Safety transmission method in telecommunication network
A telecommunications network and security technology, applied in security devices, transmission systems, digital transmission systems, etc., to achieve the effect of reducing the number of handshakes, making attacks difficult, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The invention can be applied to any telecommunication network. In the following, the present invention will be described in detail by taking a mobile station operating in a digital GSM mobile communication system and communicating with applications located inside or outside the GSM network as an example.
[0030] The main embodiment of the present invention will be described in detail below with reference to FIGS. 2 , 3 and 4 .
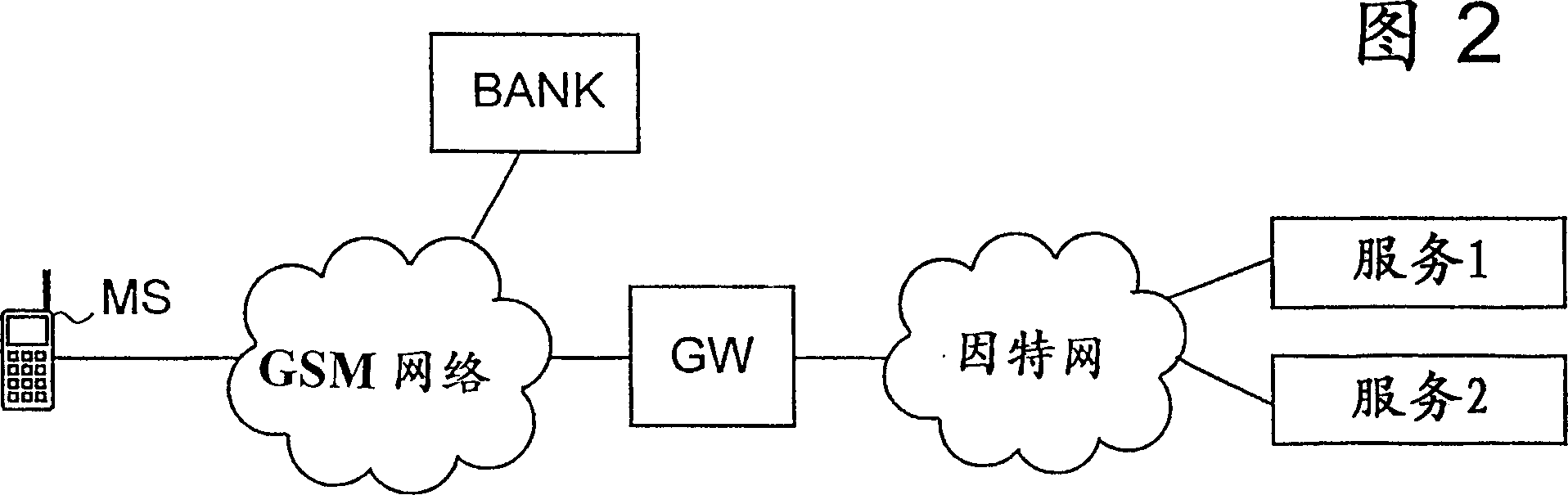
[0031] Figure 2 shows some examples of the aforementioned connections. The mobile station MS contacting the bank server first performs a handshake according to the prior art, during which the MS and the bank can authenticate each other and exchange required session key information. According to the invention, the mobile station and the bank server negotiate and agree on appropriate intervals for recalculating security parameters for providing confidentiality, data integrity and authentication during communication, eg during a handshake. For e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com