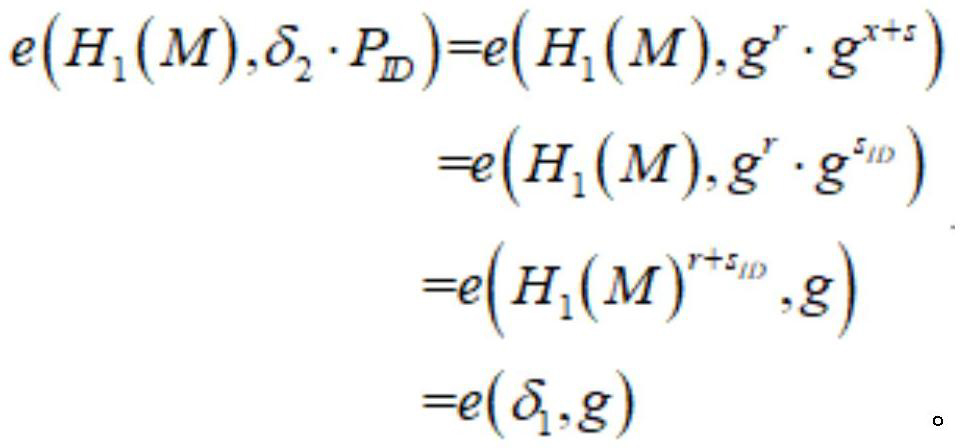Alliance chain consensus identity authentication method
An identity authentication and alliance technology, applied in the blockchain field, can solve the problem that CA needs to maintain a large number of public key certificates, achieve efficient and secure access control, and solve fast and secure effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The technical solution of the present invention is further described below, but the scope of protection is not limited to the description.
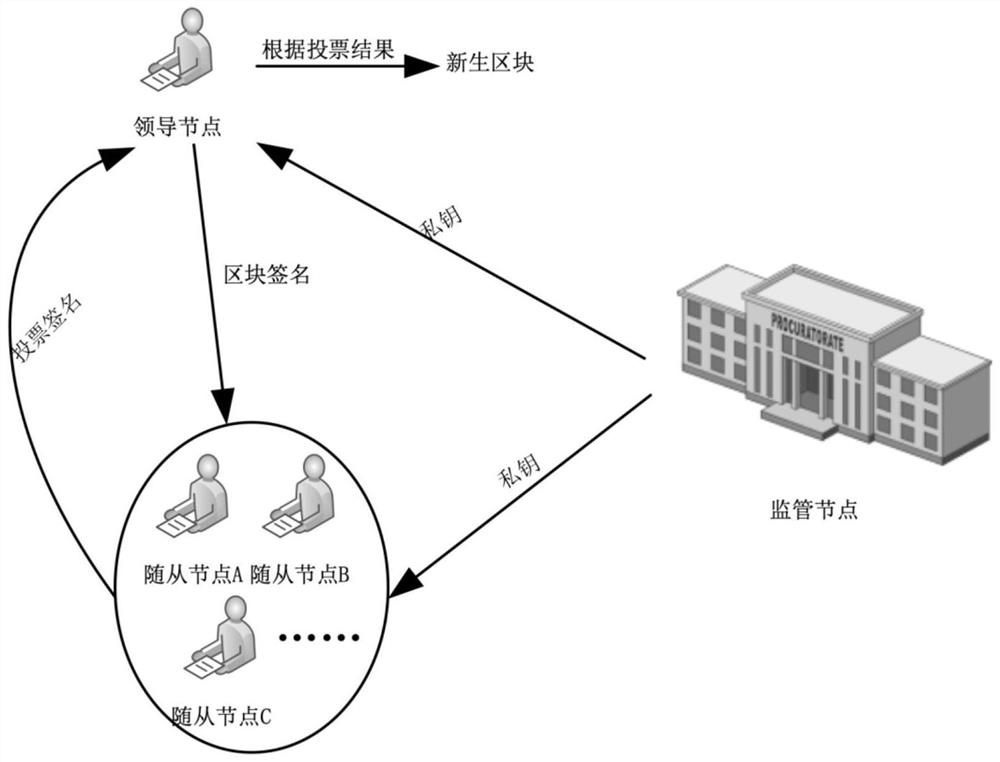
[0039] Such as figure 2 As shown, a consortium chain consensus identity authentication method includes the following steps:
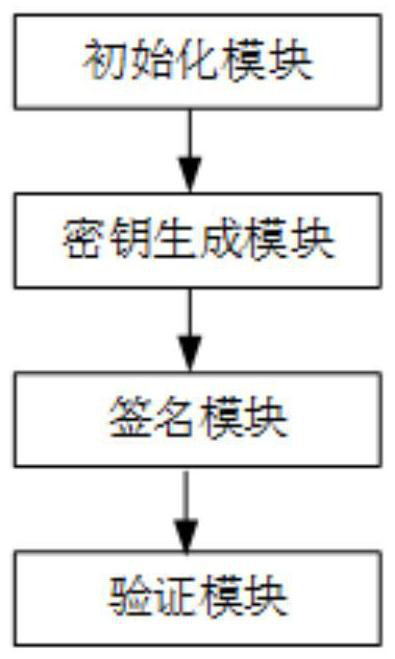
[0040] ①The user joins the alliance chain through the access mechanism of the alliance chain and becomes an alliance member. The supervision node runs the initialization algorithm to generate the public parameter PK, and at the same time generates digital identity information according to the unique identity information of the alliance member, and uploads the public parameter PK and digital identity information to the blockchain, and then generate the corresponding identity private key for each node's alliance members through the key generation algorithm;
[0041] ②The leader node packs and verifies a batch of transactions to form a block, signs the block with its own private key, and sends it to the follo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com