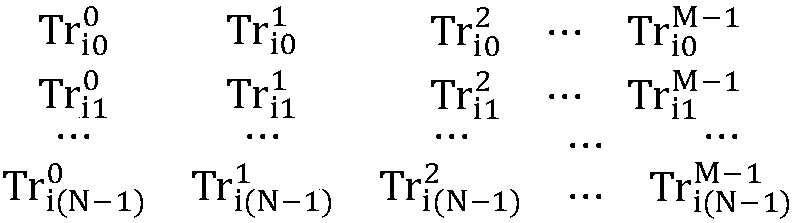Patents
Literature
45results about How to "Reduce the probability of attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
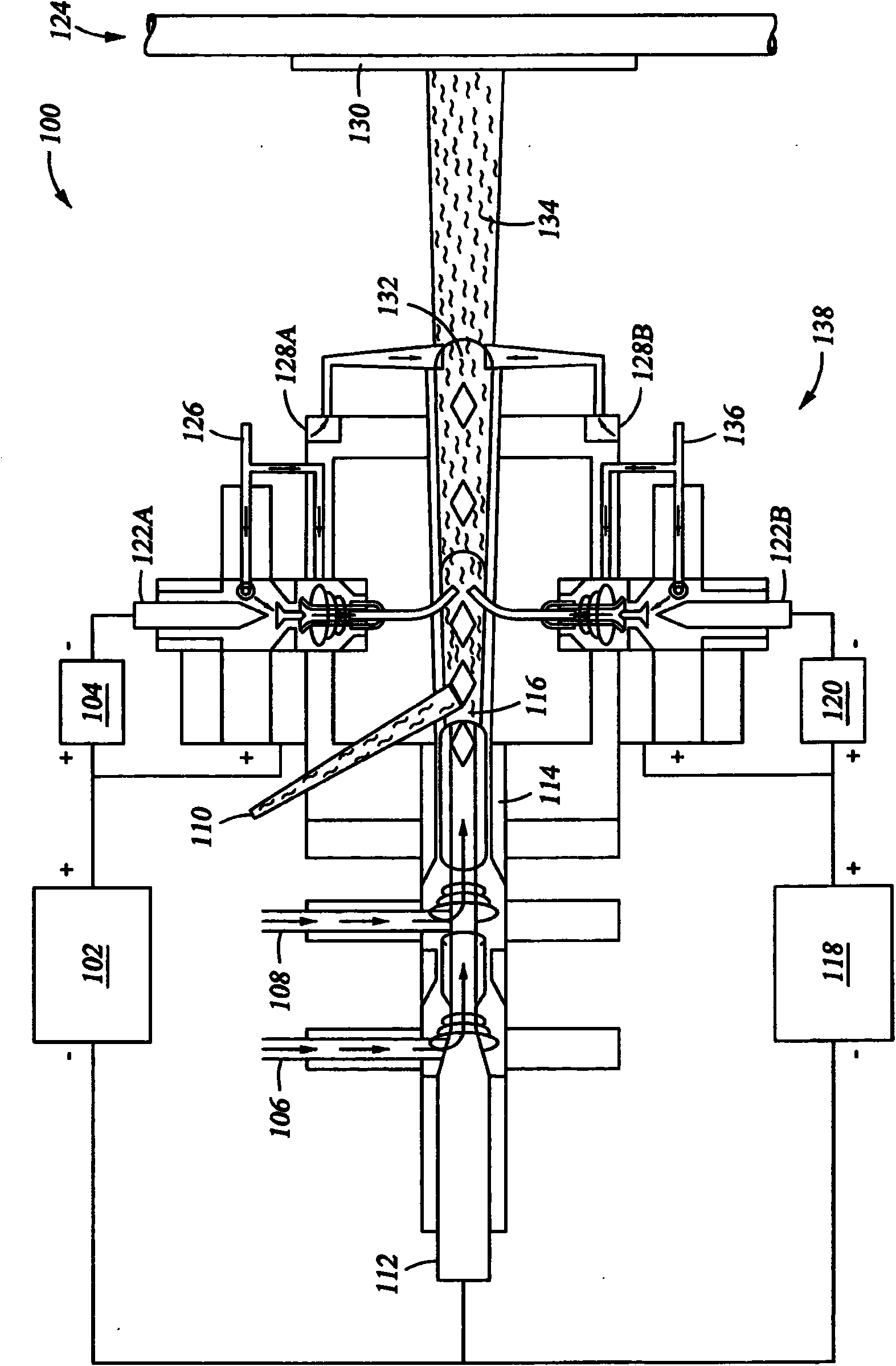
Ceramic coating comprising yttrium which is resistant to a reducing plasma
ActiveCN102084020AReduce formationReduce the probability of attackMolten spray coatingThin material handlingParticulatesPorosity
Particulate generation has been a problem in semiconductor device processing in highly corrosive plasma environments. The problem is exacerbated when the plasma is a reducing plasma. Empirically produced data has shown that the formation of a plasma spray coated yttrium-comprising ceramic such as yttrium oxide, Y2O3-ZrO2 solid solution, YAG, and YF3 provides a low porosity coating with smooth and compacted surfaces when such ceramics are spray coated from a powder feed having an average effective diameter ranging from about 22 [mu]m to about 0.1 [mu]m. These spray-coated materials reduce the generation of particulates in corrosive reducing plasma environments.
Owner:APPLIED MATERIALS INC
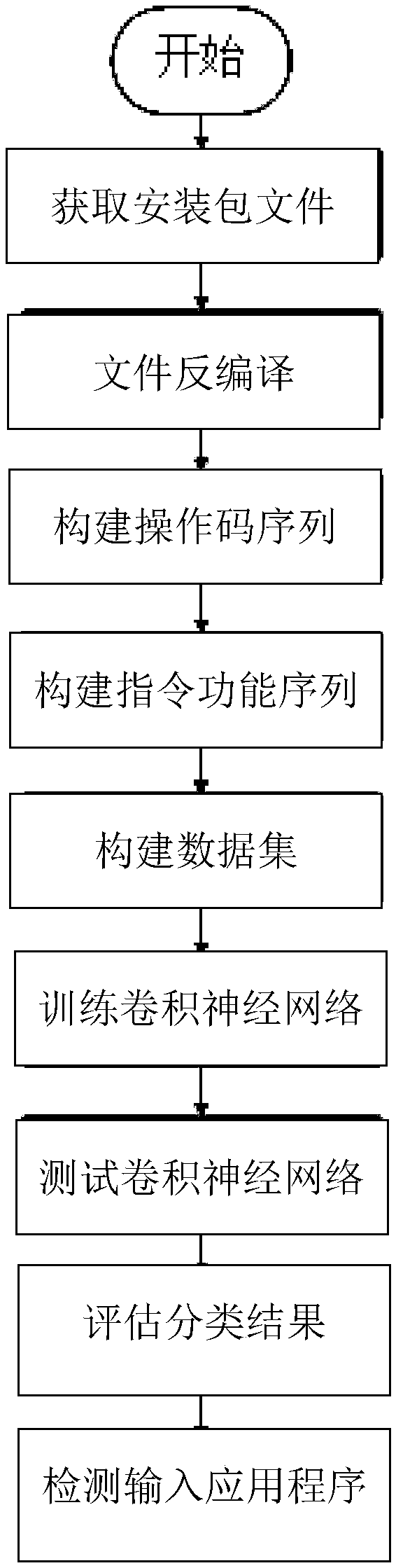
Android malicious application detection method based on dual-channelconvolutional neural network
ActiveCN109165510AHigh classification precision and recallReduce the probability of being attackedPlatform integrity maintainanceApplication softwareNerve network
An Android malicious application detection method based on a dual-channel convolutional neural network is provided. The method includes obtaining an installation package file; decompiling the installation package files; constructing an opcode sequence; construct an instruction function sequence; carrying out vectorization processing on the features of the operation code sequence and the instruction function sequence; training a convolutional neural network; testing the convolutional neural network; evaluating the malicious application detection model; detecting an application to be detected, etc. Compared with the traditional detection model, the malicious application detection model generated by the method provided by the invention has higher classification accuracy and recall rate, and reduces the probability of the Android system being attacked due to missing detection.
Owner:CIVIL AVIATION UNIV OF CHINA
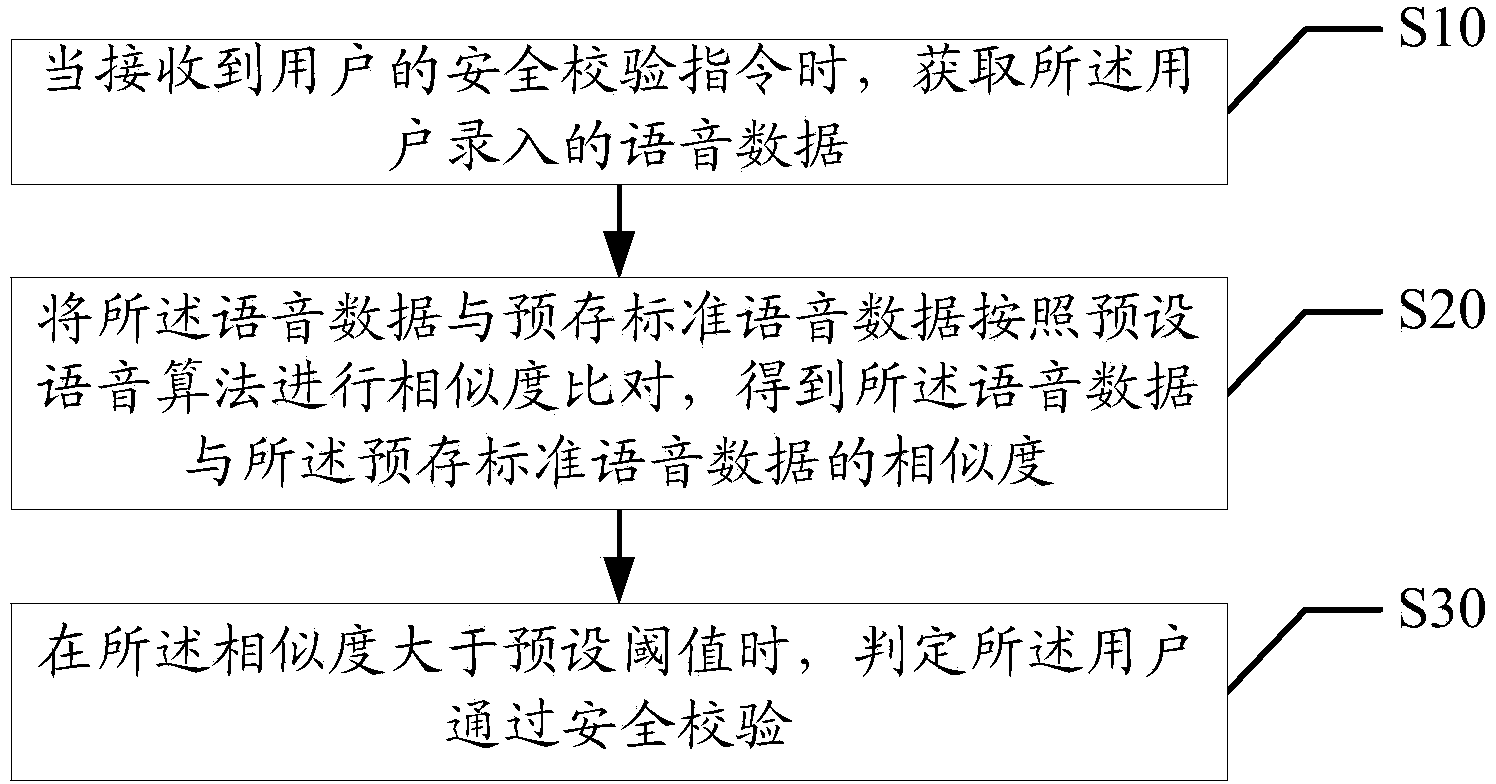
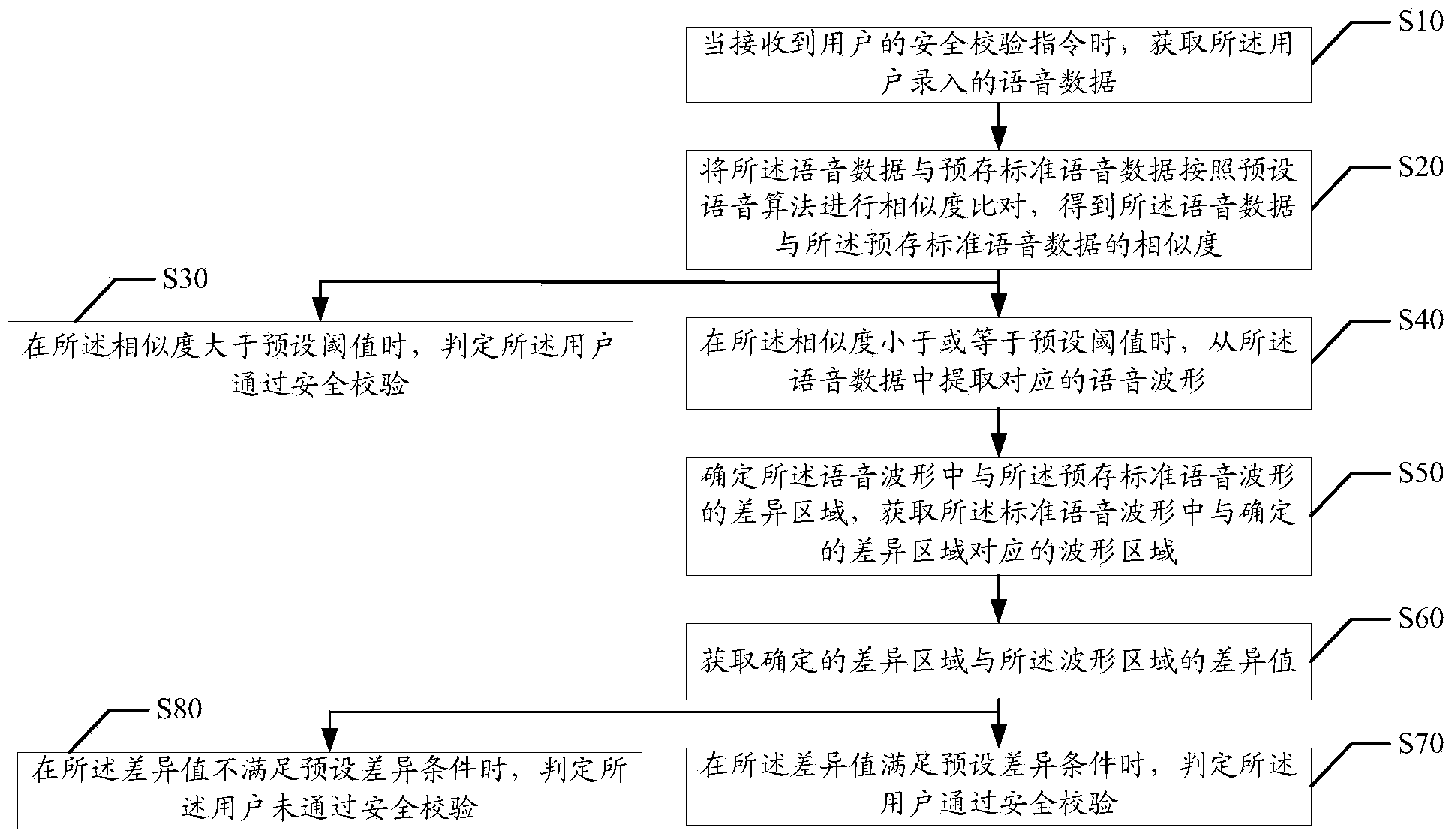
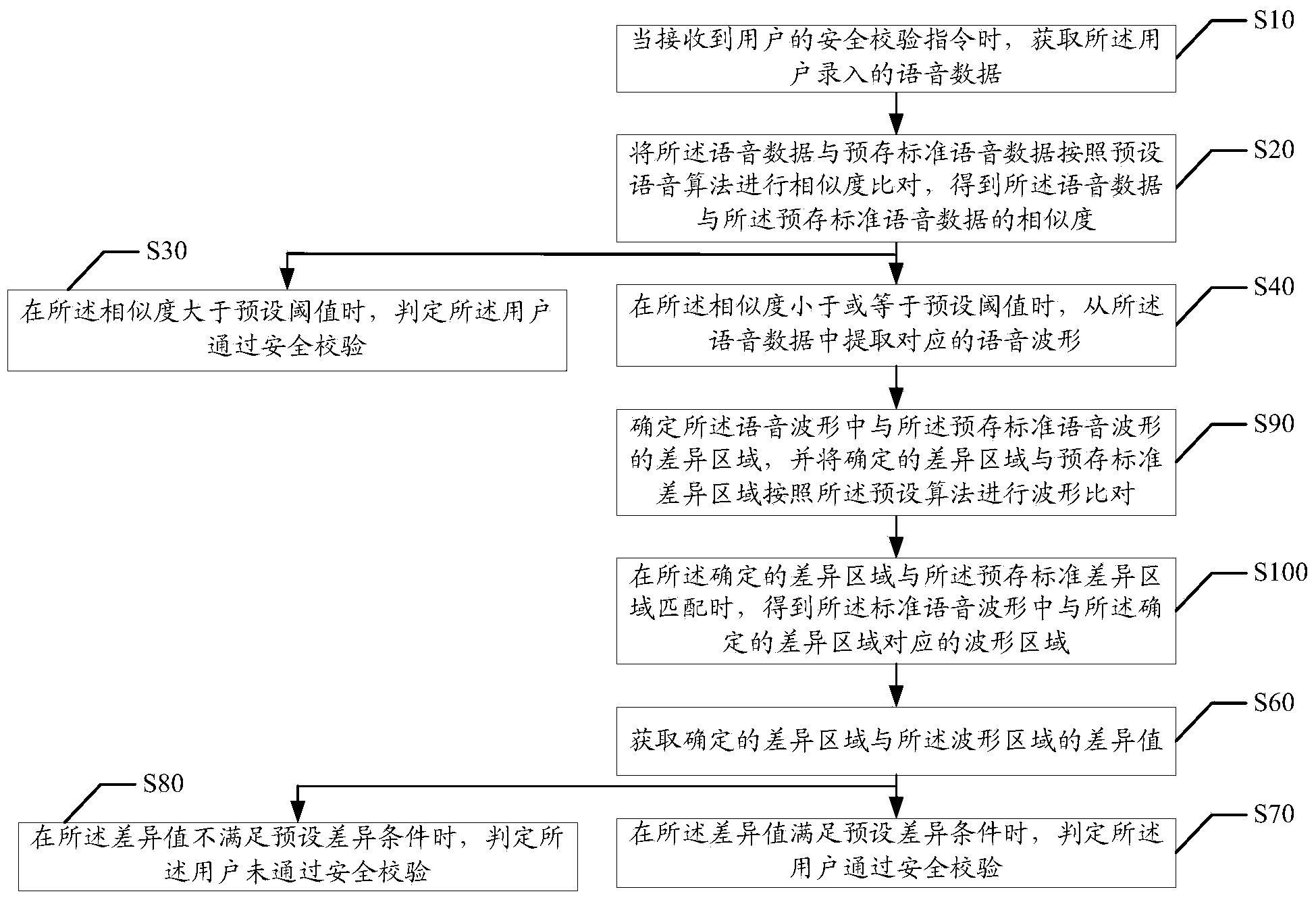
Voice security verification method and apparatus
ActiveCN104022879AGuarantee SimplicityReduce the probability of attackUser identity/authority verificationInformation securityComputer science
The invention discloses a voice security verification method. The method comprises the following steps: when a security verification instruction of a user is received, obtaining voice data recorded by the user; performing similarity comparing between the voice data and prestored standard voice data according to a preset voice algorithm to obtain the similarity between the voice data and the prestored standard voice data; and when the similarity is greater than a preset threshold, determining that the user passes security verification. The invention also discloses a voice security verification apparatus which effectively reduces the hacker attack probability and improves information security while ensuring simplicity of security verification operation.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
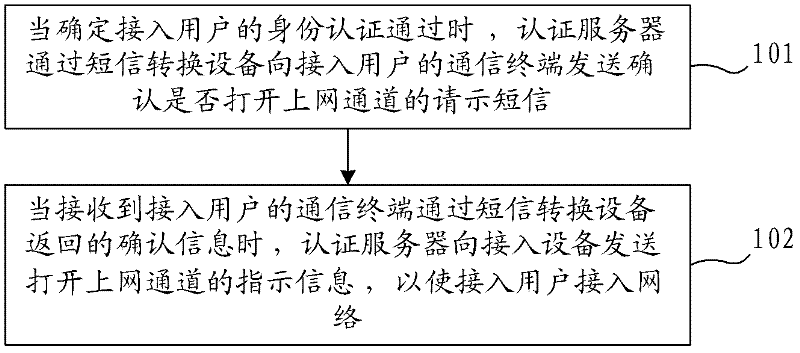
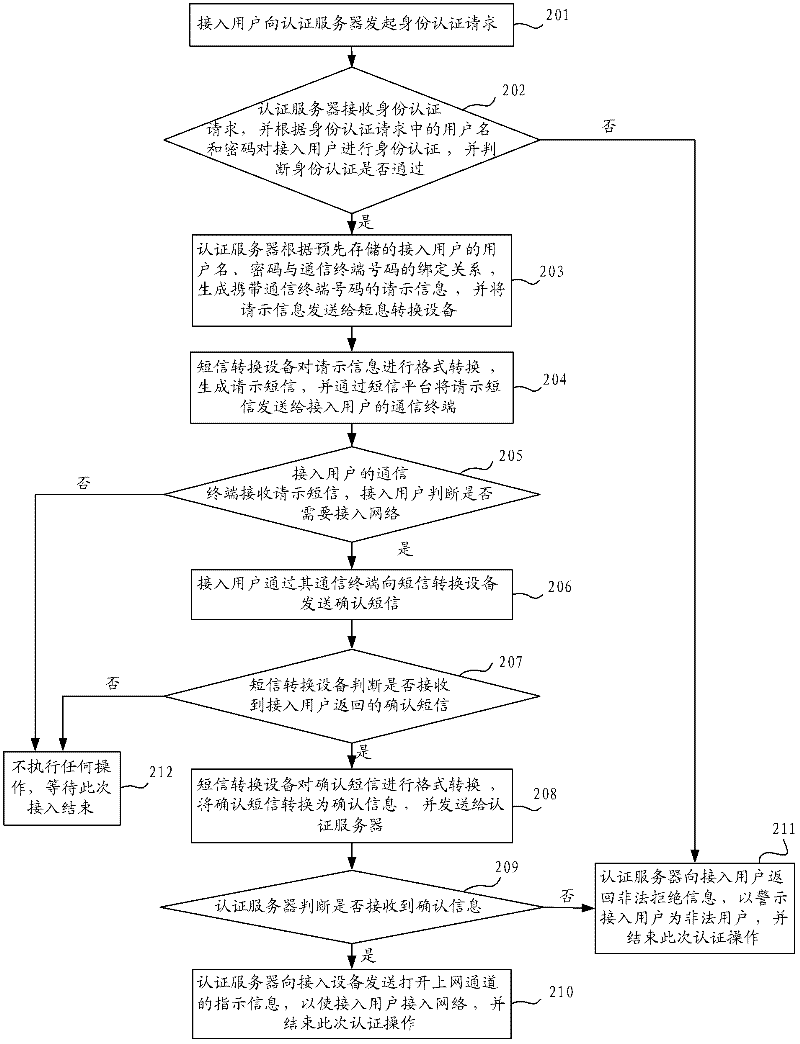
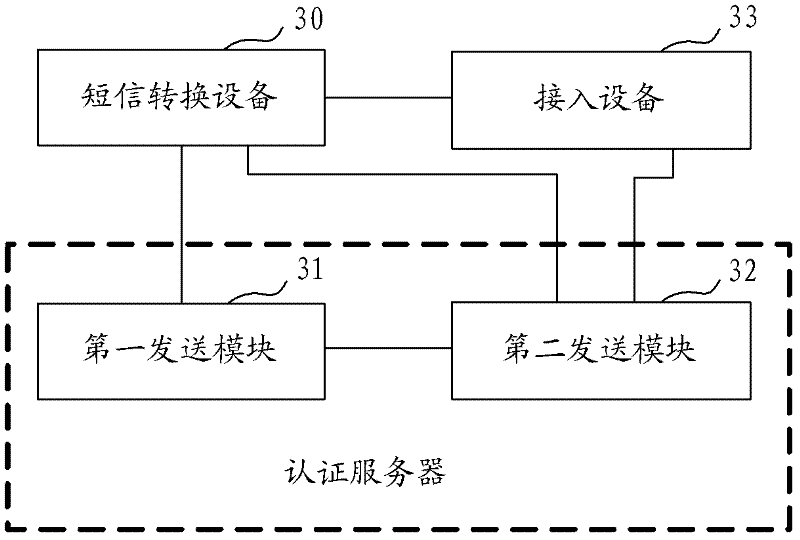
Network access method, system and authentication server
ActiveCN102264050AReduce the probability of attackImprove securityMessaging/mailboxes/announcementsSecurity arrangementAccess methodPassword
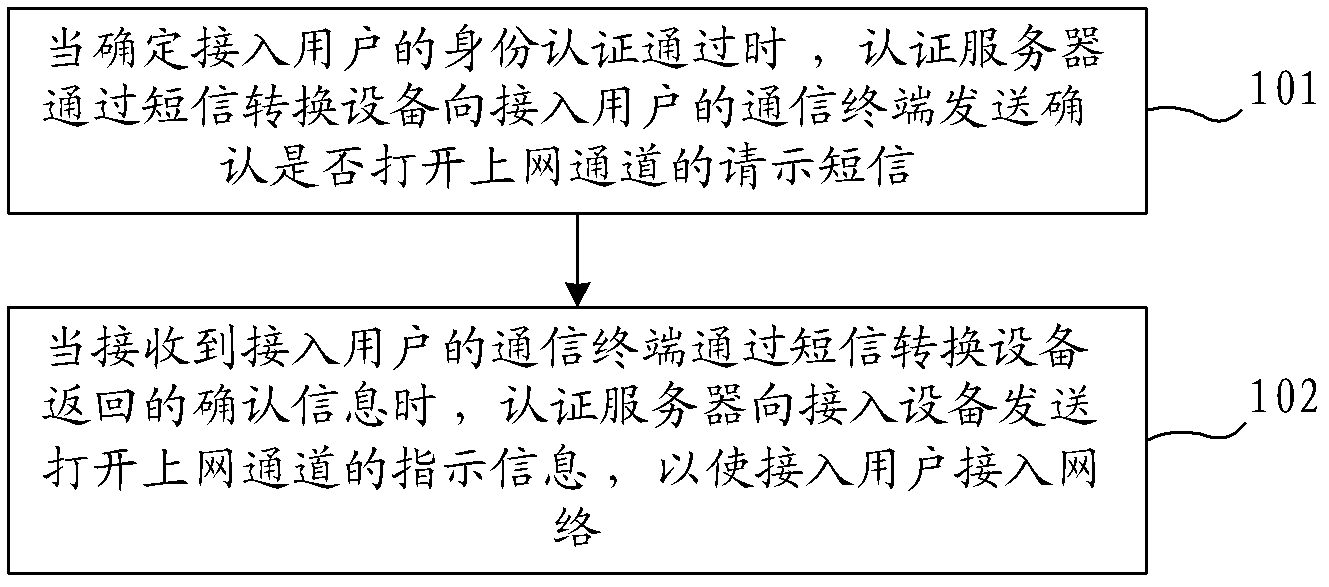
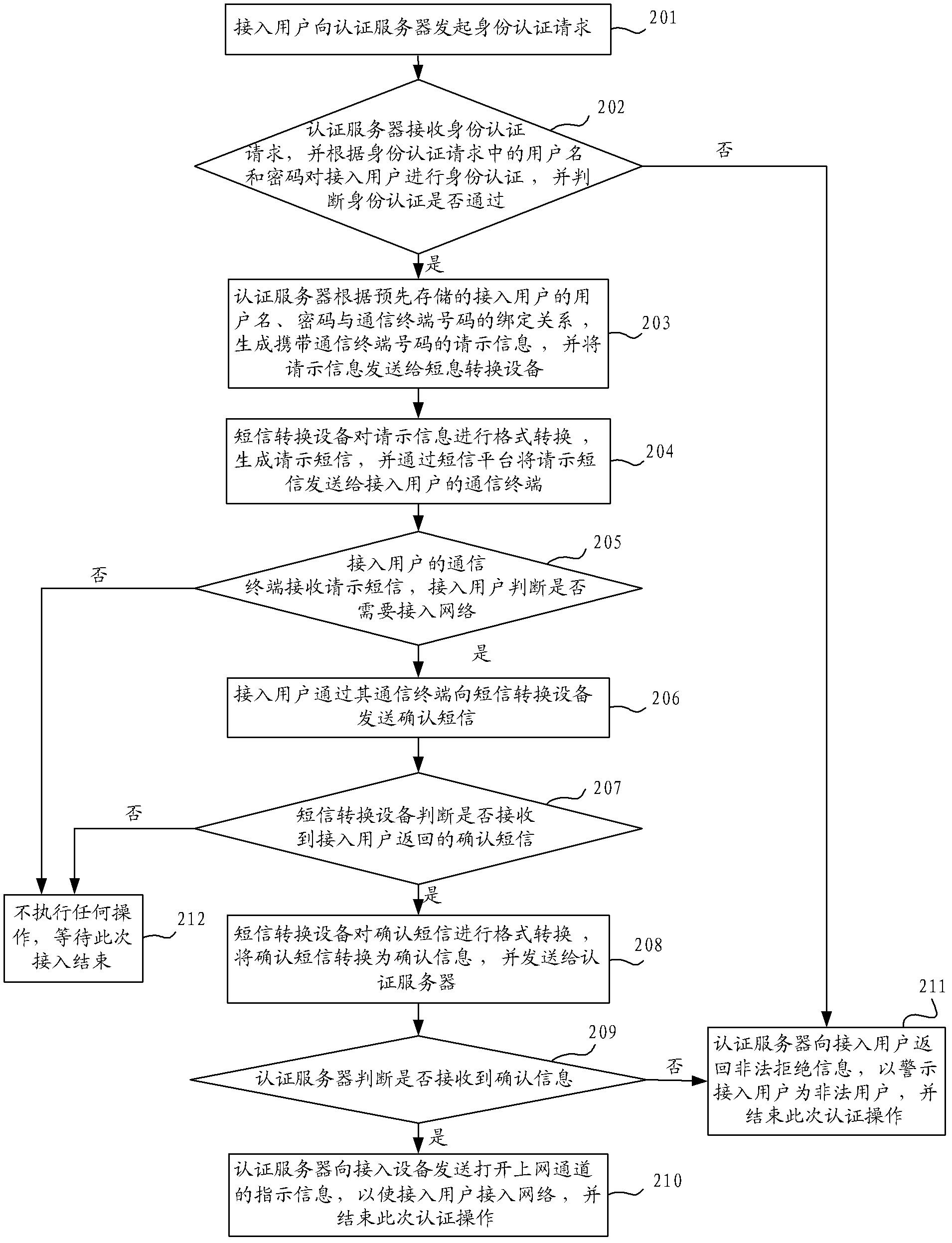
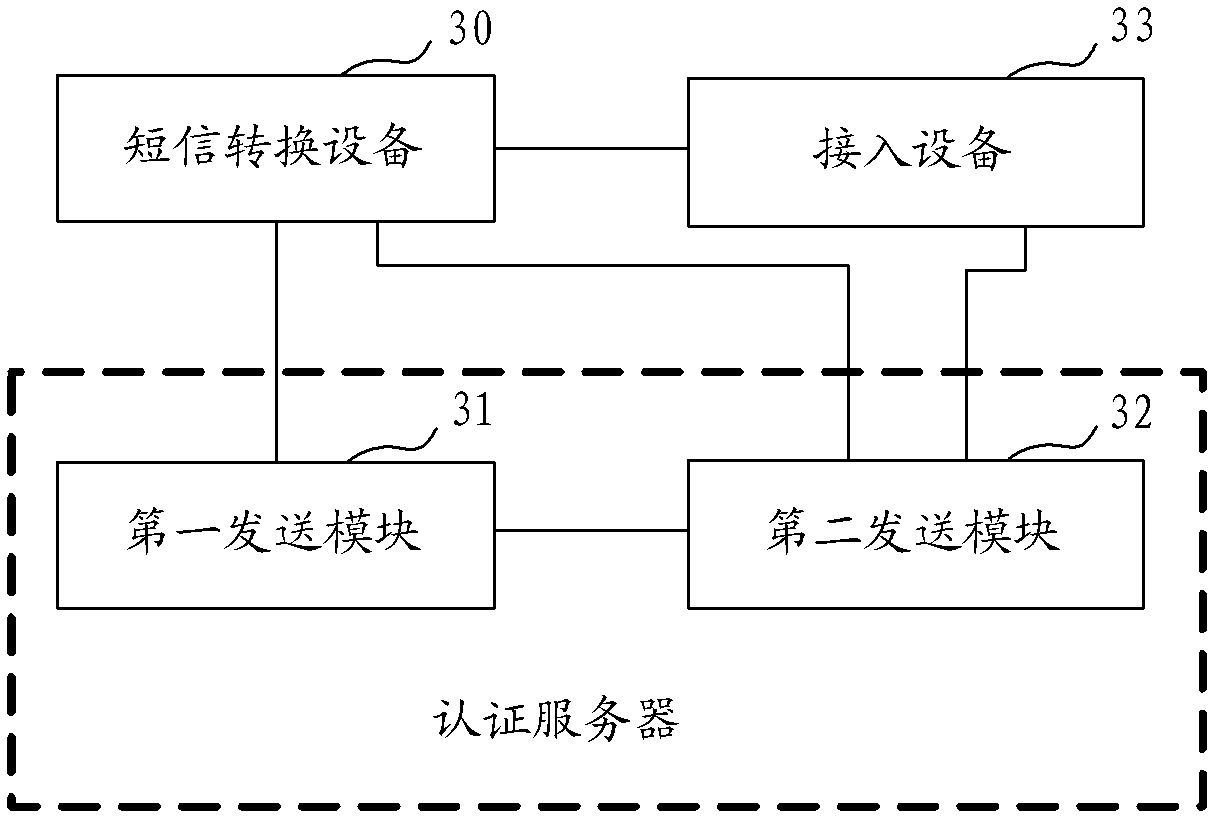
The invention provides a network access method, a network access system and an authentication server. The network access method comprises the following steps that: when an access user passes the identity authentication, the authentication server transmits a request short message for confirming whether an access channel is opened to a communication terminal of the access user through short-message conversion equipment; when a confirmation message returned by the communication terminal of the access user through the short-message conversion equipment is received, the indication information of opening the access channel is transmitted to the access equipment so that the access user accesses the network. By adoption of the technical scheme, the problem that the illegal user uses stolen user names and passwords for identity authentication can be solved, the probability of network attack by the illegal user is reduced and the safety of the network is improved; in addition, compared with the prior art, the technical scheme has the advantages of simplicity in access process and lower access cost.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
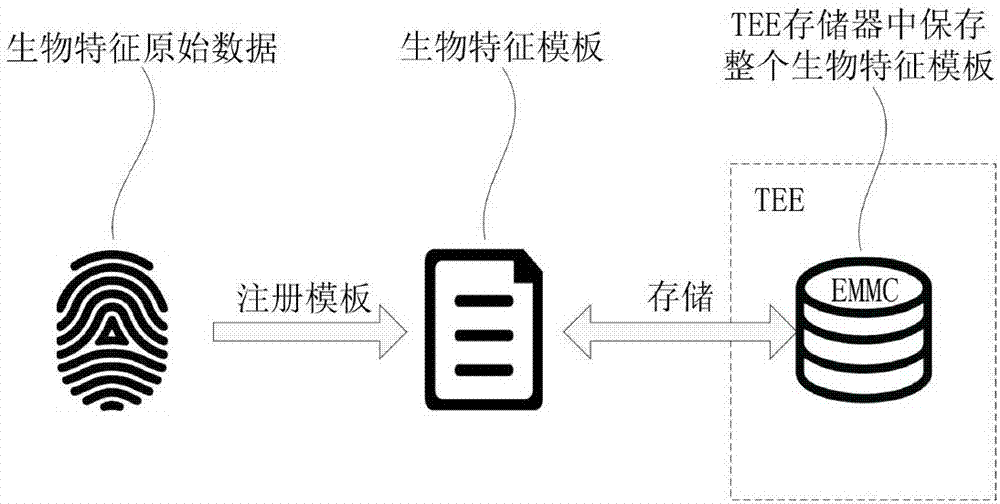
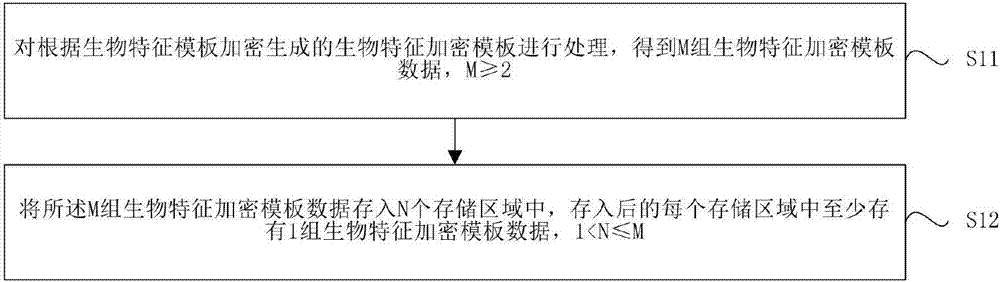
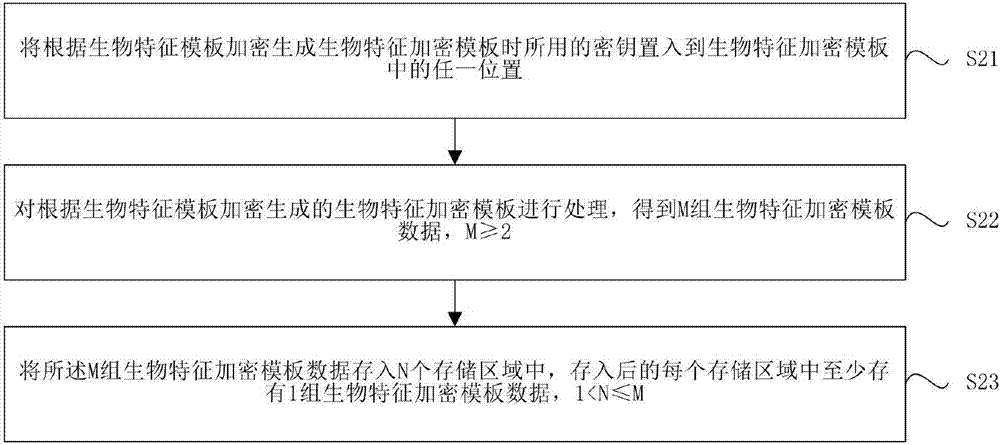
Biological feature template saving and verification method and biological feature identification device and terminal
ActiveCN107113170AReduce the probability of attackReduce leak rateKey distribution for secure communicationUser identity/authority verificationIdentification deviceBiometric encryption
The embodiments of the present invention provides a biological feature template saving and verification method and a biological feature identification device and terminal, and belongs to the biological identification technology field. The biological feature template saving method comprises the steps of processing a biological feature encryption template encrypted and generated according to a biological feature template to obtain M sets of biological feature encryption template data, wherein M >=2; storing the M sets of biological feature encryption template data in N storage areas, at least one set of biological feature encryption template data is saved in each storage area, wherein 1<N<=M. According to the embodiments of the present invention, the biological feature encryption template is processed into multiple sets of biological feature encryption template data, and then the biological feature encryption template data is saved in at least two storage areas dispersedly, so that the multiple sets of biological feature encryption template data is saved in the plurality of storage areas dispersedly, is not easy to leak overall, and accordingly the larger potential safety hazards brought by the prior art to the application of the biological feature template can be eliminated effectively.
Owner:SHENZHEN GOODIX TECH CO LTD
Improved forest algorithm-based Android malicious software detection method
InactiveCN107092827AImprove accuracyReduce the probability of attackPlatform integrity maintainanceFeature vectorData set
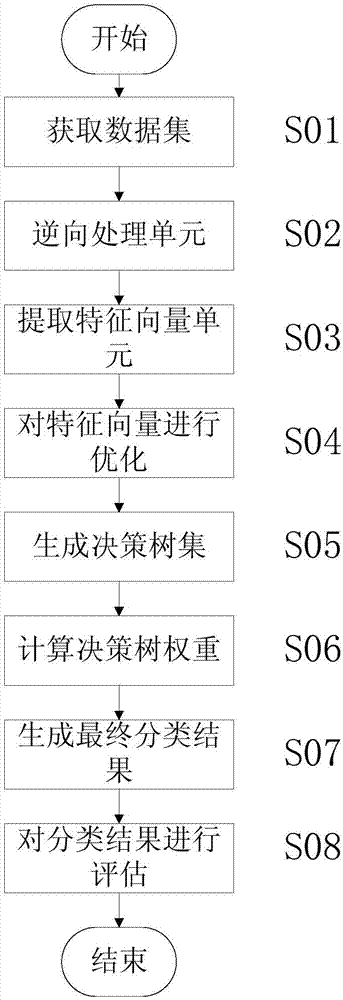
The invention discloses an improved forest algorithm-based Android malicious software detection method. The method comprises an S01 stage of obtaining a data set, an S02 stage of carrying out reverse processing, an S03 stage of extraction feature vectors, an S04 stage of optimizing the feature vectors, an S05 stage of generating a decision tree set, an S06 stage of calculating a decision tree weight, an S07 stage of generating a final classification result and an S08 stage of assessing the classification result. Compared with the traditional detection method, the improved forest algorithm-based Android malicious software detection method has higher classification precision, and has the effects of improving the correctness of malicious software detection and reducing the probability that Android systems are attacked due to detection errors.
Owner:CIVIL AVIATION UNIV OF CHINA
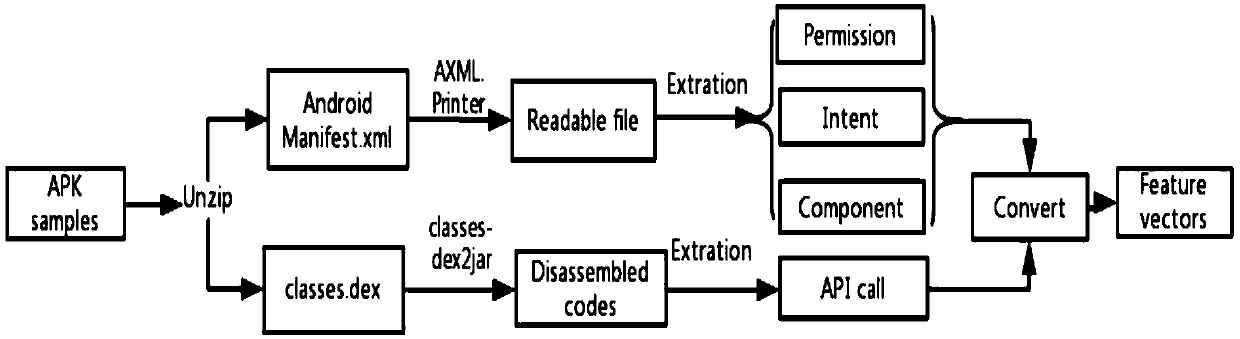
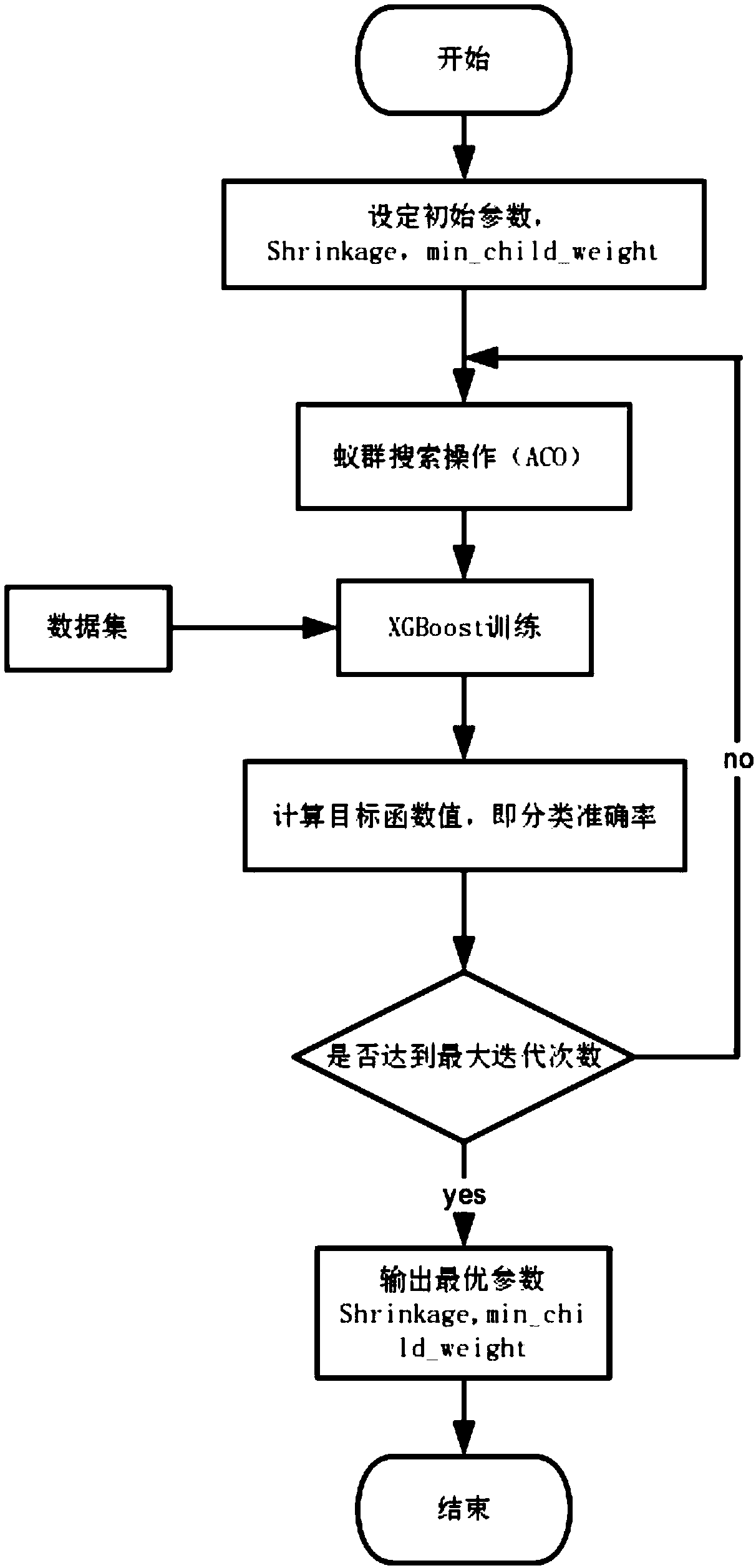
An Android malware detection method based on XGBoost machine learning algorithm
ActiveCN109543406AImprove accuracyEasy to classifyArtificial lifePlatform integrity maintainanceSoftwareFeature matrix
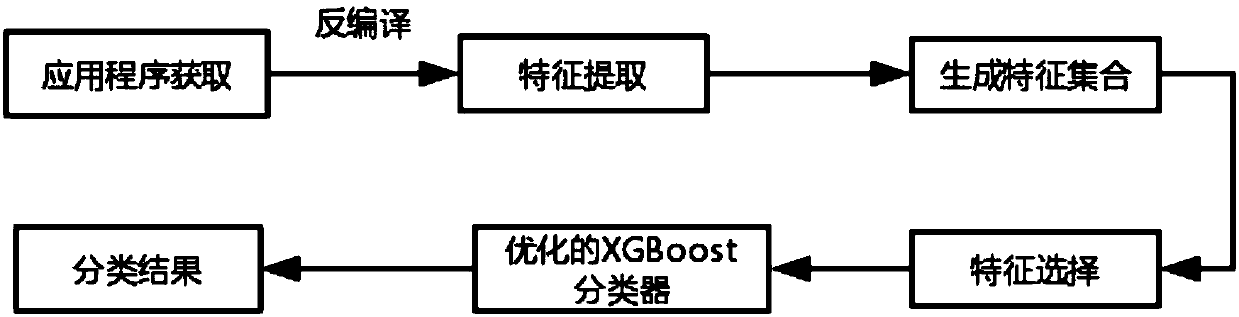
The invention relates to an Android malware detection method based on XGBoost machine learning algorithm. The method includes: extracting Permission Intent, Component and API call feature by decompiling the apk file, and composing a feature matrix quantitatively; using the parallelism and strong robustness of ant colony algorithm, optimizing the parameters of XGBoost classifier to obtain the optimal target and the optimal parameter combination of XGBoost. Compared with the traditional XGBoost algorithm, the improved XGBoost machine learning algorithm proposed by the invention, has higher classification accuracy during Android malware detection, improves the accuracy of malware detection, and reduces the probability of Android system attack due to detection errors.
Owner:GUANGDONG UNIV OF TECH
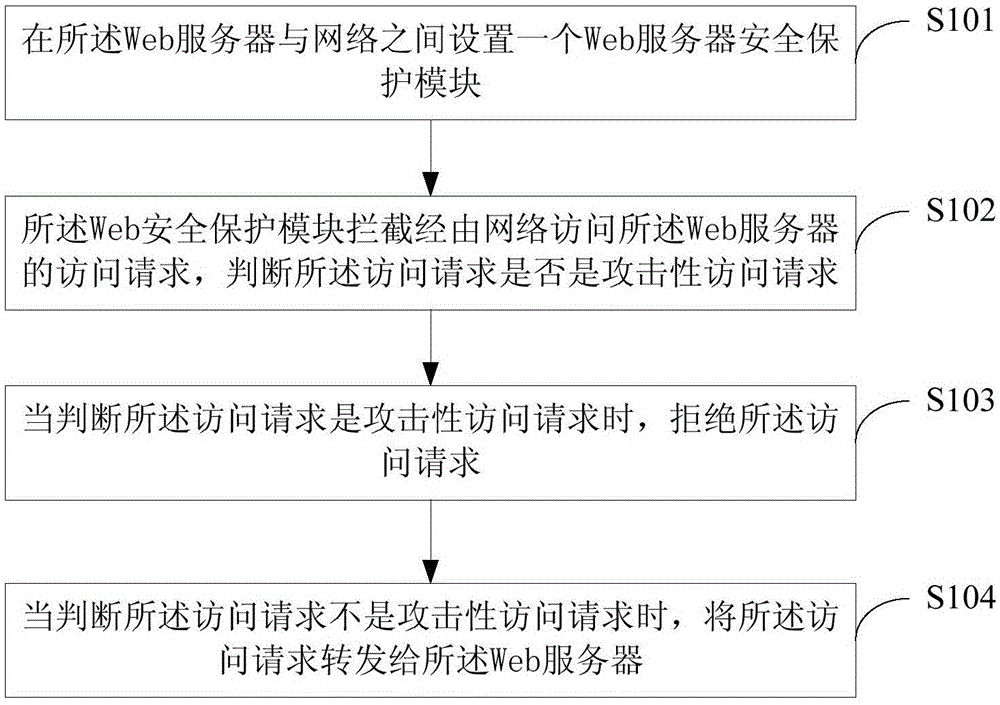
Method and device for preventing Web server from being attacked
InactiveCN106341377AReduce the probability of attackMeans of preventing attacksTransmissionComputer networkWeb service
The invention discloses a method and a device for preventing a Web server from being attacked, and the method and the device relate to the technical field of the internet. The method comprises the steps of: setting a Web server security protection module between the Web server and a network; intercepting an access request for accessing the Web server over the network by means of the Web server security protection module, and judging whether the access request is an attacking access request; rejecting the access request when judging that the access request is an attacking access request; and forwarding the access request to the Web server when judging that the access request is not an attacking access request. The method and the device provided by the invention effectively prevent various kinds of emerging attack means, and reduce the probability of the Web server being attacked.
Owner:山东捷讯通信技术有限公司
Method, device and electronic equipment for protecting target application
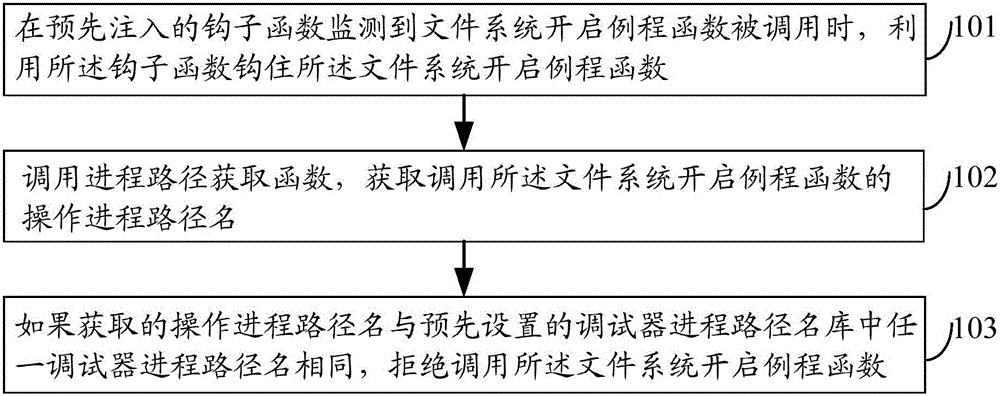
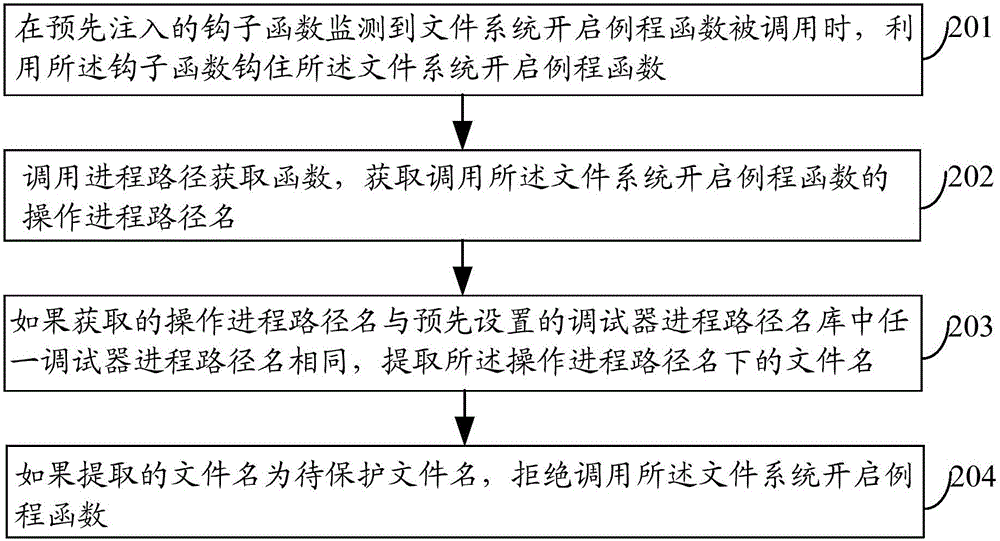
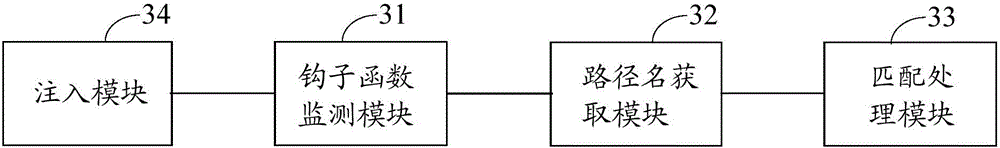
InactiveCN105893846AImprove securitySolve the problem of vulnerability to attack and low securityPlatform integrity maintainanceFile systemApplication software
The embodiment of the invention discloses a method, device and electronic equipment for protecting target application, and relates to the information security technology, wherein the probability of application attack can be reduced, and the application security is improved. The method comprises the following steps: when the pre-input hook function monitors that a file system opening routine function is called, hooking the file system opening routine function using the hook function; calling a progress path acquisition function, and acquiring the operation progress path name calling the file system opening routine function; and if the acquired operation progress path name is the same as any debugger progress path name in a preset debugger progress path name library, rejecting the calling of the file system opening routine function. The method, device and electronic equipment are applicable to the anti-debugging protection of application.
Owner:ZHUHAI BAOQU TECH CO LTD
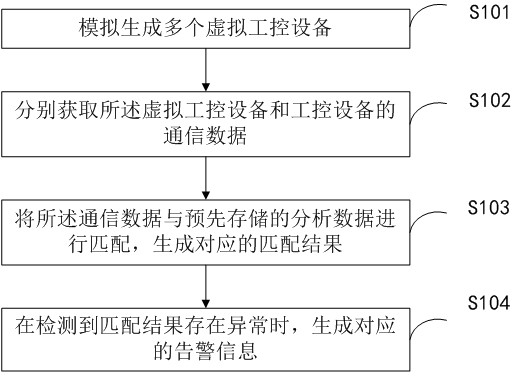
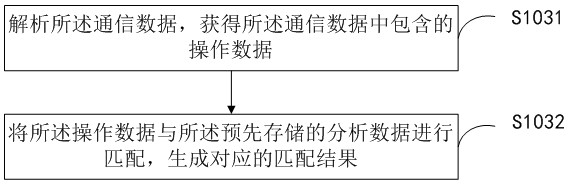
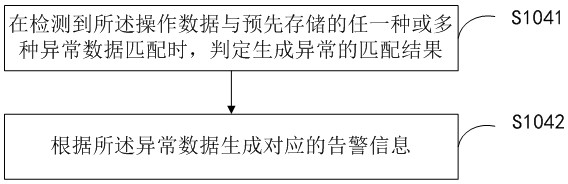
Monitoring method and device for industrial control equipment
PendingCN112822291AReduce the probability of attackImprove Anomaly Detection EfficiencyData switching networksAnomaly detectionControl engineering
The invention provides an industrial control equipment monitoring method and device, wherein the method comprises the steps: simulating and generating a plurality of virtual industrial control equipment, respectively obtaining the communication data of the virtual industrial control equipment and the industrial control equipment, carrying out the matching of the communication data with the pre-stored analysis data, generating a corresponding matching result, and when the abnormality of the matching result is detected, carrying out the monitoring of the industrial control equipment, and generating corresponding alarm information. According to the method and the device, the probability that the industrial control equipment is attacked is reduced by simulating and generating a plurality of virtual industrial control equipment, the communication data of the virtual industrial control equipment and the industrial control equipment are respectively acquired and are matched with the pre-stored analysis data, and the corresponding alarm information is generated when the communication data is detected to be abnormal, so that the abnormal detection efficiency of the industrial control equipment is improved, and the safety of the industrial control network is ensured.
Owner:STATE GRID FUJIAN ELECTRIC POWER RES INST +1
Method for protecting overflow of buffer zone
InactiveCN101350051ATroubleshoot technical issues with overflowTime-consuming to writeProgram/content distribution protectionData segmentBuffer overflow
The invention relates to a method for protecting the readin and the readout of computer information, in particular to a method for protecting buffer overflow. The method is mainly realized through a non-executive buffer area, and attackers can not execute a code of an input baffle area which is implanted with an attacked program through enabling the data segment address space of the attacked program to be non-executive. The method of the invention mainly solves the technical problems of a method which is realized through compiling a correct code that not only the compiling procedure wastes time, but also the buffer overflow can not be completely solved, and the probability that a system is attacked due to the buffer overflow is lowered.
Owner:SHANGHAI MINHANG HIGH SCHOOL +1
Method and device for writing safety verification
ActiveCN104021324AGuarantee SimplicityReduce the probability of attackCharacter and pattern recognitionDigital data authenticationProgramming languageData input
The invention discloses a method for writing safety verification. The method includes the steps that when a safety verification command of a user is received, writing data input by the user are obtained; similarity comparison is conducted on the writing data and pre-stored standard writing data according to a preset writing algorithm, so that similarity between the writing data and the pre-stored standard writing data is obtained; when the similarity is larger than a preset threshold value, it is judged that the user passes safety verification. The invention further discloses a device for writing safety verification. Simplicity of safety verification is guaranteed, the probability of hacker attacks is effectively reduced, and information safety is improved.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
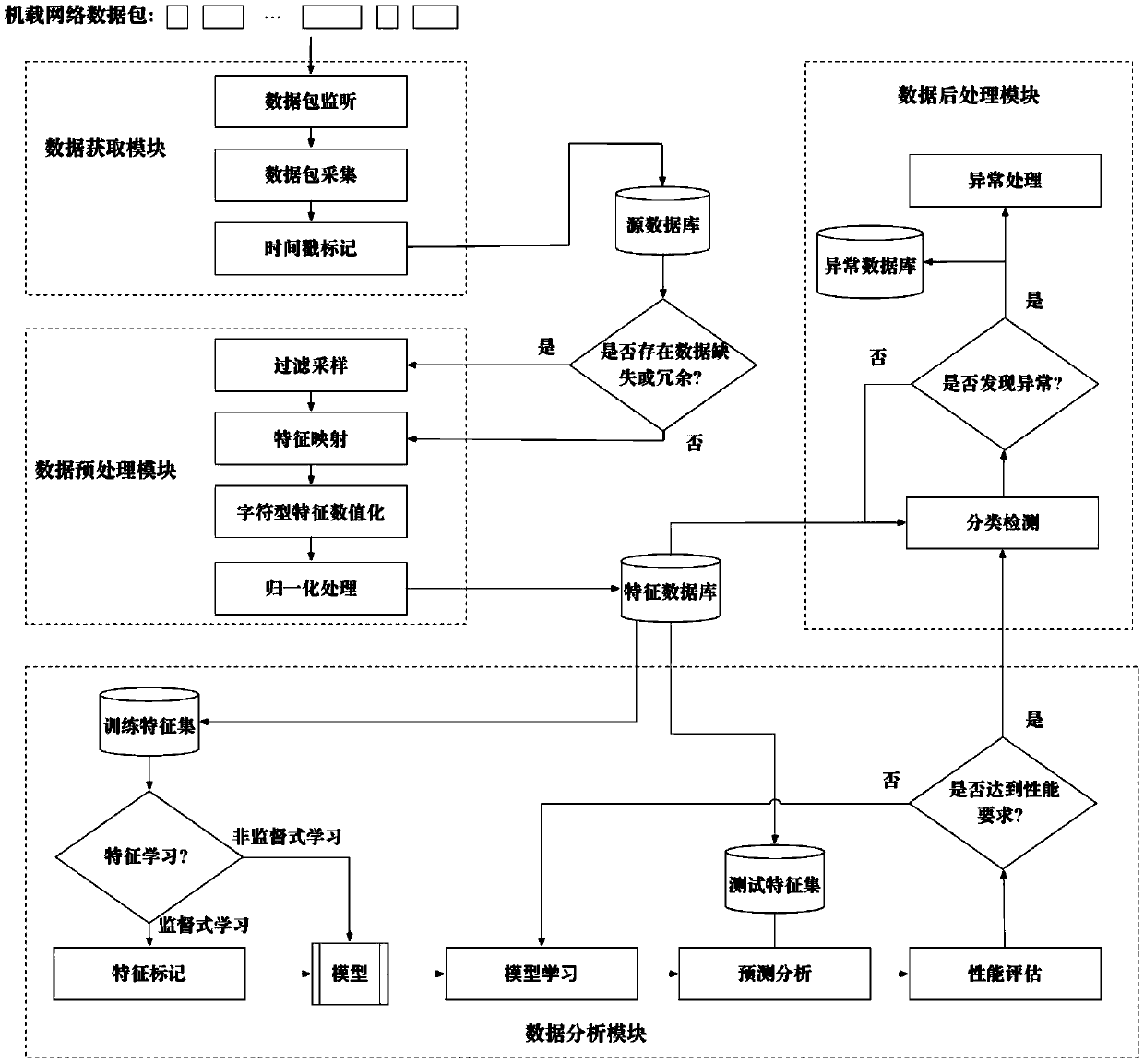
Airborne network intrusion detection method based on deep learning
InactiveCN109639662AReduce the probability of attackEasy to detectNeural architecturesTransmissionNetwork packetFeature learning
The invention discloses an airborne network intrusion detection method based on deep learning. The method includes the steps of data packet monitoring, data packet collection, time stamp labeling, filtering sampling, feature mapping, character-type feature digitization, normalization processing, feature learning, performance evaluation and the like. Compared with traditional detection models, an airborne network intrusion detection model generated by the method provided by the invention has better detection performance, and decreases probability that an airborne network is attacked due to missed detection or false reporting.
Owner:CIVIL AVIATION UNIV OF CHINA
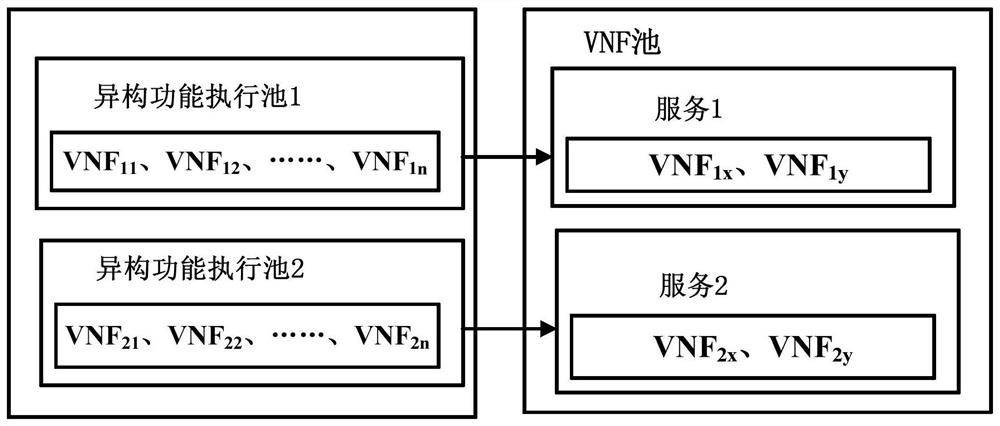
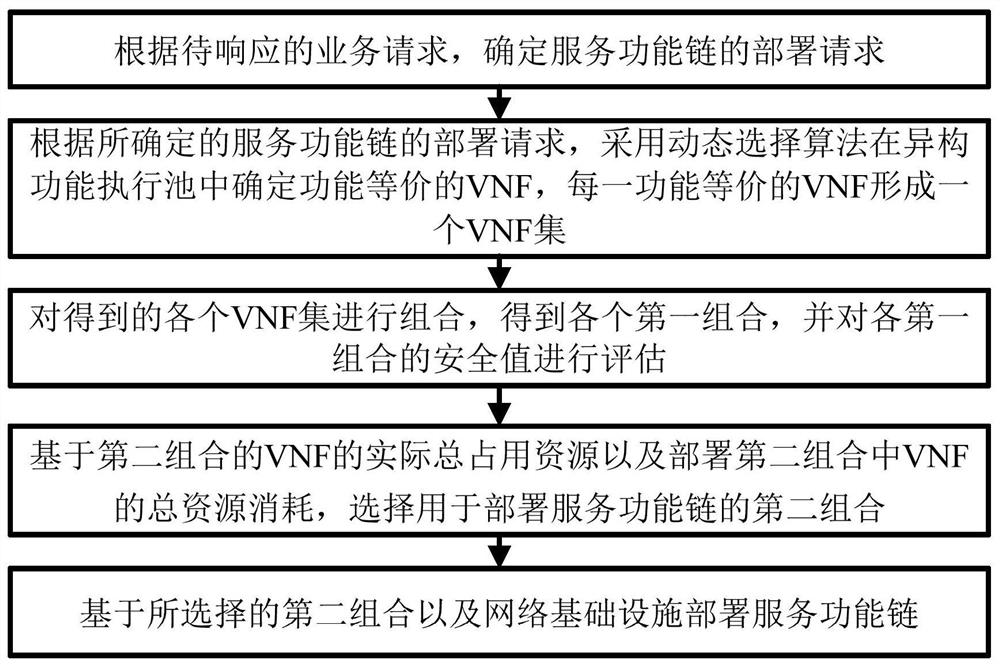
Service function chain deployment method and device
ActiveCN111800291AMeet security needsReduce the probability of attackData switching networksVirtualizationEngineering
The embodiment of the invention provides a service function chain deployment method and device, and the method comprises the steps: selecting a VNF from all preset virtual network functions (VNFs) ofeach service type requested by a service request, and obtaining a VNF set with the number of VNFs being all numbers in a preset number range; obtaining each first combination, wherein each first combination comprises a VNF set corresponding to each service type; based on the adjusted security value and deployment consumption of each second combination, selecting a second combination for deployingthe service function chain to be deployed in each second combination, the second combination being a first combination in which the security value of the first combination is greater than an expectedsecurity value; and deploying the to-be-deployed service function chain for the VNF in the selected second combination according to a preset logic sequence. When the scheme provided by the embodimentof the invention is applied to deploy the service function chain, the security of the deployed service function chain can be improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
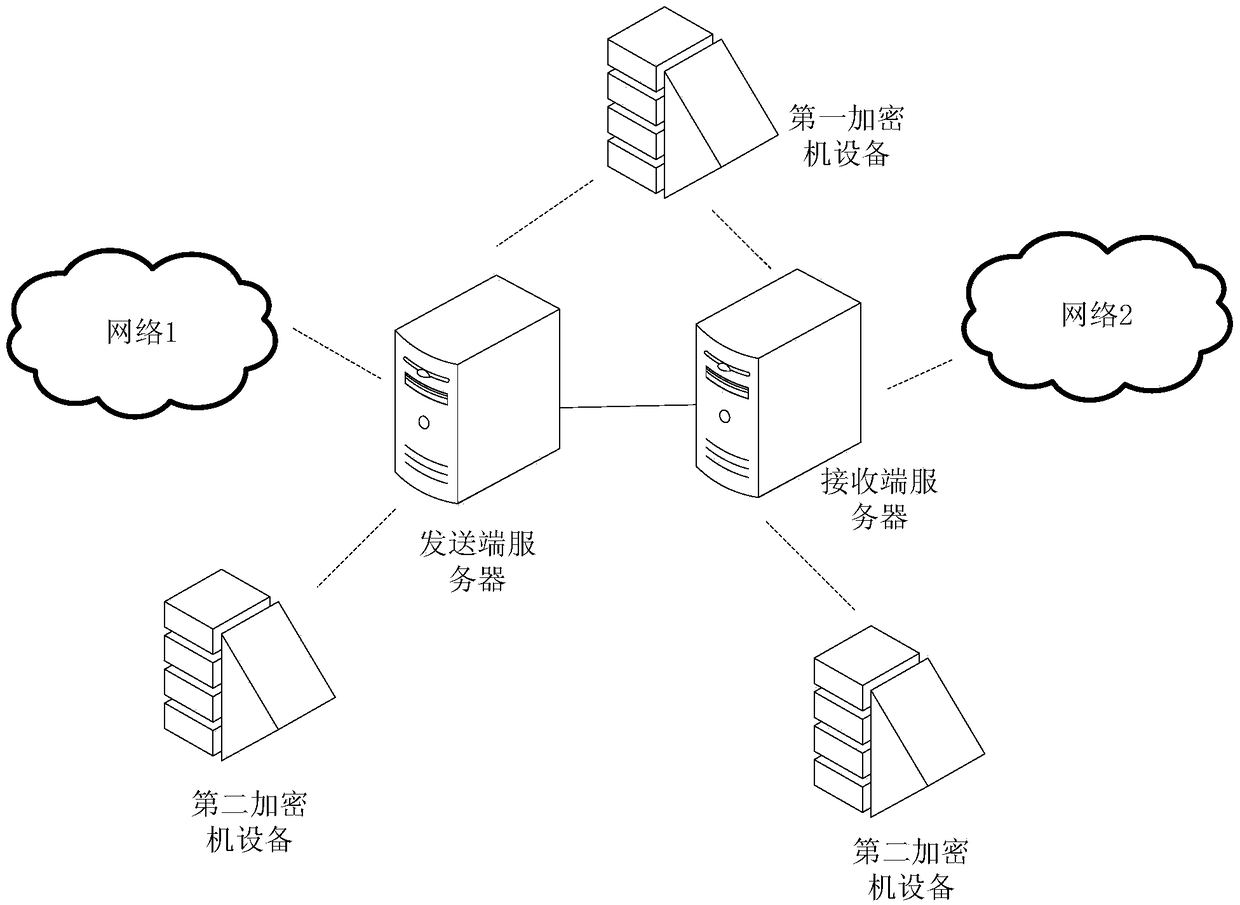
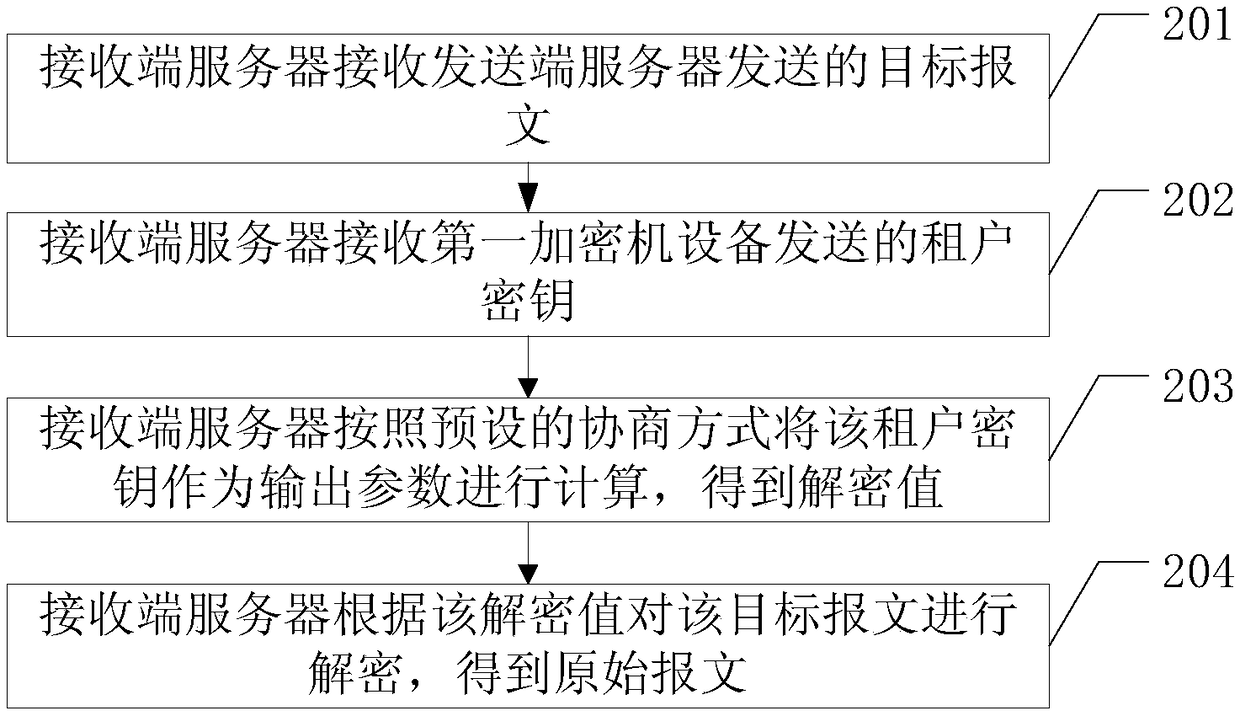
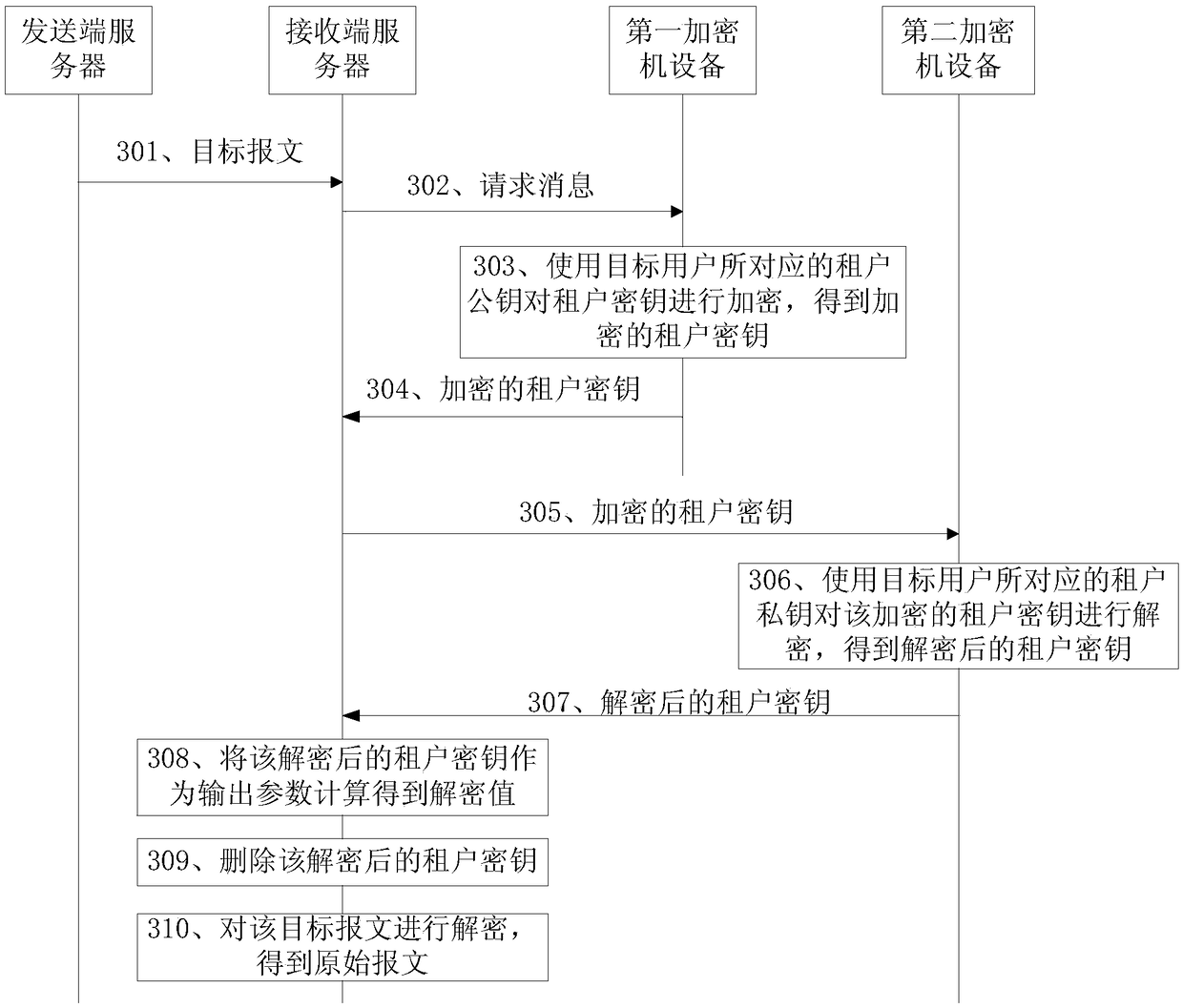
A message processing method and a server at a receiving end
ActiveCN109104273AImprove confidentialityImprove securityKey distribution for secure communicationComputer hardwareMessage processing
The embodiment of the application discloses a message processing method and a receiving end server. A method for embodiment of the present application includes: the receiving end server receives the target message sent by the sending end server, the target message is the message encrypted by the sending end server according to the encryption value, and the encryption value is the encryption valuecalculated by the sending end server according to the preset negotiation mode by taking the tenant key corresponding to the target user as an output parameter. The receiving end server receives the tenant key sent by the first encryptor device, and the first encryptor device is a device storing a tenant key corresponding to a user; the receiving end server calculates the tenant key as an output parameter according to the preset negotiation mode to obtain a decryption value; the receiving end server decrypts the target message according to the decryption value to obtain the original message.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
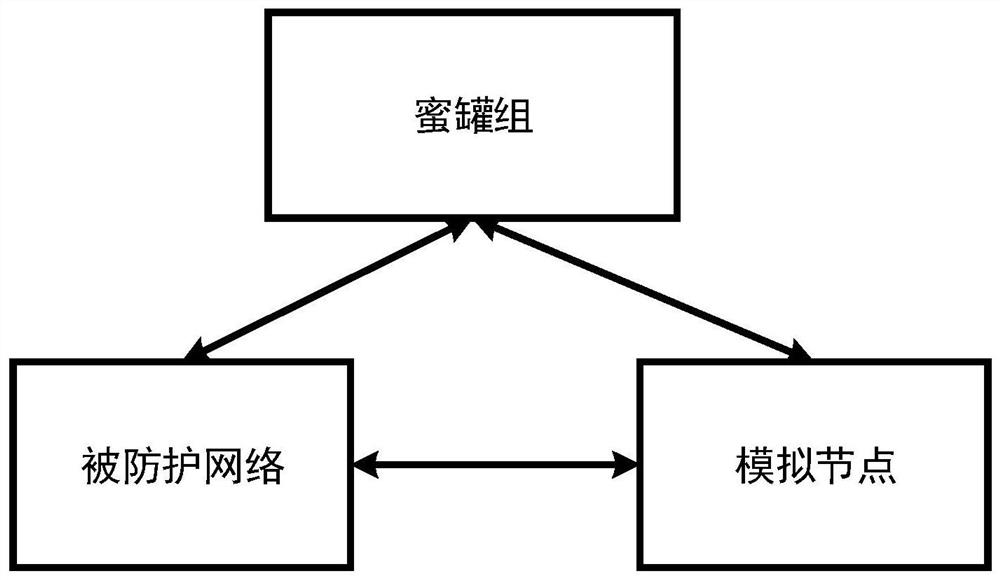
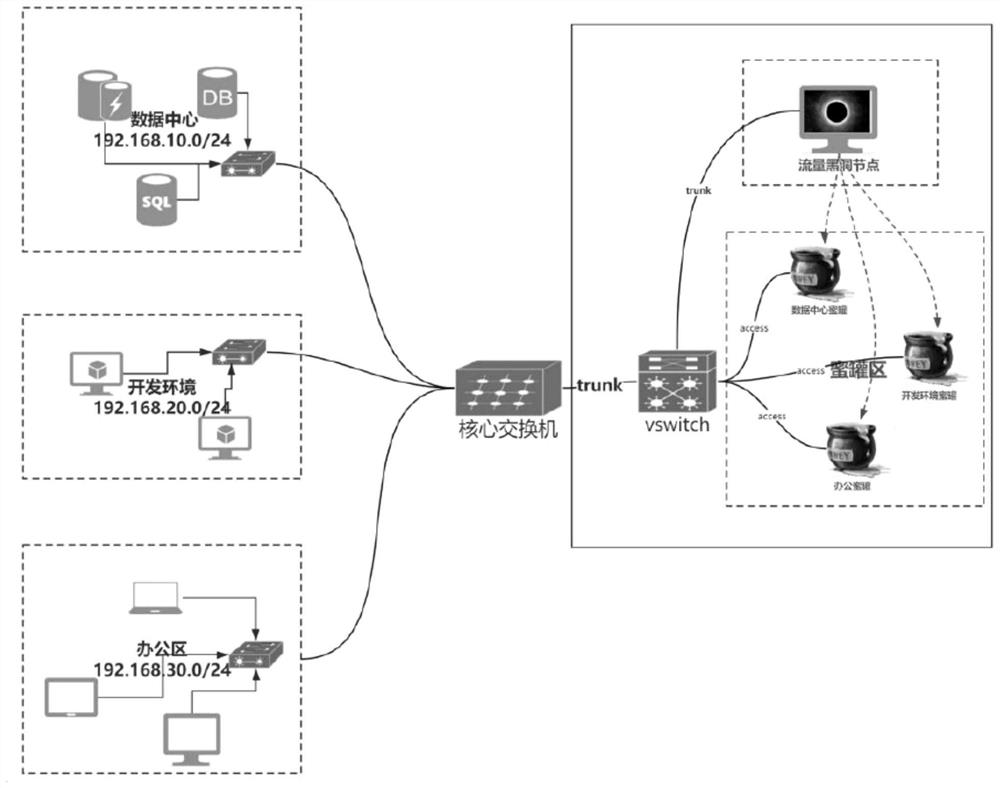
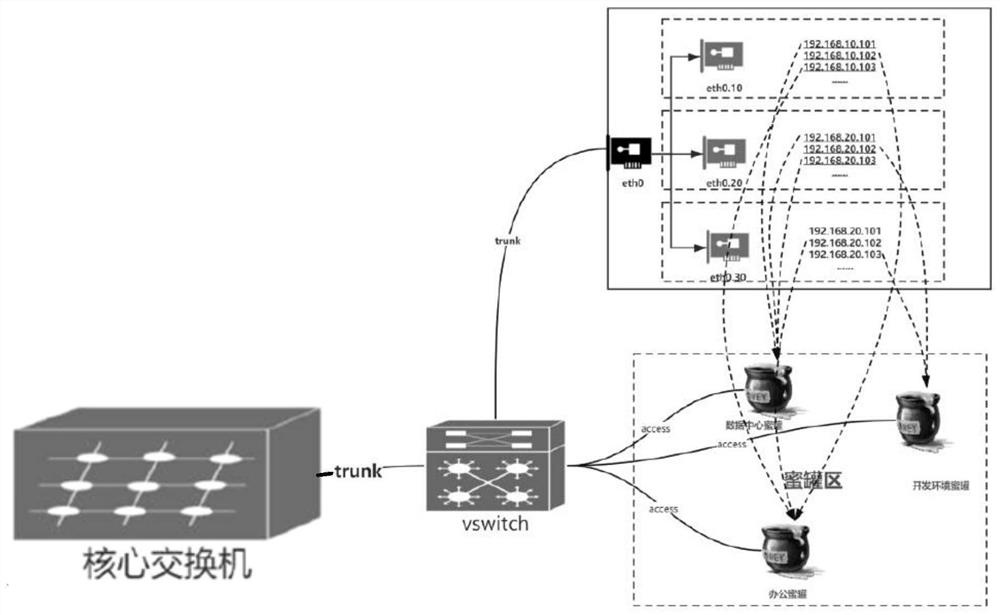
Honeypot protection system
ActiveCN113612783AImprove securityReduce the probability of being attackedTransmissionSoftware simulation/interpretation/emulationIp addressAttack
The invention discloses a honeypot protection system, which uses a simulation node to simulate a real node in a protected network, and the simulation node is configured with all idle IP addresses in the protected network, so that the simulation node can be accessed externally as the real node in the protected network. Under the condition, if an attacker accesses the protected network, the attacker does not only access the real node in the protected network but possibly accesses the simulation node, but the simulation node does not run the actual network service, so that the probability that the protected network is attacked is reduced, and the probability that the real server is attacked is also reduced. Meanwhile, the honeypot group can capture the flow data of the access simulation node and the protected network, so that the attack information can be captured by the honeypot, and the network safety is protected and improved.
Owner:杭州安恒信息安全技术有限公司
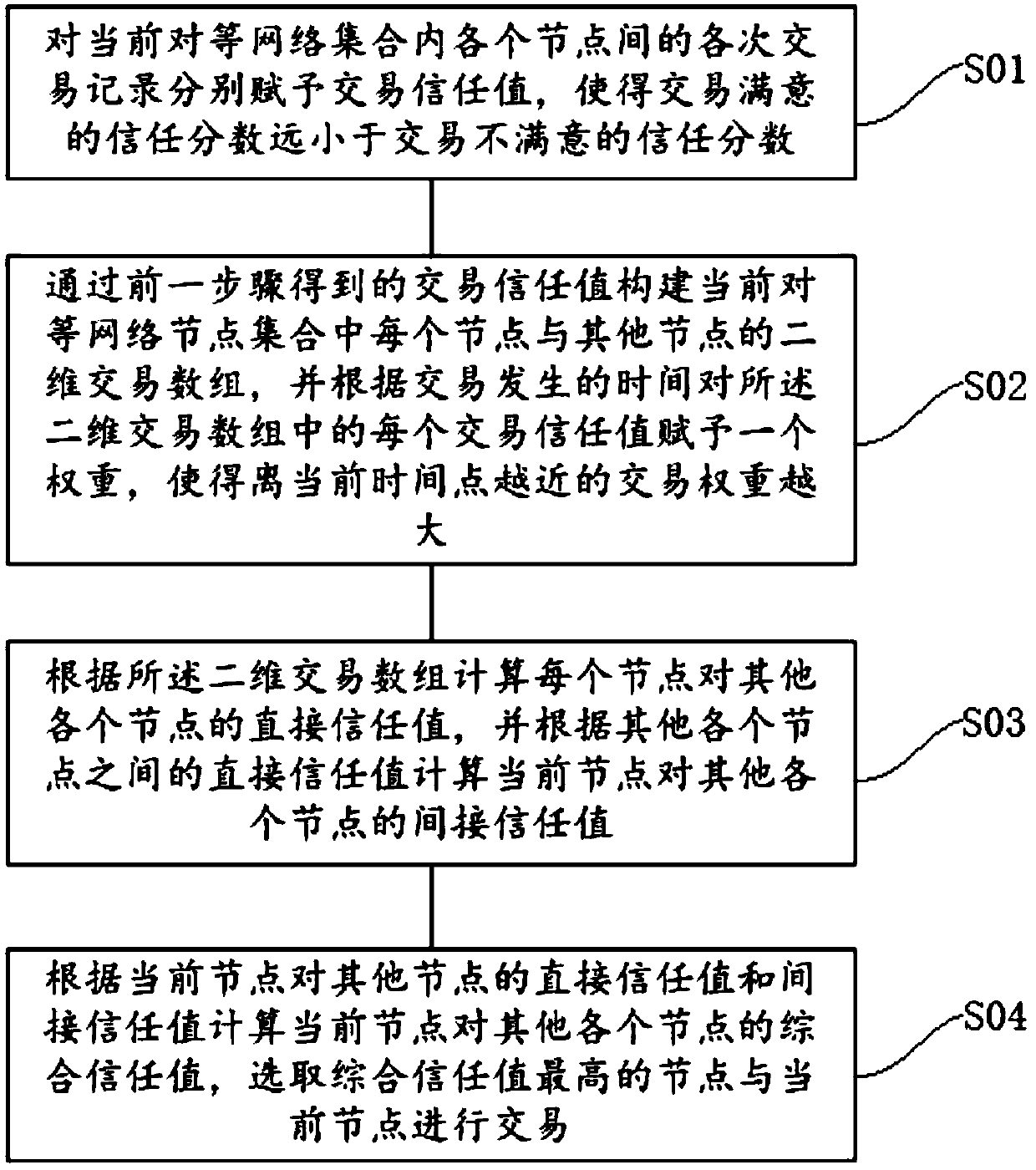
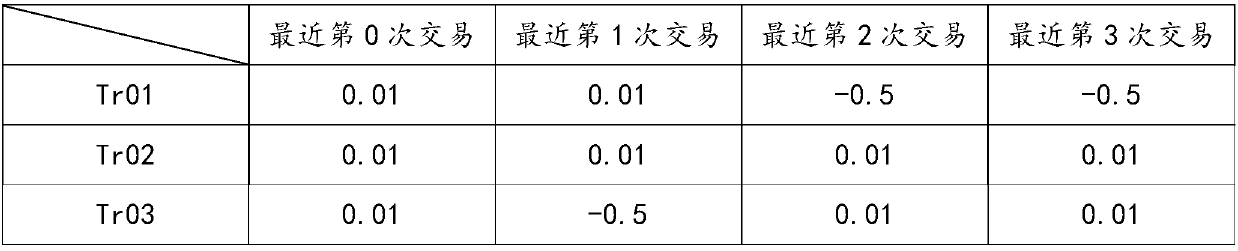
Method and system for selecting optimal transaction node in peer-to-peer network set, and storage medium
InactiveCN108833493AComprehensive trust value dropsReduce the probability of attackTransmissionArray data structureTrust score
The invention discloses a method and system for selecting an optimal transaction node in a peer-to-peer network set, and a storage medium. The method comprises: transaction trust values are given to all transaction records among all nodes in a current peer-to-peer network set respectively, so that the trust scores with transaction satisfaction are far less than trust scores of transaction dissatisfaction; on the basis of the transaction trust values, a two-dimensional transaction array between each node and other nodes in the current peer-to-peer network set is constructed and a time weight isassigned for each transaction trust value in the two-dimensional transaction array; according to the two-dimensional transaction array, direct trust values of all nodes with all other nodes are calculated and indirect trust values of one current node with all other nodes are calculated based on the direct trust values between all other nodes; and according to the direct trust values and indirecttrust values of the current node with other nodes, a comprehensive trust value of the current node with all other nodes is calculated and the node with the highest comprehensive trust values is selected to carry out transaction with the current node.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
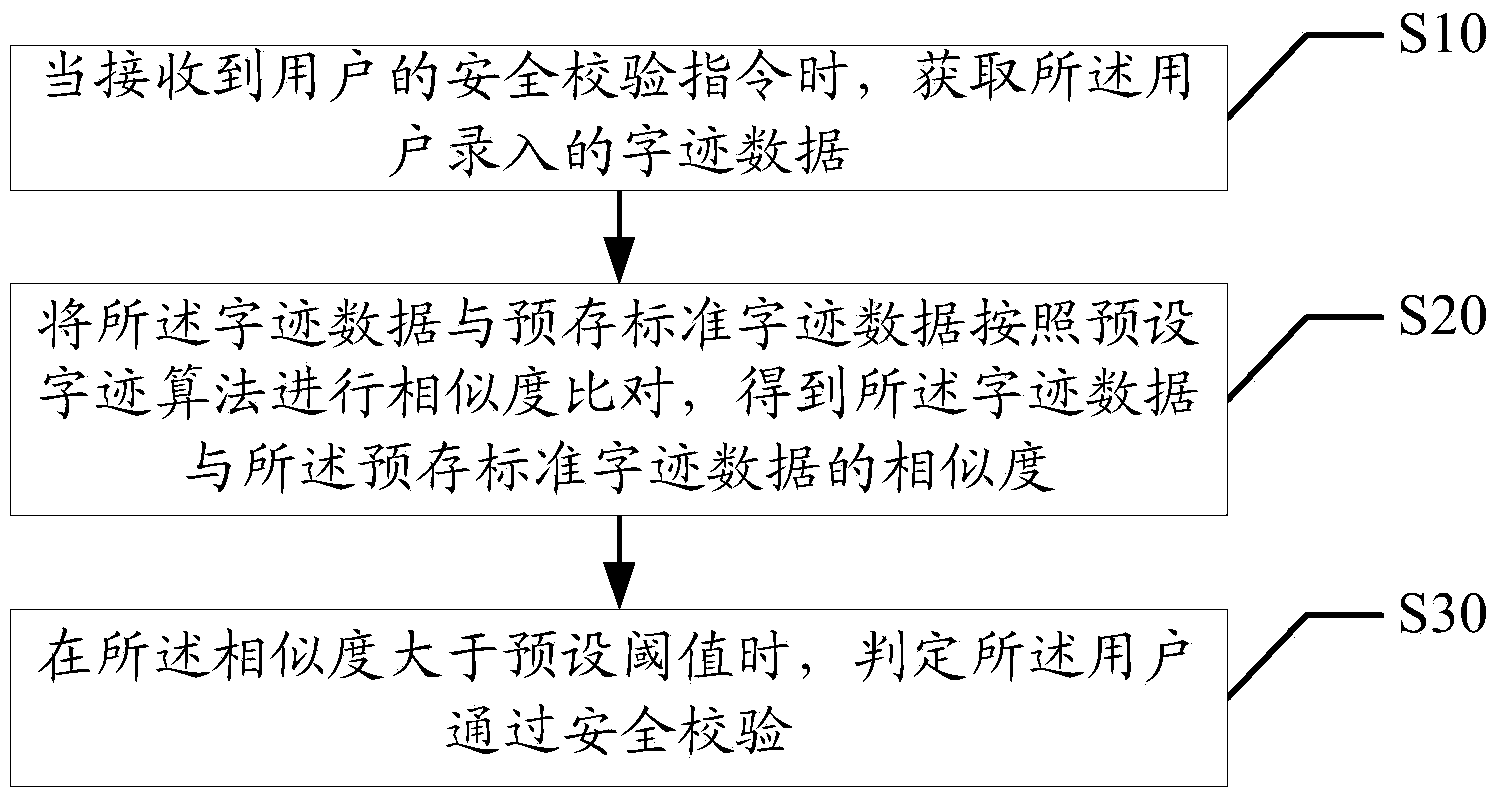
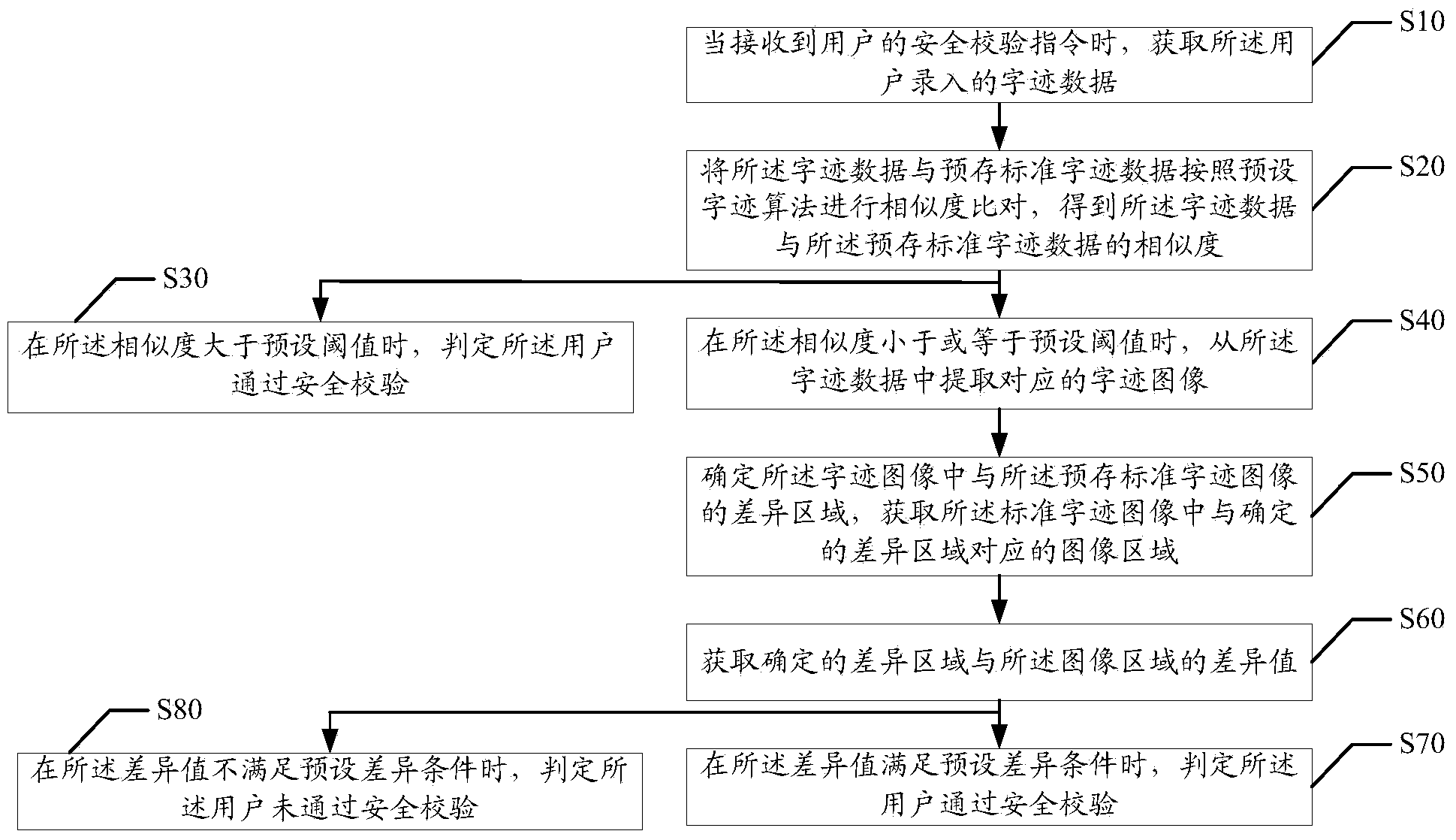
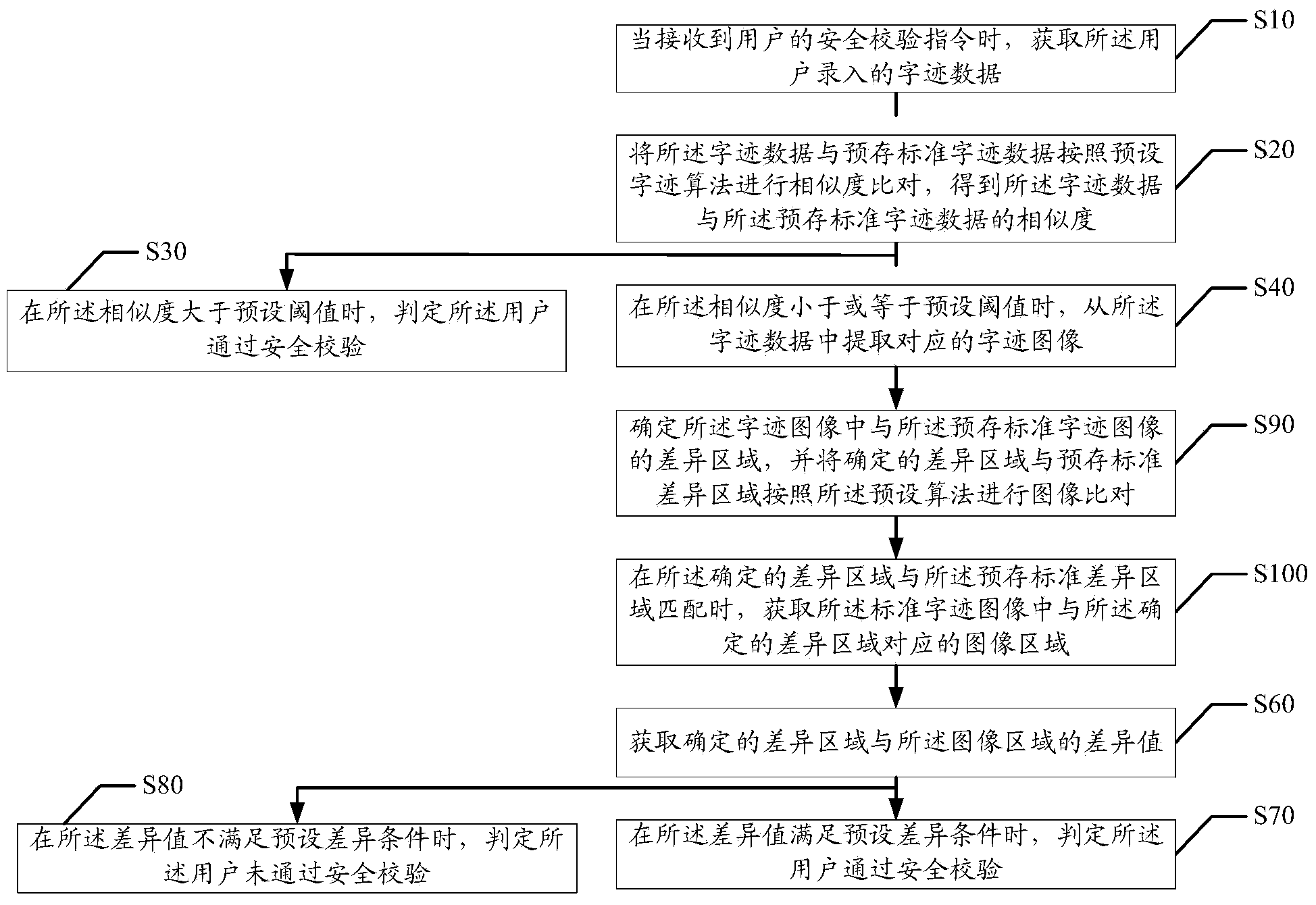
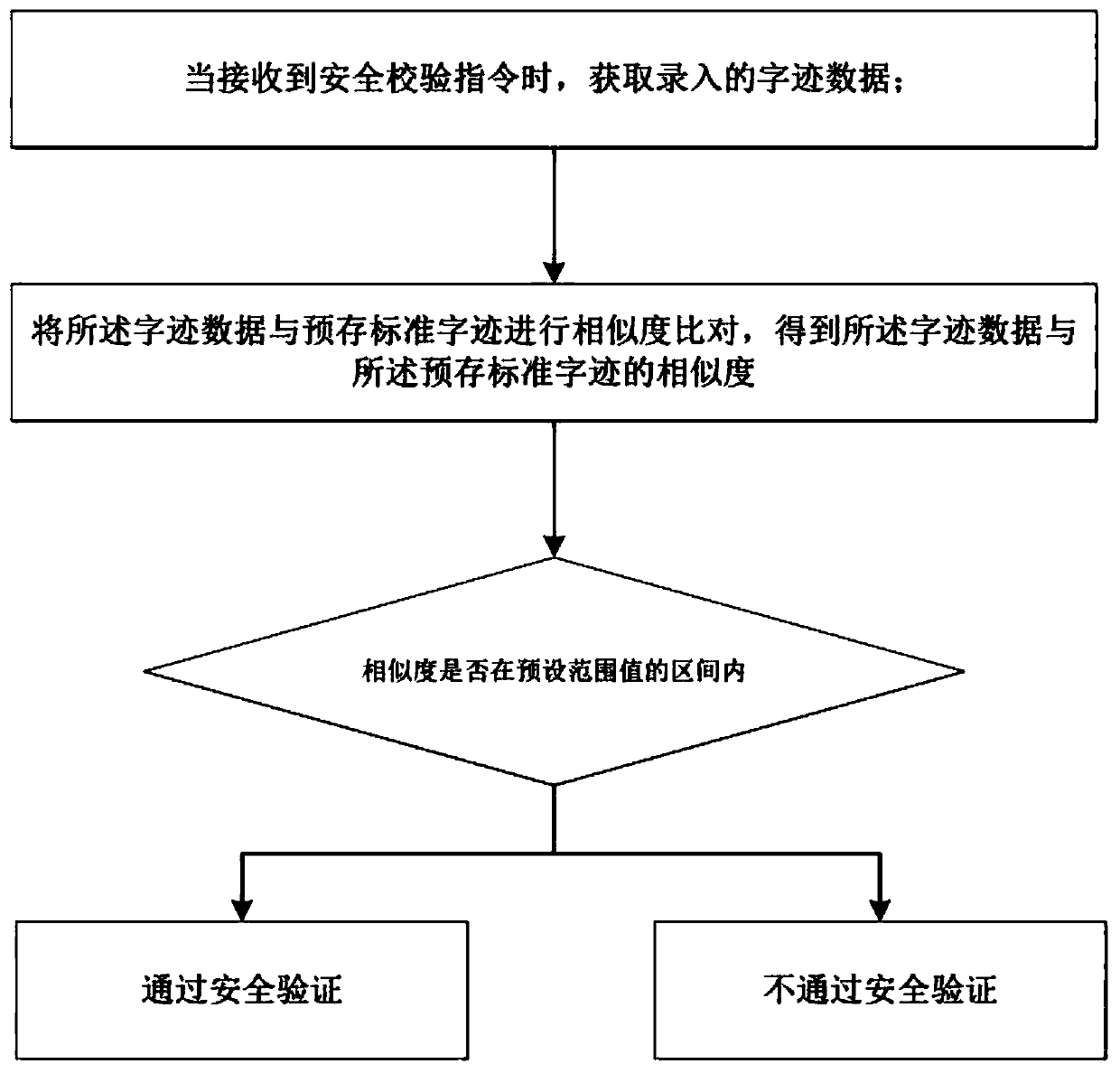
Safety verification method and device
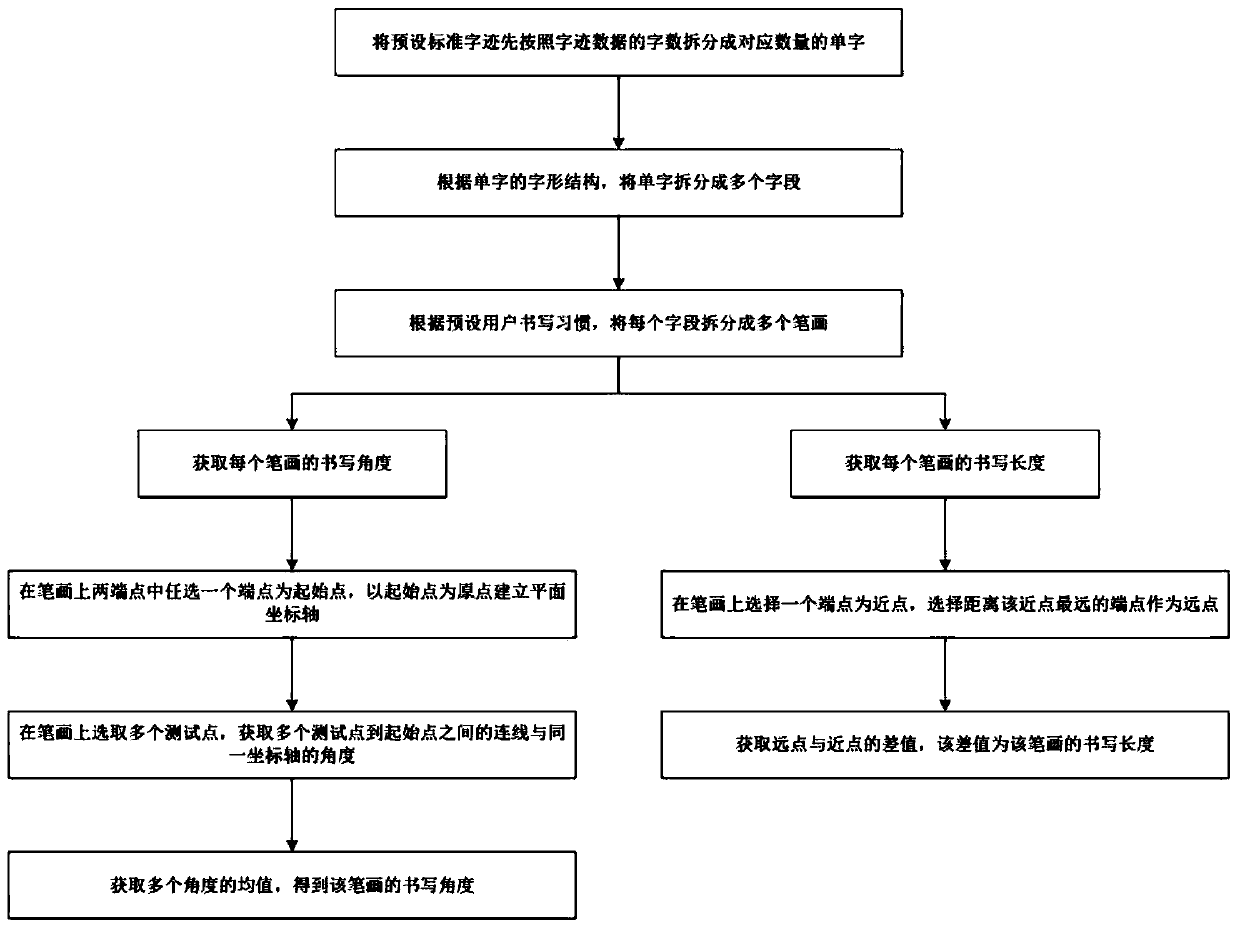
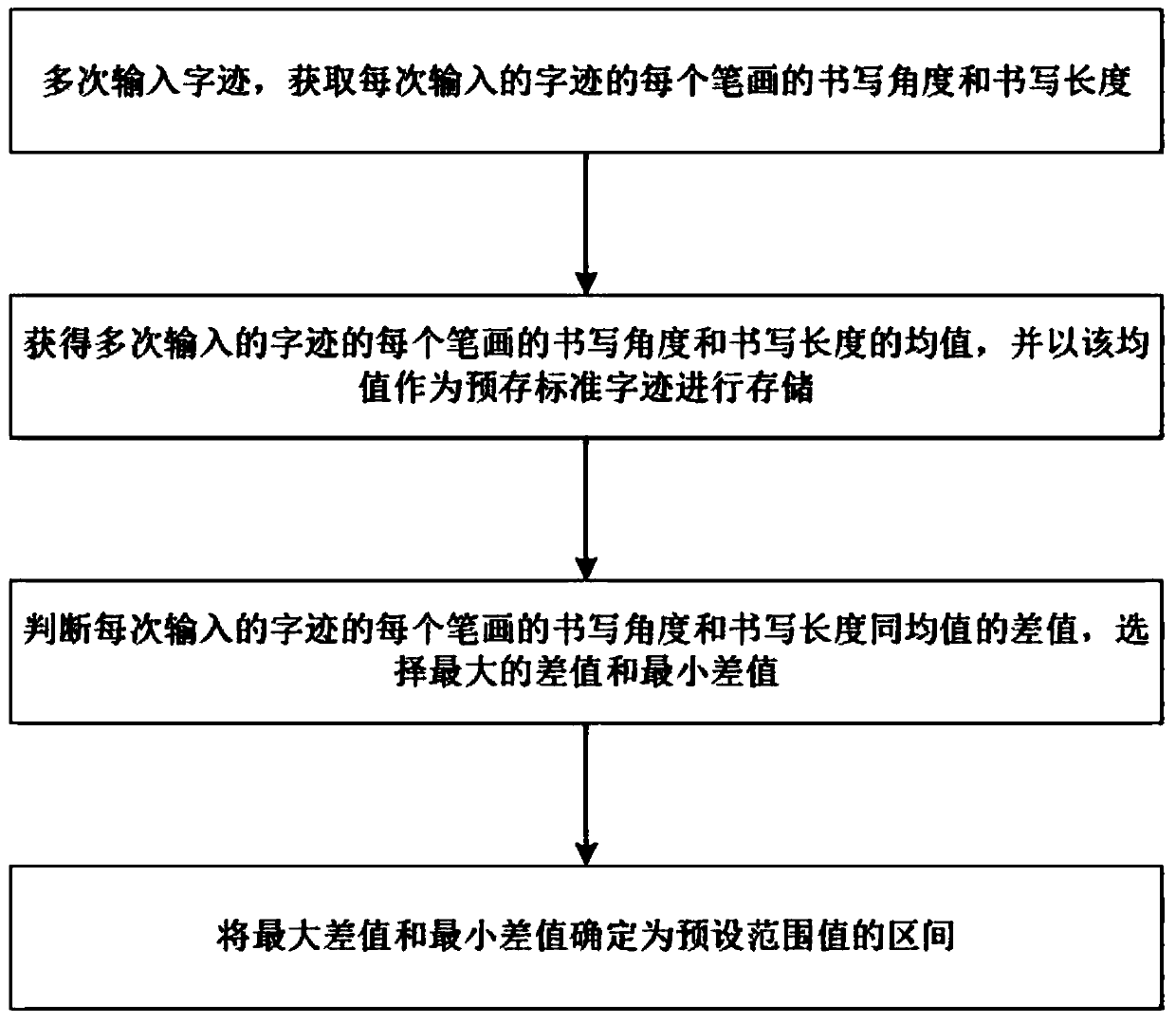
PendingCN111209549AGuarantee SimplicityReduce the probability of attackDigital data authenticationProgramming languageHandwriting
The invention discloses a safety verification method, which comprises the following specific steps of: A, when a safety verification instruction is received, obtaining input handwriting data; b, performing similarity comparison on the handwriting data and pre-stored standard handwriting to obtain the similarity between the handwriting data and the pre-stored standard handwriting; c, judging whether the similarity is within an interval of a preset range value or not, If so, judging that the user passes the safety check; If not, judging that the user does not pass the safety check. According tothe safety verification method and device provided by the invention, the probability of hacker attacks is effectively reduced while the simplicity of safety verification operation is ensured, and thesafety of information is improved.
Owner:FOSHAN HECAI TECH SERVICE
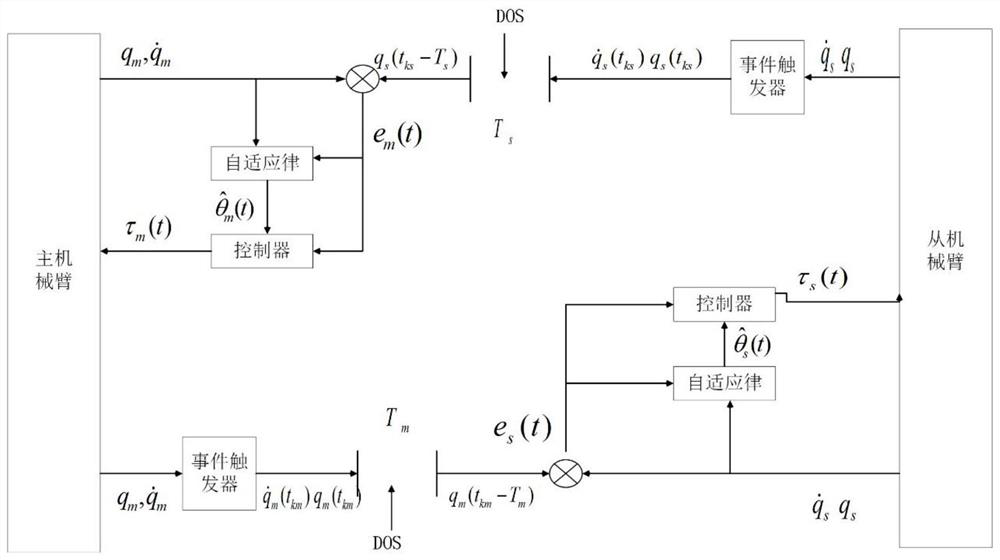
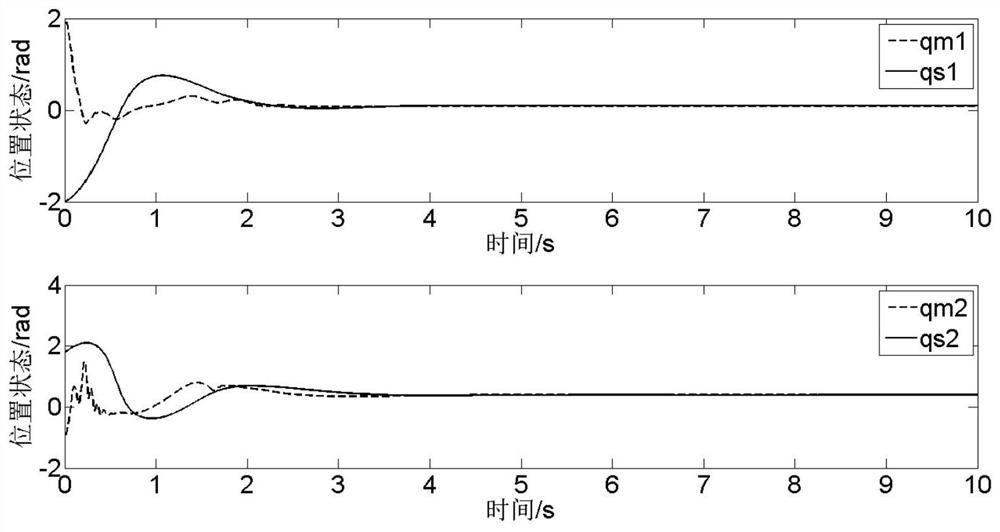
Control method for processing teleoperation system under DOS attack
ActiveCN113043280AMeet transient performance requirementsReduce the probability of attackProgramme-controlled manipulatorTotal factory controlInformation transmissionControl engineering
The invention provides a control method for processing a teleoperation system under a DOS attack. The control method comprises the following steps of: constructing a parameter identification rule on a master mechanical arm and a slave mechanical arm by utilizing respective measurement information and received position information of the master mechanical arm and the slave mechanical arm respectively; designing event triggers on the master mechanical arm and the slave mechanical arm respectively; and considering communication time-varying delay, and designing moments of the master mechanical arm and the slave mechanical arm based on an event trigger communication mechanism to realize bilateral control of the teleoperation system. According to the control method, the stable tracking problem of the bilateral teleoperation system with uncertain parameters and time-varying delay in information transmission under the DOS is researched, and the parameter identification rule is constructed, so that an ideal parameter estimation value can be obtained when an excitation signal does not meet a continuous excitation condition, and the requirement on the transient performance of the teleoperation system can be met; and furthermore, the elastic event trigger is designed, so that data is sent as required, and the probability that the data is attacked on a communication network is reduced.
Owner:NANJING UNIV OF POSTS & TELECOMM
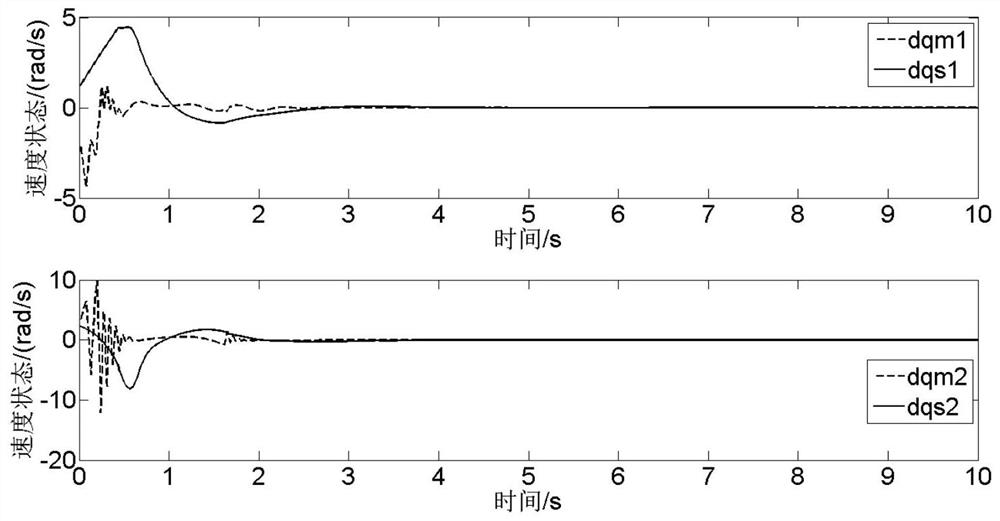
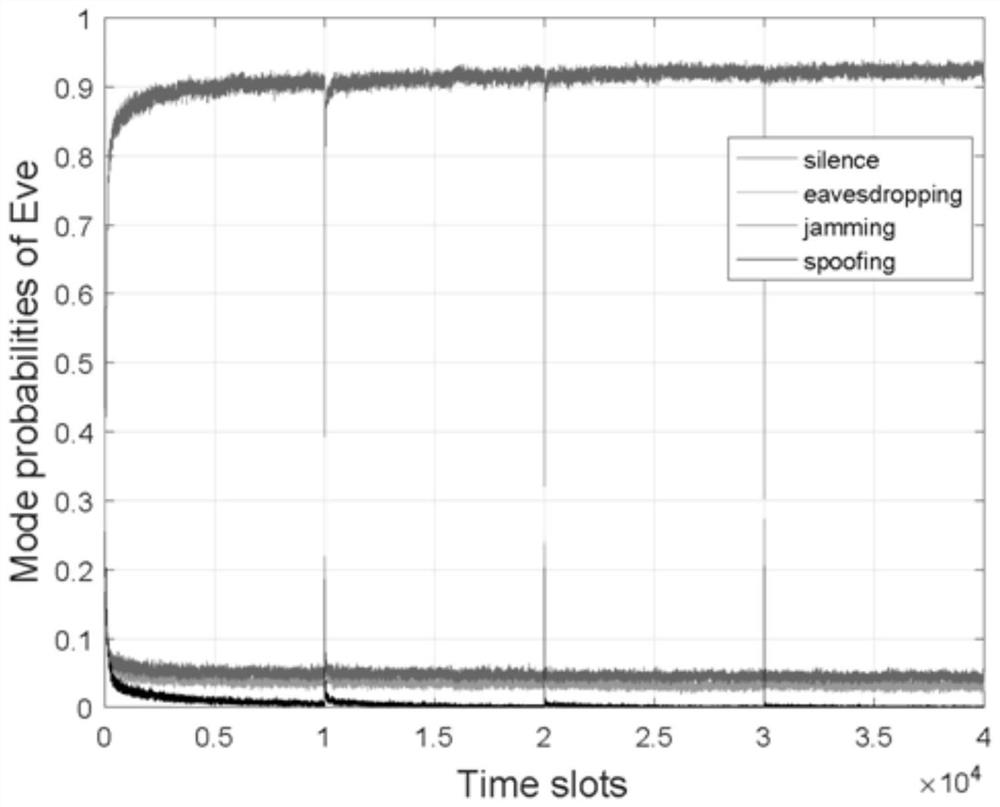
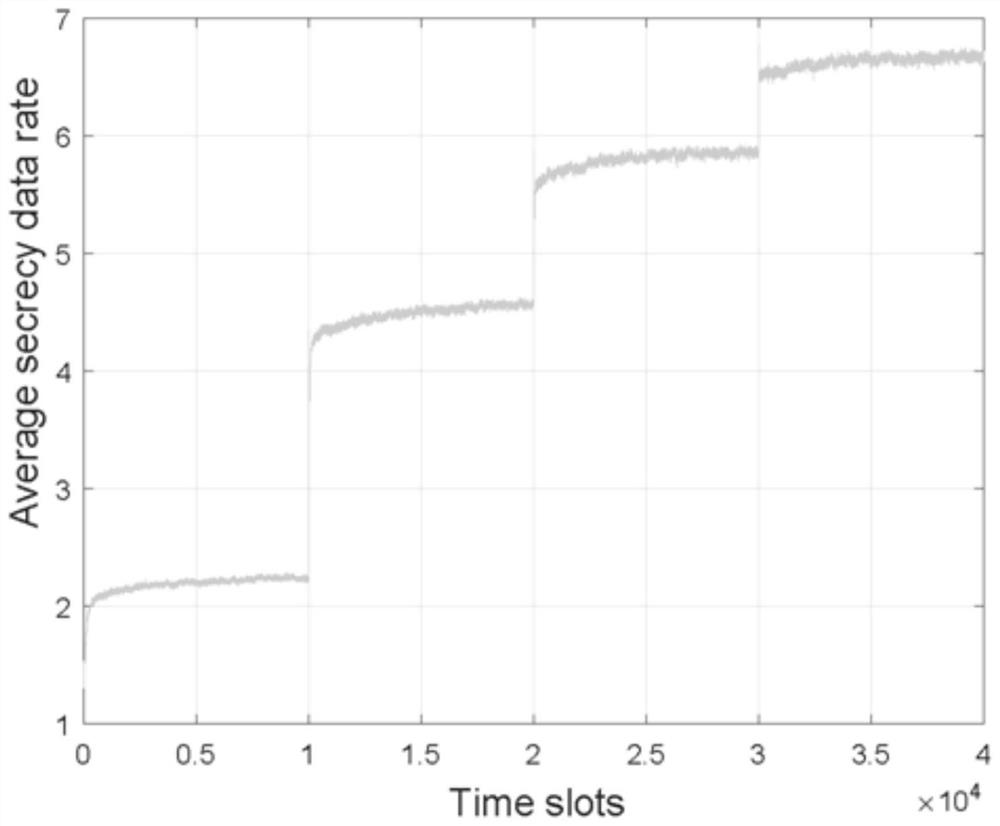
A secure transmission method against intelligent attacks based on reinforcement learning
ActiveCN110061982BImprove physical layer security performanceIncrease transfer ratePower managementTransmissionAlgorithmEngineering
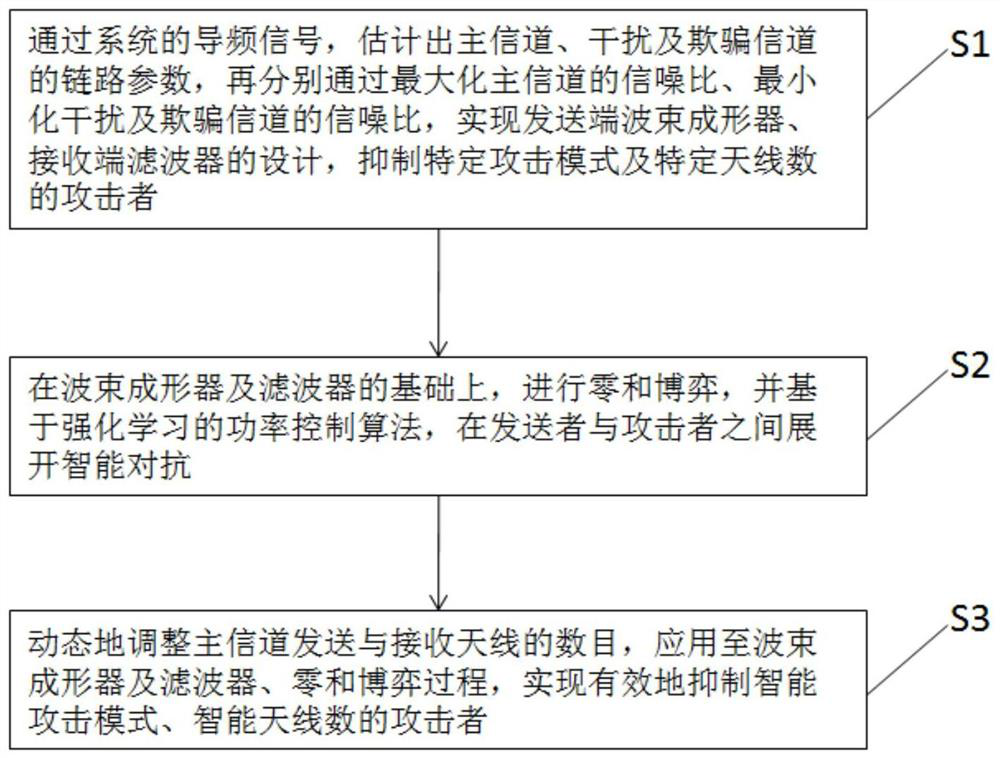
The invention discloses a security transmission method against intelligent attacks based on reinforcement learning, including: S1, through the channel parameter matrix signal of the system, estimate the link parameters of the main channel, interference and spoofing channels, and then respectively maximize the main channel Signal-to-noise ratio, minimize interference and spoof the signal-to-noise ratio of the channel, realize the design of the beamformer at the sending end and the filter at the receiving end, and suppress the attacker with a specific attack mode and a specific number of antennas; S2, in the beamformer and filter On the basis of S3, the zero-sum game is carried out, and based on the power control algorithm of reinforcement learning, intelligent confrontation is launched between the sender and the attacker; S3 dynamically adjusts the number of main channel sending and receiving antennas, and applies it to the beamformer And filter, zero-sum game process, effectively suppressing the attacker with smart attack mode and number of smart antennas; the invention can suppress the attack intention of the smart attacker, reduce the attack probability, and improve the system data transmission rate.
Owner:南方电网互联网服务有限公司
Anti-invasion detection method based on RFID bill
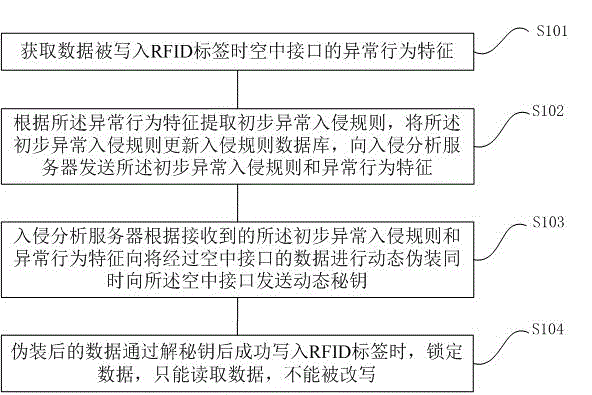
ActiveCN104537328AReduce the probability of attackProtection securitySensing record carriersTransmissionComputer hardwareAir interface
The invention discloses an anti-invasion detection method based on an RFID bill. The anti-invasion detection method comprises the following steps: obtaining the abnormal behavior characteristics of an air interface when data are written into an RFID tag; extracting a primary abnormal invasion rule according to the abnormal behavior characteristics, updating an invasion rule database by use of the primary abnormal invasion rule and sending the primary abnormal invasion rule and the abnormal behavior characteristics to an invasion analysis server; performing dynamic masquerading on data to be passed through the air interface by the invasion analysis server according to the received primary abnormal invasion rule and abnormal behavior characteristics, and meanwhile, sending a dynamic secret key to the air interface; when the masqueraded data are successfully written into the RFID tag by decrypting the private key, locking the data so that the data only can be read and cannot be rewritten. The anti-invasion detection method is capable of reducing the attack rate of the RFID data and protecting the security of a user.
Owner:BEIJING HONGMA MEDIA CULTURE DEV
Terminal virus detection method and device based on data packet, and storage equipment
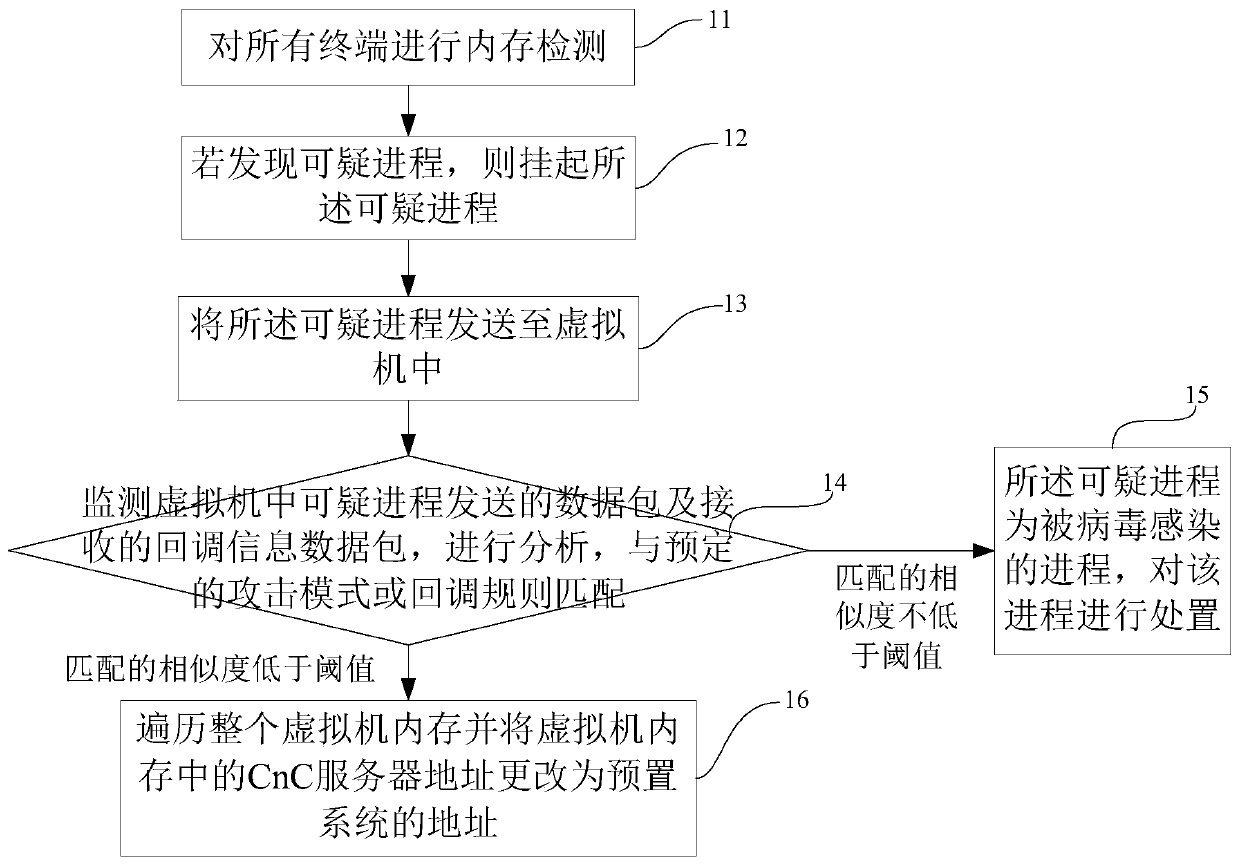
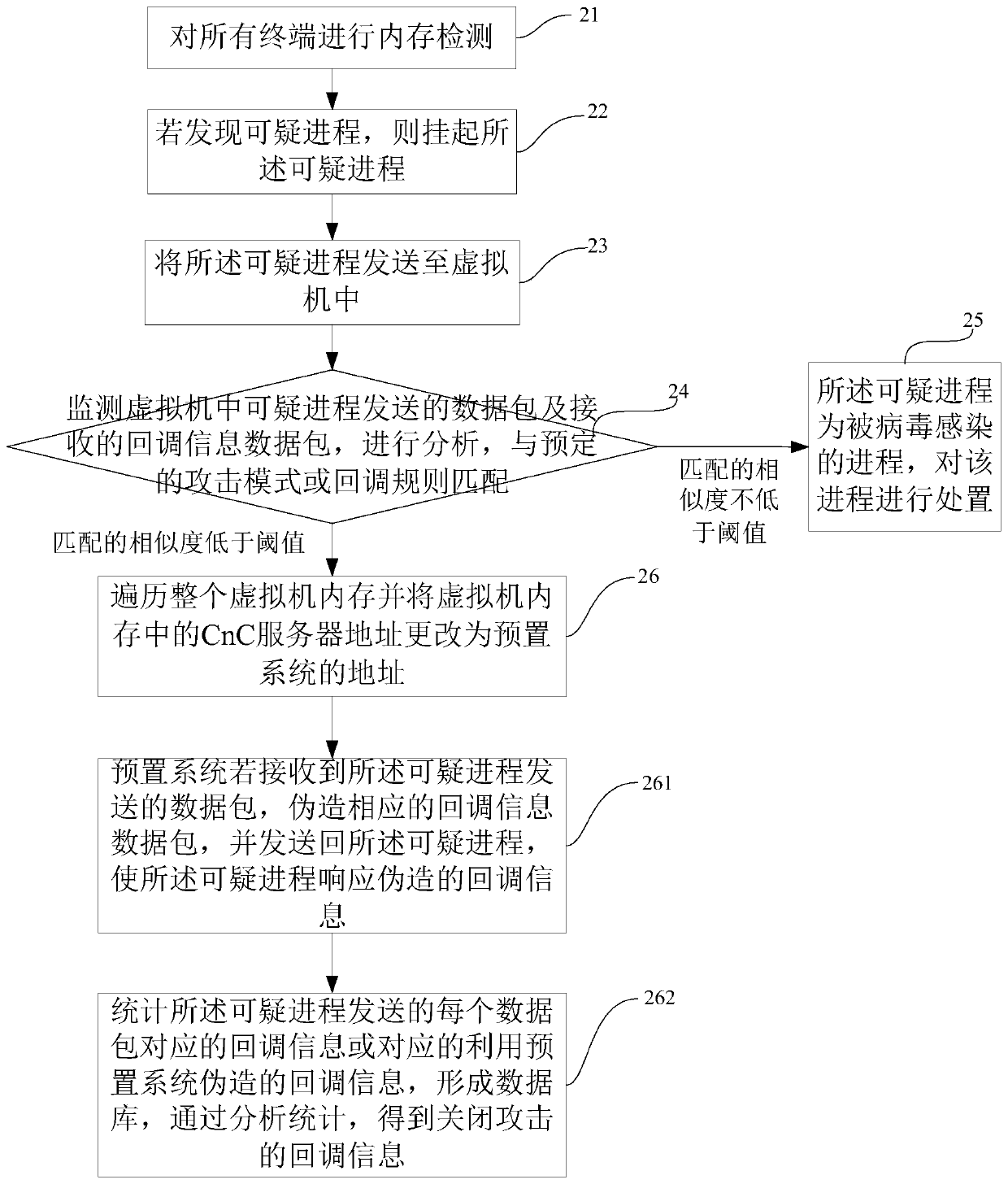
PendingCN111027061AReduce the probability of attackPlatform integrity maintainanceTransmissionEmbedded systemVirus detection
Embodiments of the invention disclose a terminal virus detection method and device based on a data packet, and a storage device, and aim to solve the problem that a virus-infected terminal attacks other terminals with more vulnerabilities in a local area network. The method comprises the following steps: performing memory detection on all terminals; if the suspicious process is found, suspending the suspicious process; sending the suspicious process to a virtual machine; monitoring a data packet sent by a suspicious process in the virtual machine and a received callback information data packet, analyzing the data packet, and performing matching with a predetermined attack mode or callback rule; if the matching similarity is not lower than a threshold value, determining that the suspiciousprocess is a process infected by viruses, and handling the process; and if the matching similarity is lower than the threshold value, traversing the whole virtual machine memory and changing the CnC server address in the virtual machine memory into the address of the preset system.
Owner:BEIJING ANTIY NETWORK SAFETY TECH CO LTD
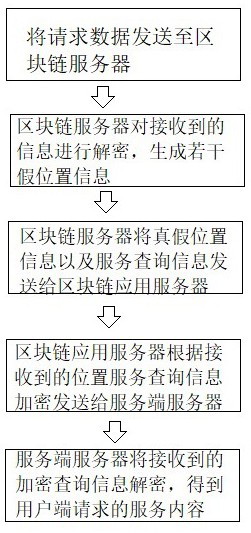
Communication method based on block chain technology
PendingCN113259336AEfficient storageReduce the probability of attackDatabase distribution/replicationTransmissionCommunications securityApplication server
The invention relates to a communication method based on a block chain technology. The method comprises the following steps that when a terminal user sends request data to a server, firstly the request data is sent to a block chain server; the block chain server decrypts the received information and generates a plurality of pieces of false position information according to the real position information and privacy protection parameters; the block chain server packages the true and false position information and the service query information together and sends the packaged information to a block chain application server; the block chain application server generates a fuzzy result query data set according to the received location service query information; the block chain server performs refinement processing on the fuzzy result query data set according to the real position information of the user, encrypts refinement result query information and sends the refinement result query information to a service-side server; and the service-side server decrypts the received result query information so as to obtain the final result information of the service query. According to the invention, the communication security can be effectively improved.
Owner:STATE GRID FUJIAN ELECTRIC POWER CO LTD
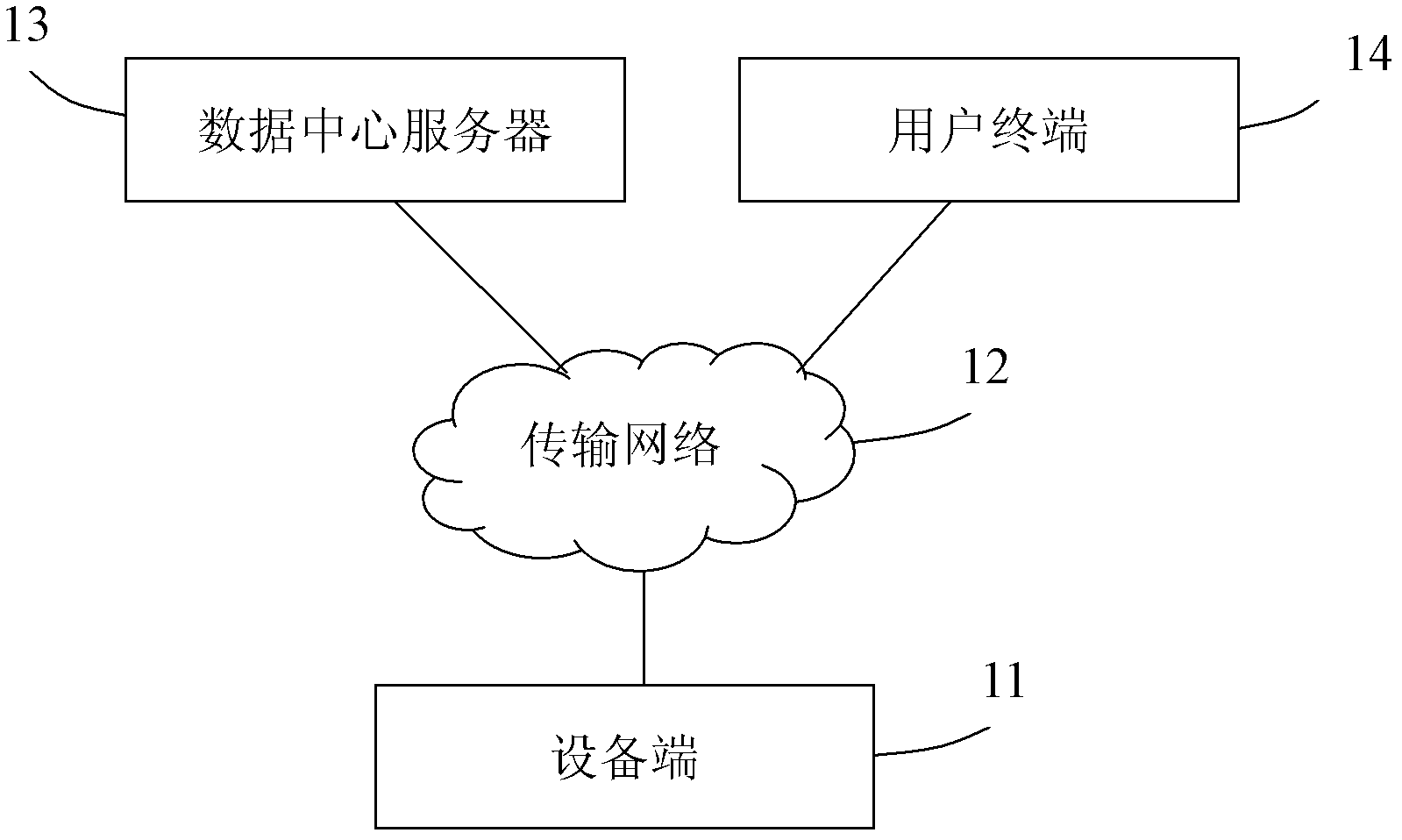
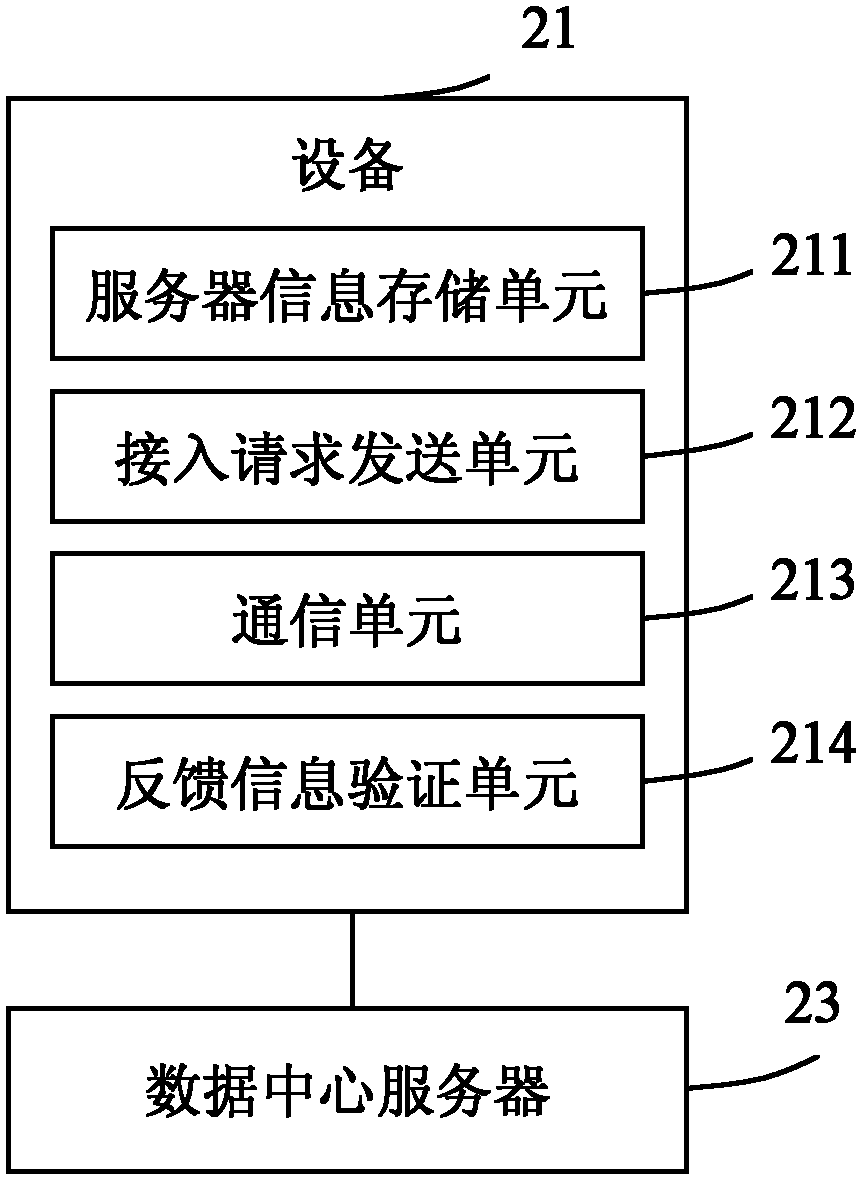
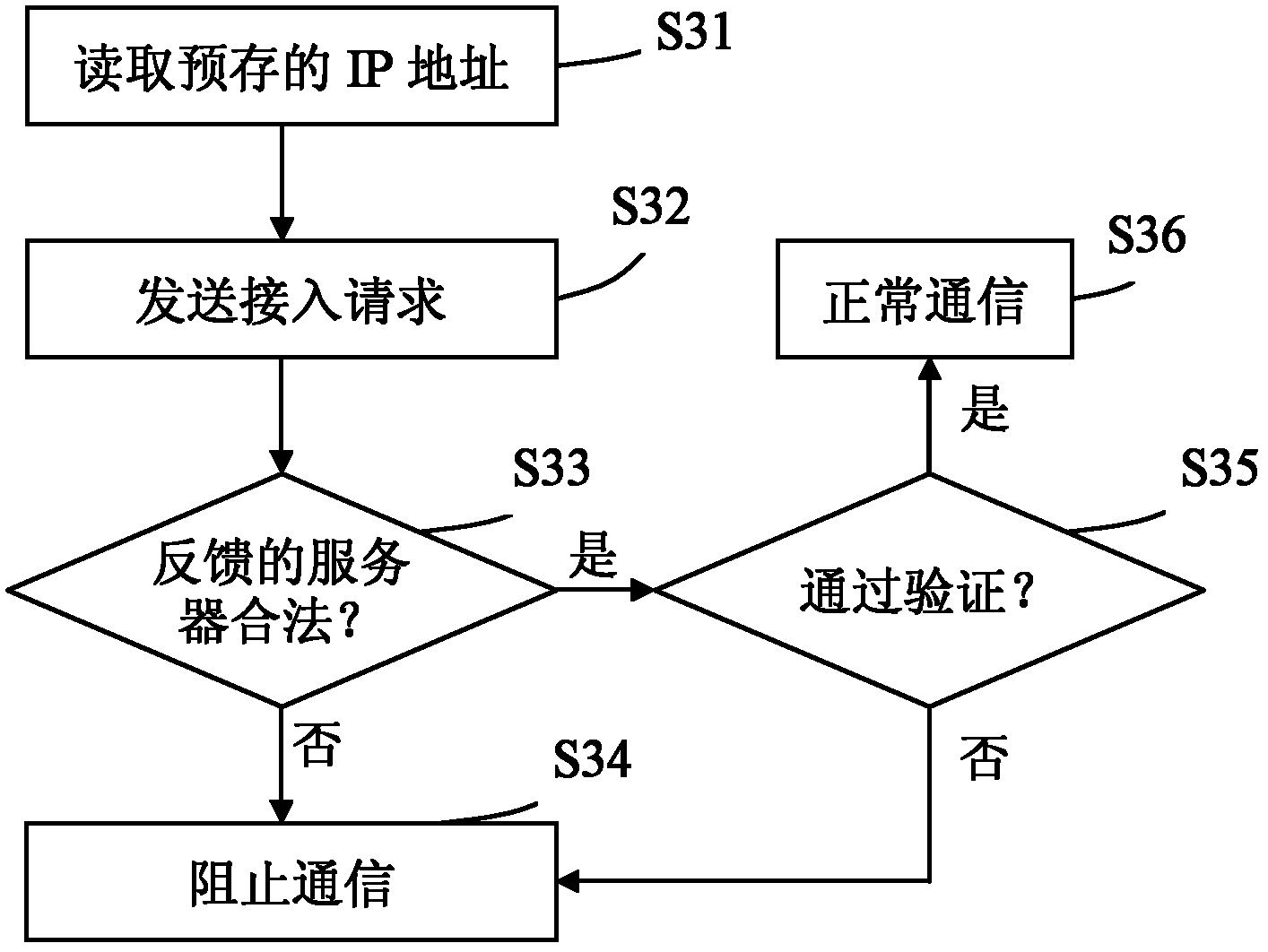
Method and system for server to safely access Internet of things
InactiveCN102882836AImprove securityReduce the probability of attackTransmissionInternet of ThingsThe Internet
The invention relates to a method for a server to safely access Internet of things. The method comprises the following steps that: (a) equipment reads prestored server information and sends access request data to a data center server according to the server information; (b) the equipment judges whether the data center server which sends feedback information is legal or not according to the server information prestored in the equipment when receiving the feedback information from the data center server, and a step (c) is performed if the data center server is legal; and (c) the equipment communicates with the data center server when the feedback information is request passing information. The invention also provides a system for the server to safely access the Internet of things. Through directional sending and server verification modes, the probability that an Internet of things system is attacked by the disguised data center server is reduced to ten thousandth, and the safety of the Internet of things is greatly improved.
Owner:SHENZHEN HUICHUAN CONTROL TECH +1
Ceramic coating comprising yttrium which is resistant to a reducing plasma
ActiveCN102084020BReduce formationReduce the probability of attackMolten spray coatingThin material handlingPorosityCeramic coating
Particulate generation is often a problem with semiconductor component processing in a highly corrosive plasma environment. This problem is more serious when the above-mentioned plasma is reducing plasma. Experimental data shows that when forming a plasma-sprayed yttrium-containing ceramic (such as yttrium oxide, Y2O3-ZrO2 solid solution, YAG and YF3), when the average effective particle size range of the powder feed for spraying ceramics is between about 22 μm to about 0.1 μm provides a low porosity coating with a smooth and compact surface. These sprayed materials reduce particle generation in corrosive reducing plasma environments.
Owner:APPLIED MATERIALS INC
Method for enhancing wireless communication system security and wireless network equipment
InactiveCN101252772AImprove securityIncrease the difficulty of guessingRadio/inductive link selection arrangementsSecuring communicationAir interfaceWireless network
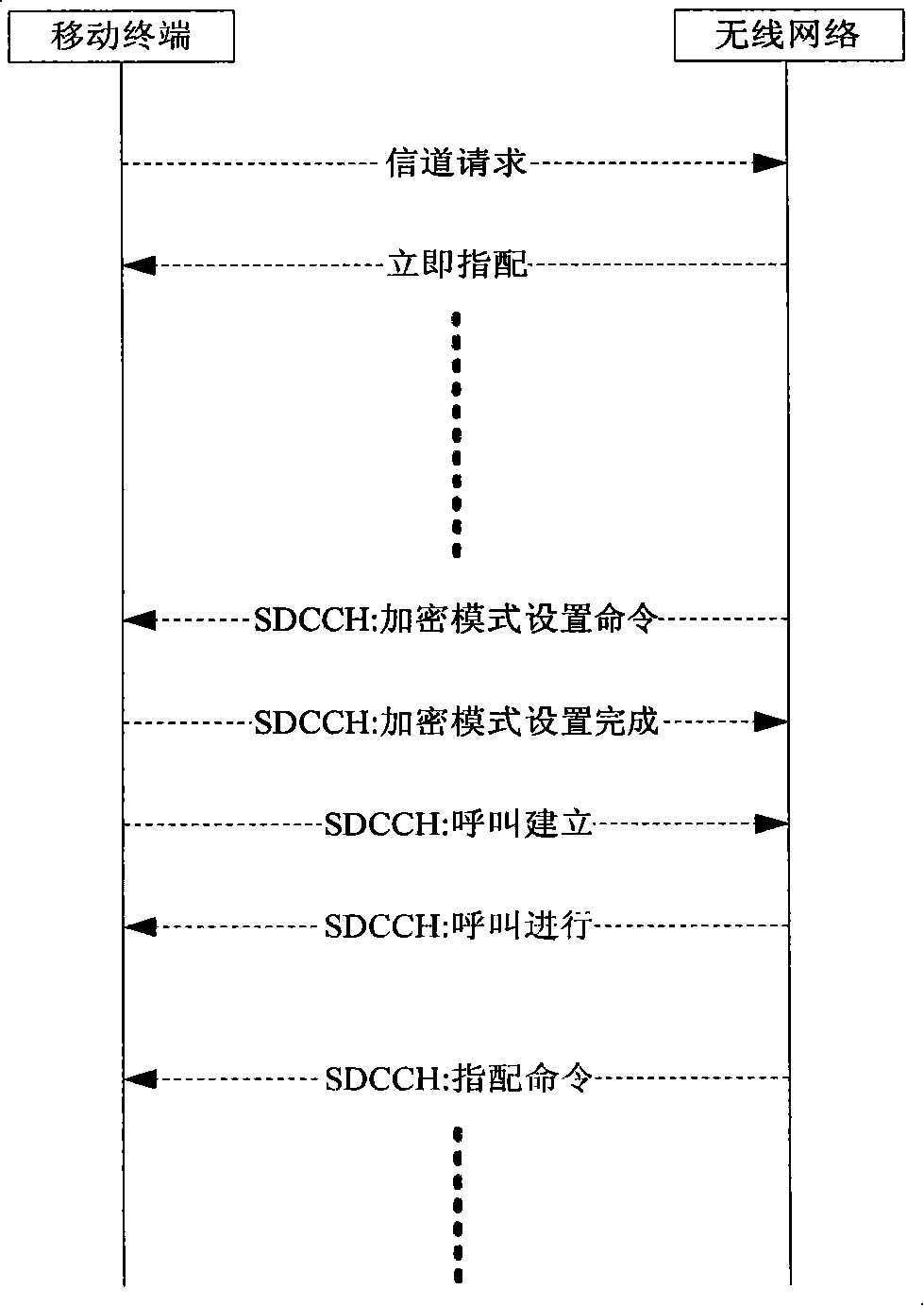
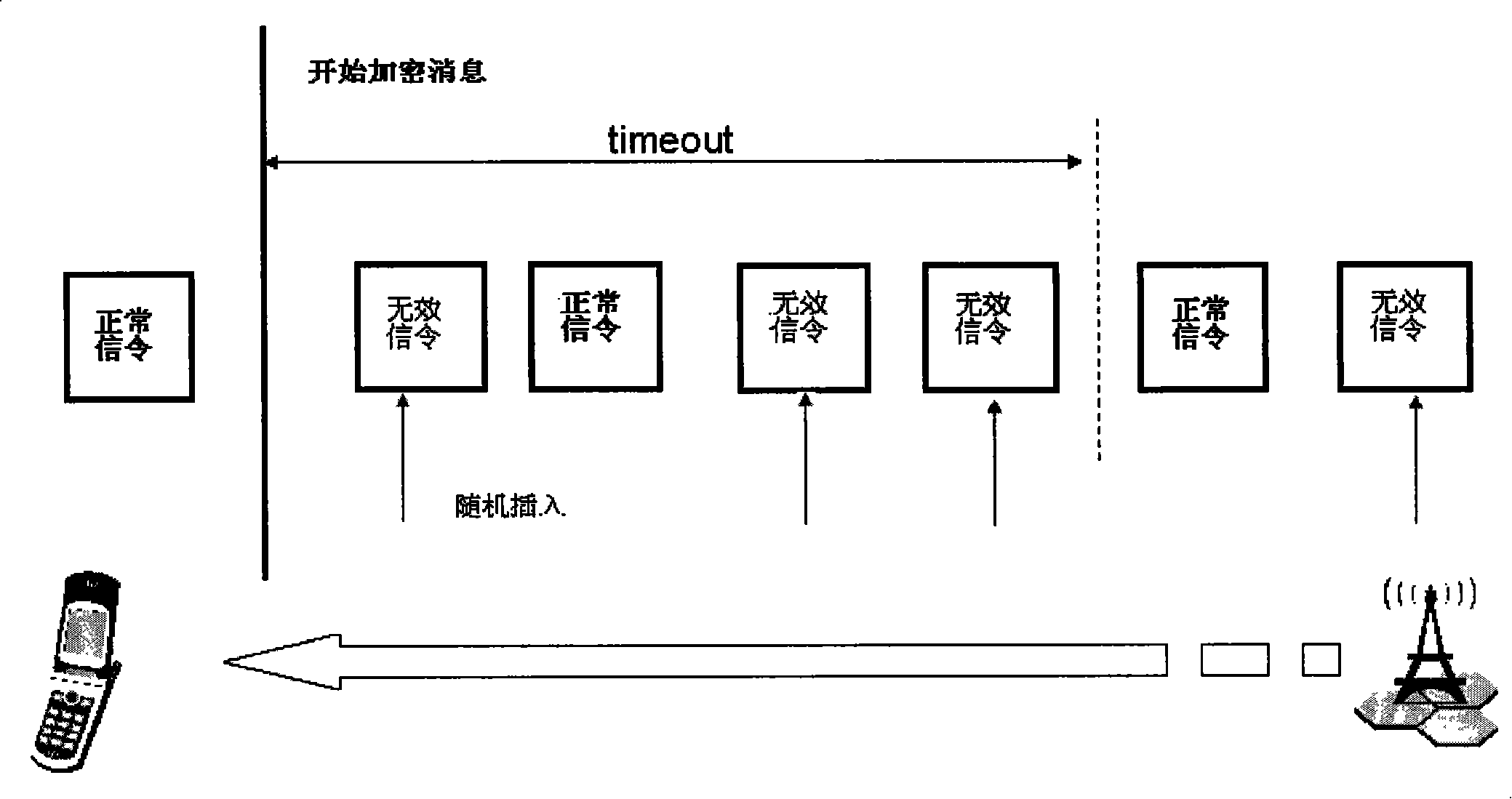
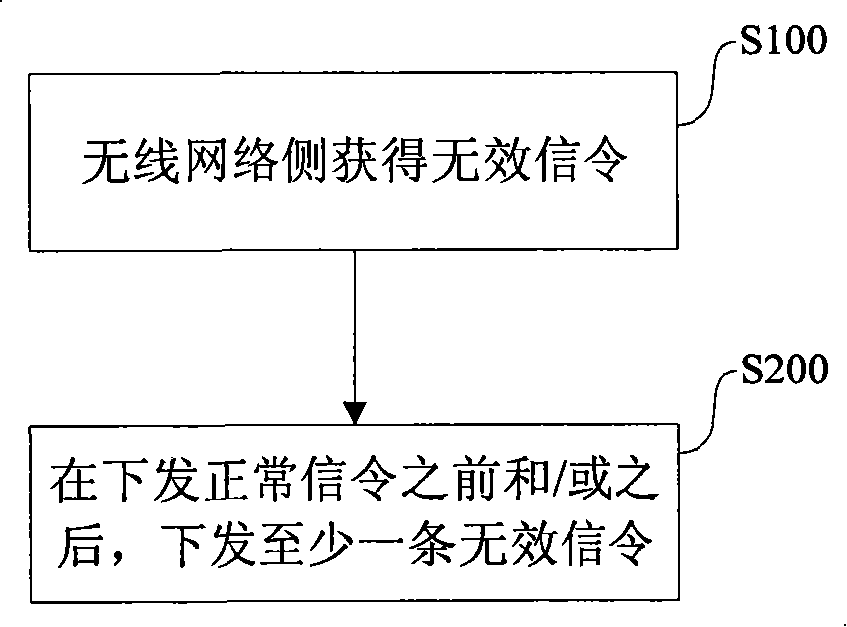
The invention discloses a method for improving the security of a wireless communication system and the wireless network equipment thereof, wherein the method comprises the following steps: a wireless network side acquires invalid signaling which can not be substantially processed by the terminal; before and / or after normal signaling is distributed, the wireless network side distributes at least one piece of invalid signaling. Correspondingly, the invention also discloses wireless network equipment. Through implementing the method and the wireless network equipment of the invention, the guess difficulty for a hacker is increased, the air interface security of the wireless communication system is enhanced, and the privacy of the communication system is guaranteed.
Owner:HUAWEI TECH CO LTD
Cloud-computing network real-time monitoring method
InactiveCN106385337AAvoid attackReduce the probability of attackData switching networksPush technologySecure state
The present invention relates to a cloud-computing network real-time monitoring method. According to the monitoring method, based on the cloud computing technology, a server and resources are effectively integrated, and a CPU, a memory and a magnetic disk are virtualized; based the cloud computing, load is shared equally, and pressure is dispersed; and the PUSH technology of the NetworkBOX is adopted, so that network real-time monitoring can be achieved effectively, and the virus feature codes and patches of a client can be updated in real time within 45 seconds. The method of the invention is simple in structure, can prevent network attacks, improve a safety protection coefficient, perform automatic updating, reduce operating cost, reduce the probability of being attacked of a user in an empty stomach period, and cover various kinds of security protection applications on the Internet at present. With the method adopted, it can be ensured the user is in a safest state, and the user will not increase cost for function upgrade in a future use process.
Owner:汉兴德创(武汉)科技有限公司
Network access method, system and authentication server
ActiveCN102264050BReduce the probability of attackImprove securityMessaging/mailboxes/announcementsSecurity arrangementAccess methodInternet privacy
The invention provides a network access method, system and authentication server. The method includes: when it is determined that the identity authentication of the access user passes, the authentication server sends a short message requesting instructions to confirm whether to open the Internet access channel through the short message conversion device to the communication terminal of the access user; When the confirmation information is returned, the instruction information of opening the Internet access channel is sent to the access device, so that the access user can access the network. The technical scheme of the invention solves the problem that illegal users use stolen user names and passwords for identity authentication, reduces the probability of illegal users attacking the network, and improves the security of the network. In addition, compared with the prior art, the technical solution of the present invention has the advantages of simple access process and low access cost.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
System and method for accessing client end to next network
InactiveCN101227361BReduce the probability of attackReduce complexityError preventionData switching by path configurationExchange networkEngineering
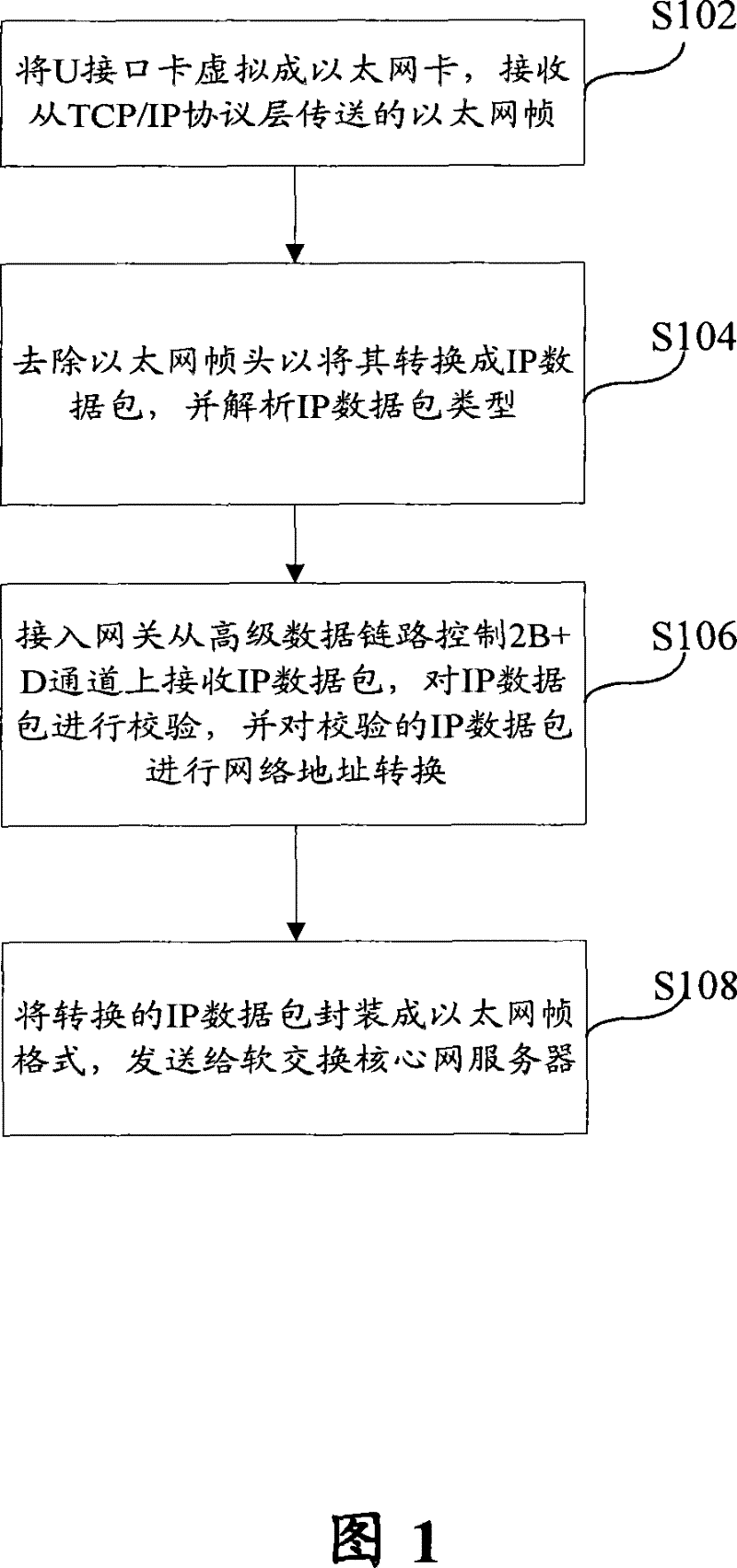
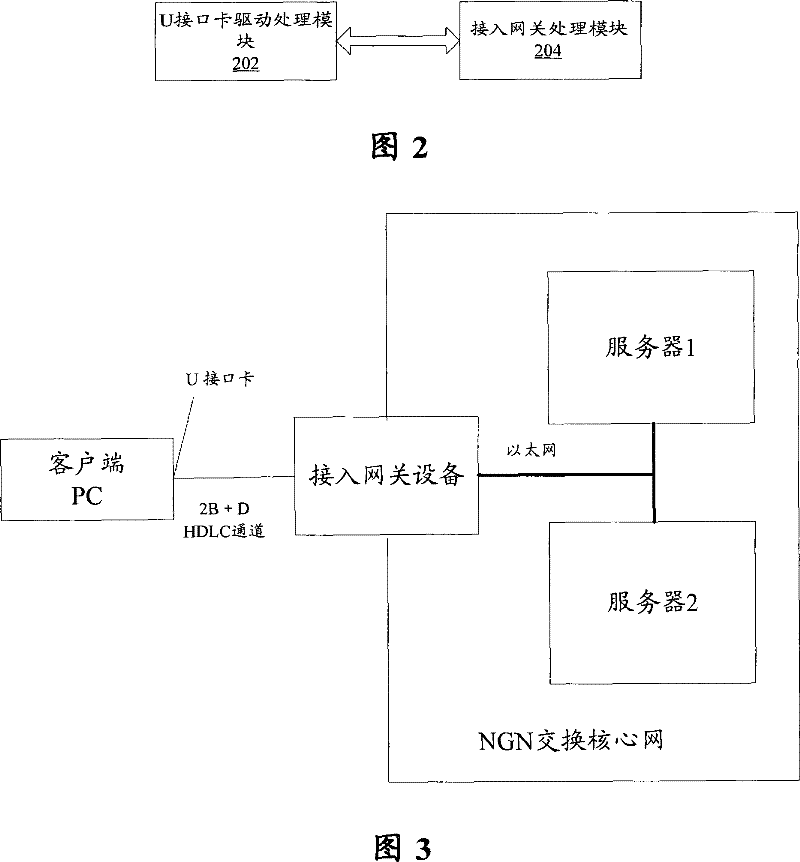
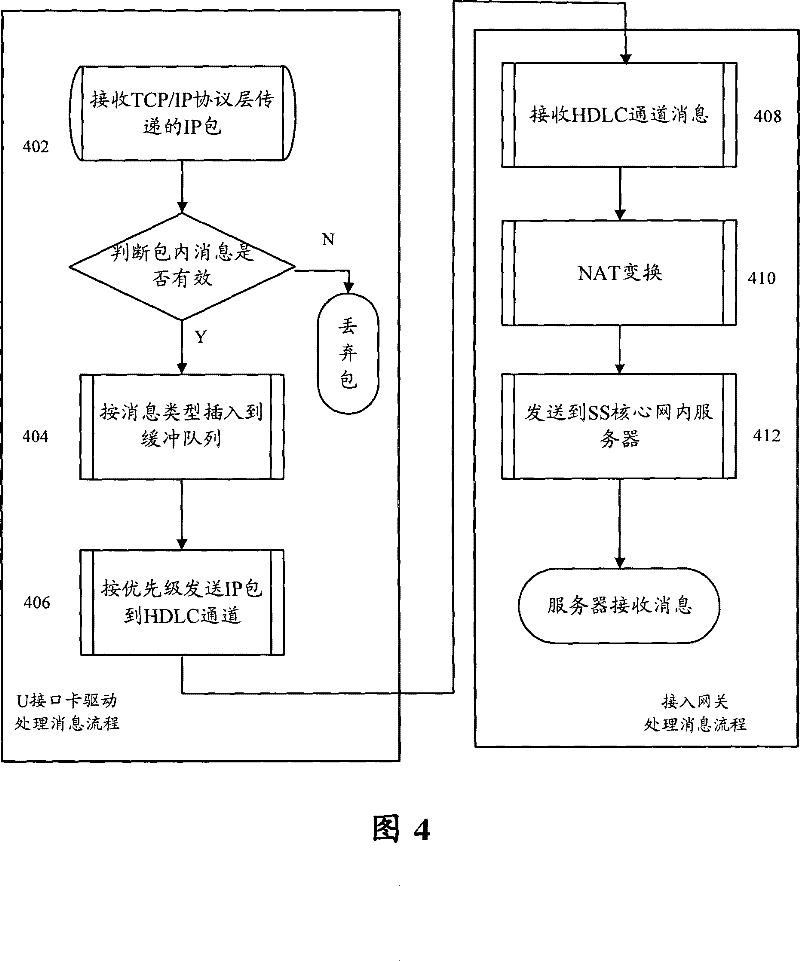
The invention discloses a method for accessing a user end to next generation network, the method comprises the following steps: hypothesizing a U interface card into an Ethernet network card, receiving Ethernet frame which is transferred from a TCP / IP protocol layer, step S104, removing Ethernet frame head and exchanging the Ethernet frame head into an IP data packet, and analyzing IP data packettypes, step S106, accessing getaway and receiving data packet from high-grade data link control 2B+D channel, checking the IP data packet, exchanging network address for the IP data packet which is checked, and step S 108, packing the exchanged IP data packet into an Ethernet frame format and sending to soft exchanging core network server. The invention also discloses a system which accesses a user side to a next generation network. The invention achieves the safe and stable transmission of information in different networks under the circumstance without needing to modify any user end application program which is based on TCP / IP communication, which reduces the probability of core switching network service period which is attacked, and lowers complexity of important customer system network building.
Owner:ZTE CORP
Universal safety grade consulting method
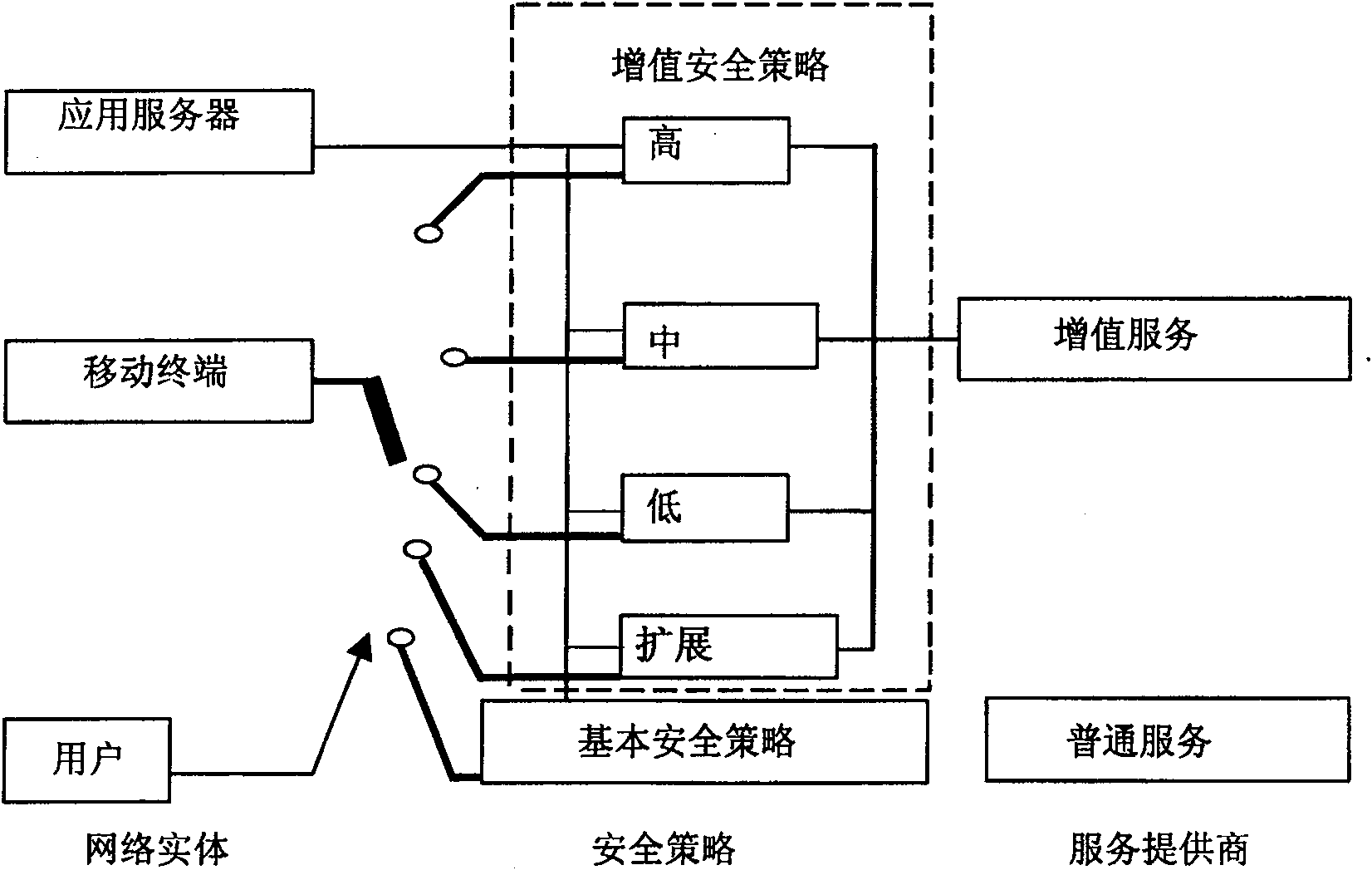
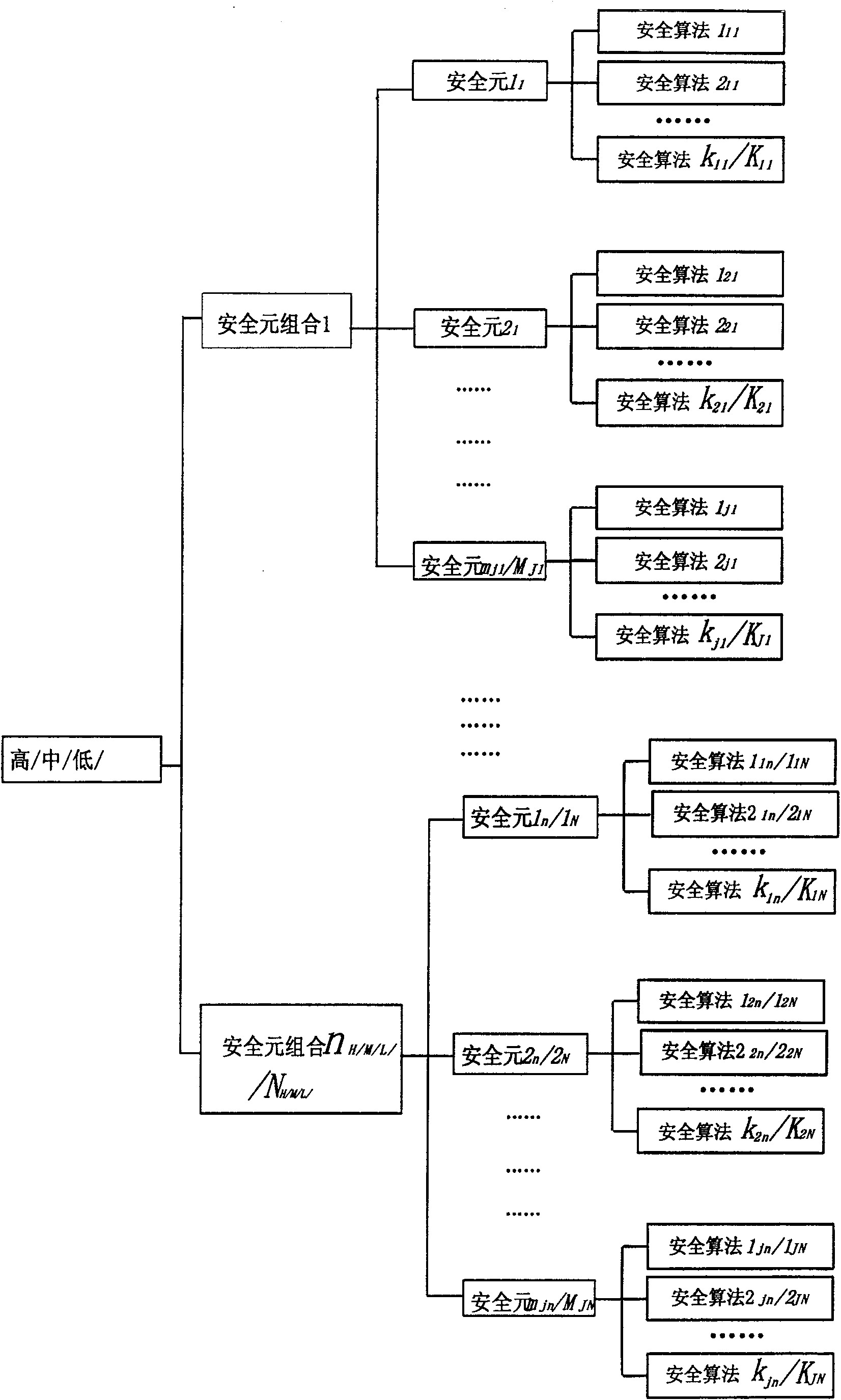
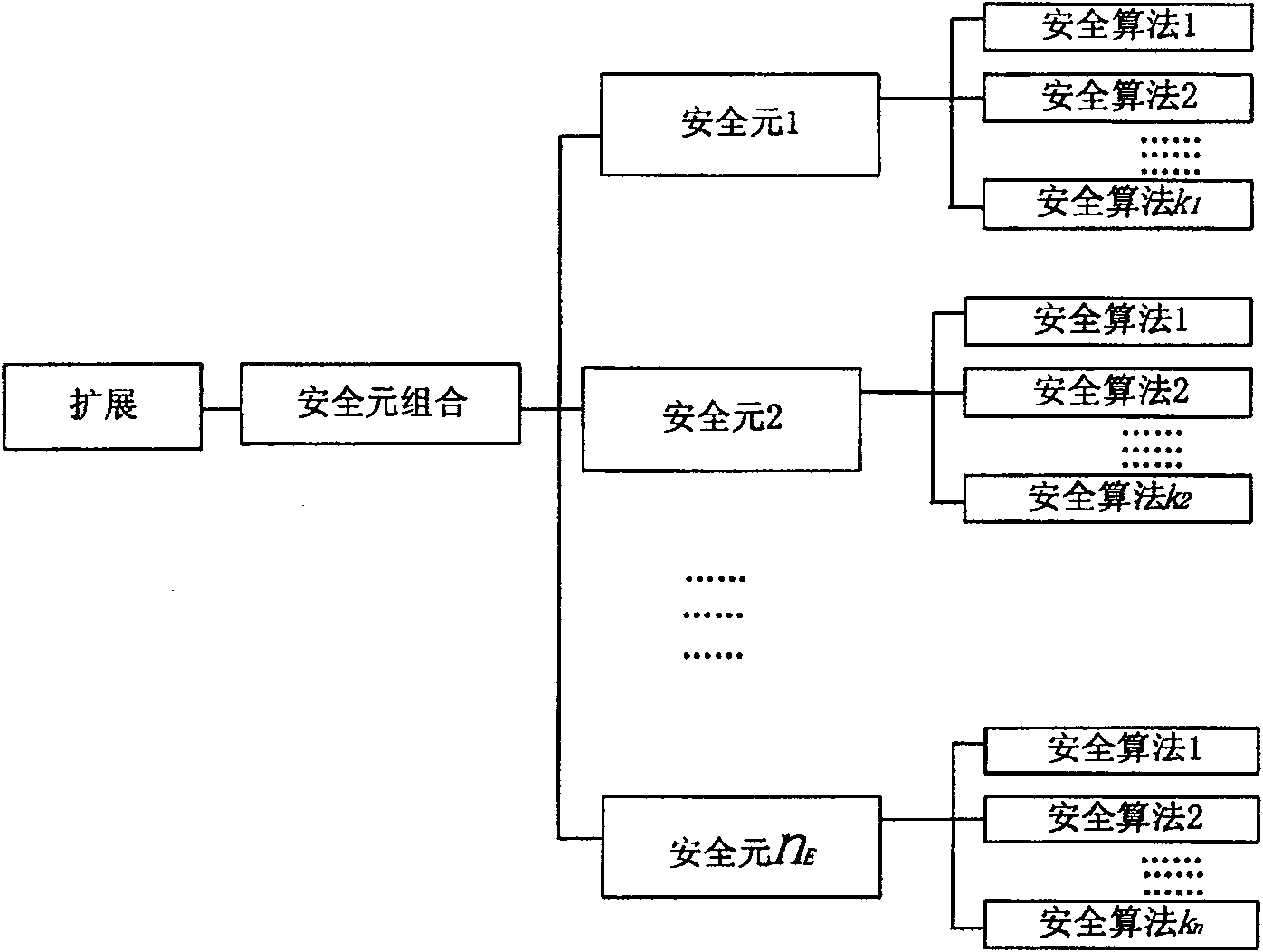
ActiveCN100571130CReduce the probability of attackFewer negotiation stepsSynchronising transmission/receiving encryption devicesUser identity/authority verificationSecure communicationConsultation process
The invention discloses a general security level negotiation method, which includes the following steps: first, the initiator sends the security level selected by the called party to the called party; A security algorithm with the best performance; in the third step, the two parties establish a secure communication channel by executing the negotiated security algorithm. The invention can reduce the probability of being attacked during the negotiation process, can also improve the negotiation efficiency and narrow the search range.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com