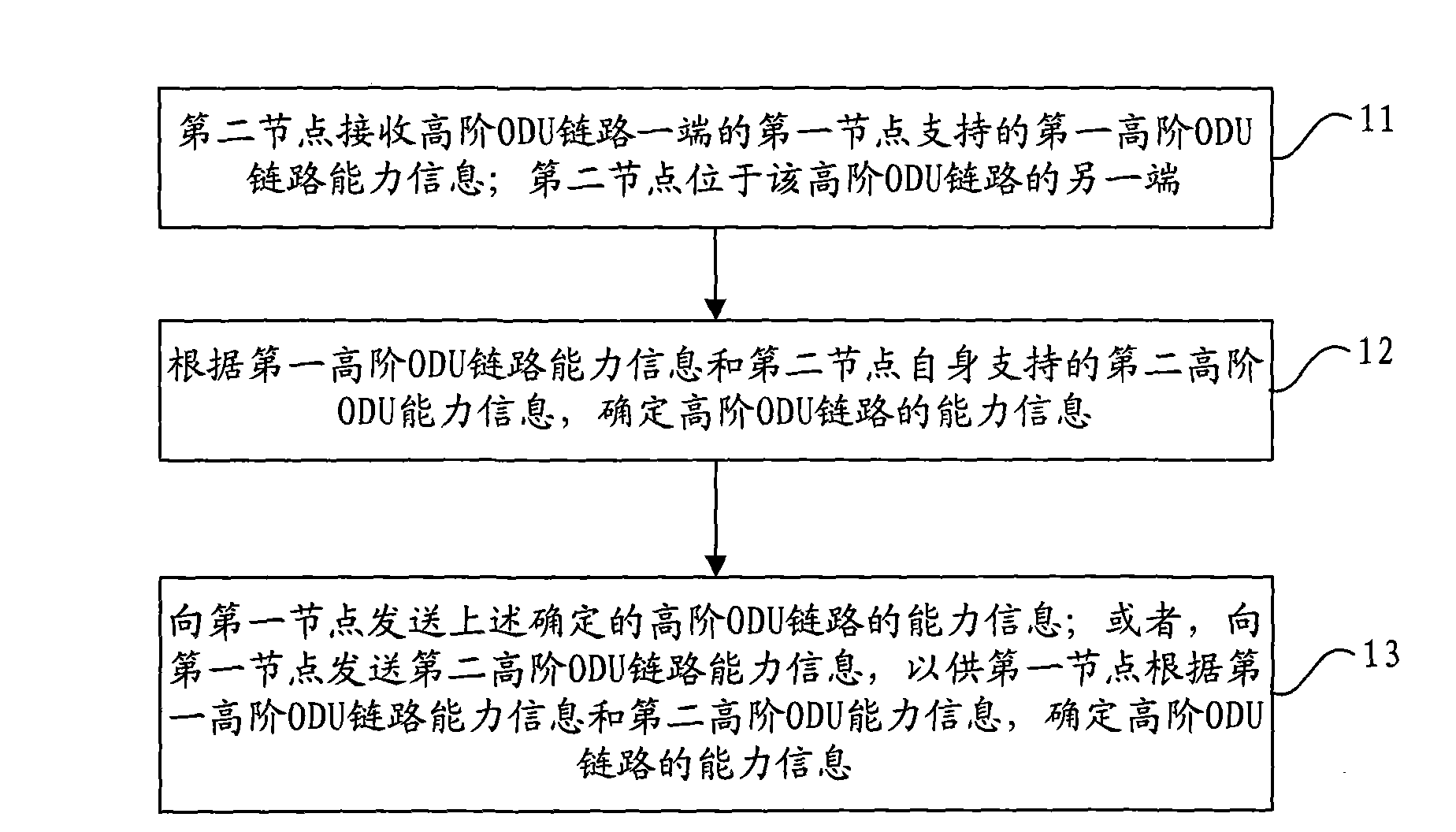
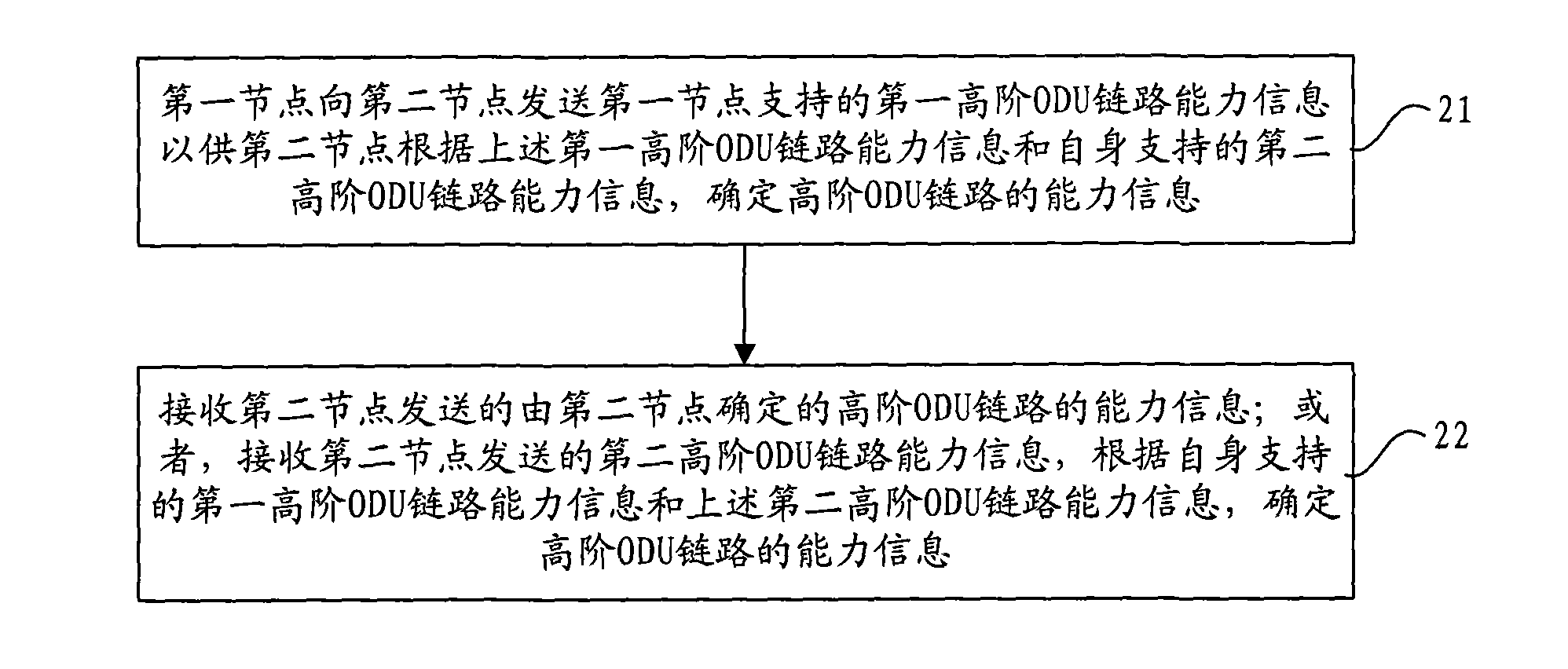
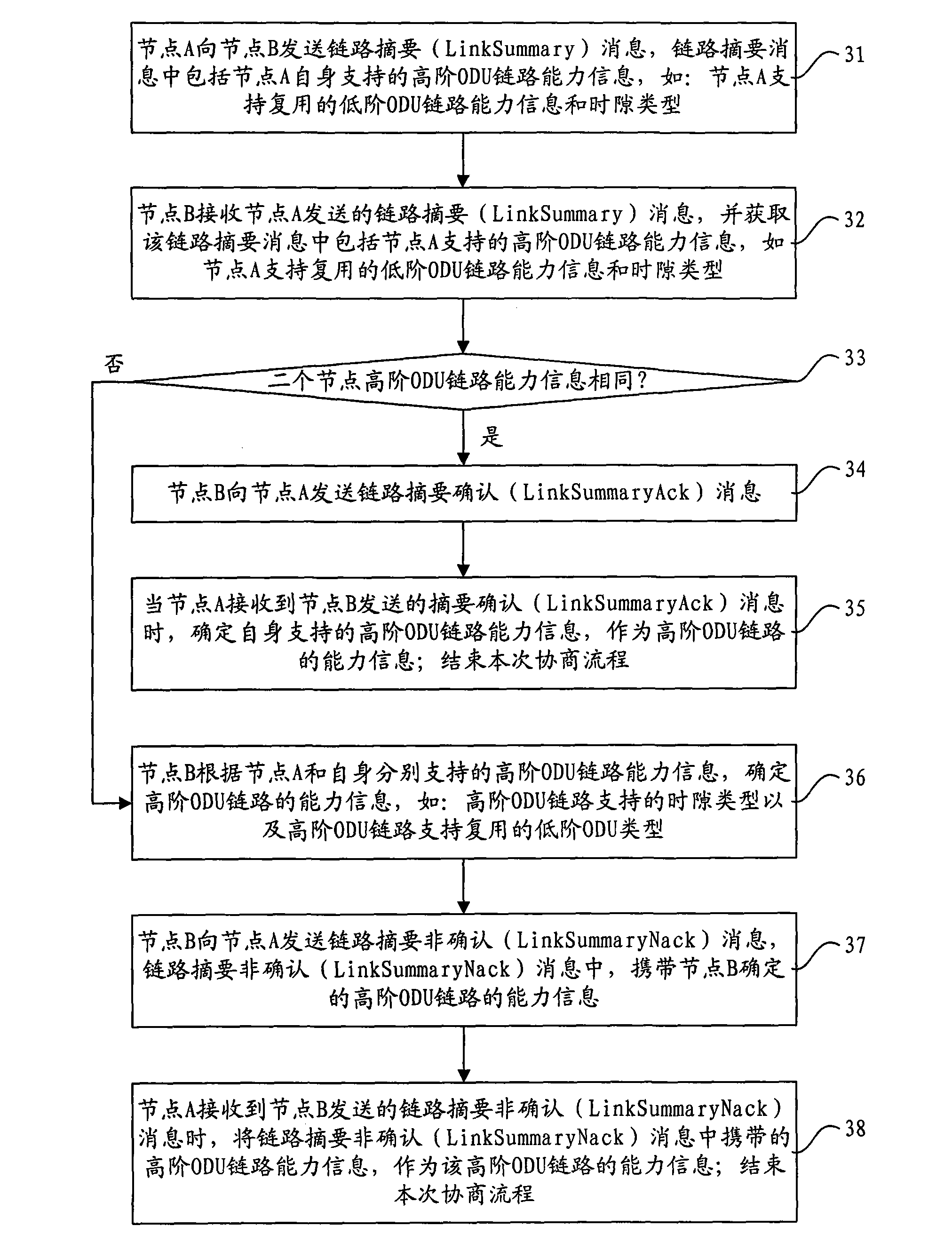
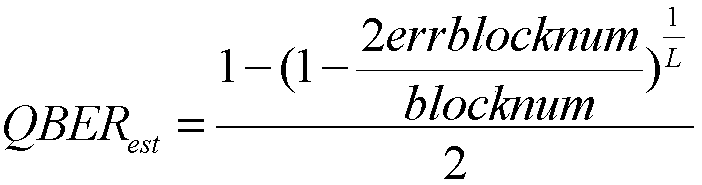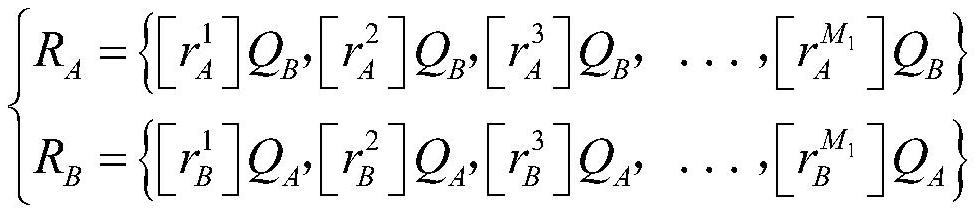Patents
Literature
55results about How to "Improve negotiation efficiency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
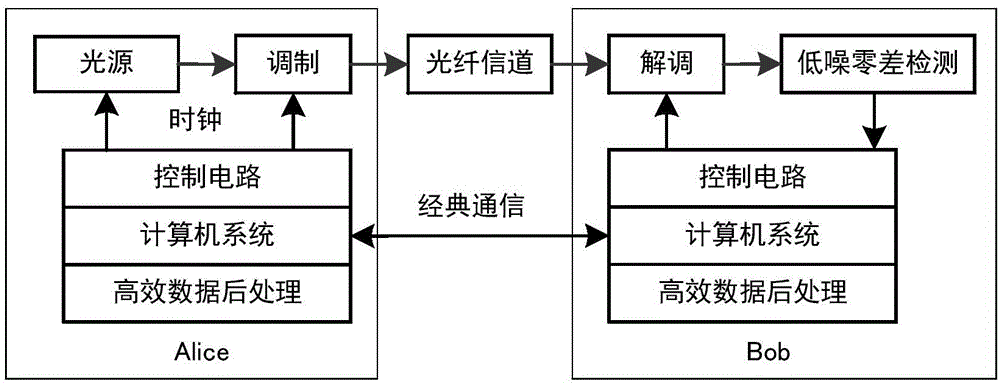
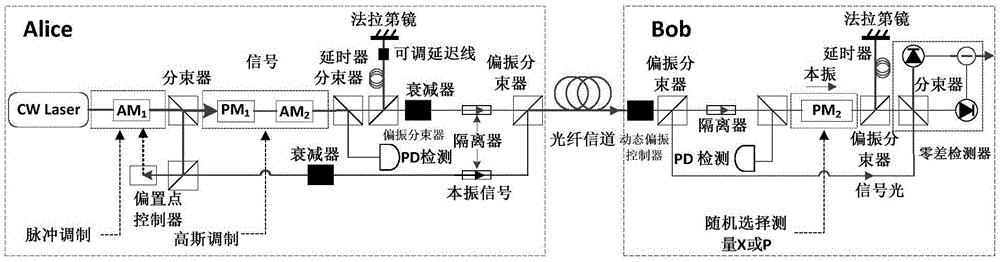
Long range continuous variablequantum key distribution method based on Gaussian-modulationcoherent state
ActiveCN105024809ASafe communication distance extensionReduce noiseKey distribution for secure communicationComputer hardwareCoherent states
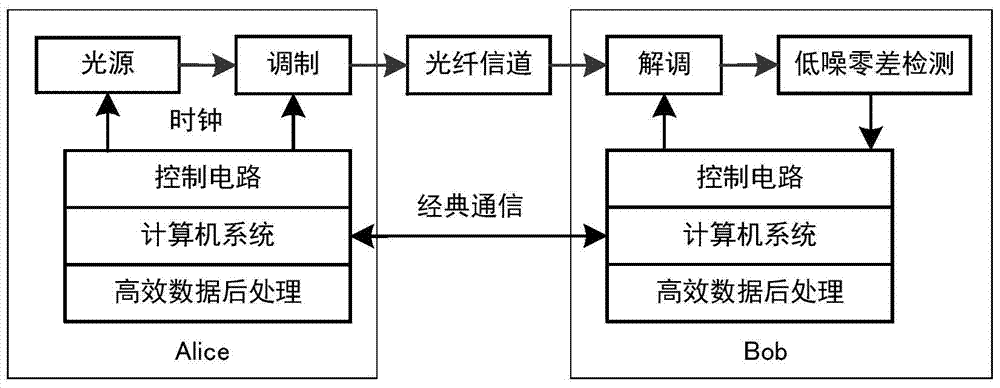
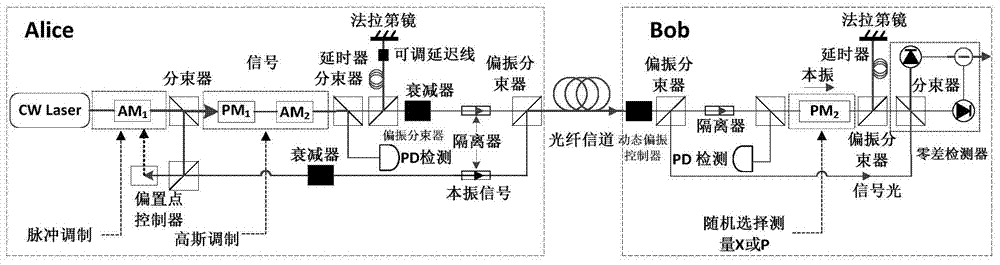
The invention discloses a long range CVQKD (Continuous Variable Quantum Key Distribution) method based on a Gaussian-modulationcoherent state. The method includes a step A of continuous variable initial key distribution which includes Gaussianmodulation of initial continuous key data through a coherent state by a sender Alice, long range transmission through an optical channel, demodulation and detection by a receiver Bob, and acquisition of initial continuous key data; and a step B of pre-treatment, error correction and confidentiality enhancement on acquired initial continuous key data by utilizing a data post-treatment algorithm and acquisition of a final binary digit safe key. According to the invention, the safe communication range of a CVQKD system based on the Gaussian-modulationcoherent state can be enlarged to 100-150 km.
Owner:上海循态量子科技有限公司
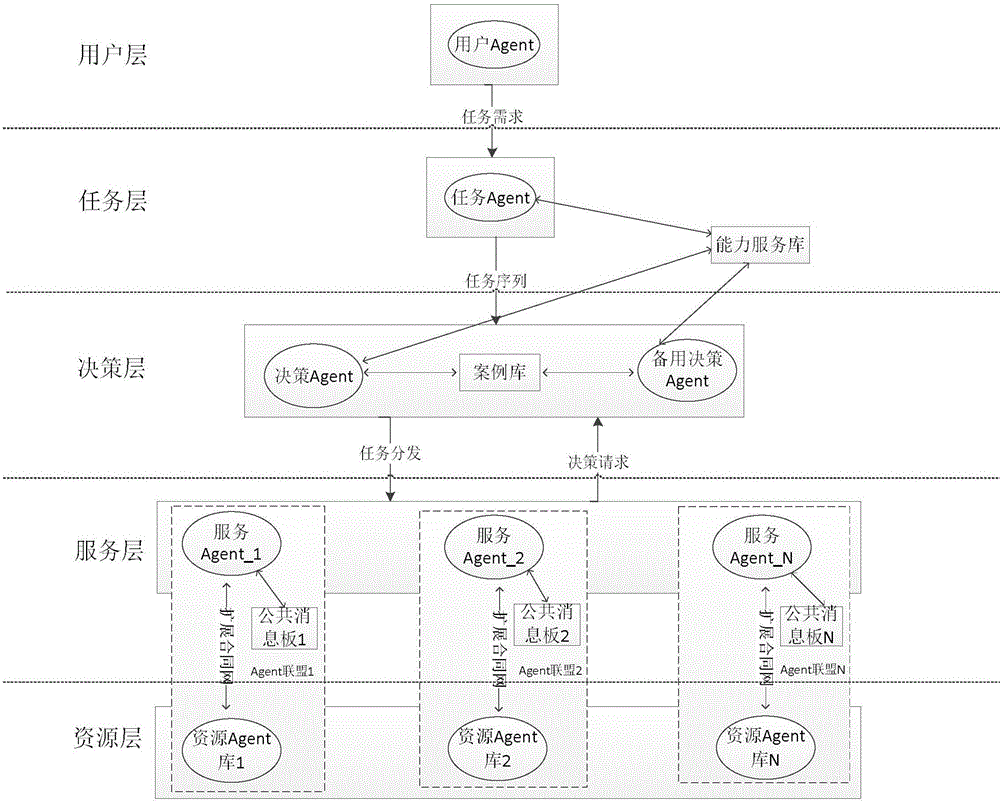
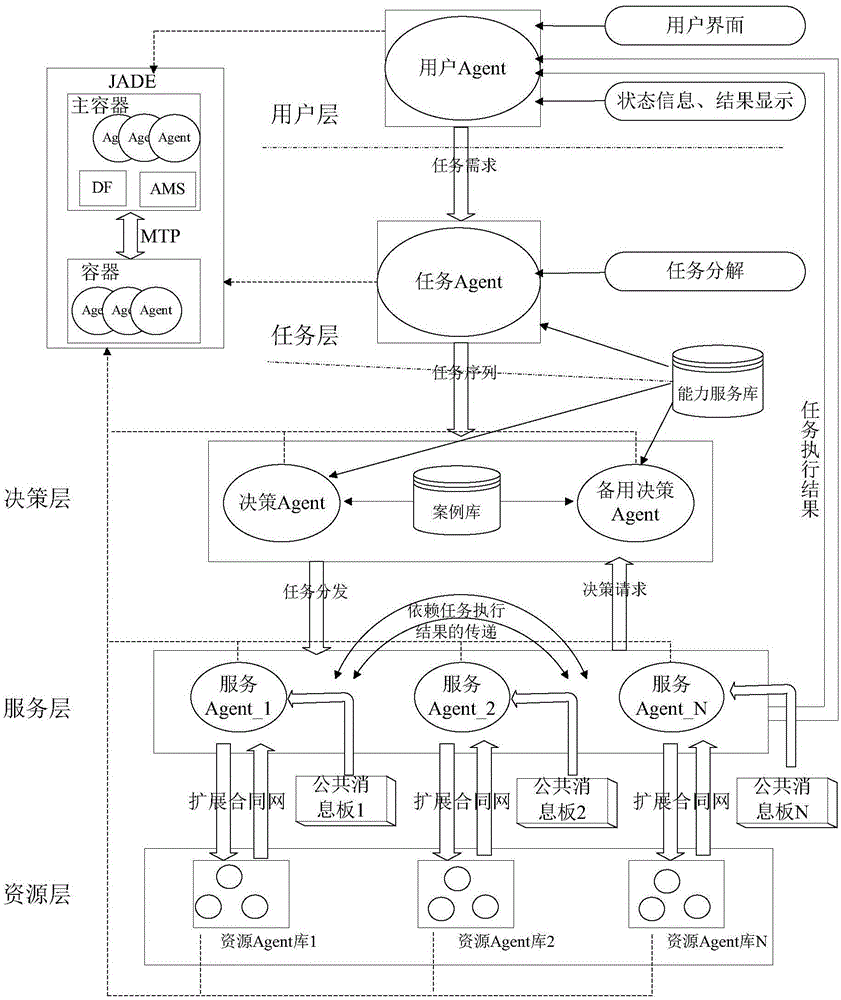
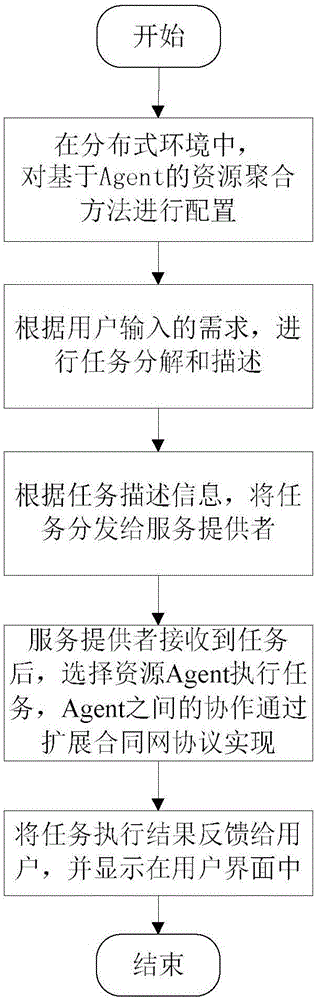
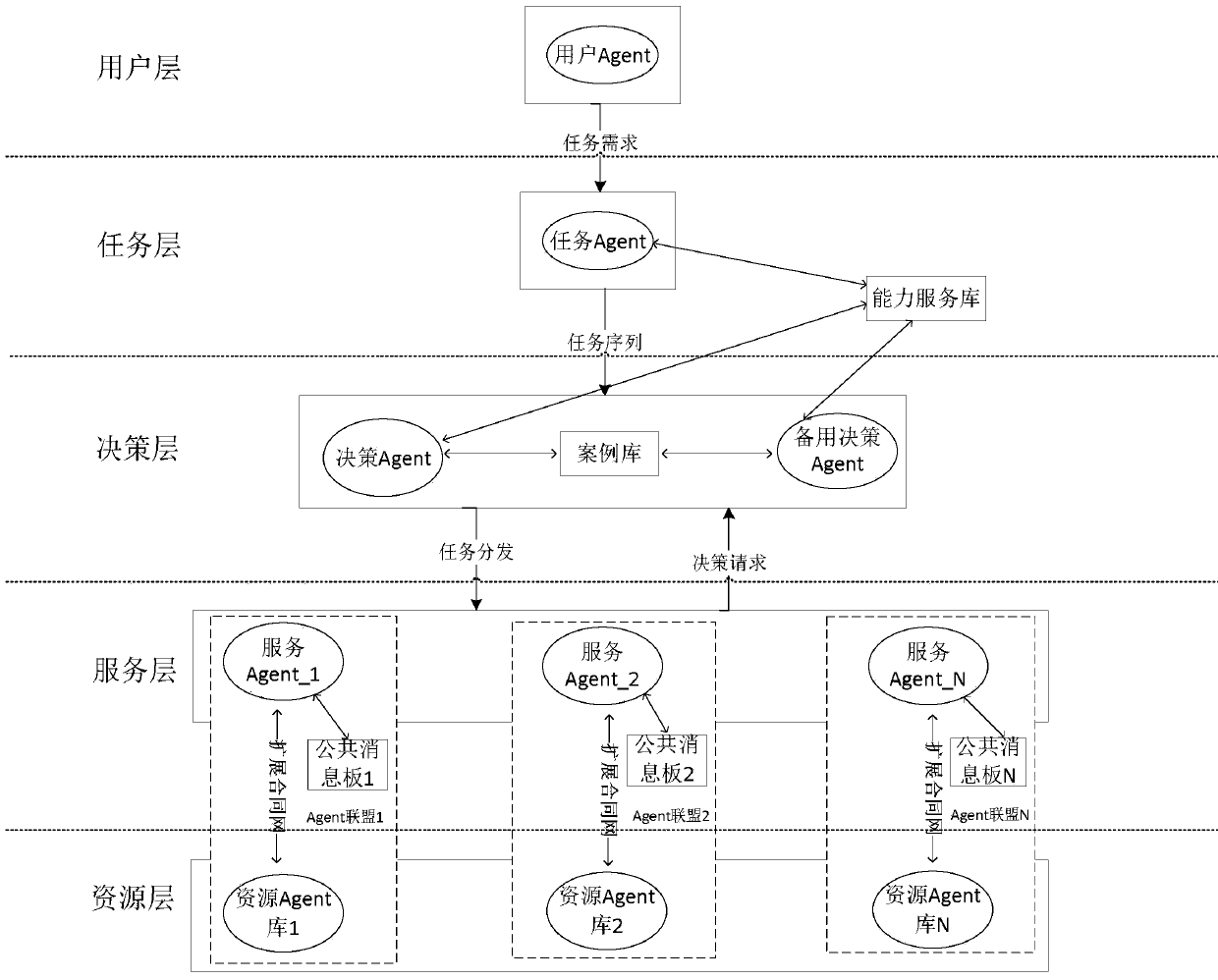
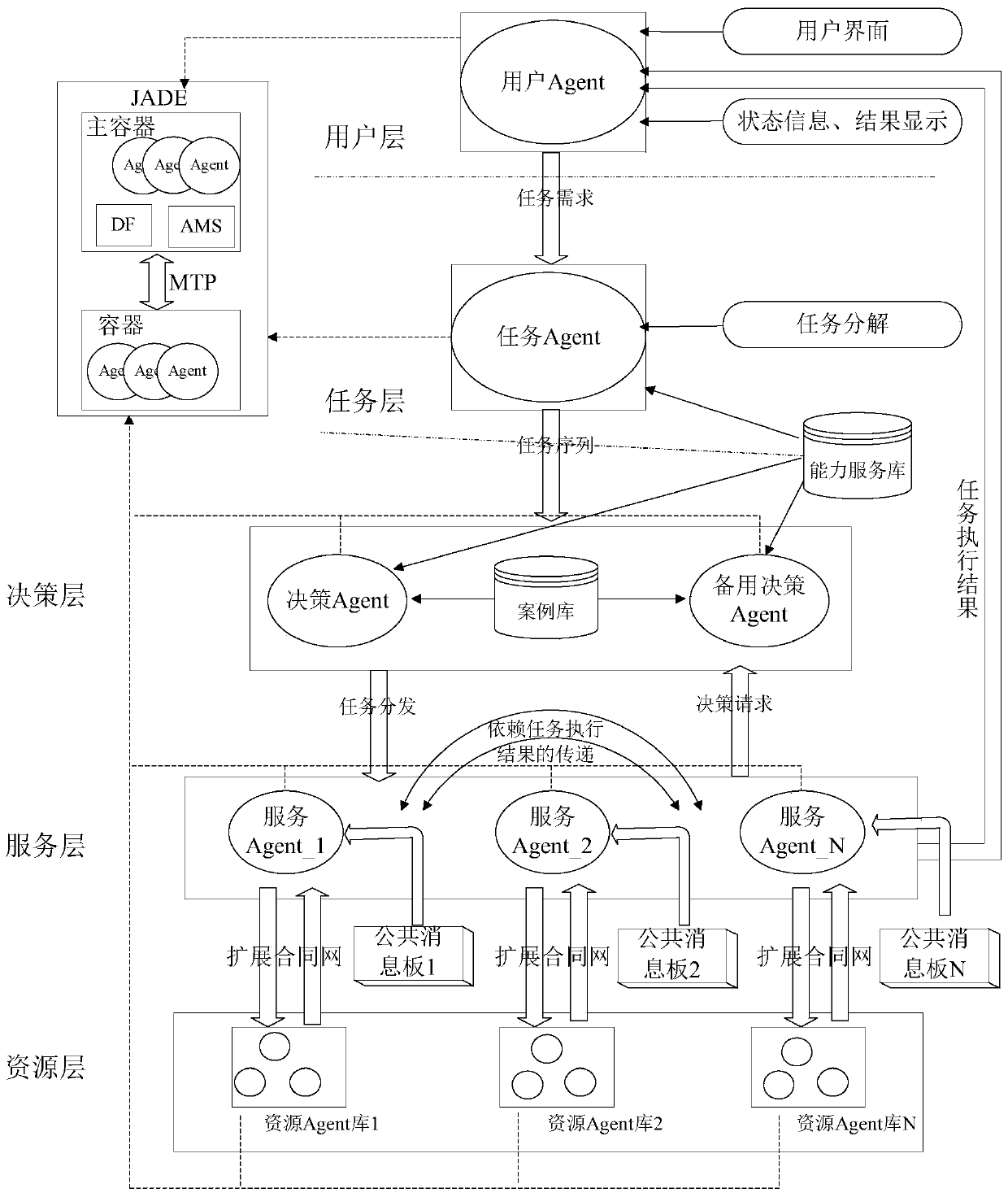
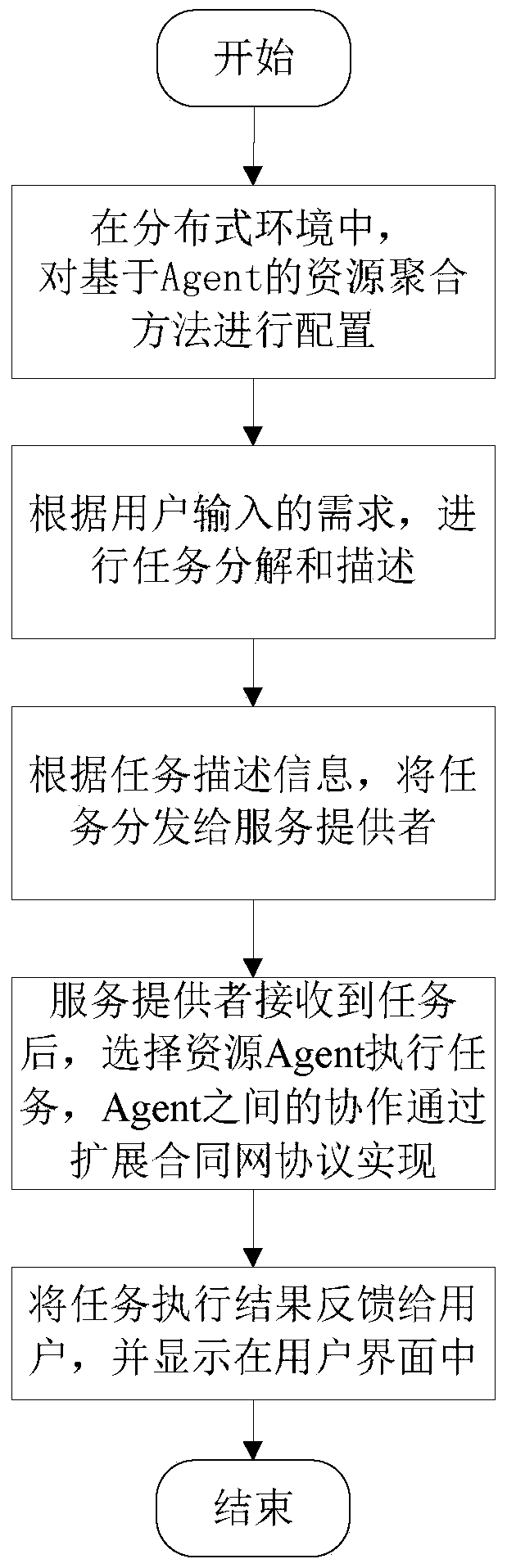
Resource polymerization method based on Agent
ActiveCN105069010AReduce trafficRespond quickly to mission needsWeb data indexingSpecial data processing applicationsContract Net ProtocolHeterogeneous network
The invention discloses a resource polymerization method based on Agent; in computer and network technology wide application, resources scattered in a complex heterogeneous network become more and more, and the method can effectively gather the resources scattering in the distributed environment; the method comprises the following steps: configuring the resource polymerization method based on Agent in a distributed system; a task agent resolves and describes according to a user inputted task demand; a decision agent distributes the task to a corresponding service agent according to task description information; the service agent selects a resource agent in an Agent alliance to execute the task, a task execution result is returned to a user Agent, and displayed in a user interface. Communication between the service agent and the resource agent complies with an expansion contract net protocol, thus reducing communication load between Agents, and fast responding to the user task demand. The resource Agent can joint or withdraw from the Agent alliance, so dynamic characteristic is provided, thus enhancing resource polymerization method flexibility and scalability.
Owner:XIDIAN UNIV
Quadratic congruence equation-based method for resisting denial-of-service attacks of wireless network
InactiveCN102196432AReduce the number of negotiationsIncrease the number of negotiationsAssess restrictionSecurity arrangementWireless mesh networkBeacon frame
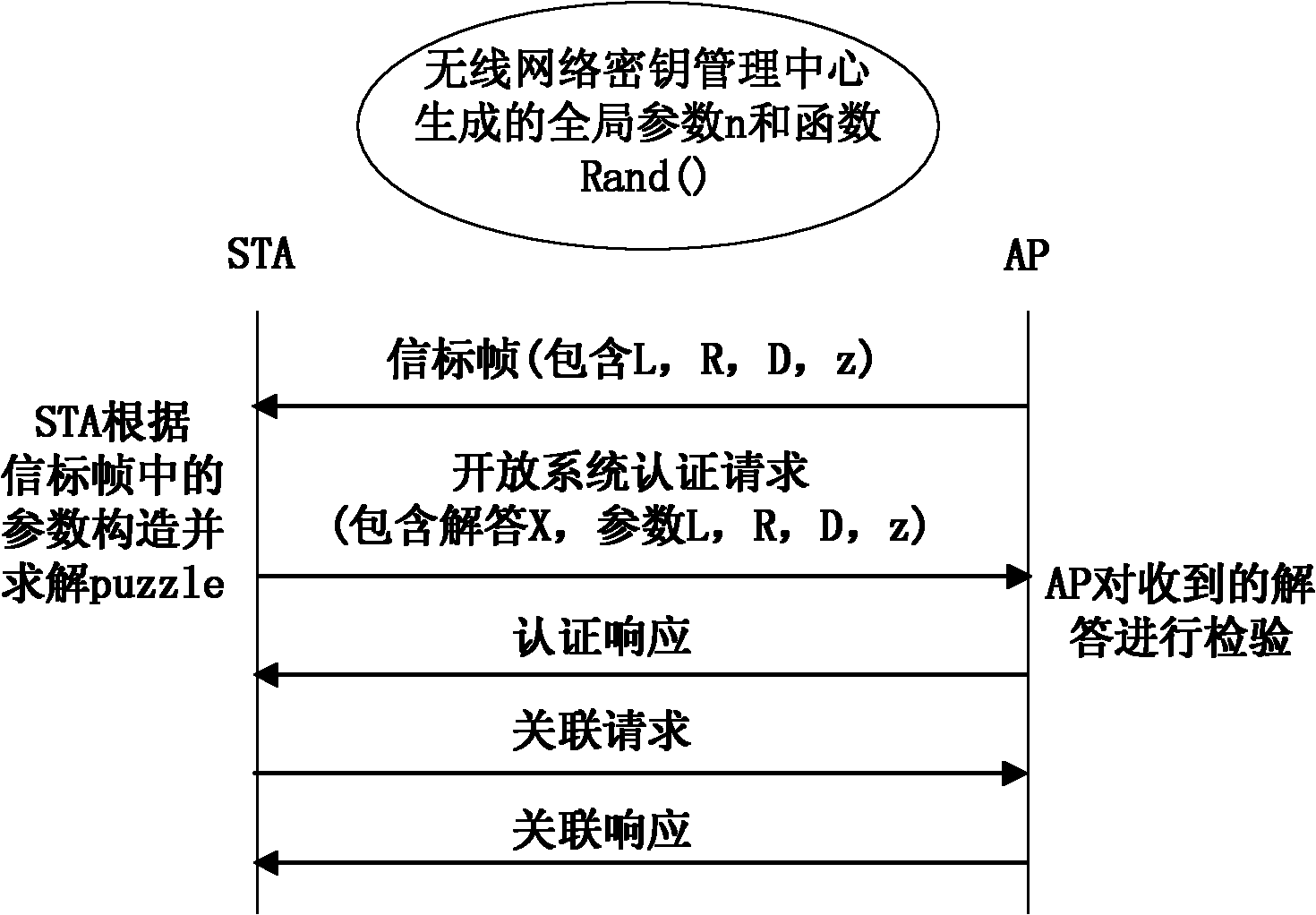
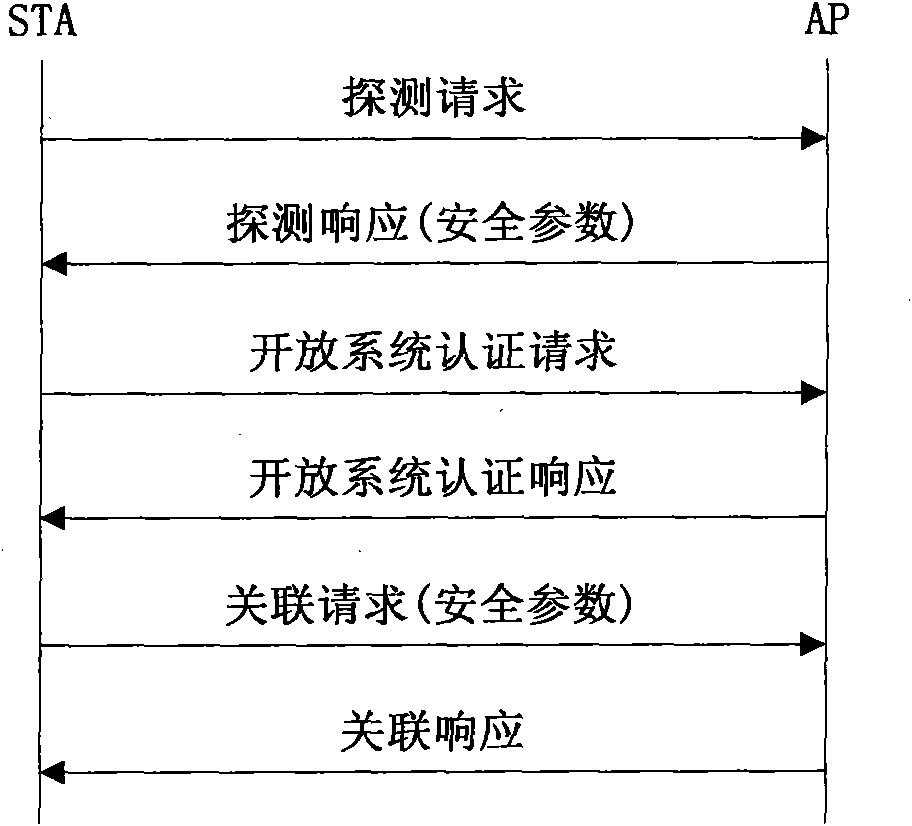
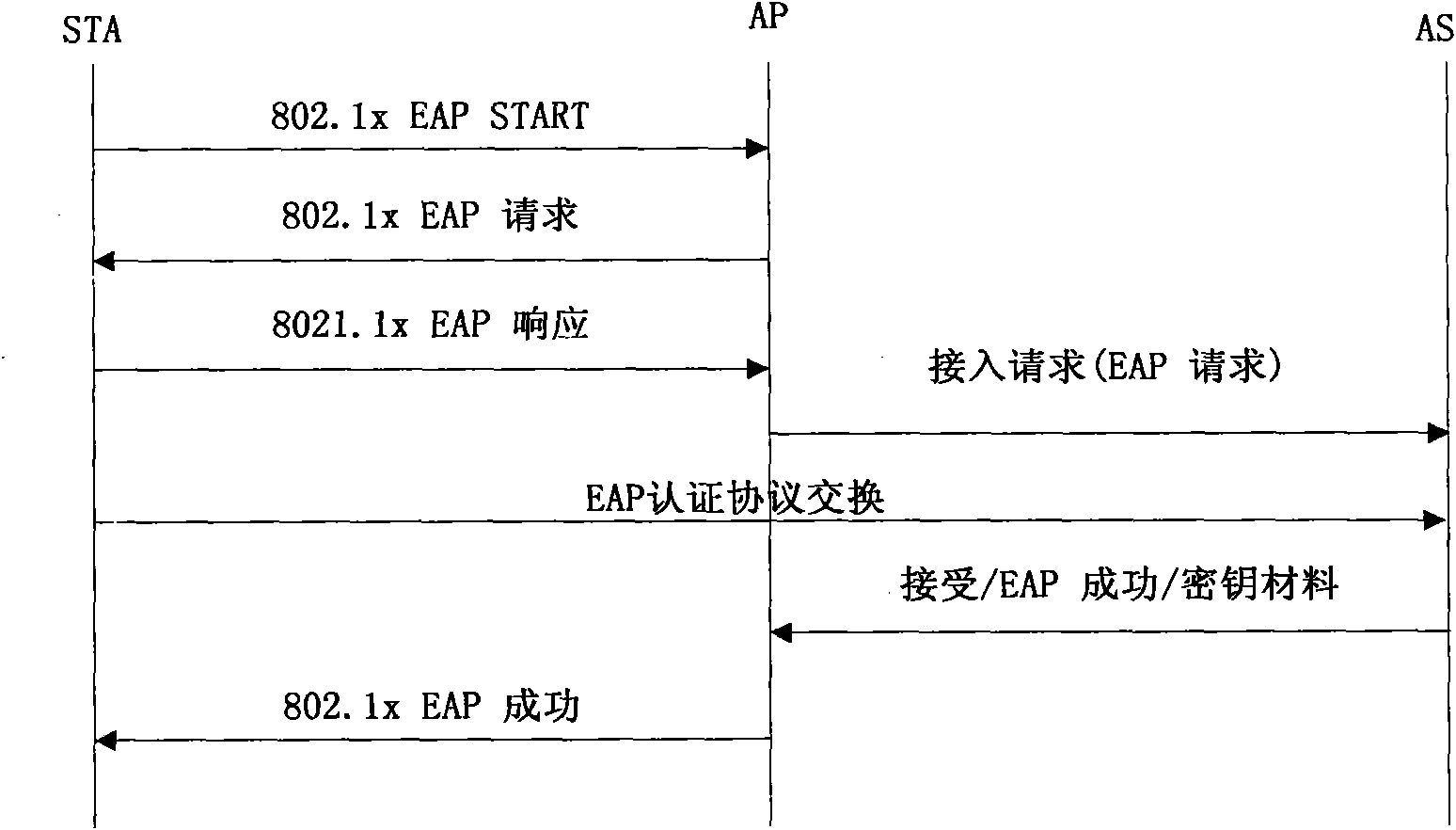
The invention discloses a quadratic congruence equation-based method for resisting denial-of-service attacks of a wireless network, which belongs to the technical field of network safety, and mainly solves the problem that the DoS (Denial-of-Service) attacks exist in a wireless access authentication process of an IEEE (Institute of Electrical and Electronic Engineers) 802.11i protocol. The method is implemented by the following steps: an AP (Access Point) adds parameters used for constructing a puzzle into a beacon frame and broadcasts the beacon frame periodically by using the beacon frame in the IEEE 802.11i protocol; a client STA (Special Temporary Authority) acquires the beacon frame, extracts puzzle parameters from the beacon frame, constructs and solves the puzzle in combination with the current global parameters of the wireless network, adds the puzzle parameters and the solution into an authentication request message, and sends an authentication request message to the AP; and the AP receives an open system authentication message of the STA, and the AP sends the authentication request message to the STA to complete the association process when the solution of the puzzle is correct, or the request of the STA is terminated. When the method is adopted, the negotiation times increased to construct the puzzle in a traditional client puzzle scheme are reduced, and the negotiation efficiency and the DoS attach resistance of the wireless access authentication protocol are improved.
Owner:XIDIAN UNIV
Method for resisting denial of service (DoS) attack for wireless local area network access authentication
InactiveCN101778387AReduce the number of negotiationsImprove negotiation efficiencySecurity arrangementCombined useBeacon frame
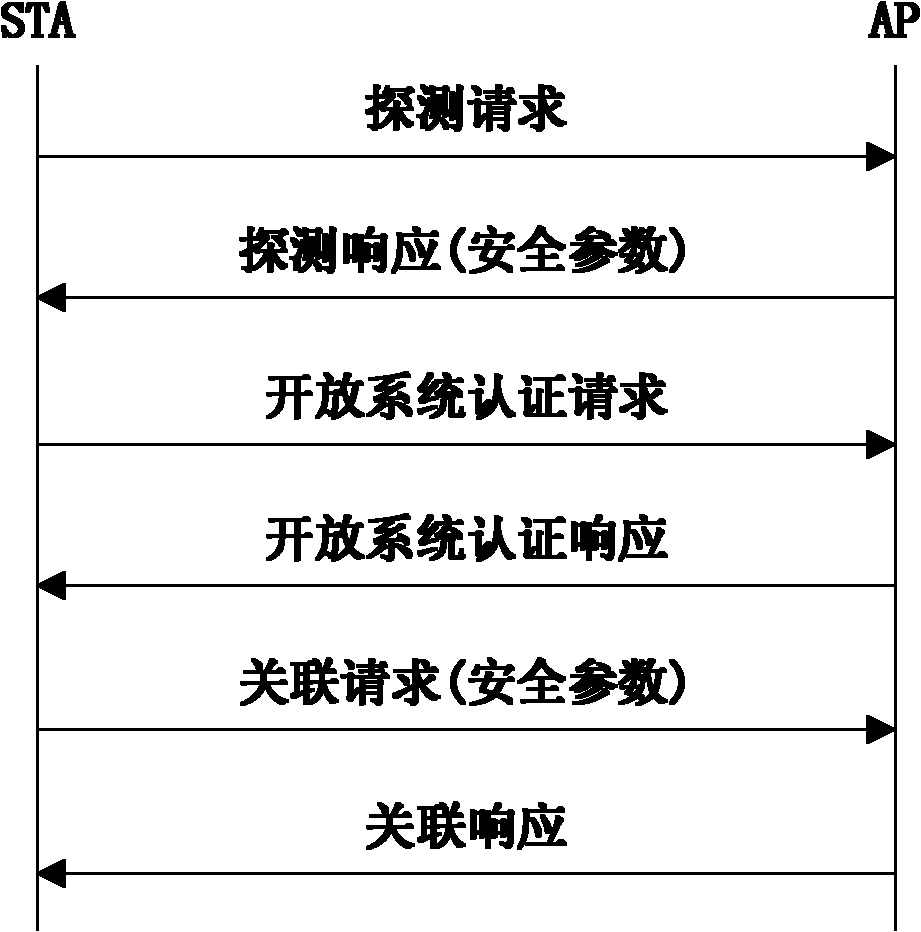
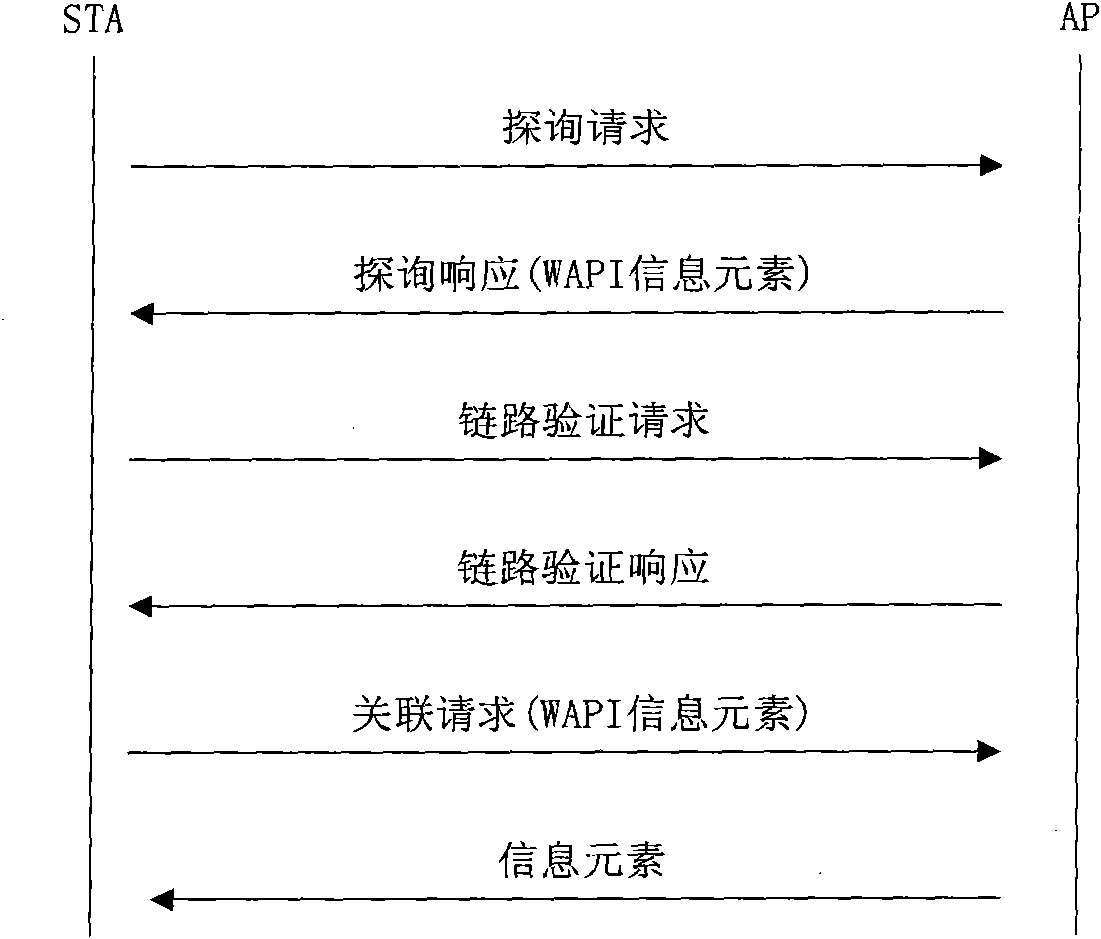
The invention discloses a method for resisting a denial of service (DoS) attack for a wireless access authentication protocol, which mainly solves the problem of DoS attack threat existing in the process of wireless access authentication of the traditional 802.11i protocol and the WAPI protocol. The method realizes the resistance on the DoS attack in the process of access authentication association by utilizing the combined use of a beacon frame issuing mechanism and a client-puzzle mechanism. The method comprises the following realizing steps of: (1) obtaining a beacon frame issued by an access point by a user in a monitoring way and obtaining the parameter needed for constructing a puzzle; (2) generating the puzzle and solving when the authentication interaction is finished; (3) containing the puzzle and the solution into an association request and transmitting the association request to the access point; and (4) judging whether the association process is finished or not by the access point through the authentication on the puzzle and the solution. The invention has stronger DoS attack resistance and adaptability and is suitable for the traditional wireless access authentication protocol.
Owner:XIDIAN UNIV
Trust negotiation building method and system based on history roles
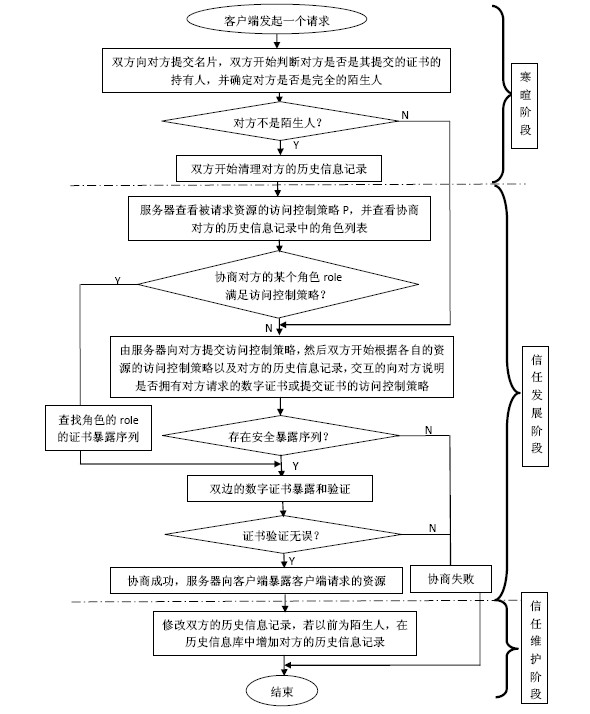
InactiveCN102075518AImprove negotiation efficiencyShorten follow-up negotiationsTransmissionInformation repositoryRelevant information
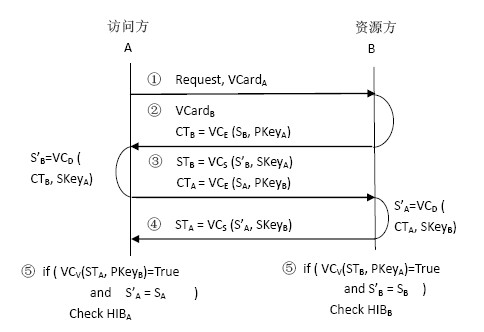
The invention discloses a trust negotiation building method based on history roles, which comprises the following steps that: (1) when a request party submits requests on a certain resource to a resource party, firstly, a chinchin stage of the trust negotiation is triggered, and the identities of the two parties and whether the historical negotiation success record information exists or not are verified; (2) after the chinchin stage is completed, the two parties enter a trust development period, a safe certificate disclosing sequence is found out to visit the requested resources through mutually disclosing visit control tactics and certificates; and (3) the two parties enter the trust maintenance stage after the trust negotiation is successful, relevant information of the other negotiation party in the current negotiation is stored for accelerating the subsequent negotiation process of the two parties. The method provided by the invention has the advantages that the successfully negotiated two parties update the roles for the other parties in self history information databases and record and obtain the certificate disclosing sequences of the two parties of the role. When the two parties negotiate again, the negotiation does not need to be carried out again, the disclosing can be directly carried out according to the certificate disclosing sequences of the role, the subsequent negotiation of the two parties is shortened, and the certificate collection activities of venomous negotiation adversaries is avoided.
Owner:HUAZHONG UNIV OF SCI & TECH
Link state self consulting method
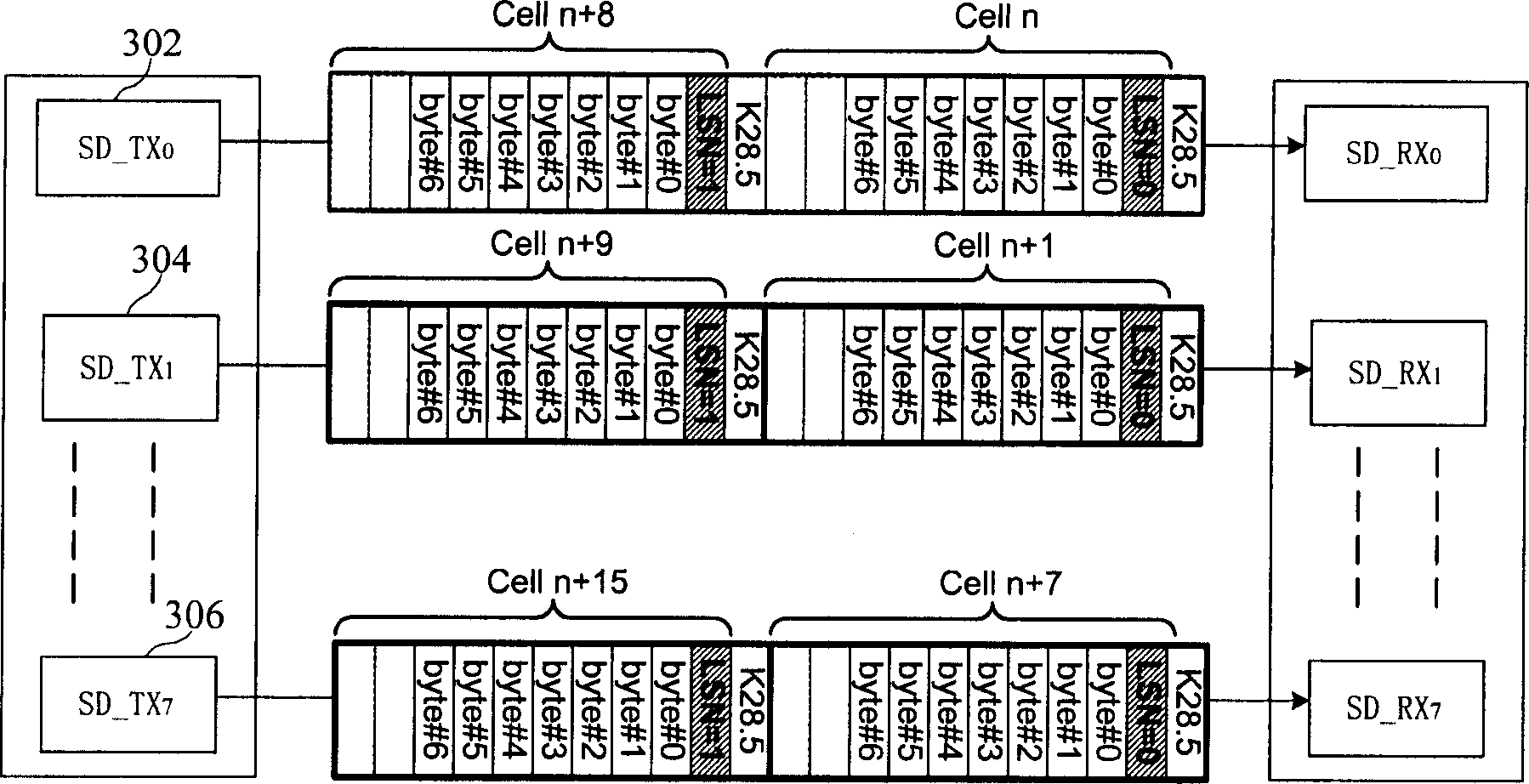
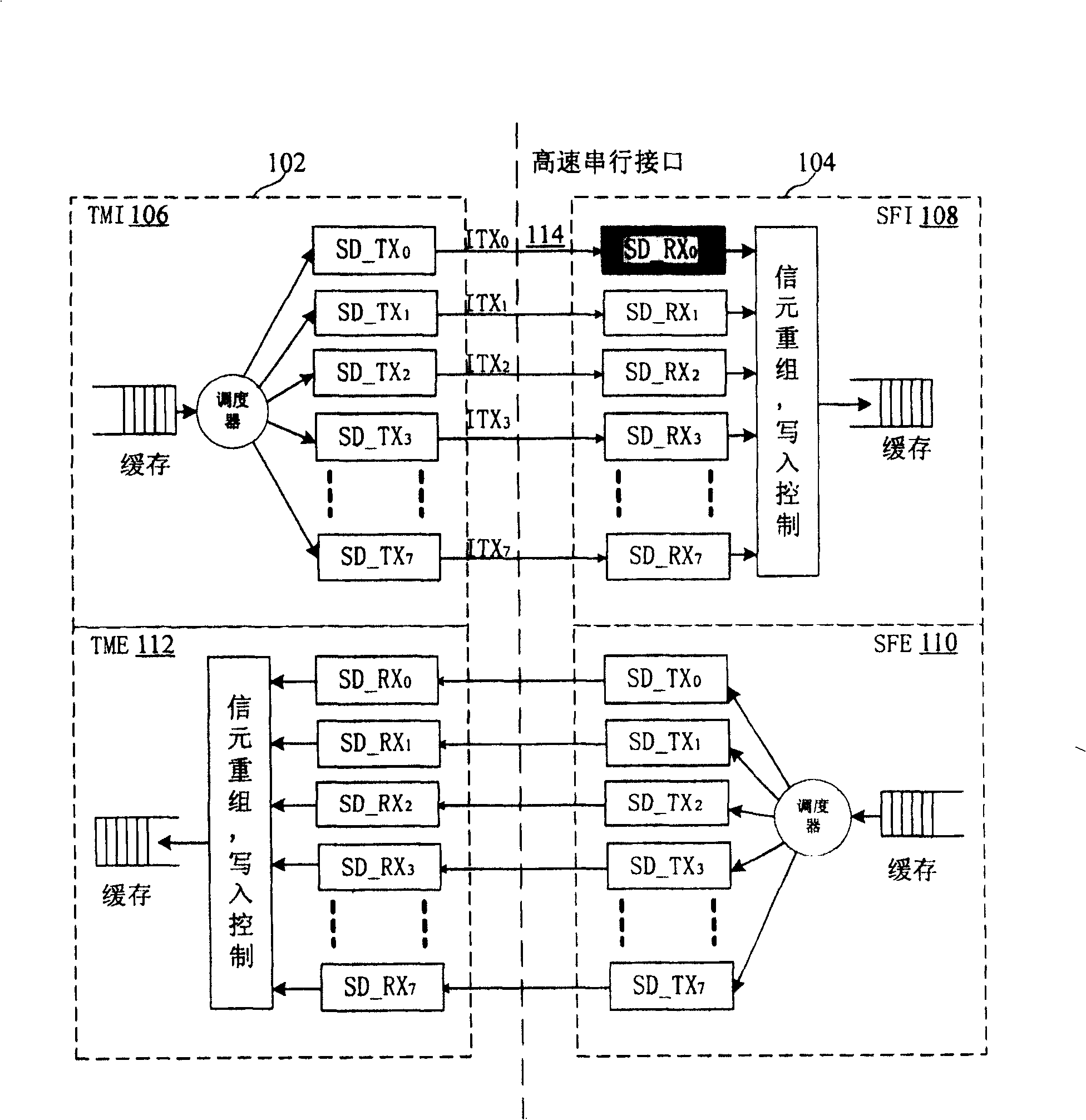
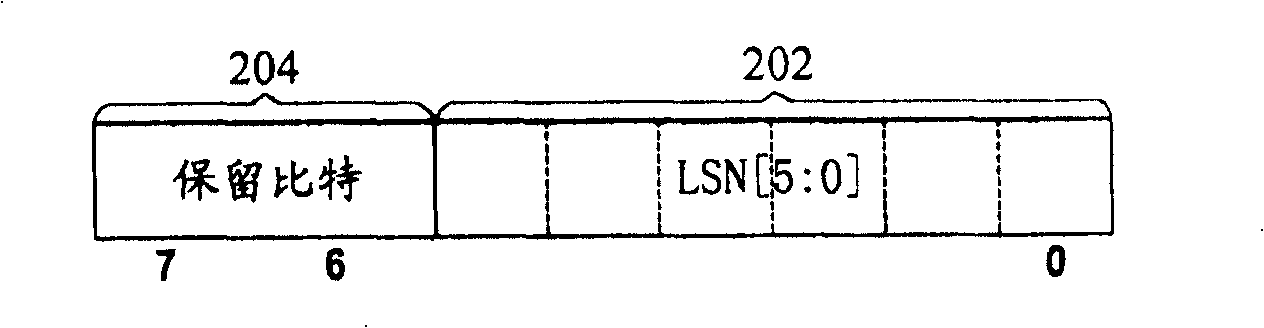
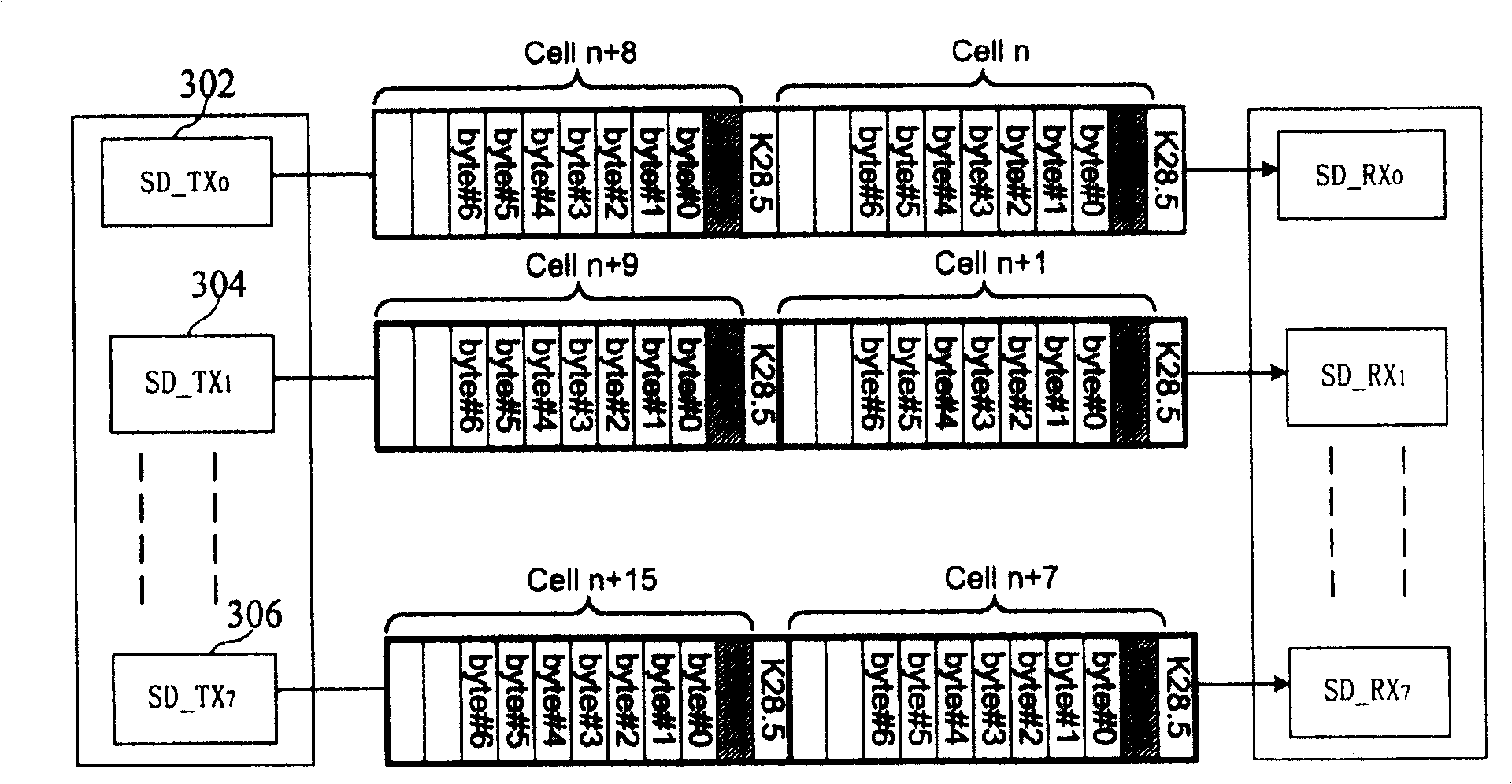
InactiveCN1859155AEasy to implementConsume less resourcesData switching by path configurationControl dataSoftware development
A link status self negotiation method is used for data transmission link state negotiation between transmitting end and receiving end. It contains receiving end receiving data according to right sequence through querying serial number in cell head; through cell head link gateway bit and line error bit to transfer link status; increasing link status list at receiving end and transmitting end; in link fault occurrence and link recover process through receiving end and transmitting end transmitting / receiving state to control data receiving and transmitting, to complete link self negotiation process. In link status self negotiation process, said invention also complete link self negotiation process through querying and configuring parallel-series / series-parallel convert on off state list. The present invention raises negotiation efficiency and systematical reliability.
Owner:HUAWEI TECH CO LTD
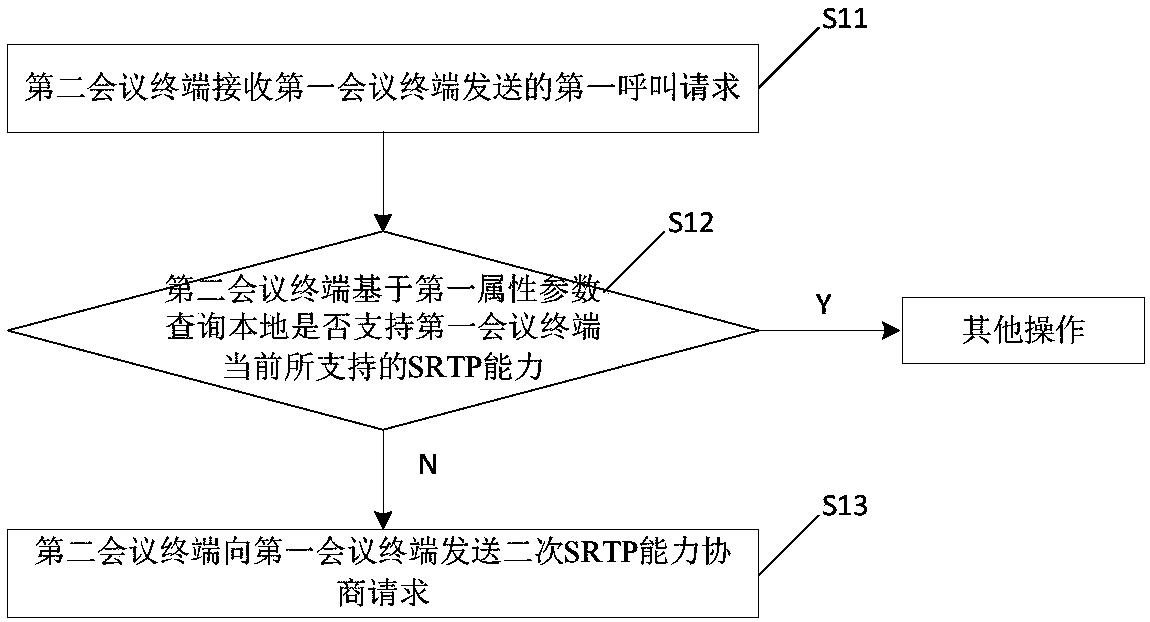
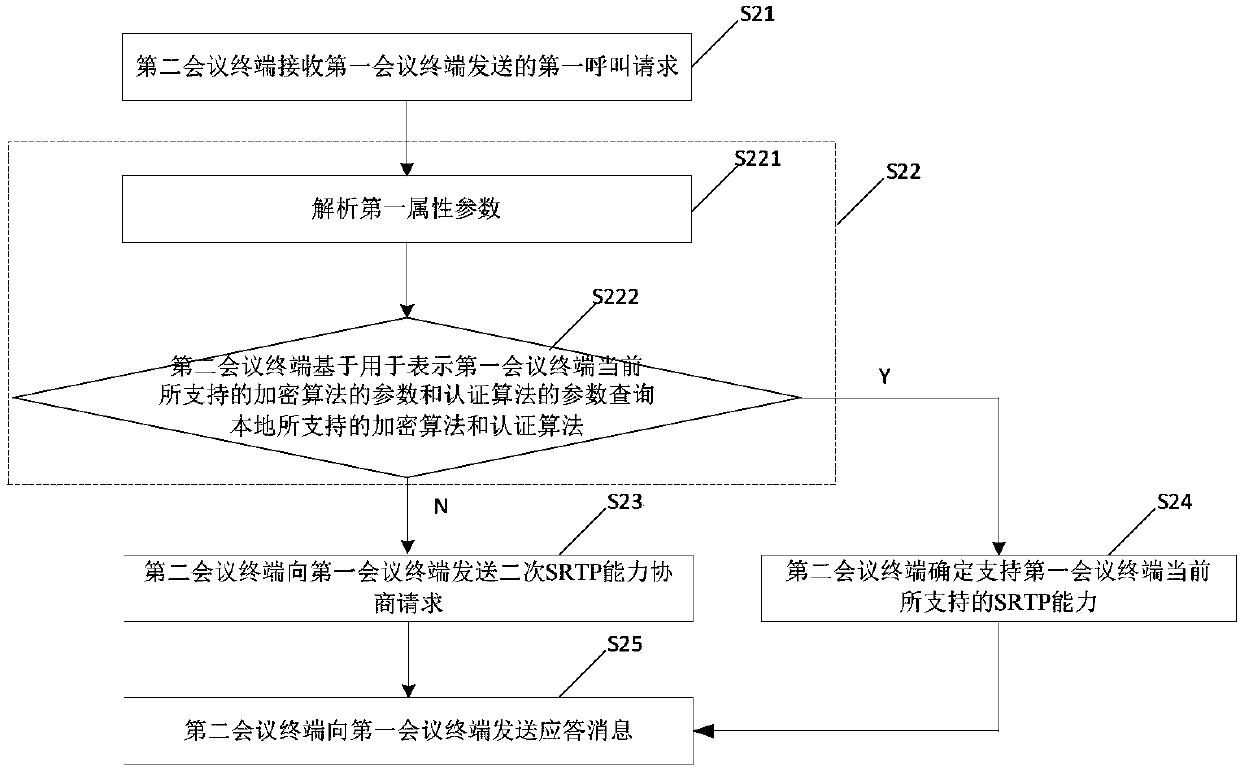
SRTP capability negotiation method and conference terminal
ActiveCN107846567AReduce failure rateGuaranteed validityKey distribution for secure communicationTelevision conference systemsTelecommunicationsResponse model
The invention discloses an SRTP capability negotiation method and a conference terminal. The method comprises the following steps: a second conference terminal receives a first call request sent by afirst conference terminal; the second conference terminal queries whether the SRTP capability supported by the first conference terminal at present is supported locally based on a first attribute parameter in the first call request, so as to perform primary SRTP capability negotiation; and if not, the second conference terminal sends a secondary SRTP capability negotiation request to the first conference terminal, wherein the secondary SRTP capability negotiation request is used for requesting to perform secondary SRTP capability negotiation with the first conference terminal. Related SRTP capability negotiation is performed by a request / response model; if the negotiation fails, it can be negotiated again through a secondary negotiation mechanism to ensure the effectiveness of the final SRTP capability, reduce the failure rate of the SRTP capability negotiation, and avoid the situation of negotiation failure due to SRTP capability updating or failure of all negotiation in the primary SRTP capability negotiation process.
Owner:SUZHOU KEDA TECH
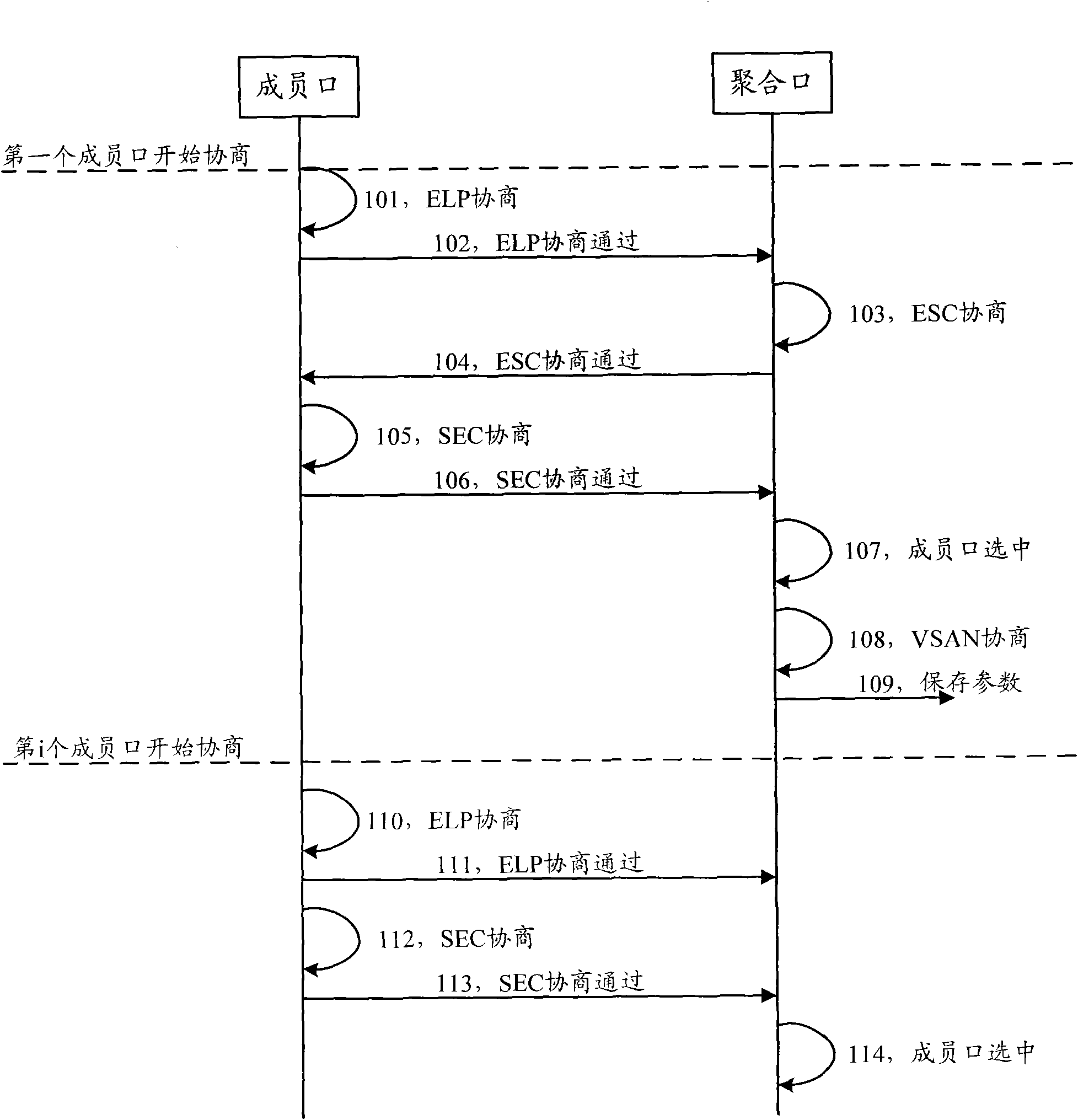
Link negotiation method based on fiber channel aggregate port and device
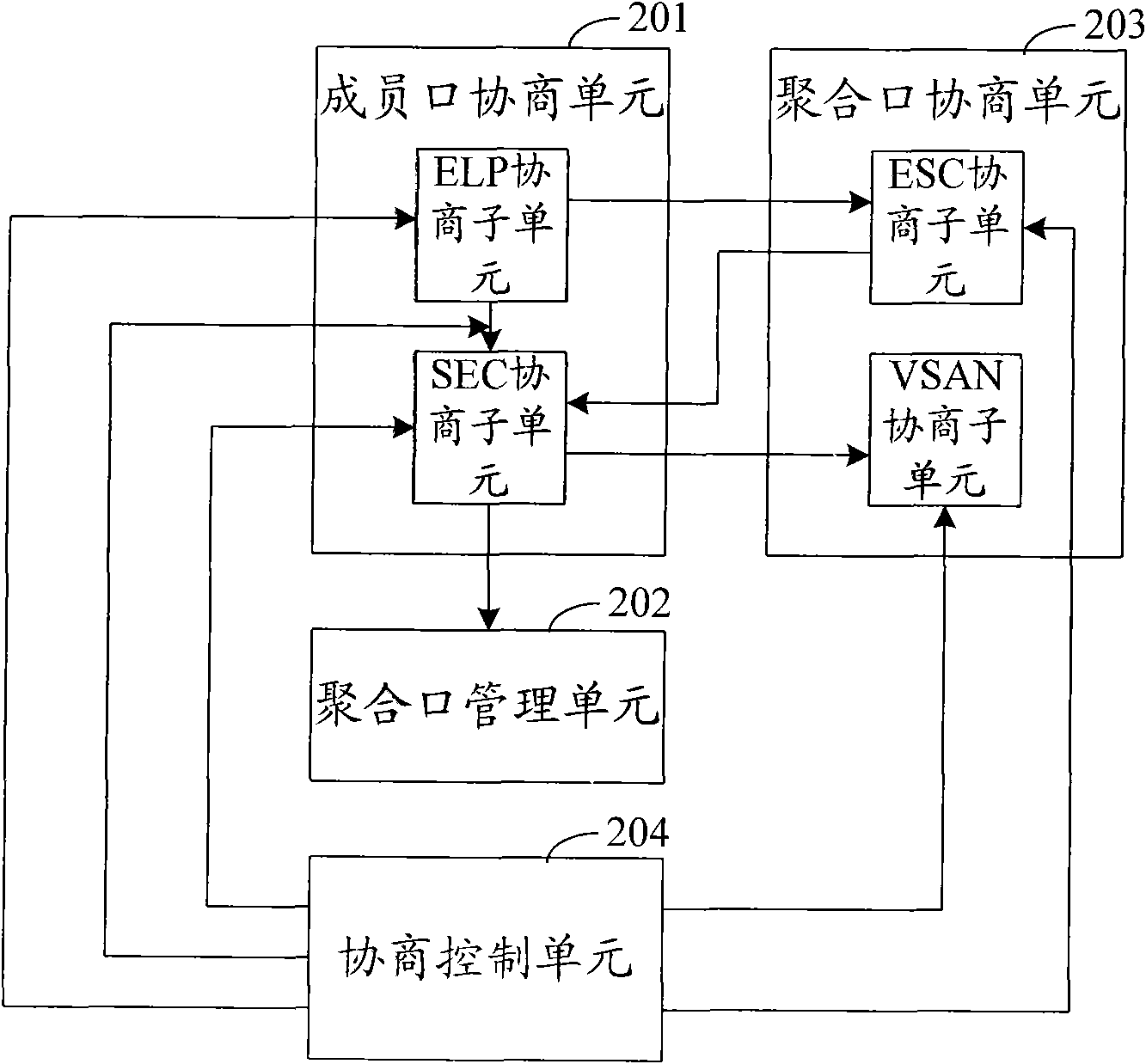
ActiveCN101582892AImprove negotiation efficiencyReduce configuration workloadTransmissionFiberFibre Channel
The invention discloses a link negotiation method based on a fiber channel aggregate port and a device. Configuration used for negotiation of the aggregate port is set at the aggregate port in advance in a unified way aiming at all member ports, aggregate port negotiation is only executed once when the first member port is added, and the parameter obtained by the aggregate port negotiation is stored in the aggregate port; while, the stage of aggregate port negotiation is omitted for other member ports which are subsequently added; therefore, all the member ports are unnecessary to execute the whole link negotiation process once, thus improving the efficiency of link negotiation. Furthermore, when the member ports approved by member negotiation are selected, the member port negotiation parameters are unnecessary to be compared with aggregate port negotiation parameters to determine whether the parameters are consistent, thus the same configuration on all the member ports is not needed, and the configuration workload of the member ports is further reduced; meanwhile, the problem of difficult processing caused by inconsistent negotiation parameters does not exist.
Owner:NEW H3C TECH CO LTD
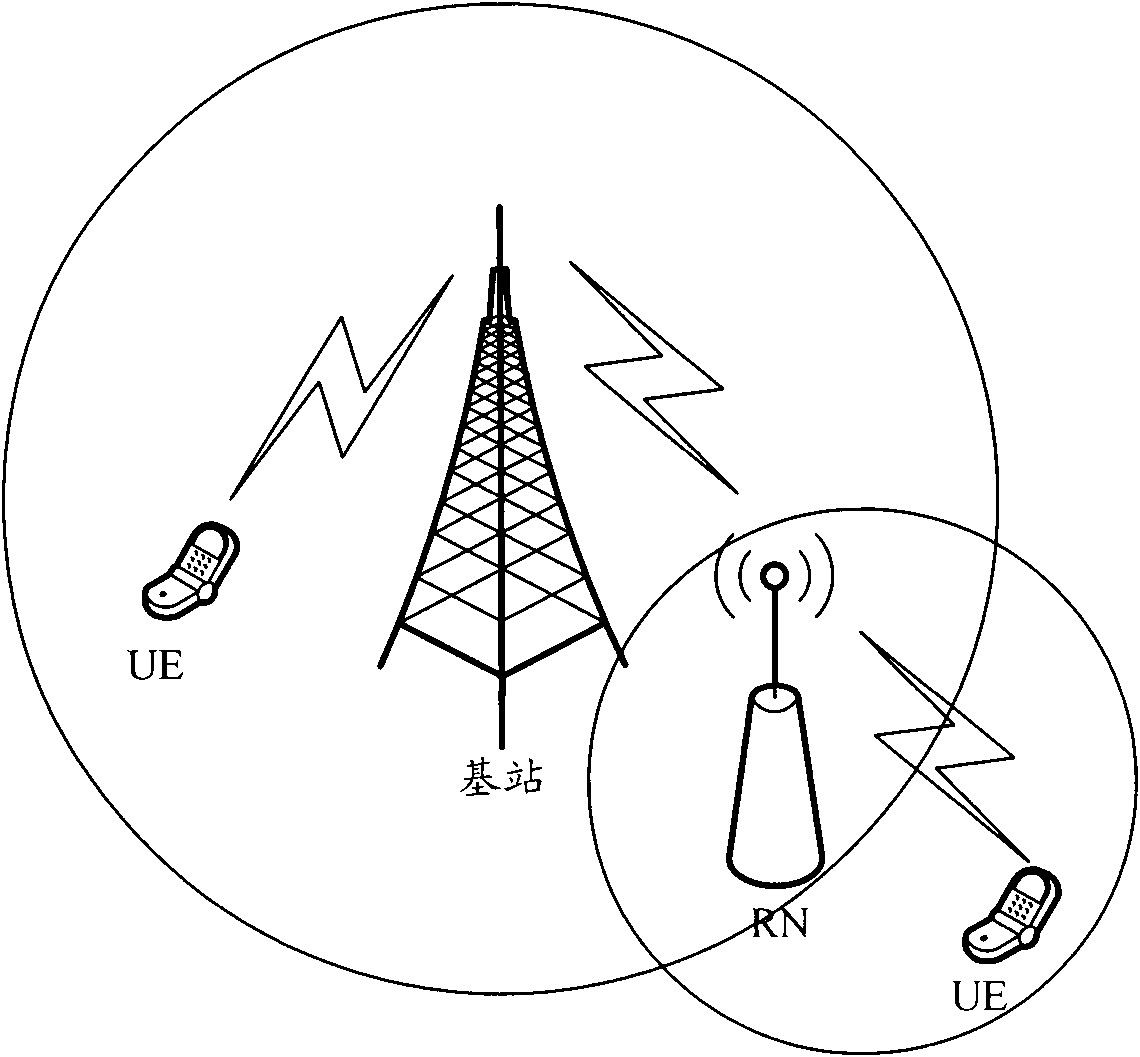
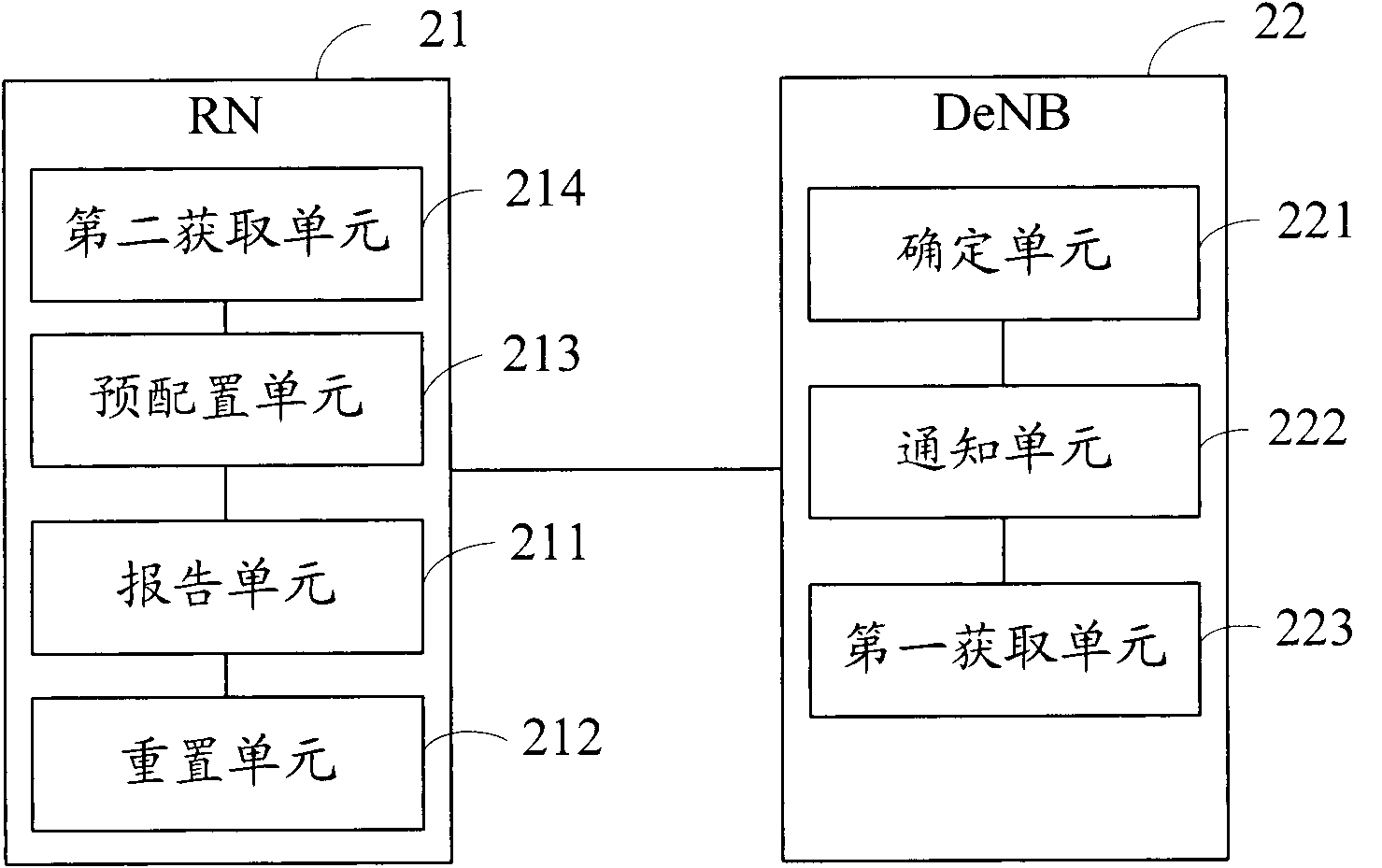
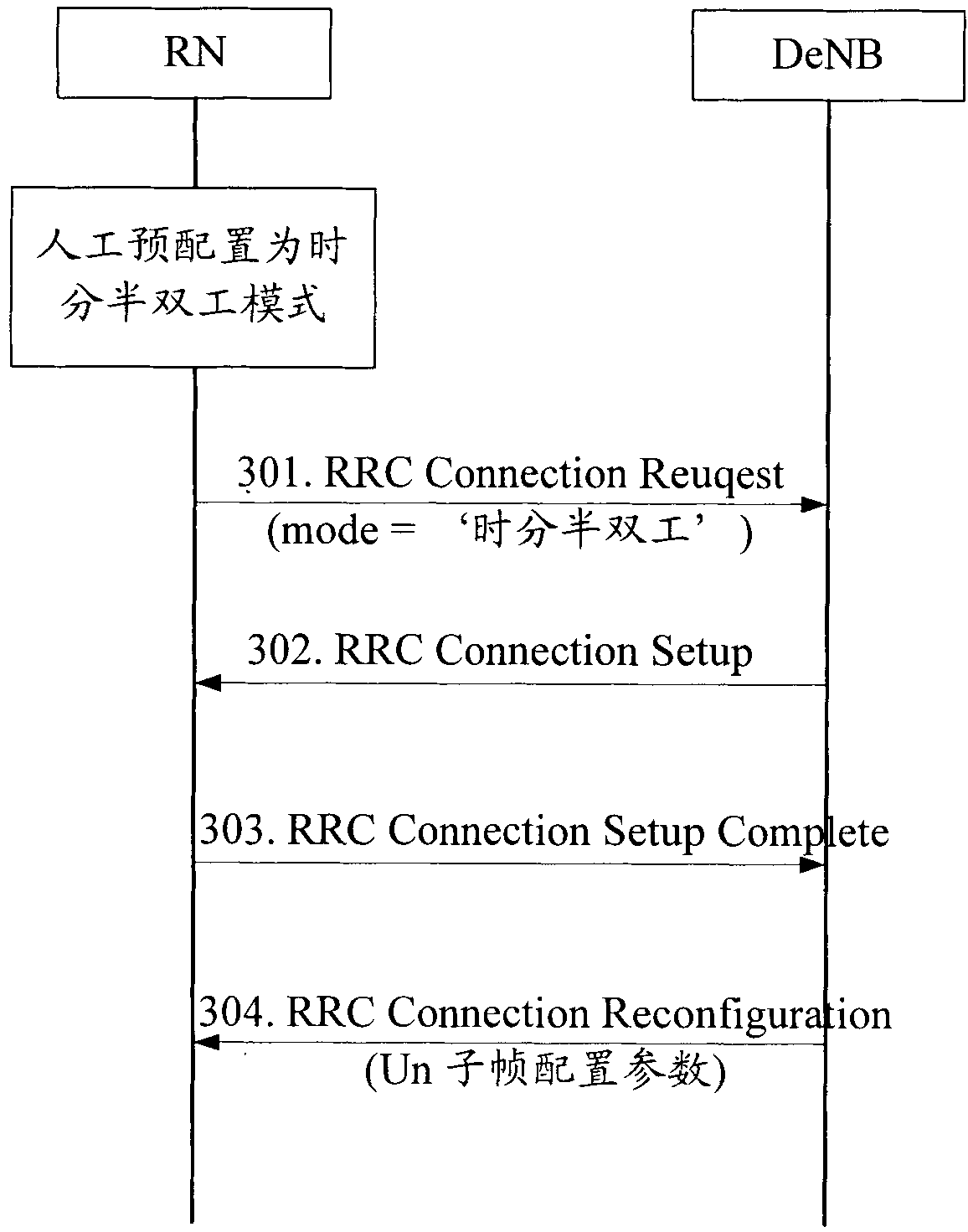
Method and system of negotiating and determining operating mode of RN (Role Network)
InactiveCN102404100AAvoid interactive negotiation processImprove negotiation efficiencyConnection managementRadio transmissionNegationComputer science
The invention discloses a method of negotiating and determining an operating mode of a RN (Role Network). The method mainly comprises the steps that the RN reports a preconfigured operating mode of the RN to a DeNB (donor eNB); and the DeNB determines the operating mode of the RN according to the operating mode reported by the RN and the information of equipment capacity of the DeNB and informs the RN of the determined operating mode. The invention also disclose a system of negotiating and determining the operating mode of the RN; the system not only can ensure the operating mode of the RN and the operating mode of the RN recorded on the DeNB to be consistent when the RN is connected into the DeNB but also can avoid an unnecessary interactive negation flow, thereby effectively improving the negotiation efficiency and saving resources; meanwhile, by adopting the system, the preconfigured operating mode inappropriate for the DeNB can be modified; and the system is simple, flexible and reliable.
Owner:ZTE CORP
Management method and system of electric power Internet-of-Things terminal layer equipment secret key and storage medium
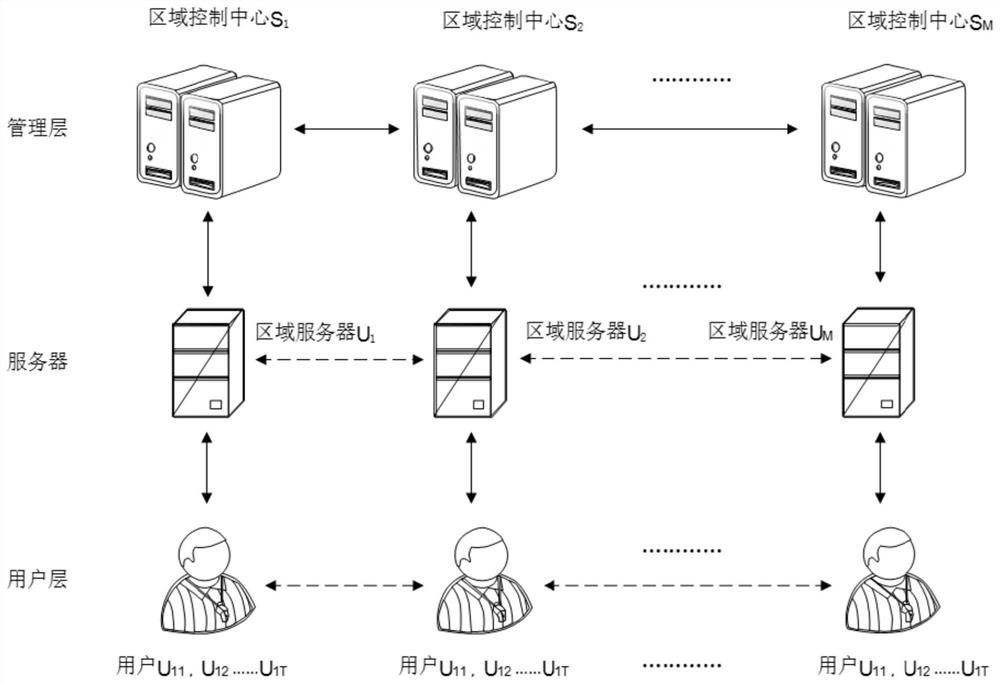
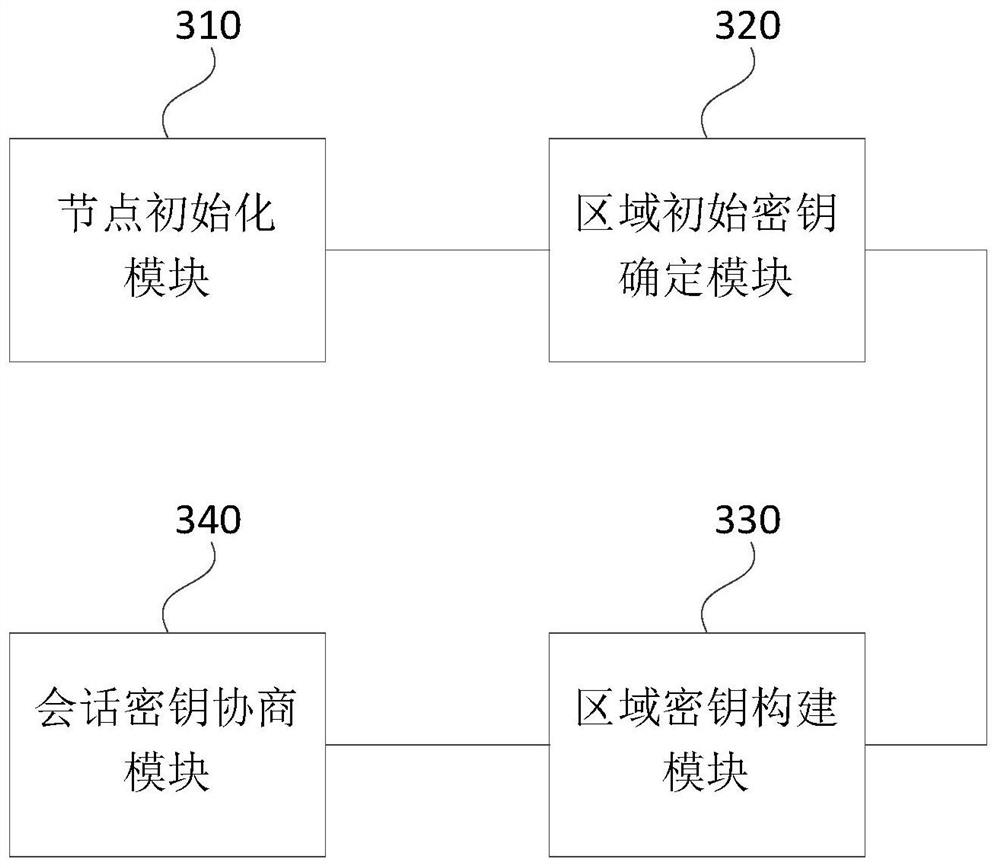
InactiveCN111698238AEfficient managementImprove securityKey distribution for secure communicationPublic key for secure communicationComputer networkEngineering
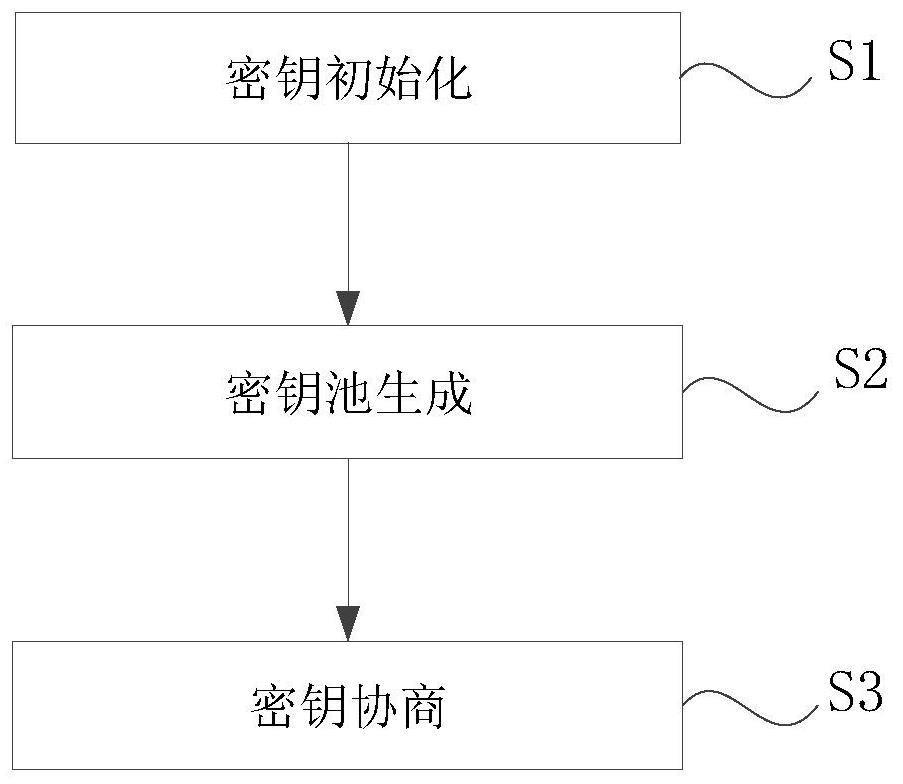
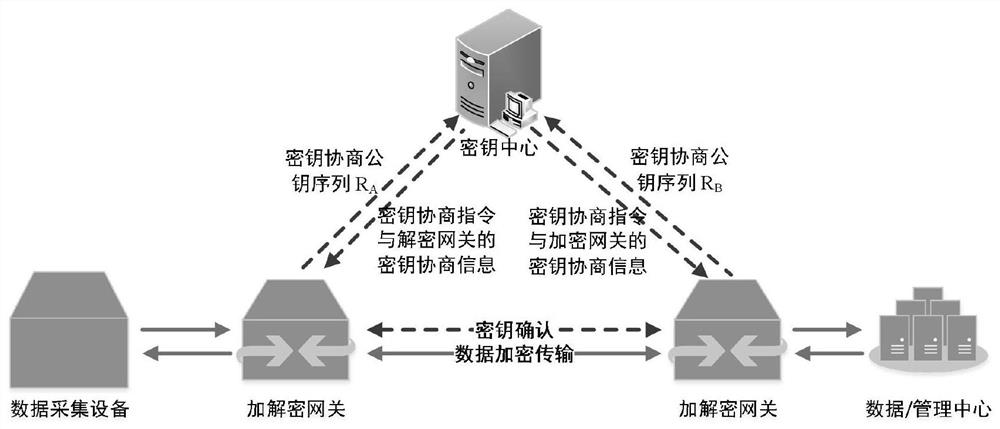
The invention discloses a management method and system for an electric power Internet-of-Things terminal layer equipment secret key and a storage medium. The method comprises the following steps: initializing a secret key; using the terminal layer equipment as a node for initialization, and completing regional key initialization; generating a key pool; randomly numbering all nodes in the region, and randomly sorting the numbers by adopting a Hamilton algorithm; according to the random sorting of the node numbers in the region, selecting the sub-keys of the corresponding nodes to construct a complete region key, and collecting all the region keys to obtain a key pool; key negotiation; before the two nodes carry out encrypted data communication, randomly selecting sub-keys of the corresponding nodes from the key pool, carrying out mutual verification on the sub-keys of the two communication parties, and after identity information in the sub-keys is verified to be correct, calculating a session key through key parameters; and performing session key negotiation based on the session key, if the negotiation succeeds, sending a communication identifier by the two parties, opening the session, and starting data communication encrypted by the session key.
Owner:CHINA ELECTRIC POWER RES INST +2
Key exchanging method for end-to-end VoIP encryption communication
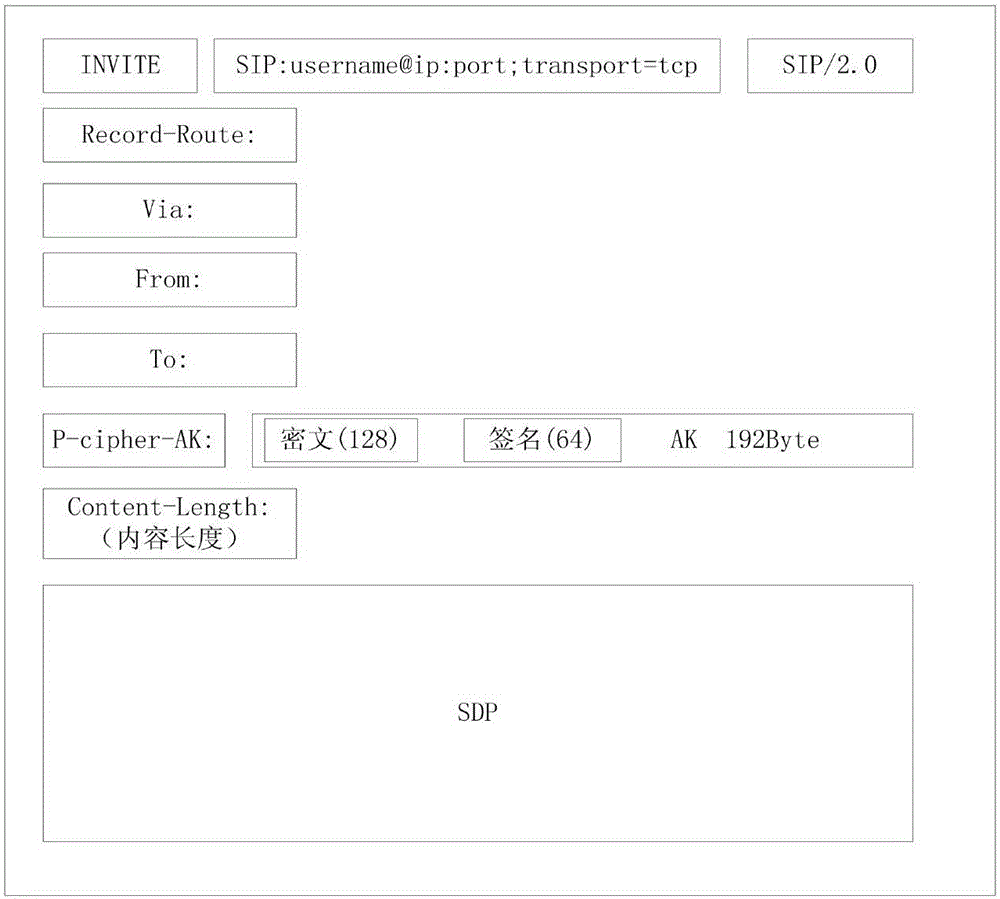
InactiveCN106850521AImprove negotiation efficiencyInterconnection arrangementsTransmissionProtocol for Carrying Authentication for Network AccessCiphertext
Owner:INST OF INFORMATION ENG CAS
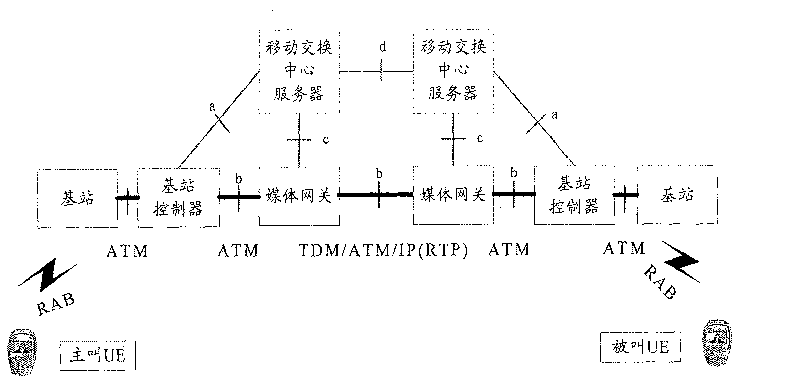
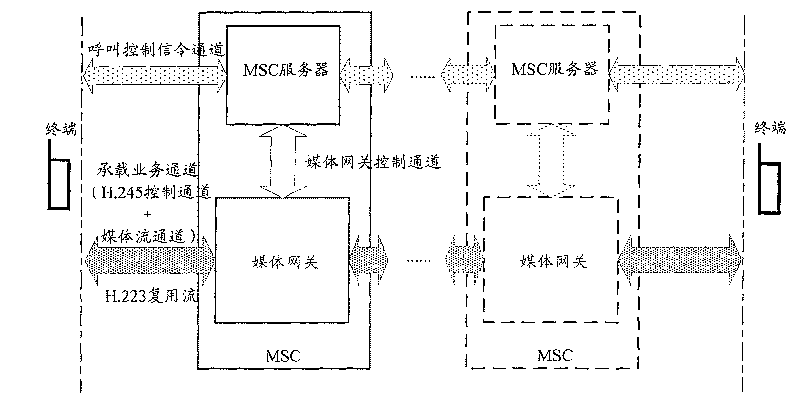
Method, system and apparatus for realizing multimedia calling service
InactiveCN101064680AControl managementSave resourcesNetwork traffic/resource managementConnection managementMedia controlsComputer science
The invention discloses a method, system and device which realize multimedia calling operation, it is used to resolve problem that current WCDMA circuit field structure and multimedia calling operation can not make network provide additional functions which are relative with medium flow. The method includes: A. the load operation channel built when the MSC SERVER calls and the every part participating in multimedia calling operation build medium control command channel; B. MSC SERVER participates in medium arranging via said medium control command channel to accomplish the building of medium flow logical channel to realize the multimedia calling operation. By application of the invention, the MSC SERVER can participate in medium arranging, so the additional functions which are relative with medium flow can be provided for user.
Owner:INVT SPE LLC
IPSEC negotiation method, apparatus, equipment and system
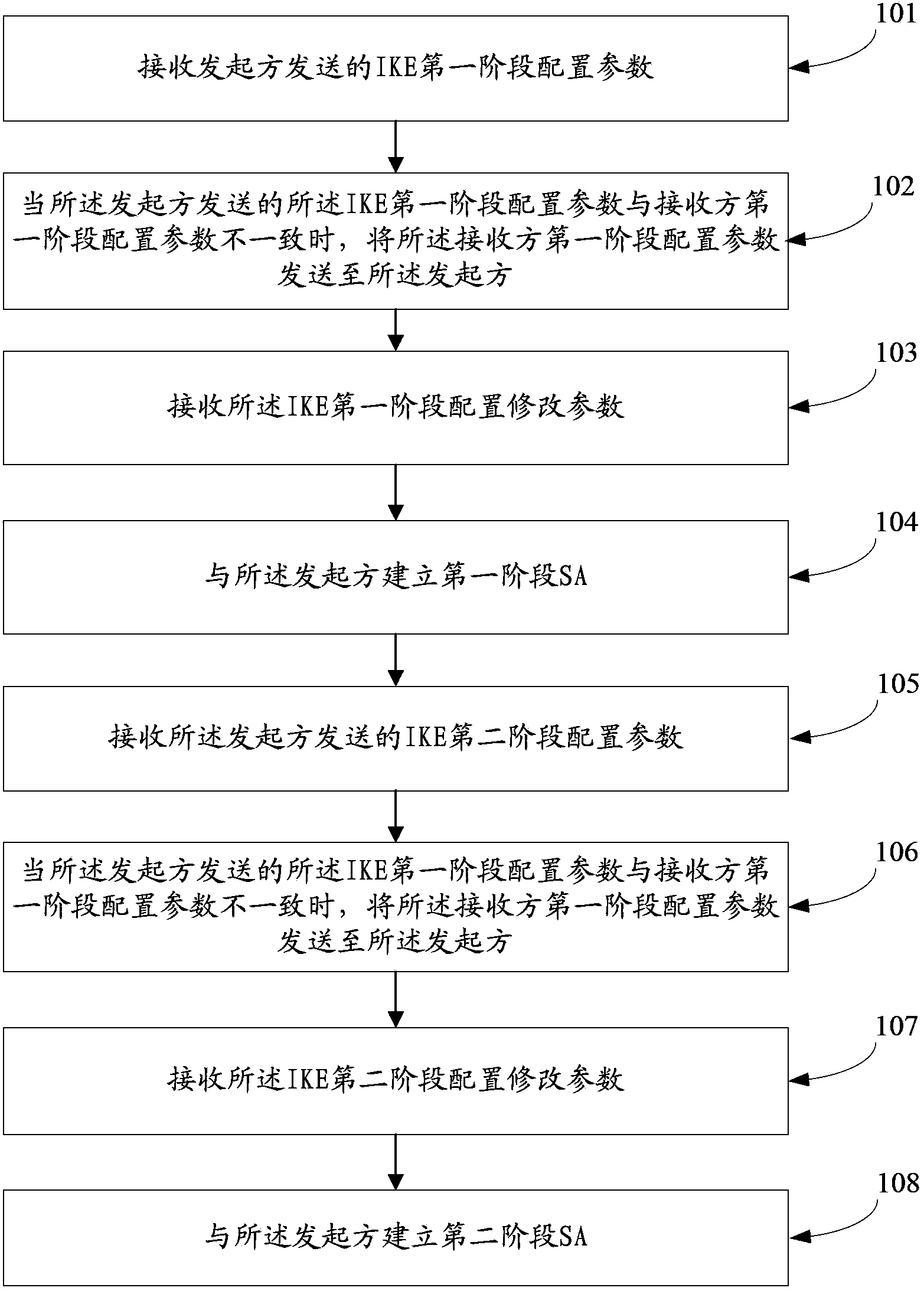
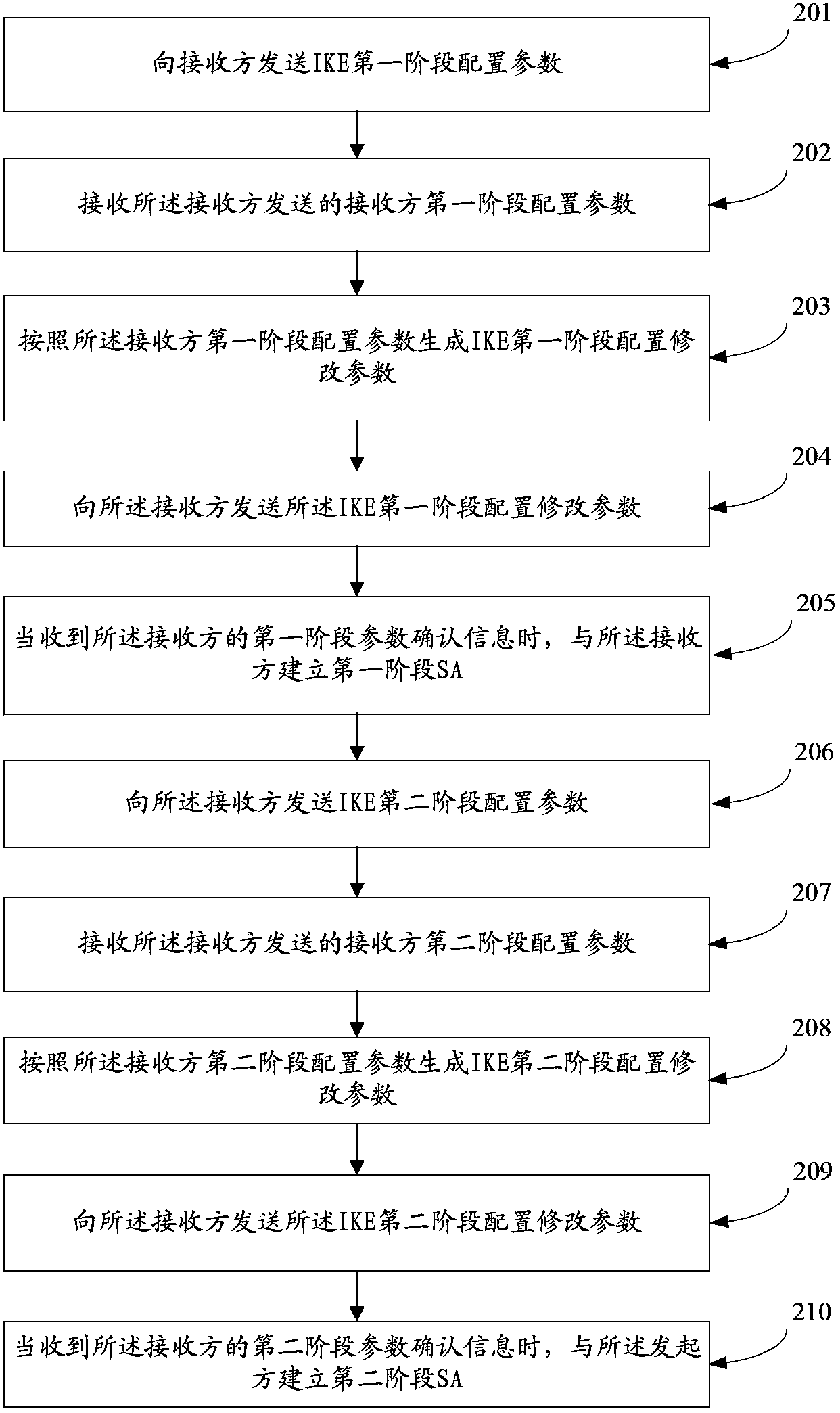
ActiveCN103392323AShorten the timeImprove negotiation efficiencyUser identity/authority verificationIPsecData transmission
The embodiment of the invention discloses an IPSEC negotiation method, which refers to communication field, and solves the problems of long IPSEC negotiation process and low negotiation efficiency. The IPSEC negotiation method comprises a first step of sending a receiver first stage configuration parameter to a starter by a receiver when an IKE first stage configuration parameter differs from the receiver first stage configuration parameter, and then receiving an IKE first stage configuration modify parameter to establish a first stage SA; and a second step of receiving an IKE second stage configuration parameter by a receiver, and sending a receiver second stage configuration parameter to the starter when the IKE second stage configuration parameter sent by the starter differs from the receiver second stage configuration parameter, and then receiving the IKE second stage configuration modify parameter and establishing a second stage SA. The invention is mainly applied in data transmission.
Owner:HUAWEI TECH CO LTD
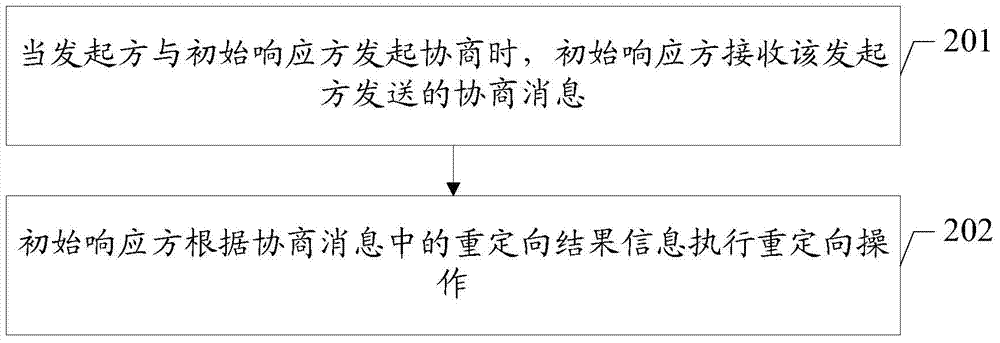
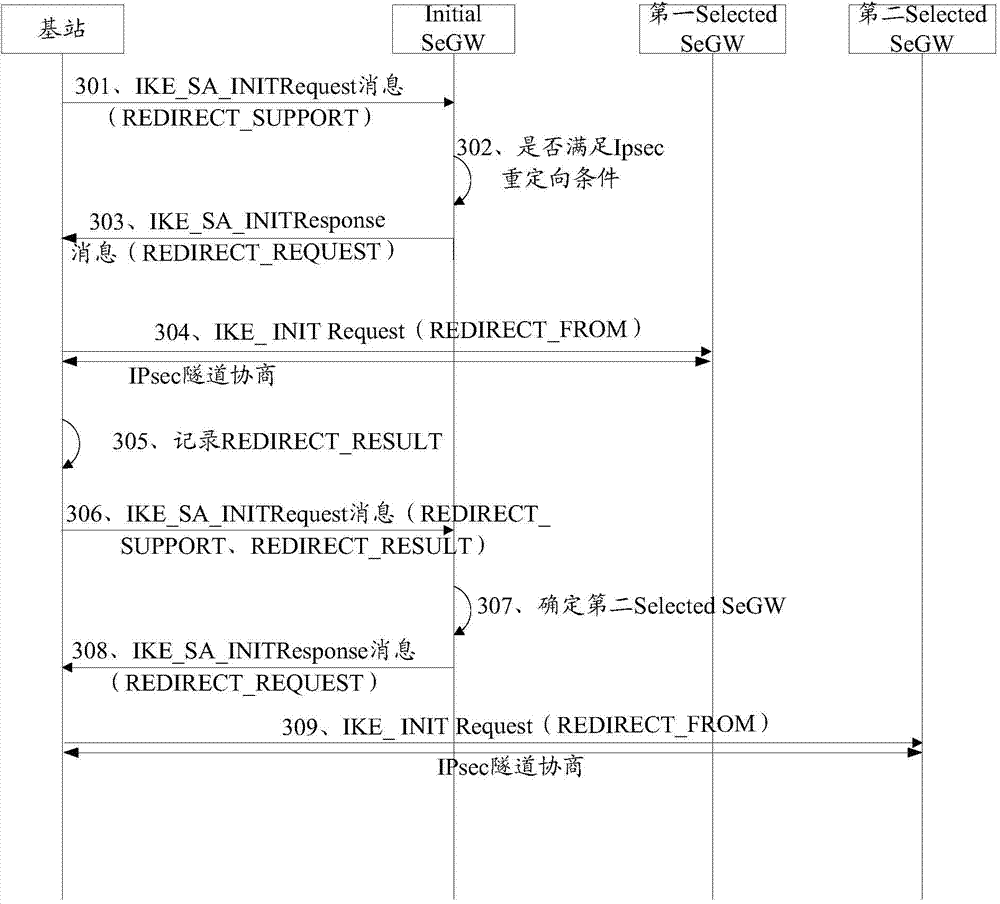
Redirection method and related equipment
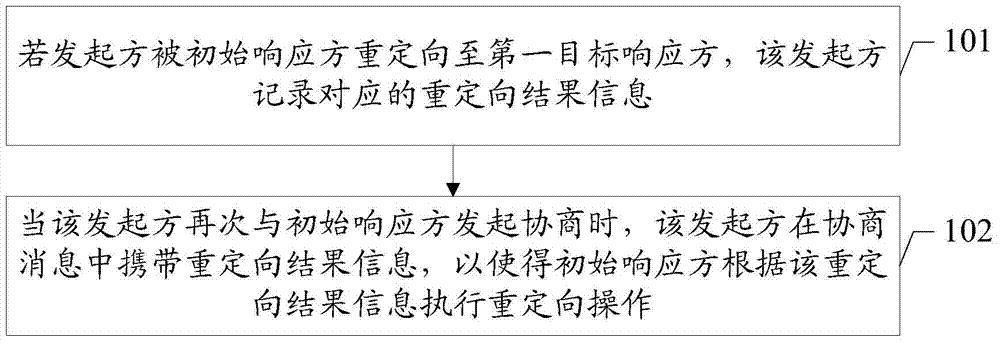
InactiveCN104754672AImprove negotiation efficiencyWireless communicationTransmissionComputer scienceHistorical record
The embodiment of the invention discloses a redirection method. The redirection method can guide redirection operation according to a redirection historical record in a negotiation process of an initiator so as to improve the negotiation efficiency. The method disclosed by the embodiment of the invention comprises the following steps: in the negotiation process of the initiator and an initial responding party, if the initiator is redirected to a first target responding party by the initial responding party, the initiator records corresponding redirection result information; when the initiator is negotiated with the initial responding party again, the initiator carries the redirection result information in a negotiation message so that the initial responding party can carry out redirection operation according to the redirection result information.
Owner:SHANGHAI HUAWEI TECH CO LTD
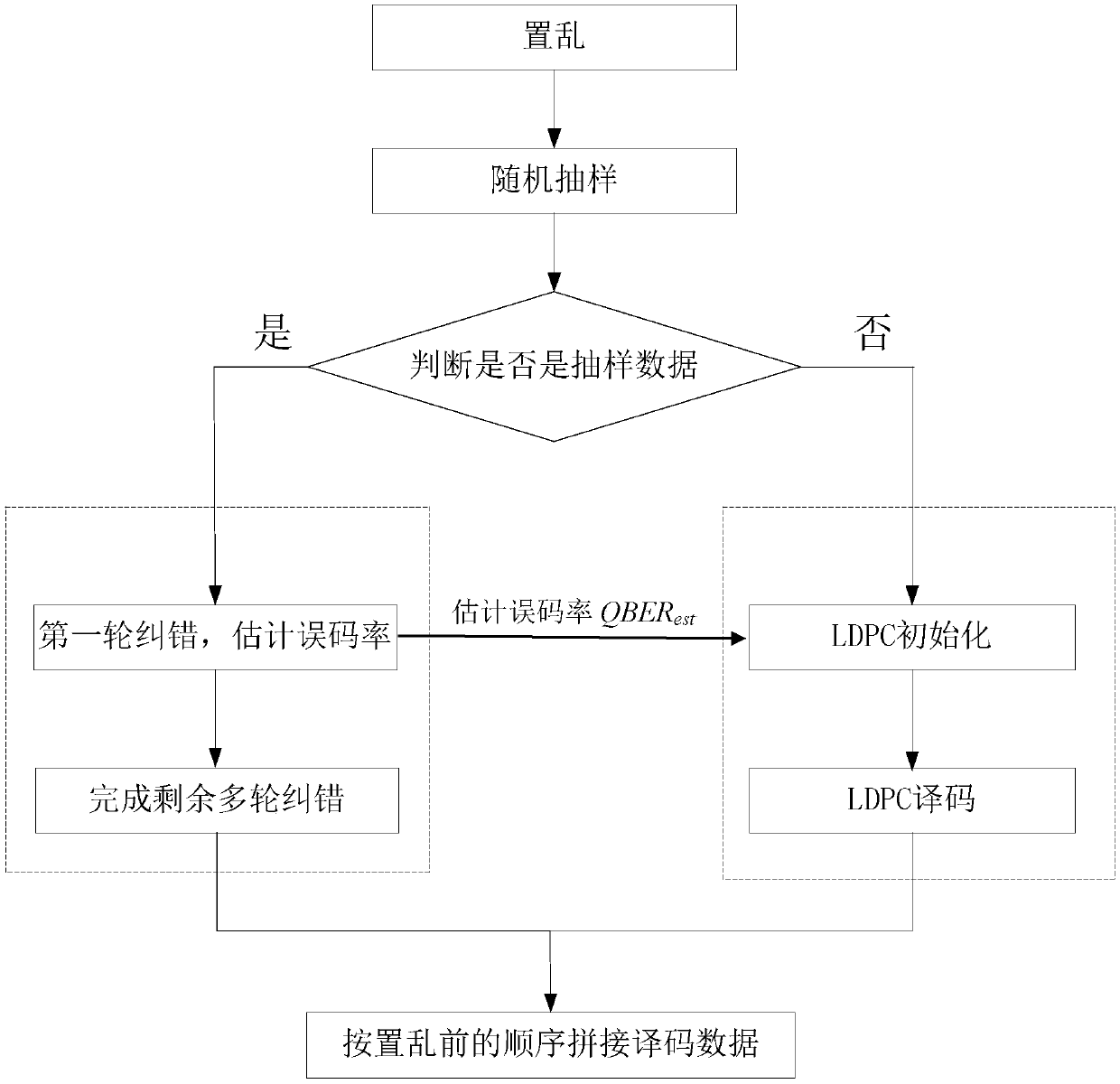
Error code negotiation method and device for discrete quantum key distribution system
ActiveCN109639422AReduce exposureImprove negotiation efficiencyKey distribution for secure communicationForward error control useForward error correctionQuantum key distribution
The invention provides an error code negotiation method and device for a discrete quantum key distribution system for simultaneously improving the processing rate and the negotiation efficiency, and belongs to the technical field of quantum communication. The method comprises the following steps: performing scrambling processing on a data block D; performing random sampling on scrambled data to obtain sampled data Ds; correcting and decoding the sampled data Ds by using an interactive negotiation algorithm, obtaining an estimated error rate by using the relationship between the first round ofparity bits and the error rate, and executing an initialization work via a forward error correction negotiation algorithm when the interactive negotiation algorithm waits for the interaction information in the first round; performing, by the forward error correction negotiation algorithm, adjustment based on the estimated error rate, completing, by the interactive negotiation algorithm, the remaining multi-round error correction decoding work of the sampled data, and decoding, by the forward error correction negotiation algorithm, the remaining data after sampling in each round of waiting forthe interaction information; and splicing the decoding results of the interactive negotiation algorithm and the forward error correction negotiation algorithm according to the orders before the scrambling.
Owner:HARBIN INST OF TECH +1
A Long-Distance Continuous Variable Quantum Key Distribution Method Based on Gaussian Modulated Coherent States
ActiveCN105024809BSafe communication distance extensionReduce noiseKey distribution for secure communicationSecure communicationCoherent states
Owner:上海循态量子科技有限公司
Industrial internet data encryption transmission method based on stream cipher
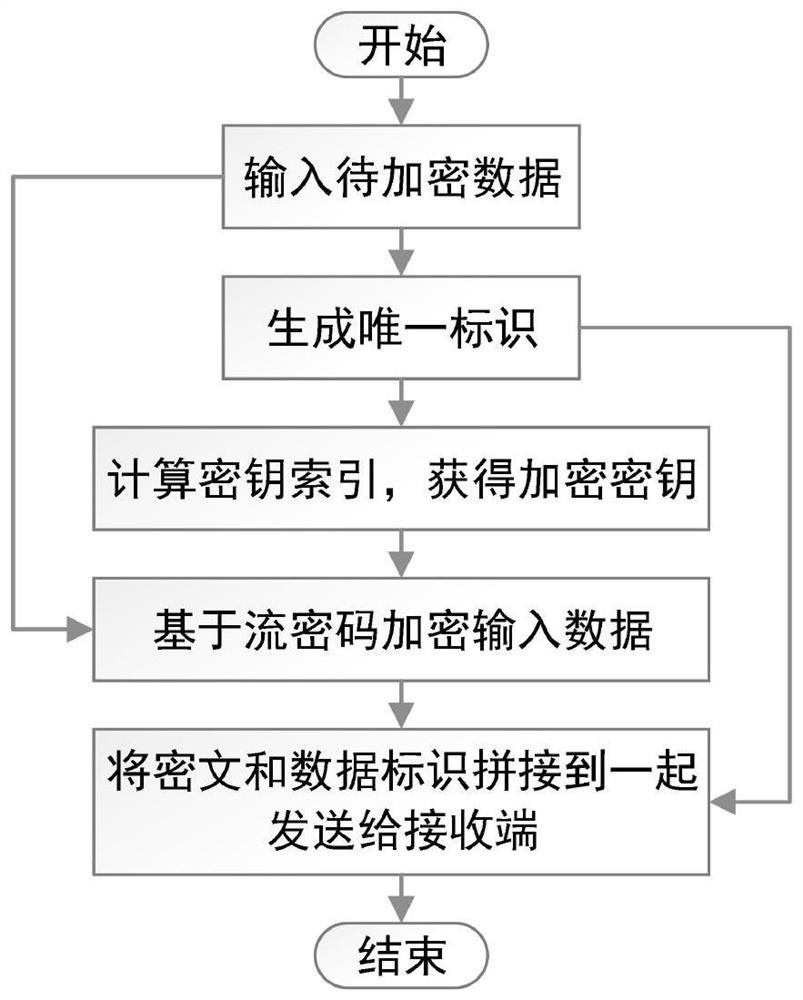
PendingCN114363086ACorrectly decryptedImprove efficiencyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCiphertextThe Internet
The invention discloses an industrial internet data encryption transmission method based on a stream cipher, which is used for realizing data encryption transmission between a sender and a receiver in an industrial internet. The method comprises the following steps: a sender sends data to be sent to an encryption gateway; the encryption gateway generates a unique identifier, calculates a stream key index used for encrypting current data based on the identifier, extracts a stream key from a stream key sequence according to the stream key index, encrypts the current data by using the stream key, and then sends the identifier and ciphertext data to a decryption gateway of a receiver together; and the decryption gateway firstly extracts data identification information, then calculates a stream key index for decrypting the current ciphertext based on the identification, extracts a stream key from a stream key sequence according to the stream key index, decrypts the current ciphertext by using the stream key, and finally sends the obtained plaintext data to a receiver. According to the data encryption transmission method, correct transmission of the data can be ensured, the calculation amount of encryption and decryption is reduced, and the data transmission efficiency is improved.
Owner:北京北卡星科技有限公司
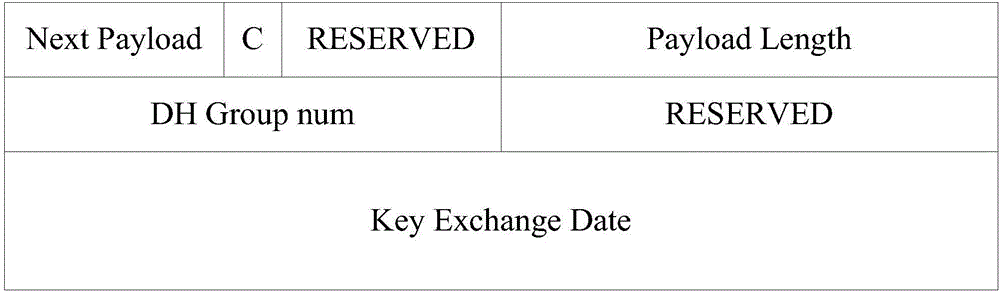
Method and device for DH (Diffie-Hellman) algorithm negotiation based on IKEv2
ActiveCN106789023AReduce the number of interactionsImprove negotiation efficiencyKey distribution for secure communicationComputer hardwareKey generation
The invention provides a method and a device for DH (Diffie-Hellman) algorithm negotiation based on IKEv2. The method comprises the following steps of enabling initiator equipment to judge whether the equipment supports multiple algorithms in the DH algorithm or not; when the equipment supports multiple algorithms in the DH algorithm, sending an IKEv2 negotiation message to responder equipment, wherein the IKEv2 negotiation message carries identifications of multiple locally-supported DH algorithms, and initiator key generation parameters correspond to the multiple DH algorithms; receiving a response message which is returned by the responder equipment and corresponds to the IKEv2 negotiation message; obtaining the identification of the target DH algorithm carried in the response message, and the responder key generation parameters, so as to complete the DH algorithm negotiation. The method solves the problem of decreasing of negotiation efficiency caused by additional one-time message interaction between the initiator equipment and the responder equipment in case of negotiation failure in the prior art.
Owner:HANGZHOU DPTECH TECH
Terminal comprising a transceiver
InactiveCN1866965AMultiple possibilitiesImprove negotiation efficiencyNetwork traffic/resource managementVideo gamesHuman–machine interfaceTransceiver
Terminals comprising transceivers for exchanging messages with further transceivers of further terminals are provided with negotiation modules for exchanging negotiation messages with further negotiation modules of the further terminals, to increase the flexibility. The negotiation messages define proposal actions for activations and / or deactivations of terminal capabilities and proposal reactions to the proposal actions. As a result, it is no longer necessary that each terminal has the same entire application and that each terminal is treated the same way. Individual possibilities of different terminals are used and are allowed. Capability modules exchange capability messages with further capability modules of the further terminals. The capability messages define terminal capabilities such as human machine interfaces. Application modules for exchanging application messages with further application modules of the further terminals define at least a part of an application. Application interface modules for interfacing the application modules are activatable and / or deactivatable in response to proposal reactions.
Owner:ALCATEL LUCENT SAS
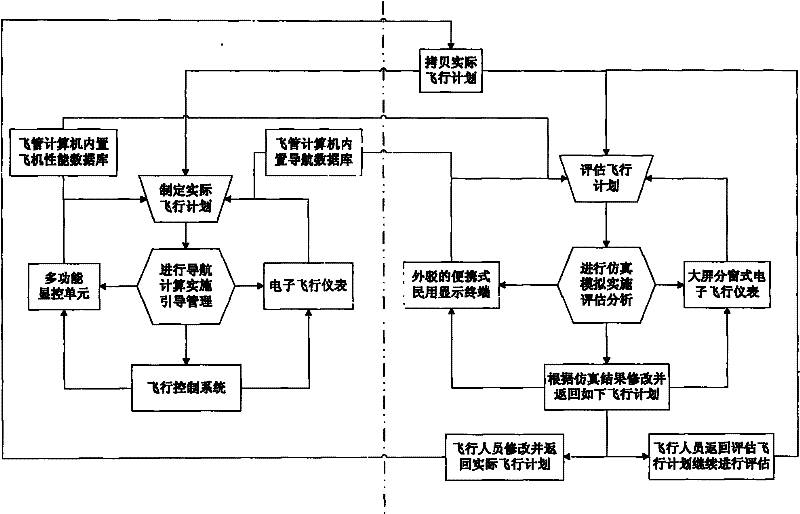
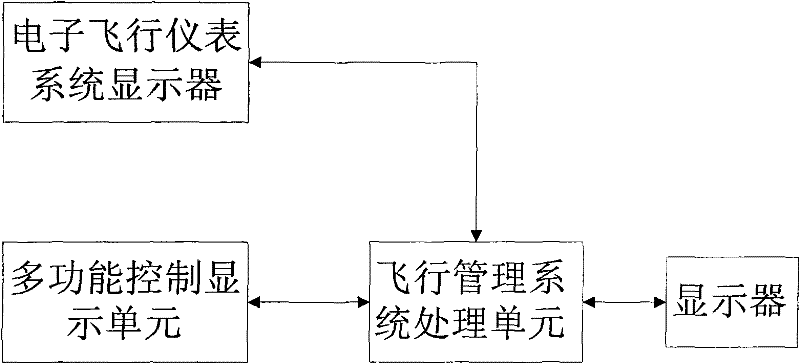
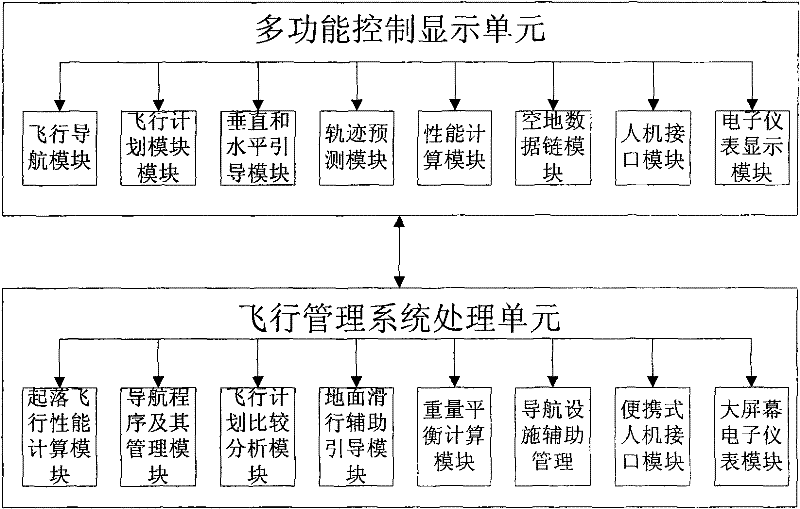
Flight management system and method thereof based on multi-task parallel processing
InactiveCN101881969BMeet the needs of sustainable developmentImprove efficiencyVehicle position/course/altitude controlPosition/direction controlDisplay deviceParallel processing
The invention relates to flight management system and method thereof based on multi-task parallel processing. The system comprises an electronic flight instrument system display unit, a multifunctional control display unit, a flight management system processing unit and a display unit with a control button, wherein the multifunctional control display unit is used for maintaining existing functions of formulating and executing a flight plan; and the flight management system processing unit is connected with the multifunction control display unit and used for copying the formulated flight plan and carrying out assessment and dynamic modification on the flight plan. The invention converts the traditional signal processing scheme into a parallel processing scheme: one processing scheme is used for maintaining the traditional functions of formulating and executing the flight plan, and the other processing scheme is used for providing the dynamic modification and assessment functions; and flight personnel can effectively prepare and scientifically assess the change basis by dynamically modifying an assessment scheme, therefore, the invention can satisfy the changeful practical needs andimprove the flight safety and the flight operation effectiveness.
Owner:CHINESE AERONAUTICAL RADIO ELECTRONICS RES INST
Method, system and apparatus for realizing multimedia calling service
InactiveCN101064680BControl managementSave resourcesNetwork traffic/resource managementConnection managementMedia controlsTelecommunications
The invention discloses a method, system and device which realize multimedia calling operation, it is used to resolve problem that current WCDMA circuit field structure and multimedia calling operation can not make network provide additional functions which are relative with medium flow. The method includes: A. the load operation channel built when the MSC SERVER calls and the every part participating in multimedia calling operation build medium control command channel; B. MSC SERVER participates in medium arranging via said medium control command channel to accomplish the building of medium flow logical channel to realize the multimedia calling operation. By application of the invention, the MSC SERVER can participate in medium arranging, so the additional functions which are relative with medium flow can be provided for user.
Owner:INVT SPE LLC
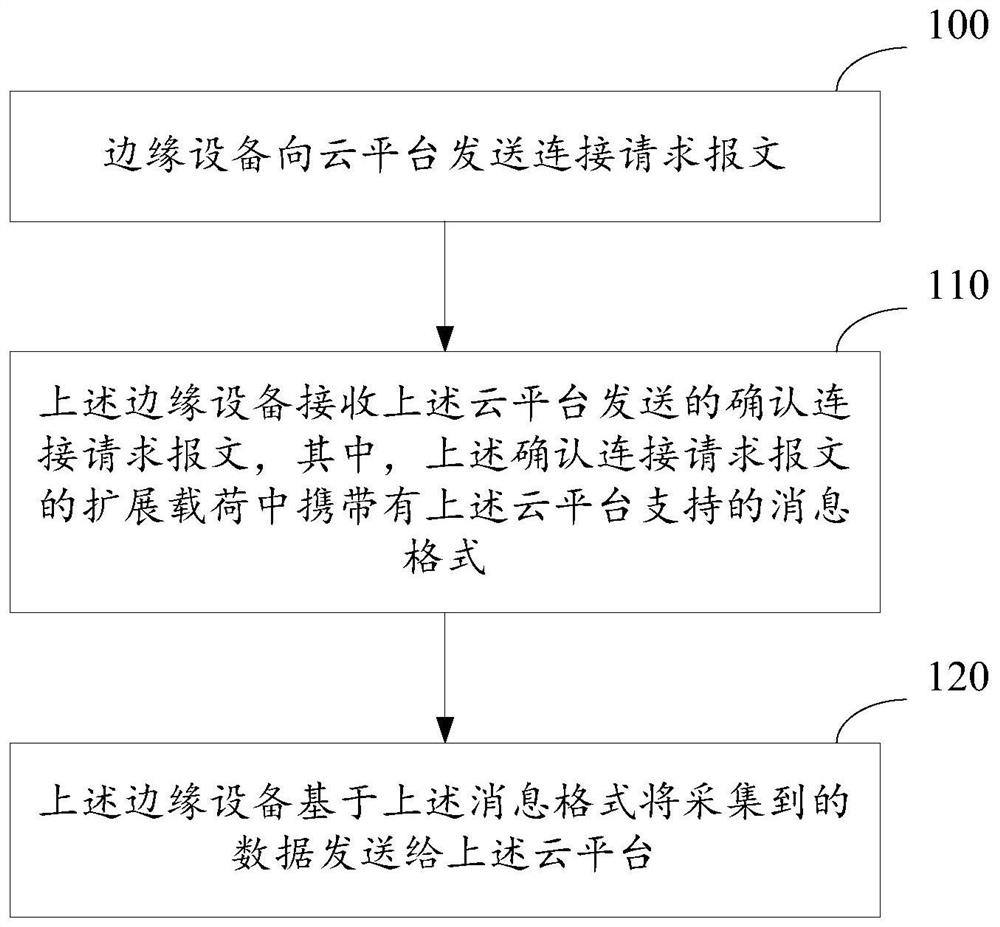
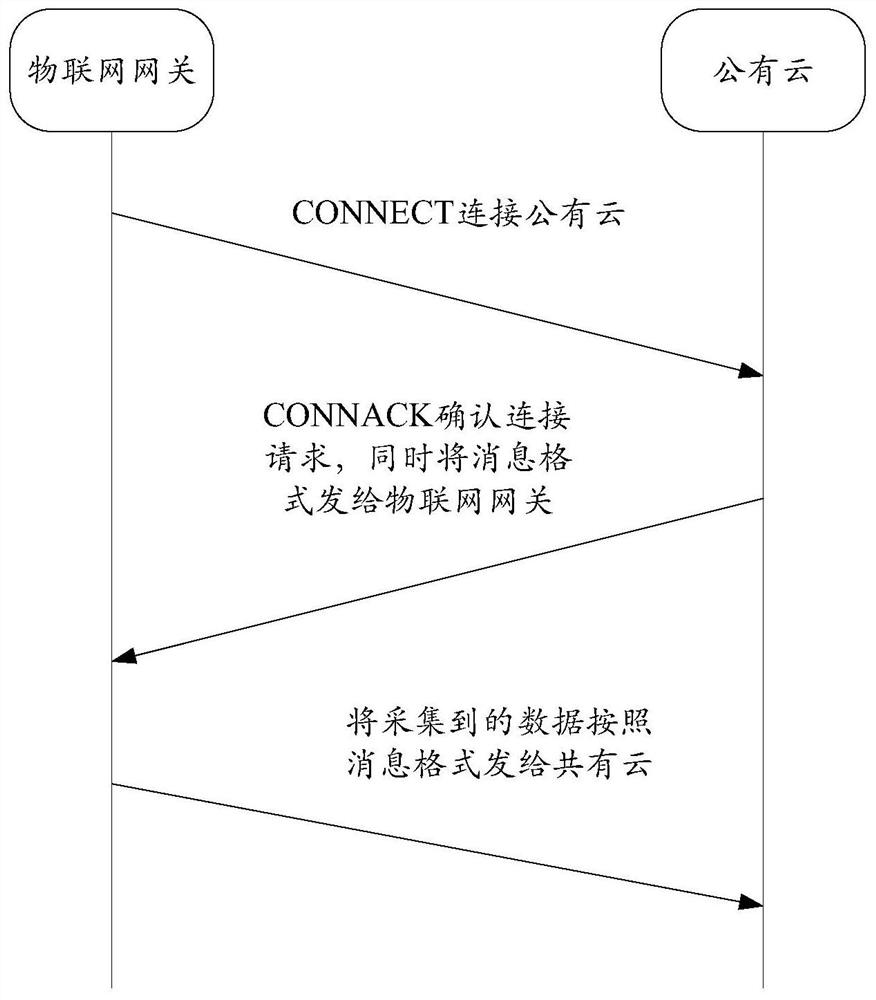
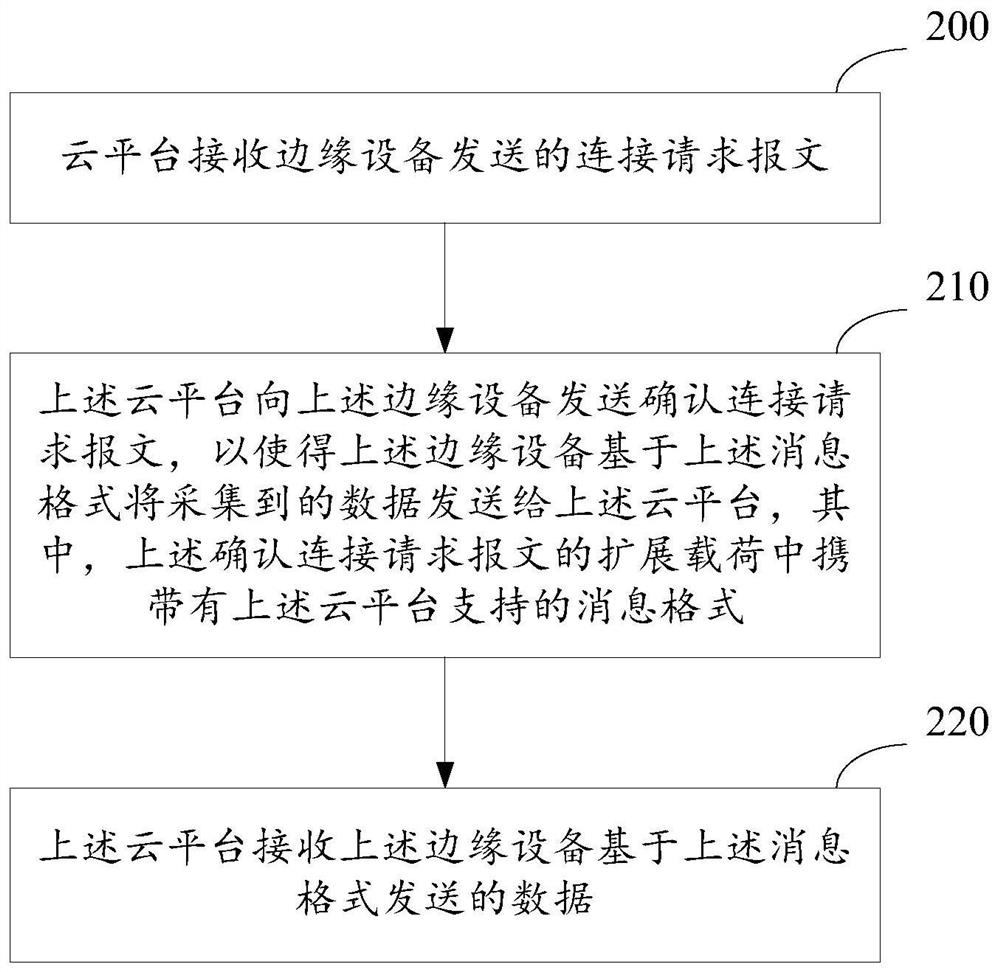
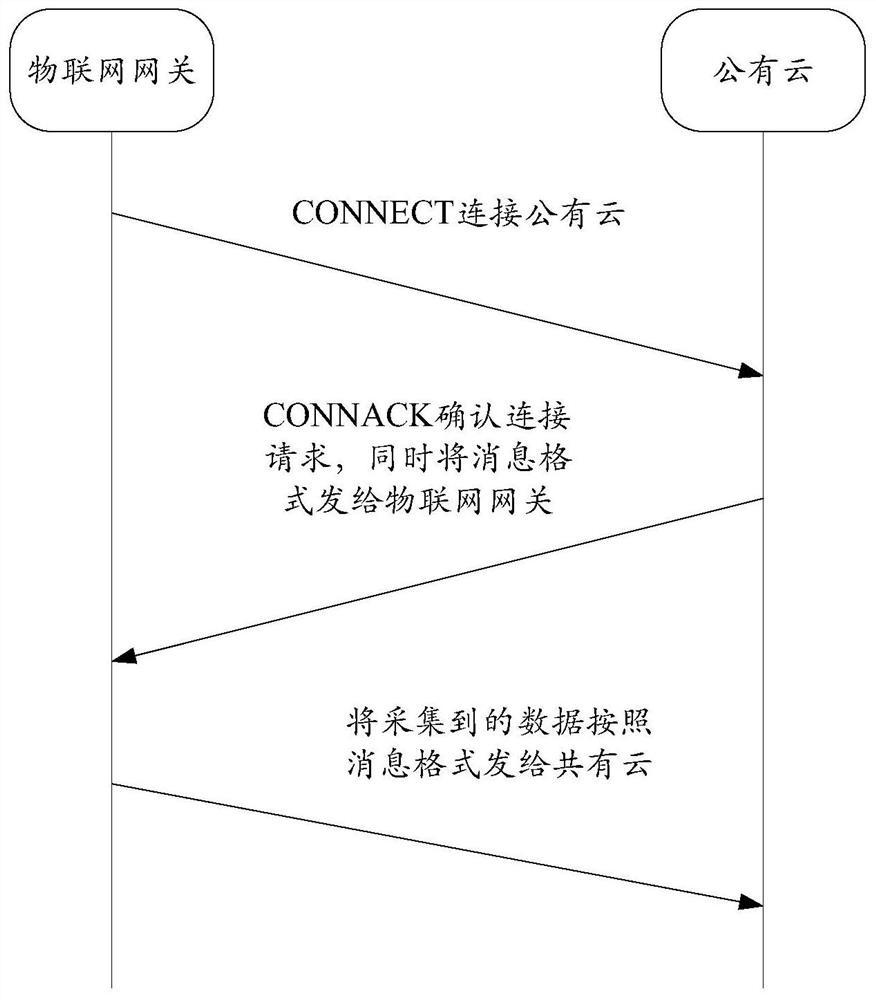
A message format negotiation method and device
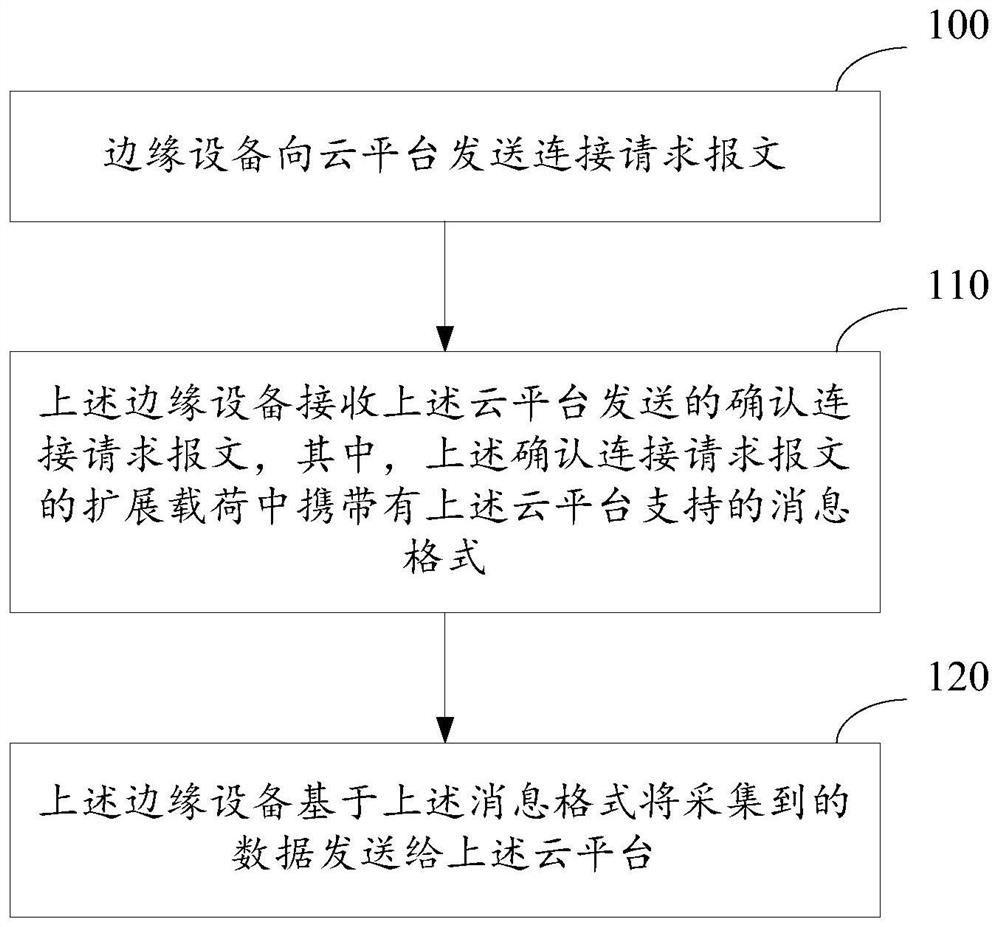
ActiveCN112003686BSimplify the negotiation processImprove negotiation efficiencySignal allocationTransmission technologyEngineering
The present application relates to the technical field of data transmission, in particular to a message format negotiation method and device. The method is applied to an edge device, and the method includes: the edge device sends a connection request message to a cloud platform; the edge device receives a confirmation connection request message sent by the cloud platform, wherein the confirmation connection request message The message format supported by the cloud platform is carried in the extended payload; the edge device sends the collected data to the cloud platform based on the message format. Using the message format negotiation method provided by this application, the edge device can directly complete the negotiation of the message format during the process of establishing a network connection with the cloud platform, without modifying the program code on the edge device for adaptation.
Owner:NEW H3C BIG DATA TECH CO LTD
Message processing method and device
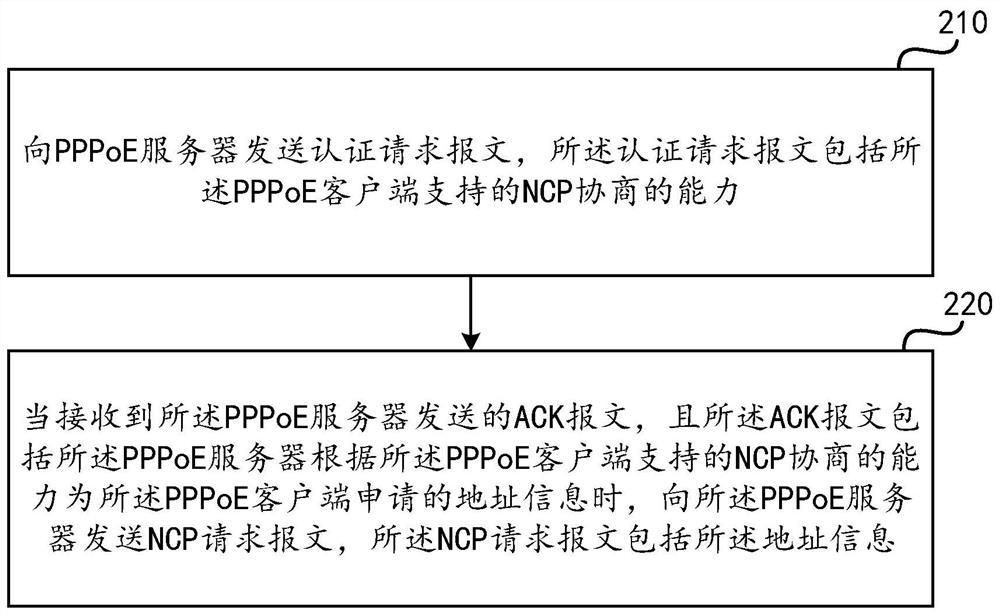
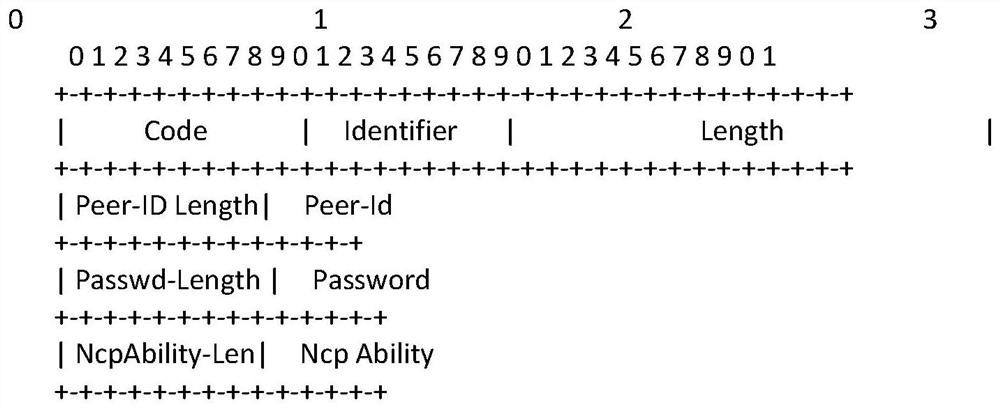
ActiveCN113206827ASolve the problem of online efficiencyShort processTransmissionMessage processingDistributed computing
The invention provides a message processing method and device. The method is applied to a PPPoE client, and the method comprises the following steps: sending an authentication request message to a PPPoE server, wherein the authentication request message comprises an NCP negotiation capability supported by the PPPoE client; when an ACK message sent by the PPPoE server is received and the ACK message comprises address information which is applied by the PPPoE server for the PPPoE client according to the NCP negotiation capability supported by the PPPoE client, sending an NCP request message to the PPPoE server, wherein the NCP request message comprises the address information.
Owner:北京华三通信技术有限公司
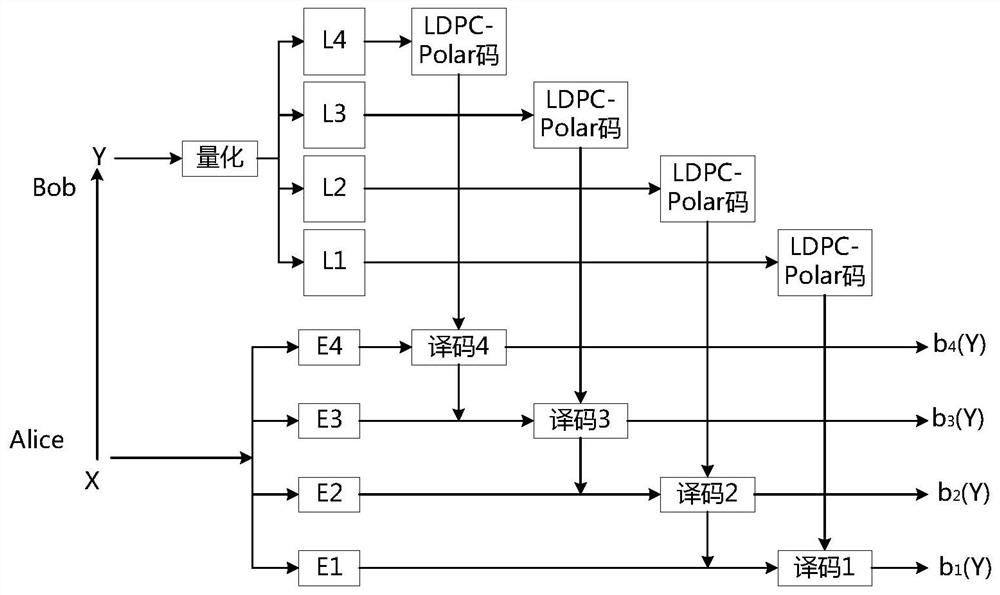
Quantum key distribution data negotiation method and system based on LDPC-Polar joint coding
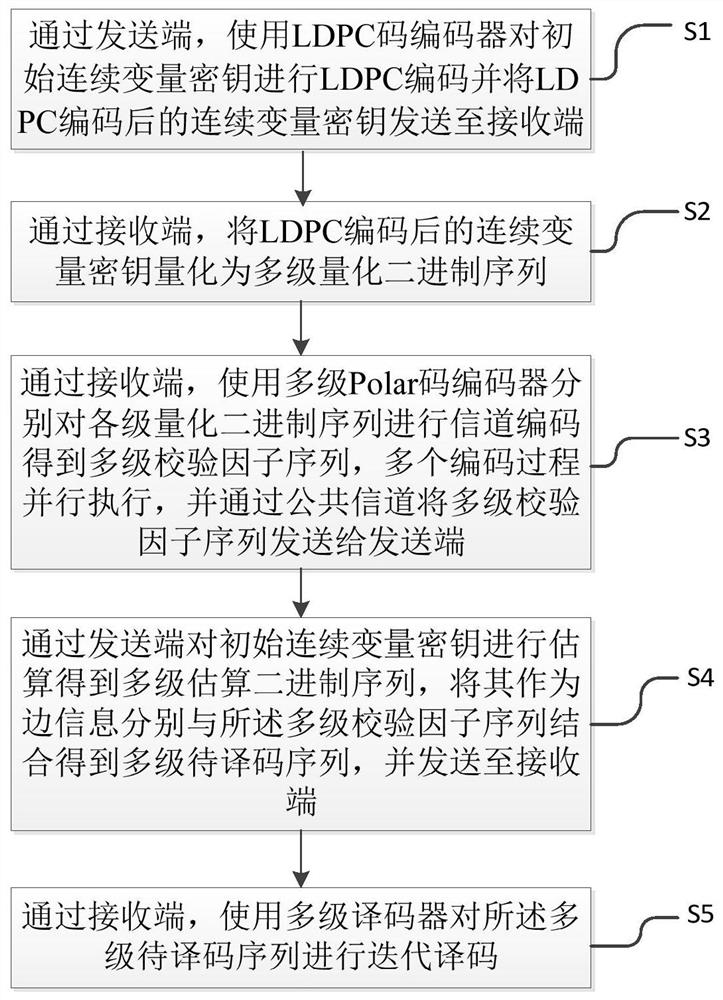
PendingCN112332985AImprove error correction success rate and negotiation efficiencyEnsure data negotiation efficiencyKey distribution for secure communicationForward error control useKey distributionQuantum key distribution
The invention discloses a quantum key distribution data negotiation method and system based on LDPC-Polar joint coding. The method and the system are based on a traditional multi-level coding / multi-level decoding model structure, LDPC-Polar joint coding is used as channel coding in multi-level coding, and multi-level coding and multi-level decoding of LDPC-Polar joint coding are carried out. According to the invention, the secret key error rate can be better reduced, the long-distance quantum secret key distribution negotiation efficiency is obviously improved, and the quantum secret key codeforming rate is better improved.
Owner:STATE GRID FUJIAN ELECTRIC POWER CO LTD +4
Channel resource scheduling strategy based on event response
ActiveCN107332650ASimplify the distribution processImprove negotiation efficiencyTransmission path divisionWireless communicationResource utilizationFrequency-division multiplexing
The invention discloses a channel resource scheduling strategy based on event response, which uses a compound module of which multiple radio frequency units cooperatively work as a platform, is on the basis of time division multiplexing and frequency division multiplexing technologies, distributes channel resources in a centralized mode and flexibly uses and control channels. According to the channel resource scheduling strategy disclosed by the invention, the channel distributing process is simplified, channel negotiation efficiency is improved, the channel resources are flexibly scheduled, the broadcast problem in a multi-channel network is also solved when a channel resource utilization rate is sufficiently improved, simultaneous multi-channel parallel data transmission of nodes is implemented, and communication efficiency is greatly improved; and the channel resource scheduling strategy disclosed by the invention is low in complexity and easy to implement.
Owner:YANSHAN UNIV
A key online negotiation method and system suitable for the communication environment of the Internet of Things
ActiveCN113259096BStrong computing powerReduce the number of communicationsKey distribution for secure communicationSecure communicationInformation transmission
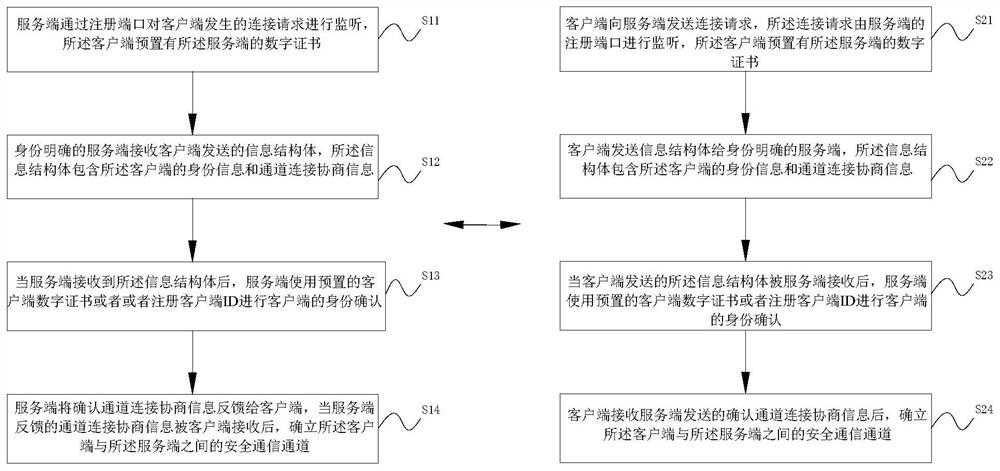
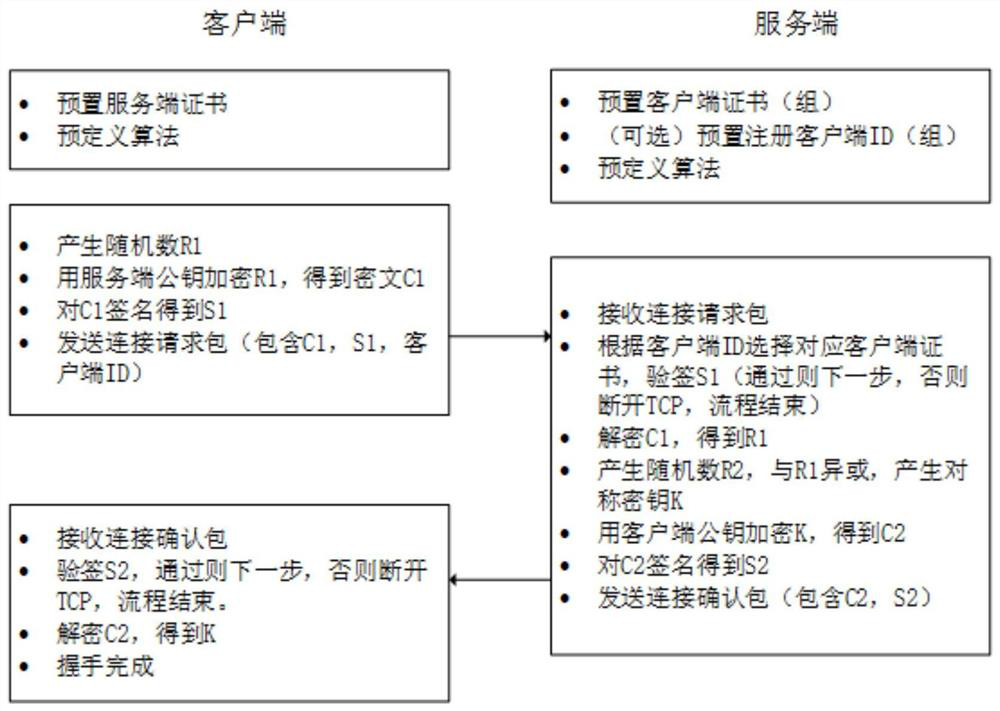
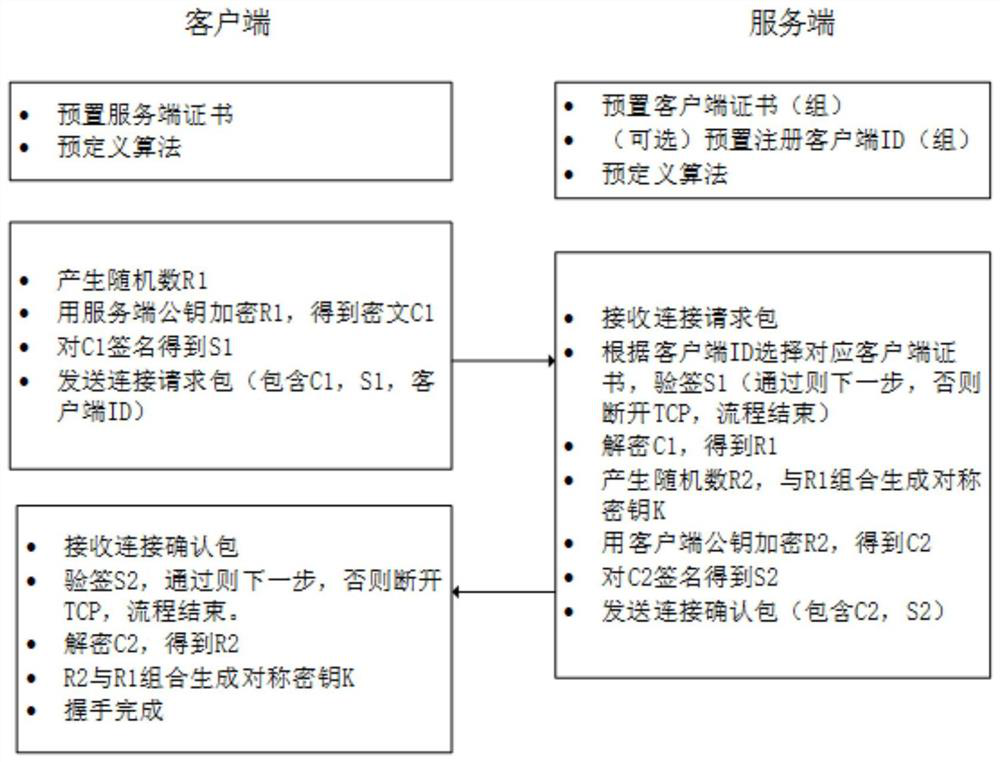
An online key negotiation method and system suitable for the communication environment of the Internet of Things. The server monitors the connection request of the client through the registration port, and the client is preset with the digital certificate of the server; the server with a clear identity receives the client The information structure sent, the information structure contains the identity information of the client and the channel connection negotiation information; when the server receives the information structure, the server uses the preset client digital certificate or registered client ID to confirm the identity of the client ; The server feeds back the confirmation channel connection negotiation information to the client, and when the channel connection negotiation information fed back by the server is received by the client, a secure communication channel between the client and the server is established. The invention cancels the transmission of extended information; directly specifies the algorithm, no algorithm negotiation is performed; the content of the certificate is no longer transmitted, the number of communications in the handshake stage of the TLS protocol is reduced, and the negotiation efficiency of the encryption key in the communication of the Internet of Things is improved.
Owner:江南信安(北京)科技有限公司
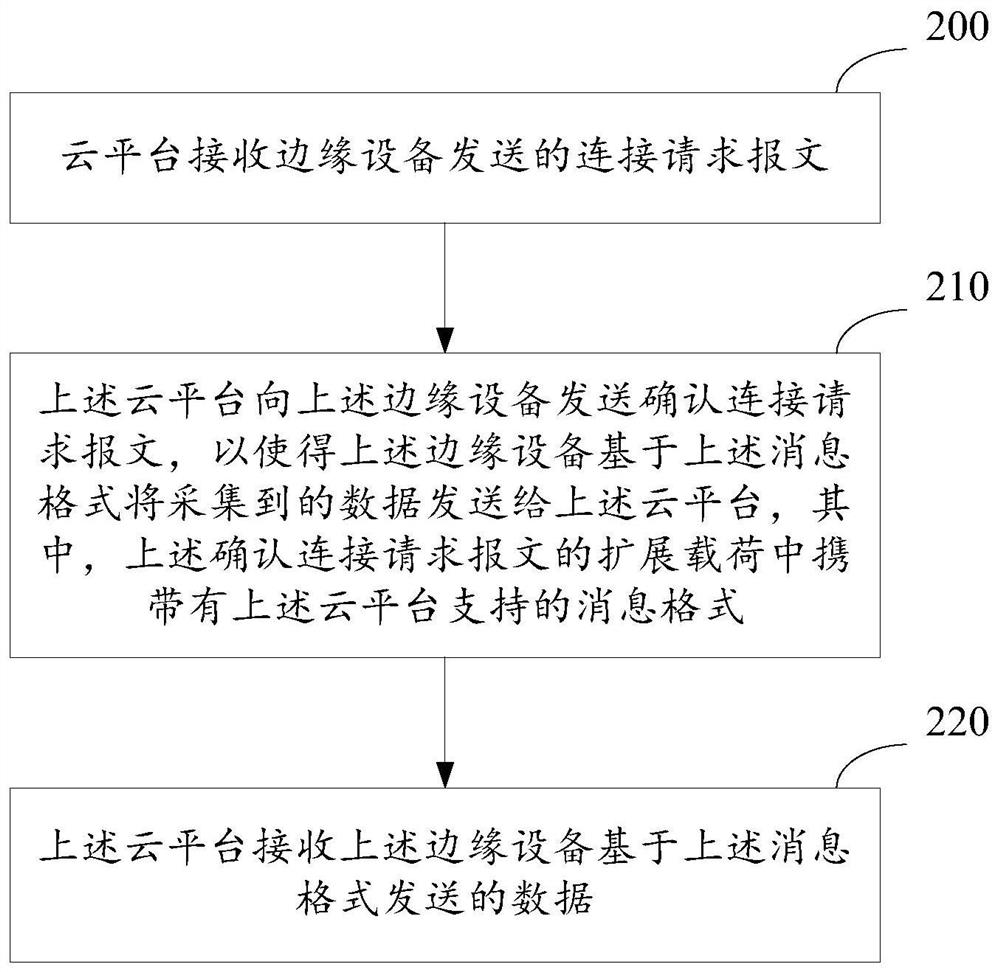
Message format negotiation method and device
ActiveCN112003686ASimplify the negotiation processImprove negotiation efficiencySignal allocationData transmissionReal-time computing
The invention relates to the technical field of data transmission, and in particular relates to a message format negotiation method and device. The method is applied to an edge device. The method comprises the steps that the edge device sends a connection request message to a cloud platform; the edge device receives a connection confirmation request message sent by the cloud platform, and an extended load of the connection confirmation request message carries a message format supported by the cloud platform; and the edge device sends the collected data to the cloud platform based on the message format. By adoption of the message format negotiation method provided by the invention, the edge device directly completes the negotiation of the message format in the process of establishing the network connection with the cloud platform, and adaptation does not need to be performed on the edge device in a mode of modifying a program code.
Owner:NEW H3C BIG DATA TECH CO LTD
Resource Aggregation Method Based on Multi-agent
ActiveCN105069010BEasy maintenanceIncrease flexibilityWeb data indexingSpecial data processing applicationsTask demandContract Net Protocol
The invention discloses a resource polymerization method based on Agent; in computer and network technology wide application, resources scattered in a complex heterogeneous network become more and more, and the method can effectively gather the resources scattering in the distributed environment; the method comprises the following steps: configuring the resource polymerization method based on Agent in a distributed system; a task agent resolves and describes according to a user inputted task demand; a decision agent distributes the task to a corresponding service agent according to task description information; the service agent selects a resource agent in an Agent alliance to execute the task, a task execution result is returned to a user Agent, and displayed in a user interface. Communication between the service agent and the resource agent complies with an expansion contract net protocol, thus reducing communication load between Agents, and fast responding to the user task demand. The resource Agent can joint or withdraw from the Agent alliance, so dynamic characteristic is provided, thus enhancing resource polymerization method flexibility and scalability.
Owner:XIDIAN UNIV
Link state self consulting method
InactiveCN100417083CEasy to implementConsume less resourcesData switching by path configurationControl dataSoftware development
A link status self negotiation method is used for data transmission link state negotiation between transmitting end and receiving end. It contains receiving end receiving data according to right sequence through querying serial number in cell head; through cell head link gateway bit and line error bit to transfer link status; increasing link status list at receiving end and transmitting end; in link fault occurrence and link recover process through receiving end and transmitting end transmitting / receiving state to control data receiving and transmitting, to complete link self negotiation process. In link status self negotiation process, said invention also complete link self negotiation process through querying and configuring parallel-series / series-parallel convert on off state list. The present invention raises negotiation efficiency and systematical reliability.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com