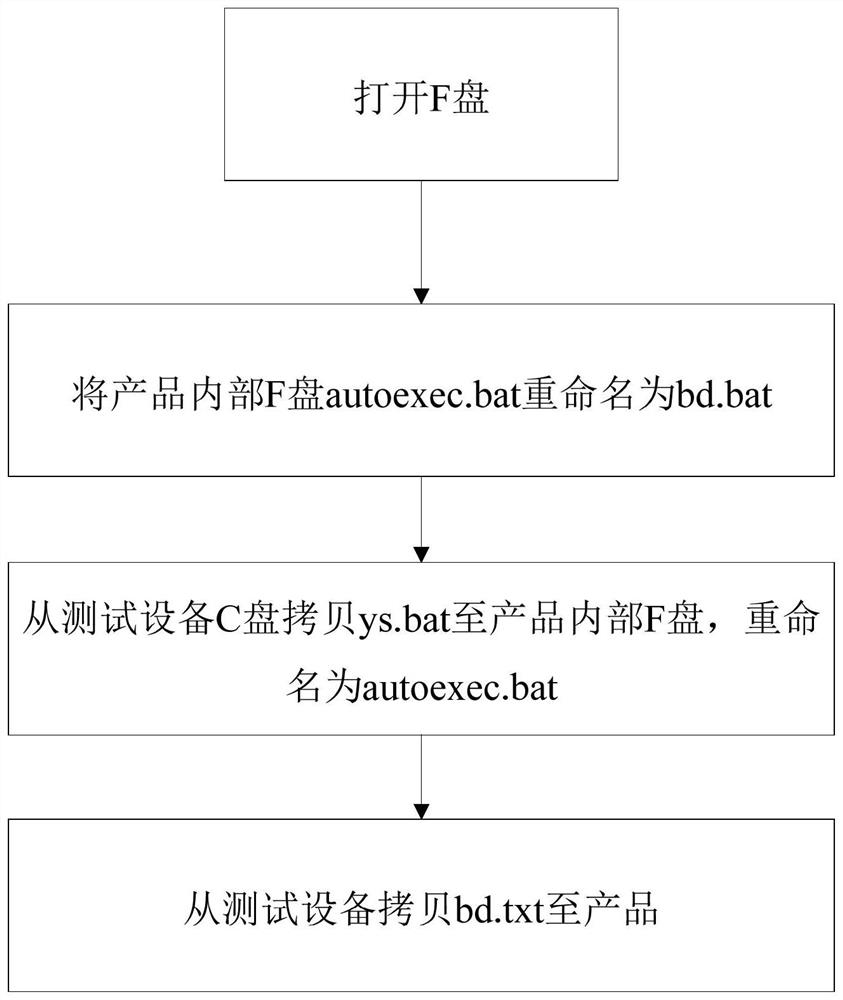
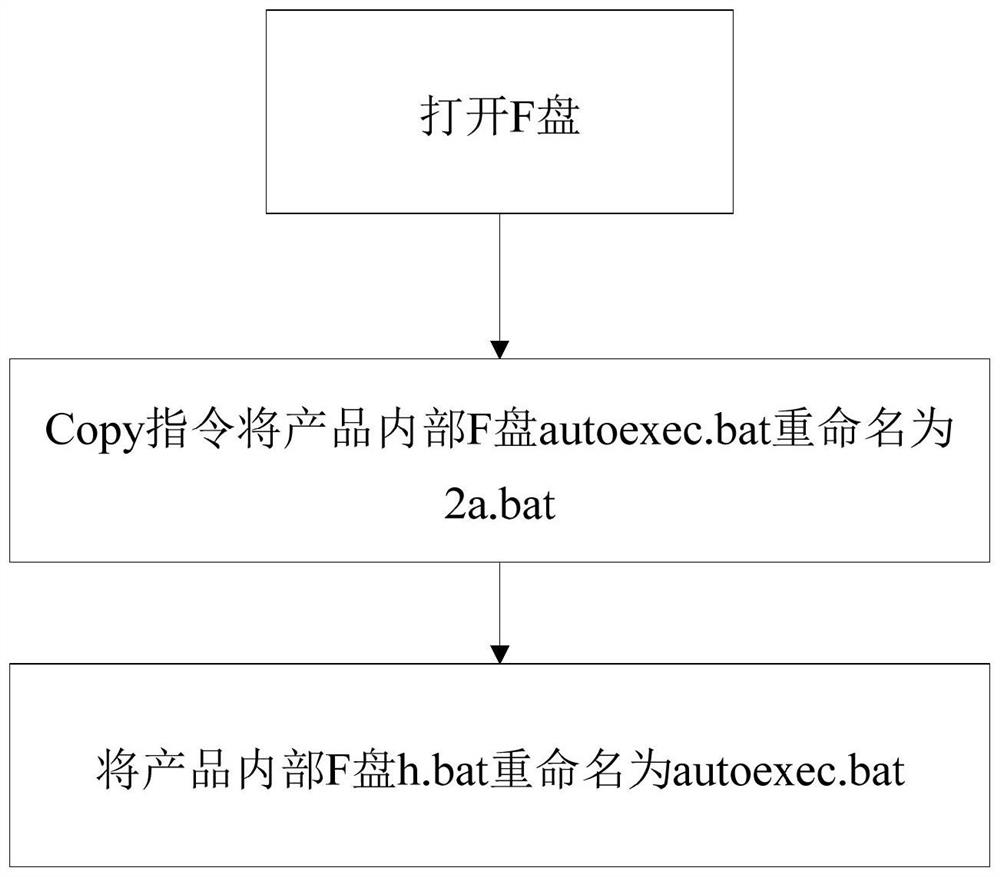
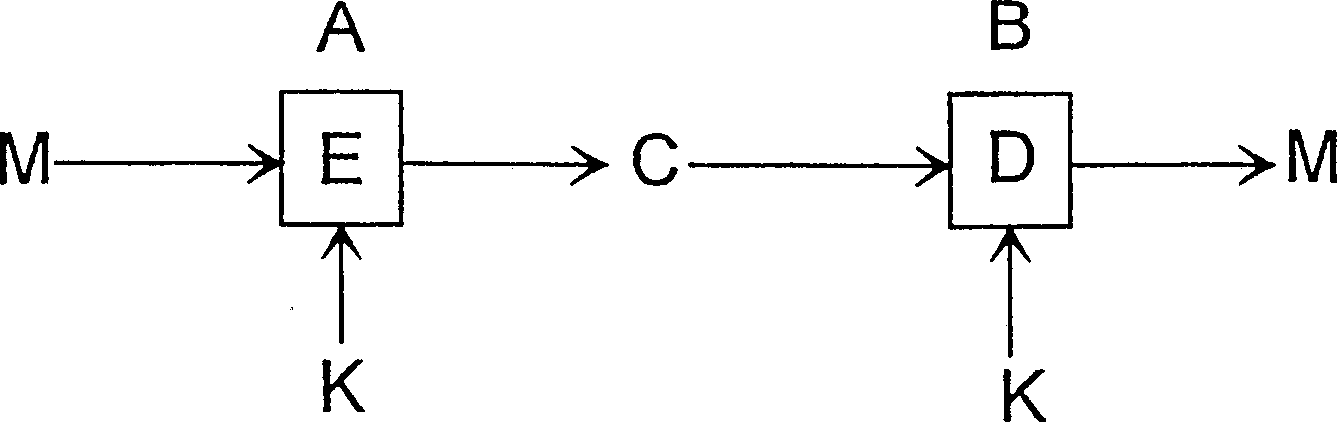
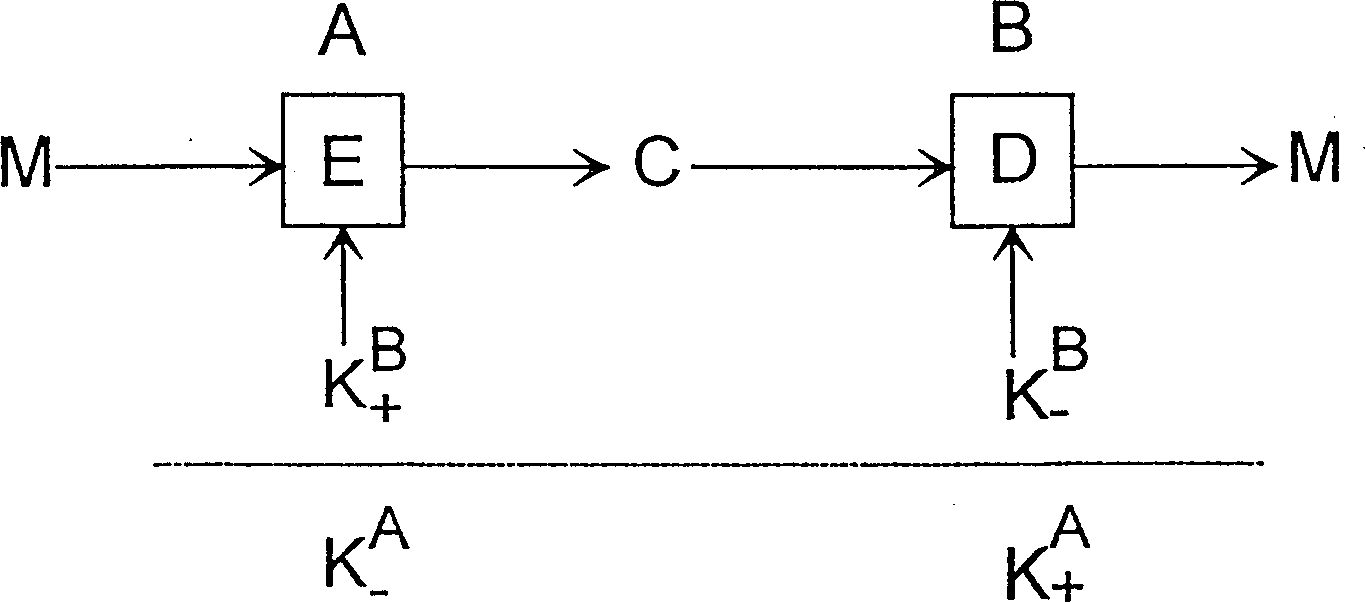
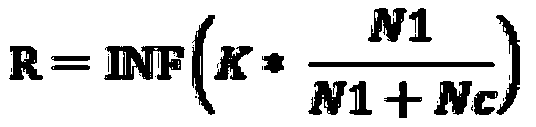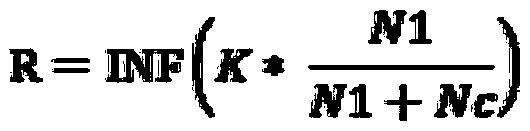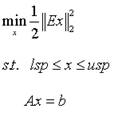Patents
Literature
34results about How to "Reduce the number of handshakes" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
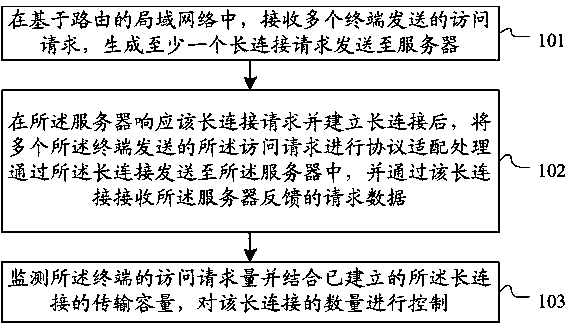
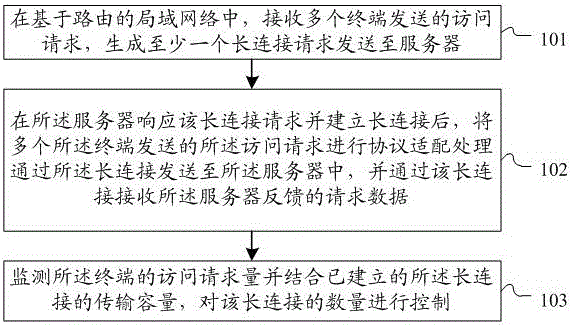
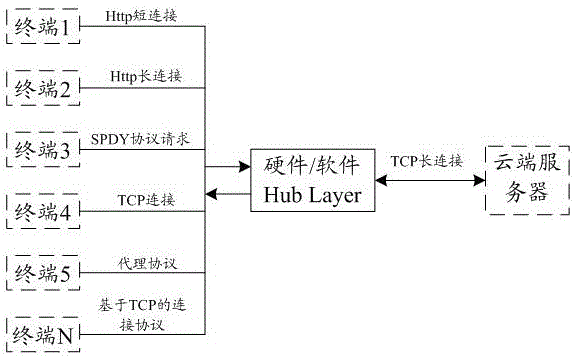
Method and system for long connections based on router level
ActiveCN104009938AReduce the number of handshakesAddressing Lack of Unified Communications ManagementData switching networksProtocol for Carrying Authentication for Network AccessLocal area network
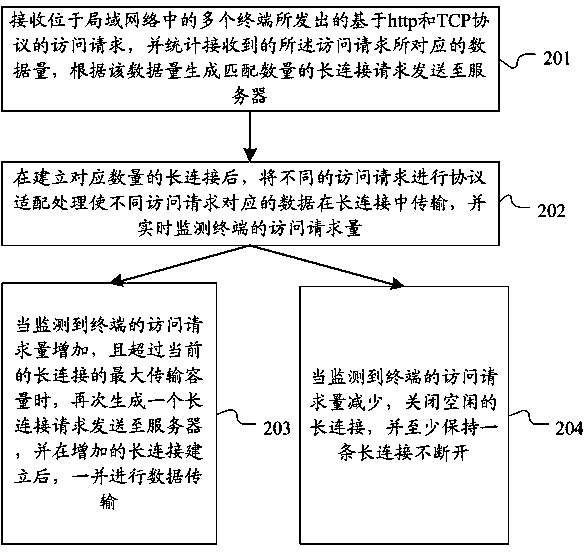
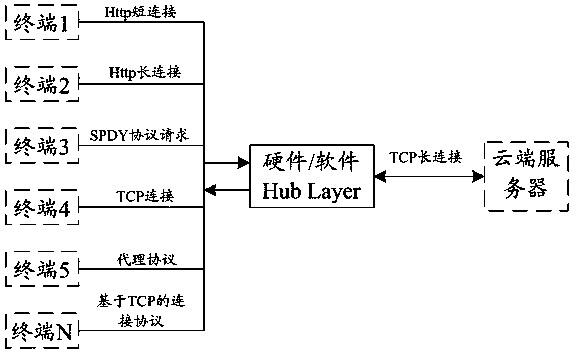
The invention discloses a method and system for long connections based on a router level. The method includes the steps that in a local area network based on a router, access request sent by multiple terminals are received, and at least one long connection request is generated and sent to a server; after the server responds to the long connection requests and establishes the long connections, protocol fit processing is conducted on the access requests sent by the terminals, the access requests are sent to the server through the long connections, and request data fed back by the server are received through the long connections; the number of the access requests of the terminals is monitored, and in combination with the transmission capacity of the established long connections, the number of the long connections is controlled. The method and system solve the problems that in the environment of the local area network based on the router, the long connections are established through the terminals, unified communication management is not available, and the router can only establish short connections.
Owner:ALIBABA (CHINA) CO LTD
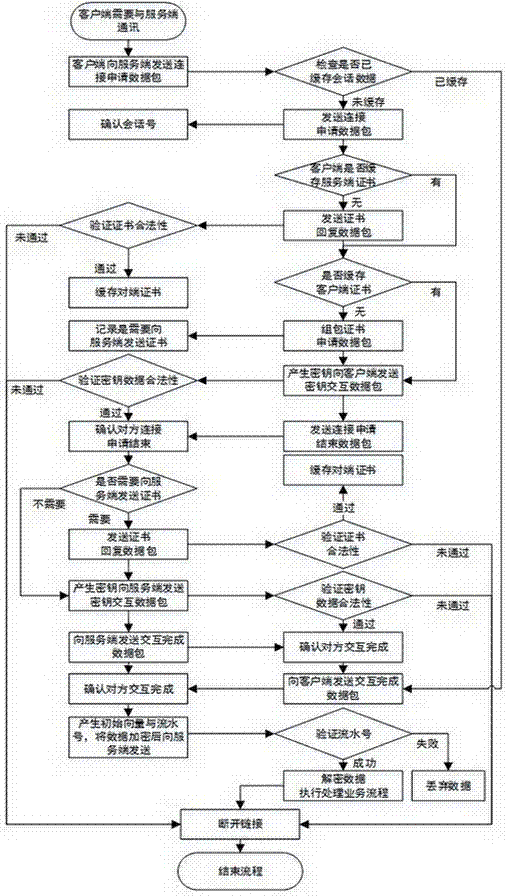
Safety channel establishment method, and data protection method and safety channel key updating method thereof
ActiveCN104683359AReduce the number of handshakesReduce consumptionKey distribution for secure communicationSecure communicationComputer terminal
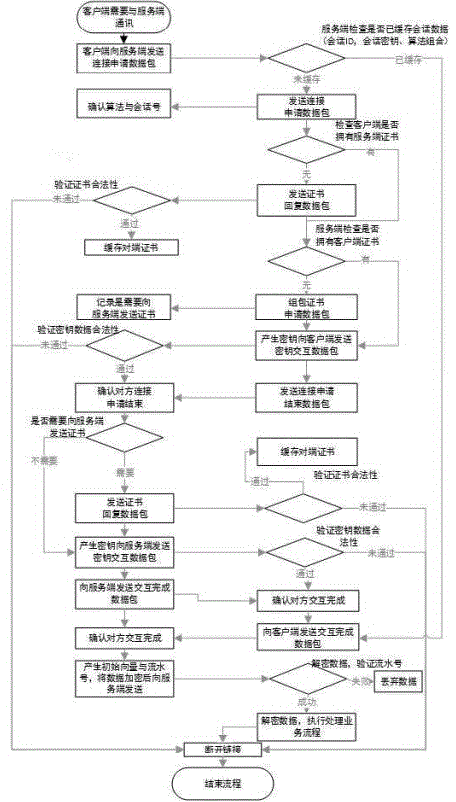
The invention provides a safety channel establishment method, and a data protection method and a safety channel key updating method thereof. When executing the establishment of handshake flow of the safety communication channel, a terminal and a server side check whether the safety communication channel is successfully established and a key is unchanged, and checks whether the certificate of the opposite side is cached; if related data is cached, the transmitted data and flow during the handshake flow of the two parties can be reduced, so that the purposes of shortening the time for establishing the safety communication channel for the two parties aiming at the packet domain communication characteristic of a mobile communication network and under the conditions of ensuring the data safety during the data communication of the terminal and the server side can be achieved, and the purpose of having no need of always maintaining TCP chain between the two communication parties can be achieved.
Owner:成都三零瑞通移动通信有限公司
Digital transformer substation distribution testing method based on ZigBee wireless technology
InactiveCN103178987AReduce the number of handshakesReduce loadCircuit arrangementsTime-division multiplexMeasurement deviceTransceiver
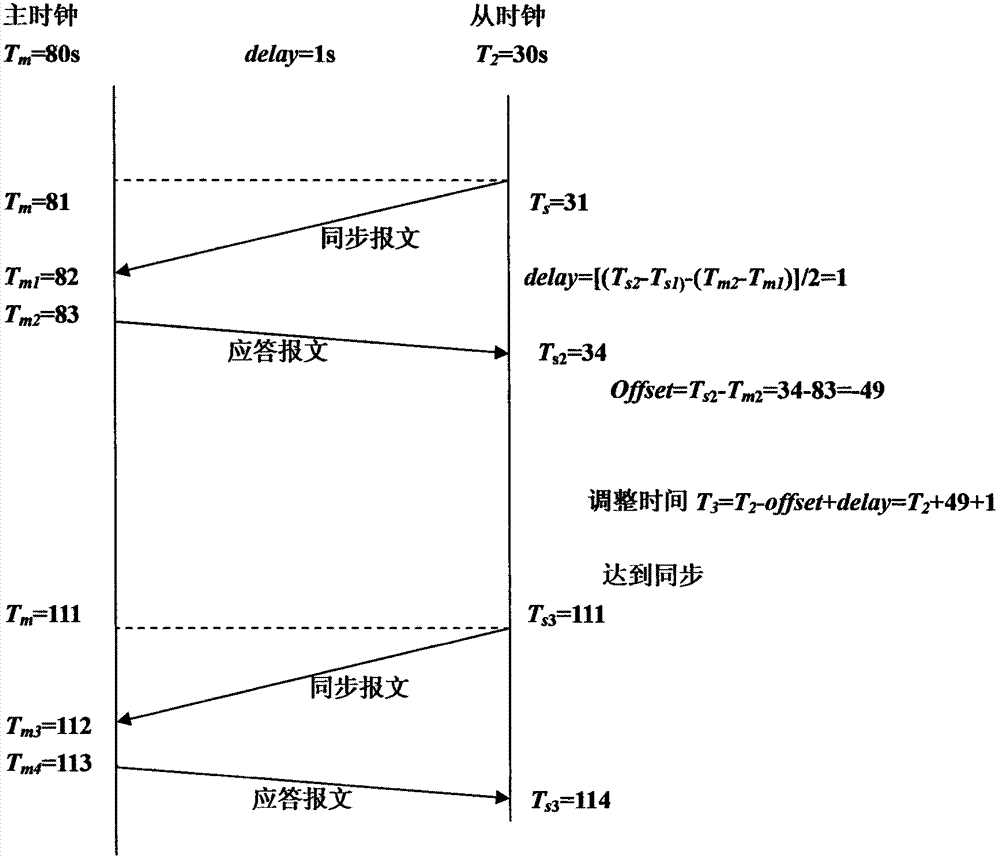
The invention discloses a digital transformer substation distribution testing method based on the ZigBee wireless technology. A digital transformer substation control system comprises a process layer, a space layer and a transformer substation layer. Protection, measurement, control and measurement devices are arranged in the space layer; information between the space layer and the process layer are interacted according to sampling values of specific communication service mapping and generic object oriented substation events, and problems about analog simulation tests of the space layer with the primary devices mounted in a dispersed manner are solved. Different from results of utilization of a PTP (precision time protocol), after the clock synchronization principle is adopted, drift metering and delay metering are completed within one communication process rather than in two steps, so that handshaking times of synchronous communication are reduced, network load is lowered effectively, reliability in synchronization is improved while affection to network transmission performance is decreased.
Owner:深圳市康必达中创科技有限公司
Secure transmission method using time-varying incidental information flow as key information
ActiveCN101656728AReduce redundancyReduce the number of handshakesData switching networksSecuring communicationData streamSecure transmission
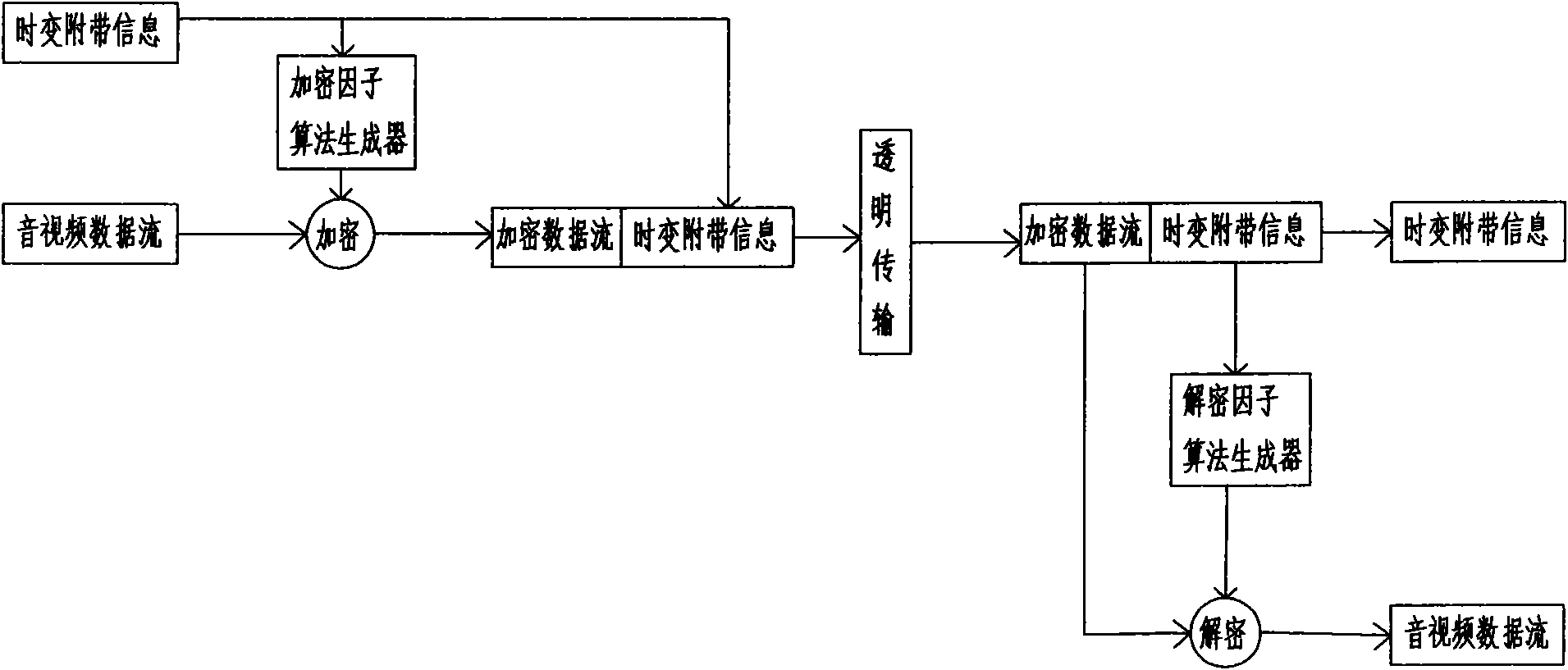
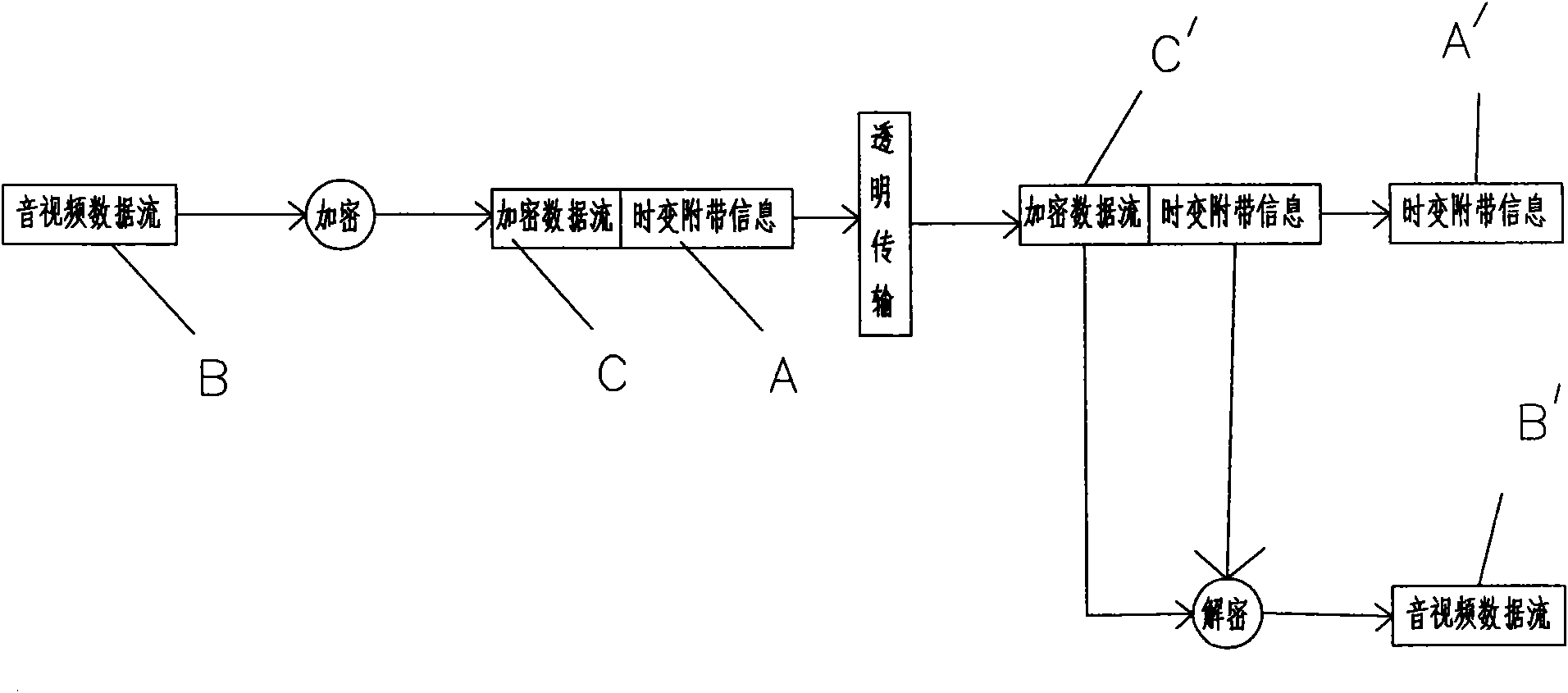
The invention discloses a secure transmission method using time-varying incidental information flow as key information, which uses binary codes for transmitting data flow; in addition, in the sender data processing procedure, an algorithm generator uses the time-varying incidental information for generating a time-varying encrypted factor, the logical operation of the time-varying encrypted factor and the original data flow to be sent is carried out to generate the encrypted data flow, and the encrypted data flow and the time-varying incidental information are combined in a specific mode to form and send information data flow; a receiver receives the information data flow, detects the time-varying incidental information in the information data flow, separates the time-varying incidental information from the encrypted data flow, and uses the algorithm generator for generating a time-varying decrypting factor according to the time-varying incidental information; and the logical operation of the time-varying decrypting factor and the encrypted data flow is carried out to obtain the original data flow. The method has no need of strict synchronization, can achieve the asynchronous receiving, can reduce the handshaking times, improves the communication efficiency and has better safety.
Owner:HANGZHOU YONGKONG TECH
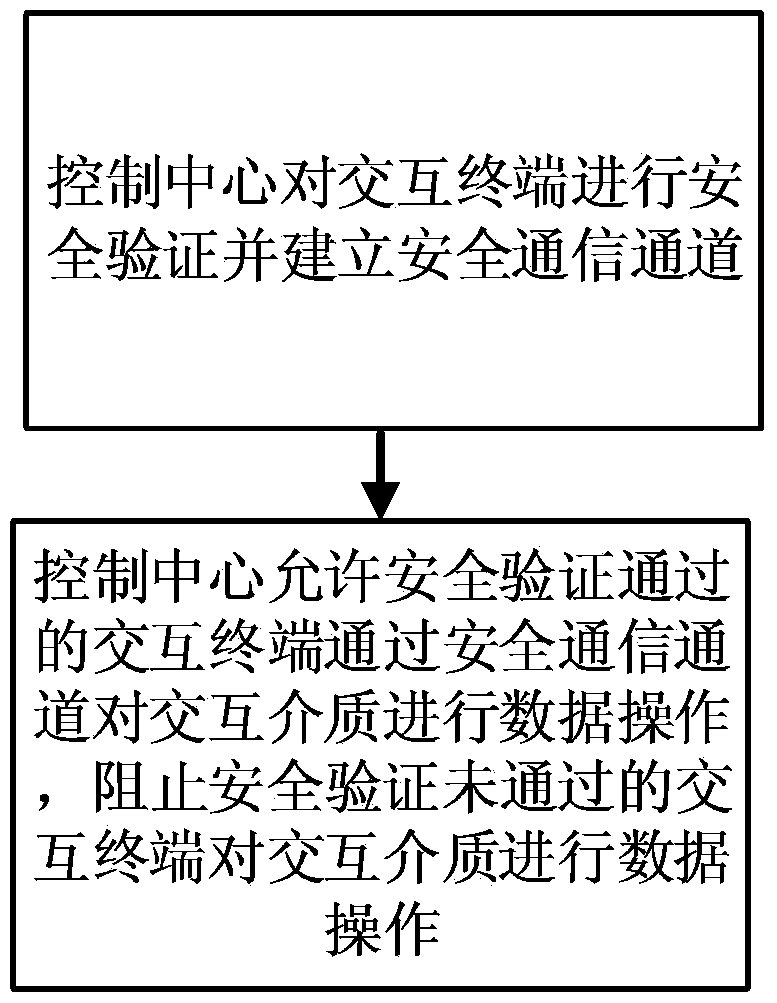
Data secure communication method
InactiveCN105430017AReduce the number of handshakesReduced settling timeTransmissionSecure communicationCommunications system
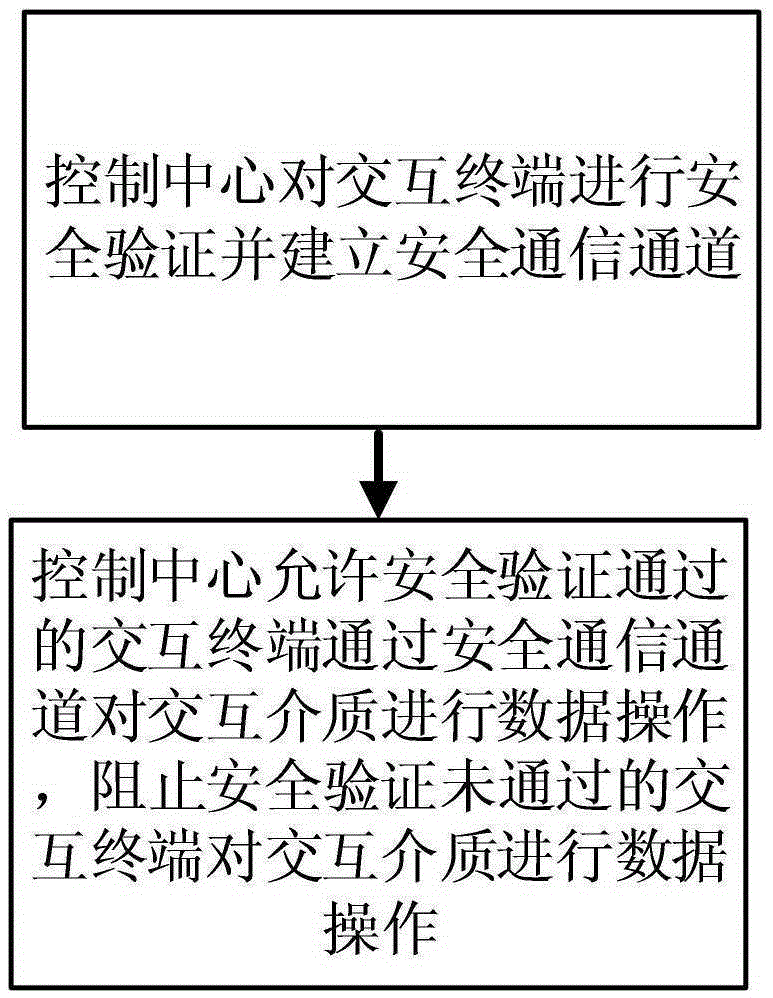
The invention belongs to the data secure communication technical field and relates to a data secure communication method. The data secure communication method includes the following steps that: 1) a control center performs security authentication on interaction terminals and establishes secure communication channels; and 2) the control center allows interaction terminals which pass the security verification to perform data operation on an interaction medium through the safe communication channels, and prevents interaction terminals which do not pass the security verification from performing data operation on the interaction medium. With the data safe communication method of the invention adopted, the secure communication channels can be established more fast, and cracking difficulty of digital certificates can be increased, and the safety and reliability of a data communication process can be enhanced, and the consumption of resources of a communications system by the communication process can be reduced.
Owner:STATE GRID SHANDONG LINQU POWER SUPPLY +2
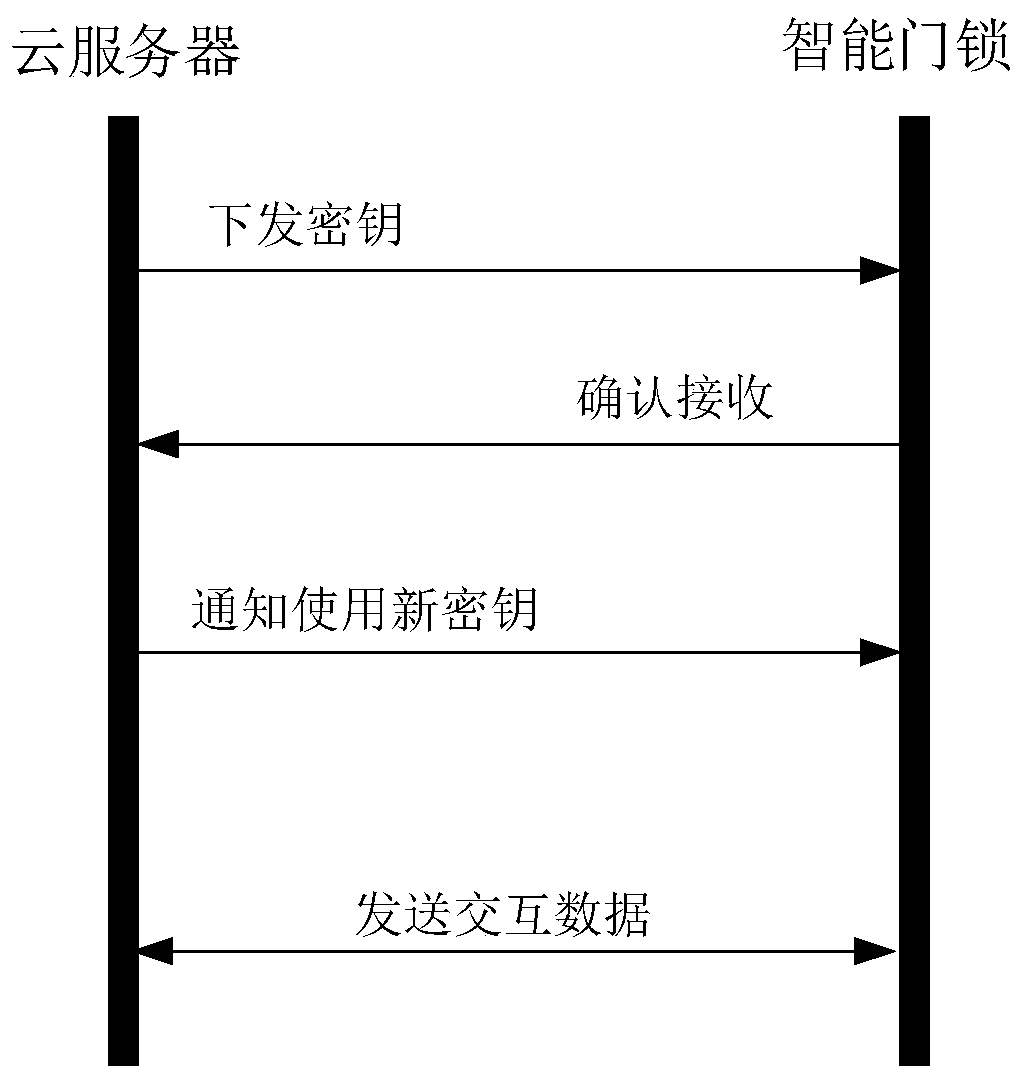
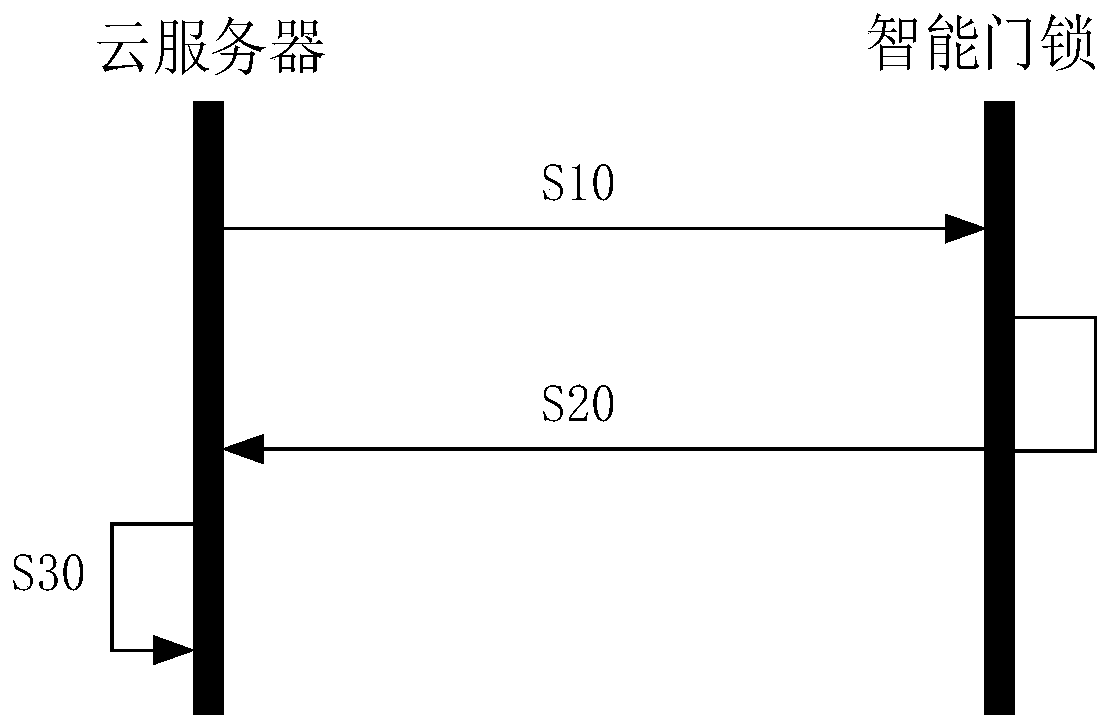
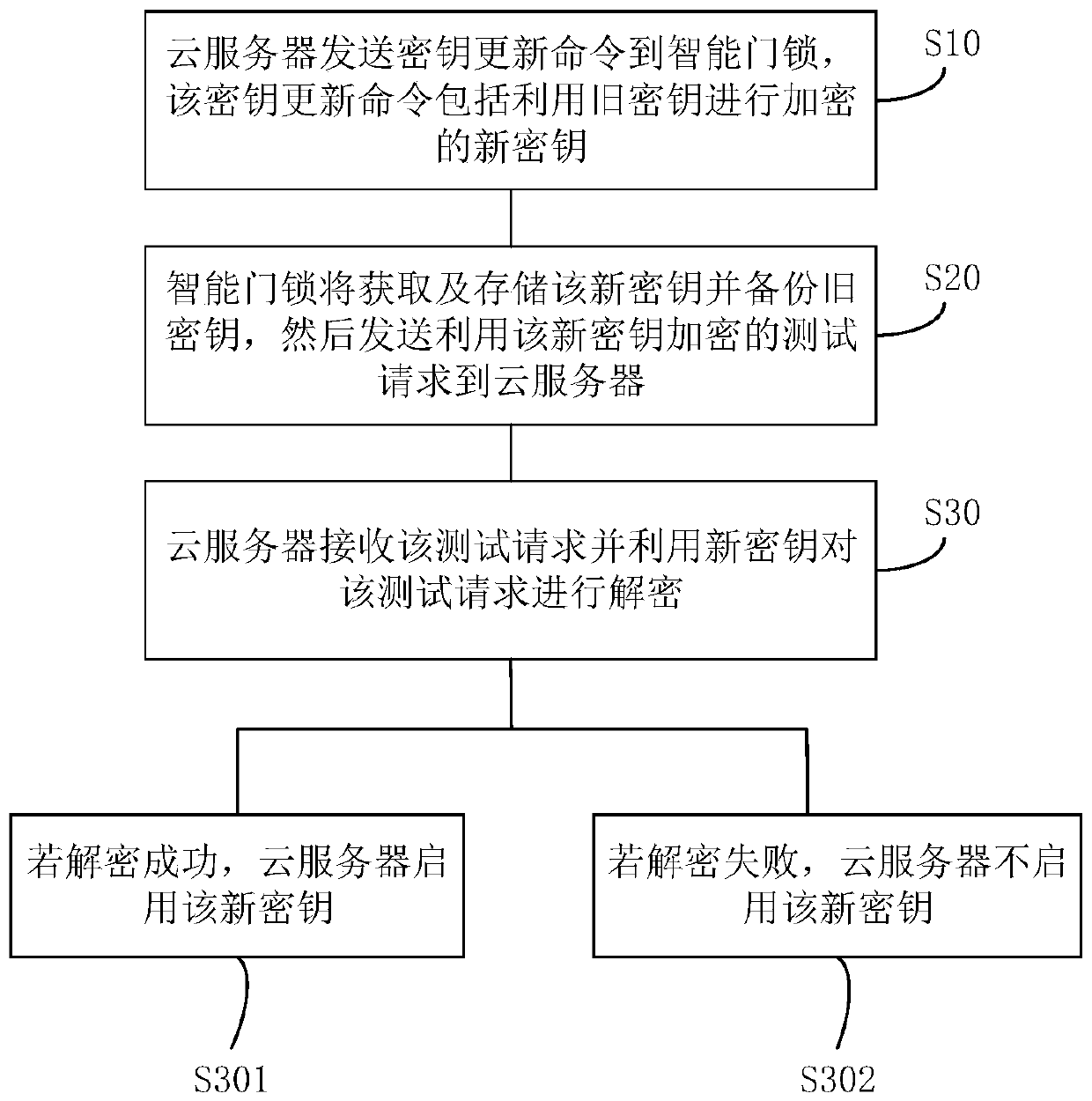
Intelligent door lock secret key updating method and system and computer storage medium
InactiveCN110445607AReduce the number of handshakesOptimize communication handshake mechanismKey distribution for secure communicationIndividual entry/exit registersComputer hardwareTest requirements
The invention discloses an intelligent door lock secret key updating method and system and a computer storage medium. The method comprises the steps that a secret key updating command issued by a cloud server is received, the secret key updating command comprises a new secret key encrypted through an old secret key, and the old secret key is a default secret key agreed in advance or a secret key used by an intelligent door lock in the last updating process; and a new key is acquired and stored, an old key is backed up and a test request encrypted by using the new key is sent to the cloud server, so that the cloud server successfully decrypts the test request and then starts the new key. According to the technical scheme provided by the invention, the handshake times of the intelligent doorlock and the cloud server can be reduced by using a double-key mode, a communication handshake mechanism between the intelligent door lock and the cloud server is optimized, and the communication efficiency is improved.
Owner:北京百佑科技有限公司
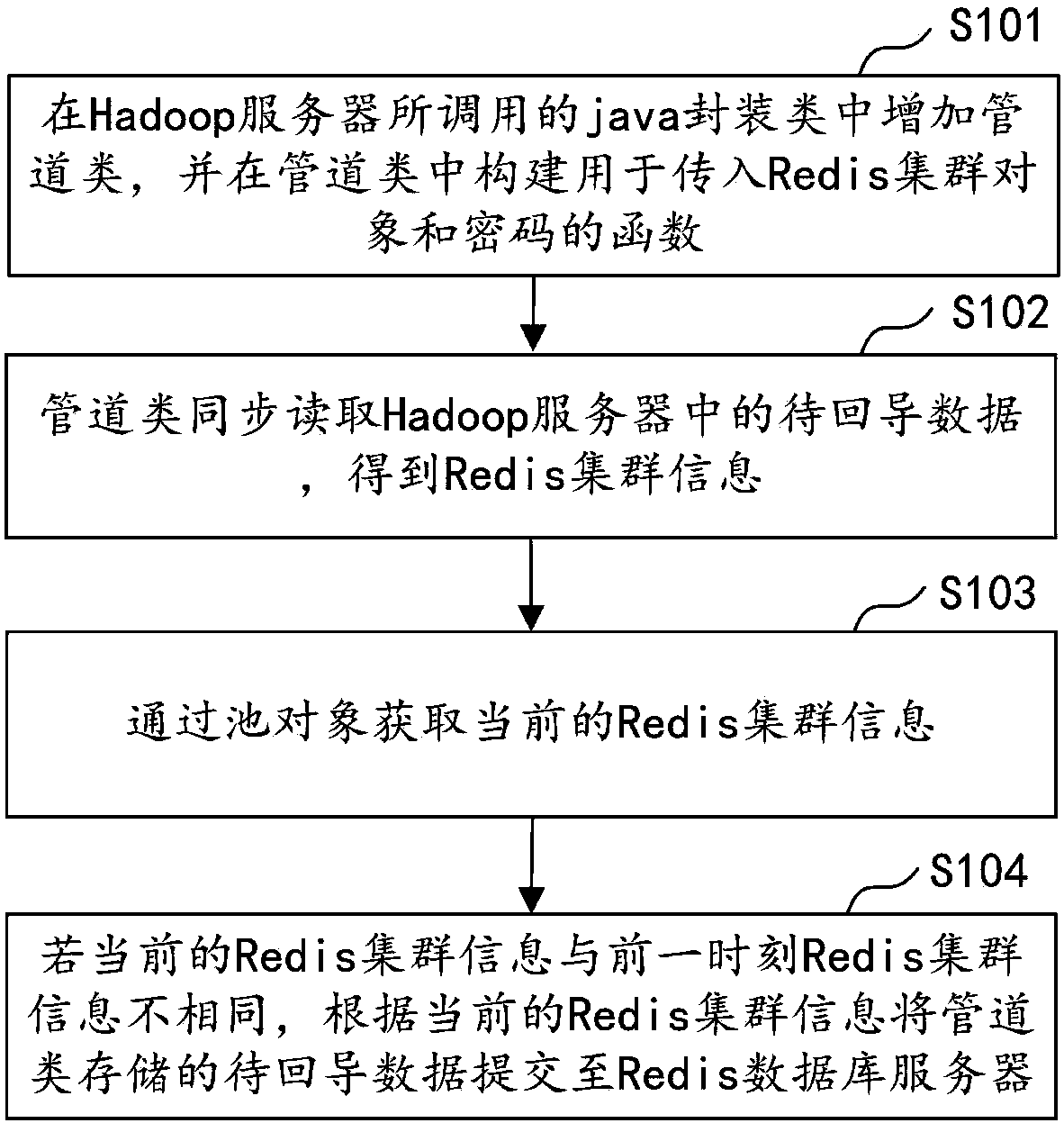
Cross-wide area network (WAN) data return method and device, computer equipment and storage medium
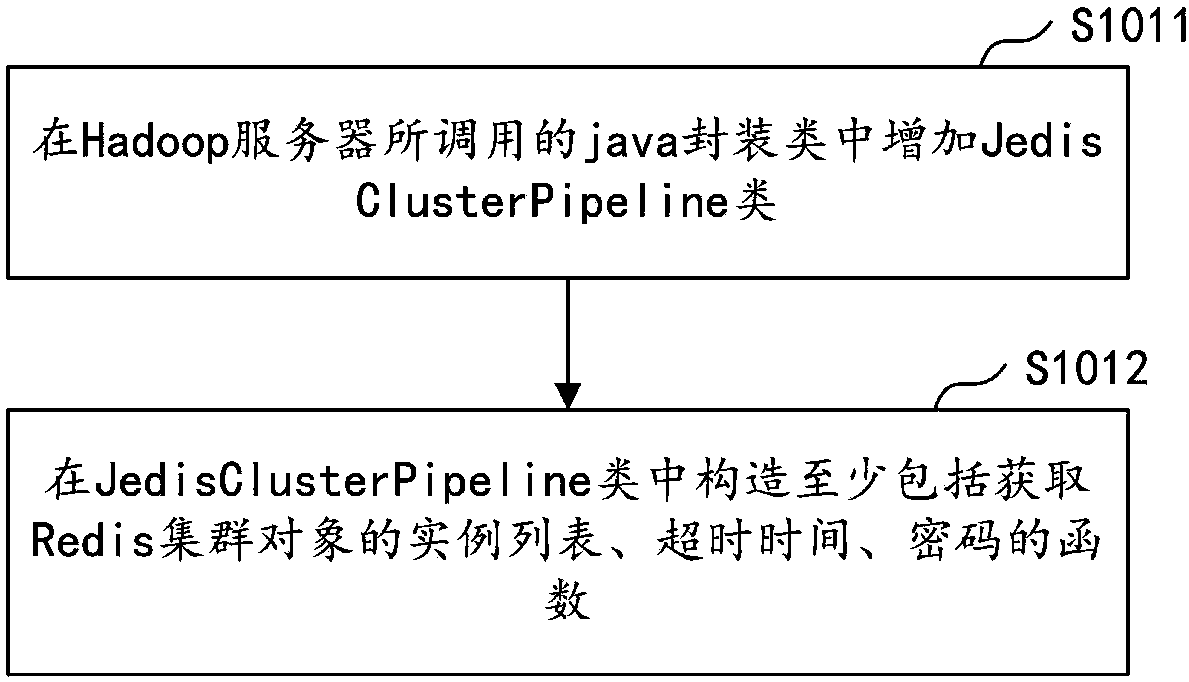
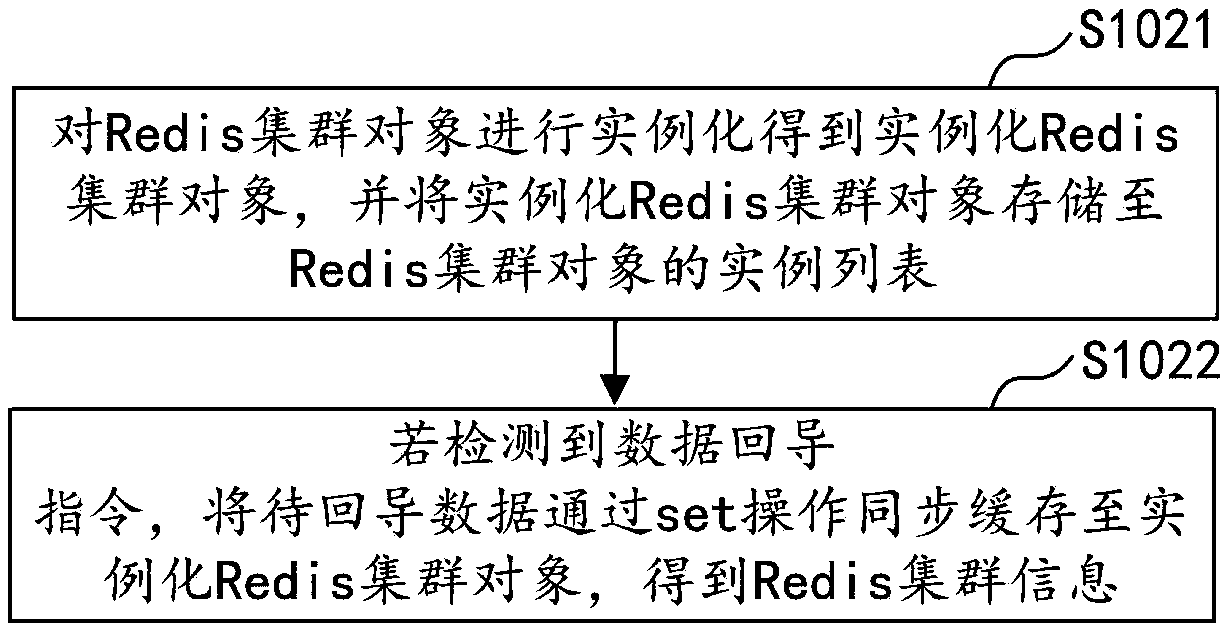
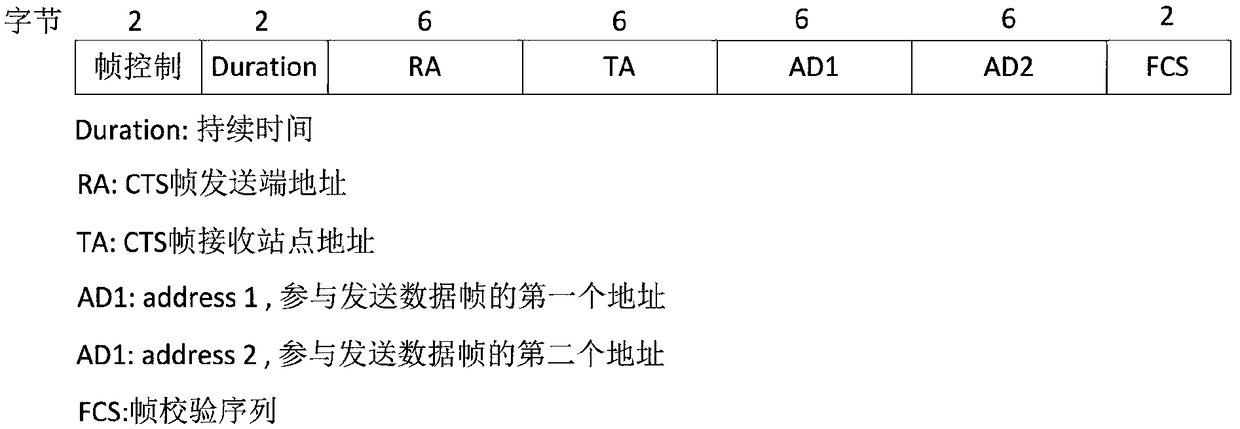
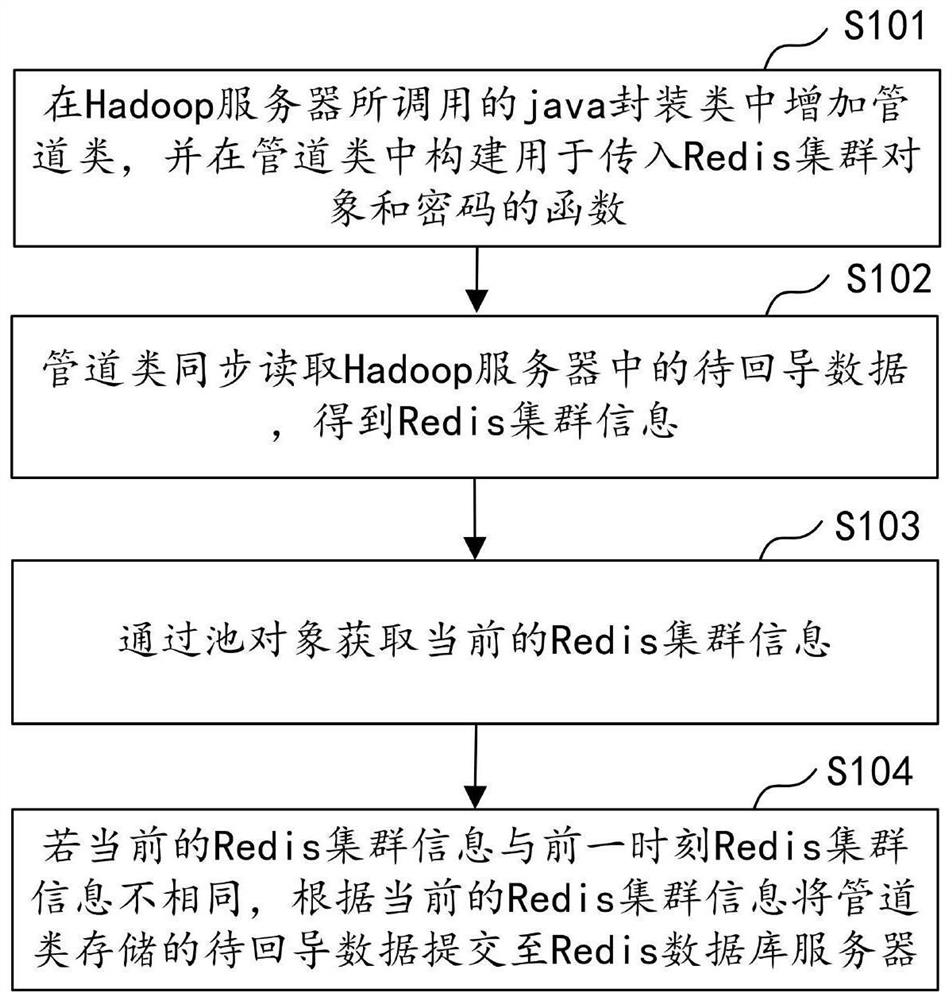
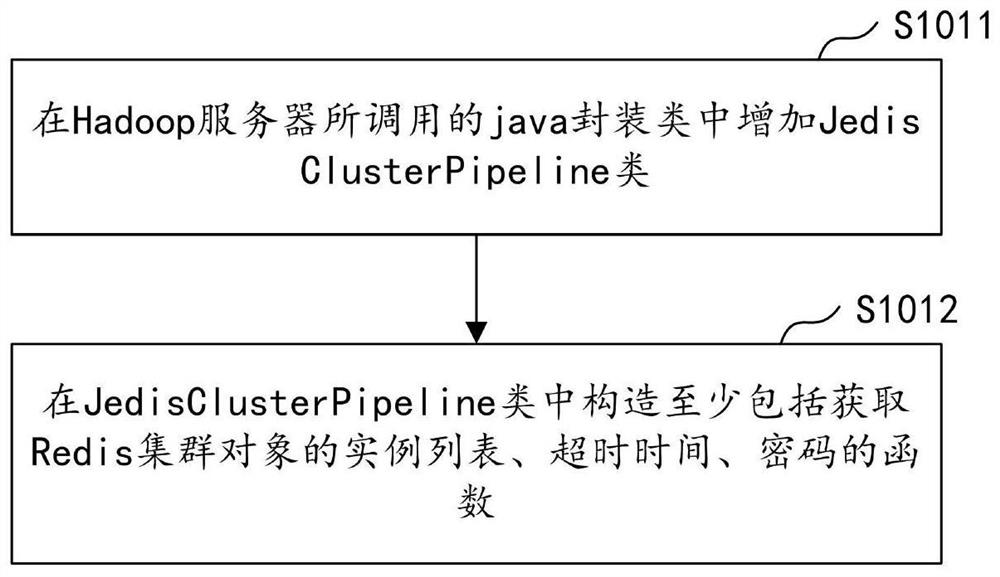
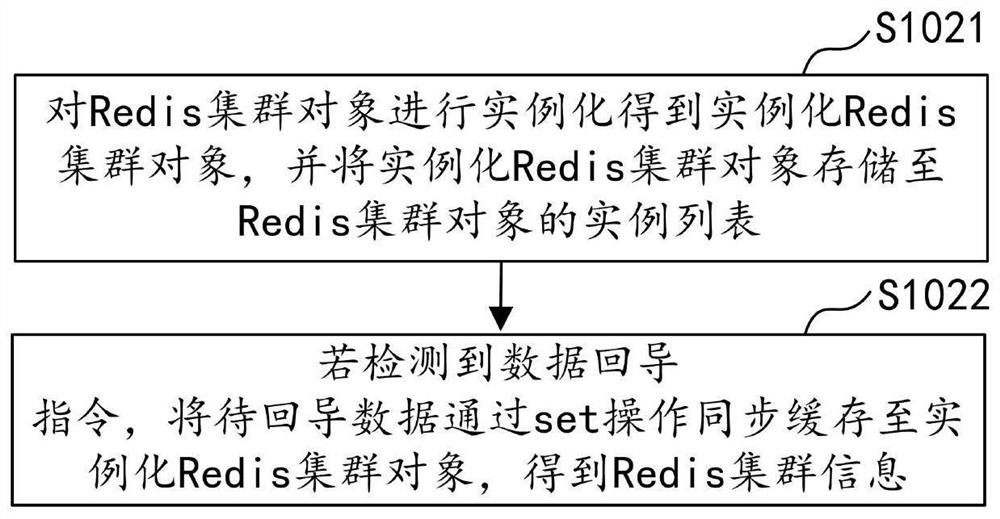
ActiveCN108418874AImprove return efficiencyReduce the number of handshakesTransmissionPasswordDatabase server
The application discloses a cross-wide area network (WAN) data return method and device, computer equipment and a storage medium. The method includes the following steps: adding a pipeline class to ajava package class called by a Hadoop server, and constructing a function for inputting a Redis cluster object and a password in the pipeline class; enabling the pipeline class to synchronously read data to be returned in the Hadoop server to obtain Redis cluster information; obtaining current Redis cluster information through a pool object; and if the current Redis cluster information is different from the Redis cluster information at the previous moment, submitting the data to be returned stored in the pipeline class to a Redis database server according to the current Redis cluster information. According to the method, only when the Redis cluster information is updated, the pipeline class submits batch data to the Redis database server, and thus the number and time of handshakes of a remote TCP protocol can be reduced, and the data return efficiency can be improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
Hydroacoustic media access control method based on reservation scheduling mechanism
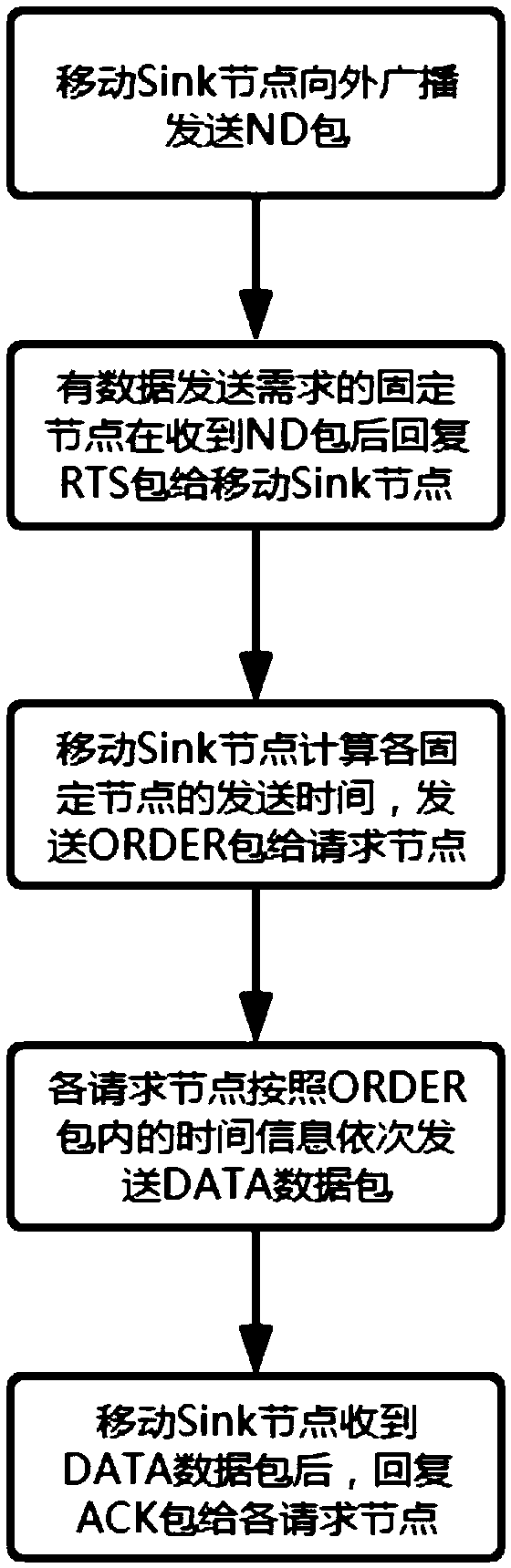
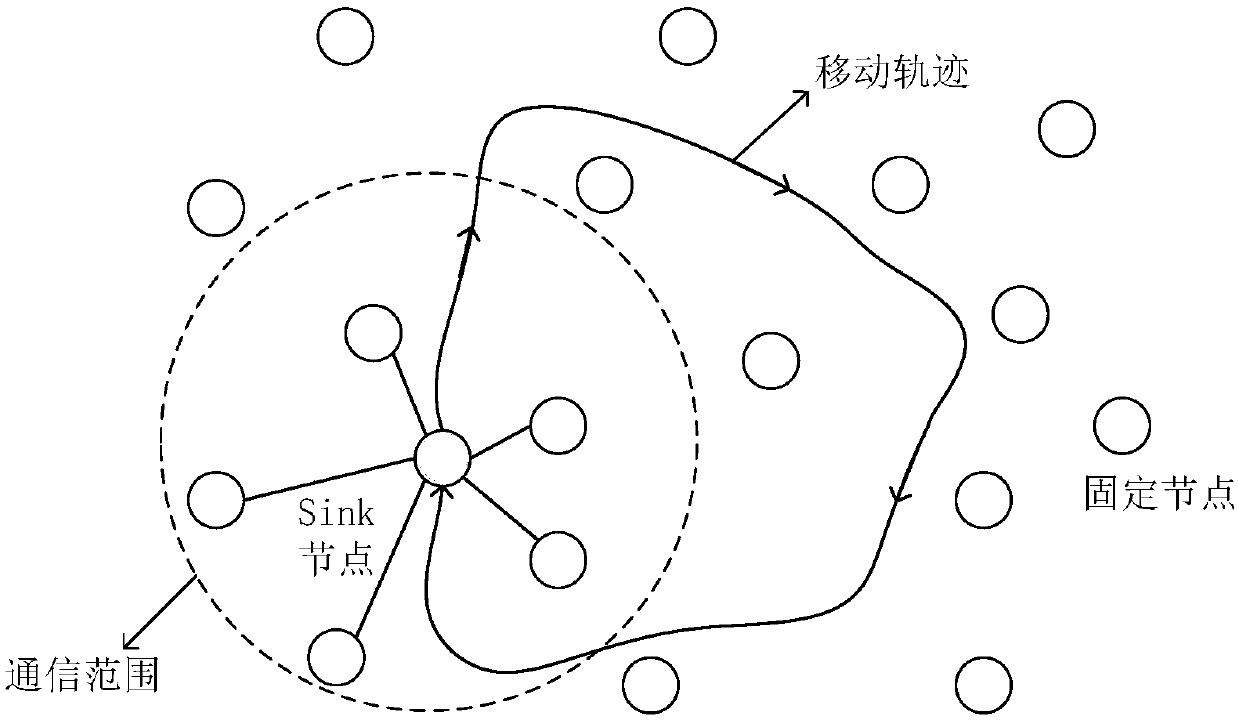
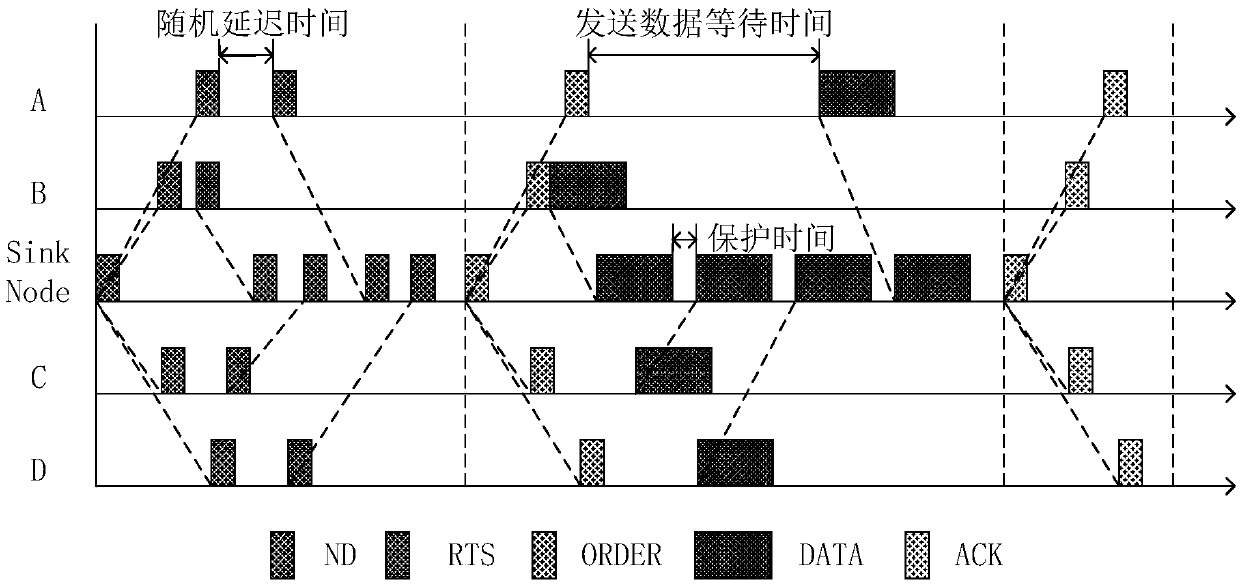
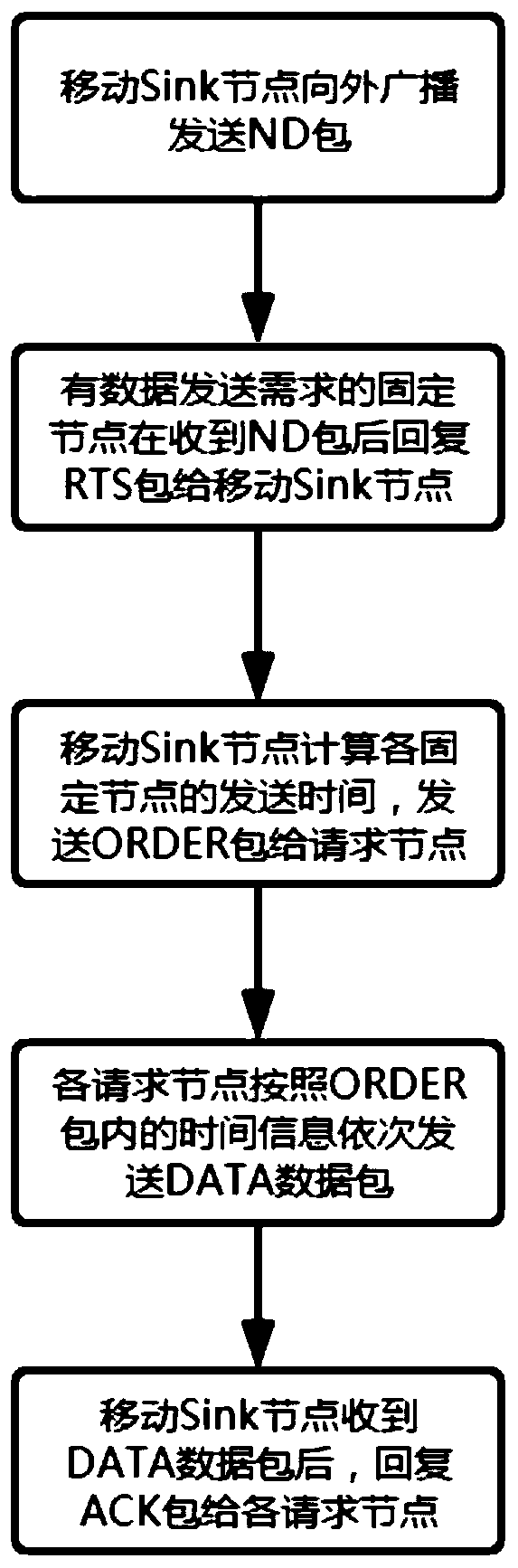
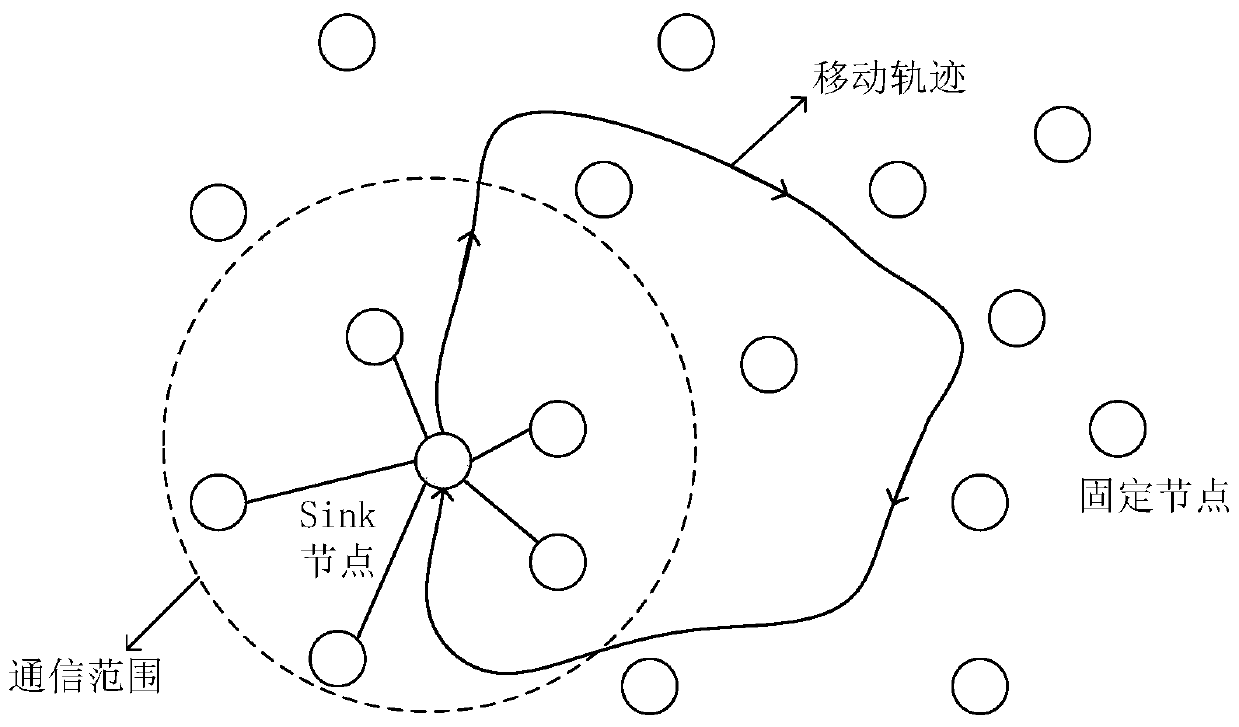
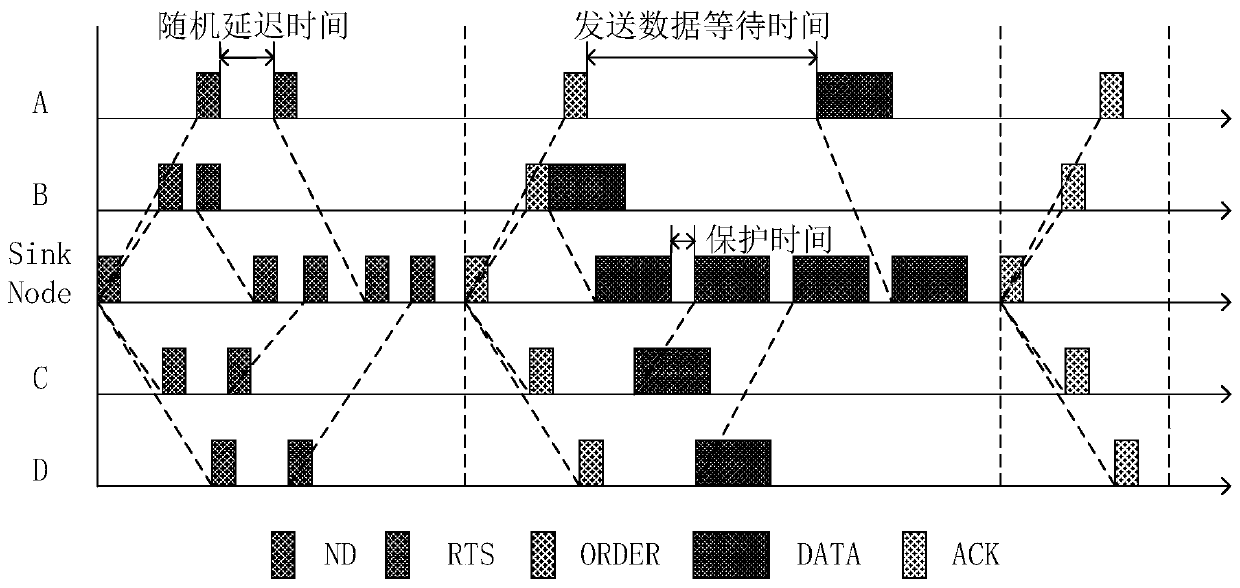
ActiveCN109688554ASolve conflictsIncrease profitPower managementBroadcast service distributionPropagation delayNetwork packet
The invention provides a hydroacoustic media access control method based on a reservation scheduling mechanism. After a fixed node with a data transmission requirement receives an ND packet of a Sinknode, an RTS packet is sent to the Sink node for carrying out data transmission reservation; and the Sink node calculates information of propagation delay and the like according to information in theRTS packet, and then calculates data transmission time of each node, so that data transmission scheduling of each node is completed. The conflict problem of the data packets is effectively avoided based on the reservation scheduling mechanism, the handshaking time between the nodes is shortened, the channel utilization rate is obviously improved, and the data transmission efficiency is improved; and in addition, the nodes do not need to be subjected to time synchronization in advance, so that the implementation requirements of a hydroacoustic communication network are remarkably reduced.
Owner:INST OF DEEP SEA SCI & ENG CHINESE ACADEMY OF SCI
Connection establishment method and device, electronic equipment and storage medium
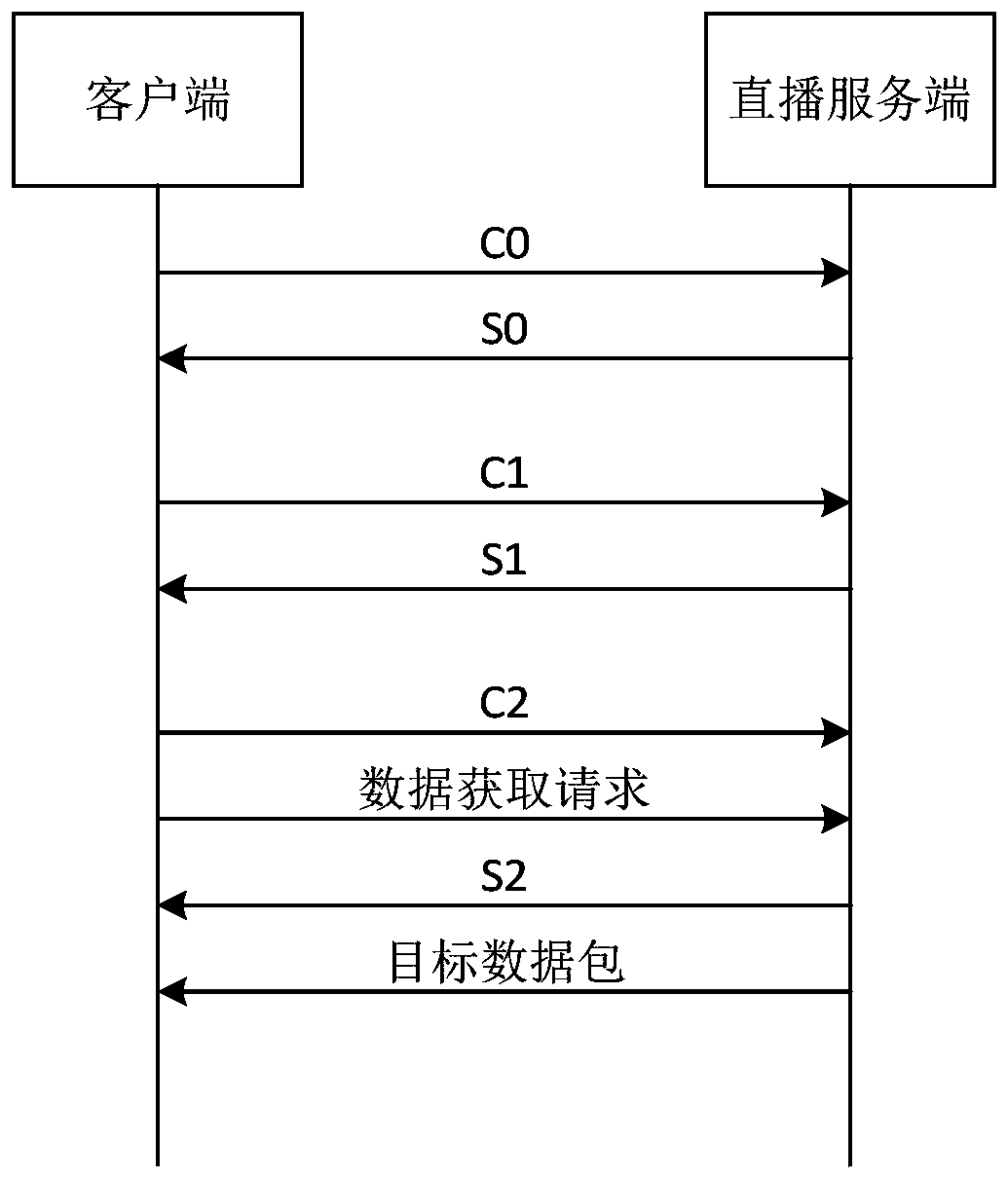
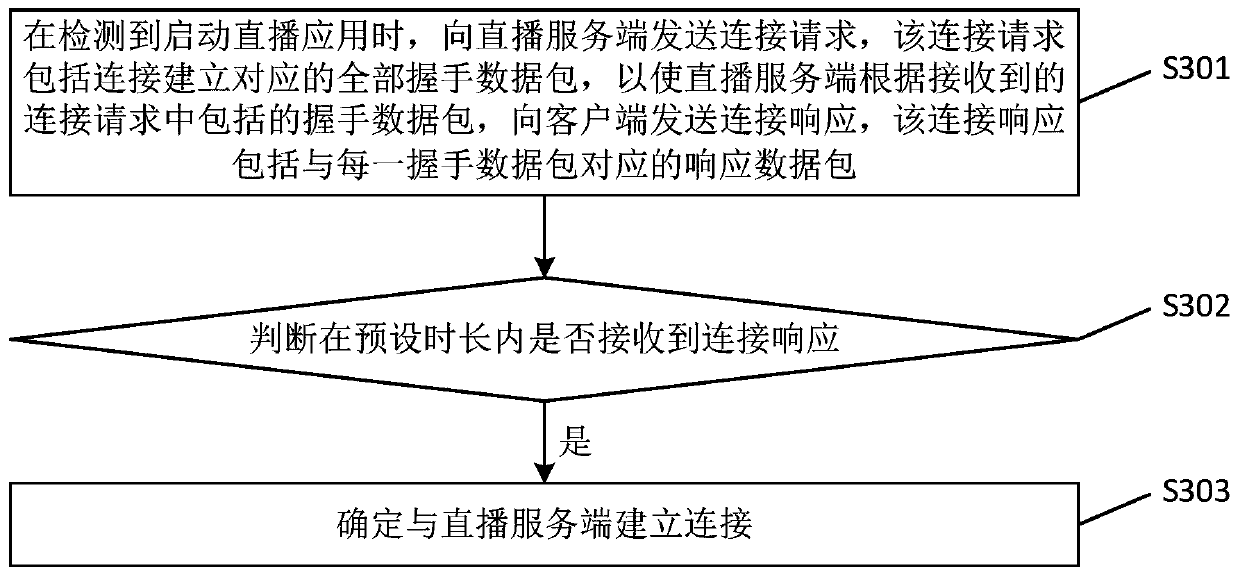
The embodiment of the invention provides a connection establishment method and device, electronic equipment and a storage medium. The scheme is as follows: a scheme is adopted; when the client detectsthat the live broadcast application is started; sending a connection request to a live broadcast server, wherein the connection request comprises all handshake data packets corresponding to connection establishment; and sending a connection request to the live broadcast server, thereby enabling the live broadcast server to send a connection response to the client according to the handshake data packets included in the received connection request, the connection response comprising response data packets corresponding to each handshake data packet, judging whether the connection response is received within a preset duration, If so, determining to establish a connection with the live broadcast server. Through the technical scheme provided by the embodiment of the invention, the handshake frequency is effectively reduced, so that the time consumption of a connection establishment process is reduced, and the video second-on time is shortened.
Owner:JOYME PTE LTD
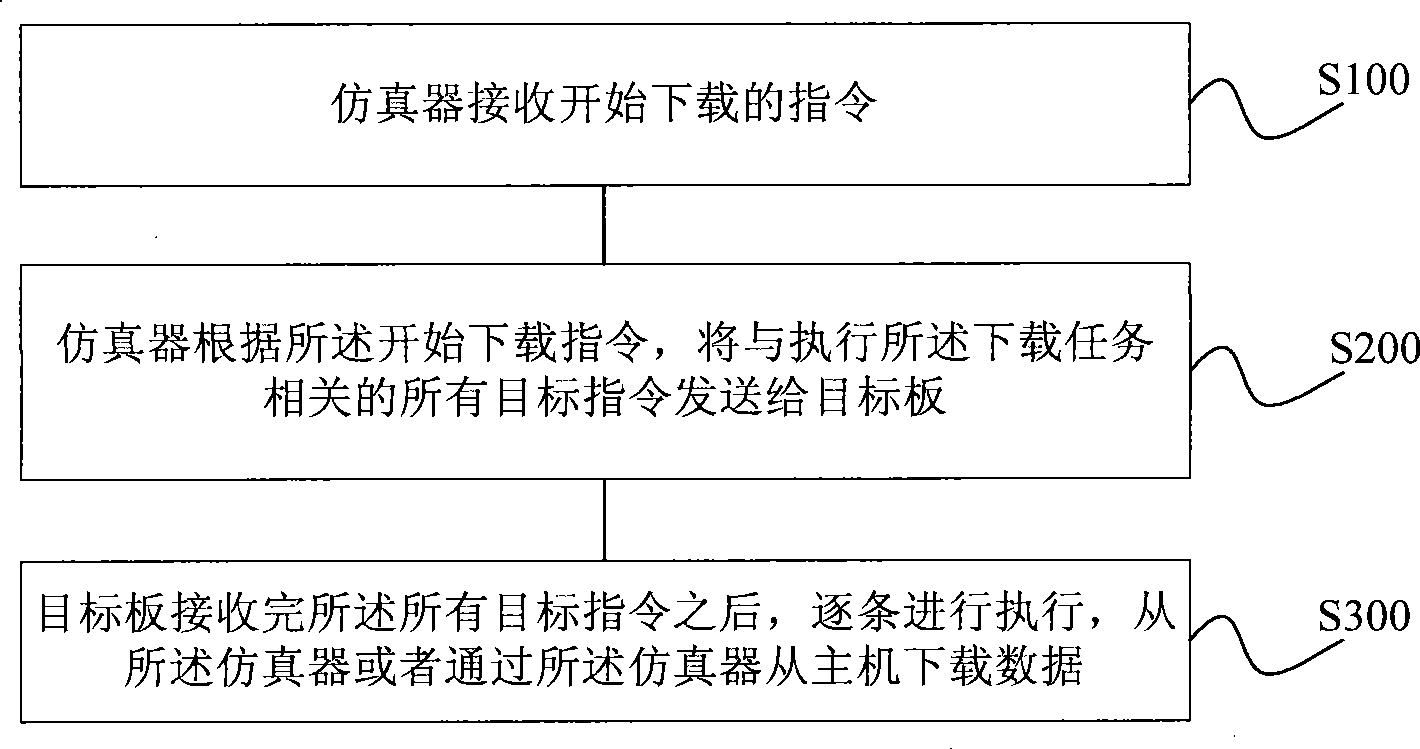
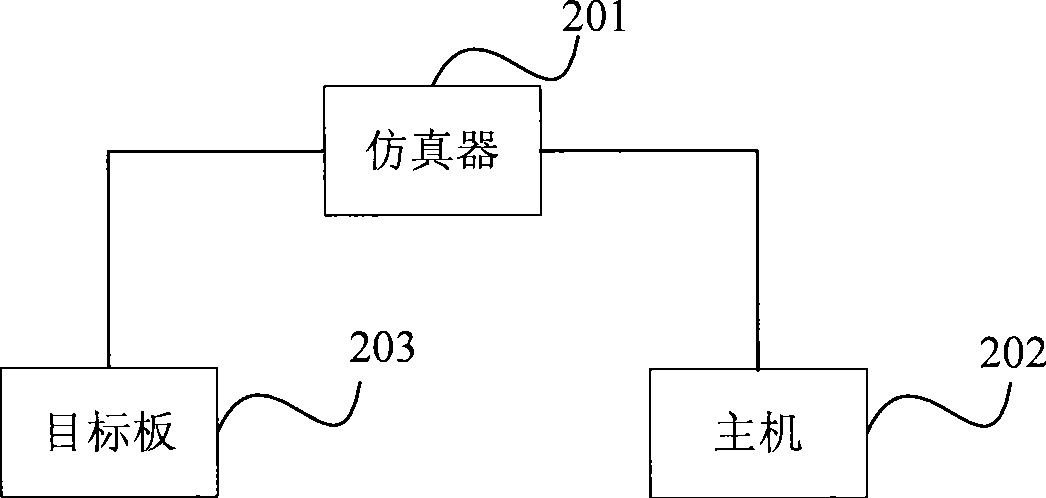
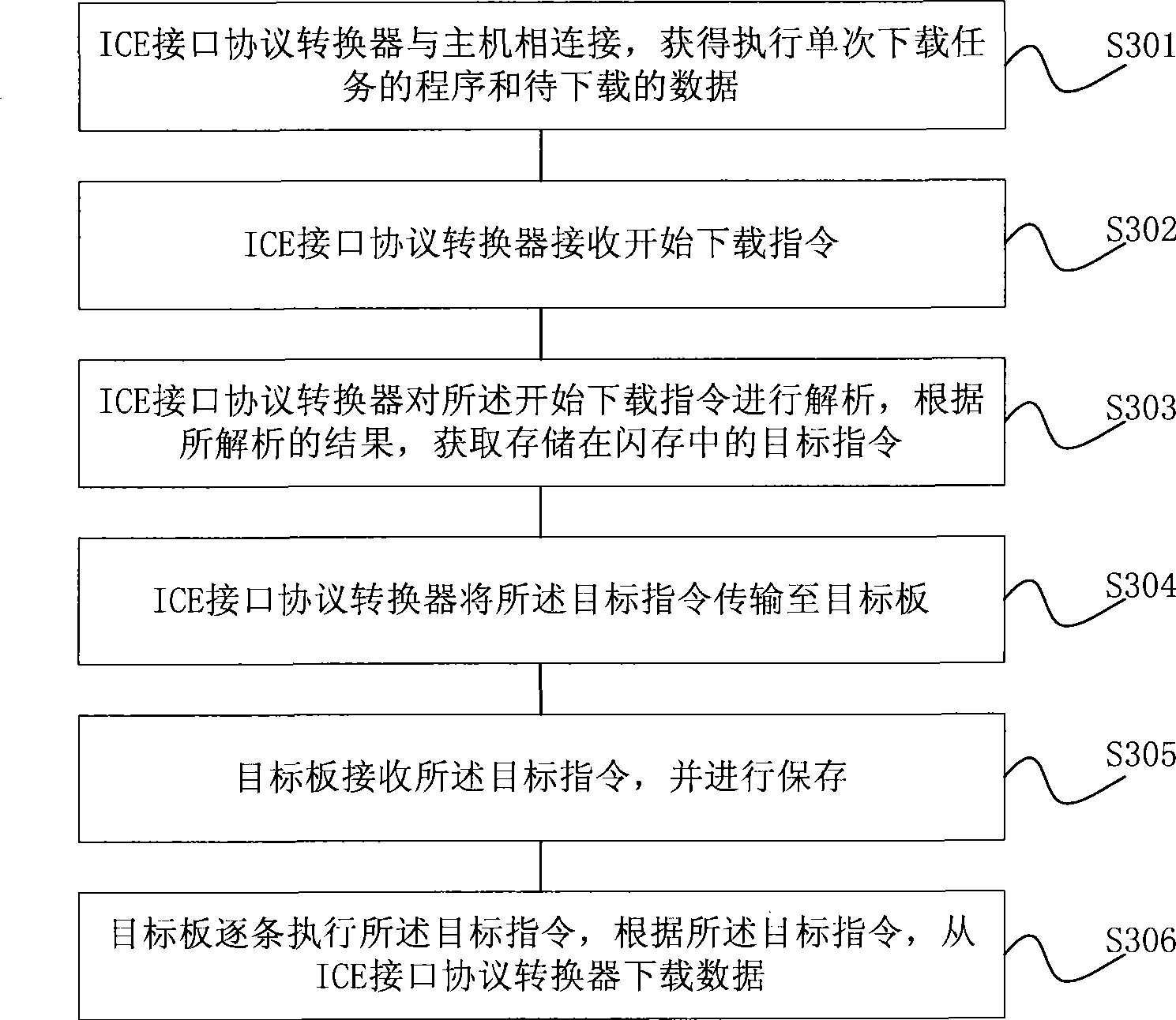
Simulation method
InactiveCN101482896AReduce the number of handshakesSave download timeSpecial data processing applicationsSimulationSimulation methods
The invention provides a simulation method, wherein implementing a single download task comprises: a simulator receives a start-to-download instruction; the simulator sends all object instructions interrelated to implementing the download task to an object board according to the start-to-download instruction; after receiving the all interrelated object instructions, the object board implements the instructions item by item. The simulation method of the invention firstly transfers the all object instructions implementing the single download task, then uses the object board to store and implement the instructions item by item to complete to download the data, thereby reducing the times of handshaking between the simulator and the object board, shortening the download time, and also improving the simulation efficiency and saving the bandwidth.
Owner:HUAYA MICROELECTRONICS (SHANGHAI) INC
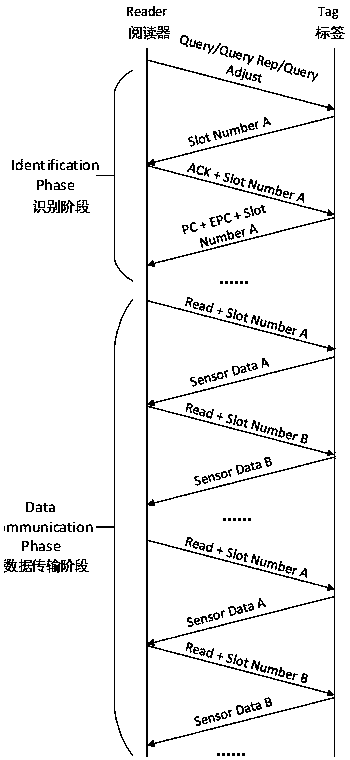
EPC protocol improvement method for improving CRFID data transmission rate
ActiveCN111343617AReduce the number of handshakesSimplify the communication processNetwork traffic/resource managementWireless network protocolsCommunications systemEngineering
The invention discloses an EPC protocol improvement method for improving the CRFID data transmission rate, and belongs to the technical field of wireless radio frequency recognition. The objective ofthe invention is to improve the data transmission rate in a passive communication system, simplify the communication process of a reader and a WISP label, and improve the throughput of the system by improving the existing EPC C1G2 protocol in a media access control layer. The method specifically comprises a stage in which a reader starts to identify by using a Query command, a stage in which the reader starts to transmit data by using a Read command, and a step in which the data transmission round number R is adjusted according to the proportion of the conflict time slot number in the total number of reply time slots of a single label in the recognition stage. A large number of tags are identified in the recognition stage, and the tags do not need to be identified again in different tag data transmission stages. According to the invention, the data transmission rate in the passive communication system is improved, the communication process is simplified, and the throughput of the system is improved.
Owner:TAIYUAN UNIV OF TECH
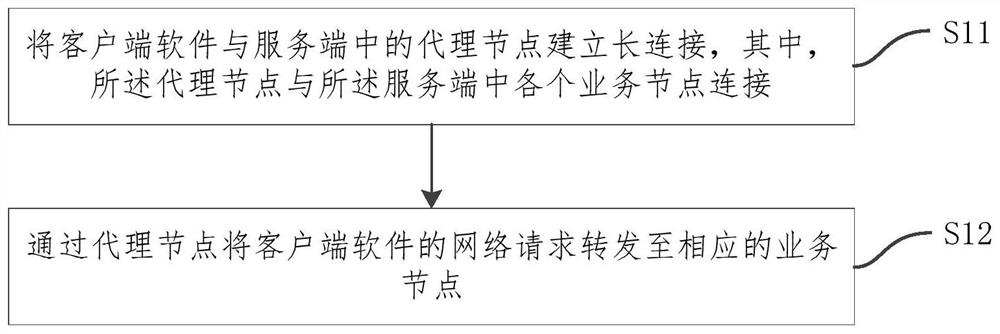
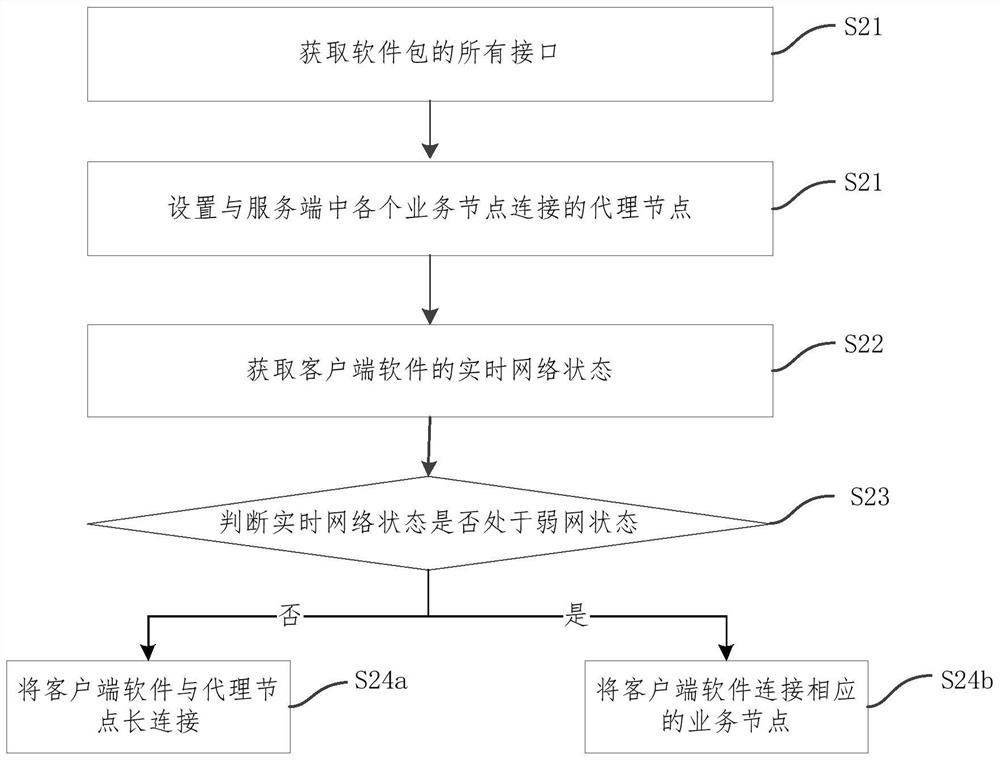
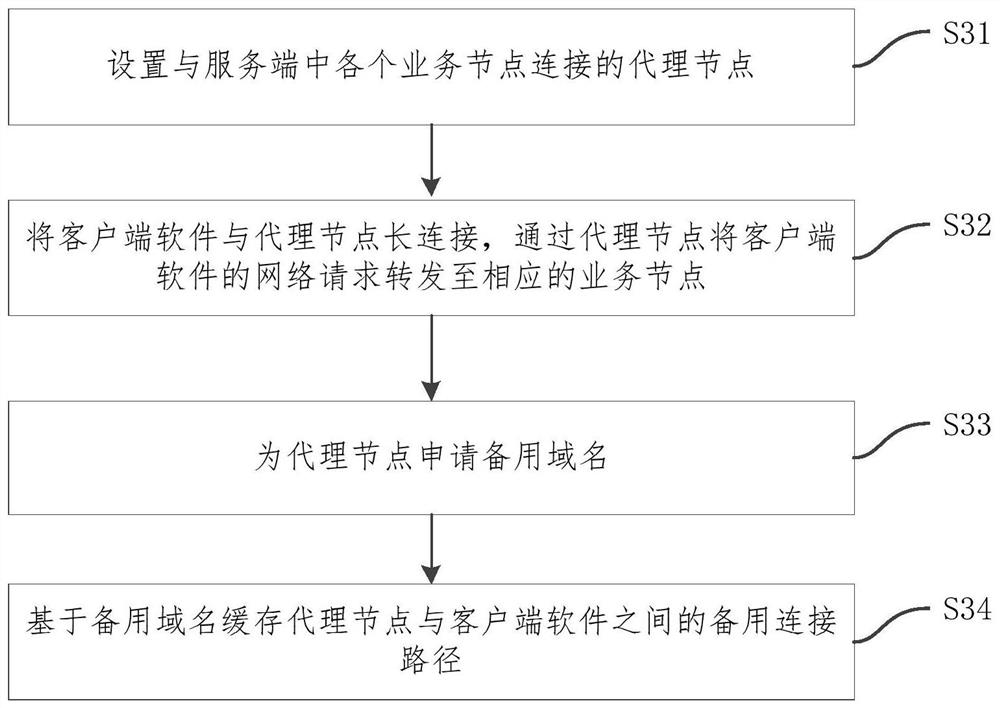
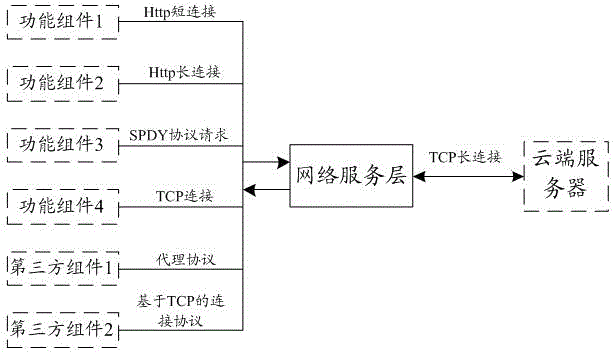
Client software network optimization method, system and device and storage medium
PendingCN111786809AReduce the number of handshakesImprove interaction efficiencyData switching networksSoftware networkEngineering
The invention relates to a client software network optimization method and system and a storage medium. The optimization method comprises the steps: establishing long connection between client software and a proxy node in a server, and forwarding a network request of the client software to corresponding service nodes through the proxy node, wherein the proxy node is connected with all the servicenodes in the server. Proxy nodes are added on the basis of the conventional architecture and direct interaction between the client software and the server is organized, so that the client software isonly in long connection with the proxy node, the network request is forwarded to each service node through the proxy node, the problem of repeated reconnection between the client software and the server is avoided on the basis of not modifying the original service logic, the data transmission efficiency is improved by reducing the handshake frequency, the optimization of the network performance iscompleted, and the user experience is improved.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
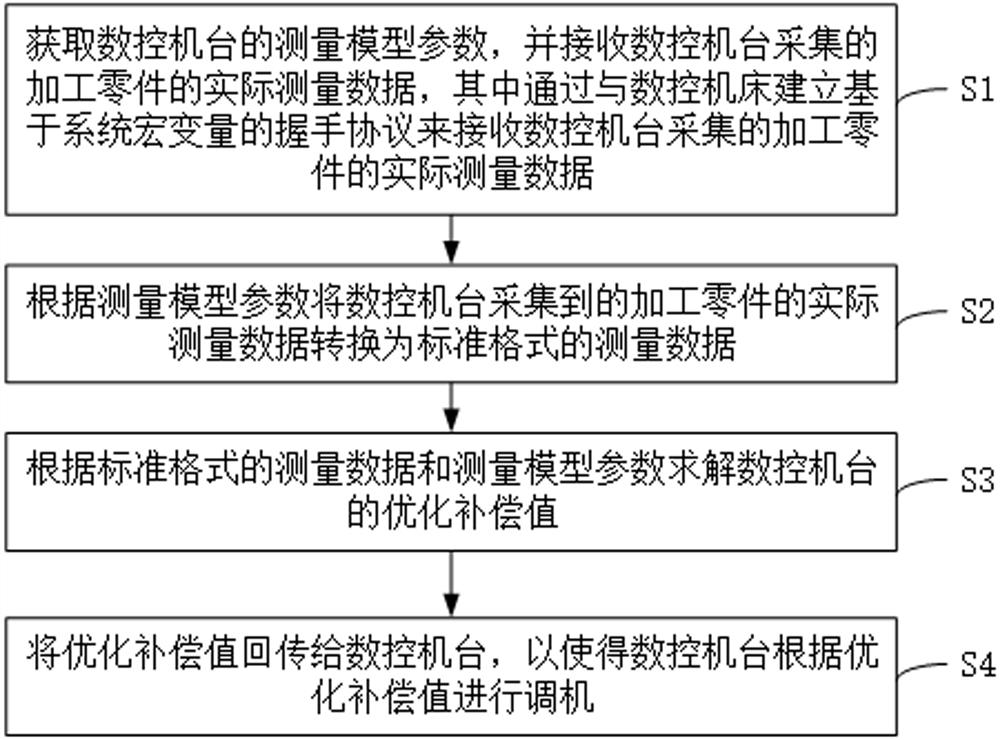
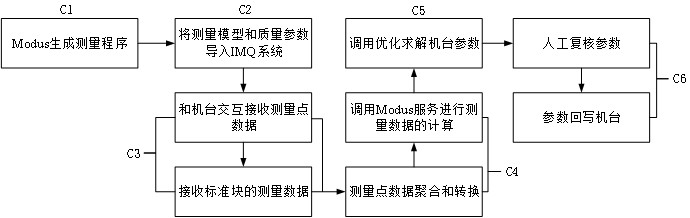
Intelligent debugging method and system based on handshake protocol
ActiveCN113589759ADoes not affect normal processingReduce machine set-up timeProgramme controlComputer controlNumerical controlMachine parts
The invention discloses an intelligent debugging method and system based on a handshake protocol, and the method is used for carrying out the intelligent debugging of at least one numerical control machine, and comprises the following steps: S1, obtaining the measurement model parameters of the numerical control machine, and receiving the actual measurement data of a machining part collected by the numerical control machine, wherein a handshake protocol based on a system macro variable is established with a numerical control machine table to receive actual measurement data, collected by the numerical control machine table, of a machined part; S2, according to the measurement model parameters, converting actual measurement data, collected by the numerical control machine, of the machined part into measurement data in a standard format; S3, solving an optimized compensation value of the numerical control machine according to the measurement data in the standard format and the measurement model parameters; and S4, transmitting the optimized compensation value back to the numerical control machine, so that the numerical control machine is adjusted according to the optimized compensation value. According to the invention, the problem of machine adjustment in the prior art is solved.
Owner:INREVO CO LTD
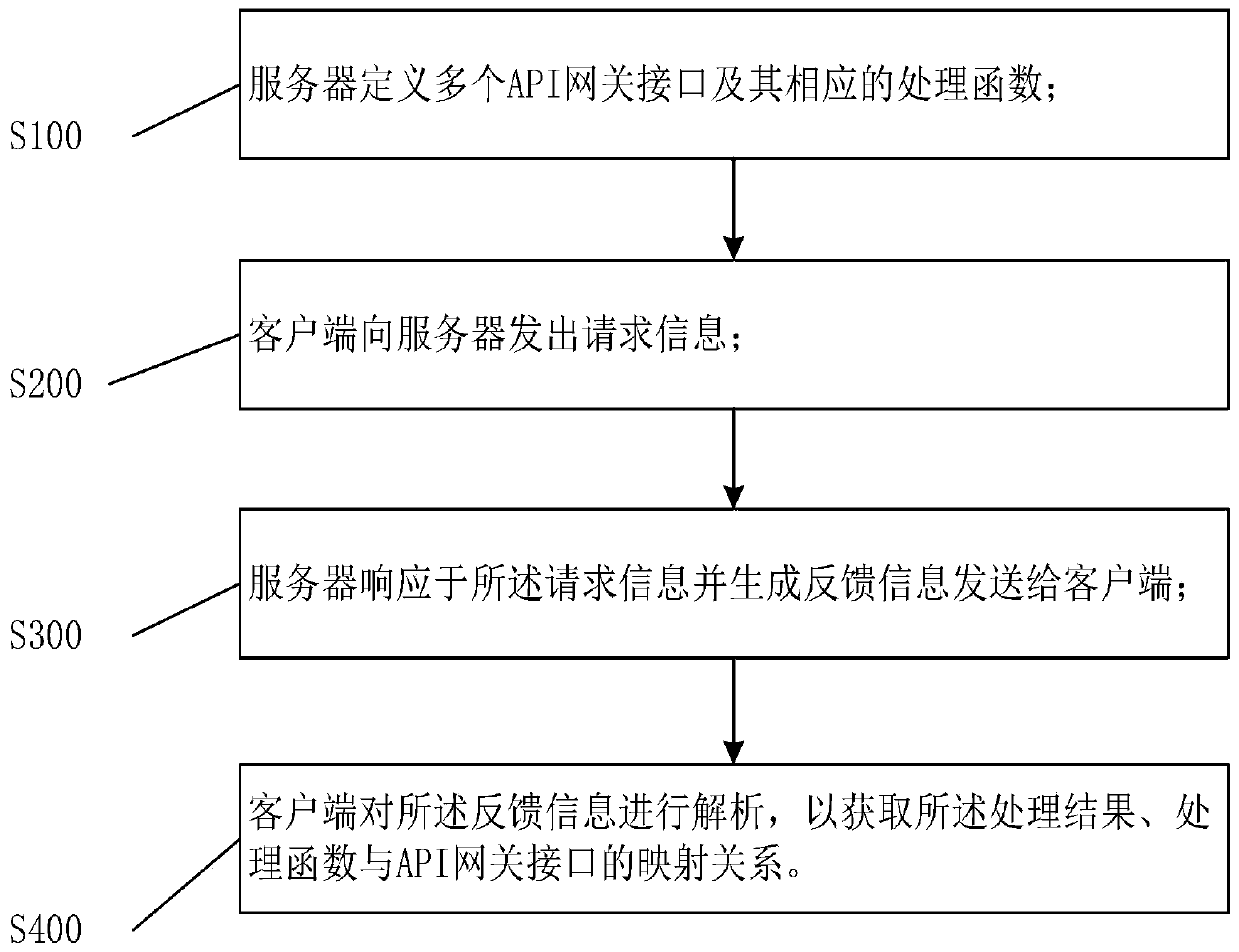
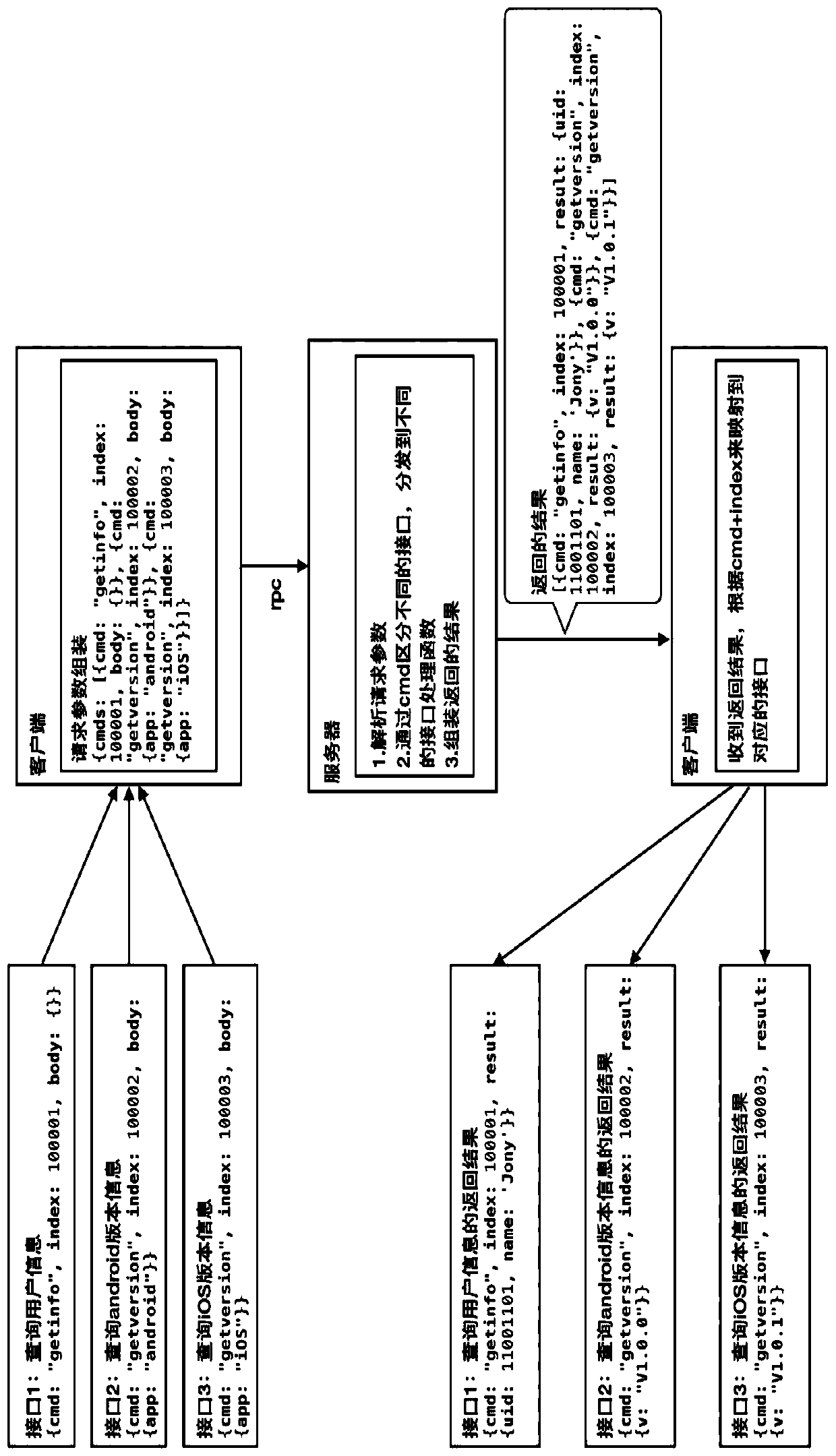
API gateway configuration method and API gateway system
InactiveCN111585879AReduce duplication of workAvoid error rateNetwork connectionsEngineeringHandshake
The invention discloses an API gateway configuration method and a gateway system. The API gateway configuration method comprises the following steps that S100, a server defines a plurality of API gateway interfaces and corresponding processing functions; S200, the client sends request information to the server; sS300, the server, in response to the request information, generates feedback information and sends the feedback information to the client; and S400, the client analyzes the feedback information to obtain a mapping relationship among the processing result, the processing function and the API gateway interface. According to the invention, the plurality of API gateway interfaces can correspond to the same route, and routes do not need to be added for the newly added API gateway interfaces so that repeated work is reduced, and the error probability is avoided; the data of the plurality of API gateway interfaces can be requested in one request of the client, and the data of the plurality of API gateway interfaces can be randomly combined, so that the network handshake frequency is reduced, and meanwhile, the purpose of improving the performance of the API gateway is also achieved.
Owner:北京静帆科技有限公司
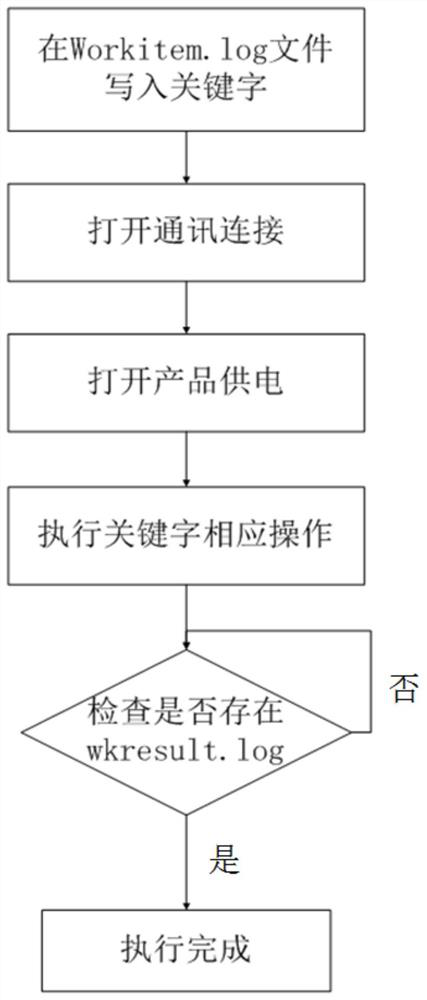
Engine control software testing method
PendingCN114265762AReduce the number of handshakesImprove access and transfer efficiencySoftware testing/debuggingSoftware simulation/interpretation/emulationControl softwareData packing
The invention relates to a software testing method, in particular to an engine control software testing method, and solves the technical problem that the data throughput capacity of an RS-232 serial port communication mode cannot meet the rapid data access requirement due to the fact that the baud rate cannot be increased under the condition that the serial port communication mode is ensured by an existing engine software testing method. Comprising the following steps of: writing a keyword in a Workitem.log file, supplying power after communication between test equipment and a product is established, executing a keyword instruction at the moment, running content indicated by the keyword, finishing checking whether the Wkresut.log file exists or not, and writing 'Done!' if the Wkresut.log file exists, and the like. Different functions are operated according to actual conditions, each function corresponds to a respective keyword, mode switching and data packaging downloading are carried out on instructions in a product, the number of handshake times between communication and the product is reduced, the whole access and transmission efficiency is improved by properly reducing data traffic on serial port communication, and the service life of the product is prolonged. Therefore, the purpose of improving the communication transmission efficiency of the RS-232 serial port is achieved.
Owner:XIAN AERO ENGINE CONTROLS
Method and system for long connection based on routing layer
ActiveCN104009938BReduce the number of handshakesLower latencyData switching networksUnified communicationsComputer terminal
The present application discloses a method and system for a persistent connection based on a routing layer, including: in a routing-based local area network, receiving access requests sent by multiple terminals, generating at least one persistent connection request and sending it to a server; After responding to the persistent connection request and establishing the persistent connection, performing protocol adaptation processing on the access requests sent by multiple terminals to the server through the persistent connection, and receiving feedback from the server through the persistent connection the request data; monitor the amount of access requests of the terminal and combine the established transmission capacity of the long connection to control the number of the long connection. The present application solves the problem that in a routing-based local area network environment, long connections are established by terminals without unified communication management and routing can only establish short connections.
Owner:ALIBABA (CHINA) CO LTD
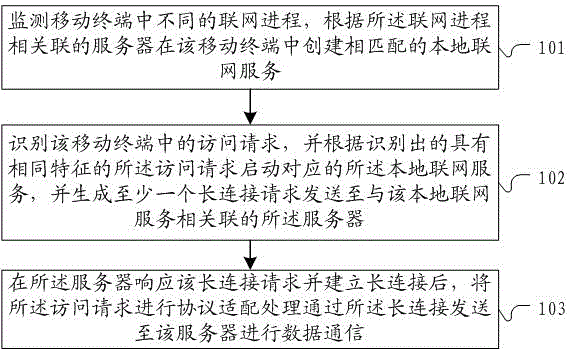
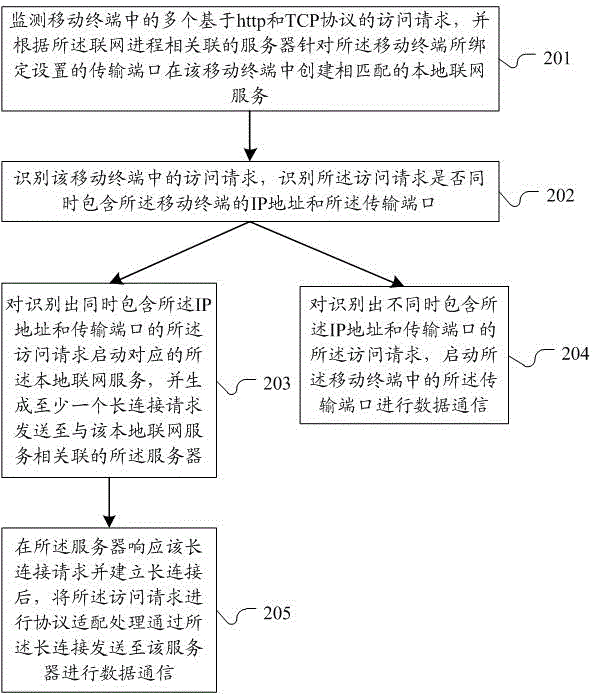
Method and system for connecting and communicating with the same kind of networking request in a mobile terminal
ActiveCN104010001BReduce workloadAvoid repeated callsData switching networksCommunications systemNetwork connection
The invention discloses a method and system for carrying out connection communication on same networking requests in a mobile terminal. The method comprises the steps of monitoring different networking progresses in the mobile terminal, establishing matched local networking services in the mobile terminal according to servers related to the networking progresses, recognizing access requests in the mobile terminal, starting the corresponding local networking serves according to the recognized access requests with the same characteristics, generating and sending at least one long connecting request to the server related to the local networking services, carrying out protocol adaptation processing on the access requests after the server responds to the long connecting request and establishes the long connection, and sending the access requests to the serve through the long connection so that data communication can be carried out. The method and system solve the problem that the same networking requests issued by different applications and threads in the mobile terminal cannot carry out network connection communication through a unified networking port.
Owner:ALIBABA (CHINA) CO LTD
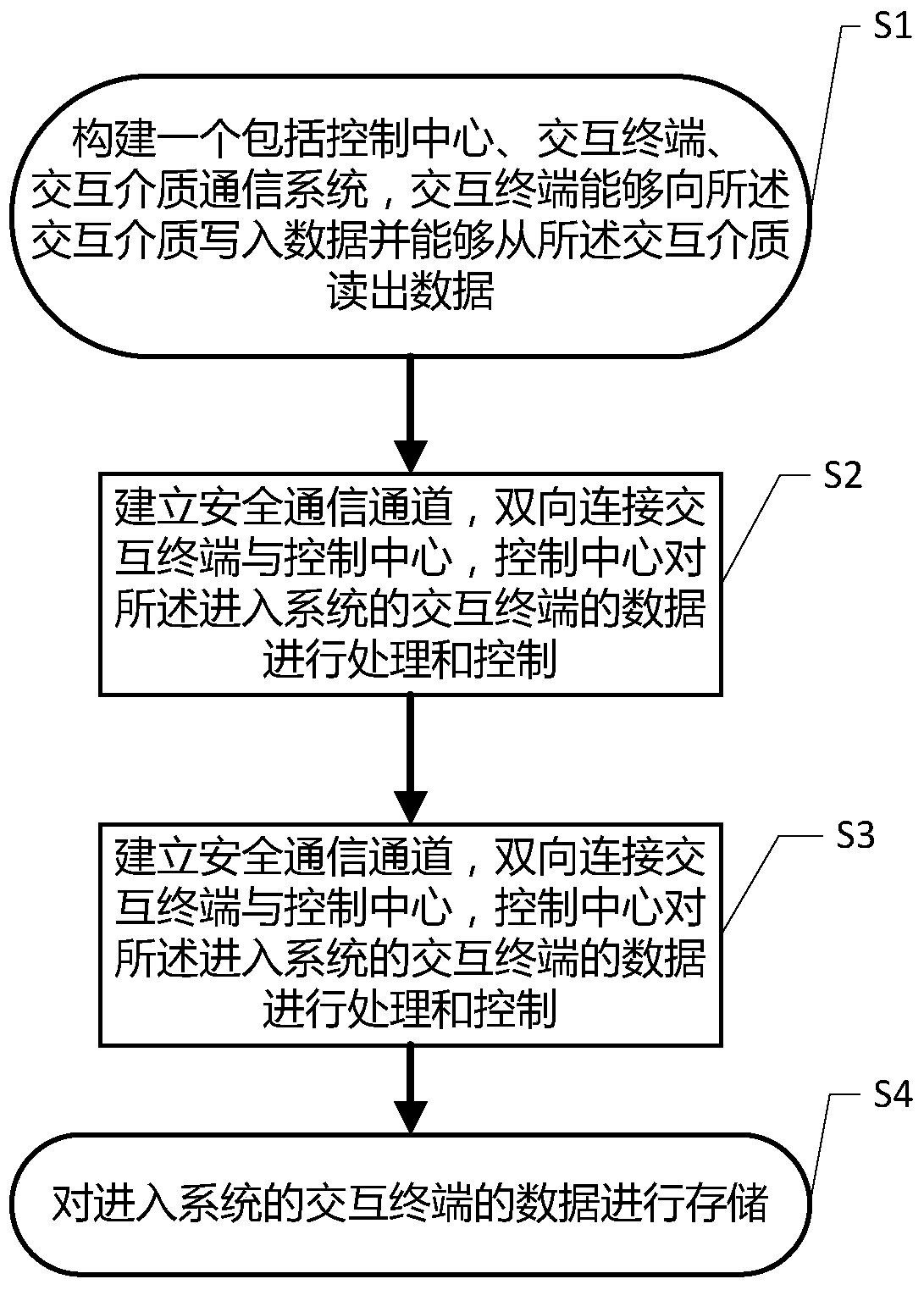
A data communication and storage method
InactiveCN105491015BReduced settling timeEliminate structural differencesTransmissionCommunications systemComputer compatibility
A data communication and storage method, comprising the following steps: (1) constructing a communication system including a control center, an interactive terminal, and an interactive medium, where the interactive terminal can write data to the interactive medium and can read data from the interactive medium (2) establish a secure communication channel, bidirectionally connect the interactive terminal and the control center, and the control center processes and controls the data of the interactive terminal entering the system; (3) the control center completes the security verification of the interactive terminal through the secure communication channel, If the interactive terminal is not safe, prevent the data of the interactive terminal from entering the system, and if the interactive terminal is safe, allow the data of the interactive terminal to enter the system; (4) store the data of the interactive terminal entering the system. This method can establish a secure communication channel more quickly, increases the difficulty of cracking digital certificates, and can enhance the security and reliability of the data communication process. At the same time, this method has good compatibility and read-write efficiency in the data storage process. .
Owner:国网山东潍坊市寒亭区供电公司 +1
A Realization Method of IP Address Negotiation Based on PPP Protocol
ActiveCN111092961BSolve the problem of negotiationDoes not affect the main functionWide area networksNetworked systemNetwork communication
The invention discloses a method for realizing IP address negotiation based on the PPP protocol. Each node of the fully connected network is configured with the same address pool for dynamic negotiation. The main function of the negotiation is realized in the plug-in, and the calling party is responsible for the IP address Assignment of address pairs. Compared with the prior art, the positive effect of the present invention is: the present invention proposes a method of using PPP-IPCP enhanced plug-in for the situation that the existing traditional PPP-IPCP negotiation method cannot satisfy the point-to-point full-connection network communication requirements , satisfying that in a network system, any two communicating parties can automatically assign IP addresses through dynamic negotiation, without causing address conflicts between nodes, and realizing message intercommunication.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
A Method of Underwater Acoustic Media Access Control Based on Reservation Scheduling Mechanism
ActiveCN109688554BSolve conflictsIncrease profitPower managementBroadcast service distributionData packData transmission time
The invention provides a hydroacoustic media access control method based on a reservation scheduling mechanism. After a fixed node with a data transmission requirement receives an ND packet of a Sinknode, an RTS packet is sent to the Sink node for carrying out data transmission reservation; and the Sink node calculates information of propagation delay and the like according to information in theRTS packet, and then calculates data transmission time of each node, so that data transmission scheduling of each node is completed. The conflict problem of the data packets is effectively avoided based on the reservation scheduling mechanism, the handshaking time between the nodes is shortened, the channel utilization rate is obviously improved, and the data transmission efficiency is improved; and in addition, the nodes do not need to be subjected to time synchronization in advance, so that the implementation requirements of a hydroacoustic communication network are remarkably reduced.
Owner:INST OF DEEP SEA SCI & ENG CHINESE ACADEMY OF SCI
Intelligent tuning method and system based on handshake protocol
ActiveCN113589759BDoes not affect normal processingReduce machine set-up timeProgramme controlComputer controlNumerical controlData transformation
The invention discloses a method and system for intelligent machine tuning based on a handshake protocol, which is used for intelligent machine tuning of at least one numerical control machine. The method includes the following steps: S1: Acquiring the measurement model parameters of the numerical control machine, And receive the actual measurement data of the processed parts collected by the CNC machine, wherein the actual measurement data of the processed parts collected by the CNC machine is received by establishing a handshake protocol based on the system macro variable with the CNC machine; S2: According to the measurement Model parameters convert the actual measurement data of the processed parts collected by the CNC machine into measurement data in a standard format; S3: Solve the optimized compensation value of the CNC machine according to the measurement data in the standard format and the measurement model parameters; S4: The optimized compensation value is sent back to the numerical control machine, so that the numerical control machine performs machine adjustment according to the optimized compensation value. The invention solves the problem of "adjustment" in the prior art.
Owner:INREVO CO LTD
A High Coding Opportunity Bidirectional Access Method Based on Cache Information Assistance
ActiveCN108738100BTake advantage ofImprove coding opportunitiesError prevention/detection by using return channelBroadcast service distributionAccess methodNetwork code
The present invention proposes a two-way access method with high coding opportunities based on cache information assistance, which is mainly applied in two-hop relay networks, and mainly includes two stages of code matching for sending control messages and data transmission after matching. Three new mechanisms: "replacement from four-way handshake to two-way handshake", "cache information assists in improving coding opportunities", "updating virtual buffer area by modifying frame format"; the first and second new mechanisms work in the coding matching stage , the third new mechanism works in the data transmission stage. By using the above three new mechanisms, the new access method proposed by the present invention can reduce the unnecessary control overhead of the message interaction process, and can effectively improve the coding opportunities, so that the overall Make full use of network coding technology to achieve the purpose of reducing the average delay of data frames and increasing the throughput of the network.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
High coding opportunity bidirectional access method based on cache information assistance
ActiveCN108738100ATake advantage ofImprove coding opportunitiesError prevention/detection by using return channelBroadcast service distributionAccess methodNetwork code
The invention provides a high coding opportunity bidirectional access method based on cache information assistance. The method is mainly applied to a two-hop relay network, and mainly comprises a coding matching stage for sending a control message and a data transmission stage after the matching; three mechanisms as follows are adopted: four handshakes are changed as twice handshakes, the cache information assistance improves the coding opportunity, and the virtual cache area is updated by modifying a frame format; the first new mechanism and the second new mechanism are worked at the coding matching stage, and the third new mechanism is worked at the data transmission stage. By using above three new mechanisms, the new access method provided by the invention can reduce unnecessary expenditure in the unnecessary message interaction process, the coding opportunity can be effectively improved, thereby realizing the aims of reducing the data frame average delay and increasing the networkthroughput by sufficiently utilizing the network coding technology on the whole.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
A method for establishing a secure channel, its data protection method, and a method for updating the secret key of the secure channel
ActiveCN104683359BReduce consumptionReduced settling timeKey distribution for secure communicationSecure communicationTerminal server
The invention provides a method for establishing a safe channel, a data protection method thereof, and a method for updating a secret key of the safe channel. During the handshake process of establishing a secure communication channel between the terminal and the server, both parties check whether the secure communication channel has been successfully established and the key has not changed, and check whether the other party's certificate is cached. If the relevant data has been cached, the data and process transmitted in the handshake process between the two parties can be reduced, so as to achieve the characteristics of the packet domain communication of the mobile communication network and ensure the data security in the data communication process between the terminal and the server. Minimize the establishment time of the two parties to establish a secure communication channel, and achieve the purpose that the two parties do not have to maintain the TCP chain all the time.
Owner:成都三零瑞通移动通信有限公司
Cross-wide area network data return method, device, computer equipment and storage medium
ActiveCN108418874BImprove return efficiencyReduce the number of handshakesTransmissionDatabase serverPassword
The application discloses a cross-wide area network data return method, device, computer equipment and storage medium. The method includes: adding a pipeline class in the java encapsulation class called by the Hadoop server, and constructing a function for passing in the Redis cluster object and password in the pipeline class; the pipeline class synchronously reads the data to be returned in the Hadoop server, Obtain Redis cluster information; obtain the current Redis cluster information through the pool object; if the current Redis cluster information is different from the previous Redis cluster information, submit the data to be imported back stored in the pipeline class to the Redis database according to the current Redis cluster information server. In this method, the pipeline class submits batch data to the Redis database server only when the Redis cluster information is updated, which reduces the number and time of remote TCP handshakes and improves the efficiency of data return.
Owner:PING AN TECH (SHENZHEN) CO LTD
Data Security Communication Method
InactiveCN105430017BReduce the number of handshakesReduced settling timeTransmissionSecure communicationCommunications system
Owner:STATE GRID SHANDONG LINQU POWER SUPPLY +2
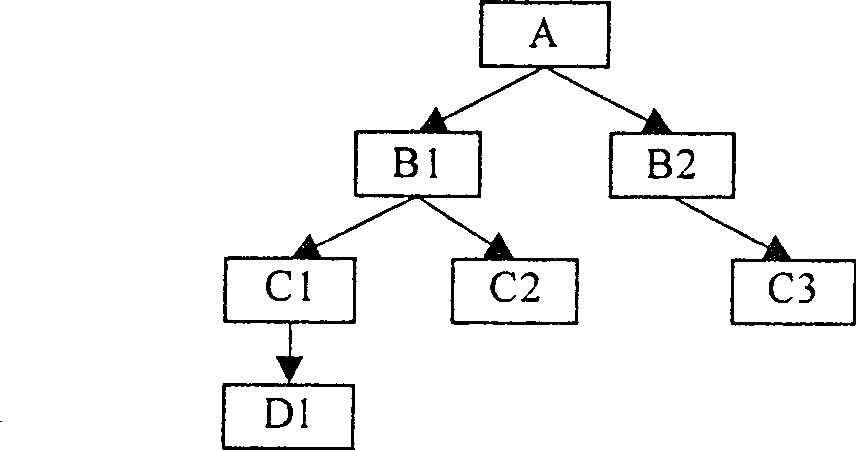
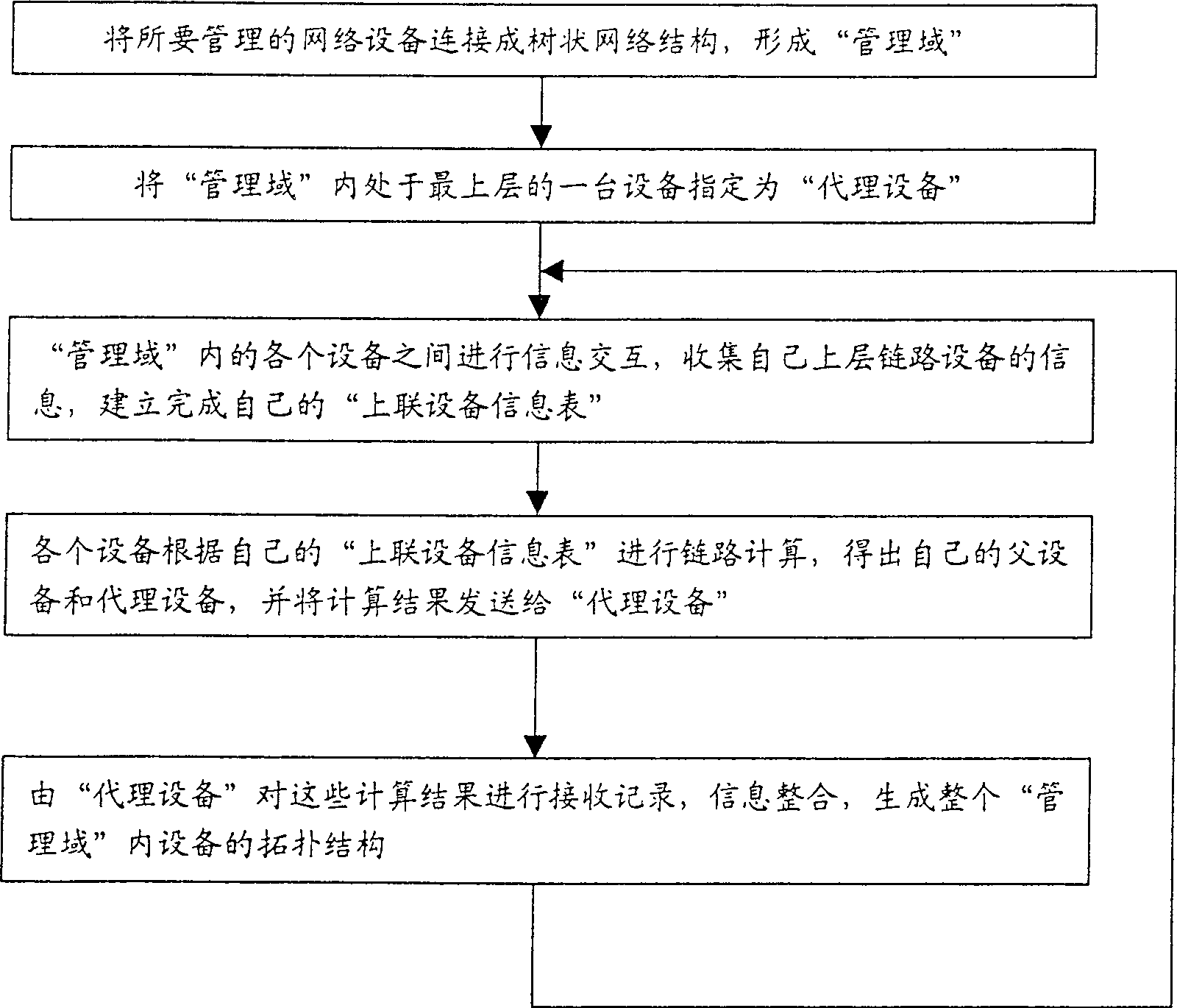
Method for rapidly forming dendriform topology structure of network equipment
ActiveCN100514928CImprove production efficiencyEasy loadingStar/tree networksAdministrative domainNetwork structure
The invention discloses a method for quickly generating a tree-like topology structure of network equipment. The method comprises the following steps: 1. Connecting the network equipment to be managed into a tree-like network structure and considering it as a "management domain"; 2. .Designate the topmost device in the "management domain" as a "proxy device"; 3. The devices in the "management domain" exchange information, collect information about their own upper-layer link devices, and enable each device to establish Complete your own "uplink device information table"; 4. Each device performs link calculation according to its own "uplink device information table", obtains its own parent device and proxy device, and sends the calculation result to the "proxy device" ;5. The "agent device" records and integrates the calculation results of each device in the domain to generate the topological structure of the devices in the entire "management domain"; 6. Repeat steps 3 to 5 to maintain the topology regularly and troubleshooting.
Owner:CHINA GREATWALL TECH GRP CO LTD
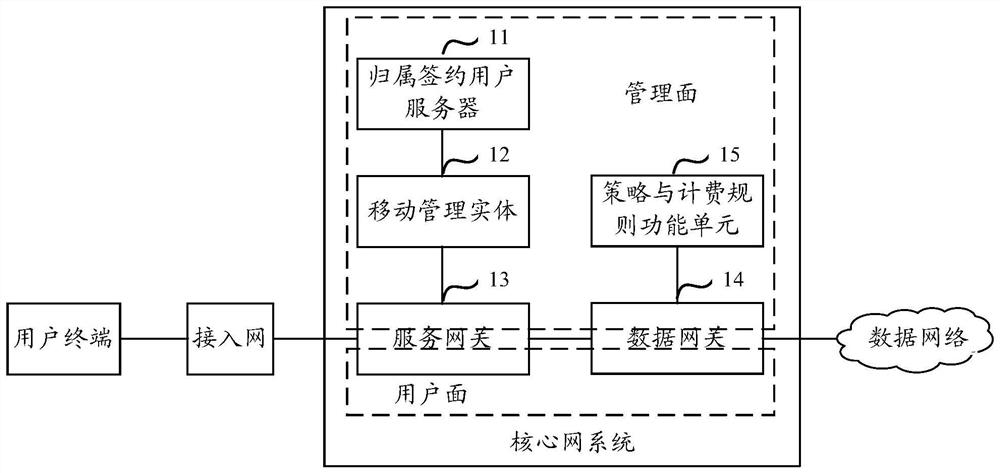
A core network system based on non-stack protocol for b5g
ActiveCN108650125BEnhanced interactionReduce overheadNetwork topologiesData switching networksNetworked systemDistributed computing
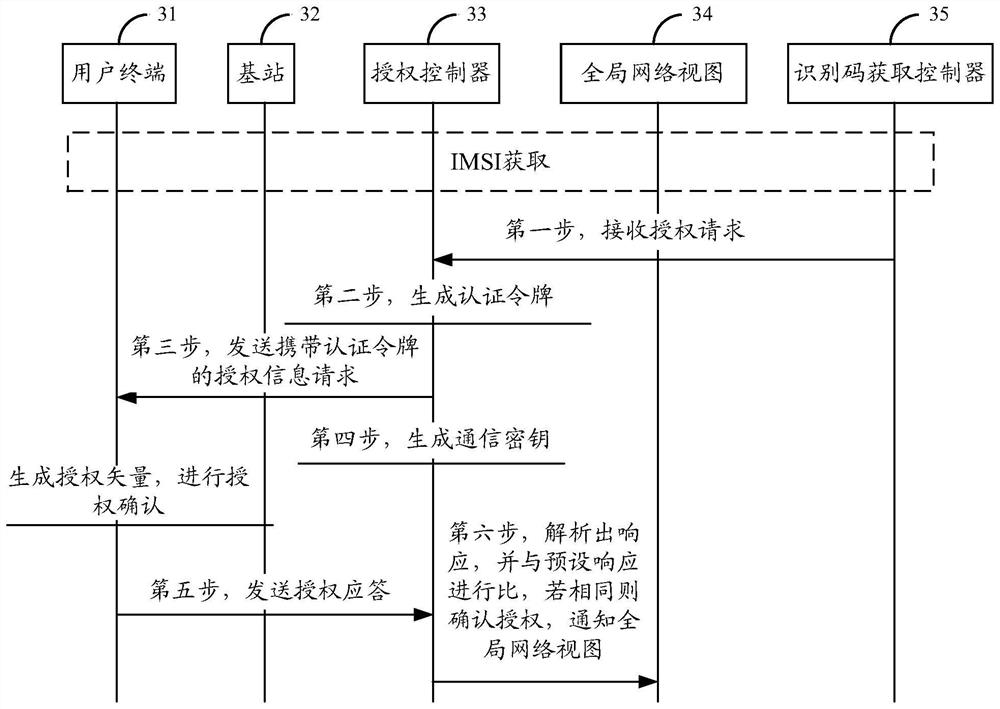
The present application relates to the field of communication technology, and in particular to a B5G-oriented core network system based on a non-stack protocol, which is used to solve the problems of large signaling overhead and delay in the prior art. This application mainly includes: a global network database, a control plane, a management plane, and a user plane. Among them, by introducing the non-stack protocol framework into the 5G-oriented core network system, reorganizing the network elements in the network system, decoupling the control of the network The control plane and the user plane integrate the control function logic in the core network system into the control plane. At the same time, the control plane and the data plane are separated. The control function logic is centralized and the data plane is flattened to simplify signaling interaction and reduce The purpose of delaying the process and reducing network signaling overhead.
Owner:TSINGHUA UNIV
Method and device for improving dequeuing efficiency in queue management
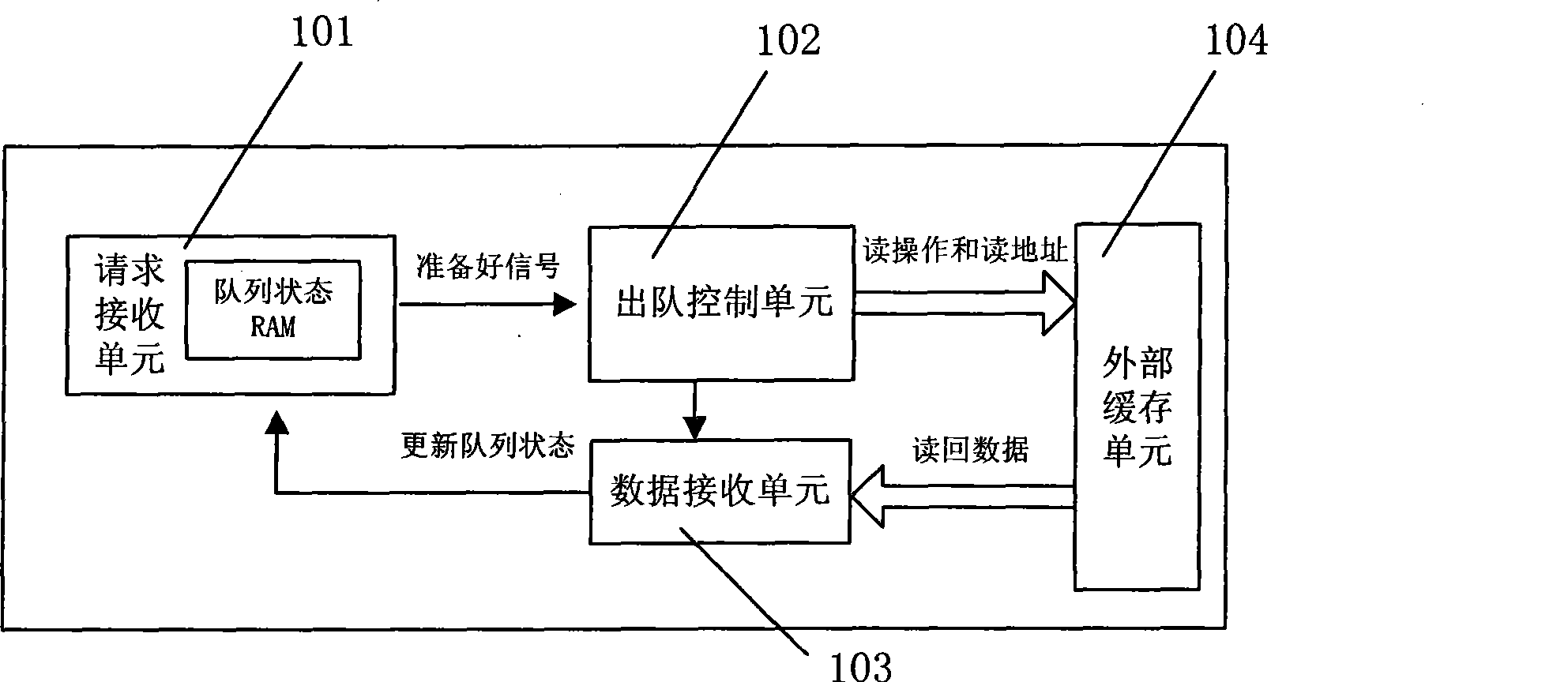
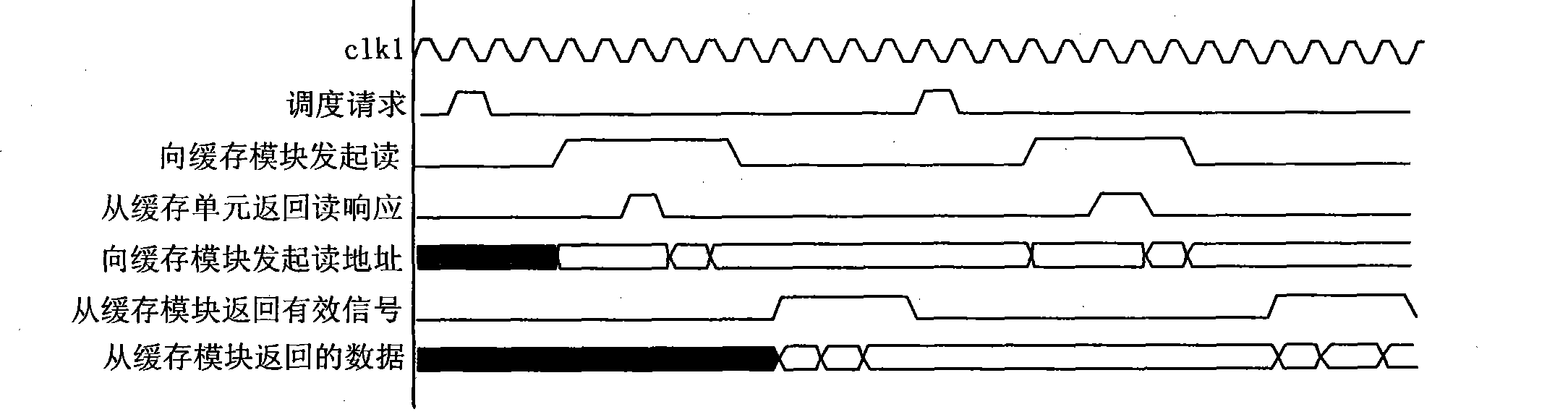
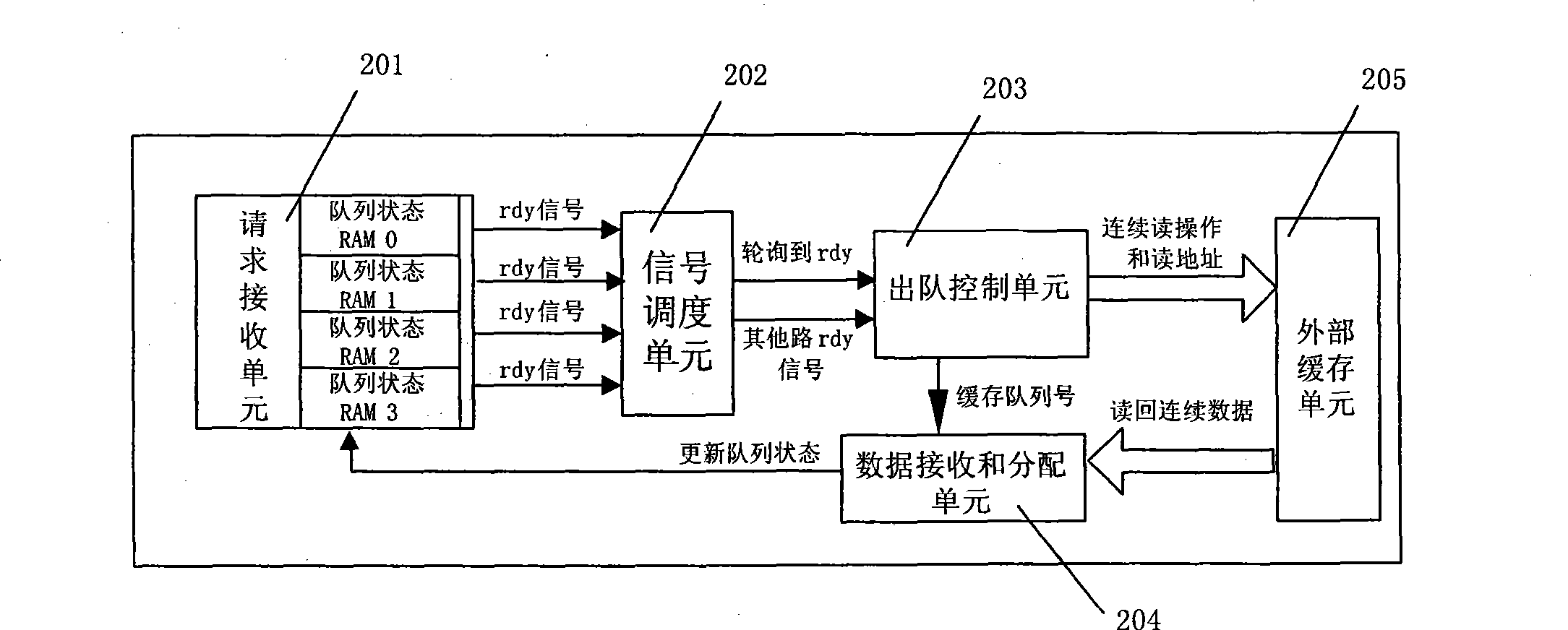
ActiveCN101656658BReduce the number of handshakesEase internal arbitrationData switching networksControl cellEngineering
The invention discloses a device and a method for improving the dequeuing efficiency in queue management, wherein the device comprises a request receiving unit, a signal scheduling unit, a dequeuing control unit, an external buffer unit and a data receiving and allocation unit. The device sets one queue state storage unit for each request and simultaneously processes a plurality of queue requests;and the device adopts a method for continuously sending read operations to the external buffer unit so that the external buffer unit can process a plurality of the queue requests once so as to avoideach request from applying for operations from the buffer unit, save the buffer response time and the data-reading time, and simultaneously lighten the internal arbitration of the external buffer unitand greatly improve the working efficiency because the handshake number to the external buffer unit is reduced, thereby promoting the processing performance of a chip and having a certain applicationvalue to systems with high speed requirement.
Owner:ZTE CORP +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com