Data secure communication method
A communication method and data security technology, applied in the field of data communication, can solve the problems such as the inability of the owner to modify the password actively, the data is not completely consistent, and the lack of initiative, etc., to shorten the establishment time, improve the speed of the handshake protocol, and reduce the power consumption. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
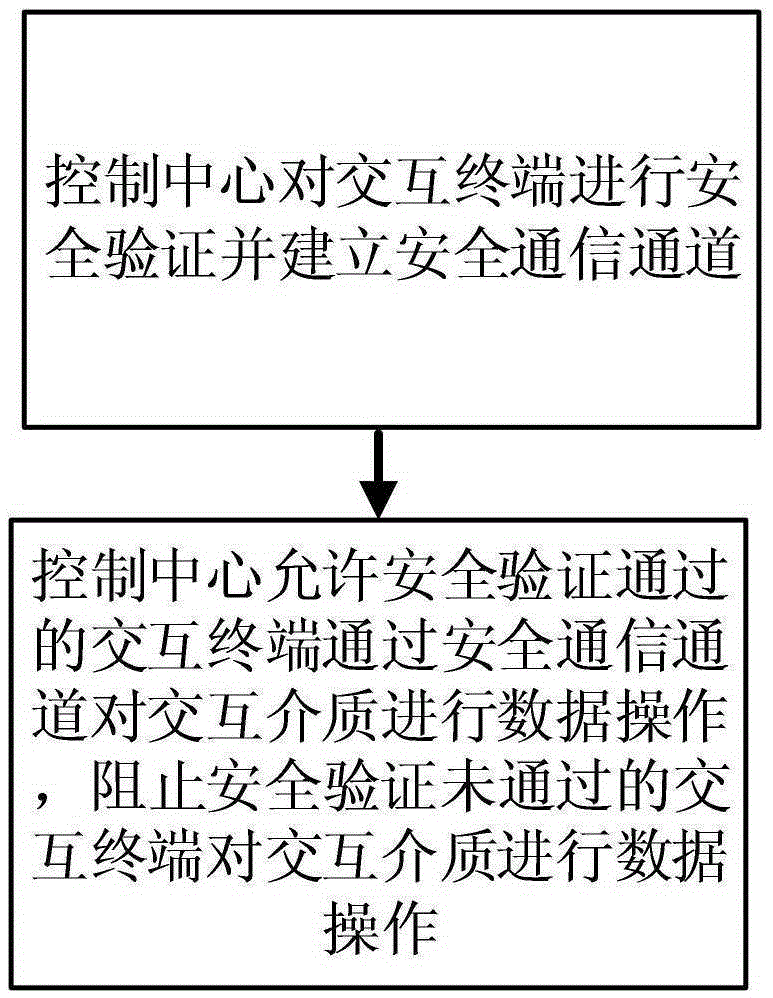
[0042] see figure 1 , the data security communication method of the present embodiment, comprises the following steps:
[0043] A data security communication method, comprising the steps of:
[0044] 1) The control center performs security verification on the interactive terminal and establishes a secure communication channel; specifically includes the following steps:
[0045]101) The interactive terminal queries the cached session connection information with the control center, uses the digest algorithm cached in the session connection information to perform digest calculation on the session key, and writes the session number and the digest calculation result into the connection application packet;
[0046] 102) The interactive terminal queries the cached control center certificate, and writes the serial number of the control center certificate and the serial number of the interactive terminal certificate into the connection application packet;
[0047] 103) The interactiv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com