Quadratic congruence equation-based method for resisting denial-of-service attacks of wireless network
A denial of service attack and wireless network technology, applied in the field of network security, can solve problems such as the inability to guarantee the verification result of the puzzle, and achieve the effects of improving the ability to resist DoS attacks, increasing difficulty, and ensuring diversity and randomness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
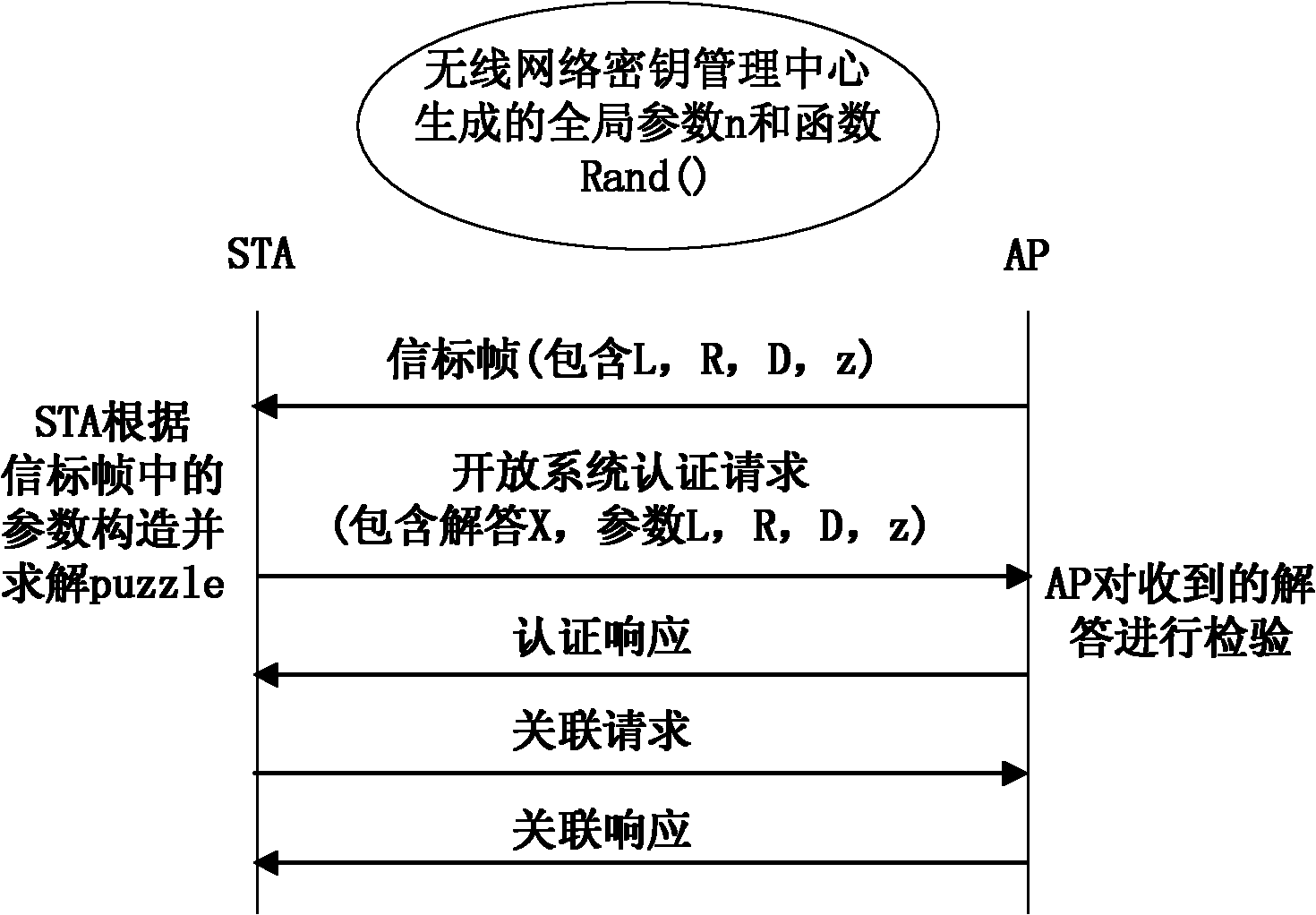
[0032] refer to image 3 , the specific implementation steps of the method for resisting the denial of service attack of the wireless network based on solving the quadratic congruence equation proposed by the present invention are as follows:
[0033] In step 1, the key management center of the wireless network system generates a global public parameter n and a function Rand(z).
[0034] The global public parameter n is the product of two random prime numbers larger than 512 bits and is regularly updated by the key management center. The function Rand(z) is a uniform pseudo-random number generation function whose output value is in the interval [1, w], w is The bit length of n, z is the input seed of the function Rand(z).
[0035] Step 2, the access point AP periodically broadcasts to the wireless local area network a beacon frame adding question puzzle construction parameters.
[0036] The access point AP adds the parameters z, L, R, and D used to construct the puzzle in th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com