Anti-invasion detection method based on RFID bill
A detection method and RFID tag technology, applied in the field of RFID bills, can solve problems such as hindering market development and hidden dangers of RFID storage security, and achieve the effect of protecting security and reducing attack rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
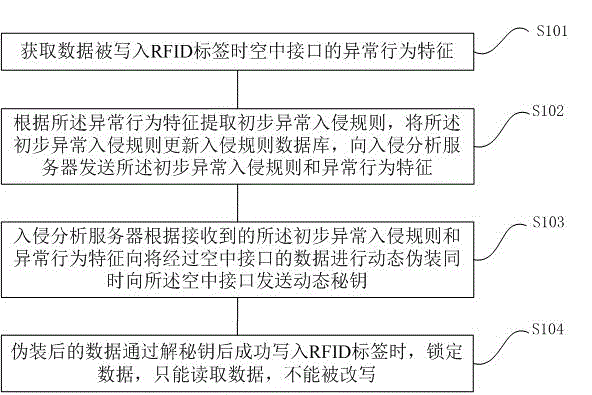
[0031] Such as figure 1 As shown, the embodiment of the present invention provides a technical solution of an RFID ticket-based anti-intrusion detection method as follows:
[0032] S101: Obtain abnormal behavior characteristics of the air interface when data is written into the RFID tag;
[0033] S102: Extracting preliminary abnormal intrusion rules according to the abnormal behavior characteristics, updating the preliminary abnormal intrusion rules to an intrusion rule database, and sending the preliminary abnormal intrusion rules and abnormal behavior characteristics to an intrusion analysis server;
[0034] S103: The intrusion analysis server dynamically camouflages the data passing through the air interface according to the received preliminary abnormal intrusion rules and abnormal behavior characteristics, and at the same time sends a dynamic key to the air interface;
[0035] S104: When the disguised data is successfully written into the RFID tag after passing the decry...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com