Universal safety grade consulting method
A technology of security level and security algorithm, applied in the field of mobile communication and information security, can solve problems such as increasing negotiation steps, and achieve the effect of narrowing the search range, reducing negotiation steps, and improving negotiation efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] According to the content of the invention, we introduce the specific implementation of the invention.
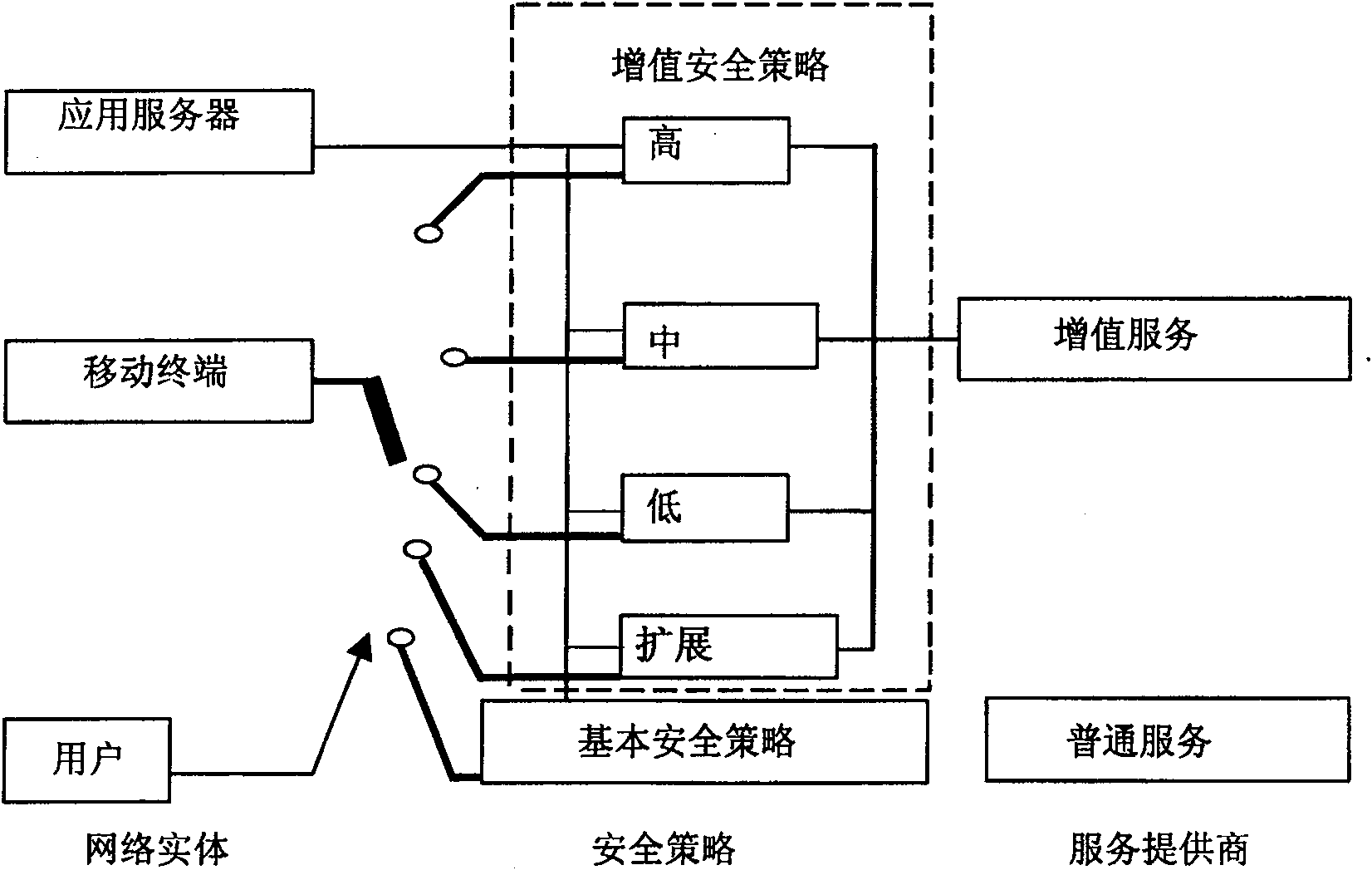
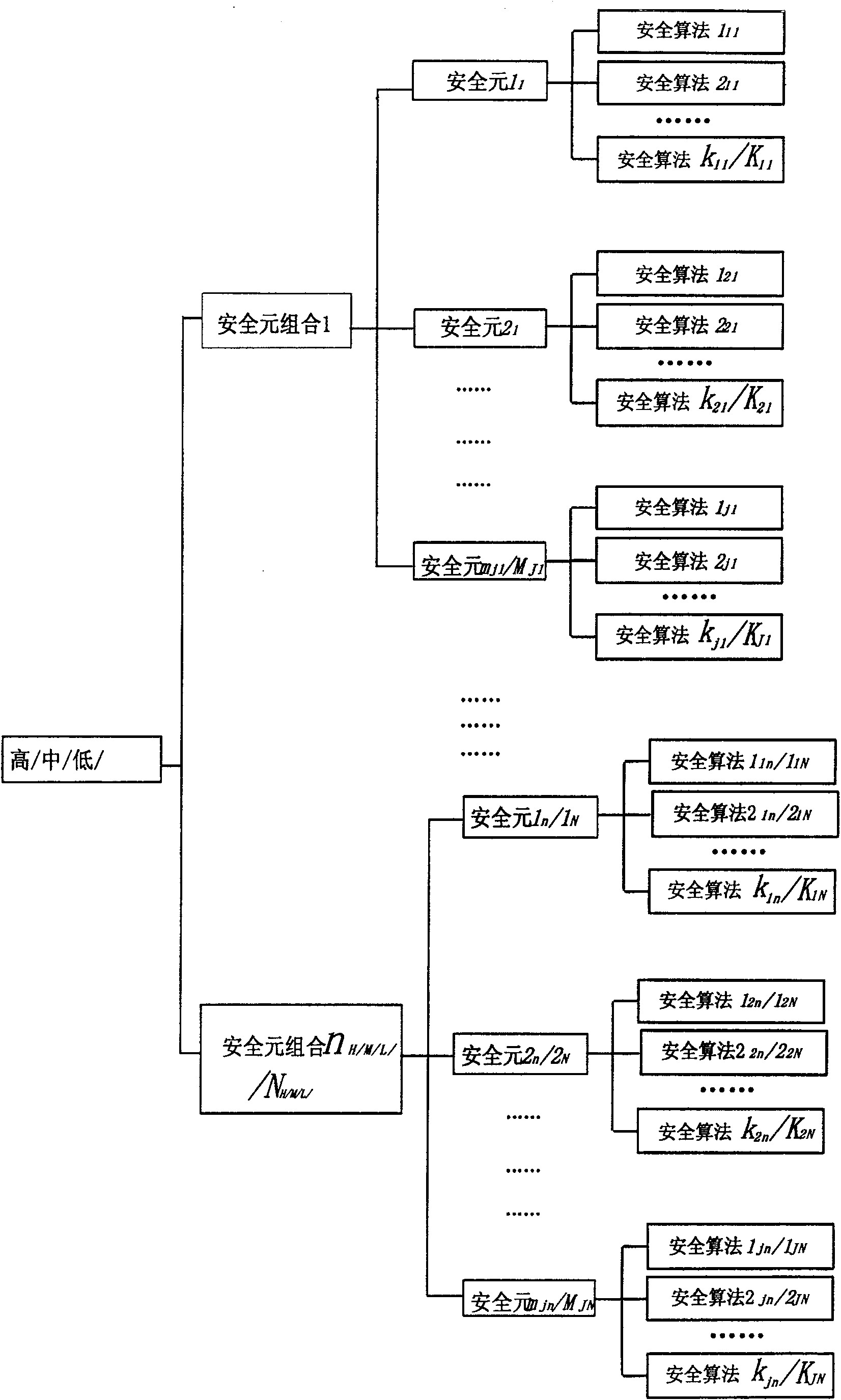
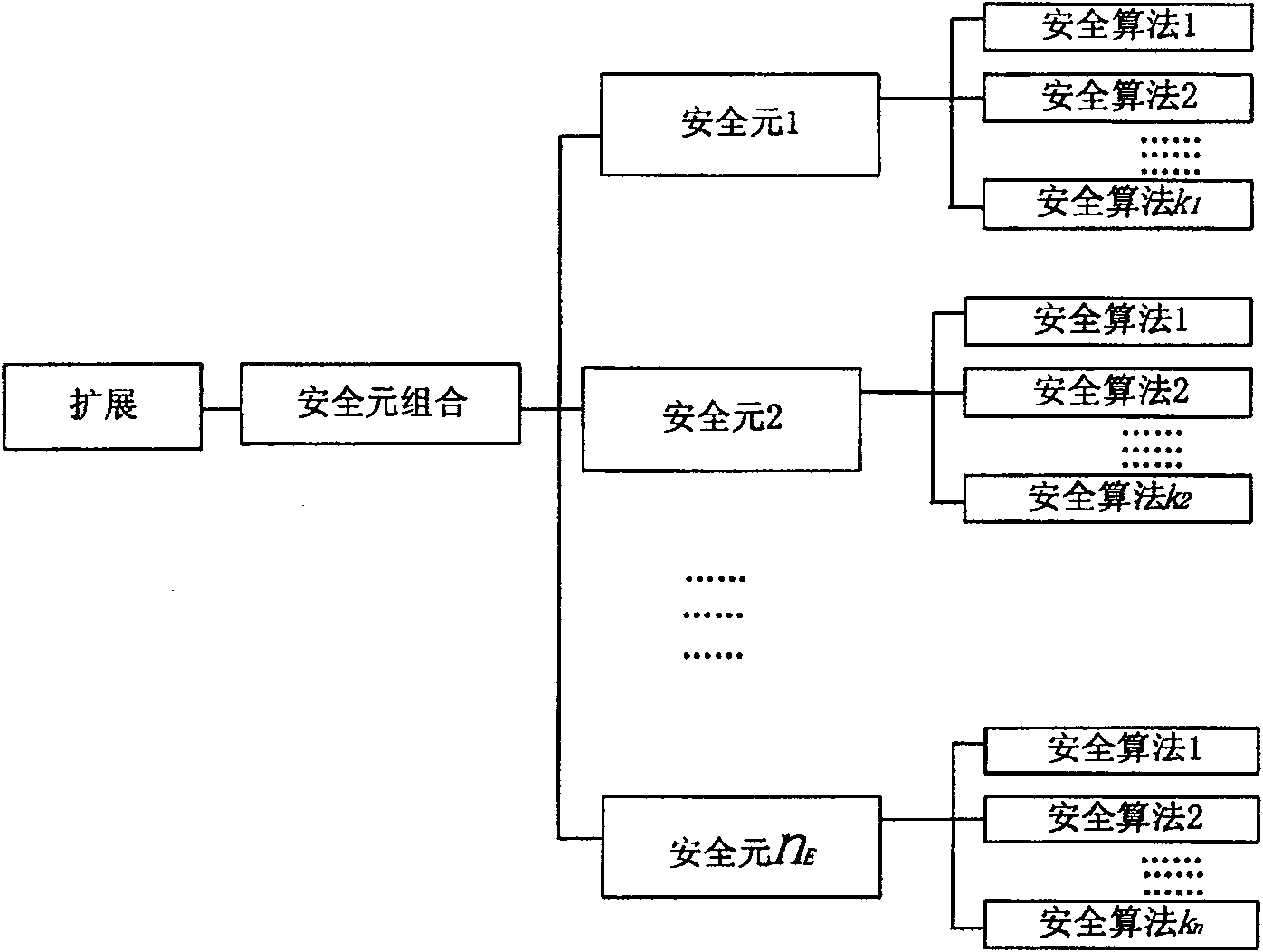
[0033] Refer to figure 1 As shown, the security strategy is divided into a basic security strategy and a value-added security strategy. The basic security policy corresponds to ordinary services. Value-added security policies correspond to value-added services. Operators need to provide security guarantees for value-added services. The realization of security guarantee requires operators to increase investment in mobile networks. Therefore, four security layers of high, medium, low and extended are configured in the value-added security strategy. The high, medium, and low levels are configured by the operator, and the extended level is configured by the user. Each security layer achieves different strength security guarantees. The security layer of each security level contains its corresponding security element combination and the security algorithm corresponding to the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com