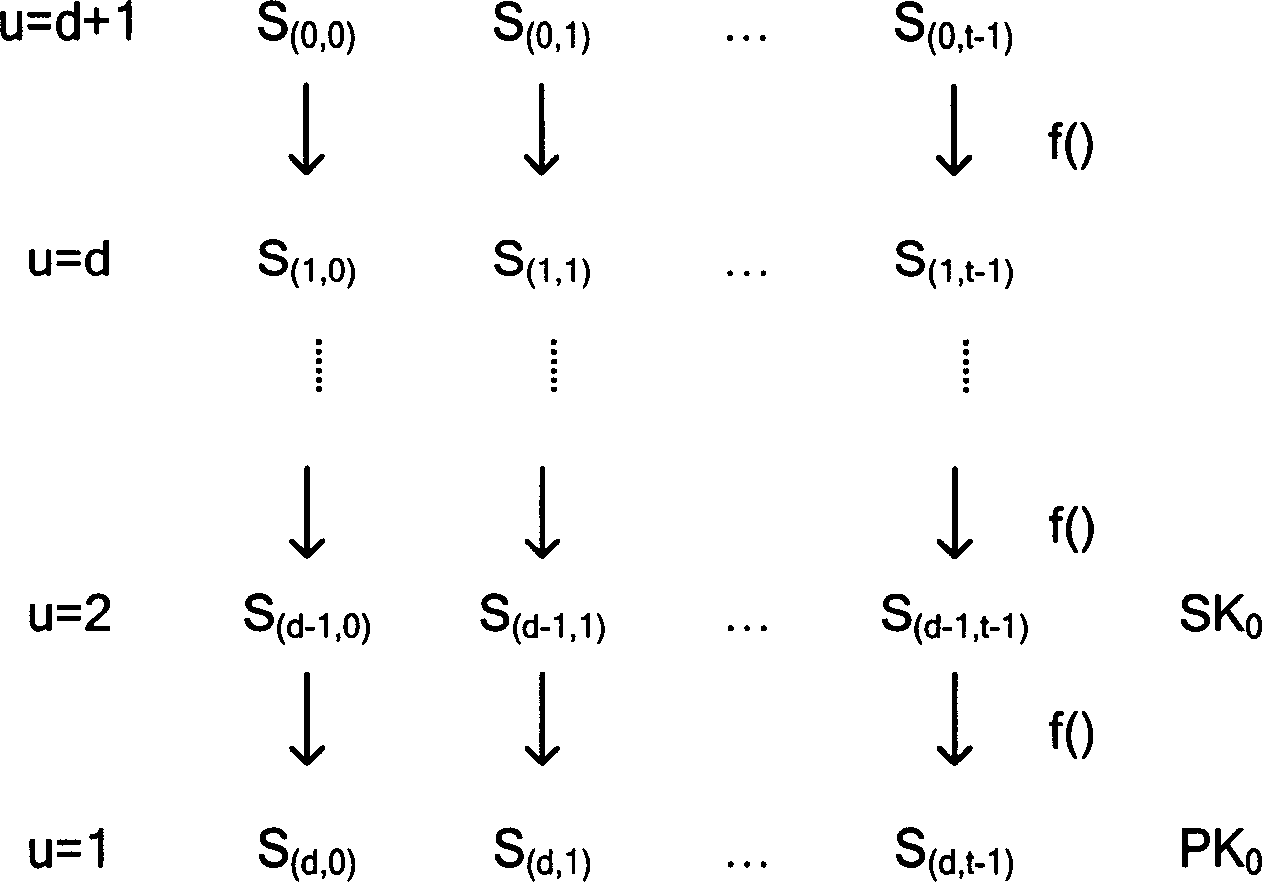
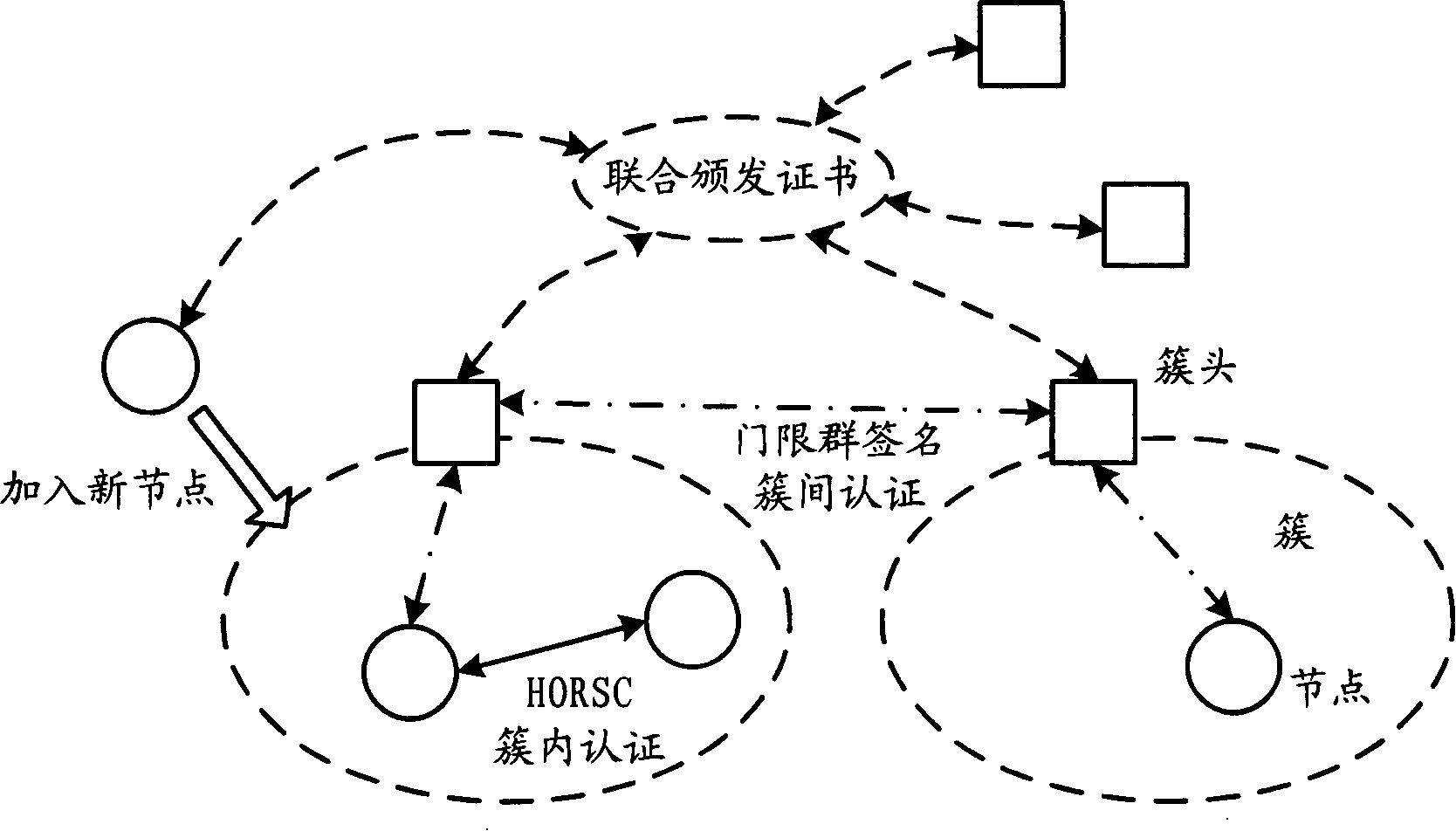
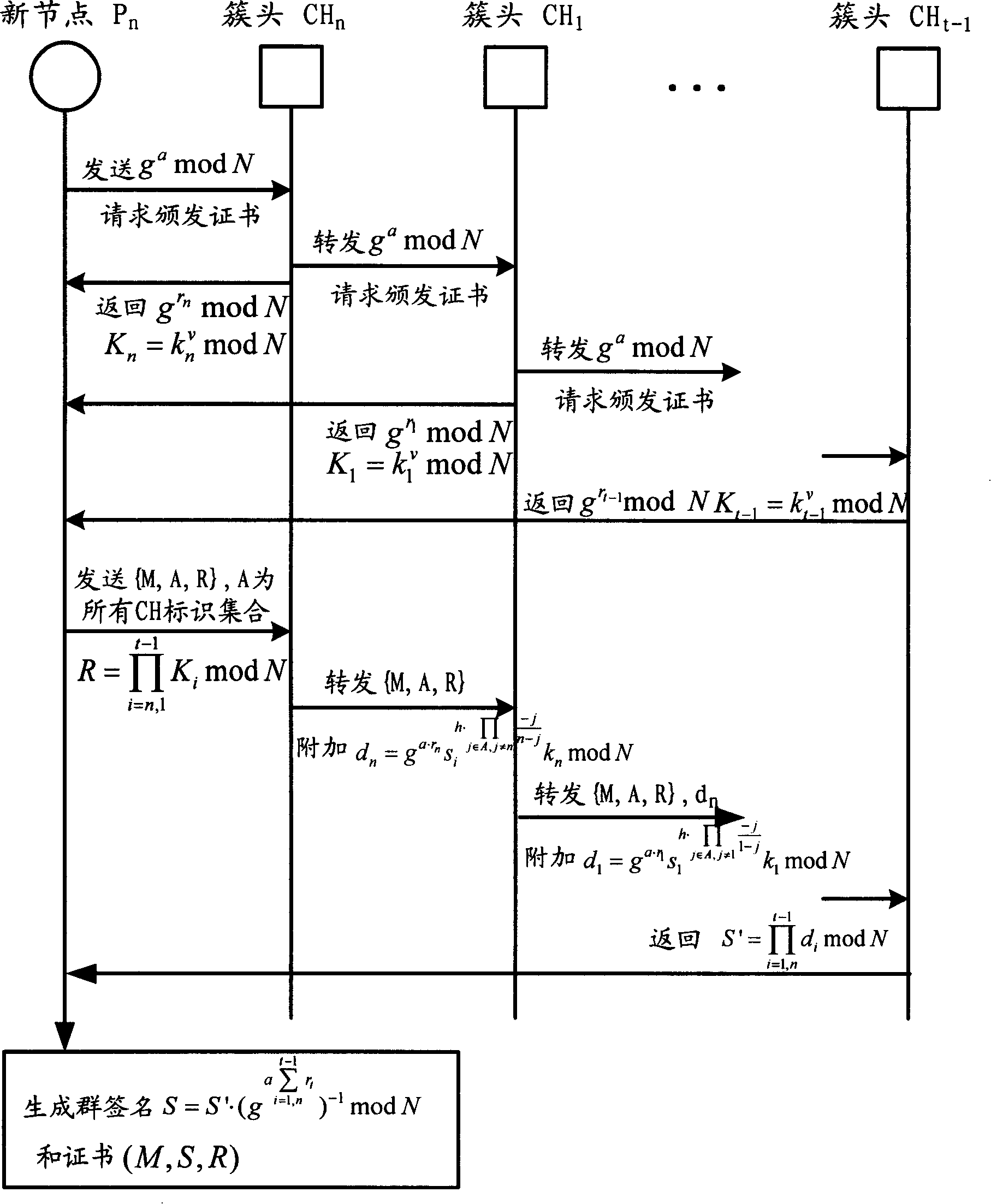
The invention relates to the communication field and discloses an authentication method, a network and a system of mobile ad hoc network, which ensures the realization of layer distribution type authentication scheme of cluster mobile ad hoc network; and the requirement on computer processed resources is rational, which can be realized in practical application environment. The invention adopts a group network structure of cluster mobile ad hoc network and advocates layer distribution identity authentication scheme; and the inter-cluster communication used an improved new threshold group signature protocol which improves the original threshold group signature method based on GQ and decreases power index calculation times, improves calculation parallelism and reduces the requirement on processed resources; at the time of initialization, a certificate and a sub key are issued by the system uniformly; cluster heads which have enough numbers of sub keys can jointly recover system keys, thereby carrying out the group signature to issue certificates to new added nodes and using multi-leap serial communication for realizing united group signature.
Owner:HUAWEI TECH CO LTD +1
Method for constructing virtual environment trust
ActiveCN101350044ASecure Distributed ApplicationGuaranteed credibilityPlatform integrity maintainanceTrusted applicationIsolating mechanisms
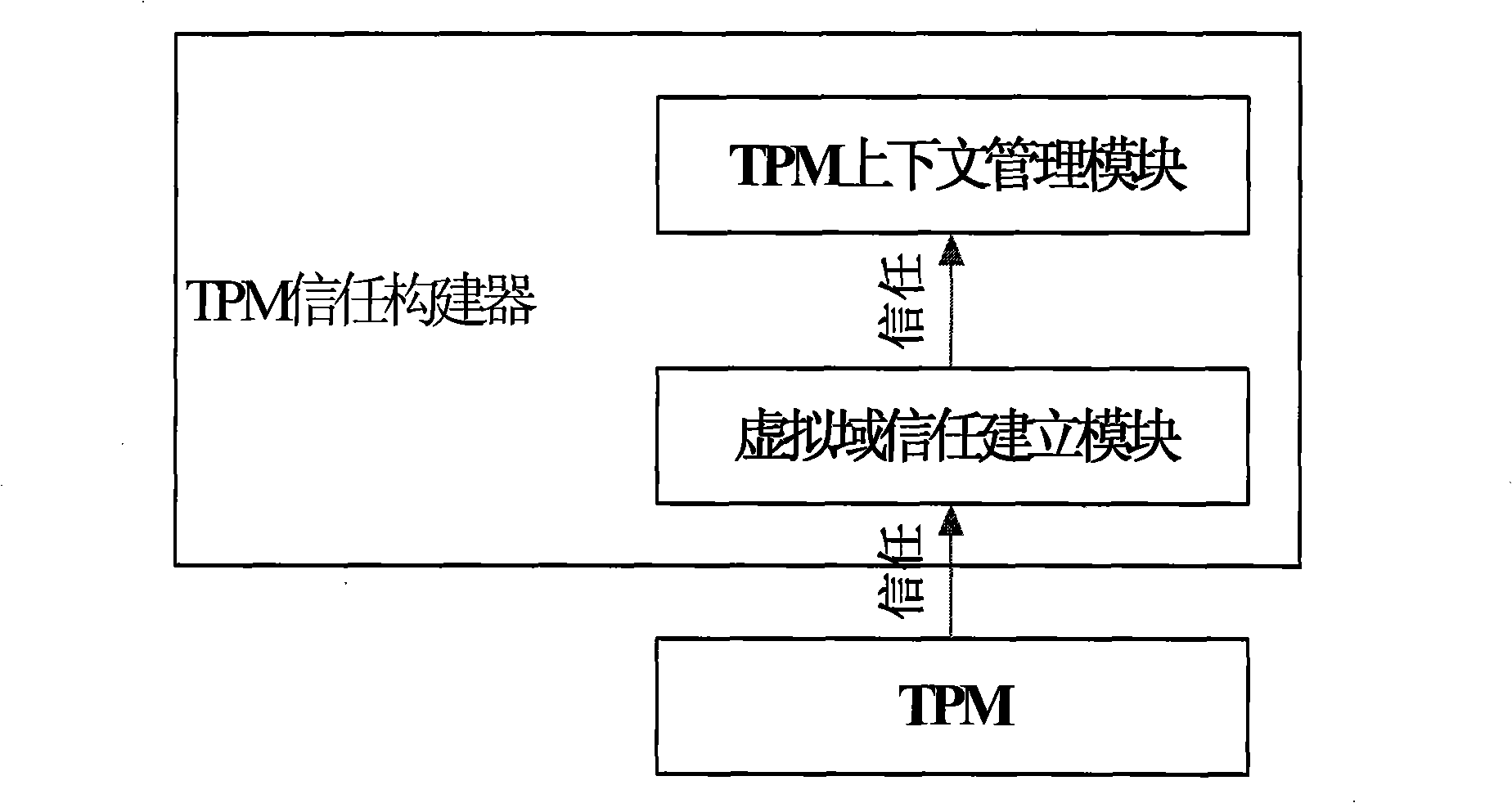
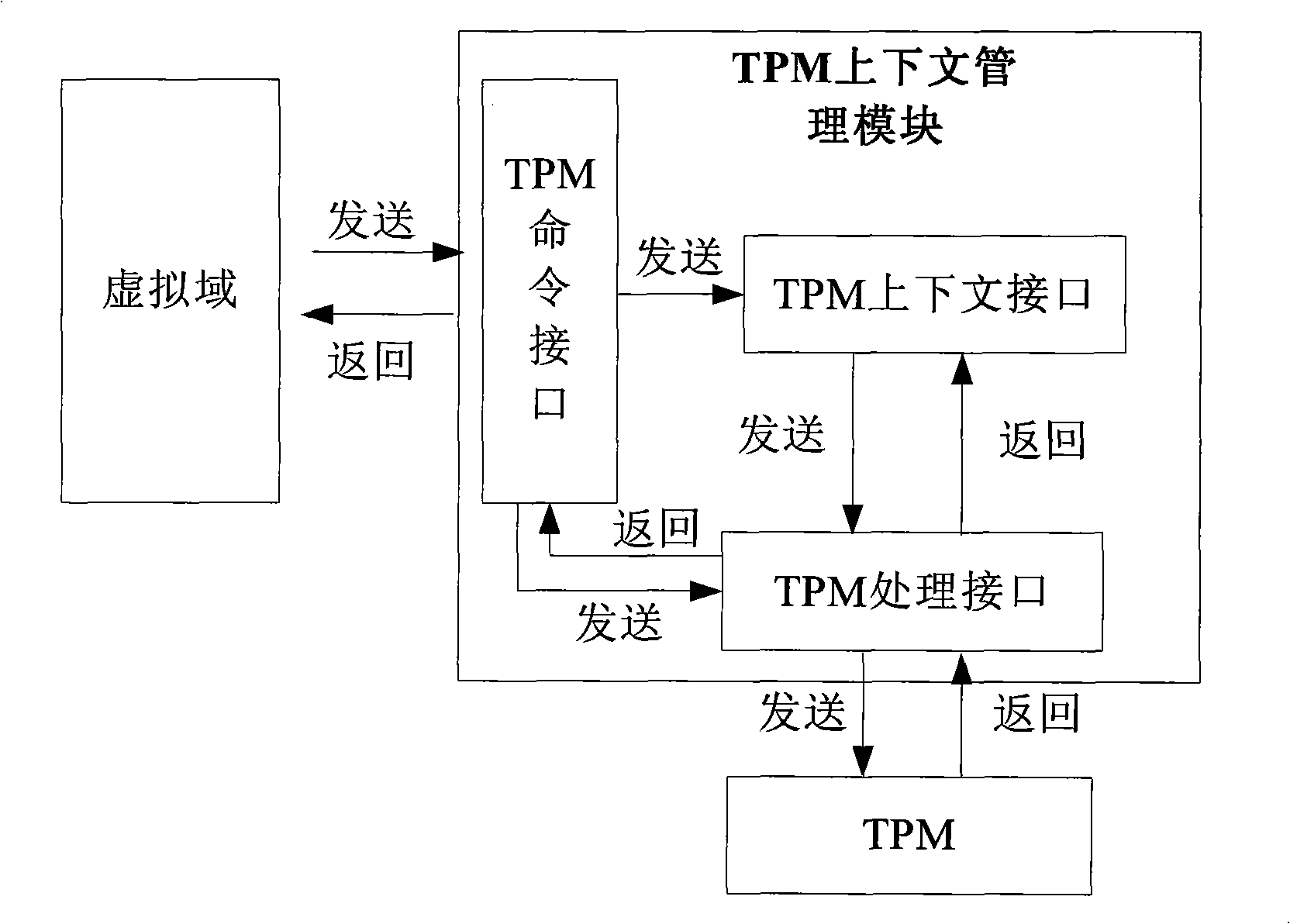
The invention discloses a virtual environment trust building method, which belongs to the trusted computing field in information security. The invention uses a single TPM to realize the trust of one or a plurality of virtual domains and comprises the following steps: firstly, measuring hardware, a virtual layer, a management virtual domain and one or a plurality of application virtual domains in turn by the TPM, realizing the trust of the application virtual domains, secondly, receiving and processing TPM command requests from each virtual domain, and establishing and maintaining TPM context for each virtual domain. The invention has the advantages that firstly, the platform safety and credibility are intensified through a complete trusted isolating mechanism, the trusted application service is better supported, and secondly, the safe sharing of each virtual domain to a trusted hardware root TPM is realized.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
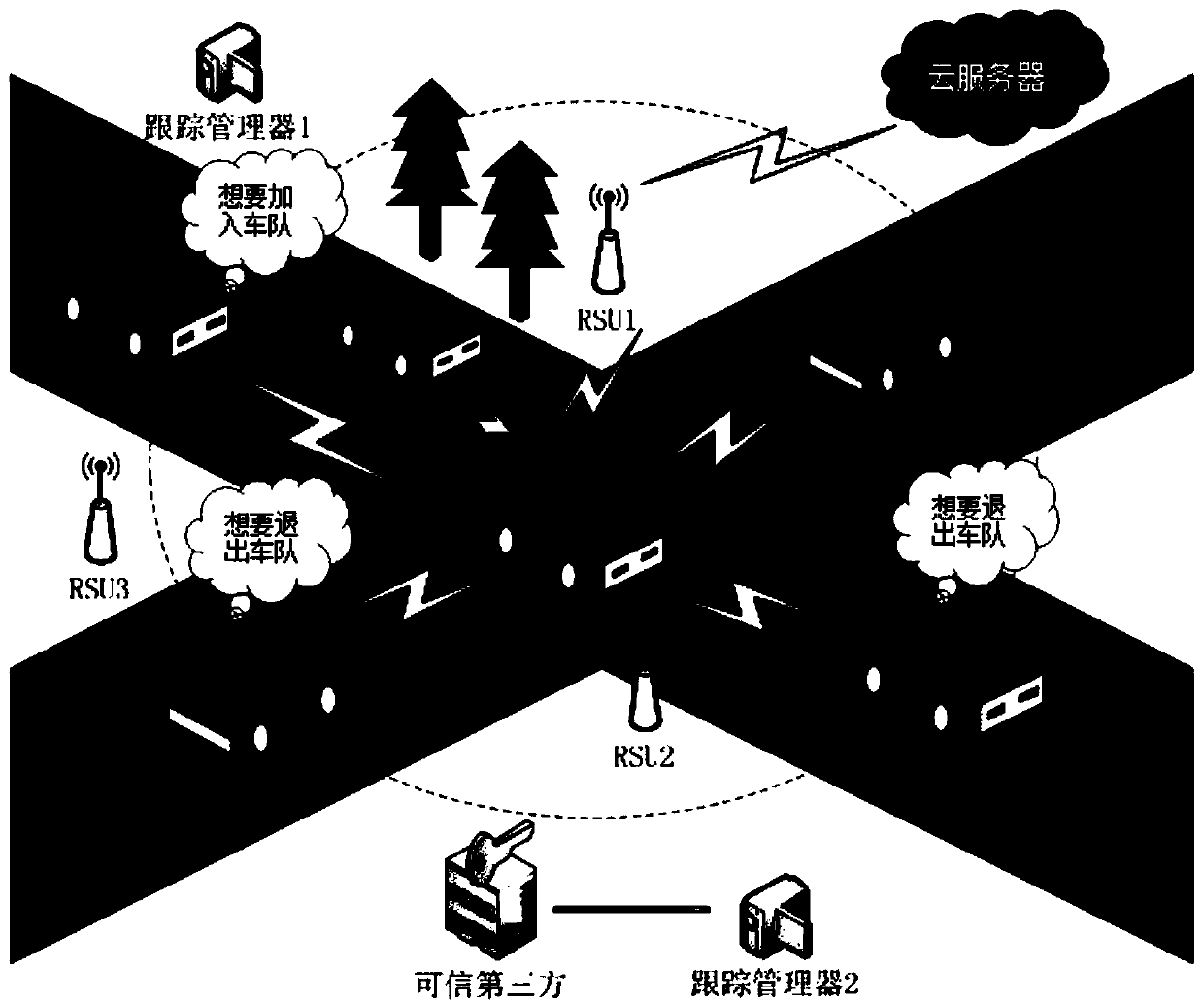
Motorcade establishment and management method and system based on block chain and PKI authentication mechanism
ActiveCN109687976ASolve authentication problemsTroubleshoot account management issuesKey distribution for secure communicationParticular environment based servicesSecure communicationThe Internet
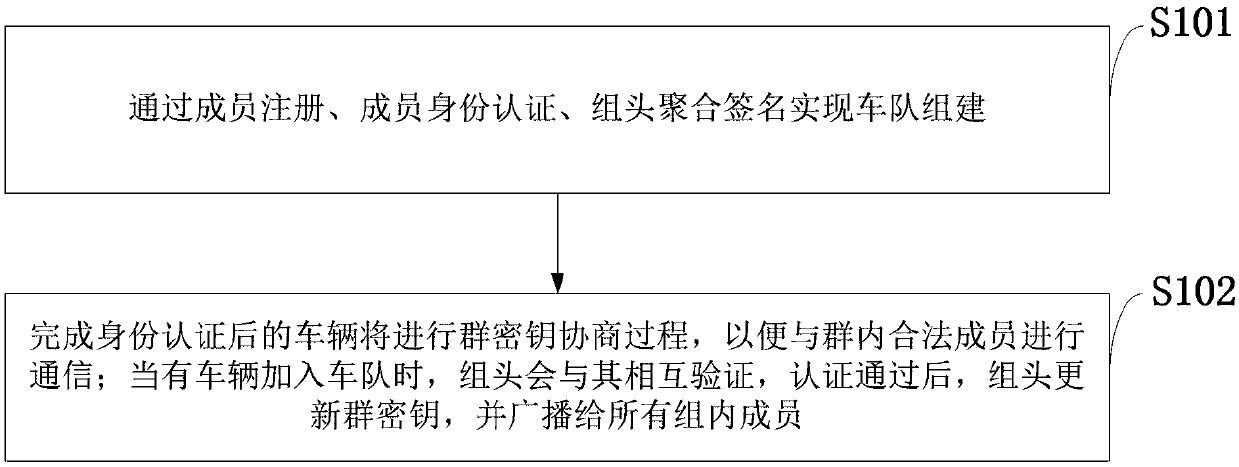
The invention belongs to the technical field of safety communication between motorcades in Internet of Vehicles, and discloses a motorcade establishment and management method and system based on a block chain and a PKI authentication mechanism. The method is mainly divided into two parts of motorcade establishment and group key agreement and update; the motorcade establishment part comprises the following main processes of member registration, member identity authentication and group head aggregate signature; and the group key agreement and update part comprises the following main processes ofgroup key agreement and group key update for dynamic joining and exiting of a vehicle. According to the method and the system, the block chain is combined with the PKI authentication mechanism, a problem of identity authentication of the vehicle, a server and an RSU in the Internet of Vehicles is solved; the motorcade establishment is completed based on an elliptic curve, a bilinear pairing technology and an aggregate signature; and the group key agreement and update can be realized based on a DDH difficulty problem, the forward and backward safety is achieved, and the safety of member communication in the motorcade is ensured.
Owner:XIAN UNIV OF POSTS & TELECOMM
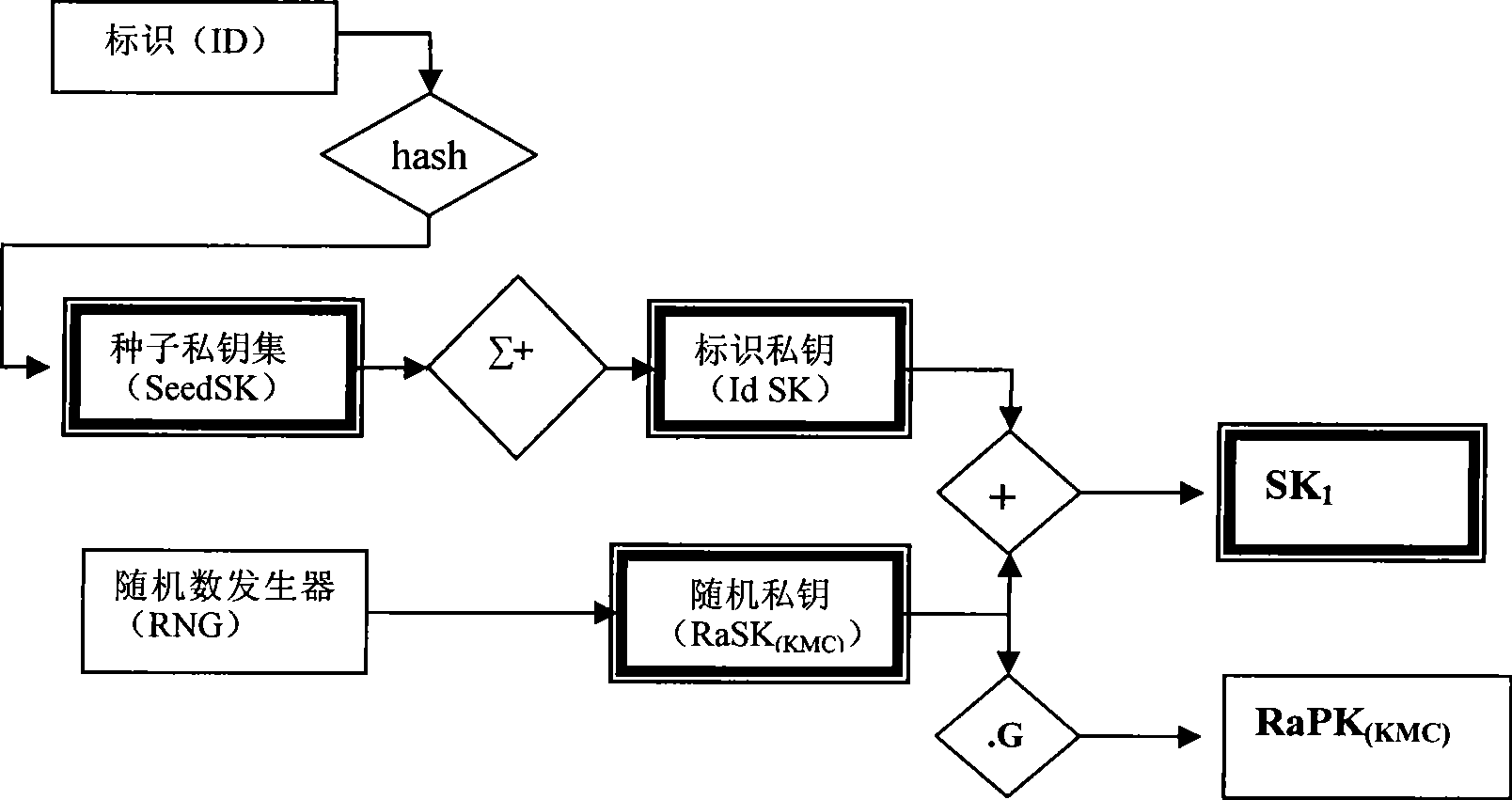
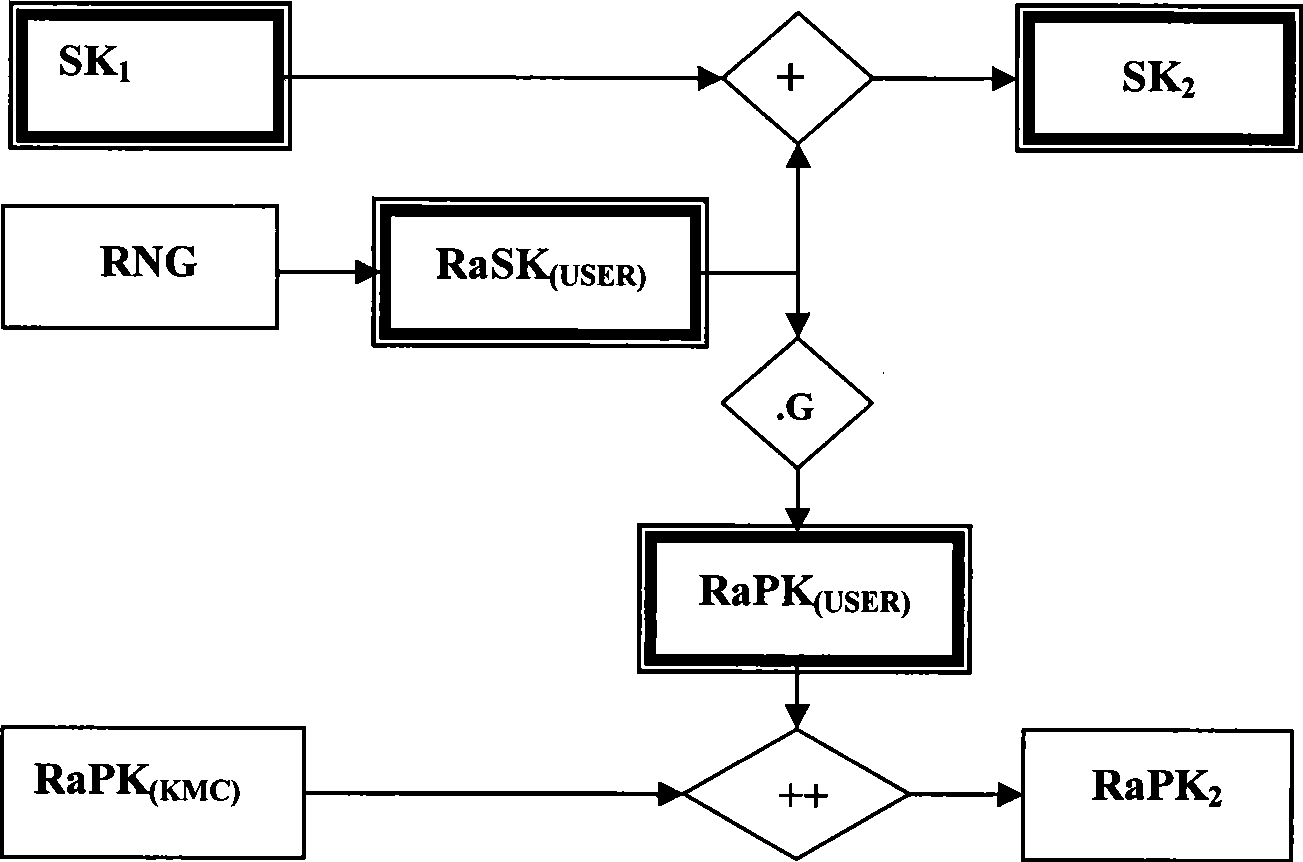
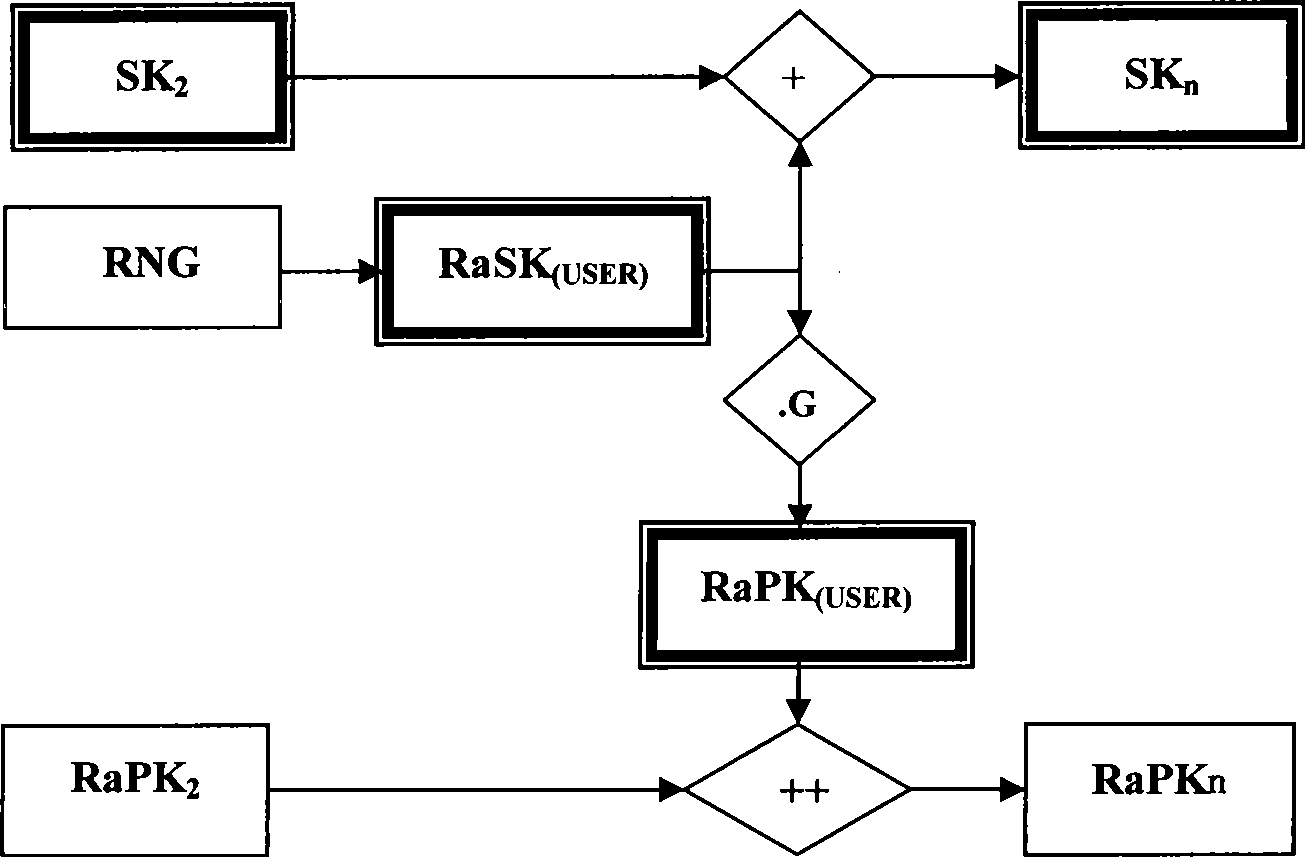
Double factor combined public key generating and authenticating method
InactiveCN101420300AMeet the needs of centralized managementImprove securityKey distribution for secure communicationPublic key for secure communicationIdentification keyLogistics management
The present invention provides an identification key and random key complicated two-factor combined public key system and an authentication method. The identification keys are generated by selecting and combining seed key sets by the user identification generated sequence; the random keys are generated on the basis of one-way function principle which is also the basis of general public key ciphers. Multiple complication modes of the random key and the identification key can not only satisfy the requirement of centralized management, but also provide the proprietary right of private keys for users. An authentication system based on the key generating method has the characteristics of the identification authentication which does not need a third part certificate to prove and high randomization and privacy of general public key cipher and random private key. The present invention can be widely applied to authentication of systems with various scales, especially the authentication of public systems with enormous scale, and the applicable fields comprises reliable access, reliable load, electronic bank, reliable transaction, reliable logistics and the like.
Owner:BEIJING E HENXEN AUTHENTICATION TECH
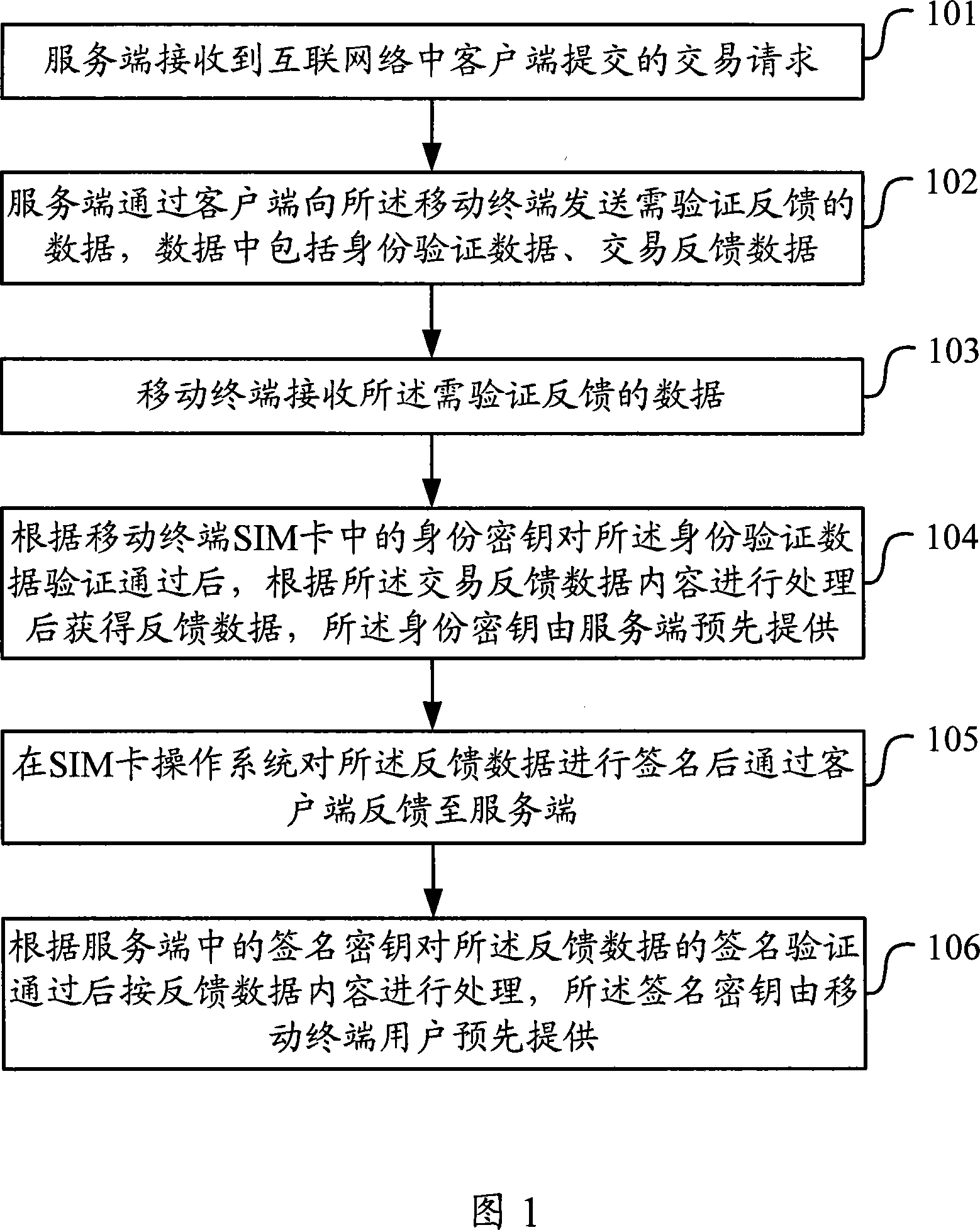
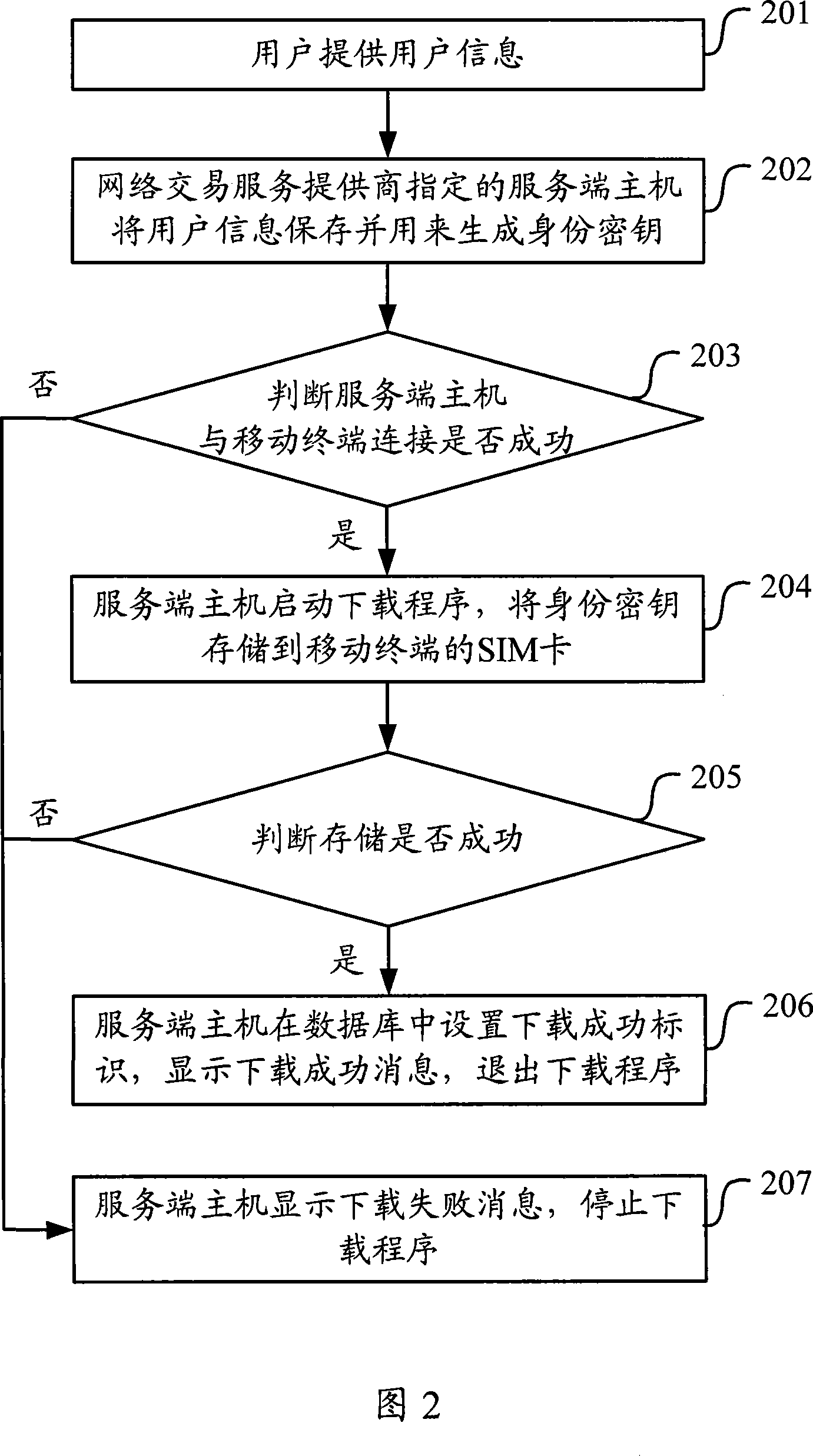
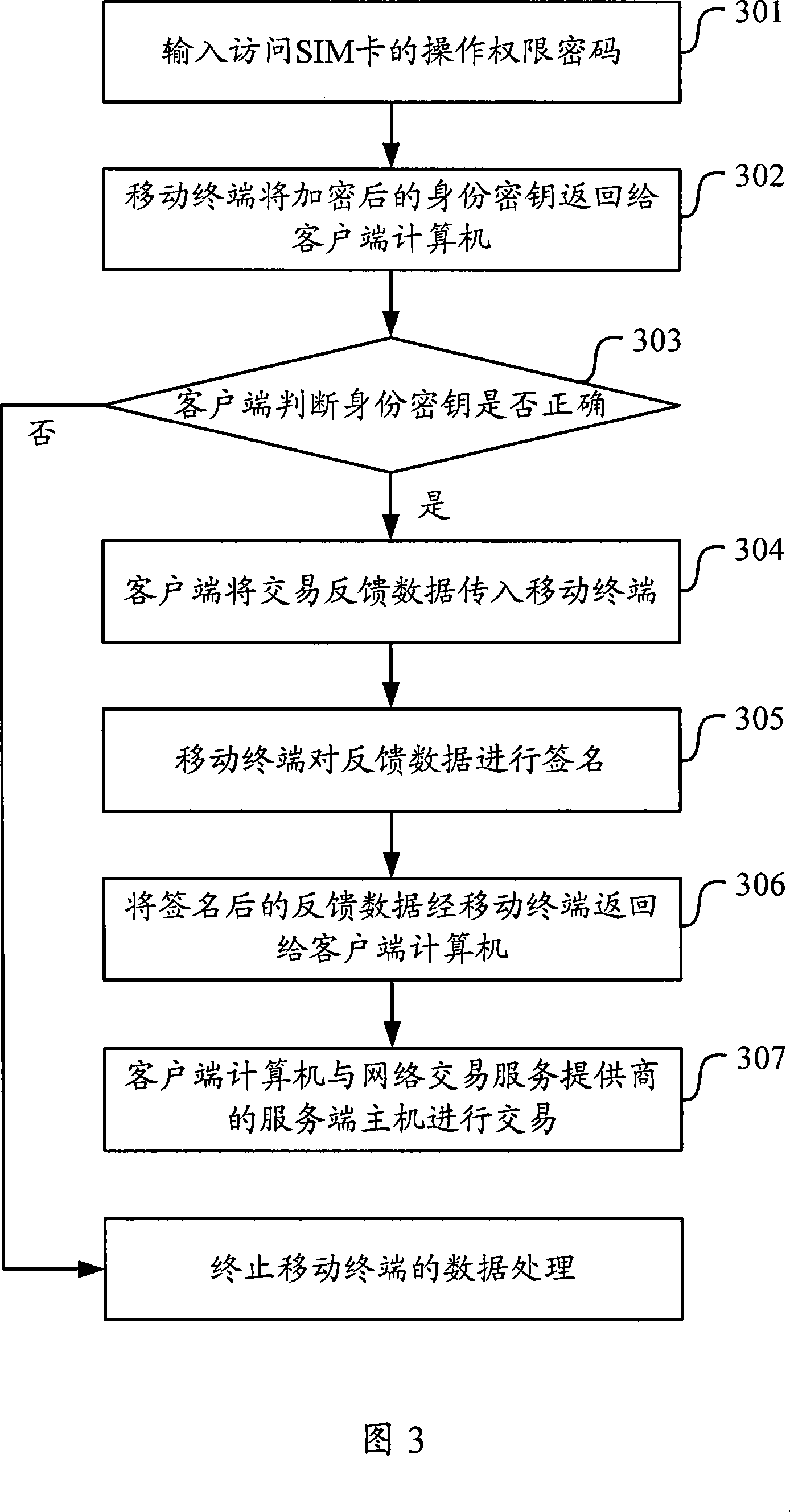
Data transaction processing method and apparatus
ActiveCN101222333AOvercome the hidden danger of interceptionEnsure safetyUser identity/authority verificationRadio/inductive link selection arrangementsOperational systemIdentity recognition
The invention discloses a data transaction processing method and a device thereof, including that after a service end receives a transaction request submitted by a client end through the internet, the service end sends data including identification data and transaction feed-back data, which need to be identified and fed back to a movable terminal by the client end; after the movable terminal receives data needing to be identified and fed back, the identification data are verified according to identity key in the movable terminal user identity recognition module card, which is offered in advance, after the verification is passed, the feed-back data is acquired after processing according to transaction feed-back data content; after a user identity recognition module card operating system makes a signature on the feed-back data, the feed-back data is fed back to the service end by the client end; the signature of the feed-back data is verified according to a signature key in the service end, which is offered by the movable terminal user in advance, after the verification is passed, the feed-back data is processed based on the feed-back data content. By utilizing the invention, the identity certification and the transaction certification problems in the network transaction are resolved, and the safety of the client end in the network environment is ensured.
Owner:BEIJING WATCH DATA SYST
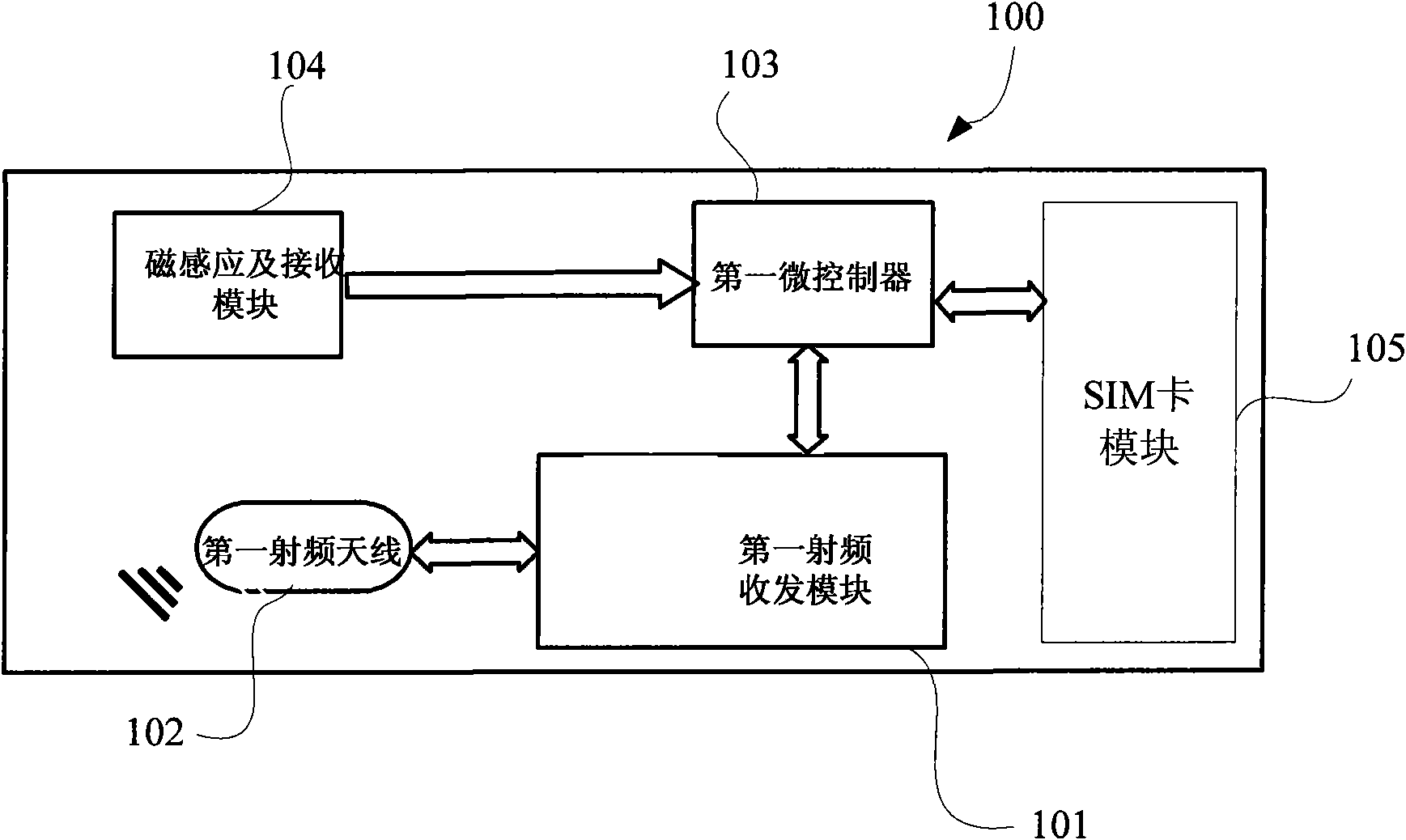
Radio frequency device, radio frequency card reader and related communication system and communication method
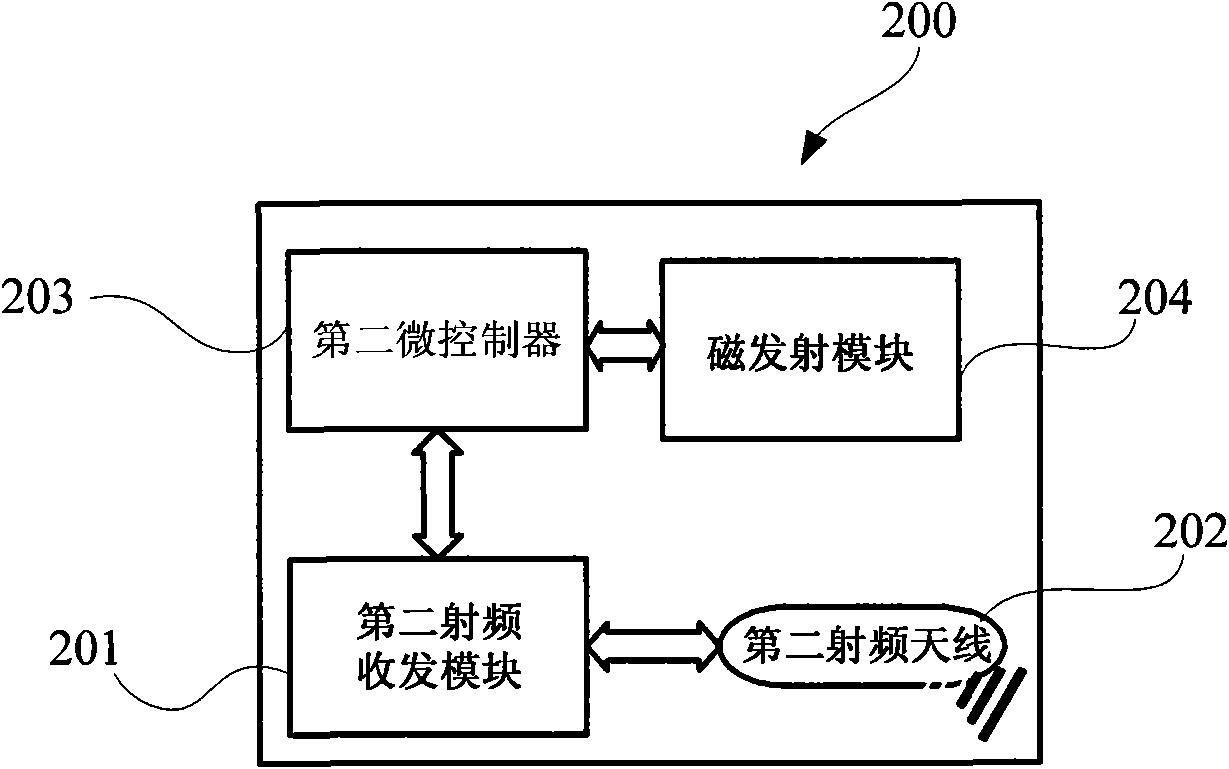
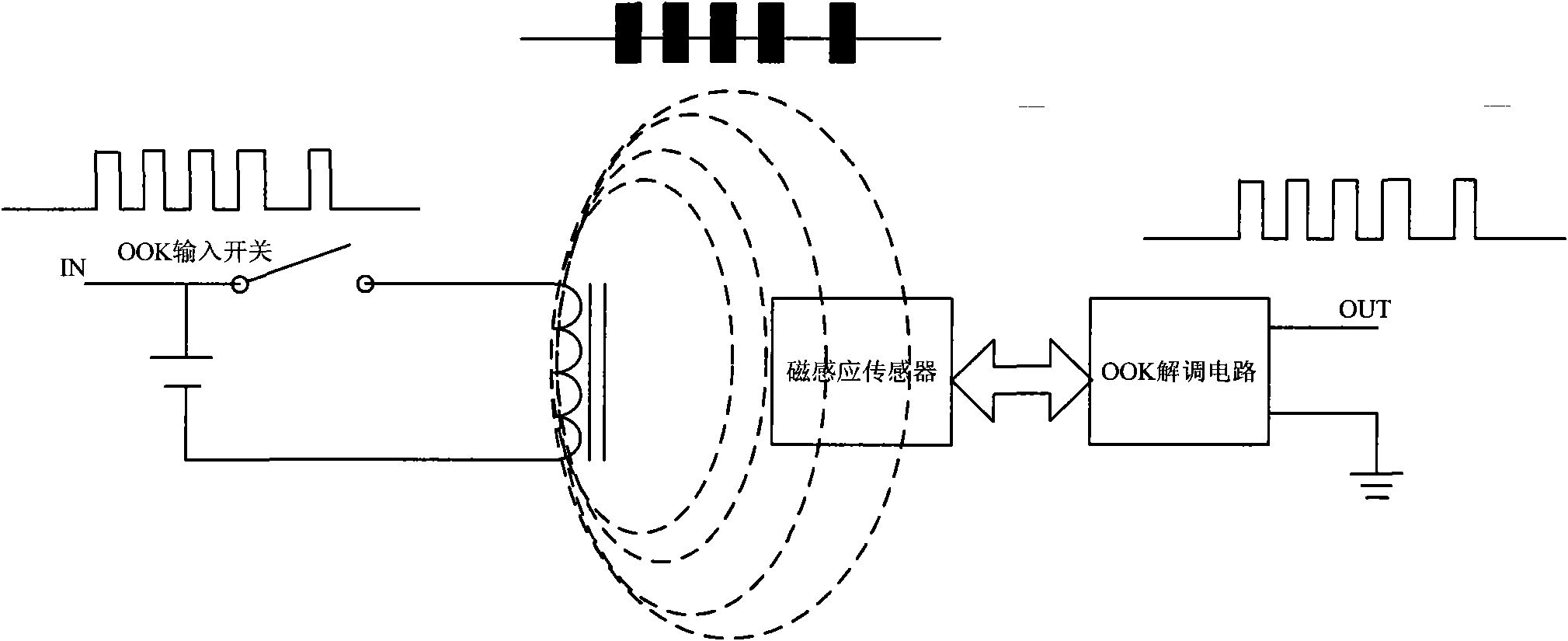
ActiveCN102096836AOvercoming the distance control problemAuthentication is reliableSensing record carriersTransmissionSecure communicationLow speed
The invention relates to the field of radio frequency secure communication and provides a radio frequency device, a radio frequency card reader corresponding to the radio frequency device, and a communication system and a radio frequency secure communication method which use the radio frequency device and the radio frequency card reader. The radio frequency device comprises a radio frequency receiving and transmitting module, a radio frequency antenna and a magnetic induction and receiving module; and the radio frequency card reader comprises a radio frequency receiving and transmitting module, a radio frequency antenna and a magnetic transmitting module. Two communication channels, namely a first low-speed unidirectional communication channel with a stable and controllable distance and asecond high-speed communication channel, with different characteristics are available between the radio frequency device and the radio frequency card reader, wherein the first communication channel is formed by communicating with a magnetic field and is used for transmitting a small data volume of information for identity authentication so as to prevent malicious interference and attack; the second communication channel is formed by using the radio frequency receiving and transmitting module and is used for finishing the identity authentication and a main transaction process; and through the system and the communication method, near field secure communication with a controllable distance can be realized better.
Owner:NATIONZ TECH INC
Data storage and sharing system
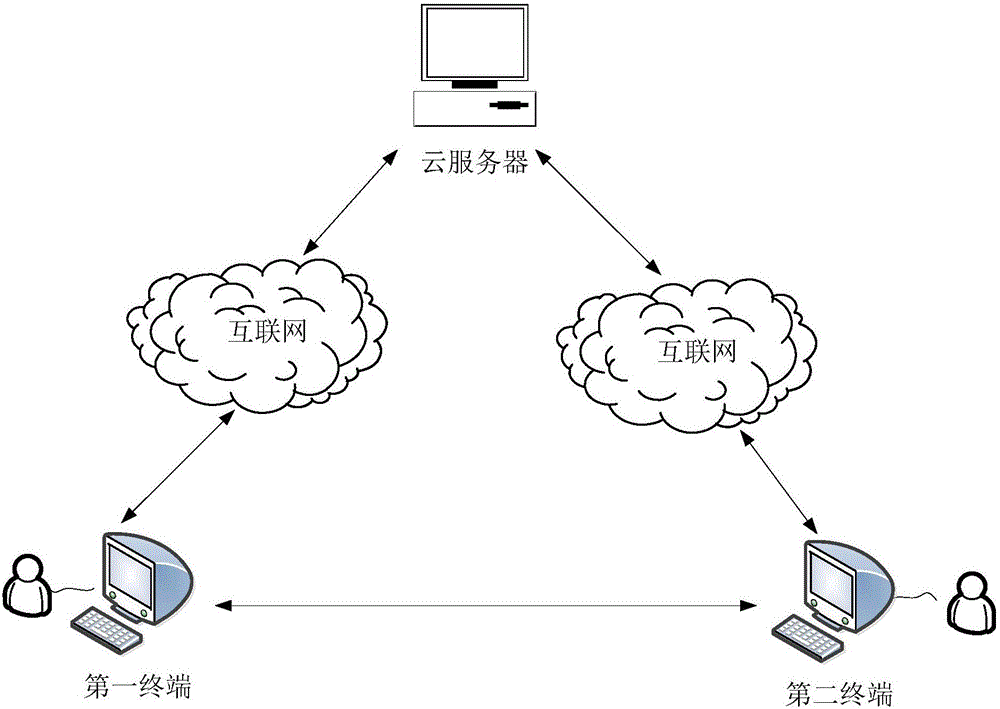
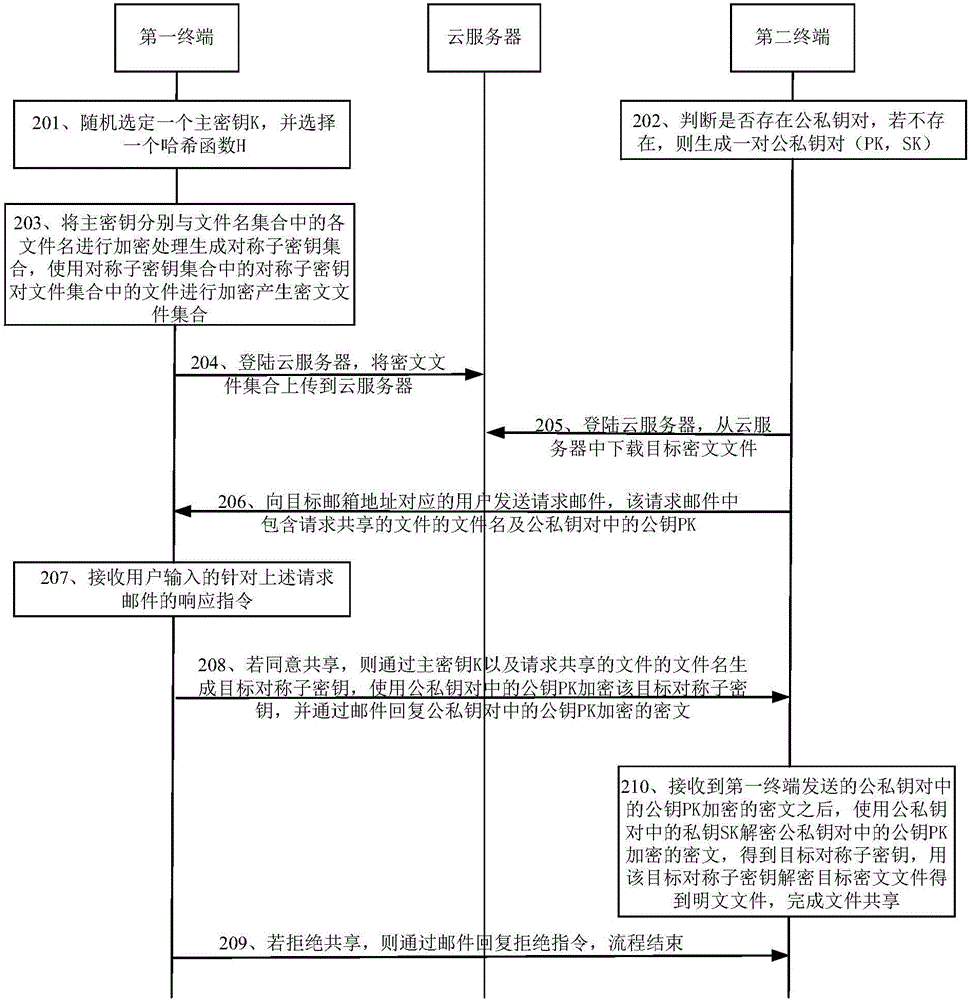
ActiveCN106453612AImplement secure cloud storageEnable secure sharingData switching networksPlaintextCiphertext
The invention discloses a data storage and sharing system, comprising a first terminal, a cloud server and a second terminal, wherein the first terminal is used for encrypting main keys and file names to generate a symmetrical sub-key set, then encrypting files to be encrypted by using symmetrical sub-keys to generate an encrypted file set, and uploading the encrypted file set; the second terminal is used for downloading a target encrypted file from the cloud server, and sending a requested mail to a target mail address; the first terminal is further used for, when a user agrees with sharing files, sending the encrypted target symmetrical sub-keys to the second terminal via a mail, and when the user does not agree with sharing, replying a rejection instruction via a mail; and the second terminal is further used for, after receiving the encrypted target symmetrical sub-keys, decrypting the encrypted target symmetrical sub-keys to obtain the target symmetrical sub-keys, and decrypting the target encrypted file by using the target symmetrical sub-keys to obtain a decrypted file, thus completing file sharing. The system can improve the data storage and sharing security.
Owner:HUAZHONG UNIV OF SCI & TECH
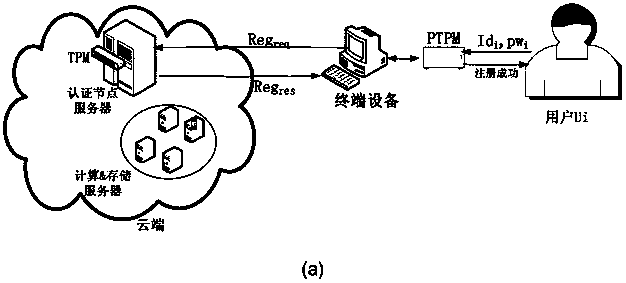
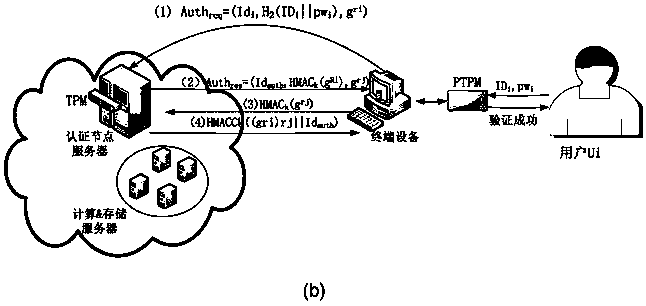
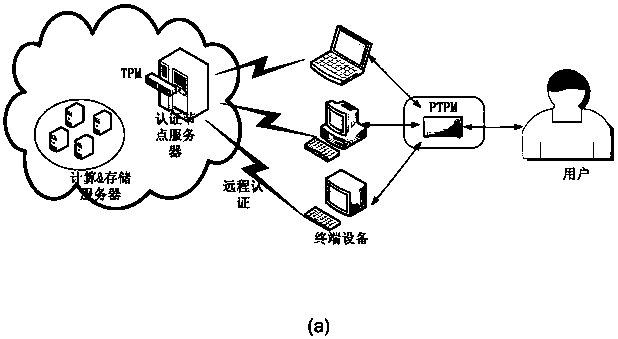
Two-factor authentication method based on portable TPM (PTPM) and certificateless public key signature for cloud
InactiveCN107733657AImprove computing efficiencyMake sure it's trueKey distribution for secure communicationPublic key for secure communicationPasswordTerminal equipment
The invention discloses a scheme for implementing two-way identity authentication between a user and cloud by applying a portable TPM (PTPM) and certificateless public key cryptography to a cloud environment, aiming at solving the security problems and deficiencies existing in identity authentication between the user and the cloud in a current cloud environment in a cloud computing mode. Comparedwith existing schemes, a new scheme has the following advantages: on the basis of realizing the uniqueness of user and cloud identities through the establishment of an identity management mechanism, firstly, the PTPM is adopted to ensure the security and credibility of a terminal platform and ensure the authenticity and correctness of authentication results between the cloud and the user, and moreover, the user is supported to use any terminal equipment to complete an identity authentication process with the cloud; secondly, the new scheme implements a 'password + key' two-factor authentication process based on a certificateless public key signature algorithm; and finally, the proposed scheme can significantly improve the computing efficiency of identity authentication between the user andthe cloud while ensuring the security of EUF-CMA.
Owner:SHENYANG NORMAL UNIV
Rail transportation ticket-card processing intelligent system and data encryption auditing method
InactiveCN101826219AImprove consistencyGuaranteed to be strictly enforcedRegistering/indicating time of eventsTicket-issuing apparatusServices computingTransaction log
The invention discloses a rail transportation ticket-card processing intelligent system, which comprises a sorting center and an automatic ticketing system for a plurality of rail transportation lines. The sorting center comprises a set of service computers, and the automatic ticketing system comprises a set of equipment computers and a ticket-card processing intelligent terminal connected with the equipment computers; and the card processing intelligent terminal is used for processing of ticket transaction flow, issuing of single ticket transaction keys, online authentication of value-stored ticket recharge and generation and verification of transaction logs. The sorting center also comprises an encryption computer which is connected with the ticket-card processing intelligent terminal and is used for receiving an encryption certification request of the ticket-card processing intelligent terminal; and the equipment computers are used for transmitting service commands to the ticket-card processing intelligent terminal and receiving the service command processing result. The modification of the ticket-card processing service is realized through the online update function of the parameters or ticket-card processing programs and the maintenance cost due to the updated card processing programs is reduced. The invention also discloses a data encryption auditing method.
Owner:NANJING PANDA INFORMATION IND +1
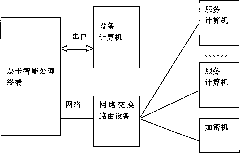
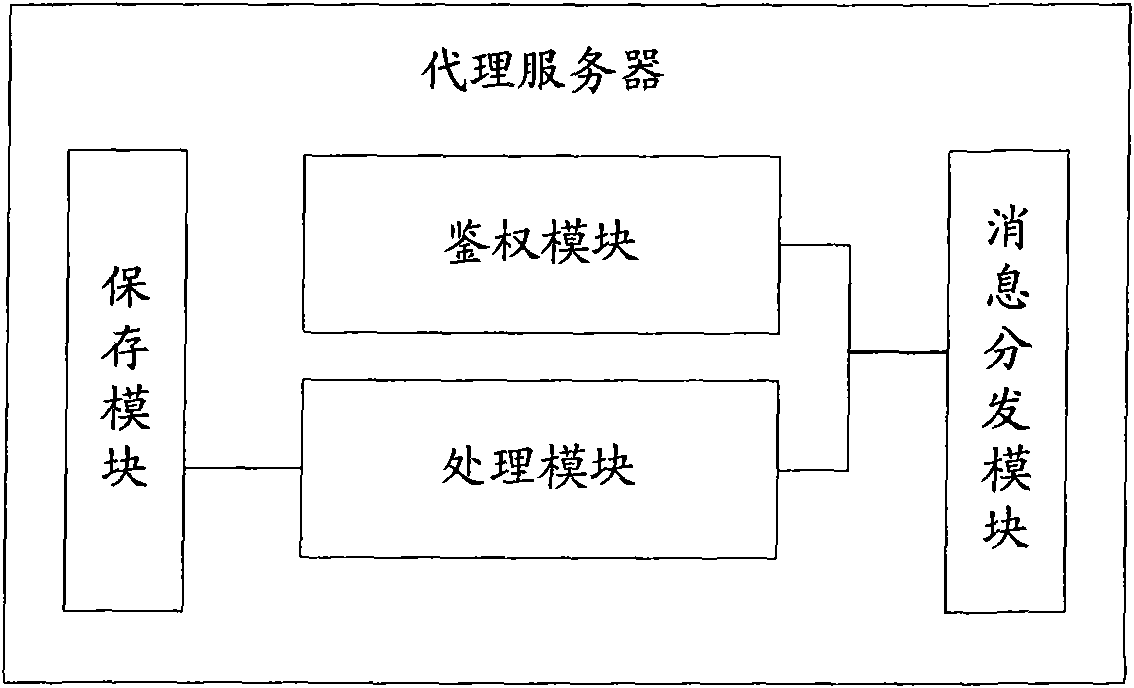
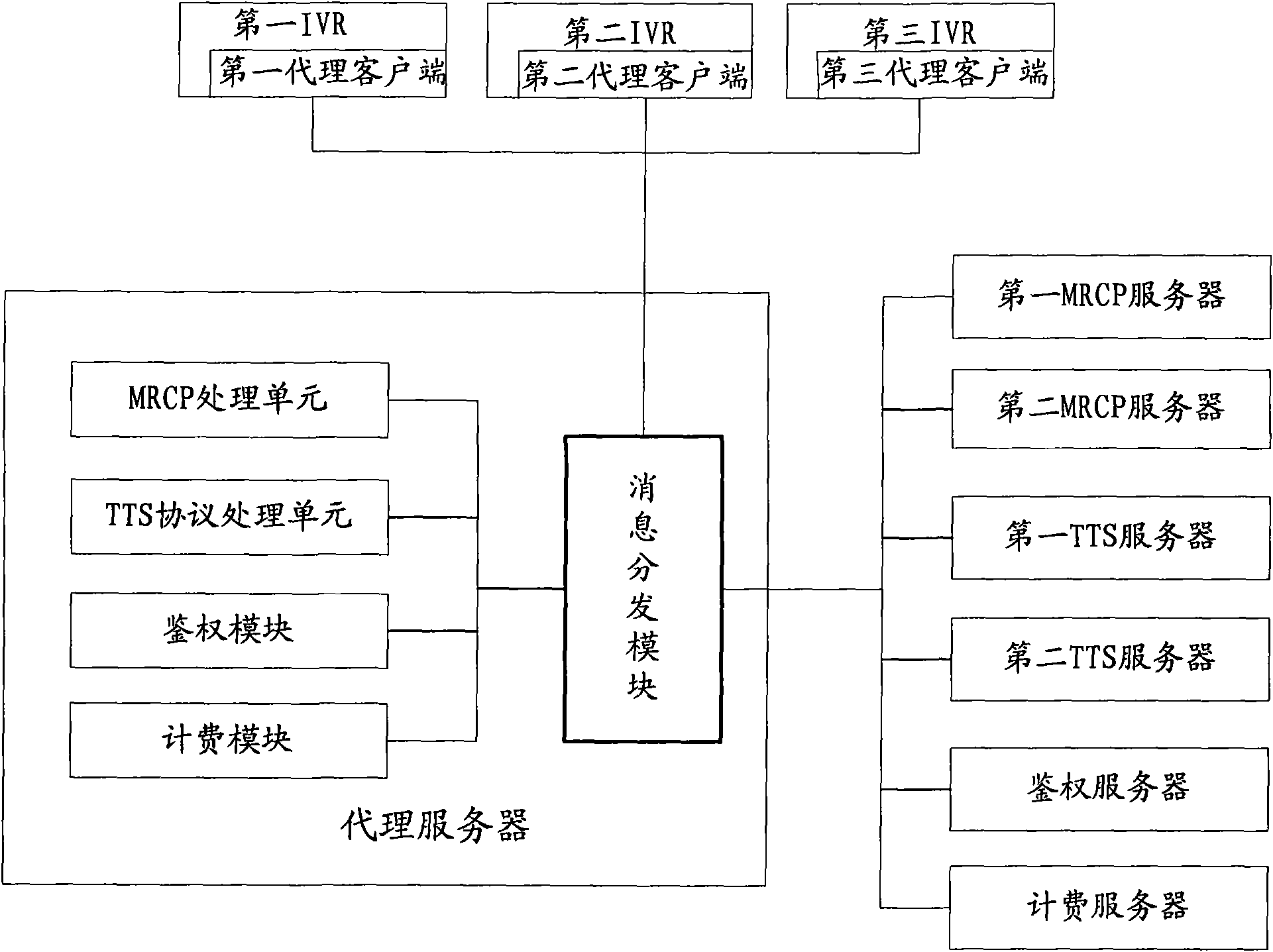
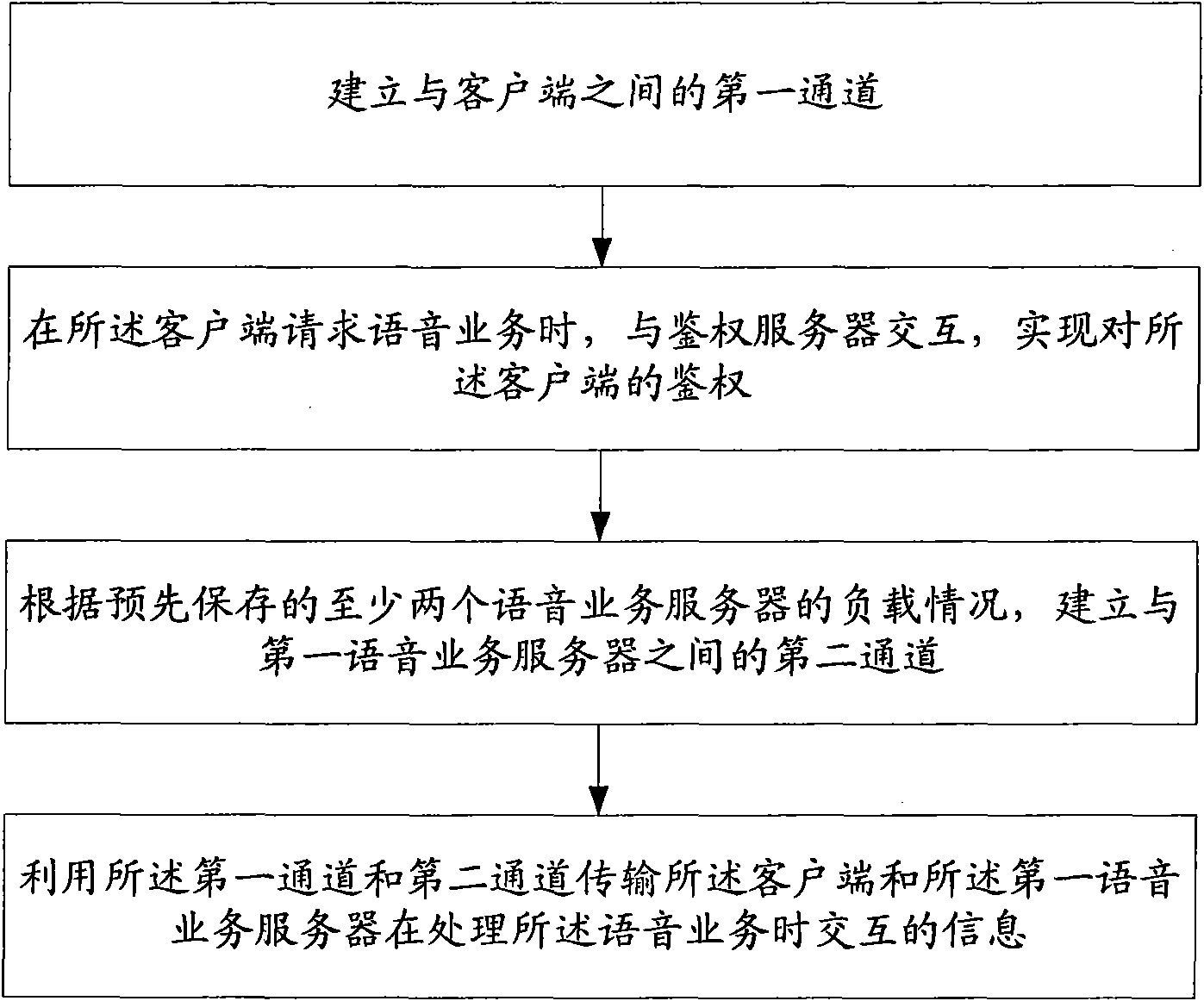
Comprehensive voice resource platform proxy server and its data processing method
InactiveCN101677329AEasy accessSolve authentication problemsError prevention/detection by using return channelSpecial service for subscribersNetwork agentAuthentication server
The invention provides a comprehensive voice resource platform proxy server and its data processing method, wherein the method includes: the proxy server establishing a first channel to the client; when the client requests voice service, the proxy server interacting with an authentication server to realize authentication to the client; the proxy server establishing a second channel with a first voice service server, based on the preserved load condition of at least two voice service servers; after the first and second channels are established, the proxy server transmitting the interactive information of the client and the first voice service server during processing of the voice service by the first and second channels. The invention combines the widely used network proxy server technology and the TTS / ASR technology, balances loads based on the routing of request types, and realizes quick access of TTS / ASR voice resource platform on the basis of load balancing, to realizes the performance of the comprehensive voice platform.
Owner:ZTE CORP
Network access method, system and authentication server
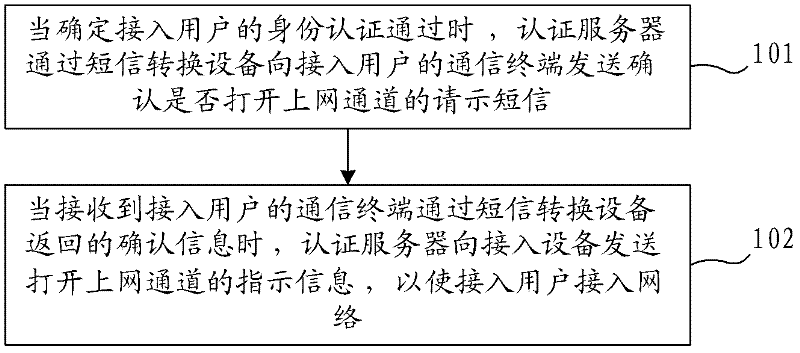
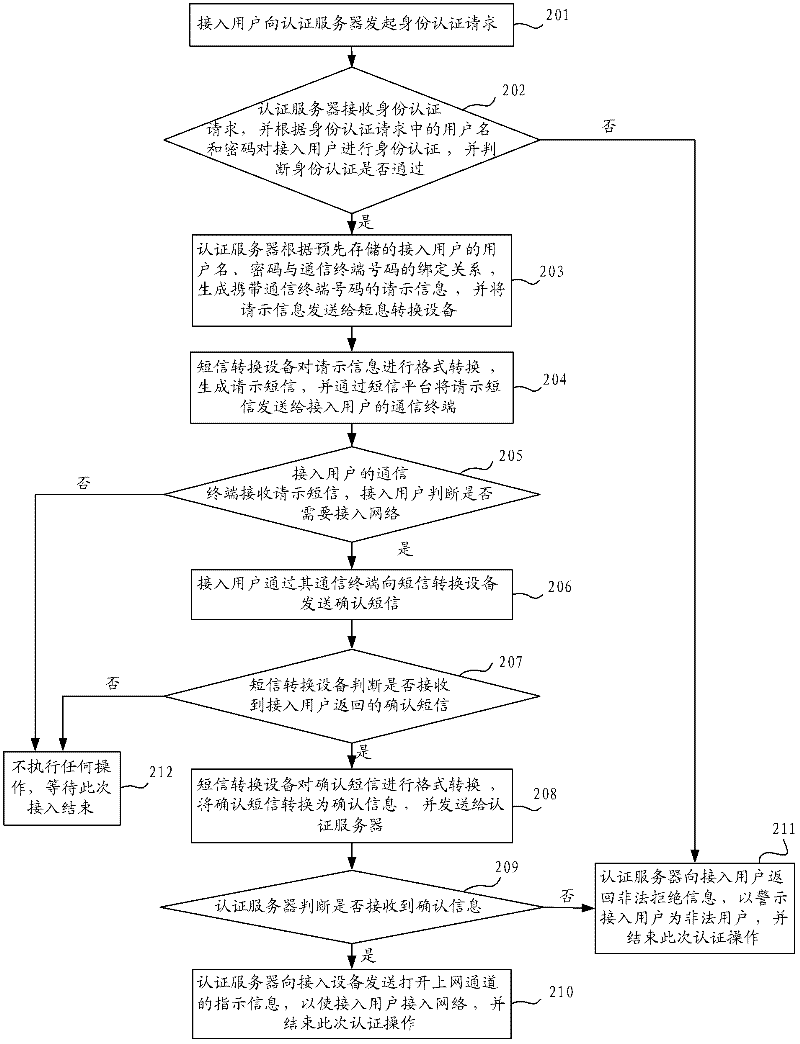
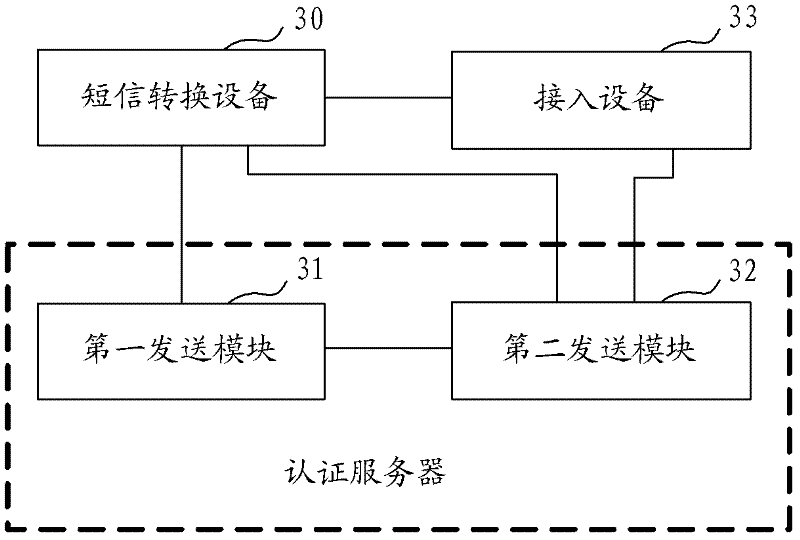
ActiveCN102264050AReduce the probability of attackImprove securityMessaging/mailboxes/announcementsSecurity arrangementAccess methodPassword
The invention provides a network access method, a network access system and an authentication server. The network access method comprises the following steps that: when an access user passes the identity authentication, the authentication server transmits a request short message for confirming whether an access channel is opened to a communication terminal of the access user through short-message conversion equipment; when a confirmation message returned by the communication terminal of the access user through the short-message conversion equipment is received, the indication information of opening the access channel is transmitted to the access equipment so that the access user accesses the network. By adoption of the technical scheme, the problem that the illegal user uses stolen user names and passwords for identity authentication can be solved, the probability of network attack by the illegal user is reduced and the safety of the network is improved; in addition, compared with the prior art, the technical scheme has the advantages of simplicity in access process and lower access cost.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
Method for implementing wireless network safety communication
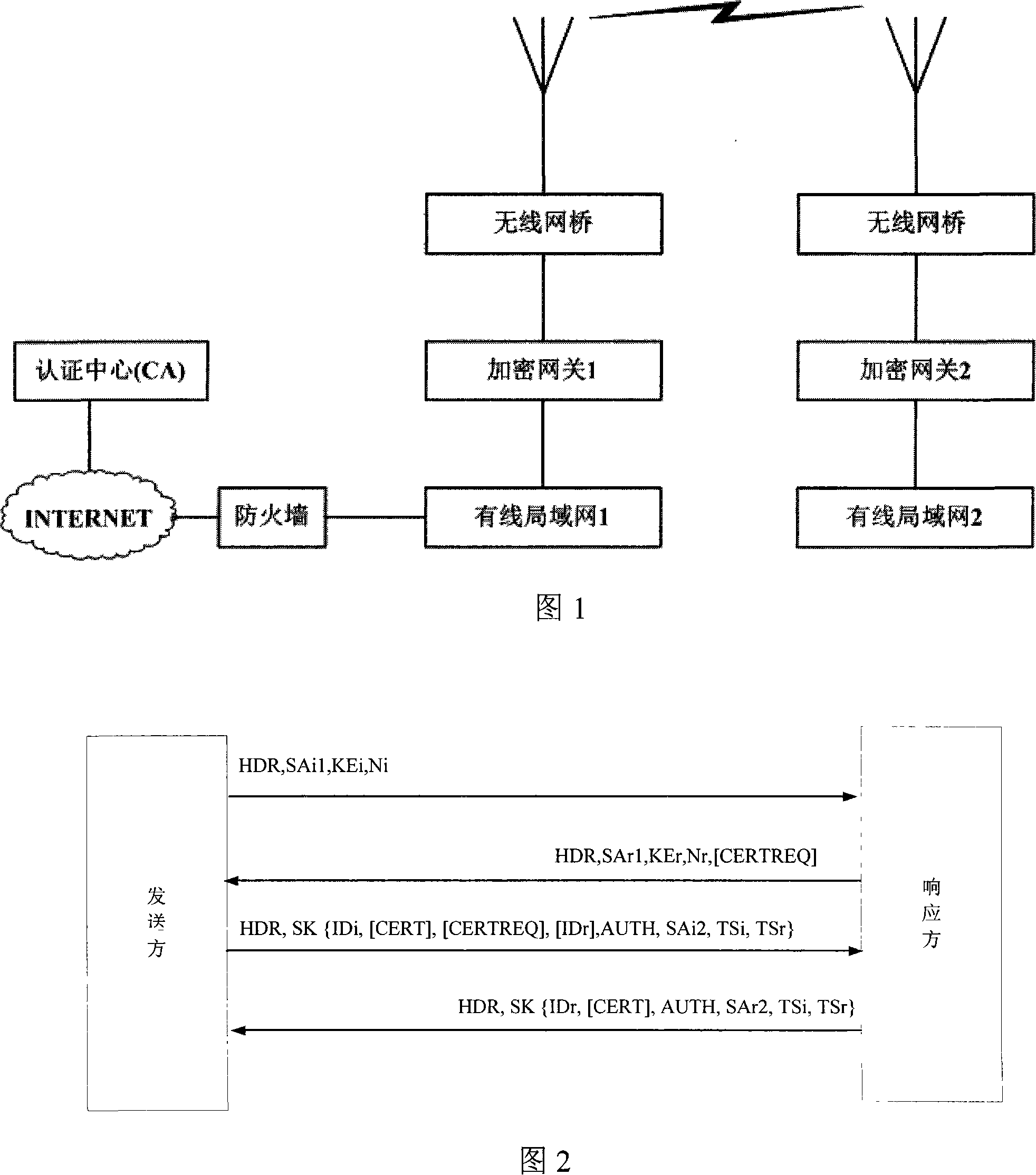
InactiveCN101119368AReduce overheadLow costUser identity/authority verificationNetworks interconnectionData integritySecure transmission
The invention belongs to the safety technical field of computer networks and discloses an achieving method of the safe communication of a wireless network. The achievement on the method bases on the identification of identity and the processed innovation of IKEV2 protocol. The invention adds an encrypted gateway between a wireless bridge and a wire local area network. The communicating physical body in the method has two encrypted keys (a common key and a private key). Each physical body has an incommon private key. The senders of the message adopt the private key to sign and the receivers carry out inspection with the identity of the senders (namely the common key). The communicating physical body does not need the signature of the identifying center (CA) to the certificates, and thus saves the computing capacity of the communicating physical bodies. The method included in the invention ensures the transmitting safety of the information for the wireless network communication solves the problems such as data encryption, identity identification, maintenance on the integrity of the data and management on the encryption, with the safe transmission of the business data.
Owner:BEIJING JIAXUN FEIHONG ELECTRIC CO LTD
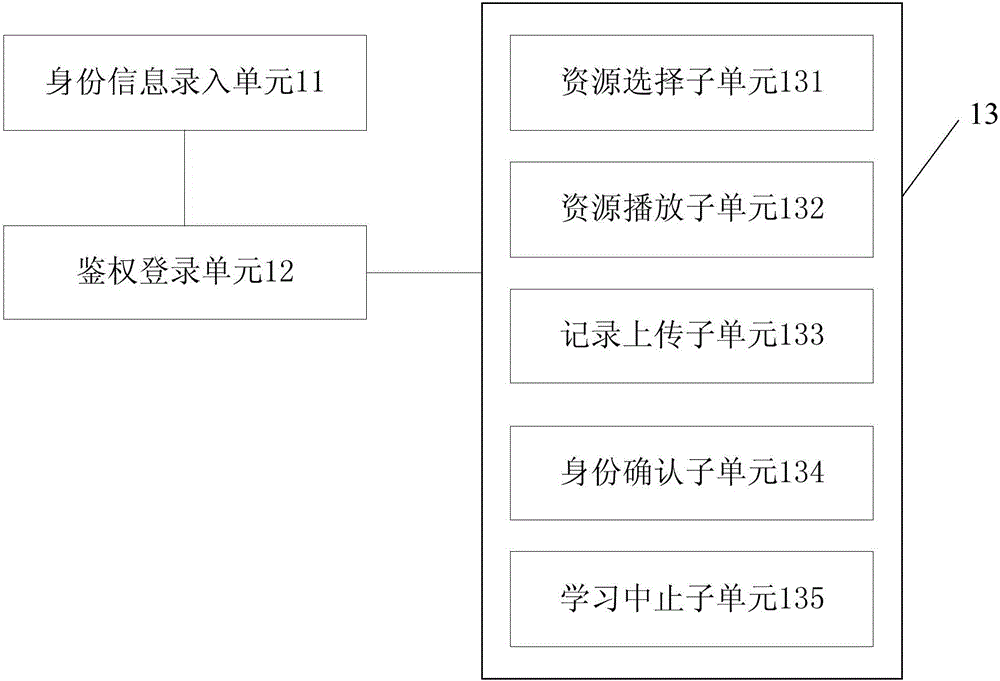
Mobile learning system based on fingerprint mobile phone
InactiveCN105868612AFix security issuesSolve authentication problemsData processing applicationsDigital data authenticationComputer terminalOnline learning
The invention discloses a mobile learning system based on a fingerprint mobile phone. The mobile learning system comprises the fingerprint mobile phone, an interaction learning terminal, a fingerprint server and an educational resource cloud server. The fingerprint mobile phone is used for being in communication with the interaction learning terminal after the identity information of a user passes authentication and sending the identity information and a learning resource obtaining request to the interaction learning terminal. The interaction learning terminal is used for sending identity information and a learning resource obtaining request to the learning resource cloud server. The educational resource cloud server is used for judging whether the fingerprint information in the identity information coincides with finger information stored in the fingerprint server; if yes, the educational resource cloud server sends learning resources to the interaction learning terminal so as to be transmitted to the fingerprint mobile phone through the interaction learning terminal; If not, the educational resource cloud server sends alarm information to an manager and rejects the learning resource obtaining request. By the adoption of the mobile learning system, online learning resource safety and identity authentication problems can be solved, and learning efficiency and examining fairness are improved.
Owner:GUANGZHOU JINGXIN HERB GARDEN INFORMATION TECH CO LTD
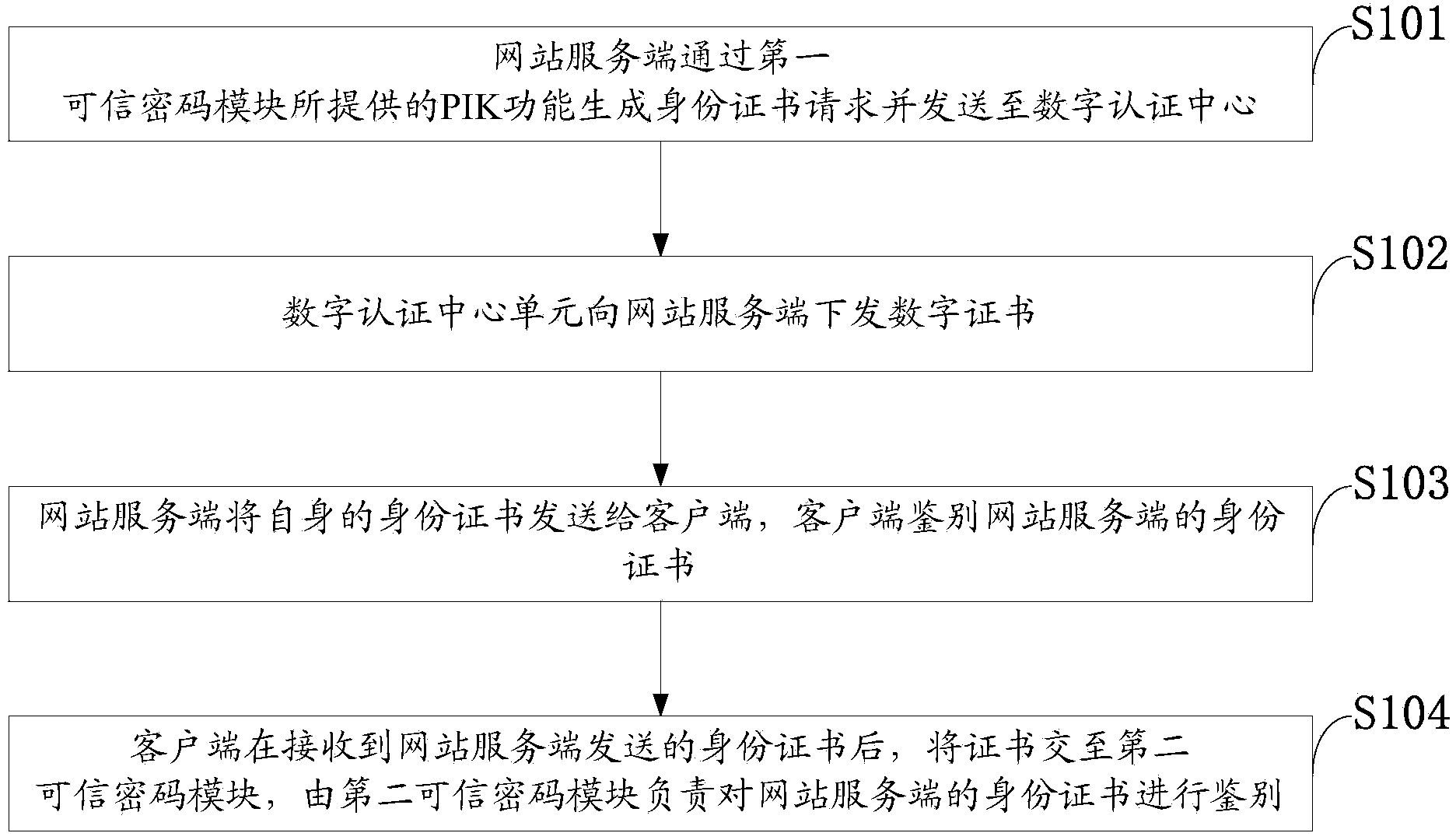
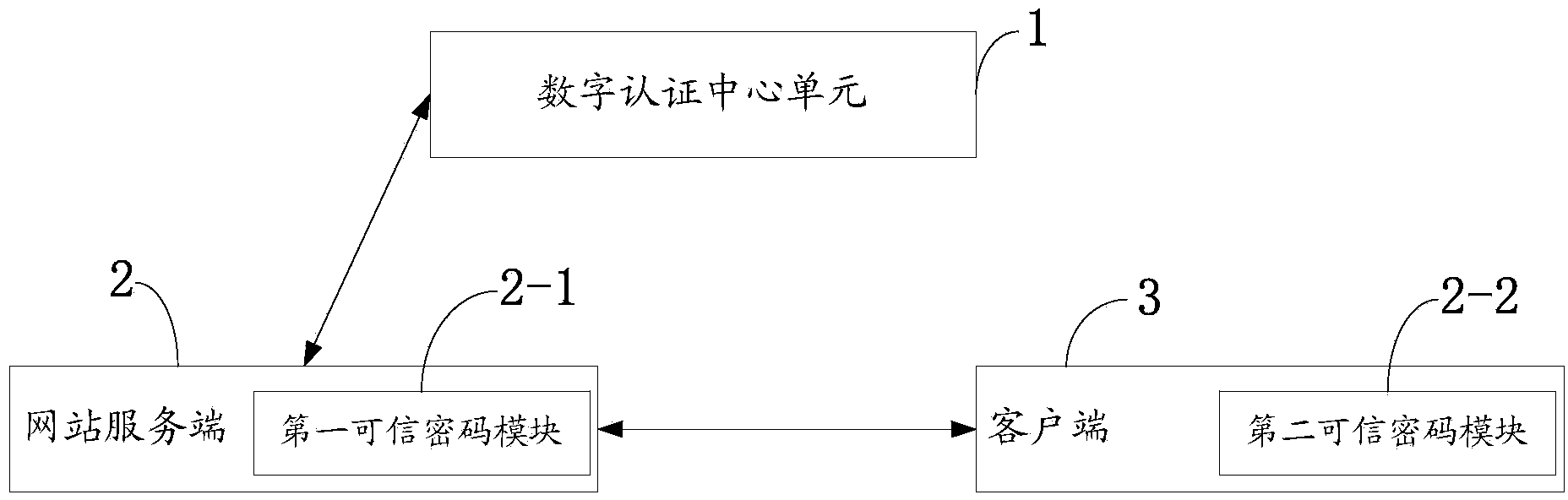
Method and system for authenticating identity of power grid website based on trusted crypto modules
InactiveCN103532961AImprove securityReliable authentication methodUser identity/authority verificationClient-sidePower grid
The invention discloses a method and a system for authenticating the identity of a power grid website based on trusted crypto modules. The method comprises the following steps: producing an identity certificate request and sending the identity certificate request to a digital authentication center unit by a website service-side through a PIK function which is provided by a first trusted crypto module; issuing a digital certificate to the website service-side by the digital authentication center unit; sending the self identity certificate to a client-side by the website service-side, and identifying the identity certificate of the website service-side by the client-side; identifying the identity certificate of the website service-side by a second trusted crypto module after the identity certificate which is sent by the website service-side is received by the client-side. The system comprises the digital authentication center unit, the website service-side, the first trusted crypto module, the client-side and the second trusted crypto module. The identity authentication of the website and the protection over user sensitive information are realized through the provision of a reliable user certificate issuing and identity authenticating method under the condition of realizing the bidirectional identity authentication of the power grid website and the client-side user.
Owner:STATE GRID CORP OF CHINA +2
High-efficiency distributed parallel authentication system
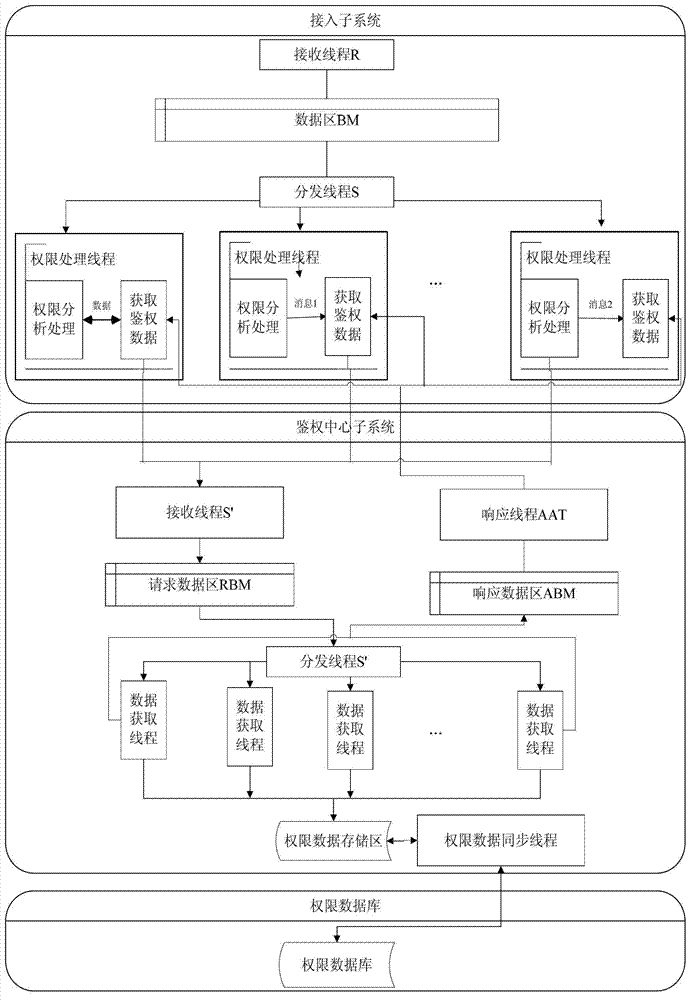
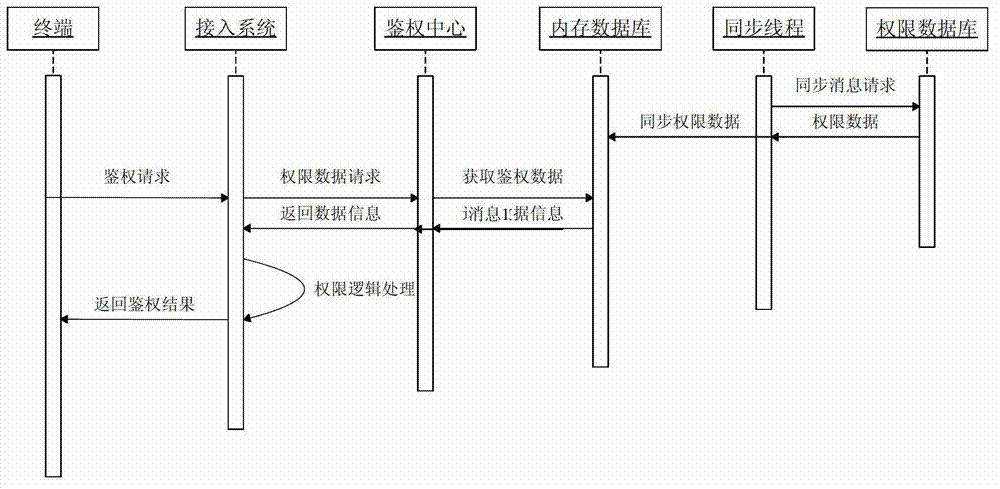
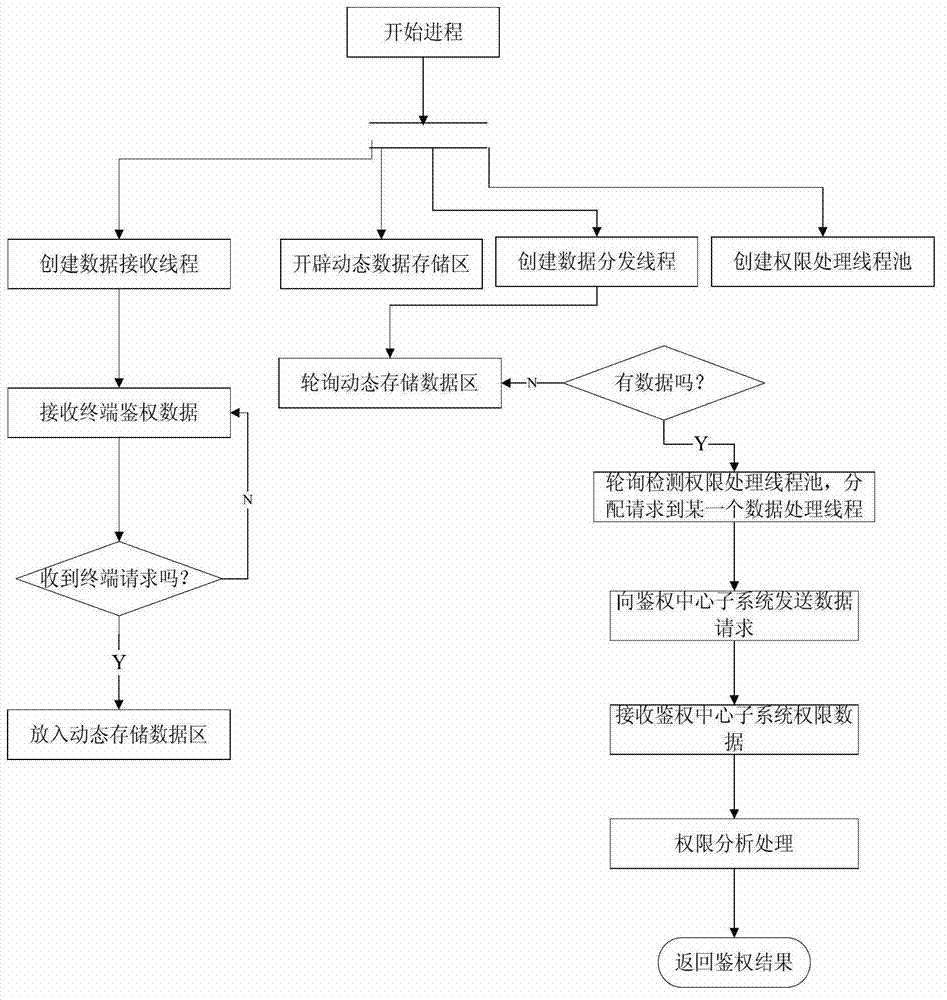
ActiveCN102831017ASolve authentication problemsSolve bottlenecksResource allocationData synchronizationAuthentication system
The invention discloses a high-efficiency distributed parallel authentication system. The authentication system is connected with an authority database; when the system is started up, a thread pool and an authority data synchronism thread are created, a section of authority data storage region is arranged in an internal storage, wherein thread pool contains a plurality of authority processing threads; the authority data synchronism thread regularly synchronizes authority data in the authority database to the authority data storage region; different authority processing threads are distributed for authentication requests sent by different terminals to process the authentication requests; when the authority processing threads processes the authentication requests, corresponding authority data is firstly searched from the authority data storage region, if no corresponding authority data exists in the authority data storage region, corresponding authority data is acquired from the authority database directly and is stored in the authority data storage region; and then the authentication requests are analyzed and processed according to the authority data; and finally an authority result is output. The authentication problem existing when multiple terminals access the system in parallel can be effectively solved.
Owner:HOHAI UNIV
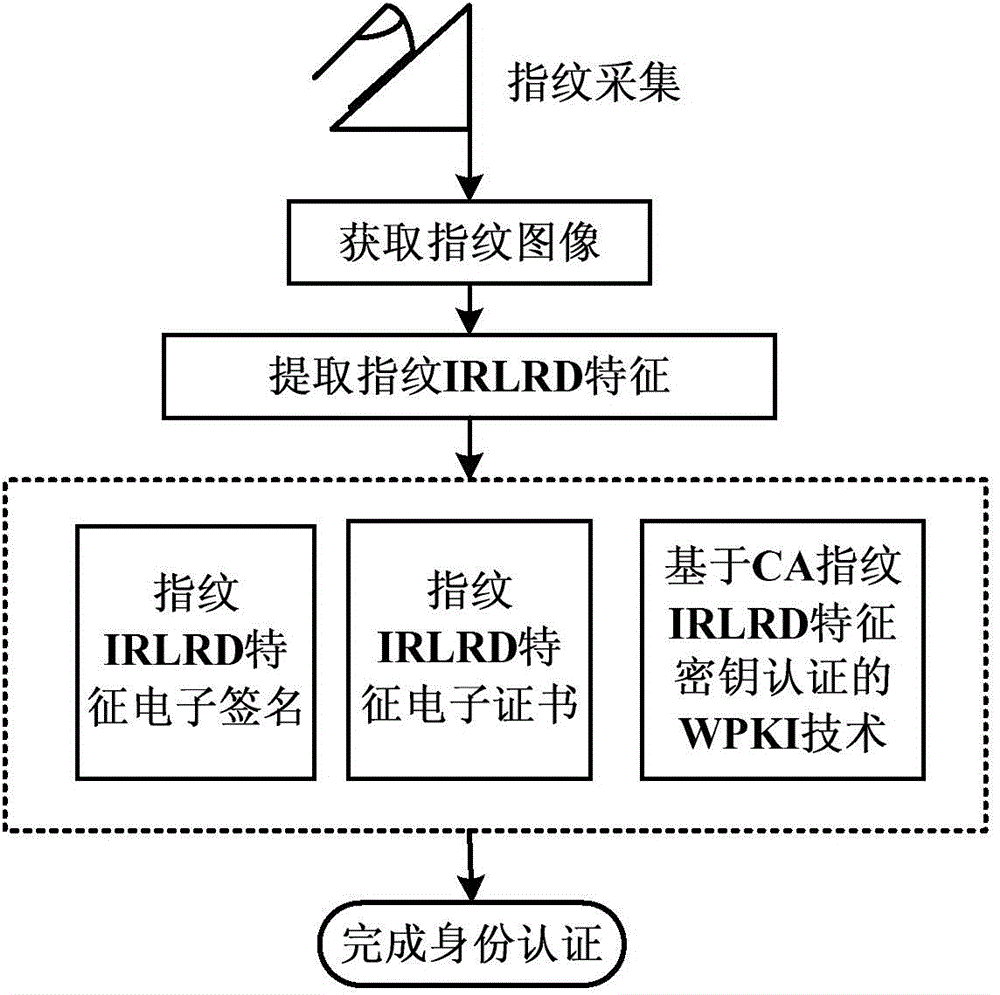
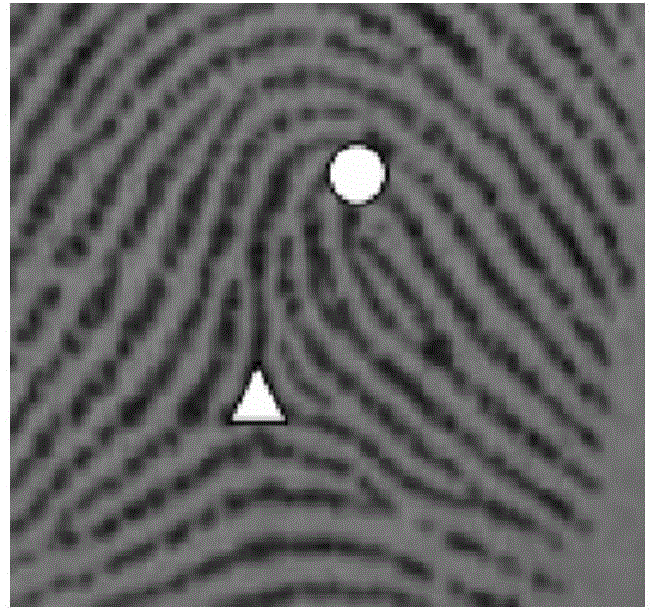
Fingerprint IRLRD characteristic encryption method, and mobile payment system and method based on encryption method
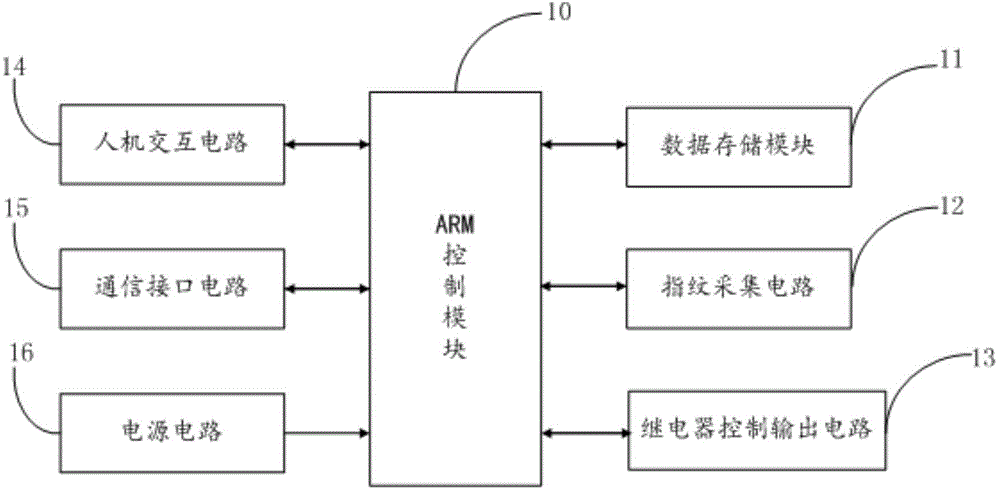
InactiveCN104899737ASolve the problem of self-certificationEnsure safetyProtocol authorisationCommunication interfaceMobile payment
The present invention discloses a fingerprint IRLRD characteristic encryption method, a mobile payment system and a mobile payment method based on the fingerprint IRLRD characteristic encryption method. The mobile payment system comprises an ARM control module, a data storage module, a fingerprint collection circuit, a human-machine interaction circuit, a communication interface circuit, a relay control output circuit, and a power supply circuit for supplying power to all the circuits. The ARM control module implements fingerprint IRLRD characteristic encrypted identity authentication by encrypting an ARM fingerprint IRLRD characteristic. Compared with the prior art, the invention has the following advantages: the mobile payment system obtains a user fingerprint image and extracts a fingerprint IRLRD characteristic as a key; implements secure transaction of mobile payment by multiple identity authentication protection; prevents payment information from being attacked and broken by a hacker; stops a security crisis that payment information is tampered, leaked or falsified during mobile payment, and ensures orderly proceeding of the mobile payment.
Owner:ANHUI XINHUA UNIV
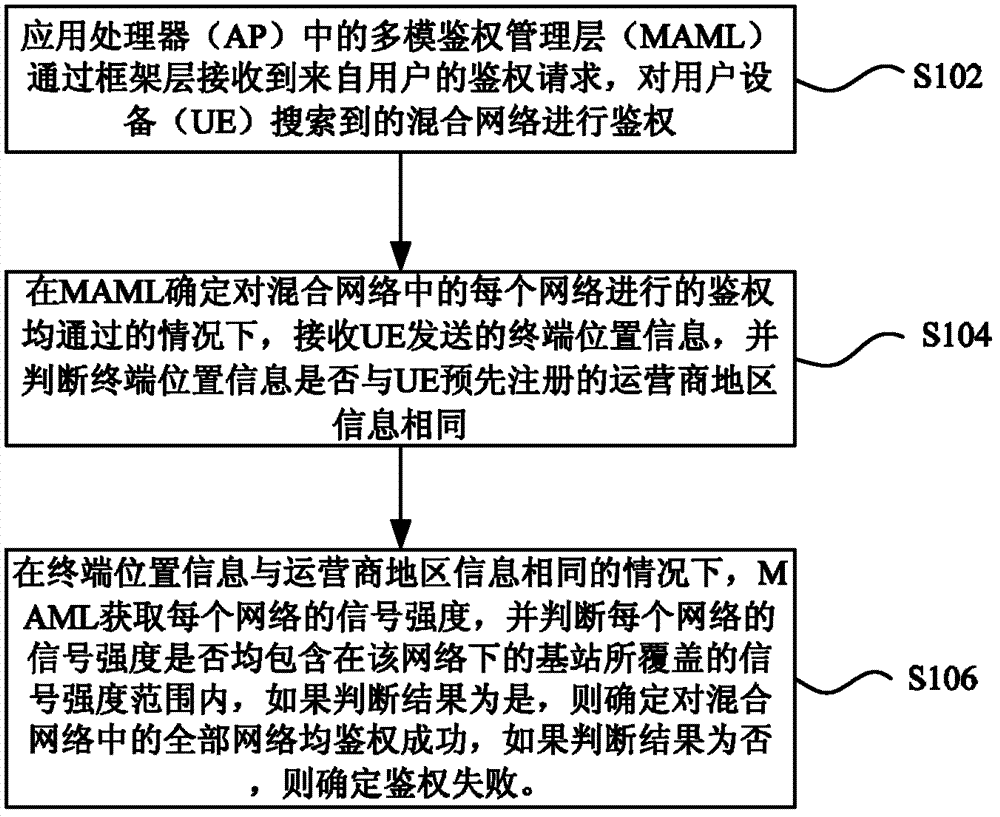
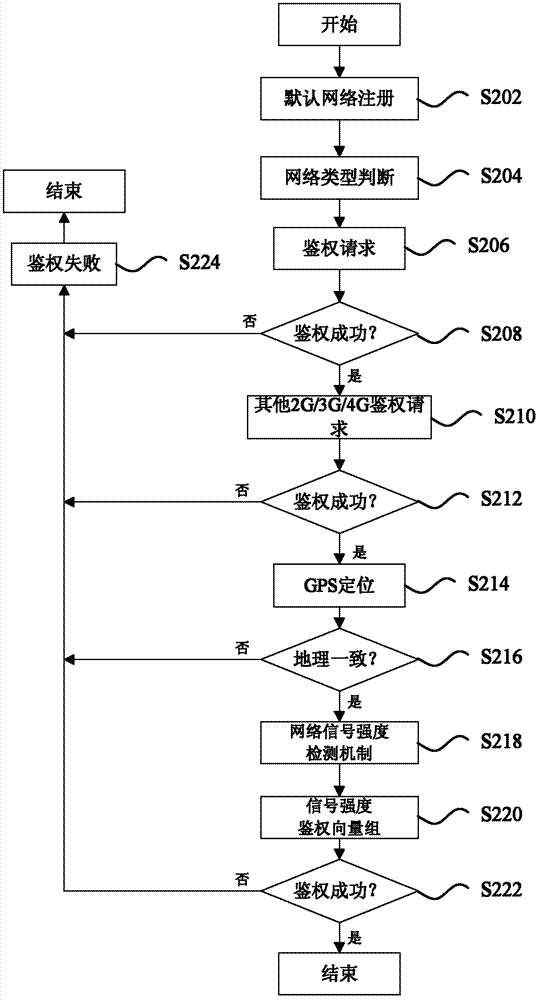
Single-card multi-mode multi-operator authentication method and device
InactiveCN102769850ASolve authentication problemsEnsure safetyTransmissionSecurity arrangementMix networkMulti operator
The invention discloses a single-card multi-mode multi-operator authentication method and a single-card multi-mode multi-operator authentication device. The method comprises the followings steps of: receiving an authentication request from a user through an MAML in an AP (Access Point), and authenticating a mixing network found by UE (User Equipment); under the condition of confirming the authentication of each network in the mixing network to pass, receiving terminal position information transmitted by the UE, and judging whether the terminal position information is the same as operator area information pre-registrated by the UE or not; and when the terminal position information is the same as operator area information pre-registrated by the UE, acquiring signal strength of each network through the MAML, and judging whether the signal strength of each network is contained in a signal strength range covered by a base station under the network or not, if yes, confirming that all networks in the mixing network are authenticated successfully, otherwise, confirming to be fail. Through the method and the device, the safety in using an SIM (Subscriber Identity Module) card by a valid user and secure network service are ensured, and the effect of favorable network operation of operators is ensured.
Owner:ZTE CORP
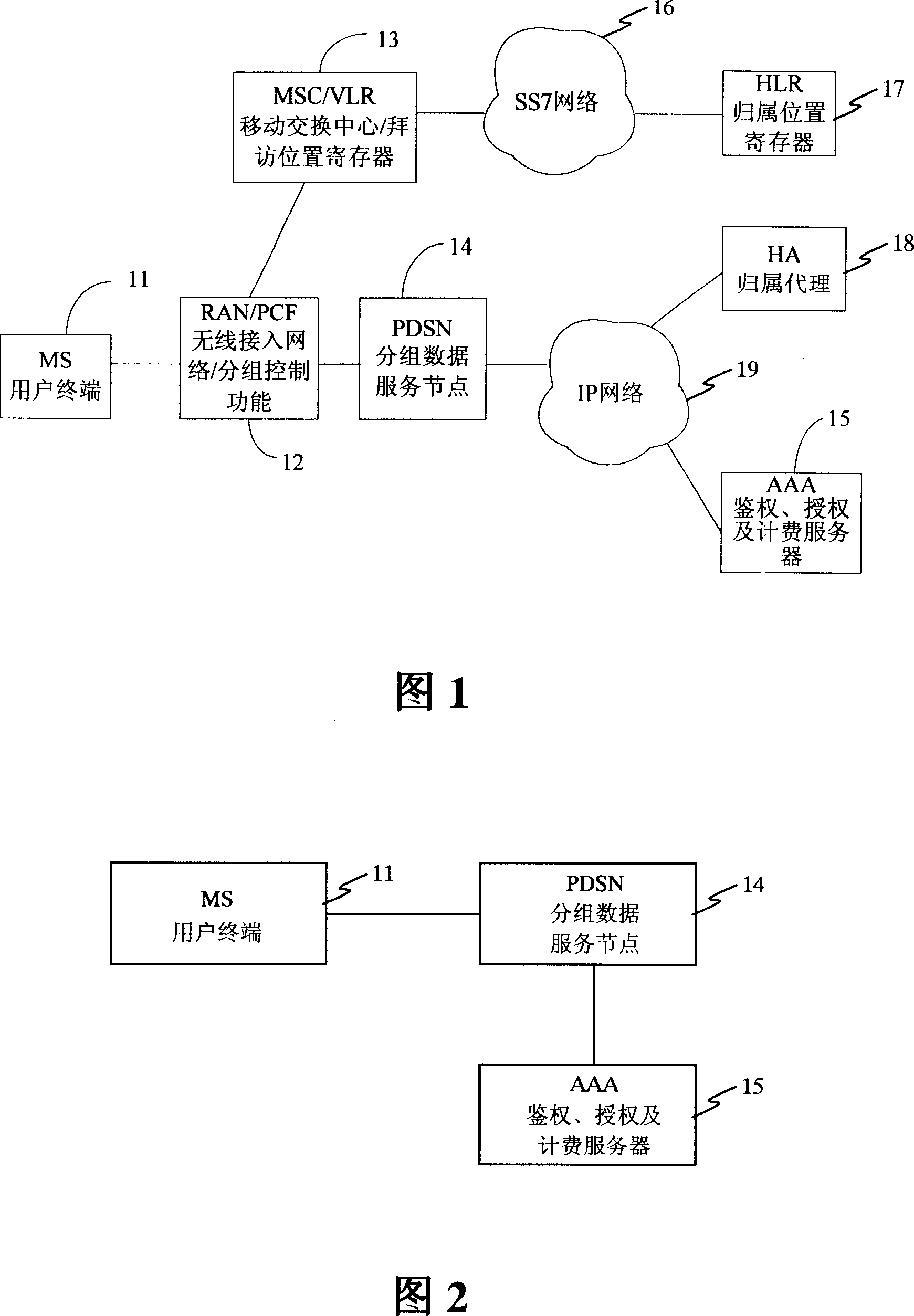
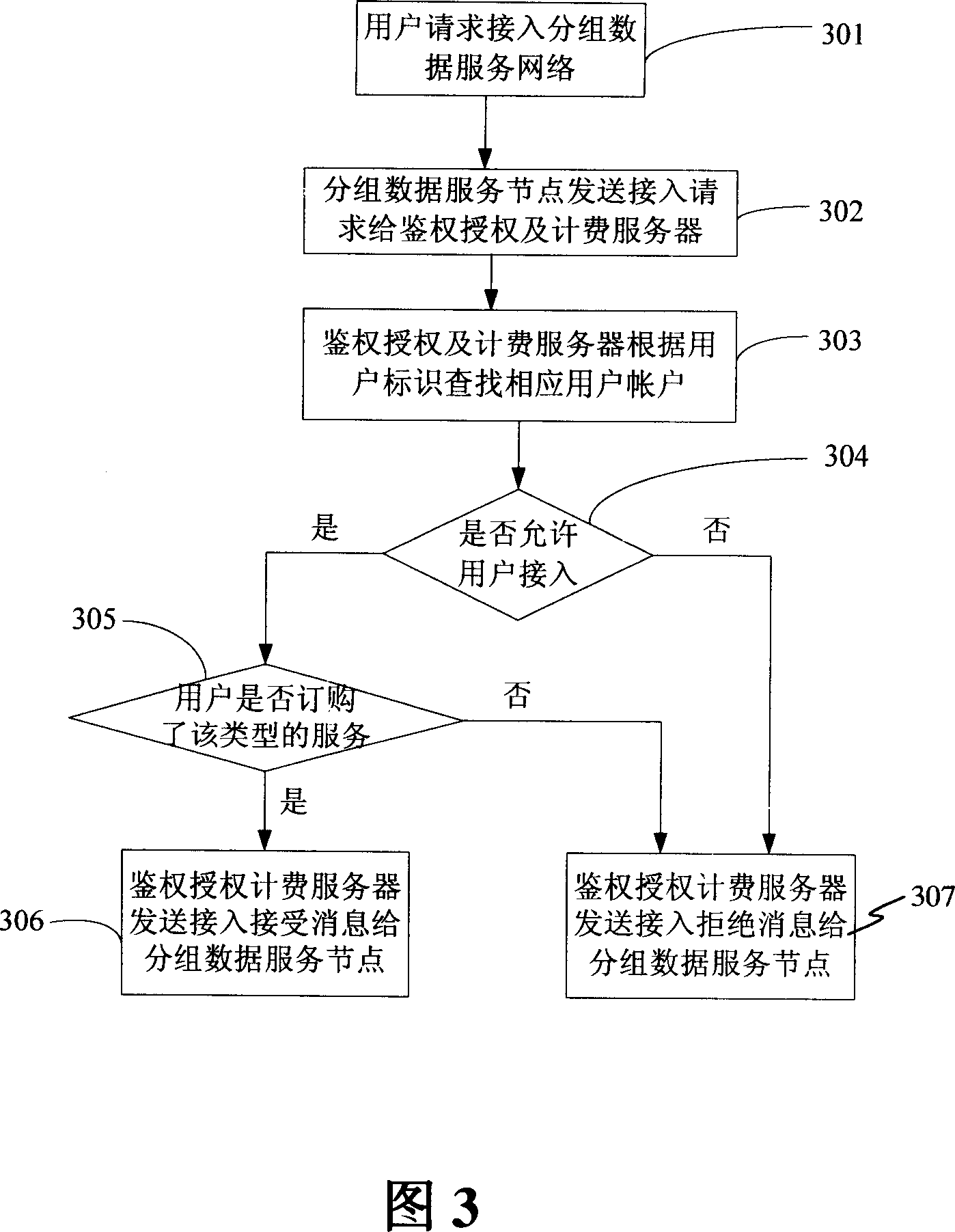
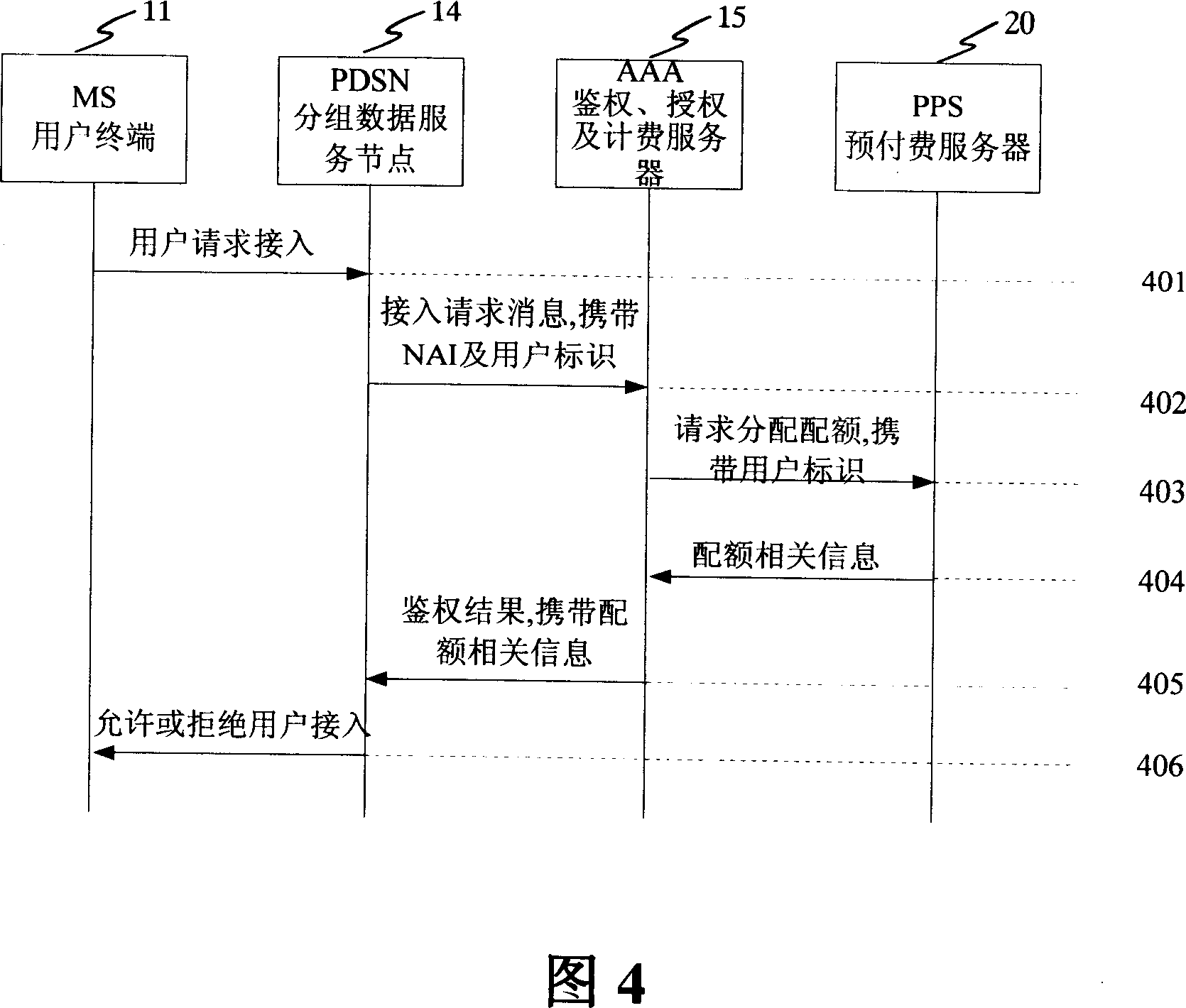
Method and device for authorizing userí»s terminal in CDMA system
ActiveCN101094067ASolve authentication problemsUser identity/authority verificationRadio/inductive link selection arrangementsCdma systemsAuthorization
The method comprises: user end requests to access the general packet radio service (GPRS) network; the GPRS node determines what authentication treatment will be made for the user end, and sends request message containing the ID of user's access network and the ID of user to authentication, authorization and accounting (AAA) server; said AAA server looks up the account information about relevant UE according to user's ID, and based on the ID of user's access network makes authentication process for the UE, and returns the authentication result to said GPRS node; according to the authentication result, said GPRS node determines whether or not providing the data service for the UE.
Owner:ZTE CORP
Method, system and equipment for enhancing MQTT protocol identity authentication by using symmetric cryptographic technology
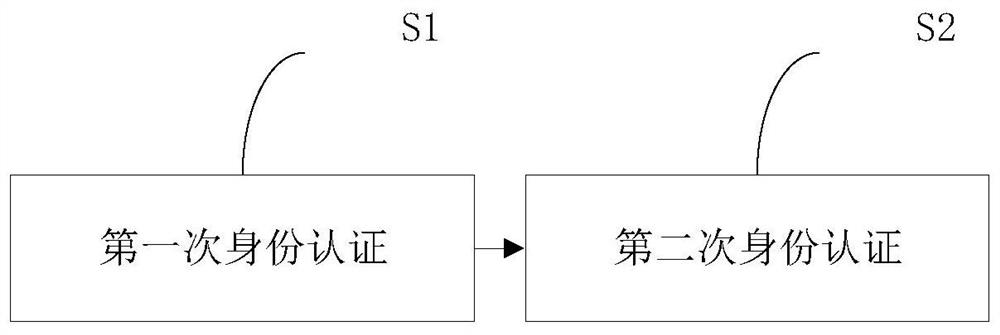
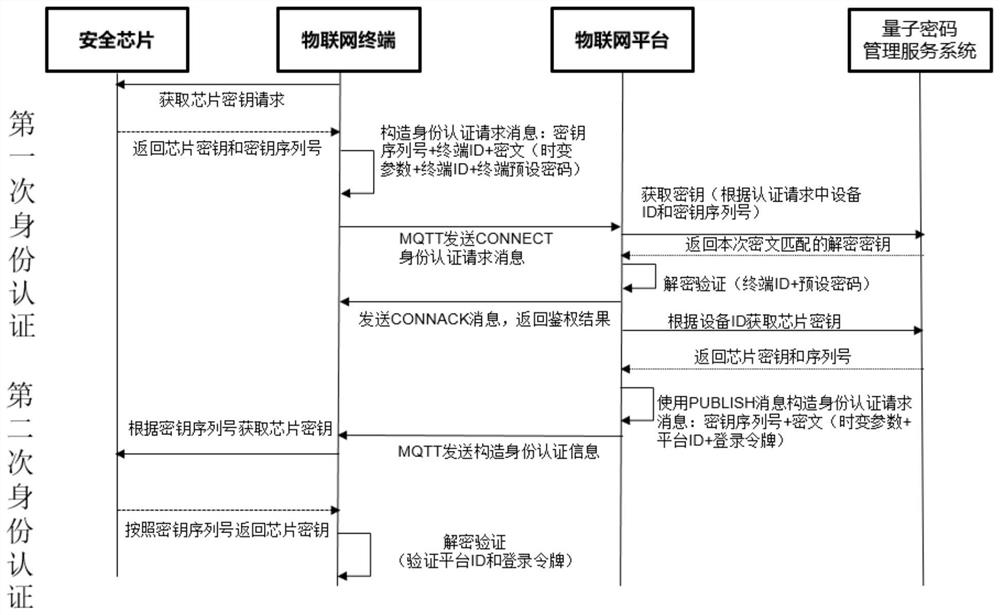
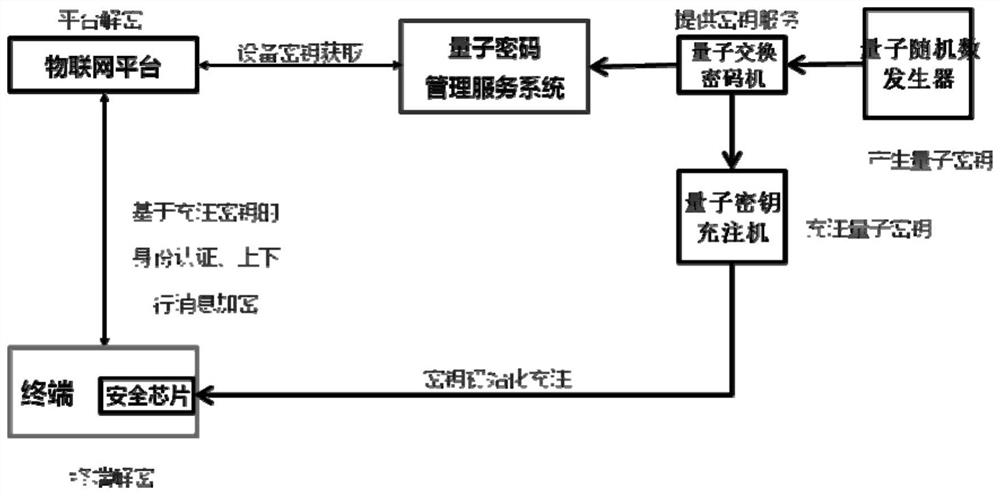
PendingCN113612605AImprove safety performanceReduce the risk of tripartite agreementsKey distribution for secure communicationUser identity/authority verificationProtocol for Carrying Authentication for Network AccessThird party
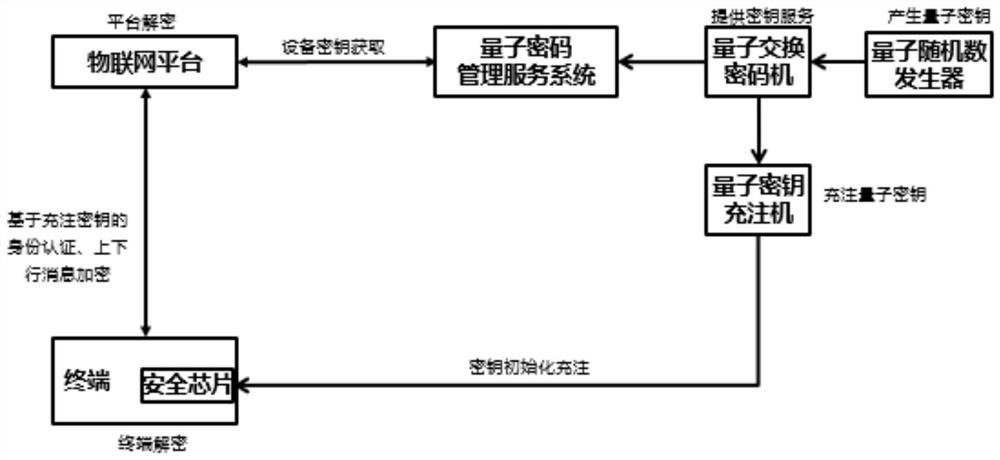
The invention provides a method for enhancing MQTT protocol identity authentication by using a symmetric cryptographic technology, which comprises the following steps of: performing first identity authentication from an Internet of Things terminal to an Internet of Things platform: charging a quantum key into a quantum safety chip by a quantum key charging machine, and recording and storing a corresponding relationship between the charging safety chip and the key, the Internet of Things terminal calls a quantum key in a chip to construct an identity authentication request message to the Internet of Things platform, the Internet of Things platform obtains symmetry, carries out decryption and identity comparison, generates a login token after successful authentication, and returns a verification message to the terminal; second identity authentication: the Internet of Things platform applies for a key according to the terminal ID and constructs an identity authentication request message to the terminal; and the terminal decrypts and verifies the platform ID and the login token. The invention further provides a system and equipment corresponding to the method. The invention has the advantages that identity authentication is performed by using a key set symmetric algorithm in the quantum safety chip, one key is pad at a time, a third party does not need to issue and authenticate a digital certificate. Therefore, the safety is improved.
Owner:中电信量子科技有限公司
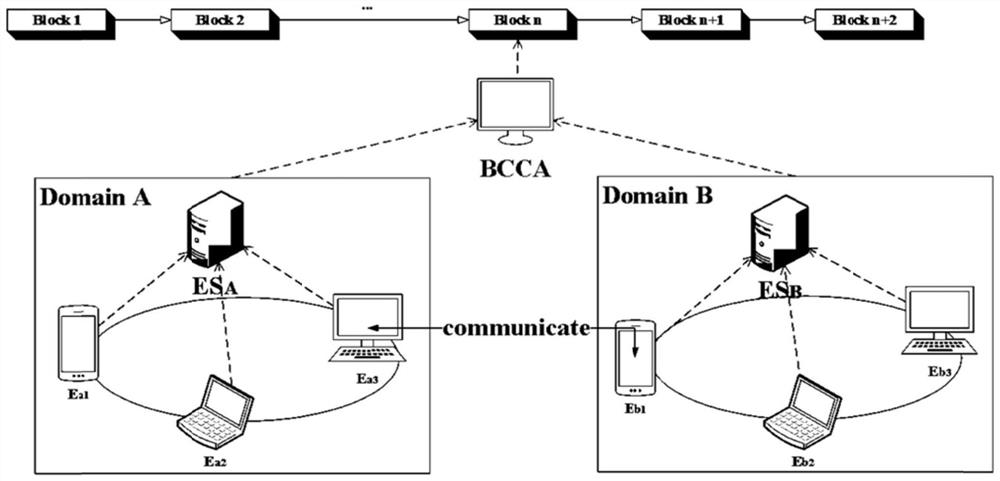
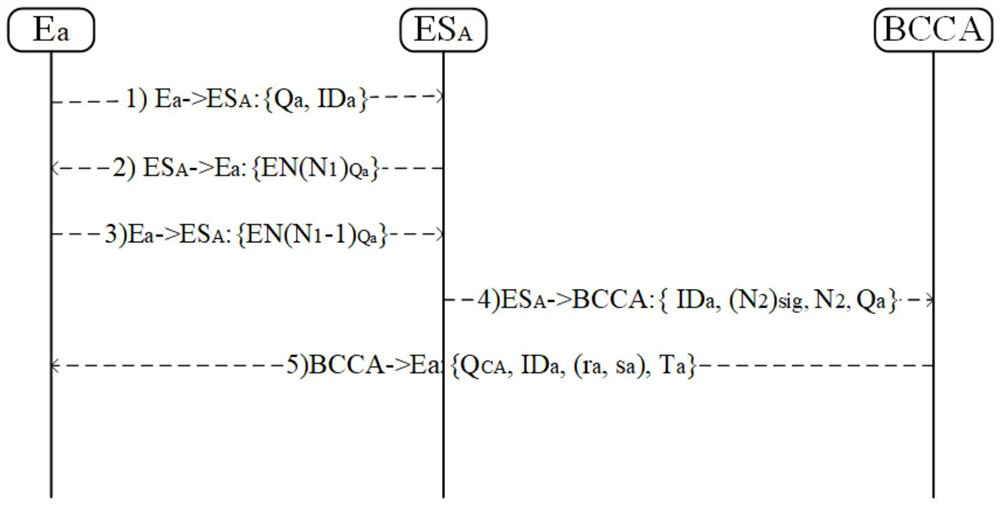
Cross-domain authentication and key agreement method based on block chain in Internet of Things environment
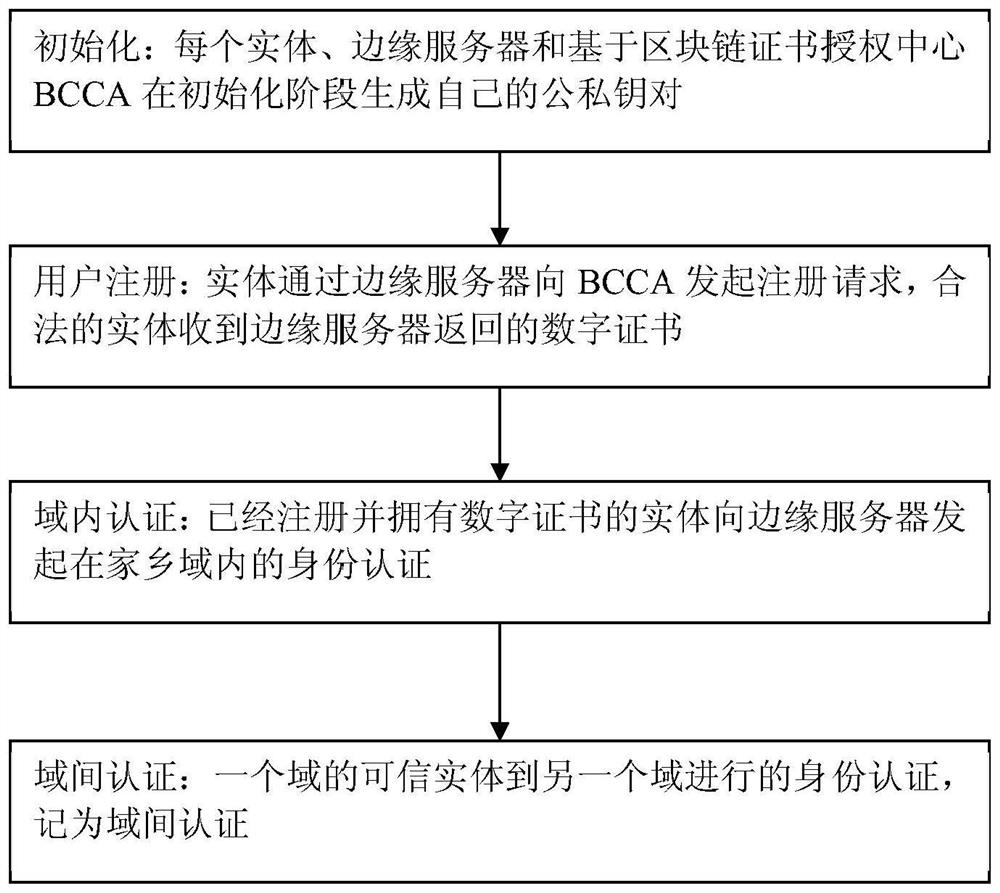
PendingCN114710275AAvoid failureSolve authentication problemsKey distribution for secure communicationPublic key for secure communicationEdge serverKey-agreement protocol
The invention discloses a cross-domain authentication and key negotiation method based on a block chain in an Internet of Things environment. The method comprises the following steps: (1) initialization: each entity, an edge server and a block chain-based certificate authority center BCCA generate own public and private key pairs in an initialization stage; (2) user registration: the entity initiates a registration request to the BCCA through the edge server, and the legal entity receives a digital certificate returned by the edge server; (3) intra-domain authentication: initiating identity authentication in the home domain to the edge server by the entity which has been registered and has the digital certificate; and (4) inter-domain authentication: identity authentication performed by the trusted entity of one domain to another domain is recorded as inter-domain authentication. According to the invention, an Internet of Things entity identity authentication and key agreement protocol based on an elliptic curve is designed, high-efficiency communication of low-performance terminal equipment is ensured, higher security performance can be provided, and the method is more suitable for Internet of Things edge equipment with lower performance.
Owner:HUNAN UNIV OF SCI & TECH
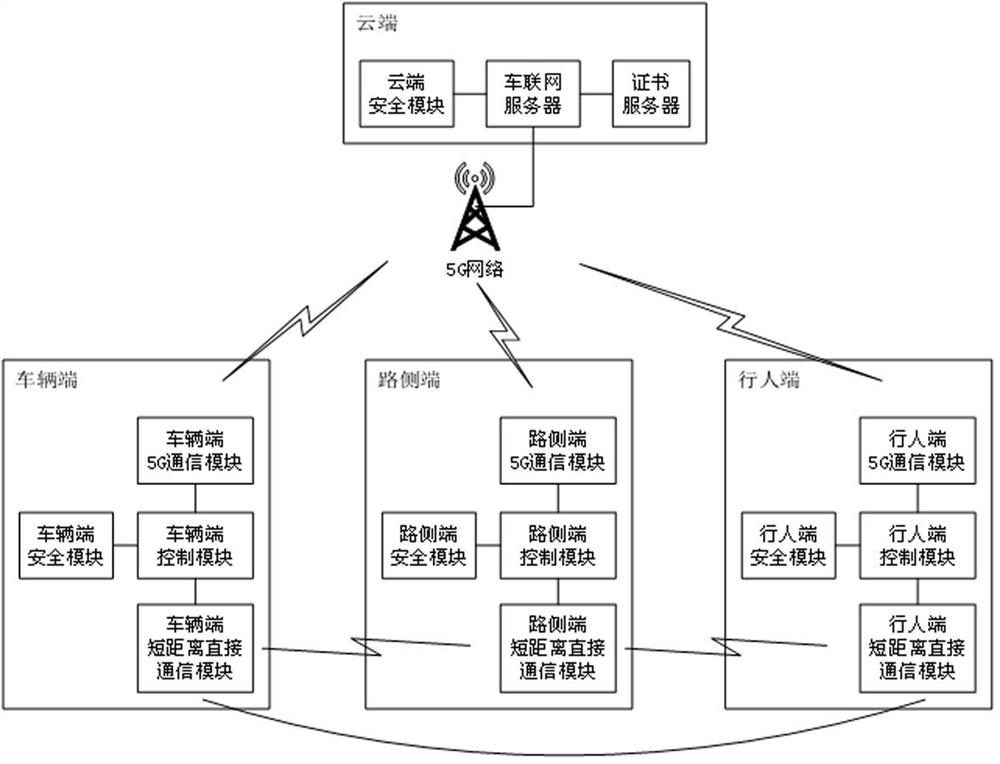
V2X Internet-of-vehicles safety communication system and method based on 5G
ActiveCN112055330AEasy to useImprove securityKey distribution for secure communicationPublic key for secure communicationEmbedded systemSecure communication
The invention relates to a V2X Internet-of-vehicles safety communication system and method based on 5G. The V2X Internet-of-vehicles safety communication system comprises a cloud terminal, a vehicle terminal, a road side terminal and at least two pedestrian terminals, wherein the sum of the number of the road side terminals and the number of the pedestrian terminals is at least two; the cloud terminal comprises a certificate server, a cloud security module and an Internet-of-vehicle server; the vehicle end comprises a vehicle end short-distance direct communication module, a vehicle end 5G communication module, a vehicle terminal safety module and a vehicle terminal control module; the roadside end comprises a roadside end short-distance direct communication module, a roadside end 5G communication module, a roadside terminal safety module and a roadside terminal control module; the pedestrian terminal comprises a pedestrian end short-distance direct communication module, a pedestrian end 5G communication module, a pedestrian end safety module and a pedestrian end control module; V2X Internet-of-vehicles identity authentication and group security encryption communication are realized according to the characteristics of 5G and V2X Internet-of-vehicles, so that the V2X Internet-of-vehicles identity authentication and group security encryption communication are safe, reliable, simple and efficient.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Mass Internet of Things equipment authentication method, storage medium and information data processing terminal
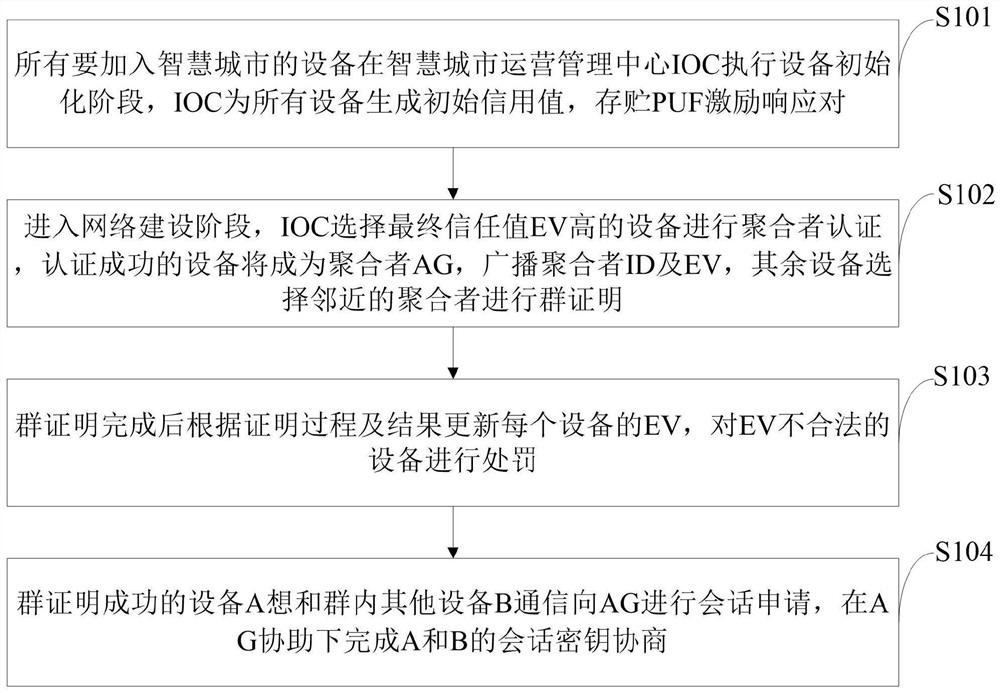
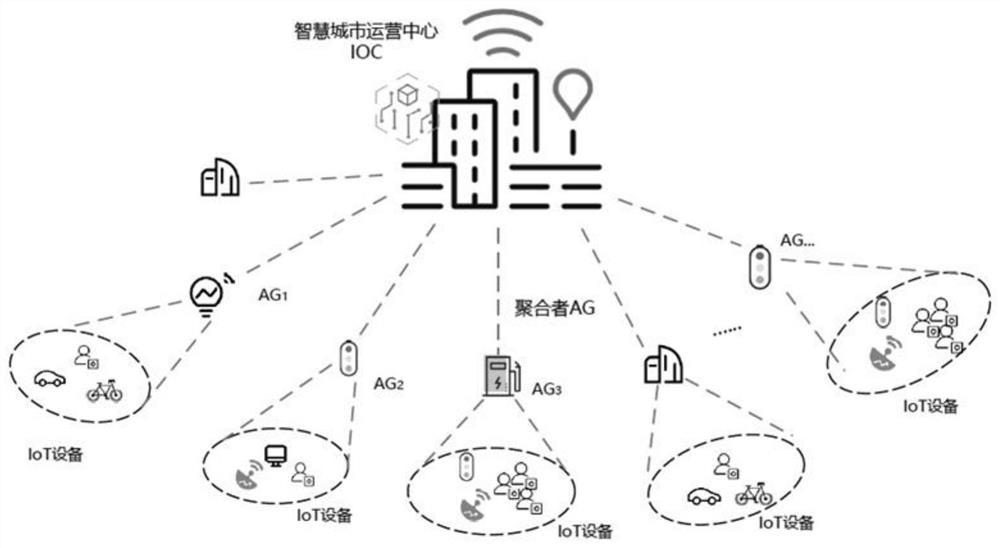
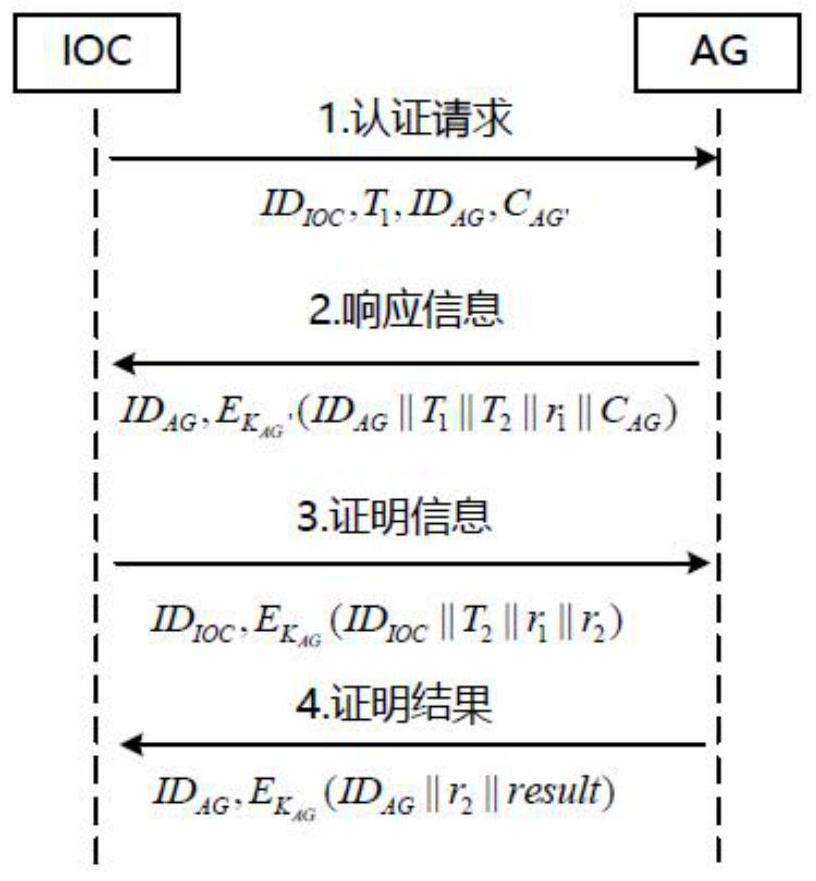
ActiveCN113079132ARemotely proven reliable and efficientEnsure safetyKey distribution for secure communicationUser identity/authority verificationEngineeringSmart city
The invention belongs to the technical field of Internet of Things security, and discloses a massive Internet of Things equipment authentication method, a storage medium and an information data processing terminal. The massive Internet of Things equipment authentication method comprises the steps: IOT equipment interacts with a smart city operation center IOC, and equipment initialization is completed through a secure channel; the equipment initialization stage is completed, and an aggregator AG is selected through the IOC to perform aggregator authentication; after the aggregator authentication is completed, the IOT equipment completes group authentication under the assistance of the AG; and after the group authentication is completed, the intra-group equipment completes session key negotiation under the assistance of the AG. According to the method, the equipment with the high trust value is selected as an aggregator to assist the IOC to carry out group certification on other equipment, so that remote certification of massive IOT equipment is more reliable and efficient. Meanwhile, a reputation mechanism is used for supervising the trust value of the equipment, and the situation that the whole system network is affected due to the fact that the successfully authenticated equipment is dealt with by an attacker is prevented.
Owner:XIDIAN UNIV
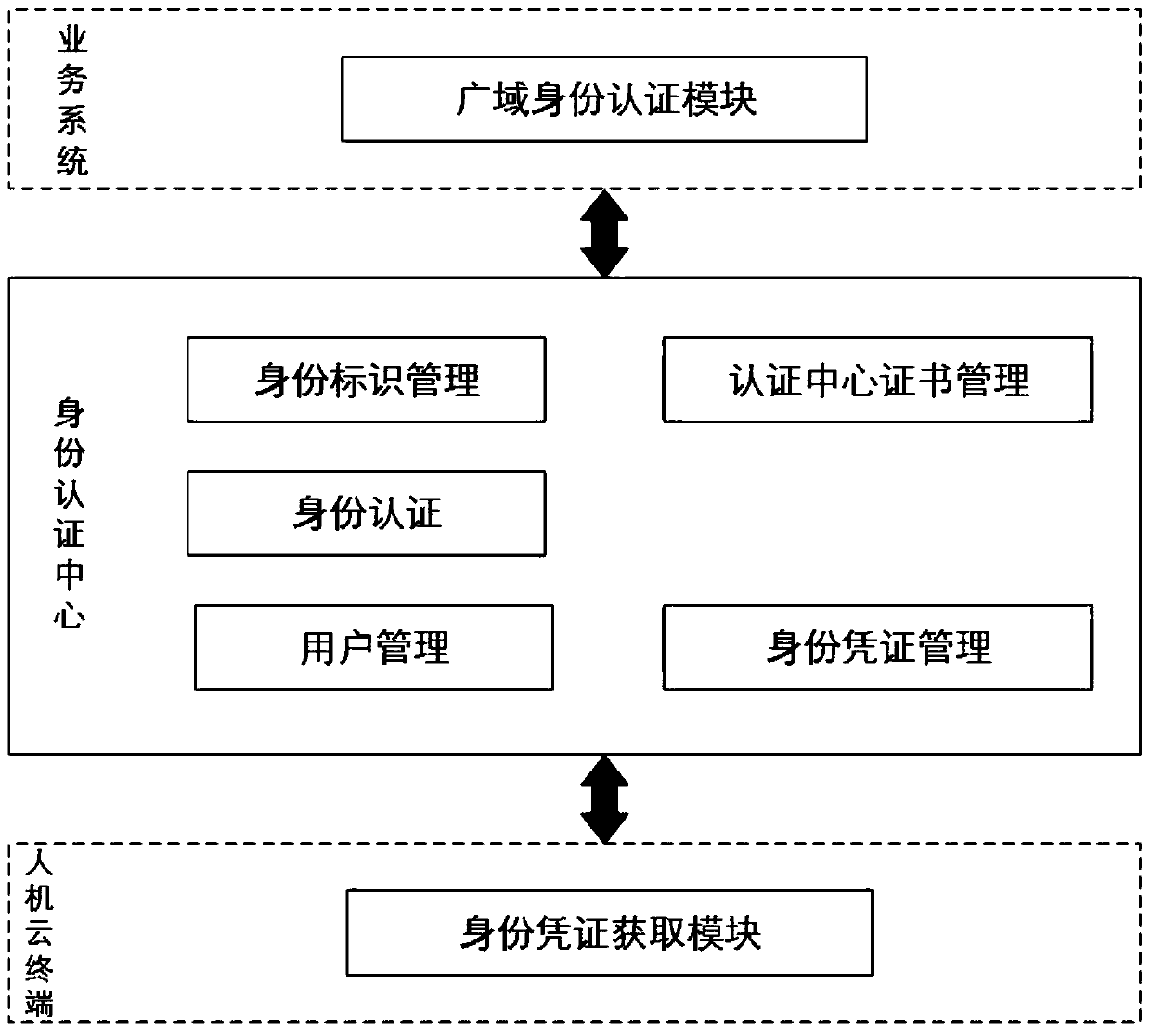
A unified identity authentication method for a power dispatching control system
ActiveCN109902462AImprove reliabilityImplement wide-area authenticationDigital data authenticationResourcesControl systemPublic key certificate
The invention discloses a unified identity authentication method for a power dispatching control system, which comprises the following steps of: sending a user identity identifier sent by a remote user in a wide area network to an identity authentication center, and receiving a verification result returned by the identity authentication center; adopting an identity authentication mode combining ascheduling digital certificate and face recognition on the non-mobile man-machine cloud terminal; adopting an identity authentication mode combining a username password and face recognition on the mobile man-machine cloud terminal; An authentication center certificate management module of each identity authentication center generates a secret key pair by adopting a domestic cryptographic algorithm, writes the secret key pair into a p12 file to generate a soft certificate, writes a public key into a pem file to generate a public key certificate, and distributes the public key certificate to other identity authentication centers deployed in a new generation of scheduling control system. According to different types of the man-machine cloud terminal, the identity authentication method combining multiple identification technologies is adopted, and strong identity authentication of personnel local login can be achieved.
Owner:STATE GRID CORP OF CHINA +3
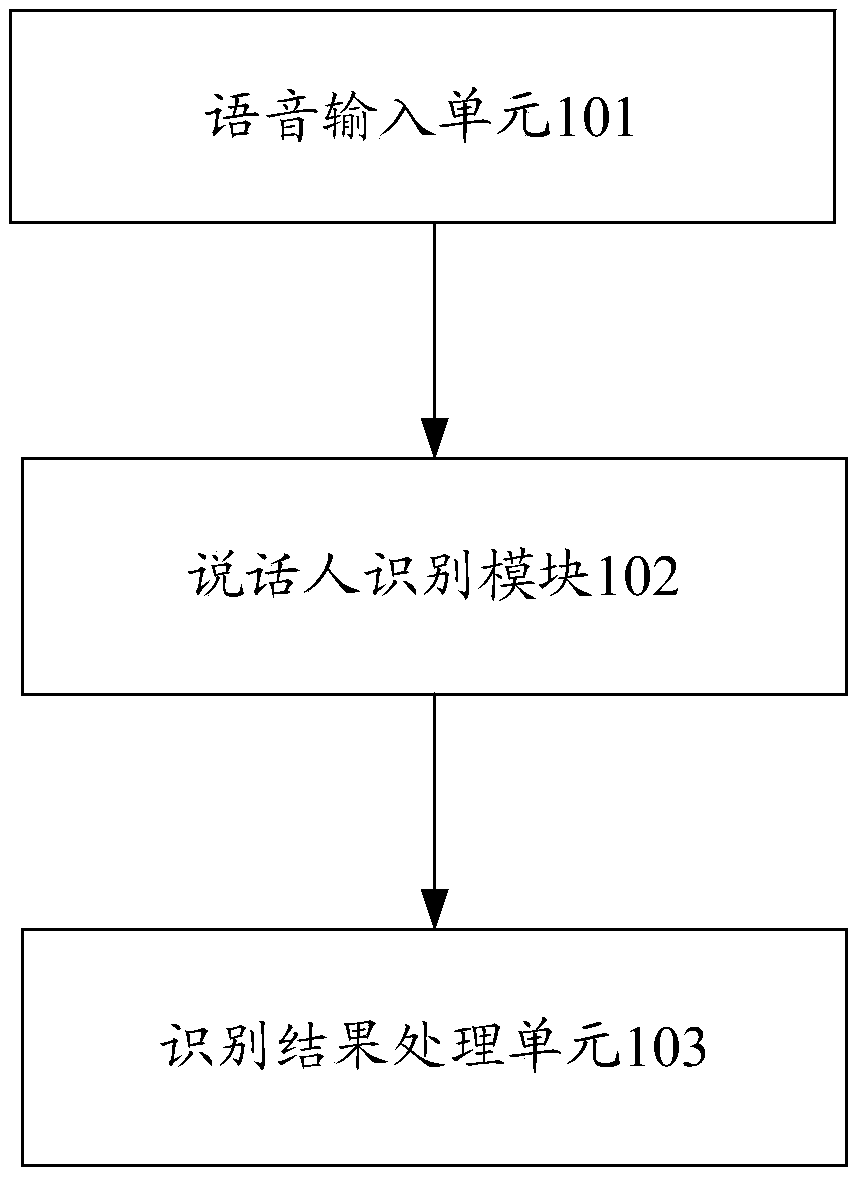
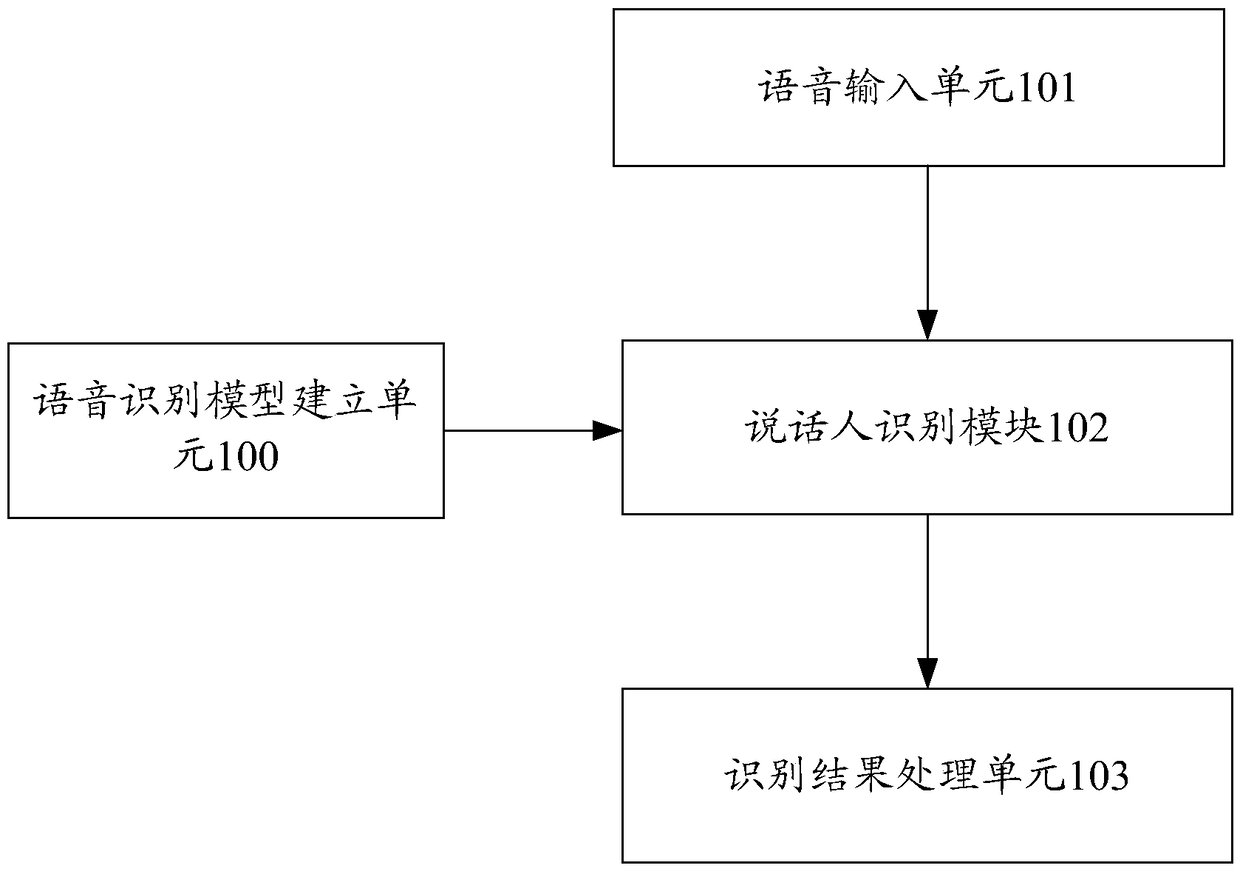
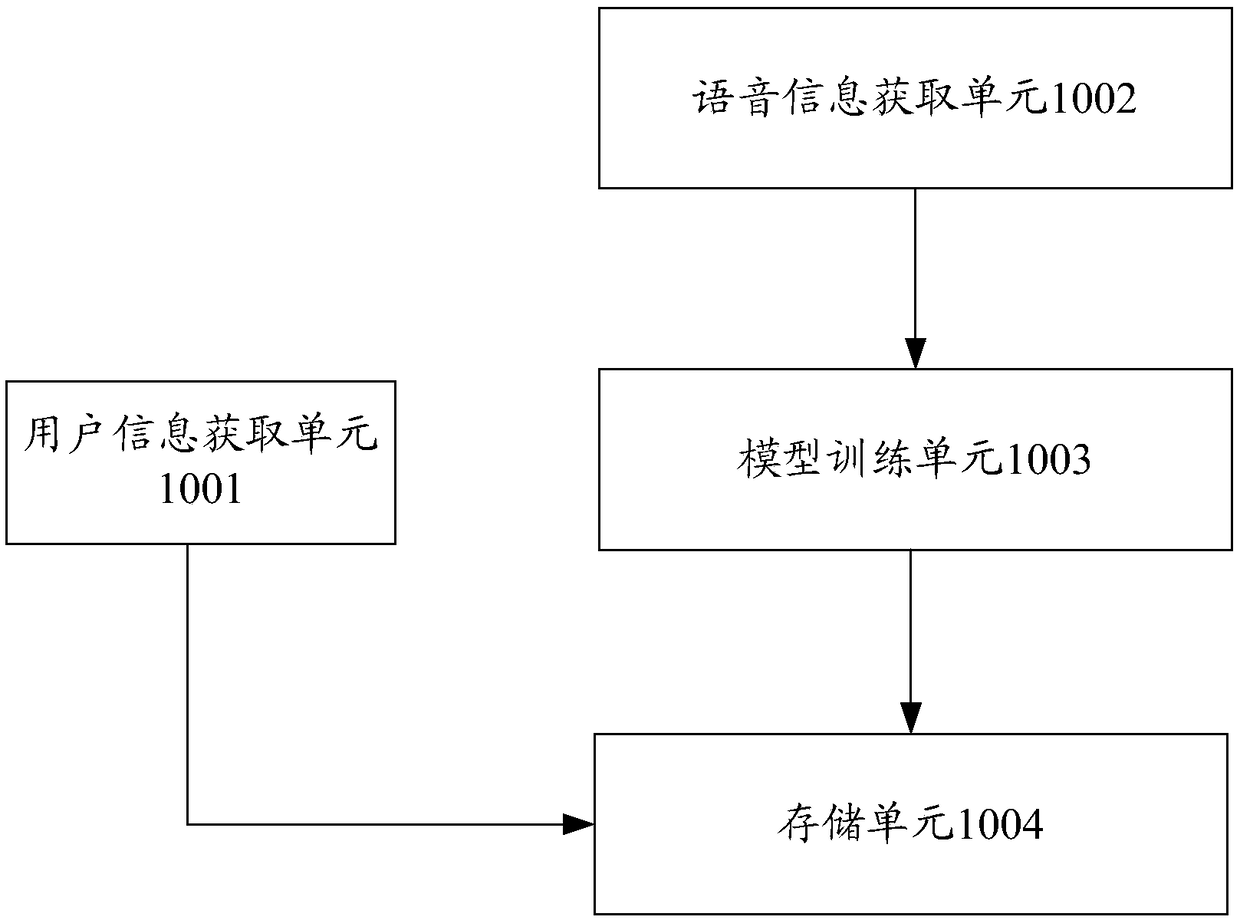
Operator identification system capable of automatically updating model and method
InactiveCN109273011ASolve authentication problemsSolve problemsSpeech analysisSpeech inputSpeech sound
The invention discloses an operator identification system capable of automatically updating a model and a method. The system comprises a speech input unit for acquiring speech data of a speaker, a speaker recognition module configured to perform speaker identification by using a pre-established speech recognition model, and a recognition result processing unit used to determine whether the identification of the speaker is passed or not according to the recognition result of the speaker recognition module. The invention can realize an operator identification technology which is safe, reliable,simple and easy to use, can meet the actual application scene requirements and ensures the long-term identification accuracy.
Owner:EAST CHINA BRANCH OF STATE GRID CORP +1
Cloud service auditing system and method based on digital signature and time stamp
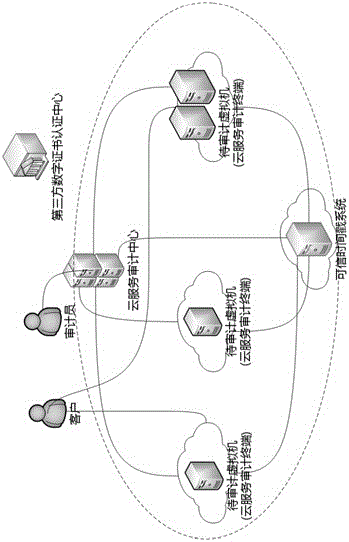
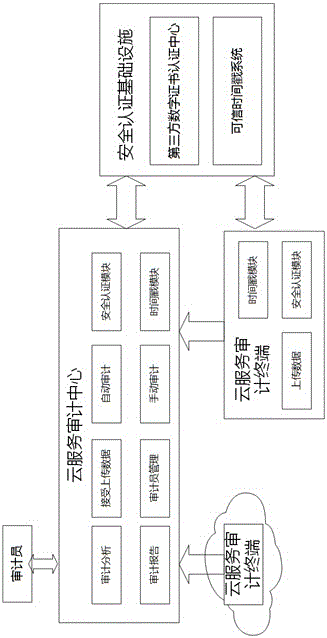
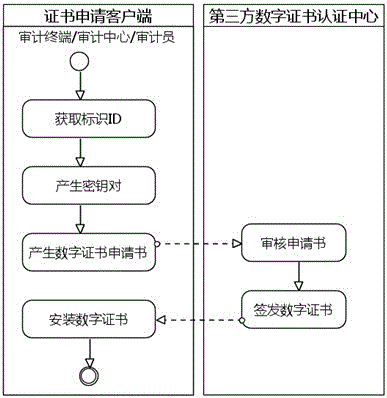
InactiveCN106169954AResolve integritySolve authentication problemsUser identity/authority verificationThird partyDigital signature
The invention belongs to the technical field of server safety, and specifically relates to a cloud service auditing system and method based on a digital signature and a time stamp. The auditing system comprises a cloud service auditing center, a cloud service auditing terminal, a third party digital certificate authentication center and a credible time stamp system. Based on the system, auditing management can be carried out on a cloud virtual machine to be audited and a cloud application installed in the virtual machine by the auditing method. Compared with the prior art, the auditing validity authentication problem of each virtual machine and the application system in the cloud calculation environment can be solved, the reality and integrality of the auditing information and process is ensured, forged or falsified auditing data is prevented, and the responsibility of each party of the auditing process and result is clearly identified.
Owner:INSPUR GROUP CO LTD
Alliance chain consensus identity authentication method
PendingCN114499952AGuaranteed not to be tampered withSolve authentication problemsUser identity/authority verificationDigital identityData transport
The invention provides a consensus identity authentication method for an alliance chain, which comprises the following steps that: a user joins in the alliance chain through an access mechanism of the alliance chain to become an alliance member, a supervision node operates an initialization algorithm to generate a public parameter PK, and generates digital identity information according to unique identity identification information of the alliance member; and the public parameter PK and the digital identity information are uploaded to the block chain, and then a corresponding identity private key is generated for the alliance member of each node through a key generation algorithm. The method has the beneficial effects that the data transmission process can be ensured not to be tampered, and the identity information of a signer can be identified; the method is applied to a public data resource development and utilization scene, and is combined with an identity signature-based technology, so that not only is efficient security access control realized, but also the use scene of the alliance chain is expanded, and the problem of quickly and safely realizing identity authentication between consensus nodes under the background of the alliance chain can be effectively solved.
Owner:CETC BIGDATA RES INST CO LTD
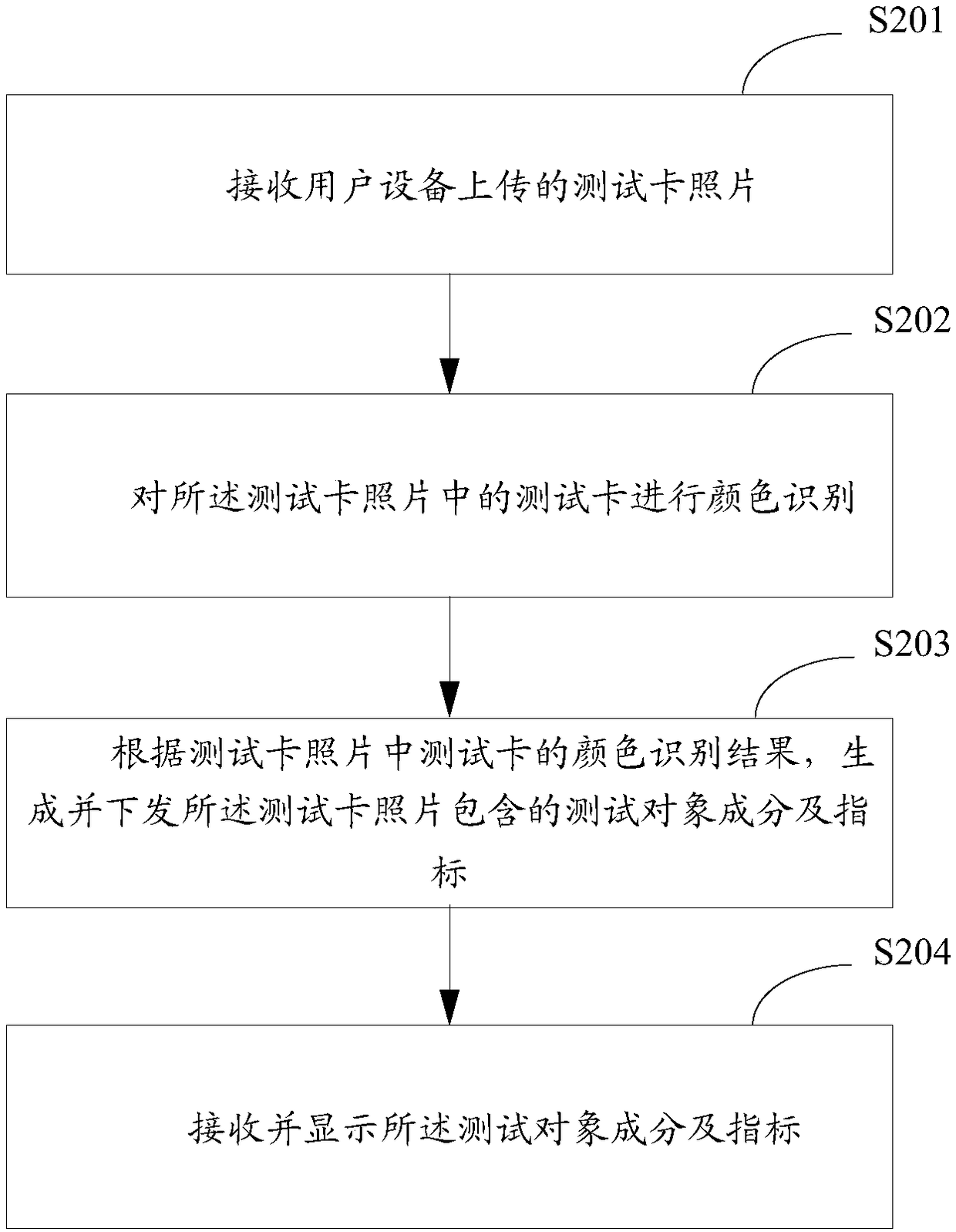
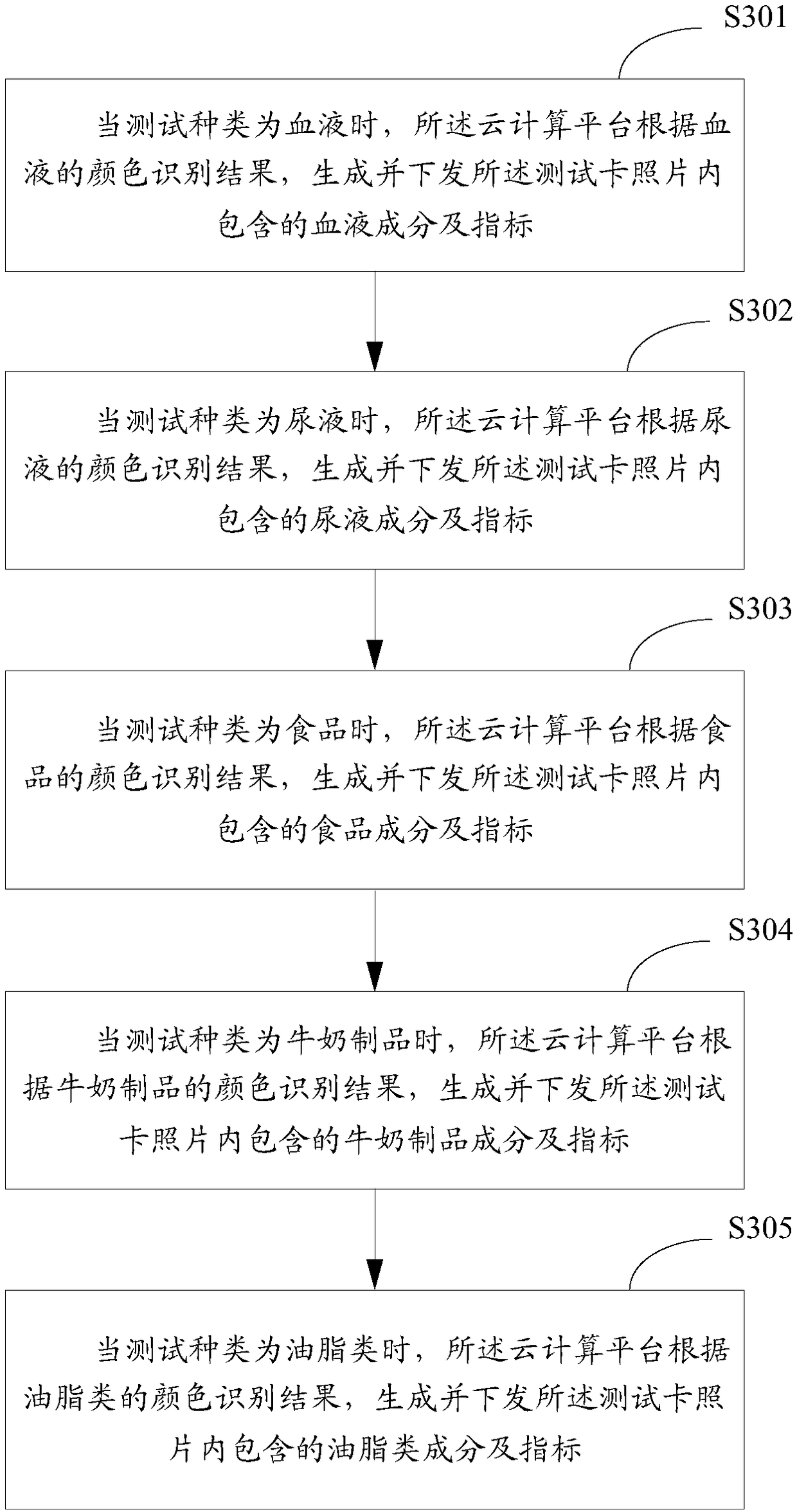
Image recognition system and image recognition method
InactiveCN108062748AEasy to detectAvoid inconvenienceImage enhancementImage analysisHealth indexTest card
The invention is suitable for the technical field of image recognition, and provides an image recognition system and an image recognition method. The system comprises a cloud computing platform whichis used for receiving a test card image uploaded by user equipment and generating and transmitting test object components and indexes in the test card image according to the color of a test card in the test card image; and the user equipment which is provided with a wireless communication module and a photographing module, and is used for capturing the test card image, uploading the captured testcard image, and receiving and displaying the test object components and indexes. The system can enable a user to complete the detection, which had to be executed through professional equipment ago, ofsome health indexes and food components conveniently at any time and any place, and avoids the inconvenience in carrying various types of detection instruments. Meanwhile, the cloud computing platform integrates all detection functions, can quickly generate a detection result, and improves the detection efficiency visually. In addition, the cloud computing platform also has the fingerprint and face recognition functions, and can solve problems of identity verification and safety.
Owner:深圳大森智能科技有限公司
Method and system for enhancing MQTT protocol transmission security by using symmetric cryptographic technology
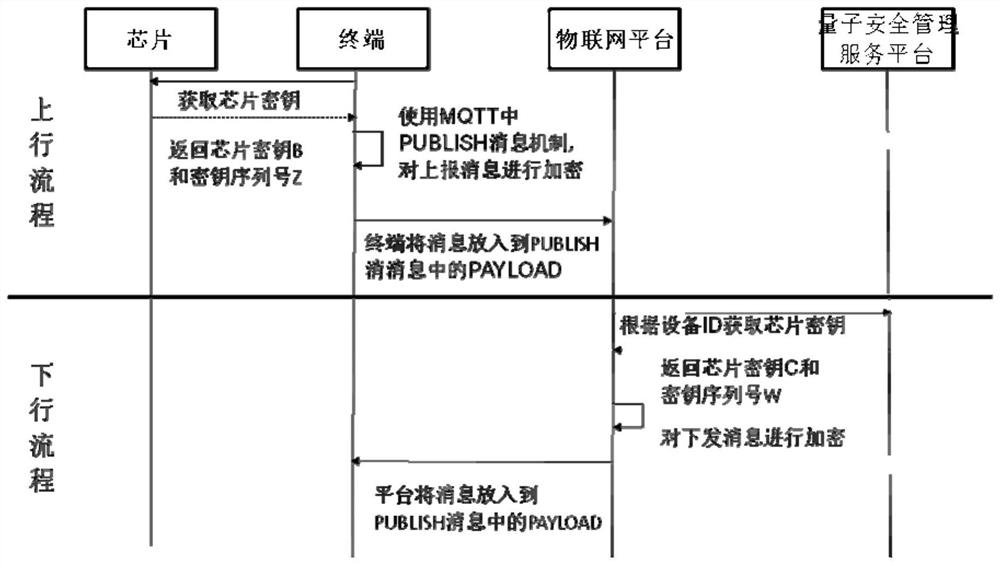
ActiveCN113630407AAvoid security impactSolve authentication problemsKey distribution for secure communicationUser identity/authority verificationProtocol for Carrying Authentication for Network AccessEngineering
The invention provides a method for enhancing MQTT protocol transmission security by using a symmetric cryptographic technology, and the method comprises the steps: carrying out the encryption and decryption of data: carrying out the encryption and decryption from an Internet of Things terminal to an Internet of Things platform, and carrying out the encryption and decryption from the Internet of Things platform to the Internet of Things terminal; in encryption and decryption, employing a quantum key filling machine for filling a symmetric key of a quantum security chip arranged in or outside the Internet of Things terminal and a key stored in a quantum exchange cipher machine, and enabling the quantum exchange cipher machine to record and store a corresponding relation between the filled quantum security chip and the key. The method has the advantages that the quantum key is used for protecting uplink and downlink information of the MQTT, and the problems that the key is reused in the transmission process of uplink and downlink information of the Internet of Things terminal, and the security is reduced along with use are solved by using a quantum security chip and a symmetric cryptographic technology.
Owner:中电信量子科技有限公司
Separate management method of authentication charging and system
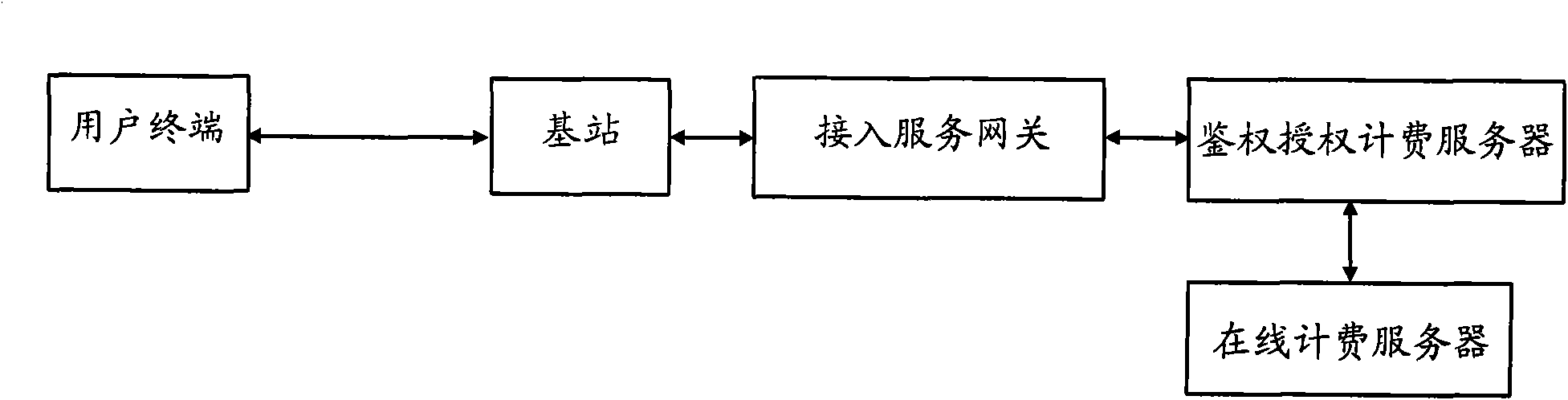
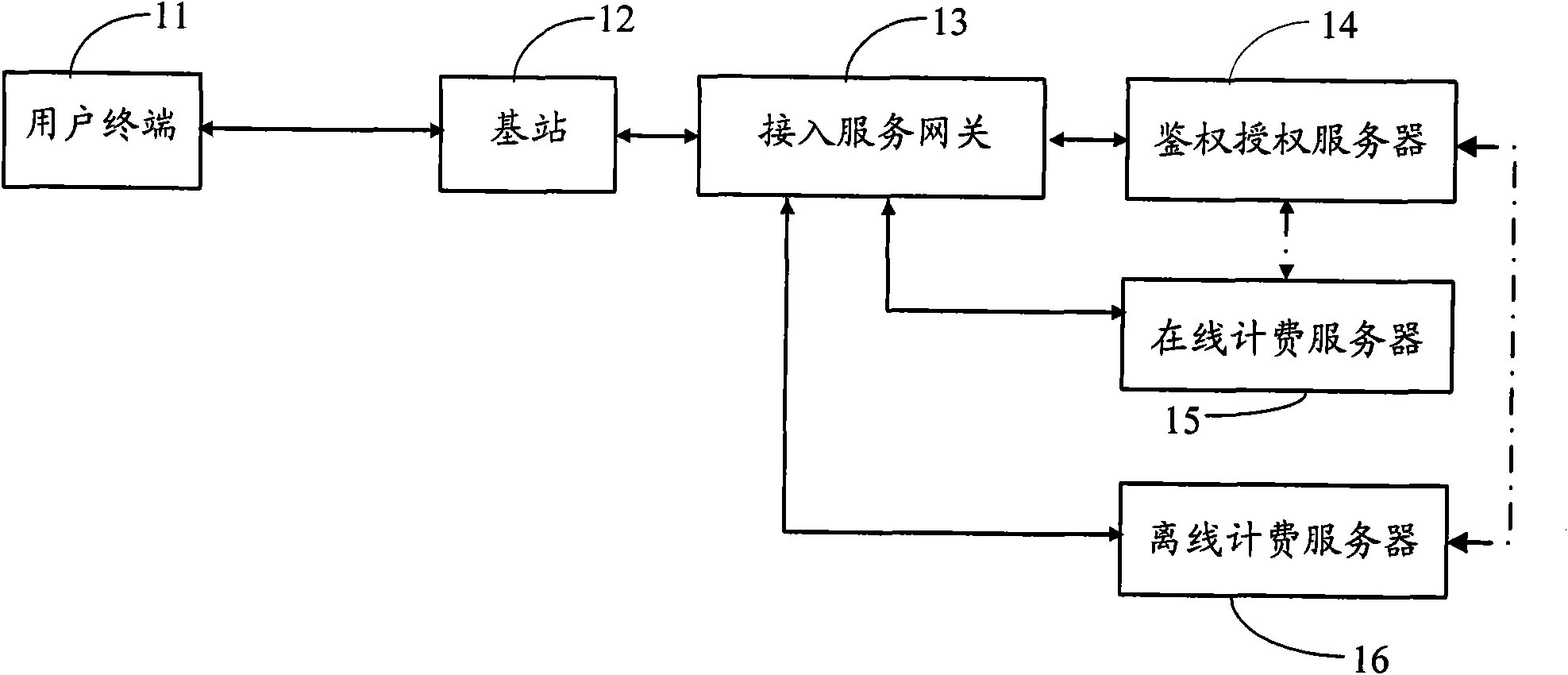
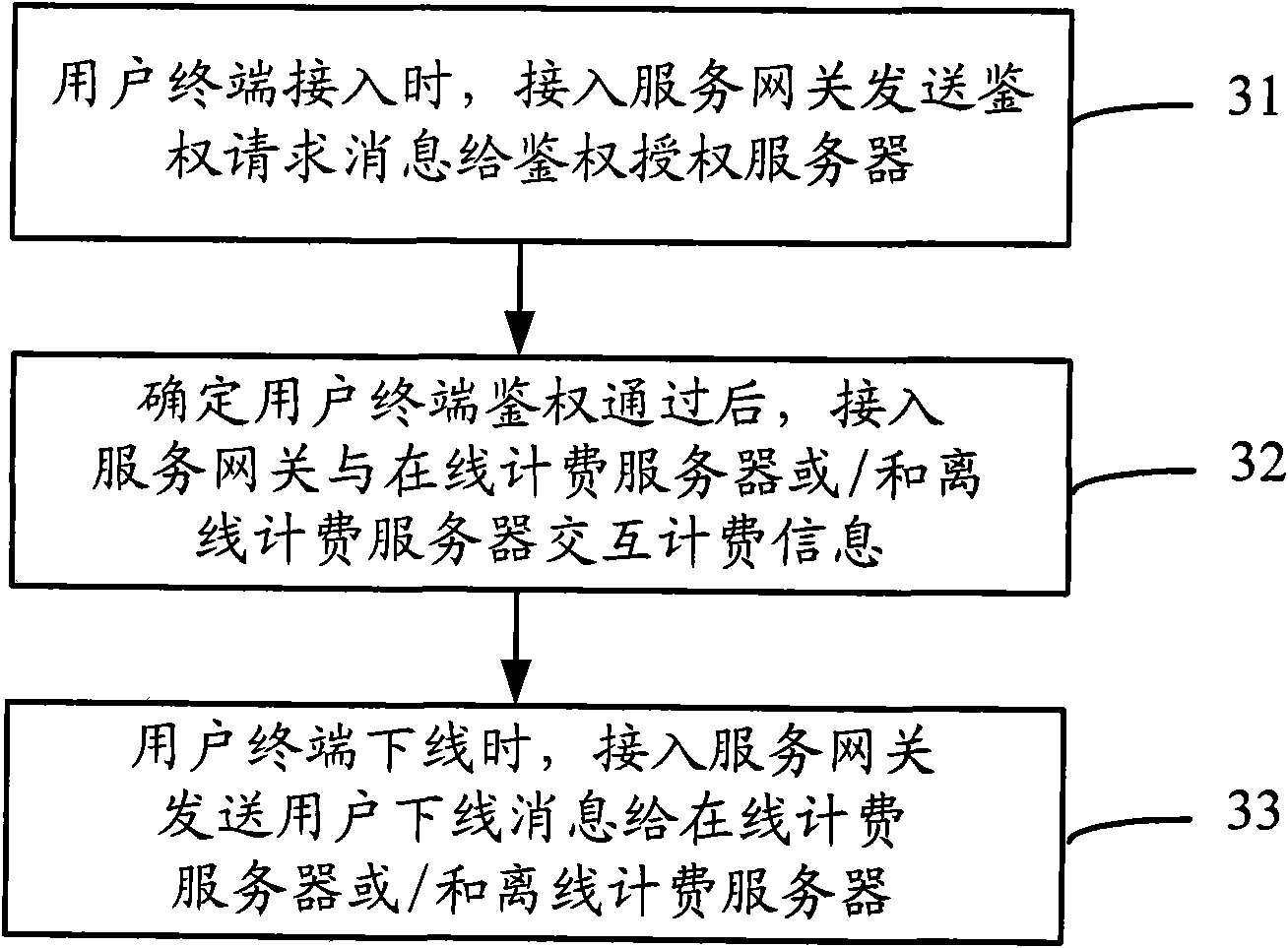
InactiveCN102056122AImprove processing efficiencyEasy to arrange and implementAccounting/billing servicesSecurity arrangementService gatewayWiMAX
The invention discloses a separate management method of authentication charging, comprising the following steps of: sending an authentication request message to an authentication authorization server by an access service gateway to inform the authentication authorization server to process authentication authorization on a user terminal when the user terminal is confirmed to be accessed into a Wimax system; allowing the user terminal to use corresponding data service and informing a charging server to record relevant charging information on the data service after the authentication of the user terminal is confirmed to be passed by the access service gateway according to a response message returned from the authentication authorization server; and sending a user off-line message to the charging server to inform the charging server to stop recording the relevant charging information when the user terminal is confirmed to be off-line by the access service gateway.
Owner:ZTE CORP
Authentication method, electronic equipment and authentication server
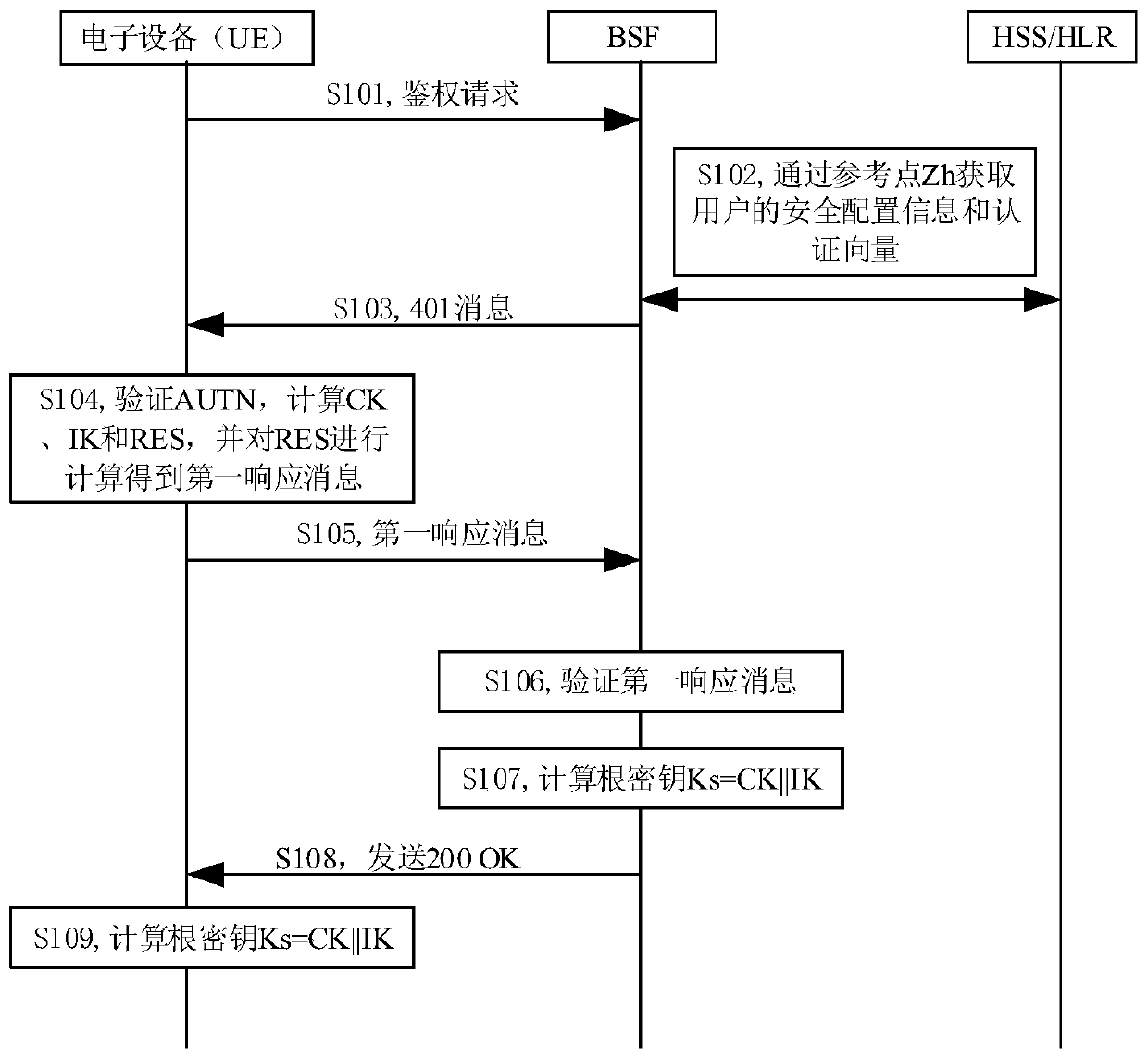
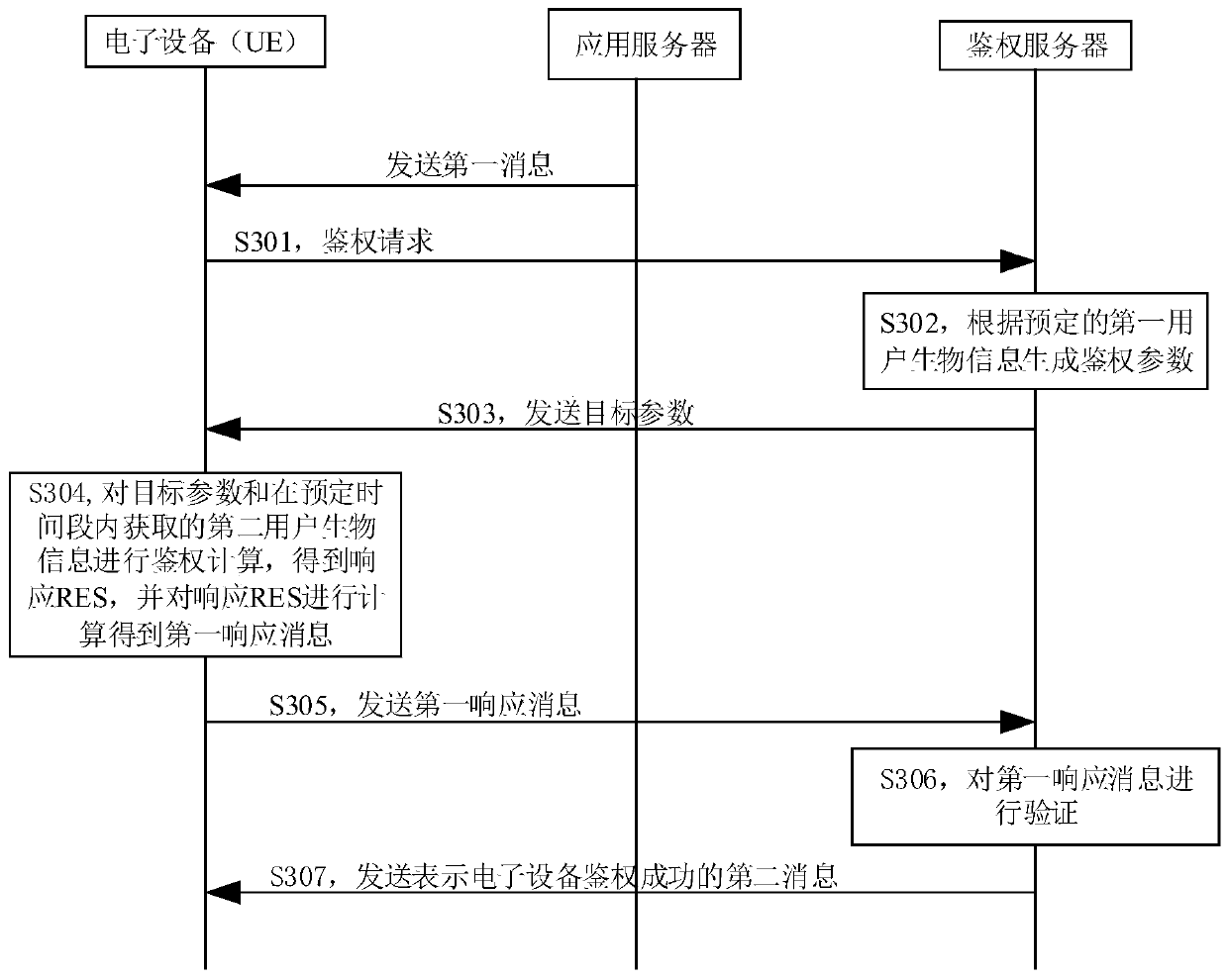
ActiveCN111404933ASolve authentication problemsEncryption apparatus with shift registers/memoriesApplication serverEngineering
The embodiment of the invention discloses an authentication method, electronic equipment and an authentication server, and the authentication method comprises the steps: transmitting an authenticationrequest to the authentication server under the condition that a first message transmitted by an application server is received, so as to enable the authentication server to generate an authenticationparameter according to preset first user biological information; receiving a target parameter in the authentication parameters sent by the authentication server; calculating the target parameter andsecond user biological information acquired in a predetermined time period to obtain RES, and calculating the RES to obtain a first response message; sending the first response message to the authentication server, so that the authentication server verifies the first response message; and if the authentication server verifies the first response message successfully, receiving a second message sentby the authentication server, the second message being used for prompting that the electronic equipment is authenticated successfully. By utilizing the embodiment of the invention, the identity of the user of the electronic equipment can be authenticated, and the safety is ensured.
Owner:VIVO MOBILE COMM CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com