IPSEC negotiation method, apparatus, equipment and system
A total and consistent technology, applied in the field of communication, can solve the problems of long time and low efficiency in IPSEC negotiation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0187] An embodiment of the present invention provides an IPSEC (Internet Protocol Security, Internet Protocol Security) negotiation method.
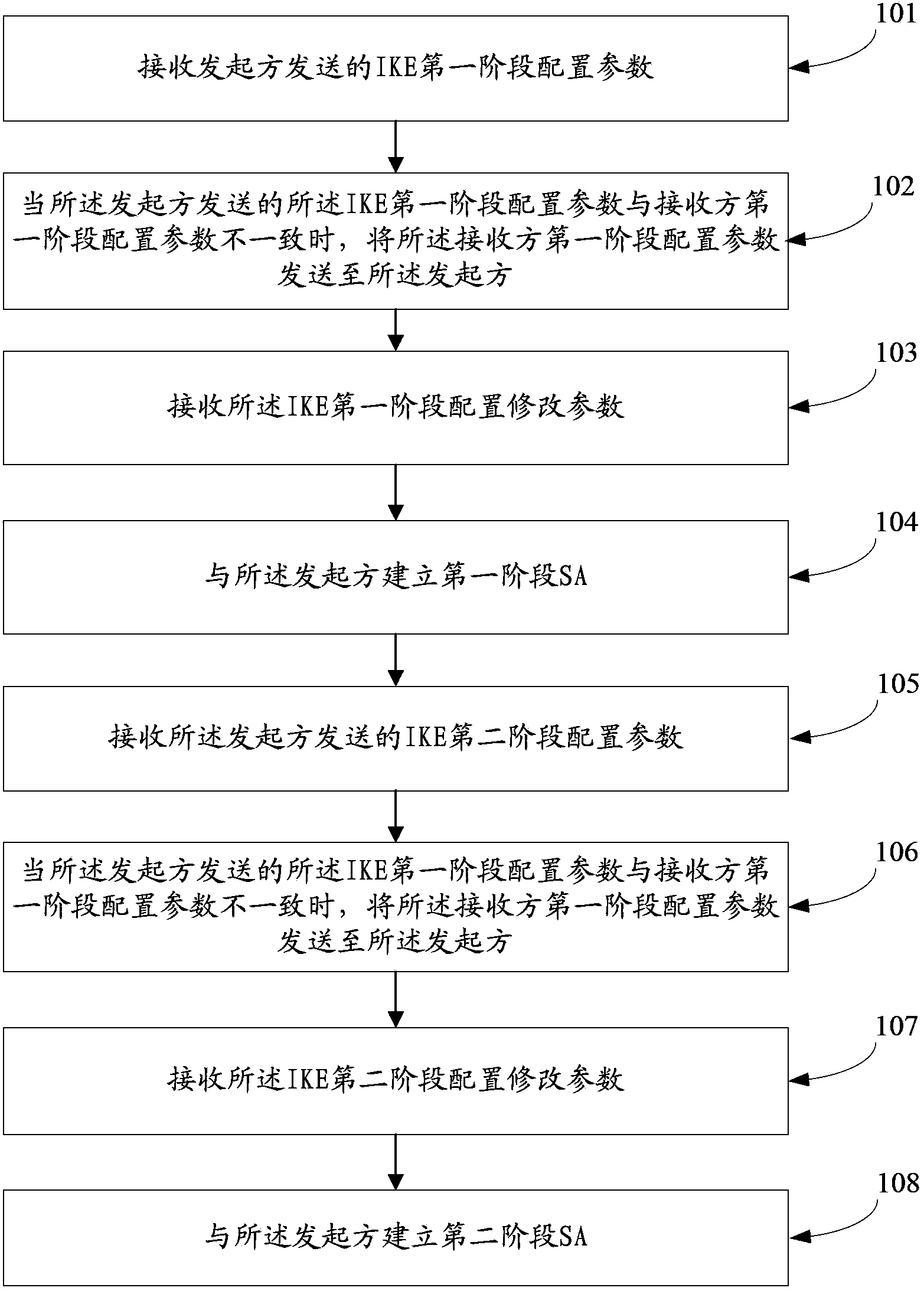
[0188] On the one hand, the receiver involved in IPSEC negotiation, such as Figure 1b shown, including the following steps:
[0189] 101. Receive the first phase configuration parameters of IKE (Internet Key Exchange, Internet Key Exchange Protocol) sent by the initiator.
[0190] The IKE Phase 1 configuration parameters sent by the initiator to the receiver include: initiator IKE version, initiator negotiation mode, initiator authentication method, initiator authentication algorithm, initiator encryption algorithm, and initiator key exchange algorithm group.
[0191] 102. When the first phase configuration parameters of the IKE sent by the initiator are inconsistent with the first phase configuration parameters of the receiver, send the first phase configuration parameters of the receiver to the initiator so that the initiator Gener...
Embodiment 2
[0254] An embodiment of the present invention provides a method for IPSEC negotiation.
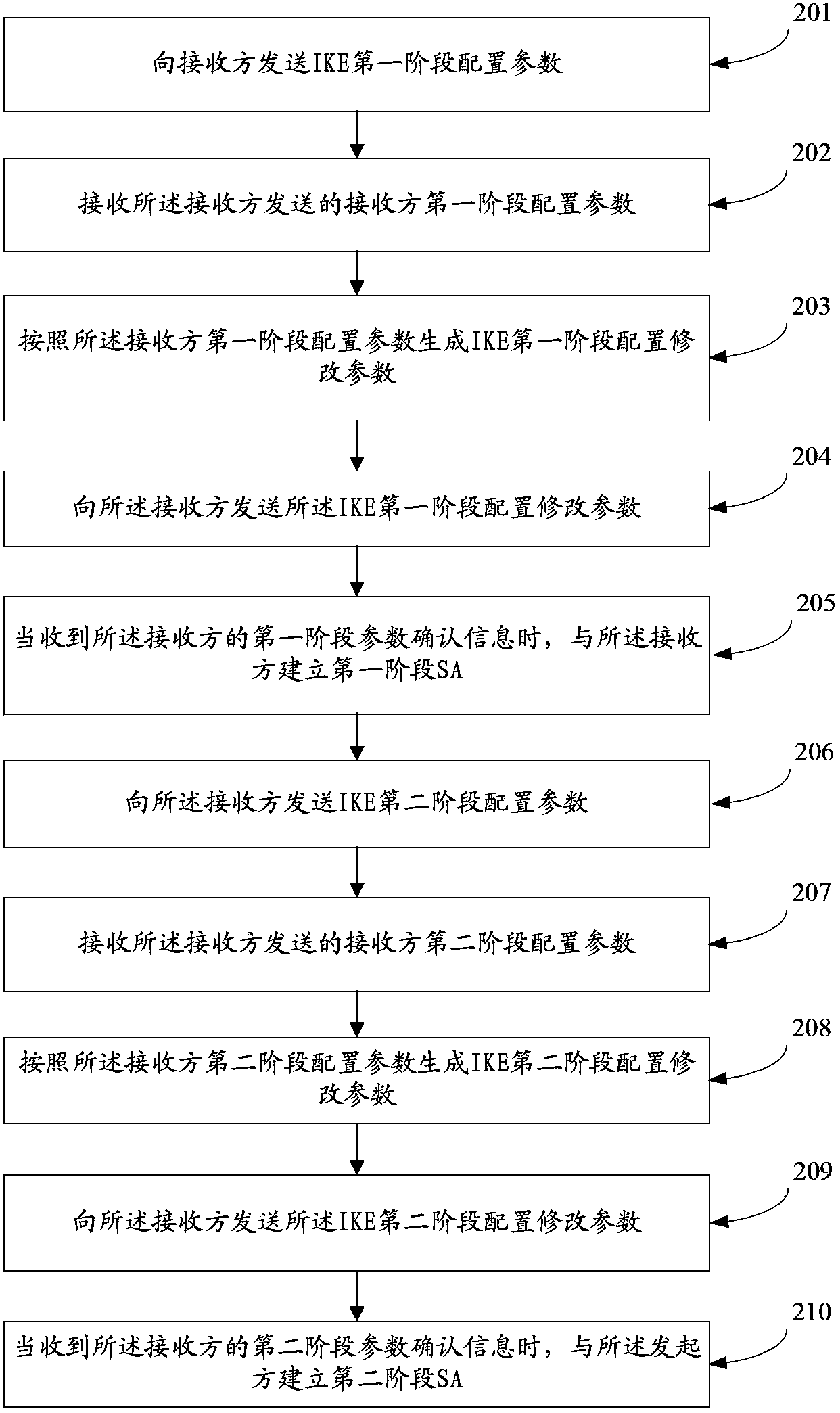
[0255] On the one hand, the receiver involved in IPSEC negotiation, such as image 3 shown, including the following steps:
[0256] 301. Receive the configuration parameters of the first phase of Internet key exchange IKE sent by the initiator.
[0257] The IKE Phase 1 configuration parameters sent by the initiator to the receiver include: initiator IKE version, initiator negotiation mode, initiator authentication method, initiator authentication algorithm, initiator encryption algorithm, and initiator key exchange algorithm group.
[0258] 302. Determine whether the first-phase configuration parameters of the IKE are consistent with the first-phase configuration parameters of the receiver.
[0259] If consistent, execute 305, and when inconsistent, execute 303.
[0260] 303. When the first phase configuration parameters of the IKE sent by the initiator are inconsistent with the first p...
Embodiment 3
[0331] An embodiment of the present invention provides an IPSEC negotiation device.
[0332] On the one hand, the receiver involved in IPSEC negotiation, such as Figure 5 As shown, the device includes:
[0333] The first-stage receiving unit 51 is configured to receive the first-stage configuration parameters of the Internet Key Exchange IKE sent by the initiator.
[0334] The first-stage judging unit 52 is configured to judge whether the first-stage configuration parameters of the IKE sent by the initiator are consistent with the first-stage configuration parameters of the receiver.
[0335] The first-stage sending unit 53 is configured to: when the receiver’s first-stage judging unit judges that the IKE first-stage configuration parameters sent by the initiator are inconsistent with the receiver’s first-stage configuration parameters, send the receiver’s first-stage configuration parameters to The first-phase configuration parameters are sent to the initiator, so that the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com